Don't wanna be here? Send us removal request.
Text
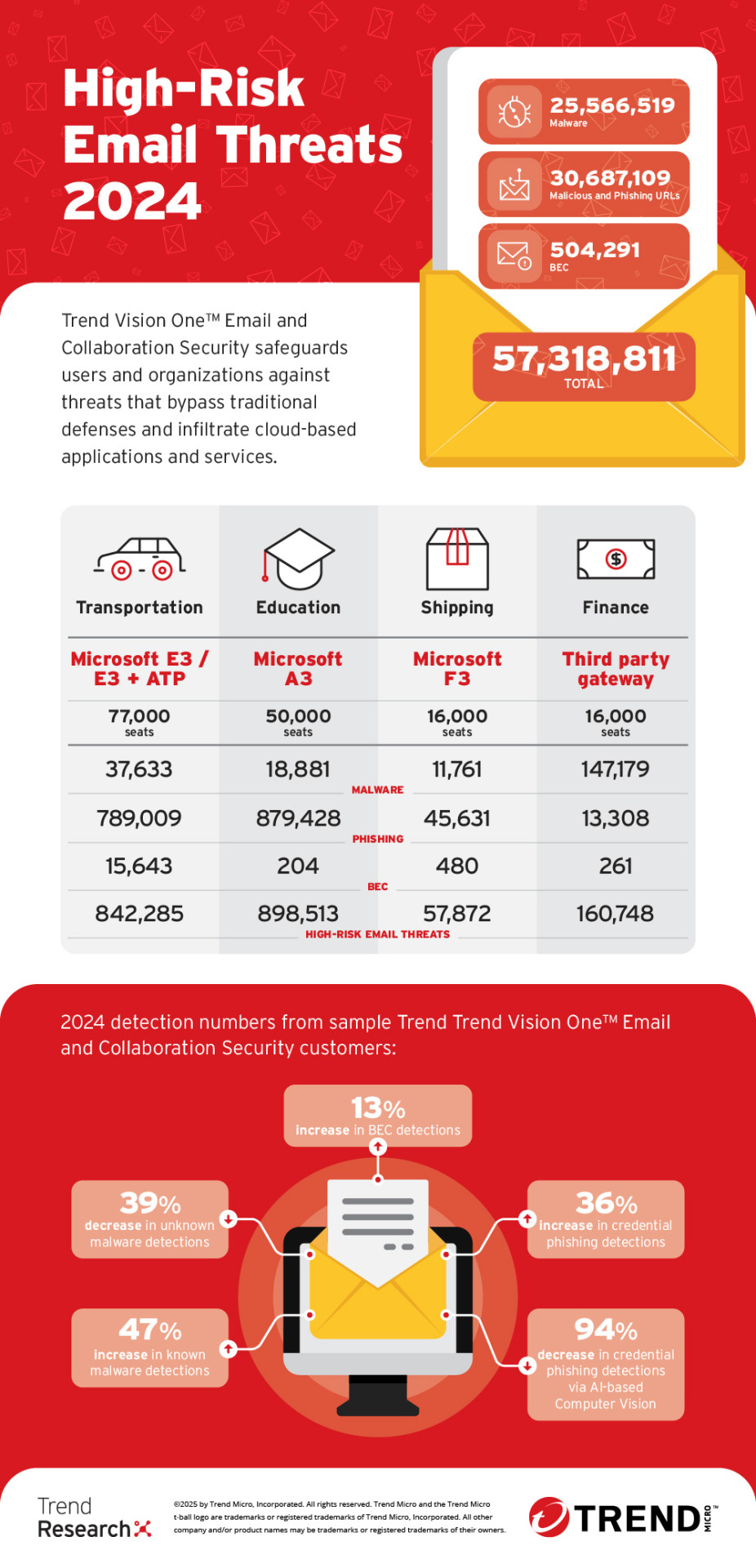
The continuing threat from email based attacks
It is relatively easy for cybercriminals to obtains tool and support to instigate a Phishing or Quishing email attack campaign. Their challenge is to find enough targets to make the attacks work and like the other criminals in their space, the spammers, scammers and BECers it is a numbers game and luckily for them there is enough compromised data out there to help them create a lucrative…
View On WordPress
0 notes
Text
A consolidated list of 2025 predictions
Over the years I have consolidated a few “next year” predictions as it is interesting, well at least for me, to see how accurate the predictions are but also how geopolitical and technological developments can impact the security industry and therefore the outcomes of the predictions. If you want to look back in time, my consolidated list for 2011 click here The 2025 predictions are below,…
#2025#ai#CISO#cloudsecurity#Cyberattack#Cyberrisk#cybersecurity#Cyberthreat#Data breach#edge security#Fraud#hackers#PCI DSS#Privacy#Ransomware#skills shortage#zero trust
0 notes
Text
The most common Phishing Attacks in one simple Infographic from KnowBe4
A picture paints a thousand words and this useful image from KnowBe4 quickly and simply summarises the current Phishing activities. The main Phishing topic for business based attacks was HR with 42% of the attacks followed by IT related emails at 30%. Outside of HR the usual suspects come into play with Amazon Prime, PDFs and QR codes causing a lot of headaches.

View On WordPress
0 notes
Text
Instant Expertise: How Interim CISOs fill Critical Leadership Gaps
A blog by Luke Rupnow of Online Business Systems Inc. The demand for Chief Information Security Officers (CISOs) continues to increase due to the rising complexity of cyber threats and the critical role of cybersecurity pertaining to business strategy and operations. According to PwC’s 2024 Global Digital Trust Insights, a significant portion of executives acknowledge the need for enhanced cyber…

View On WordPress
0 notes
Text
The ISO 27000 family of protocols and their role in cybersecurity
The ISO 27000 family of protocols represent a series of standards developed by the International Organization for Standardization (ISO) to address various aspects of information security management. These standards provide a framework for organizations to establish, implement, maintain, and continually improve their information security management systems (ISMS). Each standard within the ISO…

View On WordPress
#certificate authority#cybersecurity#domains#ISMS#ISO#ISO27001#iso27701#IT Security Policies#Risk management#UKAS
0 notes
Text
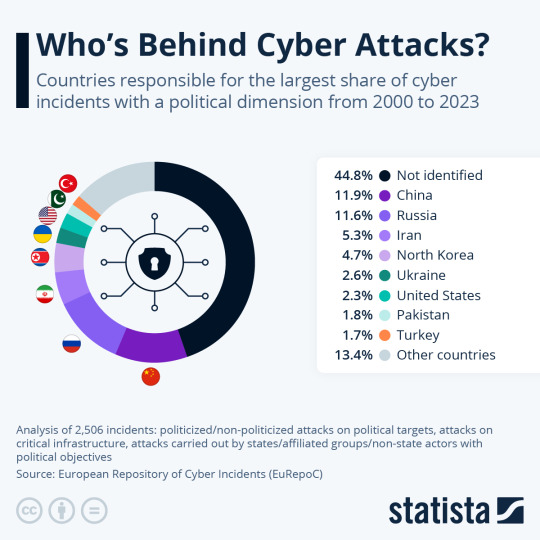
Which countries account for the most hacking?
Despite the very detailed analysis by Statista the “not identified” cyber incidents account for more that the the four usual nations. This could mean the usual suspects are doing a good job of hiding their attacks and they are getting away with a considerable amount of cybercrime or a lot of other more “friendly” nations are doing a lot more hacking that they are being credited with. Either way…
View On WordPress
#cyber risk#China#Critical Infrastructure#Cyber Attack#cyber breach#cyber crime#cyber incidents#Cyber Insurance#Cyber Risk#cybercrime#Cyberrisk#cybersecurity#Data breach#DORA#EuRepoC#hackers#hacking#hacktivism#Iran#Malware#Nation State#NIS2#OG86#Russia#state sponsored hacking#statista
0 notes
Text
26 Cyber Security Stats every user should be aware of in 2024
Cyber Crime Surge: During COVID-19, cyber crimes shot up by 600%, showing how threats adapt to global changes. Phishing Attacks: Phishing is the top cyber attack, causing 90% of data breaches. Shockingly, 96% of these attacks come through email. Ransomware Attacks: In 2023, a whopping 72.7% of organizations faced ransomware. The cost of these attacks could hit $265 billion annually by…
View On WordPress
0 notes
Text
Top 10 Cyber Incidents Report 2023, based on the financial impact and reputational damage
Tokio Marine HCC International Cyber team has published their fourth annual Top 10 Cyber Incidents Report 2023. Here is their Top 10 with the link to the report at the bottom of the post. Israel – Hamas war (Nation State attack)Impact – Kinetic cyber attack causing direct or indirect physical damage, injury or death to people ION Derivatives (Financial institution)Impact – Systemic risk due to…

View On WordPress
#Air Euopa#Boeing#Caesars Palace#Critical Infrastructure#cyber crime#Cyber Insurance#Data breach#DDoS#MoveIT#Nation State#NIS2#NISD#OG86#Ransomware#Reputational Damage#Royal Mai#Tokio Marine
0 notes
Text
Cybersecurity Glossary
Over the course of this year I have explained to colleagues and clients who’s roles are not in Cybersecurity what certain phrases or abbreviations mean. After I while I started to drop them into a word document so I could reuse them. Then I decided to make this post so I can easily share the explanations. There are bound to be things missing, please drop a comment if I have missed something and…
View On WordPress
#anonymisation#Attack Surface#authentication#BCP#Biometrics#Botnet#Compliance#Critical Infrastructure#cybersecurity#DDoS#DFIR#Embedded software#Encryption#Firewalls#GRC#ICS#IEC62443#Industrial Control System#IR#ISO27001#Malware#mfa#NIS2#Operational Technology#OSINT#OT#OT Security#PCI DSS#Penetration test#phishing
2 notes
·
View notes
Photo
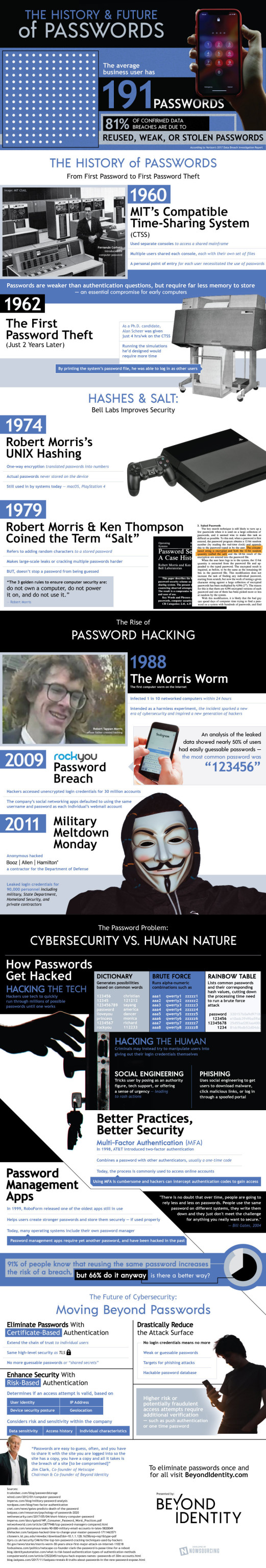
THE HISTORY AND FUTURE OF PASSWORDS – Infographic The Infographic is from Beyond Identity
2 notes
·
View notes
Photo
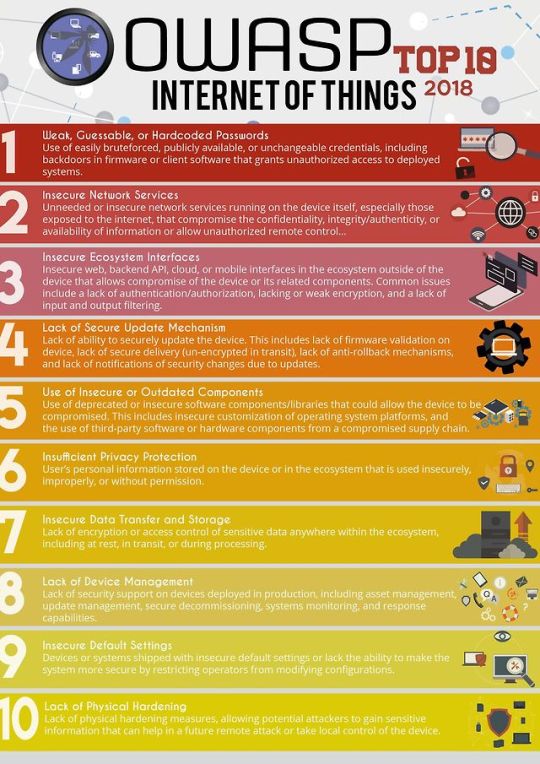
The OWASP IoT Project Top 10
2 notes
·
View notes
Photo

21 Significant 21st Century Data Breaches – Infographic OptimumSecurity has created an infographic that is a great representation of many significant data breaches.
2 notes
·
View notes
Photo

Infographic: How to solve the cybersecurity talent gap in your organization
0 notes
Photo

11 Cyber Security Questions Every Small Business Should Ask
0 notes
Text
2018 changes to PCI DSS v3.2
2018 changes to PCI DSS v3.2
Several PCI DSS requirements from version 3.2 come into effect at the end of January, 2018 (that’s just five months from now!).
Here is a list of some of the changes that will come into effect:-
3.5.1: Full documentation of all cryptographic architecture (service providers only)
6.4.6: Change management processes that include verification of any PCI DSS impact for changes to systems or networks
View On WordPress
0 notes
Text
ICO: Warning to SMEs as firm hit by cyber attack fined £60,000
ICO: Warning to SMEs as firm hit by cyber attack fined £60,000
Small and medium sized businesses are being warned to take note as a company which suffered a cyber attack is fined £60,000 by the UK Information Commissioner’s Office.
An investigation by the ICO found Berkshire-based Boomerang Video Ltd failed to take basic steps to stop its website being attacked.
Sally Anne Poole, ICO enforcement manager, said:
“Regardless of your size, if you are a business…
View On WordPress
0 notes
Text
Is the North West a hub for nuisance calls?
Is the North West a hub for nuisance calls?
In the last few months it appears that the North West of England has become a hub of nuisance calls after three raids undertaken on behalf of the Information Commissioners Office.
The ICO executed two search warrants this week, one in Gatley, Greater Manchester, on Wednesday and the other in Wilmslow, Cheshire, on Thursday.
Computers and phones were seized during the searches as the ICO continues…
View On WordPress
#data protection#Gatley#GDPR#Health Green#Information Commissioner&039;s Office#Manchester#Operation Pelham#Wilmslow
0 notes