We offer a wide spectrum of software and consulting services; business-technology consulting, Internet and e-business consulting, system integration, custom application development, training & workshops from global software experts and application re-engineering.
Don't wanna be here? Send us removal request.
Text
PKI-Based Identity with Blockchain

In this guest post by Rajneesh Gupta, the author of Hands-On Cybersecurity with Blockchain, you’ll learn how to deploy a decentralized PKI (DPKI) using Ethereum.
Organizations have several applications to manage, and these are hosted by different systems and servers. There are several ways to authenticate users based on methods like multi-factor authentication system, one for each system/application, single sign-on (SSO), and the directory server. However, authenticating users on the internet is comparatively a difficult mechanism.
Further, it is extremely important to achieve trust over the internet before exchanging information as the internet is open for trusted and untrusted parties alike. In order to establish trust over a public network, there is a need for an independent trusted party. A public key infrastructure (PKI) is an open framework built to resolve trust factors between the internet-connected users.
Businesses can simplify the deployment and management issues that are encountered with applications by employing a PKI. As businesses are moving more toward cloud-based applications, it is critical to protecting security-sensitive applications from emerging threats. There are several security threats when communicating online such as identity theft, man-in-the-middle (MITM) attacks, and data leaks.
However, traditional PKI models are centralized and consequently pose the following challenges:
Problem 1 – The need for Additional Security: According to a report from the Ponemon Institute’s 2016 research, 62% of businesses have deployed cloud-based applications using PKI, with an increase of 50% in 2015. If the central certificate repository gets compromised, it will lead to a massive data breach and account theft. Organizations tend to use an additional layer of security such as hardware security modules (HSMs) to secure their PKI. HSMs are deployed to protect PKIs for the most critical root and issuing CA private keys. Organizations are opting for multi-factor authentication for administrators and HSM usage.
Problem 2 – Central Authority: In the current state of the internet, a central authority (root authority) is responsible for managing DNS requests and responses (root authority), X.509 certificates, and much more. Therefore, all internet-connected devices and systems have to trust the third party to manage public keys and identifiers. For instance, take the example of a domain name; even though it has been purchased by its owner, it practically belongs to third parties, such as the Internet Corporation for Assigned Names and Numbers (ICANN), domain registrars, and certificate authorities.
Furthermore, these trusted third parties are very much capable of intercepting and compromising the integrity and security of users worldwide. There have been several cases where these trusted third parties have shared their customer’s information to security agencies and other bodies. They can either do this for financial gain or to prepare customer behavior analytics.
How can Blockchain Help?
PKI has major vulnerability because of its centralized management system. Blockchain, however, is fundamentally decentralized and allows communication between several parties without any third party involvement. The approach of going decentralized can be a paradigm shift in the world of PKI; however, it needs a systematic approach to deploy it.
Decentralized Infrastructure
Blockchain is about achieving a decentralized network of multiple participants without third-party involvement. A decentralized public key infrastructure (DPKI) is an innovative concept that achieves authentication over public systems without depending on a single third party that can compromise the integrity and security of the system.
As you may already know, blockchain is built with a trustless approach that allows both trusted and untrusted parties to communicate with each other. However, trust is usually established among geographically and politically disparate participants with several consensus models for the state of the ledger. By definition, blockchain allows you to store any kind of value with several nodes in the network. With DPKI, this value will be a form of secret properties.
A principal can be given direct control over global readable identifiers, such as a website domain, by registering the identifier in the blockchain. With the key-value database, the principal uses the identifier as a lookup key.
Blockchain can assign confidential assets (public keys and other attributes) and permit these values to be globally readable in a secure manner that can’t be compromised by any MITM, which is possible in PKIX. This is accomplished by allowing the most correct public key to link with the identifier value, and authentication is performed by an identifier lookup to the latest public key.
By design, the DPKI system remains decentralized and control over the identifier remains with the principal,thereby eliminating the risk of the identifier data store getting compromised.
Deployment Method
Ethereum, among other platforms, is one of the most flexible and reliable blockchains. It is a programmable blockchain and fits with a granular and policy-based PKI. The PKI is implemented as a function in a smart contract in an Ethereumblockchain. Each entity can have multiple attributes to authenticate ownership.
These entities can be public keys or Ethereum addresses. Each transaction is identified using a public key and then represented by a corresponding entity ID and PKI. A smart contract is used to program the events and functions of various operations in the PKI. The smart contract can also be configured to invoke specific PKI operations, such as create, derive, remove, destroy, and many more.
Such functions and processes will be written in Solidity and deployed in EVM, which will deliver an ease of user management for PKI operations. The following sets of PKI operations are made available by programming a smart contract:
Entity registration: Users or systems are added to the PKI system by calling a registration event from the smart contract. The entity can be as simple as an Ethereum address, a public key, an attribute ID, data, and data hashes. The configured event on the smart contract collects the entity and forwards it as a transaction to Ethereum. The queued transactions are mined, and a block is created that will be later added to the blockchain.
Signing of Attributes: An entity can be characterized using a registration event. Each attribute of the entity can be signed by the PKI system through a smart contract, and a transaction will be issued. This signed entity will later be made available to other entities or users.
The Retrieval of Attributes: The attributes of the entities can be located by applying a filter to the blockchain using the respective IDs of events that have been configured on the smart contract.
Revoke Signature: This is one of the most critical functions required by any PKI solution to revoke the digital signature on attributes or entities. Revocation becomes extremely important when a user loses his/her key or if it is compromised. Smart contracts can be configured to invoke the revocation event and revoke the signature on a specific entity.
Requirements
In the DPKI deployment, the registrar still has a role in the infrastructure, but it is restricted as follows to ensure that identities to entities are represented in the network:
It is required to ensure that software is always under the control of principals and corresponding keys.
Private keys have to be generated in a decentralized way to ensure that they remain under control of the principal. The generation of a key pair on behalf of a principal has to be strictly prohibited.
There has to be no single entity that can change other entities without consent from the principal.
Once a namespace is created within a blockchain through an Ethereum smart contract, it can’t be destroyed.
The registration and renewal of identifiers has to be transparent.
By default, the software to manage identifiers must ensure that all activities, such as creating, updating, renewing, or deleting identifiers,are forwarded via a decentralized mechanism.
DPKI Deployment
Start by turning up the Node.js and Ganache-CLI framework. Installation of ganache-cli has to be performed carefully as it creates the entire Ethereum environment in your local system. Perform the following steps:
Install Node.js using the commands shown in the website at https://nodejs.org/uk/download/package-manager/#arch-linux.
Run the following command in the Terminal:
npm install -g ganache-cli
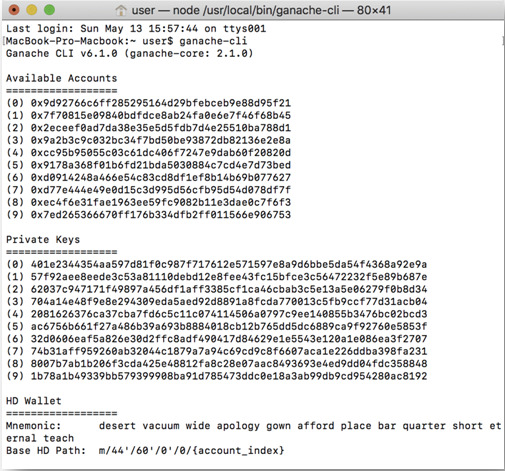
Now, start the test network by using the command as shown in the following screenshot in the Terminal:
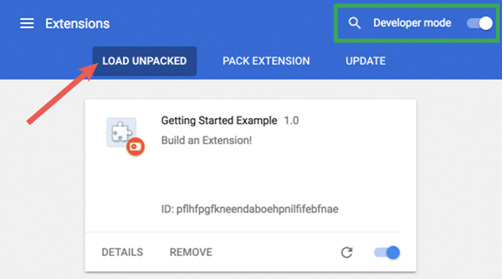
3. You’ll now have to enable the developer mode to see the browser content in detail. You also have to enable the LOAD UNPACKED extension, as shown in the following screenshot:
Testing
CAs can issue Reaction Policies (RP), which take effect if an unauthorized certificate for a domain is issued. In the process of testing, you need to register Domain Certificate Policies (DCPs) and create RPs. The testing can be done via the following steps on your local system:
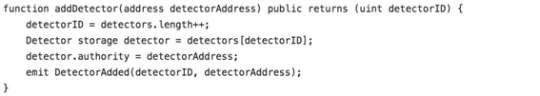
You first need to add a detector and register it. The following script is required to add a detector by defining its detector ID:
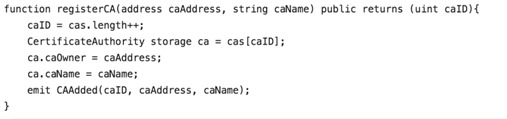
2. Now register a CA used by the domain owner to issue certificates. It is mandatory to define CA ID, CA owner address and name, as follows:
3. Register DCP with CAs as follows:
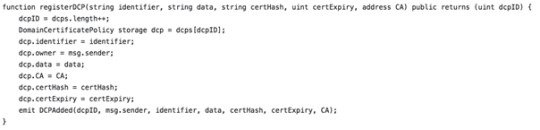
4. Create an associated RP under the smart contract:
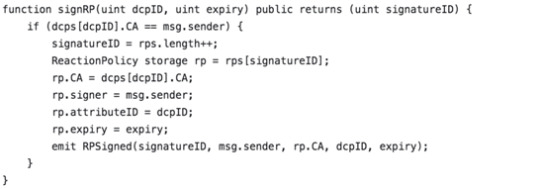
5. Revoke a certificate when the detector receives reports of a malicious certificate in the wild:
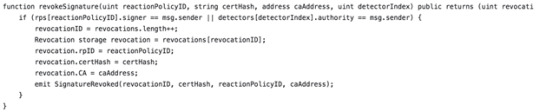
6. The detector can now blacklist the CA when a rogue CA misbehaves frequently:
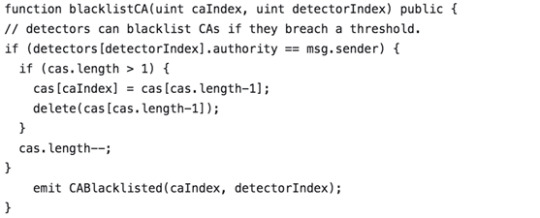
You have now successfully deployed the PKI with an Ethereumblockchain. You have also developed a model describing reaction payouts and a method to enforce accountability on misbehaving CAs. If you wish to explore more on this subject, you can refer to Hands-On Cybersecurity with Blockchain. The book follows a practical approach to explain the blockchain technology to transform cybersecurity solutions.
Source: https://blog.tetratutorials.com/pki-based-identity-with-blockchain/
#bitcoin blockchain technology#blockchain platform#blockchain technology explained#Tutorial on Blockchain Architecture#understanding blockchain technology
0 notes
Video
youtube
Video Transcript: Hello and welcome to this module of this course on Apache CloudStack. in this the module we will introduce you to Apache cloud stock we will go over its history in brief, speak about the core components and key concepts and terminology associated with Apache CloudStack. this the module forms the foundation for the upcoming modules where we will start to implement our own cloud environment using a patchy cloud stack.
Before we talk about Apache cloud stack let's quickly try to understand the basics of cloud computing. traditional methods of hosting and deploying IT infrastructure. meant we had to deploy monolithic data centers and physical servers. the lead time for this heavy infrastructure the deployment was few days to few weeks. it needed a large amount of capital spending upfront this model often led to energy wastage low utilization and high efforts for the administration of hardware servers.
It was rather difficult to scale these operations very quickly whether it was to expand the operation to meet growing demand or to shrink operations due to reasons like seasonality. cloud is a generic term used for a platform that provides hosted services over a network. at the core of cloud computing is hardware virtualization because of this cloud infrastructure can provide us access to shared pool of computing resources which could be rented or leased on on-demand.
Basis some of the main benefits and drivers behind cloud computing is cloud computing allows companies to avoid upfront infrastructure costs and focus on projects that differentiate their services. and products in the recent years this has enabled technology startups to invent and come up with innovative technologies and products without worrying about spending a lot on front fixed infrastructure. cloud computing allows enterprises to get their applications up and running faster with improved manageability and less maintenance.
Cloud computing enables us to rapidly adjust resources to meet fluctuating and unpredictable business demand. major cloud providers are vastly trying to use renewable energy sources to run their data centers. and they're also coming up with more efficient data center designs to reduce energy consumptions per unit of the computing resource. this obviously, has tremendous advantages for the environment. since cloud providers can manage their data centers more efficiently and cheaply these savings can be passed on to the cloud consumers.
The availability of high capacity networks low-cost computers and storage devices, as well as the widespread adoption of hardware virtualization service-oriented architecture and atomic utility computing, have led to a growth in cloud computing. companies can scale up as computing needs increase and then scale down again as demands decrease cloud computing. has become a highly demanded service or utility due to the advantages of high computing power cheap the cost of service high-performance scalability accessibility as well as availability. some cloud vendors are experiencing growth rates of 50% year-over-year to learn more about cloud Compound.
#cloudcomputing#cloudstack#cloud technology#apache#apachecloudstack#apachetutorial#cloudcomputingtutorial
0 notes