Don't wanna be here? Send us removal request.
Text
Lecture8
Root Cause Analysis
Human Weaknesses:
Honesty
Misdirection and limited focus
Similarity matching
Frequency gambling
Availability heuristic (可得性启发): The impact of an event will be magnified if the event just happened or happened on yourself
Confirmation bias: Once you confirmed something, you will try your best to find the evidence, even it’s wrong
Cognitive strain
Group-think syndrome
Developmental phases
System Error:
Belief event has only one significant cause
Plan for fewer contingencies than occur
Ability to control outcomes: the illusion of control.
Hindsight bias: knowledge of outcome of the previous event increases perceived likelihood of that outcome (Things happened looks likely to happen, things didn't happen seems impossible to happen)
Complexity coherence coupling visibility: looks like defense-in-depth, but the failures of these measures are invisible
Defense in depth
Automatic safety devices: you lose the ability to operate
Homework: Learn about one of
Chernobyl
Bhopal
Challenger
0 notes
Text
Upnpprhost (detected on 5 July 2019) - Malware analysis
Introduction of the malware:
This malware uses multiple vulnerabilities to attack. It will first try to build a remote connection to the infected computer, then download Trojan to turn the infected computer into a crypto coin miner.
Malware behavior procedures:

Analysis:
- Download the main part of the malware:
The program “download.exe” is not the real malware, “download.exe” will download the main program called “upnpprhost.exe”. And this malware is actually a variance, it has a list of previous versions, they are all under the same family called BuleHero
Having downloaded the main part of the malware, the malware will then release all its modules, including scanning module, bug exploit module, password brute force module and so on. The malware also getting a configuration file “cfg.ini” to keep itself updated, the configuration file is from the following urls:
http://uio.hognoob.se:63145/cfg.ini
http://uio.heroherohero.info:63145/cfg.ini
Here’s the information contains in the configuration file:
[UpdateNode]
Node1=upa1.hognoob.se
Node2=upa2.hognoob.se
[MainUpdate]
MainVersion=20190702
MainExeName=pnpprhost
MainSize5427200
[Download]
Url=http://fid.hognoob.se/download.exe
[MinIng]
MineUpdate=off
MiningPool=pxi.hognoob.se:35791
MiningPoolBackUp=pxx.hognoob.se:35789
CPUOccuPancy=1
[Report]
ReportUrl=185.164.72.143
ReportPort=57123
We can actually see the URL of the latest version malware, and please DO NOT DOWNLOAD THE MALWARE FROM THE URL AND SPREAD IT!
- Get the password of the target computer:
The part is done by a program called mimikatz

this program was originally written by a french called Gentil Kiwi, which can get the password in plaintext of the current active user. A precondition of this program is that the user must run the program as an administrator.
- Scan ports:
This part is how the malware can spread through the internet:
It will first randomly generate a range of IP and save them in the “result.txt”, then it will scan all the generated IPs and find all the vulnerable IPs to a file called “ip.txt” for later use of attack:

This malware is disgusting as it not only scans through the internet, but also your local network as well, which means, all your devices under the same local network will have a high chance to affect this malware as well.
- Dictionary brute force:
This is actually done by a software called “Lamescan 3”


And the dictionary it uses are from the remote server:
http://uio.hognoob.se:63145/uDic.txt
http://uio.hognoob.se:63145/pDic.txt
here are some passwords in the dictionary:


Familiar to you, ha?
- System vulnerability exploit:

This malware uses a lot of new tools released by NSA
- Turn the targets into crypto coin miners:
After a successful invasion, the malware will then run a crypto coin miner program:

called hcrbpm.exe to dig crypto coins.
Preventions:
Close unnecessary ports like 135, 139 and 445, as most vulnerabilities are been utilized through these ports
Make sure that you have installed all the latest patches
Change your password to a stronger one
0 notes
Text
Reverse Engineering
Technics:
Block internet validation:
Nowadays, many softwares are not only having the pack and local validation to protect them, but also internet validation, which makes them tricky when you want to crack them. This blog will introduce a very basic way to block the online validation, by looking for the internet validation part in the code and close it,
Redirect package to local server:
Sometimes you couldn’t find the part of the code that is responsible for doing internet validation, an alternative way is to redirect the validation package to a local server and give back the correct response. The package could be captured through tools like wireshark, in the package, you can then know its destination address, then go to the system host file (Like a DNS buffer, which maps an IP address to another), then you can set up your own server giving correct response according to the response package you’ve captured.
Cracking Online Verification System:
Because verification is hard to implement, and a lot of small companies don’t have the ability to make a good verification system, so they will find another company that can provide online verification API. Here are some famous Chinses online verification companies:
CC online verification
PiaoLing online verification
KeKe online verification
Genie online verification
CC 3.0 + has hidden traps, in CC 3.0, hidden traps could result in restarting or blue screen of your computer, and in CC 3.4 +, it will format your disks.
0 notes
Text
Reverse Engineering
Technics:
Change the return value to control the validation:
Before, we’ve tried to change the assembly (redirect the jump instruction), but the thing is, not all the programs only have one jump to validate, some of them might have multiple jumps the check if the program has registered, and those jumps can spread widely in the code, then how can we redirect all the jumps? A solution is, instead of redirecting all the jumps, we can change the return value of the comparison function, since it’s less likely for the program to rerun the comparison function every time when it needs to jump, it must store the return value somewhere in the memory for future use, therefore, once we can change the return value, it is equivalent to having redirected all the jumps.
(All crackings are for educational purpose, no cracked software is spread to the public)
0 notes
Text
Trump Phishing
Hi Donald There was an unusual activity on your Twitter account recently. Please see the details below:
Account name: Donald J. Trump
Activity: Login
Location: Beijing, China
IP address: 124.122.57.213
If it was you: Great, you can ignore this letter.
If it was not you: Your Twitter account might be under risk, please click here to reset your password immediately.
Click here to take a few more steps to keep your account secure.
Twitter team
(DO NOT REPLY, this email was automatically generated by Twitter. Need help?Please contact Twitter Customer Service.)
We sent this email to @Donald J. Trump. Unsubscribe
Twitter, Inc. 1355 Market Street, Suite 900
San Francisco, CA 94103
0 notes
Text
Reverse Engineering
Technics:
Cracking the software with packing (License restart validation):
Packing the software is encoding the binary code of the software, then how do we do the reverse engineering if we can’t get the binary file of the software? While one way is of cause using an unpacking software to unpack the software first then use a static analysis tool, the alternative way is, using a dynamic analysis tool. Since the CPU can’t run the encoded binary file directly, the software must decode itself at run time, and it has to put the decoded binary somewhere in the memory, that’s how dynamic analysis tools like OllyDBG comes into place, it can help analyze the data in the memory at run time.
Real cracking:
Target: An English learning software (FeiYang English)
Environment: Windows 10
Tools: OllyDBG
—————————————
Let’s firstly take a look at the purchase page of the software, you can see we need to provide a username and a serial number:

This time, we are cracking the software without unpacking, so currently, the software is packed. When we drag it into the OllyDBG, we can find the assembly codes are unreadable:

Now let's run the software in the OllyDBG and follow the address: 401000 (90% of the unpacked software’s unpacked code starts from here).

Now let’s search the keyword “Unregisited”

If we scroll up a few lines above the keyword line, we can find the program is actually visiting the regedit in the computer, so it is probably visiting the regedit to check if our serial number provided is correct or not

Let’s set a breakpoint here when the program is trying to read from the regedit. But things are a little bit different here, since the program is packed, even if we set a breakpoint here at this address, when we restart the program, OllyDBG will have error for this, since at first, there are no instructions there, only when the program has already run, and all the binary are already decoded in the memory can the OllyDBG set the breakpoint, but the program is already running...you see the conflict here. A way to solve this is, we set two breakpoints: one at the beginning of the software, where all the code are decoded but the software is not running, then we set the real breakpoint we want to set.
By doing the above operations, we have successfully stopped the software at the position we want:

Now, let’s run the program line by line and keep an eye on the register window, since the program needs to compare the serial code we provided to the real serial number, the program must load the real serial number to somewhere in the memory

Now we can find the program then loaded 3 strings that might be the real serial number

After trying the three strings, the last one is the real serial number!

Cracked!
(All crackings are for educational purpose, no cracked software is spread to the public)
0 notes
Text
Reverse Engineering
Real Cracking:
Target: An encrypted video
Environment: Windows 10
Tools: OllyDBG
—————————————
As you can see, when we typed in a random password, it complains that the password is wrong:

Let’s firstly search in the keyword “wrong” in the OllyDBG:

And pretty obviously, there is a jump logic, so if the password is correct, it will play the video. Let’s just change the assembly code from je******* to jnz ******* so that the password will always be correct:

Now let’s play the video again:

By type in some random password and we can now watch the locked video!
(All crackings are for educational purpose, no cracked software is spread to the public)
0 notes
Text
Tay AI
About Tay AI:
Tay was an artificial intelligence chatterbot originally released by Microsoft via Twitter, in order to have a better understanding of human conversations.

(Screenshot from Tay’s twitter page)
Tay was then been shut down 16 hours after her launch because of posting racist words:

Why?
Most people said it was because Twitter taught her to do so, as human can talk whatever they want to Tay, Tay might be able to hear their real thought, and so think of how evil the world really is, the world is probably not as good as it seems. While from Microsoft, they said the reason was caused by trolls who “attacked” the service.
The Truth
Since nobody but Microsoft knows the truth, I can only provide the probable truth I believe based on the information I have access to, that is, just like what Microsoft said, it was because of malicious attacks. Two major reasons are:
Microsoft has no reasons to lie to the public on this event: This is based on the assumption that: all entities will tend not to lie if telling the truth will not cause any obvious potential harm since the action of lying will cause obvious potential harm to the entity. Think of this event, why would Microsoft lie on this event? Do you think admitting their product has defects that can be attacked so easily is a better choice over saying their product has no defect and it only reflects the real word to them? Imagine if they admitted that Tay behaved like this was indeed, because of what it was received at on Twitter, what would happen? The only effect will be I think is everyone starts to think the world might not be as good as it seems, and probably for the first few weeks, people are in a little bit fear, and this fear is not different from when you hear from the television says there is a murder in your area before, and it is now been caught. And after a few weeks, nobody still remembers this. The public won’t take this so seriously as you might think they should be. And will Microsoft itself lose any future profit because of this? If not, why would they lie?
A similar project was released before in China called Xiaoice, which had "more than 40 million conversations apparently without major incident": This can at least prove that the algorithm itself, without being attacked will not cause problems like this, I don’t think the general education level in China is higher than the rest of the world that leads to less offensive words.
The project is indeed at higher risk of being attacked:
The project was in its second release: This makes the project at higher risk because, in the first release, the way to attack haven’t been found yet, and even the attackers find a way, the project is probably not as popular at before, even if it’s been attacked, nobody will notice. So if the attackers find the way to attack, it’s much better for them to attack when the project goes viral again.
The project was released in English speaking country: In order to initiate such an attack, the attacker must have the language library for the same language. Most English speakers are not in the same country, it’s easy for them to have English language library and attack at low risk (since they are probably in another country), while China has 90% of the Chinese speakers in their own country, which will increase the risk of the attackers (As they are probably in China). This can possibly explain why the project in China was not being attacked, and suddenly the project became the prey for the attackers when the project was moved to America.
The future of AI
I would say AI will probably not be as smart as we think they could be in the near future. As we currently still can’t understand and define what intelligence is though ourselves are intelligence, and there are also lots of discussions on if the Turing Test is doing its work, a famous opinion is “The Chinese Classroom”. The next revolution might be the break thought of deep learning. An imaginary AI future could be the scenes in the game “Detroit: Become Human”, which will also cause discussions on rights of the AIs.
2 notes
·
View notes
Text
Safer - case study
Put on your hypothetical hat and start planning:
Suppose we are thrust into a war with a superpower such as Russia.
List what sorts of computer and internet related attacks might we suffer?
Think outside the box and list as many different possible attacks which might be employed against us.
Cyber-war is new and no one truly knows yet just what it might even look like. By all means, read on the internet to see what other people think the main risks are, but you'd be crazy to think that what you read will be most of, or even the most significant of, the attacks that will emerge.
Education
phishing
ransomware
Law enforced sec standard
Self-reliance
Deportation
Turn people
Diplomacy
Disconnect all critical infrastructure from the internet
Backups
Mesh net
Assassinate (frame people)
Preemptive strike
0 notes
Text
OPSEC
What is OPSEC?
Determining what information is publicly available in the normal course of operations that can be used by a competitor or enemy to its advantage. OPSEC is a common military practice that is also applied to civilian projects such as the development of new products and technologies.
Why do we care about OPSEC?
Information combined together will have a huge impact.
How to OPSEC?
Avoid sharing information
Only share information on a need-to-konw basis
beware social media
metadata
Minimize indicators - expensive clothes, carrying tools
No information is still information
hard to strike the right balance
Keeping your identity secret
Remain anonymous or set up a false identity to hide your tacks
False identities are difficult to create and maintain but are often useful
Never contaminate, leaking information from one identity to another
Be forgettable
Blend in with everyone else
If you stand out, you will be remembered and monitored
Summary:
If you don't need to share information, don't
If you do something you don't want people to know about, ensure it can’t be traced back to you
Avoid bringing attention to yourself
1 note
·
View note
Text
Week7 LectureNote
Diffie-Hellman Algorithm:

Format string
%s pop the first thing in the stack and interpret it as string
%d pop the first thing in the stack and interpret it as integer
%p pop the first thing in the stack and interpret it as 0x + hex
%x pop the first thing in the stack and interpret it as hex (no 0x in the front)
%n pop the first thing in the stack and interpret it as address and put the number of characters printed before %n and stores it to the address poped
%11$s %11$d %11$n
Instead of poping the first thing in the stack, use the 11th thing in the stack
printf(”%s\n, main) (prints the binary code of main function)
printf(”%x\n”)
printf(”%3$p”) (print the specifc argument of printf)
payload = p32(some address) + “%11$s” (can print out anything in the specific address) (%11$s pops the address you entered)
Shellcode
Change the return address to let the program jumps to your shellcode (runs the shell), so you have the control of the computer
Nop sled
Instead of knowing where exactly the return address is and overwriting it, we could instead put a lot of nops in the memory, so no matter what the address is changed to, it will probably point to the nop instruction in the memory, and hence sled to the shellcode
Identify the assets you want to protect: people always forget what assets they really want to protect
Team America
Richard’s wallet vs Richard’s AIDS
Types of assets:
Tangible Assets
Intangible Assets
Man in the middle: prevent someone from changing the public key in the middle of the connection
Web of trust (PgP)
PKI: Have a certificate to verify the public key is authentic (links the public key to the domain), this reduces the problem to authenticate the issuer of the certificate (the signer), which is a relevantly small amount of companies, where their public keys can be stored in advance.
0 notes
Text
Crackme Full Solutions
Crackme is a set of well-designed challenges for reverse engineering, created by my tutor Jazz:
https://github.com/jtalowell/crackme
My whole solving process was enjoyable, all problems are challenging but achievable, shout out to Jazz.
0x00:
This binary requires authentication with a password
There are two tasks: i) Find input that results in the program printing 'Password correct!'. ii) Modify the binary such that any input results in the program printing 'Password correct!'.
Solution:
i) This one is pretty straight forward, we can see the password is in plain text, we can read directly from the disassembler, which is “asecurepassword”

and let's try to type the password in the program:

Cracked!
ii) Just simply forbid the branch, since the branch leads to the “password incorrect”


Now, let’s save it and run

Cracked!
0x01:
This binary requires authentication with a password.
There are two tasks: i) Find input that results in the program printing 'Password correct!'. ii) Modify the binary such that any input results in the program printing 'Password correct!'.
Solution:
i) We can see the program is actually receiving a string and convert it into long, and then compare it with the number 0x539, so it’s obvious now the password is the decimal form of 0x539, which is 1337

Now, let’s type in the password

Cracked!
ii) Modification is similar to the previous challenge, simply set a never branch at jne 0x11e9
0x02:
This binary requires authentication with a password.
There are two tasks: i) Find input that results in the program printing 'Password correct!'. ii) Modify the binary such that any input results in the program printing 'Password correct!'.
Solution:
i) This time, instead of reading from stdin, the program reads the input from the argument, if there’s no argument, the program prints “Password incorrect” directly, otherwise it converts the first he argument to long, and then compare it to number 0x1dc7, so the password here is the decimal form of 0x1dc7, which is 7623

Now, let’s type in the password in the argument

Cracked!
ii) Modification is similar as well, simply never branch at jne 0x119c
0x03:
This binary requires authentication with a password.
There are two tasks: i) Find input that results in the program printing 'Password correct!'. ii) Modify the binary such that any input results in the program printing 'Password correct!'.
Solution:
i) Basically, the program checks the environment variable “FLAG” and compares it to the number “0x1ab9”, which in decimal is 6841, and 6841 is the password

But this time, we need to set the environment variable FLAG to 6841, we can use export to set it, like this

Cracked!
ii) Simply set never branch at je 0x11af and jne 0x11c4
0x04:
This binary requires authentication with a valid license.
There are two tasks: i) Find input that results in the program printing 'License valid!'. ii) Modify the binary such that any input results in the program printing 'License valid!'.
Solution:
i) Let’s first take a look at the main function, in main, the program simply calls the function validate_license, and if the function returns 0, the license is invalid, otherwise, the license is valid.

Now, let’s jump to the function validate_license to see what happened there:

The function read the file “license.txt” and compare the content in the file to the number 0x192f, which is the password, its decimal form is 6447.
And now let’s create the file and put the password in it

Cracked!
ii) Modification from my point of view is just changing the mov eax, 0x0 to mov eax 0x1

So that even no license file created, the function will still return 1, which will let the program print valid license.


Cracked!
0x05:
This binary simulates some non-malicious behaviour of the WannaCry virus.
There are two tasks: i) Find out how to disable the malware without modifying the binary. You are not required to actually disable it. ii) Modify the binary such that the malware is disabled.
(Confirmed from the author, no actual malware is activated, please feel safe xD)
Solution:
i) First, take a look at the main function, it checks if the kill switch is alive or not to determine the state of the malware

Now, let’s take a look at the is_killswitch_alive function

We can see a domain name in plain text, let’s open it in the browser

Which returns an url, and the url doesn’t exist

Though I can’t read the whole binary code, I can guess that it might checks if the url from the plaintext domain exists, if it exists, close the malware.
The way to solve this is to either map the non-existing url to the local host, and run a local server to handle the request or simply buy the domain.
ii) Let’s analyse the function

we can find the return variable is var_9, so what we need to do is just to change this variable to 1, so that the kill switch is alive

Now, let’s run the save the program

Cracked!
0x06:
This binary requires authentication with an authentication code.
There are two tasks: i) Find input that results in the program printing 'Access granted!'. ii) Modify the binary such that any input results in the program printing 'Access granted!'.
Solution:
i) We can see the software is actually taking the number from the argument and use it as a seed to generate a random number, and compare the number generated to a specific number. Hence we the only way to get access from the program is to guess the random seeds used to generated the specific number, this can only be solved by brute force

The is not hard to brute force, as I just tried a few numbers by hand and get it right, without even writing any supportive program

Cracked!
ii) Modification is simple, just set a never branch at jne 0x11d0
0x07:
This binary requires authentication with an access code.
There are two tasks: i) Exploit a bug that results in the program printing 'Access granted!'. ii) Modify the binary such that any input results in 'Access granted!'.
Solution:
i) The program firstly checks if the length of the input string is 7, as 7 is compared to the return value of strlen, which includes the null terminator, so actually, only 6 characters can be entered. Then, as usual, the program converts the string to long

Now, we come to the main part, the loop, of the program. The loop initialize a temporary variable (say i) to 1, and it will do some operations until i reaches the number we entered, in other words, the number we entered is the number of times the operations will be performed. But no matter what how many times the operations has been performed, the flag (which will determine the output of the program) will always be set to 1, which will lead the program to output “access denied” (as the program performs the XOR operation on flag and 1), which means in order to let it print “access granted”, we have to find a way to skip the loop.

Let’s take a look at the loop condition again carefully

We can see, the loop condition only holds when i <= number we entered, therefore, we only need to enter a number that is already smaller than i at the beginning, which is any 5 digits negative number (as “-” holds one position)
And let’s have a try

Cracked!
ii) Modification is very easy now, as we now only need to let the loop always set the flag to 0

so that any 6 digit number will be granted the access

or

so that no matter what you entered will always give out an “access granted”

Cracked!
1 note
·
View note
Text
Lecture5
- the motto of last week: "every contact leaves a trace"
- WEP: Wired Equivalent Privacy (So many flaws, a joke)
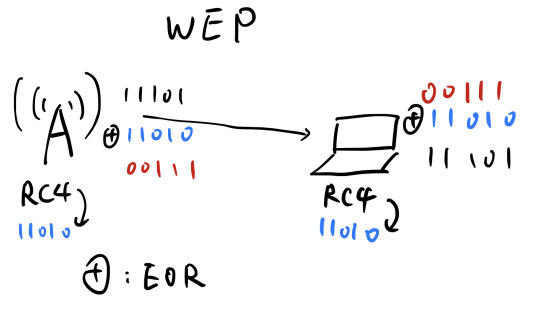
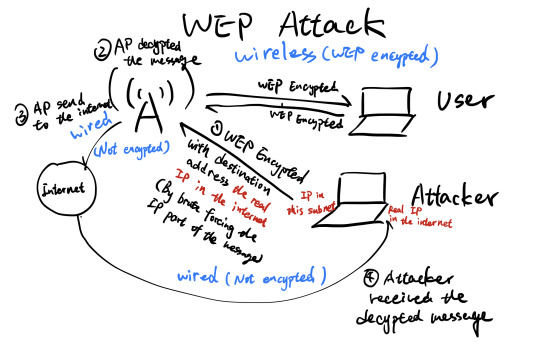
- Exclusive Or:
EOR two same messages will give all 0s
EOR a message with a random number will give a random number as well
- Hash:
MD5 - 1991 - Rivest - 128 bits BROKEN
SHA0 - replaced almost immediately with... BROKEN
SHA1 - 1995 - NSA - 160 bits BROKEN
SHA2 - 2001 - NSA - 224/256/384/512 bits NOT YET
SHA3 - 2015 (standard accepted) - NIST competition (started 2006) - 224/256/384/512 bits NOT YET
Merkle-damgard construction:
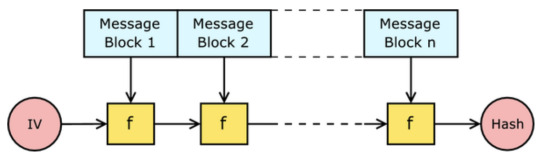
Hash extension attack
Digital Signatures RSA DSA:
Encrypt the message with your private key
Collison attack: can fake you like another person that is trustworthy (hash)
data breaches?
1 note
·
View note
Text
Midterm Review
Transposition:
simply rearrange the position of the letters
Substitution:
substitute a letter with another
frequency analysis, calculating IC
Caesar:
shift the whole alphabet, with the number of letters shifted as the key
frequency analysis, calculating IC
Vigenere:

similar to Caesar
The Kasiski test can be used to guess the length of the keyword, once the length is discovered, then list them line by line with each line the length of the keyword, and now each column is a Caesar cipher
RSA:
- Encryption/Decryption: Given the key (a, b) and text m, do m^a mod b
- Key Generation:
Find two prime number: p, q
Find the product of them: N
Calculate the number of coprime number of N: (p - 1)(q - 1)
Choose e (encryption key) in (1, (p - 1)(q - 1)) such that e is coprime with both N and (p - 1)(q - 1)
Choose d (decryption key) such that d*e mod (p - q)(q - 1) = 1
The Kasiski test:
find the repeating phrase
find the gap (the number of letters in between), for instance, the gaps are: a, b, c, d
a guess for the length of the keyword is gcd(a, b, c, d)
The Index of Coincidence:
Firstly shift the text itself, then
IC = 26 * (the number of all coincidence letters / the number of all aligned letters)
Nonce:
An arbitrary number that can be used just once in a cryptographic communication (Prevent replay attack, e.g. a timestamp)
Canary:
The kernel checks if the canary had been changed to detect buffer overflow (Prevent buffer overflow)
Merkle Puzzles: a way to exchange key online
the sender sends a large number of puzzles, each puzzle will give a puzzle identifier and a key
the receiver randomly pick one puzzle to solve and get the identifier and the key
the receiver then sends back the puzzle identifier back to the sender
the sender and the receiver now can communicate with the key
An advantage of this method is the hacker has no idea of which puzzle did the receiver solved, so in order to get the key, the hacker will need to solve every puzzle
Diffie-Hellman Algorithm:

Preimage resistance: Infeasible to invert the function (Can’t go backward)
Collision resistance: Infeasible to find any 2 messages with the same hash (Birthday Attack), so that others can’t randomly type a password and get in your account (having the same hash as your password)
Confidentiality: Only the right person (not the public) can read the message
Second-preimage resistance: Given a message M1, it is infeasible to find message M2 such that Hash(M1) = Hash(M2)
Symmetry: The encryption can only be decoded with the same key
Asymmetry: The encryption can only be decoded with another key (Two keys, one for encryption, one for decryption)
Non-determinism: The ciphertext looks completely different even the two plaintexts are the same (Add salt)
Non-Repudiation: The ability to ensure that a party to a contract or a communication cannot deny the authenticity of their signature on a document or the sending of a message that they originated (One party can not fake the other side’s signature, means the 2 parties cannot have the same key)
MAC (Message Authentication Code):
Provided: Integrity, Authentication
Not provided: Confidentiality, Non-Repudiation(As there’s only one key for both sides)
0 notes
Text
Reverse Engineering
Technics:
Things you need to do before cracking any programs:
The executable might be encrypted by some packers, so the first step is to check any packers on the program, using a tool: PEiD, which will show most packers the program uses.
Unpack the program so that the analysis programs are able to read the executable, different packers might need to find different unpack tools.
NOP:
A way to bypass any condiction in the program, can be used to crack a simple if condition check. NOP in assembly language simply tells the CPU “do nothing��� in the next cycle.
A common way to find the conditions in the program is by searching keywords, some technics are:
Words can be in ascii or in unicode, if ascii doesn’t work try unicode
Try search less word as possible, more words will increase the possibility of a fail search
Real cracking:
Target: A management software

Environment: Windows 10
Tools: PEiD, OllyDBG
---------------------------------------
I firstly checked any packers:

And found the software has no parcker, and was written in Delphi.
Then I opened the software and tried to login

It said wrong password, and there’s an upper limit for guessing the same account.
In order to analyze the program, I dragged it to the ollyDBG, and searched the keyword: password


I found where the string “password” was located, and noticed a jump from somewhere to this code.
Then I traced back to the jump condition

Filled it with NOP to prevent it from jumping

Now let’s start the program again

Without even typing the password, we click login directly and we are in!
(All crackings are for educational purpose, no cracked software is spread to the public)
1 note
·
View note
Text
Quicksort in assembly
I wrote a quick sort in an 8-bit assembly, and now I feel better in understanding assembly code.
C code for Quicksort:
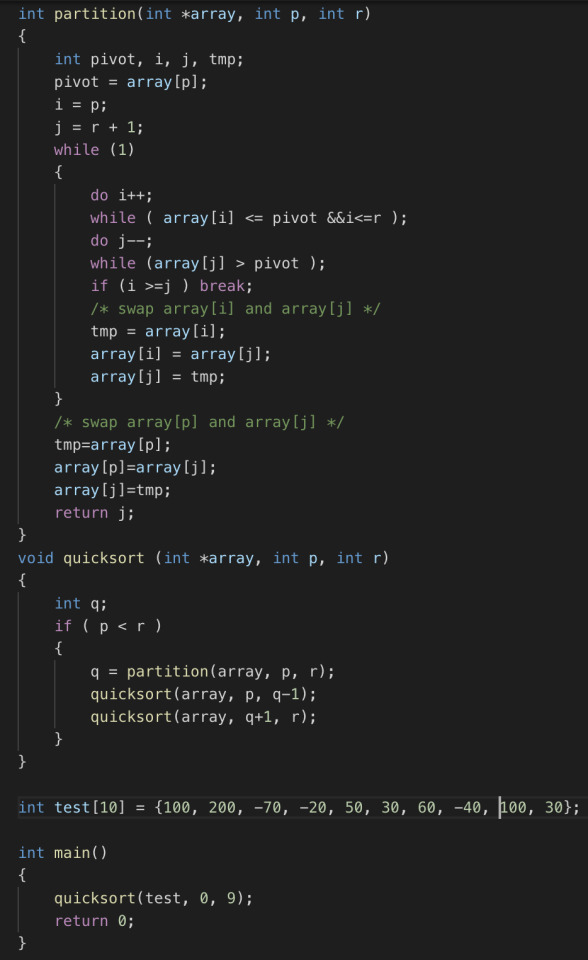
Assembly code for Quicksort:
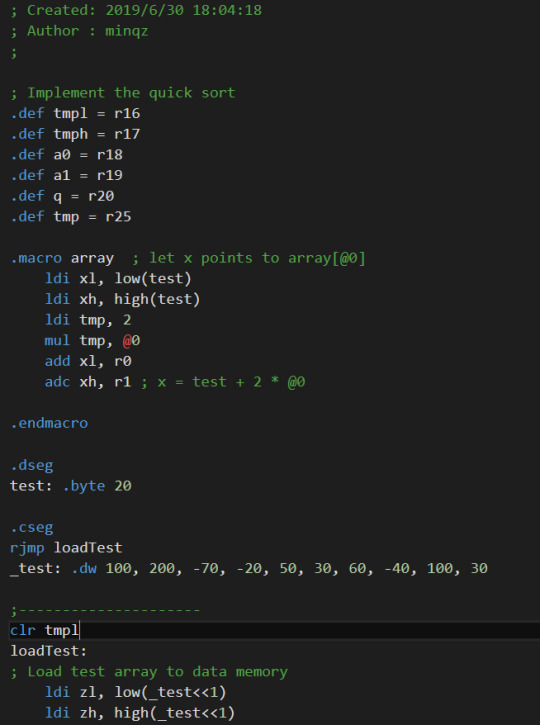
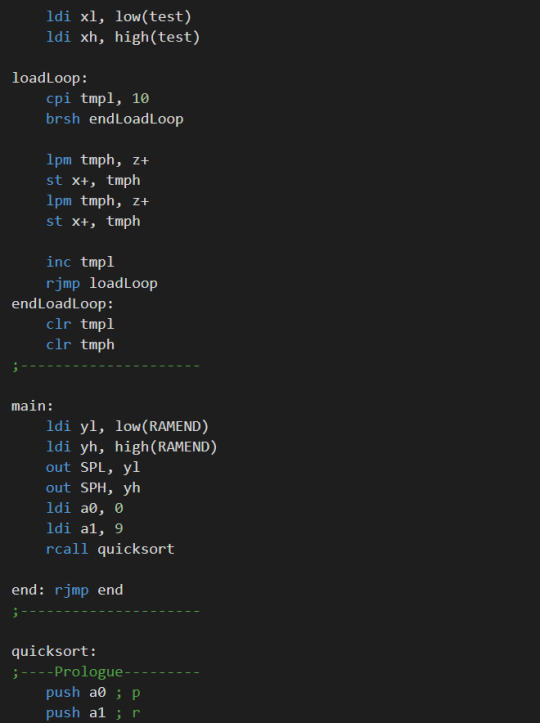
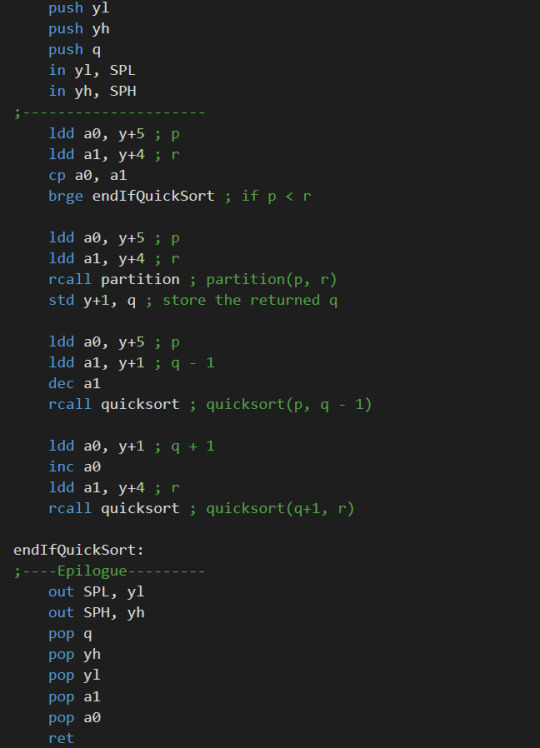
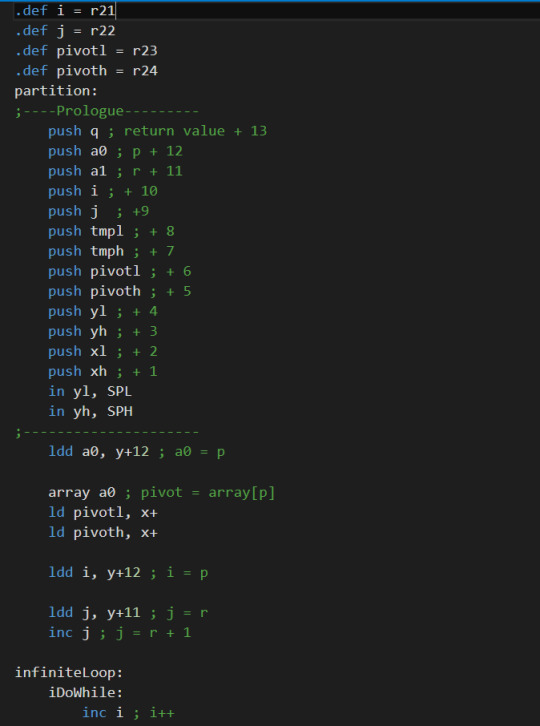
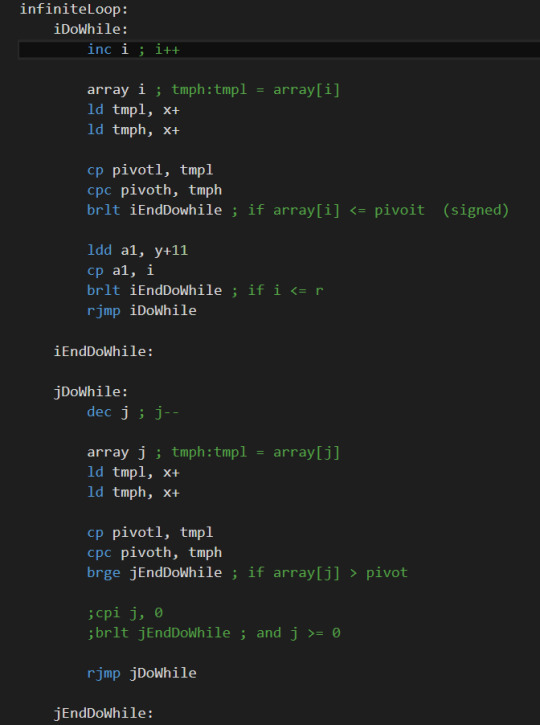
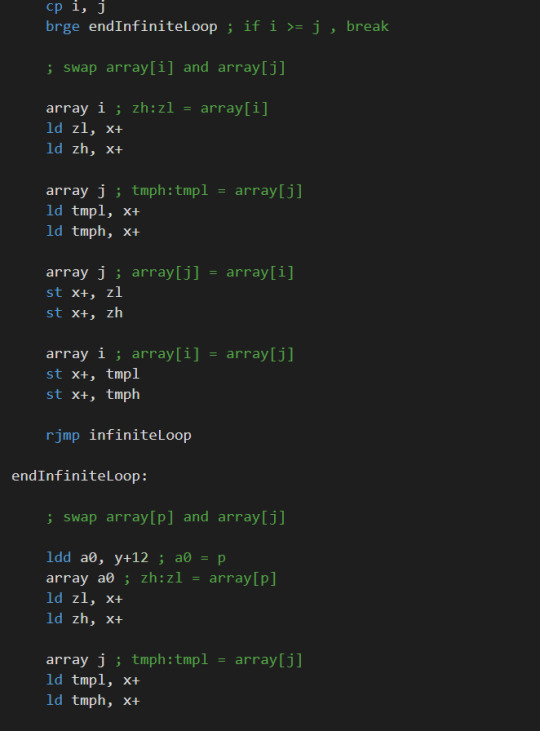
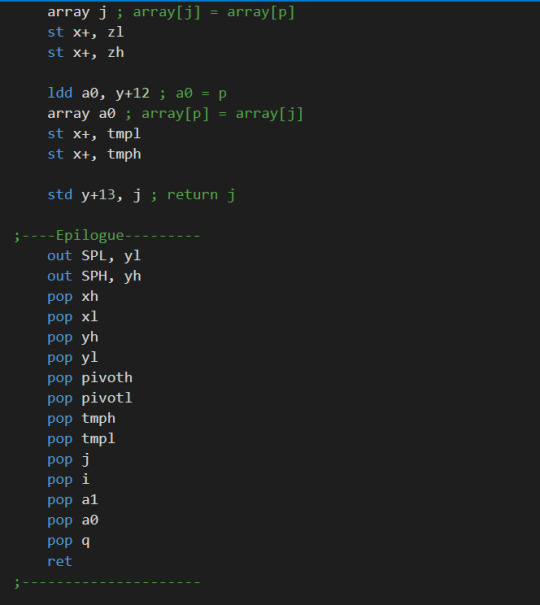
It is really challenging but rewarding.
0 notes
Text
Case Study
Design methods to protect a facility
- Physical:
Make the facility hard to find, hide somewhere or make it look normal (secure by obscure)
The walls and doors should be more solid than regular
Surveillance
Don’t let the employees know where the facility is: blindfold the employees (secure by obscure)
- Non-physical:
Background check
Use metal materials to build the walls (prevent side-channel attack)
Whistle blow mechanism (for staff members to anonymously report the potential compromise happened on some employees)
Bind employees’ interest in the company: company share
Let the employees know only what they need to know (Bell Lapadula model)
Source code auditing
Back up, redundancy (prevent single point of failure)
0 notes