#Australian Address Database
Explore tagged Tumblr posts
Text
#Australian Address Database#High-Quality Address Lists#Lead Generation Address Lists#NSW Postcode Address Data
0 notes
Text
Western Australia Postcode Data - DataTools Verified Address Lists
Get reliable WA postcode address data with verified residential, unit, and geographic info. Ideal for sales, research, logistics, and data-driven strategies. Download Western Australia address lists instantly for accurate results.
#Western Australia Address Lists#Australian Address Database#Targeted Address Lists#Residential And Business Address Lists
0 notes
Text
Disability Aid Databases
Hey!
So. Originally this was going to just be a quick little post where I shared four databases I've found that really help me when it comes to updating my resource. However! In doing that, I discovered more??
These are essentially sites that collect a big list of different disability aid suppliers, specialists and support services across different countries and continents and then list them all for easy access.
And now I'm listing them here so you can access them! 😁[grinning face emoji]
-
Assistive Technology Australia: Australian Database Personally, I quite like the little pictures they use for their categories. I think it's quite well organised, although it took a little while to get used to. This site is in English.
Canadian Disability Resource Society: Canadian Database I found this site just a little harder to use than some of the others, but after playing around a bit I got the hang of it. I like that you can search by specific keywords and postcodes. I think the contact details are also very clear, and there is an online chat function if you run into any issues. There are extensive language choices for this site.
Disability Info South Africa: South African Database Just going to put a quick warning for potential eye strain and/or flashing lights here as there's a moving graphic on the home page. However, I really like the fact you can change the font size and contrast of the page. I do think the site is a bit wordy but it's so good; there's a lot of information and advice on here once you know where to look. This site is in English.
EASTIN: European Database This might be a bit difficult to use at first, but the search function on this site is so specific it's honestly incredible. It acts as a big data hub for disability aid databases across Europe. Also, there are extensive language options for this site, including mostly European languages, Arabic, Hebrew, Chinese and Thai!
Handicat: French Database Again, I like the little pictures for the categories. It gives a good visual representation of each area before you've even read the category title. There's also a little tool that lets you search by trade name, the type of product and the manufacturer. This page is in French.
Hjælpemiddelbasen: Danish Database Or, AssistData. This site lets you search for disability aids by purpose/classification and target group (i.e. disability). It also offers guides on choosing and maintaining different items. I like that the search function also has the option to include discontinued items. You can change the language of this site to either English or Dansk.
Living Made Easy: UK Database Or, the Disability Living Foundation. This was actually the first one I found. The organisation system isn't as specific as some of the others but I quite like that everything is still separated by category, and it's not too overwhelming. This site is in English.
REHADAT: German Database I really like the organisation of this site, but I'm going to put a warning for potential eye strain here as some of the blue graphics are a bit faded and hard to see despite the dark background. As well as assistive technology, this site also offers information on things like disability law, education, employment and financial advice, and addresses and contacts for additional support services. You can change the language of this site to either English or Deutsch.
SIVA: Italian Database I think this site is a little confusing, but I like the guided search and advanced search functions. You can really get down into the specifics of what you're looking for. You can change the language of this site to either English or Italian.
-
Unfortunately, there were a couple of extra databases that I couldn't access, but if I find any others then I will update this post.
Let me know if there's anything you want me to add/change!
#resources#disability resources#disability resource#disability aids#disability aid resources#assistive technology#databases#database#disability databases#informative#psa#links#long post#please add to this
81 notes
·
View notes
Text

THE eSAFETY PROBLEM
The eSafety Commisioner holds office under the Online Safety Act 2021. This world-first attempt at regulating the internet has instead been a disaster for Australians and our international reputation.
Whilst the Online Safety Act 2021 was supposed to have safeguards protecting political expression, the Commissioner has been able to entirely circumvent them. Her office has acted in a partisan manner pursuing political vendettas. It is time to put an end to this failed experiment.
Commonly asked questions
Q. What is the Online Safety Act 2021?
The Online Safety Act is the primary legislation that governs the 'eSafety Commissioner'. It provides a range of powers that allow for content to be ordered to be removed from the internet.
Q. What has gone wrong with the Online Safety Act 2021?
In short, it has been misused. Rather than protecting the public, the eSafety Commissioner has engaged in removing material for political purposes. People who have been genuinely subject to abuse have not been protected, whilst her office has waged political crusades. The result has been to undermine Australian democracy and damage Australia's international reputation.
Q. The Online Safety Act 2021 has safeguards? Surely they could stop this?
Unfortunately, with these types of powers, the safeguards are easily avoided. The Commissioner fails to give notice to all the affected people, thus limiting challenges. Her office also simply ignores many of the constraints in the legislation, including the requirement that she is not entitled to intervene with the implied freedom of political communication.
Q. Who is behind this petition?
The Free Speech Union of Australia. We exist to protect and promote Freedom of Expression for all Australians. To find out more, follow our Twitter feed, or visit our website, where you can join us.
Q. What will happen with signatures?
We will deliver a list of names and postcodes to Parliament in due course. Your email address information will only be known to the Free Speech Union of Australia.
Further questions about the eSafety Commissioner
Q. Doesn't eSafety keep people safe on the internet? Why would you abolish them?
The claims that the eSafety Commissioner is effective at keeping people safe on the internet is a myth. They have issued very few formal notices. For children, she issued a grand total of 13 notices in the space of a year, which were letters to School Principal's telling them to stop particular children bullying others.
The 'informal' investigations are also ineffective. It is easier to report directly to platforms, rather than contacting the eSafety Commissioner. Here's an illustration.
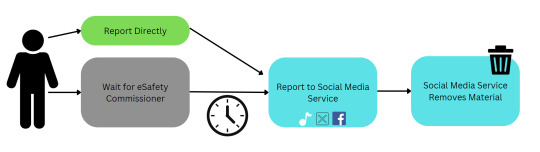
Q. Hang on, the eSafety Commissioner says that they do ten's of thousands of investigations a year? Is that true?
It depends what you consider to be an 'investigation'. If reading a report saying a post is 'bad' and taking a few minutes to decide if that complaint is justified counts as an investigation, then the Commissioner is right.
The truth is that this activity is done millions of times a day by each social media provider, when they moderate posts, one can see the scale in the European Union's own database. On that basis, we would say the the eSafety Commissioner is considerably exaggerating what they do.
Q. How is the eSafety Commissioner a threat to the internet and democracy?
Her approach is authoritarian. You don't need to take our word for it. The Electronic Frontier Foundation has said that the injunction she sought "set[s] a dangerous precedent that could legitimise practices of authoritarian governments, which do not fully value the rights to freedom of speech and access to information."
They also noted that her approach risks "a fragmented and splintered internet, undermining freedom of expression and access to information worldwide".
In the XCorp proceedings, she has also been alleged to exceed her jurisdiction, in other words, purport to exercise legal powers she does not have. We are also aware of her failing to give end users notice of their appeal rights (thus making it impossible for them to challenge). This makes her conduct even more worrying.
Q. How can we keep children safer on the internet without the eSafety Commissioner?
There are many answers. It starts with parental responsibility and controlling the use of devices. For example, it is possible for parents to take steps to keep children away from social media, or limiting access at the device level.
The idea that an eSafety Commissioner will help by taking down content is untrue. In respect of genuine abuse, existing platforms have very powerful incentives. Advertisers do not wish to see their content next to porn, or genuine cyber-abuse. Unfortunately, the eSafety Commissioner spends their days targeting other material, including lawful political speech.
If there is a need for the issue of take down notices, then this should be done judicially, following a professional process. For example, New Zealand's process has the safeguard of requiring this to be done with a judicial officer involved, as well as a technology expert to advise on appropriate action. Australia has one unaccountable person attempting to do this, namely the eSafety Commissioner.
Q. What is happening in the X case that is currently before the Federal Court of Australia?
The eSafety Commissioner obtained an temporary injunction seeking to enforce its original notice to take down a video of Mar Mari Emmanuel. X have challenged this injunction, as well as the underlying notice.
The legal arguments primarily concern:
What content the eSafety Commissioner is entitled to ban as likely being 'Refused Classification' content.
What steps are 'reasonable' for X to take the material unavailable to Australians.
Whether there was a valid notice to begin with.
We expect these arguments and the parties positions will evolve throughout the case.
Q. What is the main difference between X's case and Billboard Chris's case?
They are under different sections of the Act. In X's case, the Commissioner claimed it was due to the video likely being 'RC' (or Refused Classification) rated content, and thus should be taken down. The main error is that it is unlikely to meet that standard.
In Billboard Chris's case, the claim is that it was 'adult cyber abuse', namely content targeted at an individual (Teddy Cook), with a view towards causing him serious psychological harm. The main legal error is that the removal notice was aimed at material that does not meet the statutory definition of adult cyber abuse. It was not targeted at an Australian adult and was a relatively mild political statement. There was nothing obscene or violent about it.
As it does not meet the statutory definition, the Commissioner simply had no jurisdiction to issue the notice.
Q. What does X's case and Billboard Chris's case have in common?
They reflect the same conduct of the eSafety Commissioner in exceeding her jurisdiction and misunderstanding her powers. They also both illustrate the risks of setting up an eSafety Commissioner and giving one person the purported power to police the internet.
==
Australia's "eSafety Commissioner" is a known disgruntled ex-Twitter employee with an authoritarian streak, who has a vendetta against Elon Musk, and is abusing her unnecessary position to wage her personal war.
If you're an Australian and care about free speech and opposing censorship, sign the petition from the Free Speech Union of Australia.
#Free Speech Union of Australia#Australia#Free Speech Union#Julie Inman Grant#censorship#eSafety Commissioner#free speech#freedom of speech#internet censorship#authoritarianism#religion is a mental illness
6 notes
·
View notes
Text
Police and federal agencies are responding to a massive breach of personal data linked to a facial recognition scheme that was implemented in bars and clubs across Australia. The incident highlights emerging privacy concerns as AI-powered facial recognition becomes more widely used everywhere from shopping malls to sporting events.
The affected company is Australia-based Outabox, which also has offices in the United States and the Philippines. In response to the Covid-19 pandemic, Outabox debuted a facial recognition kiosk that scans visitors and checks their temperature. The kiosks can also be used to identify problem gamblers who enrolled in a self-exclusion initiative. This week, a website called “Have I Been Outaboxed” emerged, claiming to be set up by former Outabox developers in the Philippines. The website asks visitors to enter their name to check whether their information had been included in a database of Outabox data, which the site alleges had lax internal controls and was shared in an unsecured spreadsheet. It claims to have more than 1 million records.
The incident has rankled privacy experts who have long set off alarm bells over the creep of facial recognition systems in public spaces such as clubs and casinos.
“Sadly, this is a horrible example of what can happen as a result of implementing privacy-invasive facial recognition systems,” Samantha Floreani, head of policy for Australia-based privacy and security nonprofit Digital Rights Watch, tells WIRED. “When privacy advocates warn of the risks associated with surveillance-based systems like this, data breaches are one of them.”
According to the Have I Been Outaboxed website, the data includes “facial recognition biometric, driver licence [sic] scan, signature, club membership data, address, birthday, phone number, club visit timestamps, slot machine usage.” It claims Outabox exported the “entire membership data” of IGT, a supplier of gambling machines. IGT vice president of global communications Phil O’Shaughnessy tells WIRED that “the data affected by this incident has not been obtained from IGT,” and that the firm would work with Outabox and law enforcement.
[...]
Floreani of Digital Rights Watch says that the incident illustrates the “significant negative consequences” that can arise from collecting sensitive biometric data. “We need bold privacy reform and strict limitations on facial recognition technology,” she says. “As always, surveillance isn’t safety.”
2 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
Australian popping in. i sent this to our government through the parliament website
"
I do not wish to be writing this, I would hope that the people we, as Australians, elect to our parliament would have the mind to ask us, as Australians,what we want and need.
The Social Media ban, is a bad idea that excuses negligent parenting and actively makes life harder for Queer and minority teenagers to seek support and normalisation in a society hostile towards our existence.
The bill allows the sharing of data with third parties including location and private information which empowers fishing schemes and insurance discrimination.
The date gathering is encouraged with no clear opt out enshrined into the TOS (that's terms of Service, since the government seems to have a thoroughly limited view of the internet as a landscape). The data collection requirements are also allowed to be expanded with no input from parliament or the people.
Considering the historical weakness of government databases I am sceptical of any demands for private information.
not to mention how this will isolate Queer and disabled teenagers looking for support groups and information. Many of us used social media as a mode for self discovery and connection with communities, if you take that away their blood will be on your hands. It’s a bandair solution which could work if we were talking about a benign cut but the problems that this bill purports to address are much more complex than taking the site away. Parents need to be equipped, kids need to be taught things like empathy and resilience. This bill is just the same rhetoric which has seen so many robbed of their human rights and dignities.
If this sounds too aggressive that's because it is, because this problem is important. The government either needs to drip the bill, edit it heavily or own up to the truth; that this is a surveillance bill with no ones safety in mind.
While it is still not too late, I would encourage you to speak up or send this to any senate members you have access to and think about what the government is doing. This bill cannot pass as it is, if we want to keep people safe.
Best"
If you live in Australia you can submit and inquiry at https://www.aph.gov.au/Parliamentary_Business/Committees/Senate/Environment_and_Communications/SocialMediaMinimumAge
You can also follow LillahRPG on Tik Tok they have great information about the bill and why it's a glorified surveillance bill
Be aware: Australia is likely implementing a bill similar to KOSA. However it is a complete ban for social media for under 16 year olds. Raise awareness about this like you did for KOSA.
#Australia social media ban#tumblr#hellsite#hellsite (derogatory)#important#please#ASMB#auspol#australia
2K notes
·
View notes
Link
0 notes
Text
AML Tranche 2 for Accountants: What You Must Know Now
As the Australian government moves closer to implementing AML Tranche 2 reforms, accountants across the country are facing a new regulatory landscape. These changes are not just compliance requirements—they are critical measures aimed at strengthening Australia’s financial system against money laundering and terrorism financing.
In this blog, we’ll explore what AML Tranche 2 means for accountants, why it matters, and how to prepare. With practical steps, compliance tips, and solutions from NameScan, this guide will help you stay ahead of the curve.
What is AML Tranche 2?
AML Tranche 2 refers to the proposed expansion of the Anti-Money Laundering and Counter-Terrorism Financing (AML/CTF) Act to cover high-risk sectors such as lawyers, accountants, real estate agents, and trust and company service providers (TCSPs).
Currently, Australia’s AML/CTF laws primarily apply to the financial services sector. However, under pressure from international bodies like the Financial Action Task Force (FATF), Australia is taking steps to broaden its AML/CTF coverage—hence, the introduction of Tranche 2.
Once implemented, accountants will be required to adopt full AML/CTF compliance programs, including customer due diligence (CDD), transaction monitoring, suspicious matter reporting, and recordkeeping.
Why AML Tranche 2 Matters for Accountants
Accountants often handle large financial transactions, corporate structuring, and tax matters—areas that are susceptible to abuse by criminals seeking to launder illicit funds. AML Tranche 2 aims to ensure that accountants are no longer an unregulated entry point into the financial system.
Key Risk Areas for Accountants:
Assisting clients with company formation
Managing trust accounts
Providing tax or financial advice involving large transactions
Handling international transfers
Failing to address these risks could expose accountants to legal penalties and reputational damage.
What Will Change Under AML Tranche 2?
Once AML Tranche 2 is enacted, accountants will face several new compliance obligations, including:
1. Customer Due Diligence (CDD)
Accountants must verify client identity, assess the purpose and intended nature of the business relationship, and understand the source of client funds.
2. Ongoing Monitoring
You’ll need to implement systems to continuously monitor business relationships and transactions for unusual or suspicious activity.
3. Suspicious Matter Reporting (SMR)
Any activity suspected to be linked to money laundering or terrorism financing must be reported to AUSTRAC immediately.
4. AML/CTF Program Implementation
You’ll need to develop and maintain an AML/CTF compliance program, including risk assessments, policies, procedures, and staff training.
5. Recordkeeping
Keep detailed records of client identification, transactions, and AML procedures for at least seven years.
How Accountants Can Prepare for AML Tranche 2
With the introduction of AML Tranche 2 on the horizon, accountants must start preparing now to ensure compliance and avoid regulatory penalties.
Step 1: Conduct a Risk Assessment
Understand the specific money laundering risks associated with your services and clients. Assess which services might be vulnerable and design risk mitigation strategies.
Step 2: Develop an AML/CTF Program
Create a comprehensive AML/CTF program tailored to your accounting practice. This should include internal controls, employee training, and independent reviews.
Step 3: Implement Identity Verification Systems
Use reliable Know Your Customer (KYC) tools to verify client identities efficiently. Automating this process reduces human error and speeds up onboarding.
Step 4: Leverage AML Screening Tools
Tools like NameScan provide real-time screening against global watchlists, sanctions lists, and Politically Exposed Persons (PEPs) databases. This is vital for identifying high-risk clients and transactions.
Step 5: Stay Informed and Educate Staff
Regular training ensures your team understands AML obligations and how to spot red flags. Keep up with guidance from AUSTRAC and the accounting industry.

Why Use NameScan for AML Compliance?
NameScanoffers a suite of powerful and cost-effective tools designed to help accountants meet AML/CTF obligations with ease:
PEP & Sanction Screening Instantly screen clients against global watchlists and identify politically exposed persons.
Ongoing Monitoring Get real-time alerts when client risk status changes.
Adverse Media Checks Monitor clients for negative news or risk indicators that may not appear on official watchlists.
Risk Assessment Reports Generate clear reports that support your compliance documentation.
With automated workflows and advanced risk detection, NameScan helps streamline your AML processes, reduce manual effort, and ensure your practice remains compliant under Tranche 2.
Explore NameScan's AML solutions for accountants
Semantic SEO Keywords Naturally Included:
AML Tranche 2 for Accountants
AML/CTF compliance for accountants
Know Your Customer for accountants
AML risk assessment accounting firms
PEP and Sanctions screening
AML software for accountants
AUSTRAC reporting for accountants
Frequently Asked Questions (FAQ)
Q1: When will AML Tranche 2 be implemented in Australia?
The government has announced its commitment to implementing AML Tranche 2, with legislation expected soon. However, no exact date has been set. Accountants are advised to begin preparations now.
Q2: Are all accountants affected by AML Tranche 2?
Only those providing services that may involve financial transactions, such as managing client funds, setting up companies, or offering tax planning, will fall under the scope.
Q3: What happens if I don’t comply with AML/CTF obligations?
Non-compliance may result in significant penalties, legal action, and reputational harm. It could also put your clients and business at risk of being exploited for money laundering.
Q4: Can small accounting firms manage AML compliance affordably?
Yes. Tools like NameScan are scalable and affordable, offering tailored solutions for small to medium accounting practices.
Q5: Where can I find guidance on AML Tranche 2 requirements?
Refer to AUSTRAC’s official website for regulatory updates and guidelines. You can also explore educational resources provided by industry bodies and compliance platforms like NameScan.
Final Thoughts
The introduction of AML Tranche 2 for Accountants marks a significant shift in regulatory responsibilities. While the new obligations may seem daunting, they are a necessary step in protecting Australia’s financial integrity. By preparing now and leveraging digital compliance tools like NameScan, accountants can ensure smooth adoption, reduce risk, and build client trust.
✅ Ready to Future-Proof Your Accounting Practice?
Let NameScan help you stay compliant, secure, and efficient. 👉 Start your AML compliance journey with NameScan today
#AML Tranche 2 for Accountants#tranche 2 aml for tcsps#aml/ctf act#aml checks for legal industry#aml/ctf rules in australia
0 notes
Text
Overcoming Cloud Migration Challenges with Microsoft Azure

In today’s fast-paced digital economy, cloud migration has become a strategic imperative for businesses striving for agility, scalability, and innovation. However, migrating to the cloud is not without its challenges. From technical complexities to organizational resistance, businesses often encounter roadblocks that can delay or derail their migration plans.
That’s where Microsoft Azure comes in—not just as a cloud platform, but as a comprehensive ecosystem designed to simplify and accelerate cloud migration. In this article, we’ll explore common Azure cloud migration challenges and how Azure helps businesses overcome them efficiently and effectively.
The Growing Need for Cloud Migration
As companies adopt hybrid work, AI-powered tools, and data-intensive applications, traditional on-premises infrastructure is proving inadequate. Cloud migration offers:
Scalability to support fluctuating workloads
Cost-efficiency through pay-as-you-go models
Security and compliance with global standards
Faster innovation through automation and integrated services
Despite these benefits, many organizations hesitate due to the perceived risks and challenges involved in the migration journey.
Common Cloud Migration Challenges
Let’s take a closer look at the top hurdles companies face when moving to the cloud:
1. Lack of a Clear Migration Strategy
Many organizations jump into migration without a clear roadmap, resulting in cost overruns, missed deadlines, or application failures.
2. Data Security and Compliance Concerns
When moving sensitive workloads to the cloud, organizations fear data breaches, compliance violations, and loss of control over their data.
3. Downtime and Business Disruption
A poorly planned migration can cause unexpected system outages or performance issues, disrupting business continuity.
4. Legacy System Dependencies
Old applications often have tight integrations or outdated architectures that make cloud transition difficult.
5. Skill Gaps and Resistance to Change
Internal teams may lack the cloud expertise needed to manage the transition effectively. Additionally, organizational resistance to change can slow down adoption.
6. Cost Management
Without proper cost forecasting and governance, businesses may overspend on cloud resources or underutilize their investments.
How Microsoft Azure Helps Overcome These Challenges
Microsoft Azure offers a powerful suite of tools, frameworks, and services that directly address the above obstacles. Here's how:
1. Strategic Planning with Azure Migrate
Azure Migrate is Microsoft’s all-in-one hub to assess, plan, and execute migrations. It provides:
Discovery tools to assess your current environment
Dependency mapping to understand application relationships
Cost estimation calculators to budget effectively
Readiness reports to reduce guesswork
By providing a structured approach, Azure Migrate ensures that you move the right workloads at the right time, with minimal risk.
2. Built-In Security and Compliance Tools
Azure is built with zero-trust architecture and offers more than 100 compliance certifications, including:
ISO/IEC 27001
GDPR
HIPAA
IRAP (for Australian government workloads)
Tools like Microsoft Defender for Cloud and Azure Security Center help monitor workloads, detect threats, and ensure secure configurations across hybrid environments.
3. Minimal Downtime with Azure Site Recovery
Azure Site Recovery enables real-time replication of workloads, allowing you to:
Perform non-disruptive testing
Set up automated failovers
Maintain business continuity during migration
It’s especially useful for migrating critical applications like databases, ERP systems, and financial platforms that require zero or minimal downtime.
4. Modernizing Legacy Systems with Azure App Services and Containers
Azure supports various modernization strategies:
Rehosting legacy apps to Azure VMs
Refactoring with Azure App Services or Azure Kubernetes Service (AKS)
Rearchitecting monolithic applications into microservices
Azure's hybrid support and integration with Visual Studio and GitHub make modernization more accessible—even for outdated tech stacks.
5. Bridging Skill Gaps with Azure Learning and Managed Services
Azure provides extensive training resources, including:
Microsoft Learn and Azure certifications
Partner-led migration services for enterprises lacking in-house expertise
Azure Lighthouse to manage multiple tenants securely through a single portal
Plus, Azure’s native integrations with Microsoft 365 and Dynamics 365 reduce the learning curve for teams already familiar with Microsoft ecosystems.
6. Cost Optimization with Azure Cost Management
Azure includes tools to monitor and optimize cloud spend:
Azure Pricing Calculator to estimate costs before migration
Cost analysis dashboards to track usage and avoid overruns
Budgets and alerts to ensure governance
Additionally, features like Azure Reserved Instances, Spot VMs, and Hybrid Use Benefits can help you save up to 72% on long-term workloads.
Tips for a Smooth Azure Cloud Migration
Whether you're planning a full-scale migration or a phased hybrid approach, keep these tips in mind:
✅ Start Small and Scale
Begin with non-critical workloads to build confidence and learn from experience.
✅ Focus on Business Goals
Align your migration roadmap with business outcomes like performance improvement, cost reduction, or faster go-to-market.
✅ Involve All Stakeholders
IT, security, finance, and business units must collaborate to ensure a successful transition.
✅ Monitor and Optimize Continuously
Post-migration, continue to analyze performance, usage, and costs to maximize ROI.
Final Thoughts
Cloud migration doesn't have to be risky or disruptive. With the right strategy, tools, and partner ecosystem, Microsoft Azure empowers businesses to overcome migration challenges and unlock the full benefits of the cloud.
Whether you're modernizing legacy apps, expanding globally, or preparing for AI-powered transformation, Azure provides the flexibility, security, and scalability your business needs.
#cloud migration services#azure cloud solution#azure cloud migration#azure migration services#microsoft azure migration#azure migration strategy#cloud migration services companies
0 notes
Text
Scraping WhitePages Business Directory by DataScrapingServices.com

Scraping WhitePages Business Directory by DataScrapingServices.com
In the digital age, data plays a pivotal role in driving business growth, especially for companies seeking targeted leads and contacts. Scraping business directories like WhitePages can offer valuable insights into potential clients, partners, or competitors. WhitePages Business Directory Scraping by DataScrapingServices.com provides an efficient way to extract critical data, helping businesses make informed decisions and drive successful marketing campaigns.
Scraping the WhitePages Business Directory provides businesses with invaluable insights for lead generation, customer outreach, and competitive analysis. By extracting essential data like business names, contact details, emails, and addresses, companies can build targeted marketing campaigns and reach potential clients effectively. Additionally, gathering business ratings, reviews, and industry categories allows businesses to analyze competitors and market trends. DataScrapingServices.com offers customized WhitePages scraping solutions to ensure accurate, up-to-date information that helps businesses optimize their marketing strategies and drive growth.
List of Data Fields
Our WhitePages Business Directory Scraping service gathers comprehensive and essential information, including:
- Business Name
- Contact Person
- Phone Numbers
- Email Addresses
- Business Addresses
- Industry Categories
- Website URLs
- Business Ratings and Reviews
- Operating Hours
By capturing these data points, businesses gain access to a wealth of information to refine their strategies and target specific markets with precision.
Benefits of Scraping WhitePages Business Directory
1. Targeted Lead Generation: Extracting accurate contact details such as phone numbers, emails, and business addresses helps companies build high-quality lead databases, enhancing outreach efforts and boosting conversion rates.
2. Cost-Effective Marketing: With comprehensive data from WhitePages, businesses can focus their marketing efforts on the most relevant contacts, reducing wasted resources and improving the efficiency of campaigns.
3. Competitive Advantage: By analyzing competitor information such as business ratings and reviews, companies can identify market gaps, trends, and strategies that give them an edge over their competitors.
4. Business Expansion: For businesses looking to expand into new geographic locations or industries, our WhitePages scraping service provides the insights necessary to navigate unfamiliar markets effectively, offering direct access to potential partners or clients.
5. Improved Customer Relationships: By understanding customer feedback through ratings and reviews, businesses can improve their services and tailor their offerings to meet the evolving needs of their clientele.
Best Business Directory Scraping Services Provider
Scrape Australian Businesses Listing from Truelocal
Scrape Business Listings from FreeIndex
Yellowpages.com Business Data Extraction
Aussieweb.com.au Business Data Extraction
Extract Business Listings from Thomsonlocal
Scraping Plumber Listings from Ezlocal.com
Owler.com Business Information Scraping
Gelbeseiten.de Business Directory Data Scraping
Google Map Businesses Data Scraping
Goldenpages.bg Data Extraction
Best Scraping WhitePages Business Directory Services in USA:
Nashville, Denver, Colorado, Fresno, Sacramento, El Paso, Washington, Fort Worth, Kansas City, Orlando, San Francisco, Sacramento, San Jose, Boston, Albuquerque, San Francisco, San Diego, Raleigh, Long Beach, Omaha, Mesa, Bakersfield, Atlanta, Indianapolis, Virginia Beach, Oklahoma City, Wichita, Columbus, Milwaukee, Colorado, Louisville, Charlotte, Tulsa, Las Vegas, Jacksonville, Austin, Philadelphia, Houston, Chicago, Memphis, San Antonio, Seattle, Dallas, Orlando, Long Beach, Fresno, New Orleans, Tucson and New York.
Conclusion
At DataScrapingServices.com, our WhitePages Business Directory Scraping solution offers an indispensable tool for businesses looking to maximize their marketing efforts and improve lead generation. Whether you're looking to expand into new markets or enhance your existing customer base, our tailored data extraction services will provide the actionable insights you need to succeed. Contact us today at [email protected] for customized solutions that fit your business goals.
Website: Datascrapingservices.com
Email: [email protected]
#scrapingwhitepagesbusinessdirectory#whitepagesbusinessdetailsextraction#usabusinessdirectoryscraping#usabusinessdatascraping#businessdirectorydatascraping#businessdirectoryscraper#datascrapingservices#webscrapingexpert#websitedatascraping
0 notes
Text
How Does AusPost Address Validation Work?

Accurate address data is crucial for efficient mail delivery, customer satisfaction, and operational efficiency. Australia Post (AusPost) offers robust address validation solutions to ensure that addresses are correct, standardized, and deliverable. This article delves into how AusPost's address validation works, its components, benefits, and implementation strategies.
Understanding Address Validation
Address validation is the process of verifying and correcting addresses to match the standardized format recognized by postal services. It ensures that mail reaches the intended recipient without delays or returns.
Components of AusPost Address Validation
1. Real-Time Address Validation
AusPost's real-time address validation checks and corrects addresses at the point of entry. This immediate verification ensures that addresses are accurate and standardized before being used for mailing or storage. The system leverages advanced validation tools to guarantee address accuracy .
2. Address Matching Approval System (AMAS)
The Address Matching Approval System (AMAS) is a certification program that measures the accuracy of address matching software. AMAS confirms that your software can match and correct addresses to the standard recognized by AusPost, ensuring consistency and reliability in mail delivery .
3. Postal Address File (PAF)
The Postal Address File (PAF) is a comprehensive database containing every address recognized by AusPost. It is updated monthly and sourced from AusPost's core address management database, ATLAS. ATLAS is updated daily through modifications from postal delivery staff and state address management teams liaising with local councils .
Benefits of Using AusPost Address Validation
Improved Delivery Accuracy: Validated addresses reduce the risk of mail being returned due to incorrect or incomplete information.
Cost Savings: Minimizing undeliverable mail saves on postage, printing, and operational costs.
Enhanced Customer Satisfaction: Ensuring timely and accurate deliveries improves customer trust and loyalty.
Data Quality Maintenance: Regular validation keeps your address database current, especially important as approximately 1.14 million Australians move house annually .
Implementing AusPost Address Validation
Step 1: Integrate Real-Time Validation
Incorporate real-time address validation into your data entry systems to ensure addresses are checked and corrected as they are entered. This can be achieved through APIs or software solutions compatible with your existing systems.
Step 2: Utilize AMAS-Certified Software
Ensure your address matching software is AMAS-certified to guarantee it meets AusPost's standards for address accuracy. This certification confirms that your software can effectively match and correct addresses.
Step 3: Access and Maintain PAF Data
Regularly update your address database using the latest PAF data to ensure you have the most current address information. This practice helps in maintaining data accuracy and reliability.
Conclusion
AusPost's address validation services are essential tools for businesses aiming to ensure accurate mail delivery and maintain high-quality address data. By leveraging real-time validation, AMAS-certified software, and up-to-date PAF data, organizations can enhance operational efficiency, reduce costs, and improve customer satisfaction.
youtube
SITES WE SUPPORT
Forward AusPost With Address – Wix
0 notes
Text
Why Land Title Search in Australia is Crucial Before Buying Property?

Regardless of whether the objective is to acquire or sell a property, the first step in each real estate transaction is a land title search in Australia. Verifying land titles is a procedure performed when purchasing real estate in order to determine ownership and check for encumbrances. These days, the greatest websites that provide access to this important information on the legal status of the land are an excellent spot to look for it. After they receive payment from the customer, the top portals offering title search services also send the papers.
Using trustworthy web portals, one can easily conduct a title check and get a certificate of title in Victoria or throughout Australia, making sure they are fully aware of any liens, easements, or restrictions that could be applicable to the property. For Australian property buyers and investors, locating accurate and current title information has never been simpler thanks to the availability of internet tools and services. Using the greatest online portals, you can choose, buy, and obtain the property papers for a specific property.
Let's Examine More Clearly What Important Information These Searches Provide
Reverse title search on certain websites can provide information on transactions, ownership, land descriptions, and more. Clients who want this information can get a certificate of title by providing the property's address or title reference number. These internet search portals give consumers access to a wide range of information, including complete names and current property ownership records. Information on any unregistered deals, pertinent notifications and encumbrances, survey plan number and kind, etc. are also provided.
Keep in mind that the plan can be used to verify the property's borders and that it is a different document from the title. Several documents and information that are useful for various real estate transactions may be found by someone looking for the title.
The plan is a crucial document since it outlines how land allocated inside a specific border may be developed. Understanding the facts and important aspects of the plan is also necessary in the case of a disagreement. To find the necessary paperwork for the property you need, search the top land title database.
Source: https://landtitles.blogspot.com/2025/04/why-land-title-search-in-australia-is.html
0 notes
Text
ASCS Q&A
I hope to create a curation of resources and support available to autistic Australians.
Q. So why the name?
A syndrome is a collection of symptoms that indicate a condition. The DSM, from which the prevalence of the name Autism Spectrum Disorder comes, has never been able to accurately describe the experiences of those living with the condition. Many issues have and will continue to be raised about the DSM and its usefulness as a diagnostic tool. The three-level system is hard to navigate and promotes the unhealthy coping strategy of heavy masking as an indicator of less need for support. Regardless, I am not aiming to rename the condition but wish to highlight a symptomatic approach to support rather than a diagnostic one.
Q. Will the resources be paid?
The goal is to never have people have to pay for support, but I am aiming to change legislation in Australia.
Q. What about the NDIS?
The original goals for the NDIS were to support people with disabilities, both devices used to support people, such as mobility aids, and to higher paid support workers. There was always a focus on creating an industry of providing disability services, which has become counterintuitive to the goal of supporting independence and daily life. There are many examples of the NDIS providing support workers when the funding would be far more impactful if used in other ways.
Q. So what will the focus be on?
For now, the goal is to provide an easy-to-navigate database for autistic life in Australia. Clear guides on what is currently available for adults who can self-manage access and support. This is mostly due to limitations in the scope of a personal project. I do wish to expand. If possible, secondary goals are to rewrite the most used definitions of Autism in Australia and create a service that better addresses the needs of the autistic community, similar to the National Diabetes Services Scheme, addressing a community's needs.
0 notes
Text
Chronic Disease Programmes and Their Contribution to Chronic Disease Management" is a good example of a literature review on nursing. The aim of this work was to identify and review the contribution of current health promotion programs, initiatives, and campaigns in addressing chronic conditions based on their intervention outcomes. In addition, to provide recommendations that can improve their efficiency and effectiveness in meeting their objectives regarding the chronic disease. Methods A systematic review with synthesis of qualitative data was conducted in several databases – Cumulative Index to Nursing and Allied Health Literature (CINAHL), Ovid Medical Literature Analysis and Retrieval System Online (MEDLINE), Excerpta Medica data BASE (EMBASE), PsychLit, the Cochrane Library, the Database of Abstracts of Evidence (DARE), and reports from the Department of Health, Australian Institute of Health and Welfare and Australian Bureau of Statistics. Further results were yielded from the reference lists in articles that were found to be relevant. A total of 25 sources, comprising of 10 articles and 15 reports, were found to be relevant for the literature review, and were, therefore, included in this review. Results There are several health promotion programs, initiatives, and campaigns with intervention activities to prevent, treat and manage chronic disease in Australia. Most of these programs target Indigenous Australians as they are more vulnerable to chronic conditions compared to the rest of the population. Since their commencement, most of these programs have gone a step forward in addressing the burden of chronic conditions in Australia. However, they are more effective in urban areas and still have limited access to services provided by some of the programs, especially for Indigenous people living in very remote areas of Australia. The programs contribute to the country’s effort in reducing the burden of chronic conditions among its populations. This has been achieved through improved access to healthcare and patient support systems for people with chronic conditions, mass media education, and public awareness campaigns. Conclusion The programs reviewed in this literature work were found to be adequately effective in the prevention, treatment, and management of chronic diseases, especially among the Indigenous population. Through program expansion, education, mass media, and training, the public awareness of chronic diseases can be increased to reduce knowledge gaps and improve self-management of chronic conditions. These will make the programs to have a far-reaching impact. The recommendations provided are intended to make the programs more effective in the delivery of their services to people with chronic conditions. Read the full article
0 notes
Text
TL;DR - cannot emphasise enough that I am a mere law student and not giving anybody legal advice. i agree with what previous said about profits. unfortunately even if someone wanted to seek account of profits like prev reblog mentioned, their individual contribution amongst a truly colossal dataset doesn't guarantee a big payout. it could well be infringement, but it might not be worth the legal costs to act on it. depends on the funds you're working with and depends on the lawyers. that said, law evolves over time. governments may decide to build in protections for authors/creators of copyrighted works as far as compensation goes, or maybe attribution rights. also to an extent you can control what your work is used for, but i don't get into the ethics of that here, only an existing legal framework as i understand it.
What I meant with my tags was to agree with previous that yes, people often perceive the law in general to be protecting some ever-changing but identifiable set of 'rights', but that truly depends on what sorts of things your government counts as 'rights' (like human rights). For example there are countries don't have a legal document like a Charter or Bill of Rights. But whether or not such a document exists, the only enforceable 'rights' you have are, as prev said, legal rights and not always ethics-based. There are situations where courts are allowed to intervene because a party's conduct was 'unconscionable', but they don't have to use it. So it's important for people to know that some things they consider 'rights' are not 'legal rights' that you would actually be able to sue someone for. Or that even if you do have certain legal rights, it may not be practical to enforce them for the reason previous reblog mentioned.
For example, in Australia eligible works (i.e. not all) are protectable by copyright with no registration required, giving with it a host of legal rights including what's rather confusingly called 'moral rights' or 'personal rights'. So if I was a photographer and took a copyrightable photograph, then someone uses that photograph in an exhibition but didn't say that I was the photographer, that would probably infringe my right of attribution protected by law. I might be able to get a remedy like an account of profits proportionate to how much my work was part of that exhibition (this is not a realistic example but for explanation only). But as prev mentioned, that's not exactly what AI large language models or image generators are doing. They necessarily use a database of images or texts larger than any human being could possibly consume or draw from, so completely different rules for fair use (as it's known in the US) or fair dealing (as it's known in Australia) are needed. Previous specifically mentioned the transformative works exception, which is the most relevant one in an American context. You'd need new legal definitions of what counts as 'transformation' from precedent (will take time) or from legislation (may take even more time) in order to be able to address this specifically.
Now, jurisdictions like Australia don't actually have a transformative works exception. So should Australian creators or people in countries with no transformative works exception sue image generators and the like? Maybe. Technically any use of your work that isn't private use or under some other exception like research and study purposes is infringement. But again, nobody really has proper legislation about this yet and there isn't much case law yet to rely on. Depends how much money you're willing to throw at it - hence, protection of capital. There are cases being filed right now against companies like OpenAI for copyright infringement and we don't know how it will all shake out yet.
As to what you've said about artistic traditions being rooted in transformation - sure. Many people have had this argument and many people will continue to argue it. I won't discuss the ethics here. But violation of consent to use a work - or rather the failure to get consent in the first place - is something that can be and has been protected outside the exceptions. Copyright actually does give some level of control over what gets associated with your work. There's specifically a 'moral right' sometimes known as the 'right to integrity' for signatories to the Berne Convention (like the EU, the US and Australia), which means people can't take your work and tweak it slightly to be really problematic or something. It's why people couldn't distribute, say, controversial statements accompanied by Mickey Mouse from the Steamboat Willie era until this year when it entered public domain. Obviously the way in which generative software uses works to generate content would look different and the end product might not be prejudicial to creators from the dataset it used, but you definitely can control how your work gets used to an extent. We just don't know what that extent is when it involves AI, or how liable the person using the AI is for what it produces.

26K notes
·
View notes