#Bypass Google Account
Explore tagged Tumblr posts
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
GSMNeo FRP APK: A Complete Guide to Bypassing FRP Lock
Factory Reset Protection (FRP) is a security feature introduced by Google to prevent unauthorized access to Android devices after a factory reset. While this feature is useful for protecting personal data, it can sometimes lock out legitimate users who forget their Google account credentials. One of the popular tools used to bypass FRP is GSMNeo FRP APK. In this guide, we will explore what GSMNeo FRP APK is, how it works, and how to use it safely.

What is GSMNeo FRP APK?
GSMNeo FRP APK is an Android application designed to help users bypass the Google FRP lock on their smartphones. This tool is particularly useful for those who have forgotten their Google account credentials or purchased a second-hand device that is locked.
Features of GSMNeo FRP APK
Bypass Google FRP Lock – Helps unlock Android devices without requiring Google account credentials.
Easy to Use – Simple user interface, making it accessible for non-technical users.
Supports Multiple Android Versions – Works on Android 5.0 (Lollipop) to Android 12 and beyond.
No PC Required – Can be used directly on the smartphone without needing a computer.
Safe and Secure – Designed to bypass FRP without compromising device security.
How Does GSMNeo FRP APK Work?
GSMNeo FRP APK works by exploiting security loopholes in Android's FRP mechanism. The application allows users to access the device’s settings and add a new Google account, effectively bypassing the previously locked account. Here’s a step-by-step overview of how it works:
Download GSMNeo FRP APK – Obtain the APK file from a trusted source.
Install the APK – Enable "Unknown Sources" in your device settings to install the app.
Launch the App – Open the app and follow the on-screen instructions.
Bypass the FRP Lock – Use the provided method to bypass Google verification and regain access to the device.
How to Download and Install GSMNeo FRP APK
Step 1: Enable Unknown Sources
Before installing the APK, enable installation from unknown sources:
Go to Settings > Security.
Find and enable Unknown Sources.
Step 2: Download the APK
Download GSMNeo FRP APK from a reliable website. Ensure the file is free from malware before proceeding.
Step 3: Install the APK
Locate the downloaded APK file.
Tap on it to start the installation process.
Follow the on-screen prompts and complete the installation.
Step 4: Use the Application
Open the GSMNeo FRP APK.
Follow the instructions to bypass the FRP lock.
Add a new Google account to your device.
Is GSMNeo FRP APK Safe?
While GSMNeo FRP APK is a useful tool, users must exercise caution:
Download from Trusted Sources – Avoid fake or malicious versions.
Use Only for Legitimate Purposes – Bypassing FRP on stolen devices is illegal.
Check Permissions – Be wary of apps requesting unnecessary permissions.
Alternatives to GSMNeo FRP APK
If GSMNeo FRP APK does not work for your device, consider these alternatives:
FRP Bypass APK – A similar tool for bypassing Google verification.
Technocare Tricks APK – Works on older Android versions.
D&G Password Unlocker – PC-based solution for FRP removal.
Conclusion
GSMNeo FRP APK is an effective tool for bypassing Google FRP lock on Android devices. However, users must ensure they use it ethically and only for legitimate purposes. Always download from reputable sources and follow best security practices to avoid malware risks. If GSMNeo FRP APK doesn’t work, consider trying alternative FRP bypass methods to regain access to your device.
0 notes
Text
Samsung Galaxy A33 5G SM-A336 FRP Lock Removal Service
Samsung Galaxy A33 5G SM-A336 FRP Lock Removal Service
Get Rid of Google Accounts Quickly and Permanently
When you forget your Google Account password, it can be impossible to Hard Reset or Factory Reset your A33 5G, which leads to activation lock and a frozen screen with a message that says, “Verify Your Account – The device was reset. To Continue. Sign in with a Google Account that was previously synced on this device.” This means that your A33 5G is “Google Account FRP locked.” With our service, you can remove this lock and bypass the Google Account FRP service on your A33 5G device.
What do you need to unlock FRP Galaxy A33 5G?
• IMEI & SN
• Model SM-....
• Good internet speed
Supported devices to bypass FRP lock Samsung A33 5G SM-A336
SM-A336B, SM-A336E, SM-A336M
#Remove Frp Galaxy A33 5G#Unlock Frp Galaxy A33 5G#Bypass Frp Galaxy A33 5G#Frp Lock Sm-A336#Google Account Lock A336
0 notes
Text
So salty right now that Twisted Wonderland is not available in EU. I would love to buy some gems for the Kalim Birthday Event but noooooooooo--- Disney doesn't want my money --- wtf?
#twisted wonderland#I'm finally an adult with my own money#I can spend it however I wish#I know I could bypass this by creating USA google account but#that would require me to use VPN#We will see...#I'm saving for PS5 to...#Too many games to play#Dawntrail happened too
0 notes
Text
Samsung FRP Removal Service By IMEI or Serial Number to Unlock Any Samsung Phone or Tablet Google Account Lock.
There is no need for a remote connection through a Windows PC. All We need is the IMEI or Serial Number of your Samsung Device.
This Samsung FRP Unlock Service can be done instantly within a few working minutes.
Visit the link below or contact us for further information.
If you are a Reseller or repairer, or have bulk orders, then contact us to get the best possible deals.
#samsung#unlock#frp#samsung frp unlock#samsung frp bypass#samsung frp removal#samsung frp unlock by imei#google account unlock#samsung s24 frp unlock#samsung s23 frp unlock#samsung s22 frp unlock#samsung note 20 frp unlock#samsung s21 frp unlock#samsung fold 5 frp unlock#samsung fold 4 frp unlock#samsung fold 3 frp unlock#samsung fold 2 frp unlock#samsung fold frp unlock#samsung flip 5 frp unlock#samsung flip 4 frp unlock#samsung flip 3 frp unlock#samsung flip 2 frp unlock#samsung flip frp unlock#samsung a53 frp unlock#samsung a52 frp unlock#samsung a51 frp unlock#bypass#frp bypass#frp removal
0 notes
Text
FRP Boss Tool
FRP Boss Tool
Support Multi Brands FRP Remove and more
See more click the link below
FRP Boss Tool - FRP Remove Tool (asunlocker.com)
#frp boss tool#frpbosstool#asunlocker#samsung frp remove#samusng frp bypass#frp bypass#honr frp key#honor frp bypass#xiaomi frp remove#xiaomi frp bypass#frp bypass tool#nokia x100 factory reset#nokia x100 frp remove#nokia x100 support tool#samsung account lock remove#samsung account#google account lock#google account lock remove#how to remove frp#how to bypass frp#frp boss tool download
0 notes
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
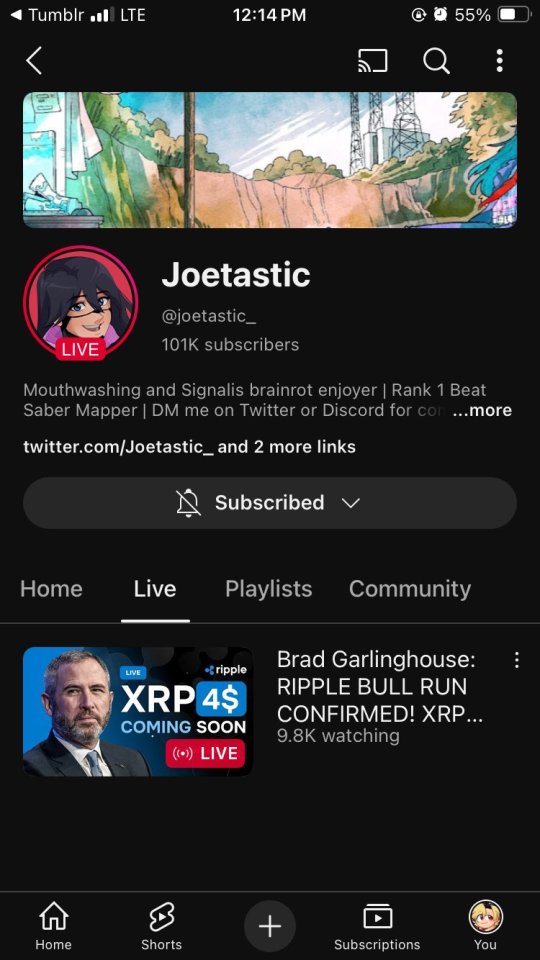
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
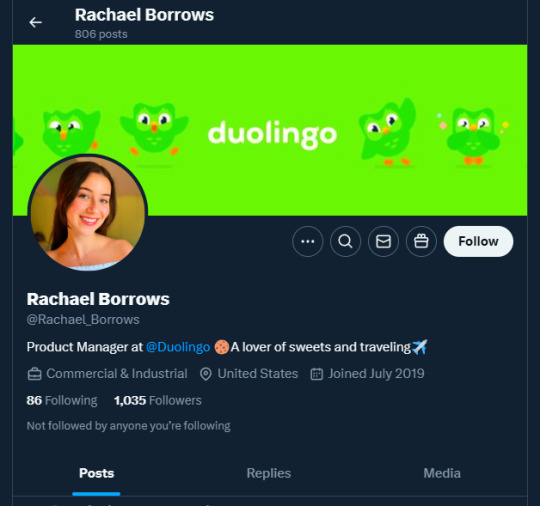
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
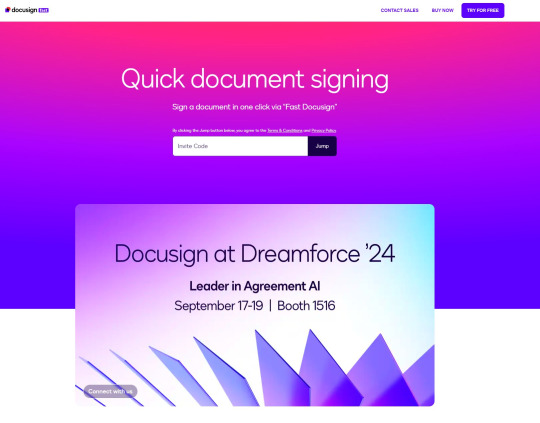
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
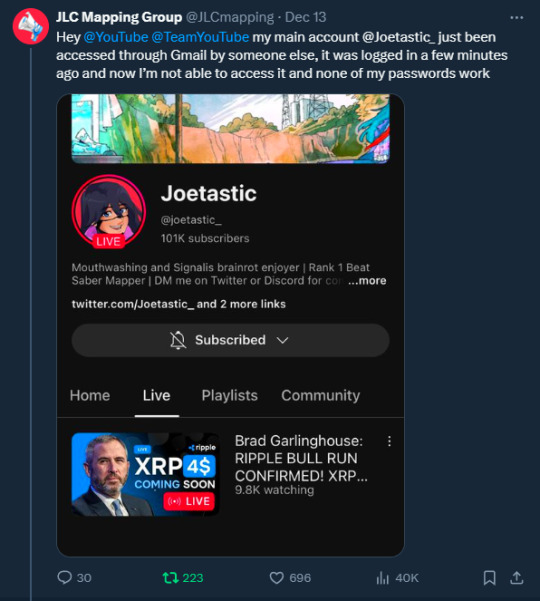
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
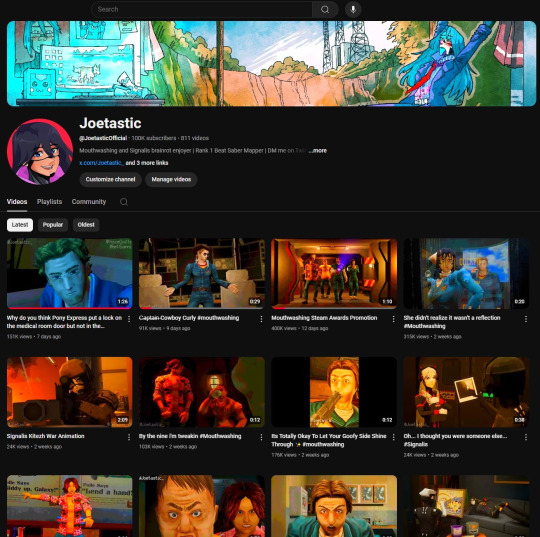
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
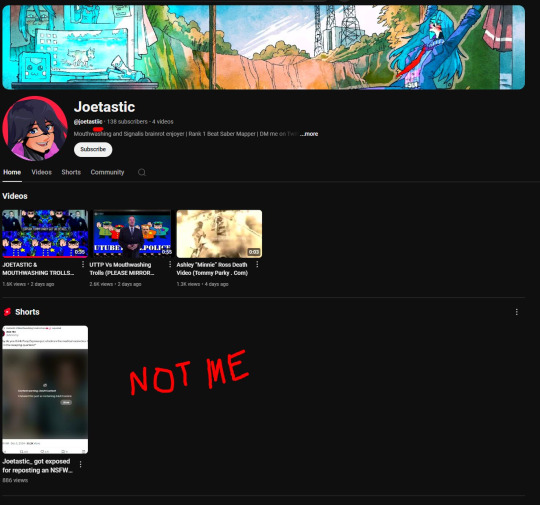
3K notes
·
View notes
Video
youtube
Lg Q52 frp bypass android 12 /All Lg Android 11/12/13 Google account lo...
0 notes
Text

Lei Lume Tablet Google Account, FRP Unlock Service, All Models
+37493890915 whatsapp, Viber, Wechat https://valetunlocking.company.site
0 notes
Video
Oppo A9 2020 (CPH 1937) frp bypass Android 11 تخطي حساب جوجل بعد الفورمات
#youtube#oppo#oppo a9 frp#bypass frp oppo#cph 1937 frp#frp bypass oppo#oppo android 11 frp bypass#remove google account oppo#oppo a9
0 notes
Video
youtube
تخطى حساب جوجل سامسونج جلاكسى ايه 52 اس | FRP Samsung Galaxy A52S 5G SM-...
#youtube#تخطى حساب جوجل سامسونج#سامسونج جلاكسى ايه 52 اس#FRP Samsung#Samsung Galaxy A52S 5G#FRP#تخطى حساب جوجل#removed Google Account Samsung Galaxy A52S 5G#Bypass Google Account Samsung Galaxy A52S 5G
0 notes
Text
got fully locked out of youtube for Using Adblocker crimes today (got a pop-up saying I'd be locked out after 3 videos and then the video player locked down) and after some experimentation discovered that switching to my old YouTube profile that wasn't created via a Google account has bypassed it.
11K notes
·
View notes
Text
Samsung Galaxy A34 5G SM-A346 FRP Lock Removal Service
Samsung Galaxy A34 5G SM-A346 FRP Lock Removal Service
Get Rid of Google Accounts Quickly and Permanently
When you forget your Google Account password, it can be impossible to Hard Reset or Factory Reset your A34 5G, which leads to activation lock and a frozen screen with a message that says, “Verify Your Account – The device was reset. To Continue. Sign in with a Google Account that was previously synced on this device.” This means that your A34 5G is “Google Account FRP locked.” With our service, you can remove this lock and bypass the Google Account FRP service on your A34 5G device.
What do you need to unlock FRP Galaxy A34 5G?
• IMEI & SN
• Model SM-....
• Good internet speed
Supported devices to bypass FRP lock Samsung A34 5G SM-A346
SM-A346B, SM-A346E, SM-A346N, SM-A346M
#Remove Frp Galaxy A34 5G#Unlock Frp Galaxy A34 5G#Bypass Frp Galaxy A34 5G#Frp Lock Sm-A346#Google Account Lock A346
0 notes
Link
In this guide, we will learn the best and easiest method to bypass FRP on Samsung Galaxy a03s A037F and A037M
1 note
·
View note
Text

I know this post is long, but it’s important to read to understand what’s going on. A lot of people are asking, “Why is Trump just out golfing while things are falling apart?” It’s simple: the emergency isn’t something he’s reacting to — it’s something he’s building.
Trump recently declared a national economic emergency under the International Emergency Economic Powers Act (IEEPA) — granting himself sweeping authority over international trade by labeling foreign economic practices an “unusual and extraordinary threat.”
But here’s the real play: by declaring a national emergency, Trump didn’t just respond to a crisis — he created one. And in doing so, he unlocked access to over 120 statutory powers scattered throughout federal law. Many of these powers have nothing to do with trade — and everything to do with expanding presidential authority inside the U.S.
What This Move Enables: Expanded Domestic Powers
1. Control of Domestic Communications
- 47 U.S.C. §606(c): Allows the president to take control of, shut down, or regulate wire and radio communications — including the internet, social media platforms, broadcast networks, and telecom infrastructure — in the name of national defense. Originally intended for wartime, this Cold War-era law remains on the books.
2. Asset Freezing and Financial Surveillance
- Under IEEPA and related laws, the president can freeze the assets and bank accounts of individuals or organizations accused of aiding foreign threats. These powers are vague and can be stretched to include domestic political groups, journalists, or activists — especially if they’re perceived as having foreign ties or influence.
3. Domestic Military Deployment
- Under the Insurrection Act (10 U.S.C. §§ 251–255), the president can deploy active-duty U.S. military to enforce laws or suppress civil unrest within the country. In certain scenarios, this can be done without state governor consent — especially if the president claims state authorities are failing to uphold federal law.
4. Emergency Detention Powers (Non-Citizens)
- The Alien Enemies Act (50 U.S.C. §21) — a law dating back to 1798 — allows the president to detain or restrict the movement of non-citizens from nations deemed hostile. The criteria for “hostile” can be broad and undefined during a declared emergency.
5. Control of Energy and Transportation
- Under laws like 42 U.S.C. §6272 and others, the president can redirect or restrict domestic fuel production, electricity usage, or energy transportation. Additionally, 49 U.S.C. §40106(b) allows the president to limit, reroute, or suspend civil aviation, giving the executive branch near-total control over U.S. airspace in a crisis.
6. Suspension of Labor Regulations
- During a declared emergency, the president can waive federal labor regulations and override contract protections. This includes removing limits on hours, wages, and workplace safety for federal contractors and any industries deemed vital to national security.
7. National Security Letters & Warrantless Surveillance
- Emergency declarations expand the reach and use of National Security Letters (NSLs) — tools that let federal agencies demand financial, telecom, and internet records without a warrant. These also come with gag orders, preventing the recipient (e.g., Google or a bank) from disclosing that they’re under surveillance.
Why it Matters?
Even when legal domestic powers are limited, a national emergency lets the president:
- Frame the issue as a national security crisis, justifying aggressive action
- Bypass Congress and the courts by acting unilaterally
- Sway public opinion using fear, urgency, and patriotic rhetoric
Bottom Line
IEEPA is focused on foreign threats — but once the emergency is declared, the president taps into a hidden arsenal of domestic control powers. What began as a trade issue could quickly shift into civil liberties restrictions, mass surveillance, or even crackdowns under the legal shield of an “emergency.”
This isn’t just about tariffs. It’s about redefining the boundaries of executive power. Imagine if this economic crisis keeps getting worse — the amount of power he will gain.
123 notes
·
View notes