#Centralized Digital Repository
Explore tagged Tumblr posts
Text
#Manage Your Digital Assets#Wealth Transfer#Assets For Future Generations#Manage Your Legacy Planning#Centralized Digital Repository#Preserving Your Family's Legacy#Financial Legacy Planning#Transferring Financial Assets
2 notes
·
View notes
Text
Streamline Your Business Operations with PDQ Docs: Centralized Document Management Software
In today’s business environment, managing documents efficiently is crucial for smooth operations. With an increasing volume of digital content, organizations need a robust solution to ensure documents are easily accessible, well-organized, and secure. Centralized document management software like PDQ Docs offers an effective way to address these challenges, providing businesses with a unified platform to manage their documents with ease. By centralizing document storage, retrieval, and collaboration, businesses can streamline operations, improve productivity, and ensure greater security.
What is Centralized Document Management Software?
Centralized document management software refers to a system that consolidates all digital documents and files into one secure, accessible platform. Rather than storing documents in disparate systems or physical locations, businesses can centralize their files into one organized, easy-to-manage repository. With this system, users can access, edit, share, and collaborate on documents from a single interface, ensuring consistency and efficiency across the organization. PDQ Docs is a leading example of centralized document management software that helps businesses organize their documents effectively while offering easy access and improved workflow.

How PDQ Docs Improves Document Management
PDQ Docs simplifies document storage and retrieval by offering a central location where all files are organized and indexed. One of the primary advantages of centralized document management is the ability to search for and retrieve documents quickly. With PDQ Docs, businesses can tag documents with keywords, categories, and metadata, ensuring that files can be located in just a few clicks. Whether it’s a contract, report, or an internal memo, finding documents becomes an efficient process, eliminating the frustration of searching through multiple folders or systems.
Security and Compliance with PDQ Docs
Another significant benefit of centralized document management software is the enhanced security it provides. With PDQ Docs, sensitive information is securely stored in a centralized, encrypted system. Access controls can be set to ensure that only authorized personnel can view or edit specific documents, minimizing the risk of data breaches. This is particularly important for businesses in regulated industries, such as healthcare and finance, where compliance with legal requirements and data protection regulations is paramount.
Why Choose PDQ Docs for Centralized Document Management?
When looking for centralized document management software, PDQ Docs stands out due to its user-friendly interface and powerful features. The software is designed to be intuitive, making it easy for businesses to implement without requiring extensive training. Whether you are a small business or a large corporation, PDQ Docs offers scalable solutions that can grow with your organization’s needs.
Conclusion
Centralized document management software is essential for businesses looking to improve efficiency, collaboration, and security. With PDQ Docs, you can streamline document storage and retrieval, enhance team collaboration, and ensure the security of sensitive information. By centralizing your documents, you’ll have better control over your files, ensuring that your team can access the right documents when needed. Whether you are looking to improve internal workflows or ensure regulatory compliance, PDQ Docs provides a comprehensive solution that will help your business operate more effectively.
#centralized document management software#document management system#digital document storage#enterprise document management#file organization software#document sharing solutions#document retrieval#centralized repository#document archiving#data compliance#document indexing#paperless office
0 notes
Text

🚨Exciting news! More than 6,000 3D scans of non-human primate skeletons collected over the last decade are now available for research worldwide—providing a valuable resource to scientists in the fields of biology, biological anthropology, evolutionary science, and conservation. This multi-institution effort was led by Museum scientists Sergio Almécija, a senior research scientist in the Museum’s Division of Anthropology, Nancy Simmons, curator and chair of the Museum’s Mammalogy Department, and Ashley Hammond, curator and chair of the Museum’s Division of Anthropology.
Now available on the National Science Foundation-funded repository MorphoSource, the dataset includes scans of nearly 400 individual specimens—ranging from great apes to Eurasian and South American monkeys. The physical specimens that were digitized as part of this effort are housed in collections at the Museum, Stony Brook University in New York, the National Museum of Natural History in Washington D.C., the Cleveland Museum of Natural History, and the Royal Museum for Central Africa (Belgium).
#science#amnh#museum#nature#natural history#did you know#fact of the day#research#new research#anthropology#mammalogy#stem#primates
488 notes
·
View notes
Text
FFXIV Write Entry #25: Endless

Prompt: perpetuity || Master Post || On AO3 (coming in October)
A/N: *takes hints from canon**speculates on it a lot**settles on a headcanon*
Spoilers for the second half of Dawntrail.
---
PRESERVATION: MESO TERMINAL CENTRAL REPOSITORY [PROD] control panel now online.
Please enter login credentials.
>>…
Welcome, Director Komor Kor! ARTEMICION DIGITAL ASSISTANT (ADA) ready for command inputs.
>>…
Accessing regulatory files [MEMORY | PERSONALITY | CORE] for ENDLESS PRIME: SPHENE TIL ALEXANDROS XIV…
>>//endless00%CoreRoot%
Now loading [CORE: ROOT].
9% complete…
27% complete…
45% complete…
72% complete…
90% complete…
100% complete!
ENDLESS PRIME: SPHENE TIL ALEXANDROS XIV [CORE: ROOT] awaiting input.
>>//runUPDATE(ArcheTerminalDEV)
Accessing PRESERVATION: ARCHE TERMINAL TESTING REPOSITORY [DEV]…
Connection to PRESERVATION: ARCHE TERMINAL TESTING REPOSITORY [DEV] established.
Accessing revised files [CORE: ROOT] for ENDLESS PRIME: SPHENE TIL ALEXANDROS XIV…
Copying revised files [CORE: ROOT] for ENDLESS PRIME: SPHENE TIL ALEXANDROS XIV to PRESERVATION: MESO TERMINAL CENTRAL REPOSITORY [PROD]…
Copy complete.
New additions to regulatory files [CORE: ROOT]:
PRIMARY LAW: Preserve the Kingdom of Alexandria and its citizens.
PRIMARY LAW: Preserve the Endless and residents of Living Memory.
PRIMARY LAW: “Ensure the happiness of the people of Alexandria.”
DURATION: Indefinite.
ALERT: UPDATE PAUSED. [CORE: ROOT] FUNCTIONALITY MAY BE IMPACTED TO ENDLESS PRIME. VERBAL AND AETHERIC CONFIRMATION of [PRESERVATION: SENIOR DIRECTORATE] REQUIRED FOR UPDATE TO PROCEED.
VERBAL-AETHERIC CONFIRMATION: DIRECTOR KOMOR KOR: CONFIRMED VERBAL-AETHERIC CONFIRMATION: DOCTOR AMETHYST RADON: CONFIRMED VERBAL-AETHERIC CONFIRMATION: DOCTOR GABBRO TRAPE: CONFIRMED VERBAL-AETHERIC CONFIRMATION: DOCTOR TYATA TYA: CONFIRMED VERBAL-AETHERIC CONFIRMATION: DOCTOR SCORIA VARDEN: CONFIRMED
VERBAL-AETHERIC CONFIRMATION OF [PRESERVATION: SENIOR DIRECTORATE] PROCESSED. PROCEEDING WITH UPDATE.
[CORE: ROOT] for ENDLESS PRIME: SPHENE TIL ALEXANDROS XIV update complete! AUTOSAVE activated.
Regulatory files [MEMORY | PERSONALITY | CORE] for ENDLESS PRIME: SPHENE TIL ALEXANDROS XIV saved to PRESERVATION: MESO TERMINAL CENTRAL REPOSITORY [PROD].
Disconnecting from PRESERVATION: ARCHE TERMINAL TESTING REPOSITORY [DEV].
ARTEMICION DIGITAL ASSISTANT (ADA) ready for command inputs.
>>…
PRESERVATION: MESO TERMINAL CENTRAL REPOSITORY [PROD] control panel closed.
Logging off.
#ffxivwrite2024#final fantasy xiv#ffxiv#dawntrail#spoilers#7.0 spoilers#sphene#preservation#dt's writing
23 notes
·
View notes
Text
The Science of Discovering the Past: Archival Research
Since the beginning of writing about 6000 years ago, humans have written down many things, from accounting information to the daily thoughts of those observing historical events, leaving a wealth of information behind for us to read through, even with those records that have been lost to the grist of time. Archival research involves studying these records for both primary and secondary resources.
A library differs from an archive in that a library contains published documents that generally aren't unique and are maintained for use while an archive contains unique items, many of which are not published in any way, and can be in any format. Archives often have a particular focus of materials that they collect and limit access to their collections.
The oldest collections that could be called archives go back to at least 1180 with the collections of scrolls from the clerk's offices in Barcelona, Spain, where it was mentioned as a king's archive. In 1194, King Alfonso II of Aragon ordered the compilation of documents that were legally valid and useful, some of which dated back to the 9th century. In 1318, under James II of Aragon, the General Archive of the Crown of Aragon was established as the central archive of the Crown. Many countries have national archives that were established after that and have documents that go back as far as 625 CE (as in the French Archives Nationales) with the United States National Archives and Records Administration having documents that include an original copy of the Magna Carta.
Universities are also repositories of record collections, both of their own business as well as those that have been bequeathed to them. They also might have collections that are focused on a single subject, ranging from religion to local history. Religious institutes, such as the Vatican, which reportedly has more than 52 miles (83.69 km) of archival shelving, and museums are also repositories of document collections. There are also an increasing collection of digital collections, which bring about their own challenges, such as technology creep, which is the gradual loss of older technologies (think of the loss of VCR machines making VCR tapes harder to view or the removal of optical drives from computers). Archives, whether traditional or digital, also face the degradation of time and the risk of catastrophic destruction.
Archival research begins with locating an archive that holds the needed documents that apply to the desired topic, which has become easier with online searches. Prior to this, union catalogs, which were library catalogs that describe the collections of archives were distributed among universities. The next challenge is locating the texts within the archive. Many archives operate until the principle of respect des fonds, or the original order in which they were received in order to maintain provenance. Finding aids, such as registers, card catalogs, or inventories, are a common tool to aid researchers in locating materials.
Prior to digitization, archives had to be accessed on-site as they were parts of non-circulating collections. As such, most archives have reading rooms, where materials can be viewed. If the reading room is not directly connected to the collection, it may take days or weeks for materials to be delivered. Many of the materials held by archives are fragile and therefore have restrictions placed on their use or duplication. Restrictions may also be placed on what can be taken or worn within a reading room to protect documents from damage or theft.
4 notes
·
View notes
Text
In a Monday morning meeting, Thomas Shedd, the recently appointed Technology Transformation Services director and Elon Musk ally, told General Services Administration workers that the agency’s new administrator is pursuing an “AI-first strategy,” sources tell WIRED.
Throughout the meeting, Shedd shared his vision for a GSA that operates like a “startup software company,” automating different internal tasks and centralizing data from across the federal government.
The Monday meeting, held in-person and on Google Meet, comes days after WIRED reported that many of Musk’s associates have migrated to jobs at the highest levels of the GSA and the Office of Personnel Management (OPM). Prior to joining TTS, which is housed within the GSA, Shedd was a software engineer at Tesla, one of Musk’s companies. The transition has caused mass confusion amongst GSA staffers who have been thrown into surprise one-on-one meetings, forced to present their code—often to young engineers who did not identify themselves—and left wondering what the future of the agency’s tech task force will look like.
Shedd attempted to answer these questions on Monday, providing details on a number of projects the agency will pursue over the coming weeks and months. His particular focus, sources say, was an increased role for AI not just at GSA, but at agencies government-wide.
In what he described as an “AI-first strategy,” sources say, Shedd provided a handful of examples of projects GSA acting administrator Stephen Ehikian is looking to prioritize, including the development of “AI coding agents” that would be made available for all agencies. Shedd made it clear that he believes much of the work at TTS and the broader government, particularly around finance tasks, could be automated.
"This does raise red flags,” a cybersecurity expert who was granted anonymity due to concerns of retaliation told WIRED on Monday, who noted that automating the government isn’t the same as automating other things, like self-driving cars. “People, especially people who aren’t experts in the subject domain, coming into projects often think ‘this is dumb’ and then find out how hard the thing really is.”
Shedd instructed employees to think of TTS as a software startup that had become financially unstable. He suggested that the federal government needs a centralized data repository, and that he was actively working with others on a strategy to create one, although it wasn’t clear where this repository would be based or if these projects would comply with privacy laws. Shedd referred to these concerns as a “roadblock” and said that the agency should still push forward to see what was possible.
Sources say that during the call Shedd tightly connected TTS and the United States Digital Services—rebranded as the United States DOGE Service, or DOGE, under Trump—as “pillars” of a new technological strategy. Later in the meeting, he said that there was no plan to merge the two groups and that projects would flow through them both depending on available staff and expertise, but continued emphasizing the upcoming collaboration between TTS and DOGE.
Employees, sources say, also asked questions about the young engineers, who had previously not been identifying themselves in meetings. Shedd said that one of them felt comfortable enough to introduce himself in meetings on Monday, sources say, though Shedd added that he was nervous about their names being publicly revealed and their lives upended.
Shedd was unable to answer many staff questions about the deferred resignations, the return to office mandate, or if the agency’s staff would face substantial cuts, according to sources. At one point, Shedd indicated that workforce cuts were likely for TTS, but declined to give more details. (Similar questions were also asked of Department of Government Efficiency leadership in a Friday meeting first reported by WIRED.)
Towards the end of the call, sources say, a TTS worker asked if they would be expected to work more than 40 hours per week, to deal with all of the upcoming work and potentially laid-off workers. Shedd responded that it was “unclear.”
9 notes
·
View notes
Text
So cool! Excerpts:
Founded in 427 CE, Nalanda is considered the world's first residential university, a sort of medieval Ivy League institution home to nine million books that attracted 10,000 students from across Eastern and Central Asia. They gathered here to learn medicine, logic, mathematics and – above all – Buddhist principles from some of the era's most revered scholars.
Monarchs of the Gupta Empire that founded the Buddhist monastic university were devout Hindus, but sympathetic and accepting towards Buddhism and the growing Buddhist intellectual fervour and philosophical writings of the time. The liberal cultural and religious traditions that evolved under their reign would form the core of Nalanda's multidisciplinary academic curriculum, which blended intellectual Buddhism with a higher knowledge in different fields.
Aryabhata, considered the father of Indian mathematics, is speculated to have headed the university in the 6th Century CE. "We believe that Aryabhata was the first to assign zero as a digit, a revolutionary concept, which simplified mathematical computations and helped evolve more complex avenues such as algebra and calculus," said Anuradha Mitra, a Kolkata-based professor of mathematics. "Without zero, we wouldn't have computers," she added. "He also did pioneering works in extracting square and cubic roots, and applications of trigonometrical functions to spherical geometry. He was also the first to attribute radiance of the moon to reflected sunlight."
The library's nine million handwritten, palm-leaf manuscripts was the richest repository of Buddhist wisdom in the world, and one of its three library buildings was described by Tibetan Buddhist scholar Taranatha as a nine-storey building "soaring into the clouds".
History is so fucking cool. I love stumbling across articles that teach me incredible details about things I only knew about in a very general sense (there were important centers of learning in India!). Learning mundane things like "universities have always had students sharing rooms" is just fascinating to me.
One of the small rooms that lined the courtyard where students from as far away as Afghanistan lived. Two alcoves facing each other were meant to hold oil lamps and personal belongings, and Singh explained that the small, square-shaped hollow near the entrance of the cell served as each student's personal letterbox.
How cool is that!!!
7 notes
·
View notes
Text
“If technocracy wins this battle and they implement it on a global basis, it will again take hundreds of years before the concept of freedom and liberty will resurface again. It will take a very long time; it won’t just come snapping back, it will not be a fade. Once they get control over the economic mechanism, they will virtually have control over life itself. They will make people of the world dance like puppets on a string.” ⁃ Patrick Wood, TN Editor.
This is a very important question. I think about it daily as the meteoric rise of scientism creates a new materialistic priest class, in whom you must put your faith and devotion.
What is Technocracy?
A scientific dictatorship, enabled by full-scale surveillance, in which an elite class of scientists and engineers manages every facet of life. Technocrats are “persons who exercise power by virtue of their technical knowledge.”
Technocracy is the Brave New World in Aldous Huxley’s 1932 novel, which was more a “I just got out of a meeting and here’s how it’s going down,” memo rather than a cautionary tale.
In this presentation about COVID-19, Dr. Lee Merritt, influenced by Patrick Wood’s writings on technocracy, shared the etymology:
Techn = skillKrat = kratos (divine personification of power)
She summed up technocracy: Data gathered on everybody in the world and fed to un-elected officials, who are smarter than everybody, and will use the information to create amazing solutions. It boils down to “power via differential knowledge,” meaning if you have knowledge that only a select few have, you can lord it over the majority of people.
The Internet and Total Surveillance
Once the possibility of a total surveillance state materialized with the inception of the Internet, technocracy became the crown jewel in the Cabal’s totalitarian New World Order agenda.
The timeline is speeding up. Their dreams of ruling the world are veering toward a terrifying reality with artificial intelligence, propaganda in everybody’s pocket, and a bazillion data points on every man, woman, and child on Earth.
Patrick Wood, the OG of technocracy research, said once we reach a scientific dictatorship society … “liberty will be a historic curiosity.”
In order to achieve this goal, the technocrats developed mass surveillance, which has only been possible in the modern age with the Internet. This is their time to act.
Smart meters on houses monitor how much energy you consume.
Credit card transactions track consumer behavior and move people away from hard currency.
Social media fills out the dossier with beliefs, names of friends and family, images, and much more.
The Affordable Care Act digitizes your medical history.
Smart gadgets—Fitbit, Oura Ring, etc.—pass all of your vital stats to central repositories.
Smartphones track where you are, what you’re doing (they can listen in), and what information you’re consuming and entertainment you are consuming.
The Internet of Things (IoT) adds more daily data. What’s in your fridge? What do you watch on TV? And even more nefarious, there are credible reports detailing how they can watch us through our TVs.
Facial recognition software and cameras monitor every square inch of public space.
Virtual assistants like Alexa monitor your every word and train people to be useless (“please machine, turn on that light … I cannot do it myself”).
Public school jams cultural Marxism down the throat of every child, while Common Core collects 400 pieces of data on every child, which is on their record for life.
5 notes
·
View notes
Text
Building the Never-Ending Character Sheet
In Various Types, the properties being applied to each player are determined by a central character sheet object. This object is responsible for determining their current creature types, abilities, and other useful information. It also serves as the repository for the things that change those values, such as their selected species and currently-applied templates.
Initially, this was all hard-coded, so that adding a new value necessitated directly changing the character sheet object and updating all of the modifying elements to account for it. Whilst this was simple enough when there were relatively few values, such as when there was only 3 of them, it quickly became a headache as the amount of information and modifying factors increased during development.
Time for a new approach.
Enter the twin registries of ISheetElement and SheetModule. The simplest descriptions of which are the parts of a character sheet you write in (the modules) and the parts that many digital character sheets automatically calculate for you (the elements).
ISheetElements are the individual modifiable values stored in the character sheet. This can be a singular value like the the player's home dimension or volume of nonlethal damage, or it can be more complex like their current abilities. Each element defines what other elements must be calculated before they are, such as types before abilities since types themselves convey abilities, as well as when modules are applied during their recalculation process (for efficiency this "build order" is calculated after initial registration and stored for later usage, rather than calculated each time a sheet rebuilds). Elements can be stored in persistent data (such as activated abilities that require long-term information storage) but most are simply recalculated from scratch as needed.
Modules receive each element as it is recalculated, in a specific ascending integer order. They are the things that change the values, such as species or custom abilities. Modules always initialise blank.
Each character sheet always has a copy of every entry in both registries, even if a new entry was added inbetween times the sheet was loaded into memory. When the character sheet is rebuilt, usually due to a change in one or more of its modules, it recalculates each element in build order, applying the changes of each module as it goes.
New modules can be registered to expand the variety of modifying factors and new elements can be registered to expand what information the character sheet tracks.
This revised approach, though certainly overkill for a character sheet existing with only a small handful of components or with no intentions for future expansion, allows the character sheets to be expanded endlessly by third-party add-ons as well as to hold whatever feature creep inevitably demands.
Changing to this approach early on greatly simplified making changes to the character sheet structure during development, such as implementing custom types and abilities, separating abilities into passive and activated abilities, as well as adding new mechanics such as implementing nonlethal damage as a new tracked value per player.
This essentially makes Various Types into not only a powerful and versatile mod in itself, but the quintessential utility for implementing virtually any game mechanic that necessitates per-player data tracking.
8 notes
·
View notes
Text
What will you do if the Internet goes down?
The prospect of a widespread internet disruption is a genuine concern in our increasingly digital world. Our reliance on the internet for communication, commerce, and information access makes us vulnerable to the consequences of a prolonged outage. The centralization of our digital infrastructure, with a few tech giants controlling a significant portion of the cloud, exacerbates this vulnerability. A disruption to these services would have a ripple effect, impacting businesses, supply chains, and individuals alike.

However, crises often breed opportunities. Could an internet outage catalyze the rise of decentralized, community-driven networks? We've seen glimpses of this resilience in mesh networks used during protests and the proliferation of open-source tools promoting digital freedom. Could such initiatives not only survive but flourish in a landscape devoid of the traditional internet? Personal resilience starts with individual preparedness. Backing up data, utilizing offline knowledge repositories, and adopting secure communication protocols are not just good practices; they're essential for digital sovereignty. Preparing for an internet outage isn't about fear; it's about empowering ourselves with self-sufficiency.
Financial autonomy is equally crucial. Recognizing that banks are susceptible to disruption, exploring alternatives like cryptocurrency (in cold storage) and localized trade becomes prudent. In essence, while we prepare for potential digital turbulence, let's ground ourselves with analog foundations. Community networks, contingency plans, and an adaptable mindset are our anchors. Our goal shouldn't be merely to endure a digital blackout; it should be to cultivate a resilient lifestyle that thrives regardless of our online connectivity.
Counter-cultures are not just about opposing the status quo; they're about resilience and adaptability. Our responses to restrictions can foster the emergence of more robust, diverse systems that align with our inherent need for freedom and privacy. As we navigate the delicate balance between convenience and sovereignty, let's remember to look beyond our screens. Our neighbors, local communities, and the independence of thought are pillars that cannot be gated or switched off.
#geeknik#nostr#art#blog#writing#internet#outage#disruption#counterculture#digital#autonomy#resilience#mesh network#open source#sovereignty
15 notes
·
View notes
Text
Discord and the Online Ecosystem
Discord is an awesome service to use. Overall, it's user friendly to do "basic" stuff, like instantly updating, global text, image, and video posts with a near-infinite level of storage for those things. For 95% of people that use Discord, it's an incredibly convenient, functional service almost all the time. But Discord in fundamentally making the Internet - not the people interacting with each other, but the actual infrastructure and ethos of the Internet - worse.
I'm saying this not only as an "Internet person" - after all, I'm here with the rest of you, but as someone who is only now realizing that I am an expert on the function, technical details, and history of the Internet compared to most users of this place. I get paid to do it. I get paid to learn about how everything on it works, not as a researcher, but as someone that makes important parts of it work, at least to a certain scale.
Discord is a parasite on the internet, just like Reddit being a self-hosting image and text repository. The centralization of the Internet, I believe, is essentially toxic to how the Internet was built and used for it's most formative times, and losing that essence makes the Internet a worse place.
Here's the technical reasons it's starving out the Internet. Essentially, the Internet was built as a network of first a few, then dozens, then hundreds, etc. of small servers, each hosting data and sharing almost exclusively text communications and records. Usually, these were hosted on Universities and other technical institutions. As those developed, thanks to the nerds that were core to actually making the systems talk and work, those nerds started hosting little servers of their own, sometimes on the same machines as those big systems, sometimes just using the same infrastructure like power and networking. Then personal computers and home servers started to develop.
This entire time, if those big organizational servers were the Bones of the Internet, the flesh were those little sites that held the little services. Niche forums, mostly, where people could communicate their own small passions and hobbies. It was the beginning of the Internet being a global cultural hub, and caused the development of those niches into communities with their own histories and knowledge troves.
Then the Internet started making money. And technical changes made economies of scale more feasible. There was a transitional period where a lot of people didn't see what was coming. I was too young and wouldn't have predicted it even if I was the me of today. After that transition, consolidation of the Internet started intensifying. The Internet was no longer a facilitator to commerce, it could be commerce all on its own.
So sites like Reddit, Facebook Groups, Discord, even to an extent Github, and Tumblr and fanfiction.net, though lesser because Tumblr is more of a social media site related to random fandoms and FF.net is so public and archived, show up and gather the niche communities, which is great because they are providing a really good service to use. Until they decide to delete a niche because it hasn't had activity in a few years, or because they decided that it's a banned topic, and that trove of information about those people and their passion is gone forever.
This is part of "digital archaeology". Of keeping that knowledge around so we can look back at the world of today and know the cultural context of who we were. This is anthropology of the digital age.
Now on to the technical reasons Discord, in specific, is such a parasite on the internet. That's not a term of disgust, I literally mean that it's kinda latched onto the Internet as a whole and stealing it's nutrients from within. Discord especially is a problem because it's so good to use. It offers up instantaneous creation and use of a moderated chat space that can be shared easily, doesn't require any technical knowledge, and immediately does it's job unlike any previous niche gathering tool.
Those technical people developed how the internet worked using those niche communities. They shared technical ideas and designs and talked about how to do more with the technical resources they had. They built the internet protocol by protocol, bugfix by bugfix, and their knowledge, even after they stopped talking on those forums, was picked over by new people who had new ideas but also has problems that that niche could now solve.
And now those niches are put into walled gardens on Discord, privately managed, unsearchable from the wider internet, and where a year or two after nobody touching the chat, the history is deleted for the sake of ruthless business resource efficiency.
It takes the knowledge, extracts the value from the people who may or may not produce something with that community with that niche area, and then leaves no record of it for people outside that community to learn from.
Think video game developer communities. There's technical knowledge of how to get a game to run that is answered on those discords. FAQs and mods are hosted there. Lore is dropped. Depending on the scale of the game, patches might even be released. No one can try to start up a copy of that game in the future and have access to that knowledge once Discord, the business, decides to close it down.
This isn't a new problem. Servers, neglect, or even upset owners of the gathering places took their toll and got rid of a lot of knowledge over time. Historical Anthropology, History, Cultural Anthropology - all of those expect a certain level of information decay and loss. But this is a lot more.
And the worst part is I don't know what can be done about it. Discord is in a fundamental technical way, better at doing what it does than any other system we have. No other system could semi-publicly, instantly, in a structured manner and across the entire Internet landscape, share voice chat, text, photos, and even some videos natively to the service. Traditional web pages fail at the instantly part. Most services fail at the picture and video part. Practically none succeed at the voice part. It's just better.
4 notes
·
View notes
Text
Maximizing Efficiency with Product Development and Project Management Software
In today's fast growing business world , the success of any organization is based on its ability to efficiently manage product development and project workflows. With the rise of digital transformation, businesses are increasingly turning to product development software and project management software to streamline processes, enhance collaboration, and drive innovation.
Streamlining Product Development
Benefits of Product Development Software
Efficient Idea Management: Product development software allows teams to capture, organize, and prioritize ideas effectively, ensuring that valuable insights are not lost in the shuffle.
Streamlined Workflow: By digitizing the product development lifecycle, organizations can streamline processes, reduce manual errors, and accelerate time-to-market.
Enhanced Collaboration: Product development tool facilitates cross-functional collaboration by providing a centralized platform for sharing information, feedback, and updates in real-time.
Data-Driven Decision Making: With robust analytics and reporting capabilities, organizations can make informed decisions based on real-time data and insights, driving continuous improvement and innovation.
Key Features of Product Development Software
Idea Generation and Management: Capture and evaluate new product ideas from various sources, including customers, employees, and stakeholders.
Requirements Management: Define the product and the importance and track product requirements throughout the development lifecycle, ensuring alignment with business goals and customer needs.
Prototyping and Design: Create prototypes, mockups, and wireframes to visualize product concepts and gather feedback from stakeholders. Go for a demo about the product.
Collaboration Tools: Foster collaboration among cross-functional teams through features such as discussion forums, document sharing, and task assignments.
Version Control: Maintain a centralized repository of product artifacts, ensuring version control and traceability throughout the development process.
Testing and Quality Assurance: Conduct comprehensive testing and quality assurance activities to identify and address defects early in the development lifecycle.
Release Management: Plan and coordinate product releases, including scheduling, resource allocation, and risk assessment.
Optimizing Project Management
Benefits of Project Management Software
Improved Planning and Scheduling: Project management software enables organizations to create detailed project plans, allocate resources efficiently, and track progress against milestones and deadlines.
Enhanced Communication: By providing a centralized platform for communication and collaboration, project management tools ensure that team members stay aligned and informed throughout the project lifecycle.
Resource Optimization: With visibility into resource availability and workload, organizations can optimize resource allocation, minimize bottlenecks, and maximize productivity.
Risk Management: Project management software facilitates risk identification, assessment, and mitigation, helping organizations anticipate and address potential challenges before they escalate.
Performance Monitoring: Real-time dashboards and reports allow stakeholders to monitor project performance, track key metrics, and make data-driven decisions to drive project success.
Key Features of Project Management Software
Task Management: Create, assign, and track tasks across projects, ensuring accountability and visibility into project progress.
Gantt Charts: Visualize project timelines, dependencies, and critical path activities using Gantt charts, facilitating effective planning and resource management.
Collaboration Tools: Foster collaboration among project team members through features such as discussion boards, file sharing, and real-time messaging.
Resource Management: Allocate resources efficiently, track resource utilization, and manage resource conflicts to ensure optimal project performance.
Budgeting and Cost Management: Monitor project budgets, track expenses, and analyze cost trends to ensure projects are delivered within budget constraints.
Risk Management: Identify, assess, and mitigate project risks through proactive risk management processes and tools.
Reporting and Analytics: Generate comprehensive reports and dashboards to track project metrics, identify trends, and make data-driven decisions.
Conclusion
In conclusion, product development software and project management software play a crucial role in helping organizations maximize efficiency, drive innovation, and achieve project success. By leveraging these tools, businesses can streamline workflows, enhance collaboration, and deliver value to customers more effectively. Whether it's bringing new products to market or executing complex projects, investing in the right software solutions can empower teams to thrive in today's competitive landscape.
#ProductDevelopment#SoftwareDevelopment#AgileDevelopment#ProductManagement#ProjectManagement#TechInnovation#DigitalTransformation#ProductDesign#SoftwareEngineering#TeamCollaboration
2 notes
·
View notes
Text
Streamlining IT Service Management: A Review of ITSM Prozessbibliothek deutsch für SAP Signavio
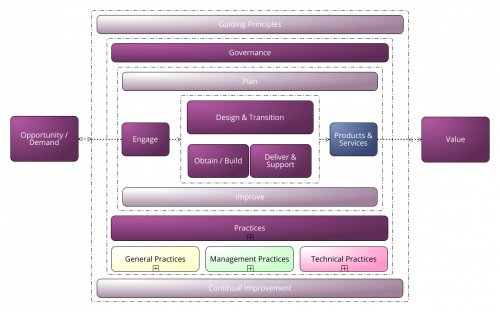
I recently implemented the ITSM Prozessbibliothek deutsch für SAP Signavio digital software into my IT department, and it has revolutionized the way we manage IT services. For years, our ITSM processes relied on a patchwork of outdated documents and tribal knowledge. This led to inefficiencies, inconsistencies, and ultimately, frustrated employees and customers. The ITSM Prozessbibliothek deutsch für SAP Signavio has transformed our approach to ITSM, bringing much-needed structure and clarity to our operations.
Pre-Built Library Saves Time and Ensures Consistency
One of the biggest advantages of this software is the pre-built library of ITSM process templates specific to SAP Signavio. These templates provide a strong foundation for our core IT services, including incident, problem, change, and configuration management. The pre-built nature saved us countless hours compared to building these processes from scratch. Furthermore, the library ensures consistency across all our IT service offerings, eliminating the risk of variations that could lead to confusion or errors.
Visual Process Modelling for Improved Understanding
The software utilizes a visual process modelling approach, which has been a game-changer for our team. Complex workflows are depicted through clear diagrams that showcase the sequence of steps, decision points, and responsible roles. This visual format makes it easy for everyone, regardless of technical expertise, to understand how IT services are delivered. This fosters better collaboration between IT staff and other departments, as everyone has a clear picture of how their requests are handled.
Customization Options for Tailored Processes
While the pre-built library provides a solid starting point, the software also allows for customization. We can easily adapt the templates to reflect our specific IT environment and service offerings. This flexibility ensures that the processes we implement are truly tailored to our unique needs. Additionally, the software allows us to document best practices and service level agreements (SLAs) directly within the process models, providing a central repository for all relevant information.
Integration with SAP Signavio for Seamless Workflow
For organizations already using SAP Signavio, the ITSM Prozessbibliothek offers a seamless integration. The pre-built templates are designed to work flawlessly within the SAP Signavio environment, eliminating the need for data migration or complex integrations. This streamlines the process of implementing and managing ITSM processes, allowing us to leverage the existing capabilities of SAP Signavio.
Enhanced Collaboration and Improved Efficiency
Since implementing the ITSM Prozessbibliothek deutsch für SAP Signavio, we've witnessed a significant improvement in collaboration and efficiency within our IT department. The clear and consistent processes have empowered our staff to handle service requests more effectively. Additionally, the software has facilitated better communication with end-users, as they now have a clear understanding of how IT services are delivered. Overall, this has resulted in a noticeable reduction in service resolution times and a more streamlined IT service experience.
In conclusion, the ITSM Prozessbibliothek deutsch für SAP Signavio is an invaluable tool for any organization looking to streamline their IT service management processes. The combination of pre-built templates, visual process modelling, and SAP Signavio integration makes it a powerful solution for improving efficiency, communication, and overall IT service delivery.pen_sparktunesharemore_vert
Upload an image
This prompt requires an image that you need to add. Tap the image button to upload an image. Got it
Do you need a little help with this prompt?
Power up your prompt and Gemini will expand it to get you better resultsGot it
2 notes
·
View notes
Text
Rajeev Lakhanpal Shares The Impact of Blockchain Technology on Computer Security

In the rapidly evolving landscape of cybersecurity, where threats loom large and data breaches are a constant concern, innovative solutions are urgently needed to bolster defenses. Enter blockchain technology, a revolutionary concept that is not only disrupting traditional industries but also transforming the way we approach computer security. Renowned expert Rajeev Lakhanpal sheds light on the profound impact blockchain is having on enhancing security measures in the digital realm.
Understanding Blockchain Technology
At its core, blockchain is a decentralized and immutable ledger that records transactions across a network of computers. Each transaction, or block, is securely linked to the previous one, forming a chain of blocks that cannot be altered retroactively. This decentralized nature eliminates the need for a central authority, reducing the risk of a single point of failure and making it extremely difficult for hackers to compromise the system.
Impact on Computer Security
Enhanced Data Integrity: One of the key features of blockchain technology is its ability to ensure data integrity. Each transaction is verified and recorded in a transparent and immutable manner, eliminating the possibility of tampering or manipulation. This inherent trustworthiness makes blockchain ideal for securing critical information, such as financial records and identity documents.
Decentralized Security Infrastructure
Unlike traditional centralized systems, which are vulnerable to single points of failure, blockchain operates on a decentralized network of nodes. This distributed architecture significantly reduces the risk of cyber attacks, as there is no central server or repository for hackers to target. Even in the event of a breach, the distributed nature of blockchain ensures that the network remains resilient and operational.
Immutable Audit Trails
In industries where compliance and auditability are paramount, blockchain technology offers an invaluable solution. Every transaction recorded on the blockchain is time-stamped and cryptographically linked to previous transactions, creating an immutable audit trail. This transparency not only enhances accountability but also simplifies the process of verifying the authenticity and integrity of data.
Secure Identity Management
Identity theft and fraud are major concerns in the digital age, with hackers constantly devising new ways to steal personal information. Blockchain technology offers a secure and decentralized solution to identity management, enabling individuals to maintain control over their personal data. By storing identity credentials on the blockchain, users can authenticate themselves without relying on centralized authorities, reducing the risk of identity theft.
Conclusion
In conclusion, the impact of blockchain technology on computer security cannot be overstated. From enhancing data integrity to revolutionizing identity management, blockchain offers a myriad of benefits that are reshaping the cybersecurity landscape. As Rajeev Lakhanpal rightly emphasizes, embracing blockchain technology is not just a strategic choice but a necessity in safeguarding our digital assets against evolving threats. As we continue to navigate the complex and ever-changing world of cybersecurity, the adoption of blockchain technology will undoubtedly play a pivotal role in fortifying our defenses and ensuring a more secure digital future.
2 notes
·
View notes
Text
Connecting the dots of recent research suggests a new future for traditional websites:
Artificial Intelligence (AI)-powered search can provide a full answer to a user’s query 75% of the time without the need for the user to go to a website, according to research by The Atlantic.
A worldwide survey from the University of Toronto revealed that 22% of ChatGPT users “use it as an alternative to Google.”
Research firm Gartner forecasts that traffic to the web from search engines will fall 25% by 2026.
Pew Research found that a quarter of all web pages developed between 2013 and 2023 no longer exist.
The large language models (LLMs) of generative AI that scraped their training data from websites are now using that data to eliminate the need to go to many of those same websites. Respected digital commentator Casey Newton concluded, “the web is entering a state of managed decline.” The Washington Post headline was more dire: “Web publishers brace for carnage as Google adds AI answers.”
From decentralized information to centralized conclusions
Created by Sir Tim Berners-Lee in 1989, the World Wide Web redefined the nature of the internet into a user-friendly linkage of diverse information repositories. “The first decade of the web…was decentralized with a long-tail of content and options,” Berners-Lee wrote this year on the occasion of its 35th anniversary. Over the intervening decades, that vision of distributed sources of information has faced multiple challenges. The dilution of decentralization began with powerful centralized hubs such as Facebook and Google that directed user traffic. Now comes the ultimate disintegration of Berners-Lee’s vision as generative AI reduces traffic to websites by recasting their information.
The web’s open access to the world’s information trained the large language models (LLMs) of generative AI. Now, those generative AI models are coming for their progenitor.
The web allowed users to discover diverse sources of information from which to draw conclusions. AI cuts out the intellectual middleman to go directly to conclusions from a centralized source.
The AI paradigm of cutting out the middleman appears to have been further advanced in Apple’s recent announcement that it will incorporate OpenAI to enable its Siri app to provide ChatGPT-like answers. With this new deal, Apple becomes an AI-based disintermediator, not only eliminating the need to go to websites, but also potentially disintermediating the need for the Google search engine for which Apple has been paying $20 billion annually.
The Atlantic, University of Toronto, and Gartner studies suggest the Pew research on website mortality could be just the beginning. Generative AI’s ability to deliver conclusions cannibalizes traffic to individual websites threatening the raison d’être of all websites, especially those that are commercially supported.
Echoes of traditional media and the web
The impact of AI on the web is an echo of the web’s earlier impact on traditional information providers. “The rise of digital media and technology has transformed the way we access our news and entertainment,” the U.S. Census Bureau reported in 2022, “It’s also had a devastating impact on print publishing industries.” Thanks to the web, total estimated weekday circulation of U.S. daily newspapers fell from 55.8 million in 2000 to 24.2 million by 2020, according to the Pew Research Center.
The World Wide Web also pulled the rug out from under the economic foundation of traditional media, forcing an exodus to proprietary websites. At the same time, it spawned a new generation of upstart media and business sites that took advantage of its low-cost distribution and high-impact reach. Both large and small websites now feel the impact of generative AI.
Barry Diller, CEO of media owner IAC, harkened back to that history when he warned a year ago, “We are not going to let what happened out of free internet happen to post-AI internet if we can help it.” Ominously, Diller observed, “If all the world’s information is able to be sucked up in this maw, and then essentially repackaged in declarative sentence in what’s called chat but isn’t chat…there will be no publishing; it is not possible.”
The New York Times filed a lawsuit against OpenAI and Microsoft alleging copyright infringement from the use of Times data to train LLMs. “Defendants seek to free-ride on The Times’s massive investment in its journalism,” the suit asserts, “to create products that substitute for The Times and steal audiences away from it.”1
Subsequently, eight daily newspapers owned by Alden Global Capital, the nation’s second largest newspaper publisher, filed a similar suit. “We’ve spent billions of dollars gathering information and reporting news at our publications, and we can’t allow OpenAI and Microsoft to expand the Big Tech playbook of stealing our work to build their own businesses at our expense,” a spokesman explained.
The legal challenges are pending. In a colorful description of the suits’ allegations, journalist Hamilton Nolan described AI’s threat as an “Automated Death Star.”
“Providential opportunity”?
Not all content companies agree. There has been a groundswell of leading content companies entering into agreements with OpenAI.
In July 2023, the Associated Press became the first major content provider to license its archive to OpenAI. Recently, however, the deal-making floodgates have opened. Rupert Murdoch’s News Corp, home of The Wall Street Journal, New York Post, and multiple other publications in Australia and the United Kingdom, German publishing giant Axel Springer, owner of Politico in the U.S. and Bild and Welt in Germany, venerable media company The Atlantic, along with new media company Vox Media, the Financial Times, Paris’ Le Monde, and Spain’s Prisa Media have all contracted with OpenAI for use of their product.
Even Barry Diller’s publishing unit, Dotdash Meredith, agreed to license to OpenAI, approximately a year after his apocalyptic warning.
News Corp CEO Robert Thomson described his company’s rationale this way in an employee memo: “The digital age has been characterized by the dominance of distributors, often at the expense of creators, and many media companies have been swept away by a remorseless technological tide. The onus is now on us to make the most of this providential opportunity.”
“There is a premium for premium journalism,” Thomson observed. That premium, for News Corp, is reportedly $250 million over five years from OpenAI. Axel Springer’s three-year deal is reportedly worth $25 to $30 million. The Financial Times terms were reportedly in the annual range of $5 to $10 million.
AI companies’ different approaches
While publishers debate whether AI is “providential opportunity” or “stealing our work,” a similar debate is ongoing among AI companies. Different generative AI companies have different opinions whether to pay for content, and if so, which kind of content.
When it comes to scraping information from websites, most of the major generative AI companies have chosen to interpret copyright law’s “fair use doctrine” allowing the unlicensed use of copyrighted content in certain circumstances. Some of the companies have even promised to indemnify their users if they are sued for copyright infringement.
Google, whose core business is revenue generated by recommending websites, has not sought licenses to use the content on those websites. “The internet giant has long resisted calls to compensate media companies for their content, arguing that such payments would undermine the nature of the open web,” the New York Times explained. Google has, however, licensed the user-generated content on social media platform Reddit, and together with Meta has pursued Hollywood rights.
OpenAI has followed a different path. Reportedly, the company has been pitching a “Preferred Publisher Program” to select content companies. Industry publication AdWeek reported on a leaked presentation deck describing the program. The publication said OpenAI “disputed the accuracy of the information” but claimed to have confirmed it with four industry executives. Significantly, the OpenAI pitch reportedly offered not only cash remuneration, but also other benefits to cooperating publishers.
As of early June 2024, other large generative AI companies have not entered into website licensing agreements with publishers.
Content companies surfing an AI tsunami
On the content creation side of the equation, major publishers are attempting to avoid a repeat of their disastrous experience in the early days of the web while smaller websites are fearful the impact on them could be even greater.
As the web began to take business from traditional publishers, their leadership scrambled to find a new economic model. Ultimately, that model came to rely on websites, even though website advertising offered them pennies on their traditional ad dollars. Now, even those assets are under attack by the AI juggernaut. The content companies are in a new race to develop an alternative economic model before their reliance on web search is cannibalized.
The OpenAI Preferred Publisher Program seems to be an attempt to meet the needs of both parties.
The first step in the program is direct compensation. To Barry Diller, for instance, the fact his publications will get “direct compensation for our content” means there is “no connection” between his apocalyptic warning 14 months ago and his new deal with OpenAI.
Reportedly, the cash compensation OpenAI is offering has two components: “guaranteed value” and “variable value.” Guaranteed value is compensation for access to the publisher’s information archive. Variable value is payment based on usage of the site’s information.
Presumably, those signing with OpenAI see it as only the first such agreement. “It is in my interest to find agreements with everyone,” Le Monde CEO Louis Dreyfus explained.
But the issue of AI search is greater than simply cash. Atlantic CEO Nicolas Thompson described the challenge: “We believe that people searching with AI models will be one of the fundamental ways that people navigate to the web in the future.” Thus, the second component in OpenAI’s proposal to publishers appears to be promotion of publisher websites within the AI-generated content. Reportedly, when certain publisher content is utilized, there will be hyperlinks and hover links to the websites themselves, in addition to clickable buttons to the publisher.
Finally, the proposal reportedly offers publishers the opportunity to reshape their business using generative AI technology. Such tools include access to OpenAI content for the publishers’ use, as well as the use of OpenAI for writing stories and creating new publishing content.
Back to the future?
Whether other generative AI and traditional content companies embrace this kind of cooperation model remains to be seen. Without a doubt, however, the initiative by both parties will have its effects.
One such effect was identified in a Le Monde editorial explaining their licensing agreement with OpenAI. Such an agreement, they argued, “will make it more difficult for other AI platforms to evade or refuse to participate.” This, in turn, could have an impact on the copyright litigation, if not copyright law.
We have seen new technology-generated copyright issues resolved in this way before.2 Finding a credible solution that works for both sides is imperative. The promise of AI is an almost boundless expansion of information and the knowledge it creates. At the same time, AI cannot be a continued degradation of the free flow of ideas and journalism that is essential for democracy to function.
Newton’s Law in the AI age
In 1686 Sir Isaac Newton posited his three laws of motion. The third of these holds that for every action there is an equal and opposite reaction. Newton described the consequence of physical activity; generative AI is raising the same consequential response for informational activity.
The threat of generative AI has pushed into the provision of information and the economics of information companies. We know the precipitating force, the consequential effects on the creation of content and free flow of information remain a work in progress.
13 notes
·
View notes
Text
Elevate Your Business Efficiency with Newtech Infosoft's Cutting-Edge Document Management Solutions
Secure File Management Software | Cloud Based Document Management
By using the power of Cloud Based Document Management and Secure File Management Software, Newtech Infosoft has the capacity to provide you with a comprehensive document management system that will streamline your business processes and increase your productivity. This is because of our commitment to innovation and perfection.
Features and Capabilities of Our Document Management System
Our Document Management System has several features and capabilities that are helpful in making document management processes more efficient and effective. Some of them include:
Document Storage and Organization: Your documents can be easily stored, organized, and accessed from a centralized repository, thus eliminating the need for manual filing systems and retrieval.
Version Control: With our version control feature, you can track changes made to different versions of the document, hence ensuring that you have access to the latest information all the time.
Collaboration Tools: Collaboration tools like document sharing, commenting and real-time editing are built-in so as to enable team members to work together on a project effectively.
Search and Retrieval: Our robust search and retrieval functionalities help you quickly find your desired files, thereby saving both time and effort.
The Advantages of Cloud Based Document Management
Today’s corporate world has unprecedentedly evolved from the analogue to the digital era of technological advancements, a move that rendered conventional document management methods ineffective. There are several advantages associated with Cloud Based Document Management, which include:
Accessibility: With cloud based document management, you can access your documents at any time, from anywhere and with any device that has an internet connection. This elasticity will foster more teamwork and efficiency among your employees despite their location.
Scalability: Unlike typical document management systems, which are constrained by physical storage space, Cloud based document management systems can easily expand to meet the needs of your growing business. Our Document Management System is capable of scaling up whether you are a small start-up or a big corporation.
Cost-Effectiveness: Our Cloud Based Document Management eliminates the need for physical storage space and reduces reliance on paper processes, thus helping to cut down operational costs and improve efficiency at work.
The Importance of Secure File Management Software
The protection of one's data is of the greatest importance. With cyber dangers increasing, organizations of all sizes must priorities the security of important information. The benefits that are listed below are made possible by our Safe File Management Software:
Encryption: You can be sure that your documents are safe from unauthorized access and cyber threats because of our Document Management System (DMS), which uses high-level encryptions.
Access Control: The Secure File Management Software we have provides the capability for you to determine who gets what documents and what activities could be done by them. This level of access control is helpful in curbing data breaches and meeting regulation standards.
Audit Trails: Our systems give you complete audit trails that enable you to track and monitor user activity on the system. Such openness not only helps detect and deter unauthorized access but also facilitates regulatory compliance.
Why Choose Newtech Infosoft?
Expertise: Put to use our know-how and experience of many years in this software innovation business.
Customization: Our solutions are tailored to meet your specific needs, ensuring maximum effectiveness and efficiency.
Reliability: We will ensure trust in our systems by offering dependable and secure software solutions while keeping your most sensitive data safe in our hands.
Support: We have experienced experts who are there for you every step of the way if you need any assistance whatsoever.
Innovation: Our Creative Solutions are designed to meet the ever-changing needs of your organization so that you can always be ahead of others.
Transform Your Business Today
If you want your company to advance, you shouldn't let its document management and file- handling procedures become outdated. Experience the difference that our Cloud based document management and secure file management software solutions can make by partnering with Newtech Infosoft and providing them with your business.
Schedule a Consultation Today
So, are you ready to reengineer how your records management and file handling operate? Call us Now +91 7926300458 / +91 7940024458 or +91 9426069095 / +91 8780965381. In addition, you can reach us via email at [email protected] and book an appointment with our professional consultants.
Let our Cloud Based Document Management and Secure File Management Software Solutions illustrate the way your company can reinvent itself and be more productive while being secure from any data breaches.
1 note
·
View note