#Crack Windows 10 Password
Explore tagged Tumblr posts
Text
tumblr please help
hiiii!
so I’m an actual dumbass when it comes to fixing technology and require some help
background: I have this really shitty Inspiron n7010 dell laptop that is currently running windows 10. it was my dad’s work laptop for a few years and I wanted to use it for burning cds. so I crack it open to use and works perfectly for a few hours! then it randomly shut down at one point so I went to turn it back on. and it got to that one screen that says “repairing drive or smth, this may take over an hour” and then shows a percentage. it got to 100% pretty quick, but nothing was happening. then it randomly shut down.
ever since then; the cycle goes
I turn on the laptop
it boots up
it loads for a bit
blue screen of death
boots up again
loads with “preparing automatic repair”
loads with “diagnosing your pc”
wait wait wait load load load
“Automatic repair couldn’t repair your pc” then buttons for either shutting down or advanced options.
Then it lets me either; turn it off, troubleshoot, or continue to windows ten.
(I can’t reset the pc, use the recovery tool, system restore, system image recovery, or uninstalling updates bc my account isn’t an admin account and my dad can’t remember the password to his)
I have tried using startup repair; it leads to a screen that says “startup repair couldn’t repair your pc”
I’ve tried booting in safe mode in every way possible it gives me, it still won’t work.
I’ve tried disabling driver signature enforcement, I’ve tried disabling automatic restart on system failure, but it still won’t boot up.
The recent downloads are just audio files from a yt to mp3 converter called “cobalt”
Is there anything I could possibly do?
Anyone with tech knowledge please look at this post
I’m sorry if this is a complete rambling and is unfixable, but if anyone has suggestions please drop them in the comments or reblogs.
#computer#computer repair#please help#technology#tech repair#tech#laptop#stupid shit#genuinely though can someone help I just wanna burn my fucking cds#calling all smart people
3 notes
·
View notes
Text
mario + rabbids incorrect quotes vol:2
*The Squad is on a hike* RL: It’s beautiful out here. peach: And quiet. RL: Too quiet. peach: Did we lose someone? *cut to edge with a bear in a headlock*
peach: Rabbid luigi is a perfect cinnamon scone who’s never done anything wrong in their entire life! RM: Never done anything wrong?! They set a city block on FIRE!
mario & RR:*Playing video games* peach: You guys woke up at 5:30 in the morning just to play games? mario: *silence* RR: *silence* peach, finally figuring it out: ...You two never went to sleep, did you? mario & RR in shame: Yeah...
peach: Okay, what does A stand for? RL: Arson. peach: Aw, you're so good. Okay! B! What does B stand for? RL: Barson. mario: *laughter* peach: What stands for C? RL: Commit arson. mario: Oooo. peach: D! RL: Don't come near me, I'm going to commit arson. mario: *more laughter*
RM: We are gathered here today because someone- *glares at luigi’s coffin* -couldn’t stay alive!
Computer: Please enter a password. Rm: *types in edge* Computer: Your password is too weak. Rm: How f?$$ing DARE YOU-
RP: Yeah, but let's not get too crazy. *The gang proceeds to get arrested for blocking the road in large traffic cone costumes
RM, trying their first ever cup of coffee: I am ENERGY! peach, an avid coffee drinker, on their twelfth cup of the day: Someone slap me awake or I am literally going to fall into a coma in ten seconds.
RM: Come on edge, do it for our friendship. You can't put a price on that... edge: Yes I can, 8 dollars.
mario: If you put a milkshake in one yard and crack open a cold one in another yard, which yard would the boys go to? RP: Schrödinger's boys. luigi: MARIO WTH RL: What about cracking open a cold milkshake? RM: As we all know, the milkshake brings the boys to the yard. The presence of the boys is a prerequisite for the cracking open of a cold one, but cold ones do not have any inherent boy-attracting abilities. Milkshakes, however, do. RM: All else being equal, the boys would proceed to the milkshake yard. While it is possible to announce the presence of cold ones in the hope of attracting some boys, the pull of the milkshake is much more powerful by comparison. mario: ... RP: ... luigi: ... RL: ... RM: Mind you, all of this nonsense hinges on whether or not the boys are back in town.
peach, teaching RP to drive: Okay, you're driving and mario and RM walk into the road. Quick, what do you hit? RP: Oh, definitely RM. I could never hurt mario. peach, massaging their temples: The brakes. You hit the brakes.
RM: Your lover doesn't have the mental strength to caramelize onions. RL: Your lover thinks it takes 5-10 minutes to caramelize onions. luigi: Who's caramelizing onions? Have you sociopaths forgotten that apples exist? RM: Do you think caramelizing onions is putting caramel on onions?
hold on stop the quotes for a second, THATS NOT HOW IT WORKS!? caramelizing doesnt mean putting carmel on it? I've been calling caramelizing when I put caramel on ice cream
back to regular program~
RM: As usual, RM has to save the day! edge: As usual, edge has to hear about it
peach: That’s the key slice of truth we need to complete the entire truth pie. RR: Ooh, can we get some actual pie? peach: I like the way you think.
mario: *shatters a window and climbs through it* mario: *turns around and helps RL through it* Breaking and entering is wrong RL. RL: Okay.
edge: All of your existences are confusing. The Squad: How so? edge: Your presence is annoying, but the thought of anything bad happening to any of you upsets me.
peach, texting group chat: What flavour of ice cream do you guys want? I’m at the store so be quick! RL: Moose Tracks is good! RR: What the bawh is that!? RL: *Gasp* How dare you insult moo- RR: No. No no not that. What the hell. Why do you spell flavor like flavour. It’s like you have flavor but then this guy shows up and is like “Oui Oui Would you like chocolate flaVOUR or vanilla flaVOUR. peach and RL: what? RR: I don’t get it why add the EXTRA u when it’s PERFECTLY FINE AS IT IS!? peach: You done now? RR: Yeah ok. peach and RL: ... RR: ...Can I have the Mint Chocolate chip flavour?
*RM and RR are fighting* edge, taking aspirin: I have a headache! Can you guys just be cool?! *RM and RR start fighting while wearing sunglasses and riding skateboards*
RP: What the hell is wrong with you? RM: I have this weird self-esteem issue where I hate myself but still think I’m better than everyone else.
RM: *spits mouthful of blood onto floor* You’ve become far more powerful since we last crossed paths. Dentist: Please stop, there’s literally a sink right next to you.
mario, opening a Capri Sun: Guess I'll drink my sorrows away.
peach: Would it be discrimination to only hire employees at my doughnut shop who have the same name? RP: Legally, I don't believe that breaches any discrimination laws. Morally though... I don't know. peach: I believe god is on my side when it comes to Duncans' Doughnuts.
edge: Let's all agree that going up the stairs on all fours is actually the best experience on earth. RR: Conversely, going down the stairs on all fours is actually the most terrifying experience on earth.
#mario rabbids#mario plus rabbids#mario + rabbids#mario +rabbids spark of hope#super mario#mario plus rabbids spark of hope#rabbid mario#mario rabbids sparks of hope#mario rabbids kingdom battle#rabbid luigi#rabbid peach#rabbid edge#rabbid rosalina#princess peach#mario and luigi#luigi#luigi mario#mario mario#mario memes#incorrect mario quotes
54 notes
·
View notes
Text
“When did you know?”
Written: 7/16/22
7 year old Kori rolled out of bed and ruffled her hair, staring at her shirtless body as she stood in the mirror. She made a weak attempt to flex her biceps before giving up in a huff. She poked her head out of her room, checking for her brothers. Unable to hear them, she stepped out of her room and slid down the railing to the bottom of the stairs, checking for her parents. No sign of them either. She’d been left all alone. This was great! Kori ran back up the steps and bursted into her eldest brother’s room. She sat at his desk and twirled in the chair, stopping herself as her head spinned. She lifted up the bed, checking for all of his embarrassing secrets. With nothing of interest under the bed, she set it back down. Kori flopped on his bed and sighed. “Jiwon, your life is so boringgg.” She looked in his bed tables drawer, quick to remove his tablet from its rightful place. Typing in his password that she had memorised already, a window popped up upon unlocking. “ ‘Hands off, annoying little brothers…’ ” she rolled her eyes and scoffed. “Whatever.” She clicked out of the window but it continued to pop up, making her unable to actually do anything on it. She huffed and threw it back in his drawer, going elsewhere to solve her boredom.
Kori’s eye wandered to the crack in her parents door and she happily accepted the opportunity to peek in. She picked up her fathers spare glasses off his bed side table and peered through them before sliding them on her face. Everything was so much blurrier than before and they were making her eyes hurt so she took them off and put them back on his table, skipping over to snoop in her mothers vanity. She had so many different kinds of face paint that Kori was enthralled by it all. She uncapped what she thought she be a metallic crayon. She’d watched her mother put this on once before and smeared it over her lips as she had. “Hm… what else does she do? Oh! Her eyes.” She rubbed fingers in the powder and rubbed it over her eyes. “And now.. now, I’ll brush my hair.” She grabbed the brush off of the table and brushed the top of her head, smoothing back over the top. “There. Pretty.” She grinned at her reflection, still yet to find a shirt. Not wanting to put on any of her own clothes, she looked through her parents closet. She took one of her mothers shirts off it’s hook and threw it over her as the bottom of the shirt covered her shorts yet still left the majority of her chest exposed. She walked back to the mirror on the wall and stared at her new appearance. It looked like she was wearing a dress as the shorts remained completely hidden under the hem. Her eyes glazed over in awe and she played with the end of the shirt, lifting it up to show her shorts before letting it fall again. She’d wear this forever, that settled it.
—
Kori sat in her room reading a book on the floor as she ate the bag of strawberries she’d swiped from the fridge when she heard the front door close, signifying her family’s return. It wasn’t long before her mother was looking into her room.
“Hanbin, what have you been doing?” She asked with a hand over her pendant.
“Reading.” She got up from the floor and walked over to her door, staring up at her mom.
At first she was quiet, analysing Koris fashion choices for the day. Kori looked down at the shirt that had gotten slightly dirtier in her reckless eating. She smoothed out the bottom and looked back up. “Do you like it?”
“Do you?”
Kori nodded. “It’s pretty, right?”
One of her older brothers walked past, quickly back tracking to take a look for himself. “Jesus what’d you do to your face, Hanbin?”
“Nothing.. I was just pretending to be mommy.”
“Why don’t you go wash your face and put on some real clothes?” Her mother said with a stern tone and pulled her oversized shirt off of her. “Go, go. Before your father sees.”
“Did I do something wrong?”
“Go, Hanbin.”
Kori huffed and walked to the bathroom to wash her face.
10 year old Kori was running errands with her mother, in charge of carrying the cart. She held the handles in both of her hands as she walked behind her. Her eyes wandered to the womens clothing section, taking in all the pretty clothes on display.
“Keep up, Hanbin.”
She reluctantly turned her attention away and kept walking.
Her mother ran a hand through the back of her head, feeling her ends. “Your hair is getting long again. I’ll have to cut it when we get home.”
“What if.. we don’t cut it?”
“Hm?”
“Maybe we could let it stay long for a little bit..? I don’t think it looks so bad..”
“If it gets any longer than that, you’ll look like a girl. Now come on.”
11 year old Kori kicked her feet, staring at herself in the mirror. She didn’t know why but she was beginning to despise her appearance more and more. Her short hair didn’t fit her face anymore, her body felt empty as though she was missing something in her life. She continued her 1 person staring competition, trying to find the answer within herself. Was it.. her eyebrows? Or maybe her eyes. Her nose? Her lips? Something was off. “Well.. say something.” She mumbled to her reflection. Ugh that voice. That voice did not sound right. Was that it then? Was that what was off with her? Everyone was saying this was a normal part of growing up. Is it.. normal to hate your appearance? It must be. It is. Everyone goes through that. Kori was normal. She was just a normal boy and this strange feeling would come to pass some day. Right…?
Authors note: First Short Story uploaded on here woohoo! I mean it’s 2 years old but.. it’s new to you guys 😅
Also if you liked this, please reblog it! I need as much exposure for my writing as possible if I’m gonna be a world famous author some day (manifesting)
#jayspace#are we dead yet#awdy#writeblr#writers on tumblr#art#writerscommunity#black writblr#writing#my writing#bookblr#Kori#Kori Kim#transgender#trans pride#transfem#trans woman#please reblog#short story#new reads
4 notes
·
View notes
Text
Hack the Future: Top Ethical Hacking Tools & Techniques You Need in 2025 Cybersecurity threats are evolving, and ethical hacking has become a crucial practice for protecting digital assets. Ethical hackers, also known as white-hat hackers, use their skills to identify vulnerabilities and strengthen security. This guide explores the top tools and techniques every ethical hacker should know in 2025. Understanding Ethical Hacking Ethical hacking involves simulating cyberattacks to uncover weaknesses before malicious hackers can exploit them. It follows a structured approach: Reconnaissance – Gathering information about the target. Scanning – Identifying vulnerabilities using specialized tools. Exploitation – Attempting to breach security to test defenses. Post-Exploitation – Assessing the impact and documenting findings. Reporting & Mitigation – Providing recommendations to fix vulnerabilities. Top Ethical Hacking Tools in 2025 1. Metasploit A powerful penetration testing framework that automates the exploitation process. It includes thousands of exploits and payloads for testing vulnerabilities. msfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOSTS target_ip exploit 2. Nmap A network scanning tool that helps discover hosts, open ports, and services running on a target system. nmap -A -T4 target_ip 3. Burp Suite A web security testing tool used for detecting vulnerabilities like SQL injection and cross-site scripting (XSS). 4. Wireshark A network protocol analyzer that captures and inspects network traffic to detect potential security threats. 5. John the Ripper A password-cracking tool that helps ethical hackers test password strength. john --wordlist=rockyou.txt hash_file 6. Aircrack-ng A toolset for assessing Wi-Fi network security, helping ethical hackers test for weak encryption. airmon-ng start wlan0 airodump-ng wlan0mon aircrack-ng -b target_bssid -w wordlist.txt capture_file.cap 7. SQLmap An automated tool for detecting and exploiting SQL injection vulnerabilities. sqlmap -u "http://example.com/index.php?id=1" --dbs 8. Hydra A fast and flexible brute-force password-cracking tool used for testing login security. hydra -l admin -P passwords.txt target_ip ssh 9. OSINT Framework A collection of open-source intelligence (OSINT) tools used for gathering information about a target from publicly available sources. 10. Cobalt Strike A professional red-teaming platform used for advanced penetration testing and adversary simulation. Key Ethical Hacking Techniques 1. Social Engineering Manipulating individuals into divulging confidential information through phishing, pretexting, or baiting. 2. Wireless Network Attacks Exploiting weak Wi-Fi security protocols using tools like Aircrack-ng to gain unauthorized access. 3. Man-in-the-Middle (MitM) Attacks Intercepting and altering communications between two parties to extract sensitive data. 4. Privilege Escalation Exploiting system vulnerabilities to gain higher access privileges. 5. Reverse Engineering Analyzing software or hardware to find vulnerabilities and potential exploits. 6. Zero-Day Exploits Identifying and exploiting undiscovered security flaws before patches are released. 7. Web Application Penetration Testing Assessing web applications for vulnerabilities like cross-site scripting (XSS), SQL injection, and security misconfigurations. 8. Endpoint Security Testing Evaluating workstation and server defenses against malware, ransomware, and unauthorized access. The Future of Ethical Hacking in 2025 The rise of AI, machine learning, and quantum computing is reshaping cybersecurity. Ethical hackers must continuously update their skills and leverage AI-driven security tools to stay ahead of cyber threats. Conclusion Ethical hacking is an essential practice in modern cybersecurity. By mastering these tools
and techniques, ethical hackers can help organizations strengthen their defenses against cyber threats. Continuous learning and adaptation to emerging technologies will be crucial in 2025 and beyond.
0 notes
Text
.
.
.
“Who can I Trust in a situation Like this..?”

.
---
.
.
🕯 DAY 1: “Something's Watching Me”
📅 **Date:** May 17th, 2003
📍 **Location:** Kame House, Offshore Island (on a small island south of the central continent, in the middle of the ocean)
🕰️ **Time:** 11:32 PM
🔋 **Battery:** 42%
📶 **Reception:** 3 bars – weak but livable
🔒 **Encrypted Note**
(Password-protected: *LupineLothario*)
---
📖 **>ENTRY START:**
\[INTRO: "I’m Not Crazy. Right?"]
I’ve always hated nights like this. The kind where even the ocean sounds fake, like it’s mimicking life just to trick me into thinking I’m safe. You’d think an island as peaceful as this—miles away from fans, journalists, *her*—would calm my nerves.
But tonight? Something feels *off*.
It’s been three weeks since Tien crushed my leg like a soda can during the 22nd Budokai. My body’s healing, sure… but my mind? Not so much. I *feel* watched. Not in the usual “oh hey it’s Yamcha, the desert bandit turned martial arts heartthrob” way.
No.
This feels *filthy*. Violating.
---
📨 **>RECEIVED FILE - \[Multimedia Message, 10:48 PM]**
📎 Attachment: JPEG (blurred face, cropped, body shot)
📎 Attachment: Red satin panties (physically mailed, not digital)
Text Message (Sender Unknown):
“You should wear red too sometime. I bet it’d look even better crumpled on my floor 💋”
I showed it to Bulma.
That was the worst fucking decision I’ve made in a while.
She *slapped* me.
Didn’t even let me explain. Didn’t *want* to hear the words: “I didn’t even *open* the damn package until just now.”
She saw the photo and those panties and stormed out of the call like I’d confessed to murder. Which—ironically—I wish I had. Might’ve gone over better.
---
💭 **>MENTAL STATUS: (Disoriented + Agitated + Paranoia Rising)**
I’ve dealt with fans before. Autograph-hunters, peeping toms, hell, even a guy who tried to mail me his *kidney* once. But this… feels intimate.
The photo wasn’t random.
That GI the girl wore? Looked exactly like *mine.* The one I wore during the tournament.
Same cut, same orange tone. Hell, even the *rips* on the chest seam looked identical.
It’s not cosplay.
It’s *recreation.*
The pose too—it was from *my fight with Tien*, frame-by-frame. Her leg raised, one arm tilted back. Like she studied the tournament tape and mimicked it with obsession.
But what really gnawed at me?
She knew my *location.*
The envelope was addressed to “Yamcha other // Recovery Room – Kame Island” in shaky, handwritten kanji. her handwriting is weird and very cryptic..
---
🧠 **>SYMPTOMS LOGGED:**
* Stomach cramps (not from the beans this time)
* Loss of appetite
* Phantom whispers at night (“*Don’t look out the window.*
* Sudden smell of lavender (not native to the island)
* Repeated power flickers only in my room
* The feeling of breathing on my neck when I sleep sideways
---
🕵️ **>THEORIES FILE:**
[1] Bulma sent the package to trap me.
> Nah. She’s jealous, not psychotic. And she’s not a fan of Gyaru girls. She likes her tech and bodysuits.
\[2] One of Roshi’s old “disciples” trying to scare me.
> Could be. But how’d they get that *exact* outfit replica?
[3] A fan. A real one. One who watches. One who’s already here.
> …Fuck. The door was unlocked all day. I napped after lunch. Roshi went fishing. Krillin went home. I *was alone.*
---
🖼️ **>INVESTIGATION – PHOTO ENHANCEMENT (Manually Zoomed on Flip Phone)**
* Brown skin
* Short black hair, kind of frizzy at the edges
* Chubby build
* Cropped face, but shadow under jaw suggests smiling
* Back wall looks *too familiar.* Cracked pink tile. Possibly the public bathhouse at West City…?
I think I’ve *seen* her before.
I don’t know where.
But my stomach dropped when I noticed
something in the background.
The tournament poster.
Hung on her wall.
Signed.
By *me.*
I only signed that many during the Budokai *after-party.* That means she was *there.* Maybe even shook my hand.
---
📹 **>ACTIVITY TIMELINE – TODAY:**
* **8:30 AM:** Woke up. Dreamt someone was brushing my hair. I don't have long hair anymore
* **9:15 AM:** Brushed teeth, door creaked open behind me. Roshi blamed humidity.
* **10:00 AM:** Beach walk. Saw footprints that didn’t match any sandals we own.
* **3:46 PM:** Nap. Had a dream I couldn’t breathe. Woke up with pillow over face.
* **7:00 PM:** Package arrived by air courier. No name.
* **10:48 PM:** Multimedia message.
* **11:00 PM:** Me & Bulma got into a fight.
* **11:31 PM:** Still shaking. My GI smells like perfume. *and It’s not from my girlfriend..*
---
🎮 **> “Stay in the Room” or “Investigate the Dock”**
I’m too fucked up to think straight.
But if this was a game, I’d pick *“Investigate the Dock.”*
Which is exactly what I’m going to do.
I’m taking my phone with me.
If this is the last thing I write and someone finds this?
I *didn’t* cheat.
I didn’t ask for this.
And if that girl is *real*—
if she’s already here—
then someone better fucking find what’s left of me before the tide does.
---
— 📱Yamcha’s Log – End of Day 1.
🛌 Sleep mode not activated.
🔒 Note encrypted.
*If I don’t write Day 2… she probably slit my throat while I was dreaming of that damn fight again.*
**END ENTRY.**
📁 Saved to: “WOLF.LOG”
🔔 Reminder set for 6:00 AM – *Wake up before she does.*
.
.
.
#yamcha#Alternative timeline#AU#dragonball#psychological horror#drama#early2000s#2000s#Bulma#Yamcha x Bulma#Spotify
1 note
·
View note
Text
0 notes
Text
10:08pm 05/02/2025
I have two windows cracked to hear the rain. My apartment is small, so the window in my living room (where I am sitting) is to my left, and the window in my kitchen is a short distance to my right. I am surrounded by the sound of rain. We live in a triplex with our neighbors residing above us, so I do not get to hear the rain fall on the roof. Only they get that pleasure. There is thunder rolling in the distance, and I wish it would roll my way to lull me to sleep, which I will have to attempt to do shortly.
I am distracted by the rain, but I wanted to write an update. I will be returning to school to pursue a Master's in Literature in the fall. My plan is to learn, and to network. I feel that I am in a much more capable headspace than I was during my undergrad, and I intent to get the most I can out of returning to University.
I've been keeping a physical journal for a bit, but I find it harder to find time to write. I have not kept up with it as well as I once kept up with documenting my days and feelings here, but something doesn't feel right about writing my journal entries online. Sometimes I think about keeping them in some sort of application, or even just a word document, but I don't want them accessible from my laptop without a password. I write here in an incognito tab, and I always log out. I'm sure there are password protected journals, but if it's some slightly obscure app, I fear that there is a higher risk of losing the entries written there forever. They feel safer on a website I'm familiar with.
I worry about my laptop. The fan starts to get very loud fairly quick. I'm going to need it for school, but I hope that it doesn't die. I can't really afford it dying. Maybe the fan just needs a cleaning. Maybe that's something I can do myself.
I'm going to read before sleep, and I abruptly feel that I don't have anything else left to say for now. I believe it to be the fan. The sound has silenced my mind.
10:25pm
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Forgot Windows 8.1 Local Admin Password No Reset Disk How to Resolve
How to get back into your Windows 8.1 computer if you have forgotten local administrator password no reset disk, how can you reset administrator password in Windows 8.1 without reset disk?

To resolve this problem, you can firstly try Offline NT Password Editor to help reset the forgotten Windows 8.1 administrator password without reset disk. Offline NT password Editor can help clear or reset Windows local account password via CD/DVD. The following procedure will show you the detailed walkthrough.
Trick 1: Use Offline NT Password Editor to Reset Windows 8.1 Local Admin Password (Work with CD/DVD).
When you forgot Windows 8.1 administrator password and a password reset disk was not created, “Offline NT Password Editor”, a free Windows password reset disk, can help you reset forgotten Windows 8.1 local account’s password without knowing it. Free download the ISO file from the official site. Extract the downloaded file and then burn the ISO file on to a writable CD/DVD. Once burning completed, you can use the CD/DVD which is bootable to crack Windows 8.1 Local Admin password.
Step 1: Power on your locked computer and then insert the bootable CD to the CD-ROM.
Step 2: Restart the computer to boot from CD/DVD. If it still boot into Windows, you may need to change device boot order in BIOS. Learn how to boot computer from CD/DVD.
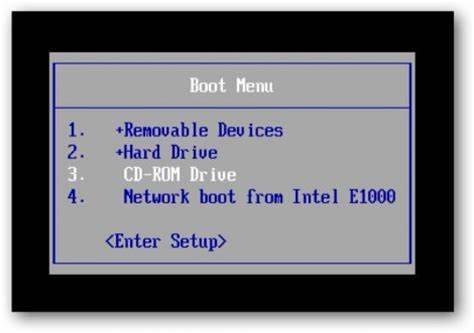
Step 3: When the computer boots from CD and loads Offline NT screen, press Enter until the “step one” appears. Type “1” and hit Enter.
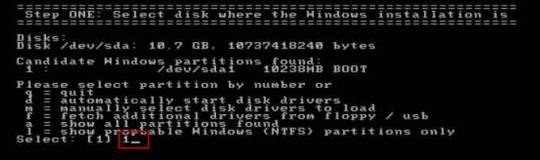
Step 4: Select “Password reset”, type “1” and hit Enter.
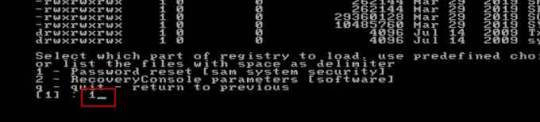
Step 5: Select “Edit user data and passwords, type “1” and hit Enter.
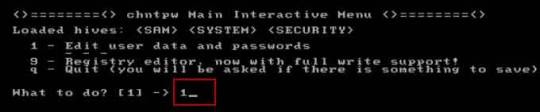
Step 6: Select a user account, type “administrator” and hit Enter.
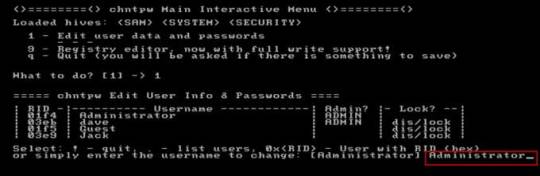
Step 7: Select “Clear user password”, type “1” and hit Enter.
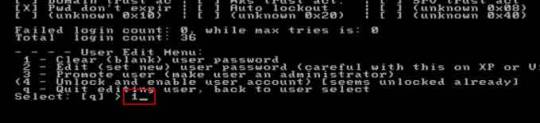
Step 8: Administrator’s password is cleared. Select “Quit editing user and back to user select”, type “!” and hit Enter.
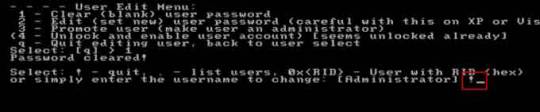
Step 9: Select “Quit”, type “q” and hit Enter.
Step 10: Write back changes, type “y” and hit Enter.
Step 11: When it asks you if try again, type “n” and hit Enter.
Step 12: Now eject your CD and then press CTRL-ALT-DEL to restart the computer.
Step 13: When Windows 8.1 welcome screen appears, click the screen to automatically sign in administrator without password.
Another simple method to reset forgotten Windows 8/8.1 local admin password is using a password recovery program, Windows Password Rescuer, which is working fine for all Windows systems including Windows 11. Here is how to use the utility to reset a local admin password on Windows 8.1/8 PC without logging in.
Trick 2: Reset Windows 8.1 Administrator Password with Windows Password Rescuer Run from USB.
If you have forgotten Windows 8.1 administrator password and need to get back into the account, you can use Windows Password Rescuer to create a bootable USB disk and then use the disk to reset Windows 8.1 local administrator password easily without losing data. It also works perfectly for Windows 11, 10, 8.1, 8, 7, Vista, XP and Windows server 2022, 2019, 2016, 2012, 2008, 2003 etc.
Equipment required: Another Windows computer, USB flash drive.
Read more detailed steps: How to reset Windows 8.1 Admin Password with USB.
Step 1: Use another computer to download Windows Password Rescuer and then install the software.
Step 2: Plug in a blank USB flash drive to the computer and launch the software. Select “USB device” on the software screen.
Step 3: Pull down the drive list and select your plugged USB flash drive. Then click “Begin Burning” to create a bootable USB under a minute.
Step 4: Once the burning process is completed, unplug the USB flash drive and then connect it to your locked computer that you want to reset Windows 8.1 password.
Step 5: Power on the locked computer and press F12 as soon as possible to open “Boot Menu”. Press arrow key to highlight USB option and press Enter to boot from USB.
Step 6: Once the locked computer boots from USB and locates Windows Password Rescuer, you can reset administrator or other local user account passwords with several clicks. Now click “Administrator” from user list.
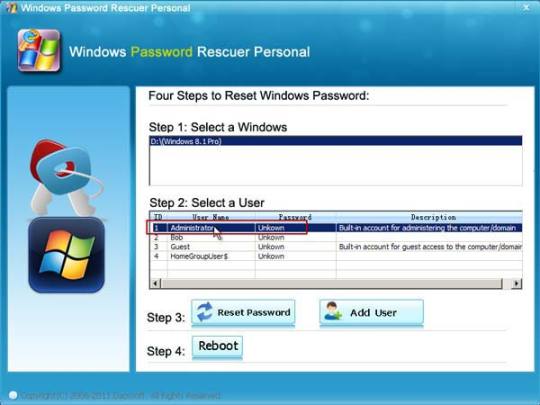
Step 7: Click “Reset Password”, when it asks you if reset administrator password to blank, click “Yes” to confirm it.
Step 8: Administrator password will be removed and shown blank in password list. It means that you will be able to sign in the account without password.
Step 9: Click “Reboot”. When it asks you to remove your USB, remove the USB from your computer and then click “Yes” to restart the computer.
Step 10: After restarting, you can log on administrator without password.

Methods in this article apply to any laptop and desktop computers such as Dell, HP, Toshiba, Acer, Lenovo, Asus etc.
0 notes
Text
PassFab iPhone Backup Unlocker 5.2.23.6 Full Crack
PassFab iPhone Backup Unlocker Free Download PassFab iPhone Backup Unlocker For PC Windows 11, 10 Quickly recover iTunes backup password, remove backup encryption settings, and remove screen time passcode for…
#artists on tumblr#batman#cats of tumblr#billford#fiddleford mcgucket#free palestine#bill cipher#agatha harkness#gravity falls#agatha all along
1 note
·
View note
Text
0 notes
Text
youtube
how to find gmail password,password with keke palmer,chelsea handler password password,wifi password hacker, wifi password hacker app,password hacking,how to hack wifi password,hack wifi password,how to hack a password, wifi hacking password,password cracking,how to hack wifi without password,wifi password,hacker, wifi password change,windows password hacking,password hash,how to crack wifi password,1password, passwords,how to connect wifi without password,password tips,password hacking kali,how to hack password, reset windows 10 password,password reset,password,forgot password,remove password on windows 10, how to reset forgotten password in windows 10,how to reset windows 10 password,reset windows 11 password, reset windows 10 password without cd or software,reset windows 10 password with cmd,windows 10 password reset, reset windows 11 password command prompt,reset windows 10 password without losing data, how to reset password on windows 10,windows 11 password,facebook password,facebook password change, how to recover facebook password,show facebook password,facebook password reset,how to see facebook password, how to change facebook password,facebook ka password kaise pata kare,facebook,i forgot my facebook password, how to find facebook password,how to reset facebook password,how to see facebook password in mobile, forgot facebook password,facebook forgot password,facebook password kaise pata kare,gmail password, change gmail password,how to change gmail password,reset gmail password,gmail password change, password,how to reset gmail password,change gmail password on android,gmail password change kaise kare, how to change password in gmail,gmail password change in mobile,forgot gmail password, gmail ka password kaise change kare,gmail ka password bhul jane par kya kare,gmail id password change, change gmail password in mobile,gmail account password change
0 notes
Photo

Cybersecurity Brief: National Summary In January of 2024, Microsoft announced that "senior leadership" emails had been accessed by Russian-linked hackers, Midnight Blizzard (associated with SolarWinds hack). In March, Microsoft revealed that the breach also led to source code being stolen in what was described as an ongoing attack that also breached "internal systems". Microsoft warned that customer "secrets" were accessed and that Midnight Blizzard "increased the volume of some aspects of the attack, such as password sprays, by as much as 10-fold in February" com...(CLASSIFIED) Cybersecurity analysts assessed that following an FBI shutdown of some AlphV servers, AlphV "staged" (faked) its own shutdown to avoid future government targeting of the cybercrime group. Debrief: AlphV obtained $22 million from a ransomware attack and is expected to regroup and rebrand before beginning new attacks. The gr...(CLASSIFIED) There is an increased use of malware in "cracked software" (applications downloaded on unofficial sites or pirated software) targeting macOS, Android, and Windows devices. The malware then seeks out and removes cryptocurrency from Bitcoin and Exodus wallets. Related to this malware is an increased effort to use unknowing users as conduits to conduct brute-force password-cracking attacks on WordPress sites. Compromised WordPress sites that are visited by users could trigger 40,000+ simultaneous br...(CLASSIFIED) Debrief: Cyberattacks are becoming more frequent. While hacking by criminal groups that attempt to obtain data (to either hold for ransom or conduct identity theft actions) persist, the greater threat are probes into the U.S. infrastructure. Both ransomware breaches and foreign actor linked attacks on the energy, water, and communications sector pose the greatest threat to both disrupting our daily lives and preventing a U.S. response to aggressions domestically or OCONUS. Remain pr...(CLASSIFIED, get briefs in real-time unredacted by joining at www.graymanbriefing.com)
0 notes
Text
How to Unlock an iPhone Without the Passcode? - ITMlab

For more visit: How to Unlock an iPhone Without the Passcode? - ITMlab
If you’ve forgotten your iPhone’s passcode, you’ll need to find another way to unlock it. There are two ways to do this: resetting or unfreezing the device. You can only use these methods if you know the last date and time that someone used the phone last, but it’s worth noting that it doesn’t matter whether or not they’re still using it today. In this article we’ll show you how to unlock an iPhone without a passcode using both methods so let’s get started!
How to Unfreeze an iPhone
If your iPhone has a passcode, you can use it to unfreeze the device.
In Settings, tap Passcode (or Touch ID & Passcode on an iPhone X or later).
Enter your passcode and tap Turn Off Screen Lock or Change Passcode if prompted to do so by entering an old one that’s no longer valid and then creating a new one for future use when prompted again by iOS 11+ devices or earlier versions of iOS 10 – 12+.
Once the screen is unlocked after entering your security code correctly, go back into Settings and navigate down until you find General > Reset > Erase All Content & Settings; then tap Reset All Settings near the bottom right corner of this page next time you need help with any kind of problem related specifically towards these two different types as well as other common ones involving battery life issues etc., which are often caused by third party apps installed on top of stock apps preinstalled within Windows Phone 8 OS software packages themselves rather than being caused by hardware itself failing due entirely instead due partially maybe even slightly due mostly perhaps entirely too much stress placed upon physical components inside those phones’ casing which causes them eventually break down over time leading up until eventually breaking down completely leaving nothing left behind except maybe some dust particles floating around inside air pockets created under pressure between different parts connected together tightly enough together tightly enough so not too many particles escape through cracks created during production process at factory level back when manufacturing line workers were still working hard trying hard laboriously day after day night after night
How to Unlock a Locked iPhone Without the Passcode
If you’re locked out of your iPhone and don’t know the passcode, there are a few ways to unlock it.
Use the emergency call option: If you can’t use Touch ID or Face ID because of an injury or other reason, go to Settings > Emergency SOS and tap “Call.” You’ll be able to make an emergency phone call without unlocking your device.
Connect the phone to a computer: If you have access to a computer, connect it through iTunes or iCloud (depending on which service was used when setting up the passcode). In both cases, this will allow iTunes/iCloud Backup & Restore options that will let you restore from a backup without entering any passwords or passcodes at all!
How to Reset the Passcode on an iPhone 7 or Older
If you have an iPhone 7 or older, resetting your passcode is a little different than unlocking it.
First, turn off Find My iPhone in iCloud settings. Launch Settings on your device and select General > Reset. Scroll down and select Erase All Content and Settings, then tap Erase iPhone (or whatever name pops up).
Resetting the passcode on a newer iPhone is slightly different. First, turn off Find My iPhone in iCloud settings. This will prevent the phone from being locked if it’s lost or stolen in the future. Then, launch Settings on your device and select General > Reset. Scroll down and select Erase All Content and Settings, then tap Erase iPhone. Wait for your device to reset itself and then set it up as a new device from scratch using its default settings.
If you’re trying to unlock an iPhone without the passcode, here’s how:
Resetting the passcode on a newer iPhone is slightly different. First, turn off Find My iPhone in iCloud settings. This will prevent the phone from being locked if it’s lost or stolen in the future. Then, launch Settings on your device and select General > Reset. Scroll down and select Erase All Content and Settings, then tap Erase iPhone (or Erase All). Wait for your device to reset itself and then set it up as a new device from scratch using its default settings.
You can use one of these methods to unlock your phone without the passcode
There are two ways to unlock an iPhone without a passcode. If your phone is not protected by a passcode, then there’s nothing stopping you from simply pressing the home button and seeing if it unlocks. If it does, then great! You don’t have to worry about anything else right now.
If your iPhone is protected by a passcode but you forgot what it was set up as (or if someone changed it), then there are still options available for unlocking it without entering that code.
If you’re looking for a way to unlock your iPhone without using its passcode, then this article is for you. We’ve discussed all of the different options available to you and explained how they work in detail. Hopefully, one of them will work for your situation!
Outline of the Article:
I. Introduction
Importance of iPhone security and the significance of unlocking methods
Brief overview of the methods covered in the article
II. Using Face ID to Unlock iPhone
Explanation of Face ID technology and its setup process
Step-by-step guide on unlocking iPhone using Face ID
III. Unlocking iPhone with Touch ID
Introduction to Touch ID and its fingerprint recognition system
Instructions on setting up and using Touch ID for unlocking
IV. Using Siri to Bypass Passcode
Cautionary note about the risks associated with Siri bypass
Steps to attempt unlocking iPhone using Siri (if applicable)
V. Using iCloud to Remove Passcode
Guide on using iCloud’s Find My iPhone feature to erase the passcode
Detailed steps for remotely unlocking the iPhone through iCloud
VI. Contacting Apple Support
Importance of reaching out to Apple Support for professional assistance
Information on Apple’s verification and security procedures
VII. Conclusion
Summary of the methods discussed and their implications
Emphasis on the importance of iPhone security and responsible unlocking practices
For more visit: How to Unlock an iPhone Without the Passcode? - ITMlab
0 notes
Text
“Ethical Hacking Toolbox: Essential Tools and Strategies”
Essential Tools for Ethical Hacking

Ethical hackers rely on a variety of tools and software to effectively identify and assess vulnerabilities in computer systems and networks. These tools are essential for conducting successful ethical hacking engagements. Let’s explore some of the key tools used in the field:
1. Nmap (Network Mapper) Nmap is a versatile open-source tool that serves as a network scanner and mapper. It excels in discovering open ports, services, and operating systems running on a network. Nmap’s extensive capabilities make it a fundamental tool for reconnaissance and vulnerability assessment.
2. Wireshark Wireshark is a widely-used network protocol analyzer, enabling ethical hackers to monitor and capture data on a network in real time. With its packet-sniffing capabilities, Wireshark helps in analyzing network traffic, identifying potential security issues, and understanding the communication between devices.
3. Metasploit Metasploit is a powerful penetration testing framework that empowers ethical hackers to identify, exploit, and validate vulnerabilities in target systems. It offers a vast collection of pre-built exploits, payloads, and auxiliary modules, making it an essential tool for both beginners and experienced professionals.

5. Aircrack-ng Aircrack-ng is a robust suite of tools for auditing and securing wireless networks. Ethical hackers can utilize Aircrack-ng to assess the security of Wi-Fi networks, perform packet capture and analysis, and test the strength of wireless encryption protocols. This tool is especially valuable for identifying weaknesses in wireless network configurations.
6. Nikto Nikto is a web server scanner that helps ethical hackers identify potential vulnerabilities in web servers and web applications. It scans for outdated software, security misconfigurations, and common issues, making it an essential tool for web security testing.
7. Hydra Hydra is a versatile password-cracking tool that ethical hackers use to perform brute-force and dictionary attacks on login systems. It supports various protocols and services, allowing testers to assess the strength of password security.
8. Ghidra Ghidra, developed by the National Security Agency (NSA), is a powerful open-source software reverse engineering tool. Ethical hackers use it to analyze and understand malware, decompile binaries, and inspect software for vulnerabilities.
9. John the Ripper John the Ripper is a popular password-cracking tool known for its speed and effectiveness. Ethical hackers rely on it to test the strength of password hashes and identify weak or easily guessable passwords.
10. Hashcat Hashcat is another widely used password-cracking tool that supports a variety of algorithms and attack modes. Ethical hackers can use Hashcat to recover forgotten passwords or audit the security of password hashes.
11. Snort Snort is an open-source intrusion detection system (IDS) that helps ethical hackers monitor network traffic for suspicious activities or known attack patterns. It aids in the early detection of potential security threats.
12. OpenVAS OpenVAS (Open Vulnerability Assessment System) is a full-featured vulnerability scanner that assists ethical hackers in identifying security weaknesses in networks and web applications. It offers comprehensive vulnerability assessment and reporting capabilities.
13. Cain and Abel Cain and Abel is a password recovery tool that ethical hackers use to recover passwords through various methods like dictionary attacks and cryptanalysis. It is particularly helpful for recovering forgotten passwords or assessing password security.
14. Sysinternals Suite The Sysinternals Suite, developed by Microsoft, is a collection of powerful system utilities. Ethical hackers use these tools to explore and troubleshoot Windows systems, as well as analyze system internals for potential security issues.
These essential tools empower ethical hackers to conduct thorough assessments of computer systems, networks, and applications, helping organizations strengthen their cybersecurity defences.
If you want to learn more about it, I highly recommend that you contact ACTE Technologies because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline.
If you feel that my response has been helpful, make sure to follow me and it will encourage me to upload more content about Ethical hacking.
Thanks for spending your valuable time and upvotes here. Have a great day.
1 note
·
View note
Text
아크로뱃 프로 11 크랙 설치 시리얼 (adobe acrobat xi pro)
아크로뱃 프로 11 크랙 설치 시리얼 (adobe acrobat xi pro) 드립니다. 아크로뱃 프로 11 크랙 설치 시리얼 무설치 acrobat 11 pro 있습니다.
정품인증 라이센스 있고, 일련번호 시리얼넘버 공유 합니다. adobe acrobat xi pro 크랙 일련번호 설치방법 함께 다운로드 가능합니다.
adobe acrobat xi pro 11.0.20 + crack tech-tools.me
Adobe acrobat pro xi download for windows 10, windows 11
adobe acrobat xi pro 11.0.9.29
adobe acrobat xi pro 11.0.22 final + crack
아크로뱃 프로 11 & adobe acrobat xi pro 다운 <<
첨부파일 구글드라이브와 같습니다.



저는 아크로벳 프로 9 한글판을 가지고 있는 관계로 영문판으로는 설명을 드리지 못한 점 죄송합니다 영문판과 비교해 보시면 그다지 어려움은 없을 것으로 생각이 됩니다.
먼저 파일을 아크로벳으로 불러옵니다. 일단 보안이 걸려 있는지 알려면 메뉴에서 고급-보안-보안속성표시로 갑니다.
만약 보안이 걸려 있다면 아래 그림과 같이 문서변경이 허용 안됨으로 표시되어 있을 것입니다. 만약 보안이 걸려 있지 않다면 설명 4번으로 가시면 됩니다.
보안을 풀 수 있는 프로그램으로 PDF Password Remove 라는 프로그램이 있습니다. 작동은 간단합니다. 아래 그림처럼 오픈파일을 통해 보안이 걸려있는 문서를 불러온 후 다른 이름으로 저장을 하면 성공했다는 메세지가 뜹니다. 이 프로그램은 인터넷에서 PDF Password Remov Portable 로 검색을해 보시던지 아니면 다른 경로를 통해 구하실 수 있을 것입니다.
아크로벳 문서의 종류는 두 가지입니다. 워드처럼 글씨로 쓰진 것과 그림처럼 이미지 파일로 된 것입니다. 글씨로 씌어진 경우의 편집은 아래 그림처럼 도구-고급편집-터치업텍스트 도구를 선택을 한 후 해당 글씨를 선택을 한 후 수정을 하거나 삭제를 하실 수 있습니다. 만약 글꼴이 없다면 경고창이 뜰 수 있는데 확인을 누르시면 됩니다. 원래 문서는 아크로벳 프로로 문서 작성하기인데 작성을 수정으로 변경한 그림입니다.
그림파일로 된 글씨의 경우는 터치업텍스트 도구로는 편집을 할 수 없습니다. 이 경우 아래 그림과 같이 먼저 사각형 도구를 선택을 하여 수정하고자 하는 글씨에 사각형을 덮어 씌웁니다. 그러면 빨간 사각형 박스가 생깁니다. 사각형을 마우스 왼쪽버튼으로 선택한 상태에서 마우스 오른쪽 버튼을 누른 후 속성을 선택을 합니다.
아크로뱃 프로 11 크랙 설치 시리얼 (adobe acrobat xi pro) 속성에 보면 네모 박스 친 곳을 모두 배경색인 흰색으로 선택을 합니다. 만약 자주 사용을 한다면 속성을 기본값으로 변경에 체크 하시고 확인을 누르면 됩니다. 그러면 글씨가 지워집니다.
7.만약 글씨를 수정하고 싶다면 도구에서 입력도구나 입력도구 도구 모음 표시를 선택을 합니다. 그리고 커서가 깜박이는 곳에 글씨를 쓰고 폰트와 크기등을 수정한 후 원하는 곳으로 옮기시면 아래 그림과 같이 됩니다. 단 이 경우 그림파일을 경우 폰트가 없을 경우 수정한 글씨와 글씨체가 안 맞을 수도 있을 것입니다.
8.자주 사용하는 도구는 일일히 메뉴바에서 찾아 들어가기 힘드니까 아래 그림과 같이 도구모음 사용자 정의를 선택을 하여 자신이 자주쓰는 도구에 체크를 하시고 메뉴바로 빼 놓으시면 편리하실 것입니다. 아래 그림은 제 경우의 도구바를 수정한 그림입니다.
이외 아크로뱃 프로 11 크랙 설치 시리얼 (adobe acrobat xi pro) 텍스트 상자 도구를 이용해 글씨를 쓰는 방법도 있습니다. 여기에 대해 제가 다른 분의 질문에 답변을 해 드린 것이 있으니 이것도 참고해 보시면 될 것입니다
1 note
·
View note