#Data Verification Services
Explore tagged Tumblr posts
Text
The Role of Data Verification in Strengthening Data Trustworthiness for Better Decision-Making
Making informed decisions depends on the reliability of data. This blog dives into how data verification serves as a foundation for building data trustworthiness, ensuring businesses work with accurate, consistent, and reliable information.

What is Data Trustworthiness?
Data trustworthiness refers to the degree to which data can be trusted to guide decision-making. It involves accuracy, consistency, completeness, and relevance.
Challenges in Ensuring Data Trustworthiness
Organizations often face:
Incomplete or outdated records
Duplicate or inconsistent entries
Errors from manual data entry
Difficulty in tracking data lineage
Understanding Advanced Data Verification
Data verification goes beyond basic checks. It involves validating data at every stage, detecting inaccuracies early, and maintaining consistent quality.
Advanced Data Verification Techniques
The blog explains several advanced techniques that strengthen data accuracy, such as:
Pattern recognition algorithms
Machine learning-based anomaly detection
Real-time validation systems
Core Components of Data Verification
Key components include:
Data Cleansing: Removes errors and inconsistencies
Data Standardization: Aligns data formats for uniformity
Integrity Checks: Ensures consistency across systems
Data Enrichment: Adds value with contextual information
Compliance and Governance: Adheres to legal standards
Address and Contact Verification: Confirms communication accuracy
Real-Time Verification: Validates data instantly
Auditing and Monitoring: Tracks ongoing data health
How Data Verification Enhances Trustworthiness
Ensure data is complete, consistent, and up-to-date, verification services boost confidence in insights derived from it—resulting in better, faster, and risk-aware decisions.
For businesses aiming to improve operational accuracy and strategic decisions, investing in data verification is not optional—it’s essential.
Read More: https://www.damcogroup.com/blogs/role-of-data-verification-in-strengthening-data-trustworthiness
0 notes
Text
Data verification services play a crucial role in the healthcare industry, ensuring the accuracy and reliability of patient information. By minimizing errors and enhancing decision-making, these services support better patient care and operational efficiency. Organizations benefit from secure, validated data to maintain compliance and trust. Discover how verified data can transform healthcare operations for improved outcomes.
0 notes
Text
Weekly output: Mark Vena podcast, Verizon customer service, AI fair use, Comcast ditches data caps, Aurora's autonomous trucks, age verification for porn sites, Universal Service Fund, Trump tariffs
View On WordPress
#age verification#AI training#Anthropic#Aurora#autonomous trucks#autonomous vehicles#Comcast#Comcast data caps#copyright#data caps#Electronics Home Mexico#First Amendment#LLMs#Mark Vena#podcast#Supreme Court#tariffs#Universal Service Fund#USF#Verizon customer service#Verizon support#Vz#Xfinity
0 notes
Text
Why Forensic Investigation is Becoming Essential for Corporate Fraud Detection

As businesses have become more fast-paced in today's world of digital technology, fraud is today more present than ever before, and the situation is still deteriorating. It is an unpleasant reality that quietly entered the boardrooms, financial departments, and vendor relations among different sectors. Among the many different kinds of fraud are the ones originating from proving the need for new working space or the handling of customers' finances wrongly. However, companies regardless of their size are facing the threat of theft from their employees, financial manipulation as well as the access to their data as a result of the growth of the company. The present times present forensic investigation as a tool not just a thought which is to fight off corporate fraud and that too in a critical manner.
Now let's look at the reasons that make forensic investigation (https://www.forensicexpertsindia.com/cyber-forensics-investigation.html) the main tool for detecting and privatizing fraud in the modern business environment.
The Overview of Corporate Fraud in Today's World of Business
Emerging Crimes amongst Professionals
Corporate fraud does not only happen in prominent cases, but it is also part of the daily business operations — examples include compromised invoices, leaks of inside information, cooked-up ledgers, fictitious employees, etc. According to The Association of Certified Fraud Examiners (ACFE), 5% of the annual revenue of companies is what's lost to the fraud cases they suffer. and that is the extent of their global business transactions. This is a topic that you can write a subsequent textbook about, trust me.
White-collar criminals are sophisticated. Often, people who commit such crimes are a step ahead of consensus, even before the external audit happens, which makes their task a little less burdensome; those who cover their tracks using a forensic investigation have a different story altogether.
Why Traditional Audits Are No Longer Enough
While agencies of oversight regard periodic auditing as a key tool, it is not really designed to detect fraud. Auditors work based on what is visible, structured, and disclosed. And fraudsters are extremely brilliant in hiding behind falsified transactions and appearance of legitimate paperwork.
Herein lies the limitation of traditional auditing processes. A forensic investigator, on the other hand, looks for red flags, manipulations, and linking evidence. So, it is more of an investigation than just a review, which is why it is so pertinent in the fight against complex frauds.
What Is Forensic Investigation And How It Works
Definition and Scope
Forensic investigation refers to applying a structured approach to analyses and collects financial, digital, or physical evidence for presentation before a court or an internal disciplinary body. It combines investigative skills with an understanding of accounting, technology, and law.
In complex fraud incidents within the corporate environs, forensic investigators are called upon to detect irregular financial activities, identify fraudulent transactions, analyze employee conduct, and compile a strong case backed by evidence and digital forensics.
Key Tools and Techniques
In forensic investigations today, technological interventions are used. The experts use these instruments for:
In-depth data analysis across databases and accounting software.
Recovering deleted or hidden files.
Tracking email communication and metadata.
Cross-checking vendor records and payment trails.
Blockchain analysis in case of cryptocurrency-related fraud.
Such a technical complement with human intervention makes forensic services way more effective in unearthing fraud than the traditional reviews.
Why Forensic Investigation Is Crucial in Corporate Fraud Detection
Early Fraud Detection and Risk Mitigation
The earlier fraud occurs, the less damage to take action immediately. Forensic investigators do not only find evidence after a crime-but help uncover suspicious patterns before it becomes irreparable.
Like during a vendor payments review, the forensic team might notice the unusual invoicing during payments made to unfamiliar entities. Quick intervention at this stage can save huge financial loss and damage to reputation.
Strengthening Legal Actions & Regulatory Compliance
Once companies detect fraud, the next hurdle is proving it legally. Forensic investigators gather evidence that is concrete and admissible in court. They then prepare forensic reports, present expert testimony, and validate that all their findings comply with local laws and global standards.
In India, where compliance with authorities such as SEBI or the Ministry of Corporate Affairs is of utmost importance, forensic backup can mean the difference between a verdict and a dismissal.
Protecting Reputation and Investor Confidence
Today's stakeholders demand transparency. Companies that carry out a thorough forensic investigation once fraud is identified and then take remedial measures stand a far better chance of maintaining credibility. Investors, partners, and clients appreciate organizations that seek an ethical path to recovery rather than engaging in cover-ups.
In this sense, a Forensic Investigation Services in India becomes a real instrument for trust building-the message being that the company is serious about accountability.
Use Cases and Real-World Examples
Forensic Investigation in Employee Fraud
One Indian manufacturing firm had found its payroll system tainted with discrepancies. The forensic audit revealed ghost employees, manipulated time logs, and fake reimbursement claims with one senior HR executive involved. Thus, after intervention of the investigation, the fraud was contained, legal proceedings were taken, and internal controls were strengthened.
Vendor and Supply Chain Fraud Detection
In one case, a multinational company kept on getting overbilled in installments from its vendor. The forensic investigators uncovered a chain of shell companies and routed through legitimate channels the inflated invoices. These payments were stopped before they could prevent a fraud of multi billion rupees.
These real-world instances demonstrate how forensic services bring to light those frauds which escape regular checks.
Choosing the Right Forensic Investigation Partner
Key Qualities to Look For
It is not every investigation service that is equal to others. What distinguishes a forensic team are:
Demonstrable experience in both financial and digital investigations
The best tools and methodologies of the trade
An extensive knowledge of the legal aspects, including presentation and documentation
And, must maintain absolute confidentiality on all sensitive data
Experience across industries such as finance, IT, retail, and real estate
Questions to Ask Before Hiring
Some questions you need to consider asking to be sure:
What kind of frauds did you conduct investigations into?
Are your skirmishes legally admissible?
How long does a normal investigation take?
What is your procedure when it comes to finding and documenting?
Choosing wisely means you are not getting just an investigator but a strategic partner within your fraud-prevention framework.
Conclusion
Corporate fraud is not just about money losses—it is integrity, trust, and long-term sustainability. They become more sophisticated by day and so must the tools of detection.
Forensic investigation can no longer be seen as some kind of optional service—it is the henceforth. It equips companies to identify bunkers at an early stage, creates solid cases and confidently safeguards their reputation. Whether you are an executive, a compliance officer, or an investor, this is the time to start valuing forensic assistance rather than be a victim of it.
Seeking Expert Help? Select a choice from the best forensic investigation teams to safeguard your company for good.
#Forensic Investigation#Handwriting Signature Verification#Forensic Investigation Services in India#Cyber Forensic Data recovery#fire/arson investigation#cyber forensic investigation
0 notes
Text
Unleashing Efficiency: The Rise of Industrial Automation Software Solutions
In the age of digital transformation, industrial sectors across the globe are undergoing a fundamental shift. One of the most significant developments driving this evolution is the rise of Industrial Automation Software Solutions. These intelligent systems are redefining how industries operate, streamline processes, and respond to real-time data — all while reducing human error and maximizing productivity.
Industrial automation is no longer just a competitive advantage; it’s quickly becoming a necessity for modern manufacturing, logistics, energy, and production-based businesses. At the core of this transformation lies powerful software designed to integrate machinery, manage workflows, and monitor operations with precision and efficiency.
One of the key strengths of Industrial Automation Software Solutions is their ability to centralize control over complex industrial processes. From programmable logic controllers (PLCs) to supervisory control and data acquisition (SCADA) systems, this software enables seamless communication between machines, sensors, and operators. The result is a smarter, more connected operation that can adapt quickly to changing demands.
Beyond basic automation, these solutions offer deep analytics capabilities. Using machine learning and AI, the software can detect patterns, predict equipment failures, and recommend proactive maintenance — ultimately helping businesses avoid costly downtime. This predictive approach not only increases reliability but also extends the lifespan of expensive equipment.
Flexibility is another crucial advantage. Most modern Industrial Automation Software Solutions are highly customizable and scalable, allowing companies to tailor systems to their unique needs and expand functionality as they grow. Whether an organization is automating a single production line or an entire facility, the right software can be scaled appropriately without significant disruptions.
In today’s globalized economy, remote access and cloud integration are more important than ever. Many automation platforms now offer web-based dashboards and mobile apps, giving managers and technicians the ability to monitor and control systems from virtually anywhere. This level of accessibility promotes faster response times and better decision-making, even across multiple locations.
Security, too, has become a top priority. As more industrial systems connect to the internet, they become more vulnerable to cyber threats. Industrial Automation Software Solutions are now being developed with robust cybersecurity features, including encrypted communication, multi-layered access control, and real-time threat monitoring.
These solutions also play a key role in sustainability efforts. By optimizing energy usage, reducing waste, and ensuring consistent product quality, industrial automation supports greener operations. Businesses not only improve efficiency but also meet environmental standards more effectively.
As industries continue to adopt smart technologies and prepare for Industry 4.0, the demand for reliable and intelligent automation software is set to grow exponentially. Investing in Industrial Automation Software Solutions is no longer just about keeping up with competitors — it's about laying the foundation for a resilient, future-ready operation.
Whether it's enhancing productivity, improving safety, or driving innovation, automation software is reshaping what’s possible in the industrial world. The future of manufacturing and production isn’t just automated — it’s intelligent, adaptive, and incredibly powerful.

#Traceability Software Great Lakes Region#Machine Vision Integration Great Lakes#Great Lakes Industrial Marking Solutions#Factory Monitoring Software Great Lakes Region#Lean Manufacturing Solutions Great Lakes#Automated Data Collection Systems Great Lakes#Industrial Traceability Solutions Detroit#Machine Vision Systems Detroit#Detroit Barcode Verification Services#Laser Marking Services Detroit MI#Production Management Software Detroit#Detroit Manufacturing Systems#product traceability software Detroit#industrial marking systems Detroit#Laser Marking Services Auburn Hills#Industrial Traceability Solutions Michigan#Barcode Verification Systems Auburn Hills#Machine Vision Systems Michigan#Auburn Hills Laser Part Marking#Industrial Marking Solutions Michigan#Traceability Software Auburn Hills#Turnkey Laser Systems Michigan#Auburn Hills Barcode Reader Solutions#Advanced Laser Marking Auburn Hills MI#laser marking systems#laser marking machine#laser part marking#uv laser marking machine#uv laser marking#dot peen marking machine
0 notes
Text
Tyler Technologies: Payment Service, Credit Card Charge Inquiry
Have you Inquire about a payment service charge from your credit or debit card statement. Manage payments and accept various card types using our technology. Noticed a mysterious charge from Tyler Technologies on your credit card statement? Don’t worry—you’re not alone. Many people spot this name and wonder what it’s for. This guide breaks down what Tyler Technologies is, why they might appear on…
#agency payments#agency verification#automated billing#billing management#consumer protection#court fines#court systems#credit card charge#customer service#data analytics#data protection#digital payments#dispute charges#electronic payments#financial alerts#financial institution#financial security#fraud prevention#fraud reporting#government fees#government services#identity theft#licenses#mobile payments#online payments#payment confirmations#payment disputes#payment methods#payment platform#payment portals
1 note
·
View note
Text

Melissa's Data Quality and Identity Verification solutions fights dirty data in your Salesforce®, Microsoft Dynamics CRM®, or Oracle CRM and ERP and other customer applications and platforms by verifying, standardizing, correcting and appending your customer contact data records. The result - clean, vibrant, valuable data you can use for squeaky clean omnichannel marketing and sales success. • Autocomplete, verify and correct contacts before they enter the CRM • Add valuable demographic and geographic (lat/long coordinates) information for effective targeting and segmentation • Keep contacts clean and up-to-date with change of address processing to improve student communications • Verify identity with name to address validation, biometrics and document scanning for fast, accurate onboarding
0 notes
Text
Data Management Services at Infosearch
Infosearch BPO provides outstanding data services including Data Processing, Data Mining, Data Cleansing, Data Verification & Extraction, Data Conversion and Data Analysis.
Visit the page for more information and contact us to outsource your data management services. https://www.infosearchbpo.com/data-management-india.php enquiries(@)infosearchbpo(.)com
#data services#data management#data processing#data mining#data cleansing#data verification#data extraction#data conversion#data analysis
0 notes
Text
Ensure Accuracy With Effective Customer Data Verification Solutions
Ensure trust and security in your online interactions with our tailored customer data verification solutions. Safeguard sensitive information and enhance user confidence in your business. Our user-friendly verification process adds an extra layer of protection, making your digital experiences seamless and secure. Protect what matters most – your customers and their data.

0 notes
Text
BAD CALIFORNIAN INTERNET BILLS
While it is good that KOSA is now dead in the House (for now) I would like to ask for people's attention on AB1949 and SB976, which could push for Age verification by showing your ID.
There was a third bill named AB3080 that had similar goals, but luckily it received revisions so it is no longer a threat or require ID verification to access websites. So it would be possible to get AB1949 and SB976 to be revised so they aren't dangerous anymore.
You can read the text for AB1949 right here
AB1949 doesn't explicitly ask for ID verification anymore, as it used to, due to a revision, but there is a provision stating if they deem a website "willfully disregards" the age of the user they will be deemed to have actual knowledge of the user's age.
This broad part could be left to abuse, which is why it needs to be revised before passing, in order to confirm ID verification is not required. FIND YOUR REPS HERE!
For AB1949, you can find your Senate representative with the link above as I said, and check to see if they're a member of the CA Senate Appropriations Committee. Then call them to tell them you oppose this bill. Try to add reasons you think this bill would negatively affect California financially because that's what this committee focuses on.
As for SB976, which you can read here
Its goal is to "keep kids off social medias and addictive feeds" But the concerning part is that "it would make it unlawful for the operator of an addictive internet-based service or application, as defined, to provide an addictive feed to a user, unless the operator does not have actual knowledge that the user is a minor; commencing January 1, 2027, has reasonably determined that the user is not a minor; or has obtained verifiable parental consent to provide an addictive feed to the user who is a minor."
How are you supposed to know that you have "verifiable parental consent" without ID and age verification of both parents and child?Even then, holding the ID of a minor feels pretty illegal given how sensitive how an info this is, in case of a data breach (which will happen) this would endanger kids even more, and no one in general want to give their ID to access a website or an app.
The bill would also make it unlawful for a website or app to send notifications to a minor according to a certain timeframe.
For SB976, find your Assembly representative using the link below and check to see if they're a member of the CA Assembly Appropriations Committee. Then call them to tell them you oppose this bill. https://apro.assembly.ca.gov/members
You can tell them how this is terrible for privacy, and the safety of children, and that it would be terrible for the economy of California, as they seem to focus on it. You can try sending faxes for either bills, but calling IS MUCH MORE efficient. https://faxzero.com/
Here is the time schedule, bills must be taken care before the end of August so it is a matter of time crunch:

You may use the following scripts for the respective bills, you can try to trim it if you deem it too long!

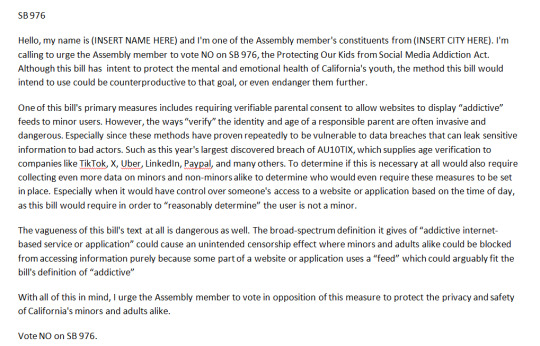
Might be worth a shot to contact Gavin Newsom (Californian governor) here to voice your concerns for these bills
345 notes
·
View notes
Text
WASHINGTON (AP) — The acting commissioner of the Internal Revenue Service is resigning over a deal to share immigrants’ tax data with Immigration and Customs Enforcement for the purpose of identifying and deporting people illegally in the U.S., according to two people familiar with the decision.
Melanie Krause, who had served as acting head since February, will step down over the new data-sharing document signed Monday by Treasury Secretary Scott Bessent and Homeland Security Secretary Kristi Noem. The agreement will allow ICE to submit names and addresses of immigrants inside the U.S. illegally to the IRS for cross-verification against tax records.
Two people familiar with the situation confirmed Krause was resigning and spoke to The Associated Press on condition of anonymity because they were not authorized to discuss it publicly.
63 notes
·
View notes
Text
Data Verification Company | Data Validation Services | Damco Solutions
Ensuring data accuracy is crucial for businesses aiming to make informed decisions, reduce operational risks, and maintain customer trust. This service page offers a complete overview of Damco Solutions' data verification and validation services—designed to help organizations maintain data integrity across multiple channels.

Improved Decision Making Through Reliable and Cost-Effective Data Verification and Validation Services
Accurate and validated data leads to more confident decision-making and streamlined business processes. Damco’s services support businesses in verifying customer information, eliminating inconsistencies, and enhancing database reliability without straining internal resources.
Service Offerings
Damco delivers a wide range of specialized data validation services tailored to meet industry-specific needs:
Outsource Data Validation Services: Manual and automated checks to identify and fix data errors
Geo-Location Address Verification Services: Verifies physical address accuracy against official sources
Phone Verification Services: Validates mobile and landline numbers for active use
Email Address Validation Services: Ensures email addresses are accurate and deliverable
OCR Data Validation Services: Validates data extracted from scanned images and documents
Social Profile Verification: Confirms user identity by verifying social presence and credentials
Why Damco for Data Verification Services?
With years of experience and a global delivery model, Damco stands out as a trusted partner for scalable and secure data validation solutions.
Key benefits include:
High-quality, accurate data verification
Fast turnaround times for time-sensitive projects
Flexible, cost-effective pricing models
Scalable operations that grow with your business
Custom solutions aligned with your industry
Global delivery presence with local expertise
Share Your Project Requirements with Us!
Ensure data accuracy and reduce risks. Let Damco Solutions handle your data validation needs with confidence and efficiency.
Get in Touch: https://www.damcogroup.com/data-verification-and-validation-services
0 notes
Text
Tired of navigating data chaos? Embrace the potential of verification services to streamline processes, reduce errors, and save both time and money. These services ensure accurate data, enabling businesses to make informed decisions with confidence. Whether it's compliance or operational efficiency, verified data lays the foundation for success. Explore how this solution transforms data management today!
0 notes
Text
Update on AB 3080 and AB 1949
AB 3080 (age verification for adult websites and online purchase of products and services not allowed for minors) and AB 1949 (prohibiting data collection on individuals less than 18 years of age) both officially have hearing dates for the California Senate Judiciary Committee.
The hearing date for these bills is scheduled to be Tuesday 07/02/2024. Which means that the deadline to turn in position letters is going to be noon one week before the hearing on 06/25/2024. It's not a lot of time from this moment, but I'm certain we can each turn one in before then
Remember that position letters should be single topic, in strict opposition of what each bill entails. Keep on topic and professional when writing them. Let us all do our best to keep these bills from leaving committee so that we don't have to fight them on the Senate floor. But let's also not stop sending correspondence to our state representatives anyway.
Remember, the jurisdiction of the Senate Judiciary Committee is as follows.
"Bills amending the Civil Code, Code of Civil Procedure, Evidence Code, Family Code, and Probate Code. Bills relating to courts, judges, and court personnel. Bills relating to liens, claims, and unclaimed property. Bills relating to privacy and consumer protection."
Best of luck everyone. And thank you for your efforts to fight this so far.
Below is linked the latest versions of the bills.
Below are the links to the Committee's homepage which gives further information about the Judiciary Committee, and the page explaining further in depth their letter policy.
Edit: Was requested to add in information such as why these bills are bad and what sites could potentially be affected by these bills. So here's the explanation I gave in asks.
Why are these bills bad?
Both bills are essentially age verification requirement laws. AB 3080 explicitly, and AB 1949 implicitly.
AB 3080 strictly is calling for dangerous age verification requirements for both adult websites and any website which sells products or services which it is illegal for minors to access in California. While this may sound like a good idea on paper, it's important to keep in mind that any information that's put online is at risk of being extracted and used by bad actors like hackers. Even if there are additional requirements by the law that data be deleted after its used for its intended purpose and that it not be used to trace what websites people access. The former of which provides very little protection from people who could access the databases of identification that are used for verification, and the latter which is frankly impossible to completely enforce and could at any time reasonably be used by the government or any surveying entity to see what private citizens have been looking at since their ID would be linked to the access and not anonymized.
AB 1949 is nominally to protect children from having their data collected and sold without permission on websites. However by restricting this with an age limit it opens up similar issues wherein it could cause default requirements for age verification for any website so that they can avoid liability by users and the state.
What websites could they affect?
AB 3080, according to the bill's text, would affect websites which sells the types of items listed below
"
(b) Products or services that are illegal to sell to a minor under state law that are subject to subdivision (a) include all of the following:
(1) An aerosol container of paint that is capable of defacing property, as referenced in Section 594.1 of the Penal Code.
(2) Etching cream that is capable of defacing property, as referenced in Section 594.1 of the Penal Code.
(3) Dangerous fireworks, as referenced in Sections 12505 and 12689 of the Health and Safety Code.
(4) Tanning in an ultraviolet tanning device, as referenced in Sections 22702 and 22706 of the Business and Professions Code.
(5) Dietary supplement products containing ephedrine group alkaloids, as referenced in Section 110423.2 of the Health and Safety Code.
(6) Body branding, as referenced in Sections 119301 and 119302 of the Health and Safety Code.
(c) Products or services that are illegal to sell to a minor under state law that are subject to subdivision (a) include all of the following:
(1) Firearms or handguns, as referenced in Sections 16520, 16640, and 27505 of the Penal Code.
(2) A BB device, as referenced in Sections 16250 and 19910 of the Penal Code.
(3) Ammunition or reloaded ammunition, as referenced in Sections 16150 and 30300 of the Penal Code.
(4) Any tobacco, cigarette, cigarette papers, blunt wraps, any other preparation of tobacco, any other instrument or paraphernalia that is designed for the smoking or ingestion of tobacco, products prepared from tobacco, or any controlled substance, as referenced in Division 8.5 (commencing with Section 22950) of the Business and Professions Code, and Sections 308, 308.1, 308.2, and 308.3 of the Penal Code.
(5) Electronic cigarettes, as referenced in Section 119406 of the Health and Safety Code.
(6) A less lethal weapon, as referenced in Sections 16780 and 19405 of the Penal Code."
This is stated explicitly to include "internet website on which the owner of the internet website, for commercial gain, knowingly publishes sexually explicit content that, on an annual basis, exceeds one-third of the contents published on the internet website". Wherein "sexually explicit content" is defined as "visual imagery of an individual or individuals engaging in an act of masturbation, sexual intercourse, oral copulation, or other overtly sexual conduct that, taken as a whole, lacks serious literary, artistic, political, or scientific value."
This would likely not include websites like AO3 or any website which displays NSFW content not in excess of 1/3 of the content on the site. Possibly not inclusive of writing because of the "visual imagery", but don't know at this time. In any case we don't want to set a precedent off of which it could springboard into non-commercial websites or any and all places with NSFW content.
AB 1949 is a lot more broad because it's about general data collection by any and all websites in which they might sell personal data collected by the website to third parties, especially if aimed specifically at minors or has a high chance of minors commonly accesses the site. But with how broad the language is I can't say there would be ANY limits to this one. So both are equally bad and would require equal attention in my opinion.
#california#kosa#ab 3080#ab 1949#age verification#internet safety#online privacy#online safety#bad internet bills
192 notes
·
View notes
Text
As the Online Safety Act comes into effect in the UK, impacting websites where sex workers advertise our services, we find ourselves on the cusp of a nation-wide censorship effort that will push sex workers towards third party managers and brothel or street work. Requirements for age verification of viewers (for everything from nudity to written sexual fantasies) puts platforms in a position where they must work out a way to store extremely sensitive personal data of their users at a significant financial cost. Since clients are unsurprisingly reticent to verify their identity with escorting sites, particularly in a country where efforts are being made by certain MPs to criminalize the purchase of sex, this restricts sex workers’ ability to reach clients online.
An article about the impact of the Online Safety Act on sex workers in the UK, including the changes that are about to go into effect to censor escort advertising websites!
35 notes
·
View notes
Text
Maximize Efficiency with Track-Pac Traceability Solution
Stay ahead in production with customizable tools built for precision. Discover how Track-Pac Traceability Solution can help!
#advanced laser marking auburn hills mi#auburn hills laser part marking#automated data collection systems great lakes#detroit barcode verification services#Track-Pac Traceability Solution
0 notes