#ISO digital integration
Explore tagged Tumblr posts
Text
🔄 Process Approach Across ISO & IATF Standards with 🚗 OEM Requirements in 2025
✅ Introduction: Why the Process Approach Matters in 2025 The process approach isn’t just a buzzword from ISO standards—it’s the engine behind operational excellence. As we step into 2025, OEMs (Original Equipment Manufacturers) demand more than compliance—they expect traceability, zero-defect culture, and real-time performance. In this guide, you’ll learn: 📌 How the process approach is defined…

View On WordPress
#5W2H model ISO#Automotive manufacturing#automotive quality system#clause 4.4 explained#EHS process compliance#energy management ISO 50001#environmental compliance ISO 14001#IATF 16949 process control#ISO digital integration#ISO standards 2025#lean manufacturing#occupational health ISO 45001#OEM compliance 2025#PFMEA process improvement#process approach ISO#process mapping ISO 9001#process ownership in QMS#quality management ISO 9001#risk-based thinking ISO#SIPOC diagram example#smart factory process control#Turtle diagram QMS
0 notes
Text
Yvette Heiser - Teaches Photography Basics in Texas
Photography, an art form that captures moments in time and tells stories through imagery, is accessible to everyone willing to learn. Yvette Heiser, a renowned photographer based in Texas, has made it her mission to help budding photographers master the fundamentals of this beautiful craft. With her extensive experience and passion for teaching, Yvette offers insightful guidance on how to transform a simple photograph into a captivating piece of art. Here’s an in-depth look at what Yvette Heiser– Learn the fundamentals of photography with Yvette Heiser, Texas and classes entail and the strategies she employs to help her students excel.

The Basics of Photography with Yvette Heiser
Understanding the Camera
The journey into photography begins with understanding the camera, the primary tool of the trade. Yvette Heiser’s classes start with a comprehensive overview of different types of cameras, including DSLRs, mirror less cameras, and even smartphones. She explains the fundamental components such as the lens, sensor, viewfinder, and memory card, ensuring that her students are well-versed in the basic anatomy of their equipment.
Mastering Camera Settings
One of the key aspects of Yvette’s teaching is demystifying camera settings. She breaks down the exposure triangle—aperture, shutter speed, and ISO—highlighting how these elements interact to create a perfectly exposed photograph. Students learn how to adjust these settings based on different lighting conditions and desired effects, such as depth of field and motion blur.
Composition and Framing
Rule of Thirds
Yvette emphasizes the importance of composition in photography. One of the first rules she teaches is the rule of thirds, a fundamental principle that helps create balanced and engaging images. By dividing the frame into nine equal parts, students learn to position their subject along these lines or at their intersections, resulting in a more dynamic and aesthetically pleasing composition.
Leading Lines and Symmetry
Yvette also explores advanced composition techniques such as leading lines and symmetry. Leading lines draw the viewer’s eye towards the main subject, creating a sense of depth and guiding the viewer through the image. Symmetry, on the other hand, introduces balance and harmony, making the photograph more visually appealing. Through practical exercises, students develop an eye for these elements and learn to incorporate them into their work.
Lighting Techniques
Natural Light
Lighting is a crucial element in photography, and Yvette Heiser’s classes cover the basics of working with natural light. Students learn to observe and utilize different qualities of natural light, from the soft, diffused light of a cloudy day to the harsh shadows of midday sun. Yvette teaches techniques for shooting during the golden hour and blue hour, times when natural light is most flattering and dramatic.
Artificial Light and Flash Photography
In addition to natural light, Yvette introduces her students to artificial lighting techniques. She covers the basics of flash photography, including on-camera and off-camera flash, and how to use reflectors and diffusers to control and modify light. These lessons equip students with the skills to handle various lighting situations, both indoors and outdoors.
In the digital age, smartphones have revolutionized the way we capture and share moments. With their advanced cameras and user-friendly features, smartphones have become powerful tools for photography, accessible to everyone and Yvette Heiser Texas: A Complete Guide to Mastering Phone Photography from Texas has made it her mission to help individuals unlock the full potential of their smartphone cameras.
Basic Editing Techniques
Post-processing is an integral part of modern photography, and Yvette Heiser ensures her students are proficient in basic editing techniques. Using software like Adobe Light room and Photoshop, students learn how to adjust exposure, contrast, colour balance, and sharpness to enhance their images. Yvette emphasizes the importance of maintaining a natural look while correcting minor flaws and bringing out the best in each photograph.
Creative Editing and Filters
Beyond basic adjustments, Yvette encourages her students to explore creative editing. She introduces concepts such as black-and-white conversions, selective color, and the use of filters to create unique and artistic effects. By experimenting with different techniques, students discover their own style and develop a personal artistic vision.
Practice and Patience
Yvette Heiser believes that practice and patience are key to mastering photography. She advises her students to take their cameras everywhere and practice shooting in different conditions and environments. This hands-on experience helps them understand their equipment better and develop a keen eye for composition and lighting. Yvette reminds her students that photography is an art that requires time and dedication, and progress often comes through trial and error.
Continuous Learning and Inspiration
Another strategy Yvette advocates is continuous learning and seeking inspiration. She encourages her students to study the work of famous photographers and understand the techniques they use. Attending workshops, reading books on photography, and participating in online communities can provide new perspectives and ideas. Yvette also suggests keeping a photography journal to document progress and reflect on what works and what doesn’t. This continuous learning process helps photographers stay inspired and motivated to improve their craft.
In addition to traditional camera techniques, Yvette Heiser also offers insights into mastering phone photography. With the advancements in smartphone camera technology, learning to take stunning photos with your phone has become more accessible than ever. Yvette’s guide to phone photography covers essential tips and tricks for capturing high-quality images, utilizing the various features and settings available on smartphones
Conclusion
Yvette Heiser’s dedication to teaching photography basics in Texas has helped countless students develop their skills and passion for this art form. Through her comprehensive classes and practical strategies, she empowers aspiring photographers to capture the world around them with creativity and confidence. Whether you’re using a professional camera or your smartphone, Yvette’s guidance ensures that you can create beautiful, impactful images that tell a story.
#camera#photographer#wedding#moments#photography#yvette heiser#pictures#childphotography#photographytips#events
7 notes
·
View notes
Text
Tutorial De Instalação Do The Sims 2 No Linux
Oi Pessoal! Tudo Bem?… Hoje Iremos Instalar o The Sims 2 No Nosso Linux! Mais Antes De Tudo Gostaria de Deixar Uns Avisos…
Instale o Linux Se Por Acaso Deseje Sair Do Windows Aqui Está Um Video Passo A Passo
Para Instalar o linux Em Qualquer Pc: Clique Aqui Para Assitir
2: Atualize Seus Drivers.. Se Por Acaso Você Não Saiba Instalar/Atualizar Os Drivers No Linux Vou Deixar Aqui 3 Vídeos Para Vocês… Só Clicar Se Caso Sua Placa De Video For:
NVIDIA
AMD / DEDICADA OU INTEGRADA
INTEL / DEDICADA OU INTEGRADA
Atualizando Seus Drivers Vamos Começar O Passo a Passo Completo
1: Requisitos Para Começar..
Antes De Começarmos Instale Esses Seguintes Programas:
Wine
Lutris
Winetricks
Qbittorent
Todos Esses Programas Podem Ser Encontrados a Loja de Apps Da Sua Distro Linux..
No Caso A Do Linux Mint (distro que uso) o Nome Dela È Gerenciador De Aplicativos
Caso Use Outra Distro No Exemplo: ZORIN OS O Nome Da Loja è Software….
Instalando Tudo Vamos Ao Próximo Passo…………….
2: Instalando O Mono..
Para instalar o mono: Clique nesse link
Selecione A distribuição Onde Seu Sistema È Baseado Exemplos:
Linux Mint: Ubuntu
ZORIN OS: Ubuntu
q4OS: Debian
Debian: Debian
Ubuntu: Debian
Selecionando Abra O Terminal E Cole Os Comando Um Por Um ….
Terminou? Vamos Ao Próximo Passo
3: Instalando O The Sims 2
Acesse Um Desses Sites e Instale o Game Via Qbittorent:
KNYSIMS
SIMSTARAC
REDDIT (recomendo Muito)
Terminando De Instalar Caso Tenha Instalado Pelo Simtarac:
Extaria A Iso Usando O Power Iso (Instale Na loja De Apps Da Sua Distro)
Terminado Tudo.. Agora Sim Vamos Ao Proximo Passo:
4: Configurando o Prefixo Com o Wine
Para Fazermos Um Prefixo.. Faça Uma Pasta No Seu Diretorio Home Do Gerenciador de Arquivos
Recomendo Criar Uma Pasta Com o Nome Pequeno Como Essa:

Pasta Criada Agora Feche o Gerenciador De Arquivos e Abra o Terminal
Ele Está Localizado No Menu Iniciar Da Sua Distro (Caso Não Saiba, Pressione a tecla Windows Do Seu Teclado)
Com Seu Terminal Aberto Digite Ou Copie E cole Esse Comando:
WINEPREFIX=~/pasta que você criou winecfg
Dê enter E espere….
Abrindo A Janela Do Wine Coloque Essas Configurações:
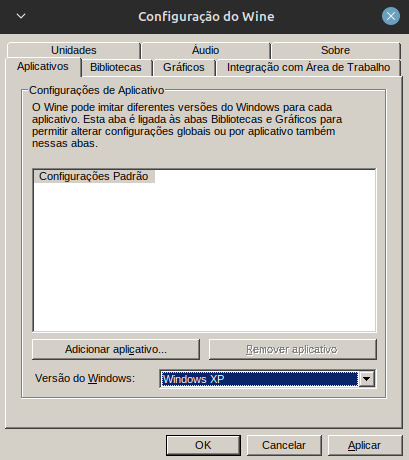
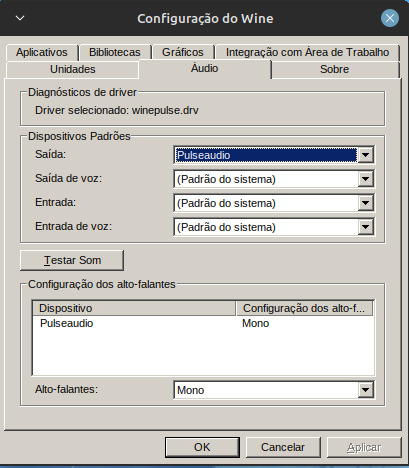
Aplique Tudo E Clique Em Ok.
Com O Terminal Ainda Aberto Digite Ou Copie esse Comando
WINEPREFIX=~/pasta que Você Criou winetricks
Abrindo A Janela Clique em Select the Default Prefix
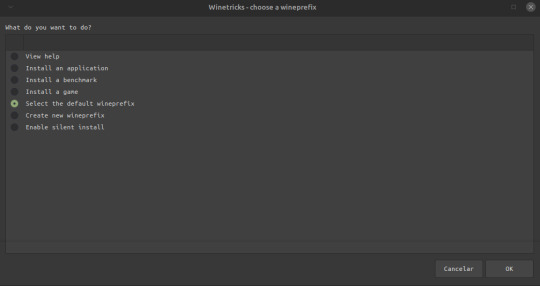
Install a windows DLL or Component
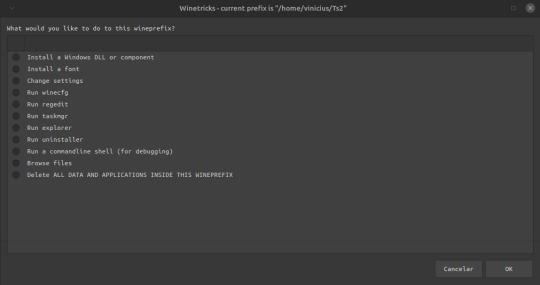
Selecione o vcrun6sp6 e o vcrun6 e clique em ok pra instalar, Terminado De Instalar Feche a janela…
5 Instalando o Jogo
Abra o Lutris… Lutris Aberto Clique em +
Adicionar Jogo Instalado Manualmente:
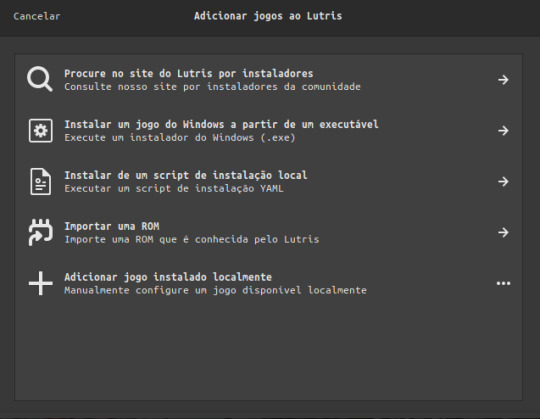
E Coloque Essas Configurações:
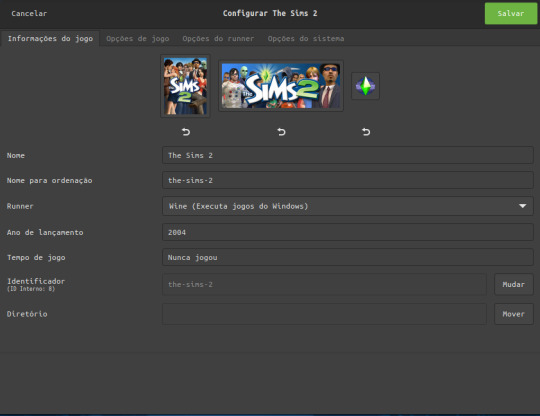
Em Runner Coloque O Wine Para Rodar o Executável de instalação do The sims 2..
Em Opções de jogo:
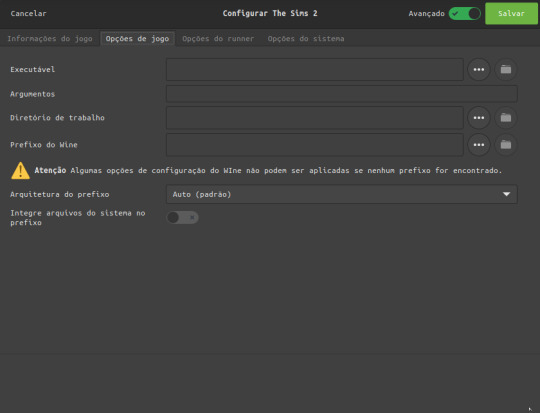
Clique Nos Tres Pontinhos para Selecionar Onde você fez o Download O Torrent Do The Sims 2
(caso você instalou pelo simstarac é a onde você extraiu a iso)
em prefixo wine é a mesma coisa só que iremos escolher a pasta onde criamos nosso prefixo no Diretorio Home
E marque a opção integre arquivos do sistema Ela é Crucial Para Instalar Os Mods
Em Opçoes Do runner:
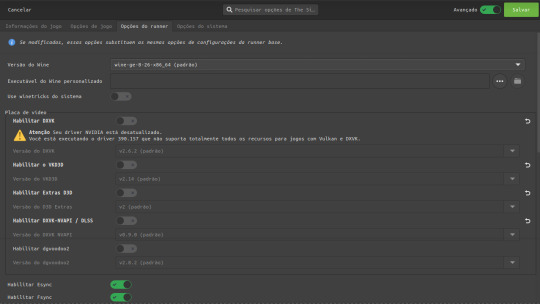
Deixe a versão do wine padrão
Desabilite o dxvk, vkd3d, extras d3d, dxvk nvapi e o dgvoodoo
E deixe Somente Habilitado O Esync e o Fsync
Descendo a Pagina Em Driver De Audio Coloque alsa, e
Ative a opção de mostrar caixas de dialogo de falha..
LEMBRANDO QUE PARA ESSAS CONFIGURAÇÕES ACONTECER TEM QUE ATIVAR AS OPÇÕES AVANÇADAS!
Terminando Tudo Clique Em Salvar E Clique em Jogar e instale o jogo…….
(pode demorar dependendo do pc)
Jogo Instalado Agora Iremos Configura-lo
Como Por Padrão no Linux O The Sims 2 Dá Erro Por Conta Do Wine Que o Lutris Usa Dando Esse Erro:
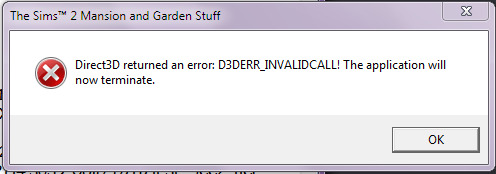
Vamos Prevenir Isso!
Acesse Esse Link: Clique Aqui
Após Ter Baixado o Arquivo Entre no Diretório Home do Gerenciador De Arquivos Da Sua Distro..
Entrando Lá Pressione as Teclas CTRL + H Após Isso Você Pode Ver Varias Pastar Começando Com Ponto “.” Localize A pasta .var Entrando Nela Faça Esse Caminho:
.var/app/net.lutris.Lutris/data/lutris/runners/wine/ E cole A pasta Que Você baixou Com O Link que Disponibilizei… Após Colocar A Pasta Renomeie Para: sims2 Após Isso Feche O gerenciador de Arquivos E Abra O Lutris Clique Com o Botão Direito No The Sims 2 E Clique Em Configurar, Após Abrir A Janela, Clique em Opçoes de Jogo, e mude o Executavel do jogo, Localizado no seu prefixo Após Isso Mude A Versão Do Wine Que Você colocou Lá Na Pasta Do Lutris… Após Isso Rode O jogo… A Seguir Os Passos Listados São Para pessoas Que Tem Placa De video Com O driver Mais Atualizado Caso Não Tenha, Pule Para O Passo Da Tradução Se você Instalou O Jogo
Pelo SimsTarac Ou Pelo Knysims..
6: DXVk (somente Placas De Video Avançada)
No Lutris Clicando Com o Botão Direito Do Mouse No The Sims 2 E indo Em Configurações Vá Em Opçoes Do runner Habilite As Seguintes Opçoes
Mude A Versão Do Wine Para A Padrao e Habilite O
DXVK
VKD3
EXTRAS D3D
DXVK-NVAPI (placas De Video Nvidia)
Dgvooodo
(lembrando que se você tiver Vulkan na sua placa de vídeo não será necessário rodar esse patch que coloquei pra download)
Como Na Imagem:

Salve E Rode O Jogo
7 Traduzindo o Jogo (SOMENTE VERSÃO MR DJ)
No Lutris Ao Lado Do Jogar Clique Na Taça De Vinho E Clique Em Registro Do Wine
Espere Carregar..
Caso Não Carregue Abra o Terminal E Digite ou Cole Esse Comando:
WINEPREFIX=~/Pasta que você criou regedit E Espere Carregar Tudo..
Abrindo A Janela Siga Este Caminho:
HKEY_LOCAL_MACHINE/Software/WOW6432NODE/EA GAMES Após isso Clique em The sims 2 e em seguida em 1.0 ao Lado Localize o Language, Clique Duas Vezes e coloque a letra “a’ como valor faça Isso Com Todas As Expansões…..
8:Instalando Mods
Para Instalar Mods è bem Simples
Abra O Gerenciador de Arquivos E Entre em Documentos/EA GAMES/ The Sims 2/Downloads
Se Caso Não Tenha Esta Pasta Crie Uma Ai é Só Colocar Seus Conteúdos lá E Ser Feliz!
Muito Obrigado Por Ter Lido este Tutorial.. caso Tenha duvida Me Mande Uma Mensagem.. Ficarei Muito Feliz em Te Responder! Caso Não Consiga Me Contacte Nas Minhas redes!
Discord: iam_saiko
Intagram:sales.xz__
Muito Obrigado e até o Proximo Tutorial!
Duvidas Frequentes:
Precisa otimizar? Não O Wine ele Faz todo o processo do 4gb patch, Grafic Rules Maker e afins
Como rodo o Rpc? Mude A VERSÃO DO WINE Para a Padrão do lutris e ative o dxvk para seu jogo rodar Caso Não Tenha Vulkan Na Sua Placa Infelizmente Não será Possível Rodar o Jogo Causando O erro Do DirectX
O Original funciona? Sim Funciona, O Lutris Irá Instalar o EA App Para você Ai só logar na sua conta e instalar o jogo, Mais Lembrando que Travamentos, Lags, Bugs E crashs Irão Acontecer Pelo Fato Do Jogo Ser Mal Otimizado Com o EA APP
Precisa das dependencias? Sim E Não, o Lutris Carrega Todas as Dependencias Do Jogo Antes De Executa-lo, Mais Caso Precise, Abra O Terminal e Digite Seguinte Comando: WINEPREFIX=~/SEU PREFIXO WINE winetricks, Dê enter e espere a janela abrir, Abrindo A janela Instale as DLLS Do Windows e as Fontes E Rode O Jogo
2 notes
·
View notes
Text
Best Practices for Safe and Efficient LV Electrical Installations in 2025

Introduction
Low Voltage (LV) electrical installations are the backbone of safe and reliable power distribution in residential, commercial, and industrial settings. In 2025, as energy demands rise and smart technologies evolve, following best practices in LV installations is more important than ever to ensure safety, efficiency, and compliance.
This blog outlines the latest best practices for designing, installing, and maintaining LV electrical systems according to international standards and industry trends.
What Is an LV Electrical Installation?
LV (Low Voltage) refers to electrical systems that operate at voltages up to 1000V AC or 1500V DC. These installations include:
· Electrical panels and switchboards
· Distribution circuits
· Lighting systems
· Sockets and fixed appliances
· Motor control systems
Proper LV installation ensures that power is distributed safely and efficiently without risk of fire, equipment failure, or personnel injury.
Why Best Practices Matter in 2025
In the age of smart buildings, renewable integration, and digital energy management, the quality of your LV installation affects:
· Operational reliability
· Energy efficiency
· System lifespan
· User safety
· Regulatory compliance
Failing to adhere to best practices can result in costly downtime, legal penalties, and even life-threatening hazards.
Top Best Practices for Safe and Efficient LV Electrical Installations
1. Conduct Detailed Load Analysis
Before starting any LV installation, carry out a comprehensive load assessment to determine the power requirements, load types, and future expansion needs. This ensures:
· Proper cable sizing
· Correct protection device selection
· Optimized system capacity
Use load flow software tools and factor in diversity and demand coefficients for accuracy.
2. Follow International Standards (IEC, NEC)
Compliance with recognized standards ensures installations meet safety and performance benchmarks. Key references include:
· IEC 60364 for LV electrical installations
· NEC (NFPA 70) for code-compliant wiring in the U.S.
· ISO 50001 for energy management integration
Also, refer to local electrical regulations where applicable.
3. Use Certified, High-Quality Components
Always use LV components from certified manufacturers — this includes:
· Circuit breakers (MCCBs/MCBs)
· Residual current devices (RCDs)
· Surge protection devices (SPDs)
· Busbars, cables, and enclosures
Poor-quality components may not withstand fault conditions, leading to short circuits, fires, or system failure.
4. Ensure Proper Cable Management and Sizing
Correct cable selection and layout are critical:
· Size cables based on current capacity, voltage drop, and ambient temperature
· Use LSZH (Low Smoke Zero Halogen) cables for fire safety
· Label and route cables cleanly using trays, ducts, and tie-downs
Improper cable management is a leading cause of overheating and system inefficiency.
5. Install Proper Earthing and Grounding Systems
An effective earthing system protects against:
· Electric shock
· Equipment damage
· Lightning surges
Use TT, TN, or IT systems as per the application and ensure resistance values are within acceptable limits (e.g., <1 ohm for sensitive equipment).
6. Use Protection Coordination and Selectivity
Install protective devices in a coordinated hierarchy to ensure:
· Quick isolation of faults
· Minimal disruption to unaffected areas
· Avoidance of cascading tripping
Selectivity between breakers and fuses enhances safety and ensures continuity of service.
7. Integrate Smart Monitoring and Control
Modern LV installations benefit from IoT-enabled devices and energy monitoring software. This helps with:
· Real-time energy usage tracking
· Predictive maintenance alerts
· Power quality monitoring
· Remote switching and control
Smart LV systems are increasingly used in data centers, green buildings, and industrial automation setups.
8. Conduct Periodic Testing and Maintenance
Post-installation, regular inspection and testing ensure sustained safety and performance. Best practices include:
· Thermal imaging to detect overheating
· Insulation resistance testing
· RCD trip time checks
· Earth loop impedance measurement
Document all tests and create a preventive maintenance schedule based on manufacturer recommendations and operating conditions.
Common Mistakes to Avoid
· Overloading circuits without upgrading breakers
· Skipping grounding in temporary setups
· Using outdated wiring diagrams
· Mixing incompatible components
· Neglecting ventilation in panel enclosures
Conclusion
Safe and efficient LV electrical installations in 2025 require more than just technical knowledge — they demand a proactive approach that combines regulatory compliance, technology integration, and quality workmanship. By following these best practices, contractors and facility managers can minimize risks, optimize performance, and build future-ready electrical systems.
Whether you’re designing a commercial building, upgrading an industrial site, or installing a smart home system, investing in safe LV practices today is the smartest move for tomorrow.
Connect With Us
Whether you’re a project engineer, contractor, facility manager, or developer — Almond Enterprise is ready to support your next electrical challenge with confidence and capability.
🔗 Visit: www.almondenterprise.com 📞 Contact: [email protected] | +974 33858416
6 notes
·
View notes
Text
HID Access Controls UK for Data Centers: Advanced Protection
In an era where data is one of the most valuable assets, securing the physical infrastructure that houses sensitive information is critical. Data centers are the backbone of the digital world, and any breach—whether digital or physical—can have devastating consequences. That’s why implementing HID Access Controls UK for data centers is vital for ensuring advanced protection. With HID’s cutting-edge technology, data centers across the UK are able to safeguard their facilities with highly secure, scalable, and intelligent access control systems.
What are HID Access Control Systems?
HID Global is a world leader in trusted identity solutions, offering secure physical and logical access control systems. Their solutions are designed to protect people, assets, and data, using technologies such as smart cards, mobile credentials, biometric readers, and cloud-based identity management.
HID Access Controls UK for data centers provide tailored security solutions that meet the complex needs of high-risk environments, including server rooms, telecom infrastructure hubs, and cloud computing facilities. These systems are designed to restrict access, monitor activity, and respond instantly to potential threats—ensuring that only authorised personnel can enter designated zones.
Why Data Centers Need HID Access Controls UK
Data centers store highly sensitive data from governments, financial institutions, corporations, and consumers. While cyber security often takes the spotlight, physical access control is equally crucial. A breach in physical security can allow malicious actors to damage hardware, steal data, or compromise entire systems. This is where HID Access Controls UK for data centers becomes indispensable.
1. Multi-Layered Physical Security
HID access control systems provide multiple layers of protection—from perimeter gates and main entrances to server cages and individual cabinets. Each access point can be secured with different authentication methods, including proximity cards, mobile IDs, PINs, and biometrics. This layered approach ensures that even if one level is breached, the next barrier prevents unauthorised access.
2. Role-Based and Zone-Based Access
With HID Access Controls UK for data centers, administrators can assign access based on roles. For example, a network engineer may have access to server racks but not to storage rooms, while cleaning staff may only access common areas during designated hours. This granularity minimizes insider threats and enhances accountability.
3. Real-Time Monitoring and Alerts
HID systems offer real-time access tracking and alert notifications. If an unauthorised attempt is made or a door is left open longer than allowed, security teams are immediately alerted. This rapid-response feature is essential for incident prevention and audit compliance.
Key Features of HID Access Controls UK for Data Centers
Data centers require access control systems that are not only secure but also scalable and easy to manage. HID delivers on all fronts with a robust set of features:
Mobile Access Credentials: Employees can use their smartphones as secure credentials, reducing the risk of lost or cloned keycards.
Biometric Authentication: Fingerprint or facial recognition adds an extra layer of identity verification.
Cloud-Based Management: HID’s cloud solutions allow security teams to manage access permissions, monitor activity, and generate reports remotely.
Integration with Surveillance and Fire Systems: Access control can be linked with CCTV, fire alarms, and environmental sensors to create a unified security ecosystem.
Visitor Management Systems: Temporary credentials can be issued to vendors or maintenance personnel with time and zone restrictions.
Compliance and Audit-Ready Access
One of the most significant advantages of HID Access Controls UK for data centers is its ability to support compliance. Whether it’s ISO 27001, GDPR, or industry-specific regulations such as PCI-DSS or HIPAA, HID systems generate audit-ready reports that document every entry and exit.
Comprehensive logs of who accessed which area, at what time, and for how long are crucial during audits or investigations. This transparency boosts client trust and ensures that the facility maintains high security standards.
Scalable and Future-Proof Security
As data centers expand or adapt to new technologies, their security systems must evolve too. HID’s modular approach allows easy integration with future upgrades or added infrastructure. Whether expanding to another facility or upgrading existing systems, HID Access Controls UK for data centers can grow without the need for a full overhaul.
Energy Efficiency and Sustainability
Modern data centers aim to be energy-efficient. HID access control systems are designed with power-saving components and can be integrated with building automation systems. For example, lighting and HVAC systems can be automated to activate only when authorised personnel are present—contributing to sustainability and cost savings.
Conclusion
As the demand for secure and compliant data storage solutions continues to rise, so does the need for robust physical security. HID Access Controls UK for data centers provide advanced protection by combining cutting-edge technology with intelligent management systems. From biometric authentication to real-time monitoring, HID delivers a holistic solution that meets the highest standards of physical security.
1 note
·
View note
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
What makes Indian rice manufacturers the top choice for global importers?

Indian rice manufacturers have built a strong global reputation for their quality, variety, and consistent supply. As one of the largest rice exporting countries, India supplies premium and affordable rice varieties to over 150 countries. But what makes them the preferred choice for international buyers? Let’s look at the factors that make Indian rice exporters stand out in the global market.
Introduction to Indian Rice Manufacturing
India has long been a global leader in rice production, exporting over 40% of the world’s total rice supply (Source: FAO). The country’s manufacturing capacity is supported by its vast paddy fields, skilled workforce, and advanced milling facilities. Indian rice manufacturers cater to the market’s diverse needs, offering everything from high-quality Basmati to cost-effective bulk options.
This adaptability and focus on quality ensures that Indian rice continues to dominate the global market.
Quality Standards and Certifications
Quality assurance is the cornerstone for rice suppliers in India. They follow international guidelines to ensure that rice meets the expectations of global importers. Some of the key certifications include:
ISO 22000 and HACCP: highlighting their commitment to food safety.
Organic certifications: ensuring compliance with USDA and EU standards.
Fair trade and sustainability practices: signifying ethical production.
Many manufacturers use state-of-the-art milling techniques and conduct strict quality checks. These efforts make Indian rice a reliable choice for consumers around the world.
Wide variety of rice types
India offers an unmatched variety of rice, enabling manufacturers to meet the diverse preferences of global markets. Popular choices include:
Basmati rice: Famous for its aroma and long-grained texture, it is widely in demand in Europe and the Middle East.
Non-Basmati Rice: Varieties such as IR64 and Sona Masuri are staples in Africa and Asia.
Specialty and Organic Rice: Catering to niche markets focused on health and sustainability.
This broad portfolio allows Indian exporters to meet the needs of a variety of customers, from gourmet chefs to wholesale distributors.
Cost-effectiveness and supply reliability
Indian rice manufacturers maintain a balance between quality and affordability. This is achieved through:
High production efficiency: Leveraging large-scale operations and advanced machinery.
Government policies: Subsidies for farm equipment and fertilizers reduce production costs.
Geographical advantage: Fertile land and favorable weather ensure consistent yields.
Their ability to handle bulk orders while adhering to strict timelines makes Indian rice exporters reliable partners for global importers.
Commitment to sustainability and innovation
Sustainability has become a priority for Indian rice manufacturers. Many companies are adopting environmentally friendly practices such as:
Water conservation: Using innovative irrigation techniques to reduce water consumption.
Renewable energy: Integrating solar and bioenergy into milling processes.
Waste utilization: Converting rice husk into biofuels and fertilizers.
Such practices align with the values of environmentally conscious consumers, strengthening India’s position in the global market.
Additionally, advances in traceability and quality control, including digital systems, enhance transparency and trust between manufacturers and importers.
India’s global prominence in rice exports is supported by its strong manufacturing base, diverse offerings, and commitment to quality. By choosing Indian rice manufacturers, importers benefit from reliable, high-quality rice that meets a variety of market demands. Whether it’s aromatic basmati for fine eating or affordable bulk varieties for everyday use, Indian exporters continue to set benchmarks in the global rice trade.
2 notes
·
View notes
Text
Why Corporate Events in Belgium Are Fueling the Catering Market
Belgium Catering Services Market Overview: Thriving Amid Changing Consumer Dynamics
The Belgium Catering Services Market is undergoing a transformational shift as it responds to rapid urbanization, increasing corporate demand, and evolving consumer preferences. With an estimated belgium catering services market valuation of USD 1,360.1 million in 2023, and a projected CAGR of 5.5% through 2030, the industry stands at the forefront of innovation and service diversification.
As Belgium’s economy strengthens post-pandemic and businesses reinvigorate employee engagement strategies, outsourced catering solutions are becoming integral across corporate, healthcare, educational, and public sectors. Technological integration, growing health awareness, and the need for operational efficiency further amplify the market’s momentum.
Request Sample Report PDF (including TOC, Graphs & Tables): https://www.statsandresearch.com/request-sample/40586-belgium-catering-services-market
Key Belgium Catering Services Market Drivers:
Corporate Sector Catalyzing Market Growth
The rise in corporate catering demand is one of the primary accelerators of market expansion. Companies are investing in well-curated dining experiences to enhance employee morale, attract talent, and host impactful client-facing events. Corporate canteens, executive lunches, training seminars, and boardroom meals now rely heavily on professional catering firms to deliver consistency, nutritional value, and gourmet excellence.
Employee retention is increasingly tied to workplace wellness initiatives. Outsourced catering reduces operational costs while improving service quality. Demand for tailored menu options supports the inclusion of global cuisines and dietary-specific plans.
Get up to 30%-40% Discount: https://www.statsandresearch.com/check-discount/40586-belgium-catering-services-market
Healthcare Sector Prioritizing Specialized Nutrition
The healthcare catering segment is forecasted to grow at 5.9% CAGR, driven by Belgium’s aging population and the rising number of assisted living and rehabilitation centers. Nutrition plays a vital role in patient recovery and long-term care, prompting providers to outsource meal services to catering companies equipped with clinical dietitians and food safety certifications.
There is increasing emphasis on regulatory compliance, such as HACCP and ISO 22000. Tailored menus for diabetic, renal, low-sodium, and allergy-sensitive patients are in high demand. Partnerships with healthcare institutions fuel contract-based recurring revenues.
Tech Integration & Automation
Digitalization has emerged as a strategic tool in the Belgian catering ecosystem. From AI-powered kitchen waste management to online ordering platforms, catering companies are embracing technology to enhance transparency, sustainability, and operational precision.
In 2023, Compass Group Belgium partnered with Winnow to introduce AI systems for food waste analysis, resulting in measurable environmental and financial benefits.
Evolving Consumer Preferences
Demand for Health-Conscious & Sustainable Meals
As Belgian consumers become increasingly health-conscious, catering services must offer nutritious, organic, and sustainably sourced options. Menu transparency, calorie labeling, and traceability are no longer optional—they’re expected.
There is a growing preference for plant-based meals, locally grown produce, and zero-waste packaging. Flexitarianism and meatless meal alternatives are rising in popularity, particularly in corporate and educational institutions. Vegan, gluten-free, and low-carb options continue to gain traction.
Shift Toward Experience-Driven Dining
Experiential catering—such as live cooking stations, interactive menus, and gastro-themed events—is gaining traction. Companies are elevating corporate dining and private events with personalized culinary journeys.
High-end presentation and thematic customization are now value propositions. Hybrid models combining in-person catering and gourmet meal kits for remote teams are emerging.
Belgium Catering Services Market Segmentation Analysis:
By Type of Service
Off-premise catering dominates the belgium catering services market with a share of 64.6% in 2023. Its success is attributed to flexibility, convenience, and scalability. The model is widely adopted for corporate events, weddings, and private celebrations as it eliminates the need for on-site kitchen facilities. On-premise catering remains relevant, particularly for institutions and facilities with dedicated dining infrastructure.
By Food Type
Continental cuisine leads the belgium catering services market, accounting for 31.6% of the total share. Belgium’s European culinary influence supports this trend, particularly among corporate clients who favor refined, familiar dishes. Traditional Belgian cuisine also holds a significant share, reflecting national pride and consumer nostalgia. Asian and Middle Eastern cuisines continue to expand in urban areas, while vegetarian, vegan, and special dietary offerings are increasingly integrated into mainstream menus to accommodate dietary diversity.
By End User
The corporate sector remains the largest end-user segment due to sustained demand for employee-focused meal programs, event catering, and boardroom hospitality. The healthcare sector is poised for robust growth as medical institutions seek reliable partners to deliver nutritionally customized meals. Educational institutions, government agencies, and recreational venues are stable contributors, while the private events segment has rebounded strongly following the pandemic, bolstered by weddings, family gatherings, and cultural celebrations.
Competitive Landscape
Major Belgium Catering Services Market Players
Compass Group Belgium
Sodexo Belgium
Aramark
Elior Group
Choux de Bruxelles
Delaware North
Autogrill S.p.A.
These companies dominate the competitive landscape, collectively accounting for more than 65% of the market. Their strategies include mergers, certification renewals, digital innovation, and sustainability programs aimed at strengthening market position.
Notable Strategic Initiatives
In June 2023, Compass Group Belgium renewed its ISO 9001 and ISO 22000 certifications, reinforcing its commitment to food safety and quality management. In April 2023, the company partnered with Winnow to implement AI-driven waste tracking in its kitchens. These efforts support both environmental goals and cost control, setting new industry benchmarks.
Growth Opportunities & Future Outlook
Emphasis on ESG & Carbon Reduction
Environmental and social governance (ESG) compliance is becoming a market differentiator. Catering companies that track their carbon footprint, reduce food waste, and prioritize ethical sourcing will increasingly attract institutional clients. Clients are now aligning catering choices with their broader sustainability strategies.
Expansion in Educational & Recreational Sectors
The return of full-time in-person learning and an uptick in recreational events are boosting demand for high-volume catering contracts. These sectors offer underleveraged opportunities for growth through government tenders and public-private partnerships.
Innovation in Meal Personalization
Catering companies are exploring AI-driven menu planning and real-time customer feedback tools to offer hyper-personalized dining experiences. This trend is expected to dominate urban centers and institutions with diverse dietary preferences.
Purchase Exclusive Report: https://www.statsandresearch.com/enquire-before/40586-belgium-catering-services-market
Conclusion
The Belgium Catering Services Market is experiencing a renaissance fueled by corporate investment, health-focused consumer behavior, and digital innovation. As demand grows for personalized, sustainable, and efficient food solutions, providers must align their offerings with changing expectations and emerging technologies.
By harnessing flexible service models, global culinary trends, and strategic partnerships, catering companies can not only meet but exceed the dynamic needs of Belgium’s evolving marketplace. The path forward is clear: innovate, personalize, and sustain.
Our Services:
On-Demand Reports: https://www.statsandresearch.com/on-demand-reports
Subscription Plans: https://www.statsandresearch.com/subscription-plans
Consulting Services: https://www.statsandresearch.com/consulting-services
ESG Solutions: https://www.statsandresearch.com/esg-solutions
Contact Us:
Stats and Research
Email: [email protected]
Phone: +91 8530698844
Website: https://www.statsandresearch.com
1 note
·
View note
Text
Best data extraction services in USA
In today's fiercely competitive business landscape, the strategic selection of a web data extraction services provider becomes crucial. Outsource Bigdata stands out by offering access to high-quality data through a meticulously crafted automated, AI-augmented process designed to extract valuable insights from websites. Our team ensures data precision and reliability, facilitating decision-making processes.
For more details, visit: https://outsourcebigdata.com/data-automation/web-scraping-services/web-data-extraction-services/.
About AIMLEAP
Outsource Bigdata is a division of Aimleap. AIMLEAP is an ISO 9001:2015 and ISO/IEC 27001:2013 certified global technology consulting and service provider offering AI-augmented Data Solutions, Data Engineering, Automation, IT Services, and Digital Marketing Services. AIMLEAP has been recognized as a ‘Great Place to Work®’.
With a special focus on AI and automation, we built quite a few AI & ML solutions, AI-driven web scraping solutions, AI-data Labeling, AI-Data-Hub, and Self-serving BI solutions. We started in 2012 and successfully delivered IT & digital transformation projects, automation-driven data solutions, on-demand data, and digital marketing for more than 750 fast-growing companies in the USA, Europe, New Zealand, Australia, Canada; and more.
-An ISO 9001:2015 and ISO/IEC 27001:2013 certified -Served 750+ customers -11+ Years of industry experience -98% client retention -Great Place to Work® certified -Global delivery centers in the USA, Canada, India & Australia
Our Data Solutions
APISCRAPY: AI driven web scraping & workflow automation platform APISCRAPY is an AI driven web scraping and automation platform that converts any web data into ready-to-use data. The platform is capable to extract data from websites, process data, automate workflows, classify data and integrate ready to consume data into database or deliver data in any desired format.
AI-Labeler: AI augmented annotation & labeling solution AI-Labeler is an AI augmented data annotation platform that combines the power of artificial intelligence with in-person involvement to label, annotate and classify data, and allowing faster development of robust and accurate models.
AI-Data-Hub: On-demand data for building AI products & services On-demand AI data hub for curated data, pre-annotated data, pre-classified data, and allowing enterprises to obtain easily and efficiently, and exploit high-quality data for training and developing AI models.
PRICESCRAPY: AI enabled real-time pricing solution An AI and automation driven price solution that provides real time price monitoring, pricing analytics, and dynamic pricing for companies across the world.
APIKART: AI driven data API solution hub APIKART is a data API hub that allows businesses and developers to access and integrate large volume of data from various sources through APIs. It is a data solution hub for accessing data through APIs, allowing companies to leverage data, and integrate APIs into their systems and applications.
Locations: USA: 1-30235 14656 Canada: +1 4378 370 063 India: +91 810 527 1615 Australia: +61 402 576 615 Email: [email protected]
2 notes
·
View notes
Text
Garantizando la Seguridad Empresarial con Certificación en ISO 27001 y ENS: Servicios de Consultoría, Auditoría e Implementación
En el vertiginoso mundo digital actual, la seguridad de la información se ha convertido en un pilar fundamental para la continuidad y éxito de cualquier empresa. En este contexto, la certificación en normativas como ISO 27001 y el Esquema Nacional de Seguridad (ENS) se erigen como sellos de confianza que fortalecen la posición de las organizaciones frente a posibles amenazas cibernéticas. En Certificado27001.es, nos enorgullece ofrecer servicios especializados en consultoría, auditoría e implementación de medidas técnicas, brindando a las empresas una protección robusta ante riesgos digitales.
Protección Integral con ISO 27001 y ENS
La certificación ISO 27001, reconocida internacionalmente, establece estándares para la gestión de la seguridad de la información. Nuestros servicios de consultoría 27001 no solo te guiarán en el proceso de certificación, sino que también te ayudarán a integrar prácticas seguras en la cultura organizacional. Esto se traduce en un aumento de la resiliencia ante amenazas, la protección de la confidencialidad, integridad y disponibilidad de la información.
Además, nuestra oferta se extiende al Esquema Nacional de Seguridad (ENS), un marco normativo español diseñado para salvaguardar la información en el ámbito de las administraciones públicas. Contamos con expertos en el ENS que te asesorarán en la implementación de medidas técnicas necesarias para cumplir con los requisitos de esta normativa y garantizar la seguridad de los datos sensibles.
Servicios de Consultoría 27001 y ENS Personalizados
Reconocemos que cada empresa es única, enfrentando desafíos y operando en entornos específicos. Nuestros servicios de consultoría son completamente personalizados para adaptarse a las necesidades individuales de tu organización. Comenzamos con una evaluación exhaustiva de tus sistemas, identificando vulnerabilidades y definiendo un plan de acción preciso.
La implementación de medidas técnicas es una parte crucial de nuestro servicio. Nos aseguramos de que tu infraestructura esté protegida mediante la aplicación de controles de seguridad, cifrado de datos y otras prácticas recomendadas. Nuestro compromiso es garantizar que tu empresa no solo cumpla con los estándares de certificación, sino que también cuente con una sólida defensa ante las amenazas cibernéticas emergentes.
Auditoría Rigurosa para Garantizar el Cumplimiento Continuo
La certificación no es un evento puntual; es un compromiso continuo con la seguridad. Nuestros servicios de auditoría periódica aseguran que tu empresa cumpla con los estándares ISO 27001 y ENS de manera constante. Detectamos posibles brechas de seguridad, evaluamos la eficacia de las medidas implementadas y ofrecemos recomendaciones para mantener la excelencia en seguridad.
Compromiso con el Esquema Nacional de Seguridad 2022
En Certificado27001.es, nos mantenemos actualizados con las últimas evoluciones normativas. Nuestros servicios se alinean con las exigencias del Esquema Nacional de Seguridad 2022, asegurando que tu empresa esté a la vanguardia en seguridad cibernética y cumpla con las regulaciones más recientes.
Conclusiones
Proteger la seguridad de tu empresa es esencial en el entorno digital actual. Nuestros servicios de consultoría, auditoría e implementación en ISO 27001 y ENS ofrecen una garantía de confianza, fortaleciendo la resiliencia de tu organización ante amenazas cibernéticas. Visita nuestro sitio web Certificado27001.es para conocer más sobre cómo podemos ayudarte a construir un futuro digital más seguro. La seguridad de la información no es una opción, ¡es una necesidad!
2 notes
·
View notes
Text
What Is the Role of the 21st Century Post Digital Photographer?
“Within the limits of his medium, without resorting to any method of control that is not photographic (i.e., of an optical or chemical nature), the photographer can depart from literal recording to whatever extent he chooses.” Edward Weston, (1964) ‘Seeing Photographically’, The Encyclopaedia of Photography, Vol.18
’electronic imaging’ ‘post-photography’, my take on the role of the photographer has definitely been challenged and opened after reading this article.
The idea of visually recording via photographs was addressed in this article as it challenges the question of what the role of photographers are. Calling out the falsity of image manipulation that is encouraged and enabled by digital capture features as well as specific jobs asking more from photographers - creating new roles and more tasks for them.
The practice of post-production effects and features can quickly turn an image into a poorly judged norm that images are masked with. Likewise, the decision to alter images to attain a certain outcome not captured on camera, creates a piece that lacks integrity. More often than not, the results of work with these practices are deemed to be quite like a "'magpie' collection of work, rather than a photographic language unique to the photographer", like the article states.
Gran Scott establishes the responsibility of creating a personal visual body of work is vital in the means of formulating an honest and substantial foundation of photographic practice in the 21st Century, however the role of the photographer must first be understood.
Scott addresses the responsibilities of photographers nowadays being not only a storyteller, but to also name a few, they are also writers, publishers, marketers and filmmakers. The role of the photographer has changed from that of creating and disseminating and it is in that dissemination or butchering, that the photographer has inherited the power of communication that they have for so many years longed for. However, said power comes with unconsidered realities of implications and sensitivities that concern both legal and international aspects.
Edward Weston commented in a pre-digital world, the process of creating and capturing a moment remains in the control of the photographer. From the camera position to the choice of camera, lens, ISO and use of light; the documentation of the subject is their interpretation of that moment in time. But today, the photographer has to be considerate and aware of how the image would be viewed and consumed within the context given - considerations previously taken by a publisher. The photographer has to take the responsibility not only for their work, but for those involved within the images and potentially the image creation. This is because of the reach of said image, being posted online, seen at exhibitions or an environment unexpected. By sharing photos, they are adopting the role of a publisher and therefore must accept outcomes that may result into a irresponsible and ill-informed publication.
The reality is, photographers of the 21st century can no longer remain purely as an author dependant on others to give foundational directions for their practice. Acceptance of the realities and responsibilities in the new forms of storytelling is a part of the unspoken agreement photographers take on, having to embrace personal and ethical responsibility to address the issues of unscrupulous and deceitful image creation. It is no longer acceptable to play the ignorance card.
The constant changes of the 21st Century photographer evolves in ways that must consider and respond rationally to realities that also continue to change.
2 notes
·
View notes
Text
Reinventing Healthcare: Top Trends and Insights in the Medical Billing Industry for 2024
Revolutionizing Healthcare: Top Trends and Insights in the Medical Billing Industry for 2024
The medical billing industry is an essential component of healthcare, ensuring providers are compensated accurately and promptly for their services. As we move into 2024, innovative trends and technological advancements are transforming how medical billing operates, driven by the need for efficiency, accuracy, and compliance. In this thorough guide, we will explore the top trends shaping the future of healthcare billing, practical benefits, real-world case studies, and actionable insights to help healthcare providers stay ahead of the curve.
Introduction
Recent years have seen rapid changes in healthcare technology, regulations, and patient expectations. The evolution of medical billing in 2024 is no exception, with a focus on digital transformation, data security, and automation. These advancements are not only streamlining workflows but also improving revenue cycle management and patient experiance. Understanding these key trends empowers healthcare organizations to adapt proactively, optimize revenue, and deliver superior patient care.
Top Trends in Medical Billing for 2024
1. Increased Adoption of AI and Machine Learning
Artificial Intelligence (AI) and machine learning are revolutionizing medical billing by automating complex claim processes, detecting errors, and predicting reimbursement outcomes. AI-driven tools can analyze vast amounts of data quickly, reducing claim denials and speeding up payment cycles.
Automated claim validation and coding accuracy
predictive analytics for revenue forecasts
Enhanced fraud detection capabilities
2. Integration of Telehealth and Virtual Care Billing
With the surge in telehealth services, billing for virtual care has become a significant aspect of healthcare revenue. 2024 sees better integration of telehealth platforms with billing systems, ensuring compliance with evolving regulations and proper reimbursement for virtual visits.
Standardized coding for telehealth services (e.g.,CPT,HCPCS codes)
Automated documentation for remote consultations
Improved tracking of telehealth-specific reimbursements
3. Robust data Security and Compliance
As cyber threats grow, securing patient data and ensuring compliance with HIPAA and other regulations remain top priorities. Advanced encryption, multi-factor authentication, and secure cloud storage options are now integral to medical billing systems in 2024.
ISO-certified security protocols
Regular compliance audits
Real-time monitoring of data breaches
4. Cloud-Based Billing Solutions
Cloud technology allows healthcare providers to access billing data anytime, anywhere, facilitating remote work and enhanced collaboration. Cloud-based systems also offer scalable infrastructure and automatic updates, reducing IT overhead.
Advantages
Details
Accessibility
Remote access from multiple devices
Cost-effectiveness
lower upfront infrastructure costs
Scalability
Easy to scale as your practice grows
Automatic Updates
Always stay compliant with latest regulations
5. Enhanced Patient Self-Service Portals
Empowering patients with self-service portals improves collection rates and patient satisfaction. These portals allow patients to view bills, make payments, and update personal information effortlessly.
Secure online payment options
Real-time billing updates
Integration with mobile apps for convenience
Benefits and practical Tips for Healthcare Providers
Staying ahead in the medical billing industry offers numerous benefits:
Increased Revenue: Faster claim processing reduces delays and denials, boosting cash flow.
Improved Accuracy: AI and automation minimize human errors.
Enhanced Security: Advanced cybersecurity protocols protect sensitive patient data.
Better Patient Experience: Self-service portals and clear billing foster trust and loyalty.
To capitalize on these trends, consider the following practical tips:
Invest in AI-powered billing software to streamline workflows.
Integrate telehealth billing protocols into your existing systems.
Prioritize staff training on new technologies and compliance standards.
Implement secure, cloud-based solutions for flexible access and scalability.
Enhance patient engagement through user-kind portals and dialogue channels.
Case Study: Successful Implementation of Automated Billing System
Harmony Medical Group,a mid-sized clinic,faced persistent claim denials and delayed payments.By adopting an AI-driven billing platform, they achieved the following results within six months:
Denial rates decreased by 30%
Cash flow improved by 25%
Operational efficiency increased, saving 15 hours/week in administrative tasks
This real-world example illustrates how embracing technological innovation can transform revenue cycle management, reduce overhead, and improve overall profitability.
Emerging Technologies & Future Outlook
The future of medical billing in 2024 and beyond will likely be shaped by:
Blockchain technology for enhanced clarity and security
real-time claim adjudication with AI assistance
Greater integration of Electronic Health Record (EHR) systems
Personalized patient billing experiences powered by data analytics
Staying abreast of these innovations ensures healthcare providers can adapt their billing processes, stay compliant, and optimize revenue.
Conclusion
As healthcare continues to advance rapidly into 2024, the medical billing industry is experiencing a transformative shift driven by technology, regulatory changes, and patient expectations. Embracing these top trends-such as AI automation, telehealth billing integration, cloud solutions, and enhanced patient portals-can substantially boost operational efficiency, ensure compliance, and improve revenue. Healthcare providers who adapt proactively will not only navigate the complexities of modern healthcare billing but also set themselves up for sustained success in this digital age.
Whether you’re a small practice or a large healthcare organization, understanding and implementing these innovative trends will position you at the forefront of healthcare billing excellence. Stay informed, invest in technology, and prioritize patient engagement to revolutionize your practice’s billing process in 2024 and beyond!
https://medicalbillingcertificationprograms.org/reinventing-healthcare-top-trends-and-insights-in-the-medical-billing-industry-for-2024/
0 notes
Text
The Rising Demand for BIM Consultants in Dubai: Building the Future of Construction

In recent years, Building Information Modeling (BIM) has emerged as a transformative force in the global construction industry. Nowhere is this transformation more evident than in Dubai—a city known for its iconic skyline, ambitious architectural projects, and commitment to smart city initiatives. As developers strive for efficiency, sustainability, and innovation, the demand for skilled BIM Consultants in Dubai is on a sharp rise.
What is a BIM Consultant?
A BIM consultant specializes in implementing and managing Building Information Modeling processes throughout the design, construction, and facility management phases of a project. Their role includes coordinating digital models, ensuring adherence to standards, and streamlining collaboration among architects, engineers, and contractors. In essence, they are the digital backbone of modern construction projects.
Why Dubai Needs BIM Consultants
Dubai’s construction sector is characterized by its scale, complexity, and emphasis on futuristic design. From mega shopping malls and high-rise towers to smart infrastructure and sustainable developments, the city requires advanced tools to bring these visions to life. BIM consultants provide exactly that—offering a digital representation of the physical and functional characteristics of a facility.
Some reasons for their growing importance include:
Government Regulations: Dubai Municipality and other authorities now mandate BIM usage for large-scale public projects. This regulatory push has increased the need for professionals who can ensure compliance and manage BIM workflows effectively.
Mega Projects: Projects like the Museum of the Future, Expo 2020 legacy developments, and the Dubai Urban Master Plan 2040 rely heavily on precise, collaborative planning—areas where BIM consultants play a key role.
Cost and Time Efficiency: With rising construction costs, developers are turning to BIM to reduce waste, avoid rework, and ensure timely delivery. Consultants help optimize these processes by detecting clashes early and ensuring smooth execution.
Skills and Services Offered
BIM consultants in Dubai typically offer a wide range of services, including:
BIM strategy and implementation planning
3D, 4D, and 5D modeling
Clash detection and coordination
Model-based cost estimation and scheduling
Training and support for in-house teams
Integration with facilities management systems
They are also well-versed in local and international BIM standards such as ISO 19650, which is crucial for compliance and quality assurance.
The Future of BIM Consultancy in Dubai
As Dubai continues to position itself as a global hub for innovation and smart technologies, the role of BIM consultants will only become more critical. The rise of digital twins, AI-driven design, and IoT integration into building management systems further emphasizes the need for BIM expertise.
Construction firms that embrace BIM early and effectively—with the help of skilled consultants—will have a competitive advantage in delivering high-quality, sustainable, and cost-efficient projects.
Conclusion
BIM Consultants are no longer a luxury but a necessity in Dubai's fast-paced construction environment. Their ability to bridge the gap between design and execution through technology makes them key players in shaping the city's architectural future. For developers, engineers, and contractors alike, partnering with the right BIM consultant can make the difference between project success and failure.
0 notes
Text
Cloud Backup Solutions: Secure, Scalable, and Essential for Business Continuity
In today’s digital-first world, businesses of all sizes are producing and storing enormous amounts of data. From financial records and client information to communication logs and intellectual property, this data forms the backbone of modern operations. But with growing cyber threats, hardware failures, and the unpredictability of natural disasters, securing this data has become more important than ever. That’s where cloud backup solutions come in — providing an essential layer of protection that is both secure and scalable.

What is Cloud Backup?
Cloud backup, also known as online backup, is a process where data is copied and stored on a remote server over the internet. Instead of relying on local physical devices like hard drives or tapes, cloud backup uses off-site data centers operated by specialized providers. This allows for continuous, automated, and secure backup of essential data, making it available for quick restoration in case of loss.
Why Cloud Backup is Essential for Business Continuity
1. Disaster Recovery Preparedness Natural disasters, power outages, and hardware malfunctions can strike at any time, threatening the integrity of your data. Cloud backup ensures that your files are safe in geographically dispersed locations, ready to be restored instantly when needed. This means businesses can recover quickly with minimal disruption.
2. Protection Against Cyber Threats Ransomware and malware attacks are on the rise, targeting organizations to steal or lock their critical data. A secure cloud backup allows businesses to restore clean, uninfected versions of their data, rendering cyberattacks less damaging and helping avoid costly downtimes or ransom payments.
3. Accessibility and Flexibility Cloud backups are accessible from anywhere with an internet connection. Whether employees are working remotely or switching between offices, they can retrieve data easily, improving workflow and flexibility. This is especially beneficial for businesses with distributed teams or hybrid work models.
4. Scalability as You Grow Traditional backup systems can become expensive and hard to scale as data needs grow. Cloud solutions offer pay-as-you-go models, allowing businesses to only pay for the storage they use. As your organization expands, your backup capacity can grow with it, effortlessly.
5. Cost-Effective and Low Maintenance With cloud backup, there’s no need to invest in physical infrastructure or hire a dedicated team for backup management. The cloud provider takes care of storage, maintenance, and security, reducing the IT burden on your in-house team and lowering overall costs.
6. Automation for Peace of Mind Manual backups are prone to human error and forgetfulness. Most cloud backup solutions offer automatic scheduling, ensuring your data is consistently backed up without requiring manual input. This keeps your business protected 24/7 without the need for constant monitoring.
Key Features to Look for in a Cloud Backup Service
When choosing a cloud backup provider, consider the following features:
End-to-End Encryption: Your data should be encrypted both during transit and while at rest.
Multi-Version Backup: Ability to restore previous versions of files, not just the latest.
User-Friendly Interface: Easy setup, monitoring, and data recovery process.
24/7 Support: Reliable customer support to resolve issues quickly.
Compliance and Certifications: Ensure the provider meets industry regulations like GDPR, HIPAA, or ISO 27001.
Use Cases Across Industries
Healthcare: Patient records must be kept secure and recoverable to meet regulatory standards. Cloud backup ensures both compliance and continuity in emergencies.
Finance: Banking institutions rely on continuous access to transaction data. Cloud backups help protect this sensitive information from cyber threats or loss.
Education: Schools and universities store academic records and research. Cloud backup allows seamless data recovery, even in the face of campus closures or hardware failures.
Retail & E-Commerce: With high volumes of customer and transaction data, cloud backup keeps retail operations running smoothly, even if internal systems go down.
Final Thoughts
As businesses become increasingly reliant on digital operations, cloud backup is no longer optional — it’s a necessity. The combination of security, scalability, and low overhead makes it one of the most strategic investments an organization can make to safeguard its data. Whether facing a cyberattack, a system crash, or a natural disaster, companies with cloud backup solutions in place can bounce back faster, maintain their reputation, and keep serving their customers without interruption.
Investing in a robust cloud backup system today is one of the smartest moves you can make to future-proof your business and ensure long-term success.
0 notes
Text

ISO 27001:2022 Lead Auditor – Your Gateway to a Career in Information Security Auditing
In the modern digital world, the demand for secure information systems has never been greater. Organizations worldwide are under mounting pressure of compromising data integrity, confidentiality, and availability. Consequently, trained experts capable of evaluating and auditing Information Security Management Systems (ISMS) are in great demand. Here is where ISO 27001:2022 Lead Auditor certification is a must-have qualification — and WiseLearner IT Services is here to assist you in getting it.
What is ISO 27001:2022? ISO/IEC 27001:2022 is the new version of the world's only internationally recognized standard for managing information security. It offers a methodical approach to the protection of confidential data using risk management, process controls, and continuous improvement. The standard assists organizations in showing compliance with global regulations and dedication to information security.
Why become an ISO 27001:2022 Lead Auditor? Becoming an ISO 27001:2022 Lead Auditor allows professionals to:
Conduct and lead audits of an organization's ISMS
Ensure compliance with ISO 27001 standards
Assist companies in identifying vulnerabilities and taking corrective measures
Assist in improving governance and data protection policies
Enhance career prospects in auditing, compliance, and information security
It's a job that mixes extensive technical expertise with communication and leadership skills.
Who Should Take This Course? Our ISO 27001:2022 Lead Auditor training is suitable for:
Information Security Officers
Compliance Managers
IT and Risk Management Professionals
Internal and External Auditors
Consultants wanting to help organizations implement ISO 27001
If you want to upskill or transition into a career that is security-intensive, this course is an intelligent investment.
Course Overview at WiseLearner IT Services Here at WiseLearner IT Services, training is not just theory. Here's what you can expect:
Detailed knowledge of ISO/IEC 27001:2022 and ISO 19011 guidelines for audit
Hands-on skills in planning, performing, and leading an ISMS audit
Realistic scenarios and case studies to support learning
Audit reporting techniques and skills to handle nonconformities
Expert-led classes by veteran trainers and auditors
Certification test to authenticate your skills and knowledge
Our adjustable learning options (classroom, online, or blended) allow working professionals to learn at their own pace without sacrificing quality.
Key Benefits of the Certification International Recognition: ISO 27001 Lead Auditor is a globally recognized certification.
Career Advancement: Open doors to lucrative career opportunities in security auditing and compliance.
Organizational Impact: Assist businesses in protecting their information and obtaining ISO compliance.
Confidence: Discover how to evaluate controls, determine risks, and enhance ISMS practices effectively.
Why Choose WiseLearner? At WiseLearner IT Services, we hold ourselves to the goal of providing training that meets current industry needs. Our instructors have decades of experience in the field and love guiding working professionals toward meaningful, fulfilling careers. With our hands-on training, certification guidance, and lifetime access to materials, you're not only learning — you're creating a career that's future-proof.
Final Thoughts As cyber threats grow and compliance demands evolve, certified ISO 27001:2022 Lead Auditors are critical in today’s business landscape. Whether you’re a professional aiming to lead audits or an organization looking to train your team, WiseLearner IT Services is your trusted partner in learning and certification.
Start your journey today — secure your certification, secure the future.
#ISO 27001:2022 Lead Auditor#ISO 27001 certification#Information Security Management System (ISMS)#Lead Auditor training#ISO 27001 auditor course#Cybersecurity certification#ISMS audit training
0 notes
Text
IOTE2025 Shenzhen Exhibitor Introduction Collection Part 7 : including 5 exhibitors products Recommendation
AGIC + IOTE 2025, the 24th International Internet of Things Exhibition — Shenzhen Station, will take place from August 27 to 29, 2025, at the Shenzhen World Exhibition & Convention Center.
This article will introdce the following exhibitors:
1.GUANG ZHOU ZHI LIAN INTERNET OF THINGS TECHNOLOGY CO.,LTD.
2.Shandong Huayi Micro-Electronics Technology Co., Ltd
3.Shenzhen Yuanmingjie Technology Co., Ltd.
4.Zinergy ShenZhen Ltd.
5.YOUHAOSUJIAO

GUANG ZHOU ZHI LIAN INTERNET OF THINGS TECHNOLOGY CO.,LTD.
Booth number:9D38
August 27–29,2025
Shenzhen World Convention and Exhibition Center (Bao’an New Hall)
Company Profile
Guangzhou Zhilian IoT Technology Co., Ltd. was established in 2016 and is located in the Guangzhou Airport Zone — Huadu. The company specializes in the research, development, and production of RFID tag printing, reading, and testing equipment; digital printing and digital coating/cold stamping equipment; vision inspection systems; and industrial automation equipment. It is a technology-driven company integrating R&D, design, manufacturing, sales, and after-sales service. It was recognized as a “National High-Tech Enterprise” in 2019, designated as a “Specialized, Refined, and Innovative Enterprise” in 2022, and certified under ISO 9001.
Product Recommendation

Features and Benefits
1. The equipment integrates UV printing, RFID reading and verification functions, streamlining production processes, improving production efficiency, and reducing labor costs.
2. The printing station features dust removal, UV printing, pre-curing, and main curing functions.
3. The reading/writing station includes TID verification, EPC writing, EPC verification, and scrap marking functions.
4. Multi-station RFID parallel reading/writing further improves reading/writing efficiency.
5. A multi-station collaborative control system ensures the reliability of synchronized RFID parallel reading/writing.

Features and Benefits
1. The equipment integrates UV printing and RFID reading/writing verification functions, streamlining production processes, improving production efficiency, and reducing labor costs.
2. The printing station features dust removal, double-sheet detection, UV printing, pre-curing, and main curing functions.
3. The RFID read/write station includes visual inspection, TID verification, EPC writing, double EPC verification and rejection, bin counting and material collection, with automatic order replenishment based on rejection.
4. The device can be equipped with an irregular-shaped material feeding mechanism.
5. Fully servo-driven high-speed material feeding platform ensures stable material feeding and high precision.

Shandong Huayi Micro-Electronics Technology Co., Ltd
Booth number:9C19–1
August 27–29,2025
Shenzhen World Convention and Exhibition Center (Bao’an New Hall)
Company Profile
Shandong Huayi Micro-Electronics Technology Co., Ltd is positioned at the intersection of integrated circuits and information security, serving as a professional provider of information security solutions. The company has been recognized as a National High-Tech Enterprise, a National Specialized and Innovative “Little Giant” Enterprise, an Outstanding Enterprise in the National Electronics Industry, and a Shandong Province Gazelle Enterprise, among other accolades. It has accumulated over 150 independently owned intellectual property rights and completed R&D for 11 customized projects. The company has undertaken over 20 national and provincial-level research projects and has been approved as the Shandong Province Integrated Circuit Design Center, Shandong Province Software Engineering Technology Center, and five other innovation platforms. It坚持 independent R&D, achieving full autonomy and control from IP core libraries to the supply chain. It has accumulated dozens of core technologies, including system-level chip design processes, low-power consumption, true random number generation, reconfigurable cryptographic algorithm engines, post-quantum cryptography rapid implementation, and secure isolation.
Product Recommendation

The HYS-701 Intelligent Document Circulation Cabinet is a high-efficiency document circulation cabinet independently designed and developed by Shandong Huayi Microelectronics Technology Co., Ltd. This product is based on ISO18000–3 Mode 3/EPC Class-1 RFID high-frequency identification technology, integrating an identity recognition system, lock control system, and Android operating system. It is an intelligent device designed for comprehensive management of documents and archives. It enables secure storage of documents, authorized borrowing, precise location tracking, rapid inventory, real-time monitoring, data analysis, process tracing, and SMS notifications.

The HY5960 passive smart electronic tag chip is the world’s first high-anti-collision IoT security chip independently developed by Shandong Huayi Microelectronics Technology Co., Ltd. It supports the ISO 18000–3 Mode 3/EPC Class-1 standard, EPC encoding, and national cryptographic security algorithms. The product employs an independently developed high-performance anti-collision algorithm, offering high recognition rates and advanced security and anti-counterfeiting levels. It is widely applicable in scenarios with high anti-collision requirements and precise, dense, and rapid reading needs.

Shenzhen Yuanmingjie Technology Co., Ltd.
Booth number:9A17
August 27–29,2025
Shenzhen World Convention and Exhibition Center (Bao’an New Hall)
Company Profile
Shenzhen Yuanmingjie Technology Co., Ltd. was established in 2010 and specializes in the research, development, and manufacturing of production equipment for RFID electronic tags, smart cards, and wireless intelligent products. With its advanced technology, unique design, and stable performance, the company has broken free from the traditional reliance of domestic enterprises on foreign technology, becoming China’s first comprehensive provider of end-to-end production solutions for smart cards and RFID tags.

1. The YMJ-FC180 is a device designed for the IoT RFID industry, specifically for the placement of HF and UHF electronic tag inlay chips. The entire machine is compatible with antenna widths ranging from 20 to 200 mm in roll-to-roll applications.
2. The entire production line consists of automatic roll-to-roll unwinding, automatic material feeding, automatic dispensing, chip mounting, automatic hot pressing, automatic marking detection, and automatic roll-up. The equipment supports 8-inch and 12-inch wafer discs.

Roll-to-roll inspection, rejection, and re-labeling integrated machine: Inspects the quality and appearance of high-frequency or ultra-high-frequency finished labels (including dirt, misalignment, printing defects, scratches, and barcodes, QR codes, or numeric codes); verifies consistency between internal and external codes; Defective labels are inkjet-printed, and replacement labels can be selected as blank or pre-printed with codes or QR codes, barcodes, etc.; compatible with labels of different thicknesses and widths, high production capacity, stable equipment operation, and high reliability.

Zinergy ShenZhen Ltd.
Booth number:10D22–1
August 27–29,2025
Shenzhen World Convention and Exhibition Center (Bao’an New Hall)
Company Profile
Zinergy ShenZhen Ltd.. was established in 2017. Its core technology originates from the team of academicians at the Oatley Laboratory of the University of Cambridge. The company is dedicated to the research, development, production, and sales of flexible batteries. With its research and production center in Shenzhen, the company also has a research base in Cambridge, UK. It has established scientific research and innovation platforms such as the “Guangdong Provincial Advanced Flexible Electronic Materials Engineering Technology Research Center” and the “Shenzhen Academician (Expert) Workstation.” The company’s core technical team has over 20 years of technical expertise in new materials and energy storage, with flexible battery products leading the world in performance. Currently, the company has a monthly production capacity of several million flexible batteries, and has obtained certifications including ISO 9001 international quality system, RoHS, and aviation transport safety. It is one of the most promising flexible battery suppliers globally.
Product Recommendation
(1) 1.5V Flexible Battery

(2) 3.0V Flexible Battery


YOUHAOSUJIAO
Booth number:9C51
August 27–29,2025
Shenzhen World Convention and Exhibition Center (Bao’an New Hall)
Company Profile
Hubei YOUHAOSUJIAO IoT Technology Co., Ltd. was established in 2018 and is a professional enterprise engaged in the research, design, and production of animal tags, ear tags, glass tubes, ankle bands, temperature-sensitive pedometer ear tags, syringe electronic chips, and reader/writer devices. The company occupies a total area of 6,000 square meters. The company has obtained ISO 9001 quality management system certification and certification from the International Committee for Animal Recording (ICAR). We are committed to providing solutions based on RFID, wireless sensor networks, and other IoT technologies for applications such as animal tracking, livestock industry informatization, food safety, and traceability.
Product Recommendation

German-imported glass tube bio-electronic tags, suitable for livestock animals: cats, dogs, horses, pigs, cattle, sheep, rabbits, mink, raccoon dogs,foxes, dragonfish, etc., for identification purposes. Manufactured using biocompatible medical-grade materials and processes, compliant with ISO 11784/85 international standards, utilizing advanced bio-glass material, with a coating to effectively prevent migration and animal rejection. They are small in size, lightweight, and remain effective for 30 years after injection, enabling lifelong tracking of animals. Currently widely used both domestically and internationally, they effectively manage and control animal growth and breeding, providing comprehensive tracking and management throughout the entire growth process.
Features:
Small size, lightweight
Simple injection/implantation
Bioglass encapsulation
Surface coated with anti-slip material
Application areas:
Cats, dogs, laboratory mice, pet ferrets, raccoons, foxes, goldfish, salmon, horses, rabbits, pigs, cattle, sheep, etc.
Certifications: This product is certified by the International ICAR and complies with the ISO 11784/11785 communication protocol!

The electronic ear tags are injection-molded from TPU material to prevent allergic reactions from prolonged animal contact. Male tags use a secondary injection-molded encapsulation method, while female tags are one-piece molded. They offer excellent UV protection, waterproofing (IP68 rating), and operate at temperatures ranging from -30°C to 150°C. The built-in chip uses UHF tags with a read range of 0.5 to 3 meters, suitable for various livestock farming environments.
RFID electronic ear tags are animal electronic tags that use RFID technology for individual animal identification. This product supports two frequency bands: high-frequency and ultra-high-frequency. The electronic ear tag employs RFID technology, enabling non-contact, long-range automatic identification and measurement of animal bodies. The RFID electronic ear tag is equipped with an embedded electronic chip and antenna, storing individual livestock information, serving as an individual identification document for livestock. Through the electronic ear tag, it is possible to accurately track information about each livestock animal from birth to transportation to various final consumption locations, thereby ensuring animal meat quality and public food safety.

YOUHAOSUJIAO’s custom-designed product for livestock farming uses non-toxic, odorless, non-irritating, soft, and durable TPU material to ensure suitability for use in various environments. It is primarily used for animal tracking, identification, and management in the livestock industry: enabling the association of each animal’s ear tag number with its breed, origin, vaccination status, health condition, Once an epidemic or livestock quality issue occurs, the source can be traced (traceable), responsibilities clarified, and loopholes sealed.
Application Areas:
Animal epidemic prevention, intelligent identification and inventory, intelligent weighing, intelligent feeding, and daily information management such as slaughter records.
0 notes