#Internet Safety Tips
Explore tagged Tumblr posts
Text
Boost Your Internet Security: How Sigzen Technologies Makes It Easy
In the ever evolving landscape of cybersecurity, the importance of robust Network and Firewall Management cannot be overstated. Sigzen Technologies has emerged as a trailblazer in this domain, offering a cosmprehensive suite of services designed to fortify your online defenses. Let’s explore the new features in Network and Firewall Management provided by Sigzen Technologies, ensuring your…

View On WordPress
#Boost Your Internet Security#Data Protection#Internet Safety Tips#Online Safety#Secure Browsing#Tech Security
3 notes
·
View notes
Text
youtube
A video that came across my recommended and felt it important to share. It is long, but it is worth the watch.
1 note
·
View note
Text
McAfee
Stay safe online, up to 5 devices, with a 30 day free trial of McAfee Security Products. Protect yourself and your love ones online.
#warrenwoodhouse#2024#bookmark#bookmarks#link#links#.lnk#.url#online safety#internet safety#internet safety tips#free#free software#freebies
0 notes
Text
I've been griping about the normalization of identity outing via social media for a while now. To put it simply, it's become almost some weird societal requirement that if you don't have every detail listed about yourself in your Twitter/FB/etc. bio, then it means you have "something to hide" or that you're not as "verifiable" because your account looks indistinct from that of a bot.
But that societal norm has really only benefited the people who profit off of that information in some way, whether it's through selling user data or through weaponizing details about a person against them.
I know that a lot of us love to use the fun little labels and acronyms in our bio that help others like us identify us as a 'safe person' or as someone who's in the same social/racial/identity groups as them. We're humans, we love to categorize things, it's in our nature (and it's fun!)
But if there's any time to start regulating that habit and challenging the norm that you're obligated to include all your personal info online - it's now.
There was a time when sock puppet accounts were expected and typical, not "suspicious".
There was a time when even age-sex-location was considered "too much information", but once it became the norm, we only EVER gave our personal information beyond generic ASL to people who we knew both online and in real life, or at the very least, people who we had known online for a significant enough amount of time that they had proved to be trustworthy (and even then, we didn't owe that information to anyone, ever; there are forum friends who I made online 10+ years ago and still talk to who do not know my personal information beyond broad strokes).
There was a time when simply being an avatar with a funny username was enough. And it still is enough, but massive platforms like Facebook and Twitter have been brainwashing us for years to believe that's not the case, under the guise of, "You wouldn't want to be dishonest, would you?" Through these same norms, we were led to believe that anime profile pictures are cringe, that having a fake online name is stupid, that the photos of you having fun at social events have to be taken JUST right otherwise you might imply to others that you're not actually having fun.
And considering how long these platforms have been around now, we have entire generations of children now who have been born and raised on that version of the ZuckMusk web, who have been taught that it "protects them" to express to everyone publicly their age, their school, their workplace, their family members, everything about themselves, because to not do so would be disingenuous.
None of this is to imply that the Internet was "safer" back in the day. I definitely should not have been on the Internet as much as I was when I was 13 in the late 2000's, it definitely did not benefit my brain development or my social skills. But the version of the Internet we currently exist in now is one that's been predicated on the false sense of security - the belief that if you're honest, everyone else has to be, too.
We've always had ways of identifying our safe people - by participating in the communities that we know are designed around our hobbies, our interests, our people. They might be small, they might not be as "cool" as the idea of netting yourself a big following of thousands of people, but they're also a lot safer and more genuine than that idealized following ever could be.
Don't feel pressured to include every bit of information about yourself in your bio. Even on Facebook, there's no rule that says you have to list your workplace, your school, your family members. There's no rule that says you have to list your personality type, queer labels, and neurodivergent disorders in your Twitter bio. There's no rule that you have to "prove" your life is real and fulfilled through the verification of photos, location tagging, and open-book sharing. If you share those photos, it should be because you genuinely want to share them, not because you feel some societal pressure to live up to others' expectations.
And I guarantee you, even your local mutuals on Facebook - your former classmates, family friends, distant relatives, coworkers, etc. - do not actually give that much of a damn about your personal life that they should be owed that much of a look into it on a daily basis. They've got their own shit going on, they literally do not need to know every detail about you.
I know it sounds scary. It also sounds kind of boring, when we've been used to a certain "way" of browsing and participating for years, that if we don't do so, it feels like being in the "out group" and that we're "breaking the rules". But I promise you, after spending over half my life online, those rules do not exist or benefit anyone who wouldn't profit off that information.
If you're wanting to learn how to branch off from major platforms like Facebook and Twitter and/or become more self-sufficient online, here are some guides to navigating the Internet like an old schooler that may help you!
FREE SITE BUILDER:
DIGITAL PIRACY 101:
(also in addition to everything mentioned here ^^^ they neglect to also mention Tor Browser which is a light and free-to-use browser software that allows you to browse anonymously; note that it's similar to a VPN in that it helps hide your identity online, HOWEVER it won't mask you from your ISP quite as effectively as a VPN, and if you sign into personal accounts with Tor, that's still going to obviously out you online lmao but I love using Tor for the odd time when I need to make a sock puppet for something and don't want it linked to my IP! and unlike a VPN, it's free to use!)
LEARN HOW TO USE RSS FEEDS:
People still use these! They're especially helpful for getting updates from your favorite pages and sites directly to your browser WITHOUT having to worry about stupid algorithm bullshit picking and choosing what you see. And many sites DO have RSS support once you know how to find it! (like adding in /rss at the end of a URL! Like this!)
FAKE EMAIL SERVICES:
LEARN HOW TO CODE IN HTML/CSS/JAVASCRIPT (AND MORE!):
DECENTRALIZED SOCIAL MEDIA PLATFORMS:
I hope this helps arm you with some new knowledge in how to navigate the Internet like a Certified Old Person™️(like meeee!) Make your secret alt blogs for besties! Make your formal Facebook accounts that are clean of personal information and present the most neutral, safe-for-work version of yourself and keep the fun stuff to the secret profiles and chat groups that are just for you and friends/family/etc!! It might be "inconvenient" to have multiple accounts for the same purpose, but it's also INCREDIBLY freeing and can make your online experience both safer and more enjoyable.

Being "less" of yourself online does not make you any less you. It is your identity - you do not owe any amount of it to anyone beyond yourself. And in times like these, your identity is your greatest asset. Protect it.
#how to#online safety tips#be safe on the internet y'all#oh and delete those period trackers#just get yourself an old school calendar / notebook for tracking#trust me on this one
480 notes
·
View notes
Text
ReproductiveRights.Gov Information
Copied all of the information off of ReproductiveRights.Gov using the WayBackMachine (<3) seeing as it's gone now. I don't know how much of it will hold in the coming days but it's still important now. If you want to see the website here's a link that works (as of 21/1/25), and if it stops I copied all the info below the cut.
YOUR RIGHTS
Update on Medication Abortion
On June 13, the Supreme Court issued a unanimous decision holding that the plaintiffs in FDA v. Alliance for Hippocratic Medicine lacked standing to challenge FDA’s actions. Mifepristone—which FDA approved as safe and effective more than 20 years ago—remains available under the conditions of use approved by FDA.
The Biden-Harris Administration remains committed to protecting reproductive rights, ensuring women can make their own decisions about their own bodies, and preserving the FDA’s authority to make science-based determinations about what medications are safe and effective. Read statements from President Joe Biden, Attorney General Merrick Garland, and Health and Human Services Secretary Xavier Becerra.
Know Your Rights: Reproductive Health Care
Reproductive health care, including access to birth control and safe and legal abortion care, is an essential part of your health and well-being. While Roe v. Wade was overturned, abortion remains legal in many states, and other reproductive health care services remain protected by law. The U.S. Department of Health and Human Services (HHS) is committed to providing you with accurate and up-to-date information about access to and coverage of reproductive health care and resources. Our goal is to make sure you have appropriate information and support.
Your Reproductive Rights
Below you will find information on your right to access reproductive health care, what your health insurance is required to cover, and where to go if you need health insurance.
Whether you get coverage through your employer, Medicaid, HealthCare.gov, or elsewhere in the private insurance market, most plans cover family planning counseling, birth control, and other preventive services at no additional cost to you. Federal law allows federally-funded health coverage (like Medicaid) to cover abortion in some situations, and some private health insurance plans also cover abortion care.
Your Right to Emergency Care
In light of the Supreme Court's decision to overturn Roe v. Wade, it's more important than ever that you know your rights on receiving emergency medical care.
The Emergency Medical Treatment and Labor Act (EMTALA) requires Medicare-participating hospital emergency departments to offer any person who requests it an appropriate medical screening examination within the capability of the hospital’s emergency department.
If the hospital determines that you have an emergency medical condition, federal law requires the hospital to offer you treatment until your emergency medical condition is stabilized, or an appropriate transfer to another hospital if you need it.
An emergency medical condition includes any medical condition manifesting itself by acute symptoms and that, in the absence of immediate medical attention, could reasonably be expected to place the person’s health in serious jeopardy. Emergency medical conditions involving pregnant patients may include, but are not limited to, ectopic pregnancy, complications of a pregnancy loss, or emergent hypertensive disorders, such as preeclampsia with severe features. In some instances, the treatment reasonably necessary to stabilize a pregnant woman’s emergency medical condition may be an abortion.
These federal rights preempt any directly conflicting state laws or mandates that apply to specific procedures.1
To learn more click here.
1 Please note: pursuant to the injunction in Texas v. Becerra, No. 5:22-CV-185-H (N.D. Tex.), HHS may not enforce the following interpretations contained in the July 11, 2022, CMS guidance (and the corresponding letter sent the same day by HHS Secretary Becerra): (1) the Guidance and Letter’s interpretation that Texas abortion laws are preempted by EMTALA; and (2) the Guidance and Letter’s interpretation of EMTALA — both as to when an abortion is required and EMTALA’s effect on state laws governing abortion — within the State of Texas or against the members of the American Association of Pro Life Obstetricians and Gynecologists (AAPLOG) and the Christian Medical and Dental Association (CMDA).
Your Right to Birth Control Coverage
The Affordable Care Act requires most employer-based health plans and private health insurance plans to cover family planning counseling and to cover certain birth control methods with no out-of-pocket costs to you if you have a prescription. This includes, but is not limited to:
Hormonal methods, like birth control pills and vaginal rings
Implanted devices, like intrauterine devices (IUDs)
Emergency contraception, like Plan B® and ella®
Barrier methods, like diaphragms and sponges
Patient education and counseling
Sterilization procedures
And additional forms of contraceptives approved, granted, or cleared by the Food and Drug Administration (FDA)
To learn more about birth control coverage requirements for different types of health coverage, visit here. To learn more about birth control methods, visit here.
Some birth control methods are available over-the-counter and without a prescription including:
Emergency contraception, like Plan B®
Condoms
Birth control pills, like Opill®
Your Right to Access Medication
The law prohibits pharmacies that receive federal financial assistance from discriminating on the basis of race, color, national origin, sex, age, and disability in their health programs and activities. While pharmacies regularly dispense medications; make determinations regarding the suitability of a prescribed medication for a patient; and advise patients about medications and how to take them, pharmacies that receive federal financial assistance may not discriminate against pharmacy customers on the bases prohibited by statute when they do so. Read the guidance for the nation's retail pharmacies here.
HHS is committed to ensuring that people are able to access health care free from discrimination. If you believe that you or another person’s civil rights have been violated, you can file a complaint with HHS here
Your Right to Access Abortion
As a result of the Supreme Court's decision to overturn Roe v. Wade, access to abortion will depend on the state you live in even more than before.
Mifepristone, in a regimen with misoprostol, has been approved by the Food and Drug Administration (FDA) since 2000 for the termination of early pregnancy, and is safe and effective when used as directed. Mifepristone for medication abortion currently is available for dispensing by mail by certified prescribers or by certified pharmacies for prescriptions issued by certified prescribers, in addition to in-person dispensing in clinics, medical offices, and hospitals.
If you are covered through Medicaid:
While federal Medicaid funds can only cover abortion in the circumstances of rape, incest or if the patient’s life is in danger, there are over a dozen states that provide more comprehensive coverage for abortion using state Medicaid funds. To find out more on state funding of abortions under Medicaid visit this website
If you are covered through your employer, a plan offered through the Affordable Care Act Marketplaces, or elsewhere in the private market:
Coverage will vary by state, employer, and insurance company. In some states, private health insurance plans (including employer coverage) are required or allowed to cover abortion in either all or certain circumstances. Review your plan benefits document to find out whether your plan covers abortion. If you are using a plan where you are not the primary policy holder (for example if you are on a parent’s or spouse’s plan), be mindful that the policy holder may receive documentation from the plan known as an “Explanation of Benefits” that includes information about your care.
If you need help paying for an abortion, abortion funds may be able to provide financial assistance. Information about abortion funds and resources to help are available at AbortionFinder.org
If you need information on your state’s laws or legal help, you may consider this website: AbortionFinder.org
Your Right to Coverage of Other Preventive Health Services
Most employer health plans and health insurance plans must cover certain other preventive health services with no out-of-pocket costs because of the Affordable Care Act. Specifically, they are required to cover women’s preventive health services, including:
An annual well-woman visit to screen your health (which may be completed at a single visit or part of a series of visits over time) including a pap smear, breast exam and regular checkup
Certain counseling and screening services
Breast and cervical cancer screenings
Prenatal care, which is care you would receive while pregnant
Breastfeeding services and supplies
Interpersonal violence screening and counseling (e.g., sexual assault evidence collection exams)
HIV screening and sexually transmitted infection (STI) counseling
If You Do Not Have Health Insurance Coverage
Go to HealthCare.gov and see if you qualify for insurance coverage and financial assistance to make coverage more affordable.
Title X Family Planning Clinics provide a broad range of family planning services and provide preventive health services that benefit reproductive health, such as STI and HIV testing, HIV counseling, and HPV vaccines. Find a Title X Family Planning Clinic near you.
Health centers are community-based organizations that deliver high-quality primary health care services, regardless of your ability to pay. Find a health center near you.
The Ryan White HIV/AIDS Program provides medical care, medications, and essential support services to people with HIV. Find how to get HIV care and services through the Ryan White HIV/AIDS Program near you.
Civil Rights Complaints
The U.S. Department of Health and Human Services’ Office for Civil Rights (OCR) enforces federal civil rights laws that prohibit discrimination in health programs receiving federal financial assistance. If you believe that your or another person’s civil rights or health information privacy rights have been violated, you can file a complaint with HHS here.
Patient Privacy
Federal law prohibits health care providers, health insurance plans, and other entities subject to the HIPAA Privacy Rule from using or sharing your health information to investigate or impose liability on yourself or any person for the mere act of seeking, obtaining, providing, or facilitating lawful reproductive health care.2 To learn more click here.
Understand your rights to protect your private medical information under federal law. If you think your privacy has been violated, click here to learn how to file a complaint.
Guidance on Protecting the Privacy and Security of Your Health Information When Using Your Personal Cell Phone or Tablet may be found here.
Guidance on the HIPAA Privacy Rule and Disclosures of Information Relating to Reproductive Health Care may be found here.
Guidance on the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates may be found here.
Department of Justice Resources
The U.S. Department of Justice is also working to protect access to reproductive health services under federal law. Visit the Justice Department's Reproductive Rights Task Force website for more information.
EMERGENCY CARE
Update on Emergency Medical Care
On June 27, the Supreme Court issued its order in Moyle v. United States, reinstating the protections of the Emergency Medical Treatment and Labor Act (EMTALA) for pregnant women experiencing emergency medical conditions in Idaho. On July 2, the Department of Health and Human Services sent a letter reminding hospitals and provider associations that it is a hospital’s legal duty to offer necessary stabilizing medical treatment, including abortion care (or transfer, if appropriate), to all patients in Medicare-participating hospitals who are found to have an emergency medical condition.1
The Biden-Harris Administration remains committed to protecting reproductive rights and maintains our long-standing position that women have the right to access the emergency medical care they need. Read statements from President Joe Biden, Attorney General Merrick Garland, Health and Human Services Secretary Xavier Becerra, and CMS Administrator Chiquita Brooks-LaSure.
Your Right to Emergency Medical Care
In light of the Supreme Court's decision to overturn Roe v. Wade, it's more important than ever that you know your rights on receiving emergency medical care.
The Emergency Medical Treatment and Labor Act (EMTALA) requires Medicare-participating hospital emergency departments to offer any person who requests it an appropriate medical screening examination within the capability of the hospital’s emergency department.
If the hospital determines that you have an emergency medical condition, federal law requires the hospital to offer you treatment until your emergency medical condition is stabilized, or an appropriate transfer to another hospital if you need it.
An emergency medical condition includes any medical condition manifesting itself by acute symptoms and that, in the absence of immediate medical attention, could reasonably be expected to place the person’s health in serious jeopardy. Emergency medical conditions involving pregnant patients may include, but are not limited to, ectopic pregnancy, complications of a pregnancy loss, or emergent hypertensive disorders, such as preeclampsia with severe features. In some instances, the treatment reasonably necessary to stabilize a pregnant woman’s emergency medical condition may be an abortion.
These federal rights preempt any directly conflicting state laws or mandates that apply to specific procedures.1
1 Please note: pursuant to the injunction in Texas v. Becerra, No. 5:22-CV-185-H (N.D. Tex.), HHS may not enforce the following interpretations contained in the July 11, 2022, CMS guidance (and the corresponding letter sent the same day by HHS Secretary Becerra): (1) the Guidance and Letter’s interpretation that Texas abortion laws are preempted by EMTALA; and (2) the Guidance and Letter’s interpretation of EMTALA — both as to when an abortion is required and EMTALA’s effect on state laws governing abortion — within the State of Texas or against the members of the American Association of Pro Life Obstetricians and Gynecologists (AAPLOG) and the Christian Medical and Dental Association (CMDA).
If you are a health care provider:
For frontline health care providers, EMTALA requires a hospital to provide stabilizing medical treatment to any pregnant patients presenting to the hospital with an emergency medical condition, regardless of any directly conflicting restrictions in the state where you practice.
This means that physicians and other qualified medical personnel are required by federal law to offer stabilizing medical treatment (or an appropriate transfer) to a patient who presents to the emergency department and is found to have an emergency medical condition. This requirement preempts any directly conflicting state law or mandate that might otherwise prohibit such treatment, such as state prohibitions or restrictions on abortions.
Stabilizing treatment could include medical and/or surgical interventions (such as abortion, removal of one or both fallopian tubes, anti-hypertensive therapy, or methotrexate therapy), irrespective of any directly conflicting state laws or mandates that apply to specific procedures.
Health care professionals and institutions with religious or conscience objections to providing abortions do not have to do so. To learn more click here.
If you are a patient:
If you present to the emergency department, you must be offered an appropriate medical screening examination to determine if you have an emergency medical condition. If you do, your health care providers in the emergency department are not permitted to wait until your emergency medical condition deteriorates before they provide stabilizing treatment.
The enforcement of EMTALA is a complaint driven process. If you or someone you know did not receive the emergency stabilizing medical care to which they were entitled, you can file an EMTALA complaint either by contacting your state’s survey agency or by using the Centers for Medicare & Medicaid Services webform.
To contact your state's survey agency, use the tool below.
To file a complaint with the Centers for Medicare & Medicaid Services click here.
Contact Info (Take into account I don't know if these still work)
200 Independence Ave., S.W. Washington, DC 20201
1-877-696-6775
Contact Us
#feminism#womens rights#abortion#pro choice#us politics#lgbtqia#lgbtqia rights#Internet archiving#human rights#reproductive rights#lgbtq+ rights#reproductive health#united states#stay safe#menstruation#menstrual cycle#menstrual health#menstrual period#safety#project 2025#trans rights#usa politics#usa#birth control#safety tips#inauguration#inauguration day#reproductiverights.gov
152 notes
·
View notes
Text
Online Harassment
Online harassment has become an increasingly pervasive issue, affecting individuals across all platforms. From subtle microaggressions to outright threats, harassment takes many forms, each with its own set of consequences. In this post, we'll break down the different types of online harassment, their impact, and what can be done to address them.
Important vocabulary: Misinformation is false or inaccurate information—getting the facts wrong. Disinformation is false information that deliberately intends to mislead—intentionally misstating the facts.
Let's start with what does not count as harassment:
What Doesn't Count as Harassment
Constructive Criticism: Offering feedback aimed at improving someone's work or behavior. For example, a manager providing an employee with feedback on how to improve their performance.
Disagreement or Debate: Engaging in a civil disagreement or discussion on a topic. For example, two colleagues having a heated but respectful debate about a work-related issue.
Enforcing Rules or Policies: Applying rules or policies in a consistent and fair manner. For example, a teacher enforcing classroom rules or a supervisor addressing attendance issues according to company policy.
Isolated Incidents: A single, non-repetitive instance of a comment or action that might be offensive but is not part of a pattern of behavior. For example, a colleague making an offhand remark that could be seen as rude but immediately apologizes.
Perceived Slights or Misunderstandings: Situations where an action or comment is misinterpreted or taken out of context. For example, someone feeling slighted because of a misunderstood joke that wasn’t meant to offend.
Friendly Banter or Jokes (If Mutual): Light-hearted exchanges that both parties understand and accept as non-offensive. For example, friends or close colleagues teasing each other in a way that both find funny and acceptable.
Normal Management Actions: Legitimate management actions taken in the course of business, like performance reviews, promotions, or disciplinary actions. For example, a supervisor assigning tasks based on job performance and business needs.
Cultural Differences: Actions or behaviors rooted in cultural norms that may be misunderstood but are not intended to be offensive. For example, a greeting or gesture that is customary in one culture but may seem strange or awkward in another.
Refusal of Unreasonable Requests: Declining a request that is not reasonable or within someone’s rights to refuse. For example, an employee refusing to work overtime that was not agreed upon in their contract.
Addressing Harassment: Communicating to someone that their behavior is harassing you, when it is true. This can help make the individual aware of the impact of their behavior, seek resolution, validate your experience, set boundaries, and follow legal or organizational procedures. For example, telling a coworker that their repeated comments about your appearance are making you uncomfortable and asking them to stop.
Now let's break down what does count as harassment:
Disinformation and Defamation of Character
Definition:
Disinformation: This refers to false information that is deliberately created and spread to deceive or mislead others. It’s often used to manipulate public opinion, discredit individuals, or cause confusion.
Slander: This involves making false spoken statements that damage someone’s reputation.
Libel: Libel is similar to slander but involves false statements made in a fixed medium, typically written or published online.
Defamation of Character: This is a broader term encompassing both slander and libel, referring to any false statement, whether spoken or written, that harms a person's reputation.
As Harassment:
Disinformation becomes harassment when it is used maliciously to harm an individual's reputation or cause them distress. This might involve spreading false rumors about someone’s actions or beliefs, or fabricating stories to discredit them.
Slander/Libel/Defamation become harassment when false statements are made with the intent to damage someone's character or standing in the community, leading to social, professional, or personal harm. This is particularly damaging when spread online, where false information can quickly reach a wide audience.
Examples:
Disinformation: A group creates and spreads a false narrative that a well-known activist has engaged in illegal activities, with the aim of discrediting their work and damaging their public image. The false information is shared widely across social media platforms, leading others to believe the activist is untrustworthy.
Slander: During a live podcast, a speaker falsely accuses a colleague of being involved in unethical business practices. Even though the accusation is baseless, listeners begin to question the colleague's integrity.
Libel: An online blog publishes an article falsely claiming that a local politician has been accepting bribes. The article spreads rapidly, causing the politician to face public scrutiny and potentially affecting their career.
Impact on the Victim:
Emotional Distress: The victim may experience anxiety, stress, and a sense of powerlessness as their reputation is attacked. This can lead to mental health issues such as depression or anxiety disorders.
Social Isolation: As the false information spreads, the victim may find themselves ostracized by their community, friends, or professional network. They may be unfairly judged or treated differently by others who believe the falsehoods.
Professional Consequences: Defamation can result in job loss, damage to professional relationships, or loss of business opportunities, especially if the victim’s reputation is central to their work.
Financial Damage: The victim might incur legal costs in attempting to clear their name or experience a loss of income due to damaged reputation.
Legal and Ethical Considerations:
Legal Recourse: In many jurisdictions, victims of defamation of character can pursue legal action against the perpetrator. They may sue for damages to compensate for the harm done to their reputation. However, these cases can be complex, requiring proof that the statements were false, made with malicious intent, and caused harm.
Platform Policies: Many social media platforms have guidelines against spreading false information and may take action by removing content or banning users who engage in such activities. However, enforcement can be inconsistent.
Ethical Implications: Even if legal action isn’t taken, spreading false information or engaging in defamation is ethically wrong and can have serious consequences for both the victim and society as a whole. It undermines trust in information sources and can contribute to a culture of misinformation and cynicism.
Disinformation and slander/libel can be deeply damaging, both personally and professionally, and are forms of harassment that are taken seriously both legally and ethically.
Amplifying Disinformation and Slander
Definition:
Amplifying Disinformation: This refers to the act of spreading or sharing deliberately false or misleading information created by someone else. It involves reblogging, retweeting, sharing posts, or forwarding messages that contain disinformation, even if the person amplifying it isn’t the original creator.
Amplifying Slander: This involves spreading spoken false statements about someone that are damaging to their reputation. It often occurs in social interactions, such as sharing gossip or rumors.
Amplifying Libel: This is similar to amplifying slander but involves sharing written or published false information that harms someone’s reputation. It typically occurs on social media, blogs, or other written formats.
As Harassment:
Amplifying Disinformation becomes harassment when it is done with malicious intent or reckless disregard for the truth. By spreading false information, individuals contribute to the harm caused to the victim, including damage to their reputation, emotional distress, and social or professional consequences.
Amplifying Slander/Libel becomes harassment when the person sharing the information knows it is false or harmful but continues to spread it, thereby further damaging the victim’s reputation and standing. Even if the person amplifying the content isn't the original source, they are still participating in and perpetuating the harm.
Examples:
Amplifying Disinformation: After seeing a tweet that deliberately spreads a false narrative about a political figure being involved in a criminal activity, a user retweets it with a comment that suggests they believe it, spreading the disinformation to their followers. The false claim quickly gains traction, causing the political figure significant public backlash.
Amplifying Slander: During a group chat, one person repeats a false rumor they heard about a coworker being unfaithful. Even though the rumor is baseless and was created with malicious intent, it quickly spreads through the workplace, damaging the coworker’s reputation and personal relationships.
Amplifying Libel: A person shares an article on their Facebook page that falsely accuses a local business owner of engaging in fraudulent activities. Although they didn’t write the article, their act of sharing it contributes to the spread of the disinformation, leading to a decline in the business owner’s customer base.
Impact on the Victim:
Increased Harm: The more widely disinformation or slander is shared, the more damage it can cause. As the false information reaches a larger audience, the victim may face increased social ostracization, professional setbacks, or emotional distress.
Difficulty in Correcting the Record: Once disinformation or slander is amplified, it can be challenging for the victim to correct the falsehoods. The spread of false information can take on a life of its own, making it hard for the truth to prevail.
Reputational Damage: The victim may suffer long-term harm to their personal and professional reputation, which can affect their relationships, career, and social standing.
Legal and Ethical Considerations:
Legal Recourse: Amplifying disinformation, slander, or libel can expose the person spreading the false information to legal liability, particularly if they knowingly shared it with the intent to cause harm. In some cases, they may be sued for defamation or held responsible for damages caused by the spread of false information.
Ethical Responsibility: Even if there is no legal liability, those who amplify false information have an ethical responsibility to verify the accuracy of what they share. Spreading disinformation or slander without regard for the truth is unethical and can contribute to a culture of harassment and mistrust.
Platform Policies: Social media platforms often have policies against the spread of disinformation and may take action against users who repeatedly amplify harmful content. This could include warnings, suspensions, or permanent bans.
Amplifying disinformation and slander is a serious issue that can cause significant harm to individuals and communities. Those who engage in this behavior, even if they aren’t the original creators of the content, play a crucial role in perpetuating the damage and may face legal and ethical consequences.
Cyberbullying
Definition:
Cyberbullying involves the use of digital platforms, such as social media, messaging apps, or online forums, to repeatedly target, intimidate, or belittle an individual. It is a form of bullying that occurs online and can include various forms of aggressive behavior.
As Harassment:
Cyberbullying becomes harassment when the behavior is intentional, repeated, and causes significant emotional distress or harm to the victim. It can involve sending threatening or abusive messages, spreading rumors, or using online platforms to isolate or degrade someone.
Examples:
Personal Attacks: A student repeatedly sends mean-spirited and threatening messages to a classmate through a messaging app. These messages include insults, threats of violence, and derogatory comments about the victim’s appearance and personal life.
Public Shaming: A group of people creates a social media page specifically to post embarrassing photos and make derogatory comments about an individual. The posts are shared widely, leading to public humiliation.
Spreading Rumors: An individual creates fake profiles to spread false and harmful rumors about someone, such as accusing them of dishonest or immoral behavior. This false information is shared across multiple platforms, damaging the victim’s reputation.
Impact on the Victim:
Emotional Distress: Victims of cyberbullying may experience feelings of anxiety, depression, and low self-esteem. The constant online attacks can lead to severe emotional distress and a sense of helplessness.
Social Isolation: The victim may withdraw from online and offline social interactions due to fear of further harassment. This isolation can lead to a decline in social support and relationships.
Academic and Professional Impact: For students, cyberbullying can lead to decreased academic performance and school avoidance. For adults, it can affect job performance and professional relationships.
Physical Effects: The stress and anxiety caused by cyberbullying can result in physical symptoms such as headaches, sleep disturbances, and a weakened immune system.
Legal and Ethical Considerations:
Legal Recourse: Many jurisdictions have laws specifically targeting cyberbullying. Legal actions can include restraining orders, criminal charges for harassment or threats, and civil lawsuits for damages. Laws vary by location, so the availability and extent of legal recourse depend on local regulations.
Platform Policies: Social media platforms and online services often have policies against cyberbullying. Users who engage in such behavior may face account suspension, bans, or content removal. Reporting mechanisms are available for victims to report abusive behavior.
Ethical Implications: Cyberbullying is ethically unacceptable as it inflicts unnecessary harm and distress on individuals. It contributes to a toxic online environment and can have severe consequences for victims. Promoting respectful and positive online interactions is crucial for fostering a supportive digital community.
Cyberbullying is a serious issue with far-reaching effects on individuals’ mental health and well-being. Addressing it requires both legal action and ethical responsibility, with efforts focused on prevention, support for victims, and creating a safer online environment.
Doxxing
Definition:
Doxxing (or "doxing") is the act of publicly revealing or publishing private, sensitive, or personal information about an individual without their consent. This information might include details like home addresses, phone numbers, email addresses, and workplace locations. The term "doxx" originates from the word "documents," reflecting the sharing of documents or personal details.
As Harassment:
Doxxing becomes harassment when the intention is to harm, intimidate, or distress the individual whose information is being exposed. It can be used to provoke harassment from others, incite physical threats, or damage the victim's privacy and security.
Examples:
Public Exposure: An individual’s personal details, such as their home address and phone number, are posted on a public forum or social media site after a heated online argument. This leads to unwanted contact and harassment from strangers.
Threatening Behavior: An online user publishes sensitive information about a journalist who has been critical of certain groups. The journalist starts receiving threatening messages and is forced to take security precautions.
Intimidation Tactics: After a disagreement in a gaming community, a player’s real-life address and contact information are shared with the community, leading to in-person threats and harassment.
Impact on the Victim:
Safety and Security Risks: The victim may face threats of physical harm or stalking due to the exposure of their personal information. This can lead to a heightened sense of vulnerability and fear.
Emotional Distress: Victims often experience significant emotional stress, including anxiety, fear, and a sense of invasion of privacy. The knowledge that their personal information is publicly accessible can be deeply unsettling.
Social and Professional Consequences: The victim’s reputation can be damaged, leading to unwanted attention and negative interactions in their personal and professional life. They might experience social ostracism or job-related issues as a result of the doxxing.
Financial Impact: In extreme cases, victims may incur costs related to increased security measures, legal fees, or changes in their contact information.
Legal and Ethical Considerations:
Legal Recourse: Many jurisdictions consider doxxing a criminal offense, particularly if it involves threats, harassment, or incitement to violence. Laws related to privacy, harassment, and cybercrime can be applied to address doxxing. Victims can often seek legal protection or file complaints with law enforcement.
Platform Policies: Social media platforms and online services typically have policies against doxxing. They may take action such as removing the offending content, suspending accounts, or providing support to affected users. However, enforcement can vary.
Ethical Implications: Doxxing is ethically problematic as it involves a deliberate invasion of privacy and can lead to severe consequences for the victim. It violates principles of respect and confidentiality and contributes to a hostile online environment.
Doxxing represents a serious breach of privacy and security, with the potential for significant harm to individuals. Addressing doxxing requires both legal measures and a strong ethical commitment to protecting personal information and respecting others’ privacy.
Stalking
Definition:
Stalking involves persistent and unwanted attention or surveillance of an individual that causes them to feel fear or distress. It can occur through various means, including physical following, digital monitoring, or repeated harassment through communication channels. The intent is often to intimidate or control the victim.
As Harassment:
Stalking becomes harassment when it is done with the intent to cause emotional or psychological harm, invade the victim’s privacy, or exert control over their actions. The behavior is characterized by its repetitive nature and the fear it instills in the victim.
Examples:
Physical Stalking: An individual repeatedly shows up at the victim’s home or workplace, waits for them outside, or follows them in public places despite being asked to stop.
Digital Stalking: A person continually monitors the victim’s online activities, sends frequent and unwanted messages or emails, tracks their location through social media check-ins, and creates fake profiles to gain more access.
Harassing Communication: The stalker sends numerous threatening or intrusive messages, calls, or letters, making the victim feel unsafe and overwhelmed. This can include persistent contact despite clear requests to cease communication.
Impact on the Victim:
Emotional Distress: Victims often experience high levels of anxiety, fear, and paranoia. The constant sense of being watched or followed can lead to severe emotional trauma and mental health issues, such as depression or panic attacks.
Social Isolation: Victims may withdraw from social activities or change their routines to avoid the stalker. They might also feel compelled to move or alter their personal lives significantly to ensure their safety.
Professional Disruption: Stalking can interfere with the victim’s work life, leading to decreased productivity, job dissatisfaction, or even job loss if the stalking occurs at their workplace or affects their professional reputation.
Physical Safety: In severe cases, stalking can lead to physical threats or attacks, putting the victim's safety and well-being at risk. This may necessitate physical security measures or legal protections.
Legal and Ethical Considerations:
Legal Recourse: Many jurisdictions have specific laws against stalking, which can include criminal charges and restraining orders. These laws address both physical and digital stalking behaviors, providing legal avenues for victims to seek protection and hold perpetrators accountable.
Platform Policies: Social media platforms and online services often have policies against stalking and harassment. Victims can report stalking behavior to these platforms, which may take action such as banning the perpetrator or removing harmful content.
Ethical Implications: Stalking is ethically unacceptable as it infringes on an individual’s right to privacy and security. It represents a severe violation of personal boundaries and can cause lasting harm. Ethical behavior involves respecting others' personal space and ensuring that interactions remain consensual and respectful.
Stalking is a grave form of harassment that involves a persistent invasion of privacy and control over the victim’s life. Addressing it requires both legal intervention and ethical commitment to safeguarding individuals' personal safety and well-being.
Hate Speech
Definition:
Hate speech refers to any communication—whether verbal, written, or visual—that disparages or incites violence or hostility against an individual or group based on attributes such as race, religion, ethnicity, sexual orientation, gender identity, or disability. It involves expressions that promote hatred or violence towards people based on these characteristics.
As Harassment:
Hate speech becomes harassment when it is used to target individuals or groups with the intent to demean, intimidate, or incite violence against them. It often creates a hostile environment and contributes to systemic discrimination and exclusion. The impact of hate speech can extend beyond the immediate target to affect entire communities.
Examples:
Social Media Posts: A user posts derogatory comments and slurs about a specific racial or religious group, encouraging others to join in and spread similar messages. These posts can lead to a climate of hostility and exclusion for members of the targeted group.
Online Forums: On a discussion board, members share and amplify content that advocates violence against LGBTQ+ individuals, including graphic threats and dehumanizing rhetoric. This can make LGBTQ+ users feel unsafe and unwelcome on the platform.
Hate Groups: Organized hate groups use websites and social media to recruit and spread propaganda that targets specific ethnic or religious groups. Their messages include misinformation, inflammatory statements, and calls for discriminatory actions.
Impact on the Victim:
Emotional Harm: Victims of hate speech often experience emotional and psychological distress, including feelings of fear, anxiety, and depression. They may feel dehumanized or marginalized.
Social Exclusion: Hate speech can lead to social ostracization and reduced participation in community or public activities. Victims may withdraw from online communities or public spaces to avoid hostility.
Physical Safety: In severe cases, hate speech can incite real-world violence or harassment against individuals or groups, leading to physical harm or threats. It can also contribute to a climate of fear and insecurity.
Community Impact: Hate speech can contribute to broader societal divisions and tensions, fostering environments where prejudice and discrimination are normalized.
Legal and Ethical Considerations:
Legal Recourse: The legality of hate speech varies by jurisdiction. Some countries have specific laws that criminalize hate speech, while others protect freedom of speech more broadly, making legal action challenging. In regions with laws against hate speech, victims may have the option to report incidents to law enforcement or seek legal remedies.
Platform Policies: Many social media platforms have policies prohibiting hate speech and may take action by removing content, suspending accounts, or banning users who engage in such behavior. However, enforcement can be inconsistent, and some platforms may struggle to balance moderation with free speech considerations.
Ethical Implications: Hate speech is widely regarded as unethical because it promotes discrimination and intolerance. It undermines the principles of respect and equality, contributing to societal harm. Addressing hate speech requires a commitment to fostering inclusive and respectful communities, both online and offline.
Hate speech is a serious form of harassment with far-reaching effects on individuals and communities. Recognizing its impact and taking action to prevent and address it is crucial for promoting a more respectful and inclusive digital environment.
Trolling
Definition:
Trolling is the act of making deliberately provocative, offensive, or off-topic comments with the intention of eliciting strong emotional responses from others. It often involves disrupting conversations, creating conflicts, or stirring up controversy for amusement or to upset others.
As Harassment:
Trolling becomes harassment when the intent is to target specific individuals or groups with the purpose of causing emotional distress, confusion, or frustration. This involves consistently targeting someone with offensive or inflammatory comments, aiming to disrupt their online experience or provoke a reaction.
Examples:
Social Media Comments: A user repeatedly posts inflammatory or offensive comments on posts related to sensitive topics like mental health or personal identity. Their goal is to provoke arguments, upset the original poster, and attract attention to their own posts.
Forum Disruption: On an online forum focused on a specific hobby or interest, a troll deliberately posts off-topic or derogatory comments to derail discussions, causing frustration and confusion among regular members.
Live Stream Interference: During a live stream, a troll bombards the chat with spam, offensive messages, and provocative statements to distract the streamer and viewers, disrupting the content and conversation.
Impact on the Victim:
Emotional Distress: Victims may experience frustration, anger, and stress as a result of trolling. The constant need to address or ignore disruptive comments can be mentally exhausting.
Disruption of Conversations: Trolling can derail meaningful discussions and create a hostile environment, making it difficult for others to engage in productive or enjoyable conversations.
Reduced Participation: The presence of trolls can lead to decreased participation in online communities, as users may avoid engaging with platforms or topics where they have previously been targeted.
Psychological Impact: Persistent trolling can contribute to anxiety, depression, or feelings of helplessness, particularly if the troll’s comments are deeply personal or offensive.
Legal and Ethical Considerations:
Legal Recourse: The legal response to trolling varies by jurisdiction and the nature of the trolling. While many forms of trolling do not constitute a criminal offense, behaviors that involve threats, harassment, or incitement to violence may be actionable under cybercrime or harassment laws.
Platform Policies: Most social media and online platforms have community guidelines that address trolling. They may take action such as removing offending content, suspending accounts, or banning users who engage in trolling behavior. Enforcement can vary, and some platforms struggle to effectively manage trolling.
Ethical Implications: Trolling is generally considered unethical because it aims to disrupt, harm, or manipulate others for personal amusement. It undermines respectful and constructive communication and can contribute to a negative online culture. Addressing trolling involves fostering a more respectful online environment and encouraging positive interactions.
Trolling is a form of online harassment that can have significant emotional and social impacts on individuals and communities. Recognizing and addressing trolling behavior is important for maintaining healthy and respectful online interactions.
Impersonation
Definition:
Impersonation involves creating or using a fake identity to deceive others into believing that you are someone else. This can include pretending to be a public figure, a private individual, or a professional entity. The goal is often to mislead or manipulate others for various purposes, including personal gain, harassment, or deception.
As Harassment:
Impersonation becomes harassment when it is used to target individuals with the intention of causing harm, spreading false information, or engaging in malicious activities. This might involve creating fake profiles or accounts to misrepresent someone or to exploit their identity for harmful purposes.
Examples:
Social Media Accounts: A user creates a fake social media profile pretending to be a well-known celebrity or public figure, using it to post misleading or harmful content that could damage the real person’s reputation.
Email Scams: An individual sends emails from an address that looks like it belongs to a trusted authority or organization (e.g., a company executive or a government official) to deceive recipients into providing sensitive information or making financial transactions.
Online Fraud: Someone impersonates a person in an online dating profile, using fake photos and personal details to manipulate or exploit other users emotionally or financially.
Impact on the Victim:
Reputation Damage: The victim may suffer from reputational harm if false or misleading information is spread using their identity, leading to confusion, mistrust, or negative perceptions among their audience or associates.
Emotional Distress: Being impersonated can lead to significant emotional distress, including anxiety, embarrassment, and frustration. The victim may feel violated and powerless, particularly if the impersonation is done in a malicious or humiliating way.
Professional Consequences: For public figures, professionals, or businesses, impersonation can lead to professional repercussions, including loss of business opportunities, legal issues, or damage to professional relationships.
Financial Impact: If impersonation involves fraud, the victim may suffer financial losses or be involved in lengthy and costly legal battles to address the situation.
Legal and Ethical Considerations:
Legal Recourse: Many jurisdictions have laws against impersonation, including identity theft, fraud, and misrepresentation. Victims may have legal avenues to pursue, such as filing complaints with law enforcement or taking civil action to seek damages. The specifics of legal recourse vary depending on local laws and the nature of the impersonation.
Platform Policies: Social media and online platforms often have policies against impersonation. They may take actions such as verifying identities, removing fake accounts, or suspending users who engage in impersonation. Effective enforcement of these policies can be challenging, especially given the scale of online interactions.
Ethical Implications: Impersonation is generally considered unethical because it involves deception and manipulation. It undermines trust and can have serious consequences for individuals and organizations. Ethical behavior online includes respecting others' identities and avoiding deceptive practices.
Impersonation can be a serious form of online harassment with far-reaching effects on both individuals and organizations. Addressing and preventing impersonation involves understanding its impacts, pursuing legal remedies when necessary, and fostering ethical online behavior.
Spamming
Definition:
Spamming refers to the repeated, unsolicited sending of messages or content, often with the intent to overwhelm, disrupt communication, or promote something, usually in a commercial context. It can occur through email, social media, messaging platforms, or other digital channels.
As Harassment:
Spamming becomes harassment when it is used to intentionally annoy, intimidate, or overwhelm an individual or organization. This might involve flooding someone's inbox with unwanted messages, bombarding a social media profile with repetitive or abusive comments, or inundating forums with irrelevant or harmful content. The goal is often to disrupt normal communication or to cause distress.
Examples:
Email Spamming: A user receives hundreds of unsolicited promotional emails, some of which contain malicious links or phishing attempts. The volume of spam clutters their inbox and makes it difficult to manage legitimate communications.
Social Media Spamming: An individual’s social media account is flooded with repetitive comments or messages from the same user or group. These comments might be abusive, irrelevant, or aimed at disrupting the user’s ability to engage with others on the platform.
Forum Spamming: A user continuously posts irrelevant or disruptive messages in online forums or discussion boards, often to derail conversations, promote products, or harass other users.
Impact on the Victim:
Overwhelm and Stress: The victim may feel overwhelmed by the sheer volume of messages or content, leading to stress and frustration. Managing or filtering through spam can be time-consuming and mentally taxing.
Disruption of Communication: Spam can disrupt normal communication, making it difficult for the victim to focus on important messages or tasks. It can also crowd out legitimate content or conversations, reducing the effectiveness of communication platforms.
Privacy and Security Risks: Some spam messages may contain malicious links or attachments that can compromise the victim’s privacy or security, leading to potential data breaches or identity theft.
Financial Impact: For businesses, spamming can lead to loss of productivity, increased costs related to managing or mitigating spam, and potential damage to their reputation if customers are affected.
Legal and Ethical Considerations:
Legal Recourse: Many jurisdictions have laws against spamming, especially when it involves malicious intent or financial fraud. For instance, the CAN-SPAM Act in the U.S. regulates commercial email and provides guidelines for managing spam. Victims of spam may also seek legal remedies for damages or file complaints with relevant authorities.
Platform Policies: Most digital platforms and services have policies against spamming. Violations can result in penalties such as account suspension, banning, or removal of the offending content.
Ethical Implications: Spamming is considered unethical as it disregards the recipient’s consent and aims to exploit or harass individuals. It disrupts normal communication practices and can contribute to a negative online experience for users.
Spamming, when used maliciously, can have significant negative impacts on individuals and organizations, and is addressed by legal frameworks and platform policies to protect users and maintain the integrity of digital communication.
Making Threats
Definition:
Threats to Harm Others: These are statements or actions that express an intention to cause physical harm or violence to another person. These threats can be explicit (directly stating the intention to harm) or implicit (suggesting harm or intimidation).
Threats to Harm Oneself: These are statements or actions that express a desire or intention to self-harm or commit suicide. Such threats may be made in distressing contexts and can indicate serious emotional or psychological issues.
As Harassment:
Threats to Harm Others: When threats are made to harm others, they can be a form of harassment if the intent is to intimidate, control, or manipulate the target. This can involve direct threats or veiled warnings intended to cause fear or distress. The impact can be significant, causing emotional and psychological trauma, and creating a sense of insecurity or danger for the victim.
Threats to Harm Oneself: Threats of self-harm can also be a form of harassment if they are used manipulatively or to provoke a response from others. In some cases, individuals may use threats of self-harm to exert control or to gain attention, which can create distress and concern among those who are aware of the threats.
Examples:
Threats to Harm Others:
Direct Threat: A user posts a message on social media stating, "I will come to your house and hurt you if you don’t stop talking about me." This explicit threat aims to intimidate the recipient.
Implicit Threat: An individual leaves a comment on a public forum suggesting, "People like you should be careful about what they say," followed by a vague reference to "consequences." This implies potential harm without explicit details.
Threats to Harm Oneself:
Direct Threat: A user posts on a social media platform saying, "I’m going to end my life tonight. I don’t see any way out." This expresses a clear intention to self-harm.
Implicit Threat: An individual frequently posts messages or updates about feeling hopeless and discusses self-destructive thoughts without explicitly stating their intent to self-harm, but hinting at severe distress.
Impact on the Victim:
Emotional and Psychological Trauma: For threats to harm others, victims may experience fear, anxiety, and a sense of vulnerability. The threat of violence can lead to psychological stress and trauma.
Behavioral Changes: Victims of threats may change their behavior to avoid potential harm, such as avoiding certain places or people, or taking additional precautions for their safety.
Distress and Concern: For threats of self-harm, friends, family, and others may experience significant emotional distress and concern, feeling helpless or anxious about the individual’s well-being.
Intervention and Support: Threats of self-harm often prompt intervention from mental health professionals or emergency services, which can be disruptive and may lead to involuntary treatment or hospitalization for the individual making the threats.
Legal and Ethical Considerations:
Legal Recourse:
Threats to Harm Others: Making threats of violence can be illegal in many jurisdictions. Victims can report these threats to law enforcement, who may investigate and take legal action if necessary. Criminal charges can be brought against individuals making credible threats of harm.
Threats to Harm Oneself: While threats of self-harm are not typically illegal, they often prompt intervention by mental health professionals and emergency services to ensure the individual’s safety. In some cases, these threats may lead to involuntary hospitalization or treatment if the person is deemed a danger to themselves.
Platform Policies: Many online platforms have policies against threats of violence and self-harm. Content that violates these policies may be removed, and users making such threats may be banned or suspended. Platforms often have mechanisms for reporting and addressing these issues.
Ethical Implications: Both types of threats raise serious ethical concerns. Making threats to harm others is fundamentally unethical and can have legal consequences. Threats of self-harm require sensitive handling, as they indicate significant distress and necessitate a compassionate response to address the underlying issues and provide appropriate support.
Threats, whether directed towards others or oneself, are serious and can have profound impacts on all involved. They are addressed through legal channels, platform policies, and ethical guidelines to protect individuals and provide necessary support.
Sexual Harassment
Definition:
Sexual Harassment: This is unwanted and unwelcome behavior of a sexual nature that creates a hostile or intimidating environment. It can occur in various forms, including physical, verbal, or non-verbal conduct. Sexual harassment is often characterized by a power imbalance and can occur in both professional and personal contexts.
As Harassment:
Sexual Harassment becomes harassment when it involves making someone feel uncomfortable, threatened, or demeaned through sexual advances, comments, or behavior. This includes behavior that interferes with the victim’s ability to participate in work or social environments and can create an atmosphere of intimidation or hostility.
Examples:
Verbal Harassment: Making inappropriate or suggestive comments, jokes, or propositions about someone's body or sexual activities. For instance, repeatedly commenting on a colleague’s appearance or making unwelcome advances.
Physical Harassment: Unwanted physical contact, such as touching, groping, or brushing up against someone in a manner that makes them uncomfortable. This can also include gestures or displays of sexually explicit material.
Non-Verbal Harassment: Sending sexually suggestive messages, images, or using body language that implies sexual interest or intent. This includes persistent staring or creating an atmosphere with sexually explicit material.
Online Harassment: Sending unsolicited explicit messages or images through social media, email, or messaging platforms. This can also involve tagging someone in inappropriate content or making unwanted advances through digital communication.
Impact on the Victim:
Emotional Distress: Victims may experience a range of emotional responses, including anxiety, depression, and fear. The harassment can lead to a diminished sense of safety and self-worth.
Professional Consequences: In a workplace setting, sexual harassment can affect job performance, career progression, and workplace relationships. Victims may face challenges in their professional environment, such as being passed over for promotions or experiencing isolation from colleagues.
Social and Personal Impact: Harassment can lead to a loss of confidence, social withdrawal, and strained personal relationships. Victims might avoid certain places or situations to escape harassment or its reminders.
Physical Health: The stress and emotional impact of harassment can manifest physically, leading to issues such as sleep disturbances, headaches, or other stress-related health problems.
Legal and Ethical Considerations:
Legal Recourse: Many jurisdictions have laws and regulations against sexual harassment. Victims may have legal avenues to pursue claims, such as filing complaints with the Equal Employment Opportunity Commission (EEOC) in the U.S. or similar bodies in other countries. Legal action can result in compensation for damages, changes in workplace policies, or other remedies.
Platform Policies: Online platforms and workplaces typically have policies prohibiting sexual harassment. Violations can lead to account suspension, removal of content, or disciplinary actions against offenders. Reporting mechanisms are often available to address harassment claims.
Ethical Implications: Sexual harassment is a severe violation of ethical standards and personal boundaries. It undermines the dignity and rights of individuals and perpetuates a culture of inequality and fear. Ethical responses involve creating safe and respectful environments, actively addressing and preventing harassment, and supporting victims.
Sexual harassment is a serious issue with significant legal, ethical, and personal implications. Addressing it effectively requires a combination of legal action, supportive policies, and a commitment to creating respectful and safe environments for all individuals.
Understanding and addressing online harassment is crucial for fostering a safer and more respectful digital environment. From the deliberate spread of disinformation and defamation to the invasive impact of spamming and threats, each form of harassment has its own set of consequences that can deeply affect individuals and communities. Sexual harassment, in particular, represents a severe violation of personal dignity and can lead to significant emotional and professional harm.
By recognizing the different manifestations of harassment, from slander and libel to online threats and unwanted sexual advances, we can better equip ourselves to combat these issues effectively. Legal frameworks, platform policies, and ethical practices all play essential roles in addressing and mitigating harassment.
It is our collective responsibility to create and maintain environments—both online and offline—where individuals feel safe, respected, and heard. By staying informed, supporting victims, and holding perpetrators accountable, we can contribute to a more just and compassionate society. Everyone deserves to be treated with dignity and respect, and it is up to all of us to uphold these values in every interaction.
#alex talks#alex explains things#anti harassment#online safety#internet tips#internet things#internet safety#internet#online#online harassment#stop cyber bullying#cyber bullying#disinformation#defamation#doxxing#online stalking#impersonation#how the fuck do i tag this#yeah#safety#important#information#informative post#important information
195 notes
·
View notes
Text
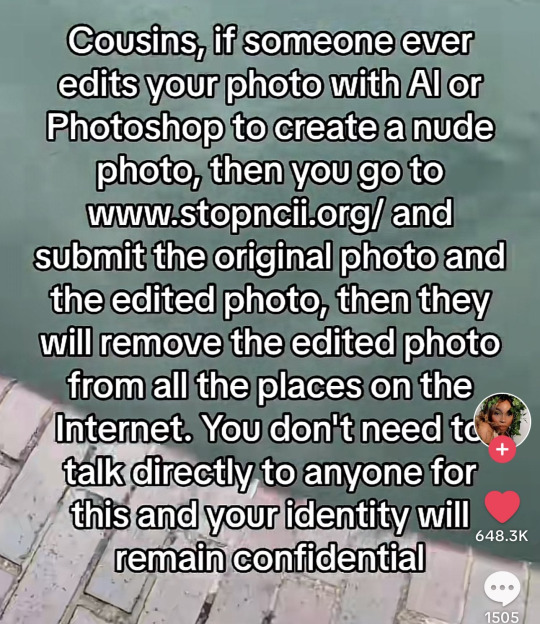
"Stopncii.org is a free tool designed to support victims of Non-Consensual Intimate Image (NCII) abuse."
"Revenge Porn Helpline is a UK service supporting adults (aged 18+) who are experiencing intimate image abuse, also known as, revenge porn."
"Take It Down (ncmec.org) is for people who have images or videos of themselves nude, partially nude, or in sexually explicit situations taken when they were under the age of 18 that they believe have been or will be shared online."
#important information#image desc in alt text#informative#stop ai#anti ai#safety#internet safety#exploitation#tell your friends#stay informed#the internet#internet privacy#online safety#stay safe#important#openai#tiktok screenshots#tiktok#life tips#ysk#you should know#described#alt text#alt text provided#alt text added#alt text in image#alt text described#alt text included#id in alt text
729 notes
·
View notes
Text
dear minors on tumblr
hello everyone and welcome to another rant about internet safety and boundaries.
Since I’ve gotten many messages from minors because I’m one of the few blogs in this community that allow them. It’s my responsibility as a 20 year old interacting with teens and kids to give tips for when they interact with adults.
age: Never ever lie about your age, it puts both parties in danger. It’s important they know your age so they can adapt to your age group.
If an adult ever lies about their age don’t contact them again, and that’s period.
lying or misleading about age is not only dangerous but also illegal. So you can avoid many dangers if you’re honest.
Jokes:
as a minor you can joke about whatever you want but remember if an adult engages in sexual jokes with you even if your the one what started them. It’s a red flag, an adult has no business talking sex or sexuality with a minor.
Even if it’s a joke it still shows a lot about the person if they make resist, ableist, discriminating and disrespectful jokes or comments. If they always and can only use dark humor to be funny and nothing else. It’s a red flag as well.
questions:
Don’t ever give them your phone number, full name, address. Don’t ever send pictures of yourself, your house, school or things that can identify you. Even if it’s a picture of your tummy or you in your school uniform. It’s a red flag if someone ever asks you about anything this personal.
General:
don’t answer to personal questions
set boundaries about what you can talk about
tell your parents and friends who you interact with online
take a few breaks and reflect on how they make you feel
if they ever lie about something, personality, interests, hobbies to connect more with you it’s a red flag
and finally my dear kids before I let you go,
a no is a complete sentence
a block is an answer
speaking up is very brave
setting boundaries are mature
and finally you don’t need to grow up faster, enjoy your 18 years of childhood and teenage fun
#tickle thoughts#answered#ask answered#sfw tickling community#tword community#asks#ler#heds#lee#tword content#kids toys#children#child#parenting#online#online safety#tips#minors dni#minors do not interact#minors will be blocked#minors and men dni#minors don't look#internet privacy#internet safety#minors allowed
122 notes
·
View notes
Text

Important Internet Safety PSA!
This post is specifically targeted at minors.
Hi kiddos! I'm making this post to remind all regressors on here that they should be extra sure to stay safe online!
For a while now, I've seen minors posting things that are not safe 🙅 but anyone can benefit from following these tips. Especially those who regress, and can be mentally children at times, should be extra cautious online.
Warning! : mentions of potentially triggering topics in relation to online safety, stranger danger, etc. Please only read when big, not regressed!
Read Under The Cut ⬇️

Things Minors Should Not Share Online:
1) Your Real Name.
Never share your full name online. Your first name is less dangerous, but if you can, I would still go by pseudonym (Ex: Sunny, Lambie, Tiny, Bear, Baby Bat, etc.) or fake name. Your name may feel innocent, but personal information is very important.
2) Your Location.
This one feels obvious, but more people do it than you think! Yes, I mean do not share your address...but I also mean: Do not share what school you attend. Do not share what state you live in. Do not share what city you live in.
3) Your Age.
Do not tell anyone that you are a minor. People online should not know that you are a child. As a child, you are especially vulnerable to being targeted by people online.
Age regressors in general are pretty commonly targeted by p/redators online, but stating you're a minor won't make you more safe from them - it will make those predators more likely to want to message you.
Remember to also not share your birthday! Your exact birth date is personal info. If you wish to share birthday stories, gifts, etc, or tell people of your birthday, be broad. Mention it's your birthday month at the beginning/end of the month :) rather than the exact day.
4) Your Triggers.
People online should not know what specific things trigger you. This information can be used against you. Yes, this includes information in DNIs.
If you must have a DNI, be generic.
"DNI if you post kink, blood, eating disorders, transphobia, these things trigger me." is too much personal information. This is just a list of things that trigger you. People online should NOT know this information. ❌ ❌
❤️ Generic DNI examples:
"DNI if your blog is unsafe for children"
"DNI if you post N/S/F/W content."
"DNI if your blog is k/i/n/k, c/g/l, or NSFW." ❤️
Remember to use your block button liberally, for anyone who makes you uncomfortable.
5) Photos of yourself.
There are multiple reasons why posting photos of yourself, as a minor, may not be a good idea.
First, regression is very stigmatized. Choosing to connect your face to something so stigmatized is a very big decision, one that can be difficult to make at a young age. The internet is forever, and it's very important to consider how you might feel about these photos later in life.
Second, regression is SFW, but p/redators don't care. While the pictures of you with a paci, or you in a diaper may be completely innocent and nonsexual, bad people can still access them. This doesn't mean you can never post photos - but waiting until you're old enough to really understand the risks is a good idea.
In general, photos of your regression can be unsafe but...you can share photos without you in them! Pictures of your snacks, or a toy can be nice to share. Just make sure there's no personal, or identifying info in your pictures :) and then show off your cute drawings or toys.

Personal information is very precious. Be very careful with who you share it with! If you are an adult, you have the knowledge to make the decision on whether or not you think it's a good idea to share this information. But if you are a child, you're usually not old enough to understand what sharing personal info can mean.
I know a lot of these may feel really restricting. You might think "isn't that a little much?" and yes, they can be a lot to ask. But staying safe is super important.
It's important for you kiddos to remember that most of you are in categories that can make you extra vulnerable. Being minors, being neurodivergent, being queer, having faced past trauma, being an age regressor...are all things that can make you especially vulnerable.
If you decide to share these things anyway, I hope I've encouraged you to try to do so sparingly. Maybe you can share some of these, but decide to make others private.
Stay safe kiddos!


#internet#internet safety#agere#agere safety#age regression#agere caregiver#agere tips#agere help#safety#sfw interaction only
129 notes
·
View notes
Text
The scariest people are never the ones who immediately creep you out. They are the ones who are expert at seeming trustworthy. You may already know someone like this, and not realize it yet.
Be it on the Internet or in real life, it is important to be cautious around anyone who starts suggesting things you aren't comfortable with or asking for information that is none of their business.
Things no one taught you about the Internet!
Starting with minors (17 and under in the US)
DON'T POST YOUR AGE! Or age rage. Or birth year. Do not write 'minor' in your bio. This is probably the most common and most dangerous mistake! You will be actively targeted.
Don't pretend you're an adult!!! If a creep sees that you wrote 18 or older but act like a minor, they will do all the same tricks to become your friend, and know they have a legal loophole because they can always claim they didn't know! This is almost more dangerous than just saying "I'm a kid, come hurt me"
Instead just don't say anything! Don't post it anywhere, and don't add it to your bio. If someone asks you for your age, just block them.
Don't share your name or nickname! Even if you don't share your last name, they can pick up enough details about you over time that even a first name is enough to find you.
Instead, use a totally different name! Something like Eli_Bloodsucker is way more fun, just don't use it if your real name or even a real life nickname is Eli, Eliza, Ellie, or anything else even remotely similar!
Don't talk to anyone directly! Be it in comments or asks or in direct messages, they're all dangerous. It doesn't matter if they say they are a minor or an adult. If you can't see their face, don't talk to them. If you find a real life friend you didn't know had an account, don't talk to them. That might not be your friend. You can text your friend directly or talk to them in real life about it later.
Instead, just spread positivity purely form likes and reblogs. Pretend the comment and chat buttons are lava or acid or something. Don't touch them.
Don't share ANYTHING about where you live. Not even country. Don't tell someone about how it's always humid where you live or that there's a storm where you are.
Instead, you can share about weather vaguely later. For example, "a few months ago it snowed and I slipped on ice."
Don't, talk about an activity that would even hint that you are a minor. Don't talk about school, don't talk about piano lessons, don't talk about martial arts class, or football practice. Don't mention growing out of your clothes. Don't mention how your mom grounded you. Don't talk about your little brother barging into your room.
Instead, before posting any stories from your real life, ask yourself if this could also easily apply to someone in their 20s living with roommates instead of family members and working a full-time job. If the answer is yes, then post it, if not, don't. (Good example: I burnt my eggs but I didn't want to waste it so I still ate it. Bad example: My dad made me eggs this morning even though I hate them, and made me eat them.)
Don't post or share pictures or videos of yourself online. Someone can either use it to find you or steal them to lure your friends or other people your age into trusting them.
Instead, find a picture of a duck with a mustache online, and make that you're profile picture. Find a map of Australia and post that as your "outfit check". Way more fun.
Do not trust the person who reblogged this. Do not trust the original poster. Creeps will sometimes post about Internet safety as part of their plan to make you trust them.
So how can you tell who to trust, and who not to? You can't! That's the Internet. Better to play it safe than to risk your actual life over a post or a trend
Adult Internet safety:
Idk, it's your life. You know the consequences you might face. Make your own damn decisions. If your dad can't tell you what to do, then I sure can't.
Oh, and don't interact with people you know, or think, are kids. There is help available for those who are tempted to do this. Don't go down that path. There are resources, there are other ways. Having thoughts isn't a crime, acting on them is. PLEASE talk to a licensed professional.
#tw intrusive thoughts#cw intrusive thoughts#tw pedophila mention#cw pedophila mention#internet safety#safety tips#online safety#online friends#internet friends#friends in my phone#tumblr friends#friends on tumblr#poppy playtime#trolls poppy#trolls velvet#trolls veneer#trolls branch#my litte pony friendship is magic#my little pony#my little pony rarity#mlp rarity#daniel tiger#peppa pig#cocomelon#baby shark#bluey heeler#bingo heeler#bluey and bingo#paw patrol#mickey mouse clubhouse
58 notes
·
View notes
Text
Free: Snort
No, not related to pigs or their snouts (though they do use a pig’s face as their mascot). 🤣🤣🤣 The tool for your computer, by Cisco, is a tool for analysing and detecting intrusions on private home networks as well as for business use. Yes, it is free!! 😁
Something to protect you and your data during the holidays and the new year fast approaching. Keep safe my fellow readers!!
#bookmark#bookmarks#link#links#free#free software#internet safety#online safety#online safety tips#internet safety tips#how to stay safe online#BeingSafeOnline#Snort.org#Cisco.com
1 note
·
View note
Text
Hey everyone, I hope all of you are doing well. I have a bit of a PSA regarding Internet safety and I am directing this more towards the minors that are on here so please read this if you have a moment.
I see many of you are quite comfortable with this platform and you state your age and that you're a minor in hopes of keeping the weirdos away. Totally get that. However, I think you're still endangering yourselves that way because maybe people like that won't interact with you but they may still spy your blog because you have personal conversations on there. You wouldn't necessarily be able to block or report them since you don't know that they are doing this. Of course, if you do have a case where they do interact with you inappropriately, block and report IMMEDIATELY.
I think that we should stick to redacting ages and names (I sincerely hope most if not all of you are using fake names to protect your identities) because there was a reason parents used to say don't mention your age, name, etc., online. And while I get your blogs are personal, keep your conversations in the messages with your friends; reblogs give more insight about you than you might realize. I'm happy you are comfortable and feel safe on Tumblr but you can never be too precautious, especially with the Internet nowadays. While I hope many adults on here are for protecting you, like myself, not everyone is. You have to be careful. YOU NEVER KNOW WHO IS WATCHING.
Same goes with saying where you're from. DON'T DO IT. It can be very telling for any amount of dangers. I also encourage you to stick to nonpersonal topics if possible. It can get tempting but do you truly know that you'll ever meet this person in real life and be who they say they are? Not all the time. So, I end this off by stating again; be alert, be wary, avoid, block, report, BE SAFE. There's already so many that have succumbed by being innocent naïve lambs.
Like, share, reblog, whatever. Make this more known. Please, I beg you; be on your guard and heed warnings when there may be blaring alarms in your head.
Have a good day.
35 notes
·
View notes
Text
Online Safety Tips
As someone who has been in agere communities online for 8+ years across various platforms, I have noticed many safety concerns and scary situations. Unfortunately, predators tend to prey on vulnerable people and communities like ours. I have noticed many patterns and want to make suggestions on how to stay safe based on what I have seen.
For everyone:
Do not look for a caregiver online, and especially do not announce that you are looking for a caregiver. This will attract predators and almost never attracts caregivers. If you are looking for a cg, do it irl with someone you have established trust with first.
Do not tell people details that make you vulnerable, such as specific information about your trauma and triggers.
Be careful about what media you consume while regressed. Social media can be a dangerous place overall, you never know what you will see and unfortunately, people often do not respect boundaries and post nsfw content where they shouldn't
Do not tell people where you live.
For under 18:
Do not talk to people you don't know online, not even platonically. Block anyone 18+ who tries to talk to you.
Do not ask for or accept gifts from strangers.
Do not share your age or that you are a minor.
Do not share that you live with your parents, and especially do not complain about your parents. This highly suggests you are a vulnerable minor and predators might pose as trying to "rescue" or "help" you.
Do not post photos with your face or other identifying information.
Do not use your real name, especially your full name.
Do not engage with nsfw content at all.
For over 18:
Highly consider not showing your face or identifying information online. Do research and realize what this means if you want to. A youtuber I follow was posted on fox news without her consent. "Cringe content" creators and other bullies could get ahold of your content and show it to unsafe people. Ultimately, it is your choice as an informed adult, but be careful.
Highly consider not using your real name, especially full name for the same reasons.
Be very careful in talking to strangers online. Even if they seem kind, you don't know their intentions.
Do not talk to minors privately, even platonically. Remember, even if you regress, you are still an adult.
If you are uncomfortable interacting with minors in a public setting, such as comments, make sure to make that clear in your blog and block those who do not respect this boundary.
Do not cross tag with any nsfw content, and keep nsfw content off agere blogs and accounts. Minors and regressed people could see it.
If you are on the verge of barely being 18+, say 18-25, be warry of people much older trying to talk to you. Predators will often go for the minimum legal age.
I didn't want to elaborate on why for every single point, because this post is long enough as is, but if you have any questions, doubts, or want to know why for specific points, feel free to ask in the comments. I know some of these tips seem strict, but they are based on true things I have seen, often multiple times. I can also give vague stories of what has happened to people who haven't followed these tips. Stay safe friends!
10 notes
·
View notes
Text
Guys begging you
Do not click on links you don’t know
Don’t play link roulette
One of my friends almost got fucking hacked this morning bc they’re a dumbass
Don’t click on links don’t put your email into sites that look shady
I know there’s not any like
Way to stop a hacker that *really* wants what you got
But do the bare minimum and don’t be dumb with your information
56 notes
·
View notes
Text
im thinking about making a short post about internet safety for all the digital angels out there. just general stuffs they aint saying out loud anymore . . expect something later today mhm mhm
#i think internet safety n tips helps us use th online world better . .#but what do i know#blah blah blah
7 notes
·
View notes
Text

short answer: yeah its fine
long answer: well, youre already giving them your address, so theres that. but i dont use my real name for anything online/use a pseudonym for shipping. i have paranoid psychosis though.
longest answer: use a vpn set outside the states, use protonmail/a month-long minuteinbox address/other throwaway email, download an alternate internet browser (maybe even tor!) for the purchase itself, buy with crypto, clear your history and cookiies, uninstall the new browser and youll be fine. this is what i would say is the safest method outside of like, microwaving your hard drive after, but again:
short answer: yeah its fine.
#.din#.pic#.ask#<- as in it was in my inbox but i am a kind and generous dictator and so i permit my subjects to maintain anonymity#im not a good person to ask internet safety tips of because i an and will recommend that you microwave your hard drive after
6 notes
·
View notes