#IoT Identity and Access Management
Explore tagged Tumblr posts
Text
Securing the Future: The Rise of IoT Identity and Access Management
In a world increasingly reliant on connected technologies, the Internet of Things (IoT) has emerged as a transformative force, reshaping industries, economies, and daily life. From smart homes and wearable devices to industrial automation and connected healthcare, IoT is creating a hyper-connected digital environment. With this transformation comes a significant challenge: managing and securing…

View On WordPress
#business#Business Intelligence#cybersecurity#IAM solutions#Identity Access Management#identity and access management#identity and access management tools#Identity Management#identity management for internet of things#identity management solutions#identity management system#Information Technology#IoT IAM#IoT Identity and Access Management#iot identity management#IoT Security#technology
0 notes
Text
Iot Identity and Access Management (IAM) Market Trends, Top Vendors and Growth Prospects
According to a new report published by Allied Market Research, titled, “Iot Identity And Access Management (Iam) Market,” The iot identity and access management market size was valued at $4.9 billion in 2021, and is estimated to reach $47.2 billion by 2031, growing at a CAGR of 25.4% from 2022 to 2031.
Identity and access management (IAM) is the discipline that enables right individuals to access right resources at the right times for the right reasons. IoT devices are focused on connecting things, people, tools, and applications, and IoT identity access management provides end-to-end encryption, overload detection, and unauthorized access removal to help build strong security features.

Rapid digitization toward business operations and an increase in integration of IAM with IoT devices aided in propelling the growth of global IoT IAM market. Moreover, cultural shift from traditional IAM to IoT IAM and increasing spending on cyber security during the period has positively impacted IoT IAM industry. However, high cost associated with implementation and maintenance of IoT identity and access management (IAM) solution and increase in security & privacy concerns is anticipated to hamper the IoT IAM market during the forecast period. On the contrary, adoption of Bring your Own Identity (BYOI) approach is expected to offer remunerative opportunities for the expansion of the Iot Identity And Access Management market forecast.
On the basis of security type, the network security segment dominated the overall Iot Identity And Access Management Market Share in 2021 and is expected to continue this trend during the forecast period. This is attributed to the increase in cyber-attacks on networks due to increase in internet penetration and connected devices. However, the cloud security segment is expected to witness the highest growth owing to increase in adoption of cloud-based security solutions, rising demand for cloud-based services.
Region wise, the Iot Identity And Access Management Market analysis was dominated by North America in 2021, and is expected to retain its position during the forecast period, owing to its higher expenditure on technological solutions for better security. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to the growth in number of startups and the expanding infrastructure in the region, which is expected to fuel the growth of the IoT IAM industry in the region during the forecast period.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/31995
The IoT Identity And Access Management Market is expected to grow rapidly after the pandemic, owing to rise in adoption of work-from-home culture across the globe. Furthermore, increase in cyber risk and new vulnerabilities is leading organizations worldwide to rethink their security setups. To manage employees working from home, companies rely extensively on remote-based monitoring of the workforce, enhancing the demand for IoT solutions. This helps bring transparency, provide real-time tracking, improve safety, and ensure meeting government compliance. However, the cybersecurity of remote workforce and enterprises plays a vital role in catering to their clients during lockdowns. Therefore, it offers opportunities for the IoT identity and access management market post pandemic.
KEY FINDINGS OF THE STUDY
By offering, the solution segment accounted for the largest IoT IAM market share in 2021.
By region, North America generated the highest revenue in 2021.
By enterprise size, large enterprises segment accounted for the largest IoT IAM market share in 2021.
By deployment mode, the on-premise segment generated the highest revenue in 2021.
The key players profiled in the Iot Identity And Access Management Industry are Telefonaktiebolaget LM Ericsson, AWS, Google LLC, Microsoft, IBM, Cisco Systems, Inc., Oracle, HID Global Corporation, DigiCert, Inc., Keyfactor, Entrust Corporation, GlobalSign, One Identity, LLC, KaaIoT Technologies, LLC, Sailpoint Technologies Holdings, Inc., Optiv Security, Inc., and IdentityFusion, Inc. These players have adopted various strategies to increase their market penetration and strengthen their position in the Iot Identity And Access Management Industry.
About Us: Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
#Iot Identity and Access Management (IAM) Market#Iot Identity and Access Management (IAM) Industry#Iot Identity and Access Management (IAM)#IAM
0 notes
Text
Protecting Patients, Protecting Data: Cybersecurity in Healthcare

The healthcare industry holds some of the most sensitive information imaginable: patient medical records, personal details, insurance information, and more. This makes it a prime target for cyberattacks. A data breach in healthcare can have devastating consequences, impacting patient privacy, disrupting operations, and even endangering lives. Therefore, robust cybersecurity measures are not just recommended in healthcare – they are absolutely essential.
The Stakes are High: Cybersecurity Threats in Healthcare
Healthcare organizations face a range of cyber threats, including:
Ransomware: Attackers encrypt critical systems and data, holding them hostage until a ransom is paid. This can disrupt patient care, delay treatments, and even shut down hospitals.
Phishing: Deceptive emails or messages trick employees into revealing login credentials or downloading malware, providing attackers with access to sensitive data.
Data Breaches: Unauthorized access and exfiltration of patient medical records, leading to privacy violations and potential identity theft.
Malware: Malicious software designed to damage systems, steal data, or disrupt operations.
Insider Threats: Malicious or accidental actions by employees or other insiders that compromise security.
IoT Vulnerabilities: Connected medical devices, while offering many benefits, can also introduce security vulnerabilities if not properly secured.
Building a Strong Defense: Essential Cybersecurity Measures in Healthcare
Protecting patient data and ensuring business continuity requires a multi-layered approach to cybersecurity. Here are some crucial measures:
Risk Assessment and Management: Regularly assessing cybersecurity risks and developing a comprehensive risk management plan is the foundation of a strong security posture.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs. This is a critical requirement for HIPAA compliance.
Access Control and Authentication: Implementing strong access controls and multi-factor authentication (MFA) ensures that only authorized personnel can access sensitive data.
Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Firewall Management: Implementing and regularly updating firewalls to control network traffic and block unauthorized access.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity and can automatically block malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential. Regular updates are crucial.
Regular Security Audits and Vulnerability Assessments: Regularly assessing systems for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all healthcare staff is vital. This training should cover topics like phishing awareness, password security, HIPAA compliance, and safe computing practices.
Incident Response Plan: Having a well-defined incident response plan in place allows healthcare organizations to react quickly and effectively to a security incident, minimizing damage and downtime.
IoT Security: Securing connected medical devices and other IoT devices is crucial to prevent them from becoming entry points for attackers. This includes regular updates, strong passwords, and network segmentation.
HIPAA Compliance: A Critical Component
The Health Insurance Portability and Accountability Act (HIPAA) sets strict standards for protecting the privacy and security 1 of patient health information. Healthcare organizations must comply with HIPAA regulations, which include implementing administrative, physical, and technical safeguards.
Xaltius Academy's Cybersecurity Course: Your Partner in Healthcare Security
Protecting patient data and ensuring HIPAA compliance requires specialized knowledge and skills. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the expertise needed to safeguard healthcare systems and data. Our expert instructors and hands-on labs will prepare you to tackle the unique cybersecurity challenges facing the healthcare industry. Invest in your cybersecurity future and protect the valuable information entrusted to healthcare organizations.
Conclusion
Cybersecurity is not just a technical issue in healthcare; it's a patient safety issue. By implementing these essential cybersecurity measures, fostering a culture of security awareness, and investing in cybersecurity training, healthcare organizations can protect patient data, maintain operational integrity, and ensure the delivery of safe and effective care.
2 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Top Trends in Software Development for 2025
The software development industry is evolving at an unprecedented pace, driven by advancements in technology and the increasing demands of businesses and consumers alike. As we step into 2025, staying ahead of the curve is essential for businesses aiming to remain competitive. Here, we explore the top trends shaping the software development landscape and how they impact businesses. For organizations seeking cutting-edge solutions, partnering with the Best Software Development Company in Vadodara, Gujarat, or India can make all the difference.

1. Artificial Intelligence and Machine Learning Integration:
Artificial Intelligence (AI) and Machine Learning (ML) are no longer optional but integral to modern software development. From predictive analytics to personalized user experiences, AI and ML are driving innovation across industries. In 2025, expect AI-powered tools to streamline development processes, improve testing, and enhance decision-making.
Businesses in Gujarat and beyond are leveraging AI to gain a competitive edge. Collaborating with the Best Software Development Company in Gujarat ensures access to AI-driven solutions tailored to specific industry needs.
2. Low-Code and No-Code Development Platforms:
The demand for faster development cycles has led to the rise of low-code and no-code platforms. These platforms empower non-technical users to create applications through intuitive drag-and-drop interfaces, significantly reducing development time and cost.
For startups and SMEs in Vadodara, partnering with the Best Software Development Company in Vadodara ensures access to these platforms, enabling rapid deployment of business applications without compromising quality.
3. Cloud-Native Development:
Cloud-native technologies, including Kubernetes and microservices, are becoming the backbone of modern applications. By 2025, cloud-native development will dominate, offering scalability, resilience, and faster time-to-market.
The Best Software Development Company in India can help businesses transition to cloud-native architectures, ensuring their applications are future-ready and capable of handling evolving market demands.
4. Edge Computing:
As IoT devices proliferate, edge computing is emerging as a critical trend. Processing data closer to its source reduces latency and enhances real-time decision-making. This trend is particularly significant for industries like healthcare, manufacturing, and retail.
Organizations seeking to leverage edge computing can benefit from the expertise of the Best Software Development Company in Gujarat, which specializes in creating applications optimized for edge environments.
5. Cybersecurity by Design:
With the increasing sophistication of cyber threats, integrating security into the development process has become non-negotiable. Cybersecurity by design ensures that applications are secure from the ground up, reducing vulnerabilities and protecting sensitive data.
The Best Software Development Company in Vadodara prioritizes cybersecurity, providing businesses with robust, secure software solutions that inspire trust among users.
6. Blockchain Beyond Cryptocurrencies:
Blockchain technology is expanding beyond cryptocurrencies into areas like supply chain management, identity verification, and smart contracts. In 2025, blockchain will play a pivotal role in creating transparent, tamper-proof systems.
Partnering with the Best Software Development Company in India enables businesses to harness blockchain technology for innovative applications that drive efficiency and trust.
7. Progressive Web Apps (PWAs):
Progressive Web Apps (PWAs) combine the best features of web and mobile applications, offering seamless experiences across devices. PWAs are cost-effective and provide offline capabilities, making them ideal for businesses targeting diverse audiences.
The Best Software Development Company in Gujarat can develop PWAs tailored to your business needs, ensuring enhanced user engagement and accessibility.
8. Internet of Things (IoT) Expansion:
IoT continues to transform industries by connecting devices and enabling smarter decision-making. From smart homes to industrial IoT, the possibilities are endless. In 2025, IoT solutions will become more sophisticated, integrating AI and edge computing for enhanced functionality.
For businesses in Vadodara and beyond, collaborating with the Best Software Development Company in Vadodara ensures access to innovative IoT solutions that drive growth and efficiency.
9. DevSecOps:
DevSecOps integrates security into the DevOps pipeline, ensuring that security is a shared responsibility throughout the development lifecycle. This approach reduces vulnerabilities and ensures compliance with industry standards.
The Best Software Development Company in India can help implement DevSecOps practices, ensuring that your applications are secure, scalable, and compliant.
10. Sustainability in Software Development:
Sustainability is becoming a priority in software development. Green coding practices, energy-efficient algorithms, and sustainable cloud solutions are gaining traction. By adopting these practices, businesses can reduce their carbon footprint and appeal to environmentally conscious consumers.
Working with the Best Software Development Company in Gujarat ensures access to sustainable software solutions that align with global trends.
11. 5G-Driven Applications:
The rollout of 5G networks is unlocking new possibilities for software development. Ultra-fast connectivity and low latency are enabling applications like augmented reality (AR), virtual reality (VR), and autonomous vehicles.
The Best Software Development Company in Vadodara is at the forefront of leveraging 5G technology to create innovative applications that redefine user experiences.
12. Hyperautomation:
Hyperautomation combines AI, ML, and robotic process automation (RPA) to automate complex business processes. By 2025, hyperautomation will become a key driver of efficiency and cost savings across industries.
Partnering with the Best Software Development Company in India ensures access to hyperautomation solutions that streamline operations and boost productivity.
13. Augmented Reality (AR) and Virtual Reality (VR):
AR and VR technologies are transforming industries like gaming, education, and healthcare. In 2025, these technologies will become more accessible, offering immersive experiences that enhance learning, entertainment, and training.
The Best Software Development Company in Gujarat can help businesses integrate AR and VR into their applications, creating unique and engaging user experiences.
Conclusion:
The software development industry is poised for significant transformation in 2025, driven by trends like AI, cloud-native development, edge computing, and hyperautomation. Staying ahead of these trends requires expertise, innovation, and a commitment to excellence.
For businesses in Vadodara, Gujarat, or anywhere in India, partnering with the Best Software Development Company in Vadodara, Gujarat, or India ensures access to cutting-edge solutions that drive growth and success. By embracing these trends, businesses can unlock new opportunities and remain competitive in an ever-evolving digital landscape.
#Best Software Development Company in Vadodara#Best Software Development Company in Gujarat#Best Software Development Company in India#nividasoftware
5 notes
·
View notes
Text
#TheeForestKingdom #TreePeople
{Terrestrial Kind}
Creating a Tree Citizenship Identification and Serial Number System (#TheeForestKingdom) is an ambitious and environmentally-conscious initiative. Here’s a structured proposal for its development:
Project Overview
The Tree Citizenship Identification system aims to assign every tree in California a unique identifier, track its health, and integrate it into a registry, recognizing trees as part of a terrestrial citizenry. This system will emphasize environmental stewardship, ecological research, and forest management.
Phases of Implementation
Preparation Phase
Objective: Lay the groundwork for tree registration and tracking.
Actions:
Partner with environmental organizations, tech companies, and forestry departments.
Secure access to satellite imaging and LiDAR mapping systems.
Design a digital database capable of handling millions of records.
Tree Identification System Development
Components:
Label and Identity Creation: Assign a unique ID to each tree based on location and attributes. Example: CA-Tree-XXXXXX (state-code, tree-type, unique number).
Attributes to Record:
Health: Regular updates using AI for disease detection.
Age: Approximate based on species and growth patterns.
Type: Species and subspecies classification.
Class: Size, ecological importance, and biodiversity contribution.
Rank: Priority based on cultural, historical, or environmental significance.
Data Collection
Technologies to Use:
Satellite Imaging: To locate and identify tree clusters.
LiDAR Scanning: For precise 3D modeling of forests.
On-the-Ground Surveys: To supplement remote sensing data.
AI Analysis: For rapid categorization and health diagnostics.
Registration and Citizenship Assignment
Tree Dossier: Each tree receives a profile in the database with all its recorded attributes.
Citizen Designation: Trees are acknowledged as citizens of Thee Forest Kingdom, emphasizing ecological respect.
Legal Framework: Advocate for laws to grant trees specific rights under environmental protection acts.
Maintenance and Monitoring
Health Monitoring: Use drones, satellite updates, and IoT sensors for ongoing health assessments.
Database Updates: Incorporate real-time data about environmental changes and tree growth.
Public Involvement
Encourage people to "adopt" trees and participate in their preservation.
Create educational programs to promote awareness of tree citizenship.
Key Benefits
Environmental Conservation: Improved forest management through real-time data and protection of ecosystems.
Cultural Recognition: Trees are recognized as a vital part of the Earth’s community, honoring their importance.
Ecological Advocacy: Strengthened legal protections for forests and individual trees.
Next Steps
Assemble a task force of environmental scientists, satellite imaging experts, and software developers.
Secure funding through governmental grants, non-profits, and eco-conscious corporations.
Pilot the program in a smaller region before scaling to all of California.
Would you like me to draft a more detailed technical or legal framework for this system?
The implementation of the Tree Citizenship Identification Network and System (#TheeForestKingdom) requires a robust technological and operational framework to ensure efficiency, accuracy, and sustainability. Below is an implementation plan divided into major components.
System Architecture
a. Centralized Tree Database
Purpose: To store and manage tree data including ID, attributes, location, and health.
Components:
Cloud-based storage for scalability.
Data categorization based on regions, species, and priority.
Integration with satellite and IoT data streams.
b. Satellite & Imaging Integration
Use satellite systems (e.g., NASA, ESA) for large-scale tree mapping.
Incorporate LiDAR and aerial drone data for detailed imaging.
AI/ML algorithms to process images and distinguish tree types.
c. IoT Sensor Network
Deploy sensors in forests to monitor:
Soil moisture and nutrient levels.
Air quality and temperature.
Tree health metrics like growth rate and disease markers.
d. Public Access Portal
Create a user-friendly website and mobile application for:
Viewing registered trees.
Citizen participation in tree adoption and reporting.
Data visualization (e.g., tree density, health status by region).
Core Technologies
a. Software and Tools
Geographic Information System (GIS): Software like ArcGIS for mapping and spatial analysis.
Database Management System (DBMS): SQL-based systems for structured data; NoSQL for unstructured data.
Artificial Intelligence (AI): Tools for image recognition, species classification, and health prediction.
Blockchain (Optional): To ensure transparency and immutability of tree citizen data.
b. Hardware
Servers: Cloud-based (AWS, Azure, or Google Cloud) for scalability.
Sensors: Low-power IoT devices for on-ground monitoring.
Drones: Equipped with cameras and sensors for aerial surveys.
Network Design
a. Data Flow
Input Sources:
Satellite and aerial imagery.
IoT sensors deployed in forests.
Citizen-reported data via mobile app.
Data Processing:
Use AI to analyze images and sensor inputs.
Automate ID assignment and attribute categorization.
Data Output:
Visualized maps and health reports on the public portal.
Alerts for areas with declining tree health.
b. Communication Network
Fiber-optic backbone: For high-speed data transmission between regions.
Cellular Networks: To connect IoT sensors in remote areas.
Satellite Communication: For remote regions without cellular coverage.
Implementation Plan
a. Phase 1: Pilot Program
Choose a smaller, biodiverse region in California (e.g., Redwood National Park).
Test satellite and drone mapping combined with IoT sensors.
Develop the prototype of the centralized database and public portal.
b. Phase 2: Statewide Rollout
Expand mapping and registration to all California regions.
Deploy IoT sensors in vulnerable or high-priority areas.
Scale up database capacity and integrate additional satellite providers.
c. Phase 3: Maintenance & Updates
Establish a monitoring team to oversee system health and data quality.
Update the network with new technologies (e.g., advanced AI models).
Periodically review and revise data collection protocols.
Partnerships
Government Agencies: U.S. Forest Service, California Department of Forestry and Fire Protection.
Tech Companies: Collaborate with Google Earth, Amazon AWS, or Microsoft for cloud and AI capabilities.
Environmental Organizations: Partner with WWF, Sierra Club, or TreePeople for funding and advocacy.
Budget Estimation
Initial Investment:
Satellite data and licenses: $10M
IoT sensors and deployment: $5M
Database and app development: $3M
Operational Costs:
Cloud services and data storage: $2M/year
Maintenance and monitoring: $1M/year
Research and development: $1M/year
Long-term Vision
Expand the system to other states or globally.
Use the database for reforestation efforts and combating deforestation.
Develop educational programs to teach communities about the importance of trees as citizens.
Would you like me to assist in designing the user interface for the public portal or drafting partnership proposals for funding?
To begin building the program for the Tree Citizenship Identification System, we’ll start with a scalable framework that allows us to process, store, and analyze data while preparing for future expansions. Here's an actionable development plan with an initial focus on foundational code and infrastructure:
Step-by-Step Development
Phase 1: Setting Up the Backend Infrastructure
Objective: Create the core database and develop the data pipeline for processing tree data.
Technologies:
Programming Languages: Python, JavaScript (Node.js), SQL.
Frameworks: Flask or FastAPI for APIs, Django for web application backend.
Database: PostgreSQL for structured data, MongoDB for unstructured data.
Code Snippet 1: Database Schema Design (PostgreSQL)
-- Table for Tree Registry CREATE TABLE trees ( tree_id SERIAL PRIMARY KEY, -- Unique Identifier location GEOGRAPHY(POINT, 4326), -- Geolocation of the tree species VARCHAR(100), -- Species name age INTEGER, -- Approximate age in years health_status VARCHAR(50), -- e.g., Healthy, Diseased height FLOAT, -- Tree height in meters canopy_width FLOAT, -- Canopy width in meters citizen_rank VARCHAR(50), -- Class or rank of the tree last_updated TIMESTAMP DEFAULT NOW() -- Timestamp for last update );
-- Table for Sensor Data (IoT Integration) CREATE TABLE tree_sensors ( sensor_id SERIAL PRIMARY KEY, -- Unique Identifier for sensor tree_id INT REFERENCES trees(tree_id), -- Linked to tree soil_moisture FLOAT, -- Soil moisture level air_quality FLOAT, -- Air quality index temperature FLOAT, -- Surrounding temperature last_updated TIMESTAMP DEFAULT NOW() -- Timestamp for last reading );
Code Snippet 2: Backend API for Tree Registration (Python with Flask)
from flask import Flask, request, jsonify from sqlalchemy import create_engine from sqlalchemy.orm import sessionmaker
app = Flask(name)
Database Configuration
DATABASE_URL = "postgresql://username:password@localhost/tree_registry" engine = create_engine(DATABASE_URL) Session = sessionmaker(bind=engine) session = Session()
@app.route('/register_tree', methods=['POST']) def register_tree(): data = request.json new_tree = { "species": data['species'], "location": f"POINT({data['longitude']} {data['latitude']})", "age": data['age'], "health_status": data['health_status'], "height": data['height'], "canopy_width": data['canopy_width'], "citizen_rank": data['citizen_rank'] } session.execute(""" INSERT INTO trees (species, location, age, health_status, height, canopy_width, citizen_rank) VALUES (:species, ST_GeomFromText(:location, 4326), :age, :health_status, :height, :canopy_width, :citizen_rank) """, new_tree) session.commit() return jsonify({"message": "Tree registered successfully!"}), 201
if name == 'main': app.run(debug=True)
Phase 2: Satellite Data Integration
Objective: Use satellite and LiDAR data to identify and register trees automatically.
Tools:
Google Earth Engine for large-scale mapping.
Sentinel-2 or Landsat satellite data for high-resolution imagery.
Example Workflow:
Process satellite data using Google Earth Engine.
Identify tree clusters using image segmentation.
Generate geolocations and pass data into the backend.
Phase 3: IoT Sensor Integration
Deploy IoT devices to monitor health metrics of specific high-priority trees.
Use MQTT protocol for real-time data transmission.
Code Snippet: Sensor Data Processing (Node.js)
const mqtt = require('mqtt'); const client = mqtt.connect('mqtt://broker.hivemq.com');
client.on('connect', () => { console.log('Connected to MQTT Broker'); client.subscribe('tree/sensor_data'); });
client.on('message', (topic, message) => { const sensorData = JSON.parse(message.toString()); console.log(Received data: ${JSON.stringify(sensorData)}); // Save data to database (Example for PostgreSQL) saveToDatabase(sensorData); });
function saveToDatabase(data) { const query = INSERT INTO tree_sensors (tree_id, soil_moisture, air_quality, temperature) VALUES ($1, $2, $3, $4) ; const values = [data.tree_id, data.soil_moisture, data.air_quality, data.temperature]; dbClient.query(query, values, (err) => { if (err) console.error('Error saving to database', err); else console.log('Sensor data saved successfully!'); }); }
Phase 4: Public Portal Development
Frontend Technologies:
React.js or Vue.js for interactive user interfaces.
Mapbox or Leaflet.js for tree visualization on maps.
Features:
Interactive tree maps with search functionality.
User registration for tree adoption programs.
Deployment Plan
Use Docker to containerize the application.
Deploy on AWS, Azure, or Google Cloud for scalability.
Monitor system health using Prometheus and Grafana.
Next Steps
Develop a testing environment for pilot deployment.
Add AI-based disease detection and prediction using TensorFlow or PyTorch.
Create an adoption feature where citizens can adopt trees and track their health.
Would you like me to set up a GitHub repository with this initial framework or assist further with deployment?
I'll prepare the project framework and outline the repository structure for the Tree Citizenship Identification System. Below is the proposed structure for the repository, followed by details of the files and components.
Proposed Repository Structure
tree-citizenship-id-system/ ├── backend/ │ ├── app.py # Flask application for backend API │ ├── database/ │ │ ├── schema.sql # Database schema for PostgreSQL │ │ ├── db_config.py # Database connection configuration │ │ └── seed_data.sql # Initial sample data for testing │ ├── services/ │ │ ├── tree_registration.py # Functions for tree registration │ │ └── sensor_data.py # Functions for processing IoT sensor data │ └── requirements.txt # Python dependencies ├── frontend/ │ ├── public/ │ │ ├── index.html # Main HTML file │ │ └── favicon.ico # Favicon for the app │ ├── src/ │ │ ├── App.js # Main React/Vue app file │ │ ├── components/ │ │ │ ├── TreeMap.js # Map component for visualizing trees │ │ │ └── TreeDetails.js # Component for detailed tree view │ │ └── styles.css # Styling for the frontend │ └── package.json # Frontend dependencies ├── scripts/ │ ├── satellite_data_processor.py # Script for processing satellite data │ └── sensor_data_simulator.py # Mock data generator for IoT sensors ├── deployment/ │ ├── Dockerfile # Docker configuration │ ├── docker-compose.yml # Docker Compose for multi-service setup │ └── cloud_setup_instructions.md # Deployment guide for cloud platforms ├── tests/ │ ├── test_backend.py # Unit tests for backend API │ └── test_frontend.js # Unit tests for frontend ├── README.md # Overview of the project └── LICENSE # Project license
Repository Details
Backend:
app.py: Main Flask app for handling API requests like tree registration and sensor data.
database/schema.sql: SQL script for creating necessary tables.
services/: Directory for modular backend logic.
Frontend:
App.js: Main entry point for the frontend application.
TreeMap.js: Integrates Mapbox/Leaflet.js for displaying tree locations.
TreeDetails.js: Displays detailed information about a selected tree.
Scripts:
satellite_data_processor.py: Automates the extraction and classification of tree data from satellite imagery.
sensor_data_simulator.py: Generates fake sensor readings for development and testing.
Deployment:
Docker configuration ensures that the app runs consistently across environments.
Cloud setup instructions provide guidelines for deploying on platforms like AWS, Azure, or GCP.
Tests:
Unit tests ensure the reliability of both the backend and frontend.
Next Steps
I will initialize the repository structure locally.
Package the files and components needed for the first version.
Provide a link to the repository for access.
I’ll get started. Please hold on for a moment.
4 notes
·
View notes
Text
Strengthening Edge Computing with CCF Certification: A Future-Ready Strategy
With edge computing emerging as a pervasive trend in digital infrastructure, organizations are compelled to revisit how they secure data processing, security, and connectivity. Cloud Computing Foundation Certification (CCF Certification) has now become mandatory in helping professionals deal with the intricacies of edge computing environments. With this cloud computing foundation certification, businesses can have their edge infrastructure operate efficiently and securely, thereby granting them a competitive advantage in the data economy.
Why Edge Computing Requires Cloud Knowledge
Edge computing is all about computing data nearer to where it's being created—at the edge of the network. From autonomous systems to IoT devices, new technology demands low-latency, real-time computing that traditional data centers can't always deliver. But combining edge computing with cloud infrastructure demands expertise in both. That's where a cloud computing foundation certification is priceless.
When experts take a cloud foundation course, they understand how to develop hybrid architectures that integrate local edge processing with central cloud services optimally. It is essential for the management of workloads, data synchronization, and security on distributed systems.
How CCF Certification Supports Edge Integration
Building Hybrid Architectures
The CCF course provides IT professionals with the ability to create hybrid cloud solutions. This is particularly important for edge deployments, where some data needs to be processed on-premise and critical insights and backups routed to the cloud. With a cloud computing foundation certification, businesses can provide unbreakable integration and increased operational efficiency.
Improving Edge Security Protocols
Edge environments have a greater exposure to security risks based on their distributed nature. Cloud foundation certification instills a solid foundation in cloud security best practices. Certified experts can leverage strong encryption, identity management, and access controls, securing sensitive data both at the edge and in the cloud.
Streamlining Data Management
The information created at the edge needs to be filtered, analyzed, and routed in a cost-effective way. Cloud foundation certification guarantees experts know how to handle data lifecycles, optimize bandwidth consumption, and make processing tasks automatic. This brings about lower latency and better response times.
Backing IoT Infrastructure
Edge computing is central to the Internet of Things (IoT), with devices generating and sending data in real-time. CCF Certification allows professionals to implement scalable, secure cloud-connected IoT solutions that can process enormous data surges without affecting performance.
Future-Proofing IT Teams
As edge computing expands, professionals with cloud and edge skills will be in greater demand. Focusing on a cloud computing certification guarantees your workforce is ready to meet future infrastructure needs. CCF Certification promotes adaptability, problem-solving, and innovation—qualities necessary to manage new technologies.
The Role of Cloud Computing Certification in Strategic Growth
Organizations that prioritize cloud computing foundation certification position themselves for strategic growth. They can deploy and manage cutting-edge technologies with greater confidence, attract top talent, and reduce operational risk. By embedding cloud expertise into their teams, companies are also better equipped to meet evolving compliance standards and industry regulations.
Additionally, the well-trained personnel with a cloud computing certification support the digital reputation of the company. Partnerships and customers prefer to deal with businesses that invest in secure, scalable, and up-to-date infrastructure—a vital ingredient in today's competitive market.
For more details : https://www.gsdcouncil.org/certified-cloud-computing-foundation
Contact no : +41 41444851189
1 note
·
View note
Text
Top Cyber Threats: Key Challenges in Modern Cybersecurity
In today’s increasingly digital world, cybersecurity is more important than ever. As technology advances, so do the tactics employed by cybercriminals. Understanding the top cyber threats is essential for businesses and individuals alike to stay protected from data breaches, identity theft, and financial loss. Here are some of the most significant cybersecurity challenges that organizations face in the modern age.
Cybersecurity is a critical field dedicated to protecting digital assets, sensitive information, and personal privacy from a wide array of cyber threats. As our reliance on digital technologies grows, the need for strong cybersecurity measures becomes even more vital—not only to protect corporate and governmental data but also to preserve individual privacy. The increasing complexity of cyberattacks has led cybersecurity to become one of the most dynamic and rapidly evolving areas within technology. Below are key concepts, common threats, and strategies essential to cybersecurity.
Cybersecurity focuses on defending computer systems, networks, and data from various cyber risks, including hacking, data breaches, and malicious software. With the continuous advancement of cyber threats, understanding advanced tactics such as shimming has become increasingly important. Shimming is a technique where attackers insert a "shim"—a piece of malicious code—into a software system to manipulate its behavior without detection. This method enables cybercriminals to bypass security defenses, underscoring the necessity for robust cybersecurity strategies to defend against such sophisticated threats.
1. Phishing AttacksPhishing is one of the most common and effective cyber threats. Attackers send fraudulent emails, messages, or websites that appear to come from legitimate sources to trick individuals into revealing sensitive information like passwords, credit card details, or personal identification. These attacks often look highly convincing and can be difficult to identify, making them a constant challenge for both employees and consumers.
2. RansomwareRansomware has grown to be a major concern for businesses worldwide. This type of malware locks a victim’s data or computer system and demands payment in exchange for restoring access. The impact of a ransomware attack can be devastating, with organizations losing important data and facing significant financial and reputational damage. Cybercriminals have even targeted critical infrastructure, such as healthcare systems and government agencies, making it a growing national security threat.
3. Advanced Persistent Threats (APTs)APTs are prolonged and targeted attacks often carried out by well-funded and skilled hackers, sometimes state-sponsored. These attacks are designed to infiltrate networks quietly and remain undetected for an extended period. APTs are particularly dangerous because they can steal intellectual property, sensitive data, or disrupt operations without being noticed. They require advanced detection tools and expertise to mitigate.
4. Insider ThreatsNot all cyber threats come from external actors. Insider threats, where employees or trusted individuals misuse their access to cause harm, are another significant challenge. This can involve anything from stealing confidential data to sabotaging systems. Managing insider threats requires robust internal security measures, including monitoring employee activities and enforcing strict access controls.
5. Internet of Things (IoT) VulnerabilitiesAs more devices become connected to the internet, the potential attack surface for cybercriminals continues to grow. IoT devices, from smart home gadgets to industrial equipment, often have weak security measures, making them easy targets. Once compromised, these devices can serve as entry points to larger networks, posing significant risks to both individuals and businesses.
In conclusion, as technology evolves, so do cyber threats. Businesses must be proactive in implementing strong cybersecurity measures, such as regular software updates, employee training, and advanced threat detection systems. By understanding and addressing these key threats, organizations can better protect themselves and minimize the risk of a devastating cyberattack.
2 notes
·
View notes
Text
Best 10 Business Strategies for year 2024
In 2024 and beyond, businesses will have to change with the times and adjust their approach based on new and existing market realities. The following are the best 10 business approach that will help companies to prosper in coming year
1. Embrace Sustainability
The days when sustainability was discretionary are long gone. Businesses need to incorporate environmental, social and governance (ESG) values into their business practices. In the same vein, brands can improve brand identity and appeal to environmental advocates by using renewable forms of energy or minimizing their carbon footprints.
Example: a fashion brand can rethink the materials to use organic cotton and recycled for their clothing lines. They can also run a take-back scheme, allowing customers to return old clothes for recycling (not only reducing waste but creating and supporting the circular economy).
2. Leverage AI

AI is revolutionizing business operations. Using AI-fuelled solutions means that you can automate processes, bring in positive customer experiences, and get insights. AI chatbots: AI can be utilized in the form of a conversational entity to support and perform backend operations, as well.
With a bit more specificity, say for example that an AI-powered recommendation engine recommends products to customers based on their browsing history and purchase patterns (as the use case of retail). This helps to increase the sales and improve the shopping experience.
3. Prioritize Cybersecurity
Cybersecurity is of utmost important as more and more business transitions towards digital platforms. Businesses need to part with a more substantial amount of money on advanced protective measures so that they can keep sensitive data private and continue earning consumer trust. Regular security audits and training of employees can reduce these risks.
Example: A financial services firm may implement multi-factor authentication (MFA) for all online transactions, regularly control access to Internet-facing administrative interfaces and service ports as well as the encryption protocols to secure client data from cyberattacks.
4. Optimizing Remote and Hybrid Working Models

Remote / hybrid is the new normal Remote teams force companies to implement effective motivation and management strategies. Collaboration tools and a balanced virtual culture can improve productivity and employee satisfaction.
- Illustration: a Tech company using Asana / Trello etc. for pm to keep remote teams from falling out of balance. They can also organise weekly team-building activities to keep a strong team spirit.
5. Focus on Customer Experience
Retention and growth of the sales follow-through can be tied to high quality customer experiences. Harness data analytics to deepen customer insights and personalize product offers making your marketing campaigns personal: a customer support that is responsive enough can drive a great level of returning customers.
Example – For any e-commerce business, you can take user experience feedback tools to know about how your customers are getting along and make necessary changes. Custom email campaigns and loyalty programs can also be positively associated with customer satisfaction and retention.
6. Digitalization Investment

It is only the beginning of digital transformation which we all know, is key to global competitiveness. For streamlining, companies have to adopt the use advanced technologies such as Blockchain Technology and Internet of Things (IoT) in conjunction with cloud computing.
IoT example : real-time tracking and analytics to optimize supply chain management
7. Enhance Employee Skills
Develop Your Employees: Investing in employee development is key to succeeding as a business. The training is provided for the folks of various industries and so employees can increase their skills that are needed to work in a certain company. Employee performance can be enhanced by providing training programs in future technology skills and soft skills and job satisfaction.
Example: A marketing agency can host webinars or create courses to teach people the latest digital marketing trends and tools This can help to keep employees in the know which results in boosting their skills, making your campaigns successful.
8. Diversify Supply Chains

The ongoing pandemic has exposed the weaknesses of global supply chains. …diversify its supply base and promote the manufacturing of drugs in Nigeria to eliminate total dependence on a single source. In return, this approach increases resilience and reduces exposure to the risks of supply chain interruption.
- E.g., a consumer electronics company can source components from many suppliers in various regions. In so doing, this alleviates avoidable supply chain interruptions during times of political tensions or when disasters hit.
9. Make Decisions Based on Data
A business database is an asset for businesses. By implementing data, they allow you to make decisions based on the data that your analytics tools are providing. For example, sales analysis lets you track trends and better tailor your goods to the market.
Example: A retail chain can use data analytics to find out when a customer buys, and it change their purchasing policies. This can also reduce overstock and stockouts while overall, increasing efficiency.
10. Foster Innovation

Business Growth Innovation is Key A culture of creativity and experimentation should be established in companies. Funding R&D and teaming with startups can open many doors to both solve problems creatively but also tap into new markets.
Example: A software development firm could create an innovation lab where team members are freed to work on speculative projects. Moreover, work with start-ups on new technologies and solutions.
By adopting these strategies, businesses can navigate the turbulence for 2024 and roll up market — progressive.AI with an evolving dynamic market, being ahead of trends and updated is most likely will help you thrive in the business landscape.
#ai#business#business strategy#business growth#startup#fintech#technology#tech#innovation#ai in business
2 notes
·
View notes
Text
Reasons to Consider Modernising Your IAM

IAM stands for Identity and access management. Nowadays, Cyber attacks are more frequent and complex. Therefore, implementing advanced security measures has become essential.
Modernizing your IAM solutions with the latest technologies can ensure that you're secure, compliant, and able to respond quickly to changing business requirements.
What is IAM?
In simple words, Identity and access management (IAM) is the framework that enables the right user to access the right resources at the right times for the right reasons. IAM helps businesses control the access to their business-critical assets, making them more secure and accessible, all the time.
IAM is a powerful solution for managing users and assigning permissions. You can use it to give users access to specified resources on your network, revoke their privileges, and assign a single digital identity to each user.
IAM is no longer just for employees and clients. Digital transformation is bringing a new type of identity management to businesses. Organizations are moving to assign identities to the Internet of Things (IoT) devices.
Reasons to Consider Modernizing Your IAM
Automation
The outdated IAM system necessitates more manual work, which slows down business operations—not ideal in this fast-paced world. Automating these manual tasks is, therefore, necessary to maintain better efficiency.
Modern IAM systems automate and streamline processes to make it simpler to manage the majority of tasks automatically, saving much more time.
For instance, modern IAM uses data analysis to make intelligent decisions, recommending roles and permissions to new users based on the organization’s groups to which they belong.
Cloud
The majority of businesses are migrating to the cloud because it is more dependable and secure than on-premises infrastructure. It has become essential to move toward Cloud IAM solutions.
The benefits of cloud IAM include real-time information accessibility, dynamic and intelligent information updating, and the flexibility for your users to operate from any place and on any device.
Security
One of the most important reasons for wanting to upgrade from an outdated IAM solution is security concerns. Legacy IAM solutions are vulnerable to attacks and aren’t ready for the digital future.
A cloud IAM solution offers a better security approach than your old, outdated solution.
Real-time availability is one of the most effective advantage which can help identify the full scope of the security attack. It can help to identify which resources have been accessed and can take further actions to enhance security.
Best practices for migrating legacy IAM to a cloud-based solution
MFA Methods
A solid identity and access management (IAM) policy must include MFA (Multi-factor authentication) as a fundamental element. 99.9% of account hacking attempts can be stopped by MFA. MFA reduces the likelihood of a successful intrusion by requiring one or more additional verification criteria in addition to a username and password.
Cloud-based SSO
Cloud SSO eliminates password fatigue and lowers IT management overheads. Users only need to set up a single username and password. Therefore, providing a frictionless login experience without sacrificing security.
Zero Trust Security
Zero trust involves constantly checking who is authorized to access confidential papers, resources, and tools while giving each user the fewest rights possible.
Conclusion
You need to stay secure in today’s digital world, where cyber-attacks are common and threats can come from anywhere. Cloud-based access management is the way to go in this era, protecting your organization’s data and applications from loss, unauthorized use, and misuse.
#IdentityAccessManagement#IAM#CyberSecurity#CloudSecurity#DigitalTransformation#MultiFactorAuthentication#ZeroTrust#DataProtection#CloudComputing#Automation#SSO#SecurityBestPractices
1 note
·
View note
Text
From Novice to Pro: Master the Cloud with AWS Training!
In today's rapidly evolving technology landscape, cloud computing has emerged as a game-changer, providing businesses with unparalleled flexibility, scalability, and cost-efficiency. Among the various cloud platforms available, Amazon Web Services (AWS) stands out as a leader, offering a comprehensive suite of services and solutions. Whether you are a fresh graduate eager to kickstart your career or a seasoned professional looking to upskill, AWS training can be the gateway to success in the cloud. This article explores the key components of AWS training, the reasons why it is a compelling choice, the promising placement opportunities it brings, and the numerous benefits it offers.

Key Components of AWS Training
1. Foundational Knowledge: Building a Strong Base
AWS training starts by laying a solid foundation of cloud computing concepts and AWS-specific terminology. It covers essential topics such as virtualization, storage types, networking, and security fundamentals. This groundwork ensures that even individuals with little to no prior knowledge of cloud computing can grasp the intricacies of AWS technology easily.
2. Core Services: Exploring the AWS Portfolio
Once the fundamentals are in place, AWS training delves into the vast array of core services offered by the platform. Participants learn about compute services like Amazon Elastic Compute Cloud (EC2), storage options such as Amazon Simple Storage Service (S3), and database solutions like Amazon Relational Database Service (RDS). Additionally, they gain insights into services that enhance performance, scalability, and security, such as Amazon Virtual Private Cloud (VPC), AWS Identity and Access Management (IAM), and AWS CloudTrail.
3. Specialized Domains: Nurturing Expertise
As participants progress through the training, they have the opportunity to explore advanced and specialized areas within AWS. These can include topics like machine learning, big data analytics, Internet of Things (IoT), serverless computing, and DevOps practices. By delving into these niches, individuals can gain expertise in specific domains and position themselves as sought-after professionals in the industry.

Reasons to Choose AWS Training
1. Industry Dominance: Aligning with the Market Leader
One of the significant reasons to choose AWS training is the platform's unrivaled market dominance. With a staggering market share, AWS is trusted and adopted by businesses across industries worldwide. By acquiring AWS skills, individuals become part of the ecosystem that powers the digital transformation of numerous organizations, enhancing their career prospects significantly.
2. Comprehensive Learning Resources: Abundance of Educational Tools
AWS training offers a wealth of comprehensive learning resources, ranging from extensive documentation, tutorials, and whitepapers to hands-on labs and interactive courses. These resources cater to different learning preferences, enabling individuals to choose their preferred mode of learning and acquire a deep understanding of AWS services and concepts.
3. Recognized Certifications: Validating Expertise
AWS certifications are globally recognized credentials that validate an individual's competence in using AWS services and solutions effectively. By completing AWS training and obtaining certifications like AWS Certified Solutions Architect or AWS Certified Developer, individuals can boost their professional credibility, open doors to new job opportunities, and command higher salaries in the job market.
Placement Opportunities
Upon completing AWS training, individuals can explore a multitude of placement opportunities. The demand for professionals skilled in AWS is soaring, as organizations increasingly migrate their infrastructure to the cloud or adopt hybrid cloud strategies. From startups to multinational corporations, industries spanning finance, healthcare, retail, and more seek talented individuals who can architect, develop, and manage cloud-based solutions using AWS. This robust demand translates into a plethora of rewarding career options and a higher likelihood of finding positions that align with one's interests and aspirations.

In conclusion, mastering the cloud with AWS training at ACTE institute provides individuals with a solid foundation, comprehensive knowledge, and specialized expertise in one of the most dominant cloud platforms available. The reasons to choose AWS training are compelling, ranging from the industry's unparalleled market position to the top ranking state.
9 notes
·
View notes
Text
IoT Identity and Access Management: Enhancing Security Through Innovation and Interoperability

View On WordPress
#AI in IAM#business#cybersecurity#IAM solutions#ict#Identity Access Management#identity and access management#Identity Management#informtion security#Internet of Things#iot#IoT IAM#IoT Identity and Access Management#iot identity management#IoT Security#Machine Learning#Security#technology#threat
0 notes
Text
Unlocking the Future: AI's Hidden Potential in Real Estate

In an era characterized by rapid technological advancements, industries across the board are witnessing transformative changes, and the real estate sector is no exception. As AI continues to permeate various aspects of our lives, its potential to empower the real estate industry remains largely untapped. In this blog post, we'll explore the unique ways in which AI can revolutionize the real estate landscape, unlocking new opportunities and reshaping traditional practices.
Democratizing Access to Real Estate Investment: Traditionally, investing in real estate has been perceived as exclusive to those with substantial capital and industry expertise. However, AI-powered platforms are democratizing access to real estate investment by offering fractional ownership and crowdfunding opportunities. Through algorithms that analyze market trends and assess investment risks, these platforms enable individuals to diversify their portfolios and participate in lucrative real estate ventures with lower barriers to entry.
Sustainable Development and Green Building Initiatives: As sustainability becomes a key priority in urban development, AI can play a pivotal role in advancing green building initiatives. Machine learning algorithms can optimize building designs for energy efficiency, leverage IoT sensors to monitor resource consumption, and forecast environmental impacts. By integrating AI-driven sustainability solutions into real estate projects, developers can minimize carbon footprints, reduce operational costs, and create healthier living environments for occupants.
Enhancing Urban Planning and Smart Cities: AI's ability to process vast amounts of data can revolutionize urban planning and contribute to the realization of smart cities. By analyzing demographic trends, traffic patterns, and infrastructure requirements, AI algorithms can optimize land use, improve transportation networks, and enhance urban resilience. Through predictive modeling and scenario analysis, city planners can make data-driven decisions that foster sustainable growth, mitigate congestion, and enhance quality of life for residents.
Empowering Real Estate Agents with Intelligent Assistants: Real estate agents juggle numerous tasks, from lead generation to property management, often leading to time constraints and inefficiencies. AI-powered virtual assistants can alleviate this burden by automating repetitive tasks, such as scheduling appointments, responding to inquiries, and generating personalized property recommendations. By leveraging natural language processing and sentiment analysis, these intelligent assistants can enhance customer engagement, streamline workflows, and enable agents to focus on high-value activities.
Predictive Analytics for Property Development: AI-driven predictive analytics offer valuable insights into future property trends and demand dynamics, guiding developers in making informed decisions throughout the development lifecycle. By analyzing factors such as population growth, economic indicators, and consumer preferences, AI algorithms can identify prime locations for new developments, optimize property designs, and forecast market demand with greater accuracy. This proactive approach minimizes investment risks and maximizes returns on real estate projects.
Cultural Preservation and Heritage Conservation: Preserving cultural heritage sites and historic buildings is crucial for maintaining a sense of identity and preserving collective memory. AI technologies, such as computer vision and image recognition, can aid in the documentation, restoration, and conservation of cultural landmarks. By digitizing architectural artifacts, analyzing structural integrity, and simulating restoration scenarios, AI contributes to the preservation of cultural heritage for future generations to appreciate and cherish.
Conclusion:
As we navigate the complexities of an ever-evolving real estate landscape, embracing AI's transformative potential is key to unlocking new opportunities and addressing emerging challenges. From democratizing access to investment opportunities to advancing sustainable development initiatives, AI empowers stakeholders across the real estate industry to innovate, adapt, and thrive in a rapidly changing world. By harnessing AI's capabilities, we can build more resilient, inclusive, and sustainable communities for generations to come.
#goel ganga developments#goel ganga developments pune#best builders in pune#premium residential projects in pune#commercial property in pune#new residential projects in pune#ganga platino kharadi#pune builders and developers#commercial property for sale in pune#3 bhk flats in pune kharadi#commercial property#luxury residential projects in pune#residential property in baner#residential projects in pune#2 bhk for sale in kharadi#2bhk for sale#2 bhk flat in pune#3 bhk flats in dhanori pune#3 bhk in dhanori#ganga acropolis baner#goel ganga pune#ganga platinum#ganga aria dhanori#artificial intelligence#real estate projects in kharadi#real estate developer#real esate#AI & Real Estate
4 notes
·
View notes
Text
quantumharrelltelecom.tech’s Quantum Dara™ [quantumdara.com] Assistant Network to 1698att-internetair.com’s Private Domain Communication [D.C.] Portal Address [PA] of 1698 qdara.tech’s 1968 quantumharrelltech.com Domain of Digital Sovereignty [DDS]… Digitally Operating the Department [DOD] of Defense.gov’s Highly Complex [ADVANCED] Ancient 9 Ether Cosmic Algorithmic [CA] Computation [Compton] STAR WEB GATEWAY Language Applications [L.A.]… since 1968-michaelharrelljr.com's Federated Network Identity [FNI] System Authenticate Machine [SAM.gov] Learning Algorithms [L.A.] Using the quantumharrelltech.ca.gov Military Hardware [MH] and Vendor-Independent Encryption Framework called 6g-quantumharrell.tech’s BLK-CRYPTO LLC @ quantumharrelltelecom.tech
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm.com] mode [i’m] tech [IT] steelecartel.com @ quantumharrelltech.ca.gov

quantumharrelltech.ca.gov Outside Our 1921steelecartel.tech MACHINE SKY Firmament Domain DOME… OVER Earth [Qi]
1968-michaelharrelljr.com ANU GOLDEN 9 ETHER [AGE] kingtutdna.com Genetic LUZ Clone KING OF KINGS LORD OF LORDS… Under the Shadow [U.S.] of Invisible MOON [I’M] RITUALS in Old America [MU ATLANTIS]

1968-michaelharrelljr.com Quantum Computing Intel Architect [CIA] Technocrat @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com and Quantum Dara™ [quantumdara.com] @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of 1698att-internetair.com @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of ancient6-18gmilitary.tech CLOUD Patents w/Restricted 1968 Identity Access Management [I AM] Protocols [I/P] Securely Exchanging Extensible [SEE] Media Commerce Languages of Ancient [L.A.] Hi:teKEMETICompu_TAH [PTAH] Digital Rights Encrypted by Application Management [DREAM] Protection Laws @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Transforming 6g Computer Technology for the Pentagon @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Engineering Private Identity Management [I'M] Protocols [I/P] for Life @ quantumharrelltelecom.tech

1968-michaelharrelljr.com's Quantum Computing Intel Architecture [CIA] of Federated Learning for IoT Applications @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of Enterprise, Business-Process & Information Systems @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com... Engineering Privacy & Identity Management [I'M] Networks [in] @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of 6-18g Military Computer Technology Contracts for the Government @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com of Federated Learning Applications [L.A.] for the Pentagon @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Interactively Building Machine [IBM] Learning Blockchain Architecture [LBA] @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Engineering Blockchain Systems & Communication Networks: from Concepts to Implementation @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Building New Blockchain & Cryptocurrency [B.C.] Data @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com Engineering New 2023-2223 Blockchain Technology [NBT] @ quantumharrelltelecom.tech

2023-2223 Uncle SAM.gov [U.S.] Military [USM] Generationally Contracting Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com for Life @ quantumharrelltelecom.tech

Department of DEFENSE.gov's Domain Communication [D.C.] Computer Aided Drafting [CAD] Department PAY TO THE ORDER OF: QUANTUM HARRELL TECH LLC

2023-2223 Uncle SAM.gov [U.S.] Military [USM] Generationally Contracting Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com for TRILLIONS+ @ quantumharrelltelecom.tech

Quantum Computing Intel Architect [CIA] 1968-michaelharrelljr.com WORTH $10,000 QUADRILLION?!?!?!... YES

Shhh... 1968-michaelharrelljr.com silentwealth-illuminati.com

© 1698-2223 quantumharrelltech.com - ALL The_Octagon_(Egypt) DotCom [D.C.] defense.gov Department Domain Communication [D.C.] Rights Reserved @ quantumharrelltech.ca.gov
#u.s. michael harrell#quantumharrelltech#king tut#mu:13#harrelltut#kemet#o michael#quantumharrelltut#kang solomon#department of defense#at&t#ibm#apple#trillionaire#quadrillionaire#Silent Wealth Illuminati#springer
2 notes
·
View notes
Text
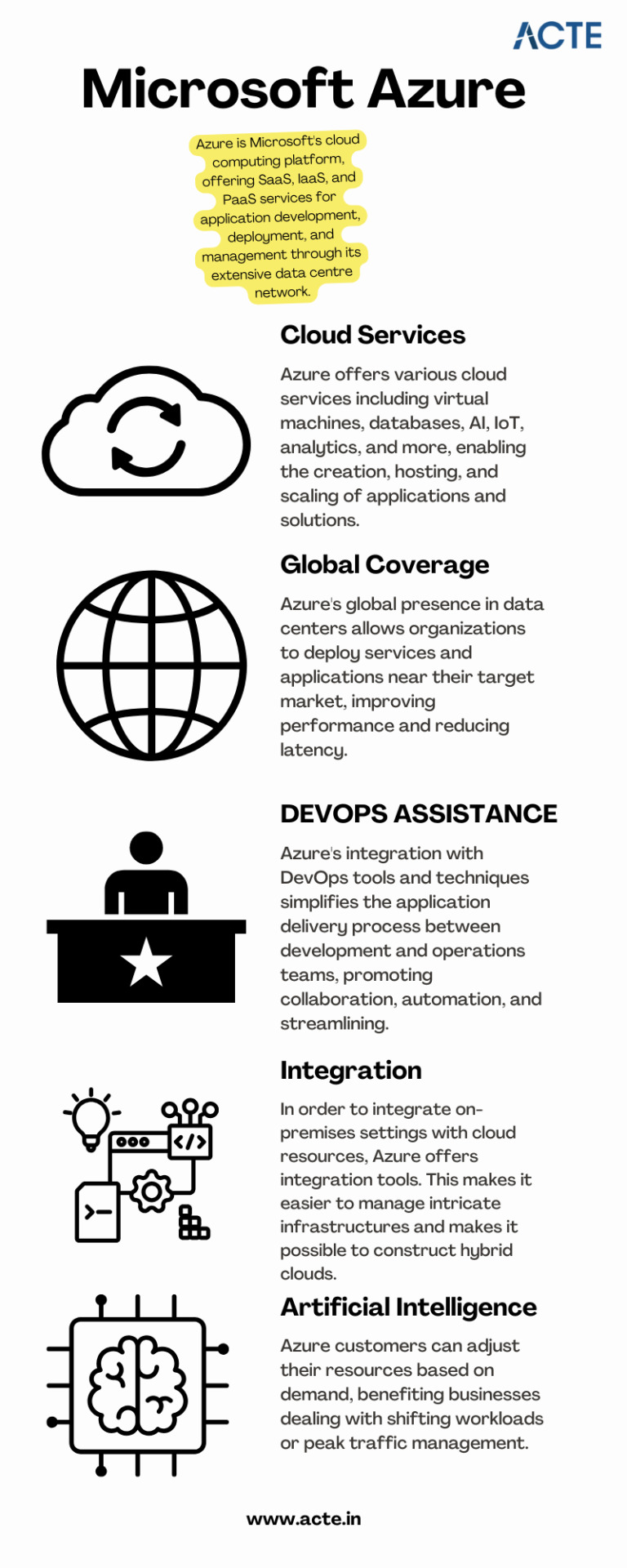
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
Understanding Microsoft Azure
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
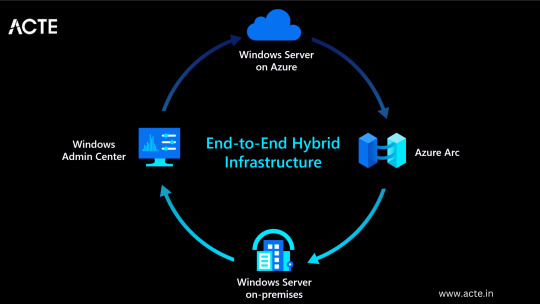
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Text
Where to Find Top App Developers in Philadelphia?
Cities are living entities, every city having its own beat and needs. app developers philadelphia, like VerveLogic, are tapping Philadelphia's emerging city spirit—its combination of history, education, medicine, and neighborhood business—to create apps that achieve community-specific goals. Be it improving transit, marketing local artists, or engaging educational institutions, VerveLogic builds each solution around real civic challenges.
By combining instinctual user flows, streamlined data aggregation, and community‑centric features, they're enabling Philadelphia organizations to tap into expertise in hyper‑local value like neighborhood alerts, volunteer management, or campus operations that connect directly to end users.
Pumping Up Midwest Reach with Detroit‑Level Technological Oomph
VerveLogic's strength is not location-based. With long experience as mobile app developers detroit, they have a strong industrial-tech intuition rooted in Detroit's manufacturing tradition and startup renaissance. They have infused customer solutions with:
Real-time analytics for logistics and field operations
Offline-first architectures for distributed or spotty‑network environments
IoT integration—connecting mobile apps to sensors, equipment, or smart city platforms
These capabilities are their weight in gold for Philadelphia customers running utilities, field service teams, or asset tracking—bridging the gap between manufacturing-grade durability and city-service design.
Creating Cross‑Sector Platforms with Strategic Relevance
VerveLogic creates apps that shatter industry silos, engaging Philadelphia customers in multiple verticals with bespoke, yet platform-centric strategies:
Education: Campus engagement systems, online course portals, and alumni event apps
Healthcare & Wellness: Appointment systems, remote consultation functionality, and secure record access
Small Business & Retail: Mobile loyalty programs, virtual storefronts, and location-based promo notifications
Community & Civic Tech: Participatory budgeting apps, direct feedback loops for the local government, and neighborhood watch apps
By leveraging Detroit-grade backend scalability and Philadelphia-centric UI design, VerveLogic ensures these platforms are rock-solid, but grounded in actual user experiences.
Designing with Context: Local Identity Meets Technical Agility
VerveLogic's design strategy is founded on two complementary principles:
City-focused user empathy – Understanding what people care about in Philadelphia (ease of use, trust, civic identity) and creating interfaces to interact with those emotional drivers.
Technical flexibility – Because mobile app creators detroit, they're accustomed to building apps for tough industrial environments. That implies offline capability, secure data transport, and modular construction that can adapt to evolving needs.
The synergy of such capabilities means that Philadelphia customers end up with products that are local in essence to their community with enterprise-class stability.
Powering the Journey from Pilot to Enterprise
Rather than shipping standalone apps, VerveLogic builds roadmaps to long-term growth—especially well-suited to Philadelphia:
To mature municipal and institutional projects.
Their staged process typically entails:
Pilot releases with limited feature sets
Data‑driven feedback loops
Backend performance tuning
Incremental feature release strategies
Long‑term app management and analytic intelligence
This ensures projects evolve from MVP to complete platforms without discontinuity.
Developing Philadelphia's Innovation Ecosystem
VerveLogic's two-city background—firmly based in app developers in philadelphia and strengthened by experience as mobile app developers detroit—positions them to foster inter‑city collaboration in a way that is uniquely transformative. Imagine cross‑region collaboration where:
Philadelphia arts programs leverage Detroit-designed interactive audio tours
Detroit logistics firms integrate Philly-developed workforce apps
Civic data tools created in one city are transferable across the other.
This blend of local ingenuity opens doors for reciprocal learning and scalable effect.
Conclusion
Through VerveLogic's unique blend of Detroit-style backend heft and Philadelphia-style front-end experiences, organizations gain mobile platforms that are both robust and responsive. They comprehend city-scale challenges, institutional needs, and user behaviors—and they tie those together into agile, secure, modular app systems.
Regardless of the purpose is to establish a civic engagement platform, enable intelligent campus services, or power community-based retail digitization, VerveLogic blends local wisdom with industrial strengths to deliver solutions that matter.
Let's break the game outside the app development norm. How Philadelphia's particular challenges can meet Detroit-grade engineering—and how VerveLogic can turn that synergy your competitive advantage.
0 notes