#Linux-Smart-Enumeration
Explore tagged Tumblr posts
Text
Linux-Smart-Enumeration - Linux Enumeration Tool For Pentesting And CTFs With Verbosity Levels
First, a couple of useful oneliners 😉 wget "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -O lse.sh;chmod 700 lse.sh curl "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -Lo lse.sh;chmod 700 lse.sh Note that since version 2.10 you can serve the script to other hosts with the -S flag! Linux enumeration tools…

View On WordPress
#Ctfs#Hackthebox#KitPloit#Linux Enumeration#Linux-Smart-Enumeration#Oscp#PENTESTING#Privilege Escalation
1 note
·
View note
Text
[Media] Linux enumeration
Linux enumeration This shell script will show relevant information about the security of the local Linux system, helping to escalate privileges. https://github.com/diego-treitos/linux-smart-enumeration t.me/hackgit
0 notes
Photo

linux-smart-enumeration v1.9 releases: Linux enumeration tools for pentesting and CTFs | TheHackerNews.Co #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Photo

linux-smart-enumeration v1.9 releases: Linux enumeration tools for pentesting and CTFs | MrHacker.Co #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo
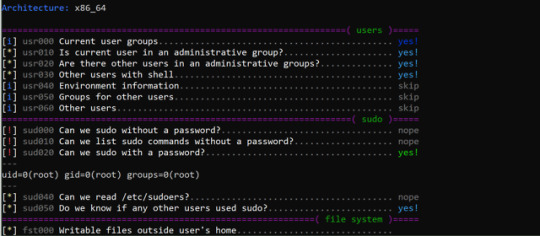
linux-smart-enumeration v1.8 releases: Linux enumeration tools for pentesting and CTFs
0 notes
Link
Ethical Hacking with KALI LINUX
What you’ll learn
Learn simplified ethical hacking techniques from scratch
Learn Linux basics
Learn more than 9 ways to perform LAN attacks
Master 2 smart techniques to crack into wireless networks
Perform an actual Mobile attack
Learn 10+ web application attacks
Learn more than 5 proven methods of Social Engineering attacks
Obtain 20+ skills any penetration tester needs to succeed
Make better decisions on how to protect your applications and network
Upgrade your information security skills for a new job or career change
Learn how to write a professional penetration testing report
Requirements
Intermediate computer knowledge
Fair knowledge of Windows systems
Networking basics
Programming basics
Web applications basics
Mobile applications basics
General idea about information security
Description
Welcome to this comprehensive course on penetration testing with KALI. The course examines the various penetration testing concepts and techniques employed in a modern ubiquitous computing world, and will take you from a beginner to a more advanced level. We will discuss various topics ranging from traditional to many modern ones, such as Networking security, Linux security, Web Applications structure and security, Mobile Applications architecture and security, Hardware security, and the hot topic of IoT security. At the end of the course, I will show you some real attacks.
The layout of the course is easy to walk-through, and the videos are made short and engaging. My purpose is to present you with case exposition and show you live demos, while utilizing a large set of KALI tools (Enumeration, Scanning, Exploitation, Persistence Access, Reporting and Social Engineering tools) in order to get you started quickly. The necessary resources and tools are posted for each sections of the course.
Before jumping into penetration testing, you will first learn how to set up your own lab and install the needed software to practice Penetration Testing along with me. All the attacks explained in this course are launched against real devices, and nothing is theoretical. The course will demonstrate how to fully control victims’ devices such as servers, workstations, and mobile phones. The course can also be interesting to those looking for quick hacks such as controlling victim’s camera, screen, mobile contacts, emails and SMS messages.
At the end of the course you will be equipped with the necessary tools and skills to:
1) Assess security risks by adopting a standard Threat Modeling technique
2) Adopt a structured approach to perform Penetration Tests
3) Protect yourself and the organization you work at
4) Compile security findings and present them professionally to your clients
5) Make the world a safer place
You can as well enjoy the JUICY BONUS section at the end of the course, which shows you how to setup useful portable Pentest Hardware Tools that you can employ in your attacks.
I have put my 14 years of experience into this course by trying to answer many of the questions I had during my journey of learning. I have as well took the feedback and input of many of my students, peers, and professional figures.
I will be happy to answer all your inquiries and connect with you.
Join TODAY and enjoy a life-time access.
PS: The course is available in Arabic as well as Russian versions.
Hack Ethically !
Who this course is for:
Anyone who wants to learn how to secure their systems from hacker
Anyone who wants to learn how hackers can attack their computer systems
Anyone looking to become a penetration tester (From zero to hero)
Computer Science, Computer Security, and Computer Engineering Students
Created by Mohamad Mahjoub Last updated 5/2020 English English [Auto-generated]
Size: 4.35 GB
Download Now
https://ift.tt/3e1xKaC.
The post Penetration Testing with KALI and More: All You Need to Know appeared first on Free Course Lab.
0 notes
Link
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
by Augusto Remillano II and Mark Vicente
We found a Golang-based spreader being used in a campaign that drops a cryptocurrency miner payload. Golang, or Go, is an open source programming language that has been recently associated with malware activity. Trend Micro has been detecting the use of the spreader since May and saw it again in a campaign this month.
The spreader used in this campaign scans for machines running vulnerable software to propagate. The campaign’s attack chain is detailed below.
Figure 1. The attack infection chain
Technical details
The Golang-based spreader This malware looks for several entry points to spread to other systems. It not only uses the common SSH service, but also several exploits. It does this using the Golang-based spreader (which Trend Micro detects as Trojan.Linux.GOSCAN.BB) that scans for the following:
SSH
Misconfigured Redis server
ThinkPHP exploit
Drupal exploit
Atlassian Confluence server (CVE-2019-3396)
A snapshot of the spreader’s code (shown in Figure 2) shows that it scans for a Redis port.
Figure 2. Code showing the use of Redis
Aside from using misconfigured Redis ports, the malware can also infect servers through vulnerable web applications, particularly ThinkPHP and Drupal. The code in the image below shows that it scans for CVE-2019-3396, a vulnerability in Atlassian’s Confluence server that was previously seen being used to distribute a different cryptocurrency-mining malware.
Figure 3. Code showing the use of several vulnerabilities
And finally, it also propagates through SSH ports, as seen in the code snapshot below.
Figure 4. Code showing the use of SSH to propagate
Other components Once the malware reaches the system, it will connect to Pastebin to download the dropper component (detected as Trojan.SH.SQUELL.CC). The dropper will then download and extract a TAR file from mysqli[.]tar[.]gz. The TAR file contains the miner payload, the Golang-based scanner, and other necessary components, enumerated below:
Configuration file for the miner components
Trojan.SH.SQUELL.CB that will execute the miner and scanner
The Golang-based spreader
The miner
File used to determine the malware’s installation status
Aside from executing the miner and the scanner, Trojan.SH.SQUELL.CB performs several other actions. It tries to infect other systems through SSH. It disables security tools and clears command history and logs. It also kills previously ongoing cryptocurrency mining activities (if there were any) by blocking network traffic, and killing their processes. For persistence, it installs itself as a service in the system. It also sets up a cron job that will download and execute the latest version of the malware from Pastebin. All these activities are shown in the code snapshots below.
Figure 5. Code showing the use of SSH to infect other systems
Figure 6. Code showing how the malware disables security tools
Figure 7. Code showing the command to clear history and logs
Figure 8. Code showing the malware eliminating other possibly installed miners in the system
Figure 9. Code showing the persistence mechanisms of the malware
Conclusion and security recommendations
This isn’t the first time a Golang-based script has been used for a campaign. As mentioned earlier we’ve been seeing the same Golang-based spreader since May, used also for a different cryptocurrency-mining malware. The Go programming language was also used in a data stealer malware earlier this year, as reported by Malwarebytes.
Go provides cybercriminals with easy cross-platform development, allowing them to infect both Linux and Windows machines. However, this characteristic is not unique to the programming language. Cybercriminals are possibly turning to Golang to make the analysis of their malware more difficult, as it’s not as commonly used for malware as compared to other languages.
Whatever the reason, users can take steps to reduce the effectivity of a similar campaign by strengthening their network security and defenses. Here are some steps users can take to defend against similar threats.
Applying the necessary patches and updates as soon as they become available
Being mindful of the methods attackers use to spread malware and tailor defenses against them
Changing system and device settings with security in mind to prevent unauthorized access
Trend Micro solutions
Trend Micro endpoint solutions such as the Trend Micro Smart Protection Suites and Worry-Free Business Security can protect users and businesses from threats such as cryptocurrency miners by detecting malicious files and blocking all related malicious URLs. Enterprises can also monitor all ports and network protocols for advanced threats with the Trend Micro Deep Discovery Inspector network appliance.
Trend Micro Deep Discovery Inspector protects customers from the mentioned exploits through these rules:
2573: MINER – TCP (Request)
2626: CVE-2018-7600 – Drupal Remote Code Execution – HTTP (Request)
2786: ThinkPHP 5x Remote Code Execution – HTTP (Request)
2887: CVE-2019-3396 – ATLASSIAN CONFLUENCE – HTTP (Request)
Indicators of compromise (IoCs):
URLs:
hxxps://pastebin[.]com/raw/xvfxprtb
hxxp://m[.]jianlistore[.]com/images/qrcode/1414297571.jpg
xmr[.]pool[.]minergate[.]com:45700
xmr-eu1[.]nanopool[.]org:14444
xmr-asia1[.]nanopool[.]org:14444
Wallet address:
489N5AAY5igKmcD7gfYxmg6GrGJEXy46HbX23XRTHe1JYiSg4yo9iwBW9XcoCKaJ9xXbwBVSndKerbMvZdwoHMb23QyAFtz
SHA256 Detection name 2acf625f3842a6dfebf3ffa1df565ec48837838bd503a3f6c5f46a7c6564c6c9 Coinminer.Linux.TOOLXMR.AC.component 53622ec8ed5381230734e4695be737ff804ccb3f0e3ba241dda24bb00f37bd4d Trojan.Linux.GOSCAN.BB 6c3c0cd32e9b78485c5acec11a3d44f7a72a06d90ba0f3bfc260ea9698028797 Trojan.Linux.GOSCAN.BB 84fb31603c05804c17a2c6747927c48f3ef7d03986a50ecc5efe5cf9c9d830f5 Coinminer.Linux.TOOLXMR.AC 9295b6b635cd6e33b8f5589d142d95f7cfcc48abde4193374433fa3a379f0c5a Trojan.SH.SQUELL.CC 9ea5a0e97e9ddcfce5b068426593de4f6e81fbddde50930c20eee74c779dd7e7 Coinminer.Linux.TOOLXMR.AC eb3b284bcfce567d059f47df46a777d600499c413e86310c9a95ae8edc8f0156 Trojan.SH.SQUELL.CB
The post Golang-based Spreader Used in a Cryptocurrency-Mining Malware Campaign appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro Golang-based Spreader Used in a Cryptocurrency-Mining Malware Campaign Original Post from Trend Micro Author: Trend Micro by Augusto Remillano II and Mark Vicente We found a Golang-based spreader being used in a campaign that drops a cryptocurrency miner payload.
0 notes
Text
95% off #The Complete iOS Bootcamp – $10
Learn iOS9 with Swift2 along with iOS8 and WatchKit with Actual iOS Apps with Source Code
All Levels, – 30.5 hours, 255 lectures
Average rating 4.6/5 (4.6 (20 ratings) Instead of using a simple lifetime average, Udemy calculates a course’s star rating by considering a number of different factors such as the number of ratings, the age of ratings, and the likelihood of fraudulent ratings.)
Course requirements:
We assume you have some basic knowledge of programming Knowledge of some Scripting Language Preferred, but Not Necessary
Course description:
In this iOS Bootcamp you will learn fundamentals of developing iOS applications using Swift programming language both the versions.
This course contains 255 lectures spread over 30 hours of video.
You will have access to actively ask Rick any questions you like related to the content.
At the end of the course, you’ll be able to write iOS applications that use tables, hierarchical and tabbed navigation, and understand the principles behind developing any iOS application.
The course will be complimented with shorter sessions on the various extension frameworks at a later date, including SpriteKit, SceneKit, HealthKit, WatchKit, etc
We will also cover everything you need to develop compelling apps for Apple Watch using the WatchKit framework and the Swift programming language.
We’ll cover the techniques of app development, starting with some simple apps and working our way up to more complex techniques..
We’ll build several apps together, including a simple note taker, a few different kinds of calculator, a few of games, a simple memo systems with voice recording and playback, etc.
All topics are easy to learn and presented in digestible short 5 to 15 minute videos with real world examples and demos. The course contains discussions and demos to test your skill. All demos come with full source codes that you can download which is complimentary and use for your projects.
Topics include:
Introduction to working with Xcode Data types, optionals, and tuples Collection types: arrays, sets, and dictionaries If statements and loops functions and closures Enumerations Classes and structures Stored and computed properties Inheritance in Swift Introduction to iOS Model – View – Controller and its role in iOS programming Delegation Navigation controllers and segues Tab bar controllers Table view controllers Using various cell sty les Using headers and footers Grouping vs. plain table styles Indexing a table view A case study: NoteTaker: Swift Primer Variables Functions Arrays Enumerations Classes Methods Views Arrays Enumerations Classes Methods Views Watchkit 7 real apps
I hope you join me as we explore this course together!
Full details Become and expert in App development with iOS9 Learn by example by walking you through real live projects step by step Become a Master in Developing Compelling Apps for Apple Watch using the WatchKit Framework Beginners and advanced level developers who want to learn WatchKit Framework Students wish to upgrade their Swift programming language
Reviews:
“Rick is thee Best Instructor on Udemy, IMHO! He clearly explains (to OOP beginners), the important intricacies of OOP & how Swift implements OOP, in consistent details, without skipping over anything. I’m sure even knowledgeable developers will learn from this wonderful course. He has the best explanation of Delegation I have ever heard or read before. He deserves 5 stars. I’m only up to lecture 51” (Peter Thomas)
“So far easy to understand and plenty of good examples…” (Scott Hatmaker)
“Everything is very clearly explained with examples easy to undrstand and come back to later on if necessary.” (Jesper Von Segebaden)
About Instructor:
EDUmobile Academy
EDUmobile Academy develops high quality video training courses around topics in mobile development including iPhone, Android, Windows Phone, Java, Responsive Web Design and other emerging technologies. Every course is created by an expert developer AND a trained mentor in the area of expertise. Each course undergoes a rigorous planning, review and an internal quality check phase – to ensure that the teaching is of highest standards available online. EDUmobile Academy was founded in 2008 when smart phones were just emerging into the market. Founder Vishal Lamba is experienced in multiple areas of digital design, mobile development and design, web technologies and digital marketing. He has a mathematics and computer science degree from Lawrence University, USA. Vishal works closely with content creators and teachers to ensure that every course released meets the internal rigorous quality standards. All course creators and trainers are currently based in the USA. Support for each course on Udemy is provided with quick turn around by a small team of developers and trainers.
Instructor Other Courses:
Learn Basic Commands in Linux Shell EDUmobile Academy, Programming Made Easy (120) Free Become A Full Stack Web Developer in 14 Days Learn Directives in AngularJS with Simple Demos …………………………………………………………… EDUmobile Academy coupons Development course coupon Udemy Development course coupon Mobile Apps course coupon Udemy Mobile Apps course coupon The Complete iOS Bootcamp The Complete iOS Bootcamp course coupon The Complete iOS Bootcamp coupon coupons
The post 95% off #The Complete iOS Bootcamp – $10 appeared first on Course Tag.
from Course Tag http://coursetag.com/udemy/coupon/95-off-the-complete-ios-bootcamp-10/ from Course Tag https://coursetagcom.tumblr.com/post/159663537288
0 notes
Text
Create Custom Subtotal Labels & Add Glow, 3D Effects for Shapes in Worksheet inside Android Apps
What’s new in this release?
Aspose development team is pleased to announce the new release of Aspose.Cells for Android v16.12.0. This release includes a number of new features, enhancements and bug fixes that further improve the overall stability and usability of the API. It has added the support for the creation of custom subtotal labels allowing the application developers to customize the labels according to the region or personal preferences. In order to provide this feature, the latest version of the Aspose.Cells for Android has exposed the GlobalizationSettings class offering the following 2 methods which can be overridden in a custom class to get desired labels for the Subtotals. The GlobalizationSettings class also offers the getOtherName method which is useful to give the “Other” label of Pie charts a custom value. Sometimes, application requirement could be to load just a particular type of objects while loading existing spreadsheets in Aspose.Cells’ object model. For instance, users may require to load only the cells along with formulas & formatting or just the document properties. Aspose.Cells APIs now provide a flexible yet comprehensive mechanism to achieve such requirements by exposing the LoadFilter class. The LoadFilter class along with LoadOptions.LoadFilter property can control the type of data/objects to be loaded while initializing an instance of Workbook from a template file. The constructor of the LoadFilter class can accept constant(s) from the LoadDataFilterOptions enumeration that specifies the type of objects to be loaded. It has added the support for reflection effects for a Shape object as Excel provides it via Effects tab under Format Shape dialog as shown on the blog announcement page. It has also added the support for Shadow Effects for a Shape object as Excel provides it via Effects tab under Format Shape dialog. It also supports the Glow Effects for a Shape object and 3-D Formats for Shape objects as Excel provides it via Effects tab under Format Shape dialog. Aspose.Cells for Android APIs now supports to add WordArt objects with built-in styles. In order to provide this feature, it has exposed the ShapeCollection.AddWordArt method along with PresetWordArtStyle enumeration which together allows to add preset WordArt objects since Excel 2007. It has fixed a few critical bugs as well as enhanced its core for more stability. This release includes plenty of improved features and bug fixes as listed below
Support Subtotal/Total labels in other languages
Specify Chart points' positions
Refreshing PivotTable is not working in the rendered PDF file
XLSM becomes corrupted by simple load and save operation
Hyperlinks are not working as expected after converting spreadsheet to HTML
Some characters do not render in the output PDF
Order of chart legend changed in Chart's PDF
Z order of high-low lines is not correct in PDF
Spreadsheet becomes corrupted after re-saving with Aspose.Cells
Formula is changed after inserting to a cell
Strange behaviour with simple bean using Smart Markers
Cell's text overflows to next cell
CalculateFormula has issue to recalculate cells with reference to cells with formulas
Hebrew control characters are not rendered correctly in PDF
XLS to PDF conversion is taking too much time
Layout problem when converting spreadsheet to PDF
X-axis labels are overlapping with Legend when rendered to PDF
Picture does not scale well and its SVG file is not correct
Incorrect rendering of Chart while converting spreadsheet to HTML
Spaces are omitted from text in PNG output of Chart
Selection or check state not saved when saving to PDF
Text and text alignment is messed up in the file
Extending MS Excel table/ list object changes cells formatting
Adding Arc to a new Workbook generates a potentially unsafe spreadsheet
Table column resolving broken if containing '['
Issue with extending Excel Table/List Object content regarding formulas
Incorrect formula returned from a worksheet cell
XLSM becomes corrupted after re-save operation
DataBar width is not correct while converting spreadsheet to HTML
Orange Row is not included in the Sum of Pivot Table
Image is cut off in the output HTML
Chart is missing while converting spreadsheet to HTML
Row height is not correct while converting XLSX to HTML
DCOUNTA Excel formula is not evaluated fine by Aspose.Cells formula calculation engine
Issue with DataBar Conditional Formatting when Saving an XLSM file as PDF
The space between certain characters gets removed at a few places in the output PDF file
Chart labels are not displayed/rendered the same (as per the original Excel file) in the output PDF file
Issue with font attributes of TextBox in the output PDF
TextBox's content color & size is changed while converting worksheet to EMF
TextBox's content color & size is changed while converting spreadsheet to PDF
Hebrew words are not rendered correctly when converting an Excel file to PDF file format
Content in TextBox is clipped while rendering spreadsheet to PDF
Arrowed lines are misplaced while rendering spreadsheet to PDF
Issue with the SVG image of the Chart in the rendered HTML file
Font substitution does not seem to take effect for Chart legend while using Chart.toPdf
Legend overlapping with text in Chart's PDF
Incorrect ChartPoint's ShapeXPx & ShapeYPx values
Incomplete rendering of the Rectangle shape while converting XLS to HTML
Text is getting truncated while converting spreadsheet to PDF file format
Extra pages are added due to some pages are not rendered completely in one PDF page
SheetRender - Invalid column index
Extending Excel Table modifies data
Opening and saving the file while using SheetRender corrupts the output Excel file
Setting the shape text changes the text style
Text of some cells like C2 and C3 gets unbold
Worksheet.autoFitColumns method does not seem to take effect when required font is not present in Linux
Unexpected background color applied to TextBoxes while rendering spreadsheet to PDF
Other most recent bug fixes are also included in this release.
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Cells for Android documentation that may guide users briefly how to use Aspose.Cells for performing different tasks like the followings.
Filtering Objects while Loading Template Spreadsheets
Managing Reflection Effects for Shapes
Overview: Aspose.Cells for Android
Aspose.Cells for Android is a MS Excel spreadsheet component that allows programmer to develop android applications for reading, writing & manipulate Excel spreadsheets (XLS, XLSX, XLSM, SpreadsheetML, CSV, tab delimited) and HTML file formats without needing to rely on Microsoft Excel. It supports robust formula calculation engine, pivot tables, VBA, workbook encryption, named ranges, custom charts, spreadsheet formatting, drawing objects like images, OLE objects & importing or creating charts.
More about Aspose.Cells for .NET
Homepage of Aspose.Cells for Android
Download Aspose.Cells for Android
#Create Custom Subtotal Labels#Render Other Label for Pie Chart#Filter Object for Loading Templates#Reflection Effects Support#Shadow Effects Support#Glow Effects Support#Android Excel API
0 notes
Text
#Linux #PrivEsc Enumeration Tools LinPeas:...
#Linux #PrivEsc Enumeration Tools LinPeas: https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS LinEnum: https://github.com/rebootuser/LinEnum LES (Linux Exploit Suggester): https://github.com/mzet-/linux-exploit-suggester Linux Smart Enumeration: https://github.com/diego-treitos/linux-smart-enumeration Linux Priv Checker: https://github.com/linted/linuxprivchecker

PEASS-ng/linPEAS at master · carlospolop/PEASS-ng - GitHub PEASS - Privilege Escalation Awesome Scripts SUITE (with colors) - PEASS-ng/linPEAS at master · carlospolop/PEASS-ng
0 notes
Photo
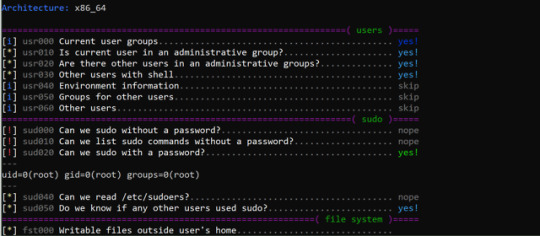
linux-smart-enumeration v1.7 releases: Linux enumeration tools for pentesting and CTFs
0 notes
Photo
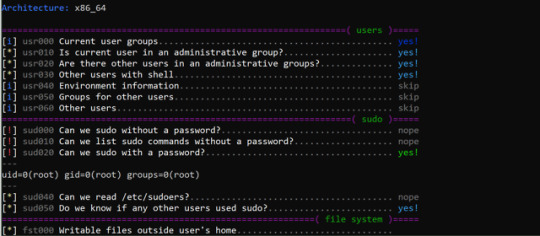
linux-smart-enumeration v1.6 releases: Linux enumeration tools for pentesting and CTFs
0 notes
Photo
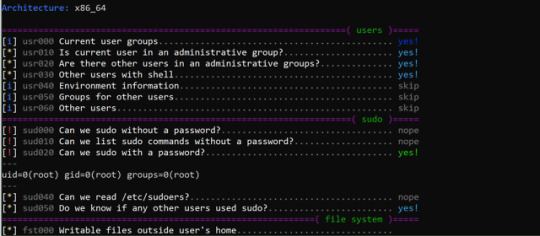
linux-smart-enumeration v1.5 releases: Linux enumeration tools for pentesting and CTFs
0 notes
Photo
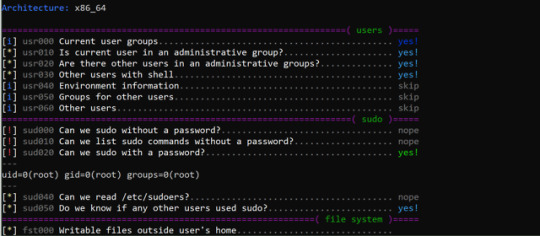
linux-smart-enumeration v1.5 releases: Linux enumeration tools for pentesting and CTFs
0 notes
Text
95% off #Getting Started with iOS 9 Development – $10
This course teaches the fundamentals of developing iOS applications using version 2 of the Swift programming language
All Levels, – 9.5 hours, 78 lectures
Average rating 4.5/5 (4.5 (28 ratings) Instead of using a simple lifetime average, Udemy calculates a course’s star rating by considering a number of different factors such as the number of ratings, the age of ratings, and the likelihood of fraudulent ratings.)
Course requirements:
We assume you have some basic knowledge of programming. Knowledge of some Scripting Language Preferred, but Not Necessary.
Course description:
This course teaches the fundamentals of developing iOS applications using version 2 of the Swift programming language.
The course is in 10 units: the first six cover the Swift language itself; the last four concentrate on the core view controller architecture of an iOS app.
At the end of the course, you’ll be able to write iOS applications that use tables, hierarchical and tabbed navigation, and understand the principles behind developing any iOS application.
The course will be complimented with shorter sessions on the various extension frameworks at a later date, including SpriteKit, SceneKit, HealthKit, WatchKit, etc. Topics include:
– Introduction to working with Xcode – Data types, optionals, and tuples – Collection types: arrays, sets, and dictionaries – If statements and loops – functions and closures – Enumerations – Classes and structures – Stored and computed properties – Inheritance in Swift – Introduction to iOS – Model – View – Controller and its role in iOS programming – Delegation – Navigation controllers and segues – Tab bar controllers – Table view controllers – Using various cell sty les – Using headers and footers – Grouping vs. plain table styles – Indexing a table view – A case study: NoteTaker: Showing the full development of an app from start to finish in seven lessons.
I hope you join me as we explore this course together.
Full details Become and expert in App development with iOS9 Learn by example by walking you through real live projects step by step Learn the fundamentals of Swift 2, programming language from Apple Students wish to upgrade their Swift programming language to Swift 2 Beginners and advanced level developers who want to learn the new and trending Swift 2 and iOS9
Reviews:
“very clear and precise.” (Jamal Ait Lhassan)
“This is information the way I like to see it. You are told what you need to know in a very well laid-out fashion. I’m getting a lot of good information from this course.” (Justin Cook)
“Clear and concise. Very good course for beginners.” (Isaac Greene)
About Instructor:
EDUmobile Academy
EDUmobile Academy develops high quality video training courses around topics in mobile development including iPhone, Android, Windows Phone, Java, Responsive Web Design and other emerging technologies. Every course is created by an expert developer AND a trained mentor in the area of expertise. Each course undergoes a rigorous planning, review and an internal quality check phase – to ensure that the teaching is of highest standards available online. EDUmobile Academy was founded in 2008 when smart phones were just emerging into the market. Founder Vishal Lamba is experienced in multiple areas of digital design, mobile development and design, web technologies and digital marketing. He has a mathematics and computer science degree from Lawrence University, USA. Vishal works closely with content creators and teachers to ensure that every course released meets the internal rigorous quality standards. All course creators and trainers are currently based in the USA. Support for each course on Udemy is provided with quick turn around by a small team of developers and trainers.
Instructor Other Courses:
Learn Basic Commands in Linux Shell EDUmobile Academy, Programming Made Easy (120) Free Become A Full Stack Web Developer in 14 Days Learn Directives in AngularJS with Simple Demos …………………………………………………………… EDUmobile Academy coupons Development course coupon Udemy Development course coupon Mobile Apps course coupon Udemy Mobile Apps course coupon Getting Started with iOS 9 Development Getting Started with iOS 9 Development course coupon Getting Started with iOS 9 Development coupon coupons
The post 95% off #Getting Started with iOS 9 Development – $10 appeared first on Course Tag.
from Course Tag http://coursetag.com/udemy/coupon/95-off-getting-started-with-ios-9-development-10/ from Course Tag https://coursetagcom.tumblr.com/post/157435914743
0 notes