#Network Security Monitoring
Explore tagged Tumblr posts
Text
These vpn sponsorships gotta stop I watched a youtuber imply they can prevent malware and viruses from infecting ur PC
#all a vpn does is route your traffic thru them#hiding ur traffic from your provider and changing ur ip address (to my understanding)#best it will do security wise is hide your traffic when acessing public networks which can be monitored by intrusive parties (hackers)#for personal info#malware n viruses are client side shit if you worried bout that uhhhhhh virtual machines? a good firewall and malware checker?#atlas.txt#original post
2 notes
·
View notes
Text
Top 5 Best Small Business Wireless Access Points for 2024

Wireless Access Points (WAPs) play a crucial role in modern networking, particularly for Internet Service Providers (ISPs). This comprehensive guide aims to demystify the world of WAPs, providing valuable insights for both seasoned professionals and those new to the field. From understanding the core principles of WAP technology to practical deployment strategies, we cover it all. Additionally, we delve into the latest trends and innovations in the industry, ensuring you're equipped with the knowledge to make informed decisions when selecting ISP supplies for your network.
Read More: Top 5 Best Small Business Wireless Access Points for 2024
#wifi6#wifi#wifi connection#free wifi#tech news#security#monitor#lady wifi#networking#wireless#internet#the internet#websites#the two towers#cambium#tp link#wisp#wisp (oc)#equipment#startup#software engineering#marketing
2 notes
·
View notes
Text
Seamless Intelligence in Your Palm: The Future of IoT Control

The next evolution in IoT app development, where AI integration, Bluetooth mesh networking, and edge computing combine to enable seamless control of smart systems. From real-time data to over-the-air updates, the mobile interface brings intelligent automation to your fingertips — built for scale, security, and sustainability.
#IoT App Development#Bluetooth Mesh Networking#Edge Computing#AI-Driven Automation#Smart City Solutions#IoT Mobile Control#Real-Time IoT Monitoring#Secure IoT Communication#OTA Firmware Updates#Low Power IoT Devices#Scalable IoT Platforms#Intelligent Device Management#IoT
0 notes
Text
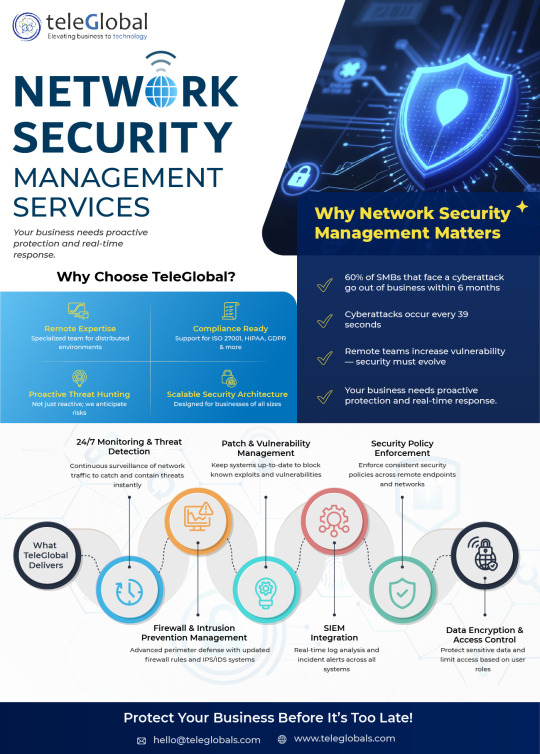
Network Management Services in Pune | Teleglobal
Empower Your Network for Efficient Performance From network setup and monitoring to firewalls and load balancer setup, we offer a secure, optimized, and high-performing network infrastructure. Our Network Management Services provides end-to-end solutions that boost network security, performance, and reliability, ensuring nothing interrupts connectivity of your business.
Optimize Your Network Today https://teleglobals.com/contact-us
#Network Management Services#Network Management#IT Infrastructure#Remote Monitoring#IT Support#Managed Services#Tech solutions#Digital Transformation#Cloud Computing#Cyber Security#Business Continuity
0 notes
Text
Why the Best Network Video Recorder is Crucial for Surveillance

In the modern era of smart security, the quality of your surveillance system can make all the difference. A Network Video Recorder (NVR) is the brain behind the camera system, managing video footage from IP cameras and ensuring it is stored securely. The best NVR systems provide high-resolution video, intelligent storage solutions, and remote access. For industries like vertical transportation, this technology is not just helpful—it’s essential. Whether it's a small business or a large facility, investing in a reliable NVR ensures you never miss a moment that matters.
When it comes to elevator surveillance, having the best network video recorder isn’t just a bonus—it’s a necessity. Elevators present a unique challenge for surveillance due to their confined space and constant movement. A top-tier NVR must be compatible with compact, high-definition cameras and deliver real-time footage without lag. Moreover, it needs to offer ample storage and seamless access for reviewing historical footage. This becomes vital in case of emergencies, disputes, or maintenance issues. The right NVR enhances both security and operational efficiency, making it a critical tool in comprehensive elevator monitoring systems.
How Smart Surveillance Protects Elevator Passengers
Smart surveillance is transforming how elevator security is managed. Instead of relying solely on basic CCTV, modern systems integrate smart features like motion detection, real-time alerts, and cloud-based storage. These capabilities ensure that building managers and security teams receive timely updates about any unusual activity. Particularly in elevators—where incidents can escalate quickly—this proactive monitoring can be life-saving. The NVR plays a key role by coordinating camera inputs and storing video securely for future use. With better analytics and instant access, elevator passengers enjoy safer and more secure rides in residential, commercial, and public facilities.
Beyond just storing footage, the best NVRs support high-efficiency video coding (HEVC) and other compression technologies. This allows them to retain high-quality footage without requiring excessive storage space. For elevator systems, where space and connectivity can be limited, this is essential. The system must also withstand environmental challenges like vibrations or electrical fluctuations. For this reason, ruggedized, elevator-specific NVR models are now becoming the norm. These advanced systems support redundancy and remote diagnostics, helping technicians and facility managers identify and fix issues before they cause system downtime. Reliable storage and rapid access to footage are non-negotiable in elevator security.
Key Features That Define a Top-Tier NVR System
The best network video recorders are equipped with features that support a wide range of surveillance needs. Essential features include multi-channel input, real-time video processing, and remote access through secure applications. In elevator settings, they must also support integration with emergency systems and intercoms. Intelligent video analytics—such as facial recognition or people counting—can add an extra layer of monitoring. In multi-floor buildings, these features help improve passenger safety and manage elevator usage more efficiently. Another important factor is reliability; a good NVR should continue to function even during network outages, ensuring no footage is ever lost.
In elevator environments, security must balance discretion and effectiveness. This is where compact NVR designs shine. A small form factor ensures the system can be installed in tight spaces like elevator control rooms or maintenance closets. Remote monitoring allows building management to observe real-time footage without needing physical access. This saves time and enables rapid response to incidents. Furthermore, with cybersecurity concerns rising, modern NVRs come equipped with encrypted data streams and user authentication. These protections guard against unauthorized access, ensuring that both recorded and live footage are only available to authorized personnel at all times.
Tailored Elevator Security Solutions That Work
Generic surveillance solutions don’t meet the unique demands of elevator systems. This is why specialized products, such as those offered by Elevator Video Systems, are essential. Their offerings are designed specifically for elevator environments, addressing challenges like limited space, signal interference, and vibration. By combining durable hardware with high-performance software, Elevator Video Systems delivers reliable and intuitive NVR setups. These solutions ensure that footage remains clear, secure, and accessible whenever it's needed. Choosing a provider that understands the vertical transportation space ensures optimal performance, lower maintenance, and greater long-term value.
By selecting an elevator-focused surveillance provider, facilities benefit from industry-specific support and guidance. Whether it's a retrofitting project or a new installation, companies like Elevator Video Systems offer customized consultation and scalable options. This means building owners get the right number of cameras, proper NVR capacity, and expert installation. When elevator security is handled with this level of attention, the results are clear: reduced vandalism, faster incident resolution, and better passenger safety. Investing in tailored solutions makes a difference not just in performance, but in the peace of mind it delivers to everyone using the building.
The Future of Elevator Surveillance Technology
As surveillance continues to evolve, the next wave of elevator security will lean heavily into AI and cloud integration. Advanced NVRs will not only store data but analyze it in real time, identifying anomalies and alerting security teams instantly. Features like behavioral analytics and predictive maintenance are becoming part of comprehensive systems. This proactive approach minimizes downtime and improves passenger experience. The shift toward centralized, intelligent control panels makes monitoring multiple elevators across a property easier than ever. With scalable cloud solutions, security managers can access footage and insights from any device, anywhere in the world.
With the rise of smart buildings, elevator security is no longer optional—it’s a necessity. A powerful NVR system is the cornerstone of any reliable setup, bridging high-quality video capture with efficient storage and retrieval. As buildings get taller and smarter, the need for robust surveillance grows. Choosing a system built specifically for elevators ensures durability, compliance, and superior performance. Whether you're managing a high-rise condo, hospital, or commercial tower, equipping your elevators with smart surveillance powered by a top-tier NVR isn't just about protecting property—it's about protecting people. Make the right investment today, and stay ahead of tomorrow’s security challenges.
#elevator security#network video recorder#elevator surveillance#NVR system#smart surveillance#video monitoring#security technology#elevator camera#surveillance system#building security
1 note
·
View note
Text
Top 5 IT Infrastructure Monitoring Tools to Boost Your Business Performance
IT infrastructure monitoring provides insight into the overall health of your project. By collecting and analyzing data from IT infrastructure, systems, and processes, you may prevent issues, analyze performance, better optimize and scale, or identify the underlying cause of everything that occurs within your system. The world is getting increasingly digital every day. This puts pressure on…

View On WordPress
#business#Business Intelligence#Information Technology#infrastructure#IT infrastructure monitoring#it infrastructure monitoring software#IT infrastructure monitoring tools#IT infrastructure security#it monitoring systems#it network monitoring#ITIM#ITIM tools#monitoring system it#technology
0 notes
Text
Container Security Market to Reach $12.75 Billion by 2032

Meticulous Research®—a leading global market research company, published a research report titled ‘Container Security Market—Global Opportunity Analysis and Industry Forecast (2025-2032)’. According to this latest publication from Meticulous Research®, the container security market is expected to reach $12.75 billion by 2032, at a CAGR of 23.6% from 2025 to 2032.
Rising integration of AI and ML technologies in container security solutions, increasing acceptance of cloud-native microservices architectures, and growing risks of cyberattacks in business operations are factors driving the growth of the container security market. However, market growth is restrained by budgetary issues among SMEs and a scarcity of skilled workforce.
In addition, the expanding utilization of the zero-trust security model and the development of vulnerability scanning tools and practices create growth opportunities for market players. The market faces substantial challenges, including frequent security patches and updates and integration of container security solutions with legacy systems. However, enhancing container management with complementary technologies is a prominent technology trend in the container security market.
Key Players
The container security market is characterized by a moderately competitive scenario due to the presence of many large- and small-sized global, regional, and local players. The key players operating in the container security market are Microsoft Corporation (U.S.), Google LLC (A Subsidiary of Alphabet Inc.) (U.S.), Cisco Systems, Inc. (U.S.), Check Point Software Technologies Ltd. (Israel), Amazon.com, Inc. (U.S.), International Business Machines Corporation (U.S.), Tenable, Inc. (U.S.), Zscaler, Inc. (U.S.), Palo Alto Networks, Inc. (U.S.), Broadcom Inc. (U.S.), Juniper Networks, Inc. (U.S.), Trend Micro Incorporated. (Japan), CrowdStrike Inc. (U.S.), Rapid7 LLC (U.S.), Qualys, Inc. (U.S.), McAfee, LLC (U.S.), Fidelis Security, LLC (U.S.), Sophos Ltd. (U.K.), Anchore, Inc. (U.S.), Docker, Inc. (U.S.), and Aqua Security Software Ltd. (Israel).
The container security market is segmented based on offering, deployment mode, organization size, application, and end-use industry. The report also evaluates industry competitors and analyzes the container security market at the regional and country levels.
Among the offerings studied in this report, the solutions segment is anticipated to dominate the container security market in 2025, with a share of 74.0%. The rapid growth of container security solutions to automate scanning for vulnerabilities and real-time monitoring of container activities and the increased need for unified security management platforms to allow for centralized control over container security policies and configurations are factors contributing to the segment’s dominant position in the container security market.
Among the deployment modes studied in this report, the cloud-based segment is anticipated to dominate the container security market in 2025, with a share of 56.0%. The High growth of cloud-based container security solutions to manage multiple environments and regions of business applications and the rise in technological advancement in cloud-based solutions such as AI and ML to enhance threat detection and anomaly detection are factors contributing to the segment’s dominant position in the container security market.
Among the organization sizes studied in this report, in 2025, the large enterprises segment is anticipated to dominate the container security market, with a share of 67.0%. Growth in the adoption of container security solutions in large enterprises for real-time monitoring of applications for tracking container activity, network traffic, and interactions and the rise in security solutions to mitigate threats and minimize security incidents for large enterprises with complex IT environments are factors contributing to the segment’s dominant position in the container security market.
Among the applications studied in this report, in 2025, the vulnerability management segment is anticipated to dominate the container security market, with a share of 28.0%. High growth in container security solutions by integrating continuous integration/continuous deployment (CI/CD) pipeline for vulnerabilities and rapid use of security solutions for vulnerability management by automating scanning and remediation processes threat intelligence and improving overall visibility and compliance are factors contributing to the segment’s dominant position in the container security market.
Among the end-use industries studied in this report, in 2025, the IT & telecommunications segment is anticipated to dominate the container security market, with a share of 24.0%. The rise in the growth of container security solutions to provide up-to-date information on emerging threats and vulnerabilities for threat intelligence and the rise in the adoption of container security solutions in IT & telecommunications to run applications across different environments to identify and address security vulnerabilities are factors contributing to the segment’s dominant position in the container security market.
Geographic Review
This research report analyzes major geographies and provides a comprehensive analysis of North America (U.S., Canada), Europe (Germany, U.K., France, Italy, Netherlands, Spain, Sweden, and Rest of Europe), Asia-Pacific (Japan, China, India, South Korea, Singapore, Australia & New Zealand, Indonesia, and Rest of Asia-Pacific), Latin America (Brazil, Mexico, and Rest of Latin America), and the Middle East & Africa (UAE, Saudi Arabia, Israel, and Rest of Middle East & Africa).
Among the geographies studied in this report, in 2025, North America is anticipated to dominate the container security market, with a share of 38.0%. High growth in vulnerability scanning tools and practices in organizations, rise in the integration of AI and ML technologies in container security solutions, and rapid growth in vulnerabilities and cyberattacks in business operations in the region are factors contributing to the segment’s dominant position in the container security market.
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=6070
Key Questions Answered in the Report:
What is the value of revenue generated by the sale of container security?
At what rate is the global demand for container security projected to grow for the next five to seven years?
What is the historical market size and growth rate for the container security market?
What are the major factors impacting the growth of this market at global and regional levels?
What are the major opportunities for existing players and new entrants in the market?
Which offering, deployment mode, organization size, application, and end-use industry segments create major traction in this market?
What are the key geographical trends in this market? Which regions/countries are expected to offer significant growth opportunities for the manufacturers operating in the container security market?
Who are the major players in the container security market? What are their specific product offerings in this market?
What recent developments have taken place in the container security market? What impact have these strategic developments created on the market?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Container Security Market#Container Monitoring#Container Scanning Tools#Container Network Security#Container Runtime Protection#Container Orchestration
0 notes
Text
Top 10 Live Cyber Attack Maps Digital Threats Visualisation
Digital crime has escalated to unprecedented levels, with cybercriminals generating approximately 1.5 trillion dollars annually in illicit profits. As major organisations like GitHub face increasingly sophisticated attacks daily, understanding the global landscape of cyber threats becomes crucial. Live cyber attack maps provide real-time visualisation of digital threats, offering valuable…
#cyber attack maps#cybercrime visualisation#cybersecurity#DDoS attacks#digital threats#Malware#malware monitoring#Monitor#Monitoring#network security#News Articles#real-time security#Security#threat intelligence#threat monitoring
0 notes
Link
#accesspoint#cloud#configuration#Controller#firewall#Install#IT#Monitoring#networkmanagement#networking#Performance#Security#self-hosted#Server#systemadministration#Ubiquiti#Ubuntu22.04#Ubuntu24.04#UniFi#WiFi#Wireless
0 notes
Text
#Network Performance Monitoring Market#Network Monitoring Solutions#Market Research Report#IT Infrastructure Monitoring#Network Performance Management#Cloud Network Monitoring#Network Optimization Tools#Market Size and Forecast#Network Security and Performance#Real-Time Network Monitoring#Competitive Landscape#Network Analytics and Insights#Emerging Trends in Network Monitoring#Software-Defined Networking (SDN) Monitoring#Network Troubleshooting Tools#Global Network Monitoring Market#AI in Network Performance Monitoring#Network Performance for Enterprises#5G Network Monitoring#Network Health and Diagnostics
0 notes
Text
The Backbone of Business Success: Reliable IT and AV Workforce Solutions
In today’s fast-paced digital world, businesses rely heavily on technology to stay ahead. Whether it’s IT infrastructure or AV systems, having the right support in place is crucial. Reliable IT and AV Workforce Solutions ensure that organizations operate seamlessly without unexpected disruptions.

Technology downtime can lead to significant losses, both in productivity and revenue. That’s why companies need 24/7 Network Monitoring Services to keep their systems running smoothly at all times. With constant surveillance, potential issues are detected and resolved before they escalate into major problems.
Security threats are on the rise, making Proactive IT Security Solutions more important than ever. Businesses must protect their networks, data, and devices from cyber threats that could compromise sensitive information. A well-managed security strategy keeps operations safe from evolving risks.
At Avcom Infotech Pvt. Ltd., we understand that a strong IT and AV backbone is essential for any business. That’s why we provide Skilled Managed Workforce for AV Systems to ensure optimal functionality. From setup to troubleshooting, our experts are equipped to handle every technical challenge.
Imagine a scenario where an unexpected system failure brings your operations to a halt. With Reliable IT and AV Workforce Solutions, businesses can prevent such occurrences by having a dedicated team to address IT concerns in real time. A proactive approach minimizes downtime and maximizes efficiency.
With 24/7 Network Monitoring Services, companies can detect unusual network activity instantly. This level of monitoring reduces the risk of cyberattacks and system failures, allowing businesses to focus on growth rather than IT concerns.
Cybersecurity should never be an afterthought. By implementing Proactive IT Security Solutions, organizations can safeguard themselves from hackers, malware, and phishing attempts. Prevention is always better than cure when it comes to digital security.
A robust AV setup is just as critical as IT infrastructure. Businesses that rely on conference rooms, digital displays, or virtual events need a Skilled Managed Workforce for AV Systems to ensure flawless execution. Technical glitches during an important meeting can leave a poor impression—having experts on board eliminates that risk. Technology should be a driving force, not a challenge. That’s why investing in Reliable IT and AV Workforce Solutions makes all the difference. Whether you need 24/7 Network Monitoring Services or Proactive IT Security Solutions, Avcom Infotech Pvt. Ltd. is here to support your business every step of the way.
#Reliable IT and AV Workforce Solutions#24/7 Network Monitoring Services#Proactive IT Security Solutions#Skilled Managed Workforce for AV Systems
0 notes
Text
https://www.esds.co.in/blog/managed-security-service-provider-mssp/
#Managed Security Service Provider#MSSP#MSP vs MSSP#SOC services#data protection#IT security#cloud security#network security#security monitoring#vulnerability management#threat management
0 notes
Text
MeshTek’s Smart IoT Framework: Building the Future of Connected Systems

MeshTek’s advanced IoT development service in action — where powerful software meets real-time automation. From smart connectivity to integrated mesh-based communication, the setup represents how businesses can monitor, manage, and optimize connected devices through a seamless, intelligent platform. The background workspace and digital overlays highlight MeshTek’s vision for scalable, secure, and low-latency IoT ecosystems designed for the modern world.
#MeshTek#IoT development service#Bluetooth mesh IoT#connected devices#smart automation#real-time IoT monitoring#low-latency communication#industrial IoT platform#smart infrastructure#scalable IoT systems#IoT software development#next-gen connectivity#AI-powered IoT#secure IoT network#edge computing solutions#smart business automation#intelligent IoT services#future-ready technology#MeshTek solutions#IoT mesh technology
0 notes
Text
Stay Ahead of the Curve: Why Entrepreneurs Are Turning to Auvik for Cloud-Based Network Management
🚀 Stay Ahead of the Curve with Auvik Networks! 🚀 Entrepreneurs, are you ready to streamline your business and boost efficiency? 📈 Discover how Auvik's cloud-based network management is helping businesses improve operational efficiency by up to 42%!
As more businesses turn to digital solutions, network management software has become a critical factor in boosting efficiency—companies that invest in automated IT management see up to a 42% improvement in operational efficiency by reducing downtime and IT labor costs. Auvik Networks, founded in 2011, is a Canadian company providing cloud-based network management solutions, primarily serving…
#Auvik Network Management#Auvik Networks review#business#Business network monitoring#Cloud solutions for entrepreneurs#Cloud-based network tools#Entrepreneurs#Free trial#IT automation for businesses#Managed Service Providers (MSPs)#Network management#Network security and visibility#Networking#Networking tools#news#Scalable IT solutions#startups#Tech solutions for startups
0 notes
Text
#🔐 Robust Security Measures: Cisco firewalls provide advanced security protocols#enabling organizations to monitor and control incoming and outgoing network traffic efficiently! 💪✨#CiscoFirewalls#NetworkSecurity#Cybersecurity#📈 Scalability & Flexibility: With solutions like the ASA and Firepower series#Cisco firewalls can adapt to various network sizes and requirements#ensuring your business remains secure as it grows! 🚀🔄#Scalability#CiscoASA#Firepower#🛡 Stateful Inspection Technology: Utilizing stateful firewalls#Cisco effectively tracks active connections and makes real-time decisions about which packets to allow or block#enhancing overall network performance! ⚙📊#StatefulFirewall#NetworkPerformance#Cisco
1 note
·
View note
Text
Network Operating Systems Market: Trends, Innovations, and Future Outlook
In today’s digital-first world, where enterprises and service providers rely on highly connected infrastructures, the role of Network Operating Systems (NOS) has become more critical than ever. From managing internal communications to supporting global cloud-based applications, NOS platforms are at the core of networking architecture. As demands grow, NOS solutions must evolve—emphasizing…

View On WordPress
#a network operating system#ai#artificial intelligence#best network os#business#Business Intelligence#computer network operating system#Digital Transformation#edge computing#Information Security#Information Technology#iot#IT Infrastructure#Machine Learning#ML#Network Automation#network innovation#network management in operating system#Network Monitoring#Network Operating Systems#network scalability#Network Security#NOS#smart networks
0 notes