#Packet Data Network Gateway
Explore tagged Tumblr posts
Text
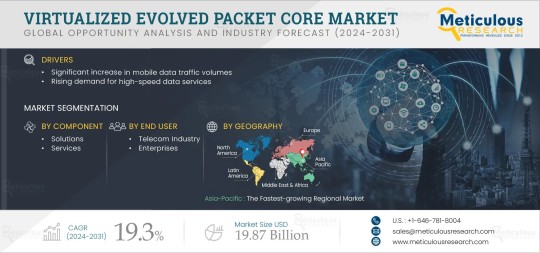
Virtualized Evolved Packet Core Market Projected to Reach $19.87 Billion by 2031
According to the latest publication from Meticulous Research®, the virtualized evolved packet core (vEPC) market is projected to reach $19.87 billion by 2031, growing at a CAGR of 19.3% from 2024 to 2031. This growth is driven by the significant increase in mobile data traffic volumes and the rising demand for high-speed data services. However, data security risks associated with vEPC infrastructure pose challenges to market growth.
#Virtualized Evolved Packet Core Market#VEPC Market#Mobility Management Entity#Home Subscriber Server#Packet Data Network Gateway#Policy and Charging Rules Function#Mobile Private Network & Mobile Virtual Network Operator (MPN & MVNO)#Long-term Evolution & Voice over Long-term Evolution (LTE & VoLTE)#Telecom Operators#Internet of Things & Machine to Machine
0 notes
Text
What is the difference between LoRa and LoRaWAN?
Introduction:
LoRaWAN serves as the communication protocol connecting the LoRa signal (which carries sensor data) to the respective application(s). To simplify, think of LoRa as the radio signal transporting the data, while LoRaWAN acts as the governing framework that dictates how this data travels and communicates within the network.

What is LoRa?
LoRa, short for Long Range, is a wireless technology known for its extended range and energy-efficient characteristics. It operates within unlicensed wireless frequencies, similar to how Wi-Fi utilizes the unregulated 2.4 GHz and 5 GHz bands. The specific frequency employed by LoRa varies depending on the geographic location of the deployment. For instance, in North America, LoRa operates in the 915 MHz band, while in Europe, it utilizes the 868 MHz band and in India it is 865 MHz to 867 MHz.
It is crucial to be aware of the legally permitted frequencies for LoRa deployments in each respective location. In terms of its communication range, LoRa can transmit data up to a distance of 10 kilometers in ideal conditions with a clear line of sight.
Low Power Wide Area (LPWA) technology can be categorized into two main types. On one hand, there's cellular LPWA, which utilizes mobile networks. Examples of cellular LPWA technologies include Narrowband IoT (NB-IoT) and Long Term Machine Type Communications (LTE-M). On the other hand, there's non-cellular LPWA like LoRa, which disseminates data by dividing it into encoded packets and transmitting them across various frequency channels and data rates.
What is LoRaWAN?
LoRaWAN is a network protocol that serves as the bridge between the LoRa signal, which carries sensor data, and the applications that use this data. In simpler terms, LoRa represents the radio signal responsible for transmitting the data, while LoRaWAN is the communication protocol that manages and defines how this data is transmitted across the network.
LoRaWAN offers several valuable advantages, including low power consumption, extensive coverage range, and cost-effective connectivity for devices that don't require high data transfer speeds. It's an excellent choice when cellular connectivity is too expensive or Wi-Fi coverage is unavailable. Some of the most compelling use cases for LoRaWAN include:
Agriculture: LoRaWAN's long-range capabilities provide reliable connectivity for rural applications where high data transfer rates are not necessary, making it ideal for agricultural applications. LoRaWAN sensors for agriculture are used for cattle management, soli monitoring, and temperature monitoring.
Asset Tracking and Logistics: LoRaWAN supports cost-effective location tracking of assets, with optimized battery life, making it a practical choice for asset management and logistics.
Smart Metering: LoRaWAN's sensors have the ability to reach even in underground utility locations makes it a suitable choice for smart metering applications.
Smart Homes: LoRaWAN can penetrate obstacles like walls and supports battery-powered devices with low data consumption, making it an attractive connectivity option for smart home applications.LoRaWAN sensors for smart homes are used for Air quality monitoring, water quality monitoring, and temperature & humidity monitoring.
Healthcare: The low power consumption, affordability, and reliability of LoRa technology make it suitable for connected health applications. IoT solutions based on LoRa hardware can monitor high-risk patients or systems around the clock, ensuring comprehensive health and medical safety management.LoRaWAN Gateways and sensors enhance production practices, enable efficient tracking and monitoring of shipments, and facilitate the development of cutting-edge medications.
Industrial Applications: LoRa-enabled devices and sensors play a crucial role in the transformation of industrial IoT operations like mentioned above. They digitize legacy processes and equipment, leading to increased profits, lower costs, and enhanced efficiency. These devices provide real-time data for predictive maintenance, machine health monitoring, reduced downtime, and more.
3 notes
·
View notes
Text
Firewall Hardware Device Market - Business Outlook and Innovative Trends | New Developments, Current Growth Status
Firewall Hardware Device Market, Trends, Business Strategies 2025-2032
The Global Firewall Hardware Device Market was valued at USD 4.92 billion in 2024 and is projected to reach USD 8.67 billion by 2032, exhibiting a CAGR of 7.3% during the forecast period. The U.S. market accounted for USD 1.8 billion in 2024, while China is expected to witness accelerated growth, reaching USD 1.2 billion by 2032.
Firewall hardware devices are specialized network security systems designed to monitor and control incoming and outgoing network traffic based on predefined security rules. These devices act as barriers between trusted internal networks and untrusted external networks, such as the internet, to prevent unauthorized access and cyber threats. The two primary types include stateless firewalls (filtering packets individually) and stateful firewalls (tracking active connections for context-aware filtering).
The market growth is driven by escalating cyber threats, stringent data protection regulations, and the rapid adoption of cloud-based infrastructure. Enterprises increasingly prioritize advanced threat prevention capabilities, such as intrusion detection and deep packet inspection. Leading players like Cisco, Palo Alto Networks, and Fortinet dominate the market, collectively holding over 45% revenue share in 2024. Recent innovations include AI-powered firewalls and hybrid models supporting SD-WAN integration.
Our comprehensive Market report is ready with the latest trends, growth opportunities, and strategic analysis. https://semiconductorinsight.com/download-sample-report/?product_id=103347
Segment Analysis:
By Type
Stateful Firewall Segment Leads Due to Its Advanced Network Threat Detection Capabilities
The market is segmented based on type into:
Stateless Firewalls
Subtypes: Packet filtering firewalls, circuit-level gateways
Stateful Firewalls
Subtypes: Next-generation firewalls (NGFW), unified threat management (UTM) systems
Application-level gateway firewalls
Proxy firewalls
Others
By Application
Business Segment Dominates with Rising Cybersecurity Needs Across Enterprises
The market is segmented based on application into:
Home networks
Business networks
Subtypes: Small & medium enterprises, large enterprises
Government organizations
Cloud service providers
Others
By Deployment
On-Premises Deployment Remains Prevalent for Critical Infrastructure Security
The market is segmented based on deployment into:
On-premises solutions
Cloud-based solutions
Hybrid deployment
By Organization Size
Large Enterprises Account for Significant Adoption Due to Complex Network Infrastructures
The market is segmented based on organization size into:
Small & medium enterprises (SMEs)
Large enterprises
Regional Analysis: Firewall Hardware Device Market
North America The North American firewall hardware market is characterized by high adoption rates driven by stringent cybersecurity regulations and increasing cyber threats. The U.S. alone accounts for over 40% of the global market revenue, propelled by widespread enterprise digitization and government mandates like NIST frameworks. Large-scale migrations to cloud environments and remote work infrastructures continue to fuel demand for next-generation firewalls with advanced threat detection capabilities. Industry leaders such as Palo Alto Networks, Cisco, and Fortinet dominate the landscape through continuous product innovation in AI-powered security solutions. Canadian adoption focuses heavily on compliance with PIPEDA data protection laws, though telecom and financial sectors show particularly strong demand for high-throughput firewall appliances.
Europe Europe’s firewall hardware market grows steadily under GDPR compliance requirements and increasing cyberattack sophistication. Germany and the UK collectively represent over 50% of regional firewall investments, particularly in manufacturing and banking sectors. The EU’s Network and Information Systems (NIS) Directive pushes critical infrastructure operators toward stateful inspection firewalls with deep packet inspection capabilities. However, price sensitivity in Southern European markets favors unified threat management solutions over premium standalone firewall appliances. Recent supply chain disruptions have accelerated localization trends, with EU-based firms increasingly sourcing from regional providers like Sophos and Barracuda Networks to ensure continuity.
Asia-Pacific APAC represents the fastest-growing firewall hardware market, projected to exceed 30% CAGR through 2032 due to rapid digital transformation across enterprises. China’s cybersecurity law mandates comprehensive firewall deployments across all critical industries, creating massive demand for domestically manufactured solutions from Huawei and H3C. India’s market expansion correlates with rising broadband penetration and SME digitization, though budget constraints drive preference for SMB-focused offerings from Ubiquiti and Mikrotik. Japan and South Korea emphasize high-performance solutions capable of handling 5G network security workloads, while Southeast Asian nations increasingly adopt cloud-managed firewall hardware to overcome IT skill shortages.
South America The South American firewall hardware market shows moderate but inconsistent growth patterns. Brazil accounts for nearly 60% of regional firewall spending, concentrated in the financial and oil/gas sectors where cyber threats pose existential risks. However, economic instability and currency fluctuations frequently delay enterprise security upgrades, causing extended replacement cycles for existing firewall infrastructure. Price competition remains fierce, with regional buyers prioritizing basic functionality over advanced features. This has led major vendors to establish local manufacturing partnerships and introduce scaled-down appliance models specifically for cost-conscious Latin American markets.
Middle East & Africa MEA presents a bifurcated firewall hardware landscape. Gulf Cooperation Council countries demonstrate sophisticated demand, with UAE and Saudi Arabia investing heavily in military-grade firewall solutions for smart city projects and oil infrastructure protection. Israeli cybersecurity innovation spills over into commercial firewall appliances featuring behavioral analysis capabilities. Meanwhile, African adoption remains constrained by limited enterprise IT budgets, though Chinese vendors gain traction through government-backed infrastructure projects. The region’s overall growth potential remains strong as cyber insurance requirements and mobile payment security concerns drive basic firewall adoption beyond traditional enterprise buyers.
List of Key Firewall Hardware Device Manufacturers
Cisco Systems (U.S.)
Palo Alto Networks (U.S.)
Fortinet (U.S.)
NETGEAR (U.S.)
SonicWall (U.S.)
Sophos (U.K.)
WatchGuard Technologies (U.S.)
Juniper Networks (U.S.)
Barracuda Networks (U.S.)
Huawei (China)
The global firewall hardware market is experiencing strong growth driven by escalating cyber threats across industries. Recent data indicates cyberattacks have increased by nearly 40% year-over-year, with ransomware incidents particularly targeting vulnerable network infrastructures. This surge has compelled enterprises to prioritize advanced security solutions, with next-generation firewall hardware deployments growing at approximately 15% annually. Large-scale breaches costing organizations an average of $4.5 million per incident have made firewall investments mandatory rather than optional for most businesses.
Stringent data protection regulations globally are significantly contributing to firewall hardware adoption. The implementation of frameworks like GDPR in Europe and CCPA in California has made enterprise-grade firewalls essential for compliance. Recent enforcement actions with penalties exceeding $1 billion collectively have demonstrated the consequences of inadequate network security measures. Over 60% of organizations now consider compliance requirements as the primary driver for firewall hardware upgrades, particularly in regulated sectors like healthcare and finance where data sensitivity is paramount.
The post-pandemic shift to hybrid work models has fundamentally changed network security requirements. Enterprise networks now extend beyond traditional office perimeters, with remote employees accessing corporate resources from various locations. This distributed architecture has increased the average attack surface by nearly 35%, compelling organizations to deploy sophisticated firewall solutions. The market is responding with innovative offerings, such as the recent launch of SD-WAN integrated firewall appliances that provide centralized management for dispersed network environments.
The accelerating shift to cloud infrastructure presents substantial growth opportunities for firewall hardware vendors. Over 75% of enterprises now operate hybrid environments combining on-premises and cloud resources, driving demand for unified security solutions. The market is responding with innovative offerings like cloud-managed firewall appliances that provide consistent policy enforcement across distributed networks. Recent product launches demonstrate this trend, with major vendors introducing hardware specifically optimized for securing cloud edge environments.
The global 5G infrastructure buildout is creating significant opportunities for next-generation firewall solutions. Telecom operators are investing heavily in security for their 5G core networks, with firewall expenditures projected to grow at 18% CAGR through 2030. This market segment requires specialized high-throughput appliances capable of processing traffic at multi-gigabit speeds while maintaining stringent security controls. Recent developments include purpose-built 5G firewall solutions achieving throughputs exceeding 100Gbps without compromising security functionality.
The integration of artificial intelligence into firewall hardware represents a transformative market opportunity. AI-enhanced threat detection capabilities are proving particularly effective, with some solutions demonstrating 95% accuracy in identifying zero-day attacks. Major vendors are actively acquiring AI security startups and incorporating machine learning algorithms directly into firewall appliances. These advanced capabilities command premium pricing while reducing operational overhead through automated policy management and threat response.
The market is highly fragmented, with a mix of global and regional players competing for market share. To Learn More About the Global Trends Impacting the Future of Top 10 Companies https://semiconductorinsight.com/download-sample-report/?product_id=103347
Key Questions Answered by the Firewall Hardware Device Market Report:
What is the current market size of Global Firewall Hardware Device Market?
Which key companies operate in Global Firewall Hardware Device Market?
What are the key growth drivers?
Which region dominates the market?
What are the emerging trends?
Browse More Reports:
CONTACT US:
City vista, 203A, Fountain Road, Ashoka Nagar, Kharadi, Pune, Maharashtra 411014
[+91 8087992013]
0 notes
Text
Inline System Market: Emerging Trends and Business Opportunities 2025–2032
Inline System Market, Trends, Business Strategies 2025-2032
The global Inline System Market size was valued at US$ 298.6 million in 2024 and is projected to reach US$ 467.2 million by 2032, at a CAGR of 5.7% during the forecast period 2025-2032
Our comprehensive Market report is ready with the latest trends, growth opportunities, and strategic analysis https://semiconductorinsight.com/download-sample-report/?product_id=103489
MARKET INSIGHTS
The global Inline System Market size was valued at US$ 298.6 million in 2024 and is projected to reach US$ 467.2 million by 2032, at a CAGR of 5.7% during the forecast period 2025-2032.
Inline systems are network devices that receive and forward data packets to their intended destinations. These systems form the backbone of modern network infrastructure, including routers, switches, firewalls, intrusion detection/prevention systems, and web application firewalls. The technology plays a critical role in cybersecurity, data flow optimization, and network traffic management across industries.
The market growth is driven by increasing digital transformation initiatives, rising cybersecurity threats, and expanding industrial automation. While North America currently leads in market share with the U.S. contributing approximately 38% of global revenues, Asia-Pacific is witnessing the fastest growth due to rapid infrastructure development. The online automation segment is particularly strong, projected to maintain a 7.2% CAGR through 2032 as manufacturers prioritize Industry 4.0 solutions. Key players like OLBRICH GmbH and Von Ardenne Institut GmbH are expanding their portfolios to address evolving demands in sectors ranging from automotive to medical technology.
List of Key Inline System Manufacturers
OLBRICH GmbH (Germany)
Von Ardenne Institut GmbH (Germany)
Horizon GmbH (Germany)
MIMOT GmbH (Germany)
E. Zoller GmbH & Co. KG (Germany)
INTEGO GmbH (Germany)
RAYONICS (Switzerland)
BST eltromat International GmbH (Germany)
GÖPEL electronic GmbH (Germany)
Vision Tools Bildanalyse Systeme GmbH (Germany)
HEUFT SYSTEMTECHNIK GmbH (Germany)
ISRA VISION PARSYTEC AG (Germany)
IT Concepts GmbH (Germany)
Inline System Market Segment Analysis
By Type
Online Automation Segment Dominates with Increasing Adoption in Industrial IoT and Smart Manufacturing
The market is segmented based on type into:
Online Automation
Offline Automation
By Application
Automotive Industry Segment Leads Owing to High Demand for Production Line Automation
The market is segmented based on application into:
Mechanical Engineering
Automotive Industry
Aerospace
Oil and Gas
Chemical Industry
Medical Technology
Electrical Industry
By End User
Manufacturing Plants Hold Major Share Due to Industry 4.0 Adoption
The market is segmented based on end user into:
Manufacturing Plants
Research Facilities
Industrial Facilities
Laboratories
By Technology
Network Security Applications Drive Demand for Advanced Inline Systems
The market is segmented based on technology into:
Routers and Switches
Firewall Systems
Intrusion Detection Systems
Antivirus Gateways
Web Application Firewalls
Regional Analysis: Inline System Market
North America The U.S. dominates the North American inline system market, leveraging advanced manufacturing ecosystems and high adoption of Industry 4.0 technologies. With major players like Cisco and Palo Alto Networks headquartered here, the region benefits from strong R&D in network security and automation solutions. The increasing need for real-time data processing in sectors like aerospace and automotive (where 78% of manufacturers use inline inspection systems) drives demand. Furthermore, strict cybersecurity regulations (e.g., NIST standards) compel enterprises to adopt advanced inline network devices. Canada follows closely, supported by 5G infrastructure projects valued at $26 billion, which require robust inline systems for seamless operations.
Europe Europe prioritizes precision engineering and industrial automation, with Germany accounting for 30% of the region’s inline system market. EU-funded initiatives like Horizon Europe accelerate smart factory adoption, necessitating inline monitoring tools for quality control. The automotive sector (contributing 7% of EU GDP) relies heavily on inline measurement systems for defect detection. However, data privacy laws (GDPR) and high compliance costs somewhat slow cloud-based inline solution deployments. Meanwhile, the U.K. and France focus on AI-driven inline inspection in aerospace, with Airbus investing €2.5 billion annually in automation.
Asia-Pacific China, Japan, and South Korea collectively contribute over 45% of global inline system revenues, propelled by electronics manufacturing (60% of global PCB production occurs here). China’s “Made in China 2025” policy and India’s $1.3 billion PLI scheme for electronics boost demand for high-speed inline testing equipment. Japan’s dominance in robotics (supplying 52% of industrial robots globally) integrates inline sensors for precision tasks. Challenges persist in Southeast Asia, where SMEs’ cost sensitivity limits adoption of premium solutions, but government incentives for smart manufacturing are gradually changing this trend.
South America Brazil leads the regional market (65% share), especially in oil & gas inline monitoring, where Petrobras allocates $68 billion for digital transformation. The food packaging industry also adopts inline vision systems to comply with export quality standards. However, economic instability in Argentina and Venezuela restricts capital expenditure on advanced systems. Local players focus on retrofitting older machinery with cost-effective inline modules rather than full-scale automation due to budget constraints. Chile emerges as a growth pocket, supported by copper mining automation (world’s largest copper producer).
Middle East & Africa Gulf nations drive adoption through megaprojects like NEOM ($500 billion) requiring IoT-enabled inline infrastructure. The UAE’s “Industry 4.0” roadmap prioritizes inline AI analytics for manufacturing, with Dubai targeting 25% of GDP from advanced industries by 2031. In Africa, South Africa’s automotive sector (exporting 64% of production) invests in inline robotic welders. Underdeveloped IT infrastructure in other African countries slows growth, though partnerships with Chinese tech firms are bridging gaps in telecom inline systems.
MARKET DYNAMICS
Despite their advantages, inline systems face significant adoption barriers due to integration challenges with legacy infrastructure. Many manufacturing facilities operate heterogeneous equipment from multiple vendors spanning different generations, making unified inline monitoring difficult to implement. Retrofitting older production lines with modern inline inspection systems often requires substantial capital investment and production downtime, creating resistance among cost-sensitive manufacturers.
Skill Shortages The specialized nature of inline systems requires technicians trained in both industrial processes and advanced networking. However, the manufacturing sector worldwide faces a growing skills gap, with an estimated 2.1 million unfilled positions expected by 2030 due to retirements and technology shifts.
Latency Sensitivity Certain high-speed manufacturing and network applications demand sub-millisecond response times from inline systems. Achieving this performance while maintaining comprehensive inspection capabilities remains technically challenging, limiting adoption in some mission-critical applications.
The sophisticated technology embedded in modern inline systems results in significant upfront costs that deter many small and medium enterprises. Full production line inline monitoring solutions can require investments exceeding $500,000 – a prohibitive sum for organizations without large capital budgets. While larger manufacturers achieve ROI through efficiency gains and quality improvements within 2-3 years, smaller operators often cannot justify the expenditure despite the potential benefits.
Additionally, the rapid pace of technological advancement creates obsolescence concerns. Companies hesitate to invest in what they perceive as solutions that may require replacement within 5 years as next-generation alternatives emerge. This financial uncertainty further suppresses broader market adoption across cost-conscious industry segments.
The integration of artificial intelligence with inline systems creates compelling new market opportunities. AI-enhanced vibration analysis and thermal imaging systems now detect equipment anomalies before failures occur, reducing unplanned downtime by up to 45%. As predictive maintenance transitions from luxury to necessity in asset-intensive industries, demand grows for inline systems capable of continuous condition monitoring with advanced analytics capabilities.
Moreover, the medical device manufacturing sector presents significant untapped potential. With stringent quality requirements and growing regulatory scrutiny, inline vision inspection systems that incorporate machine learning for defect detection are experiencing 25% annual growth. Pharmaceutical companies similarly adopt these technologies to ensure compliance with evolving serialization and traceability mandates.
Emerging applications in renewable energy infrastructure, particularly for wind turbine and solar panel manufacturing, further expand the addressable market. As these industries scale globally, inline quality assurance becomes critical for maintaining performance standards across distributed production networks.
The market is highly fragmented, with a mix of global and regional players competing for market share. To Learn More About the Global Trends Impacting the Future of Top 10 Companies https://semiconductorinsight.com/download-sample-report/?product_id=103489
FREQUENTLY ASKED QUESTIONS:
What is the current market size of Global Inline System Market?
Which key companies operate in Global Inline System Market?
What are the key growth drivers?
Which region dominates the market?
What are the emerging trends?
Related Report:
https://semiconductorblogs21.blogspot.com/2025/07/gas-scrubbers-for-semiconductor-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/medium-frequency-system-market-economic.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/solar-charge-regulator-market-swot.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/piezoelectric-bending-actuator-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/multimode-pump-combiner-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/polarisation-separator-market-demand.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/fibre-optic-combiner-market-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/digital-displacement-sensor-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/inset-polariser-market-emerging-trends.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/channel-coil-actuator-market-revenue.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/reconfigurable-optical-wavelength.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/electroluminescent-backlight-driver.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/battery-separator-quality-control-tool.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/standard-voltage-regulator-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/radiation-resistant-converter-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/07/intelligent-memory-controller-market.html
CONTACT US: City vista, 203A, Fountain Road, Ashoka Nagar, Kharadi, Pune, Maharashtra 411014 [+91 8087992013] [email protected]
0 notes
Text
What Your Firewall Isn’t Telling You: Hidden Security Gaps Modern Businesses Can’t Ignore

Introduction: Your Firewall Is Working… or Is It?
If you're reading this, you're probably confident that your business is protected by a firewall. Good news? Not quite. Because what if the very thing you trust the most — your firewall — is quietly allowing gaps that hackers are counting on?
In the age of advanced persistent threats, evolving malware, and human error, traditional firewall setups are like castles in a world of drones. They weren’t built for today’s fast-paced, cloud security, AI-powered cyber battlefield.
At EDSPL, we believe security isn’t about adding layers — it’s about understanding what those layers are missing.
Chapter 1: Firewalls Were Designed for a Simpler Time
Once upon a time, businesses ran on static IPs, limited ports, and in-house servers. Firewalls worked as gatekeepers. But things have changed:
SaaS apps now run critical functions
Remote teams access sensitive data from coffee shops
APIs connect everything from your CRM to your IoT devices
Your firewall didn’t sign up for this level of complexity.
Keyword Focus: network security, legacy firewall limitations, modern network threats, cybersecurity for cloud era
Chapter 2: The 5 Major Gaps Your Firewall Might Be Hiding
Even if you’ve configured everything right, these five threats might still slip through:
1. Encrypted Threats (SSL/TLS Blind Spots)
Hackers hide payloads in encrypted traffic. Basic firewalls don’t inspect encrypted traffic deeply — making it the perfect cover.
🔍 Solution: EDSPL’s Advanced Deep Packet Inspection services detect threats in real time—even within encrypted streams.
2. Shadow IT & Unsanctioned Apps
Employees use tools that IT doesn’t approve. Firewalls might miss these if they mimic normal traffic patterns.
🛠 Solution: With EDSPL’s Endpoint & Application Visibility tools, you see everything happening — even what isn’t officially “visible.”
3. East-West Movement Inside the Network
Firewalls protect the perimeter, but once inside, attackers can move freely.
🔒 Solution: Microsegmentation and Zero Trust from EDSPL stop lateral movement cold.
4. APIs – The Blindly Trusted Gateways
Firewalls aren’t built for API-level validation. An exposed or misconfigured API can open floodgates.
🌐 Solution: EDSPL’s application security solutions analyze behavior and stop exploits in real time.
5. BYOD and Remote Access Risks
Your firewall doesn’t know if that phone accessing your CRM is an employee’s or a thief’s.
🧠 Solution: Identity-aware access control and mobility architecture by EDSPL create context-aware defenses.
Chapter 3: Why Compliance Isn’t Protection
Passing a security audit ≠ being secure. Firewalls may meet compliance standards but still leave you vulnerable. Think of:
Zero-day threats bypassing known signature filters
Misconfigured rules or outdated firmware
Internal user negligence (accidental or intentional)
Keyword Focus: firewall security audit, cybersecurity compliance vs. real protection
Chapter 4: Real-World Incidents — Where Firewalls Failed
🚨 Case 1: A finance firm had a Next-Gen Firewall but still suffered data exfiltration via encrypted Dropbox sync. 🚨 Case 2: An e-commerce company had a properly configured firewall, but internal movement allowed attackers to infect backup servers.
These aren’t hypotheticals. These are the new normal — and proof that a firewall alone is not enough.
Chapter 5: How EDSPL Closes These Gaps (The Right Way)
Let’s talk solutions. Here’s how EDSPL turns these weaknesses into strengths:
✅ Next-Gen Visibility
Our tools provide deep visibility across endpoints, APIs, and cloud apps.
✅ 24x7 SOC Monitoring
Our Managed and Maintenance Services detect and neutralize threats in real time — even those firewalls miss.
✅ Zero Trust Architecture
We don’t trust anything by default — not even internal traffic. Every connection is verified, authenticated, and monitored.
✅ SASE + ZTNA Integration
Move beyond hardware boundaries. EDSPL integrates identity, context, and data control into one seamless edge-to-cloud solution.
✅ Cloud-Native WAF & DDoS Protection
We defend your digital front doors at app and API levels — not just the perimeter.
Chapter 6: The Psychology of False Security
Many decision-makers stick with firewalls because it feels safe. It’s tangible. It's visible. But comfort isn’t protection.
Ask yourself:
Can your firewall detect behavior anomalies?
Does it understand your routing, switching, and compute environments?
Can it respond automatically to a breach?
If the answer is no, you’re not protected — you’re just hopeful.
Chapter 7: A Modern Security Blueprint – Built with EDSPL
Here’s a smarter architecture to replace blind firewall dependence:
Layered Detection (SIEM + SOAR)
User & Entity Behavior Analytics
Adaptive Access Controls
Threat Intelligence Integration
Endpoint + Network + Application Harmony
We include robust data center switching, storage, and backup frameworks in your enterprise blueprint.
At EDSPL, we design this blueprint around your real-world needs — not legacy models.
Conclusion: The Firewall Isn’t Dead. But It’s Not Enough.
Your firewall has served you well. But to protect your enterprise today, you need more than a wall — you need real-time visibility, behavioral intelligence, and automated response.
At EDSPL, we don’t just spot weaknesses — we rebuild security from the inside out.
Ready to see what your firewall isn’t telling you?
Call-to-Action
Book a Free Security Gap Assessment Let our experts assess your real-time firewall effectiveness and uncover blind spots before attackers do.
📞 9873117177 | 🌐 www.edspl.net | ✉️ [email protected] Reach Us or Get In Touch
Learn more about our vision
0 notes
Text

OPC UA Field eXchange (UAFX)
OPC UA Field eXchange (UAFX) is a new generation of field layer communication standard launched by the OPC Foundation, which aims to solve the core pain points of the long-standing coexistence of multiple protocols and poor device interoperability in the field of industrial automation. As an extension of the OPC UA standard, UAFX realizes end-to-end standardized data interaction from the control layer to field devices through a unified information model and communication framework, providing key infrastructure for Industry 4.0 and smart manufacturing. Its core value lies in breaking the technical barriers of traditional fieldbuses, enabling devices from different manufacturers to achieve plug-and-play interconnection without relying on dedicated gateways, while meeting the stringent requirements of modern industry for real-time, security and flexibility.
Core Functions and Applications of OPC UAFX
I. Key Features
1. Cross-vendor Interoperability
Enables seamless communication between controllers/devices from different brands through standardized OPC UA information models
Supports three-tier communication architectures: Controller-to-Controller (C2C), Controller-to-Device (C2D), and Device-to-Device (D2D)
2. Real-time Data Exchange
Delivers deterministic communication via Ethernet TSN and 5G networks
Achieves microsecond-level synchronization using UDP/IP (IEEE 802.1AS)
3. Unified Engineering Configuration
Built-in Connection Manager for automatic secure link establishment
Supports integration with standard engineering tools (e.g., FDT/DTM, AML)
4. Advanced Diagnostics
Real-time monitoring of device health (network latency, packet loss, etc.)
Asset Information Model (AIM) for full lifecycle data tracking
5. Secure Communication
Inherits OPC UA's native X.509 certificate authentication and AES-256 encryption
Complies with both functional safety (IEC 61508) and cybersecurity (IEC 62443) standards
II. Industrial Applications
1. Smart Factories
Plug-and-play configuration for PLCs, robots, AGVs, etc.
Use case: Multi-brand robot collaboration in automotive welding lines
2. Process Automation
Eliminates protocol conversion between DCS and field instruments (flow meters/temperature transmitters)
Application: Direct data transmission from smart instruments to MES in petrochemical plants
3. Motion Control
Enables precision synchronization (<1μs jitter) for servo drives and CNC equipment
Typical scenario: Multi-axis synchronization in packaging machinery
4. Energy Management
Standardized monitoring for PV inverters, energy storage PCS, etc.
Implementation: Gateway-free data acquisition for wind farm SCADA systems
III. Technical Advantages

IV. Implementation Benefits
Lower TCO: 30+% reduction in protocol conversion hardware costs
Faster Deployment: 50% shorter engineering configuration time
Higher OEE: Predictive maintenance reduces unplanned downtime
Currently supported by leading automation vendors like ABB and Siemens, UAFX is expected to achieve widespread adoption in discrete manufacturing by 2025. This standard is particularly suited for Industry 4.0 scenarios demanding high real-time performance and multi-vendor device integration.
0 notes
Text
Carrier Aggregation Solutions Market Size, Share, Analysis, Forecast, and Growth Trends to 2032 – Infrastructure Investments Fuel Market Size
Carrier Aggregation Solutions Market was valued at USD 3.92 billion in 2023 and is expected to reach USD 17.77 billion by 2032, growing at a CAGR of 18.35% from 2024-2032.
Carrier Aggregation Solutions Market is witnessing significant growth as telecom providers race to deliver faster, more reliable mobile data services. By combining multiple frequency bands, carrier aggregation enables higher throughput and enhanced spectrum efficiency—crucial for meeting the rising demand for high-speed connectivity across 4G, 5G, and beyond. The surge in mobile traffic in regions like the USA and Europe has positioned carrier aggregation as a vital enabler of next-gen network performance.
Carrier Aggregation Solutions Gain Momentum in U.S. 5G Rollout Strategy
Carrier Aggregation Solutions Market is evolving rapidly due to increased network densification, the rollout of 5G infrastructure, and heightened user expectations for seamless streaming, gaming, and real-time communications. Vendors are investing in R&D to deliver scalable, software-defined solutions that improve bandwidth usage and optimize user experience in urban, suburban, and rural environments.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6671
Market Keyplayers:
Anritsu (MD8430A Signaling Tester, MT8821C Radio Communication Analyzer)
Artiza Networks, Inc. (DuoSIM-5G, 5G Load Tester)
Cisco Systems Inc. (Cisco Ultra Packet Core, Cisco 5G Cloud Core)
Huawei Technologies (SingleRAN LTE, SingleRAN@Broad)
Nokia Corporation (AirScale Baseband, AirScale Radio Access)
Qualcomm Technologies, Inc. (Snapdragon X75 Modem-RF System, Snapdragon X65 Modem-RF System)
Rohde and Schwarz GmbH and Co. KG (CMW500 Tester, SMW200A Vector Signal Generator)
Sprint.com (Sprint Spark, Sprint LTE Advanced Pro)
Telefonaktiebolaget LM Ericsson (Ericsson Radio System, Ericsson Cloud RAN)
ZTE Corporation (Uni-RAN, 5G NR Base Station)
Broadcom Inc. (5G RF Front-End Modules, 5G Modem SoCs)
Verizon Communications Inc. (5G Ultra Wideband, LTE Advanced)
Qorvo Inc. (RF Front-End Modules, High Band PADs)
Alcatel Lucent S.A. (9926 eNodeB, 9768 Metro Cell Outdoor)
AT&T Inc. (AT&T 5G+, LTE Advanced Network)
Capestone BV (5G Outdoor Routers, Industrial IoT Gateways)
Ciena Corporation (6500 Packet-Optical Platform, Adaptive IP)
CommScope, Inc. (ERA DAS, Small Cell Antennas)
Fujitsu Limited (5G NR Base Station, Carrier Aggregation Solution)
Hewlett Packard Enterprise L.P. (HPE 5G Core Stack, Open RAN Solution)
Intel Corporation (vRAN Accelerator ACC100, FlexRAN Platform)
Juniper Networks (Contrail Networking, Cloud-Native Router)
Keysight Technologies (CMW500 LTE Test Solution, Signal Studio Software)
LG Electronics (V60 ThinQ 5G, Velvet 5G)
NEC Corporation (5G Radio Units, Open RAN Solution)
Market Analysis
The Carrier Aggregation Solutions Market is being driven by the growing consumption of mobile data, the proliferation of smart devices, and telecom operators’ push for better network utilization. By merging non-contiguous frequency bands, operators can provide faster, more stable connections without acquiring additional spectrum. In the USA, aggressive 5G rollouts and demand for high-speed enterprise applications are fueling adoption, while in Europe, regulatory support and spectrum auctions are accelerating the integration of carrier aggregation technologies.
Market Trends
Rapid adoption of 5G NR (New Radio) technologies with multi-band support
Integration of AI and automation for dynamic spectrum management
Growing investments in small cell deployment for urban coverage
Network slicing enabled by advanced aggregation techniques
Expansion of software-based solutions for easier network upgrades
OEM partnerships to ensure hardware-software compatibility
Demand for real-time, ultra-low latency applications driving performance upgrades
Market Scope
Carrier aggregation is becoming a cornerstone of telecom strategy worldwide, unlocking greater efficiency and superior customer experiences. The market scope is expanding across industries—from telecom and enterprise networks to IoT connectivity and smart city infrastructures.
Enhanced mobile broadband and video streaming performance
Critical support for autonomous systems and low-latency apps
Seamless integration with existing LTE and 5G infrastructure
Improved quality of service (QoS) in high-density areas
Key enabler for industrial automation and private networks
Flexible deployment models through cloud-native solutions
Forecast Outlook
The future of the Carrier Aggregation Solutions Market is marked by technological advancement and strategic telecom transformations. As operators intensify 5G coverage and prepare for 6G experimentation, carrier aggregation will remain a core solution to meet evolving connectivity demands. Ongoing innovation in spectrum utilization and software-defined networking will shape the next wave of growth. Both the USA and Europe will be central to this trajectory, driven by innovation leadership, robust demand, and regulatory alignment.
Access Complete Report: https://www.snsinsider.com/reports/carrier-aggregation-solutions-market-6671
Conclusion
The momentum behind the Carrier Aggregation Solutions Market is redefining what’s possible in mobile and wireless communication. With demand for speed, consistency, and intelligent networks reaching new heights, carrier aggregation is emerging as a game-changer for operators, enterprises, and consumers alike.
Related Reports:
U.S.A Media Asset Management Market empowers broadcasters with seamless media organization tools
U.S.A. sees booming growth in Conversational Systems as businesses go digital
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
Why Radios Still Matter for Certain Businesses

In an age where smartphones dominate personal and professional communication, many commercial organizations still rely on radio systems to support their daily operations. While it might seem outdated, the reality is quite the opposite—today’s radio systems are more advanced than ever, powered by digital transformation and enhanced by IP (Internet Protocol) connectivity. This evolution has made radios an indispensable part of modern secure communication systems, especially in industries that require instant, reliable, and resilient communication.
Why Radios Over Cell Phones?
Cellular networks are great for consumer use, but they fall short in mission-critical situations. Five types of organizations that greatly benefit from using radios over cellular connections include:
Public Safety and Emergency Services – Fire departments, police forces, and EMS teams depend on instant communication that works in tunnels, during disasters, or in remote areas where cell coverage is unreliable.
Construction and Infrastructure – Job sites often have patchy cell reception and require rugged, push-to-talk systems that work in noisy environments.
Transportation and Logistics – Fleet managers, dispatchers, and drivers rely on continuous updates and coordination across wide geographical areas.
Hospitality and Events – Coordinating large teams in real-time across venues, from hotels to concerts, requires communication that’s fast, clear, and uninterrupted.
Utilities and Energy Companies – These sectors need to maintain service uptime and safety, especially in remote substations or offshore facilities where conventional networks don’t reach.
For these industries, two-way radios are often the lifeline of operations. But these aren’t the same static analog radios of decades past.
The Rise of IP Radio Systems
Modern radio solutions have evolved to leverage the power of IP networks, allowing voice and data to travel over existing LANs, WANs, and even the internet. An IP radio system transmits audio and control signals digitally, which improves range, clarity, and reliability. With IP integration, these systems also support remote management, seamless scalability, and better interoperability between devices and locations.
A good example is when a utility company integrates their dispatch system with IP radios connected across substations. Even if the facilities are hundreds of miles apart, they can communicate in real time over the same network, with lower latency and higher clarity than traditional analog or UHF-based systems.
Understanding RoIP Systems
RoIP systems (Radio over Internet Protocol) are an extension of the VoIP (Voice over IP) concept. These systems allow radios to communicate over IP networks by converting audio into data packets. This opens the door to linking multiple sites, enabling nationwide radio coverage without the need for expensive repeater infrastructure or leased lines.
Think of RoIP as an audio bridge between traditional radio devices and the internet. A construction company can, for example, connect different job sites across the state by using RoIP gateways, allowing supervisors and operators to coordinate without relying on cellular networks, which may falter in rural or crowded environments.
Transitioning from Analog to Digital Radio
Many companies hesitate to upgrade from legacy analog systems, fearing cost or complexity. However, transitioning to digital radio communications is easier than most expect. Modern communication systems companies in the USA offer hybrid devices and infrastructures that support both analog and digital modes. This allows organizations to phase in digital capabilities over time without disrupting operations.
By switching to digital, businesses gain access to features like enhanced audio quality, text messaging, GPS tracking, and programmable emergency alerts. These capabilities improve both safety and efficiency across departments.
Ensuring Security Through Encryption
Security is a top concern for any business, especially those managing critical infrastructure or sensitive information. Digital radio systems provide built-in encryption options that protect communications from interception.
There are several encryption standards available:
Basic digital encryption – Suitable for everyday use to prevent casual eavesdropping.
AES (Advanced Encryption Standard) – A robust encryption method used by military and government agencies.
End-to-end encryption – Ensures that only authorized users can listen in, as even the network cannot decrypt the communication.
By choosing secure communication systems with strong encryption features, businesses can ensure compliance with industry regulations and maintain operational integrity.
Why Work with a Communication Systems Provider?
Choosing the right partner can make all the difference in implementing a radio solution that fits your organization’s needs. A qualified communication systems company in the USA will help assess your operational requirements, design a tailored solution, and handle both the hardware installation and software configuration. This includes programming radio units, setting up IP and RoIP systems, and training your team for optimal use. In addition, working with professionals ensures ongoing technical support, firmware updates, and compliance with FCC regulations—saving time, reducing risk, and improving system uptime.
Despite the ubiquity of smartphones, radios remain a powerful tool for business communication—especially when they’re backed by IP and RoIP technology. By adopting a modern IP radio system, businesses gain access to scalable, secure, and efficient communication networks that are purpose-built for demanding environments.
From construction zones to emergency command centers, today’s secure communication systems are faster, smarter, and more connected than ever. With expert support from a reliable communication systems provider, your business can future-proof its communications with a solution that’s ready for anything.
0 notes
Text
Telecommunication Protocols Overview: VoIP
Revolutionary Transition from TDM to IP Networks Voice over IP (VoIP) technology VoIP and Triple Play: Key Protocols for Multimedia Transmission in IP Networks
Voice-over-IP (VoIP), also known as IP telephony, connects TDM networks with channel switching to IP networks with packet switching. It also facilitates the gradual transition from TDM to IP networks. Introduced in the late **1990s**, VoIP is one of the earliest telecommunication technologies to enable the use of IP phones, IP PBXs, and similar equipment; the suite of VoIP protocols is **crucial** among other telecom protocols.
According to the common definition, IP telephony is real-time voice signal transmission over a packet-switched network. It converts a phone number into an IP address and the analog voice signal into a digital one.
The birth year of Internet telephony is considered to be 1995, when Vocaltec released the Internet Phone software for telephone transmission using the IP protocol. **Until** the mid-1990s, Internet phone network implementation was possible only via telephone modems, resulting in significantly lower voice quality compared to traditional phones. Nevertheless, this laid the foundation for VoIP.
Since then, the development has been so rapid that VoIP's capabilities now far exceed its formal name. Essentially, this technology allows for the transmission of not only voice but any type of information using the IP protocol, so the term shifted to a broader one, "multimedia." Corresponding data structures can include voice, images, and data in any combination, commonly referred to as Triple Play.
The VoIP network structure can be viewed as two planes. The lower one represents the transport mechanism for non-guaranteed delivery of multimedia traffic as a protocol hierarchy (RTP, UDP/IP), and the upper one is the call service management mechanism. The key protocols here are H.323 ITU-T, SIP, MGCP, and MEGACO, each offering different implementations for call **services** in IP telephony networks.
Real-time Transport Protocol (RTP) provides transport services to multimedia applications, but it doesn't guarantee delivery or packet order. RTP helps **apps** detect packet loss or order issues by assigning a number to each packet. RTP works in point-to-point or point-to-multipoint modes with no regard to the transport mechanism, but usually it is UDP.
RTP works with the Real-Time Control Protocol (RTCP), which manages data flow and checks for channel overload. RTP session participants periodically exchange RTCP packets with statistical data (number of packets sent, lost, etc.), which senders can use to adjust transmission speed and load type dynamically.
Recommendation H.323
The recommendation H.323, historically the first method for making calls in an IP network, involves the following types of data exchange: - Digital audio - Digital video - Data (file/image sharing) - Connection management (communicating function support, logical channel management) - Session and connection establishment and termination
Key H.323 network elements include terminals, gateways, gatekeepers, and Multipoint Control Units (MCU).
A terminal provides real-time communication with another H.323 terminal, gateway, or MCU.
Gateways connect H.323 terminals with different network protocol terminals by converting the information back and forth between networks.
Gatekeepers participate in managing connections by converting phone numbers to IP addresses and **vice versa**.
Another element of the H.323 network, the proxy server, operates at the application level to identify application types and establish necessary connections.
The H.323 call service plane includes three main protocols (see picture): RAS (Registration Admission and Status) for terminal registration and resource access control, H.225 for connection management, and H.245 for logical channel management. RAS uses UDP, while H.225 and H.245 use TCP for guaranteed information delivery. UDP's delivery is not guaranteed, so if confirmation isn't received in time, UDP retransmits the message.

Pic. 1. Overview of H.323
The process of establishing a connection involves three stages. The first one is to detect the gatekeeper, register terminals with the gatekeeper, and control **terminals'** access to network resources using the RAS protocol. The next two stages involve H.225 signaling and H.245 control message exchanges.
Recommendation H.225 outlines the procedures for connection management in H.323 networks using a set of signal messages from the ITU-T's Q.931 recommendation.
Recommendation H.245 describes the procedures for managing information channels: determining the master and slave devices, communicating terminal capabilities, and opening and closing unidirectional and bidirectional channels. It also covers delays, information processing modes, and the state of information channels by organizing loops.
The exchange of signaling messages between interacting H.323 network devices happens over H.245 logical channels. The zero logical channel, which carries control messages, must remain open for the entire duration of the connection.
SIP (Session Initiation Protocol)
The second method for handling calls in VoIP networks involves using the Session Initiation Protocol (SIP), specified in RFC 2543 by the IETF. As an application-level protocol, it is designed for organizing multimedia conferences, distributing multimedia information, and setting up phone connections. SIP is less suited for interaction with PSTN but is easier to implement. It's more suitable for ISPs offering IP telephony services as part of their package.
Key features of SIP include user mobility support, network scalability, the ability to add new functions, integration with the existing Internet protocol stack, interaction with other signaling protocols (e.g., H.323), enabling VoIP users to access intelligent network services, and independence from transport technologies.
It's worth noting that user mobility support is no longer exclusively a SIP feature. H.323 now also supports it (see ITU-T H.510, "Mobility for H.323 Multimedia Systems and Services").
A SIP network contains user agents, or SIP clients, proxy servers, and redirect servers.
User agents are terminal equipment applications that include a client (User Agent Client, UAC) and a server (User Agent Server, UAS). The UAC initiates the service request, while the UAS acts as the calling party.
The proxy server combines UAC and UAS functions. It interprets and, if necessary, rewrites request headers before sending them to other servers.
The redirect server determines the location of the called subscriber and informs the calling user.
MGCP (Media Gateway Control Protocol)
The third method for building an IP telephony network relies on the Media Gateway Control Protocol (MGCP), proposed by the IETF's MEGACO workgroup. The architecture of this protocol is probably the simplest of all three in terms of functionality. An MGCP network contains a media gateway (MG) for converting voice data between PSTN and IP telephony networks, a signaling gateway (SG) for processing signaling information, and a call agent (similar to an H.323 gatekeeper) for managing gateways.
Like H.323, MGCP is convenient for organizing PSTN-compatible IP telephony networks. However, in terms of functionality, MGCP surpasses H.323. For example, an MGCP call agent supports SS7 signaling and transparent transmission of signaling information over the IP telephony network. In contrast, H.323 networks require any signaling information to be converted by a gateway into H.225 (Q.931) messages. MGCP messages are transmitted in plain text format.
The fourth method for building an IP network, an improvement over MGCP, was developed by the IETF's MEGACO group together with ITU-T's SG 16, hence the name MEGACO/H.248. It mainly differs from its older sibling in connection organization. Thanks to this, the MEGACO/H.248 controller can change the port connection topology, allowing for flexible conference management. The MEGACO protocol supports two methods of binary encoding.
MGCP has also evolved in the field of the Internet of Things (IoT), where it is used to manage media gateways and transmit voice information in various scenarios, such as smart homes or intelligent buildings.
0 notes
Text
#Virtualized Evolved Packet Core Market#VEPC Market#Mobility Management Entity#Home Subscriber Server#Packet Data Network Gateway#Policy and Charging Rules Function#Mobile Private Network & Mobile Virtual Network Operator (MPN & MVNO)#Long-term Evolution & Voice over Long-term Evolution (LTE & VoLTE)#Telecom Operators#Internet of Things & Machine to Machine
0 notes
Text
How Firewall Solutions Save Your Business from Expensive Breaches

In today’s digital-first world, cyber threats are not just an IT issue—they're a major business risk. Data breaches cost companies millions of dollars annually, not to mention the long-term damage to reputation, trust, and operations. One of the most effective ways to protect your organization from these costly intrusions is by investing in robust firewall solutions.
Firewalls have evolved far beyond the simple packet filters of the past. Modern firewall solutions provide advanced threat detection, policy enforcement, and real-time monitoring that can block malicious activity before it causes harm. In this article, we’ll explore how firewalls work, why they're critical to your cybersecurity strategy, and how they ultimately save your business from expensive breaches.
1. Understanding the Modern Firewall
A firewall is a network security system—hardware, software, or both—that monitors and controls incoming and outgoing network traffic. It is a barrier between trusted internal networks and untrusted external sources like the internet.
Modern firewall solutions, often called Next-Generation Firewalls (NGFWs), go beyond traditional port and protocol filtering. They include features such as:
Deep packet inspection
Application awareness and control
Intrusion prevention systems (IPS)
Malware and ransomware detection
Threat intelligence integration
By inspecting data at multiple layers, firewalls can identify threats that evade basic security systems.
2. The Real Cost of a Data Breach
Before diving into how firewalls can help, let’s understand what a breach costs a business.
According to IBM’s 2024 Cost of a Data Breach Report:
The average cost of a data breach globally is $4.45 million
Breaches in the U.S. are even higher, averaging over $9 million
It takes an average of 277 days to identify and contain a breach
These costs include more than just immediate remediation:
Legal fees and regulatory fines
Loss of customer trust and loyalty
Downtime and loss of productivity
Damaged brand reputation
Potential lawsuits or compliance violations
Firewalls are one of the few proactive tools businesses can deploy to significantly reduce the chances of these high-impact events.
3. Firewall Solutions Prevent Unauthorized Access
Most breaches start with unauthorized access. Whether it’s a brute-force attack or a phishing link that gives hackers credentials, once inside your network, cybercriminals can quietly exfiltrate data or install ransomware.
A firewall acts as a gatekeeper, only allowing legitimate traffic to access your internal systems. With features like:
Geo-blocking (blocking traffic from certain countries)
IP whitelisting/blacklisting
User authentication
Access control policies
You can prevent external attackers—and even internal bad actors—from reaching sensitive data.
4. Stops Malware and Ransomware at the Perimeter
One of the most financially devastating attacks a business can face is ransomware. In this scenario, hackers encrypt your data and demand a ransom for its release. Even if you pay, there’s no guarantee you’ll get your data back.
Next-gen firewalls come equipped with:
Signature-based malware detection
Sandboxing to analyze unknown files
Heuristic scanning to spot suspicious behavior
Integration with global threat databases
These tools stop malware at the gateway before it reaches endpoints, drastically reducing the chance of an infection that could cripple your business.
5. Protects Against Insider Threats
Not all threats come from the outside. Disgruntled employees or careless staff can accidentally (or intentionally) expose your systems to risk.
Modern firewall solutions offer internal segmentation, creating micro-perimeters within your network. This means:
A compromised machine can’t access the entire network
You can set different policies for departments (e.g., finance vs. marketing)
Sensitive data stays isolated from unnecessary access
This containment minimizes the impact of a breach and prevents it from spreading laterally within your environment.
6. Ensures Compliance with Industry Regulations
Whether you're in healthcare, finance, or e-commerce, regulatory compliance is non-negotiable. Standards like HIPAA, PCI DSS, and GDPR require strong data protection practices, including network security.
Firewall solutions help maintain compliance by:
Controlling access to regulated data
Providing logs and audit trails for forensic analysis
Preventing unauthorized data transfers
Supporting network segmentation to isolate sensitive systems
Failing to comply with regulations can result in steep fines, legal action, and loss of certification—costs that far outweigh the investment in a quality firewall.
7. Reduces Downtime and Business Disruption
One overlooked consequence of a breach is downtime. If your systems are taken offline, every minute equals lost revenue and productivity.
A firewall helps avoid this by:
Blocking malicious traffic before it hits internal systems
Alerting you to unusual behavior before a full-blown attack
Isolating infected systems to maintain business continuity
Downtime isn’t just a technical issue—it affects customer satisfaction, employee performance, and your bottom line.
8. Enables Secure Remote Work and Cloud Access
As hybrid work becomes the norm, businesses must secure remote access to internal resources. Firewalls support:
Secure VPN connections
SSL inspection
Cloud-native firewall capabilities
This allows employees to work from anywhere without exposing their systems to unnecessary risks. Plus, firewalls can monitor and manage access to cloud applications like AWS, Azure, or Microsoft 365, ensuring consistent security across all platforms.
9. Real-Time Threat Monitoring and Analytics
Firewalls today are more than passive filters—they’re active security hubs.
Advanced solutions provide:
Real-time alerts
Traffic visualization dashboards
Behavior analytics
With AI-driven insights, IT teams can detect anomalies and respond to threats quickly. Faster detection means faster response, and that can be the difference between stopping an attack early or dealing with a full-scale breach.
10. Firewall as a Service (FWaaS): Enterprise-Level Security for SMBs
You don’t need to be a Fortune 500 company to afford enterprise-grade security. Many vendors now offer Firewall as a Service, a cloud-based model that:
Reduces the cost of hardware and maintenance
Scales with your business
Provides automatic updates and global threat intelligence
This makes robust firewall protection accessible to small and medium businesses, who are often prime targets for attackers due to weaker defenses.
Conclusion: A Smart Investment That Pays Off
In the world of cybersecurity, prevention is far more cost-effective than cure. Firewall solutions not only protect your business from the financial fallout of a breach, but they also empower you to maintain operations, meet compliance requirements, and build customer trust.
Think of a firewall not as an expense, but as an insurance policy, a productivity booster, and a brand protector all in one. In an era where cyber threats are growing in frequency and sophistication, having a strong firewall solution isn’t just smart. It’s essential.
#firewall solutions#next generation firewall#firewall security solution#cloud based firewall#Check Point firewall#palo alto firewall#fortinet firewalls#network security
0 notes
Text
Transforming Vendor Relationships: Data-Driven Strategies for Telecom Cost Control

In today's fast-moving business environment, telecommunications expenses represent both a significant cost center and a strategic opportunity. As organizations embrace digital transformation, their reliance on telecom services—from MPLS circuits and Internet access to mobile plans and cloud connectivity—continues to grow. But without clear visibility into usage patterns and vendor performance, companies risk overspending, service disruptions, and missed opportunities for optimization.
This blog post explores how CIOs and IT leaders can strengthen vendor relationships by implementing data-driven strategies, leveraging real-time analytics to enforce service level agreements (SLAs), proactively managing contracts, and maintaining continuous cost control without compromising performance.
The Shifting Role of Vendor Management in Telecom
Historically, vendor management in the telecom industry has focused on negotiating rates and resolving outages. Today, it must evolve into a continuous, analytics-powered discipline. Modern TEM (Telecom Expense Management) platforms aggregate billing, contract, and performance data into unified dashboards. This centralized view equips IT and procurement teams with insights into which vendors deliver reliable service, which circuits underperform, and where hidden fees erode margins. By partnering with vendors as strategic allies—rather than transactional suppliers—organizations can co-innovate solutions, lock in more favorable terms, and hold providers accountable for agreed-upon standards.
Leveraging Real-Time Analytics to Monitor Vendor Performance
Consolidate Data from Multiple Sources
Begin by integrating invoices, network performance logs, and SLA reports into a single data warehouse. Whether from legacy PBX trunks, SD-WAN overlays, or mobile carriers, every data point matters. A comprehensive data lake reveals trends, such as recurring outages on specific circuits or unexplained cost spikes in data usage.
Establish Key Performance Indicators (KPIs)
Define clear metrics, such as uptime percentage, mean time to repair (MTTR), latency thresholds, and packet-loss rates, that align with business priorities. For example, an e-commerce firm might prioritize sub-50 ms latency for payment gateways, while a remote-first organization could emphasize uptime for unified communications.
Deploy Dashboards and Alerts
Use real-time visualization tools to track KPI performance against contractual SLAs. Automated alerts notify stakeholders when a vendor's service level dips below the agreed-upon levels, triggering an immediate investigation and remediation. This proactive monitoring prevents small degradations from ballooning into major outages that impact revenue and customer satisfaction.
Enforcing SLAs to Drive Accountability
Negotiate Measurable SLAs
When drafting or renewing contracts, include precise, quantifiable service level metrics. Ambiguous terms like "industry-standard uptime" leave room for interpretation. Instead, specify "99.95% uptime measured monthly" or "MTTR of under 4 hours for critical circuits."
Tie Penalties and Credits to Performance
Incorporate financial penalties or service credits for missed SLAs. This alignment incentivizes vendors to prioritize your account and invest in reliability. Over time, diligent enforcement of these clauses can yield cost offsets of 5–10% through credit recovery alone.
Conduct Quarterly Business Reviews (QBRs)
Regularly sit down with key vendors to review performance data. Present your analytics dashboard, highlight areas for improvement, and agree on corrective action plans. These collaborative QBRs foster a partnership mentality, signaling that your organization will not tolerate subpar service.
Proactive Contract Lifecycle Management
Automate Contract Milestones
Use TEM software to track contract start and end dates, renewal windows, and rate re-opportunities. Automated reminders ensure you never miss a renegotiation window, avoiding auto-renewals that lock you into outdated pricing.
Benchmark Against Market Rates
Leverage industry benchmarking data to assess whether your vendors remain competitive. Suppose your fiber circuits cost 20% more than the market average; present that data during renegotiations. Solid benchmarks empower you to secure better rates or explore alternative suppliers.
Conduct Regular Contract Audits
Every six to twelve months, reconcile contract terms against invoices and usage data. Identify instances where vendors have applied out-of-contract rates or tacked on unauthorized fees. A disciplined audit cycle can uncover incremental savings of 3–7% annually.
Using Data to Optimize Vendor Mix
Segment Services by Performance and Cost
Classify your telecom services into high-cost/high-performance (e.g., private circuits), mid-tier services (e.g., managed broadband), and low-cost ancillary offerings (e.g., SIP trunks). This segmentation enables you to match service levels to business criticality, ensuring that mission-critical workloads receive premium connectivity, while less sensitive traffic utilizes cost-effective links.
Embrace Multi-Vendor Strategies
Avoid single-vendor lock-in by maintaining at least two providers for critical services. Use your data to route traffic dynamically—perhaps sending bulk backups over broadband while reserving MPLS for real-time applications. This approach reduces risk and gives you negotiating leverage across multiple contracts.
Consolidate When It Makes Sense
Conversely, bundling services under one vendor can yield volume discounts and reduce administrative burden. Utilize cost-benefit analysis, informed by your analytics platform, to identify services that are ripe for consolidation without compromising redundancy or performance.
Cultivating a Data-Driven Vendor Culture
Share Insights Across Teams
Democratize telecom data by granting access to stakeholders in finance, operations, and customer support. When departments see the impact of telecom performance on their key metrics—whether it's MTTR for field service or latency for customer portals—they become active participants in vendor discussions.
Reward High-Performing Vendors
Set up scorecards and recognize vendors that consistently meet or exceed Service Level Agreements (SLAs). Publicly acknowledging their performance in QBRs strengthens relationships and encourages continuous improvement.
Drive Joint Innovation
Invite vendors to co-develop initiatives, such as SD-WAN proofs of concept or 5G pilot programs, that address evolving business needs. Data-backed use cases demonstrate ROI and fast-track deployment of new technologies.
The Role of Expert Guidance
While in-house teams can leverage TEM platforms to great effect, specialized partners like zLinq bring deep domain expertise and an outsider's perspective. zLinq's comprehensive services include:
Network Assessments & Invoice Audits: They identify hidden fees and performance gaps across POTS, VoIP, and cloud systems.
Vendor Management & Negotiations: Armed with robust analytics, zLinq secures more favorable rates and enforces SLAs effectively.
Seamless Integration: They help blend legacy systems with modern telecom platforms, ensuring reliable and scalable communication.
By augmenting your internal capabilities with zLinq's hands-on support, you accelerate savings initiatives, strengthen vendor accountability, and future-proof your telecom environment.
Turning Data into Competitive Advantage
Transforming vendor relationships through data-driven strategies elevates telecom management from back-office cost control to a strategic growth enabler. By consolidating performance and billing data, enforcing precise service-level agreements (SLAs), and proactively managing contracts, CIOs can reduce expenses, enhance service quality, and foster collaborative vendor partnerships. With the expertise and advanced TEM solutions that zLinq provides, mid-market enterprises gain the visibility, agility, and negotiating power needed to optimize telecom spend and support long-term innovation. As telecom costs stabilize and service reliability improves, organizations unlock resources for strategic investments, cementing telecom management as a true competitive advantage in today's digital economy.
0 notes
Text

OPC UA Field eXchange (UAFX) is a new generation of field layer communication standard launched by the OPC Foundation, which aims to solve the core pain points of the long-standing coexistence of multiple protocols and poor device interoperability in the field of industrial automation. As an extension of the OPC UA standard, UAFX realizes end-to-end standardized data interaction from the control layer to field devices through a unified information model and communication framework, providing key infrastructure for Industry 4.0 and smart manufacturing. Its core value lies in breaking the technical barriers of traditional fieldbuses, enabling devices from different manufacturers to achieve plug-and-play interconnection without relying on dedicated gateways, while meeting the stringent requirements of modern industry for real-time, security and flexibility.
Core Functions and Applications of OPC UAFX
I. Key Features
1. Cross-vendor Interoperability
Enables seamless communication between controllers/devices from different brands through standardized OPC UA information models
Supports three-tier communication architectures: Controller-to-Controller (C2C), Controller-to-Device (C2D), and Device-to-Device (D2D)
2. Real-time Data Exchange
Delivers deterministic communication via Ethernet TSN and 5G networks
Achieves microsecond-level synchronization using UDP/IP (IEEE 802.1AS)
3. Unified Engineering Configuration
Built-in Connection Manager for automatic secure link establishment
Supports integration with standard engineering tools (e.g., FDT/DTM, AML)
4. Advanced Diagnostics
Real-time monitoring of device health (network latency, packet loss, etc.)
Asset Information Model (AIM) for full lifecycle data tracking
5. Secure Communication
Inherits OPC UA's native X.509 certificate authentication and AES-256 encryption
Complies with both functional safety (IEC 61508) and cybersecurity (IEC 62443) standards
II. Industrial Applications
1. Smart Factories
Plug-and-play configuration for PLCs, robots, AGVs, etc.
Use case: Multi-brand robot collaboration in automotive welding lines
2. Process Automation
Eliminates protocol conversion between DCS and field instruments (flow meters/temperature transmitters)
Application: Direct data transmission from smart instruments to MES in petrochemical plants
3. Motion Control
Enables precision synchronization (<1μs jitter) for servo drives and CNC equipment
Typical scenario: Multi-axis synchronization in packaging machinery
4. Energy Management
Standardized monitoring for PV inverters, energy storage PCS, etc.
Implementation: Gateway-free data acquisition for wind farm SCADA systems
III. Technical Advantages

IV. Implementation Benefits
Lower TCO: 30+% reduction in protocol conversion hardware costs
Faster Deployment: 50% shorter engineering configuration time
Higher OEE: Predictive maintenance reduces unplanned downtime
Currently supported by leading automation vendors like ABB and Siemens, UAFX is expected to achieve widespread adoption in discrete manufacturing by 2025. This standard is particularly suited for Industry 4.0 scenarios demanding high real-time performance and multi-vendor device integration.
0 notes
Text
Bluetooth Low Energy (BLE) to GSM Gateway?

How Does It Work?
Local Data Collection (BLE): BLE devices, like temperature sensors or asset trackers, send small packets of data (low-energy, short-range).
Gateway Reception: The gateway picks up these signals within a range of ~10–50 meters.
Cellular Transmission (GSM): The gateway converts the BLE data and sends it via cellular networks (LTE Cat M1 for efficiency, NB-IoT for low power, or 2G for areas with older networks).
In short, the gateway acts as a bridge, extending the BLE device’s reach to anywhere there’s cellular coverage.
0 notes
Text
Connecting the World with Radio Over IP (RoIP)

In today’s hyper-connected world, communication networks are more advanced and widespread than ever before. The presence of robust IP networks, including fiber-optic networks, wide-area networks (WANs) and local-area networks (LANs), has transformed the way we connect. Long-distance communication by radios, once constrained by geography, is now seamless, thanks to modern technologies like Radio over IP (RoIP).
A key factor driving this evolution is the sheer number of communication satellites orbiting the Earth. As of 2024, there are approximately 7,550 active satellites in orbit, ensuring global coverage and uninterrupted data transmission. With these advancements, the traditional constraints of radio communications are no longer a barrier to connectivity.
The Evolution of Long-Distance Radio Communications
Decades ago, long-distance radio communications relied on networks of radio towers and repeaters to extend coverage. While effective at the time, these infrastructure-heavy solutions required constant maintenance and significant financial investment. As technology progressed, maintaining a vast network of towers became unsustainable, prompting the need for more scalable and cost-effective solutions.
RoIP has emerged as the solution to this challenge. By leveraging existing IP networks, RoIP enables users to connect digital radios using IP networks, eliminating distance limitations and enhancing communication reliability. Unlike traditional systems that required line-of-sight radio connections, RoIP utilizes the internet, fiber-optic networks, and even satellite links to provide uninterrupted connectivity over vast distances.
How Radio Over IP Works
Radio over IP works by transmitting radio signals over an IP-based network. A small RoIP gateway device acts as the bridge between conventional radios and the internet. These gateways digitize the analog or digital radio signal, converting it into packets that can be sent over any IP-based network, including:
Private and public WANs
LAN infrastructures
Satellite internet connections
Cloud-based communication platforms
This adaptability means that radio users can be located anywhere in the world and still remain connected without relying on expensive radio tower networks. A communication systems company in the USA specializing in RoIP solutions can design and deploy these networks to meet the specific needs of businesses, public safety agencies, and industries requiring mission-critical communications.
The Advantages of Radio Over IP
Unlimited Range: Since RoIP utilizes IP networks, users can communicate across the globe without the need for direct radio-to-radio line-of-sight connections.
Cost Savings: Eliminating the need for extensive radio tower infrastructure significantly reduces capital investment and maintenance costs.
Scalability: Organizations can scale their communication networks quickly by adding more RoIP gateways, ensuring coverage expansion without costly infrastructure upgrades.
Interoperability: RoIP enables different radio models and frequencies to communicate seamlessly, making it ideal for organizations that use a mix of analog and digital radio systems.
Reliability: IP-based networks provide redundant paths for data transmission, ensuring continuous connectivity even in emergencies.
Why Distance Is No Longer a Barrier
Traditional radio networks were inherently limited by the range of their transmission. Today, RoIP eliminates this limitation by using the global reach of the internet and satellite networks. Whether an organization needs to connect analog radios using IP networks across cities, states, or even continents, RoIP ensures reliable and instant communication.
For example, emergency response teams in different regions can now communicate seamlessly, regardless of distance. Transportation and logistics companies can maintain continuous communication between fleet operators without worrying about dead zones. Businesses with multiple locations can link their workforce through an efficient, always-on network.
Choosing the Right Communication Systems Provider
Deploying a reliable RoIP network requires expertise in both radio and IP-based communications. A communication systems company in the USA can help organizations select the right RoIP gateways, integrate them with existing radio systems, and configure the software to ensure optimal performance.
By working with experienced professionals, businesses can:
Ensure secure and encrypted communications.
Integrate RoIP with existing communication infrastructure.
Customize solutions based on specific operational needs.
Receive ongoing technical support and maintenance.
The advancement of IP networks and satellite technology has revolutionized long-distance radio communications. By leveraging Radio over IP for devices, organizations can overcome distance limitations, reduce infrastructure costs, and ensure uninterrupted communication. Whether for public safety, transportation, or industrial applications, RoIP provides a scalable and cost-effective solution to modern communication challenges.
Partnering with a trusted communication systems provider ensures a seamless transition to RoIP technology, helping businesses and agencies stay connected, regardless of location. As technology continues to evolve, the future of communication is undoubtedly digital, and RoIP is leading the way.
0 notes
Text
Enterprise Connectivity and Networking Market Demand, Growth Drivers, and Industry Scope 2032
The Enterprise Connectivity and Networking Market was valued at USD 57.10 billion in 2023 and is expected to reach USD 90.98 billion by 2032, growing at a CAGR of 5.33% over 2024-2032.
Enterprise Connectivity and Networking Market is witnessing unprecedented growth as businesses increasingly adopt digital transformation strategies. The demand for high-speed, secure, and scalable networking solutions is rising due to cloud computing, IoT, and remote work trends. Companies are investing heavily in advanced networking infrastructure to enhance productivity and operational efficiency.
Enterprise Connectivity and Networking Market continues to evolve with rapid technological advancements. The shift toward 5G, SD-WAN, and AI-driven network management is revolutionizing how organizations manage their IT infrastructure. Businesses across industries are prioritizing seamless connectivity to ensure real-time collaboration, data security, and efficient remote operations.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3797
Market Keyplayers:
Cisco Systems: Catalyst 9000 Series Switches
Hewlett Packard Enterprise (HPE): Aruba 500 Series Access Points
Juniper Networks: MX Series 5G Universal Routing Platforms
Arista Networks: 7280R Series Universal Leaf and Spine Switches
Huawei Technologies: CloudEngine 16800 Data Center Switch
Dell Technologies: PowerSwitch S5248F-ON
Extreme Networks: ExtremeWireless Wi-Fi 6 Access Points
Fortinet: FortiGate 6000F Series Next-Generation Firewalls
Palo Alto Networks: PA-3200 Series Next-Generation Firewalls
Check Point Software Technologies: Quantum Security Gateways
NETGEAR: Nighthawk Pro Gaming XR1000 WiFi 6 Router
Ubiquiti Networks: UniFi Dream Machine Pro
Ciena Corporation: 6500 Packet-Optical Platform
Riverbed Technology: SteelHead SD WAN Optimization
VMware: NSX-T Data Center
Zebra Technologies: FX9600 Fixed RFID Reader
CommScope: Ruckus R750 Wi-Fi 6 Access Point
ADTRAN: Total Access 5000 Series
TP-Link: Omada SDN Controller
Mellanox Technologies: Spectrum SN2100 Switch
Market Trends Driving Growth
1. Adoption of 5G and Edge Computing
Organizations are leveraging 5G technology for ultra-fast connectivity, low latency, and improved network reliability. Edge computing further enhances performance by processing data closer to the source.
2. Rise of AI-Driven Network Automation
Artificial Intelligence (AI) is optimizing network management, improving security, and automating troubleshooting, reducing downtime and operational costs.
3. Growth of SD-WAN Solutions
Software-Defined Wide Area Networks (SD-WAN) are transforming enterprise connectivity by providing cost-effective, flexible, and secure network solutions, especially for multi-branch businesses.
4. Increasing Focus on Cybersecurity
With growing cyber threats, enterprises are prioritizing secure networking solutions, integrating AI-based threat detection and Zero Trust security models.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3797
Market Segmentation:
By Component
Hardware
Software
Services
By Enterprise Type
SMEs
Large Enterprises
By Industry Vertical
BFSI
Manufacturing
IT & Telecom
Retail & Ecommerce
Healthcare
Market Analysis and Current Landscape
Cloud and Hybrid Networking Adoption: Enterprises are integrating cloud-based solutions with traditional infrastructure to ensure seamless data access and scalability.
Remote Work Acceleration: The demand for secure and stable connectivity solutions has surged as hybrid and remote work models become permanent.
Digital Transformation Initiatives: Companies across industries are investing in next-gen networking solutions to enhance agility and efficiency.
Rising Demand for High-Speed Connectivity: Industries like healthcare, finance, and manufacturing require high-speed, low-latency networks for real-time operations.
Future Prospects: What Lies Ahead?
1. Expansion of AI and Machine Learning in Networking
AI-powered predictive analytics and network automation will drive operational efficiency, minimize disruptions, and enhance security measures.
2. Evolution of 6G and Next-Gen Connectivity
As 5G adoption grows, research into 6G networks is accelerating, promising even faster speeds and improved data processing capabilities.
3. Increased Investments in Secure Cloud Networking
With businesses migrating to hybrid cloud environments, the focus on secure cloud networking solutions will continue to rise.
4. Smart Cities and IoT Integration
The increasing adoption of IoT devices and smart city initiatives will demand more sophisticated networking infrastructures for seamless data exchange.
Access Complete Report: https://www.snsinsider.com/reports/enterprise-connectivity-and-networking-market-3797
Conclusion
The Enterprise Connectivity and Networking Market is undergoing a significant transformation, driven by technological advancements, digital transformation, and the increasing need for secure, high-speed connectivity. Businesses that embrace AI-driven automation, SD-WAN, and next-gen networking solutions will gain a competitive edge. As enterprises continue to prioritize seamless and secure connectivity, the industry is poised for sustained innovation and long-term growth.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Enterprise Connectivity and Networking Market#Enterprise Connectivity and Networking Market Scope#Enterprise Connectivity and Networking Market Share#Enterprise Connectivity and Networking Market Growth#Enterprise Connectivity and Networking Market Trends
0 notes