#Password Cracking Software
Explore tagged Tumblr posts
Text
THINGS TO SCRIPT. BELONGINGS & MISC.





(in first person for easier scripting :3 copy and pasted from my script tbh)
- my posts never flop.
- my home always smells good.
- none of my equipment falters.
- my editing software never fails.
- my live streams are always fun.
- my ID photos are always pretty.
- my belongings never get stolen.
- tvs and devices never have a glare.
- food doesn’t stick to pots and pans.
- none of my belongings ever hurt me.
- my home is the perfect temperature.
- there are never any crumbs in my bed.
- my pillow is always cold on both sides.
- people always find me effortlessly funny.
- i always have phone signal & wifi connection.
- utensils don’t scrape against teeth or dishes.
- i’m not addicted to my phone or social media.
- as a model i get paid in both clothes and money.
- my air conditioning and heating system never fails.
- no one is able to hear audio through my headphones.
- whenever i order anything online it arrives the next day.
- none of my favorited posts on social media get deleted.
- when using a camera, it always has the lighting i want it to.
- things such as bugs, rodents, mold, or mildew never get into people’s living spaces.
- none of my social medias take away certain features or ban me and any username that i ever want is always available.
- my belongings never get damaged, they’re indestructible, waterproof, and always work as they should. i never lose any of my belongings or forget any of my important information such as passwords, phone numbers, passports, or other important documents or information.
- my car is immune from getting scratched, cracked windows, flat or popped tires and rust. the battery never dies and my cameras and lights are always clean. my bass is amazing and is always clear. i never lock my keys in my car and my car always smells amazing like me. i never have crumbs in my car because i never drop anything in my car.

#⋆ ౨ৎ ˚ ˖ dessarchive#dessa ★ scripts#reality shifting#shifting#shifting antis dni#shifting consciousness#shifting diary#shifting motivation#shiftingrealities#shifting script#shifting blog#kpop shifter#kpop dr#kpop shifting#shift blog#shifting realities#shifting reality#reality shift#scripting#shifters#shifting community#shifting to hogwarts#fame desired reality#fame dr#desired reality#law of assumption#law of manifestation#fame shifting#reality shifter#shiftblr
2K notes
·
View notes
Note
Kunsel says:
We should maybe have a stricter definition of what counts as "hacking", okay?
It was a slow day at work, and he decided to guess people's email passwords in 10 attempts.
How does it go?
YESSSSSSSSS
Pro tips: make your password long, that is the most important factor. Use a password manager, most of them have a free option. Adding complexity does help, but focus on length first. Size does matter here. Multi-factor authentication (MFA) also helps a lot.
---------
Kunsel: Zack, gimme your password!
Zack: ...
Kunsel: Come on man, I need it for something!
Zack: 😭😭😭 buddy I would, but I forgot it again 😭😭😭😭😭😭
Kunsel: Ok man, it's ok, let's look around your desk...here, under this pile of chip bags, I think i saw...yeah, here's the penguin toy...and yep, Password Penguin has "Zack'ss00p3rp4ssw0rd!" written on the bottom. Let's try it!
(it works)
Zack: THANK YOU KUNSEL I THOUGHT I'D LOST HIM AND I COULDN'T REMEMBER AND-
Kunsel: *wheeze* Zack let go, I need to breathe *wheeze*

-----------
Kunsel tries to guess Roche's by typing it in.
M0t0rcycle!
ShinyDancer
Sh1n33D4nc3r!
He's in.

------------
Kunsel tries to guess Sephiroth's. On the 9th try, he gets it: Seph+Jenova4ever
Horrible things are uncovered along the way and now he needs to send Sephiroth some information very discreetly.
------------
Lazard. Kunsel knows better. He gives a few guesses, but decides to actually hack this.
He sets up a hash capturing tool over the internal network and waits for Lazard to log on. He does. Kunsel captures the hash and starts cracking it.
Three days later, the hash cracker has not worked and he has to give up on that.
Kunsel: Sir, I need to get into your email, will you please send me your password?
Lazard: Of course not, that is unsafe and against company policy. However, you're welcome to come to my office to perform any actions we both deem necessary.
Kunsel goes over and Lazard is using multifactor authentication, so just having the hash cracked wouldn't have worked anyway. He sets up a keylogger surreptitiously on Lazard's workstation while "performing updates" and showing Lazard new features in his email.
The things he captures with that keylogger:
* Numerous emails covering for boneheaded shit the SOLDIERs did.
* The letter "A" typed about a thousand times into a text file labeled "definitely not screams.txt".
* Moogle searches for "how to convince your employees to get therapy", "pasta recipes", "therapists near me", "child psychology for adults", "play therapy for adults", "cat psychology", and "shrimp pasta recipes".
* The password: &oh'ihiy_-8_gi"it"gi_ipkb0(-ur#3-@--LXS4ever--9(9;0(!08(098+pihjboigig(@ukopih

Then it is a simple matter of finding a zero-day race condition hack in the MFA software, timing things just right, and entering the password and hacked MFA key at the perfect moment.
Kunsel of course has pity on the man after seeing even more emails such as...
* Explaining to Roche that doing squats over his motorcycle makes it look like he's humping it, and it is making people uncomfortable.
* Asking Genesis to please not actually firaga the recruits this week, they don't need a lawsuit. No, it's not character building. No, even though it was part of his home training and Shinra sanctioned training a few years ago.
* Inviting Sephiroth over for shrimp pasta to discuss strategy.
* Asking Angeal to seek therapy so the others will follow his lead.
* Telling Zack that he could not have a therapy flamingo in the office. Even if it was a lawn ornament.
* Warning Hojo not to take Sephiroth this week.
* Warning Hollander not to take Genesis and Angeal this week.
* Reaming Heidegger out very politely for all his BS.
Kunsel logs out without doing anything. Lazard needs a break.

--------
Kunsel calls Angeal pretending to be the help desk. Angeal, a bit embarrassed over his upbringing and unsure because he feels unused to technology, eventually gives Kunsel the password: BanoraBoys123!

----------
Genesis' is guessed on the 7th try because Kunsel didn't want to bother typing in an entire stanza of Loveless with numbers instead of vowels.
1nf1n1t3_1n_myst3ry_1s_th3_g1ft_0f_th3_g0dd3ss__w3_s33k_1t_th7s_4nd_t4k3_t0_th3_sky_r1ppl3s...
He sends an email from Genesis inviting everyone to a Loveless recital on Tuesday. It backfires because several people, including Genesis, show up and have a great time.

-----------
Kunsel tries Zack's little trooper friend next. He's a tough nut to crack. He won't pick up his PHS to get vished, won't click on Kunsel's phishing emails, and won't tell Zack or Kunsel his password.
Kunsel captures his hash and cracks it. It takes a full 24 hours, but he gets it in the end:
!1986fuck_this_shit

#ff7#sephiroth#zack fair#cloud strife#genesis rhapsodos#angeal hewley#lazard deusericus#die hojo die#kunsel#hackerman kunsel
37 notes
·
View notes
Text
Two years ago when “Michael,” an owner of cryptocurrency, contacted Joe Grand to help recover access to about $2 million worth of bitcoin he stored in encrypted format on his computer, Grand turned him down.
Michael, who is based in Europe and asked to remain anonymous, stored the cryptocurrency in a password-protected digital wallet. He generated a password using the RoboForm password manager and stored that password in a file encrypted with a tool called TrueCrypt. At some point, that file got corrupted and Michael lost access to the 20-character password he had generated to secure his 43.6 BTC (worth a total of about €4,000, or $5,300, in 2013). Michael used the RoboForm password manager to generate the password but did not store it in his manager. He worried that someone would hack his computer and obtain the password.
“At [that] time, I was really paranoid with my security,” he laughs.
Grand is a famed hardware hacker who in 2022 helped another crypto wallet owner recover access to $2 million in cryptocurrency he thought he’d lost forever after forgetting the PIN to his Trezor wallet. Since then, dozens of people have contacted Grand to help them recover their treasure. But Grand, known by the hacker handle “Kingpin,” turns down most of them, for various reasons.
Grand is an electrical engineer who began hacking computing hardware at age 10 and in 2008 cohosted the Discovery Channel’s Prototype This show. He now consults with companies that build complex digital systems to help them understand how hardware hackers like him might subvert their systems. He cracked the Trezor wallet in 2022 using complex hardware techniques that forced the USB-style wallet to reveal its password.
But Michael stored his cryptocurrency in a software-based wallet, which meant none of Grand’s hardware skills were relevant this time. He considered brute-forcing Michael’s password—writing a script to automatically guess millions of possible passwords to find the correct one—but determined this wasn’t feasible. He briefly considered that the RoboForm password manager Michael used to generate his password might have a flaw in the way it generated passwords, which would allow him to guess the password more easily. Grand, however, doubted such a flaw existed.
Michael contacted multiple people who specialize in cracking cryptography; they all told him “there’s no chance” of retrieving his money. But last June he approached Grand again, hoping to convince him to help, and this time Grand agreed to give it a try, working with a friend named Bruno in Germany who also hacks digital wallets.
Grand and Bruno spent months reverse engineering the version of the RoboForm program that they thought Michael had used in 2013 and found that the pseudo-random number generator used to generate passwords in that version—and subsequent versions until 2015—did indeed have a significant flaw that made the random number generator not so random. The RoboForm program unwisely tied the random passwords it generated to the date and time on the user’s computer—it determined the computer’s date and time, and then generated passwords that were predictable. If you knew the date and time and other parameters, you could compute any password that would have been generated on a certain date and time in the past.
If Michael knew the day or general time frame in 2013 when he generated it, as well as the parameters he used to generate the password (for example, the number of characters in the password, including lower- and upper-case letters, figures, and special characters), this would narrow the possible password guesses to a manageable number. Then they could hijack the RoboForm function responsible for checking the date and time on a computer and get it to travel back in time, believing the current date was a day in the 2013 time frame when Michael generated his password. RoboForm would then spit out the same passwords it generated on the days in 2013.
There was one problem: Michael couldn’t remember when he created the password.
According to the log on his software wallet, Michael moved bitcoin into his wallet for the first time on April 14, 2013. But he couldn’t remember if he generated the password the same day or some time before or after this. So, looking at the parameters of other passwords he generated using RoboForm, Grand and Bruno configured RoboForm to generate 20-character passwords with upper- and lower-case letters, numbers, and eight special characters from March 1 to April 20, 2013.
It failed to generate the right password. So Grand and Bruno lengthened the time frame from April 20 to June 1, 2013, using the same parameters. Still no luck.
Michael says they kept coming back to him, asking if he was sure about the parameters he’d used. He stuck to his first answer.
“They really annoyed me, because who knows what I did 10 years ago,” he recalls. He found other passwords he generated with RoboForm in 2013, and two of them did not use special characters, so Grand and Bruno adjusted. Last November, they reached out to Michael to set up a meeting in person. “I thought, ‘Oh my God, they will ask me again for the settings.”
Instead, they revealed that they had finally found the correct password—no special characters. It was generated on May 15, 2013, at 4:10:40 pm GMT.
“We ultimately got lucky that our parameters and time range was right. If either of those were wrong, we would have … continued to take guesses/shots in the dark,” Grand says in an email to WIRED. “It would have taken significantly longer to precompute all the possible passwords.”
Grand and Bruno created a video to explain the technical details more thoroughly.
RoboForm, made by US-based Siber Systems, was one of the first password managers on the market, and currently has more than 6 million users worldwide, according to a company report. In 2015, Siber seemed to fix the RoboForm password manager. In a cursory glance, Grand and Bruno couldn’t find any sign that the pseudo-random number generator in the 2015 version used the computer’s time, which makes them think they removed it to fix the flaw, though Grand says they would need to examine it more thoroughly to be certain.
Siber Systems confirmed to WIRED that it did fix the issue with version 7.9.14 of RoboForm, released June 10, 2015, but a spokesperson wouldn’t answer questions about how it did so. In a changelog on the company’s website, it mentions only that Siber programmers made changes to “increase randomness of generated passwords,” but it doesn’t say how they did this. Siber spokesman Simon Davis says that “RoboForm 7 was discontinued in 2017.”
Grand says that, without knowing how Siber fixed the issue, attackers may still be able to regenerate passwords generated by versions of RoboForm released before the fix in 2015. He’s also not sure if current versions contain the problem.
“I'm still not sure I would trust it without knowing how they actually improved the password generation in more recent versions,” he says. “I'm not sure if RoboForm knew how bad this particular weakness was.”
Customers may also still be using passwords that were generated with the early versions of the program before the fix. It doesn’t appear that Siber ever notified customers when it released the fixed version 7.9.14 in 2015 that they should generate new passwords for critical accounts or data. The company didn’t respond to a question about this.
If Siber didn’t inform customers, this would mean that anyone like Michael who used RoboForm to generate passwords prior to 2015—and are still using those passwords—may have vulnerable passwords that hackers can regenerate.
“We know that most people don't change passwords unless they're prompted to do so,” Grand says. “Out of 935 passwords in my password manager (not RoboForm), 220 of them are from 2015 and earlier, and most of them are [for] sites I still use.”
Depending on what the company did to fix the issue in 2015, newer passwords may also be vulnerable.
Last November, Grand and Bruno deducted a percentage of bitcoins from Michael’s account for the work they did, then gave him the password to access the rest. The bitcoin was worth $38,000 per coin at the time. Michael waited until it rose to $62,000 per coin and sold some of it. He now has 30 BTC, now worth $3 million, and is waiting for the value to rise to $100,000 per coin.
Michael says he was lucky that he lost the password years ago because, otherwise, he would have sold off the bitcoin when it was worth $40,000 a coin and missed out on a greater fortune.
“That I lost the password was financially a good thing.”
23 notes
·
View notes
Text
Hey Neighbor PT 10
WC:1.3k~
Previous
AO3 page
Toji
“So what exactly are you wanting me to do, sir?” the lanky male asks Toji. The computer opened and reflected in his oversized glasses.
“I am curious myself,” Shiu sits with his ankle over his knee, staring at Toji from across the kitchen table. “Your text from last night was quite unexpected”
Toji is seated with his forearms braced on the table, a slight frown on his face and a tiredness in his eyes. Which was to be expected since he hadn’t slept a wink the previous night. His mind spun from thoughts of you and this mysterious guy that had interrupted his owning up everything to you. He battled back and forth with his mind–should he really try to find out who this was or should he allow you to live your life and make your own choices? As the sun peaked over the horizon, he came to the middle ground, sorta. He’d find out who this guy was, but that was it! No background checks, no sending out people to his house, and definitely not wiping him off the planet and out of your life. Just a normal hacking of a phone.
“I need to see messages on y/n phone.” Toji answers.
Shiu’s eyes widen, taken back for a moment. Then, his face turns to one of joy. “Ah, already? The agreement must’ve been–”
“This isn’t about the agreement,” Toji interrupts, brusquely. He turns towards the hacker. “Just tell me you can do it.”
The hacker wrings his hands over his keyboard, clearly nervous in the presence of the infamous Toji Fushiguro. “Uhm, I can put spyware on it? Do you have the phone?”
“No, do it remotely. She uses an Apple phone and computer. I’m sure she has messages coming through her computer on the messaging app.” He demands.
“If we are in the range of her wifi, I can crack through her password, and then the software can gather all her credentials–logins and passwords. Then, we just enter those into the messaging app.” The hacker spoke quickly, clearly excited to show off his abilities.
“Do it,” he orders.
~
A day off work was never really a day off. Being so busy with work and honestly being lazy, the house chores had fallen behind. Though you have been living here for a few months now, the house still screams “Grandmother’s house.” You just hadn’t had the heart or the mental strength to get rid of things. Grief made you hang on to it as much as possible Until the smell of her house was replaced with your soft vanilla and lavender smell. You started in the bedroom, packing away old clothes to take to donation centers and replacing the bed sheets with ones that were more you—A soft purple comforter and an overabundance of pillows.
After folding the new bath towels and placing them in the upstairs hallway closet, you look up at the ceiling and the hatch to the attic ladder. You had been dreading going up there for a few reasons. Spiders, dust, dirt, mold, and the wild idea that someone might be up there living for all you knew. Another reason was what you DID know was up there. Pictures, memories of people you would never see again, and memories of moments you’ll never experience. But, today was the day. It had to be done.
Straightening your shoulder, you pull the string and allow the ladder to unfold to the floor. Surprisingly, no dead bodies tumbled down and no clouds of dust poured. You climbed the stairs, holding your phone as a flashlight. Once at the top, you notice it’s not the crypt you expected. It could be a spare room, the floors barely showed signs of neglect, neat stacks of books in the corner, and enough room to stand. Another string hung from the rafters to a light that still worked.
Getting to work, you pull dusty boxes from the corners, carry them to the floor below, gather the books to sort through and sweep the floor. Once satisfied with your cleaning, you gather your supplies and turn off the light. You switch all the supplies to one hand as you shuffle to the ladder.
The canister of furniture polish slips from your arm and rolls to the side of the attic. You chase after it, using your phone light again in the dark. The light bounced off the can and another glint of metal on the wall you hadn’t noticed.
Upon further inspection, you see a small gap in the wall, metal peaking out behind it. Using your phone light, a two-foot by two-foot section of the wall seems to be cut into the wall. YOu dig your finger into the exposed groove and gift it a sideways push. After getting stuck a few times, the panel recedes into the wall at the right, and the content behind it is revealed.
A silver safe about the size of a mini fridge sits behind the wall, a thin layer of dust coating it. A keypad blinks in the upper corner. You take a chance and attempt to pull the handle, hoping it would open—another part of you hoped it wouldn’t. Scared to see what was in it.
After 3 more tugs of the handle, you give up. It clearly needs a passcode. You try a few—1234, 11111, 2222 —-- before again giving up in case it had a system that locked it completely for an undetermined amount of time.
Finally, you climb back down the ladder, Confused, which seems to be your everyday emotion these days. You might as well have a giant question mark above your head
What the fuck is going on?
Toji
“I was able to hack into her cloud and find her contacts. I reverse-searched the number of the last message she received. It comes back to a Connor J. Falco but it appears he’s gone by a multitude of aliases. Here are some of the text messages I was able to—”
“I’m not going to read her messages, just give me what info you have on the guy,” Toji interrupts, slightly closing the laptop that the hacker had rotated around for him to see.
“Isn’t your concern that she is…involved with this man? Romantically?” Shiu chimes in from the living room where he is sitting on the floor with Megumi, playing with action figures. “ I believe I’d want to know what they were discussing, hmmm?”
“That’s—her business,” Toji replies, knowing how ridiculous it sounds.
“Doesn’t hacking into her phone inadvertently—”
“Just give me info on the guy,” Toji says to the hacker. He knows it doesn’t make sense. He tries to ease the guilt of spying by telling himself it’s only half spying. And it’s not spying on you, you were just the obstacle to get to the real prey. He wouldn’t read any of your messages or look through your photos and social media. That’s where he drew the line—the very thin one.
“Connor J Falco is an independent contractor, though I can’t find anything about what exactly he is contracted to do. Small online presence, just moved to town from overseas. No criminal records, no past traffic infractions.”
“See? An upstanding citizen.” Shiu laughs. “Completely harmless.”
“However,” the hacker clears his throat. “That’s just for Connor.”
“What do you mean?” Shiu stands behind the laptop.
“His other alias,” Toji answers. He knew this was what would happen. Whatever persona this guy was showing y/n was no doubt clean. It was his other personas that worried him.
“Correct. And Dmitri Sokolov?” The hacker nods and turns the laptop around for Toji to see. “He has quite a disturbing criminal history.”
Toji slides the laptop closer, clicking through the pages of court records and mugshots both international and domestic. From white-collar to violent crimes. His heart hammers in his chest. These weren’t petty crimes, this guy has experience.
“Shit.”
#Hey neighbor#toji fushiguro#Toji fushiguro reader#jjk#jujutsu kaisen#jjk x reader#jjk x you#jjk reader#jujutsu kaisen x reader#jujutsu kaisen x you#jujutsu kaisen smut#jujutsu kaisen angst#Toji fushiguro jjk#Toji fushiguro x reader#Toji fushiguro x you#Toji fushiguro headcanon#Toji fushiguro smut#Toji fushiguro fluff#dilf toji#dad toji#protective toji#Toji fushiguro you#Toji fushiguro angst#Toji fushiguro fic#megumi fushiguro#jjk toji smut#jjk toji fushiguro#toji zenin#toji zenin reader
33 notes
·
View notes
Text
I don't know why people spend billions of dollars and hours trying to develop better password cracking software
All you need is to put the phone/device in a slightly damp pocket- not only will it simply unlock, it will open thirty websites, make four calls, and send seven text messages
10 notes
·
View notes
Text
I Hate Authentication
I wake up one morning, and my kids want to watch something on a streaming service. I go to that service on my television, and find the service has logged me out. Groggy, grumpy, and unsure of the password since it uses my partner's account and email, I think "I hate authentication".
I start my day of work, noticing there's a meeting that's been added right at the beginning of the day. It seems urgent; my boss organized it. I try to open up the meeting the video conference app, and it requires Google Authentication, which in turn requires my Google password, which I keep in a password manager, which also requires a password. As I fumble around multiple apps and in turn end up late to this meeting, I think "I hate authentication".
As part of my work as a software developer, I research how to use a service's public API. I find exactly the endpoint I need, and even find some documented examples that line up with my use case. I am elated, until I notice that the API requires some kind of token in order to access it. As I enter my second hour of research to find what and where these tokens are, I think "I hate authentication".
Late in the work day, I want to login to a tool I use at work, when it prompts me. "Password expired. Please update your old password with a new one". No other information is provided. As I notice I might be late for my train, I think "I hate authentication".
At the end of a long day, I want to sit and enjoy a movie I've been looking forward to. I remember I still can't login to that streaming service from earlier, and my partner is out for the evening. As I crack open my beer, with a mixture of sadness and anger, I think "I hate authentication".
3 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Note
4735 About the people saying "having bots follow you can get you hacked", not going to lie I laughed out loud a bit, because in my head I just can't see how that would work. How would they actually get your password merely using tumblr's follow infrastructure? Last I checked, scripts aren't allowed on blog popups, just their desktop themes, and most bots don't exactly have a desktop theme. So if you click a url of a bot, it'll just open up a blank blog with no script to be used on you (in other words, stuff like cookie grabbers are definitely out). And if you start to receive sketchy shortened links via IM, like I've gotten a few times, just delete them? The mere act of someone sending an IM message isn't going to "get your account hacked". Clicking fishy links, yeah, they could lead to sites with all kinds of shit on them, but otherwise no. Accounts get "hacked" when your password is somehow released and cracked using software. That's not what's happening if a bot simply follows you.
Posting since this is a response to a previous problem.
9 notes
·
View notes
Text
Good to see the Germany military is using unsecured consumer-grade video conferencing software to discuss high-level operations.
Plus I have to assume that Cisco's Webex is probably innately capable of better security than it looks like was being used here, considering it is enterprise video conferencing sofware. Did anyone call and ask them? Probably should have done that.
"NO THE RUSSIANS JUST HACKED IT!"
Yes. And "hacking" means you get into systems where you're not wanted. And you routinely do that by waiting for some moron to use "1234" as a password, or stick a USB they found at a cafe, that you loaded with key-loggers, into their military work laptop.
Real life hacking is like 80% waiting for people to do something stupid that you can take advantage of. Moscow has a whole military unit of hackers, and most of what they do all day is sending foreign government officials spam emails with links they mindlessly click. They aren't cracking Engima machines most of the time.
7 notes
·
View notes
Text
Cybersecurity Lab Game
Hey everyone! Welcome back to the blog. Today, I had the opportunity to dive into the Nova Cybersecurity Lab Game, which was an eye-opening experience. This interactive game puts you in the shoes of a cybersecurity expert tasked with protecting a company from cyber threats. It focuses on aspects like identifying phishing attempts, managing software updates, and securing sensitive information.

Here's a picture of the challenges that had to be done to gain more coins for the defence against cyber-attacks. There were 3 levels, and with each, they became more complex with additional coding puzzles, diverse threat scenarios, and advanced encryption techniques, demanding more sophisticated strategies and problem-solving skills.
One key takeaway was the importance of vigilance and proactive measures in cybersecurity. The game shows how cyber threats exploit human errors, like falling for phishing scams or neglecting updates. It highlights the need for ongoing education and awareness to recognize and counter these threats effectively.

Above is another image that demonstrates a successful cyber defense against an attack which resulted in no loss of users.
Challenges
The password challenge was particularly interesting. It gave me a deeper understanding of the tricks hackers use to crack passwords, such as brute force attacks. This challenge highlighted the necessity of creating strong, unique passwords and using multi-factor authentication to prevent unauthorized access.
Additionally, the coding challenge was enlightening. They demonstrated how codes and virtual mazes can be designed to keep hackers from accessing vital information, allowing only authorized personnel to navigate these defenses. This reinforced the importance of robust security protocols in protecting sensitive data.

The image above showcases a Level 2 coding challenge, illustrating the complexity of the code involved.
Overall, I found the Nova Cybersecurity Lab Game to be a great way to learn about cybersecurity. It gives practical tips on protecting digital assets, which is very helpful in today’s ever-changing digital world. Hope you enjoyed today's post and see you next week!
3 notes
·
View notes
Text
Boosting WordPress security is crucial for protecting your website from potential threats. Start by regularly updating your WordPress core, themes, and plugins to ensure you’re using the latest security patches. Outdated software is a common target for hackers, making updates a vital first step in safeguarding your site.
Another essential step is to implement strong passwords and two-factor authentication (2FA) for all user accounts. Weak passwords are easy to crack, while 2FA adds an extra layer of security by requiring a second form of verification. These measures can significantly reduce the risk of unauthorized access to your WordPress site.
#wordpress#web development#wordpress crowdfunding#wordpress development company#best web development company in usa
3 notes
·
View notes
Text
I'm perfectly aware that the place to put this post is linkedin and not Tumblr.com (although i might make a more professional-looking version).
Anyway, I'm horrified by the amount of cyber attacks that are happening in the last few days. Especially because a couple of these are really big companies, and one would think they have an IT department that knows how to do their job. Even better, they should have at least one person that deals with cybersecurity.
I know that security operations centers (where we use very expensive systems to monitor the networks and the assets of the companies, plus we often investigate previous security incidents and produce intelligence reports) are expensive. I work in one and it's not the solution that works for everyone. A small company with few employees definitely cannot afford a SOC, but a big corporation? That would be nice (again, it's not the only solution and every client is different, you need to tailor the cybersecurity solution to the client).
But a videogame studio? I would expect them to take security seriously. And not only because of the data involved, but industrial espionage is a thing (although it's difficult to prove and it happens rarely that it's taken to a court, however it does happen), but it's a risk. A worldwide clothing company? A fucking bank? Sure.
The problem with certain things it's that "it won't happen to me". Until it does. And you end up paying 300x than you would be paying at least a cybersecurity consultant to prevent the attack.
Even better, a lot of the simplest measures are free to implement. No USB from home policy. Disabling local administrator accounts. Implement a strong password policy. Implement a blacklist for suspicious websites (and also, maybe stop downloading cracked software if you don't know where to find reputable sources? I see you trying to download that CoD aimbot, how embarrassing)
Implement a strong antispam policy (which is fundamental, as this is very very often the access point - you send a targeted spam email to a company with 3k employees and I can guarantee you that at least one will download the malicious file or insert the credential on the fake office 365 website, it's just what it is.)
But most people won't, because "it's annoying" and users don't want to put the effort to like, keep their fucking job and remember a 12 character password(yes, a company can suffer so much damage from a cyber attacks that it might even close the business, and yes, I had to fight with clients that refuse to change their AD admin accounts set in 2015 even when I told them about a potential leak) Not to mention that the data stolen often is the employees data. And you don't want your identity stolen by a criminal, do you?
And the danger when these attacks are carried against hospitals. People can die if the whole network shuts down because no one cared to implement basic cybersecurity.
And it's not true that organisations don't have the budget. We both know you are lying lol.
Don't get me wrong, there is nothing foolproof, there will always be a certain amount of risk.
I just expect people to use some good sense and I'm often disappointed lol.
4 notes
·
View notes
Text
If you had battery-related performance issues on an older iPhone—and you got in on a class-action lawsuit against Apple six years ago—you could soon receive some payback for your trouble.
According to a statement released by the law office involved in the suit against Apple, the tech giant will soon have to pay out up to $500 million to customers affected by its throttling of iPhones that had older batteries. The so-called Batterygate scandal affected people using iPhones in the 6, 6S, and 7 families, as well as the original SE model, and stems from complaints from users that Apple purposely slowed down the devices after they installed software updates. Apple hasn’t admitted any wrongdoing, instead positing that its practice of deliberately slowing down its phones wasn’t a technique to get people to buy a newer device but rather a safety measure to keep the phones from shutting down when the battery got too low.
The checks will be doled out to the roughly 3 million people who filed claims for the lawsuit, which works out to somewhere between $65 and $90 per person. It’s too late to make a claim now—the deadline to join the suit passed in October 2020.
Here’s some more news about the stuff on your phone.
Premium Prime
Bad streaming music news for anyone who’s somehow not on Spotify or Apple Music: Amazon’s music streaming service is getting more expensive.
The price hike from $9 to $10 was revealed by a FAQ page on Amazon’s Music site, spotted by The Hollywood Reporter. The increase is relatively small and will apply to Amazon Prime members with Unlimited Music plans and family plans. But it’s part of a trend of streaming services putting the squeeze on their customers. The cost of a Spotify Premium subscription went up by a buck last month after 12 years without an increase. Hulu and Disney+ are getting more expensive later this year. Netflix has cracked down on password sharing and introduced a paid ad-supported tier. And don't forget that HBO Max removed gobs of content from its platform. Amazon Music doesn’t seem to be ditching any of its songs quite yet—or banning password sharing—but clearly the Amazonian overlords want to squeeze a little more out of the platform.
Muting TikTok
A recent Reuters poll shows that nearly half of Americans approve of the US banning the social media app TikTok. (Disclosure: Yes, WIRED is on TikTok.)
US lawmakers have been talking about tanking TikTok for years now, citing concerns that the app’s Chinese parent company ByteDance could share Americans’ user data with the Chinese government or that the app could serve as a software backdoor for Chinese spyware. Pundits and members of Congress have posited the TikTok ban as a push to protect privacy, even though the issue is more due to international tensions between the US and China. (Cue the I Think You Should Leave “you sure about that?” clip.)
The process of actually banning the app from US soil would be laborious and controversial. Montana is going to give it a shot in 2024, when its recently passed TikTok ban goes into effect. Enforcing a ban will be nigh impossible, since users could likely circumvent the rules by using a VPN to make it appear that they are in another location or by simply downloading the app while they are traveling to another state.
Stay Cool
It’s getting hotter here on planet Earth. Heat waves intensify, oceans warm, and wildfires worsen. And all the while, humans—and everything else living on the planet—pay the price. Human influence has undeniably altered the weather of the world, and as we hurtle along in a climate emergency, it’s only going to grow hotter and more unstable.
This week on the Gadget Lab podcast, WIRED’s resident doomsday reporter, Matt Simon, joins the show to talk about extreme heat, why it keeps getting warmer, and how we might be able to adapt.
7 notes
·
View notes
Text
How to install Adobe GenP 2023
Adobe CC 2019/2020/2021/2022/2023 GenP Universal Patch 3.0 Octomber 5, 2023 - Software Download password 333555
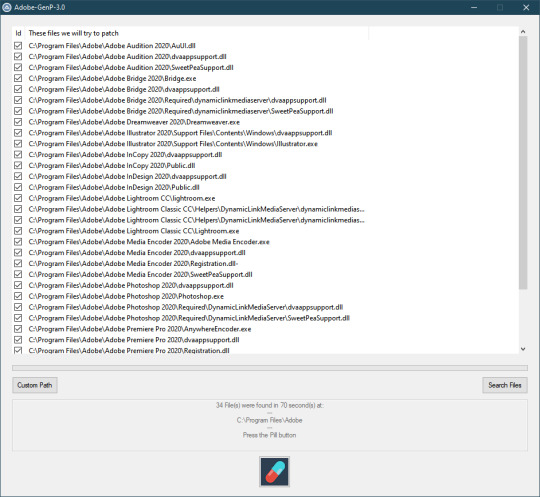
How to use GenP:
If you want to patch all Adobe apps in default location:
Press ‘Search Files’ – wait until GenP finds all files. Press ‘Pill Button’ – wait until GenP do it’s job. One Adobe app at a time: Press ‘Custom path’ – select folder that you want [depending upon the app you want to patch] Press ‘Search Files’ – wait until GenP finds all files. Press ‘Pill Button’ – wait until GenP do it’s job.
What’s New in GenP 3.0 Can patch apps from 2019 version to current and future releases. Automatic search in selected folder. New patching logic Support for all Substance products. Known Issues: InDesign and InCopy will have high CPU usage. Animate will have some problems with home screen if Signed Out. Lightroom Classic will partially work if Signed Out. Acrobat, Rush, Lightroom Online, Photoshop Express, Creative Cloud App won’t be patched or fully unlocked. Maybe in next release I’ll find solution for them. FIXES By Me:
made progressbar working
No checkbox at welcome text
nicer form size
Set dir deep level von search for files
Tags:
free adobe audition, adobe audition, adobe audition download, adobe audition cc 2022, download adobe audition, adobe audition crack free, adobe audition autotune, adobe audition crack 2022, dobe audition license 2022, adobe audition 2022 crack, download adobe audition 2022, adobe audition free, adobe audition free download, adobe audition 2022, adobe audition 2022 free, adobe audition tutorial, adobe audition crack, audition crack, adobe audition license pro
#adobe genP#adobe photoshop#adobe illustrator#adobe lightroom#adobe#adobe fresco#photoshop#graphic design#graphic art
5 notes
·
View notes
Photo
I mean... that's more scamming than hacking
There's password cracking software...
I get the feeling I should stop talking now

30K notes
·
View notes
Text
What Is the Best Way to Prepare My Device Before Taking It to a Repair Shop in Cooper City in 2025?
If your device is acting up and it's time to visit a repair shop in Cooper City, proper preparation can make all the difference. Preparing your device not only protects your data and privacy but also ensures a smoother, faster repair process. Whether you're dealing with a cracked screen, battery issues, or software glitches, understanding how to ready your device is crucial. This comprehensive guide will walk you through effective steps to back up your data, secure your personal information, and choose the right repair service in Cooper City. Read on to safeguard your device and enjoy peace of mind before handing it over for repairs.
Understanding the Importance of Preparing Your Device for Repair
Taking the time to prepare your device before sending it off to a repair technician goes far beyond convenience. It is essential to avoid data loss, protect your privacy, and streamline the diagnostic and repair process. When devices go in unprepared, you risk losing important files such as photos, contacts, or work documents. Moreover, repair technicians often need access to certain device functions to diagnose issues efficiently, but you want to control what personal information they can view.
Successful device preparation helps maintain your security by minimizing risks of unauthorized access to sensitive accounts including email, social media, and banking apps. Additionally, it can save you money and hassle—some repair shops may charge extra if complications arise from missing data or locked devices.
Understanding these benefits motivates users in Cooper City to take a proactive approach. Being prepared makes it easier to communicate device issues, safeguards your digital life, and ensures you get the best possible service.
Steps to Prepare Your Device Before Visiting a Repair Shop Backing Up Your Data
Backing up your data is one of the most important steps before any repair. By creating a backup, you safeguard your valuable information against accidental loss.
Cloud Services: For Android users, Google Drive offers seamless backup of contacts, photos, and app data. Apple users can leverage iCloud to securely store their information. External Storage: Using an external hard drive or USB flash drive to save photos, videos, and documents adds an extra layer of protection independent of internet connectivity. Backup Apps: There are numerous third-party apps designed for full-device backups, which you can use depending on your device model.
Comparing backup options, cloud storage offers ease of access and automatic syncing but depends on internet speed and subscription limits. External storage guarantees physical control but requires manual transfers. Ideally, combine both methods for maximum security.
Resetting Factory Settings
Resetting your device to factory settings removes personal data https://storage.googleapis.com/techy-cooper-city/phone-repairs.html and settings that might interfere with the repair process.
Security Benefits: Performing a factory reset wipes sensitive data like passwords, saved accounts, and downloaded apps. How to Reset: Navigate to your device’s settings menu and select “Factory Reset” or “Erase
0 notes