#Secure password examples and tips
Explore tagged Tumblr posts
Text
How to Choose Secure Passwords and Avoid Cyber Threats
Cyber threats are everywhere, and weak passwords are an open invitation for hackers. If you’re using “123456” or “password”—stop right now. A strong password is your first line of defense. Let’s dive into how to choose secure passwords and protect yourself from cybercriminals. Why Weak Passwords Are Dangerous Hackers don’t need to be geniuses to crack a weak password. They use brute force…
#Best password security practices for beginners#Cybersecurity best practices for everyday users#How to create a strong password in 2025#How to protect online accounts from hackers#Lmsint medai 2025#Secure password examples and tips
0 notes
Text
Some tips on how to survive a fascist state
From your auntie who has been around this block before.
This was made for people living in the US, but most of this is generally useful.
Assess your level of risk. For example, if you are not a citizen, going to a protest is much higher risk than it is for a citizen. But also recognize that the landscape of who is and is not being targeted is rapidly changing, so keep that in mind.
Get an updated passport. Make this a priority. If you live in a state where they have them, also get an Enhanced ID (not a Real ID, specifically an Enhanced ID) so you have a second way to cross land or sea borders into Canada and Mexico. That way, if authorities take your passport, you have another way out of the country.
Assume that the law is not there to protect you. Many parts of the law that are meant to protect you no longer apply. It's good to know your rights, but also know that the administration is not going to respect them. Just because you aren't doing anything illegal does not mean they won't come after you.
Move your communications, especially political communications, to encrypted messaging services. Use Signal for texts, ProtonMail for email, and Cryptpad as a word processor.
Get a private web browser. DuckDuckGo is a good option. I've also heard good things about Norton's private browser.
If you post political content on social media, you have two options. Make your account private and spend an evening going through your followers to weed out the ones you don't trust. Or, make it anonymous. But if you are picking the latter, know that it is hard to anonymize an account where you previously shared your identity. It's easier to go private if it's linked to your real life self, including through mutuals.
Turn off face ID on your devices. Police can force you to open them with your biometrics, even without a warrant. Additionally, make sure you have strong passwords (that are different for every account!) and keep track of them using a secure password manager.
If you go to protests or otherwise engage in subversive activity, DO NOT POST ABOUT IT ONLINE. Doing so endangers yourself and potentially others. Especially do not post pictures of protests, even if you've blurred the faces, even if you think you scrubbed the metadata. Even better, don't take photos at protests.
If you're exiting and re-entering the US, get a burner phone. I'm serious. Get an iPhone secondhand if you can afford it, but a flip phone will work if you need it to. Don't assume that just deleting anything sensitive off your device will be enough. You may not find it all, and depending on how thoroughly they search your phone, they may be able to see things that were deleted.
Mask up, especially when you're at a protest. In general, it's a good idea to mask since covid and many other viruses are going around. But masking has the added benefit of reducing the amount of biometric information you are making visible. Additionally, facial recognition software relies heavily on eyebrows, so cover them using a beanie or similar item.
Get involved or strengthen your ties with some kind of community. You are going to need others to lean on, whether that's emotionally or politically, in times like these.
22 notes
·
View notes
Note
hi, thanks for all the tech tips! I hope this isn’t a silly question, but how are password managers secure? Isn’t there a risk of a data breach there?
Each individual account managed through a password management company is (or should be in any respectable product) individually encrypted.
When we see big breaches like the 2013 tumblr leak or similar leaks over the years, typically what you're seeing is either
A) One large collection of information that was stored under the same encryption umbrella and someone was able to use illicit credentials or some other nefarious method to access that information (very bad) or
B) Information that was never encrypted in the first place and was stored in plaintext (much, much worse).
With a good password manager any data that the company has is encrypted and your individual vault is encrypted separately using a key that the company doesn't have access to.
So imagine that you walk into a room and the floor is covered in dominoes arranged in a pattern. With no encryption (scenario B), imagine that the door is unlocked and you can simply open the door and knock over all the dominoes.
With one big encrypted bucket (scenario A), what happens is if you are able to open the main door, you can knock over all the dominoes but it takes some effort to get the door open.
With individually encrypted vaults you need to open the main door, then you see thousands and thousands of tiny safes, each with a combination that you need to guess to access the dominoes inside to knock them over. Each safe has a code that will take somewhere between two years and ten thousand years to guess, depending on the computer doing the guessing, and you can customize your safe to make it harder to guess the combination.
Good encryption is extremely secure, and a lot of the breaches that we see aren't failures of encryption, they are failures of other parts of the system security. What you are typically seeing with big breaches is either someone didn't bother to encrypt anything, or someone fucked up in a big way and people who weren't supposed to gain access were able to gain access.
But what you almost never see is someone genuinely cracking encryption of a secure system.
Password managers generally speaking have a better eye toward security than a lot of other products, and open source password managers tend to be rigorously tested by some tremendously intelligent and tremendously paranoid people who are VERY invested in security.
If you have a Bitwarden account (just using it as the example because it's my favorite and it's what I recommend), Bitwarden actually *can't* access your account. If you forget your password, that's it. You're locked out (this is why it's important to make a good password hint and to make your password manager password both complex AND memorable). They can't recover it for you because they simply do not have access to that data; it is encrypted and they can't crack the encryption and they don't have your key (they have a hash of your key, which means they can recognize your key but they can't reverse engineer it - it's complicated, look up cryptographic hashing, I'm bad at explaining it). So if anyone breaches that system, they ALSO don't have access to your vault or to your key and in order to access your passwords would need to brute force your main password by guessing until they landed on the correct one. If you have a sufficiently long and complex password, that is going to be so extremely difficult that it might as well be impossible.
200 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
58 notes
·
View notes
Text
How to Watch IPTV on Phone?

How to Watch IPTV on Phone: Full Step-by-Step Guide
In today’s fast-paced world, the ability to stream your favorite live TV channels, sports, and movies directly from your smartphone is more convenient than ever. Thanks to IPTV (Internet Protocol Television), you can now watch high-quality content on the go, right from your Android or iOS phone.
This complete guide will show you how to watch IPTV on your phone, step-by-step, with real examples from IPTV providers like StreamView IPTV and Digitalizard. Whether you use Android or iPhone, this tutorial will help you get started easily.
What is IPTV?
IPTV (Internet Protocol Television) delivers live TV channels and on-demand video content through internet connections, rather than traditional cable or satellite. With IPTV, all you need is:
A reliable IPTV subscription (e.g., Streamview IPTV or Digitalizard),
An IPTV player app,
A good internet connection.
Requirements to Watch IPTV on Your Phone
To watch IPTV on your smartphone, you need:
📶 Stable internet connection (minimum 10 Mbps recommended)
📲 A compatible IPTV app for Android or iOS
🔐 Your IPTV credentials (M3U playlist link or Xtream Codes)
🔄 An updated Android or iOS device
How to Watch IPTV on Android Phone? Step-by-Step Guide
Step 1: Get Your IPTV Subscription
Sign up with a reliable IPTV provider like:
🔹 Streamview IPTV – Offers M3U and Xtream Code login, with 24/7 channels and VOD content.
🔹 Digitalizard – Known for HD quality and global channels, compatible with many IPTV players.
Once registered, they’ll email you:
M3U Playlist URL
Or Xtream Codes (Username, Password, and Server URL)
Step 2: Download a Reliable IPTV Player App
Some of the best IPTV apps for Android:
IPTV Smarters Pro
TiviMate IPTV Player
XCIPTV Player
GSE Smart IPTV
Go to Google Play Store, search for one of these apps, and install it.
Step 3: Load IPTV Playlist
Open the IPTV app (e.g., IPTV Smarters Pro).
Choose how you want to login:
Load Your Playlist or File URL (M3U)
Login with Xtream Codes API
Enter the details you received from Streamview IPTV or Digitalizard.
Tap Add User and wait for the channels to load.
Start streaming your favorite live TV channels, sports, or movies.
How to Watch IPTV on iPhone (iOS)? Step-by-Step Guide
Step 1: Subscribe to IPTV Service
Choose from verified providers like:
Streamview IPTV – Offers multi-device support including iOS.
Digitalizard – Offers fast delivery of login details and mobile-compatible links.
Step 2: Download an IPTV Player App for iOS
Top IPTV apps for iPhone:
IPTV Smarters – Player
GSE Smart IPTV
iPlayTV
Smarters Player Lite
Go to the App Store, search for one of these apps, and install it.
Step 3: Configure the App
Open the IPTV app on your iPhone.
Select either Xtream Codes Login or M3U Playlist option.
Enter:
Server URL
Username
Password (provided by Streamview IPTV or Digitalizard)
Tap Login and wait for the channel list to load.
Enjoy streaming HD content directly on your iPhone.
Key Features You’ll Enjoy
When using services like Streamview IPTV or Digitalizard, here’s what you typically get:
✅ 10,000+ Live TV Channels
✅ Video On Demand (Movies, TV Shows)
✅ 24/7 Sports & PPV Channels
✅ EPG (Electronic Program Guide)
✅ Catch-up & Recording Options (depends on player)
✅ Anti-freeze Technology
Use a VPN for Secure Streaming
To protect your privacy and avoid ISP throttling, it’s recommended to use a VPN while streaming IPTV on your phone. Apps like NordVPN, ExpressVPN, or Surfshark work great with mobile devices.
Troubleshooting Tips
Buffering? Switch to a lower-quality stream or use a VPN.
Can’t login? Double-check M3U/Xtream details or contact support.
App not loading? Clear cache or reinstall the IPTV player.
Final Thoughts
Watching IPTV on your phone is one of the easiest ways to enjoy live TV, sports, movies, and shows wherever you go. Whether you're using Android or iPhone, all you need is a trusted IPTV provider like Streamview IPTV or Digitalizard, and a reliable IPTV player app.
With a simple setup and internet access, you’ll have 24/7 entertainment right in your pocket.
FAQs
Can I watch IPTV on multiple devices?
Yes, both Streamview IPTV and Digitalizard support multi-device use. Check your plan for simultaneous connections.
Is it legal to use IPTV on my phone?
Using licensed IPTV services is legal. Avoid using pirated or unverified sources.
Do I need a VPN for mobile IPTV?
A VPN is not mandatory but is highly recommended for security and privacy.
Can I record IPTV on my phone?
Some apps like XCIPTV support recording on Android. iOS options may be limited.
#blog#blog intro#ask blog#blogging#shifting blog#tech#iptv subscription#best iptv#iptv#iptv service#iptv usa#abonnement iptv#iptv firestick
6 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
2 notes
·
View notes
Text
Social Media and Privacy Concerns!!! What You Need to Know???
In a world that is becoming more digital by the day, social media has also become part of our day-to-day lives. From the beginning of sharing personal updates to networking with professionals, social media sites like Facebook, Instagram, and Twitter have changed the way we communicate. However, concerns over privacy have also grown, where users are wondering what happens to their personal information. If you use social media often, it is important to be aware of these privacy risks. In this article, we will outline the main issues and the steps you need to take to protect your online data privacy. (Related: Top 10 Pros and Cons of Social media)

1. How Social Media Platforms Scrape Your Data The majority of social media platforms scrape plenty of user information, including your: ✅ Name, email address, and phone number ✅ Location and web browsing history ✅ Likes, comments, and search history-derived interests. Although this enhances the user experience as well as advertising, it has serious privacy issues. (Read more about social media pros and cons here) 2. Risks of Excessive Sharing Personal Information Many users unknowingly expose themselves to security risks through excessive sharing of personal information. Posting details of your daily routine, location, or personal life can lead to: ⚠️ Identity theft ⚠️Stalking and harassment ⚠️ Cyber fraud

This is why you need to alter your privacy settings and be careful about what you post on the internet. (Read this article to understand how social media affects users.) 3. The Role of Third-Party Apps in Data Breaches Did you register for a site with Google or Facebook? Handy, maybe, but in doing so, you're granting apps access to look at your data, normally more than is necessary. Some high profile privacy scandals, the Cambridge Analytica one being an example, have shown how social media information can be leveraged for in politics and advertising. To minimize danger: 👍Regularly check app permissions 👍Don't sign up multiple accounts where you don't need to 👍Strong passwords and two-factor authentication To get an in-depth overview of social media's impact on security, read this detailed guide. 4. How Social Media Algorithms Follow You You may not realize this, but social media algorithms are tracking you everywhere. From the likes you share to the amount of time you watch a video, sites monitor it all through AI-driven algorithms that learn from behavior and build personalized feeds. Though it can drive user engagement, it also: ⚠️ Forms filter bubbles that limit different perspectives ⚠️ Increases data exposure in case of hacks ⚠️ Increases ethical concerns around online surveillance Understanding the advantages and disadvantages of social media will help you make an informed decision. (Find out more about it here) 5. Maintaining Your Privacy: Real-Life Tips

To protect your personal data on social media: ✅ Update privacy settings to limit sharing of data ✅ Be cautious when accepting friend requests from unknown people ✅ Think before you post—consider anything shared online can be seen by others ✅ Use encrypted messaging apps for sensitive conversations These small habits can take you a long way in protecting your online existence. (For more detailed information, read this article) Final Thoughts Social media is a powerful tool that connects people, companies, and communities. There are privacy concerns, though, and you need to be clever about how your data is being utilized. Being careful about what you share, adjusting privacy settings, and using security best practices can enable you to enjoy the benefits of social media while being safe online. Interested in learning more about how social media influences us? Check out our detailed article on the advantages and disadvantages of social media and the measures to be taken to stay safe on social media.
#social media#online privacy#privacymatters#data privacy#digital privacy#hacking#identity theft#data breach#socialmediaprosandcons#social media safety#cyber security#social security
2 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
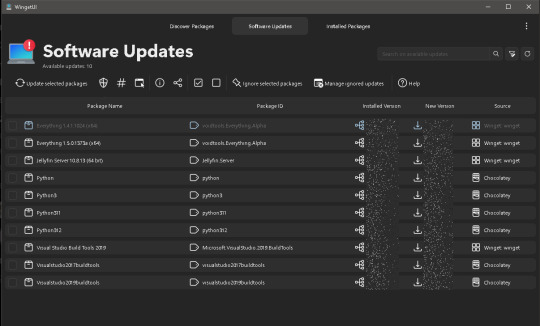
Software of the Week: WingetUI / UniGetUI
Keeping all of the programs on your computer up to date is important for security reasons; just ask LastPass, the disgraced password manager that got hacked because an employee's personal computer was running an old version of Plex Media Server. The particular vulnerability that the hackers exploited had been patched almost 3 years earlier, but because the employee never bothered to update Plex, he never got the fix.
Every month that you leave software on your computer un-patched is time in which hackers may discover the vulnerability and start using it to attack computers. But how on earth can you even figure out which of your programs need updates? Doing that one by one takes forever, and THEN you still have to actually install those updates.
This is where software updaters are essential. On Windows, SUMO used to be among the best programs for the job, but it was discontinued in early 2024. I've been searching for a replacement for a while now, and I finally settled on WinGetUI (soon to be known as UniGetUI). A LOT more detail and some tips are under the readmore!
Details:
Purpose: Provide a unified frontend for multiple package managers on Microsoft Windows to simplify installing and updating software
OS Supported: Windows 10, 11
Installer Size: 76 MB
Country of Origin: Catalonia/Spain
Languages Supported: 16 languages fully, 24 partially
License: Freeware
Download Link: https://www.marticliment.com/wingetui/
A LOT more detail and some tips are under the readmore!
Winget ("WIN-get") is the name of Microsoft Window's new-ish package manager, a program that itself takes care of installing and updating other software for you. Linux and Unix have had built-in package managers for decades, but Windows has been sorely lacking on that front until just recently. Winget provides the ability to install and update software, but it's a command line utility, meaning you have to type text into a command prompt in order to get winget to do anything for you.
WinGetUI is essentially just a nice interface using winget in the background; it shows you which programs you have installed, which ones have updates available, and it will even install the updates for you. That last part was a game changer for me personally as it saves me a lot of time (I have a LOT of programs and libraries installed on my computer).
The best part is the developer has added support for other package managers too. Computer language SDKs often come with their own package managers for downloading the little libraries that you can bundle with code that you write, and WinGetUI now supports most of them: npm, pip, .NET Tool, Chocolatey, scoop, Powershell Gallery, and it can even list software installed from the Steam shop or the Microsoft Store (though it can't update those ones for you). Incidentally, this is why the name is changing from WinGetUI to UniGetUI; it now supports a lot more package managers than just winget.
WinGetUI can even help you migrate software to a new computer. Simply install WinGetUI on your old computer, export a list of all of the software you have installed, then install WinGetUI on your new computer and import that list and then click install. You'll probably have to babysit it for a while because Windows will prompt you to give admin access to the installers that need it, but hey. At least you don't have to write down all the software you have and download and install each one by hand.
I do want to highlight that Microsoft is still working out the kinks in winget. Windows has existed for a long time and provided a lot of freedom in how you could install software. Multiple companies have made their fortunes just by providing custom installer software for Windows (InstallShield and NSIS being prime examples), so Microsoft has their work cut out for them trying to get all the different software manufacturers to list their software in the winget directory AND standardize their installers.
As such, you may run into issues like these:
WinGetUI lists a program you installed manually and tries to update it via winget; the installer succeeds, but because those installation methods are different, you end up with 2 copies of the software installed in different locations
WinGetUI fails to update a program because the hash of the downloaded installer doesn't match the hash that winget says it should have. This is usually a developer error
WinGetUI fails to determine whether some programs have updates available or not
WinGetUI downloads an installer/updater but it fails to run because it detects that the installation methods for that program are different (manual install vs. winget install)
Almost all of these can be resolved by uninstalling the manually installed version and reinstalling it using winget, either from the command line or just from WinGetUI. Once you do that one-time operation, the winget package manager (and by extension WinGetUI) should be able to handle everything from there on out. It will only get better too as winget usage becomes more common among software developers.
#software of the week#windows software#mine#wingetui#winget#package managers#microsoft windows#cybersecurity
3 notes
·
View notes
Text
How to Keep Your Information Safe on Social Media

Almost daily, it seems the news is reporting on the order of criminal incidents involving social media, such as account hacking and stalking. Protecting yourself from threats linked to these requires taking a disciplined entry to how you portion opinion online. Here are four tips for keeping your personal opinion safe even if using social media sites.
Make it Hard to Hack Your Account
Keeping your personal suggestion away from prying eyes starts following securing your social media accounts. Even taking basic stepssuch as using a hermetic unique password for each site you use, enabling two-factor authentication, and logging into sites unaided using trusted devicescan fend off most attacks.
You can toting in the works guard your accounts, even though, by avoiding using third-party apps and facilities to entry and control them. For example, many social media sites consent to you log in using your Google account. However, if your Google account gets hacked, the attacker will plus have entry to your socials via the attachment.
Though it may be a bit inconvenient, its greater than before to save your accounts walled off from each subsidiary to minimize the effects of cyber breaches and leaks.
Dont Answer Meme Questions
Youve likely seen a meme where you figure out what candy bar fits your personality by picking your birth month and hours of hours of daylight from a list. Although these memes can be fun to participate in, the realism is they are social engineering behavior to profit you into the future clean personal reference. By answering this meme, for instance, a hacker will learn the daylight and month you were born, which is a common security respond.
Social media gimmicks subsequent to these cause you to by accident have enough keep people in the expose of nefarious intentions the ammunition they compulsion to maltreatment you. Before you hop around the bandwagon and engage in memes considering this, find the recommendation its asking for and whether thats something you really hurting others to know.
Avoid Posting Photos behind Identifying Information
Photos manage to pay for in you take over and part important moments in your moving picture, but they often contain lots of identifying information. For instance, someone can meet the expense of an opinion what learned your kid goes to by the shirt theya propos wearing in the team photo. Posting pictures of your birthday party exposes later you were born, whats in your quarters, and who your buddies are.
Its sufficient to share images, but anonymize them as much as attainable. Be mindful of your background and avoid taking pictures taking into consideration than things, such as landmarks or street signs, that can aerate stuff you dont hurting known. Use photo editing tools to puzzling details youd rather remain private, and cut off EXIF embedded metadata (e.g. geolocation, phone type) from pictures back posting them online.
Choose Your Friends and Followers Wisely
While you may honoring your links and intimates, unfortunately, they can often be the source of data leaks. Not everyone values privacy or understands how dangerous sharing determined things online can be, consequently you dependence to be selective roughly who has right of entry to the stuff you gathering to your social media accounts.
Thoroughly vetting pal requests back assenting them can go a long quirk towards ensuring you without help have people in your network who esteem you permitted to save your personal details private.
Use these tips and calculation tools to on fire manage of your social media presence, hence you can have fun online safely and securely.
#smm#wholesale smm panel#digitla marketing#digitalmarketing#digital marketing#social marketing#smm panel
2 notes
·
View notes
Text
#001
site recomendation: OverTheWire
learn and practice security concepts with hands-on challenges
in this site there is a series of what they call wargames, they all increase in complexity and are very interesting
the first one, for example, is the bandit game and is aimed at very absolute beginners and teaches bash commands
each game has a different ssh port, but it's very simple to learn how to connect, just a simple "how to..." on google will help it
tip: when starting a new game, make a text file with every password so that you can always recall or pick over the level on where you left, simple example on the image

4 notes
·
View notes
Text
i know no one asked but i actually saw a good tip for this in a cybersecurity training course!
essentially you have a base phrase that is easy to remember, and modify the password for each website. the example they gave was using a common idiom (don’t put all your eggs in one basket), abbreviated it, and used that as a base phrase. so their example was DpAyEi1B! (Don’t put All your Eggs in 1 Basket !)
while that was a strong password in itself, it could be cracked with some effort and you don’t want to use the same password on every website. so they suggested modifying the password with the website it goes to (and i personally would suggest adding numbers to the end as well, maybe a special date or your favorite numbers for added security).
such as: DpAyEi1B!tumblr777 or DpAyEi1B!netflix4.20
it doesn’t have to be an idiom like that, just an easy thing for you to remember. if you like a certain game, do something with the game, or saying what your favorite color is.
in the course it said that a good password is long, has numbers and letters (both upper and lower case), and special characters. and a special character is anything that isn’t a letter or a number.
i thought it was helpful and definitely made making passwords easier, since i’m always stuck in the “i can’t remember 20 different passwords and the random gibberish that they’re supposed to be”
and if you need, you can also get a password manager or write down your base phrase, but you still want to make sure that that’s secure in some way, because if all your passwords are in one spot and that’s easy to grab, then it only takes one person to go through it and have your passwords.

#yes i’m aware that’s not the point of the post#do i care? no.#yes it’s a silly joke haha post but i had knowledge on the topic and i thought i would share it#because i can’t remember shit let alone a stupid password and its corresponding website#also in case this helps anyone else out like it did me: don’t use those example passwords as actual passwords#that’s public knowledge#which is the exact opposite thing you want for your passwords#anywho#stay safe and protect your cybersecurity#and other security ig lol
13K notes
·
View notes
Text
Mobile Security Tips for Sri Lankan Users

With increasing online threats, securing your mobile device is crucial—whether you're using a premium device or a mid-range model from an Online Mobile Store Sri Lanka.
Make Use of Biometric Locks and Strong Passwords
Mix numerals, symbols, capitals, and lowercase letters.
For faster and more secure access, turn on facial or fingerprint recognition.
Updates address known vulnerabilities in your operating system.
Turn on automatic system and app updates.
Steer clear of public wifi. Your data may be exposed on public networks if you don't have a VPN.
When using open networks for browsing, always make use of a trustworthy VPN.
Only download apps from reliable sources.
Use just the Apple App Store or Google Play Store.
Steer clear of third-party APKs and links in communications.
Make regular backups of your data.
Make use of cloud services such as iCloud or Google Drive.
To prevent data loss in the event of theft or damage, set up automatic backups.
Keep an eye on the permissions of the app
Don't give apps access to information they don't need, such as contacts or location.
Remove unused apps' permissions.
Watch Out for Phishing Messages
Never click on links in emails or texts you don't recognise.
Make use of texting apps that provide encryption.
Install security or anti-malware apps to increase protection. Bitdefender, Norton, or Kaspersky are a few examples.
Make sure the security app performs routine checks.
Turn on "Find My Device" or "Find My iPhone" on Android to be ready for the worst.
If your data is lost, use the remote wipe options to remove it. Check out security-friendly smartphones from Celltronics, one of Sri Lanka's most reputable tech companies, to enjoy the greatest technology while keeping your device completely safe.
0 notes
Text
Think Before You Click: A Simple Guide to Staying Safe Online
Imagine waking up one morning to find all your online accounts hacked, your private photos leaked, or your bank drained. Scary, right? In today’s hyper-connected world, everything — from shopping and banking to work and entertainment — happens online. That’s where cybersecurity services steps in

But don’t worry — cybersecurity doesn’t have to be complicated. Let’s break it down in simple terms, so you can understand why it matters and how to protect yourself.
What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These attacks usually aim to steal sensitive information, extort money, or disrupt normal operations.
Think of it like locking your doors at night — but for your computer, smartphone, or online data.
Why Should You Care?
Whether you're an individual browsing Instagram, a small business owner selling online, or a large organization handling customer data — everyone is a target. Hackers don’t just go after big companies. They go after whoever is vulnerable.
Here’s why cybersecurity is important:
Your personal data is valuable. Hackers want your passwords, credit card details, identity info, and more.
Cyber attacks can be devastating. One wrong click on a fake email can lead to stolen money or data loss.
Prevention is better than cure. Once your data is gone, it’s hard to recover. But staying safe isn’t that hard if you’re aware.
Common Cyber Threats (Made Simple)
Let’s simplify the jargon. Here are some common cyber threats you should know about:
1. Phishing
Fake emails or messages that trick you into clicking bad links or giving away personal information. Tip: Always double-check links and don’t trust messages that feel rushed or suspicious.
2. Malware
Malicious software that can harm your computer or steal your data. Tip: Install a trusted antivirus and avoid downloading files from unknown sources.
3. Ransomware
A type of malware that locks your files and demands money to unlock them. Tip: Backup your files regularly. If hit, don’t pay — contact experts instead.
4. Data Breaches
When hackers break into a company’s system and leak or steal customer information. Tip: Use strong, unique passwords for different accounts and enable two-factor authentication.
Real-Life Example
Remember the Facebook data leak? Millions of users’ personal info was exposed. Or when major hospitals and airlines had to shut down systems due to ransomware? These incidents remind us that cybersecurity isn’t just an IT issue — it’s a human issue.
How Can You Stay Safe Online?
You don’t need to be a techie to protect yourself. Here’s a simple checklist anyone can follow:
Use Strong Passwords: Make them long, unique, and hard to guess. Use a password manager if needed.
Enable Two-Factor Authentication: It adds an extra layer of protection — like a second lock on your door.
Avoid Suspicious Links: Don’t click unknown links, even if they come from someone you trust.
Keep Your Devices Updated: Updates fix bugs and security issues. Don’t delay them.
Back Up Your Data: Use cloud storage or an external drive. If you lose data, you’ll have a copy.
Avoid Public Wi-Fi for Sensitive Tasks: Public networks are easy to hack. Use a VPN if necessary.
Cybersecurity at Work
If you run a business — big or small — you must take cybersecurity seriously.
Train your employees to spot threats.
Protect customer and company data.
Invest in secure systems and software.
Work with IT experts for regular security audits.
One breach can cost you money, trust, and customers.
Future of Cybersecurity
With AI, smart devices, and remote work growing, cybersecurity will only become more important. Cyber criminals are evolving fast, but so are the tools and knowledge to fight back.
The first step? Awareness. And you've already taken it.
Final Thoughts
Cybersecurity isn’t about fear — it’s about awareness, responsibility, and simple habits that protect your digital life. In the online world, just like in the real one, it pays to lock your doors.
Whether you're a student, a working professional, or a business owner — cybersecurity is everyone’s business. Stay alert, stay updated, and never take your online safety for granted.
Call to Action:
Ready to make cybersecurity part of your everyday life? Follow us for easy, jargon-free insights on protecting yourself and your business online. Share this with someone who needs a reminder: your next smart click could protect a lot more than just your data.
0 notes
Text
XAT 2026 Registration Opens
The registration for XAT 2026 has officially begun from July 10, 2025. If you're aiming for admission into top management institutes like XLRI Jamshedpur, XIMB, IMT Ghaziabad, GIM Goa, and others, this is the right time to start your application process.
Whether you're a first-time applicant or repeating the exam, this guide will help you understand how to apply, important dates, eligibility criteria, top colleges, and what to expect in XAT 2026.
What is XAT?
XAT, or Xavier Aptitude Test, is a national-level MBA entrance exam conducted by XLRI Jamshedpur.
It is accepted by more than 160 B-schools across India.
XAT includes a unique Decision Making section, which tests practical and ethical reasoning — unlike most other entrance exams.
Important Dates for XAT 2026
Here are the key dates you should keep in mind:
Registration begins: July 10, 2025
Last date to apply: Likely first week of December 2025
Admit card release: Around third week of December 2025
Exam date: Expected on the first Sunday of January 2026
Result declaration: Likely by mid to late January 2026
These dates may change, so it's important to stay updated regularly.
Who Can Apply?
The eligibility criteria for XAT 2026 are simple and inclusive:
You must have a Bachelor's degree (minimum of three years) in any discipline from a recognized university.
There is no minimum marks or percentage required.
Final-year students who will complete their degree by June 2026 are also eligible.
Work experience is not mandatory, but it may be considered during selection for certain programs.

How to Apply for XAT 2026
XAT registration is entirely online. Here’s how to apply:
Visit the official XAT registration portal.
Click on "Register" and enter your name, mobile number, and email address.
You will receive your XAT ID and password via SMS and email.
Log in with your credentials and fill out the full application form, including academic details, work experience (if any), preferred test cities, and program choices.
Upload a recent passport-sized photograph and signature in the prescribed format.
Pay the application fee and submit the form.
After submission, download or print the confirmation page for your records.
XAT 2026 Application Fee
The expected application fees for XAT 2026 are:
XAT registration: Rs. 2100
Additional fee for each XLRI program: Rs. 200 per program
For example, if you apply for XAT and two programs at XLRI, your total fee would be Rs. 2500. Payment can be made through debit card, credit card, UPI, or net banking.
Top Colleges Accepting XAT Scores
In addition to XLRI Jamshedpur, many other reputed institutes accept XAT scores. Some of the well-known ones include:
XIM University, Bhubaneswar (XIMB)
IMT Ghaziabad
Goa Institute of Management (GIM)
TAPMI, Manipal
IRMA, Anand
FORE School of Management, New Delhi
K J Somaiya Institute of Management, Mumbai
LIBA, Chennai
Great Lakes Institute of Management, Chennai and Gurgaon
BIM Trichy
XIME, Bangalore, Chennai, and Kochi
Note that some institutes may require a separate application in addition to your XAT form.
What to Expect in XAT 2026
As of now, no major changes have been officially announced, but based on recent trends, here’s what you can expect:
The Decision Making section will likely remain a core part of the test.
An essay writing section may be included, though it is usually evaluated during the interview stage.
The exam will be conducted in computer-based mode in more than 70 cities across India.
Questions will be multiple choice, and the difficulty level is generally moderate to high.
Tips Before You Apply
Use an email ID and phone number that you actively use, as all communication will be sent there.
Double-check your application before submitting. Editing options are limited after submission.
Ensure that your scanned photo and signature meet the size and format requirements.
Save your XAT ID and password in a secure place for future use (admit card download, result checking, etc.).
Final Thoughts
XAT 2026 is a crucial opportunity for students who aspire to join top management institutes in India. Whether you're targeting XLRI’s Business Management or Human Resource programs, or any of the 160+ B-schools that accept XAT scores, applying early is the smart move.
The registration window is now open, and it’s better to complete the form sooner rather than waiting till the last date. This gives you time to prepare for the exam, stay organized, and focus on your study strategy.
Stay tuned to Dekho Campus for more articles on exam preparation, college cutoffs, selection processes, and admission tips.
Best of luck to all the aspirants preparing for XAT 2026.
1 note
·
View note
Text
Statutory Returns Made Easy: Tax, SSNIT & VAT Filing Tips
By Jonathan Ainoo
For many business owners—especially small to mid-sized ones—filing statutory returns feels like stepping into a maze. You know it's important. You know you can’t skip it. But the rules feel confusing, the forms seem endless, and the deadlines always seem to creep up too fast.
In Ghana, statutory compliance revolves around several pillars: income tax, VAT, and SSNIT (the Social Security and National Insurance Trust). Each one carries its own filing schedule, submission process, and penalties for non-compliance. Miss one return or under-report figures, and the penalties can pile up before you even realize what went wrong.
At JOBEX COMPANY LTD, we’ve made it part of our job to simplify this. Not just for ourselves—but for others too. Over the years, we’ve assisted dozens of clients in mining, logistics, engineering, and hospitality to get a better grip on their statutory obligations. And here’s the thing: once you understand the rhythm, it gets a lot easier.
Let’s break it down.
1. Know What You Owe—and When This sounds basic, but it's the step many businesses skip. Income tax is typically filed annually, with quarterly payments along the way. VAT? That’s monthly. SSNIT contributions for employees? Also monthly—and must be filed even if there were no staff or wages for that month.
We once supported a catering subcontractor who assumed that no workers meant no SSNIT return. She missed three zero returns. The fines? Far more than what she would’ve owed had she simply filed on time with a “Nil” return. It was a tough lesson—but a common one.
2. Keep Your Records Clean Another point that sounds obvious until you’re knee-deep in receipts. VAT-registered companies must issue VAT invoices and keep all sales and purchase records for auditing. Payroll data must match SSNIT filings. Bank statements should reflect declared income.
At JOBEX, we developed a simple system: a monthly compliance checklist. It tracks invoices issued, salaries paid, purchases made, and who was responsible for uploading what. You don’t need fancy software. Just consistency.
3. Understand the Platforms Ghana Revenue Authority (GRA) now allows online tax filing through its iTaPS platform. SSNIT also provides an employer portal for digital submissions. These systems are meant to help, but they can be intimidating at first.
We helped a vehicle rental client switch from manual filing to online submission. The first few months were bumpy—missed passwords, system outages—but by the third quarter, they were filing everything from their office, no queues, no courier costs.
4. Assign Responsibility—But Stay Involved Many business owners hand over all tax issues to an accountant or external consultant. That’s fine—but dangerous if you don’t stay informed. At JOBEX COMPANY LTD, we involve department heads during each filing cycle. Operations reviews fuel expenses, HR confirms payroll, and finance compiles the data. It takes a few hours, but we sleep better knowing everyone understands what’s been filed in their name.
5. Don’t Wait for a Letter Most tax problems don’t start with fraud. They start with forgetting. A missed return here. A delayed payment there. And then, suddenly, a demand letter with interest charges and potential audits.
I think this is where many businesses lose momentum. They feel overwhelmed, so they ignore it. The silence is deceptive. Just because no one’s knocking now doesn’t mean the system isn’t tracking. Filing late might not hurt today—but it will show up later, usually at the worst time. Like when you're applying for a loan, tendering for a contract, or being considered for something much bigger.
Take us, for example. JOBEX COMPANY LTD is proud to be a nominee for the 2025 Go Global Awards, to be held in London this November and hosted by the International Trade Council. Being part of something that brings together the world’s sharpest business minds—people creating solutions, exploring new partnerships, and adapting to change—requires credibility. And compliance is a huge part of that credibility. It’s not just about ticking boxes. It’s about showing you run your business with integrity.
So, what’s the takeaway?
Don’t fear your filings. Learn them. Tame them. Build simple systems around them. You don’t need to be a tax expert to stay compliant. You just need to pay attention—and act early.
At JOBEX COMPANY LTD, we’re not perfect. We’ve had our share of near-misses. But every time we cleaned up a system, every time we submitted on time or corrected an oversight before it became a penalty—we got stronger.
And I think that’s what sustainable business is about. Not just growing—but growing responsibly.
#StatutoryReturns#TaxFilingTips#SSNITCompliance#VATGhana#BusinessCompliance#JobexCompanyLtd#JonathanAinoo#GhanaBusiness#GoGlobalAwards2025#InternationalTradeCouncil#SMEAdvice#EntrepreneurTips#FinancialDiscipline#AccountingBasics#OperationalExcellence
0 notes