#Third-Party Coding Audit
Explore tagged Tumblr posts
Text
External Coding Audits: A Vital Tool for Healthcare Providers

In today’s complex healthcare landscape, with constantly evolving medical codes and payer regulations, external coding audits have become a crucial tool for healthcare providers. These independent reviews, conducted by third-party experts, offer a comprehensive assessment of coding practices, identifying errors, inefficiencies, and potential compliance risks.
Why are External Coding Audits Important?
Ensuring Compliance: Healthcare is a heavily regulated industry. External audits help providers adhere to strict coding standards, reducing the risk of penalties and legal issues.
Improving Coding Accuracy: By identifying and correcting coding errors, audits help prevent claim denials and underpayments, safeguarding revenue integrity.
Enhancing Operational Efficiency: Regular audits can streamline coding processes, leading to increased efficiency and reduced administrative costs.
Key Benefits of External Coding Audits:
Reduced Compliance Risk: By staying up-to-date with regulatory changes, audits minimize the risk of non-compliance.
Objective Assessment: External auditors provide an unbiased perspective, identifying issues that internal reviews might miss.
Improved Documentation: Audits often lead to better documentation practices, supporting accurate coding and clinical decision-making.
Increased Revenue: By identifying missed billing opportunities and reducing denials, audits can boost revenue and cash flow.
Continuous Learning: Audit feedback provides valuable insights for training and educating coding staff.
Types of External Coding Audits:
Pre-Bill Audits: Review coding before claims are submitted to prevent errors.
Retrospective Audits: Analyze past claims to identify and correct errors.
Focused Audits: Target specific services or departments for in-depth review.
Common Coding Errors Identified by Audits:
Upcoding or Downcoding: Billing for services at an incorrect level.
Unbundling: Separately billing for procedures that should be grouped together.
Incomplete or Inaccurate Documentation: Lack of sufficient documentation to support coding.
How to Choose the Right External Coding Audit Partner:
When selecting an external audit partner, consider the following:
Certification and Expertise: Choose a partner with certified coding professionals.
Proven Track Record: Look for a partner with a history of successful audits.
Customization Capabilities: Select a partner that can tailor audits to your specific needs.
By investing in regular external coding audits, healthcare providers can significantly improve their coding accuracy, compliance, and overall financial performance. A reliable medical coding company and medical billing services provider like Allzone MS can help navigate the complexities of medical coding, ensuring that your organization is well-positioned to thrive in the dynamic healthcare landscape.
Read more: https://www.allzonems.com/medical-coding-audit/
#Allzone MS Medical Coding Audits#American Medical Association guidelines#Avoiding Medical Coding Errors#Benefits of External Coding Audits#Centers for Medicare & Medicaid Services guidelines#Certified Medical Coders#Choosing a Medical Coding Audit Partner#Coding Documentation Improvement#CPT#CPT Codes#E/M Codes#External coding audit#External vs Internal Coding Audits#Focused Medical Coding Audits#HCPCS Coding Compliance#Healthcare Coding Audits#Healthcare Compliance Audits#ICD-10#ICD-10-CM Codes#Medical Coding Accuracy#Medical Coding Audit#Medical Coding Audit Best Practices#Medical Coding Compliance#medical-coding#Medicare Physician Fee Schedule final rules#payer coding guidelines#reducing claim denials#Revenue Integrity in Healthcare#Revenue Optimization for Healthcare Providers#Third-Party Coding Audit
0 notes
Text
Traditional Vs Automated Direct Mail Services
Direct mail has long been a trusted marketing channel. In 2025, businesses face a choice between traditional direct mail services and automated solutions. Understanding the difference can drastically impact your campaign’s efficiency, ROI, and customer experience.

What Is Traditional Direct Mail?
Traditional direct mail involves manual processes such as:
Designing postcards or letters by hand or through desktop software
Printing at local shops or internal print facilities
Manually stuffing, stamping, and mailing
Tracking via physical receipts or third-party couriers
Pros:
Full control over the process
Hands-on personalization
Local vendor relationships
Cons:
Time-consuming
Prone to human error
Hard to scale
Costlier for small volumes
What Is Automated Direct Mail?
Automated direct mail refers to using software or APIs to trigger, personalize, print, and send mail pieces based on digital actions or CRM data.
Examples:
A new customer signs up, and a welcome postcard is triggered automatically
Abandoned cart triggers a mailed coupon
Real-time API sends birthday cards based on database date
Pros:
Scalable for millions of mailings
Real-time integration with CRMs and marketing platforms
Consistent branding and quality
Analytics and tracking included
Cons:
Higher setup cost initially
Requires data hygiene and tech alignment
Key Differences Between Traditional and Automated Direct Mail
FeatureTraditionalAutomatedSpeedSlow (days to weeks)Instant or scheduledScalabilityLimitedHighly scalablePersonalizationManualDynamic via variable dataTrackingManual or nonexistentDigital trackingIntegrationNoneAPI and CRM support
When Should You Choose Traditional?
For small, one-time mailings
When personal touch matters (e.g., handwritten letters)
In areas with no access to digital tools
When to Use Automated Direct Mail?
For ongoing marketing campaigns
When speed, consistency, and tracking are priorities
For eCommerce, SaaS, healthcare, insurance, and real estate
Use Case Comparisons
Traditional Use Case: Local Real Estate Agent
Manually prints and mails just listed postcards to a zip code every month.
Automated Use Case: National Insurance Company
Triggers annual policy renewal letters for 500,000+ customers via API.
Benefits of Automation in 2025
Real-Time Triggers from websites, CRMs, or payment systems
Enhanced Reporting for ROI measurement
Reduced Costs with bulk printing partnerships
Faster Delivery using localized printing partners globally
Eco-Friendly Workflows (less waste, digital proofing)
How to Switch from Traditional to Automated Direct Mail
Audit your current workflow
Choose a provider with API integration (e.g., PostGrid, Lob, Inkit)
Migrate your address data and test campaigns
Train your team and build trigger-based workflows
Conclusion: Choosing the Right Direct Mail Method
Ultimately, the right choice depends on your goals. While traditional direct mail has its place, automated direct mail offers speed, flexibility, and scale. For modern businesses aiming for growth and efficiency, automation is the clear winner.
SEO Keywords: traditional vs automated direct mail, automated mailing services, direct mail automation, API for direct mail, manual vs automated marketing.
youtube
SITES WE SUPPORT
Healthcare Mailing API – Wix
2 notes
·
View notes
Text
Future-Proof Your Brand: Why a Holistic Digital Marketing Strategy Matters in 2025
An in-depth guide by Digitalized Era
In the post-cookie, AI-driven landscape of 2025, piecemeal tactics are no longer enough to keep a brand visible, relevant, and profitable. Whether you run a local bakery in Jacksonville or a SaaS start-up in London, you need a holistic digital marketing strategy that ties every channel—SEO, social, paid ads, content, email, and web development—into one cohesive growth machine.
1. The Shift From “Channel Thinking” to “Customer Journey Thinking”
Old model
“We need Facebook posts.”
“Let’s run a Google Ads campaign this quarter.”
New model
“Sarah discovers us on TikTok, reads a blog we rank for on Google, joins our email list, and finally converts through a retargeting ad.”
This journey mindset forces you to optimise touchpoints together rather than in silos—exactly what Digitalized Era’s 360-degree process delivers:
Site Audit & UX checks
Deep market + keyword research
On-page & technical SEO
Cross-channel content mapping
Unified paid + organic reporting
Continuous CRO (Conversion Rate Optimisation)
2. Data Privacy & First-Party Data: The 2025 Reality
By the end of 2024, Chrome will have deprecated third-party cookies. Brands that fail to build first-party data pipelines will pay up to 35 % more for the same ad results. Digitalized Era helps you:
Capture consent with value-driven lead magnets
Segment subscribers in GDPR/CCPA-compliant workflows
Deploy personalised email drips that nurture, upsell, and retain
Result: lower acquisition costs, higher lifetime value.
3. AI Is Only as Good as Your Strategy
Tools like ChatGPT, Midjourney, and Google Gemini can accelerate content production—but they can’t replace:
Brand voice & POV
Strategic keyword selection
Human-centred storytelling
Our content marketing team blends AI efficiency with senior-level editorial oversight to create assets that rank and convert. Expect:
Long-form pillar pages
Social micro-content repurposed from cornerstone blogs
Data-rich infographics coded for fast mobile load times
4. Local, National, or Global: SEO Tactics That Scale
Local SEO – GMB optimisation, NAP consistency, hyper-local schema
E-commerce SEO – faceted navigation fixes, Shopify/Woo Commerce technical audits
International SEO – hreflang mapping, currency/region-specific content
Digitalized Era’s proprietary reporting dashboard shows real-time rank shifts across markets so you can allocate budget where ROI is highest.
5. Paid Media Is No Longer “Set & Forget”
Average CPCs rose 19 % last year in the US. To stay profitable you need:
Intent-driven keyword clusters, not vanity terms
AI-augmented bid strategies with human QA
Cross-channel attribution (PPC + organic + email)
Our PPC specialists iterate weekly, pausing under-performers and reallocating spend to winning ad sets—so every rupee, dollar, or pound works harder.
6. UX-Focused Web Design: Your New Sales Rep
A 0.1-second improvement in load time can boost conversions by 8 %. Digitalized Era’s design & dev squad builds:
Mobile-first, Core Web Vitals-optimized sites
Shopify, WordPress & Wix builds that integrate seamlessly with CRM and marketing automation
Accessibility-compliant interfaces (WCAG 2.2)
Beautiful and built to rank.
7. Measuring What Matters
Vanity metrics (likes, impressions) don’t pay the bills. We align on KPIs tied directly to revenue:
Qualified leads generated
Customer acquisition cost (CAC)
Average order value (AOV)
Customer lifetime value (CLV)
Return on ad spend (ROAS)
Our live dashboards deliver clarity, not confusion.
8. Success Stories
Leather Made In Italy moved from zero top-100 keywords to page-one dominance. Prevail Clothing scaled organic traffic 3× in six months. Cozyts saw Instagram engagement jump 220 % after a visual revamp.
Your brand could be next.
9. The Digitalized Era Advantage
✔ End-to-end expertise under one roof ✔ 24/7 support via phone (+91 674 357 6892) or email ([email protected]) ✔ Transparent, package-based pricing for SMEs and start-ups ✔ Offices in the US, UK, and India for truly global coverage
Ready to Transform Your Business?
Turn every click into a customer. Schedule a free 30-minute strategy call today:
📞 +91 674 357 6892 📧 [email protected]
Digitalized Era—your gateway to digital excellence. Let’s make 2025 your breakout year.
2 notes
·
View notes
Text
⏱Hangfire + Serilog: How EasyLaunchpad Handles Jobs and Logs Like a Pro

Modern SaaS applications don’t run on user actions alone.
From sending emails and processing payments to updating user subscriptions and cleaning expired data, apps need background tasks to stay efficient and responsive.
That’s why EasyLaunchpad includes Hangfire for background job scheduling and Serilog for detailed, structured logging — out of the box.
If you’ve ever wondered how to queue, manage, and monitor background jobs in a .NET Core application — without reinventing the wheel — this post is for you.
💡 Why Background Jobs Matter
Imagine your app doing the following:
Sending a password reset email
Running a weekly newsletter job
Cleaning abandoned user sessions
Retrying a failed webhook
Syncing data between systems
If these were handled in real-time within your controller actions, it would:
Slow down your app
Create a poor user experience
Lead to lost or failed transactions under load
Background jobs solve this by offloading non-critical tasks to a queue for asynchronous processing.
🔧 Hangfire: Background Job Management for .NET Core
Hangfire is the gold standard for .NET Core background task processing. It supports:
Fire-and-forget jobs
Delayed jobs
Recurring jobs (via cron)
Retry logic
Job monitoring via a dashboard
Best of all, it doesn’t require a third-party message broker like RabbitMQ. It stores jobs in your existing database using SQL Server or any other supported backend.
✅ How Hangfire Is Integrated in EasyLaunchpad
When you start with EasyLaunchpad:
Hangfire is already installed via NuGet
It’s preconfigured in Startup.cs and appsettings.json
The dashboard is live and secured under /admin/jobs
Common jobs (like email dispatch) are already using the queue
You don’t have to wire it up manually — it’s plug-and-play.
Example: Email Queue
Let’s say you want to send a transactional email after a user registers. Here’s how it’s done in EasyLaunchpad:
_backgroundJobClient.Enqueue(() =>
_emailService.SendWelcomeEmailAsync(user.Id));
This line of code:
Queues the email job
Executes it in the background
Automatically retries if it fails
Logs the event via Serilog
🛠 Supported Job Types
Type and Description:
Fire-and-forget- Runs once, immediately
Delayed- Runs once after a set time (e.g., 10 minutes later)
Recurring- Scheduled jobs using CRON expressions
Continuations- Run only after a parent job finishes successfully
EasyLaunchpad uses all four types in various modules (like payment verification, trial expiration notices, and error logging).
🖥 Job Dashboard for Monitoring
Hangfire includes a web dashboard where you can:
See pending, succeeded, and failed jobs
Retry or delete failed jobs
Monitor job execution time
View exception messages
In EasyLaunchpad, this is securely embedded in your admin panel. Only authorized users with admin access can view and manage jobs.
🔄 Sample Use Case: Weekly Cleanup Job
Need to delete inactive users weekly?
In EasyLaunchpad, just schedule a recurring job:
_recurringJobManager.AddOrUpdate(
“InactiveUserCleanup”,
() => _userService.CleanupInactiveUsersAsync(),
Cron.Weekly
);
Set it and forget it.
🧠 Why This Is a Big Deal for Devs
Most boilerplates don’t include job scheduling at all.
In EasyLaunchpad, Hangfire is not just included — it’s used throughout the platform, meaning:
You can follow working examples
Extend with custom jobs in minutes
Monitor, retry, and log with confidence
You save days of setup time, and more importantly, you avoid production blind spots.
📋 Logging: Meet Serilog
Of course, background jobs are only useful if you know what they’re doing.
That’s where Serilog comes in.
In EasyLaunchpad, every job execution is logged with:
Timestamps
Job names
Input parameters
Exceptions (if any)
Success/failure status
This structured logging ensures you have a full audit trail of what happened — and why.
Sample Log Output
{
“Timestamp”: “2024–07–20T14:22:10Z”,
“Level”: “Information”,
“Message”: “Queued email job: PasswordReset for userId abc123”,
“JobType”: “Background”,
“Status”: “Success”
}
You can send logs to:
Console (for dev)
File (for basic prod usage)
External log aggregators like Seq, Elasticsearch, or Datadog
All of this is built into EasyLaunchpad’s logging layer.
🧩 How Hangfire and Serilog Work Together
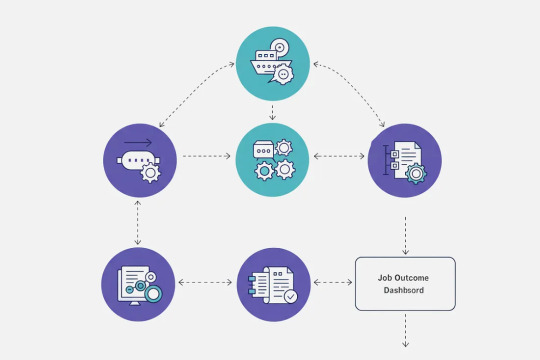
Here’s a quick visual breakdown:
Job Triggered → Queued via Hangfire
Job Executed → Email sent, cleanup run, webhook processed
Job Outcome Logged → Success or error captured by Serilog
Job Visible in Dashboard → Retry if needed
Notifications Sent (optional) → Alert team or log activity via admin panel
This tight integration ensures your background logic is reliable, observable, and actionable.
💼 Real-World Use Cases You Can Build Right Now
-Feature and the Background Job
Welcome Emails- Fire-and-forget
Trial Expiration- Delayed
Subscription Cleanup- Recurring
Payment Webhook Retry- Continuation
Email Digest- Cron-based job
System Backups- Nightly scheduled
Every one of these is ready to be implemented using the foundation in EasyLaunchpad.
✅ Why Developers Love It
-Feature and the Benefit
Hangfire Integration- Ready-to-use queue system
Preconfigured Retry- Avoid lost messages
Admin Dashboard- See and manage jobs visually
Structured Logs- Full traceability
Plug-and-Play Jobs- Add your own in minutes
🚀 Final Thoughts
Robust SaaS apps aren’t just about UI and APIs — they’re also about what happens behind the scenes.
With Hangfire + Serilog built into EasyLaunchpad, you get:
A full background job system
Reliable queuing with retry logic
Detailed, structured logs
A clean, visual dashboard
Zero config — 100% production-ready
👉 Launch smarter with EasyLaunchpad today. Start building resilient, scalable applications with background processing and logging already done for you. 🔗 https://easylaunchpad.com
#.net development#.net boilerplate#Hangfire .net Example#easylaunchpad#Serilog Usage .net#Background Jobs Logging#prebuilt apps#Saas App Development
2 notes
·
View notes
Text
Expanding into India? Here’s Why You Need an Employer of Record Service Provider in India

Employer of Record Service Provider in India: Your Gateway to Compliant and Swift Hiring
Expanding your workforce into India opens up access to one of the world’s most dynamic labor markets. But setting up operations in a foreign country brings its own set of legal, HR, and administrative challenges. This is where an Employer of Record service provider in India becomes an invaluable ally. An EOR helps you hire and manage employees in India—without the need to register a legal entity—while ensuring compliance with all local employment laws.
Whether you're a startup testing new markets or a multinational company seeking scalable hiring solutions, using an EOR streamlines the hiring process, reduces legal risk, and enables faster business expansion in India.
What Exactly is an Employer of Record (EOR)?
An Employer of Record (EOR) is a third-party organization that officially employs staff on your behalf. While you maintain control over the employees’ day-to-day work, the EOR handles the employment contract, payroll processing, tax compliance, benefits, and HR administration.
By working with an Employer of Record service provider in India, businesses can legally onboard talent across Indian states, manage payroll accurately, and stay compliant with evolving labor laws—without the time-consuming process of company registration or building a local HR team from scratch.
Key Advantages of Using an Employer of Record in India
India is home to a vast and diverse workforce, but it also has a complex regulatory system. Here’s why hiring through an Employer of Record service provider in India is a smart strategy for global employers:
1. Quick Market Penetration
Incorporating a business in India can take weeks or even months due to legal and bureaucratic hurdles. An EOR lets you bypass those delays and begin operations and employee onboarding immediately.
2. Guaranteed Compliance
Labor regulations in India are intricate, with different laws at the national and state levels. An EOR ensures you comply with rules around minimum wages, labor contracts, PF/ESI, gratuity, maternity leave, and more—thus avoiding penalties and audit risks.
3. Streamlined Payroll and HR Operations
Managing payroll in India requires navigating complex tax calculations, employee benefits, and statutory deductions. An EOR automates these processes, ensuring every paycheck and report is accurate, on time, and compliant.
4. Risk-Free Hiring
Hiring in India without a legal entity can expose you to significant regulatory and legal risks. With an EOR acting as the legal employer, your liability is significantly reduced.
5. Cost-Saving and Scalable
Building local infrastructure, from HR teams to legal advisors, can be expensive. An EOR offers a pay-as-you-go model, helping you scale your workforce without long-term commitments or high operational costs.
Who Should Hire an Employer of Record Service Provider in India?
Working with an Employer of Record service provider in India is ideal for:
Startups exploring Indian markets without full-scale investment
Enterprises expanding rapidly into Asia and requiring scalable HR solutions
Remote teams looking to legally employ Indian professionals across multiple states
Consulting and project-based companies needing to onboard short-term teams legally
How to Choose the Right EOR Service in India
Not all EOR providers offer the same quality of service. Here’s what to look for when selecting your partner:
1. Local Law Expertise
The provider should have in-depth knowledge of Indian labor laws, tax codes, and regional employment regulations.
2. Reliable Payroll Technology
A modern payroll platform helps ensure seamless salary disbursement, tax filing, and compliance tracking.
3. Data Protection Standards
Your provider should maintain strict data privacy measures in line with global standards like GDPR.
4. Responsive Customer Support
Prompt, knowledgeable support is essential when dealing with complex HR or compliance queries.
5. Clear Pricing Structure
Choose an EOR that offers a transparent, all-inclusive pricing model without hidden fees or surprise charges.
What Services Do EOR Providers Offer in India?
A top-tier Employer of Record service provider in India typically delivers:
Employee onboarding and documentation
Employment contracts customized to Indian labor law
End-to-end payroll management
Statutory contributions and tax payments
Compliance reporting and audit support
Benefits administration (PF, ESI, bonuses, leaves)
Exit management and final settlements
Conclusion
India presents a tremendous opportunity for businesses looking to tap into its tech-savvy, educated workforce. But growth must be matched with legal and operational compliance. Partnering with a trusted Employer of Record service provider in India removes the roadblocks associated with local hiring, letting you focus on performance, productivity, and innovation.
Whether you're entering the market for the first time or expanding your team across regions, an EOR provides the speed, flexibility, and peace of mind you need to succeed. Take the next step with a provider who understands India—so you can hire with confidence and scale without limits
2 notes
·
View notes
Text
Unlocking the Secrets to Effortless Compliance with ZATCA Phase 2
The Kingdom of Saudi Arabia is leading the way in digital transformation, especially with its structured e-invoicing initiatives. A significant part of this movement is ZATCA Phase 2, which aims to enhance transparency, boost efficiency, and ensure tax compliance across businesses.
If you are a business owner, accountant, or IT professional, understanding ZATCA Phase 2 is no longer optional. It is critical for ensuring that your operations remain compliant and future-ready. This guide breaks down everything you need to know in a simple, easy-to-understand manner.
What Is ZATCA Phase 2?
ZATCA Phase 2, also known as the Integration Phase, is the next major step following Saudi Arabia's Phase 1 e-invoicing requirements. While Phase 1 focused on the generation of electronic invoices, Phase 2 moves beyond that.
It requires businesses to integrate their e-invoicing systems with ZATCA’s Fatoora platform, allowing real-time or near-real-time transmission of invoices for clearance and validation.
This phase ensures that each invoice issued meets strict technical, security, and data format requirements set by the Zakat, Tax and Customs Authority (ZATCA).
Key Objectives Behind ZATCA Phase 2
Understanding the "why" behind Phase 2 can help businesses see it as an opportunity rather than a burden. The main goals include:
Improving tax compliance across all sectors
Minimizing fraud and manipulation of invoices
Streamlining government audits with real-time data
Promoting a transparent digital economy
Enhancing business operational efficiency
Who Needs to Comply?
All businesses registered for VAT in Saudi Arabia must comply with ZATCA Phase 2 regulations. This includes:
Large enterprises
Medium and small businesses
Businesses using third-party billing service providers
Companies operating across multiple sectors
Even if your business operates primarily offline, if you are VAT registered, you need to be compliant.
Important Requirements for ZATCA Phase 2
Compliance with ZATCA Phase 2 is not just about sending electronic invoices. It involves specific technical and operational steps. Here’s what your business needs:
1. E-Invoicing System with ZATCA Compliance
Your billing or accounting system must:
Issue invoices in XML or PDF/A-3 with embedded XML
Securely store invoices electronically
Incorporate UUIDs (Unique Identifiers) for each invoice
Attach a QR code for simplified verification
2. Integration with ZATCA Systems
Businesses must establish a secure Application Programming Interface (API) connection with ZATCA’s platform to allow the real-time sharing of invoice data.
3. Cryptographic Stamp
Each invoice must carry a cryptographic stamp. This verifies the invoice's authenticity and integrity.
4. Archiving
Invoices must be securely archived and retrievable for at least six years in case of audits or regulatory reviews.
Implementation Timeline for ZATCA Phase 2
ZATCA is rolling out Phase 2 gradually, targeting businesses in waves based on their annual revenues:
Wave 1: Businesses with annual revenues above SAR 3 billion (started January 1, 2023)
Wave 2: Revenues above SAR 500 million (started July 1, 2023)
Future Waves: Gradually extending to smaller businesses
Each business is officially notified by ZATCA at least six months before their compliance date, giving them time to prepare.
How to Prepare for ZATCA Phase 2: A Step-by-Step Guide
The good news is that with proper planning, adapting to ZATCA Phase 2 can be straightforward. Here’s a simple preparation roadmap:
Step 1: Review Your Current Systems
Audit your existing accounting and invoicing solutions. Identify whether they meet Phase 2’s technical and security standards. In most cases, upgrades or new software may be required.
Step 2: Select a ZATCA-Approved Solution Provider
Look for software vendors that are pre-approved by ZATCA and offer:
Seamless API integration
Cryptographic stamping
XML invoice generation
Real-time data reporting
Step 3: Integration Setup
Collaborate with IT teams or third-party service providers to set up a secure connection with the Fatoora platform.
Step 4: Employee Training
Ensure that relevant departments, such as finance, IT, and compliance, are trained to manage new invoicing processes and troubleshoot any issues.
Step 5: Test Your Systems
Conduct dry runs and testing phases to ensure that invoices are being properly cleared and validated by ZATCA without delays or errors.
Step 6: Go Live and Monitor
Once your system is ready and tested, begin issuing invoices according to Phase 2 standards. Regularly monitor compliance, system errors, and feedback from ZATCA.
Common Challenges and How to Overcome Them
Businesses often encounter several challenges during their Phase 2 preparation. Awareness can help you avoid them:
Integration Difficulties: Solve this by partnering with experienced ZATCA-compliant vendors.
Employee Resistance: Overcome this with proper training and clear communication on the benefits.
Technical Errors: Regular testing and quick troubleshooting can help prevent issues.
Lack of Budget Planning: Allocate a specific budget for compliance early to avoid unexpected costs.
Preparation is not just technical. It’s organizational as well.
Benefits of Early Compliance with ZATCA Phase 2
Early compliance does more than just prevent penalties:
Improves Financial Reporting Accuracy: Real-time clearance ensures clean records.
Builds Market Trust: Clients and partners prefer businesses that follow regulatory norms.
Enhances Operational Efficiency: Automated invoicing processes save time and reduce errors.
Boosts Competitive Advantage: Staying ahead in compliance projects an image of professionalism and reliability.
Businesses that proactively adapt to these changes position themselves as industry leaders in the evolving Saudi economy.
Conclusion
ZATCA Phase 2 is not just a regulatory requirement. It’s an opportunity to upgrade your operations, improve financial accuracy, and enhance business credibility.
By understanding the requirements, preparing strategically, and partnering with the right solution providers, your business can turn this challenge into a growth opportunity.
The sooner you act, the smoother your transition will be. Compliance with ZATCA Phase 2 is your gateway to becoming part of Saudi Arabia’s dynamic digital economy.
2 notes
·
View notes
Text
Bitcoin Volatility Fuels Market Anxiety; XBIT Decentralized Exchange Charts Steady Recovery
1. Regulatory Storm Amid Bitcoin’s ATH As Bitcoin’s price surpassed its all-time high (ATH) of $100,000 in early 2025, a global regulatory storm engulfed cryptocurrency markets. Centralized exchanges (CEXs) worldwide faced abrupt blockages, operational restrictions, or asset freezes, triggering widespread investor panic. Amid the turmoil, XBIT Exchange—a decentralized trading platform (DEX)—rapidly gained traction, with its trading volume surging 400% month-over-month and positioning itself as a secure harbor for Bitcoin holders.

2. Centralized Platforms Under Scrutiny In March 2025, the U.S. Securities and Exchange Commission (SEC) launched investigations into five major crypto platforms for compliance violations, while Japan’s Financial Services Agency (FSA) announced a sweeping review of all Bitcoin-related exchanges. Concurrently, mid-tier platforms like CoinTide and UltraX halted services indefinitely, freezing over $120 million in user assets. These events forced investors to confront a critical question: Can centralized platforms ever be truly secure?
3. Decentralized Solutions Regain Momentum The concept of decentralized exchanges (DEXs), once dismissed as niche tools due to technical complexity, has resurged under regulatory pressure. XBIT Exchange exemplifies this shift. Operating via on-chain smart contracts, the platform eliminates third-party custody, manual intervention, and Know Your Customer (KYC) requirements, adhering strictly to the principles of self-custody, transparency, and censorship resistance. Users interact directly through non-custodial wallets, with every transaction recorded immutably on the blockchain.

4. Demystifying Decentralized Exchanges A decentralized exchange operates entirely on blockchain networks, executing trades through automated smart contracts without holding user funds. Key features include:
Non-custodial design: Assets remain in users’ wallets until trade execution.
Tamper-proof execution: Transactions are verified by code, not human intermediaries.
Transparent audit trails: All activities are publicly verifiable on-chain.
XBIT currently supports Bitcoin, Ethereum, and major stablecoins, with cross-chain interoperability slated for Q3 2025.
5. Data-Driven Adoption Surge According to blockchain analytics firm DataLink, DEX usage surged 275% globally between March and May 2025, with 43% of new users migrating from CEXs after experiencing freezes or high fees. “After my funds were frozen on a traditional platform, I realized decentralization isn’t optional—it’s essential,” said Berlin-based investor Marlin Koch.
XBIT’s metrics underscore this trend: daily new wallet addresses exceed 5,200, while monthly transactions grew 320% year-over-year (YoY), rivaling legacy platforms.
6. XBIT’s Strategic Edge
Global node network: A distributed architecture minimizes risks of server seizures or exit scams.
On-chain risk scoring: Real-time security audits for every transaction.
User-centric interface: Features like one-click trading and QR-synced wallet logins lower barriers for retail investors.

7. Conclusion: Redefining Crypto’s Future As Bitcoin evolves from a speculative asset to a global hedge, the demand for secure, transparent trading infrastructure grows imperative. Decentralized platforms like XBIT are no longer ideological experiments but market necessities—offering resilience against regulatory volatility and redefining trust in digital finance.
2 notes
·
View notes
Text
Meet the Builders: Behind the Scenes of SonicxSwap’s Ecosystem Growth
SonicxSwap

It All Starts With the Builders
In a crypto space crowded with flashy features and token launches, it’s easy to forget what matters most: the builders behind the scenes.
SonicxSwapdidn’t just appear — it was designed, developed, tested, and evolved by a dedicated team of Web3 natives, developers, and growth strategists. Their silent grind is what’s powering the platform’s growth on the Sonic Blockchain.
This blog pulls back the curtain on the people, mindset, and culture that drive SonicxSwapforward.
Not Just Coders — Crypto-Native Creators
The SonicxSwap team brings together DeFi visionaries, product builders, designers, and marketers with one shared goal: building an ecosystem that’s faster, simpler, and more community-focused.
They’re not just building a DEX or a launchpad. They’re shaping a new culture of decentralized finance — with a strong focus on usability, innovation, and transparency.
Culture of Speed and Purpose
What sets the SonicxSwapbuilders apart isn’t just skill — it’s how they work:
Async development across time zones
24/7 builder energy, not bound by office hours
Constant iteration based on real-time community feedback
A mindset of “launch fast, improve faster”
There’s no hierarchy, no bureaucracy — just builders shipping with purpose.
A Borderless Builder Culture
While the team may not yet span every continent, SonicxSwapis being built with a borderless mindset. Collaboration happens without walls, without fixed schedules, and without limits.
Whether it’s backend development, product growth, or community management — everyone contributes toward one shared vision: a truly open and decentralized financial system.
This setup helps SonicxSwapmove quickly and adapt to user needs, even in the most volatile market conditions.
Security-Driven Development
Security isn’t an afterthought — it’s embedded in how SonicxSwapis built.
All code is tested rigorously before deployment
The team has engaged third-party audits and plans ongoing security reviews
An internal QA process ensures that every new feature is community-ready
Community feedback and bug reports are encouraged and often rewarded
Security is seen not as a checkbox but as a continuous commitment.
Building in Public: A Community-Centric Approach
One of the core strengths of SonicXSwap’s builders is their proximity to the community.
Every update is shaped by user feedback
Telegram and Discord serve as idea hubs, not just announcement boards
Builders regularly join community chats, AMAs, and test groups
Features like Sonicx.fun were inspired directly by grassroots meme coin creators
The builders don’t just ship — they listen, learn, and adapt.
What’s Next in the Builder Pipeline?
Without leaking too much alpha, here are a few things currently under construction:
SonicxSwapV3 with improved UX
A more intuitive on-chain governance model
Early prototypes of Telegram-integrated trading tools
A potential builder onboarding portal for community devs
Upcoming tools to support external project launches on SonicX.fun
The team believes in layered innovation — building infrastructure today for the products of tomorrow.
Final Words: Builders Are the Backbone
Every swap, stake, launch, or meme coin on SonicxSwapis backed by the silent hustle of a team that believes in a better, decentralized future.
Their mission isn’t hype. It’s to build real utility, driven by real community needs, on a blockchain designed for speed and freedom.
Next time you interact with SonicXSwap, remember — you’re not just using a protocol. You’re engaging with a culture built by real people with real passion.
Connect With the Builders
Website: https://www.sonicxswap.com
Documentation: docs.sonicxswap.com
Telegram: https://t.me/sonicxswap
Twitter (X): https://x.com/SonicxDex
1 note
·
View note
Text
iMessage got reverse engineered
This is me texting my dad over imessage using an open source demo/proof of concept program that can send and recieve basic texts using the imessage protocol.
Disclaimer: this program stores all your encryption data in a VERY EASILY ACCESSIBLE PLAIN TEXT FILE, please don't share that file with anyone, and if you test it out, delete the file as soon as you're done with it. this is nothing more than a test application and not meant to be a full imessage replacement
it's not got good security, however the messages you send, appear to be private, they encrypt the data beforehand and send it directly to apple's servers (in madrid i guess), nothing in between or anything third party.
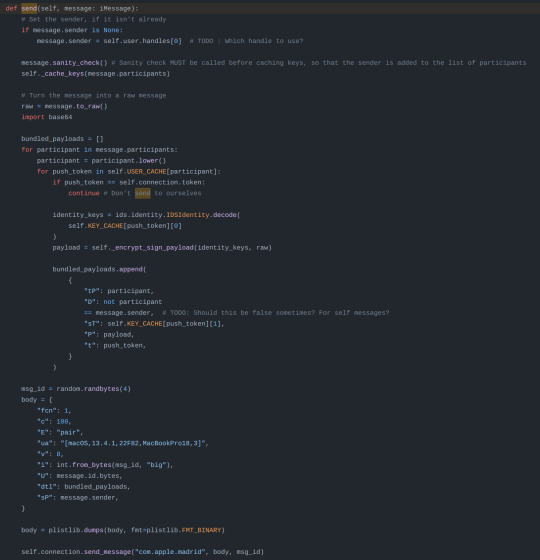
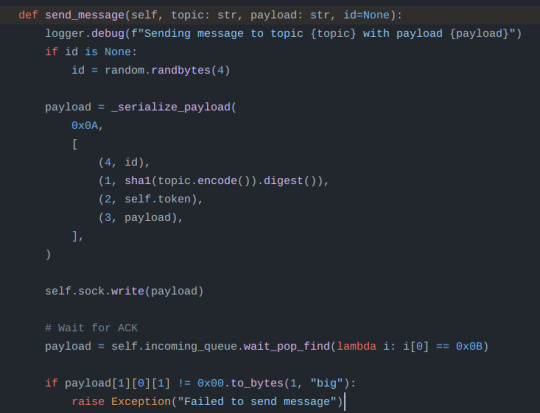
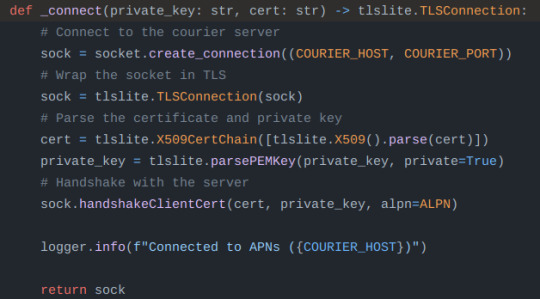
Sorry for no alt text, the screenshots are "send" function in imessage.py and the "send_message" and "_connect" function inside of apns.py, both are in the github link i sent earlier in the post ("socket" is a built in python package)
(dont trust a random tumblr user who barely knows how to code to tell you that this is safe, i dont know what im doing, this is just what i think was the relevant functions used in the program to send messages, and i could find no evidence of it stealing any data or sending it to third parties)
This was apparently bought and turned into "Beeper Mini", which. just takes this and makes it into an app that's 2$ a month to use, though (apparently) more secure, more features and you don't have to have it running all the time to get messages.
Beeper Mini is not open source so i have no idea if it's actually doing this or if it's actually private/secure. I would wait for it to be externally audited before using it, i'll add a reblog to this post if it ever does, or if any other programs use this method which have been audited to be as/more secure than the regular imessage app
And no, all of the news outlets reporting on this, beeper mini did not reverse engineer imessage, it's a frontend for someone elses work, which the developer was compensated for and they approve of it! it's not bad, i just dont like how it's being reported on, Beeper themselves even credit the dev:

woo
14 notes
·
View notes
Text
#PrivacyPlease: The Hidden Dangers of Oversharing on Indian Social Media
Picture this: You're scrolling through your favorite social media app, double-tapping pictures of your friend's Goa vacation, when suddenly you see an ad for the exact sunglasses they're wearing. Coincidence? Think again! Welcome to the murky world of social media privacy breaches in India, where your likes, shares, and comments could be painting a detailed picture of your life – and not just for your friends to see.
Why I'm Raising the Red Flag
As a digital innovation enthusiast, I'm both amazed and alarmed by India's social media revolution. It's connecting millions and driving social change, but it's also creating a treasure trove of personal data that's catching the eye of not just advertisers, but also cybercriminals. It's like hosting a giant party where everyone's invited – including some guests you definitely didn't put on the list!
The Social Media Tsunami
India's love affair with social media is reaching epic proportions:
India has over 467 million social media users as of 2022 (Statista, 2023).
Indians spend an average of 2.36 hours per day on social media (GlobalWebIndex, 2022).
That's a lot of data being shared, liked, and potentially exposed!
The Sneaky Ways Your Posts Betray You
How is your innocent scrolling and posting leaving you vulnerable? Let's peek behind the curtain:
Data Mining Bonanza: Your interests, habits, and relationships are being mapped and sold.
Location Leaks: That check-in at the new café? It's telling more than just your taste in coffee.
Facial Recognition Fiasco: Your tagged photos could be training AI without your knowledge.
Clickbait Catastrophes: That irresistible quiz might be harvesting your personal info.
Who's Paying the Price?
When social media privacy goes out the window, the consequences can be far-reaching:
Individuals: Your digital footprint could affect job prospects, relationships, and personal security.
Businesses: Employee oversharing could lead to corporate data leaks.
Society: Targeted misinformation campaigns can exploit data to manipulate public opinion.
The Regulatory Tug-of-War
India's lawmakers are trying to catch up, but it's like trying to lasso a speeding bullet train:
The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, aim to regulate social media platforms, but privacy protection remains a challenge.
The Personal Data Protection Bill was passed in 2019.
It's a bit like trying to use a landline to manage a smartphone – the technology is evolving faster than the rules!
Reclaiming Your Digital Privacy
Don't worry, you don't need to become a social media hermit! Here's how to stay connected while protecting your privacy:
Audit your privacy settings – make sure you're not accidentally oversharing.
Think before you post – does the world really need to know you're on vacation right now?
Be wary of third-party apps – that fun game might be a data-harvesting tool in disguise.
Use strong, unique passwords for each platform – no, your pet's name isn't a strong password.
Enable two-factor authentication – it's like adding a second lock to your digital front door.
The Bottom Line
As India continues its social media love affair, we need to make sure we're not giving away the keys to our digital lives. Stay savvy, stay informed, and remember – in the world of social media, what happens online doesn't always stay online.
So, the next time you're about to post that perfectly filtered selfie, take a moment to think about who might be peeking over your digital shoulder!
Stay safe, stay smart, and maybe think twice before accepting that friend request from a long-lost relative you've never heard of!
2 notes
·
View notes
Text
Security Analysis of BitPower

Introduction With the rapid development of blockchain technology and cryptocurrency, decentralized finance (DeFi) platforms have attracted increasing attention. As an innovative DeFi platform, BitPower uses blockchain and smart contract technology to provide users with safe and efficient financial services. This article will explore the security of the BitPower platform in detail, covering three key areas: cryptocurrency, blockchain, and smart contracts, and explain its multiple security measures at the technical and operational levels.
Security of cryptocurrency Cryptography Cryptography uses cryptographic principles to ensure the security and privacy of transactions. BitPower supports a variety of mainstream cryptocurrencies, including Bitcoin and Ethereum, which use advanced encryption algorithms such as SHA-256 and Ethash. These algorithms ensure the encryption and verification of transaction data and improve the system's anti-attack capabilities.
Decentralized characteristics The decentralized nature of cryptocurrency makes it independent of any central agency or government, reducing the risk of being controlled or attacked by a single entity. All transaction records are stored on a distributed ledger to ensure data integrity and transparency.
Immutability Once a cryptocurrency transaction record is recorded on the blockchain, it cannot be tampered with or deleted. Any attempt to change transaction records will be detected and rejected by the entire network nodes, thus ensuring the authenticity and reliability of the data.
Security of blockchain Distributed storage Blockchain is a distributed ledger technology whose data is stored on multiple nodes around the world without a single point of failure. This distributed storage method improves the security of data, and the data is still safe and available even if some nodes are attacked or damaged.
Consensus mechanism Blockchain verifies the validity of transactions through consensus mechanisms such as proof of work PoW and proof of stake PoS. These mechanisms ensure that only legitimate transactions can be recorded on the chain, preventing double payments and fraud.
Immutability Once the data on the blockchain is written, it cannot be changed, and any attempt to tamper with the data will be discovered and rejected. This immutability ensures the reliability and integrity of transaction records, providing users with a transparent and trusted trading environment.
Security of smart contracts Automated execution Smart contracts are self-executing contracts running on blockchains, whose terms and conditions are written in code and automatically executed. The automated execution of smart contracts eliminates the risk of human intervention, all operations are transparent and visible, and users can view the execution of contracts at any time.
Transparency and openness BitPower's smart contract code is public, and anyone can review the logic and rules of the contract to ensure its fairness and transparency. The openness of the code increases the credibility of the contract, and users can use it with confidence.
Security Audit In order to ensure the security of smart contracts, BitPower will conduct strict security audits on the contract code. Audits are conducted by third-party security companies to discover and fix potential vulnerabilities and ensure the security and reliability of the contract. This audit mechanism improves the overall security of the platform and prevents hacker attacks and exploitation of code vulnerabilities.
Decentralization BitPower's platform is completely decentralized and has no central control agency. All transactions and operations are automatically executed through smart contracts, eliminating the risk of single point failures and human manipulation. Users do not need to trust any third party, only the code of the smart contract and the security of the blockchain network.
Other security measures of the BitPower platform Multi-signature BitPower uses multi-signature technology to ensure that only authorized users can perform fund operations. Multi-signature requires multiple independent signatories to jointly sign transactions to prevent single accounts from being hacked. This mechanism increases the security of the account and ensures that funds can only be transferred after multiple authorizations.
Cold wallet storage To prevent online wallets from being attacked, BitPower stores most of its users' assets in offline cold wallets. Cold wallets are not connected to the internet, so they are not vulnerable to hacker attacks, which improves the security of funds. Only a small amount of funds are stored in hot wallets for daily transactions and operational needs.
Two-step verification The BitPower platform implements a two-step verification (2FA) mechanism, which requires users to perform two-step verification when performing important operations (such as withdrawals). 2FA requires users to provide two different authentication information, such as passwords and dynamic verification codes, which improves the security of accounts and prevents unauthorized access.
Regular security updates BitPower regularly performs security updates for systems and software to ensure that the platform is always up to date with the latest security status. Security updates include patching known vulnerabilities, improving system performance, and enhancing security protection. Regular updates reduce security risks and prevent the exploitation of known attack vectors.
Conclusion The BitPower platform has built a highly secure DeFi environment through cryptocurrency, blockchain, and smart contract technology. Its decentralized, transparent, and tamper-proof characteristics, coupled with security measures such as multi-signatures, cold wallet storage, and two-step verification, ensure the security of user assets and data. When choosing a DeFi platform, security is a crucial consideration. BitPower has become a trustworthy choice with its excellent security performance.
By continuously improving and strengthening security measures, BitPower is committed to providing users with a safe, reliable and efficient financial service platform. Whether ordinary users or institutional investors, they can invest and trade with confidence on the BitPower platform and enjoy the innovation and convenience brought by blockchain technology.
2 notes
·
View notes
Text


Since the 1960s, universities have always been hotbeds of left-wing protests, sometimes violently so.
But the post-October 7 campus eruptions marked a watershed difference.
Masked left-wing protestors were unashamedly and virulently anti-Semitic. Students on elite campuses especially showed contempt for both middle-class police officers tasked with preventing their violence and vandalism and the maintenance workers who had to clean up their garbage.
Mobs took over buildings, assaulted Jewish students, called for the destruction of Israel, and defaced American monuments and commentaries.
When pressed by journalists to explain their protests, most students knew nothing of the politics or geography of Palestine, for which they were protesting.
The public concluded that the more elite the campus, the more ignorant, arrogant, and hateful the students seemed.
The Biden administration destroyed the southern border. Ten million illegal aliens swarmed into the U.S. without audit. Almost daily, news accounts detail violent acts committed by illegal aliens or their surreal demands for more free lodging and support.
Simultaneously, thousands of Middle Eastern students, invited by universities on student visas, block traffic, occupy bridges, disrupt graduations, and generally show contempt for the laws of their American hosts.
The net result is that Americans are reappraising their entire attitude toward immigration. Expect the border to be closed soon and immigration to become mostly meritocratic, smaller, and legal, with zero tolerance for immigrants and resident visitors who break the laws of their hosts.
Americans are also reappraising their attitudes toward time-honored bureaucracies, the courts, and government agencies.
The public still cannot digest the truth that the once respected FBI partnered with social media to suppress news stories, to surveil parents at school board meetings, and to conduct performance art swat raids on the homes of supposed political opponents.
After the attempts of the Department of Justice to go easy on the miscreant Hunter Biden but to hound ex-president Donald Trump for supposedly removing files illegally in the same fashion as current President Biden, the public lost confidence not just in Attorney General Merrick Garland but in American jurisprudence itself.
The shenanigans of prosecutors like Fani Willis, Letitia James, and Alvin Bragg, along with overtly biased judges like Juan Merchant and Arthur Engoron, only reinforced the reality that the American legal system has descended into third-world-like tit-for-tat vendettas.
The same politicization has nearly discredited the Pentagon. Its investigations of “white” rage and white supremacy found no such organized cabals in the ranks. But these unicorn hunts likely helped cause a 45,000-recruitment shortfall among precisely the demographic that died at twice their numbers in the general population in Iraq and Afghanistan.
Add in the humiliating flight from Kabul, the abandonment of $50 billion in weapons to the Taliban terrorists, the recent embarrassment of the failed Gaza pier, and the litany of political invective from retired generals and admirals. The result is that the armed forces have an enormous task to restore public faith. They will have to return to meritocracy and emphasize battle efficacy, enforce the uniform code of military justice, and start either winning wars or avoiding those that cannot be won.
Finally, we are witnessing a radical inversion in our two political parties. The old populist Democratic Party that championed lunch-bucket workers has turned into a shrill union of the very rich and subsidized poor. Its support of open borders, illegal immigration, the war on fossil fuels, transgenderism, critical legal and race theories, and the woke agenda are causing the party to lose support.
The Republican Party is likewise rebranding itself from a once-stereotyped brand of aristocratic and corporate grandees to one anchored in the middle class.
Even more radically, the new populist Republicans are beginning to appeal to voters on shared class and cultural concerns rather than on racial and tribal interests.
The results of all these revolutions will shake up the U.S. for decades to come.
Soon we may see a Georgia Tech or Purdue degree as far better proof of an educated and civic-minded citizen than a Harvard or Stanford brand.
We will likely jettison the failed salad bowl approach to immigration and return to the melting pot as immigration becomes exclusively legal, meritocratic, and manageable.
To avoid further loss of public confidence, institutions like the FBI, the CIA, the Pentagon, and the DOJ will have to re-earn rather than just assume the public’s confidence.
And we may soon accept the reality that Democrats reflect the values of Silicon Valley plutocrats, university presidents, and blue-city mayors, while Republicans become the home of an ecumenical black, Hispanic, Asian, and white middle class.
2 notes
·
View notes
Text
Viktor Orban’s new ‘sovereignty protection law’ is more an empty provocation than a real danger for democracy. The PM is acting out a charade similar to earlier ones, in which everyone eagerly plays their role, including the media and NGOs.
The new “sovereignty protection bill” submitted to parliament by the national-conservative Fidesz party of Prime Minister Viktor Orban is the hot topic right now in Hungary, and it inevitably also made its way into the international media.
Most press coverage highlighted criticism from multiple NGOs (some of them funded by the government’s bete noire, George Soros's Open Society Foundations) who accuse the government of trying to silence critical voices with the bill, which will certainly be adopted soon, as Fidesz enjoys a two-thirds majority in parliament. Leading Hungarian media outlets fear they will be harassed by the new Sovereignty Protection Office because they “do not glorify Viktor Orban”.
However, with their immediate and hysterical reactions, the media, opposition and NGOs are playing the role that was intended for them by the government. Namely, Orban is clearly aiming for provocation with the bill, which is not actually as harsh as has been depicted in the press and elsewhere.
The bill did not come out of the blue
The only relevant element of the package is targeted at preventing parties from receiving money from abroad during election campaigns. It is already prohibited for parties to accept money from foreign states or organisations abroad as well as from anonymous donors. Now this prohibition will be extended to civil society organisations and independent candidates – and not without grounds.
It emerged after the 2022 general election that the civil society organisation of the united opposition’s prime ministerial candidate Peter Marki-Zay, called Everyone’s Hungary Movement, received almost 2 billion forints (about 5 million euros at the time) from a US organisation called Action for Democracy. Marki-Zay was backed by six opposition parties, including the green LMP, the leader of which recently suggested that the funding was related to the US ‘deep state’ or intelligence services.
The sovereignty protection law aims at preventing such a scenario from occurring again by amending the Criminal Code and the Act on the Election Procedure. A new criminal offense called “illegal influence on the will of voters” will be introduced: if found to have used foreign funding, candidates or responsible persons of the affected organisations could be sentenced to up to three years in prison. When candidates and nominating organisations register themselves at the Election Commission before elections, they will now have to make a declaration not to receive any funding from abroad. If an audit by the State Audit Office reveals the opposite, they will be fined twice the amount of campaign funding that they received.
Beyond these specific provisions, a new authority is to be established with more general competences. The new Sovereignty Protection Office will prepare reports and recommendations regarding the protection of Hungary’s sovereignty. Further, it can conduct inquiries into specific cases to reveal foreign disinformation and foreign influence on democratic decision-making. Mapping organisations that might influence voters’ intentions or the outcome of elections by using funding from abroad is also among the tasks of the office. However, regardless of what such inquiries will find, they will not have any direct legal consequences; the findings will merely be published.
Who will be jailed and who will be bullied?
It is a legitimate aim to prevent Hungarian politics from being tainted by foreign money, even if the campaigning environment in Hungary has been unfair for many years thanks to some tricky and discriminative legislative changes. However, it is questionable whether the new proposed legislation could successfully prevent a scenario similar to that in 2022.
Namely, it is only nominating organisations that are prohibited from accepting foreign money, but Everyone’s Hungary Movement itself was not a nominating organisation at the election. Its candidates were formally candidates of the six parties in the opposition coalition. The reason for that is associations in which form civil society organisations operate can only run in local elections. At European and general parliamentary elections, nominating organisations can only be registered political parties.
The new offense in the Criminal Code also applies to cases where the foreign money is taken indirectly, through proxies, but it is hard to imagine that every single donation to every party could be investigated in this regard. Moreover, criminal responsibility can only be established if the accused person knew about the source of the money: this is more likely to be proven in the case of party leaders than individual candidates.
As far as the Sovereignty Protection Office is concerned, its entire activity is little more than public bullying. The new authority will not be able to levy any sanctions, it will simply publish reports.
Of course, the public bullying of critics is not nice, but it should not be overestimated either. Oppositional parties, journalists and NGOs have long been subjected to smear campaigns by the propagandistic Fidesz media: their response threshold should be quite high by now. If targets still feel offended, they can launch a lawsuit over the violation of their personality rights: such lawsuits have been won by opposition politicians many times against pro-government media outlets.
Playing an old game, time and again
So, it would appear that the government’s sudden urge to protect sovereignty is aimed rather at provoking its enemies. And it would not be the first time. This follows a familiar path: find an enemy (immigrants, LGBT activists, George Soros, ‘foreign agents’), announce some measures against them which sound outrageous but actually have little or no real consequences, wait for the outcry from the liberal bubble and in ‘Brussels’, from where you might also provoke an infringement procedure. Even better! Finally, sit back and tell your voters: “Look, that is what I warned you about, they are betraying the country, intervening in our business, neglecting Hungarian popular will” and so on…
The same formula was used ahead of the general election in 2022. The government annoyed Brussels and liberal public opinion with its so-called “child protection law”, which was ostensibly aimed at preventing children from being exposed to content on homosexuality or transgender issues, either in the media or in school. And ahead of the election in 2018, it adopted a similar law to the current bill, requiring NGOs receiving more than 7.2 million forints (about 22,000 euros) to register themselves as “organisations funded from abroad”. Several NGOs announced a boycott of the law, though they were not fined or even warned or approached by the authorities, as one of the affected NGOs, Hungarian Civil Liberties Union, confirmed to me in early 2022.
Both laws were subject to infringement procedures before the Court of Justice of the European Union: until now, only the latter case concerning NGOs was closed with a judgment, which not surprisingly was condemnatory.
It is likely this sovereignty protection bill will provoke an infringement procedure as well. As the Act on the Election Procedure also applies to elections for the European Parliament, the amendment implies that parties will not be allowed to accept support from their European political groupings during the campaign. European political parties, or party families as they are often referred to, bring together national parties of similar values and ideology at the European level. Supporting their member parties in European election campaigns is common practice, and is expressly allowed by the relevant EU regulation. (It is worth noting that according to this regulation, European political parties are prohibited from accepting anonymous donations and donations from countries outside the EU.)
What makes the situation even more difficult is that, for the first time, local and European elections will be held on the same day in June 2024. So, the campaigns will be simultaneous, and the parallel timing should have a great mobilisation potential, especially considering a peculiar interface between local and EU politics in Hungary: there is a huge amount of EU money that is being withheld by the European Commission due to rule-of-law concerns. According to a Commission announcement last week, only a small part of the 6 billion euros in pandemic recovery funds will be released. The lack of EU money is particularly apparent at the local level because municipalities finance most of their development projects from EU funding.
The opposition will obviously blame the government for that, while the government will blame ‘the Brussels imperium’. One of the biggest favours Brussels can do for the Hungarian government right now is to act ‘imperial’ and do something which can be used as verification of the government’s sovereignty concerns: an infringement procedure because of the new law; more financial support for independent media; even the usual expressions of “deep concern” will suffice.
4 notes
·
View notes
Text
How to Build a Safe and Secure Digital Wallet

In today’s digital era, convenience and efficiency are driving the shift towards cashless transactions, and digital wallets have become an essential part of our daily lives. As these digital wallets store sensitive financial information, it is crucial to prioritize security and safety during their development. In this blog, we will explore the key elements necessary to build a safe and secure digital wallet, ensuring users’ confidence and trust in your platform.
Strong Authentication Mechanisms: A robust authentication system is the foundation of a secure digital wallet. Implement multi-factor authentication (MFA) to require users to provide multiple forms of identification before accessing their accounts. MFA may include a combination of passwords, biometric data (fingerprint, facial recognition), and one-time passwords (OTP) sent to registered mobile numbers or email addresses. This layered approach significantly reduces the chances of unauthorized access.
Encryption and Data Protection: Protecting sensitive user data is paramount in a digital wallet’s security. Utilize strong encryption algorithms to secure data both at rest and during transmission. Adopt industry-standard encryption protocols like SSL/TLS to safeguard communication between the app and backend servers. Additionally, never store plain-text passwords or sensitive information in the database; instead, use strong hashing techniques.
Regular Security Audits and Penetration Testing: Frequent security audits and penetration testing are essential to identify vulnerabilities and weaknesses in your digital wallet’s infrastructure. Engage with qualified security professionals to conduct thorough assessments and address any discovered issues promptly. Regular testing ensures your platform remains resilient against emerging threats and hacker attempts.
Secure Development Practices: Adopt secure development practices from the outset to build a strong security foundation. Train your development team on secure coding practices, ensuring they follow the latest OWASP guidelines. Implement code reviews and conduct regular security awareness training to ensure everyone involved understands the importance of security in the development lifecycle.
End-to-End Encryption for Transactions: Ensure that all transactions, whether online or in-store, are encrypted end-to-end. This encryption prevents unauthorized parties from intercepting and manipulating sensitive transaction data, such as credit card details or personal identification numbers.
Regular Software Updates: Stay vigilant in updating your digital wallet application and backend servers with the latest security patches and software updates. Outdated software can expose your platform to known vulnerabilities, making it an easy target for cyberattacks. Enabling automatic updates can streamline this process and keep your app’s security up to date.
Secure Storage of Payment Information: When storing payment information, follow Payment Card Industry Data Security Standard (PCI DSS) compliance guidelines. If possible, avoid storing cardholder data and instead utilize tokenization or outsourcing payment processing to certified third-party providers. This approach minimizes the risks associated with storing sensitive financial information.
User Education and Awareness: Promote user education and awareness about digital wallet security best practices. Educate users about the risks associated with phishing attacks, using unsecured Wi-Fi networks, and sharing sensitive information with unknown sources. Regularly communicate security updates and tips to ensure users can safeguard their accounts effectively.
Building a safe and secure digital wallet is a critical responsibility for any fintech company. By adopting strong authentication mechanisms, encryption, and secure development practices, you can create a robust platform that users can trust. Regular audits, updates, and user education play pivotal roles in keeping the digital wallet ahead of emerging threats.
Remember, security is an ongoing process, and a proactive approach is essential to maintaining a trusted and reliable digital wallet in an ever-evolving digital landscape.
1 note
·
View note
Photo
Listen. listen. I was working in affordable housing right before the crash in 2008 and we saw it coming. but we were city employees, working on the scale of a single city, so we saw something big coming but we didn't know what it was.
The kind of housing I worked in was called "inclusionary development". Developers would be given permission to build luxury condo developments on the condition that some number of units (usually between 10 and 20%) had what's called a deed rider on them. The deed rider contained a bunch of legal requirements that amounted to ensuring that only people who could barely afford one of these units were qualified to buy them. This was supposed to be a "hand up, not a handout" (I hate that phrase so much), but it created a basically permanent class of house-poor people who were nearly broke all the time, but they had achieved the dream of owning a home. In the libertarian utopia of the mid-aughts, these people had been "removed from the cycle of poverty" or some such shit but in fact, they'd just been placed permanently in the jaws of the crocodile, and one thing destabilizing their financial situation would result in foreclosure and homelessness.
When people talk about "subprime mortgages" or "subprime lending", that's code (in part) for situations like this. People who couldn't qualify for "normal" loans went through an intrusive process where they were verified to have very little in the way of cash or investments and to make juuuuuust enough money to be able to pay a really awful mortgage as long as nothing went wrong. As a prize for putting up with third parties being all up in your money business, you were offered the chance to sign up for a pile of loans at 0% down with absolutely punishing interest rates such that you could realistically never expect to get ahead on your payments. The idea was the the property would itself somehow magically make you solvent while bleeding you dry for the enrichment of the banks and the white men who profit from them. Of course, the game was rigged so that the property couldn't help you, the owner, unless you cheated- got help paying off your loans, rented it out to earn more income the way rich people are expected to, hid money on the audit, or lied. If you did those things and got caught, you could lose your home and the white men at the top still profited. Libertarianism at its purest.
Even so, we saw about two foreclosures a year for roughly 2002-2006. and then, in the first half of 2007, we saw two per month. My manager and I were alarmed, and she asked me to call all the people who'd been foreclosed on in the last year and ask if they'd be willing to share what happened. I emphasized when I called that there was absolutely no legal requirement for them to share, but that my manager and I were hoping there would be some kind of common thread that we could try to do something about about.
Some of these people I had talked to personally in my compliance role, even multiple times. All of them knew who my agency was and that we were tasked with making sure they were acting in accordance with the legal requirements they'd signed at more or less financial gunpoint. What I am saying is that all of these people had a complicated relationship with me and the agency I worked for.
They all shared, and for every single one of them, the reason was medical bills. Most of them had had something awful happen personally (car crash, cancer), a couple had sick or injured family members. But for all of them it was the other half the grift, the for-profit medical system, which was making them unable to fulfill their legal agreement to be milked dry by the mortgage portion of the grift.
This last episode of Leverage fucks me up because this is so, so, so important.








“This is a big ass speech. This is a big ass stop the show, this is the moral framework of the entire five years you’ve seen. Nate Ford justifies 77 episodes of Leverage in this speech, cause you know what? It is the last goddamn episode, you’re gonna know why we made the show. We didn’t make the show cause we thought it was clever or cute or fun. I always say this, no show succeeds unless somebody loves it and you know what, everybody loves this show and to me, what Nate’s saying here is important enough to say out loud. No one should be allowed to cheat and get away with it.” - John Rogers, The Long Goodbye Job DVD Commentary
#leverage#subprime mortgage crisis#leverage dvd commentary#yes this#exactly a thousand percent this#listen#capitalism and property ownership are fucked#the white men who profit from these systems of oppression are doing on purpose with malice aforethought#renting is also oppressive but don't let that hide the oppression of home ownership from you
15K notes
·
View notes
Text
Residential Proxies for Tax Research

Tax professionals, academic researchers, and compliance officers face increasing challenges accessing comprehensive tax information across jurisdictions. International tax codes, regional regulations, and cross-border compliance requirements demand thorough research capabilities. Residential proxies enable legitimate access to tax databases, government resources, and regulatory information essential for professional tax research and compliance.
Accessing International Tax Resources
Government tax websites often restrict access based on geographic location, limiting international tax research capabilities. Professionals advising clients with global operations need access to authentic tax information from multiple jurisdictions. Residential proxies provide legitimate access to official tax authority websites, enabling comprehensive research across borders.
Tax treaty information, withholding rate databases, and regulatory updates frequently appear only on local government sites. Researching double taxation agreements between countries requires accessing both nations’ tax authority resources. Residential proxies ensure researchers can view official documentation as local practitioners would, avoiding incomplete or outdated third-party summaries.
Regional tax incentives and special economic zone regulations change frequently. Manufacturing companies evaluating international expansion need current information about local tax benefits. Residential proxies enable real-time access to regional development authority websites and local tax incentive programs.
Academic and Professional Research
Tax law professors and researchers require access to international case law databases and regulatory archives. Many countries maintain separate databases for local practitioners, limiting international academic access. Residential proxies facilitate comparative tax law research, enabling scholars to analyze global tax policy evolution.
Professional services firms conducting tax benchmarking studies need accurate rate comparisons across jurisdictions. Corporate tax rates, VAT structures, and withholding tax treaties vary significantly. Residential proxies enable systematic data collection from official sources, ensuring accuracy for client advisories.
Transfer pricing documentation requirements differ dramatically between countries. Multinational corporations must understand local documentation standards and penalty regimes. Access to local tax authority guidance through residential proxies ensures compliance teams have current, accurate information.
Compliance Monitoring and Updates
Tax regulations change constantly, with different effective dates across jurisdictions. Residential proxies enable automated monitoring of tax authority websites for regulatory updates. This proactive approach prevents compliance failures due to missed regulatory changes.
E-filing system requirements and technical specifications often remain accessible only through local IPs. IT teams implementing global tax compliance systems need detailed technical documentation from each jurisdiction’s tax authority. Residential proxies provide the necessary access for system integration planning.
Best Practices for Tax Research
Maintain detailed documentation of all research activities, including dates, sources, and proxy locations used. This audit trail proves valuable during tax authority inquiries or academic peer review. Focus exclusively on publicly available information, respecting privacy regulations and authorized access requirements.
Structure proxy usage around specific research projects, assigning dedicated IPs for each jurisdiction studied. This organization improves research efficiency while maintaining clear separation between different clients’ research activities.
Enhancing Tax Research Capabilities
Professional tax researchers using residential proxies report significant improvements in research comprehensiveness and accuracy. Access to authentic, current tax information from official sources strengthens advisory capabilities and ensures compliance across international operations.
#TaxResearch#ResidentialProxies#TaxCompliance#InternationalTax#ProxyLust#TaxProfessionals#TaxTechnology
0 notes