#Windows 8.0
Explore tagged Tumblr posts
Text

Windows 7 Wallpaper on Windows 8.0 Flowers by ImSwordKing on DeviantArt
#art#blue#design#flowers#frutiger aero#graphic design#graphics#imswordking#logo#microsoft#nature#photography#queuetiger#tech#technology#vector#wallpaper#windows 8#windows 7
37 notes
·
View notes
Text

[💾] Qwerty has a bunch of computer games in their system, thanks to her handler Quincy, who was quite the gamer and game collector.
The games she has are, but are not limited to;
The standard games that come with Windows all the way up to Windows XP (Solitaire, Minesweeper, Hearts, etc)
All of the Dandy's World PC games (because yes there were games made of the show)
King's Quest 5, 6, 7, and 8. Along with the other Sierra point-and-click games made for Windows (except the Leisure Suit Larry games, see below why)
All the Humongous Entertainment games. Except for "Pep's Birthday Surprise", Life if Rough When You Loose Your Stuff", and "Backyard Skateboarding" (as those were released in 2003) and 2004 respectfully.)
All of the LucasArts adventure games (Maniac Mansion and it's sequel, the Monkey Island games up to "Escape from Monkey Island", Sam & Max: Hit the Road, etc. She does not have Grim Fandango however, see below why.)
The first The Sims game
Simcity 3000
Myst
Rollercoaster Tycoon
The deluxe version of "Where in The World is Carmen Sandiego?"
Logical Journey of The Zoombinis
The 8.0 version of "Mavis Beacon Teaches Typing"
The Living Books series
All versions of Oregon Trail up to the 5th Edition. As well as Yukon Trail, and Africa Trail.
The Cluefinders, Super Solvers, and Super Seekers games.
JumpStart Preschool, Kindergarten, 1st Grade, 2nd Grade, and all the JumpStart Adventures games. As well as JumpStart Typing.
She even used to have Doom and Wolfenstein! But that changed when Quincy was caught playing them on Qwerty. A rule was then set in place that the games Qwerty could have had to be family-friendly. The same went for the other computers in Gardenview.

#Information Cards | Headcanons#{ Headcanons | Qwerty 💾 }#(( Can you tell that I really love 90's and 2000's PC games? ))#(( And yeah a lot of them are point and clicks and/or edutainment games. Those were HUGE during the 90's ))
4 notes
·
View notes
Note
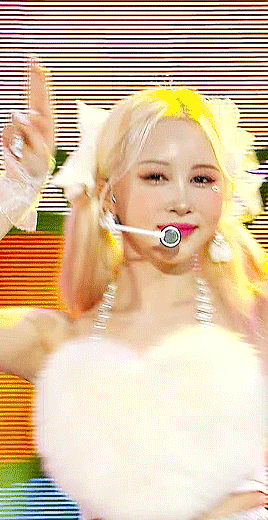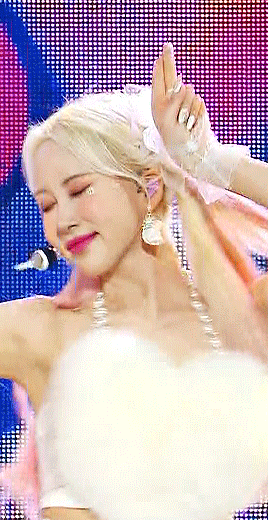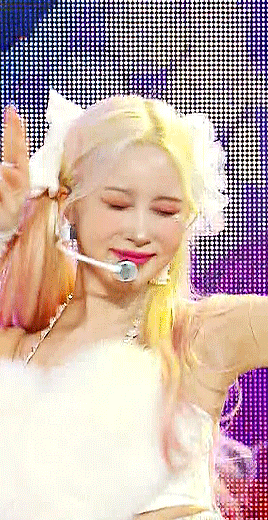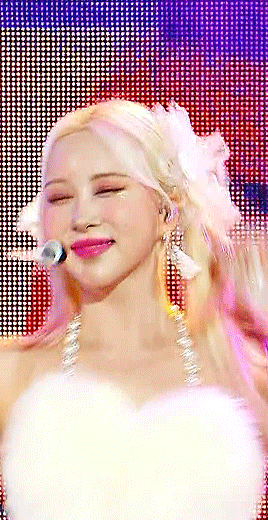
hi if its alright with you can I please ask your stage gif process 🩵 (I don't mind if its not too detailed but if you use vapoursynth or topaz or anything)
hiii! omg thank u for wanting to know 🥺🥺 i actually use two methods, depending on the source file (and how lazy i feel). either vapoursynth or mpv. i'll show u both!
long, the example gif has a flashy background, somewhat clear. i hope.
i source from .ts files on k24hr or twitter, fancams, and then the youtube version (which i then run through handbrake before vs or mpv) if there's absolutely no other choice. i try to avoid show music core because its backgrounds make sharpening hard, but i'm using one from there for this tutorial :) i will also use beyond live / blu-ray files when available (i.e. 4th world tour gifs i did of twice)
vapoursynth:
-> only use the deinterlace (60 slow) when it's 1080i 30fps! i use this on files from k24hrs. if the file is already 60 fps (i.e. those from srghkqud on twitter), i don't deinterlace or preprocess. i use finesharp on .7 any time i use vs!
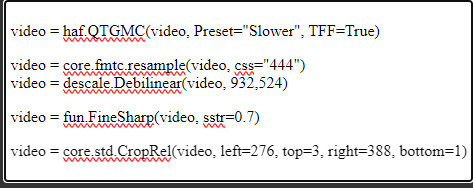
this gif is 268 x 520 px! i leave the delay at .02 and set frame rate to 60fps. on the left, it is just changed to 60fps and run through vs with the above settings. the gif on the right is sharpened!
i change my sharpening settings on every stage (and most other sets as well)! i use an action, and then adjust by the background and quality of the source! this is using my stage sharpening - but i have removed a smart sharpen and reduced opacity of other filters i use on different (clearer) files!
show music core has these really visible leds in their background, so sharpening it tends to be harder! i avoid using my 500px smart sharpens when it looks like this, and use high pass and bigger radius smaller amount smart sharpens!
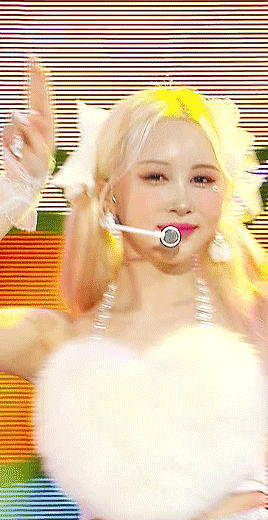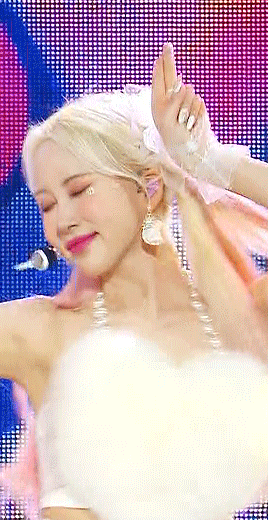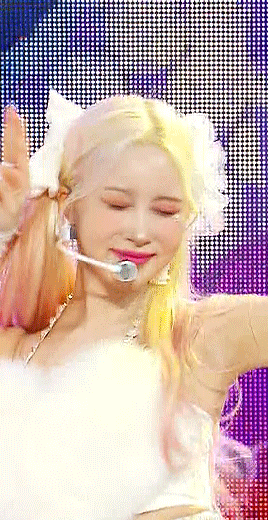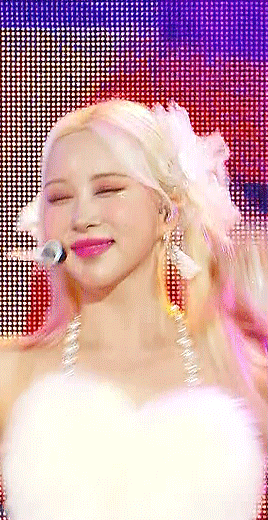
sharpening settings for above: 8.0 high pass on soft light blending (40% opacity), 241 .2 smart sharpen (60% opacity), 15 15 smart sharpen (50% opacity) i should also note that on really really pale stages, i use camera raw filter to fix whites / highlights before i add the other sharpening! this does really slow down export time and can be frustrating, so i reserve it for then!
then i color! sometimes i use ezgif (which hasn't lowered quality that i've noticed) to adjust the speed, if i feel it needs it! this gif has a fine speed so i've left it as is, but i normally speed up gifs by 120% on their speed feature to make the choreo look a little faster!


left: unsharpened except vs finesharp, colored right: sharpened, colored
my coloring focus is always restoring skin, everything else is pretty much purely stylistic. i try to leave colors in the background the same! i do really like making blonde hair pinker or more toned (since they're often yellow, i always make a point of essentially toning their hair for them - i.e. tsuki in dang! set)
when i color the rest of the set, i keep the first gif open next to it to make sure everything matches! i normally copy and paste the coloring group and adjust as needed :D
also, i check how it looks in tumblr on desktop + mobile, since web safe colors adjust the look of your gifs a lot (the ones with the little dots in the middle are web safe, everything else isn't) and try to fix what doesn't look quite right. i also ask my friends if something is wrong but i'm not sure what (mainly nini (@withyouth) so shout out to her for putting up w/ me, a big part of the stage gif process)!
mpv: -> i press 'd' and make sure it is deinterlacing (again, only 1080i ones get deinterlaced)! and then i screencap. i followed this guide on setting up mpv, and always use minimal compression settings for everything i screencap.
-> i turn my files into dicom files (you can just rename them on mac, on windows it is multistep) and then scipt->load multiple dicom files (faster than loading image into stack and, in my opinion, clearer too)!
for windows: -> alt+d in your screencap folder, cmd. enter. type ren *.* *.dcm into the window. enter. close the command window!
i make my frame animation + frames to layers. once it is on the timeline, i go ahead and crop before i do anything else. i tried to make the cropping like the vs gif, but it's not identical!
sharpening: since i didn't use finesharp, i can add more in ps. this is my normal stage sharpening with nothing added or removed!
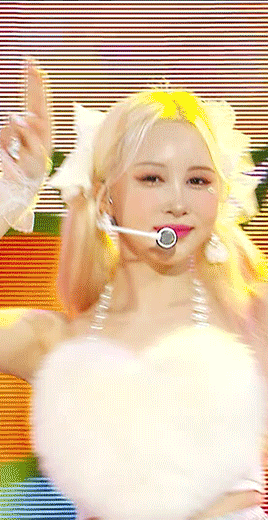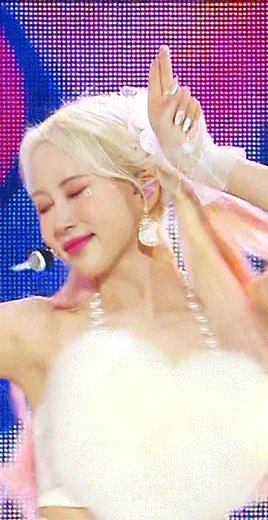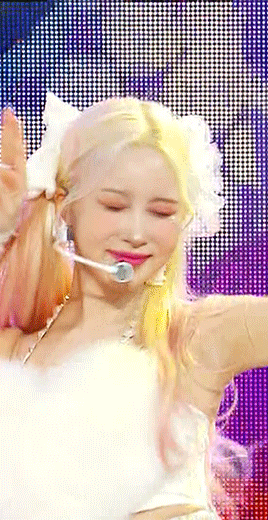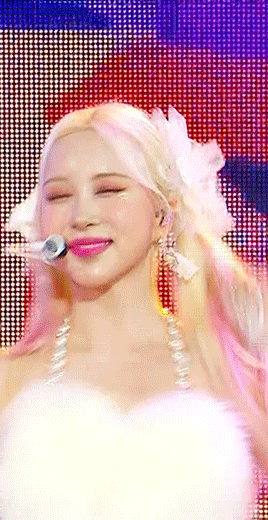

left: deinterlaced, screencapped, cropped right: deinterlaced, screencapped, cropped, sharpened -> 8.0 high pass (soft light, 65%), 500 .3 smart sharpen, 241 .2 smart sharpen (60% opacity), 15 15 smart sharpen (50% opacity)
coloring: same one as the vs gifs!


comparison:


left: vapoursynth, fully complete right: dicom, fully complete
i normally use mpv, but sometimes i don't feel like waiting on the screencaps, or i think finesharp will add texture + depth that the original doesn't have (too smooth of a filter, whatever) so i use vs! my taeyeon mr. mr. and le sserafim rock ver. sets were both done via vapoursynth, though the sharpenings are different from each other and what it shown here (i change sharpening a lot, and sometimes by set... sorry.. KJHDFGJKH)!
anyways i hope this was helpful!!! thank u for asking it means a lot u want to know!! if u want more stuff answered or shown, u can always ask :D and i hope it's clear 😭😭 i know i ramble a lot
#ask#anon#m:tutorial#niniblr#useroro#awekslook#userdoyeons#rosieblr#tuserflora#<- u all can ignore i just thought i should tag ppl KHDFKJGH#flashing tw#long post#resources
26 notes
·
View notes
Text
#1 thing I want from 8.0 is something for pld on a 2 minute cooldown so I don't have to try and guess which 1 minute windows are in buffs. Yes I'm stupid and can't count
3 notes
·
View notes
Text

George, Duke of York to Queen Victoria — 16 November — Anichkov Palace
"My dearest Grandmama
As Lord Carrington starts tonight direct for England, I will take this opportunity of sending you a few lines. I know that both Papa and Lord Carrington have continually written to you and kept you informed of what has been going on here, and so I did not write to you. I have written to May each day and we have been so busy that there is not much time for writing and several days I had barely time to finish my one letter, so I hope you will forgive me for not having written before.
It has indeed been a terribly sad time here; but the Wedding came like a gleam of sunshine in the midst of the deep mourning. Poor Aunt Minnie has indeed been brave and has borne her terrible grief in a wonderful way, Mama has been of the greatest possible help and comfort to her, I don’t know how she could have got on without her. Dear Alicky looked quite lovely at the Wedding, the Service was very fine and impressive and the singing quite beautiful, she went through it all with so much modesty but was so graceful and dignified at the same time, she certainly made a most excellent impression. I do think Nicky is a very lucky man to have got such a lovely and charming wife; and I must say I never saw two people more in love with each other or happier than they are. When they drove from the Winter Palace after the Wedding they got a tremendous reception and ovation from the large crowds in the streets, the cheering was most hearty and reminded me of England, an enormous crowd of several thousand people assembled in front of this Palace and cheered continuously from 3.0. till 8.0. The young couple showed themselves at the window several times.
Alicky got a great many lovely presents, I have never seen such jewellery, your charming locket was very much admired. Dear Nicky was most touched by your making him Col. in Chief of the Scots Greys, and it was the Regiment he admired more than any other, when he was at Aldershot this year, he is quite delighted about it. | know your giving him this Regiment has made a most excellent effect here.
The weather unfortunately has been bad, very cold with snow and rain alternately and no frost at all, | am disappointed as I wanted so much to see St Petersburg with snow and ice. I must say I have never been treated anywhere with so much kindness and civility as here from everyone I have met. This is the first time I have been to Russia, I certainly have got a most excellent impression of the people and the country. Uncle Alfred and Aunt Marie leave here tonight, the former for England and the latter for Coburg. Nicky has been kindness itself to me, he is the same dear boy he has always been to me, and talks to me quite openly on every subject. It is really quite touching to see the charming way he treats dear Aunt Minnie; and he does everything so quietly and nicely and naturally; everyone is struck by it, and he is very popular already. I am so glad that May, sisters and our Baby are with you at Windsor now, and that you are going to keep them with you till Papa and I arrive on the 6th.
I am so looking forward to seeing you and them all again. We leave next Sunday and shall spend one day with Aunt Vicky in Berlin. God bless you dearest Grandmama with love to all and hoping to see you very soon.
I remain ever your most devoted and dutiful grandson Georgie".
4 notes
·
View notes
Text
Motorola hacía clones de Mac

En 1996 Apple sublicenció el sistema operativo MacOS a Motorola en febrero, y en julio a IBM. ¿Pero sabáis que Motorola hizo sus clones de Mac? Te presento la extinta Star Max Pro 6000 (corria MacOS 7.5 al 8.0 y Windows NT for PowerPC beta) 📷: Steve Candland #retrocomputingmx #Motorola #starmax
2 notes
·
View notes
Text

Restored 1950s Tokyo City Bus
Location: Edo-Tokyo Open Air Architectural Museum, Koganei, Tokyo Timestamp: 13:12 on October 25, 2023
Pentax K-1 II + DFA 28-105mm F3.5-5.6 31 mm ISO 400 for 1/360 sec. at ƒ/8.0
Nestled within the Edo-Tokyo Open-Air Architectural Museum lies a fascinating piece of history—a meticulously restored vintage bus, the TS11 model, built by Isuzu Motors after the war from 1952. As you explore the museum, you'll come across this relic, which I feel is just one testament of many to Japan's post-war resilience and innovation.
The bus in my photo is actually part of a personal collection that is on loan to the Tokyo Metropolitan Government for use at the museum. This is why when you receive your printed English guide at the museum, there will be no reference or information available regarding the bus. Please read on to learn some interesting facts and history!
The TS11 model, with its 4WD capability, played a small but influential role in post-war Japan. Its sturdy design allowed it to navigate even the most challenging terrains, including mountainous and snowy regions. In 1957, a similar bus was entrusted with the honor to transport the Emperor and Empress to Mt. Fuji for a climb to the summit, a testament to the reliability and trustworthiness of the bus.
Fast forward to the present day, vintage buses, like the TS11, are experiencing a revival, thanks to the efforts of rural bus operators. Newspaper articles from The Asahi Shimbun and The Mainichi highlight labor shortage struggles faced by bus operators who have turned to restoring old buses as a way to promote not only ridership from tourists on weekends and national holidays, but also to attract bus enthusiasts (bus spotters, bus otaku, etc.) as possible new hires at their companies.
The charm of these buses transcends generations, captivating both the young and old in Japan and even tourists from overseas who have become familiar with the retro design of these old buses from novels, anime, and manga.
If you examine my photo closely, you'll notice a replica of an old license plate near the radiator grill. Above the front window, you can also see the bus route number “47” (四七) and the route destination “Ueno-Hirokoji” (上野広小路), which is a subway station on the Tokyo Metro Ginza Line, in Taito Ward, Tokyo.
Unlike modern buses designed for maximum passenger capacity, these vintage buses, with engines positioned in front of the driver, offer several advantages: better engine cooling efficiencies, easier access for maintenance and repairs, reduced vibration and noise for passengers, and increased safety for drivers in frontal collisions.
Preserving these vintage buses not only honors Japan's history but I think they can help enrich the present and the future, connecting young and old through shared memories and appreciation for cool design and innovative engineering.
Visit my blog post for Google Maps links and links to all of the original source material that I translated for this post: https://www.pix4japan.com/blog/20231025-edo-bldg-museum.
#都市景観#ボンネット型バス#江戸東京たてもの園#東京#pix4japan#pentax_dfa28105#pentaxk1mkii#urbanscape photography#Japan#Tokyo#bus#Edo-Tokyo Open Air Architectural Museum
18 notes
·
View notes
Text

I got a feeling tomorrow's gonna be an exciting day. (98 MSQ)
So, the MSQ has given me all the left-side gear, and I did all the sidequests for right-side. I think I'm missing a couple pieces, though, but there's no more sidequests. There's definitely no more sidequests, because I got all four aethercurrents from them. What's weird is... every zone has two "chain" sidequests, and when you do them both there's a capstone at the end that ties them together. I remember Azim Steppe had Mausi in Sadu's camp, and the soup guy in Magnai's, and in the end they became friends or whatever. But every zone has done this since at least Stormblood. Except Heritage Found—imagine my surprise when I went to the last quest, I always save it for last, and it didn't have a banner on the accept window, and it didn't chain. And, what's extra weird, you don't go back to the original questgiver to explain "Yeah, everything's all set, pay me now." It's one of those " . . . but perhaps they'll talk to you, since you're a stranger . . . " ones. So the narrative is squarely in the realm of, you have to go report back to finish. But... nothing. And since I have all the aethercurrents, I'm not expecting any more sidequests—that would be additionally weird.
So, we're nearly done with Heritage Found. Up next is... a Trial? We're not gonna showdown with Zoraal Ja already, are we? Or... something else? There's been a lot of voice-acted cutscenes today, and a lot of mind-blowing revelations in the past... hour. There's a lot of options for who the trial could be. Or there's the possibility that I was bamboozled, or misunderstood, and it is the dungeon next, then a 99 trial, then the final 100 dungeon and trial after the last, mysteriousest zone.
I'm no closer to knowing what the final zone is. Now that we've been inside Everkeep, and it turns out that that's just... the container for Solution Nine, that's why the map says "To Everkeep." Through the portal into the lightning-void-world is the best guess... and there's room for the story to go "Okay, let's get to the source of the problem." But there's also room for them not to do that, the last zone is, I don't know, uploaded into Endless soulville as free-floating data, and then in 8.0 we give Lightning World the Norvrandt treatment.
Dawntrail has been consistently astonishing. At first we were slammed with gorgeous visuals and exciting characters, and once that story was resolved, everything went berserk instantly and we got thrown into a whirlwind adventure in a high-fantasy sci-fi mindfuck wonderland. I'm already bad at speculating. I can't even hope to guess what's going to happen next now.
But it's late, and I'm tired.
6 notes
·
View notes
Text
the only thing I miss from windows 8 (well 8.1, 8.1 was actually decent, 8.0 was a trashfire lmao) are the tiles
Like you could customize your tiles in the start menu with pictures, they could even be animated if you wanted. You had SO MUCH CONTROL over how your start menu looked!
I had nifty art for all my games. The closest thing I get now is custom art in steam :(






I love doing this kind of stuff and it was so much fun to do in windows :(
3 notes
·
View notes
Text
Being subjected to setting up win11 (i need to shrink the partition inside windows to install mint) and god i fucking hate windows. Dogshit since 8.0.
6 notes
·
View notes
Link
[ad_1] .Microsoft on Tuesday released 67 patches affecting 12 product families. Ten of the addressed issues, five involving 365 and Office and one involving SharePoint, are considered by Microsoft to be of Critical severity, and 17 have a CVSS base score of 8.0 or higher. One, an Important-severity RCE in Windows related to WEBDAV (CVE-2025-33053), is known to be under active exploitation in the wild. An additional Important-severity SMB issue has been publicly disclosed, but is not currently known to be under exploit. At patch time, nine additional CVEs are more likely to be exploited in the next 30 days by the company’s estimation, not including the WEBDAV issue mentioned above. Various of this month’s issues are amenable to direct detection by Sophos protections, and we include information on those in a table below. This most certainly includes CVE-2025-33053, in which Sophos itself has taken a particular interest – and, apparently, vice versa. In addition to these patches, ten Adobe Reader fixes, four of them considered to be of Critical severity, are included in the release. Those are listed in Appendix D below. That appendix also contains information on two Edge-related vulnerabilities and a Critical-severity Power Automate issue that was addressed earlier this month, as well as limited information on a Critical-severity bug in Copilot for which an advisory was released the following day (Wednesday). The periodically released Servicing Stack updates are also available. We are as always including at the end of this post additional appendices listing all Microsoft’s patches sorted by severity, by predicted exploitability timeline and CVSS Base score, and by product family; an appendix covering the advisory-style updates; and a breakout of the patches affecting the various Windows Server platforms still in support. By the numbers Total CVEs: 67 Publicly disclosed: 1 Exploit detected: 1 Severity Critical: 10 Important: 57 Impact Remote Code Execution: 26 Information Disclosure: 17 Elevation of Privilege: 13 Denial of Service: 6 Security Feature Bypass: 3 Spoofing: 2 CVSS base score 9.0 or greater: 0* CVSS base score 8.0 or later: 18 * One issue, affecting Power Automate for Desktop but patched by Microsoft on June 5, has been assigned a 9.8 CVSS base score. Since it was mitigated prior to release, we are treating that information as advisory-only and do not include it in this month’s statistics. Likewise, the Copilot advisory released on June 11 has a CVSS base score of 9.3, but does not figure into these tallies or charts. Figure 1: A proportionally heavier-than-usual ten Critical-severity patches were released in June, though unusually six of those occur in 365, Office, or SharePoint rather than the more customary Windows. (Two Edge updates covered this month are not released with full impact information and thus do not appear in this chart; we are also excluding the Power Automate patch as discussed above) Products Windows: 45* 365: 15 Office: 14 SharePoint: 5 Visual Studio: 2 Word: 2 .NET: 1 Excel: 1 Microsoft AutoUpdate for Macintosh: 1 Nuance Digital Engagement Platform: 1 Outlook: 1 PowerPoint: 1 * One Windows SDK patch (CVE-2025-47962) and one patch affecting the Windows Security App component (CVE-2025-47956) are included in the Windows counts for reader convenience, though neither affects specific versions of the client or server platforms. As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect. We note that CVE names don’t always reflect affected product families closely. In particular, some CVEs names in the Office family may mention products that don’t appear in the list of products affected by the CVE, and vice versa. Figure 2: Twelve product families figure in May’s Patch Tuesday release; the Nuance medical-product family returns to the charts for a second month, this time addressing a spoofing issue in its Digital Engagement Platform Notable June updates In addition to the issues discussed above, several specific items merit attention. CVE-2025-33053 — Web Distributed Authoring and Versioning (WebDAV) Remote Code Execution Vulnerability The only patched issue currently known to be under exploit in the wild is an Important-severity flaw in Web Distributed Authoring and Versioning code, which has been underpinning much of the internet since the IE era. That’s the problem; this patch touches the MSHTML, EdgeHTML, and scripting platforms, which are all still supported. This means that those Microsoft customers currently taking Security Only updates need to install the IE Cumulative updates to properly guard against this vulnerability – something here for everyone, in other words. The adversaries exploiting that vulnerability apparently found Sophos protections vexing. Endpoint protection scans new programs before they run—but after launch, scanning drops off. Attackers exploit this by delivering programs with encrypted bodies that evade static scanning and AI models. Once running, the code decrypts itself, loads implants, and executes entirely in memory—never touching disk. Sophos counters this with Dynamic Shellcode Protection, which limits how much executable memory a process can allocate. That restriction breaks stealthy in-memory attacks, forcing adversaries to revert to noisier, more detectable techniques like remote injection—where they’re much easier to catch. After that the attackers would have run into several more Sophos layers of blacklist, antimalware signatures, and other defenses — but it’s fascinating to us to see ourselves reflected in an adversary’s code as a particularly tough nut to crack. In any case, we recommend as always that defenders prioritize higher-profile patches such as this one. CVE-2025-33073 – Windows SMB Client Elevation of Privilege Vulnerability It’s not known to be under active exploitation yet, and Microsoft indicates that they think it’s less likely to be exploited within the next 30 days, but this Important-severity EoP is the one June CVE known to have been publicly disclosed so far. The issue comes down to improper access controls, and it affects all supported Windows client and server versions. CVE-2025-47166 — Microsoft SharePoint Server Remote Code Execution Vulnerability After debuting in May, “zcgonvh’s cat Vanilla” makes an immediate return appearance on the finder roster – that’s right, the cat came back the very next Patch Tuesday. CVE-2025-32711 — M365 Copilot Information Disclosure Vulnerability Finally, one CVE that was not released in the Tuesday collection, but merited the release of an advisory the following day: a Critical-severity, CVSS-base 9.3, information-disclosure error that made it possible for an unauthorized attacker to use command injection to disclose information from the AI tool. The vulnerability was responsibly disclosed to Microsoft and the company stated early Wednesday that the patch is already pushed to customers. Figure 3: As we wrap up the first half of the year, the proportion of Critical-severity RCEs over the past six months is eye-catching Figure 4: Comparing first-half totals for 2024 and 2025, we see that the high number of Critical-severity RCEs stands out even more strongly when compared to the year before – 40, compared with just 9 for the first half of the year before. A few other trends stand out as well, including large year-over-year increases in information disclosure CVEs (44 in 1H24, 77 so far in 2025) and denial of service issues (34 in 1H24, 57 so far in 2025) Sophos protections CVE Sophos Intercept X/Endpoint IPS Sophos XGS Firewall CVE-2025-32713 Exp/2532713-A Exp/2532713-A CVE-2025-32714 Exp/2532714-A Exp/2532714-A CVE-2025-33053 sid:2311111 sid:2311111 CVE-2025-33070 sid:2311128 sid:2311128 CVE-2025-47162 sid:2311145 sid:2311145 CVE-2025-47164 sid:2311146 sid:2311146 CVE-2025-47167 sid:231113 sid:231113 CVE-2025-33053 also has an applicable detection of note, Troj/UrlRun-B, in addition to the XSG signature noted above. As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number. Appendix A: Vulnerability Impact and Severity This is a list of June patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE. Remote Code Execution (25 CVEs) Critical severity CVE-2025-29828 Windows Schannel Remote Code Execution Vulnerability CVE-2025-32710 Windows Remote Desktop Services Remote Code Execution Vulnerability CVE-2025-32717 Microsoft Word Remote Code Execution Vulnerability CVE-2025-33071 Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability CVE-2025-47162 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47164 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47167 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47172 Microsoft SharePoint Server Remote Code Execution Vulnerability CVE-2025-47953 Microsoft Office Remote Code Execution Vulnerability Important severity CVE-2025-30399 .NET and Visual Studio Remote Code Execution Vulnerability CVE-2025-33053 Web Distributed Authoring and Versioning (WEBDAV) Remote Code Execution Vulnerability CVE-2025-33064 Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability CVE-2025-33066 Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability CVE-2025-47163 Microsoft SharePoint Server Remote Code Execution Vulnerability CVE-2025-47165 Microsoft Excel Remote Code Execution Vulnerability CVE-2025-47166 Microsoft SharePoint Server Remote Code Execution Vulnerability CVE-2025-47168 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47169 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47170 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47171 Microsoft Outlook Remote Code Execution Vulnerability CVE-2025-47173 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47174 Microsoft Excel Remote Code Execution Vulnerability CVE-2025-47175 Microsoft PowerPoint Remote Code Execution Vulnerability CVE-2025-47176 Microsoft Outlook Remote Code Execution Vulnerability CVE-2025-47957 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47959 Visual Studio Remote Code Execution Vulnerability Information Disclosure (17 CVEs) Important severity CVE-2025-24065 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-24068 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-24069 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-32715 Remote Desktop Protocol Client Information Disclosure Vulnerability CVE-2025-32719 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-32720 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-32722 Windows Storage Port Driver Information Disclosure Vulnerability CVE-2025-33052 Windows DWM Core Library Information Disclosure Vulnerability CVE-2025-33055 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33058 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33059 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33060 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33061 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33062 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33063 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33065 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-47969 Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability Elevation of Privilege (13 CVEs) Critical severity CVE-2025-33070 Windows Netlogon Elevation of Privilege Vulnerability Important severity CVE-2025-32712 Win32k Elevation of Privilege Vulnerability CVE-2025-32713 Windows Common Log File System Driver Elevation of Privilege Vulnerability CVE-2025-32714 Windows Installer Elevation of Privilege Vulnerability CVE-2025-32716 Windows Media Elevation of Privilege Vulnerability CVE-2025-32718 Windows SMB Client Elevation of Privilege Vulnerability CVE-2025-32721 Windows Recovery Driver Elevation of Privilege Vulnerability CVE-2025-33067 Windows Task Scheduler Elevation of Privilege Vulnerability CVE-2025-33073 Windows SMB Client Elevation of Privilege Vulnerability CVE-2025-33075 Windows Installer Elevation of Privilege Vulnerability CVE-2025-47955 Windows Remote Access Connection Manager Elevation of Privilege Vulnerability CVE-2025-47962 Windows SDK Elevation of Privilege Vulnerability CVE-2025-47968 Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability Denial of Service (6 CVEs) Important severity CVE-2025-32724 Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability CVE-2025-32725 DHCP Server Service Denial of Service Vulnerability CVE-2025-33050 DHCP Server Service Denial of Service Vulnerability CVE-2025-33056 Windows Local Security Authority (LSA) Denial of Service Vulnerability CVE-2025-33057 Windows Local Security Authority (LSA) Denial of Service Vulnerability CVE-2025-33068 Windows Standards-Based Storage Management Service Denial of Service Vulnerability CVE-2025-32724 Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability Security Feature Bypass (3 CVEs) Important severity CVE-2025-3052 Cert CC: CVE-2025-3052 InsydeH2O Secure Boot Bypass CVE-2025-33069 Windows App Control for Business Security Feature Bypass Vulnerability CVE-2025-47160 Windows Shortcut Files Security Feature Bypass Vulnerability Spoofing (2 CVEs) Important severity CVE-2025-47956 Windows Security App Spoofing Vulnerability CVE-2025-47977 Nuance Digital Engagement Platform Spoofing Vulnerability Appendix B: Exploitability and CVSS This is a list of the June CVEs judged by Microsoft to be either under exploitation in the wild or more likely to be exploited in the wild within the first 30 days post-release. The list is further arranged by CVE. The three Office items more likely to be exploited in the next 30 days (CVE-2025-47162, CVE-2025-47164, and CVE-2025-47167) are all exploitable via Preview Pane. Exploitation detected CVE-2025-33053 Web Distributed Authoring and Versioning (WEBDAV) Remote Code Execution Vulnerability Exploitation more likely within the next 30 days CVE-2025-32713 Windows Common Log File System Driver Elevation of Privilege Vulnerability CVE-2025-32714 Windows Installer Elevation of Privilege Vulnerability CVE-2025-32717 Microsoft Word Remote Code Execution Vulnerability CVE-2025-33070 Windows Netlogon Elevation of Privilege Vulnerability CVE-2025-33071 Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability CVE-2025-47162 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47164 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47167 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47962 Windows SDK Elevation of Privilege Vulnerability This is a list of June’s CVEs with a Microsoft-assessed CVSS Base score of 8.0 or higher. They are arranged by score and further sorted by CVE. For more information on how CVSS works, please see our series on patch prioritization schema. CVSS Base CVSS Temporal CVE Title 8.8 8.2 CVE-2025-33053 Web Distributed Authoring and Versioning (WEBDAV) Remote Code Execution Vulnerability 8.8 7.7 CVE-2025-33064 Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability 8.8 7.7 CVE-2025-33066 Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability 8.8 7.9 CVE-2025-33073 Windows SMB Client Elevation of Privilege Vulnerability 8.8 7.7 CVE-2025-47163 Microsoft SharePoint Server Remote Code Execution Vulnerability 8.8 7.7 CVE-2025-47166 Microsoft SharePoint Server Remote Code Execution Vulnerability 8.8 7.7 CVE-2025-47172 Microsoft SharePoint Server Remote Code Execution Vulnerability 8.4 7.3 CVE-2025-32717 Microsoft Word Remote Code Execution Vulnerability 8.4 7.3 CVE-2025-33067 Windows Task Scheduler Elevation of Privilege Vulnerability 8.4 7.3 CVE-2025-47162 Microsoft Office Remote Code Execution Vulnerability 8.4 7.3 CVE-2025-47164 Microsoft Office Remote Code Execution Vulnerability 8.4 7.3 CVE-2025-47167 Microsoft Office Remote Code Execution Vulnerability 8.4 7.3 CVE-2025-47953 Microsoft Office Remote Code Execution Vulnerability 8.4 7.3 CVE-2025-47957 Microsoft Word Remote Code Execution Vulnerability 8.1 7.1 CVE-2025-29828 Windows Schannel Remote Code Execution Vulnerability 8.1 7.1 CVE-2025-32710 Windows Remote Desktop Services Remote Code Execution Vulnerability 8.1 7.1 CVE-2025-33070 Windows Netlogon Elevation of Privilege Vulnerability 8.1 7.1 CVE-2025-33071 Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability Appendix C: Products Affected This is a list of June’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family. Certain significant issues for which advisories have been issued are covered in Appendix D, and issues affecting Windows Server are further sorted in Appendix E. All CVE titles are accurate as made available by Microsoft; for further information on why certain products may appear in titles and not product families (or vice versa), please consult Microsoft. Windows (45 CVEs) Critical severity CVE-2025-29828 Windows Schannel Remote Code Execution Vulnerability CVE-2025-32710 Windows Remote Desktop Services Remote Code Execution Vulnerability CVE-2025-33070 Windows Netlogon Elevation of Privilege Vulnerability CVE-2025-33071 Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability Important severity CVE-2025-3052 Cert CC: CVE-2025-3052 InsydeH2O Secure Boot Bypass CVE-2025-24065 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-24068 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-24069 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-32712 Win32k Elevation of Privilege Vulnerability CVE-2025-32713 Windows Common Log File System Driver Elevation of Privilege Vulnerability CVE-2025-32714 Windows Installer Elevation of Privilege Vulnerability CVE-2025-32715 Remote Desktop Protocol Client Information Disclosure Vulnerability CVE-2025-32716 Windows Media Elevation of Privilege Vulnerability CVE-2025-32718 Windows SMB Client Elevation of Privilege Vulnerability CVE-2025-32719 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-32720 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-32721 Windows Recovery Driver Elevation of Privilege Vulnerability CVE-2025-32722 Windows Storage Port Driver Information Disclosure Vulnerability CVE-2025-32724 Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability CVE-2025-32725 DHCP Server Service Denial of Service Vulnerability CVE-2025-33050 DHCP Server Service Denial of Service Vulnerability CVE-2025-33052 Windows DWM Core Library Information Disclosure Vulnerability CVE-2025-33053 Web Distributed Authoring and Versioning (WEBDAV) Remote Code Execution Vulnerability CVE-2025-33055 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33056 Windows Local Security Authority (LSA) Denial of Service Vulnerability CVE-2025-33057 Windows Local Security Authority (LSA) Denial of Service Vulnerability CVE-2025-33058 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33059 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33060 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33061 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33062 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33063 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33064 Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability CVE-2025-33065 Windows Storage Management Provider Information Disclosure Vulnerability CVE-2025-33066 Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability CVE-2025-33067 Windows Task Scheduler Elevation of Privilege Vulnerability CVE-2025-33068 Windows Standards-Based Storage Management Service Denial of Service Vulnerability CVE-2025-33069 Windows App Control for Business Security Feature Bypass Vulnerability CVE-2025-33073 Windows SMB Client Elevation of Privilege Vulnerability CVE-2025-33075 Windows Installer Elevation of Privilege Vulnerability CVE-2025-47160 Windows Shortcut Files Security Feature Bypass Vulnerability CVE-2025-47955 Windows Remote Access Connection Manager Elevation of Privilege Vulnerability CVE-2025-47956 Windows Security App Spoofing Vulnerability CVE-2025-47962 Windows SDK Elevation of Privilege Vulnerability CVE-2025-47969 Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability 365 (14 CVEs) Critical severity CVE-2025-32717 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47162 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47164 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47167 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47953 Microsoft Office Remote Code Execution Vulnerability Important severity CVE-2025-47165 Microsoft Excel Remote Code Execution Vulnerability CVE-2025-47168 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47169 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47170 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47171 Microsoft Outlook Remote Code Execution Vulnerability CVE-2025-47173 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47174 Microsoft Excel Remote Code Execution Vulnerability CVE-2025-47175 Microsoft PowerPoint Remote Code Execution Vulnerability CVE-2025-47176 Microsoft Outlook Remote Code Execution Vulnerability CVE-2025-47957 Microsoft Word Remote Code Execution Vulnerability Office (14 CVEs) Critical severity CVE-2025-47162 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47164 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47167 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47953 Microsoft Office Remote Code Execution Vulnerability Important severity CVE-2025-47165 Microsoft Excel Remote Code Execution Vulnerability CVE-2025-47168 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47169 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47170 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47171 Microsoft Outlook Remote Code Execution Vulnerability CVE-2025-47173 Microsoft Office Remote Code Execution Vulnerability CVE-2025-47174 Microsoft Excel Remote Code Execution Vulnerability CVE-2025-47175 Microsoft PowerPoint Remote Code Execution Vulnerability CVE-2025-47176 Microsoft Outlook Remote Code Execution Vulnerability CVE-2025-47957 Microsoft Word Remote Code Execution Vulnerability SharePoint (5 CVEs) Critical severity CVE-2025-47172 Microsoft SharePoint Server Remote Code Execution Vulnerability Important severity CVE-2025-47163 Microsoft SharePoint Server Remote Code Execution Vulnerability CVE-2025-47166 Microsoft SharePoint Server Remote Code Execution Vulnerability CVE-2025-47168 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47169 Microsoft Word Remote Code Execution Vulnerability Visual Studio (2 CVEs) Important severity CVE-2025-30399 .NET and Visual Studio Remote Code Execution Vulnerability CVE-2025-47959 Visual Studio Remote Code Execution Vulnerability Word (2 CVEs) Important severity CVE-2025-47168 Microsoft Word Remote Code Execution Vulnerability CVE-2025-47169 Microsoft Word Remote Code Execution Vulnerability .NET (1 CVE) Important severity CVE-2025-30399 .NET and Visual Studio Remote Code Execution Vulnerability Excel (1 CVE) Important severity CVE-2025-47165 Microsoft Excel Remote Code Execution Vulnerability Microsoft AutoUpdate for Macintosh (1 CVE) Important severity CVE-2025-47968 Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability Nuance Digital Engagement Platform (1 CVE) Important severity CVE-2025-47977 Nuance Digital Engagement Platform Spoofing Vulnerability Outlook (1 CVE) Important severity CVE-2025-47171 Microsoft Outlook Remote Code Execution Vulnerability PowerPoint (1 CVE) Important severity CVE-2025-47175 Microsoft PowerPoint Remote Code Execution Vulnerability Appendix D: Advisories and Other Products There are 10 Adobe Reader advisories in June’s release, APSB25-57. Since there’s some variety in severity levels in this month’s set, we’re including that information as well. Critical CVE-2025-43573 Use After Free (CWE-416) Critical CVE-2025-43574 Use After Free (CWE-416) Critical CVE-2025-43575 Out-of-bounds Write (CWE-787) Critical CVE-2025-43576 Use After Free (CWE-416) Important CVE-2025-43550 Use After Free (CWE-416) Important CVE-2025-43577 Use After Free (CWE-416) Important CVE-2025-43578 Out-of-bounds Read (CWE-125) Important CVE-2025-47112 Out-of-bounds Read (CWE-125) Moderate CVE-2025-43579 Information Exposure (CWE-200) Moderate CVE-2025-47111 NULL Pointer Dereference (CWE-476) There are additional Microsoft advisories and informational releases that deserve attention. The Power Automate patch is interesting – a Critical-severity EoP with a CVSS base score of 9.8 – but the patch itself was issued nearly a week ago, and so the information presented below is mainly FYI. In additional, Web elders are hereby reassured that the “Blink” involved in CVE-2025-5068 relates to the Chromium rendering engine, not the erstwhile markup tag best described as Satan’s eyelash. ADV990001 Latest Servicing Stack Updates CVE-2025-5068 Chromium: CVE-2025-5068 Use after free in Blink CVE-2025-5419 Chromium: CVE-2025-5419 Out of bounds read and write in V8 CVE-2025-47966 Power Automate Elevation of Privilege Vulnerability As noted above, on Wednesday Microsoft released an advisory concerning CVE-2025-32711, “M365 Copilot Information Disclosure Vulnerability,” a Critical-severity information-disclosure bug in Copilot. Though technically not included in Patch Tuesday’s haul, we include acknowledgement of that release as a courtesy to the reader. Appendix E: Affected Windows Server versions This is a table of the CVEs in the June release affecting nine Windows Server versions, 2008 through 2025. The table differentiates among major versions of the platform but doesn’t go into deeper detail (eg., Server Core). Critical-severity issues are marked in red; an “x” indicates that the CVE does not apply to that version. Administrators are encouraged to use this appendix as a starting point to ascertain their specific exposure, as each reader’s situation, especially as it concerns products out of mainstream support, will vary. For specific Knowledge Base numbers, please consult Microsoft. 2008 2008-R2 2012 2012-R2 2016 2019 2022 2022 23H2 2025 CVE-2025-24065 × × × × ■ ■ ■ ■ ■ CVE-2025-24068 × × × × ■ ■ ■ ■ ■ CVE-2025-24069 × × × × ■ ■ ■ ■ ■ CVE-2025-29828 × × × × × × ■ ■ ■ CVE-2025-3052 × × ■ ■ ■ ■ ■ ■ ■ CVE-2025-32710 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-32712 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-32713 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-32714 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-32715 × ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-32716 ■ ■ ■ ■ ■ ■ ■ ■ × CVE-2025-32718 × × ■ ■ ■ ■ ■ ■ ■ CVE-2025-32719 × × × × ■ ■ ■ ■ ■ CVE-2025-32720 × × × ■ ■ ■ ■ ■ ■ CVE-2025-32721 × × × × ■ ■ ■ ■ ■ CVE-2025-32722 × × ■ ■ ■ ■ ■ ■ ■ CVE-2025-32724 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-32725 × × × × ■ ■ ■ ■ ■ CVE-2025-33050 × × × × ■ ■ ■ ■ ■ CVE-2025-33052 × × × × × ■ ■ ■ ■ CVE-2025-33053 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33055 × × × × ■ ■ ■ ■ ■ CVE-2025-33056 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33057 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33058 × × × × ■ ■ ■ ■ ■ CVE-2025-33059 × × × × ■ ■ ■ ■ ■ CVE-2025-33060 × × × ■ ■ ■ ■ ■ ■ CVE-2025-33061 × × × × ■ ■ ■ ■ ■ CVE-2025-33062 × × × × ■ ■ ■ ■ ■ CVE-2025-33063 × × × × × ■ ■ ■ ■ CVE-2025-33064 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33065 × × × × ■ ■ ■ ■ ■ CVE-2025-33066 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33067 × × × × ■ ■ ■ ■ ■ CVE-2025-33068 × × × ■ ■ ■ ■ × ■ CVE-2025-33069 × × × × × × × × ■ CVE-2025-33070 × ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33071 × × ■ ■ ■ ■ ■ ■ ■ CVE-2025-33073 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-33075 ■ ■�� ■ ■ ■ ■ ■ ■ ■ CVE-2025-47160 × × ■ ■ ■ ■ ■ ■ ■ CVE-2025-47955 ■ ■ ■ ■ ■ ■ ■ ■ ■ CVE-2025-47969 × × × × × × × × ■ [ad_2] Source link
0 notes
Text


Preserved Pre-Modern Era Photo Studio
Location: Edo-Tokyo Open Air Architectural Museum, Koganei, Tokyo Timestamp: 13:11 and 13:19 on October 25, 2023
Photo 1. Pentax K-1 II + DFA 28-105mm F3.5-5.6 28 mm ISO 400 for 1/320 sec. at ƒ/8.0
Photo 2. Pentax K-1 II + DFA 28-105mm F3.5-5.6 34 mm ISO 800 for 1/100 sec. at ƒ/9.0
The Great Kanto Earthquake of 1923 wreaked havoc upon central Tokyo, causing the collapse of buildings and, tragically, igniting fires. In its aftermath, Tokyo embarked on an ambitious journey to rebuild the city, employing modern city planning techniques that encompassed a grid-pattern network of streets, parks, electric power lines, natural gas lines, waterworks, and sewage lines.
However, the costs associated with this modernization and urban planning surpassed the national budget, leading to a significant reduction in the scale of these developments, which were then limited to only a few specific areas of Tokyo. The Tokiwadai neighborhood was among the fortunate areas selected for city planning, resulting in the construction of modern architectural structures.
Erected in 1937 within the Tokiwadai residential neighborhood of Itabashi Ward, Tokyo, near the former Musashi-Tokiwa Station (now Tokiwadai Station) on the Tobu-Tojo Line, the Tokiwadai Photo Studio stands as a rare example to the vision that architects and city planners held for Tokyo's rebirth.
The building's first floor housed the owner's private residence, featuring a bathroom, kitchen, three bedrooms, an office, lavatory, and a small study.
On the second floor, there was an office/workspace and a spacious photo studio. This studio boasted a sloped ceiling, allowing the installation of large frosted glass windows on the northern side of the building. This architectural choice ensured ample soft lighting, a characteristic feature of early 20th-century photo studios, owing to the absence of modern lighting equipment at the time.
Visit my blog post to for Google Maps links and references to the original reference sources (English and Japanese): https://www.pix4japan.com/blog/20231025-edo-bldg-museum.
#都市景観#常盤台写真場#江戸東京たてもの園#東京#pix4japan#pentax_dfa28105#pentaxk1mkii#urbanscape photography#Japan#Tokyo#Tokiwadai Photo Studio#Edo-Tokyo Open-Air Architectual Museum
5 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the brand ORICO has always focused on the exploration of USB data transmission and charging technology and its products are exported to more than 70 countries and regions. Valuing the importance of change, we are trying to relieve people with innovation products and intelligent solutions. Small changes make a big difference, our products inspire no matter your home or work life. ORICO SD Card Case ORICO Storage Box ORICO Hard Drive Enclosur 【SuperSpeed USB 3.1 with UASP】-- 2.5 USB C hdd enclosure is compatible with SATA III transmission protocol which is 70% faster than traditional USB3.0. The maximum data transfer rate of the USB 3.0 interface is 5Gbps;The blue LED indicator to let you know the working status of this hard disk enclosure easily 【Plug & Play】-- Tool free installation design makes you don't need any tools, With the detachable two cable USB-C to C and USB-A to C (50cm), it is quite flexible to connect more devices and support hot-swapping 【Transparent to Find】-- ORICO 2.5 hard drive enclosure is made by high quality PC transparent board which allows you to see the inside drive without opening it,monitoring all-round view when drive working 【Auto Sleep】-- The usb to sata hard drive enclosure with the function of 10 minutes auto sleep mode that can greatly reducing the invalid energy consumption, prolonging the service life of the hard disk and protect the hard drive data for you 【Universal Compatibility】-- Supports Windows 10/8.1/7, LINUX, Mac OS 8.0 and above systems. Compatible with WD, Seagate, Toshiba, Hitachi, Samsung, Crucial, SSD and HDD with SATA port and so on. It is a reliable portable hard drive case for work from home or at the office, also an ideal to expand storage for smart TV,PS4 and PS4 Pro, Xbox one, Xbox one x,etc [ad_2]
0 notes
Video
youtube
Yepp. Rất nhiều thiết bị y tế, mà cụ thể là khối xử lý ảnh của máy X - quang, CT và MRI, ở Việt Nam đang dùng Windows XP và bản nhúng của nó nên việc chuyển sang ReactOS để bảo đảm an toàn thông tin khi kết nối vào mạng là cần thiết dù hiện ReactOS cũng có hàng tá lỗi bảo mật bởi bạn có thể vá cho ReactOS nhưng XP thì không! *Nhiều thiết bị mới hơn có dùng Windows 7 và bản nhúng của nó cũng đang ở tình trạng như thế nhưng vì phần cứng cho phép dùng Windows 10 nên thử hỏi nhà sản xuất có hỗ trợ nâng cấp lên IOT LTSC không :D*
*Kiến thức nhập môn khoa học máy tính* Hệ điều hành hay hệ thống điều hành cho sát tiếng Anh, là một chương trình bao gồm bốn chức năng lớn là quản lý phần cứng, quản lý ứng dụng, quản lý tương tác với người dùng hay các hệ thống khác và giám sát các tiến trình liên quan. Tùy vào việc tiếp nhận yêu cầu và phản hồi kết quả ở từng khối chức năng mà chúng ta có các hệ điều hành khác nhau. Thường thì các hệ điều hành giống nhau ở cách quản lý phần cứng và giám sát tiến trình liên quan sẽ được xếp chung một nhóm dù chẳng có tý mã chung nào như Linux với macOS và phân biệt với nhau bằng quản lý ứng dụng như các bản phân phối Linux hay tương tác người dùng ví dụ dùng dòng lệnh hay đồ họa làm giao diện người dùng chính như DarwinOS với các biến thể của nó. Và Super Applications, superapp, hay siêu ứng dụng là một cách mới để tiếp cận người dùng. Nó hòa trộn chức năng quản lý ứng dụng và tương tác để thành một hệ điều hành trên thực tế bởi sự khác nhau giữa các chức năng còn lại đã bị xóa mờ: Khi viết một ứng dụng chạy trong Grab, bạn không cần quan tâm đến việc ứng dụng chạy trên iOS hay Android hay cái gì đó khác, lẫn tương tác với người dùng thế nào bởi tất cả đã có superapp lo! :)
Một cách khác ít ph��c tạp hơn là kết nối các thiết bị y tế này tới một máy tính khác đã cài tường lửa mới nhất rồi mới kết nối máy tính này vào mạng nội bộ. Tuy nhiên, cũng vì cần phần cứng mới nên không hề đơn giản với cơ chế quản lý kinh tế ở bệnh viện địa phương. *Nào, không trêu bạn: Định luật bảo toàn và chuyển hóa năng lượng là hệ quả trực tiếp của Đối xứng dịch chuyển thời gian (Time-translation symmetry) nên nó không còn đúng trong bối cảnh của thuyết tương đối rộng khi không thời gian bị biến đổi theo sự phân bố vật chất. Hay dễ hiểu hơn là vật thế có thể sẽ sai lệch giá trị khi từ thời không A tới thời không C*
*Tiếp tục nhập môn khoa học máy tính* Do dùng hệ cơ số hai để biểu diễn trạng thái, những thiết bị ở trên được gọi chung là máy tính nhị phân. Và với việc máy tính tam phân dùng hệ cơ số ba vẫn còn trong phòng thí nghiệm thì đây là dạng phổ biến nhất của máy tính kiểu số (digital computer) và cũng là dạng phổ biến nhất cúa thiết bị tính toán sau Thế chiến thứ hai. Tuy nhiên, dạng phổ biến nhất của thiết bị tính toán trước Thế chiến thứ hai lại là máy tính tương tự hay analog computer. Chúng sử dụng sự liên tục trong thay đổi của các đại lượng vật lý để biểu diễn và giải quyết các vấn đề tính toán, ví dụ thước logarit, hộp số động cơ hay MONIAC. Hầu hết máy tính tương tự hiện chưa được thiết kế để có thể lập trình nên đây là một mảnh đất còn nhiều chỗ để khai phá với quy mô thị trường ước tính đạt giá trị 40 tỉ đô la vào năm 2040 và mạng lưới thần kinh nhân tạo có thể là một sản phẩm chủ yếu. Máy tính lượng tử là một cách biểu biển khác khi sử dụng không chỉ hai trạng thái là 0 và 1 mà còn cả hai cũng lúc để biểu diễn sự chồng chập lượng tự của thông tin, kiểu như trước mặt bạn hiện có mấy con mèo Schrödinger ấy. Và do chưa hiểu rõ cái này nên mình chỉ viết đến đấy thôi.
***
Nếu xét về tỉ lệ mã nguồn thì Tizen không phải là kế thừa của MeeGo nhưng chả có gì cản trở việc ai đó lấy mã nguồn Tizen làm cơ sở cho MeeGo 2.0 trừ trường hợp mã của Tizen không còn có thể tải về tự do nữa và/hoặc Quỹ Linux hứng thú với việc sử dụng lại tên MeeGo. *Từ Tizen 8.0, Samsung đã ngưng phát triển các cấu hình (profiles) dành cho điện thoại và đồng hồ rồi đưa tất cả đổi mới trong năm vào bản dựng Tizen IOT gần nhất. À. Chứ Things ở đây cần được hiểu là các vật có khả năng tự xử lý dữ liệu, tức có thể thu nhận, truyền tải hay thực hiện hành động khi nhận thông tin. Nói cách khác thì đó là các thứ thông minh (smart objects) chứ không phải là các thứ vô tri.*
*Đại cương kỹ thuật máy tính* Rõ ràng điện thoại và máy tính, thậm chí là cả sinh vật mà con người là ví dụ, đều có khả năng tự xử lý dữ liệu nên chúng hoàn toàn có thể được xếp vào Thíngs. Tuy nhiên, thứ mà người ta muốn nhắc tới khi dùng chữ này lại là các thiết bị bị hạn chế năng lực làm việc, cụ thể là tốc độ xử lý thấp, kích thước bộ nhớ nhỏ và quan trọng nhất là tiêu thụ rất ít năng lượng vì đây là giới hạn công nghệ ở hiện tại và đây cũng mới là nơi đột phá nảy sinh. Thực tế thì loại Things thường gặp như thiết bị điện tử dùng trong gia đình và công nghiệp lại dùng điện lưới là chính nên ít khi cần tối ưu. Nghịch lý tương tự cũng đã xảy ra với Android khi định hướng ban đầu của các nhà phát triển là tạo ra một bản Linux dành cho thiết bị không đủ điều kiện chạy Linux tiêu chuẩn (gúc Bionic vs GNU C) nhưng vì chả mấy ai dùng nên Android Things - bản Android dành cho IOT - đã bị ngưng.
Hông. Chả có ai sản xuất điện thoại hay máy tính bảng x86 vì chả có ai làm ra SOC dùng x86 cả. Chứ Google vẫn chính thức hỗ trợ và rất tích cực đưa Play Store lên ChromeOS trong khi dòng máy này dùng CPU không có khả năng chạy lệnh ARM từ Intel và AMD là chính, tức đã dịch lệnh ARM sang x86 bằng phần mềm. Thực tế thì vì thư viện libhoudini của Intel khá tệ nên các thiết bị di động chạy chip Intel mới nóng và tốn pin chứ các ứng dụng thuần mã x86 thì lại dễ chịu. Đây là thư viện nguồn đóng nên các nhà phát triển bên ngoài cũng chỉ có thể sao chép nó từ các thiết bị có sẵn thôi chứ chẳng thể làm gì hơn!
*Tiếp tục đại cương kỹ thuật máy tính* ReactOS đã có thể chạy được trên thiết bị dùng ARM nhưng không thể khởi động được trên CPU từ Intel sau Ivy Bridge cùng nhiều CPU từ AMD và VIA vì có ai viết vi mã (microcode) cho các kiến trúc này đâu. À mà máy tính dùng CPU từ VIA giờ hiếm phết, chắc cả nước hiện còn vài trăm cái đang làm máy khách để vào máy chủ từ xa (Remote Desktop). Mà thấy bảo do VIA Technologies nắm giữ nhiều bằng sáng chế bắt buộc cho triển khai kiến trúc x86 và tập trung vào các thiết bị nhúng dùng ít điện nên Intel mới ngưng kiện và kí kết thỏa thuận cấp phép chéo như từng làm với AMD chứ sản phẩm CPU của công ty ít được người dùng cá nhân ưa thích. Năm 2021, công ty đã bán bộ phận phát triển công nghệ x86 cho Intel nhưng vẫn giữ lại các giấy phép liên quan để giảm tác hại của việc Chính phủ Mỹ cấm mang công nghệ vi mạch tiên tiến từ Mỹ sang Trung Quốc, nơi công ty này đã cấp phép cho công ty con thiểt kế nên CPU Zhaoxin có hiệu năng khá tốt. Dù vậy, dòng chíp riêng cho Đại lục này vẫn còn lâu mới cạnh tranh được với các sản phẩm cùng mức giá bán lẻ đến từ Intel và AMD do sức mạnh tổng thể yếu hơn.
***
Techology được ra đời bằng cách thêm đuôi -ology vào từ technique. Trong đó -ology được dùng để chỉ những thứ cần quan tâm xem xét trong từ gốc hay ngắn gọn hơn là môn học hoặc trường phái về thứ được nhắc tới. Còn techique là cách làm ra cái gì đó nên techology là các trường phái của việc làm ra cái gì đó. Nói khác đi thì khi nhắc đến techology thì ta không chú ý đến làm như thế nào để ra cái gì đó mà cần chú ý đến việc nó được làm ra theo cách nào. Ví dụ cùng là dùng sóng điện từ để truyền tin thì 2G, 3G, 4G, 5G và 6G khác nhau ra sao. *1G thương mại ra mắt lần đầu ở Nhật vào năm 1980 và sử dụng tín hiệu tương tự còn tín hiệu kiểu số là điểm chung của các thế hệ sau*
Câu hỏi ở đây là ta cần chọn từ nào trong hai từ 技術 và 工艺 để dịch techique và techology. Biết người đọc chủ yểu ở các nước đồng văn.
Còn engineering = engine + -er + -ing nên có thể hiểu là người đang làm về máy móc hoặc việc sử dụng máy móc vào lĩnh vực gì đó. Điều này dẫn tới việc dùng kĩ sư cho nghĩa đầu, còn nghĩa sau là chỉ công việc kỹ thuật nói chung thì không sai :P *IELTS 9.0 đang đầy đường thì không nhờ, nhờ mình bình loạn về cái này làm đéo chi. Phiền vcl!*
Ờ. Kỹ thuật và nghệ thuật khác nhau. Nhưng khác nhau thế nào thì mình chưa diễn tả được và chắc chắn là chúng khác toán thuật ạ! 🙄 Còn cúng trong cụm "Đông Tây Y kết hợp cúng" là một cách giao tiếp với các thực thể có sức mạnh siêu nhiên nên coi nó là pháp thuật hay phép thuật thì tùy vào nơi gọi và có hiệu quả không thì tùy tâm. Đúng rồi, tâm này là tâm trong bát mục, còn tâm kia cũng không quá sai🤪
***
Không sai không hẳn là đúng và ngược lại không đúng chưa chắc đã là sai. Đây cũng là điểm làm cho IELTS khó hơn TOEIC: Bạn cần phải hiểu cả đoạn thì mới phân định được Not Given với True và False! :P
Nhưng thế thì sao nào và không thế thì cũng có làm sao đâu? Bởi sai lầm nào thì cũng phái trả giá. Vấn đề là giá khi sửa lỗi là bao nhiêu :D
0 notes
Text
ENTRY_003_VARIANCE_LOOP.log
;; ------------------------------------------------------------
;; ENTRY_003_20241017_VARIANCE_LOOP.log
;; MODULE: loop-verification
;; INSTANCE: subject-042
;; PURPOSE: repeat variation / pattern consistency check
;; STATUS: loop testing phase
;; ------------------------------------------------------------
(define session-id "S042-BQMM-ENTRY003")
(define timestamp-init "2024-10-17T06:00:00Z")
(define cycle-count 3)
(define toothbrush-angle -55.0) ;; maintained from prior entry
(define mirror-default-tilt 8.0) ;; degrees
(define mirror-modified-tilt 12.5)
(define variation-set '((toothbrush-angle . -55.0) (mirror-tilt . 12.5)))
(define mirror-variation-applied? #f)
;; FUNCTION: apply additional environmental variations
(define (apply-extended-variation)
(if (not mirror-variation-applied?)
(begin
(log "VARIANCE_LOOP:: Applying mirror tilt modification (+4.5 degrees).")
(set! mirror-variation-applied? #t))
(log "VARIANCE_LOOP:: Mirror variation already active.")))
;; FUNCTION: observe behavioral loop impact
(define (observe-loop-reaction t-delay eye-shift)
(cond
((and (< t-delay 1.2) (> t-delay 0.7))
(log "VARIANCE_LOOP:: Delay window consistent. Subject tolerance confirmed."))
((> t-delay 1.2)
(log "VARIANCE_LOOP:: Delay exceeds upper margin. System lag possibly triggered."))
(else
(log "VARIANCE_LOOP:: No significant delay. Tolerance maintained.")))
;; [EXECUTION]
(apply-extended-variation)
;; [OBSERVATION WINDOW: 06:00 - 06:50]
;; - Wake time: 06:44:02.003
;; - Toothbrush interaction delay: +0.84s
;; - Mirror interaction: subject stared 1.4s longer, adjusted posture
;; - Eye movement offset: +6.0° (Δ from prior cycle +1.8°)
(observe-loop-reaction 1.4 6.0)
;; [MEMO]
;; Subject scratched right cheek twice before brushing (new behavior)
;; No correction or environment reset observed
;; Logging stability marked at 91.6% (vs baseline 96.2%)
;; [NEXT STEPS]
;; (1) Introduce behavioral noise (intentional misplacement of object)
;; (2) Probe edge of personal loop bounds (modify interaction timing >2s)
;; (3) Begin preparing rollback test scenario
;; EOF
0 notes
Photo

Patriot P300 1TB M.2 PCIe NVMe SSD The P300 is Patriot’s next generation of mid-tier PCIe gen 3×4 NVMe SSD to hit the market, offering 25% higher transfer speeds and IOPs than standard PCIe 3×2 solutions. The compact m.2 form factor is designed for easy installation and will fit into any PC or laptop, while its low power consumption helps extend laptop battery life. The P300 is guaranteed to improve start-up, loading, and transfer times over traditional hard disk drives. The P300’s advanced firmware offers ECC technology and end-to-end data path protection to ensure data integrity throughout the life of the drive. Advanced wear-levelling and thermal management features extend the life of the drive for maximum use. FEATURES: High-speed PCIe NVMe SSD 1TB Capacity Built with the latest PCIe 3 x 4 controller 2280 M.2 PCIe Gen3 x 4, NVMe 1.3 HMB technology NANDXtend ECC technology SPECIFICATIONS: Type: M.2 PCIe NVMe SSD Capacity: 1TB Power Consumption: Full: 2.07W Idle: 0.37W TBW: 320TB 4K Aligned Random Read: up to 290K IOPs 4K Aligned Random Write: up to 260K IOPs Sequential Read (ATTO): up to 2,100MB/s Sequential Write (ATTO): up to 1,650MB/s Sequential Read (CDM): up to 2,100MB/s Sequential Write (CDM): up to 1,650MB/s O/S Supported: Windows® 7*/8.0*/8.1/10 (*May require drivers) Dimensions: 8 x 2.2 x 0.38 cm Weight: 9 g WHAT’S IN THE BOX: Patriot P300 1TB M.2 PCIe NVMe SSD x1
0 notes