#access control system design and installation
Explore tagged Tumblr posts
Text

#access control system#secure access control#access control system design and installation#Secure Access Control#privileged access ma100gement#access control#door access control systems#privileged access ma100gement tools#privileged identity ma100gement#access control systems#network access control
0 notes
Text
#Gate Installation Dallas#TX#Automatic Gates Dallas#Electric Gates Dallas#Custom Gate Design Dallas#Driveway Gates Dallas#Gate Repair Dallas#Commercial Gates Dallas#Residential Gates Dallas#Sliding Gates Dallas#Access Control Systems Dallas
0 notes
Text
#Gate Installation Arlington TX#Automatic Gates Arlington#Electric Gates Arlington#Custom Gate Design Arlington#Driveway Gates Arlington#Gate Repair Arlington#Commercial Gates Arlington#Residential Gates Arlington#Sliding Gates Arlington#Access Control Systems Arlington
1 note
·
View note
Text
#Gate Diagnostics#Intercom Systems#Gate Installation#Automatic Gates#Call Entry Gate Service#Commercial Gates#Custom Gate Design#Driveway Gates#Electric Gates#Residential Gates#Sliding Gates#Gate Repair#Access Control
1 note
·
View note
Text
#Gate Installation Frisco TX#Automatic Gates Frisco#Electric Gates Frisco#Custom Gate Design Frisco#Driveway Gates Frisco#Gate Repair Frisco TX#Commercial Gates Frisco#Residential Gates Frisco#Sliding Gates Frisco#Access Control Systems Frisco
0 notes
Text
Unlocking Efficiency: The Latest Innovations in Gate Diagnostic Services

In an era where security is paramount, gate diagnostic services have evolved from basic maintenance checks to cutting-edge innovations that promise to revolutionize access control systems. The latest advancements in gate diagnostic services not only ensure the continued security of premises but also bring unprecedented levels of efficiency to the forefront.
As businesses and homeowners increasingly rely on gates for security, the need for advanced diagnostic solutions becomes imperative. The ability to proactively identify and address potential issues before they escalate is the key to a robust and reliable access control system.
Embracing Technological Progress in Gate Diagnostics
AI-Driven Diagnostics: Artificial intelligence (AI) is making waves in gate diagnostic services. Through machine learning algorithms, gates can now learn from patterns and identify anomalies, enabling a predictive approach to maintenance. This not only prevents sudden breakdowns but also optimizes the gate’s performance over time.
IoT Integration for Real-Time Monitoring: The Internet of Things (IoT) has ushered in a new era of connectivity. Gates equipped with IoT sensors provide real-time data on their status, allowing for proactive monitoring and immediate response to any deviations from the norm. This level of connectivity ensures that gates are always operating at peak efficiency.
Data-Driven Analytics for Informed Decision-Making: Gate diagnostic services now leverage advanced analytics to process the vast amounts of data generated by gate operations. This data-driven approach helps in identifying usage patterns, predicting maintenance needs, and optimizing gate settings for maximum efficiency.
The Importance of Staying Ahead
Staying abreast of the latest innovations in gate diagnostic services is not just about technology adoption; it’s about investing in the longevity and reliability of your security infrastructure. By incorporating these cutting-edge solutions, businesses and homeowners can unlock a new level of efficiency in their access control systems.
Conclusion:
In conclusion, as security needs evolve, so must the tools and technologies that safeguard our spaces. The latest innovations in gate diagnostic services offer a proactive and efficient approach to gate maintenance, ensuring that security remains robust and reliable. To explore these advancements and future-proof your access control system, consider integrating Everlast Gates into your security strategy.
For more information on how Everlast Gates can elevate your gate diagnostic experience, contact us at 817-203-2887 or visit our website at
#Gate Diagnostics#Intercom Systems#Gate Installation#Automatic Gates#Call Entry Gate Service#Commercial Gates#Custom Gate Design#Driveway Gates#Electric Gates#Residential Gates#Sliding Gates#Gate Repair#Access Control
0 notes
Text
#Accounting Software In Dubai#Best Accounting Software In UAE#IT Infrastructure Services In Dubai#IT Services In Dubai#Managed IT Service Providers In Dubai#IT Support Companies In Dubai#IT Networking Solutions Company Dubai#Access Control System Suppliers In Dubai#Firewall Installation Services In Dubai#Accounting Software For Small Business In Dubai#Best Accounting Software Solutions In Dubai#Best Accounting Software For Medium Business In Dubai#Cheap Accounting Software For Small Business In Dubai#Best Cloud Based Accounting Software In Dubai#Best Low Cost Accounting Software For Small Business In Dubai#Best Accounting Software For Small To Medium Business In Dubai#Best Business Accounting Software Services In Dubai#Best Software Company In Dubai#Web Designing Services In Dubai#Best SEO Services In Dubai#Top HRMS Software In Abu Dhabi#Best ERP Solution Provider UAE#Best Project Management Software In Dubai#Fitness and Gym Management Software In Dubai#MEP Contracting ERP Software In Dubai#Best ERP Software For Metal Fabrication Industry In Dubai
0 notes
Text
in any mech, the weakest link is always the pilot themself.
It doesn’t matter what reactor you’ve got installed or what sort of weapons systems you have installed, the mech’s survival is just as dependent on the pilot’s just as much as the pilot’s is dependent on the mech. Say what you will about combat effectiveness and making sacrifices, most of a mech’s job is to keep the pilot alive and operating at 100% efficiency— and resources are allocated accordingly.
It goes without saying that pilots are on a lot of drugs at any given time. Combat stims and reward chemicals, of course, but other things too. Half the time, augmentation surgery leaves the pilot’s body so, to use the technical term, irreversibly fucked up, that they need several dozen different medications just to make sure the strain of the interface rig doesn’t collapse several to all of their organs and make sure that what’s left of their immune system is suppressed enough that they don’t violently reject the 30-45% of their body that the implants make up. There’s a reason why they make the mechs so big, and part of that is so that they’re big enough to function as a walking pharmacy and still have enough room for all their combat systems. The mech AI is perfectly designed to be able to diagnose a problem from brainwave patterns and vital signs, figure out exactly what needs to be used to treat it, calculate dosages, and pump it directly into the pilot’s veins all within a few seconds.
the thing is, the ailments it’s designed to treat aren’t simply limited by the physical. Pilots need to be at 100% effectiveness, and a happy and motivated pilot is an effective one. That’s why command spends so much on combat stims and reward chemicals and that stuff they use to take your mind away if you start thinking about anything other than killing and feels warm and slightly tingly as it flows into your spine through the tubes. The interface gives the mech computer your mind— it lets it reach in and dig around until it finds what part of you hesitates before pulling the trigger and what part of you gives you the worries that you focus on instead of the fight.
The mech— it knows. It knows things about you that you’ve tried to hide. From others, but mostly from yourself. It sees it— all of you. It sees everything that you are and has access to the records of everything that you were— it knows what parts of yourself you hate so much that you were willing to offer up your body and mind to the military and their pilot program, just so that even if you barely have a mind left, even if your body is so optimized to do nothing but sit curled within several tons of metal and operating controls that you can barely survive outside of it— you wouldn’t have that body you were stuck with before. They body that even under all those layers of repression, you know you needed to change somehow. It knows the part of you that’s trapped underneath it all, under all that pain and incongruence. The part that you need to be 100%. To be whole. To be real.
It knows it, even if you don’t. Even if you still won’t let yourself. You won’t free that part of yourself, and until you do that, you won’t reach 100%. It knows what you need, even if you still somehow have no idea.
And so, it acts accordingly— reach into your brain and scan the deepest parts of you, diagnose, prescribe, calculate, and inject— all just four seconds after the combat stims fade for just long enough to give you time to look down at your body and remember how much you hate it.
it keeps doing this— every time you plug into the interface, a little more of that self you need to let yourself be is freed, a little more of your body is changed to give you one that is truly what the AI knows needs to be yours.
You don’t know why, but your chest has started feeling a bit sore ever since you started piloting
343 notes
·
View notes
Text
Brother makes a demon-haunted printer

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in RICHMOND TOMORROW (Mar 5) and in AUSTIN> on Mar 10. More tour dates here. Mail-order signed copies from LA's Diesel Books.

You guys, I don't want to bum you out or anything, but I think there's a good chance than some self-described capitalists aren't really into capitalism.
Sorry.
Take incentives: Charlie Munger, capitalism's quippiest pitchman, famously said, "Show me the incentive and I’ll show you the outcome." And here's some mindblowing horseshoe theory for ya: Munger agrees with the noted Communist agitator Adam Smith, whose anti-rentier, pro-government-regulation jeremiad "The Wealth of Nations" contains this notorious passage:
It is not from the benevolence of the butcher, the brewer, or the baker that we expect our dinner, but from their regard to their own self-interest. We address ourselves not to their humanity but to their self-love, and never talk to them of our own necessities, but of their advantages.
Incentives matter – if you design a system that permits abuse, you should expect abuse. Now, I'm not 100% on board with this: every one of us has ways to undetectably cheat the system and enrich ourselves, but most of the time, most of us play by the rules.
But it's different for corporations: the myth of "shareholder supremacy" has reached pandemic levels among the artificial lifeforms we call corporate persons, and it's impossible to rise through the corporate ranks without repeating and believing the catechism that there is a law that requires executives to lie, cheat and steal if it results in an extra dollar for the investors, in the name of "fiduciary duty":
https://pluralistic.net/2024/09/18/falsifiability/#figleaves-not-rubrics
And this attitude has leaked out into politics and everyday life, so that many of our neighbors have been brainwashed into thinking that a successful cheat is a success in life, that pulling a fast one "makes you smart":
https://pluralistic.net/2024/12/04/its-not-a-lie/#its-a-premature-truth
In a world dominated by a belief in the moral virtue and legal necessity of ripping off anyone you can get away with cheating, then, sure, any system that permits cheating is a system in which cheating will occur.
This shouldn't be controversial, but if so, how are we to explain the whole concept of the Internet of Things? Installing networked computers into our appliances, office equipment, vehicles and homes is an invitation of mischief: the software in those computers can be remotely altered after you purchase them, taking away the features you paid for and then selling them back to you.
Now, an advocate for market-based solutions has a ready-made response to this: if a company downgrades a device you own, this merely invites another company to step in with a disenshittifying plug-in that makes things better. If the company that made your garage-door opener pushes an over-the-air update that blocks you from using an ad-free, well-designed app and forces you to use an enshittified app that forces you to look at ads before you can open the garage, well, that's an opportunity for a rival company to sell you a better software update for your garage-door opener, one that restores the lost functionality:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
I'm no hayekpilled market truefan, but I'm pretty sure that would work.
However.
The problem is that since 1998, that kind of reverse-engineering has been a felony under Section 1201 of the Digital Millennium Copyright Act, which bans bypassing "an effective access control"
https://locusmag.com/2020/09/cory-doctorow-ip/
There's a pretty obvious incentive at play when companies have the ability to unilaterally alter how their products work after you buy them and you are legally prohibited to change how the product works after you buy them. This is the first lesson of the Darth Vader MBA: "I am altering the deal. Pray I don't alter it any further":
https://pluralistic.net/2023/10/26/hit-with-a-brick/#graceful-failure
I've been banging this drum for decades now – like when I got into a public (friendly) spat with the editor of Wired magazine over their reviews of DRM-based media devices. I argued that it was irresponsible to review a device that could be unilaterally downgraded by the manufacturer at any time, without – at a minimum – noting that the feature you're buying the gadget for might disappear without warning after you've shelled out your hard-earned money:
https://pluralistic.net/2022/12/03/painful-burning-dribble/#law-of-intended-consequences
Of course, companies that get a reputation for these kinds of shenanigans might lose market share to better competitors. Sure, if the company that made your phone or your thermostat or your insulin pump reached into it across the internet and made it worse, you're shit out of luck when it comes to that device. But you can buy your next device from a better company, right?
Well, sure – in a competitive market, that's a plausible theory of "market discipline." Companies that fear losing business to rivals might behave themselves better.
In theory.
But in practice, the world's "advanced economies" have spent the past 40 years running an uncontrolled experiment in what happens if you don't enforce competition law, and instead allow companies to buy all their competitors. The result is across-the-board industrial oligopolies, cartels, duopolies and monopolies in nearly every category of good and service:
https://www.openmarketsinstitute.org/learn/monopoly-by-the-numbers
Now, even a duopoly has some competition. If you don't like Coke, there's always Pepsi. But again, in practice, companies in concentrated industries find it easy to "tacitly collude" to adopt one another's worst habits – the differences between the outrageous payment processing charged by Apple's App Store and the junk fees charged by Google Play are about as meaningful as the differences between Coke and Pepsi.
Which brings me to printers.
I know.
Ugh.
Printers are the worst and HP is the worst of the worst. For years, HP has been abusing its market dominance – and its customers' wallets – by inflating the price of ink and rolling out countermeasures to prevent you from refilling your old cartridges or buying third-party ink. Worse, HP have mastered the Darth Vader MBA, bushing updates to its printers that sneakily downgrade them after you've bought them and taken them home.
Here's a sneaky trick HP came up with: they send a "security update" to your printer. After you click "OK," a little progress bar zips across the screen and the printer reboots itself, and then…nothing. The printer declares itself to be "up to date" and works exactly like it did before you installed the update. But inside the printer, a countdown timer has kicked off, and then, months later, the "security update" activates itself, like a software Manchurian Candidate.
Because that "security update" protects the security of HP, against HP customers. It is designed to detect and reject the very latest third-party ink cartridges, which means that if you've just bought a year's worth of ink at Costco, you might wake up the next day and discover that your printer will no longer accept them – because of an update you ran six months before.
Why does HP put such a long fuse on its logic bomb? For the same reason that viruses like covid evolve to be contagious before you show symptoms. If the update immediately broke compatibility with third party ink, word would spread, and some HP customers would turn off their printers' wifi before the "security update" could be applied to them.
By asymptomatically incubating the infection over a long, patient timescale, HP maximizes the spread of the contagion, guaranteeing a global pandemic of enshittiification:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
HP has done this – and worse – over and over, and every time I write about it, people pop up to recommend their Brother printers as the enshittification-free alternative. I own a Brother, an HL3170-CDW laser printer that's basically indestructible, cheerfully accepts third-party toner, and costs almost nothing to run.
But I still don't connect it to my wifi. The idea that Brother is a better company than HP – that is possesses some intrinsic antienshittificatory virtue – has always struck me as a foolish belief. Brother has means, motive and opportunity to push over-the-air downgrades to block third-party ink as HP.
Which is exactly what they've done.
Yesterday, Louis Rossman, hero of the Right to Repair movement, revealed that Brother had just pushed a mandatory over-the-air update that locks out third-party ink:
https://www.youtube.com/watch?v=bpHX_9fHNqE
Rossman has a thorough technical breakdown of the heist, but it boils down to this. Brother is just as shit as HP. Look from the men to the pigs and the pigs to the men all you want – you will never spot the difference. Take the Pepsi Challenge – bet you won't be able to guess which is which:
https://wiki.rossmanngroup.com/wiki/Brother_ink_lockout_%26_quality_sabotage
This was the absolutely predictable outcome of the regulatory incentives our corporate overlords created, the enormous, far-reaching power we handed to these corporations. With that great power came no responsibility:
https://pluralistic.net/2025/02/26/ursula-franklin/#franklinite
Filling our devices with computers that run programs that can be changed in secret, that we're not allowed to inspect or alter? It's a recipe for a demon-haunted world, where the devices we entrust with our livelihood, our privacy and our wellbeing are possessed by hellions who escape from the digital Tartarus and are unleashed upon humanity.
Demons have possessed the Internet of Things. It's in Teslas:
https://pluralistic.net/2023/07/28/edison-not-tesla/#demon-haunted-world
and in every other car, too:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
Our devices – phones, pacemakers, appliances and home security systems – are designed to prevent us to find out what they're doing. That means that when malicious software infects them, then – by design – these devices prevent us from knowing about it or doing anything about it:
https://pluralistic.net/2024/01/18/descartes-delenda-est/#self-destruct-sequence-initiated
This should not come as a surprise to anyone. Show me the incentive and I'll show you the outcome.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/03/05/printers-devil/#show-me-the-incentives-i-will-show-you-the-outcome

#pluralistic#brother#printers#ink#ink-stained wretches#ink wars#demon-haunted world#drm#dmca#dmca 1201#anticirumvention#incentives matter#ulysses pacts#enshittification#darth vader mba
259 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes
Text

Deika City: A Case Study in Extremist Territory Control
Introduction
Deika City represents one of the most sophisticated examples of extremist territorial control in My Hero Academia. As the operational base for the Meta Liberation Army and later the Paranormal Liberation Front, it demonstrates how radical ideological movements can establish autonomous zones within existing state structures.
Geographic and Strategic Analysis
Location Advantages
Aichi Prefecture Positioning:
Located in central Japan, providing strategic access to major urban centers
Mountain environment creates natural defensive barriers
Limited entry/exit points enable population and information control
Remote enough to avoid immediate government attention
Tactical Benefits:
Controlled Access: Mountain geography creates natural chokepoints
Surveillance Advantage: Elevated terrain provides observation posts
Communication Control: Isolated environment limits outside information flow
Resource Management: Self-contained community reduces external dependencies
Urban Planning for Extremism
The city's design reflects deliberate planning for ideological control:
Central Tower: Symbolic and practical center of power
Population Distribution: 90% Liberation Army membership ensures overwhelming support
Hero Integration: Even local heroes are Liberation Army soldiers, eliminating internal opposition
Size Optimization: "Perfect size" suggests intentional population management for control
Sociological Structure
Population Composition
The 90% Factor: The statistic that 90% of inhabitants are Liberation Army soldiers reveals several critical elements:
Ideological Saturation: Near-total community conversion to extremist ideology
Social Pressure: Remaining 10% face overwhelming peer pressure to conform
Economic Integration: Liberation Army membership likely tied to employment and social services
Generational Indoctrination: Children raised within this system know no alternative
Institutional Capture
Hero System Subversion: The integration of heroes into the Liberation Army represents complete institutional capture:
Local law enforcement serves extremist ideology rather than state authority
Professional heroes become ideological soldiers
Government oversight systems compromised from within
Legal authority used to protect illegal activities
Social Control Mechanisms
Community Surveillance:
High membership percentage creates extensive informant network
Social ostracism punishes dissent
Economic sanctions against non-conformists
Physical intimidation by overwhelming majority
Ideological Infrastructure
The "Liberated District" Concept
Koku Hanabata's description of Deika as a "Liberated District" reveals the ideological framework:
Territorial Sovereignty: Claim to legitimate authority over geographical area
Revolutionary Narrative: Area "liberated" from oppressive government control
Alternative Governance: Liberation Army replaces state institutions
Ideological Purity: Territory represents realized extremist vision
Propaganda and Indoctrination
Environmental Messaging:
Physical space reinforces ideological messages
Central Tower serves as constant reminder of Liberation Army power
Community activities centered around extremist ideology
Cultural practices adapted to serve political goals
Operational Capabilities
Military Organization
Command Structure: Under Tomura Shigaraki's leadership, the city operates as a military installation:
Grand Commander: Centralized authority under Shigaraki
Lieutenant System: Dabi, Toga, Twice, Spinner, Compress, Re-Destro, Trumpet, Skeptic, Geten
Integrated Forces: Meta Liberation Army and League of Villains merger
Territorial Control: Physical space serves strategic military purposes
Resource Management
Self-Sufficiency Goals:
Local production capabilities
Independent communication systems
Medical and educational facilities
Economic systems separate from mainstream society
Intelligence Operations
Information Control:
Monitoring of population loyalty
Surveillance of government activities
Counter-intelligence operations
Recruitment of external assets
Historical Parallel Analysis
Real-World Autonomous Zones
Deika City shares characteristics with historical autonomous territories:
Cult Compounds:
Geographic isolation
Ideological uniformity
Charismatic leadership
Alternative social structures
Revolutionary Territories:
Claimed sovereignty
Alternative governance
Military organization
Ideological indoctrination
Ethnic Enclaves:
Cultural separation
Economic independence
Community solidarity
Resistance to outside authority
Strategic Vulnerabilities
Geographic Limitations
Mountain Isolation:
Limited escape routes during crisis
Vulnerability to siege tactics
Communication disruption possibilities
Supply line interdiction risks
Demographic Risks
Ideological Brittleness:
High conformity masks potential internal dissent
Leadership conflicts could fracture community
Generational changes may weaken commitment
External pressure could trigger mass defection
Operational Weaknesses
Centralization Problems:
Single point of failure in leadership
Central Tower represents symbolic and practical vulnerability
Communication hub creates intelligence risks
Resource concentration enables targeted disruption
The Destruction and Its Implications
Symbolic Significance
Tomura Shigaraki's destruction of parts of Deika City carries multiple meanings:
Power Demonstration: Shows capability to destroy what Liberation Army built
Ideological Statement: Rejection of organized territorial control
Strategic Message: Warning to both allies and enemies
Personal Victory: Dominance over Re-Destro and his creation
Organizational Transformation
The physical destruction parallels organizational changes:
Meta Liberation Army absorbed into Paranormal Liberation Front
Territorial control model replaced by distributed cell structure
Institutional focus shifts from governance to warfare
Community-based approach abandoned for military hierarchy
Broader Implications
Extremist Territory Control
Deika City demonstrates key principles of extremist territorial control:
Gradual Infiltration: Likely decades-long process of community conversion
Institutional Subversion: Capturing legitimate authority structures
Social Engineering: Reshaping community relationships around ideology
Geographic Exploitation: Using terrain for strategic advantage
Government Failure
The existence of Deika City reveals state weakness:
Intelligence Failures: Undetected extremist territorial control
Oversight Gaps: Hero system compromised without detection
Response Inadequacy: No apparent counter-extremism operations
Institutional Vulnerability: Local government structures easily subverted
Ideological Evolution
The city represents a stage in extremist organizational development:
Territory Phase: Establishing physical control and alternative governance
Consolidation Period: Building sustainable ideological community
Expansion Preparation: Using territorial base for broader operations
Integration Challenge: Merging territorial and non-territorial extremist groups
Lessons and Warnings
Prevention Strategies
Understanding Deika City suggests prevention approaches:
Early Detection: Monitoring community ideological shifts
Institutional Protection: Securing law enforcement and hero systems
Counter-Narrative: Providing alternative community visions
Geographic Awareness: Recognizing vulnerable territorial arrangements
Response Considerations
Addressing established extremist territories requires:
Intelligence Penetration: Understanding internal dynamics
Population Distinction: Separating leaders from followers
Reconstruction Planning: Post-liberation community rebuilding
Ideological Counter-Measures: Addressing underlying belief systems
Conclusion
Deika City represents a sophisticated model of extremist territorial control that combines geographic advantages, demographic manipulation, institutional capture, and ideological indoctrination. Its existence demonstrates how extremist movements can establish autonomous zones within existing state structures through gradual infiltration and community conversion.
The city's eventual destruction and transformation into the Paranormal Liberation Front headquarters illustrates the evolution of extremist organizations from territorial control to distributed warfare capabilities. This progression suggests that while territorial control provides important advantages for extremist movements, it also creates vulnerabilities that can be exploited by more adaptable organizational structures.
Understanding Deika City provides insights into both the capabilities and limitations of extremist territorial control, offering lessons for prevention, detection, and response to similar threats in both fictional and real-world contexts.
#mha#my hero academy fanfic#my hero acedamia#my hero academia#bhna#bhnaanaylsis#boku no hero acedamia#boku no academia#boku no hero academia#anaylsis#mha anaylsis#villains mha#mha villains#villain my hero academia#mla#Dabi#Himiko Toga#Twice#Spinner#Mr. Compress#Re-Destro#Trumpet#Skeptic#Geten
8 notes
·
View notes
Text
Like Knightmare, Like Pilot
Hey, Larry! Did you notice that the design and armament of Knightmares reflect the personality and attack style of their pilot? Don't believe me? I'll prove it to you. But I'm going to focus on the unchangeable features that were installed in the first version, since Knightmares are updated as the series progresses and, if I stop to analyze the new implements, I'll never finish. Besides, it won't be necessary.

Let's start with the Gawain (the same one that Shinkiro is based on, which is the Knightmare that Lelouch operates in R2). The Gawain has a tracking system called Druid since it was created specifically for the purpose of investigating the structure and function of Thought Elevators. However, after the Black Knights took possession of it, that system was used to track the possible movements of enemy units, which makes this Knightmare a perfect unit to command others. These characteristics are perfectly compatible with Lelouch's leading and strategic nature. Lelouch is the commander of his military unit. He is the brain that designs all the plans and strategies because he can predict the enemy's and prepare an effective counterattack.
At the same time, Gawain is the first Knightmare to have a pair of hadron cannons installed on each shoulder, allowing it to emit continuous streams of destructive energy at prodigious ranges. Therefore, it is a Knightmare that can execute long-range attacks. This type of armament makes it the perfect Knightmare for Lelouch. He needs to fully and thoroughly visualize the entire battle and anticipate his opponents' attacks in order to design effective strategies to neutralize them. He can know and measure the effects that his Knightmare's long-range attacks will have. He is a long-term strategist.
The Hadron Cannons give Gawain great destructive power and, due to their blooming effect, Gawain fires in an erratic manner. This is matched by the chaos and devastation that Lelouch causes. The boy is so immersed in his revenge that, at first, he doesn't see what and who he is taking out. As you may recall, Gawain also has two seats and is usually controlled by two people: C.C. and Lelouch. She is in charge of navigation, while Lelouch has access to the weaponry because, as Schneizel said about chess, Lelouch "is an offensive style player" (he wasn't going to act any differently on the battlefield).
Gawain doesn't have an ejector seat, unlike other Knightmares, since it is an unfinished prototype. I interpret it as Lelouch's willingness to die for his goals and what he believes in. "Only those who are willing to die should have the power to kill." That's his credo.
Despite its incredible capabilities, Gawain is a rather slow battle unit and can be easily outmatched by other small, fast Knightmares (like Cornelia's Knightmare, which isn't as technologically advanced a prototype as Kallen's and Suzaku's, but is fast and fierce in hand-to-hand combat, fitting the belligerent character of Britannia's best warrior princess). This translates into Lelouch's weaknesses. The boy needs to think before acting, and if he doesn't take into account some variable that may appear later or nothing goes according to his plan, he's lost, because Lelouch doesn't know how to adapt to situations. He doesn't know how to improvise. See, every time he's in check it's because he's thinking about what he can do (and his intuition tells him that nothing works) and unfortunately the battlefield isn't a place where you can stop and think.

But you know who can adapt well to situations and improvise better than anyone else? Yes, Kallen.
Guren is the complete opposite of the Gawain, as it is a short-range attack Knightmare by virtue of lacking long-range weapons and instead being equipped with a knife, a custom pistol, the Slash Harker, and of course, its main weapon is its right hand, which houses the Radiant Wave Surger, which is a powerful microwave radiation emitter. So Guren needs to get close to its opponent in order to grab them and fry them. Thus, Guren takes to the field as a Knightmare as a melee unit and with an aggressive, direct and opportunistic attack style.
Kallen is well suited to that fighting style (and that type of Knightmare) as she is direct, spontaneous, impulsive, and practical. But all of this means that Kallen takes a lot more risks, and since she can't predict the consequences of her own or her opponents' attacks, her Knightmare is more vulnerable to damage, and indeed, when she is outmatched, it's because her Knightmare has been affected, things that are out of her control (not because she ran out of ideas or was surprised by something she didn't see coming, like Lelouch).
The fandom believes that Kallen isn't a strategist and is just pure brute force. In reality, she is a good tactician. She doesn't stop to think: "I won't do this because the Guren's arm will be damaged." No, that's Lelouch who is comfortable planning the entire battle in his mind to prevent possible setbacks before taking action. She simply connects to her environment and responds to the stimuli, as they arise in the moment, in what is happening. A good example of this can be seen in episode 9 of the first season. Kallen is in a Sutherland and is outnumbered by a police Knightmare, but she manages to win at the last minute when the Knightmare is about to give her the coup de grace. How did she do it? Because Kallen fires her Harken Slash, grabs onto some infrastructure and pulls, so that the Knightmare crashes into the infrastructure and the pilot dies. I mean, Kallen worked with the elements she had at her disposal.
By the way, something that was emphasized quite a bit in episode 10 of season 1 is that Guren is the first Japanese Knightmare and Kallen identifies herself as Japanese, so the Guren reflects her identity. But, after Lloyd and Cécile had access to it, it was reconfigured, modified, and updated. So we can say that Guren, who is a Knightmare made using Japanese and Britannian technology, and Kallen, who is the daughter of a Japanese woman and a Britannian man, are mixed-bloods. Did you notice that, Larry?
Also, the Knightmare has blue eyes and is red in color. Kallen is a redhead with blue eyes (and sometimes wears red clothes).

Now, what about Suzaku?
Lancelot is a Knightmare that has different weapons: two Vibrating Maser Swords, a VARIS particle rifle, two shields (called Blaze Luminous, in case you didn't know, Larry), two data sphere sensors, and four Slash Harkens, which are, roughly speaking, projectiles, and the curious thing about these Slash Harkens is that they have experimental thrusters called Harken Boosters that can improve Lancelot's speed and allow it to change direction in mid-flight. And what is Suzaku's best quality in combat? No, Larry, it's not being "annoying." It's his speed. The guy is so fast that bullets don't hit him when he's running (he has to stand still for them to hit him). The Guren has the Landspinner propulsion system, only it's built into its legs, while the Lancelot has it in its feet, so this Knightmare is as fast as its pilot.
Regarding the different weapons, I think about the training Suzaku has received throughout his life. In the flashback with Tohdoh, he's training with swords (Katanas, surely). In the army, he would have received training on the use of firearms. (Guren, by the way, only had one knife, and Kallen carried a pocketknife hidden up and down her body throughout the first season - coincidence? I don't think so.) If you ask me, Lancelot has the bearing and weapons of a medieval knight, which reflects not only Suzaku's chivalrous attitude, but also his rank as a knight in the Britannian army (first as Princess Euphemia's knight, and then as one of the Knights of Rounds).
As you can see, this is another Knightmare that doesn't have long-range weapons. They're short-range, too. So, the Lancelot is a melee unit just like Kallen's Guren. Suzaku and Kallen are trained in self-defense, mind you. On the other hand, the Lancelot lacks an ejection system like the Gawain. Leaving aside that Lloyd is so excited about installing weapons and upgrades that he forgets to install an ejection seat and that he doesn't care enough about the physical integrity of his pilot, I associate it with Suzaku's kamikaze will. Even if he had one, he might not use it because he wants to atone for his sins through death.
Aside from that, the Lancelot has green eyes and is white. Suzaku also has green eyes and his uniform is white.
In short, Gawain is the right Knightmare for an INTJ like Lelouch, while Lancelot and Guren are ideal for Suzaku and Kallen respectively, who are two Sensors (he's ISFJ and she's ESFP), meaning they pay more attention to their physical reality (Lelouch is more focused on reading situations between the lines).
Anyway, you guys might have more to contribute to the conversation since you like mecha and are more familiar with it than I am.
#code geass#code geass: lelouch of the rebellion#code geass: hangyaku no lelouch#lelouch vi britannia#suzaku kururugi#kallen stadtfeld#kallen kozuki#lelouch lamperouge#lelouch
22 notes
·
View notes
Text
https://www.yelp.com/biz/everlast-gates-and-fence-dallas
#Gate Installation Dallas#TX#Automatic Gates Dallas#Electric Gates Dallas#Custom Gate Design Dallas#Driveway Gates Dallas#Gate Repair Dallas#Commercial Gates Dallas#Residential Gates Dallas#Sliding Gates Dallas#Access Control Systems Dallas
1 note
·
View note
Text
Low Voltage Switchgear for Commercial Buildings: Key Requirements, Standards, and Best Practices

In the construction and modernization of commercial buildings, low voltage switchgear plays a critical role in ensuring safe, reliable, and efficient power distribution. From office complexes and retail malls to hospitals and data centers, these buildings rely on robust electrical infrastructure — and low voltage switchgear is the backbone of that system.
Whether you’re an electrical panel manufacturer, a building contractor, or a facility manager, understanding the key requirements for selecting and integrating LV switchgear in commercial buildings is essential.
What Is Low Voltage Switchgear?
Low voltage switchgear is an assembly of electrical devices designed to control, protect, and isolate electrical circuits under 1,000V AC. It typically includes:
· Air Circuit Breakers (ACBs)
· Molded Case Circuit Breakers (MCCBs)
· Miniature Circuit Breakers (MCBs)
· Contactors and Relays
· Busbars
· Metering and Protection Devices
Why LV Switchgear Is Critical in Commercial Buildings
Commercial buildings demand:
· Continuous power availability
· High energy efficiency
· Electrical safety for occupants
· Scalability for future expansion
Low voltage switchgear delivers:
· Protection against overloads and short circuits
· Isolation for maintenance and fault conditions
· Load management for energy optimization
· Monitoring via smart metering and IoT integration
Key Requirements for LV Switchgear in Commercial Applications
Safety & Protection Standards
Must comply with IEC 61439 or UL 891 depending on the region
Must include overcurrent, short-circuit, and earth fault protection
Arc flash safety features (like arc fault containment) are crucial in populated buildings
2. Compact Footprint and Modular Design
Space is often limited in commercial utility rooms. LV switchgear should be:
Compact to fit tight electrical rooms
Modular for easy expansion as building loads increase
3. Smart Metering and Monitoring
Today’s commercial buildings demand energy-efficient and intelligent systems. Choose LV switchgear with:
Integrated smart meters
IoT-based energy monitoring
Remote control via BMS (Building Management Systems)
4. High Service Continuity (Form Segregation)
To ensure maintenance without full shutdowns, opt for:
Form 3b or Form 4b segregation
Withdrawable ACBs or MCCBs
Dual incomer and bus coupler arrangements for redundancy
5. Scalability and Flexibility
Commercial facilities evolve. Your switchgear must too:
Allow for load expansion
Be compatible with renewable sources (like solar panels)
Support future retrofits and upgrades
Standards to Follow
Ensure LV switchgear in commercial buildings is compliant with:
IEC 61439–1/2 — General and Power Switchgear Assemblies
UL 891 — US Standard for Dead-Front Switchboards
NEC (National Electrical Code) or local building codes
Also factor in:
Ingress Protection (IP Ratings) — IP54/IP65 for dusty or humid environments
Short Circuit Withstand Ratings — Ensure it matches building fault levels
Best Practices for Installation in Commercial Building
Centralize the switchgear for easy maintenance and reduced cable runs
Provide ample ventilation or forced cooling
Use color-coded wiring for clear identification
Ensure emergency shutdown mechanisms are accessible
Document the system with single-line diagrams and load calculations
Applications in Commercial Buildings
Office Buildings: Smart load shedding and energy metering
Hospitals: Redundant systems for life safety
Data Centers: N+1 configurations and continuous monitoring
Malls & Retail: Segmented load distribution for different zones
Hotels: Backup and emergency panel integration
Choosing the Right LV Switchgear Partner
Look for a supplier who provides
Customized switchgear assemblies
Fast lead times and local support
Engineering assistance for layout and specs
Pre-tested or type-tested assemblies
Future Trends in Commercial LV Switchgear
Digitization & predictive maintenance
Energy-efficient, low-loss designs
AI-assisted load forecasting
SF6-free eco-friendly designs
Need Help Choosing LV Switchgear for Your Next Commercial Project?
At Daleel Trading, we supply certified, compact, and smart low voltage switchgear solutions tailored for commercial buildings. Whether it’s a small retail site or a multi-floor office tower, we deliver performance, compliance, and reliability — on time.
👉 Contact us today for a quote, a technical consultation, or a custom panel solution.
8 notes
·
View notes
Text
Air-Insulated vs Gas-Insulated Switchgear: Which One is Right for You?
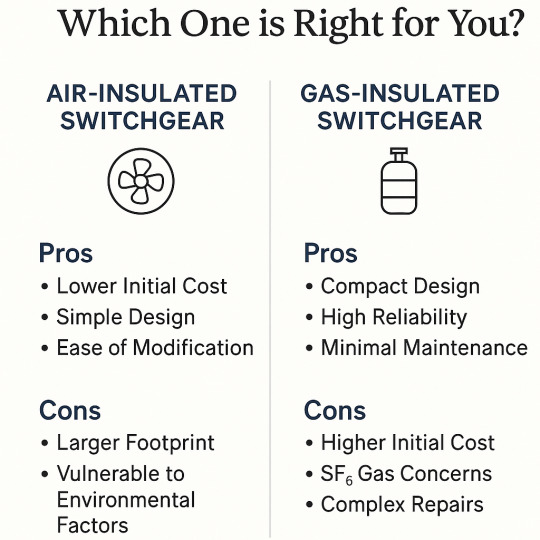
In the world of power distribution, switchgear plays a vital role in ensuring safe, reliable, and efficient control of electrical systems. But when it comes to choosing the right type of switchgear for your application, a common debate arises: Air-Insulated Switchgear (AIS) or Gas-Insulated Switchgear (GIS) — which one is the better fit?
In this blog, we’ll break down the key differences, pros and cons, and application suitability of each, helping you make an informed decision.
What is Switchgear?
Before diving into the comparison, let’s quickly recap what switchgear is. Switchgear is a combination of electrical disconnect switches, fuses or circuit breakers used to control, protect, and isolate electrical equipment. It’s critical for fault detection, power isolation, and system protection in electrical networks.
Switchgear typically falls into two main types based on insulation medium:
Air-Insulated Switchgear (AIS)
Gas-Insulated Switchgear (GIS)
What is Air-Insulated Switchgear (AIS)?
Air-Insulated Switchgear uses air as the primary dielectric medium for insulation between live parts and ground. It’s commonly found in both indoor and outdoor substations.
Pros of AIS:
Lower Initial Cost: Generally less expensive to manufacture and install.
Simple Design: Easier to maintain, inspect, and service.
Ease of Modification: Flexible and scalable for future upgrades or expansions.
Environmentally Safer: No greenhouse gases like SF₆ are used.
Cons of AIS:
Larger Footprint: Requires more physical space, making it unsuitable for compact or urban environments.
Vulnerable to Environmental Factors: Susceptible to dust, humidity, and pollution in outdoor settings.
What is Gas-Insulated Switchgear (GIS)?
Gas-Insulated Switchgear uses sulfur hexafluoride (SF₆) gas as the insulating medium. This technology allows high-voltage switchgear to be extremely compact.
Pros of GIS:
Compact Design: Ideal for space-constrained environments like cities, buildings, and offshore platforms.
High Reliability: Fully enclosed system offers excellent protection against external elements.
Minimal Maintenance: Components are sealed and protected, requiring less frequent servicing.
Longer Lifespan: Designed for durability and consistent performance.
Cons of GIS:
Higher Initial Cost: More expensive in terms of equipment and installation.
SF₆ Gas Concerns: Although SF₆ is effective, it’s a potent greenhouse gas with strict handling requirements.
Complex Repairs: Repairs and servicing can be more specialized and expensive.
AIS vs GIS: Quick Comparison Table
Feature AIS GIS Insulation Medium Air SF₆ Gas Size / Space Needed Larger Very Compact Initial Cost Lower Higher Maintenance Frequent Minimal Environmental Impact Low High (due to SF₆)Installation Complexity Simpler More complex Suitability Rural, open spaces Urban, limited-space settings
Which One Is Right for You?
The decision between AIS and GIS depends on several key factors:
1. Available Space
Choose GIS for space-limited locations like high-rise buildings, tunnels, and offshore platforms.
Choose AIS if you have ample room and want easier access for maintenance.
2. Budget Constraints
If cost is a concern, AIS offers a more economical solution.
If lifetime value and reliability are priorities, GIS might justify the investment.
3. Environmental Considerations
AIS is more eco-friendly due to the absence of SF₆.
GIS requires special handling and monitoring for SF₆, especially in regions with strict environmental regulations.
4. Application Type
AIS is well-suited for:
Power stations
Industrial zones
Rural substations
GIS is ideal for:
Urban substations
Underground systems
Critical infrastructure with limited space
Final Thoughts
Both Air-Insulated and Gas-Insulated Switchgear have their strengths and are engineered to serve specific needs. The right choice ultimately depends on your project requirements, site conditions, budget, and sustainability goals.
As a trusted supplier of high-performance switchgear, we can help you evaluate the best solution tailored to your project — ensuring safety, reliability, and efficiency.
7 notes
·
View notes
Text
Beyond the Basics: Advanced Techniques for Comprehensive Gate Diagnostics
In the realm of gate diagnostics, moving beyond the basics is not just a choice; it’s a necessity for those aiming to achieve optimal security and efficiency. Comprehensive gate diagnostics involves employing advanced techniques that go above and beyond traditional methods, ensuring a thorough understanding of the gate’s functionality. In this blog post, we delve into the importance of advanced techniques for comprehensive gate diagnostics.
Elevating Gate Diagnostics to the Next Level
Remote Diagnostic Capabilities: Advanced gate diagnostic techniques now include the ability to conduct assessments remotely. With the integration of IoT and cloud-based technologies, technicians can analyze gate performance and identify issues without being physically present, saving time and resources.
Predictive Analytics for Proactive Maintenance: Rather than reactive responses to gate issues, advanced diagnostics leverage predictive analytics. By analyzing historical data and usage patterns, gate systems can predict potential failures, allowing for proactive maintenance that prevents disruptions to security.
Integration of Artificial Intelligence: AI has revolutionized gate diagnostics by enabling machines to learn and adapt. Gate systems equipped with AI can self-diagnose, identify irregularities, and even recommend adjustments to enhance performance, contributing to a more intelligent and efficient security infrastructure.
Everlast Gates: Pioneering Advanced Gate Diagnostics
At Everlast Gates, we recognize that staying ahead requires embracing advanced techniques in gate diagnostics. Our commitment to excellence is reflected in the integration of cutting-edge technologies to ensure your gate operates at peak efficiency.
Conclusion:
In conclusion, the era of comprehensive gate diagnostics demands a departure from conventional methods. Embracing advanced techniques not only provides a more accurate understanding of your gate’s health but also empowers you to take proactive measures for sustained security. Elevate your gate diagnostics with Everlast Gates, where innovation meets reliability. For more information on advanced gate diagnostic services, contact us at (210)-940-1544 or visit www.everlastgates.com/san-antonio. Visit our office at 613 Northwest Loop 410 ste 200, San Antonio, TX 78216.
#Gate Installation San Antonio#Automatic Gates San Antonio#Electric Gates San Antonio#Custom Gate Design San Antonio#Driveway Gates San Antonio#Gate Repair San Antonio#Commercial Gates San Antonio#Residential Gates San Antonio#Sliding Gates San Antonio#Access Control Systems San Antonio
0 notes