#advance computer forensic
Explore tagged Tumblr posts
Text

$1 Million Worth of Gold Coins Stolen From 18th-Century Shipwrecks Found
After an extensive investigation, Florida officials recovered dozens of gold coins valued at more than $1 million that were stolen from a shipwreck recovery nine years ago.
The Florida Fish and Wildlife Conservation Commission announced in a news release Tuesday it had recovered 37 gold coins that were stolen from the 1715 Fleet shipwrecks.
The fleet of Spanish ships sailed from Havana, Cuba and headed to Seville, Spain on July 24, 1715. The journey was short-lived, as a hurricane wrecked the fleet just seven days later off the coast of Eastern Florida.
The first ship was discovered in 1928 by William Beach north of Fort Pierce, Florida, about 120 miles south of Orlando. Since then, gold and silver artifacts have been recovered offshore for decades following the first discovery.
In 2015, a group of contracted salvage operators found a treasure trove of 101 gold coins from the wrecks near Florida’s Treasure Coast, about 112 miles west of Orlando. However, only half of the coins were reported correctly. The other 50 coins were not disclosed and later stolen.
The years-long investigation by the state’s fish and wildlife conservation commission and FBI “into the theft and illegal trafficking of these priceless historical artifacts” came to a head when new evidence emerged in June, the news release said.
The evidence linked Eric Schmitt to the illegal sale of multiple stolen gold coins in 2023 and 2024, officials said. Schmitt’s family had been contracted to work as salvage operators for the US District Courts’ custodian and salvaging company for the fleet, 1715 Fleet - Queens Jewels, LLC. The Schmitts had uncovered the 101 gold coins in 2015.
During their hunt for the coins, investigators executed multiple search warrants and recovered coins from private residences, safe deposit boxes and auctions, the news release said. Five stolen coins were retrieved from a Florida-based auctioneer, who unknowingly purchased them from Schmitt.
Investigators used advanced digital forensics to nail down Schmitt as a suspect in the case. In most cases, digital forensics can recover data stored electronically on devices such as a cell phone, computer system or memory module.
With the help of advanced digital forensics, investigators identified metadata and geolocation data that linked Schmitt to a photograph of the stolen coins taken at the Schmitt family condominium in Fort Pierce, Florida.
Authorities said Schmitt also took three of the stolen gold coins and put them on the ocean floor in 2016. The coins were later found by the new investors of the fleet’s court custodian and salvaging company.


Throughout the investigation, the Florida Fish and Wildlife Conservation Commission worked closely with historical preservation experts to authenticate and appraise the recovered coins sold by Schmitt.
Schmitt is facing charges for dealing in stolen property, the release says.
The company commissioned to salvage the shipwreck said in a statement it “was shocked and disappointed by this theft and has worked closely with law enforcement and the state of Florida regarding this matter.”
“We take our responsibilities as custodian very seriously and will always seek to enforce the laws governing these wrecks,” the statement read.
Recovered artifacts will be returned to their rightful custodians, the news release said. But the investigation is far from over: 13 coins remain missing.

#$1 Million Worth of Gold Coins Stolen From 18th-Century Shipwrecks Found#1715 Fleet shipwrecks#gold#gold coins#collectable coins#treasure#shipwreck#ancient artifacts#archeology#archeolgst#history#history news#ancient history#ancient culture#ancient civilizations
127 notes
·
View notes
Text
Entering the United States has become more precarious since the start of the second Trump administration in January. There has been an apparent surge in both foreign visitors and US visa holders being detained, questioned, and even deported at the border. As the situation evolves, demand for flights from Canada and Europe has plummeted as people reevaluate their travel plans.
Many people, though, can’t avoid border crossings, whether they are returning home after traveling for work or visiting friends and family abroad. Regardless of the reason for travel, US Customs and Border Protection (CBP) officials have the authority to search people’s phones and other devices as they determine who is allowed to enter the country. Multiple travelers have reported being questioned or turned away at the US border in recent weeks in relation to content on their phones.
While not unique to the US border—other nations also have powers to inspect phones—the increasingly volatile nature of the Trump administration’s border policies is causing people to rethink the risks of carrying devices packed with personal information to and from the US. Canadian authorities have updated travel guidance to warn of phone searches and seizures, some corporate executives are reconsidering the devices they carry, some officials in Europe continue to receive burner phones for certain trips to the US, and the Committee to Protect Journalists has warned foreign reporters about device searches at the US border.
With this in mind, here’s the WIRED guide to planning for bringing a smartphone across the border. You should also use WIRED’s guide to entering the US with your digital privacy intact to get a broader view of how to minimize data and take precautions. But start here for everything smartphone.
What Can CBP Access?
Do CBP officials have the authority to search your phone at the border? The short answer is yes. Searches are either manual, with a border official looking through the device, or more advanced, involving forensic tools to extract data en masse. To get into your phone, border officials can ask for your PIN or biometric to unlock the phone. However, your legal status and right to enter the US will make a difference in what a search might look like at the border.
Generally, border zones—which includes US international airports—fall outside of Fourth Amendment protections that require a warrant for a device to be searched (though one federal court has ruled otherwise). As such, CBP has the power to search any traveler’s phone or other electronic devices, such as computers and cameras, when they’re entering the country. US citizens and green card holders can refuse a device search without being denied entry, but they may face additional questioning or temporary device seizure. And as the Trump administration pushes the norms of acceptable government conduct, it is possible that, in practice, green card holders could face new repercussions for declining a device search. US visa holders and foreign visitors can face detention and deportation for refusing a device search.
“Not everybody has the same risk profile,” says Molly Rose Freeman Cyr, a member of Amnesty International’s Security Lab. “A person’s legal status, the social media accounts that they use, the messaging apps that they use, and the contents of their chats” should all factor into their risk calculus and the decisions they make about border crossings, Cyr says.
If you feel safe refusing a search, make sure to disable biometrics used to unlock your device, like face or fingerprint scanners, which CBP officers can use to access your device. Instead, use only a PIN or an alphanumeric code (if available on your device). Make sure to keep your phone’s operating system up to date, which can make it hard to crack with forensic tools.
You should also consider factors like nationality, citizenship, profession, and geopolitical views in assessing whether you or someone you’re traveling with could be at higher risk of scrutiny during border crossings.
In short, you need to make some decisions before you travel about whether you would be prepared to refuse a device search and whether you want to make changes to your devices before your trips.
Keep in mind that there are simple steps anyone can take to keep your devices out of sight and, hopefully, out of mind during border crossings. It’s always a good idea to obtain a printed boarding pass or prepare other paper documents for review and then turn your phone off and store it in your bag before you approach a CBP agent.
Traveling With an Alternate Phone
There are two ways to approach device privacy for border crossings. One is to start with a clean slate, purchasing a phone for the purpose of traveling or wiping and repurposing your old phone—if it still receives software updates.
The device doesn’t need to be a true “burner” phone, in the sense that you will be carrying it with you as if nothing is out of the ordinary, so you don’t need to purchase it with cash or take other steps to ensure that it can’t be connected to you. The idea, though, is to build a sanitized version of your digital life on the travel phone, ideally with separate communication and social media accounts created specifically for travel. This way, if your device is searched, it won’t have the back catalog of data—old text messages, years of photos, forgotten apps, and access to many or all of your digital accounts—that exists on your primary phone and could reveal details of your political views, your associations, or your movements over time.
Starting with a clean slate makes it easy to practice “data minimization,” or reducing the data available to another person: Simply put the things you’ll need for a trip on the phone without anything you won’t need. You might make a travel email address, some alternate social media accounts, and a separate account for end-to-end encrypted communications using an app like Signal or WhatsApp. Ideally you would totally silo your real digital life from this travel life. But you can also include some of your regular personal apps, building back from the ground up while determining on a selective basis whether you have existing accounts that you feel comfortable potentially exposing. Perhaps, for example, you think that showing a connection to your employer or a community organization could be advantageous in a fraught situation.
Privacy and digital rights advocates largely prefer the approach of building a travel device from scratch, but they caution that a phone that is too squeaky clean, too much like a burner phone, can arouse suspicion.
“You have to ‘seed’ the device. Use the phone for a day or even for a few hours. It just can't be clean clean. That’s weird,” says Matt Mitchell, founder of CryptoHarlem, a security and privacy training and advocacy nonprofit. “My recommendation is to make a finsta for travel, because if they ask you what your profile is, how are you gonna say ‘I don't use any social media’? Many people have a few accounts anyway. One ratchet, one wholesome—add one travel.”
Cyr, from Amnesty International, also points out that a true burner phone would be a “dumb” phone, which wouldn’t be able to run apps for encrypted communications. “The advantage that we all have with smartphones is that you can communicate in an encrypted way,” Cyr says. “People should be conscious that any nonencrypted communication is less secure than a phone call or a message on an application like Signal.”
While a travel device doesn’t need to use a prepaid SIM card bought with cash, it should not share your normal phone number, since this number is likely linked to most if not all of your key digital accounts. Buy a SIM card for your trip or only use the device on Wi-Fi.
Traveling With Your Primary Phone
The other approach you can take to protecting your device during border crossings is to modify your primary smartphone before travel. This involves removing old photos and messages and storing them somewhere else, cleaning out nonessential apps, and either removing some apps altogether or logging out of them with your main accounts and logging back in with travel accounts.
Mohammed Al-Maskati, digital security helpline director at the rights group Access Now, says that people should consider this type of clean-out before they travel. “I will look at my device and see what apps I need,” he says. “If I don't need the app, I just remove it.”
Al-Maskati adds that he suggests people particularly remember to remove dating apps and anything related to LGBTQI communities, especially if they consider themselves to be at higher risk of facing a device search. And generally, this approach is only safe if you are particularly diligent about removing every app that might expose you to risk.
You could use your own phone as a travel phone by backing it up, wiping it, building a travel device with only the apps you really need while traveling, going on your trip, and then restoring from the backup when you get home. This approach is doable but time consuming, and it creates more opportunities for operational security mistakes or what are known as “opsec fails.” If you try to delete all of your old, unwanted apps, but miss one, you could end up exposing an old social media account or other historic service that has forgotten data in it. Messaging apps can have easily searchable archives going back years and can automatically save photos and files without you realizing it. And if you back up all of your data to the cloud and take it off your device, but are still logged into the cloud account underpinning other services (like your main Google or Apple account), you could be asked to produce the data from the cloud for inspection.
Still, if you assess that you are at low risk of facing scrutiny during a border crossing or you don’t have access to an additional device for travel, modifying your main smartphone is a good option. Just be careful.
What To Do, If Nothing Else
Given all of this, you may be hyped up and ready to throw your phone in the ocean. Or you may be thinking there’s no way in hell that you’re ever going to take the time to deal with any of this. For those in the latter camp, you’ve come this far, so don’t click away just yet. If you don’t want to take the time to make a bunch of changes, and you don’t think you’re at particular risk during border crossings (though keep in mind that it’s possible your risk is higher than you realize), there are still a few easy things you can do to protect your digital privacy that are better than nothing.
First, as mentioned above, print a paper boarding pass and any other documents you might need. Even if you don’t turn your phone off and stow it in a bag for your entire entry or exit process, you can put it in your pocket and have your paper ticket and other documents ready while actually interacting with agents. And taking basic digital hygiene steps, like updating your phone and removing apps and data you no longer need, can go a long way.
“We all need to be recognizing that authorities may scrutinize your online presence, including social media activity and posts you’ve published,” says Danacea Vo, founder of Cyberlixir, a cybersecurity provider for nonprofits and vulnerable communities. “Since people have gotten more vocal on social media, they’re very worried about this. Some have even decided not to risk traveling to or from the US this year.”
19 notes
·
View notes
Text
KEEP UP THE PRESSURE: CONTINUE TO FIGHT AGAINST THE TRUMP-MUSK COUP
I'll start with the Bad news since there's a lot of it here:
*Although all of the Democrats voted no, By a margin of 53-47, Russel Vought, one of the leading Architects behind Project 2025, has been confirmed
*Musk's Coup is still ongoing:
*Despite the mounting privacy lawsuits, His DOGE group has gotten access to the NOAA, Department of Labor, and Department of Education, EPA, and the Department of Health and Human Services
*USAID, the foreign aid agency of the US that provided life-saving funding for education, medicine, healthcare, and other foreign aid has been shuttered; it's been absorbed into the State Department with Marco Rubio acting as head of the agency with entire agency's numbers slashed from their original 10,000 to only 300 employees
*As of writing this post, Democrats from the House have been unable to communicate with the heads of the EPA and DOE(Department of Education)
*Even after asserting their credentials, Democrat legislators were denied access and even had federal authorities called on them
Ok, here's is some Good news to help ease you:
*19 Democratic attorneys general sued President Donald Trump on Friday to stop Elon Musk’s "Agency" from accessing Treasury Department records that contained sensitive personal data such as Social Security and account numbers for millions of Americans.
*Thanks to everyone calling so much, the Democrats actually woke up and held up the Senate floor all night, buying time for lawsuits. This led to a judge issuing an order preventing Elon Musk and any additional DOGE-connected people from accessing sensitive Treasury data while the lawsuit proceeds to a two-week hearing.
*The judge’s order restricts two Musk-connected men already housed at Treasury to “read-only” access — meaning they are not permitted to modify or copy anything.
*In response to the gutting of USAID and the firing of its employees, a legal challenge filed on behalf of the employees, the U.S. District Court in the District of Columbia will issue a temporary restraining order regarding various aspects of the Trump-Vance administration’s attempt to shutter the operations of the U.S. Agency for International Development (USAID).
*A California Student group is suing the Department of Education over reported DOGE access to financial aid databases
JUST TO REMIND YOU. YOU ARE NOT ALONE. THERE ARE PEOPLE OUT THERE FIGHTING TO STOP THIS COUP AND FIGHTING FOR YOUR RIGHTS. HERE'S HOW YOU CAN HELP:
1.Call your Senator/Rep Using 5calls: https://5calls.org/issue/elon-musk-opm-gsa-takeover/
Alongside using the script that 5calls provides, mention these actions. Despite Democrats being the minority, they still have tools and options to resist and oppose
If your senator/rep is a Republican, give them as much shit as possible, they are complicit and are willingly giving up Congress' power and responsibility.

2. Contact your State Attorney General by using 5 Calls: https://5calls.org/issue/musk-doge-data-lawsuit/
Here's an alternative script:

By using 5 calls, you probably already know who your State Attorney General is; another way to reach your AG is by searching their name, going to their website, and filing a Complaint form,
3. Contact the Secretary of the Treasury Department! – 202-622-2000
Minimal script for Secretary Scott Bessent: I’m calling to demand that you remove Musk’s access from all systems under your control, that all his equipment is confiscated, that his team is interrogated as to all actions they took under his direction, and that a computer forensics team is assigned immediately to check the system for integrity of its security systems.
After doing all of these, spread this around, not just on Tumblr, but all over the place. People need to know what's going on
and Remember, Do not obey in advance; yes, these are scary times; it's okay to feel afraid, but do not let it paralyze you; you are not alone.
More info on: https://indivisibleventura.org/2025/02/01/the-guy-nobody-trusts-with-a-full-security-clearance-now-has-access-to-all-your-private-data/
#usa politics#us politics#anti donald trump#stop trump#stop donald trump#anti trump#fuck trump#fuck donald trump#never trump#stop project 2025#fuck project 2025#save democracy#us senate#lgbtq+#civil rights#american politics#hr 9495#aclu#stop internet censorship#fight for the future#stop bad bills#american civil liberties union#tags for visibility#signal boost#please spread#please support#please reblog#urgent#very important!#important
21 notes
·
View notes
Text



Ixhika's studyblr 𐙚 (introduction)
I started my studyblr not long ago then a week I guess ? No body knows bout me yet tho but that doesn't matter for me...what matters is that this is my blog - MY JOURNEY

Hey you all ,
Myself Ishika a.k.a eunhee
She/her - INFP - capricorn - age 15 and half (yes I am small comparable to my class because I skipped several classes)
Born on 11 january......
I would say I am 5'5 and healthy weight (so you all can visualise me if you want)
A high-school student from India- 11th grader - non medical, Which means my subjects particularly are:
• Mathematics (weakest subject for me)
• Chemistry (love and hate relationship)
• Physics (second fab)
• English (oml fab)
• Computer science (piece of cake for me)
I actually started my studyblr because I lost interest in studies while ago because of all the stress and pressure.
when I see the studyblr community I actually feel really United yk what I mean...
Intrerests: 🚦
There are lot of things that interest me like seriously.....
Dance , singing , playing basketball , editing videos ,
writing books (fanfics , thriller , actions mostly) ,
programming ( I am actually a full stack web app developer) ,
Baking , stock market ( if you know what I mean) , learning korean (I am kinda trying¿)
Well I am into kpop and kdrama too
Targets : 🎯
I am actually currently aiming for 11th final exam GPA to be 4.7 atleast
Next milestone is of 12th boards final exam GPA to be around same 4.7
Most important milestone and the second final one is that JEE MAINS AND ADVANCE exam (yes I am a jee aspirant)
I want to do something related computer science yk and forensic science so I dunno
My back up is a lawyer/judge in business because I am actually really good in social science subjects yk and business interests me a lot so yeaa
Final milestone is that I want to be a dance choreographer.....that's actually my dream...idc it can even be part time but I am not gonna abandon it.
MY THIS YEAR *BTS* BLACK SWAN CHALLENGE
CYBER FORENSIC INVESTIGATOR *MASTERPOST*
MY POST CATEGORIES:
#studyblr ixh
#diaries ixh
#life goes on series
#writing ixh
#tips ixh
#venting series
#black swan challenge
#achievement ixh
Thats it for the introduction I guess.....I don't think there is more to add in it...uhh yeaa 🏷
I wish to make friends here in this studyblr community !! So let's be friends? 🫶🏻📎

#intro studyblr#academic validation#academic weapon#light academia#student life#study blog#study#study motivation#studyblr#study with me#studyblr community#kpop#kdrama#korea
29 notes
·
View notes
Text
SIC PARVIS MAGNA {Charac. Profiles Pt.1}

an au by @that-irrelevant-ricecakeaddict & @seventhcallisto
SERIES MASTERLIST, Charac. Profiles Pt.2
Reader: Kang Y/N
[21 years old]
>Forensic science student at Okja Central College
>Lives in Seoultham with her elder brother, Kang Taehyun, who travels often for work but helps to pay for expenses
>One of the 2 registered residents staying at Felony Alley, Halazia Apartments
-Level 3, unit 03-01
>Works as a convenience store cashier and a lab assistant at the college when she's not in lectures or class
>Parents were killed during a break-in at their childhood home and town that her and Taehyun chose to move out of when Taehyun had enough money to take them somewhere else (Seoultham was the cheapest option)
>Rides a bike everywhere, despite how often it gets damaged or has its parts stolen by the many thieves roaming the alleys
Kim Hongjoong {Lucky Quinn}
[25 years old]

(based on Harleen Quinzel, Harley Quinn)

Backstory: Grew up in Seoultham and started studying psychology in college at a young age. At 17, he was kidnapped by and experimented on by notorious Seoultham villain The Joker. He was eventually forced to take a serum derived from the same chemicals that drove Joker insane and bleached his skin. Naturally, Hongjoong suffered from the same effects and even developed a sick admiration for the villain. He did everything and anything he could in an attempt to earn Joker's trust and approval. However, Joker and his other followers would often ostracise and abuse him, eventually kicking him out to the streets to die after a few years. Luckily for him, his childhood friend Mingi found him and took him in. With Mingi's help, Hongjoong was able to gain back some sanity and somewhat integrate back into society. Well...the society that he had known for the past few years, at least. He founded Birds of Prey with Mingi.
>Unemployed to avoid being detected by the government
>"Kim Hongjoong" was classified as dead after getting kidnapped by the Joker, so he's known by local law enforcement as mad vigilante Lucky Quinn
>Adopted his alias from his psychology professor, Prof. Quinzel, who had been with him when Joker came to kidnap him. Professor Quinzel was killed in the process, and Hongjoong wanted to honor her
>Still a little messed up in the head, but tame in comparison to how he was when he was still under Joker
>Spends his time either at New World Underground Crime Ring or back and forth between the other members' homes
>Known in the crime scene as a dangerous and violent vigilante who crashes illegal dealings and ongoing crimes, but is highly unpopular with the police for his impulsive behaviour often causing a lot of collateral damage in the city
>Learned how to fight from living with Joker for years
>Captain of the team
>Despite his impulsive and unpredictable nature, hes very caring and understanding of his members (even though their clumsiness causes him trouble occasionally)
Song Mingi {Flying Fox}
[23 years old]

(based on Barbara Gordon, Batgirl)

Backstory: Child tech genius who grew up in Seoultham. From young, he was always very socially awkward and introverted due to how much time he spent inventing and programming. He built seemingly impractical but highly advanced machinery and programmes, which he would later on make use of as a vigilante. When Hongjoong, his only friend growing up, suddenly went off the grid, Mingi dropped everything to try to track him down. After a few years, he succeeded in finding Hongjoong and took him in. Horrified after hearing of Hongjoong's experience, he soon started the Birds of Prey with him in hopes of finding other like-minded outcasts who wanted to help keep Seoultham safe.
>Computer-science student at Okja Central College
>The only other registered resident at Felony Alley, Halazia Apartments
- Level 2, unit 02-01 (reader's downstairs neighbour)
>Learned martial arts as a kid and has photographic memory
>Due to his side gig of being a vigilante, he's quite busy, so he usually only attends online classes and lectures
>One of, if not the ONLY, Birds of Prey member thats on neutral terms with the police since he occasionally helps them with detective cases
>Tech support and happy pill of the team
>A little clueless on things that aren't related to fighting or tech, meaning that, more often than not, the members have to look after him because he himself won't
Park Seonghwa {Ivy}
[26 years old]

(based on Pamela Isley, Poison ivy)

Backstory: Moved to Seoultham at 17-18 to study biotechnology and plants there. He fell in love with his biotechnology professor and let her conduct experiments on him. After undergoing the experiment that permanently altered his DNA to that of a plant's, the professor lied about having an antidote and instead abandoned him and ran away. A 19 year old Seonghwa developed hatred of women and extreme trust issues, and started isolating himself and his plants from the world. For years, he hid away from society to learn about his new abilities, and would only leave his hiding places to go to bars to seduce people that he could bring home as food for his carnivorous plants. This was how he met Hongjoong, who had been bored and wandering the streets by himself. When trying to feed Hongjoong to his plants, he was taken aback by how the light-skinned man was more fascinated than afraid. Hongjoong talked about the Birds of Prey, and Seonghwa decided to join them. The two men bonded quickly due to shared experience and trauma of being betrayed and ruined by someone they admired.
>Certified plant biologist, works as a lab assistant at Okja Central College
>Knows and is friends with the old lady who owns Halazia Apartments, hence he stays in the basement from time-to-time
-the landlady and her daughter, Chungha, are the only women he's comfortable with (before meeting reader)
>When he's not fighting crime as Ivy, he's in his "human" form
-meaning most of the time, hes just a tall, thin and pale nerd with faded red hair, and very weak presence that is often ignored by people (in comparison to his true beauty as Ivy being too distracting and dangerous)
>Spends his free time experimenting with different plants and flowers, occasionally accidentally creates drugs that he gives to Hongjoong to sell for money
>Finds comfort in being able to look after the other members
(Park) Yeosang {Orphan}
[23 years old]

(based on Cassandra Cain, Orphan)

Backstory: His parents were contract killers from a secret society, and he was trained from a young age to be a highly-efficient killing machine. He was deprived of a normal childhood and did not fully learn to write or speak, hence his lisp when talking. Mingi had ran into a 19 year old Yeosang on accident while investigating the organisation's activities. He brought him back to the Birds of Prey because he felt sad seeing how isolated and hopeless Yeosang was with the organisation.
>Unregistered in Seoultham, or anywhere for that matter (hence the censored barcode in his profile card!)
>Spends his time either as a bodyguard for Hongjoong at New World, or following around Seonghwa and Mingi at Okja Central College
>Was only referred to as "Yeosang" while training with the secret society, so he doesn't have an official surname
>Was very quiet but clingy to Seonghwa when he first joined the team, leading to his cover story of being Seonghwa's younger brother (hence why he's sometimes referred to with the same surname 'Park')
>When fighting crime, nearly his entire face is covered
>Despite his unique and advanced set of skills, he dislikes using violence and often only uses it as a last resort
>Best fighter on the team
>Doted on and babied by the rest of the team
#ateez#ateez x reader#ateez fanfic#park seonghwa#ateez au#kim hongjoong#song mingi#kang yeosang#park seonghwa x reader#kim hongjoong x reader#kang yeosang x reader#song mingi x reader#ateez au crossover#atz fanfic#atz au
26 notes
·
View notes
Text
I've been thinking about Graces old team
And i realised this...
Agent Avery Stiller, is the only normal (neurotypical) member of the CASMIRC Advanced forensic unit.
Bitch ain't no way a unit, which a 21 year old joins and specialises in mutilation and burial and no-one bats and eye, is comprised of normal people. They fund their staff social functions with an Antisocial-Jar. And this is canon now that I've written it but their last Christmas party was hiring a stretch limo to go to Lazer tag and then an all you can eat Chinese hotpot place.
So far we know there's:
The liaison and coordinator Avery. We love him.
And that The team consults with Dr Boland from the Smithsonian, a forensic archeologist and anthropologist and her colleagues
Then there is also Grace's friends from the second floor she has mentioned, but not by name.
Someone who does the DNA and blood (a pathologist) -I imagine they are a kpop girlie for some reason.
a member who takes a peek at a raw mass spectrometer read out and just goes 'yep... Thats anthracite coal.' so we have a geologist and possible Edaphologist. (Living Soil expert) - I imagine this person is a champion Geoguessr.
So this is who else I imagine was part of the team but we haven't met:
A ballistics expert (guns and bullets) - is contrary to what you would think quite quiet personallity and more appreciative or the ingenuity of guns rather than the firepower, has flintlock pistol collection.
A handwriting analyst and linguistics expert - Karen energy from this one idk why, probably a grammar nazi.
A forensic physiologist and podiatrist (an expert in the way body's move and expert in footprints, shoe prints and gaits) - I imagine this person is older, the oldest member on the team and struggles with their computer and phone.
A chemical engineer and pyrologist (chemical damage and fire) - they are 100% a pyromaniac and have probably committed arson. Would be on the bomb squad if they passed the psych eval.
An entomologist (bugs and decomp)-who I imagine is incredibly salty that Grace identified the Sicarius Spiders before him
A technical analyst (a Garcia)- actually I do have a thought about this one, remember how the four horsemen hitmen had that kid they kidnapped and forced to run their darkweb stuff? Remember how the FBI offered him a job... Well I imagine he would end up here. (Another member of the FBI personally victimised by Cat Adams)
So Gee, Avery really is the living people expert because there is no way any of those people are going to appropriately empathise and socialise with victims or the field agents and police. (Maybe the physiologists cause they have a health care background) But they'd get on great with each other because they're all weirdos together.
So I wanted to extend an invite to you guys. If you guys want to add little head cannons, backstories or names for these team members, I'd love that, because I don't think we are going to see much of them in the story. It would be cool to have them sort of cameo here and there but also let you guys have a bit of fun and personal connection to these side characters who are very important to Grace.
Taglist: @bridgeoverstrawberryfields @cultish-corner @pleasantwitchgarden
#the protege#my fic#criminal minds fanfic#details from the protege#the protege: details#oc#avery stiller#grace matthews#dr boland
10 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Arachnoid
Part 2: Little Spider
At nine o'clock the next morning, Rory is sitting in her lab, face turned down looking into a microscope, thinking about a certain blonde woman.
"Gosh, she was beautiful," Rory mumbles to herself.
"Sorry, what was that? Didn't quite catch it," a raspy unfamiliar voice says.
"Oh, jesus!" Rory yells. She turns around, and standing there is the Black Widow. "W-what are you doing here at my place of work, M-miss Black Widow?"
"Hm, you're cute, Arachnid."
"Would you keep your voice down!" Her pitch is an octave higher than usual. "And it's Arachnoid. I resemble a spider. I'm not actually a spider. Oid, not id."
"Oh, okay. So like hemorrhoids," the redhead shrugs. Rory responds with a glare.
"What are you doing here? Shouldn't you be off saving the world or something?"
"Nothing to save it from at the moment. Thought I'd do a little digging to pass the time," she shrugs. "Rory Jade LaCroix. Born September 30, 1996. About 5'8", 150ish pounds. Your parents, James and Diana LaCroix, died in a car accident when you were seventeen, although that was likely a cover story. Your sister Hailey passed later that night in the hospital from her injuries. Three years ago, your girlfriend, Abby Smith, was murdered. You were the prime suspect. The case has since run cold. You have enhanced abilities such as super strength, web production, magnified senses, and even more that aren't yet on file."
Rory is tense and on edge at the mention of her family. Nobody talks about her family. "Alright, okay, I get it-"
"You attended Columbia University with a double major in Biomedical Engineering and Chemical Engineering. You also had minors in computer science, forensic science, and psychology. You really took advantage of that full ride they gave you, huh? Good for you, I respect that. Now you work here. Duquesne Scientific Advancements. They pay pretty well, but you're bored here, aren't you? Can't blame you. I've never been one to sit behind a desk, either."
"What's your point, Widow," Rory asks with a clenched jaw. "I already knew you were looking into me."
"Oh, you did? And how did you know that?" she quirks a brow. Rory doesn't let herself be intimidated, instead relaxing her shoulders and falling into a mindset of playful banter.
"Since you clearly know so much about me, why don't you tell me?" she smirks. If the redhead doesn't know about EDNA, she'd rather keep it that way. It could be quite advantageous. The Widow returns the smirk.
"You're quite a character, LaCroix. You could be a useful asset to us."
"And if I don't want to join SHIELD?"
Natasha bristles at the fact that Rory knows the name of the top secret organization, but she doesn't show it. Rory is extremely intelligent. She knows a lot more than she lets on.
"Well, it's your decision, of course. But I'm sure my sister would love to see you around more often."
"Sister? I don't know your sist– oh. You mean the blonde? From the other night?"
"Mhm."
"Huh. Um, well, I'll think about it, Miss Black Widow. For now, I should really get back to work."
"Alright, then. I'll see you soon, LaCroix." The redhead leaves the lab, and Rory lets out a shiver. That was fucking terrifying.
~
"She certainly didn't jump at the opportunity to join SHIELD," Natasha tells Nick. "But I think she'll come around. She's too smart for the job she has now. Too energetic. She's like a little puppy, it's disgusting. She wants to get out and do more good, I know it. And she's got a major crush on Yelena, so."
"Oh, joy. So you recruited a lovesick puppy?" Director Fury grumbles with a frown.
"Hey, this was your idea," she smirks.
"I suppose it was. What did you tell her?"
"I told her that I know who she is," Natasha shrugs, "And that she'd be useful here."
The Director hums in thought. "Don't lose her, Romanoff. I want this kid on my side."
~
"EDNA, who's she talking to?" Rory whispers as she watches the redhead move gracefully down the crowded New York streets.
"She is texting a contact saved as 'YB'. The text reads 'I'm being followed'."
"Oh, shit," Rory mutters.
"YB says 'By whom?' The target says 'A knockoff Spiderman'."
"Oh that is so rude," Rory whines.
"Would you like me to implode the cellular device? It will not kill her, but it will do some serious damage."
"No thank you, EDNA. That's very sweet of you, though."
Despite her cover being blown, Rory continues to move from rooftop to rooftop, wondering where the redheaded SHIELD agent will lead her.
The woman enters a worn down apartment building, and Rory watches from a nearby roof. After a few minutes, nothing happens so she moves closer. She uses her advanced hearing to locate the Widow's voice. Once she does, she crouches down on the fire escape, peeking in through the window. She listens intently to the conversation inside.
"How long was she following you?"
"I don't know. I didn't see her for the last few blocks. I think I might've lost her."
"Hm, or you're losing your edge and she's standing right outside that window," the blonde says, pointing to where Rory is currently crouched down out of sight. Every muscle in her body is tense, but relaxes when she realizes that they don't actually know she's there.
"Fuck off, Yelena." The sisters move onto a more mundane conversation as Rory drifts off into her thoughts. Yelena. It's nice to put a name to the face. Holy shit I feel like a stalker right now, she thinks to herself. Clearly they don't think Rory is a threat, she realizes.
She sighs, feeling like she's invading their privacy, even though she's just trying to protect herself. She moves to make her escape, and accidentally knocks over a potted plant that she hadn't seen. Oh shit. With her heart thrumming in her ears, she doesn't hear the footsteps approaching.
"Oh, come on! That was my favorite plant!" the blonde–Yelena–complains.
"Um...oops?" Rory shrugs. "I was actually just leaving, so..."
"Nuh-uh. Come inside. Come. We need to have a talk, little spider."
"Yes, ma'am," Rory deflates.
Masterlist
#yelena belova#florence pugh#natasha romanoff#yelena belova x oc#yelena belova x kate bishop#yelena belova x reader
41 notes
·
View notes
Text
Elizabeth francis dies at 115 years old
Forensic astrology reading

Crazy isn't it, to be able to live to be 115 years old! Elizabeth francis was born in St Parish, Louisiana, july 25th 1909. That's over 100 years ago.
What I know about ms francis is that she was a single mom, worked at a coffee shop in the 1970s, she never learned to drive but would take the bus and family to get from place to place, never smoke/drank but she says she ate everything lol. Her family recall her always cooking at home when they visited and think that the reason she lived so long is bc she took care of her body in that way. She also lived with her 96 year old daughter and granddaughter.
Elizabeth francis has lived through, 1909-2024.
Early Years (1909-1945) 1. World War I (1914-1918) 2. Spanish Flu pandemic (1918-1919) 3. Women's suffrage (1919) 4. The Roaring Twenties 5. The Great Depression (1929-1941) 6. World War II (1939-1945) Mid-Century (1946-1970) 1. Post-war economic boom 2. Cold War tensions 3. Civil Rights Movement (1950s-1960s) 4. Counterculture movement 5. Space exploration (1950s-1960s) 6. Moon landing (1969) Late 20th Century (1971-2000) 1. Vietnam War (1955-1975) 2. Watergate scandal (1972-1974) 3. Fall of the Berlin Wall (1989) 4. Soviet Union collapse (1991) 5. Internet and World Wide Web emergence (1990s) 6. Globalization and international relations 21st Century (2001-2024) 1. 9/11 attacks (2001) 2. War on Terror (2001-present) 3. Social media rise (2004+) 4. iPhone release (2007) 5. Global financial crisis (2007-2008) 6. COVID-19 pandemic (2020-2022) 7. Ongoing climate change and sustainability efforts Technological Advancements 1. Radio broadcasting (1920s) 2. Television (1940s-1950s) 3. Computers and internet (1970s-1980s) 4. Mobile phones (1980s) 5. Smartphones and social media (2007+) 6. Artificial intelligence and machine learning (2010s) Social and Cultural Shifts 1. Women's rights and feminism 2. LGBTQ+ rights emergence 3. Civil Rights Movement 4. Counterculture movement 5. Diversity, equity, and inclusion efforts 6. Shifts in family structures and relationships (Info above sourced by meta AI)
So today I wanna look through her birth chart to see if I find anything to attribute to her long life. I don't have her birth time so unfortunately this won't be as detailed as I would like but what I can do is see what kind of person she was that can explain any of her habits and things.
I also want to take a break from gruesome/unfortunate cases and lighten the mood with something more positive such as this story, a more natural death. An ending we all wish to have, a long lived healthy life.
For some reason I don't want anything to do with cruel cases atm, there's so many deaths that have happened in the past few years and it can all be so depressing and scary to think about, one of those cases being us one day. But yeah, let's get into this reading and brightening things up a bit.
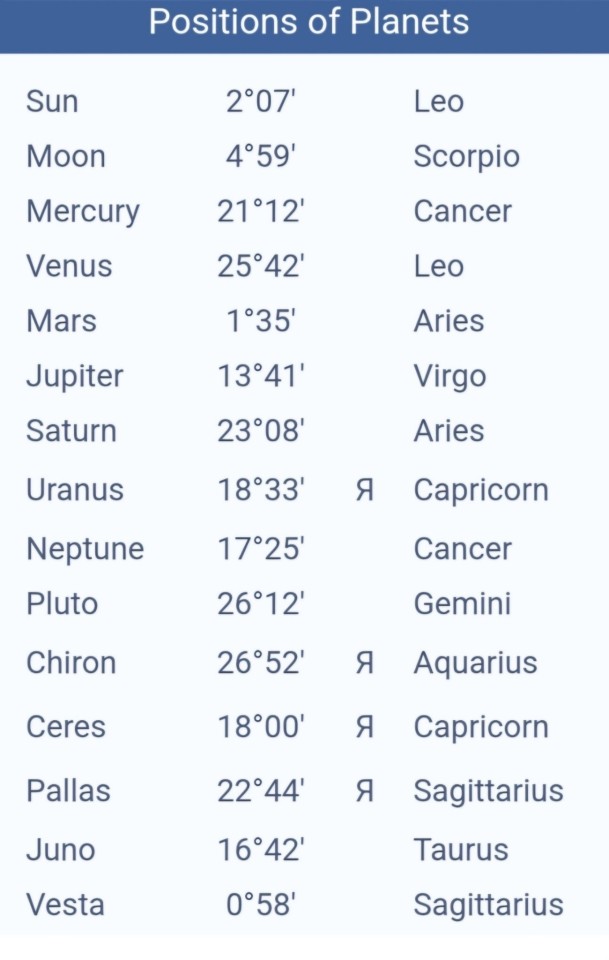

So what I'm getting from her chart right now is that she was always an easy going woman, didn't stress too much. Let's go more in depth tho.
Mercury conjunct neptune:
I love this aspect, this is similar to having a pisces mercury. She was a very intuitive person, this is not someone who would be overthinking too much, if anything she goes with the flow. She would be a good listener, be impressionable, sensitive, soft, spiritual, faith driven. She would be less logial and more emotion driven intellectually. This is good bc she would be emotionally intelligent and able to understand so many different things. She had an open mind, and was a flexible minded person.
Mercury opposite uranus:
This tells me maybe she was prone to being unpredictable at times, talking at random, traveling at random, random spurts of energy, not even she was in control of the wheel intellectually at times. She was someone who made a mark on others, maybe she had a unique way of communicating/thinking/traveling. Maybe at times she would be completely logical, versatile, adaptable to unpredictable, standoffish, independent, avoidant.
I have mercury square my uranus and this plays out as me being inappropriate at the worst times, like laughing in serious situations, saying things I shouldn't say, reacting/thinking/speaking in awkward/unpredictable ways. Imo people may view me as weird, annoying, rude at times, bc that's what you get when you have mercury in hard aspect to uranus, the planet of eccentricity, shock, unpredictability. Something about uranus also is that they don't usually do what everyone else is doing, so they are sometimes out of the loop. So this tells me maybe Elizabeth francis stayed out of the loop of some things compared to her peers and generation. She wasnt following trends or the "most traveled routes".
Mercury square saturn:
This tells me maybe she struggled with communication, activity, traveling, thinking. Maybe she had rigid thinking at times, had a tough time expressing herself in any way, vocally, creatively etc. Maybe she was sort of slow to think, or take action, but she was always determined to see things through. Maybe she could of been pessimistic and isolated herself. She may have also had a very rigid routine or way of doing things, she could of been a little controlling. Bc saturn restricts whatever planet it aspects, especially in harsh aspect but with the square here it tells me she wasnt one to sit and stay down, she would fight. So maybe she was aware of her limitations and potential, struggled to balance them out.
Sun trine mars:
This tells me she was healthy, active, assertive, confident, always youthful. She had good energy levels, she may have also enjoyed having new experiences, she was known for her martian traits. She has an aries mars so, she wasnt afraid of anything lol if anything she was the force to be reckoned with. She was direct, honest, open, childlike in a way, played no games. Passive aggression was not in her nature, so imo nothing really ate her up inside. She was the type of person to apologize when needed, say exactly how she felt, expressing herself honestly and fearlessly. I guess you can say that's very healthy for us to do bc if she had depression or introversion, maybe shed be internalizing things too much and that would cause illness like depression, chronic pain, mental health issues, digestive issues etc. So for her she was always vibrating high, no holding onto pain, trauma, bad vibes. She always had that youthful thing about her like I mentioned earlier. This is important bc if you always maintain that child like excitement, wonder, lust for life, than you are pushing yourself higher up into the world and not weighing yourself down to anything. Children don't have enemies, they don't sulk on their problems, they don't bother with stresses of life and all that, they just exist, play, adventure, they're pure and unafraid (before they become experienced adults).
Venus trine saturn:
This tells me maybe she was always respectful, kind, pleasant, took care of her body/appearance, she always wanted to look presentable and be respectable. She was charming in some way and authority figures liked her. So long story short, she made many friends and good business connections too. Maybe her father raised her well, with manners, discipline, somewhat people pleasing.
Venus sextile pluto:
This one is interesting to see in a chart bc I often see this in famous/rich peoples birth charts. This tells me she knew how to work hard, invest into things, make friends not enemies, she was very socially developed and knew how to attract wealth, power, loyalty, desires. She was a very magnetizing person, she was friendly, sweet, socially aware/intelligent, deep, loving, loyal. To me I feel like she was always working towards something, she wanted to be strong, powerful, impactful.. maybe it was just something she was naturally blessed with. I feel like she may have had a lot of support from others, family, friends, associates, etc.
Saturn sextile pluto:
I think this is the aspect ill attribute to her long life, if only I knew her house placements ugh. But what this tells me is that she was always a steadfast, consistent, dedicated, loyal person, but she was also strong, powerful, influential, self controlled. Maybe a lot of people trusted her and left a good impression on them, so she was able to weave herself into the lives of many people making her well known and thought highly of. Maybe people often came to her for help, wisdom, guidance, she was one of those people that others relied on heavily. This is giving me boss vibes also, like someone who is not just a servant to others (helping everyone else) but people also helped her too and respected her. Once you intertwine yourself in peoples lives like this, you become someone they can't live with out.. this is why I say this aspect could what's attributed to long life.
I hope that makes sense, saturn is responsibility, structure, steadiness, consistency, discipline, maturity, and pluto is debt, death, assets, transformation, power, control, sexuality, subconscious.
Venus biquintile mars:
This tells me she wasn't a cautious spender, but also wasn't reckless, she always trusted herself enough to be able to provide for herself and loved ones with whatever they needed. So she didn't have a poverty mindset imo, this is important bc it shows she may liked to indulge into things, go shopping, splurge, eat sweets, you know the pleasures of life, but she never shamed herself or struggled to keep up with her lifestyle. She always felt secure and confident.
What I got from all this, is that Elizabeth francis was a woman who lived authentically, freely, thoughtfully, fearlessly, kindly, friendly, passionately. She didn't hold onto to negative feelings for too long, she was active, adventurous, confident, pure intentioned. Maybe that's the key to a long life, don't hold back, don't be afraid to do what you feel, get in touch with your inner child/curiousity, work on your confidence by doing what you say you will do, be honest, make more friends than enemies. This allows you to always have people to rely on in your life, connection is not taken serious enough imo. Having family and friends around you keeps you fullfilled in all the areas you can't on your own. She was also disciplined, modest, never did too much of a bad thing. When you slow down and are mindful of yourself, that def helps to keep you balanced/steady in life. Every problem you have is way more manageable when you aren't inconsistent and reckless 24/7, you have to have some structure to always rely on. It's your structure that keeps you strong through the rain, wind, storm. Protect yourself, care about yourself, that's all. Thank you for reading <3
May you Rest In Peace Ms Elizabeth Francis

I'm glad you got to live my dream of a long life, maintaining your health for all those years, even being able to live to the end of your days with your daughter who's also elderly, that's such a blessing.
✨️Nine of Pentacles✨️
2 notes
·
View notes
Text
Oh btw I have absolutely no idea if there were DNA forensics in the 60s and TBH I don’t care one bit lmao I spend 20 minutes googling to make sure I don’t reference a car or a plane or a xerox machine that didn’t exist in the chosen year but this is SCIENCE FICTION BABEY. We don’t have desktop computers or cell phones or popularized color TVs or Skype but we can have whatever scientific and forensic advancements we want bc I’m the author and I say so 💗
7 notes
·
View notes
Text
Best Data Recovery Malaysia
The Superiority of SSD over HDD
When considering upgrading to a new SSD, it's important to understand the numerous advantages they offer over traditional HDDs. SSDs provide significantly faster data transfer rates, resulting in improved overall system responsiveness. Additionally, their lower power consumption leads to extended battery life, making them ideal for laptops. The absence of moving parts in SSDs not only increases durability but also ensures silent operation, unlike HDDs which produce mechanical noise during data access.
Data Recovery Malaysia
Furthermore, SSDs are lighter and more portable, making them a perfect choice for users on the move. These superior attributes position the new SSD as the preferred storage solution for modern computer systems.
Benefits of Switching to SSD
Switching to an SSD brings about enhanced system performance, minimizing waiting time for device usage and enabling smoother multitasking. Additionally, SSDs contribute to overall system cooling by generating less heat and result in faster software installations and updates, saving valuable time for users. With seamless data access, system lag is reduced, enhancing user productivity. The use of new SSDs and disk cloning software such as Macrium Reflect, Clonezilla, and MiniTool Partition Wizard is crucial for a successful transition from the old drive to the new one. Overall, the benefits of transitioning to SSD, whether for a new computer or upgrading an old one, are substantial and can significantly improve the overall user experience.
Data recovery KL
Pre-Cloning Steps: Getting Ready for the Process
Before initiating the cloning process, safeguard vital data to prevent loss. Check if the new SSD has the required space for data accommodation. Prioritize creating a backup of existing data to mitigate any potential loss during cloning. To expedite the cloning duration and streamline data management, clear disk space on the source HDD. Ensure the source HDD functions optimally to prevent cloning corrupted data.
Choosing the Suitable Disk Cloning Software
When selecting disk cloning software, finding a reliable and user-friendly solution is essential. Ensuring compatibility with both source and target disks is crucial for a seamless cloning process. Look for additional features such as disk partition management and a detailed guide for enhanced control and user assistance. The right software can make the transition to a new SSD, like the Samsung SSD, a smooth experience. Make sure to consider popular options like Macrium Reflect and MiniTool Partition Wizard, ensuring that the chosen software meets your specific needs and provides the necessary support for your cloning process.
Data Recovery Kuala Lumpur
#data recovery malaysia#data recovery#datarecoverymalaysia#datarecovery#data recovery center#datarecoveryservices#hard disk repair malaysia#recovery#data#malaysia
2 notes
·
View notes
Text
Decoding Cybersecurity: Unveiling the Future of US Digital Forensics Excellence
What is the Size of US Digital forensics Industry?
US Digital forensics Market is expected to grow at a CAGR of ~% between 2022-2028 and is expected to reach ~USD Mn by 2028.
Escalating cyberattacks targeting individuals, organizations, and critical infrastructure underscore the need for robust digital forensics capabilities. The increasing frequency and sophistication of these attacks drive the demand for advanced tools and expertise to investigate and respond effectively.
Rapid technological advancements, including IoT, cloud computing, AI, and blockchain, introduce new avenues for cyber threats. Digital forensics services are crucial to understanding these emerging technologies' vulnerabilities and mitigating associated risks.
Furthermore, stricter data protection regulations and compliance mandates necessitate thorough digital evidence collection, preservation, and analysis.
Organizations across industries has invested in digital forensics to ensure adherence to legal requirements and regulatory frameworks.
Additionally Legal proceedings increasingly rely on digital evidence. Law enforcement, legal firms, and corporations require robust digital forensics services to gather, analyze, and present evidence in a court of law, driving market expansion.
Us Digital Forensics Market By Type
The US Digital forensics market is segmented by Computer Forensics, Network Forensics, Mobile Device forensics and Cloud forensics. Based on type, Computer Forensics type segment is emerged as the dominant segment in US Digital forensics market in 2022.
Computers are ubiquitous in modern society, utilized across industries, organizations, and households. As a result, a significant portion of digital evidence related to cybercrimes and incidents is generated from computer systems, driving the demand for specialized computer forensics expertise. Computers and their software environments evolve rapidly.
Us Digital Forensics Market By End User Application
US Digital forensics market is segmented by Government and Defence, BFSI, Telecom and IT, Retail, Healthcare and Other Government and Defence market is dominant in end user application segment in Digital forensics market in 2022.
Government and defense agencies handle highly sensitive information related to national security and intelligence. The increasing sophistication of cyber threats targeting these entities necessitates robust digital forensics capabilities to investigate and respond to cyber incidents effectively.
Government and defense entities are prime targets for cyberattacks due to their critical roles. Effective incident response through digital forensics helps in containing and mitigating cyber incidents swiftly, minimizing damage and preventing further breaches.
US Digital forensics by Region
The US Digital forensics market is segmented by Region into North, East, West, South. In 2022, the dominance region is East region in US Digital forensics market.
The East region has a dense population and a well-established digital infrastructure, making it a hotspot for cybercriminal activity. The higher frequency of cyber threats and incidents necessitates a strong emphasis on digital forensics to investigate and mitigate these risks effectively. Additionally, the East region often sees a proactive approach from regulatory and legal bodies, reinforcing the demand for digital forensics services to ensure compliance and assist in investigations. The proximity of key players in law enforcement, government agencies, legal firms, and corporate headquarters further fuels the need for robust digital forensics capabilities.
Download a Sample Report of US digital forensics Solution Market
Competition Scenario in US Digital forensics Market
The US digital forensics market is characterized by a competitive landscape with several key players competing for market share. Prominent companies offering a range of digital forensics solutions and services contribute to the market's dynamism.
The competitive landscape also includes smaller, specialized firms and start-ups that focus on niche areas of digital forensics, such as cloud forensics, memory forensics, and industrial control systems forensics.
The competition is further intensified by the continuous evolution of technology, leading to the emergence of new players and innovative solutions. As the demand for digital forensics continues to grow, companies in this market are likely to invest in research and development to stay ahead of the curve, leading to a consistently competitive environment.
What is the Expected Future Outlook for the Overall US Digital forensics Market?
Download a Custom Report of US digital forensics market Growth
The US Digital forensics market was valued at USD ~Million in 2022 and is anticipated to reach USD ~ Million by the end of 2028, witnessing a CAGR of ~% during the forecast period 2022- 2028.
The US digital forensics market is poised for robust expansion due to the ever-evolving cybersecurity landscape, technological advancements, and regulatory pressures. Organizations across industries will increasingly recognize the necessity of investing in digital forensics to safeguard their digital assets and ensure compliance.
As long as cyber threats continue to evolve, the demand for sophisticated digital forensic tools, services, and expertise will remain on an upward trajectory.
The US digital forensics market appears promising, characterized by a confluence of technological advancements, increasing cyber threats, and growing legal and regulatory requirements. As technology continues to evolve rapidly, so does the nature of cybercrimes, creating a persistent demand for digital forensics solutions and services.
Additionally, the escalating frequency and complexity of cyberattacks. As more critical operations and personal information are digitized, the potential attack surface expands, leading to a higher likelihood of security breaches. This dynamic compels organizations and law enforcement agencies to enhance their digital forensic capabilities to investigate, mitigate, and prevent cyber incidents effectively.
Furthermore, the rise of emerging technologies like the Internet of Things (IoT), artificial intelligence (AI), and blockchain presents both opportunities and challenges. These technologies bring new possibilities for efficiency and connectivity but also introduce novel avenues for cyber threats. Consequently, the demand for digital forensics services is expected to surge as organizations seek expertise in unraveling incidents involving these cutting-edge technologies.
The market is also likely to see increased adoption of cloud-based digital forensics solutions. As more data is stored and processed in the cloud, digital forensic providers will need to develop tools and methodologies to effectively gather evidence from virtual environments, remote servers, and distributed systems.
2 notes
·
View notes
Text
Why a Bachelor's in Cyber Security is Your Foundation for a Future-Proof Career
The digital age has brought unprecedented convenience and connectivity, but it has also ushered in an era of escalating cyber threats. From sophisticated ransomware attacks crippling critical infrastructure to data breaches compromising personal information on a massive scale, the headlines consistently underscore a stark reality: our interconnected world is under constant siege. This urgent and ever-evolving threat landscape has created a monumental demand for skilled cybersecurity professionals. In this environment, a cyber security bachelor degree stands as the essential academic foundation for entering and thriving in this critical field, equipping individuals with the knowledge and abilities to safeguard our digital future.
Comprehensive Foundational Knowledge
A robust cyber security bachelor degree program is designed to provide a broad and deep understanding of core cybersecurity principles. Students delve into subjects like network security, learning how to build and defend secure network architectures. Ethical hacking forms a crucial component, teaching the methodologies used by malicious actors, but from a defensive perspective, enabling future professionals to identify vulnerabilities before they are exploited. Digital forensics equips individuals with the skills to investigate cybercrimes, recover compromised data, and piece together the narrative of an attack. Furthermore, the curriculum covers essential concepts such as risk management, allowing graduates to assess and mitigate potential threats, and incident response, preparing them to react swiftly and effectively when a security breach occurs.
Beyond these specialized cybersecurity topics, a bachelor's program also ensures a strong grounding in underlying IT concepts that are absolutely crucial for effective cybersecurity. This includes a thorough understanding of operating systems, the fundamental software that manages computer hardware and software resources. Networking fundamentals are explored in depth, providing the framework for understanding how data travels and how to secure its flow. Moreover, programming basics are often integrated, giving students the ability to understand and even develop secure code, and to automate security tasks, which is increasingly vital in today's fast-paced threat landscape. This comprehensive approach ensures graduates possess not only theoretical knowledge but also the practical skills necessary to navigate complex technological environments.
Direct Path to Entry-Level Roles
Earning a cyber security bachelor degree provides a direct and highly sought-after pathway into numerous entry-level and foundational roles within the cybersecurity industry. These positions are often the starting point for a rewarding and dynamic career. Common roles accessible with a bachelor's degree include:
Security Analyst: Monitoring systems for security breaches, investigating incidents, and implementing security measures.
Network Security Administrator: Managing and maintaining an organization's network security infrastructure, including firewalls, VPNs, and intrusion detection systems.
IT Auditor: Assessing an organization's IT systems and processes for compliance with security policies and regulations.
Computer Forensics Technician: Assisting in digital investigations by collecting, preserving, and analyzing electronic evidence.
SOC Analyst (Security Operations Center Analyst): Working in a security operations center, responding to security alerts and participating in incident response.
The demand for these roles is exceptionally high, driven by the global shortage of skilled cybersecurity professionals. This consistent demand often translates into competitive starting salaries and excellent opportunities for career advancement. Organizations across every sector—from finance and healthcare to government and technology—are actively seeking individuals with this foundational education to protect their invaluable digital assets.
Develop Critical Thinking & Problem-Solving
The very nature of cybersecurity demands strong analytical and problem-solving abilities. Cyber threats are constantly evolving, requiring professionals to think critically, adapt quickly, and devise innovative solutions to complex challenges. A cyber security bachelor degree curriculum is specifically designed to foster these essential skills. Through hands-on labs, real-world case studies, and project-based learning, students are challenged to:
Identify vulnerabilities: Learning to pinpoint weaknesses in systems, applications, and networks.
Analyze attack vectors: Understanding how cybercriminals exploit vulnerabilities and planning countermeasures.
Devise robust security solutions: Designing and implementing effective strategies to protect digital assets.
Respond to incidents: Developing systematic approaches to detect, contain, eradicate, and recover from cyberattacks.
This rigorous training goes beyond rote memorization, encouraging students to develop a deep understanding of security principles and apply them creatively to unforeseen situations. The ability to approach security challenges with a strategic and analytical mindset is what truly sets apart successful cybersecurity professionals.
Flexibility of Online Learning
For many aspiring cybersecurity professionals, particularly those with existing commitments or geographical limitations, the flexibility of online learning programs is a significant advantage. EC-Council University, for instance, offers a Bachelor of Science in Cyber Security that can be pursued entirely online. This allows students to study from anywhere in the world, fitting their education around work schedules, family responsibilities, or other personal commitments. Online programs often leverage cutting-edge virtual labs and collaborative platforms, ensuring that students still gain the practical, hands-on experience vital for the field without needing to be physically present on a campus. This accessibility opens the door to a cybersecurity career for a broader range of individuals, making this vital education available to those who might otherwise be unable to pursue it.
Ready to Build a Strong Foundation for a Career in Cybersecurity?
The escalating digital threat landscape is not merely a challenge; it is a profound opportunity for those prepared to defend against it. A cyber security bachelor degree offers more than just a qualification; it provides the essential knowledge, practical skills, and critical thinking abilities necessary to thrive in this high-demand, high-impact field. It is the foundation for a future-proof career, offering stability, growth, and the chance to make a tangible difference in protecting individuals, organizations, and even nations from the pervasive dangers of cybercrime. Ready to take the crucial first step towards becoming a vital defender in the digital realm? Explore EC-Council University's Bachelor of Science in Cyber Security program and lay the groundwork for a secure and prosperous future.
0 notes
Text
Photogrammetry Software Market Size, Dynamics, Market Growth & Trends 2032
Global Photogrammetry Software Market Overview The global photogrammetry software market is experiencing robust growth, driven by increasing demand for accurate geospatial data and 3D mapping across diverse sectors. As of 2024, the market size is valued at approximately USD 1.3 billion, and it is projected to reach around USD 3.5 billion by 2032, expanding at a compound annual growth rate (CAGR) of 12.5% during the forecast period. Key industries such as construction, mining, real estate, and agriculture are leveraging photogrammetry tools for site planning, surveying, and analysis. The widespread adoption of UAVs (unmanned aerial vehicles) and drones for aerial imaging and mapping is a major contributor to the market’s expansion. Additionally, improvements in computer vision, AI-based image processing, and cloud-based GIS platforms are enhancing the performance and accessibility of photogrammetry software. Global Photogrammetry Software Market Dynamics Market Drivers: Rapid urbanization and infrastructure development, increasing use of drones in surveying, and growing demand for digital twins in industrial sectors are primary drivers. The integration of photogrammetry with BIM (Building Information Modeling) and LiDAR systems is creating new use cases and efficiencies.Market Restraints: High initial software costs and a steep learning curve for new users limit adoption in smaller enterprises. In addition, data privacy regulations and strict compliance requirements across countries can restrict data acquisition and sharing, especially for government or defense applications.Opportunities: Emerging markets are opening up opportunities for localized mapping and urban planning. Remote sensing and satellite imagery integration with photogrammetry solutions are enhancing the potential of environmental monitoring and disaster response. The increased deployment of AI/ML in automation of 3D reconstruction is also a promising development.Role of Technology and Sustainability: Advancements in machine learning, cloud computing, and GPU-accelerated processing are revolutionizing photogrammetric workflows. From a sustainability standpoint, photogrammetry reduces the need for manual site visits and physical surveys, minimizing environmental impact and lowering carbon footprints associated with traditional surveying. Download Full PDF Sample Copy of Global Photogrammetry Software Market Report @ https://www.verifiedmarketresearch.com/download-sample?rid=10930&utm_source=PR-News&utm_medium=387 Global Photogrammetry Software Market Trends and Innovations Photogrammetry software is undergoing significant innovation. AI-powered automation is reducing manual processing time and increasing accuracy. Cloud-based platforms are enabling real-time collaboration and data sharing across teams. The adoption of open-source photogrammetry solutions is promoting innovation and reducing costs for small and mid-sized firms. Industry leaders are forming strategic partnerships to integrate photogrammetry with AR/VR platforms for immersive visualization in fields like architecture, gaming, and forensics. Furthermore, the use of multi-camera systems and real-time photogrammetry for live events and film production is expanding the market into creative industries. Global Photogrammetry Software Market Challenges and Solutions The market faces several challenges, including high software pricing models, lack of skilled professionals, and compatibility issues with legacy hardware or GIS systems. Data management and storage, especially for large-scale 3D models, is another significant concern. Supply chain issues related to drone hardware can impact project timelines.Solutions: Subscription-based and SaaS models are mitigating cost barriers for users. Enhanced user training and certification programs are being introduced to upskill the workforce. Interoperability features and plugin support in modern software versions are addressing compatibility concerns. Cloud-based storage and processing are solving data overload and latency issues.
Global Photogrammetry Software Market Future Outlook The future outlook for the global photogrammetry software market is highly promising. Increased investments in smart city development, digital infrastructure, and automation are expected to fuel growth. Asia-Pacific and Latin America are anticipated to witness substantial adoption due to rising demand in construction and urban planning. The market will continue to evolve with AI, real-time analytics, and edge computing playing a pivotal role. The integration of photogrammetry into broader geospatial intelligence ecosystems will further consolidate its importance across industries. By 2032, photogrammetry software will be a critical tool in achieving data-driven decision-making, virtual modeling, and sustainable development. Key Players in the Global Photogrammetry Software Market Global Photogrammetry Software Market are renowned for their innovative approach, blending advanced technology with traditional expertise. Major players focus on high-quality production standards, often emphasizing sustainability and energy efficiency. These companies dominate both domestic and international markets through continuous product development, strategic partnerships, and cutting-edge research. Leading manufacturers prioritize consumer demands and evolving trends, ensuring compliance with regulatory standards. Their competitive edge is often maintained through robust R&D investments and a strong focus on exporting premium products globally. Autodesk Pix4D Acute3D Photometrix Photogrammetry Software others. Get Discount On The Purchase Of This Report @ https://www.verifiedmarketresearch.com/ask-for-discount?rid=10930&utm_source=PR-News&utm_medium=387 Global Photogrammetry Software Market Segments Analysis and Regional Economic Significance The Global Photogrammetry Software Market is segmented based on key parameters such as product type, application, end-user, and geography. Product segmentation highlights diverse offerings catering to specific industry needs, while application-based segmentation emphasizes varied usage across sectors. End-user segmentation identifies target industries driving demand, including healthcare, manufacturing, and consumer goods. These segments collectively offer valuable insights into market dynamics, enabling businesses to tailor strategies, enhance market positioning, and capitalize on emerging opportunities. The Global Photogrammetry Software Market showcases significant regional diversity, with key markets spread across North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. Each region contributes uniquely, driven by factors such as technological advancements, resource availability, regulatory frameworks, and consumer demand. Photogrammetry Software Market, By Type • 3d Reconstruction Software• Based On Images And Video• Based On 3d Scanning Photogrammetry Software Market, By Application • 3D Printing• Drones and Robots• Films & Games• Culture Heritage and Museum Photogrammetry Software Market By Geography • North America• Europe• Asia Pacific• Latin America• Middle East and Africa For More Information or Query, Visit @ https://www.verifiedmarketresearch.com/product/photogrammetry-market/ About Us: Verified Market Research Verified Market Research is a leading Global Research and Consulting firm servicing over 5000+ global clients. We provide advanced analytical research solutions while offering information-enriched research studies. We also offer insights into strategic and growth analyses and data necessary to achieve corporate goals and critical revenue decisions. Our 250 Analysts and SMEs offer a high level of expertise in data collection and governance using industrial techniques to collect and analyze data on more than 25,000 high-impact and niche markets. Our analysts are trained to combine modern data collection techniques, superior research methodology, expertise, and years of collective experience to produce informative and accurate research.
Contact us: Mr. Edwyne Fernandes US: +1 (650)-781-4080 US Toll-Free: +1 (800)-782-1768 Website: https://www.verifiedmarketresearch.com/ Top Trending Reports https://www.verifiedmarketresearch.com/ko/product/ammonium-paratungstate-market/ https://www.verifiedmarketresearch.com/ko/product/limescale-preventer-market/ https://www.verifiedmarketresearch.com/ko/product/amorphous-silicon-market/ https://www.verifiedmarketresearch.com/ko/product/line-array-speakers-market/ https://www.verifiedmarketresearch.com/ko/product/anaerobic-membrane-bioreactor-anmbr-market/
0 notes
Text
Video Surveillance Hardware System Market: Strategic Developments and Forecast 2025–2032

MARKET INSIGHTS
The global Video Surveillance Hardware System Market size was valued at US$ 23.8 billion in 2024 and is projected to reach US$ 45.6 billion by 2032, at a CAGR of 8.5% during the forecast period 2025-2032. The U.S. market was estimated at USD 14.7 billion in 2024, while China is expected to grow to USD 22.1 billion by 2032.
Video surveillance hardware systems comprise essential components like cameras, storage devices, and monitors that work together to capture, store, and display security footage. These systems have evolved significantly from analog CCTV to advanced IP-based solutions featuring high-definition imaging, AI-powered analytics, and cloud connectivity. The camera segment alone is projected to reach USD 52.8 billion by 2032, growing at 9.1% CAGR.
Market growth is driven by rising security concerns across commercial and residential sectors, government mandates for public safety infrastructure, and technological advancements in AI-based surveillance. Recent developments include Axis Communications’ 2024 launch of thermal cameras with onboard analytics and Hikvision’s partnership with Microsoft to integrate Azure AI into their surveillance ecosystem. Leading players like Bosch Security Systems, Hanwha Techwin, and Avigilon continue to dominate the competitive landscape through innovation in edge computing and 5G-enabled devices.
MARKET DYNAMICS
MARKET DRIVERS
Rising Security Concerns and Crime Rates to Accelerate Video Surveillance Adoption
Global security threats and increasing crime rates are driving significant investments in video surveillance infrastructure. The global security equipment market continues to expand as organizations prioritize asset protection and public safety. Video surveillance systems offer proactive monitoring capabilities that deter criminal activities while providing crucial forensic evidence. Industrial facilities, transportation hubs, and government institutions are particularly investing in advanced surveillance to mitigate risks. This trend is further intensified by geopolitical tensions and the growing need for border security worldwide.
Technological Advancements in AI-Powered Video Analytics to Fuel Market Growth
The integration of artificial intelligence with surveillance hardware is transforming traditional monitoring systems into intelligent security solutions. Modern surveillance cameras now incorporate advanced features such as facial recognition, license plate detection, and behavioral analysis through machine learning algorithms. Edge computing capabilities enable real-time processing directly on cameras, reducing bandwidth requirements while improving response times. These innovations significantly enhance threat detection accuracy and operational efficiency across various sectors.
Moreover, the emergence of 5G networks facilitates high-speed data transmission, enabling more sophisticated remote monitoring applications. Cloud-based video surveillance solutions offer scalable storage and analytics, further driving adoption among SMEs and large enterprises alike.
Government Regulations and Smart City Initiatives to Drive Market Expansion
Governments worldwide are implementing stringent security regulations and investing heavily in smart city projects, creating substantial demand for surveillance hardware. Many countries now mandate video surveillance in public spaces, commercial buildings, and transportation systems. The allocation of substantial budgets for urban security infrastructure demonstrates the strategic importance of surveillance technology in modern governance and public safety management.
➤ For instance, several metropolitan cities have deployed thousands of surveillance cameras as part of comprehensive safe city programs, often integrating them with centralized command centers.
MARKET RESTRAINTS
High Installation and Maintenance Costs to Limit Market Penetration
While surveillance technology offers significant benefits, the substantial capital expenditure required for system deployment poses a major barrier, particularly for small businesses and developing regions. High-quality surveillance hardware demands significant upfront investment, with additional costs for installation, integration, and ongoing maintenance. The total cost of ownership extends beyond equipment to include network infrastructure, storage solutions, and software licensing fees.
Other Restraints
Data Privacy Regulations Stringent data protection laws in various regions create compliance challenges for surveillance system operators. Privacy concerns have led to restrictions on video recording in certain areas, requiring businesses to navigate complex legal frameworks when deploying surveillance solutions.
Cybersecurity Vulnerabilities The increasing connectivity of surveillance equipment exposes systems to potential cyber threats, deterring some organizations from adoption. Networked cameras and connected devices can become entry points for security breaches if not properly secured.
MARKET CHALLENGES
Integration Complexities with Legacy Systems to Pose Implementation Challenges
Many organizations face technical difficulties when upgrading or expanding existing surveillance infrastructure. Compatibility issues between new hardware and older systems often require additional investments in interfaces or complete system replacements. The migration to IP-based solutions from analog systems presents particular challenges in terms of network readiness and staff training.
Other Challenges
Storage Management The exponential growth in video data volume creates storage capacity and management challenges, requiring innovative compression technologies and efficient data retention policies.
False Alarm Rates Advanced analytics systems sometimes generate false alerts due to environmental factors or algorithm limitations, potentially reducing operational efficiency and user confidence.
MARKET OPPORTUNITIES
Expansion of IoT and Edge Computing to Create New Growth Avenues
The convergence of surveillance technology with IoT ecosystems presents significant opportunities for market players. Smart sensors and edge devices enable more distributed and intelligent security architectures. The ability to process video data locally reduces bandwidth requirements while enabling faster response times—particularly valuable for time-sensitive applications.
Emerging Applications in Retail Analytics and Business Intelligence
Beyond security, video surveillance hardware is finding new applications in customer behavior analysis and operational optimization. Retailers leverage advanced camera systems to track foot traffic, analyze shopping patterns, and measure promotional effectiveness. These commercial applications represent a growing revenue stream for surveillance solution providers.
The development of specialized surveillance solutions for vertical markets such as healthcare, education, and manufacturing continues to expand the addressable market for hardware vendors. Customized systems designed for specific industry requirements demonstrate strong growth potential.
VIDEO SURVEILLANCE HARDWARE SYSTEM MARKET TRENDS
AI-Powered Video Analytics Driving Smart Surveillance Adoption
The integration of artificial intelligence (AI) and machine learning (ML) into video surveillance hardware represents one of the most transformative trends in the security industry. Advanced analytics capabilities now enable real-time object detection, facial recognition, and behavioral pattern analysis, significantly enhancing threat detection accuracy. The global market for AI-based surveillance cameras is projected to grow at a CAGR of approximately 22% from 2024 to 2032 as enterprises and governments increasingly adopt these solutions. Edge computing has further accelerated this trend by allowing cameras to process data locally, reducing bandwidth requirements while improving response times for critical security events.
Other Trends
Shift Toward IP-Based Network Cameras
The transition from analog CCTV to IP-based network cameras continues to reshape the surveillance hardware landscape, with IP cameras expected to account for over 75% of total installations by 2026. This shift is driven by superior resolution capabilities (4K and beyond), easier integration with cloud platforms, and enhanced cybersecurity features. The industrial sector shows particularly strong adoption rates, with manufacturers leveraging networked surveillance for both security and operational monitoring purposes. Meanwhile, thermal imaging cameras are gaining traction in perimeter security applications, demonstrating annual growth rates exceeding 18%.
Cloud-Based Video Surveillance Gaining Momentum
Cloud-managed video surveillance systems are experiencing rapid adoption as organizations seek scalable, maintenance-free security solutions. These systems eliminate the need for on-premise servers while offering remote accessibility through web and mobile interfaces. The healthcare and education verticals are leading this transition, with cloud deployments growing at approximately 27% year-over-year. Cybersecurity remains a critical consideration, prompting hardware manufacturers to embed end-to-end encryption and multi-factor authentication directly into cameras and storage devices. Hybrid cloud/on-premise solutions currently dominate enterprise implementations, balancing data control requirements with operational flexibility.
COMPETITIVE LANDSCAPE
Key Industry Players
Market Leaders Expand AI and Cloud-Based Solutions to Gain Competitive Edge
The global video surveillance hardware system market features a dynamic competitive landscape, blending established security technology giants with agile innovators. Axis Communications maintains a dominant position, credited to its pioneering work in network cameras and intelligent analytics, holding approximately 18% revenue share in 2024. The company’s strength lies in its end-to-end solutions spanning cameras, recording devices, and AI-powered video management software.
Close competitors Hikvision��and Dahua Technology have significantly increased their market penetration through aggressive pricing strategies and government contracts, particularly in the Asia-Pacific region. These Chinese manufacturers now collectively account for nearly 30% of global shipments, leveraging China’s robust electronics manufacturing ecosystem and government-led Smart City initiatives.
The market has seen intensified competition following strategic acquisitions, with notable examples including Motorola’s purchase of Avigilon and Teledyne’s acquisition of FLIR. These moves have created integrated solution providers capable of combining thermal imaging, AI analytics, and traditional surveillance hardware into comprehensive security packages.
Emerging players like Verkada and Rhombus Systems are disrupting the market through cloud-native architectures, challenging traditional on-premise solutions. These companies recorded triple-digit growth rates from 2022-2024 by targeting the mid-market segment with subscription-based models and simplified deployments.
List of Key Video Surveillance Hardware Companies Profiled
Axis Communications (Sweden)
Bosch Security and Safety Systems (Germany)
Hanwha Techwin (South Korea)
Avigilon (Canada)
Teledyne FLIR (U.S.)
Honeywell International (U.S.)
Panasonic i-PRO Sensing Solutions (Japan)
Hikvision (China)
Dahua Technology (China)
Verkada (U.S.)
Genetec (Canada)
NEC Corporation (Japan)
Segment Analysis:
By Type
Camera Segment Dominates with Rising Demand for High-Resolution and AI-Enabled Surveillance Systems
The market is segmented based on type into:
Camera
Subtypes: Analog, IP, Thermal, PTZ, and others
Storage Device
Subtypes: NVR, DVR, and cloud-based storage
Monitor
Subtypes: LCD, LED, and OLED displays
Accessories
Subtypes: Mounting brackets, cables, enclosures, and others
By Application
Government Sector Leads Owing to Increased Security Spending on Public Safety Infrastructure
The market is segmented based on application into:
Government
Sub-applications: City surveillance, critical infrastructure protection, and border control
Industrial
Sub-applications: Factory monitoring, warehouse security, and remote site surveillance
Transport
Sub-applications: Traffic monitoring, vehicle surveillance, and smart parking
Commercial
Sub-applications: Retail stores, office buildings, and hospitality facilities
Residential
Sub-applications: Smart homes, apartment complexes, and gated communities
By Technology
IP-Based Surveillance Gains Traction Due to Network Connectivity Advantages
The market is segmented based on technology into:
Analog CCTV
IP-Based Surveillance
AI-Enabled Surveillance
Cloud-Based Surveillance
Regional Analysis: Video Surveillance Hardware System Market
North America The North American market is characterized by high adoption rates of advanced surveillance technologies, driven by stringent security regulations and increasing investment in smart city initiatives. The U.S. Department of Homeland Security has been actively promoting the use of AI-powered surveillance systems for critical infrastructure protection. Major players like Avigilon and Verkada have established strong footholds, providing integrated solutions with edge analytics capabilities. While analog systems are being phased out, the transition to IP-based and cloud-connected surveillance is accelerating. Data privacy concerns, however, remain a key challenge, particularly with increasing scrutiny on facial recognition technologies.
Europe Europe’s market is shaped by strict GDPR compliance requirements and a growing emphasis on cybersecurity in video surveillance systems. The region shows strong preference for hybrid solutions that combine local storage with cloud backup capabilities to meet data sovereignty rules. Countries like Germany and the UK are leading in adopting AI-based video analytics for traffic monitoring and retail customer behavior analysis. Recent terrorist threats have spurred additional public sector investments, though debates about surveillance ethics continue to influence procurement policies. Thermal cameras for fever detection have gained traction post-pandemic, particularly in transportation hubs.
Asia-Pacific As the fastest growing region, Asia-Pacific benefits from massive urbanization projects and government-led safe city programs. China dominates both as a manufacturing hub and end-user market, with Hikvision and Dahua capturing significant market share. India’s Smart Cities Mission has spurred deployment of over 1 million surveillance cameras nationwide, while Southeast Asian countries are upgrading coastal surveillance systems. However, price sensitivity remains high, driving demand for cost-effective solutions over premium features. The region also sees rapid adoption of 5G-connected cameras for real-time monitoring in dense urban environments.
South America Market growth in South America has been uneven, with Brazil and Chile showing more stable investments in surveillance infrastructure compared to economically volatile nations. Retail and banking sectors represent key demand drivers, though public sector projects frequently face funding delays. Chinese manufacturers have gained prominence by offering competitive pricing, while local players focus on customized solutions for specific verticals like mining and oil facilities. Power reliability issues continue to hinder system uptime, creating opportunities for solar-powered surveillance solutions in remote areas.
Middle East & Africa The Middle East leads regional adoption through massive smart city developments like NEOM in Saudi Arabia and Expo 2020 Dubai infrastructure projects. Gulf countries particularly favor high-end thermal and panoramic camera systems for border security applications. In Africa, South Africa remains the most mature market, while East African nations are investing in surveillance for port security and anti-poaching initiatives. Political instability in some regions creates demand for ruggedized systems, though budget constraints often limit deployments to essential infrastructure only. The lack of technical expertise continues to drive demand for managed surveillance services across the continent.
Report Scope
This market research report provides a comprehensive analysis of the global and regional Video Surveillance Hardware System markets, covering the forecast period 2024–2032. It offers detailed insights into market dynamics, technological advancements, competitive landscape, and key trends shaping the industry.
Key focus areas of the report include:
Market Size & Forecast: Historical data and future projections for revenue, unit shipments, and market value across major regions and segments. The global market was valued at USD 50.2 billion in 2024 and is projected to reach USD 89.7 billion by 2032.
Segmentation Analysis: Detailed breakdown by product type (cameras, storage devices, monitors), technology (IP-based, analog), application (government, industrial, transport), and end-user industry.
Regional Outlook: Insights into market performance across North America (36% market share), Europe (28%), Asia-Pacific (fastest growing at 9.2% CAGR), Latin America, and the Middle East & Africa.
Competitive Landscape: Profiles of 25+ leading market participants including Axis Communications (12% market share), Hikvision (18%), and Bosch Security Systems (8%), covering product portfolios and strategic developments.
Technology Trends & Innovation: Assessment of AI-powered analytics (adopted by 42% of new installations in 2024), 4K/8K resolution, cloud-based solutions, and thermal imaging technologies.
Market Drivers & Restraints: Evaluation of factors including rising security concerns (45% of enterprises increased budgets in 2024), smart city initiatives (USD 1.2 trillion global investment by 2030), and data privacy regulations.
Stakeholder Analysis: Insights for component manufacturers, system integrators, and government agencies regarding the USD 12.5 billion VMS software market opportunity.
Related Reports:https://semiconductorblogs21.blogspot.com/2025/06/inductive-proximity-switches-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/cellular-iot-module-chipset-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/sine-wave-inverter-market-shifts-in.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/pilot-air-control-valves-market-cost.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/video-multiplexer-market-role-in.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/semiconductor-packaging-capillary.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/screw-in-circuit-board-connector-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/wafer-carrier-tray-market-integration.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/digital-display-potentiometer-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/glass-encapsulated-ntc-thermistor.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/shafted-hall-effect-sensors-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/point-of-load-power-chip-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/x-ray-grating-market-key-players-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/picmg-single-board-computer-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/lighting-control-dimming-panel-market.html
0 notes
Text
ITM University, Gwalior
In the expanding landscape of higher education in India, ITM University, Gwalior, stands as a beacon of academic excellence, innovation, and holistic development. Located in the historic city of Gwalior, Madhya Pradesh, ITM University offers a world-class educational environment, combining modern infrastructure with traditional values. With a strong emphasis on career-oriented programs, multidisciplinary learning, and student development, the university is steadily gaining national recognition.
Established in 2011 under the Act No. 18 of 2011 of the Madhya Pradesh State Legislature, ITM University Gwalior is a private university approved by the University Grants Commission (UGC) and other professional bodies like AICTE, BCI, COA, PCI, and NCTE.
About the University
ITM University is a part of the ITM Group of Institutions, which has been involved in education and training since the early 1990s. ITM Gwalior was founded with the mission to provide high-quality education across multiple disciplines and to prepare students to meet global professional and entrepreneurial challenges.
Spread across a lush green campus of over 165 acres, the university offers a conducive learning environment with excellent academic facilities, student-centric resources, and a strong focus on research and innovation.
Academic Schools and Programs
ITM University Gwalior offers a wide range of undergraduate, postgraduate, diploma, and doctoral programs through its various schools and faculties. These include:
1. School of Engineering and Technology
Offers B.Tech, M.Tech, and Ph.D. programs in:
Computer Science and Engineering
Civil Engineering
Mechanical Engineering
Electronics and Communication Engineering
Artificial Intelligence & Data Science
Electrical Engineering
2. School of Management
Offers BBA, MBA, and Ph.D. programs with specializations in:
Marketing
Finance
Human Resources
International Business
Entrepreneurship
3. School of Law
Provides integrated law degrees like BA LLB, BBA LLB, LLB, and LLM programs, all approved by the Bar Council of India (BCI).

4. School of Science
Offers B.Sc. and M.Sc. degrees in fields such as Physics, Chemistry, Mathematics, and Forensic Science.
5. School of Computer Applications
Provides BCA, MCA, and research-oriented programs in data science, cybersecurity, and information technology.
6. School of Architecture and Design
Offers B.Arch and B.Des programs approved by the Council of Architecture (COA), with a strong focus on creativity, design thinking, and sustainable development.
7. School of Life Sciences
Offers programs in Biotechnology, Microbiology, and related life sciences disciplines.
8. School of Nursing & Health Sciences
Includes nursing, physiotherapy, and paramedical programs with clinical training in partner hospitals.
9. School of Education
Offers B.Ed and M.Ed programs approved by NCTE.
Admission Process
Admissions at ITM University Gwalior are based on:
Merit in qualifying exams (10+2 or graduation)
National entrance scores (JEE Main, NATA, CLAT, CAT, MAT, etc.)
University-conducted entrance exams or interviews for certain programs
Application forms can be submitted online via the university’s official website. Scholarships and financial aid are available based on academic merit, sports achievements, or financial need.
Infrastructure and Campus Facilities
The ITM University campus is known for its state-of-the-art infrastructure, advanced labs, and student-friendly facilities. The campus is designed as an eco-friendly and self-sustained academic hub.
Key Features Include:
Smart classrooms with multimedia tools
High-tech laboratories for engineering, biotech, forensics, and computer applications
Well-stocked Central Library with digital resources and journals
Design studios and architecture labs
Research and Innovation Centers
Cafeterias, hostels, and health clinics
24x7 Wi-Fi-enabled campus
Transportation facilities across Gwalior and nearby areas
Faculty and Learning Approach
ITM University boasts a team of highly qualified faculty members, many of whom are Ph.D. holders, researchers, and industry veterans. The university emphasizes experiential learning, project-based training, industry exposure, and skill development.
Regular guest lectures, workshops, and industry visits are part of the academic experience. Faculty also guide students in research publications, patent filings, and startup incubation.
Research and Innovation
The university is deeply invested in research and development, encouraging both faculty and students to work on real-world problems.
Dedicated Research and Development Cell (RDC)
Regular participation in Smart India Hackathon, National Innovation Challenge
Support for patent filings, product development, and research publications
Innovation labs for AI, IoT, robotics, and renewable energy
Placements and Industry Interface
ITM University has a strong placement record, especially in engineering, management, and computer applications.
Top Recruiters Include:
TCS
Infosys
Wipro
Capgemini
HCL
Cognizant
JustDial
ICICI Bank
Byju’s
Mahindra
Amazon Web Services (via partners)
Placement Highlights:
Highest Package: ₹12 LPA
Average Package: ₹4–5 LPA
Internship support from first year onwards
Career development workshops and mock interviews
The Corporate Resource Center (CRC) plays a central role in organizing placement drives, industry talks, and job fairs.
Student Life and Campus Culture
ITM University offers a vibrant student life filled with activities, clubs, and events. Students are encouraged to take part in both academic and co-curricular pursuits.
Campus Activities Include:
Annual tech and cultural fests like KRONOS
Student clubs for drama, dance, coding, entrepreneurship, photography
National Service Scheme (NSS) and NCC units
Regular sports tournaments, yoga sessions, and fitness camps
The university promotes a balanced academic and social environment, making the campus life dynamic and engaging.
International Collaborations
To provide global exposure, ITM University has established collaborations with universities and institutions in:
USA
UK
Germany
Australia
South Korea
These partnerships facilitate student exchange programs, dual degree pathways, joint research, and online global certifications.
Conclusion
ITM University, Gwalior, stands out as a multidisciplinary institution committed to nurturing future leaders, innovators, and professionals. With its industry-aligned courses, modern infrastructure, emphasis on research, and global outreach, the university is shaping students to meet the challenges of the modern world.
Whether your interest lies in engineering, law, design, science, or healthcare, ITM University offers the right mix of academics, skill development, and campus experience. For students seeking a progressive and supportive environment in Central India, ITM University Gwalior is a promising choice.
#ITMUniversity#ITMUniversityGwalior#StudyAtITM#PrivateUniversityIndia#TopUniversityMP#UGCRecognized#CollegeInGwalior#EngineeringCollege#CampusLifeIndia
1 note
·
View note