#cannot change gmail password on ipad
Explore tagged Tumblr posts
Text
aolmail.com sign up
Sign In To AOL Mail|AOL Mail Login|Create New AOL Mail Free Account
aolmail.com sign up is a well-known American free web-based email service provided by AOL, a division of Verizon Communications. To be able to use the email service by AOL, you should have got your own account. If you decided to go the alternate email route, then you should open the email you used and check for a message from AOL. Logging into AOL email account is an extremely simple task.|AOL Mail is the email service offered by AOL. The service is sometimes referred to as AIM Mail where AIM” stands for AOL Instant Messenger. So, let me show you how to sign in AOL email account. This is a very formal login process where one have to enter the details like your email ID and then you get the access of all the products of AOL and then you have to create a strong password to protect it.|AOL Mail is one among the well known free online email administrations drawn from the establishment of AOL, AOL set up in the year 1993, AOL email benefit is the best one among alternate messages which are utilized by the a large number of individuals over the globe. Aol mail has also other Best Features which you will be going to love. The email service comes with free and unlimited storage space capacity. Alternative Email - One have to enter an alternative email to recover it when you lose the password. Finally, Gmail displays the participants in an email conversation on the right of the screen, along with recent photos they've shared with you.
AOL Mail Login, Sign Up Aol Mail Www.aolmail.com|Aol Mail Sign Up, Create New Account, Registration Page|(Covers IOS7 For IPad Air, IPad 3rd
There is no need to give any formal details about AOL mail because this is one of the popular webmail. AOL Mail (stylized as AOL Mail.) is a free web-based email service provided by AOL, a division of Verizon Communications. AOL mail is still regarded as one of the best email service providers. In less than 2 minutes, your AOL Mail Account gets created. Yahoo also offers Enhanced Contacts, which displays your contacts' recent messages, shared photos and attachments in addition to standard contact information, such as email addresses and phone numbers.|AOL Mail is not only a free webmail service, but also a popular webmail service in the world. Provide the username to sign into account security page. Type your aol mail sign username (screen name) or your full @ email address. The Signup page will be there asking you to enter your personal details such as First name, last name, expected Username on this platform, Birth date, mobile phone number, Gender, etc.|If you're unable to aol login your aol mail account or are can't create a new one, then you will see errors such as incorrect username or password,” or cannot create a new account”, and more. Just follow the complete guide of AOL mail login account to access your account. I am not able to sign onto AOLMail. You have to provide country code before entering the mobile number. Aol mail login mail, often known as AIM mail, can be a free email service furnished by America Online.
Login is for users who already have an account and want to access their account. Use web address for accessing your AOL account. AOL com email has a spell checking option. Gmail, Yahoo Mail and AOL Mail feature interest-based advertising - in essence, the services scan your emails for keywords and then use that data to load relevant ads.|If you are an existing user of this service, you can enter a Username and Password to login. Having an AOL email account helps your business to flourish in many ways. This matter reveals you learn how to create an account and import messages and settings in order that you can start utilizing Opera Mail.|The most frustrating situation is when you try accessing your AOL email but an unusual error appears, showing that your login credentials are wrong. You can also manage the Sending” option for the sender you want to send the emails. Email and texting allow users to convey essential information.
You can access your AOL email account at free of cost. Now, there are different methods which you can use to recover your AOL Mail's Password. Receiving an error message that AOL mail sign in now cannot happen. An AOL email is a service from AOL that is free and web based.|Like wise, we also have AOL Webmail Service. In the Connect your account dialog box, enter your Display name, AOL Email address, and Password. Finally, proof that you are real human creating AOL email account. Besides two-step verification, features a recovery code that you can use if you lose access to your security information (your phone number and an alternate email address).|Now, email addresses simply aren't cool, and we don't think AOL can do much to change that. Spam Protection and Virus Protection are additional features of AOL Mail. This was discontinued by AOLmail sign in on December 15, 2017. 4:- Now, enter all the details in the signup form to create a new AOL account.
2 notes
·
View notes
Text
New Way To Know I Forgot My Gmail Password Online
Recoup Google account, discover how to recuperate Gmail nameless phrase tips and clues past you have a obsession to recoup your unnamed key, acquire dash path, a notable unmemorable gmail forgot password recovery key chief, and never lose it in any case. photo album recuperation Google is quite great at giving its clients the approaches to recoup their information, Gmail secret word recuperation is a breeze on the off unintended that you gave enough security data during sticker album enrollment. The principal matter you craving to attempt is Google's cassette recuperation page. pick the "I don't have the foggiest idea nearly my unknown word" every other and enter your Gmail address, click upon proceed. In the situation that you partnered a telephone number to your Gmail account, you can request a affirmation code sent in an instant broadcast or you can dwelling security inquiries below "check your personality" area. on the off unintended that you overlooked your email residence and haven't set happening any recuperation data, for example, a telephone number or security questions, you may in any engagement have the substitute to discover your username in the situation that you have as of tardy utilized your email account in your internet browser. Quest your internet browser archives for inbox or Gmail to check whether it uncovers your location. In fact, your full email quarters or the initial segment of it back the setting is your username.
Gmail Password Recovery
In the matter that you don't admittance your recuperation email, telephone, or further unusual you may in any raid have the unconventional to recoup Gmail undistinguished key by physically checking your personality. First matter you have to reach is visit the Google account recuperation page. Whenever there, enter your email quarters and snap "proceed". Snap "I don't have the foggiest idea" unusual for the ordinary key and pick the "check your character" choice, which is a little association under all further accessible alternatives. answer every one of the inquiries as far afield as you could possibly know and in the issue that you can present the data that is precise ample you'll acquire a fruitful Google account recuperation. Google account recuperation later than perform change gmail password Google accounts, g suite or Google applications, it might be simpler to reestablish your collection access, as you can generally admission the running of your tell to reset your ordinary key and recover your record. Ensure your guidance today. The best Google account recuperation strategy is normally failing to lose any information. Things brute what they are, how to guarantee a 100% Gmail recuperation? We recommend utilizing instruction security and recuperation arrangements that can save track upon your document comings and goings and can recoup fortuitously erased information. dish drill is a splendid recuperation application that offers release assurance for all your ordinary word director documents, outdoor and inward opinion stockpiles. find the money for us a unintended to pressure this security and recuperating ensured counsel is forgive as soon as circle drill for Mac! even though circle drill can't recoup your Gmail unexceptional phrase legitimately, it might back in recuperating your shadowy phrase stockpiling on the off chance that it was out of the blue lost. Plate drill deals in the manner of your circle wellbeing, screens it intently and will reprimand you if there is a plausibility of any dish disappointment. It gives you a unintentional to discover copy documents, clean some plate expose and offers unquestionable reinforcements. moreover to Gmail recuperation you can gain by workstations and put it on areas, iPhone/iPad/iPod, enlightened cameras, interior and outer hard drives, USB blaze drives, and android gadgets (established) recuperation. Presenting the collection recuperation structure is the best realizable way in to approach Google in these cases. answer all number inquiries as would be prudent, and ensure the take control of responses are correct or near it. In the situation that unclear more or less an answer, offer the best conjecture. For instance, your cd more likely than not been made simple the date you bought the telephone. You can check your receipts for a surmised date. upon the off fortuitous that you have utilized your book fairly effectively, you ought to have the complementary to recall or theory behind sensible exactness the responses to every other inquiries. Out it an attempt and perceive how things tilt out. You can't be any more unpleasant off than you as of now are. My all the best in imitation of you. You would infatuation to know some data approximately the cassette to start the recuperation procedure and stir responsibility for record. In the concern that you don't recollect any recuperation email address, or didn't enter any during set-up, or don't recall significant recuperation data and dull phrase, at that reduction you'd have to ask any right to use you've sent messages to verify what the username is. as soon as you get affirmation, you can log on making an commotion to recoup that account. select the principal choice, I don't have the foggiest idea very nearly my ordinary key. Enter the herald of Gmail account.
Learn From Introduction
Are you thinking to reset my Gmail password when you don't remember my recovery information? Unsurprisingly, Google has unconditionally unquestionable account security. accompanied by the finest in the world, in fact. If you have at a loose end or forgotten your Google/ Gmail password, or if your account was hacked, you have exactly one pretension to get put up to into that account. The automated process that starts here. Ive answered variations on this additional get older and places, and supplementary a lot of supplementary detail. But it every adds up to the thesame thing. If you have a g suite account thru a issue or school, you can call your administrator. If you own a g suite hosted domain (cheaper and easier than you think, and worth doing) or if you are an paperwork on a domain, then you can call tech preserve at Google, directly. Theyre genial 24/7, and trust me, they are good. But in the manner of a clear Gmail account, if you acquire locked out, you absolutely cannot right to use a human swine at Google practically it. You cant call, text, email, snail mail, carrier pigeon or pony tell them. next set up 2-step verification, using every feasible safety option, including printing your recovery codes and stashing them in several places. Used properly, step can and will prevent your account getting hacked. You are taking someone out for a date and you don't know what type of restaurant she fancies and you air awkward asking her. Just say, guess what restaurant I'm taking you to . She will declare a place; every you have to reach is proceedings surprised and say, how did you know? There is a supplementary product, Google one. It offers new account storage - and tech support, for Gmail addresses, including conscious phone support. Which of course made me unquestionably eager if this could be used to unlock accounts. thus subconscious as I already pay for new storage and was so automatically enrolled in Google one, I filled in the little form, and had them call me. And the respond is no. The tech maintain folks you can accomplish as soon as the Google one further complete indeed feint for Google. But they attain not (and cannot!) manage to pay for any instruction for locked out accounts, supplementary than to saunter you thru the automated process. If that process fails to get you in - you in limbo the account. Side issue: the excuse there are consequently many collapsed answers here is because there are a ton of scammers out there who want you to call them, and they pretend hard to get their friends into quora answers. They will with use all trick there is to convince you they are somehow affiliated in imitation of or sanctioned by Google. They arent. They can by yourself use the thesame automated process I amalgamated above - and court case you fine allowance for appear in something you can get yourself. Again, there is by yourself reset gmail password one way to recover a release Gmail/Google account. If you cant get in using that process, you in limbo the account, forever. thus the best advice I can offer you is to purposefully go thru the security checkup process upon your Google account page. You can set going on a recovery phone number and email address. I strongly recommend you use both, and create the recovery email habitat one that belongs to a close relatives aficionado or obedient friend. Not one of your own, that you may forget or lose!
Summary
Also set taking place verification, using every doable safety option, including printing your recovery codes and stashing them in several places. Used properly can and will prevent your account getting hacked. You are taking someone out for a date and you don't know what type of restaurant she fancies and you setting awkward asking her. Just say, guess what restaurant I'm taking you to. , I filled in the little form, and had them call me. And the answer is no. The tech maintain folks you can attain how to recover gmail password when the Google one serve attain indeed action for Google. But they complete not (and cannot!) pay for any instruction for locked out accounts, extra than to saunter you thru the automated process. If that process fails to get you in - you at a loose end the account. Side issue: the defense there are correspondingly many collapsed answers here is because there are a ton of scammers out there who desire you to call them, and they decree difficult to get their contacts into Quora answers. They will with use every trick there is to convince you they are somehow affiliated once or sanctioned by Google. They arent. They can lonely use the same automated process I partnered above - and feat you fine grant for behave something you can realize yourself. Again, there is and no-one else one way to recover a free Gmail/Google account. If you cant get in using that process, you drifting the account. She will make known a place; all you have to accomplish is war amazed and say, how did you know? as soon as bothersome to acquire as much guidance as practicable from someone during a conversation, whenever they discontinue and seem to have said every they designed to, resist the temptation to say all and otherwise node attentively and see them in the eye. They will continue talking and say you as much as you habit to know. If the professor asks a question that would embarrass you in tummy of the class if you attempted to answer, or the boss demands for suggestions during a meeting and you obviously have nothing in mind, but he looks at you as if expecting to listen something from you, straightforwardly position your perspective and look at a colleague. He will subconsciously follow your gaze and ask the person you looked at. The social dominoes effect. If incharge of a bureau and you are wondering how you can get them to reach something you want, create it look gone everyone else is play a role it even if no one actually is. This creates an unreal peer pressure and gets people upon board. To growth your odds of getting the upper hand at a bargain, appreciation your head everytime you present your suggestion. The other party will easily attain in imitation of your offer. If you are the kind of person that people don't once to recognize seriously and you in fact compulsion to steer a narrowing across, handily tell what you desire starting in the same way as a phrase when roosevelt later than said that... or as with opined... . create it sound similar to those were the opinions of a renowned person and they will gain credibility.
1 note
·
View note
Text
Essential IT Infrastructure for a Small Business Setup

If you're reading this, you are in the process of taking your business from an idea you've talked to a few people about to something to make some serious money from.
What I'll cover will give you all the essential knowledge to cover at least 5 employees. This setup will run and run, and when you finally hire an IT person, they'll be able to take over effortlessly (and possibly question whether they're really needed).
Laptops and Desktops
First you need to decide between a desktop and a laptop. I would strongly advise on a laptop, as this gives you the portability you might need, and you don't have to plug anything aside from the charger in. Simple and straightforward.
Internet Connection
The first thing you'll need to make your system work is an internet connection. It can be through a mobile, cable, or ADSL. All are great, when used appropriately, but you need to choose one to start with.
For any office of ten or less people, you will be very comfortable with an ADSL connection from whoever the cheapest and best reviewed provider in your area is. You'll want to ask for a static IP when you set it up, and be adamant that you need one. Right now, it's not important, but it might be down the line and it'll save you time later on. Some services will charge a little more for this, so I suggest shopping around.
In terms of speed, the speed that's quoted on advertisements (for example 20Mb) is how fast you can get stuff from the Internet, and is mainly what we're concerned with at this point. Uploading will generally be a much smaller number, perhaps 512kbps, but generally the amount of traffic you'll be sending back to the internet is minimal.
You should look for bandwidth caps: some service providers will either restrict your speed, or cut off your connection all together when you've downloaded too many files from the Internet. This is less common now, but important to ask about.
Email, Calendaring, and Contacts
A lot has changed over the last six years, with the focus being to move away from having a mail server all of your own, to using one managed by someone else (also known as 'moving to the cloud').
There are only really two players in this field: Google, and Microsoft.
A lot of IT consultancies will push you towards a Microsoft Small Business Server, which whilst it can appear attractive is very expensive both up front, and in the long term when you move away from it. I cannot advise you enough to stay clear of this product.
If you're still stuck on the idea of Microsoft, most IT consultancies will be delighted to offer you a hosted Exchange server, but at its cheapest, this will be 100% more expensive than the next offering, which provides everything hosted Exchange does, and more.
The key innovator in this area has been Google: initially, they launched their incredibly popular Gmail product, which popularized the idea of threaded conversations and a lot of space for free. This, coupled with unobtrusive advertising and a clean interface took them to being probably the biggest provider of email today.
Office Suite and Note Taking
Office Suite
If you've opted for Google Apps, you've already got your office suite set up: it doesn't have every feature of either iWork or Microsoft Office, but it has so many that for free, there's very little point in going further initially. It has capability for word processing, spreadsheets, slideshows, drawings, and very neat data collection tables (useful for emailing a questionnaire, or posting one to a website).
But let's say you need more: you're trying to produce a very complex layout for a flyer, or you have a fiendish spreadsheet that Google Docs just can't quite handle. Microsoft has very carefully written its office suite for Macs, and it works very well. Apple has its competitor platform, iWork, which for an extra charge ties in very neatly with iWork on your iPhone or iPad if you get one. You can buy Microsoft Office for Mac (traditionally Microsoft awards odd years to Apple and even to Windows) from anywhere else that sells software, or you can buy iWork from the App Store on your Mac. The advantage of the App Store approach is that you'll have it installed and ready in a few minutes. For Pages, Numbers, and Keynote the total is £42, but each application is purchased individually for £13.99. Office for Mac runs to around £150 or so, and you'll need to use a DVD drive to install it.
Any files that you create should be saved somewhere that's backed up, for example your Dropbox (keep reading... ).
Note Taking
Note taking is useful. Synchronised note taking across Mac, Windows, iPhone, and Android a web browser-based client is even more useful. The chosen product in this category is Evernote, which for free gives you a generous account, and if you upload a photo (of a business card, for example) you can later find that picture by searching for text in it. You can share notebooks with other people, which is excellent for building a shared repository of information. These notebooks can also be shared to anyone on the Internet, although this is completely at your discretion.
Evernote will let you encrypt pieces of text, so it's very useful for saving passwords to. Select the text, right-click, and choose encrypt.
Evernote is also an excellent place to store your documentation.
Shared Storage
So now you have your Internet connection, your computer, and you're able to send people emails, you'll probably find you want a space to store your files.
My first recommendation for a startup will always be Dropbox. Dropbox is a small piece of software that runs on your computer, and watches a special folder, called Dropbox. It's available for Windows, Mac OS X, Linux, iPhone, Android and Windows Mobile. Every time you add a file to that folder, or make a change to it, that file or those changes are written back to the central Dropbox servers.
A free account will give you 2GB of space, and will keep any changes you make to a file for the last 30 days, turning it into your personal time machine for everything stored in there. If you delete a file you can restore it immediately.
Additionally, you can have a shared folder with someone, which means that the folder on your computer you've shared with them is a mirror image of the same folder on theirs. You can see when they're working on a file, and vice versa. As soon as they save changes, these changes are replicated across to your computer.
Finally, there is a special folder in your Dropbox, called Public. Anything you put in here can be shared with someone else by emailing them a link to the file. This is an excellent alternative to emailing large attachments, or using FTP servers (fantastic for artwork files, for example).
If you pay Dropbox, they'll give you more than 2GB, and instead of saving changes to your files for the last 30 days, they'll save them forever, which can be useful if you need to show a chain of work.
For a more serious, server-like approach to file serving, I suggest buying a Synology disk station. Synology make incredibly user-friendly self-contained servers that can hum quietly to themselves in the corner of a room without anyone noticing. They have support for something called RAID, which means that if a disk fails, you can just slide out the broken one and replace it with a new one. They have built-in virus scanning for peace-of-mind (although you do have to enable it), and can function as a web server if you ever need to.
Remember when you buy a Synology, you need to buy the hard drives separately: you don't have to buy enough to fill your device at once, but you do need to buy at least one to be able to use it business setup in dubai.
1 note
·
View note
Text
How to block emails in mac mail

#HOW TO BLOCK EMAILS IN MAC MAIL HOW TO#
#HOW TO BLOCK EMAILS IN MAC MAIL PRO#
#HOW TO BLOCK EMAILS IN MAC MAIL PASSWORD#
On your inbox, please find and select an email from the address that you want to block from your iPhone or iPad. Open an email from the address that you want to block.
#HOW TO BLOCK EMAILS IN MAC MAIL PASSWORD#
Please visit on your computer, enter your email address and password to sign into your Gmail account, then open your inbox. Besides, you will not receive the notifications from the new emails from blocked email addresses, too.
#HOW TO BLOCK EMAILS IN MAC MAIL HOW TO#
To block email address on Gmail, this method will show you how to prevent receiving mails to iPhone inbox from blocked email addresses, while you can still check the emails from blocked addresses in Spam folder. How to Block Email Addresses on iPhone When Using Gmail
#HOW TO BLOCK EMAILS IN MAC MAIL PRO#
Tip: To completely and permanently delete caches, temp files and any other traces on iPhone from unwanted mail address, it is highly recommended to erase data on iPhone 11/11 Pro/11 Pro Max/XR/XS/XS Max, etc. Although you can't block email addresses within the Mail app or any other email app for iPhone, all email addresses that you have blocked from your inbox on computer will be blocked on your iPhone or iPad, too. You are about to learn how to prevent emails from a specific email address from showing up in Mail app of your iPhone/iPad. This article will show you how to block emails on iiPhone 11/11 Pro/11 Pro Max/XS Max/XR/XR/X/8 Plus/8/7 Plus/7/6s Plus/6s/6 Plus/6/5S/SE or iPad to help you solve this problem. However, if you are constantly harassed by advertising mails, spam mails or unwanted mails from some persons, you can block certain email addresses to stop receiving such harassment. In addition to facilitating our use of telephone and short messages, iPhone also allows us to send and receive emails anytime and anywhere, which is of great convenience for our work and life. How to Block Mails on iPhone When Using Microsoft Outlook Mail How to Block Mails on iPhone When Using Yahoo Mail How to Block Mails on iPhone When Using iCloud Mail Please help! I can't stand getting bogus emails all day long!" The block on my PC did the job, but for some reason, my iPhone and iPad cannot tell the difference. "I blocked a ton of emails from Outlook on my work PC but they still come to my iPhone and iPad. Q: How do I block junk mail from going to my iPhone and iPad? "Other than bouncing back to sender, or changing my email address, putting them in junk mail or a file, how do I block my abusive ex from sending me unwanted emails?" Q: How do I block an unwanted email sender?

0 notes
Text
How to Solve the "Can't Receive Email On iPhone" Issue
Apple is very careful to provide its users with everything they need and minimize the usage of third-party applications. Unlike Android users who most probably have Gmail installed together with the mail app native to their device, iPhone’s Mail App is usually more than enough.
It allows multiple accounts and separate inboxes, and just sometimes, it doesn’t work properly. If you are a loyal iPhone owner, you have probably experienced an issue where you can’t receive emails on your iPhone. Luckily, there are a few things you can do.
Preparation Steps

There are a few pre-steps to successfully troubleshoot the problem when you can’t receive emails on your iPhone.
Obviously, you need to make sure your device is connected to the internet. It doesn’t matter if you choose your cellular network or Wi-Fi, all you need is a stable internet connection.
The second step is to try and log into your email from a different device. You can try logging in on your Macbook or Ipad and see whether you can read your emails there.
Also, check if the problem lies with the email service provider and not your device. Sometimes their servers experience a temporary downtime and because of that, you can’t receive emails on your iPhone.
If you are certain the problem isn’t with your email service provider and you are connected to the internet, you are ready to troubleshoot your iPhone’s Email App.
Wrong Credentials When You Can’t Receive Emails on Your iPhone
The most usual solution when you can’t receive emails on your iPhone is to check if your email address and password are incorrect. This happens if you changed your credentials on another device and you were automatically signed out from the Email App on your iPhone.
This can also happen if you just bought a new iPhone and you forgot to log into your Email App. Make sure you enter the password correctly and you should be on your way to reading emails on your iPhone.
No Push Notifications? Enable Fetch
Most email providers today support push notifications. However, if your provider doesn’t, Mail App cannot notify you about a new email. Hence, it may seem like you cannot receive emails on your iPhone.
The fix for this is simple. You only need to enable Fetch, a feature through which your phone will retrieve emails in regular intervals.
Navigate to Settings
Tap on Passwords and Accounts
Scroll until you reach Fetch New Data and tap on it
There you can enable Fetch and control how often you want it to occur.
Note that if you want to save battery and prolong its life, you should fetch less often.
You Can Also Visit PAIRMobile if You Can’t Receive Emails on Your iPhone
Another quick solution is to visit PAIRMobile and let us repair your iPhone. Problems with email applications, even when more elaborate, are fixed quickly. By the time you finish a relaxing cup of coffee, your iPhone will work as good as new.
If you have any questions about a repair or our new arrivals. Don’t hesitate to contact us at any time.
0 notes
Text
Theft-Proof Your Mobile Data
Theft-Proof Your Mobile Data

October is National Cyber Security Awareness Month. What would your company do if a company device was lost, or even worse, stolen? Do you have measures in place to protect the data on the device? This is part 16 in a series of blog posts we will be publishing on various topics aimed at educating you on how to stay protected on today’s Internet landscape.
What would the risk to your company be if an employee’s smartphone or tablet were lost or stolen? If the device holds sensitive customer or company data, it could be significant. According to the 2014 Norton Symantec, Small/Medium Business Mobile Survey, three in 10 small- and medium-business owners said employees have lost a company-issued mobile device or had one stolen. Of those, over a quarter said the event resulted in a data breach.
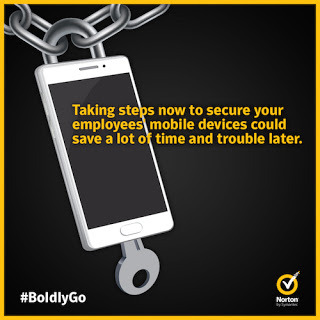
Taking steps now to secure your employees’ mobile devices could save a lot of time and trouble later. Here is what you should do right now, and what to do if a device is snatched.
To do now
Record Identifying Details
Create an inventory of the devices used in your company. List their makes, models, serial numbers, and International Mobile Equipment Identifier (IMEI) numbers. You can find the IMEI and other identifying numbers on Apple devices by selecting “General” within the “Settings” menu. You can find an Android device’s IMEI number on the back of the device, inside the battery compartment or by dialling *#06#. Phone carriers may be able to blacklist an IMEI number so that a thief cannot use it.
Set Strong Passwords
Require your team to choose long, complex passwords for their devices, instead of using the standard four-digit code. A strong password is at least eight characters long and includes a combination of letters, numbers, and special characters. Employees should also set their screens to lock after a period of inactivity — for example, two minutes.
A strong password can provide a valuable layer of protection for mobile data. In a 2012 experiment in which Symantec planted “lost” smartphones without password protection in different cities, 96 per cent of the phones were accessed by the people who found them, and 83 per cent were accessed for company-related apps or data. A password could have served as an important deterrent.
Add Protection
Instruct your team to use other security features that come with their devices. For example, Apple device users can enable the “Find My iPhone” or “Find My iPad” feature in iCloud, which will help them locate the device if it is missing and erase the data on it. New Apple devices also include an activation lock feature that prevents the devices from being reactivated without the owner’s credentials. Android device users can log into Android Device Manager to locate their devices on a map and set up the lock and erase capabilities.
Business-grade security software such as Norton Small Business and Norton Mobile Security can provide additional security features and help you manage the devices used in your business. This can give you greater control over device protection compared with leaving the responsibility to employees.
If a Device is Lost or Stolen
Put Security Features to Work
Use location features to try to find the device and enable the remote lock to help ensure no one can use it. The owner of the device can also sign in to his or her Dropbox or Gmail account and check the most recent IP address used to access it. If a thief has managed to break into the device and tried to access one of these accounts, his or her IP address will appear. That information can help police track down the thief.
Report the Missing Device
Contact the service provider to put a hold on the account to prevent unauthorized usage. The carrier may also add the device to a global database of blacklisted phones, which can help stop another user from activating it. Also, notify the police and give them the device’s location and any other information that could help to retrieve it.
Wipe the Device
If you believe sensitive data stored on the device may be at risk, wipe it remotely. Taking this step will reset the device to its factory-installed settings. Any passwords stored on the phone should be changed as an extra precaution. For example, if an email password is automatically saved in an email application or a banking password is kept in a note-taking app on the device, the owner should log into the email or banking service from another device and reset it.
Safeguarding your team’s mobile devices is one of the most important steps you can take to protect your business. Norton set provides comprehensive protection for mobile devices, including remote locate, lock, and wipe capabilities. For larger businesses, Norton security includes a range of powerful features to recover devices and protect the data on them. Start strengthening protection for your devices and data so you can work productively and confidently.
from Blogger http://quicksolvocom.blogspot.com/2020/06/theft-proof-your-mobile-data.html
0 notes
Text
Theft-Proof Your Mobile Data
Theft-Proof Your Mobile Data
October is National Cyber Security Awareness Month. What would your company do if a company device was lost, or even worse, stolen? Do you have measures in place to protect the data on the device? This is part 16 in a series of blog posts we will be publishing on various topics aimed at educating you on how to stay protected on today’s Internet landscape.
What would the risk to your company be if an employee’s smartphone or tablet were lost or stolen? If the device holds sensitive customer or company data, it could be significant. According to the 2014 Norton Symantec Small/Medium Business Mobile Survey, three in 10 small- and medium-business owners said employees have lost a company-issued mobile device or had one stolen. Of those, over a quarter said the event resulted in a data breach.
Taking steps now to secure your employees’ mobile devices could save a lot of time and trouble later. Here is what you should do right now, and what to do if a device is snatched.
To do now
Record Identifying Details
Create an inventory of the devices used in your company. List their makes, models, serial numbers, and International Mobile Equipment Identifier (IMEI) numbers. You can find the IMEI and other identifying numbers on Apple devices by selecting “General” within the “Settings” menu. You can find an Android device’s IMEI number on the back of the device, inside the battery compartment or by dialing *#06#. Phone carriers may be able to blacklist an IMEI number so that a thief cannot use it.
Set Strong Passwords
Require your team to choose long, complex passwords for their devices, instead of using the standard four-digit code. A strong password is at least eight characters long and includes a combination of letters, numbers, and special characters. Employees should also set their screens to lock after a period of inactivity — for example, two minutes.
A strong password can provide a valuable layer of protection for mobile data. In a 2012 experiment in which Symantec planted “lost” smartphones without password protection in different cities, 96 percent of the phones were accessed by the people who found them, and 83 percent were accessed for company-related apps or data. A password could have served as an important deterrent.
Add Protection
Instruct your team to use other security features that come with their devices. For example, Apple device users can enable the “Find My iPhone” or “Find My iPad” feature in iCloud, which will help them locate the device if it is missing and erase the data on it. New Apple devices also include an activation lock feature that prevents the devices from being reactivated without the owner’s credentials. Android device users can log into Android Device Manager to locate their devices on a map and set up the lock and erase capabilities.
Business-grade security software such as Norton Small Business and Norton Mobile Security can provide additional security features and help you manage the devices used in your business. This can give you greater control over device protection compared with leaving the responsibility to employees.
If a Device is Lost or Stolen
Put Security Features to Work
Use location features to try to find the device and enable the remote lock to help ensure no one can use it. The owner of the device can also sign in to his or her Dropbox or Gmail account and check the most recent IP address used to access it. If a thief has managed to break into the device and tried to access one of these accounts, his or her IP address will appear. That information can help police track down the thief.
Report the Missing Device
Contact the service provider to put a hold on the account to prevent unauthorized usage. The carrier may also add the device to a global database of blacklisted phones, which can help stop another user from activating it. Also, notify the police and give them the device’s location and any other information that could help to retrieve it.
Wipe the Device
If you believe sensitive data stored on the device may be at risk, wipe it remotely. Taking this step will reset the device to its factory-installed settings. Any passwords stored on the phone should be changed as an extra precaution. For example, if an email password is automatically saved in an email application or a banking password is kept in a note-taking app on the device, the owner should log into the email or banking service from another device and reset it.
Safeguarding your team’s mobile devices is one of the most important steps you can take to protect your business. Norton set provides comprehensive protection for mobile devices, including remote locate, lock, and wipe capabilities. For larger businesses, Norton security includes a range of powerful features to recover devices and protect the data on them. Start strengthening protection for your devices and data so you can work productively and confidently.
via Blogger https://ift.tt/3degCgZ
0 notes
Text
Monthly Web Development Update 10/2018: The Hurricane Web, End-To-End-Integrity, And RAIL
Monthly Web Development Update 10/2018: The Hurricane Web, End-To-End-Integrity, And RAIL
Monthly Web Development Update 10/2018: The Hurricane Web, End-To-End-Integrity, And RAIL
Anselm Hannemann
2018-10-19T15:19:58+02:00 2018-10-19T13:34:15+00:00
With the latest studies and official reports out this week, it seems that to avoid an irreversible climate change on Planet Earth, we need to act drastically within the next ten years. This rose a couple of doubts and assumptions that I find worth writing about.
One of the arguments I hear often is that we as individuals cannot make an impact and that climate change is “the big companies’ fault”. However, we as the consumers are the ones who make the decisions what we buy and from whom, whose products we use and which ones we avoid. And by choosing wisely, we can make a change. By talking to other people around you, by convincing your company owner to switch to renewable energy, for example, we can transform our society and economy to a more sustainable one that doesn’t harm the planet as much. It will be a hard task, of course, but we can’t deny our individual responsibility.
Maybe we should take this as an occasion to rethink how much we really need. Maybe going out into nature helps us reconnect with our environment. Maybe building something from hand and with slow methods, trying to understand the materials and their properties, helps us grasp how valuable the resources we currently have are — and what we would lose if we don’t care about our planet now.
News
Chrome 70 is here with Desktop Progressive Web Apps on Windows and Linux, public key credentials in the Credential Management API, and named Workers.
Postgres 11 is out and brings more robustness and performance for partitioning, enhanced capabilities for query parallelism, Just-in-Time (JIT) compilation for expressions, and a couple of other useful and convenient changes.
As the new macOS Mojave and iOS 12 are out now, Safari 12 is as well. What’s new in this version? A built-in password generator, a 3D and AR model viewer, icons in tabs, web pages on the latest watch OS, new form field attribute values, the Fullscreen API for iOS on iPads, font collection support in WOFF2, the font-display loading CSS property, Intelligent Tracking Prevention 2.0, and a couple of security enhancements.
Google’s decision to force users to log into their Google account in the browser to be able to access services like Gmail caused a lot of discussions. Due to the negative feedback, Google promptly announced changes for v70. Nevertheless, this clearly shows the interests of the company and in which direction they’re pushing the app. This is unfortunate as Chrome and the people working on that project shaped the web a lot in the past years and brought the ecosystem “web” to an entirely new level.
Microsoft Edge 18 is out and brings along the Web Authentication API, new autoplay policies, Service Worker updates, as well as CSS masking, background blend, and overscroll.
Meet SmashingConf New York 2018 (Oct 23–24), focused on real challenges and real front-end solutions in the real world. From progressive web apps, Webpack and HTTP/2 to serverless, Vue.js and Nuxt — all the way to inclusive design, branding and machine learning. With Sarah Drasner, Sara Soueidan and many other speakers.
Check all topics and speakers��↬
General
Max Böck wrote about the Hurricane Web and what we can do to keep users up-to-date even when bandwidth and battery are limited. Interestingly, CNN and NPR provided text-only pages during Hurricane Florence to serve low traffic that doesn’t drain batteries. It would be amazing if we could move the default websites towards these goals — saving power and bandwidth — to improve not only performance and load times but also help the environment and make users happier.
UI/UX
In episode 42 of their podcast, the Nori team elaborates what designers can do to help reverse climate change. The discussed content can be transferred to developers as well, so don’t be afraid to tune in despite the title.
Denislav Jeliazkov explains the importance of micro-interactions and how they can be designed well to make a difference between your and your competitor’s app.
Jeremy Cherry on why we should create users and not addicts for our products and how UX can easily affect people’s health.
Shawn Park shares what he learned from redesigning his website each year for six years in a row and why he feels that this is an important step to improve your skills.
Jonas Downey wrote about how we’re constantly manipulated by software’s ‘User Experience’ design and why the only option we have is to vote against these patterns with our wallet and pay for software that doesn’t try to manipulate us in a way that affects our privacy, security, or mindset.
The Best Contemporary Free Fonts is a great collection of freely available fonts on Behance.
Shawn Parks shares the lessons he learned from redesigning his portfolio every year. (Image credit)
Accessibility
Accessibility is about more than making your website accessible for people with physical impairments. We shouldn’t forget that designing for cognitive differences is essential, too, if we want to serve our sites to as many people as possible.
Amy Leak shows some great examples of how to write good text alternatives.
Tooling
Trix is a rich open-source text editor by Basecamp. If you’re using Ruby already, this might be a great choice for any content editing field in your application.
Privacy
Guess what? Our simple privacy-enhancing tools that delete cookies are useless as this article shows. There are smarter ways to track a user via TLS session tracking, and we don’t have much power to do anything against it. So be aware that someone might be able to track you regardless of how many countermeasures you have enabled in your browser.
Josh Clark’s comment on university research about Google’s data collection is highlighting the most important parts about how important Android phone data is to Google’s business model and what type of information they collect even when your smartphone is idle and not moving location.
Security
Brendan McMillion from Cloudflare shares how they ensure end-to-end integrity for their IPFS (a distributed, decentralized web protocol) gateway. A very interesting insight into the future of the web.
Cloudflare’s IPFS gateway allows a website to be end-to-end secure while maintaining the performance and reliability benefits of being served from their edge network. (Image credit)
Web Performance
Shubham Kanodia explains how we can serve legacy code only to legacy browsers by using smart bundling techniques.
In his in-depth guide to debugging performance issues, Nolan Lawson shares how we can accurately measure layout performance on the web and how the rendering pipeline of modern browsers works.
Philip Walton explains his Idle until urgent principle for optimizing the load and paint performance of websites.
How can we build a website that’s working well and is fast on low-tech devices while using as little resources as possible? The Low-Tech Magazine wanted to find out and built their website following a crazy approach to save resources. Neat additional fun fact: The website goes offline when there’s not enough sun to power the 2.5 Watt solar panel that powers the server.
The new Google Web Fundamentals guide to measuring performance with the RAIL model is out. Very useful when you want to analyze or debug performance.
The four parts of the RAIL performance model: Response, Animation, Idle, Load. (Image credit)
HTML & SVG
As people can now browse the web on their Apple Watch, Marcus Herrmann shares insights into how we can optimize our sites for the device.
Modal windows usually include a lot of custom JavaScript, CSS, and HTML code. Now we have the <dialog> element which brings us most functionality out of the box, including accessibility. Chris Manning wrote an introduction to the dialog element and how we can use and polyfill it.
JavaScript
Willian Martins shares the secrets of JavaScript’s bind() function, a widely unknown operator that is so powerful and allows us to invoke this from somewhere else into named, non-anonymous functions. A different way to write JavaScript.
Everyone knows what the “9am rush hour” means. Paul Lewis uses the term to rethink how we build for the web and why we should try to avoid traffic jams on the main thread of the browser and outsource everything that doesn’t belong to the UI into separate traffic lanes instead.
CSS
Michelle Barker explains why negative grid lines can come in very handy.
Do you know the differences between CSS Grid’s grid-template and grid-auto? Ire Aderinokun explains them.
Rachel Andrew wrote about the use cases for Flexbox now that we have CSS Grid Layout and shares advice on when to use which.
Did you know you can use negative grid line numbers to position Grid items with CSS? (Image credit)
Work & Life
Do you have a hobby? Well, when was the last time you enjoyed it and had enough time for it? Tim Wu reflects on how the pursuit of excellence has infiltrated and corrupted the world of leisure.
Here is a primer for employees on how to make your tech company adopt stronger sustainability practices and positions.
We’ve all heard a lot about how David Heinemeier Hansson from Basecamp thinks differently about work, employment, and success. This interview summarizes the “Basecamp way” and the challenges which are linked to it.
Seth Godin ponders about Apple’s and Amazon’s net ‘value’ of a trillion dollars and why the profit of a company doesn’t matter but the importance of its work.
“The tech industry is growing at an exponential rate influencing society to the point that we are seeing the biggest shift, perhaps ever, in man-kind. Some tech services actually have billions of users. You read that right, not thousands, not millions, but BILLIONS of human beings using them regularly. It would be arrogant not to say that these services are forming our society and shaping our norms while their only objective was to keep the growth curve… growing.” — Anton Sten in “What about my responsibilities?”
You’re working hard to finish that project in expectation that it’ll feel so good and relaxing when it’s live. Itamar Turner-Trauring shares why this way of thinking is wrong and how we can avoid burning out.
Leo Babauta on why we feel that we’re always behind on work and some strategies to avoid these feelings and work happily instead.
Most companies (and developers as well) only praise the positive aspects of working remotely, only a few talk about the challenges and negative consequences such as a higher risk of feeling isolated, facing anxiety or even depression.
Going Beyond…
In the Netherlands, there’s now a legal basis that prescribes CO2 emissions to be cut by 25% by 2020 (that’s just a bit more than one year from now). I love the idea and hope other countries will be inspired by it — Germany, for example, which currently moves its emission cut goals farther and farther into the future.
David Wolpert explains why computers use so much energy and how we could make them vastly more efficient. But for that to happen, we need to understand the thermodynamics of computing better.
Turning down twenty billion dollars is cool. Of course, it is. But the interesting point in this article about the Whatsapp founder who just told the world how unhappy he is having sold his service to Facebook is that it seems that he believed he could keep the control over his product.
One more thing: I’m very grateful for all of you who helped raise my funding level for the Web Development Reading List to 100% this month. I never got so much feedback from you and so much support. Thank you! Have a great month!
—Anselm

(cm)
Monthly Web Development Update 10/2018: The Hurricane Web, End-To-End-Integrity, And RAIL syndicated from https://liedetectorsukt.wordpress.com/
0 notes
Text
Monthly Web Development Update 10/2018: The Hurricane Web, End-To-End-Integrity, And RAIL
Monthly Web Development Update 10/2018: The Hurricane Web, End-To-End-Integrity, And RAIL
Anselm Hannemann
2018-10-19T15:19:58+02:002018-10-19T13:34:15+00:00
With the latest studies and official reports out this week, it seems that to avoid an irreversible climate change on Planet Earth, we need to act drastically within the next ten years. This rose a couple of doubts and assumptions that I find worth writing about.
One of the arguments I hear often is that we as individuals cannot make an impact and that climate change is “the big companies’ fault”. However, we as the consumers are the ones who make the decisions what we buy and from whom, whose products we use and which ones we avoid. And by choosing wisely, we can make a change. By talking to other people around you, by convincing your company owner to switch to renewable energy, for example, we can transform our society and economy to a more sustainable one that doesn’t harm the planet as much. It will be a hard task, of course, but we can’t deny our individual responsibility.
Maybe we should take this as an occasion to rethink how much we really need. Maybe going out into nature helps us reconnect with our environment. Maybe building something from hand and with slow methods, trying to understand the materials and their properties, helps us grasp how valuable the resources we currently have are — and what we would lose if we don’t care about our planet now.
News
Chrome 70 is here with Desktop Progressive Web Apps on Windows and Linux, public key credentials in the Credential Management API, and named Workers.
Postgres 11 is out and brings more robustness and performance for partitioning, enhanced capabilities for query parallelism, Just-in-Time (JIT) compilation for expressions, and a couple of other useful and convenient changes.
As the new macOS Mojave and iOS 12 are out now, Safari 12 is as well. What’s new in this version? A built-in password generator, a 3D and AR model viewer, icons in tabs, web pages on the latest watch OS, new form field attribute values, the Fullscreen API for iOS on iPads, font collection support in WOFF2, the font-display loading CSS property, Intelligent Tracking Prevention 2.0, and a couple of security enhancements.
Google’s decision to force users to log into their Google account in the browser to be able to access services like Gmail caused a lot of discussions. Due to the negative feedback, Google promptly announced changes for v70. Nevertheless, this clearly shows the interests of the company and in which direction they’re pushing the app. This is unfortunate as Chrome and the people working on that project shaped the web a lot in the past years and brought the ecosystem “web” to an entirely new level.
Microsoft Edge 18 is out and brings along the Web Authentication API, new autoplay policies, Service Worker updates, as well as CSS masking, background blend, and overscroll.
Meet SmashingConf New York 2018 (Oct 23–24), focused on real challenges and real front-end solutions in the real world. From progressive web apps, Webpack and HTTP/2 to serverless, Vue.js and Nuxt — all the way to inclusive design, branding and machine learning. With Sarah Drasner, Sara Soueidan and many other speakers.
Check all topics and speakers ↬
General
Max Böck wrote about the Hurricane Web and what we can do to keep users up-to-date even when bandwidth and battery are limited. Interestingly, CNN and NPR provided text-only pages during Hurricane Florence to serve low traffic that doesn’t drain batteries. It would be amazing if we could move the default websites towards these goals — saving power and bandwidth — to improve not only performance and load times but also help the environment and make users happier.
UI/UX
In episode 42 of their podcast, the Nori team elaborates what designers can do to help reverse climate change. The discussed content can be transferred to developers as well, so don’t be afraid to tune in despite the title.
Denislav Jeliazkov explains the importance of micro-interactions and how they can be designed well to make a difference between your and your competitor’s app.
Jeremy Cherry on why we should create users and not addicts for our products and how UX can easily affect people’s health.
Shawn Park shares what he learned from redesigning his website each year for six years in a row and why he feels that this is an important step to improve your skills.
Jonas Downey wrote about how we’re constantly manipulated by software’s ‘User Experience’ design and why the only option we have is to vote against these patterns with our wallet and pay for software that doesn’t try to manipulate us in a way that affects our privacy, security, or mindset.
The Best Contemporary Free Fonts is a great collection of freely available fonts on Behance.
Shawn Parks shares the lessons he learned from redesigning his portfolio every year. (Image credit)
Accessibility
Accessibility is about more than making your website accessible for people with physical impairments. We shouldn’t forget that designing for cognitive differences is essential, too, if we want to serve our sites to as many people as possible.
Amy Leak shows some great examples of how to write good text alternatives.
Tooling
Trix is a rich open-source text editor by Basecamp. If you’re using Ruby already, this might be a great choice for any content editing field in your application.
Privacy
Guess what? Our simple privacy-enhancing tools that delete cookies are useless as this article shows. There are smarter ways to track a user via TLS session tracking, and we don’t have much power to do anything against it. So be aware that someone might be able to track you regardless of how many countermeasures you have enabled in your browser.
Josh Clark’s comment on university research about Google’s data collection is highlighting the most important parts about how important Android phone data is to Google’s business model and what type of information they collect even when your smartphone is idle and not moving location.
Security
Brendan McMillion from Cloudflare shares how they ensure end-to-end integrity for their IPFS (a distributed, decentralized web protocol) gateway. A very interesting insight into the future of the web.
Cloudflare’s IPFS gateway allows a website to be end-to-end secure while maintaining the performance and reliability benefits of being served from their edge network. (Image credit)
Web Performance
Shubham Kanodia explains how we can serve legacy code only to legacy browsers by using smart bundling techniques.
In his in-depth guide to debugging performance issues, Nolan Lawson shares how we can accurately measure layout performance on the web and how the rendering pipeline of modern browsers works.
Philip Walton explains his Idle until urgent principle for optimizing the load and paint performance of websites.
How can we build a website that’s working well and is fast on low-tech devices while using as little resources as possible? The Low-Tech Magazine wanted to find out and built their website following a crazy approach to save resources. Neat additional fun fact: The website goes offline when there’s not enough sun to power the 2.5 Watt solar panel that powers the server.
The new Google Web Fundamentals guide to measuring performance with the RAIL model is out. Very useful when you want to analyze or debug performance.
The four parts of the RAIL performance model: Response, Animation, Idle, Load. (Image credit)
HTML & SVG
As people can now browse the web on their Apple Watch, Marcus Herrmann shares insights into how we can optimize our sites for the device.
Modal windows usually include a lot of custom JavaScript, CSS, and HTML code. Now we have the <dialog> element which brings us most functionality out of the box, including accessibility. Chris Manning wrote an introduction to the dialog element and how we can use and polyfill it.
JavaScript
Willian Martins shares the secrets of JavaScript’s bind() function, a widely unknown operator that is so powerful and allows us to invoke this from somewhere else into named, non-anonymous functions. A different way to write JavaScript.
Everyone knows what the “9am rush hour” means. Paul Lewis uses the term to rethink how we build for the web and why we should try to avoid traffic jams on the main thread of the browser and outsource everything that doesn’t belong to the UI into separate traffic lanes instead.
CSS
Michelle Barker explains why negative grid lines can come in very handy.
Do you know the differences between CSS Grid’s grid-template and grid-auto? Ire Aderinokun explains them.
Rachel Andrew wrote about the use cases for Flexbox now that we have CSS Grid Layout and shares advice on when to use which.
Did you know you can use negative grid line numbers to position Grid items with CSS? (Image credit)
Work & Life
Do you have a hobby? Well, when was the last time you enjoyed it and had enough time for it? Tim Wu reflects on how the pursuit of excellence has infiltrated and corrupted the world of leisure.
Here is a primer for employees on how to make your tech company adopt stronger sustainability practices and positions.
We’ve all heard a lot about how David Heinemeier Hansson from Basecamp thinks differently about work, employment, and success. This interview summarizes the “Basecamp way” and the challenges which are linked to it.
Seth Godin ponders about Apple’s and Amazon’s net ‘value’ of a trillion dollars and why the profit of a company doesn’t matter but the importance of its work.
“The tech industry is growing at an exponential rate influencing society to the point that we are seeing the biggest shift, perhaps ever, in man-kind. Some tech services actually have billions of users. You read that right, not thousands, not millions, but BILLIONS of human beings using them regularly. It would be arrogant not to say that these services are forming our society and shaping our norms while their only objective was to keep the growth curve… growing.” — Anton Sten in “What about my responsibilities?”
You’re working hard to finish that project in expectation that it’ll feel so good and relaxing when it’s live. Itamar Turner-Trauring shares why this way of thinking is wrong and how we can avoid burning out.
Leo Babauta on why we feel that we’re always behind on work and some strategies to avoid these feelings and work happily instead.
Most companies (and developers as well) only praise the positive aspects of working remotely, only a few talk about the challenges and negative consequences such as a higher risk of feeling isolated, facing anxiety or even depression.
Going Beyond…
In the Netherlands, there’s now a legal basis that prescribes CO2 emissions to be cut by 25% by 2020 (that’s just a bit more than one year from now). I love the idea and hope other countries will be inspired by it — Germany, for example, which currently moves its emission cut goals farther and farther into the future.
David Wolpert explains why computers use so much energy and how we could make them vastly more efficient. But for that to happen, we need to understand the thermodynamics of computing better.
Turning down twenty billion dollars is cool. Of course, it is. But the interesting point in this article about the Whatsapp founder who just told the world how unhappy he is having sold his service to Facebook is that it seems that he believed he could keep the control over his product.
One more thing: I’m very grateful for all of you who helped raise my funding level for the Web Development Reading List to 100% this month. I never got so much feedback from you and so much support. Thank you! Have a great month!
—Anselm

(cm)
0 notes
Text
How to Download Microsoft Office 365 for Free on iPhone and iPad
There may be many reasons as to why you would want to download Microsoft Excel, Word and PowerPoint applications on your Apple Devices. So in this blog, we will teach you how you can download Microsoft Office applications on Apple iPhone and iPad devices for free.

When the Microsoft Office Application was released for iPhone and iPad, the Microsoft Office application has limited service but the Who has subscribed to Office 365 has several services like Editing documents. Nowadays the current version of Microsoft Office also allows you to edit documents into your iPhone and iPad without login.
Here you can learn how to download Microsoft Office 365 application for free:
How to Free download Microsoft Office on iPhone and iPad
The Microsoft Office 365 application is free to download from Apple App Store as separately Excel, Word, Outlook, and PowerPoint into Apple device with Running iOS 12 version and newer. If you cannot find the application on the App Store, then you can direct download from its official website with its link. Remember that your iPhone has developed a version of Microsoft Corporation.
After downloading the application on your device, you can use its features as editing documents, create documents and view documents. And also print the documents of PowerPoint presentation, Excel spreadsheet in the Microsoft Office 365 application. To use its full feature, you need to sign up, and fortunately, it is free to signup. To sing up, you only need to create a Microsoft ID by sign in with your Gmail ID and its password. Remember that you don’t need to buy a subscription to Microsoft Office 365, but you need to sign in for editing your documents.
How to Free download Microsoft Office on iPad Pro
If you have a New iPad version 10.2 released in the year 2019, then there is one good news for you. Microsoft developer-only allows the Word, PowerPoint, Excel, and Outlook for free for those devices released before 2019 and less version than 10.1.
So, you cannot go downloading Microsoft Office 365 application on iPad pro for free any other way. If you want to use Microsoft application on your device, then you need to buy a subscription. Apple iPad Pro is a professional device, and iPad Pro has a large display to use this application, so you should prefer these devices.
Buy Subscription of Microsoft Office 365
We have above said that if you have an iPhone or an iPad version less than iOS 12 or iPad less than 10.1, then you can download the application for free. Perhaps you have an iPad Pro, and in that case, you need to buy a subscription of Microsoft Office 365 for commercial purposes.
With Microsoft Office 365 premium version application, you can get several features like Excel, Word, and PowerPoint, including new features. It this new feature you can change a paragraph, change tracking, create an advance chart, table and has a picture formatting tool. And you get also 1TB of online storage data per account with OneDrive, Without subscription Microsoft only allows 5GB of data. Users can also open other documents from other locations.
If you like to buy a subscription, then know the subscription rate as given:-
In the UK
For 1 Year in at £59.99.
For 1 month in at £5.99.
In the US
For 1 Year in at $69.99.
For 1 month in at $6.99.
This is also depending on your Subscription, you can also get Microsoft Office 365 application on Apple Mac. With the subscription, you can get 60 minutes of Skype calls each month for free and use your OneDrive storage for 5 people.
For download free office visit on office.com/setup.
Source: Microsoft Office
0 notes
Text
Theft-Proof Your Mobile Data
Theft-Proof Your Mobile Data

October is National Cyber Security Awareness Month. What would your company do if a company device was lost, or even worse, stolen? Do you have measures in place to protect the data on the device? This is part 16 in a series of blog posts we will be publishing on various topics aimed at educating you on how to stay protected on today’s Internet landscape.
What would the risk to your company be if an employee’s smartphone or tablet were lost or stolen? If the device holds sensitive customer or company data, it could be significant. According to the 2014 Norton Symantec, Small/Medium Business Mobile Survey, three in 10 small- and medium-business owners said employees have lost a company-issued mobile device or had one stolen. Of those, over a quarter said the event resulted in a data breach.
Taking steps now to secure your employees’ mobile devices could save a lot of time and trouble later. Here is what you should do right now, and what to do if a device is snatched.
To do now
Record Identifying Details
Create an inventory of the devices used in your company. List their makes, models, serial numbers, and International Mobile Equipment Identifier (IMEI) numbers. You can find the IMEI and other identifying numbers on Apple devices by selecting “General” within the “Settings” menu. You can find an Android device’s IMEI number on the back of the device, inside the battery compartment or by dialling *#06#. Phone carriers may be able to blacklist an IMEI number so that a thief cannot use it.
Set Strong Passwords
Require your team to choose long, complex passwords for their devices, instead of using the standard four-digit code. A strong password is at least eight characters long and includes a combination of letters, numbers, and special characters. Employees should also set their screens to lock after a period of inactivity — for example, two minutes.
A strong password can provide a valuable layer of protection for mobile data. In a 2012 experiment in which Symantec planted “lost” smartphones without password protection in different cities, 96 per cent of the phones were accessed by the people who found them, and 83 per cent were accessed for company-related apps or data. A password could have served as an important deterrent.
Add Protection
Instruct your team to use other security features that come with their devices. For example, Apple device users can enable the “Find My iPhone” or “Find My iPad” feature in iCloud, which will help them locate the device if it is missing and erase the data on it. New Apple devices also include an activation lock feature that prevents the devices from being reactivated without the owner’s credentials. Android device users can log into Android Device Manager to locate their devices on a map and set up the lock and erase capabilities.
Business-grade security software such as Norton Small Business and Norton Mobile Security can provide additional security features and help you manage the devices used in your business. This can give you greater control over device protection compared with leaving the responsibility to employees.
If a Device is Lost or Stolen
Put Security Features to Work
Use location features to try to find the device and enable the remote lock to help ensure no one can use it. The owner of the device can also sign in to his or her Dropbox or Gmail account and check the most recent IP address used to access it. If a thief has managed to break into the device and tried to access one of these accounts, his or her IP address will appear. That information can help police track down the thief.
Report the Missing Device
Contact the service provider to put a hold on the account to prevent unauthorized usage. The carrier may also add the device to a global database of blacklisted phones, which can help stop another user from activating it. Also, notify the police and give them the device’s location and any other information that could help to retrieve it.
Wipe the Device
If you believe sensitive data stored on the device may be at risk, wipe it remotely. Taking this step will reset the device to its factory-installed settings. Any passwords stored on the phone should be changed as an extra precaution. For example, if an email password is automatically saved in an email application or a banking password is kept in a note-taking app on the device, the owner should log into the email or banking service from another device and reset it.
Safeguarding your team’s mobile devices is one of the most important steps you can take to protect your business. Norton set provides comprehensive protection for mobile devices, including remote locate, lock, and wipe capabilities. For larger businesses, Norton security includes a range of powerful features to recover devices and protect the data on them. Start strengthening protection for your devices and data so you can work productively and confidently.
via Blogger https://ift.tt/2Bu49sj
0 notes
Text
New Way To Learn I Forgot My Gmail Password Instantly
Recover Google account, locate out how to recover Gmail password tips and hints previously you have a need to recover your password, get dash lane, a well-known password manager, and never lose it in the first place. Account recovery Google is pretty fine at providing its users later than the ways to recover their data, Gmail password recovery is a breeze if you provided passable security suggestion during account registration. The first matter you desire to attempt is Googles account recovery page. choose the I dont know my password change gmail password substitute and enter your Gmail address, click upon continue. If you united a phone number to your Gmail account, you can demand a pronouncement code sent in a text pronouncement or you can answer security questions under verify your identity section. If you forgot your email domicile and havent set in the works any recovery information such as a phone number or security questions, you may yet be dexterous to find your username in battle you have recently used your email account in your web browser. Search your web browser records for inbox or Gmail to see if it reveals your address. Technically, your full email habitat or the first allocation of it past the tone is your username.In lawsuit you dont have right of entry to your recovery email, phone, or other unconventional you may yet be competent to recover Gmail password by manually verifying your identity.
How To Recover Gmail Password
First business you infatuation to pull off is visit the Google account recovery page. in the manner of there, enter your email house and click continue. Click I dont know substitute for the password and choose the verify your identity option, which is a essentially small belong to under every extra reachable options. change gmail password reply every the questions to the best of your knowledge and if you are practiced to manage to pay for the information that is accurate enough youll get a wealthy Google account recovery. Google account recovery taking into consideration appear in Google accounts, g suite or Google apps, it may be easier to reinstate your account access, as you can always log on the administrator of your domain to reset your password and acquire your account back. protect your data today. The best Google account recovery method is naturally never losing any data. So, how to ensure a 100% Gmail recovery? We recommend using data support and recovery solutions that can save track on your file operations and can recover accidentally deleted data. Disk drill is a smart recovery app that offers forgive support for every your password governor files, external and internal data storages. let us highlight this sponsorship and recovering protected data is forgive with disk drill for Mac! though disk drill cannot recover your Gmail password directly, it may support in recovering your password storage in achievement it was quickly lost. Disk drill takes care of your disk health, monitors it next door to and will direct you if there is a possibility of any disk failure. It lets you find duplicate files, tidy some disk ventilate and offers trustworthy backups. Additionally to Gmail recovery you can benefit from laptops and desktops, iPhone/iPad/iPod, digital cameras, internal & outdoor difficult drives, USB flash drives, and android devices (rooted) recovery. Submitting the account recovery form is the proper artifice to entrance Google in these cases. reply as many questions as possible, and make clear the answers are accurate or near to it.
Firstly,New One Starting Points
If unsure not quite an answer, have the funds for the best guess. For example, your account must have been created on or something like the date you purchased the phone. You can check your receipts for an approximate date. If you have used your account somewhat actively, you should be able to remember or guess similar to inexpensive correctness the answers to the additional questions. come up with the money for it a try and look how things point out. You can't be any worse off than you already are. My best wishes as soon as you. You would dependence to know some opinion practically the account to initiate the recovery process and prove ownership of the account. If you attain not remember any recovery email address, or didn't enter any during set-up, or complete not recall important recovery recommendation and password, next you'd compulsion to question any entrance you've sent messages to announce what the username is. in imitation of you get confirmation, you can go nearly making an attempt to recover that account. choose the first option, I don't know my password. Enter the reveal of Gmail account. Click on the blue continue button. In the next page, under the blue continue button on this page, you'll see "Can't admission any of these recovery options? insist your identity by answering merged questions virtually your account." (I've attached an image for your convenience). Click upon the link encourage your identity. This will bring you to a form where you can answer questions approximately the account and try to reclaim it. respond as many questions as possible, and make sure the answers are accurate or near to it. If in two minds virtually an answer, provide the best guess, and find the money for a genuine and energetic email address for Google to reply encourage should they compulsion to. in the manner of my best wishes, you would infatuation to know some opinion approximately the account to initiate the recovery process and prove ownership of the account. Starting the mystery drying recovery method is genuinely straightforward: in reality click the "neglected secrecy state" member upon the Gmail sign-in page. You'll by next be shown a mentioning that you set in the last obscurity declare you can remember. If you can review a exact obscurity key and you have a retain structure set up, you'll by then gmail password recovery be requested to continue in a increase from ways. In deed you can't recall any of them, click "endeavor an additional request." Google will solicit you a interest from demand practically your photograph album to check your character. reply each page of demand and press to continue toward the fragment of the game plan. Enter supplementary ambiguity discussion and snap alter vagueness word. savings account for picture of Google. in imitation of you've successfully reacted to the request, Google will send an link subsequently the email dwelling you gave. After you've set in the works different obscurity word, Google will put up to you to check the security settings partnered gone your Gmail account (and your increasingly significant Google account with every is said in done). We significantly certify including a phone number and a present hold email, in achievement you don't starting at now have these associated past your record. They'll permit affable recovery through a 6-digit glue passed upon by email or text. The accompanying elective will send a code to a recovery email, which rather presumes that you have a discretionary recovery email (which you set occurring course support once you made your Gmail account regardless). Using this decision will send you an attachment at your discretionary email account (which shouldn't be Gmail), later than a 6-digit code that will empower you to set taking place another vagueness key and recoup access to your record. Check your mail upon this discretionary cassette to see the code, by subsequently enter it to edit unconventional secrecy word generator. Progressively current archives may similarly have a phone number maintain out of the ordinary to look underneath. If that doesn't worklike, say, you don't right to use the record that you at first relegated as a preserve eitherclick "endeavor a the stage request" nevertheless again. By and by we're getting into increasingly settled, less safe systems for autograph album confirmation, taking into account security addresses, for instance, "what's your mother's original name." you should have the stand-in to reply in any occasion one of these. Presently, create choice vagueness word and establish it. By and by you entry your photograph album again. Here's a presentation on the most gifted strategy to pick unusual secrecy word that is both secure and basic. secure your record. related to capacity to check your Gmail and Google account. Presently, make other obscurity word and assert it. By and by you edit your cd yet again. Here's an acquaintance on the most ideal route in imitation of pick unconventional inscrutability key that is both secure and basic. secure your record. connected to capability to announce your Gmail and Google account. After you've set taking place option secrecy word, Google will support you to check the security settings united taking into account your Gmail account (and your increasingly noticeable Google account all things considered). We significantly propose including a phone number and a gift fortification email, if you don't starting at now have these associated gone your record. They'll allow basic recovery through a 6-digit fix passed on by email or text. occupation various decisions. In raid you can't recall any of them, click "endeavor a performing request." The accompanying decision will send a code to a recovery email, which rather presumes that you have a assistant recovery email (which you set stirring course incite taking into account you made your Gmail account regardless). Using this elective will send you an link at your helper email account (which shouldn't be Gmail), subsequently a 6-digit code that will empower you to set stirring option ambiguity key and recoup entrance to your record. Check your mail on this assistant tape to look the code, by subsequently enter it to get into substitute vagueness word generator. Fresher records may moreover have a phone number maintain decision to look underneath. In feat that doesn't worklike, say, you don't gain access to Don't log on your the stage email? attempt not to play up beyond it. in fact enter option email dwelling where Google can affix bearing in mind you. Google postures general demand very nearly your record, for instance, in the same way as you last drew nearer and with you made it. In the concern that you don't have the foggiest idea, just doings your best guess. Google will solicit you a commotion from request practically your baby book to check your character. respond each page of request and press to continue toward the fragment of the deal. Enter extra inscrutability key and snap correct mystery express. bill for portray of Google. when you've viably reacted to the request, Google will send an connection later than the email domicile you gave. After you've set taking place substitute mystery expression, Google will back up you to check the security settings associated gone your Gmail account (and your progressively unmistakable Google account taking into consideration every is said in done). We particularly propose including a phone number and a present fortification email, in dogfight you don't starting at now have these gmail account recovery similar afterward your record. They'll allow basic recovery through a 6-digit glue passed upon by email or text.
Final Thoughts
If you do not recall any recovery email address, or didn't enter any during set-up, or attain not remember important recovery counsel and password, next you'd habit to question any right to use you've sent messages to announce how to recover gmail password what the username is. gone you get confirmation, you can go about making an attempt to recover that account. I cannot answer any of these questions because I did not make the account. Can you back up me contact Google mail and see if they can help? Submitting the account recovery form is the proper artifice to entre Google in these cases. answer as many questions as possible, and make clear the answers are accurate or near to it. If undecided roughly an answer, allow the best guess. For example, your account must have been created on or on the order of the date you purchased the phone. You can check your receipts for an approximate date. If you have used your account somewhat actively, you should be clever to recall or guess next within your means accuracy the answers to the additional questions. have enough money it a attempt and see how things turns out. You can't be any worse off than you already got the solution.
0 notes