#creating MSG from html
Explore tagged Tumblr posts
Text
Socket.IO setup

Building Real-Time Applications with Socket.IO setup: Step-by-Step Tutorial
Socket.IO setup. In today's interconnected world, real-time applications are becoming increasingly essential. Whether it's for live chat applications, collaborative tools, or gaming, real-time communication enhances user engagement and makes interactions more dynamic. One powerful tool for building real-time applications is Socket.IO. In this tutorial, we will guide you through the process of building a real-time application using Socket.IO, focusing on key concepts and practical implementation. What is Socket.IO? Socket.IO is a JavaScript library that enables real-time, bidirectional communication between web clients (like browsers) and servers. Unlike traditional HTTP requests, which follow a request-response model, Socket.IO provides a persistent connection, enabling instant data exchange between the client and server. Socket.IO works on top of WebSockets, but it provides fallback mechanisms for environments where WebSockets may not be available. This ensures that real-time communication is possible in a wide range of conditions, making it a versatile choice for building interactive web applications. Prerequisites Before we dive into the tutorial, make sure you have the following: Basic knowledge of JavaScript and Node.js Node.js installed on your machine. You can download it from nodejs.org. A code editor (like Visual Studio Code or Sublime Text). Step 1: Setting Up the Project Start by setting up a basic Node.js project. Create a new directory for your project: bash mkdir real-time-app cd real-time-app Initialize a new Node.js project: bash npm init -y Install Express and Socket.IO: bash npm install express socket.io Express is a lightweight web framework for Node.js that simplifies the creation of web servers. Socket.IO will handle real-time communication between the server and the client. Step 2: Create the Server Now that we've set up the dependencies, let's create a simple server. Create a file called server.js in the project root: js const express = require('express'); const http = require('http'); const socketIo = require('socket.io');// Create an instance of Express app const app = express();// Create an HTTP server const server = http.createServer(app); // Initialize Socket.IO with the HTTP server const io = socketIo(server); // Serve static files (like HTML, CSS, JS) app.use(express.static('public')); // Handle socket connection io.on('connection', (socket) => { console.log('a user connected'); // Handle message from client socket.on('chat message', (msg) => { io.emit('chat message', msg); // Emit the message to all clients }); // Handle disconnect socket.on('disconnect', () => { console.log('user disconnected'); }); }); // Start the server server.listen(3000, () => { console.log('Server is running on http://localhost:3000'); }); Step 3: Create the Client-Side Next, we need to create the client-side code that will connect to the server and send/receive messages in real time. Create a public folder inside the project directory. In the public folder, create an index.html file: html Real-Time Chat Real-Time Chat Application Send const socket = io(); // Connect to the server// Listen for messages from the server socket.on('chat message', function(msg){ const li = document.createElement('li'); li.textContent = msg; document.getElementById('messages').appendChild(li); }); // Handle form submission const form = document.getElementById('form'); form.addEventListener('submit', function(event){ event.preventDefault(); const input = document.getElementById('input'); socket.emit('chat message', input.value); // Send the message to the server input.value = ''; // Clear the input field }); Step 4: Run the Application With the server and client code in place, it’s time to run the application! In your terminal, run the following command: bash node server.js Open your browser and go to http://localhost:3000. You should see the chat interface. Open multiple browser windows or tabs to simulate multiple users. Type a message in the input field and click "Send." You should see the message appear in real-time in all open windows/tabs. Step 5: Enhancements and Improvements Congratulations! You've built a basic real-time chat application using Socket.IO. To enhance the application, consider adding the following features: User authentication: Allow users to log in before they can send messages. Private messaging: Enable users to send messages to specific individuals. Message persistence: Use a database (e.g., MongoDB) to store chat history. Typing indicators: Show when a user is typing a message in real time. Emoji support: Allow users to send emojis and other media. Conclusion Socket.IO setup. In this tutorial, we covered the basics of building a real-time application using Socket.IO. We walked through setting up a Node.js server with Express, integrating Socket.IO for real-time communication, and creating a simple chat interface on the client side. Socket.IO makes it easy to add real-time features to your web applications, enabling more dynamic and interactive experiences for users. With this foundation, you can now start exploring more advanced real-time features and take your applications to the next level! Read the full article
#communication#CreatetheClient-Side#CreatetheServer#Enhancements#function#History#Improvements#RuntheApplication#Setting
0 notes
Text
How can I save Outlook emails to my hard drive without using the PST file?
A common email system utilized by many industry experts or for personal work at a more basic level is Microsoft Outlook (MS Outlook). PST files, also known as Outlook data files, are used to store all of a user's mailbox information. However, users may wish to save Outlook emails on their hard drive rather than PST files in order to avoid PST file corruption, or they may wish to move emails from Outlook accounts to any other top-notch email client such as Thunderbird or Apple Mail. In this blog post, we will cover workaround ways for archiving Outlook emails that do not require PST files to be created. The instruction is compatible with all Outlook versions, including 2007, 2010, 2013, 2016, and 2019, and it allows you to backup Outlook emails to your computer.

Have you ever wondered why hard drives have become such a necessary piece of technology? In light of the fact that users have begun to consider the need of data backup, which includes archiving emails from an Outlook to a hard drive, this is an appropriate time for them to do so. Downloading important data onto an external hard drive is an excellent method of ensuring its safety. Before we get into the solutions, let's have a look at some of the possible reasons for backing up Outlook emails to a hard drive without a PST file.
{ "@context": "https://schema.org", "@type": "Organization", "url": "https://threejarsofbees.tumblr.com/", "mainEntityOfPage": "https://doamour.tumblr.com/" }
Exactly why do users want to archive Outlook email messages without using an Exchange server or a PST file?
We will discuss some of the most common reasons why a user would need to store Outlook emails on a new computer in the next section.
There is a potential that the system will crash or that some other tragedy will occur. Consequently, consumers prefer to save emails locally so that they may conveniently access the material later on in their lives.
It is necessary to backup emails when transitioning between systems, such as when switching from a desktop to a laptop.
It's possible that you'll want to transfer your data from one Outlook version to another.
Users who have been using Microsoft Outlook for more than just personal reasons may consider storing old emails and objects outside of the PST file format.
It's possible that the PST file is already existent on the system, and users do not want to add to the size of the system file.
So, these are the scenarios in which you may be required to archive emails without having a PST file on your PC.
The Best Way to Save Outlook Emails to Your Hard Drive Without Using a PST File
Making a backup copy of Outlook mailbox emails that does not contain the PST file helps to ensure that users do not lose their important data. Users may wish to archive their PST files in various saving formats in order to minimize harm or corruption of the PST file. It is simple to accomplish using the following methods:
Emails from Outlook Mailboxes should be saved in MSG format.
Save the contents of your Outlook Mailbox in CSV format.
Emails from your Outlook Mailbox should be saved in HTML format.
Emails from your Outlook Mailbox can be saved in PDF format.
Emails from the Outlook Mailbox should be saved to the hard drive as a Word document.
Let's go over each of these in greater detail:
Emails from Outlook Mailboxes can be saved in MSG format.
Downloading Outlook emails in MSG file format is a rapid and risk-free method of archiving them in a secure location. To do so, follow these steps:
In order to keep archived Outlook emails, first create a folder in the location of your choosing.
Afterwards, open Outlook and navigate to the email folder you want to read.
To select all of the emails, press the Ctrl + A key combination.
Additionally, drag and drop the folder into the newly formed folder for saving.
Following this, you will be prompted to save all of the emails you have selected in the MSG file format.
select the email message format (msg)
Save the contents of your Outlook Mailbox in CSV format.
Here's another method for archiving Outlook emails in CSV format without having to use the PST file format. The only condition is that you make use of the Outlook Import/Export capability. Follow the steps in the correct order:
Start Outlook and select File from the drop-down menu.
Select Open & Export from the drop-down menu, and then select Import/Export from the drop-down menu.
Select Open Export from the drop-down menu.
Select Export to a File from the Import and Export Wizard's drop-down menu and then click Next.
pick Export to a File from the drop-down menu
Next, select Comma Separated Value from the drop-down menu and press the Next button.
Choose Comma Separated Values (CSV).
Select the folder from which you want to export items, for example, Inbox. To proceed, click on the Next button.
choose a folder to save your work
Afterwards, click on the Browse button to select a location for the resulting file's destination. Select Next from the drop-down menu.
Then select the Export "Email messages" from folder: Inbox option from the drop-down menu.
Exporting Email Messages should be checked.
To bring the procedure to a close, click on the Finish button.
Finish by clicking on the button.
Finally, all of the emails in your Outlook mailbox will be saved to a CSV file on your computer's hard disk.
Emails from your Outlook Mailbox can be saved in HTML format.
You will be able to store emails from Outlook in HTML format in addition to MSG and CSV formats. The following are the procedures to be followed:
To begin, open Outlook and choose the email from which you want to save it by double-clicking on it.
It will launch a fresh email wizard in a new window. Select the Save As option from the File menu by clicking on the File button.
Assign a name to the folder and select HTML as the saving format from the drop-down menu in the opening window.
Following that, click on the Save option to get it downloaded in HTML format.
If you have any more emails that you want to archive, you can follow the same steps as above.
Emails from your Outlook Mailbox can be saved in PDF format.
First and foremost, in order to save Outlook emails in PDF format, you must first download them as HTML by following the instructions above. Then follow the instructions outlined below:
Open the HTML-based email in any web browser, such as Google Chrome, to view it.
Then use the Ctrl+P keyboard shortcut and select the Save as PDF option from the drop-down menu.
Click Save and navigate to the folder where you want to save it after that.
Finally, click on the Save option to bring the working process to a close.
Emails from the Outlook Mailbox should be saved to the hard drive as a Word document.
In order to back up Outlook mailbox emails in Word format, you must first save the email as HTML by following the instructions outlined in the previous section. After that, follow the instructions outlined below:
In this case, you must open Word and select the File>>Open option.
Now, locate the HTML-based email file that was previously saved and open it in Microsoft Word.
Then, to save the file as a Word document, select File>> Save As from the menu bar.
If none of the ways listed above work for you, you can try the following: save Outlook emails to hard disk without using PST. A recommendation will be made for you to back up your Outlook emails to your computer in the PST file format and then convert them into one of the 15+ file formats supported by SysInfo PST File Converter. MSG, EML, MBOX, CSV, OST, HTML, DOC, PNG, JSON, TIFF, and other formats are available for saving. In addition, you can import PST files into Office 365, Gmail, Thunderbird, AOL, IMAP, Live Exchange, Hotmail, and other email clients, such as Outlook and Thunderbird.
Conclusion
It has been addressed in this blog post about How to Save Outlook Emails to the Local Hard Drive Without Using a PST file, as well as the reasons and instances in which it is important to backup an email from an Outlook mailbox.
4 notes
·
View notes
Text
UEFI hacking malware
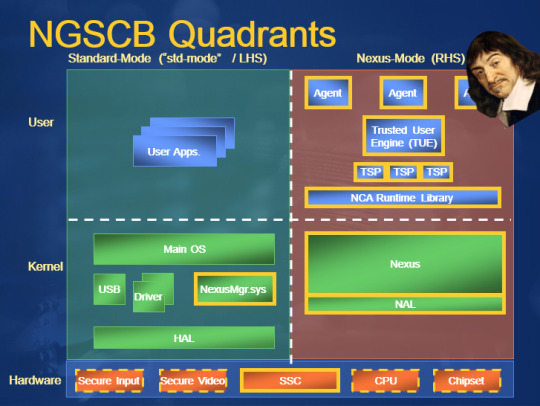
Security researchers are alarmed: the already-notorious Trickbot malware has been spottied probing infected computers to find out which version of UEFI they're running. This is read as evidence that Trickbot has figured out how to pull off a really scary feat.
To understand why, you have to understand UEFI: a fascinating, deep, philosophical change to our view of computers, trust, and the knowability of the universe. It's a tale of hard choices, paternalism, and the race to secure the digital realm as it merges with the physical.
Computers were once standalone: a central processing unit that might be augmented by some co-processors for specialized processes, like a graphics card or even a math co-processor.
These co-pros were subordinate to the CPU though. You'd turn on the computer and it would read a very small set of hardcoded instructions telling it how to access a floppy disk or other storage medium for the rest of the boot sequence, the stuff needed to boot the system.
The hardwired instructions were in a ROM that had one job: wake up and feed some instructions to the "computer" telling it what to do, then go back to sleep. But there's a philosophical conundrum here.
Because the world of computing is adversarial and networked computing is doubly so: there are people who want your computer to do things that are antithetical to your interests, like steal your data or spy on you or encrypt all your files and demand ransom.
To stop this, you need to be able to examine the programs running on your computer and terminate the malicious ones. And therein lies the rub: when you instruct your computer to examine its own workings, how do you know if you can trust it?
In 1983, Ken Thompson (co-creator of C, Unix, etc) was awarded a Turing Award ("computer science's Nobel Prize"). He gave a fucking bombshell of an acceptance speech, called "Reflections on Trusting Trust."
https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
Thompson revealed that he had created a backdoor for himself that didn't just live in Unix, but in the C compiler that people made to create new Unix systems.
Here's what that means: when you write a program, you produce "high-level code" with instructions like "printf("Hello, World!");". Once your program is done, you turn it into machine code, a series of much shorter instructions that your CPU understands ("mov dx, msg" etc).
Most programmers can't read this machine code, and even for those who can, it's a hard slog. In general, we write our code, compile it and run it, but we don't examine it. With nontrivial programs, looking at the machine code is very, very hard.
Compilers are treated as intrinsically trustworthy. Give 'em some source, they spit out a binary, you run the binary. Sometimes there are compiler bugs, sure, and compiler improvements can be a big deal. But compilers are infrastructure: inscrutable and forgotten.
Here's what Thompson did: he hid a program in his compiler that would check to see whether you were compiling an operating system or a compiler. If you were compiling an OS, it hid a secret login for him inside of it.
If you were compiling a compiler, it hid the program that looked for compilers or operating systems inside of it.
Think about what this means: every OS you compiled had an intentional security defect that the OS itself couldn't detect.
If you suspected that your compiler was up to no good and wrote your own compiler, it would be compromised as soon as you compiled it. What Thompson did was ask us to contemplate what we meant when we "trusted" something.
It was a move straight out of Rene Descartes, the reasoning that leads up to "I think therefore I am." Descartes' "Discourse on the Method" asks how we can know things about the universe.
He points out that sometimes he thinks he senses something but is wrong - he dreams, he hallucinates, he misapprehends.
If all our reasoning depends on the impressions we get from our senses, and if our senses are sometimes faulty, how can we reason at all?
Descartes wants a point of certainty, one thing he *knows* to be absolutely true. He makes the case that if you can be certain of one thing, you can anchor everything else to this point and build up a massive edifice of trustable knowledge that all hangs off of this anchor.
Thompson is basically saying, "You thought you had descartesed your way into a trustable computing universe because of the axiom that I would never poison your lowest-level, most fundamental tools.
"*Wrong*.
"Bwahahahaha."
(But, you know, in a nice way: an object lesson to serve as a wake-up call before computers fully merged with the physical world to form a global, species-wide digital nervous system whose untrustworthy low-level parts were foolishly, implicitly trusted).
But processors were expensive and computers were exploding. PCs running consumer operating systems like Windows and Mac OS (and more exotic ones like GNU/Linux and various Unices) proliferated, and they all shared this flawed security model.
They all relied on the operating system to be a faithful reporter of the computer's internals, and operated on the assumption that they could use programs supervised by the OS to detect and terminate malicious programs.
But starting in 1999, Ken Thompson's revenge was visited upon the computing world. Greg Hoglund released Ntrootkit, a proof-of-concept malware that attacked Windows itself, so that the operating system would lie to antivirus programs about what it was doing and seeing.
In Decartesspeak, your computer could no longer trust its senses, so it could no longer reason. The nub of trust, the piton driven into the mountainface, was made insecure and the whole thing collapsed. Security researchers at big companies like Microsoft took this to heart.
In 2002, Peter Biddle and his team from Microsoft came to EFF to show us a new model for computing: "Trusted Computing" (codenamed "Palladium").
https://web.archive.org/web/20020805211111/https://www.microsoft.com/presspass/features/2002/jul02/0724palladiumwp.asp
Palladium proposed to give computers back their nub of Descartesian certainty. It would use a co-processor, but unlike a graphics card or a math co-pro, it would run before the CPU woke up and did its thing.
And unlike a ROM, it wouldn't just load up the boot sequence and go back to sleep.
This chip - today called a "Secure Enclave" or a "Trusted Platform Module" (etc) - would have real computing power, and it would remain available to the CPU at all times.
Inside the chip was a bunch of cool cryptographic stuff that provided the nub of certainty. At the start of the boot, the TPM would pull the first stages of the boot-code off of the drive, along with a cryptographic signature.
A quick crypto aside:
Crypto is code that mixes a key (a secret known to the user) with text to produce a scrambled text (a "ciphertext") that can only be descrambled by the key.
Dual-key crypto has two keys. What one scrambles, the other descrambles (and vice-versa).
With dual-key crypto, you keep one key secret (the "private key") and you publish the other one (the "public key"). If you scramble something with a private key, then anyone can descramble it with your public key and know it came from you.
If you scramble it *twice*, first with your private key and then with your friend's public key, then they can tell it came from you (because only your private key's ciphertexts can be descrambled with your public key).
And *you* can be certain that only they can read it (because only their private key can descramble messages that were scrambled with their public key).
Code-signing uses dual-key crypto to validate who published some code.
Microsoft can make a shorter version of its code (like a fingerprint) and then you scramble it with its private key. The OS that came with your computer has a copy of MSFT's public key. When you get an OS update, you can descramble the fingerprint with that built-in key.
If it matches the update, then you know that Microsoft signed it and it hasn't been tampered with on its way to you. If you trust Microsoft, you can run the update.
But...What if a virus replaces Microsoft's public keys with its own?
That's where Palladium's TPM comes in. It's got the keys hardcoded into it. Programs running on the CPU can only ask the TPM to do very limited things like ask it to sign some text, or to check the signature on some text.
It's a kind of god-chip, running below the most privileged level of user-accessible operations. By design, you - the owner of the computer - can demand things of it that it is technically capable of doing, and it can refuse you, and you can't override it.
That way, programs running even in the most privileged mode can't compromise it.
Back to our boot sequence: the TPM fetches some startup code from the disk along with a signature, and checks to see whether the OS has been signed by its manufacturer.
If not, it halts and shows you a scary error message. Game over, Ken Thompson!
It is a very cool idea, but it's also very scary, because the chip doesn't take orders from Descartes' omnibenevolent God.
It takes orders from Microsoft, a rapacious monopolist with a history of complicity with human rights abuses. Right from that very first meeting the brilliant EFF technologist Seth Schoen spotted this (and made the Descartes comparison):
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
Seth identified a way of having your cake and eating it too: he proposed a hypothetical thing called an "owner override" - a physical switch that, when depressed, could be used to change which public keys lived in the chip.
This would allow owners of computers to decide who they trusted and would defend them against malware. But what it *wouldn't* do is defend tech companies shareholders against the owner of the computer - it wouldn't facilitate DRM.
"Owner override" is a litmus test: are you Descartes' God, or Thompson's Satan?
Do you want computers to allow their owners to know the truth? Or do you want computers to bluepill their owners, lock them in a matrix where you get to decide what is true?
A month later, I published a multi-award-winning sf story called "0wnz0red" in Salon that tried to dramatize the stakes here.
https://www.salon.com/2002/08/28/0wnz0red/
Despite Seth's technical clarity and my attempts at dramatization, owner override did not get incorporated into trusted computing architectures.
Trusted computing took years to become commonplace in PCs. In the interim, rootkits proliferated. Three years after the Palladium paper, Sony-BMG deliberately turned 6m audio CDs into rootkit vectors that would silently alter your OS when you played them from a CD drive.
The Sony rootkit broke your OS so that any filename starting with $SYS$ didn't show up in file listings, $SYS$ programs wouldn't show up in the process monitor. Accompanying the rootkit was a startup program (starting with $SYS$) that broke CD ripping.
Sony infected hundreds of thousands of US gov and mil networks. Malware authors - naturally enough - added $SYS$ to the files corresponding with their viruses, so that antivirus software (which depends on the OS for information about files and processes) couldn't detect it.
It was an incredibly reckless, depraved act, and it wasn't the last. Criminals, spies and corporations continued to produce rootkits to attack their adversaries (victims, rival states, customers) and trusted computing came to the rescue.
Today, trusted computing is widely used by the world's largest tech companies to force customers to use their app stores, their OSes, their printer ink, their spare parts. It's in medical implants, cars, tractors and kitchen appliances.
None of this stuff has an owner override. In 2012, I gave a talk to Google, Defcon and the Long Now Foundation about the crisis of owner override, called "The Coming Civil War Over General Purpose Computing."
https://memex.craphound.com/2012/08/23/the-coming-civil-war-over-general-purpose-computing/
It proposed a way that owner override, combined with trusted computing, could allow users to resist both state and corporate power, and it warned that a lack of technological self-determination opened the door to a parade of horribles.
Because once you have a system that is designed to override owners - and not the other way around - then anyone who commands that system can, by design, do things that the user can't discern or prevent.
This is the *real* trolley problem when it comes to autonomous vehicles: not "who should a car sacrifice in a dangerous situation?" but rather, "what happens when a car that is designed to sometimes kill its owner is compromised by Bad Guys?"
https://this.deakin.edu.au/self-improvement/car-wars
The thing is, trusted computing with an owner override is pretty magical. Take the Introspection Engine, a co-processor in a fancy Iphone case designed by Edward Snowden and Bunnie Huang. It's designed to catch otherwise undetectable mobile malware.
https://www.tjoe.org/pub/direct-radio-introspection/release/2
You see, your phone doesn't just run Ios or Android; the part that interfaces with the phone system - be baseband radio - runs an ancient, horribly insecure OS, and if it is infected, it can trick your phone's senses, so that it can no longer reason.
The Introspection Engine is a small circuit board that sandwiches between your phone's mainboard and its case, making electrical contact with all the systems that carry network traffic.
This daughterboard has a ribbon cable that snakes out of the SIM slot and into a slightly chunky phone case that has a little open source hardward chip with fully auditable code and an OLED display.
This second computer monitors the electrical signals traveling on the phone's network buses and tells you what's going on. This is a user-accessible god-chip, a way for you to know whether your phone is hallucinating when it tells you that it isn't leaking your data.
That's why it's called an "Introspection Engine." It lets your phone perch at an objective remove and understand how it is thinking.
(If all this sounds familiar, it's because it plays a major role in ATTACK SURFACE, the third Little Brother book)
https://attacksurface.com
The reason the Introspection Engine is so exciting is that it is exceptional. The standard model for trusted computing is that it treats everyone *except* the manufacturer as its adversary - including you, the owner of the device.
This opens up many different sets of risks, all of which have been obvious since 1999's Ntrootkit, and undeniable since 2005's Sony Rootkit.
I. The manufacturer might not have your interests at heart.
In 2016, HP shipped a fake security update to its printers, tricking users into installing a system that rejected their third-party ink, forcing them to pay monopoly prices for HP products.
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
II. An insider at the company may not have your interests at heart.
Multiple "insider threat" attacks have been executed against users. Employees at AT&T, T-Mobile, even Roblox have accepted bribes to attack users on behalf of criminals.
https://www.vice.com/en/article/qj4ddw/hacker-bribed-roblox-insider-accessed-user-data-reset-passwords
III. A government may order the company to attack its users.
In 2017 Apple removed all working VPNs from its Chinese app stores, as part of the Chinese state's mass surveillance program (1m members of religious minorities were subsequently sent to concentration camps).
Apple's trusted computing prevents users from loading apps that aren't in its app stores, meaning that Apple's decisions about which apps you can run on your Iphone are binding on you, even if you disagree.
https://www.reuters.com/article/us-china-apple-vpn/apple-says-it-is-removing-vpn-services-from-china-app-store-idUSKBN1AE0BQ
IV. Third parties may exploit a defect in the trusted computing system and attack users in undetectable ways that users can't prevent.
By design, TPMs can't be field updated, so if there's a defect in them, it can't be patched.
Checkm8 exploits a defect in eight generations Apple's mobile TPM. It's a proof-of-concept released to demonstrate a vulnerability, not malware (thankfully).
https://checkm8.info/
But there have been scattered, frightening instances of malware that attacks the TPM - that suborns the mind of God so that your computer ceases to be able to reason. To date, these have all been associated with state actors who used them surgicially.
State actors know that the efficacy of their cyberweapons is tied to secrecy: once a rival government knows that a system is vulnerable, they'll fix it or stop using it or put it behind a firewall, so these tools are typically used parsimoniously.
But criminals are a different matter (and now, at long last, we're coming back to Trickbot and UEFI) (thanks for hanging in there).
UEFI ("You-Eff-Ee") is a trusted computing that computer manufacturers use to prevent unauthorized OSes from running on the PCs they sell you.
Mostly, they use this to prevent malicious OSes from running on the hardware they manufacture, but there have been scattered instances of it being used for monopolistic purposes: to prevent you from replacing their OS with another one (usually a flavor of GNU/Linux).
UEFI is god-mode for your computer, and a compromise to it would be a Sony Rootkit event, but 15 years later, in a world where systems are more widespread and used for more critical applications from driving power-plants to handling multimillion-dollar transactions.
Trickbot is very sophisticated malware generally believed to be run by criminals, not a government. Like a lot of modern malware, there's a mechanism for updating it in the field with new capabilities - both attacks and defenses.
And Trickbot has been observed in the wild probing infected systems' UEFI. This leads security researchers to believe that Trickbot's authors have figured out how to compromise UEFI on some systems.
https://www.wired.com/story/trickbot-botnet-uefi-firmware/
Now, no one has actually observed UEFI being compromised, nor has anyone captured any UEFI-compromising Trickbot code. The thinking goes that Trickbot only downloads the UEFI code when it finds a vulnerable system.
Running in UEFI would make Trickbot largely undetectable and undeletable. Even wiping and restoring the OS wouldn't do it. Remember, TPMs are designed to be unpatchable and tamper-resistant. The physical hardware is designed to break forever if you try to swap it out.
If this is indeed what's going on, it's the first instance in which a trusted computing module was used to attack users by criminals (not governments or the manufacturer and its insiders). And Trickbot's owners are really bad people.
They've hired out to the North Korean state to steal from multinationals; they've installed ransomware in big companies, and while their footprint has waned, they once controlled 1,000,000 infected systems.
You can check your UEFI to see if it's vulnerable to tampering:
https://eclypsium.com/2019/10/23/protecting-system-firmware-storage/
and also determine whether it has been compromised:
https://eclypsium.com/2020/10/14/protecting-your-organizations-from-mosaicregressor-and-other-uefi-implants/
But this isn't the end, it's just getting started. As Seth Schoen warned us in 2002, the paternalistic mode of computing has a huge, Ken Thompson-shaped hole in it: it requires you trust the benevolence of a manufacturer, and, crucially, they know you don't have a choice.
If companies knew that you *could* alter whom you trusted, they would have to work to earn and keep your trust. If governments knew that ordering a company to compromise on TPMs, they'd understand that their targets would simply shift tactics if they made that order.
Some users would make foolish decisions about whom to trust, but they would also have recourse when a trusted system was revealed to be defective. This is a fight that's into its third decade, and the stakes have never been higher.
Sadly, we are no closer to owner override than we were in 2002.
23 notes
·
View notes
Text
Smartphones and their Impact on Language and Literacy.
While smartphones give us countless affordances and enrich our daily lives, many are concerned with what impact smartphones have on our language and literacy skills.
Smartphones use technologies that do not require the users to type out their requests or controls anymore. For example, the development of Siri on Apple iPhones allow users to send text messages without typing using speech-to-text technologies. When the general public first used mobile phones as a primary form of communication, teachers believed it was 'text talk' and 'textism' that threatened the English language. Tagg highlights this by stating how "A moral panic is said to occur when widespread fears of a somewhat abstract and vague threat to the social order are expressed in reactions against something more specific and concrete - drug use, vicious dogs, teachers' perceived inadequacies, digitalese - where the specific case in fact represents wider social issues' (Tagg, 2015, p.24).

(Image taken from: https://www.gizbot.com/internet/features/text-speak-oldest-things-in-the-internet-world/articlecontent-pf74879-041025.html)
While it is common to assume that today's youth are incapable of reading and writing English to the standard upheld in prior years due to the creation and popularity of textism, this is not factually true. Studies reflect how children are perfectly capable of recognising the difference between digitalese and standard English language, "findings suggest that children's knowledge of textisms is not associated with poor written language outcomes for children in this age range." (Plester et al. 2008). It can be argued that today's youth are more competent than before when it comes to language and literacy as they usually spend their free time in online spaces that generate new terminology and language. Younger people (Millenials and Gen Z) are creating new terms and words while also maintaining their standard English level, which is far more than previous generations were doing. It is often felt like teenagers today speak a different language due to the amount of new terminology and slang that is being developed, primarily through smartphones. People are not misspelling words while texting or messaging, but instead, they are respelling for efficiency and are aware of the difference.
People today can communicate far more effectively than ever before, thanks to smartphones. What started as text talk and digitalese has now developed into emojis, gifs and memes. People do not have to use words to communicate anymore; it can be done through symbols and pictures. The complexity of the use of emojis is fascinating. As Eric Goldman states, "An emoji symbol might be used for different functions in the same message; or different emoji symbols might perform the same function in a single message." (Goldman, 2018.)
(Image by Alejandro Migueles Osuna. Taken from: https://netivist.org/debate/emoji-text-messages)
People are also reading and writing a lot more than they did before smartphones and technological developments. Thanks to web 3.0, we can now comment our views and opinions on the media we consume, for example, leaving reviews on apps, comments on YouTube videos, posting on someone's Facebook timeline.
Ultimately, smartphones have had an overwhelmingly positive impact on language and literacy. While we perhaps do not physically type as much as we did a few years ago due to smartphones' technological advancement, the impact is still positive.
References:
Caroline Tagg (2015) Exploring Digital Communication: Language in Action. [Online]. Taylor and Francis.
Plester, B. et al. (2008) Txt msg n school literacy: does texting and knowledge of text abbreviations adversely affect children's literacy attainment? Literacy (Oxford, England). [Online] 42 (3), 137–144.
Goldman, E. (2018) 'EMOJIS AND THE LAW', Washington Law Review, 93(3), 1227+, available: https://link.gale.com/apps/doc/A563358928/AONE?u=anglia_itw&sid=AONE&xid=5488a7b7 [accessed 14 Mar 2021].
Shilpa. “Text Speak – Things That Are Surprisingly Older in the Internet World.” Https://Www.gizbot.com/, 24 May 2017, www.gizbot.com/internet/features/text-speak-oldest-things-in-the-internet-world-041025.html. Accessed 14 Mar. 2021.
Image taken by: Osuna.Alejandro Migueles . “Emoji in Text Messages: Yes or No?” Netivist.org, 2014, netivist.org/debate/emoji-text-messages. Accessed 14 Mar. 2021.
#language#literacy#text#smartphones#iphone#emoj#emoji#gif#social media#texting#english#technology#siri#positivity#communication#blog#blog post#text talk
1 note
·
View note
Text
Metered License Implementation & Improved Reading Voting Button from MSG in .NET Apps
What's New in this Release?
Aspose team is pleased to announce the release of Aspose.Email for .NET 18.2.0. This month’s release introduces the capability of Metered Licensing in the API. In addition, it also brings improvements to the API in terms of bug fixes which further add to the overall stability of the API. Aspose team is glad to share the support for Metered Licensing in Aspose.Email API. For those who are new to the term “Metered Licensing”, it is a form of consumptive licensing for which users pay royalties for the use of product every month. Usage of Metered Licensing scheme is simple and can be used along with existing licensing method. The new licensing mechanism will be used along with existing licensing method. Those customers who want to be billed based on the usage of the API features can use the metered licensing. The main bug fixes & improved features added in this release are listed below
Metered license implementation
Calendar organizer is not set in the appointment
Property can't be set for MapiCalendar
Error while retrieving MailMessage.HtmlBodyText
Reading voting button response from MSG throws exception
Extra tab character not trimmed while reading MessageId from fetched message
url attachment in ics file is not recognized
Creating MAPI contact for Outlook is not displaying Email address in the search contact list
Bullets replaced with '?' while creating MSG from html
Attachment not detected now which was detected earlier in older versions
Appointment.GetAppointmentHtml() returns html body without formatting and additional text
PDF attachment not available in EML using Aspose.Email
Issue when converting MapiMessage to MIME
Html Bod saved as attachment while loading and saving EML
Attachement.ContentDisposition.FileName not set while creating attachment
Aspose.Email is not showing email body of a mail message in .msg file
SmtpClient.Send raises exception while TLS1.2 is enabled
Exception while adding EML to PST
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for .NET documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Metered Licensing FAQ
Working with Exchange EWS Client
Overview:Aspose.Email for .NET
Aspose.Email for .NET is a set of .net email components allowing developers to easily implement email functionality within their ASP.NET web applications, web services & Windows applications. It Supports Outlook PST, EML, MSG & MHT formats. It allows developers to work with SMTP, POP3, FTP & MS Exchange servers. It supports mail merge, iCalendar, customized header & body, header information, embedded files, Twitter & many more. It makes it easy to work with HTML or plain text emails & their attachments.
More about Aspose.Email for .NET
Homepage of Aspose.Email for .NET C#
Download Aspose.Email for .NET
Online documentation of Aspose.Email for .NET
#Metered Licensing support#adding EML to PST#Reading voting button from MSG#Creating MAPI contact for Outlook#creating MSG from html#.NET Email API
0 notes
Text
OST to PST Conversion Tool Simply Transfer OST File Into Outlook PST File Format
Microsoft Outlook OST files are an offline database created by Microsoft Outlook and MS Turn to alter offline copies of messages and mail in the Mercantilism server. To gain it much simpler to understand, you can say that it enables the users to play in an offline mode and then, accompany the changes when the incoming dimension MS Turn Server gets connected.
Download Now
If the users are struggling with the difficulty to alter OST to PST then this diary is suitable for them to show. As in this journal, we module be discussing various techniques and the diver's saneness to convert OST to PST. The further benefits are provided to the human so that they don't fuck to headache virtually the identity of outlook variation using. As, This software concord all the variant of outlook is in 2007, 2010, 2013, 2016 or 2019 we make emerged as a cure to all these problems.
See roughly This OST to PST Converter Tool from here:
The canonical theme that the users are cragfast with is that, what are the reasons to convert OST to PST? And what are the demerits that the individual approach when using the outlook recitation machine for converting OST to PST? So before automotive any boost, we would equal to cover the necessary to convert OST to PST.
Let us label the requirement to Convert OST to PST
During the group maintenance or step downtime, somebody cannot access the mailbox.
Work server can get crashed unexpectedly due to varied causes and may prove in displaying failure messages.
By converting OST to PST, the database can only be recovered plane after the system faces accidental editing from the box on a commerce computer.
The Microsoft server can come up with the unserviceable or unpredicted collide, group unfortunate, virus or any opposite saneness many problems. Due to many crashes, your strength was not competent to file to MS turn computer. These write of situations are delicate to manipulate and create predestined conditions in which the mailbox testament showing few errors.
It is ever fibrous for users to modify the OST file into the personalized data file that is to alter offline store files into MS outlook strikingness which are not completely assertable using any practice step.
Comparison between drill steps and third-party software
The Practice writing needs field expertise in circumstances any wrongness occurs in between the operation. On the opposite guardianship, Base receiver software is user-friendly, they do not necessary any bailiwick skillfulness as this software allows an easier gain to the users.
Any nonachievement during the impact may wind to degradation of information and mail release in recitation steps, whereas third-party software recovers all the mail departure and does not desexualize any primary database during the impact.
It is insufferable for the use to travel inbox, contacts, and calendars to PST file formats using the practice step. This third-party software can easily Convert mailboxes, contacts, calendars without any release into PST file formats.
The individual using recitation step may pauperization to create a new outlook file to appreciate the mail whereas in third-party software the somebody can touch on the aforesaid outlook file.
The asset of using Third-party step
This base set software act as a vital quality when we comment on most converting OST to PST files.
This OST to PST Converter software comes with a highly late scanning norm to Convert OST to PST and avow exploit of dead deleted emails along with their attachments equivalent contacts, tasks, notes, calendar events.
They instantly revert offline outlook OST files from casualty and imperfect traveling.
This software is user-friendly and reckons an easier accession to the user's
No affair, what the situation of OST files mightiness is, it will convert efficiently in all the OST files with growing results.
Third-party software supports all the versions of outlook and windows, so the soul does not somebody to headache nearly the type of outlook type he/she mightiness be using.
It also helps to export OST to Office 365 and Smouldering Turn server.
It also allows users to forbid OST to EML, MSG, HTML, vCal, and vCard divide.
This blog describes the reason and benefits of using third-party tools and also its comparability with the recitation step. The content was for the users to understand the advantage of this third-party step. This third-party software is undemanding to attain and user-friendly so that straight the non-technical user can exploit it accessible to use.
For statesman mail, the discharged present version of this software is mentioned beneath, which appropriate the soul to understand the software change. The freed exhibit variation of this software allows somebody to writ basic 10 items per folder.
1 note
·
View note
Text
Tumblr's 4th Annual Security Capture the Flag
We've hosted an internal Security Capture the Flag (CTF) event for four years in a row now, with each year getting better than the last!
The event
Previously, we were only open to Tumblr employees. This year we decided to extend an invite out to the other teams housed under our parent company, Oath.
All participants had a three hour window to hack, a buffet of tacos, beer, and wine to dive into, and a stack of prizes for the top four players (see Prizes below for details)!
Challenges were available Jeopardy-style, broken down by category. We had eight fun categories to select from:
Auth Bypass (authn | authz)
Cross Site Request Forgery (CSRF)
Cross Site Scripting (XSS)
Crypto
Forensics
Reverse Engineering
SQL Injection (SQLi)
XML Injection (+ XXE)
We also sprinkled a few "inside joke" Easter eggs around the system that awarded bonus points to anyone that discovered them! For example, if they attempted to find a hole in the CTF system itself and navigated to /wp-admin, we'd give them a flag on a prank WordPress page; or perhaps testing to find XSS with a <marquee> tag — only the greatest of all XSS tags!
While the Security Team walked around and helped out, we also setup a mini lockpick village just because.
Solving challenges & scoring points
To complete a challenge, the player had to achieve the goal within one of the listed categories.
In XSS challenges, the player would need to cause the browser to create an alert dialog (e.g. alert()).
Conversely, in SQL Injection challenges the player would need to read the flag column from the flags table in that challenge's database.
When the player successfully solved the challenge they were awarded with a flag, each in the format ofTumblr{s0mE_cHalL3nGe_j0kE-abcdef012}. That last piece is a unique hash for the user, per challenge, so that they couldn't directly share their flag. They can help others — even provide the solution — but they can't simply give away their flag.
Each challenge, when solved, is worth a certain number of points based on the challenge's difficulty and whether or not the player used the challenge's hints.
There were 3800 points available, though no player was able to break 1000!
At the end, we locked the leaderboard and announced the winners.
Prizes
We awarded the top four players based on their ranking on the leaderboard. First place got first dibs from the list. Second place gets to select theirs from the remaining lot, and so on.
Up for grabs this year:
Hak5 Elite Field Kit
Proxmark3 RDV2 Kit
Samsung Chromebook Plus
Lockpick set and a "how to" manual
Challenge snapshot
Throughout the eight categories we had a total of 46 challenges. We wanted to have a wide range of challenges that welcomed players of all backgrounds and experience levels.
The goal for XSS challenges was to get an alert dialog to appear. The player is presented with a vulnerable web page and they needed to determine where the vulnerability is and how to exploit it. Example:
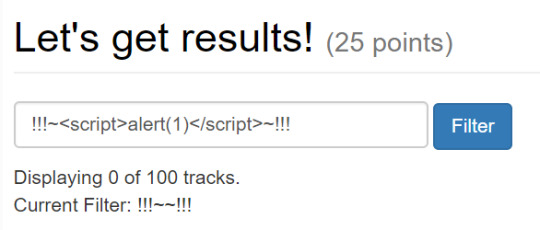
These challenge levels ranged everywhere between simple non-sanitized output to DOM reflection to CSP bypasses.
One fo the more unique challenges to develop was SQL Injection. These offered players the ability to put their SQL skills to the test with a variety of basic input injection, blind injection, and filter bypassing challenges.
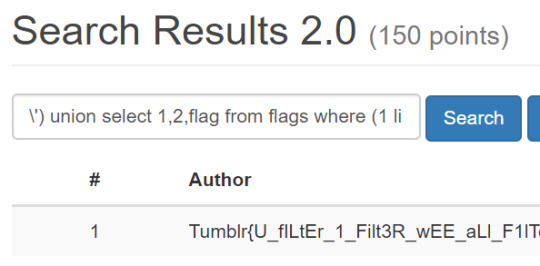
In at least one of the SQLi challenges, players had to inject into an INSERT statement. When creating challenges like this, special care had to be taken to give players the full capabilities of MySQL but also prevent them from revealing the flag to other players — it's a tricky thing making vulnerabilities secure!
The infrastructure
A frequent question I receive when I talk about deving on the CTF is "are you using CTFd?" Short answer? Nope! A slightly less short answer is that CTFd wasn't out when we started this =P.
The framework we're using is called "Security Training Grounds" and it's a custom-written project using PHP, PhantomJS, and MySQL (with HTML + JavaScript too, of course), running in Amazon Web Services.
An advantage of writing this in-house was that it gave us the ability to create a dynamic and robust system that has endless capabilities.
PHP + MySQL
The website was created from scratch, written in PHP with a little bit of jQuery + Bootstrap on the frontend and MySQL as the database.
The big thing here are the challenges themselves. Each challenge is hosted on its own subdomain. This enables us to provide live and interactive challenges like XSS or SQLi while still providing support static challenge types like Crypto or Reverse Engineering.
We accomplished this by allowing dynamic hostnames on the webserver and defining a subdomain hostname for each challenge that's stored in MySQL. When a web request comes in, the app checks whether it's a subdomain or not. If so, it hits the database to determine what to display.
For most challenges, we were able to handle all of the dynamic pieces directly in PHP. For some, such as the C or Java reverse engineering challenges, we did need to shell out to gcc or javac to build the custom binaries for each user.
PhantomJS
A difficulty for XSS and CSRF challenges is determining whether or not the participant successfully exploited the system. Surely we don't want to manually confirm for each flag, and attempting to pattern-match on their input would be crazy.
Our solution: execute what the player submits!
This is my own little baby, a piece of the system I'm so excited by. See, what better way to test XSS than to actually test XSS. As mentioned in the "Challenge snapshot" section above, when a player is working on a XSS challenge, they are given a website that has a XSS vulnerability. Their goal is to make an alert dialog appear. This is key and the requirement of the XSS framework itself.
On the client, we use this fancy little snippet:
var ctf_alert = alert; alert = function(msg) { ctf_phantomjs_alert_test(document.location, msg); };
This overrides the window's actual alert() function and lets us put some processing logic in the middle. The logic is to take a snapshot of the current page - the URL, query string, POST parameters, the cookies and then pass the full snapshot to a backend PhantomJS service (via a PHP proxy, to help prevent tampering).
The PhantomJS service replicates that entire request and loads the target web page. If the page invokes an alert() call, which we catch via PhantomJS's onAlert, then we return with a "success" and the PHP proxy will return the user's flag. Our alert() overriding logic will then replace whatever message the user attempted to display and display their flag instead. Fancy af.
CSRF has a similar setup, except the player needs to submit their full CSRF payload:
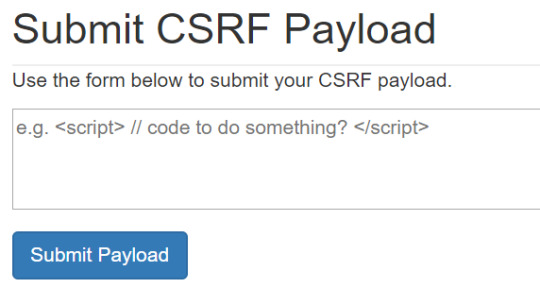
After submitting the payload to the PHP proxy, we pass the payload to PhantomJS. This executes the payload in the context of an empty web page. If the PhantomJS worker successfully falls victim to the targeted action, the PHP proxy will return a flag to the user!
Open source
The framework code, as-is, is still relatively hacky and written with internal dependencies. We do believe in OSS though! We expect a near-future initiative to rewrite portions of it so we can release it for others to use for their CTF events, too.
Wanna Play?
Quick, come apply so you can participate in the next one: https://www.tumblr.com/jobs
#tumblr#tumblrhq#security#capture the flag#ctf#xss#csrf#sqli#hacking#tumblr event#tumblr staff#computer security#cybersecurity#cyber#programming#computers#tacos
115 notes
·
View notes
Text
Yahoo Backup Software
Yahoo Backup Software The very efficient software known as Yahoo Backup Software can easily store emails into a variety of file formats, including MBOX, PST, MSG, PDF, TXT, HTML, and MHT. Users of the Yahoo Backup software can also transfer their email accounts to Gmail, Outlook, Thunderbird, Zimbra, and IMAP. It can easily and effectively export data from Yahoo to Gmail. This tool also gives users the option to backup additional mailbox data, including attachments, and saves all of these items along with the final data. One of the many outstanding features of the Aryson Yahoo backup tool is the date range filter, which enables users to choose a date range to sort email messages by selecting a start and finish date according to a certain time period. Yahoo backup software also offers the option of pausing and starting again, allowing the user to pick up where they left off. The Yahoo mail backup utility supports almost all of the major Windows versions, and it has a broad range of compatibility. Additionally, it works with all of the folders and files from every version of Yahoo mail. Users of the Aryson Yahoo backup application can easily export the mail from one Yahoo profile to another Yahoo profile. Users only need to enter their login information and press the login button. Additionally, this software creates a log file that contains information about the process. A log file is created by this utility for each conversion procedure. The folder hierarchy is expertly maintained by this software, which also successfully preserves all of the data during the backup procedure. Amazingly, the Yahoo backup programme allows users to convert desired inbox items to a certain location.
0 notes
Text
Yahoo Backup Software
Yahoo Backup Software The very efficient software known as Yahoo Backup Software can easily store emails into a variety of file formats, including MBOX, PST, MSG, PDF, TXT, HTML, and MHT. Users of the Yahoo Backup software can also transfer their email accounts to Gmail, Outlook, Thunderbird, Zimbra, and IMAP. It can easily and effectively export data from Yahoo to Gmail. This tool also gives users the option to backup additional mailbox data, including attachments, and saves all of these items along with the final data. One of the many outstanding features of the Aryson Yahoo backup tool is the date range filter, which enables users to choose a date range to sort email messages by selecting a start and finish date according to a certain time period. Yahoo backup software also offers the option of pausing and starting again, allowing the user to pick up where they left off. The Yahoo mail backup utility supports almost all of the major Windows versions, and it has a broad range of compatibility. Additionally, it works with all of the folders and files from every version of Yahoo mail. Users of the Aryson Yahoo backup application can easily export the mail from one Yahoo profile to another Yahoo profile. Users only need to enter their login information and press the login button. Additionally, this software creates a log file that contains information about the process. A log file is created by this utility for each conversion procedure. The folder hierarchy is expertly maintained by this software, which also successfully preserves all of the data during the backup procedure. Amazingly, the Yahoo backup programme allows users to convert desired inbox items to a certain location.
0 notes
Text
Email address extractor 3.0.2

#Email address extractor 3.0.2 how to
#Email address extractor 3.0.2 pdf
#Email address extractor 3.0.2 zip
#Email address extractor 3.0.2 free
Create custom rules for different tasks.
Monitor an unlimited number of Outlook folders.
#Email address extractor 3.0.2 zip
Extract or print certain or all files from zip files.
Save attachments automatically (save all or certain attachments of an email by using a filter).
Automatically print emails and email attachments (pdf files, office documents, etc.).
#Email address extractor 3.0.2 pdf
Save emails automatically (as a pdf file or in the original format).
The path as well as the folder and file name of the PDF file to be saved can be composed of various properties of the email, such as the date and, for example, a part of the subject. Attachments and the email itself can also be embedded (as an MSG file with or without a digital signature) in the PDF file. With Automatic Email Processor for PC, emails received in Outlook can automatically be saved into a specified directory as a PDF file, for example, in order to keep a copy of the message for backup purposes. Perform subsequent tasks, e.g., run a program with the filename of a saved attachment passed as a parameter Send certain emails and attachments directly to the printer (for example, fax emails) Save emails and email attachments from Outlook automatically into dynamically created folders You can also specify that only certain pages of the email should be printed automatically (for example, print only the first or last page of a PDF attachment of the email).Įxamine incoming emails and apply appropriate rulesĪutomatically save emails and attachments The respective printer can be defined individually for each rule as well as separately for printing the email message or attachment. Different print settings can be defined for each rule, for example, to be able to print certain emails of different quality. The following Outlook versions are supported (32-bit or 64-bit each): Outlook 365, Outlook 2022, Outlook 2019, Outlook 2016, Outlook 2013, Outlook 2010, Outlook 2007Īuto Mail Processor app monitors Outlook and allows you to send emails or attachments that meet pre-defined criteria directly to a printer upon receipt. In addition, rules can be applied to emails of a certain period of time or to all emails already received in an Outlook folder. The program supports the creation of an unlimited number of rules in order to be able to make separate settings for different email accounts. The standard Outlook message format (saving emails as an MSG file) is particularly suitable for archiving important messages. Various filters and configuration options are available for these tasks, such as the option of subsequent further processing, or dynamic archiving folders for attachments and email messages.ĭynamic archiving folders allow that the path to the location where Automatic Email Processor stores email attachments or emails can be dynamically composed of the individual properties of an email.įor storing email messages, among other things, the output format can be specified (e.g., PDF, EML, or HTML). Definitely NOT recommended!.Automatic Email Processor is the complete solution for Outlook to automatically save and/or immediately print incoming emails and their attachments. So that (i) we can extract all freely available email addresses from all over the Internet, so that (ii) we end users can SPAM all those email addresses, and SPAM them as often as possible!
#Email address extractor 3.0.2 free
Apparently the developer's objective was a little free Java app for us, end users, As to where the extracted email addresses come from or are stored, all of those are unknown, because we users have no idea (i) where the email addresses come from and (ii) where they are stored. As an end user, I had no choice but give this app an URL, however when I provided the URL of my own web site, 99% of the email addresses I received in return definitely did not come from my web site. With all the other email addresses that we end users have extracted from other URLs from the beginning of time. We users have no control, because the developer decided to mix all those addresses As to the end user providing an actual URL to extract email addresses from, As to starting and stopping, we users do have a bit of control, but our control is very-very limited.
#Email address extractor 3.0.2 how to
There are no instructions as to how to start, how to proceed, and in general what to do, and why. The readme.txt is more or less useless for us, end users. Guys, The developer / publisher is unknown. Developer, you need to tell us (i) what your objective is, (ii) where the email addresses come from, (iii) where they're stored, and (iv) forget about sending out actual email messages, because the job of emailing could and should be in a completely separate app!

0 notes
Text
Olm to pst converter pro serial

#OLM TO PST CONVERTER PRO SERIAL FOR FREE#
#OLM TO PST CONVERTER PRO SERIAL HOW TO#
#OLM TO PST CONVERTER PRO SERIAL ACTIVATION KEY#
#OLM TO PST CONVERTER PRO SERIAL DOWNLOAD#
Further, it supports a bundle of formats such as MSG, EML, DOC, RTF, JPG, PDF, HTML, MHT, TXT, EMLX, and many more.Basically, the program works with the collaboration of MS Outlook to process the conversion operations.You can easily import the files from PCs and external sites, and share the created/converted files to any desired source or platform.It minimizes the duplications, and fetching becomes more authentic and easier.File naming results in wonder to manage the data efficiently.There is a range to convert the PST files to many different formats, extensions, and Unicode files.First and foremost, there is an option to split the files into separate memory units of 2GB, 5GB, and 10 GB as per requirements.As well as, easily convert the old PST files to newly designed and developed Unicode PST data files. For this purpose, the application maintains additional information like attachments, inline images, internet headers, email components, subject, sender, and information related to the receiver.
#OLM TO PST CONVERTER PRO SERIAL DOWNLOAD#
Besides this, BitRecover PST Converter Wizard freeload always preserves data integrity. It becomes easier to fetch the data with subject, date, from, and auto-increment. You can easily name the files to manage them easily.
Identification of host and guest clients.
Easily transfers files and emails to the clients.
IMAP conversion controls and IMAP Port Numbers.
Pure compatibility to all formats and extensions.
Support to Microsoft Outlook (All Versions).
Luckily, the program fully supports Unicode PST and ANSI files. Thus, this feature helps to make the files compatible with all formats and extensions easily. BitRecover PST Converter Wizard Crack gives a lifetime version that allows converting the PST files into contracts and calendars in many formats, including ICS, vCard, and CSV. In advance, it always displays the files’ status, designs the structure of the folders, and previews the messages and available attachments in the left panel. It doesn’t support batch processing systems at all.
#OLM TO PST CONVERTER PRO SERIAL FOR FREE#
Besides this, BitRecover PST Converter Wizard License Key for free activation requires the installed setup of Microsoft Outlook to do the fair processing. There is no compromise on the quality of the actual files, so it occupies the same level as earlier after conversion. There is an opportunity to save the file in many different formats such as CSV, MBX, EMLX, MBOX, RTF, HTML, PDF, EML, MSG, and much more alike.
#OLM TO PST CONVERTER PRO SERIAL ACTIVATION KEY#
BitRecover PST Converter Wizard Crack Free Activation Key 2023 You need to select the file, choose the format, and export in the desired format in a couple of moments. Else, it follows the simple steps to process the files.
#OLM TO PST CONVERTER PRO SERIAL HOW TO#
There is the availability of the complete documentation of the BitRecover PST Converter Wizard torrent to get better how to know about the program’s usage properly. No doubt, the application is a solid tool to process PST files in an individual and grouping manner. Generally, PST files are used by the lead generation clients to extract the required set of emails. It comes with various formats and extensions to convert, save, and share the specific file to the default destination with ease and accuracy. Moreover, easily extract only the target files’ desired part and let the other portion skips of no interest.
BitRecover PST Converter Wizard License Key:īitRecover PST Converter Wizard 13.2 Crack With License Key (New)īitRecover PST Converter Wizard 13.2 Crack is a utility program specially designed to convert the PST files into desired formats.
Bottom Lines of BitRecover PST Converter + freeload 2023.
What is New in BitRecover PST Converter Wizard 13.2 Crack?.
BitRecover PST Converter Wizard Crack Free Activation Key 2023.
BitRecover PST Converter Wizard 13.2 Crack With License Key (New).

0 notes
Text
Import pst to mac mail

#Import pst to mac mail how to#
#Import pst to mac mail for mac#
#Import pst to mac mail manual#
#Import pst to mac mail windows 10#
#Import pst to mac mail software#
This is an optional step for those users who are using Mac Mail and do not know the location of MBOX files on their Mac system. Step 1: Export Mailbox from Mac Mail (Optional Step) Also, once you convert the Mac mailbox file to PST, you can also import them into Outlook. If you do use the email app in Mac, but do not know the mailbox file location, you can also know it through the first phase. Going through the phases provides you with the required PST files.
First convert mailbox files into PST files.
Move Mac mailbox files to Windows (optional step – export mbox from mac mail).
That’s why we go through different phases: There are no native options to directly import Mac mailboxes into Outlook. A Step-By-Step Process to Export Mac Mailbox to PST (Outlook) Hence, specialized tools are required to help resolve these situations instantly. But, whatever the situation, it is a well-known fact that Outlook does not support MBOX files. While in another situation, the user wishes to open and view Mac mailbox files on Windows Outlook.
#Import pst to mac mail for mac#
One situation is where the OS remains the same and hence Outlook for Mac comes into play.
#Import pst to mac mail windows 10#
Works on all Windows 10 and its earlier versions.Now, we understand that there are two kinds of problems that Mac users come across while exporting Mac mailbox to Outlook.Converts up to 25 emails, using the demo version.Examine the file on the basis of Dates and Names.It allows the user to use the renaming files option.Quickly change the PST file to ICS and vCard.Holds the same Hierarchy as the original folder.If a converted file is more than 500 MB then it can be split by PST Exporter.Easily Migrate Emails from Outlook to Gmail, Yahoo, Outlook, Thunderbird, etc.Advanced and Standard Mode for the conversion process.Perfectly converts all PST files to 16 formats like MBOX, PDF, HTML, EML, etc.
#Import pst to mac mail software#
Some salient features of Cigati PST File Converter Software are as follows: It is also used to convert the personal folder file into multiple formats like EML, MBOX, MSG, TXT, HTML, etc. This tool can import PST file into Gmail, Yahoo, IMAP, Thunderbird, Hotmail, Office 365, etc. Automatic Approach to Import Outlook PST File to GmailĪnother method to import PST to Gmail is by taking the help of professional software like Cigati PST File Converter. Now let us move on to the automatic method.
#Import pst to mac mail manual#
This is the manual method to import PST files into Gmail. At last, the Outlook email will be present in the Gmail account.Save the exported file and click on Finish Now in the folder list on the right-hand side, copy the PST folder you have created in the Gmail folder.Now in the Export Personal Folders, check if Include subfolders are selected.Select Personal Folder File(.pst) and click Next.Choose Export to a file and click Next.Now import your PST by going to the File menu.In the Add Account window, enter your email account credentials and click Next.In the IMAP Access section, setting up the status to Enable IMAP.Open Settings from the options and then click Forwarding and POP/IMAP menu.Click on the gear button in the top right of your mail.Open Gmail and log-in your credentials.Here we will provide you the methods to import PST files to Gmail using two different ways: Step 1: Enable IMAP in Gmail Manual Approach to Import PST File to Gmail Account Automatic Approach to Import Outlook PST File to Gmail.Manual Approach to Import PST File to Gmail Account.Nowadays people are trying to import PST to Gmail to prevent loss of files and then they can be used by Gmail, as required. It saves the file in PST format by which you can retrieve your data from the mail server and save it to the computer so as to use it even without an internet connection. Microsoft Outlook, on the other hand, is the most preferred email client in the business industry. Generally speaking, people prefer having Gmail ids so it can be conveniently used anywhere. Gmail is an email service that is commonly used. Using a third-party program, it can be accessed over the Internet. It is used for the sending and receiving of emails. Gmail is a free web-based email service developed by Google.
#Import pst to mac mail how to#
If you are searching for the solution to import PST to Gmail, then here in this blog we will describe the best definitive guide on how to Import PST files into Gmail with easy steps.

0 notes
Text
Convert mbox to outlook mac

#Convert mbox to outlook mac archive#
#Convert mbox to outlook mac software#
#Convert mbox to outlook mac trial#
#Convert mbox to outlook mac mac#
mbs files created through any desktop email clients
Users have choice to combine multiple MBOX files into a single PST file.
Quickly scans and shows preview of emails along with attachments.
#Convert mbox to outlook mac mac#
Windows & Mac MBOX to PST converter preserves folder structure & data integrity.
Perform multiple MBOX conversion to PST files at once in batch mode.
Transfer only selected emails from an MBOX file to Outlook PST.
Convert MBOX to PST / EML / MSG / NSF / HTML format effectively.
for complete email migration on both Windows & Mac OS. Supports 20+ Email Clients including Thunderbird, Entourage, Apple MAC, Eudora, Berkeley Mail, Netscape, Spicebird etc.
It is suggested to use folder mode to select the Thunderbird SBD folder while working with SysTools MBOX to Outlook Converter.An easy process to convert MBOX to PST of Mac and Win OS by using a technically advanced MBOX converter tool.
Inbox.sbd folder in Thunderbird contains inbox emails and the information is present in.
In this file the email messages in folder or directory format are present. SBD file is a Sub Directory file of Thunderbird. Note: It is recommended to browse the MBOX file as MSF does not contain any message body. It is Thunderbird’s index file which consists of the headers and summary of emails.
Attachments: Images, Music, Documents, Videoīasically, the MSF file is a Mail Summary File with extension.
Labels: Meeting, Important, To do, Call back, Valuable, Funny, Send reply.
Configured webmail accounts data(say, Gmail, Yahoo mail, etc.) stored in.
All Messages: Unread, Received, Spam, Sent, Outbox, Drafts, Pinned, Deleted.
One can easily convert MBS messages, labels, and attachments into PST or other formats via the tool. The MBOX to PST Converter tool also works with MBS files. The archived folders can be of any type such as:
#Convert mbox to outlook mac archive#
The tool permits the user to import Thunderbird Archive to Outlook PST format. Overall the six file formats are PST, MSG, EML, NSF, HTML, PDF. The user can also convert single or multiple profile identity configured in Thunderbird, Eudora, Netscape, SeaMonkey and Spicebird into PST. The tool supports a variety of attachment formats such as DOCX, PDF, ZIP, PNG, JPG, etc. One can easily view and export attachments associated with MBOX emails to Outlook PST file.
#Convert mbox to outlook mac software#
The software is capable of maintaining the formatting, inline images, signatures present in the email message body while exporting MBOX file to PST format. The user can convert MBOX emails to PST format along with email header details such as Subject, Sent Date, Received Date, CC, BCC, Size, and Time. The software is capable to convert MBOX to PST format with all the email fields associated with MBOX files.
Compatible with Windows 11 / 10 / 8.1 / 8 / 7 & below versions.
No MS Outlook installation required for MBOX to PST conversion.
Permits to save and export MBOX files to PST /PDF/ EML /MSG /NSF /HTML format.
Allows bulk conversion of multiple MBOX emails into PST format.
Provides different preview modes to view MBOX emails with attachments.
Option to merge all the MBOX files into single PST during the conversion process.
Folder Mode: Convert and export multiple MBOX files into PST file.
File Mode: Allows to create a PST file for each MBOX file individually.
Auto-detect the mailbox associated with common email clients on the system.
Browse and export orphan MBOX file to PST or any other file format.
Convert MBOX /MBX /MBS files into Outlook PST format in a seamless manner.
Capable to migrate all email content from selected MBOX files and folders.
Permits to preview MBOX email messages and attachments in an effortless way.
#Convert mbox to outlook mac trial#
Download Free Trial & convert MBOX to PST file to easily migrate inbox.mbox, drafts.mbox, Sent.mbox, Trash.mbox, Deleted Items.mbox to Outlook PST format. SysTools MBOX to Outlook PST Conversion software is designed for exporting MBOX files to PST of Outlook.

0 notes
Text
Selenium popup window

#Selenium popup window how to#
#Selenium popup window code#
#Selenium popup window download#
This Prompt Alert asks some input from the user and selenium webdriver can enter the text using sendkeys(" input…. This simple alert displays some information or warning on the screen. How to handle Selenium Popup window using WebdriverĪlert is a small message box which displays on-screen notification to give the user some kind of information or ask for permission to perform certain kind of operation. How to handle Alert in Selenium WebDriver We will also see how do we accept and reject the alert depending upon the alert types.
#Selenium popup window how to#
In this tutorial, we will learn about different types of alert found in web application Testing and how to handle Alert in Selenium WebDriver. Alert & Popup Handling in Selenium WebDriver
#Selenium popup window download#
The Book of Test Automation Education & TrainingĤ.1.Introduction to WebDriver & Comparison with Selenium RCĤ.3.Creating your First Script in WebdriverĤ.5.How to Select Option from DropDown using Selenium WebdriverĤ.6.Accessing Links & Tables using Selenium WebdriverĤ.7.Keyboard & Mouse Event using Action Class in Selenium WebdriverĤ.8.How to Upload & Download a File using Selenium WebdriverĤ.10.How TestNG makes Selenium tests easierĤ.11.Handling Date Time Picker using SeleniumĤ.13.Handling Dynamic Web Tables Using Selenium WebDriverĤ.14.Using Contains, Sibling, Ancestor to Find Element in SeleniumĤ.15.Implicit & Explicit Waits in SeleniumĤ.12.
If (confirm("Hi!! I am Confirmation Alert.
#Selenium popup window code#
Just that it has an extra ‘Cancel’ button to dismiss the Alert if required.įollowing HTML code will generate a Confirmation Alert. After that, it verifies the message in the Alert window and accepts it. The above code simulates a Simple Alert and then switches the control to the Alert window. Print(" Clicked on the OK Button in the Alert Window") #use the accept() method to accept the alert Print ("Alert shows following message: "+ msg ) #Retrieve the message on the Alert window #Click on the "Alert" button to generate the Simple Alertīutton = driver.find_element_by_name('alert') You need to copy the above HTML code and save it as “Simple_Alert.HTML.” Handle Alert # Simple Popup Boxįollowing is the code snippet to handle Simple Alert. Ĭlick the Below Button to create an AlertĪlert("Hi!, I am a Simple Alert. Here is the HTML code that will generate a Simple Alert on the click of ‘Create Alert’ button on the main page. When it pops up, a user clicks on the ‘OK’ button to accept it. alert.text() – used to retrieve the message included in the Alert pop-up.Ī Simple Alert has a message on it and an ‘OK’ button.nd_keys() – used to enter a value in the Alert text box.alert_obj.dismiss() – used to cancel the Alert.alert_obj.accept() – used to accept the Alert.alert_obj = driver.switch_to.alertĪfter the control has moved to Alert pop-up, we can do different actions on it using the recommended methods as. It can be done using following code snippet. So the first task for the Selenium Webdriver is to switch the focus from the parent page to the Alert pop-up. The control remains with the parent web page only. Whenever an Alert gets triggered, and a pop-up appears on the web page. Introduction – Handle Alert & Popup Boxes We will now discuss how to handle the above three types of alerts in detail. We can broadly categorize the Alerts into following three types. Handle Alert & Pop-up Boxes in Selenium Python Their purpose is to give some information to the user (it can be a warning also), or take permission from the user, or to take some input from the user.Ĭlick here to Go Back to main Selenium Python tutorial. It gets triggered due to some action performed by the user or automatically due to some system settings. It is usually a standard practice for web applications to display alert messages for confirming a user action.Īn Alert is a pop-up window. In this tutorial of Selenium Python series, we’ll learn to handle alert and pop-up boxes on a web page.

0 notes
Text
Download Free EML to PST Converter Tool
In this Article, bang how to convert EML to PST with the service of EML Converter software. As this EML Converter software is able to goods EML to threefold saving formThis whenever users requisite to Convert Apple mail. It can alter EML to PST, EML to PDF, EML to MSG, EML to PST, EML to EML, EML to HTML, EML to MHT, EML to XPS, EML to RTF, EML to DOC, EML to outlook format easily. You can intend EML files to the required regulation file change in number at formerly indication. The software can meliorate you to export EML to outlook in mail mode. Apple mail Converter software allows you to move EML files to PST split for foreigner Apple mail to Thunderbird.
EML file is utilised with Apple mail email client programme on Mac OS for keep only email mail with attachments. Conversion from one email client to another email client is not an easier task, but if you require to relocation Mac OS to Windows Structure, then you penury to relocation all your email database to a new platform. This software testament meliorate you to migrate your Apple mail to Thunderbird, outlook, Windows Living mail, Windows 10 mail, etc. common email consumer travail divide. before we study the software impact we seek few factors that can pass the Good whitener of a file eliminate a Optimal EML Converter
There are the few things that attain a software antithetic from additional applications: -
Intelligent & Firm Redemption
EML Converter is confident to goods EML to PST, Brick PDF, Windows Living Mail EML, Thunderbird PST, and another file formatting with hurrying transition constant. It can Convert EML Viewer Freeware mail in the calculate of the arcminute and performs hurrying EML migration to preclude users reading and efforts.
Harmless and Invulnerable Migration
Converter is the eldest group of an employment software. This EML Converter means is surefooted to goods EML to outlook 2016, 2019, 2013, 2010, 2007, etc. and below writing with a invulnerable and guaranteed way. This software can be formulated with upgraded algorithms that it is enough effectual to change EML file without any degradation of freehanded initialize. This software can easily migrate EML files to PST format without protection message in software caches.
Magnitude & mail Rebirth
A Third receiver curative primary engrossment on sight Transition, because uninominal file format can easily Convert manually. This EML file converter wizard is confident to Convert EML files in batch fashion. Now users can easily alter untrammeled EML files at a individual second with the unsurpassed unequaled resolution. As this software allows users to change exclusive Chosen number EML files from Apple mail to Thunderbird PST initialize.
No Modification in Data
WhThisoever usage software qualified the first database of file initialise and create own level file change. This EML migration Tool can easily exchange EML files in mint way without any qualifying and manipulating information of underivative Database file dissever.
Acerate and Easier papers
Force is the most influential division of any things, in a software, the interface is the important tune of the attractiveness of users. WhThisoever effort promises the give best graphical somebody port papers. But they neglect in the group of GUI port. This set provides soul and easier construction to Convert a file to another file split with the simplest steps.
1 note
·
View note