#ctf program
Explore tagged Tumblr posts
Text

With Firefox having AI added in the recent update. Here's how you can disable it.
Open about:config in your browser.Accept the Warning it gives.Search browser.ml and blank all values and set false where necessary as shown in the screenshot, anything that requires a numerical string can be set as 0 .Once you restart you should no longer see the Grey-ed out checkbox checked, and the AI chatbot disabled from ever functioning.
#mozilla#mozilla firefox#firefox#web browsers#pro tip#protips#anti ai#fuck ai#internet#how to#diy#do it yourself#artificial intelligence#signal boost#signal b00st#signal boooooost#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
481 notes
·
View notes
Text

The Air Force placed its initial order for eight new F-15EXs in 2020, and the first aircraft was formally accepted by the service on March 10, 2021, before being ferried to Eglin AFB the following day to begin a dedicated USAF flight-test program run by the CTF. To help expedite the testing needed to declare the F-15EX ready for operations, the team at Eglin leveraged previous test data from F-15 foreign military sales variants and married it up with the limited number of U.S.-only sub-systems and Operational Flight Program (OFP) software that are present on the F-15EX. Jandenth Smith
92 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Note
Hi! You mentioned there are online tutorials/sites for learning Comp Sci and OSINT - any recommendations? Thanks!
Hi! You got lucky that today is the day I check my inbox lol. So. For comp-sci: - CS50X from Harvard is a public avaiable course on youtube I'd 100% recommend. These are the undedited (so far) lectures of 2024: https://www.youtube.com/watch?v=3LPJfIKxwWc&list=PLhQjrBD2T381WAHyx1pq-sBfykqMBI7V4&ab_channel=CS50
This gives you all the basics you need to understand how coding and pcs in general works. (I had comp sci in my university course)
- Freecodecamp is a website full of FREE tutorials on several programming language. Advice: learn python. You will understand later on.
- The rest really depends on what you actually want to learn and why - each programming language has its own purpose and application. OSINT: -There is this full course: https://www.youtube.com/watch?v=qwA6MmbeGNo&t=205s&ab_channel=TheCyberMentor (But you can find more on youtube.) - Bellingcat's resources: https://www.bellingcat.com/category/resources/ -IntelTecniques: https://inteltechniques.com/ - Osint Newesletter: https://osintnewsletter.com/
But here is the catcher: if you plan to do osint it heavily depends on where you live. I'm in Europe, so it means I'm under GDPR, therefore I must abid to stricter regulations than a US OSINT analyst. A lot of data that might be considered public domain in the US(big one: conviction records) are not in europe, and you won't be able to access it unless you are a registered private investigator at least (but in my case it's rare that I go after people, that's not a part of any task I might encounter at work). Not only that, but a lot of the avaiable tools are designed to work only with specific countries in mind for various reasons and there is a big bias on US-based investigations. If youre' not in the US I recommend you reach out to your local OSINT or cybersecurity professionals association, they usually have resources and specific information, a lot of times for free. Also keep in mind: OSINT has a lot of different applications and it depends on what you're doing with it. Journalists might work more with satellites and images (a thing I know nothing about), debunkers will definitely understand social media more, if you do business intelligence you will look more at news sites, trademarks and deposits and so on to reach your conclusion. You did your course... Now what? I recommend getting on CTFs, like tracelabs that I've linked above, but there many of them (osint dojo for example) or Kase Scenarios. These are safe environments to practice on (except for tracelabs since it deal with actual cases of missing people and it can lead to... not so good leads, allow me to leave it there) You should also understand how intelligence (as the discipline) works. There are several resources, but my favourite is definitely Psychology of Intelligence Analysis. It's a series of declassified training documents from CIA analyst Richard Bauer, that was based on Daniel Kahneman (yes, the "thinking fast and slow" author, and I also do recommend this book) research on euristics. Intelligence is fundamental because OSINT might be helpful to gather the data, but the data then needs to be processed, analysed and you also need to get a conclusion from that analysis. Studying intelligence will help you avoid a lot of pitfalls that happens when you do an investigation, such as not understanding when you know enough, if you're being a victim of your own bias, if you're missing something or if you're going with the right approach. But I have to admit that the best of training I've received so far is from my local OSINT association because I've been able to train with people that work(ed) in the military, get their advice and have a deep understand of the work itself (and the reason why I have decided to actually make cyber threat intelligence my job, even if I work for a private company and I have no interest in working for the government). And yes ethics is a big thing for the OSINT community.
I hope this is helpful enough!
10 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes
Text
Matrix Breakout: 2 Morpheus
Hello everyone, it's been a while. :)

Haven't been posting much recently as I haven't really done anything noteworthy- I've just been working on methodologies for different types of penetration tests, nothing interesting enough to write about!
However, I have my methodologies largely covered now and so I'll have the time to do things again. There are a few things I want to look into, particularly binary exploit development and OS level security vulnerabilities, but as a bit of a breather I decided to root Morpheus from VulnHub.
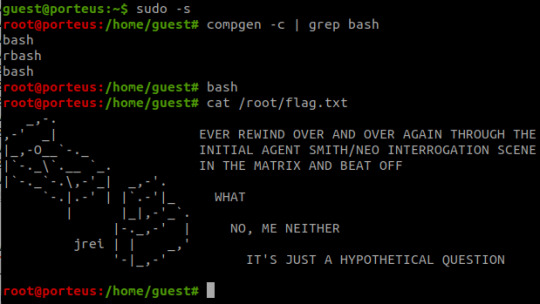
It is rated as medium to hard, however I don't feel there's any real difficulty to it at all.
Initial Foothold
Run the standard nmap scans and 3 open ports will be discovered:
Port 22: SSH
Port 80: HTTP
Port 31337: Elite
I began with the web server listening at port 80.

The landing page is the only page offered- directory enumeration isn't possible as requests to pages just time out. However, there is the hint to "Follow the White Rabbit", along with an image of a rabbit on the page. Inspecting the image of the rabbit led to a hint in the image name- p0rt_31337.png. Would never have rooted this machine if I'd known how unrealistic and CTF-like it was. *sigh*
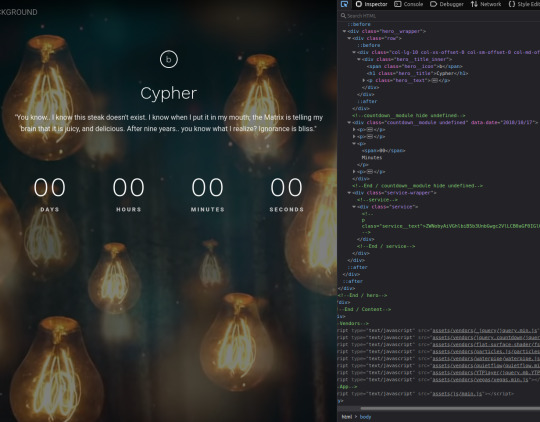
The above is the landing page of the web server listening at port 31337, along with the page's source code. There's a commented out paragraph with a base64 encoded string inside.
The string as it is cannot be decoded, however the part beyond the plus sign can be- it decodes to 'Cypher.matrix'.

This is a file on the web server at port 31337 and visiting it triggers a download. Open the file in a text editor and see this voodoo:
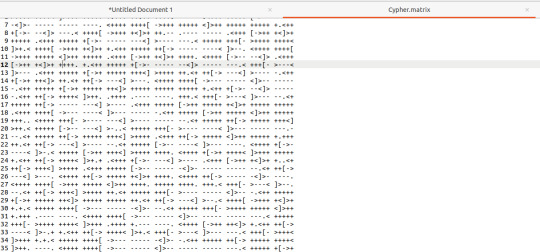
Upon seeing the ciphertext, I was immediately reminded of JSFuck. However, it seemed to include additional characters. It took me a little while of looking around before I came across this cipher identifier.

I'd never heard of Brainfuck, but I was confident this was going to be the in-use encryption cipher due to the similarity in name to JSFuck. So, I brainfucked the cipher and voila, plaintext. :P
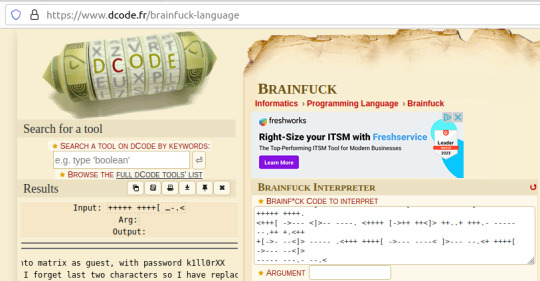
Here, we are given a username and a majority of the password for accessing SSH apart from the last two character that were 'forgotten'.
I used this as an excuse to use some Python- it's been a while and it was a simple script to create. I used the itertools and string modules.
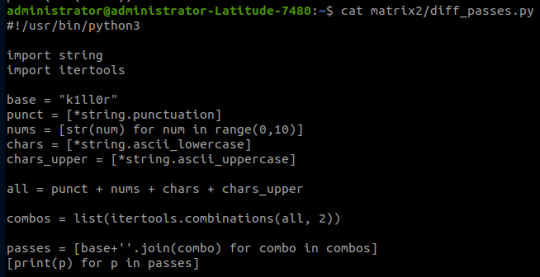
The script generates a password file with the base password 'k1ll0r' along with every possible 2-character combination appended. I simply piped the output into a text file and then ran hydra.
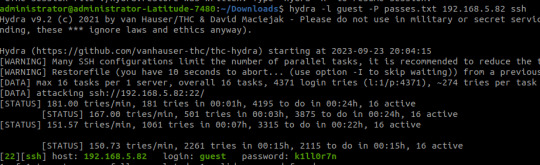
The password is eventually revealed to be 'k1ll0r7n'. Surely enough this grants access to SSH; we are put into an rbash shell with no other shells immediately available. It didn't take me long to discover how to bypass this- I searched 'rbash escape' and came across this helpful cheatsheet from PSJoshi. Surely enough, the first suggested command worked:

The t flag is used to force tty allocation, needed for programs that require user input. The "bash --noprofile" argument will cause bash to be run; it will be in the exec channel rather than the shell channel, thus the need to force tty allocation.
Privilege Escalation
With access to Bash commands now, it is revealed that we have sudo access to everything, making privilege escalation trivial- the same rbash shell is created, but this time bash is directly available.

Thoughts
I did enjoy working on Morpheus- the CTF element of it was fun, and I've never came across rbash before so that was new.
However, it certainly did not live up to the given rating of medium to hard. I'm honestly not sure why it was given such a high rating as the decoding and decryption elements are trivial to overcome if you have a foundational knowledge of hacking and there is alot of information on bypassing rbash.
It also wasn't realistic in any way, really, and the skills required are not going to be quite as relevant in real-world penetration testing (except from the decoding element!)
#brainfuck#decryption#decoding#base64#CTF#vulnhub#cybersecurity#hacking#rbash#matrix#morpheus#cypher
9 notes
·
View notes
Text
AML CTF ACT Tranche 2 for Precious Metal Dealers Explained
Australia’s fight against financial crime continues to evolve, and with it, new industries must adapt to stricter obligations. Among those significantly impacted by the AML CTF ACT Tranche 2 reforms are precious metal dealers. Understanding how these changes affect your business is critical for staying compliant, avoiding penalties, and maintaining customer trust.
This comprehensive guide explains AML CTF ACT Tranche 2 for Precious Metal Dealers, outlines what’s changing, why it matters, and how your business can prepare effectively with practical solutions.
Understanding the AML CTF ACT Tranche 2
Australia’s Anti-Money Laundering and Counter-Terrorism Financing Act 2006 (AML/CTF Act) is the foundation for preventing money laundering and terrorism financing across regulated sectors. Historically, Tranche 1 covered financial institutions like banks, remitters, and gaming providers.
However, criminal activities evolve, and so must the law. To close loopholes, AML CTF ACT Tranche 2 extends these obligations to additional sectors, including precious metal dealers, legal professionals, accountants, and real estate agents.
Under Tranche 2, businesses trading in high-value goods, like gold, silver, diamonds, and other precious metals, are classified as designated non-financial businesses and professions (DNFBPs). This means you’ll soon face the same obligations as traditional financial institutions.
Why Precious Metal Dealers Are in Focus
Precious metals are a prime target for money laundering because they’re high in value, portable, and easily traded across borders. Criminals use precious metals to clean illicit funds, move wealth discreetly, or store assets outside traditional banking systems.
The government’s aim with AML CTF ACT Tranche 2 for Precious Metal Dealers is to tighten oversight and prevent these channels from being exploited.
What Precious Metal Dealers Need to Know
If you buy or sell precious metals, even as part of jewellery, bullion, or scrap, you’ll need to comply with key AML/CTF obligations under Tranche 2. Here’s what you can expect:
1. Customer Due Diligence (CDD)
You must verify the identity of customers before completing significant transactions. This includes robust Know Your Customer (KYC) checks, especially for high-value deals.
2. Transaction Monitoring
Implement systems to detect suspicious patterns or large cash transactions that could indicate money laundering.
3. Record Keeping
Maintain clear, accessible records of all transactions and customer identification documents for at least seven years.
4. Reporting Suspicious Matters
Report suspicious transactions to AUSTRAC, Australia’s financial intelligence unit. Failing to do so can result in hefty fines or prosecution.
5. Develop and Maintain an AML/CTF Program
Create a tailored AML/CTF program outlining your business’s policies, procedures, and controls. This must be reviewed regularly and updated as regulations evolve.
Practical Steps Precious Metal Dealers Should Take Now
Adapting to the AML CTF ACT Tranche 2 for Precious Metal Dealers doesn’t have to be overwhelming if you plan proactively. Here are five practical steps:
1. Assess Your Risk Profile Understand your unique exposure to money laundering risks based on your products, customers, and transaction sizes.
2. Choose Reliable AML Tools Invest in robust AML/CTF software like NameScan’s Screening Solutions. Automated tools streamline ID checks, sanctions screening, and transaction monitoring.
3. Train Your Staff Your employees are your first line of defence. Train them to spot red flags and understand reporting obligations.
4. Consult Compliance Experts Consider seeking advice from AML/CTF compliance specialists to help design and implement your AML program.
5. Stay Updated Regulations evolve, so subscribe to AUSTRAC updates and trusted compliance resources to stay ahead.

Challenges Precious Metal Dealers May Face
While compliance is essential, it comes with challenges, especially for small and medium-sized dealers:
Cost of Implementation: Deploying KYC tools, hiring compliance officers, and updating systems can be costly.
Operational Disruption: New processes may disrupt existing workflows and require retraining staff.
Reputation Risks: Non-compliance or accidental breaches can damage your reputation and customer trust.
This is why partnering with an experienced AML/CTF solutions provider like NameScan is crucial.
How NameScan Supports Precious Metal Dealers
NameScan is your trusted partner for AML CTF ACT Tranche 2 for Precious Metal Dealers. We offer easy-to-integrate tools that help your business meet regulatory requirements with confidence and efficiency.
Key features include:
PEP & Sanctions Screening: Check customers against global watchlists and politically exposed person databases.
ID Verification: Verify identities in real time to satisfy KYC obligations.
Ongoing Monitoring: Automatically detect changes in risk status.
Compliance Reports: Generate detailed reports for audits and AUSTRAC submissions.
By using NameScan, precious metal dealers can safeguard operations while focusing on what they do best — growing their business.
FAQ: AML CTF ACT Tranche 2 for Precious Metal Dealers
1. When will AML CTF ACT Tranche 2 come into effect for precious metal dealers? The Australian government is progressing with Tranche 2 reforms, but implementation timelines are yet to be finalised. Precious metal dealers should prepare now to avoid last-minute compliance gaps.
2. Who is considered a precious metal dealer? Anyone buying, selling, or trading in gold, silver, platinum, palladium, and related high-value products. This includes refiners, jewellers, bullion traders, and scrap dealers.
3. How much is the transaction threshold for CDD? Typically, any transaction over AUD 10,000 will require enhanced due diligence, but thresholds may vary depending on risk factors and future legislative updates.
4. What happens if I don’t comply with AML CTF ACT Tranche 2? Non-compliance can lead to severe civil and criminal penalties, reputational harm, and potential closure of your business operations.
5. How can NameScan help me prepare? NameScan’s AML/CTF solutions help you meet Tranche 2 requirements cost-effectively with automated screening, ID verification, and monitoring — all from an intuitive platform.
Final Thoughts: Get Ready for AML CTF ACT Tranche 2 Today
Precious metal dealers can no longer ignore the rising tide of regulation. Understanding AML CTF ACT Tranche 2 for Precious Metal Dealers is the first step. The next step is taking action to protect your business from compliance risks and criminal exploitation.
By partnering with NameScan, you gain powerful tools, expert guidance, and peace of mind that your AML/CTF obligations are covered.
Ready to Protect Your Business?
Don’t wait until compliance deadlines arrive. Start your journey to stress-free compliance today with NameScan’s tailored solutions for precious metal dealers.
👉 Get Started with NameScan Today
#AML CTF ACT Tranche 2 for Precious Metal Dealers#tranche 2 aml for tcsps#aml/ctf rules in australia#aml ctf rules for lawyers#tranche 2 reform
0 notes
Text
Aave Deploys V3 On Aptos, Launches $100K CTF Challenge Following Cantina-Led Security Review
Decentralized finance (DeFi) lending protocol Aave has deployed its V3 version on the Layer 1 Aptos blockchain and launched a Capture The Flag (CTF) event with $100,000 in rewards for participants. The Aave V3 deployment on Aptos represents a complex adaptation of a leading DeFi platform to a Move-based blockchain environment. Built entirely using the Move programming language, this
Read More: You won't believe what happens next... Click here!
0 notes
Text
Money Services Business License in Canada: Launch Your Financial Venture with Confidence

Canada is quickly becoming a global hotspot for fintech and digital finance ventures. With a robust regulatory framework, strong financial infrastructure, and forward-thinking regulators, the country provides a favorable environment for businesses looking to operate in money transmission, currency exchange, or crypto asset services. At the heart of this opportunity is the Money Services Business license in Canada—a mandatory regulatory requirement for companies engaging in certain financial activities.
Whether you are launching a remittance company, operating a foreign exchange platform, or developing a crypto-based service, obtaining an MSB license is the first step toward legal compliance and market credibility.
What is an MSB License in Canada?
A Money Services Business (MSB) license is issued and overseen by FINTRAC (Financial Transactions and Reports Analysis Centre of Canada), which is Canada’s financial intelligence unit. Companies and individuals who offer financial services in Canada or to Canadian clients must register as an MSB if they are involved in any of the following activities:
Money transfers or remittances
Foreign exchange dealing
Issuing or redeeming money orders, traveler’s cheques, or other monetary instruments
Dealing in virtual currencies (buying/selling crypto or providing wallet services)
Crowdfunding services that involve the transfer or holding of funds
Registering as an MSB is a legal obligation. Failure to do so can lead to fines, enforcement actions, and criminal charges.
Why Choose Canada for Your MSB Operations?
Canada offers a combination of advantages that make it highly appealing for financial and fintech businesses:
1. Global Trust and Stability
Canada’s banking system is among the most stable and respected globally. Being licensed in Canada enhances your company’s credibility with customers, investors, and financial partners around the world.
2. Crypto-Friendly Regulation
Unlike many jurisdictions with unclear crypto rules, Canada provides defined regulations for virtual currency activities. If you operate a crypto exchange or wallet service, the MSB license enables you to legally serve Canadian users.
3. No Canadian Company Required
A key benefit is that foreign companies can apply for a Canadian MSB license without the need to incorporate in Canada. You simply need a Canadian compliance representative or agent.
4. Fast Licensing Process
The MSB registration process with FINTRAC is relatively straightforward, with most licenses issued within 4 to 8 weeks, assuming all compliance documents are complete and accurate.
Key Requirements for MSB Registration
To successfully obtain a Money Services Business license in Canada, you must meet several important requirements:
Business Entity: You can apply with a local Canadian company or a foreign company.
Compliance Program: You must create and implement a written AML/CTF compliance program.
Appoint a Compliance Officer: A designated individual responsible for managing your AML/CTF obligations.
KYC & Recordkeeping: Establish policies for customer identity verification and transaction recordkeeping.
Ongoing Reporting: Submit Suspicious Transaction Reports (STRs), Large Cash Transaction Reports (LCTRs), and maintain regular compliance communication with FINTRAC.
Local Presence: While a Canadian company is not required, you must have a representative or agent based in Canada.
What Can You Do with a Canadian MSB License?
With an MSB license, your company can legally operate in:
International remittance and money transfer services
Currency exchange and forex trading
Crypto exchange and wallet operations
Digital payment and e-wallet platforms
Crowdfunding and digital donation collection platforms
The license enables your business to access Canadian and international clients while building long-term trust and legitimacy.
How Interactive Dealers Can Help
At Interactive Dealers, we specialize in helping businesses successfully obtain a Canadian MSB license from scratch—no local incorporation required. Our team of experts supports you with:
Business structuring and eligibility assessment
Drafting and implementing AML/CTF compliance programs
Appointing a local compliance officer
FINTRAC registration and submission handling
Ongoing compliance support after licensing
Ready to Enter the Canadian Financial Market? Secure your Money Services Business license in Canada and launch your venture with full regulatory confidence. Contact Interactive Dealers today to begin your licensing journey.
0 notes
Text
cybersecurity training scholarship opportunity!
the scholarship program that I used to tell everyone about isn't running anymore, but this one is very similar!
the highlights:
multi-stage program that starts with a CTF, top candidates will be able to take multiple SANS courses & earn certifications (for free!)
you must be at least 18 years old
the deadline to apply is August 30th, 2024 at 11:59pm CT
you do have to be a member of Women in Cybersecurity to apply (a student membership is $20 per year), but WiCyS does a lot of other great programs (like mentorship) and it's a cool professional organization to be a member of.
#cybersecurity#scholarships#it looks a lil competitive but if you can get your hands on free SANS training I highly highly recommend that you at least try#SANS training is fantastic but stupidly expensive so any chance to get some for free is !!!
3 notes
·
View notes
Text
Navigating Ethical Hacking: Five Steps for Success
In our increasingly digital world, ethical hacking is a critical skill for safeguarding sensitive information and systems. Ethical hackers, or "white hats," play a vital role in identifying vulnerabilities before they can be exploited by malicious actors. Here, we outline five essential steps for success in ethical hacking.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Chennai

1. Build a Strong Foundation in Networking and Security
Before diving into ethical hacking, it’s essential to have a solid grasp of networking and cybersecurity principles. Understanding how networks operate and the basics of security will set you up for success.
Key Areas to Focus On:
Network Protocols: Familiarize yourself with TCP/IP, DNS, and HTTP.
Security Concepts: Learn about firewalls, intrusion detection systems, and encryption methods.
Resources:
Online courses (e.g., Coursera, Udemy)
Books like "CompTIA Network+ Guide to Networks"
2. Master the Tools of the Trade
Ethical hackers use a variety of tools to assess security vulnerabilities. Familiarizing yourself with these tools is crucial for effective testing.
Must-Know Tools:
Nmap: For network discovery and scanning.
Metasploit: A framework for developing and executing exploit code.
Wireshark: For network protocol analysis.
Practice:
Hands-on experience is vital. Set up a lab environment to experiment with these tools.
3. Learn Programming and Scripting
Understanding programming is essential for ethical hackers. It enables you to write scripts, automate tasks, and understand how applications can be exploited.
Recommended Languages:
Python: Great for scripting and automation.
JavaScript: Important for web application testing.
Bash/Shell: Useful for command-line tasks and automation.
Resources:
Online coding platforms (e.g., Codecademy, freeCodeCamp)
Books like "Automate the Boring Stuff with Python"
With the aid of Best Online Training & Placement programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly evolving. Staying updated on the latest threats, vulnerabilities, and hacking techniques is crucial for success.
How to Stay Informed:
Follow Blogs and News Sites: Websites like Krebs on Security and Threatpost.
Engage with Communities: Join forums and groups on platforms like Reddit and LinkedIn.
Attend Conferences: Participate in cybersecurity conferences and workshops.
5. Practice Ethical Hacking Regularly
The best way to hone your skills is through regular practice. Engaging in Capture The Flag (CTF) challenges and using platforms designed for ethical hacking can provide valuable experience.
Recommended Platforms:
Hack The Box: A platform for practicing penetration testing.
TryHackMe: Offers guided learning paths for various skills in cybersecurity.
Focus:
Set up personal projects or participate in ethical hacking competitions to apply what you’ve learned.
Conclusion
Navigating the world of ethical hacking requires dedication, continuous learning, and practice. By building a strong foundation in networking, mastering essential tools, learning programming, staying updated on trends, and practicing regularly, you can set yourself up for success in this dynamic field. Embrace the challenge and contribute to making the digital world a safer place!
0 notes
Text
Gamification in IT Infrastructure Training: Boosting Security Awareness in Tech Teams
In today’s digital-first world, cybersecurity isn’t just an IT concern—it’s a company-wide responsibility. Yet, engaging technical teams with traditional security training can often feel dull and ineffective. That’s where gamification steps in, transforming mundane sessions into interactive experiences that build long-term retention and sharpen real-world reflexes.
For companies managing complex IT infrastructure, embedding gamified learning modules into training programs is becoming a game-changer—quite literally.
🔗 Explore intelligent IT infrastructure solutions tailored for secure operations
What Is Gamification in IT Training?
Gamification involves using game design elements (like points, badges, leaderboards, time challenges, or simulations) in non-game contexts to encourage participation, competition, and knowledge retention. When applied to IT infrastructure training, it can make critical learning—like identifying threats or responding to breaches—more engaging and actionable.
Instead of relying solely on PowerPoint decks and lengthy documentation, gamified IT training turns learning into a more immersive and rewarding experience.
🔗 Partner with experts in infrastructure management and training delivery
Why Gamification Works for Security Awareness
Cybersecurity breaches are often the result of human error—not a lack of tools. Even in tech-savvy environments, security protocols can be overlooked due to:
Lack of awareness
Repetitive, unengaging training
Overconfidence in automation
Siloed departmental communication
Gamification helps solve these problems by creating interactive challenges, reinforcing concepts through repetition, and adding a healthy layer of competition.
🔗 Reinforce your IT policies through proactive infrastructure strategies
Core Benefits of Gamifying IT Infrastructure Training
Let’s explore how gamification boosts your team’s cyber-readiness and overall operational resilience:
✅ 1. Enhanced Engagement and Participation
By integrating levels, leaderboards, and rewards, training becomes a compelling experience rather than a compliance checklist. IT teams become more involved and invested in completing the program.
✅ 2. Improved Retention of Security Practices
Gamified exercises simulate real-world threat scenarios, helping participants practice password protection, firewall configuration, data encryption, and threat detection. This experiential learning method leads to higher retention compared to passive training.
✅ 3. Real-Time Feedback
Games provide instant responses to user actions, helping learners correct mistakes and understand consequences right away. For example, entering a weak password might generate a simulated breach response.
🔗 Deploy real-time network monitoring to reinforce secure practices
✅ 4. Encourages Team Collaboration
Some modules are designed to be played in teams, fostering collaboration between departments like IT, development, and operations. This aligns perfectly with the DevSecOps approach.
✅ 5. Fosters a Security-First Culture
By gamifying common infrastructure scenarios (e.g., unauthorized device detection, patching vulnerable servers), you reinforce a security-conscious mindset throughout your technical staff.
🔗 Integrate a security-first mindset in your IT infrastructure
Popular Gamification Techniques in IT Training
Let’s break down the most effective gamification formats used in IT security training:
🎯 1. Capture the Flag (CTF)
Widely popular in cybersecurity, CTF competitions simulate hacking environments where users must solve security puzzles or find vulnerabilities to "capture" virtual flags.
Perfect for:
Penetration testing
Vulnerability assessments
Network scanning practice
🧩 2. Scenario-Based Role Play
Teams are given simulated security incidents (like phishing emails, ransomware attacks, or server downtime), and must decide the appropriate course of action.
Great for:
Crisis management
Policy enforcement
Incident response training
📊 3. Leaderboards and Achievement Badges
Encouraging a little friendly competition through ranking boards or digital badges can help boost performance and encourage continuous improvement.
🔁 4. Gamified Quizzes with Time Limits
Rapid-fire, scenario-based quizzes test how quickly and accurately users can identify threats or respond to evolving risks—ideal for real-time preparedness.
🎮 5. Virtual Labs and Simulations
These simulate full-blown data center environments, allowing learners to practice configurations, monitoring, and threat response in a safe, sandboxed environment.
🔗 Simulate IT operations through secure digital infrastructure labs
Integrating Gamification in Infrastructure and Security Training: A Step-by-Step Guide
Thinking about introducing gamification into your IT training program? Here’s how to do it effectively:
Step 1: Identify Your Security Training Goals
Whether you're focusing on:
Data protection compliance
Employee authentication protocols
Network security configurations
Physical infrastructure security
You’ll need a clear goal to define the game’s structure and expected outcome.
🔗 Protect critical systems with a holistic infrastructure strategy
Step 2: Choose the Right Gamification Tools
There are many platforms designed for security gamification—choose one that integrates with your infrastructure systems or can be customized for your training needs.
Examples include:
Cyber Range Labs
Hack The Box for Teams
ThreatGEN Red vs Blue
Kaspersky’s Automated Security Awareness Platform
Step 3: Align Scenarios with Real Infrastructure
Simulations should reflect your actual IT environment—network configurations, access controls, endpoint devices—so that learning can be directly applied to the job.
🔗 Customize security training based on your unique infrastructure
Step 4: Incorporate Analytics and Feedback Loops
Monitor:
Completion rates
Response accuracy
User confidence scores
Time to complete challenges
Use this data to improve future training sessions or identify knowledge gaps.
Step 5: Make It Recurring and Evolving
Cyber threats change constantly. Your gamification programs must evolve accordingly, introducing new challenges and escalating complexity every quarter.
🔗 Stay ahead of evolving threats with adaptive IT strategies
Case Study: A Gamified Security Program in Action
Let’s imagine a mid-sized telecom company implementing gamified IT training for their engineers and system admins.
Challenges They Faced:
Frequent lapses in patch updates
Delayed incident responses
Poor password hygiene
Resistance to traditional training methods
Their Gamified Training Approach:
Introduced a CTF challenge involving firewall misconfigurations and lateral movement detection
Simulated an insider threat scenario using role play
Deployed monthly leaderboards across departments
Gamified a patch management module with time-based scoring
Results Achieved:
45% improvement in patch deployment within SLA
60% faster incident reporting
95% training participation across all IT staff
Positive shift in company-wide security awareness
🔗 Start building a resilient and secure infrastructure culture
Best Practices for Success
If you're planning to launch a gamification-based IT training program, keep these best practices in mind:
🔐 1. Prioritize Realism Over Flashiness
Ensure the content reflects actual day-to-day infrastructure scenarios, even if the visuals are minimal.
🔁 2. Include Repetitive Reinforcement
Reinforcement through repetition ensures that practices become second nature.
🛠 3. Make It Scalable and Modular
Start with basic modules, then introduce advanced scenarios for experienced team members.
🎯 4. Reward Performance, Not Just Participation
Offer badges, certification, or even team-based rewards to drive better performance outcomes.
🔗 Deploy scalable infrastructure solutions with performance focus
The Future of Gamified IT Training
As AI-driven threats, IoT vulnerabilities, and remote working models increase attack surfaces, the human element in IT security becomes even more critical. Gamification is not just a gimmick—it’s an essential evolution in the way businesses train their teams to be more alert, proactive, and effective.
For enterprises managing large-scale data centers, networking hardware, and multi-location IT ecosystems, this form of training is quickly becoming indispensable.
🔗 Future-proof your IT infrastructure with Leading Network Systems
Conclusion
Gamification in IT infrastructure training bridges the gap between knowledge and action. By transforming dry technical concepts into dynamic learning experiences, it cultivates a security-first mindset across all layers of your tech team.
Whether you're a startup scaling fast or an enterprise managing critical infrastructure, integrating gamified security awareness programs can significantly reduce human error, accelerate training, and strengthen your cyber defense posture.
✅ Get in touch with Leading Network Systems to design secure, intelligent infrastructure backed by skilled and engaged teams
0 notes
Text
AML/CTF Tranche 2 for Real Estate: What You Must Know
The Australian real estate sector is facing increased scrutiny as it moves closer to being included in AML/CTF Tranche 2 reforms. This potential expansion of anti-money laundering and counter-terrorism financing (AML/CTF) laws to cover real estate agents is a game-changer, and understanding the implications is vital for compliance, risk mitigation, and professional integrity.
In this blog post, we break down everything real estate professionals need to know about AML/CTF Tranche 2: what it is, why it's happening, what changes are coming, and how to prepare.
What Is AML/CTF Tranche 2?
Australia's AML/CTF Act 2006 currently applies to businesses in sectors such as banking, remittance, and gambling. However, the second tranche (Tranche 2) proposes to expand these obligations to high-risk sectors including real estate agents, lawyers, and accountants.
Tranche 2 has been discussed for over a decade, and in 2024, momentum has increased due to pressure from global bodies like the Financial Action Task Force (FATF) and a growing need to protect the property market from illicit funds.
Why Real Estate Is Targeted
AML/CTF Tranche 2 for Real Estate is a prime target for money launderers due to the high value of transactions and the ability to obscure ownership. Criminals often use property purchases to clean dirty money or store wealth, making the industry vulnerable without proper oversight.
Key Obligations Under AML/CTF Tranche 2 for Real Estate
Once implemented, real estate professionals will be subject to obligations similar to those in the financial sector. These may include:
Customer Due Diligence (CDD): Agents will need to verify the identity of clients before establishing a business relationship.
Ongoing Monitoring: Professionals must track transactions and relationships over time to identify suspicious activities.
Suspicious Matter Reporting (SMR): Real estate agents will be required to report any suspicious transactions to AUSTRAC.
AML/CTF Program Development: Agencies will need to develop internal compliance programs, risk assessments, and staff training modules.
Record Keeping: Real estate businesses must retain relevant records for up to seven years to comply with regulatory audits.
Practical Steps to Prepare for AML/CTF Tranche 2
1. Conduct a Risk Assessment
Start by understanding the specific risks your agency faces. Evaluate client types, transaction values, geographic areas, and business models.
2. Implement Identity Verification Procedures
Use reliable identity verification solutions that meet government standards. Digital onboarding and biometric checks can streamline the process.
3. Develop Internal AML/CTF Programs
Create a structured AML/CTF compliance plan that includes written policies, roles and responsibilities, employee training, and escalation protocols.
4. Invest in Screening and Monitoring Tools
Using tools like NameScan, real estate agencies can screen clients against global sanctions, politically exposed person (PEP) lists, and adverse media databases.
5. Train Your Staff
Educate your team on AML/CTF risks, regulatory expectations, red flags, and reporting procedures. Ongoing training ensures awareness and reduces compliance risks.

Benefits of AML/CTF Tranche 2 Compliance
Although it brings additional responsibilities, AML/CTF Tranche 2 compliance can be a competitive advantage. Benefits include:
Improved Reputation: Show clients and partners that you prioritize transparency.
Risk Reduction: Reduce the chance of unknowingly facilitating criminal activity.
Global Alignment: Comply with FATF expectations and enhance Australia’s international reputation.
Operational Efficiency: Leveraging AML tools automates many compliance tasks, improving workflow.
Challenges in Adopting AML/CTF Tranche 2
Cost of Implementation: Smaller agencies may struggle with the financial burden.
Complexity of Regulations: Understanding legal requirements can be daunting without expert help.
Resistance to Change: Staff may resist new processes, especially if poorly communicated.
These challenges can be overcome through proactive planning, consultation, and leveraging user-friendly compliance solutions.
How NameScan Supports Real Estate Agents
NameScan provides advanced risk screening solutions tailored for AML/CTF Tranche 2 compliance. Key features include:
PEP & Sanction Screening
Adverse Media Monitoring
Real-time Alerts
Customizable Compliance Workflows
With NameScan, real estate businesses can stay ahead of compliance deadlines while maintaining operational efficiency.
Frequently Asked Questions (FAQ)
Q1: When will AML/CTF Tranche 2 be implemented for real estate? A: The timeline isn't confirmed yet, but strong indications suggest legislative action may occur soon, possibly in 2025.
Q2: What happens if I don’t comply with Tranche 2 requirements? A: Non-compliance can lead to significant fines, reputational damage, and even criminal charges.
Q3: Can I handle compliance manually? A: While possible, manual processes are prone to error. Using automated solutions like NameScan is more efficient and reliable.
Q4: How do I know if my client is high risk? A: Factors include source of funds, geographic location, occupation, and association with PEPs or sanctions.
Q5: Where can I get AML training for my team? A: Many AML/CTF training providers exist, and NameScan can connect you with certified training solutions.
Conclusion: Don’t Wait to Get Compliant
AML/CTF Tranche 2 for real estate is on the horizon. Now is the time for agencies to assess risk, implement robust procedures, and adopt digital tools like NameScan to streamline compliance.
Real estate professionals who act early not only avoid legal trouble but also gain a reputation for trustworthiness and operational excellence.
Ready to Future-Proof Your Real Estate Business? Start your AML/CTF compliance journey today with NameScan and safeguard your agency from risk. Sign up now and stay compliant, efficient, and ahead of the curve!
#tranche 2 aml for tcsps#aml/ctf rules in australia#tranche 2 reform#aml ctf rules for lawyers#AML/CTF Tranche 2 for Real Estate
0 notes
Text

Microsoft had over 20 billion dollars of profit last quarter
#Microsoft had over 20 billion dollars of profit last quarter#microsoft#boycott microsoft#antimicrosoft#jerktrillionaires#jerkbillionaires#jerkmillionaires#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#it#i.t.#infotech#information technology#software#firmware#bloatware#fuck microsoft#bill gates#eat the rich#eat the fucking rich#class war#boycott starbucks
7 notes
·
View notes
Note
liz do you have any security podcast recs?👀 and also, in general, some recs for someone who is now very interested in cybersecurity but knows basically nothing heh?
Hi there!
The main security podcast that I listen to is the SANS Internet Stormcenter podcast. The episodes are about 5 minutes long and are published every weekday morning. They're a good way to stay up to date on general things happening in the security world: big vulnerabilities, observed attack trends, patch Tuesday, that kind of stuff. That's the only security podcast that I listen to consistently, but people have told me that the Google Cloud Security Podcast is good, too. I mostly stay up to date with the industry via blogs, so if anyone is interested in that let me know & I can share a list!
As for the second part of your question, my main recommendation is to start exploring and see what kinds of things you're interested in! I'm on the tech side of security, so my recommendations will be centered around that. If you don't enjoy the tech side but are still interested in security, you can look into the governance/privacy/risk management/threat intelligence side of things. Some basic tech skills will always be helpful, though.
Off the top of my head, these are some main areas to start looking into:
Linux (how to use the GUI/CLI, understanding of how operating systems generally work)
Networking (OSI model, how the internet works)
programming/scripting - not required, but incredibly helpful. even just having a general understanding of the basics (variables, arrays, basic syntax) will be beneficial.
Generally, you'll need a solid understanding of IT stuff before you can get into the specifics of security. There are a lot of different areas of security, though, so start exploring and finding out which topics interest you!
YouTube is a good place to start learning these sorts of things. I highly recommend Professor Messer's channel. Start with the A+ playlists if you know nothing about tech, or start with the Network+ course if you feel like you could already be decent at tech support (you know the OSI model, you could probably build a computer, you know how to troubleshoot Windows). Check your school/local library to see if you get free access to LinkedIn Learning courses, there are some good ones there, too.
A good way to get started is to try a beginner-oriented CTF. I listed some resources in this post. Cyber FastTrack starts in October, usually, so if you're a college student in the U.S. you should keep an eye on that.
I hope that was helpful! let me know if you have any more questions :D
7 notes
·
View notes