#err ssl protocol error
Explore tagged Tumblr posts
Link
There are various methods to resolve or fix Err_SSL_Protocol_Error. We are going to discuss all methods with the solutions one by one. Need help, call: 888-818-9916.
1 note
·
View note
Text
Ssl_error_bad_mac_alert

Ssl Connection Error
Ssl_error_bad_mac_alert Ilo 3
Bad Record Mac
Err Ssl Bad Mac Alert
I was receiving the message Error code: ssl_error_bad_mac_alert while connecting to a HP Proliant BL680 G7 with iLO 3 version 1.16
Secure Connection Failed
Solved: Just in the process of upgrading GW18 to GW18.1.0, then eventually GW 18 1.1. Primary domain is fine; on the secondary domain server and did the - 2756631.
Re: SSLERRORBADMACALERT message accessing AWS console since 8.2 (2004) upgrade Post by rob65732 » Fri Jun 26, 2020 9:06 am Done - the files (attached) are identical.
Hello, After configuring VoWLAN as per the following document: Voice over Wireless LAN 4.1 Design Guide and adding a network profile on the 7925g wireless phone. I still get connection failed. For those who had faced this issue before please comment any propable troubleshoot for this.
An error occurred during a connection to 172.22.250.149. SSL peer reports incorrect Message Authentication Code. (Error code: ssl_error_bad_mac_alert)
CP014002.scexe – iLO 3 version 1.20 CP022551.scexe – iLO 3 version 1.80
To solve this problem, update iLO 3 first to version 1.20 and then to version 1.80
root@linux:/tmp # ./CP022551.scexe Hls streaming download firefox.
FLASH_iLO3 v1.09 for Linux (Jan 23 2013) (C) Copyright 2002-2013 Hewlett-Packard Development Company, L.P. Firmware image: ilo3_180.bin Current iLO 3 firmware version 1.20; Serial number ILOBRC0411JYB
Component XML file: CP022551.xml CP022551.xml reports firmware version 1.80 This operation will update the firmware on the iLO 3 in this server with version 1.80. Continue (y/N)?y Current firmware is 1.20 (Mar 14 2011 ) Firmware image is 0x801664(8394340) bytes Committing to flash part… ******** DO NOT INTERRUPT! ******** Flashing completed. Attempting to reset device. Succeeded. ***** iLO 3 reboot in progress (may take up to 60 seconds.) ***** Please ignore console messages, if any.
iLO 3 reboot completed. root@linux:/tmp #
You are currently viewing a snapshot of www.mozilla.org taken on April 21, 2008. Most of this content ishighly out of date (some pages haven't been updated since the project began in 1998) and exists for historical purposes only. Ifthere are any pages on this archive site that you think should be added back to www.mozilla.org, please file a bug.
Coding
Testing
Tools
Table of Contents | Previous | Next | Index

Chapter 8 NSS and SSL Error Codes
NSS error codes are retrieved using theNSPR function PR_GetError.In addition to the error codes defined by NSPR, PR_GetErrorretrieves the error codes described in this chapter.SSL Error Codes
Ssl Connection Error
SEC Error Codes
SSL Error Codes
Ssl_error_bad_mac_alert Ilo 3
Table 8.1 Error codes defined in sslerr.h
Bad Record Mac
ConstantValueDescriptionSSL_ERROR_EXPORT_ONLY_SERVER-12288'Unableto communicate securely. Peer does not support high-grade encryption.'
The local system was configured tosupport the cipher suites permitted for domestic use. The remote systemwas configured to support only the cipher suites permitted for exportuse.
SSL_ERROR_US_ONLY_SERVER-12287'Unableto communicate securely. Peer requires high-grade encryption which isnot supported.'
The remote system was configuredto support the cipher suites permitted for domestic use. The localsystem was configured to support only the cipher suites permitted forexport use.
SSL_ERROR_NO_CYPHER_OVERLAP-12286'Cannotcommunicate securely with peer: no common encryption algorithm(s).'
The local and remote systems shareno cipher suites in common. This can be due to a misconfiguration ateither end. It can be due to a server being misconfigured to use anon-RSA certificate with the RSA key exchange algorithm.
SSL_ERROR_NO_CERTIFICATE-12285'Unableto find the certificate or key necessary for authentication.'
This error has many potentialcauses; for example:
Certificate or key not found in database.
Certificate not marked trusted indatabase and Certificate's issuer not marked trusted in database.
Wrong password for keydatabase.
Missing database.
SSL_ERROR_BAD_CERTIFICATE-12284'Unableto communicate securely with peer: peers's certificate wasrejected.'
A certificate was received fromthe remote system and was passed to the certificate authenticationcallback function provided by the local application. That callbackfunction returned SECFailure, and the bad certificate callbackfunction either was not configured or did not choose to override theerror code returned by the certificate authentication callback function.
-12283(unused)SSL_ERROR_BAD_CLIENT-12282'Theserver has encountered bad data from the client.'
This error code should occur onlyon sockets that are acting as servers. It is a generic error, used whennone of the other more specific error codes defined in this file applies.
SSL_ERROR_BAD_SERVER-12281'Theclient has encountered bad data from the server.'
This error code should occur onlyon sockets that are acting as clients. It is a generic error, used whennone of the other more specific error codes defined in this file applies.
SSL_ERROR_UNSUPPORTED_CERTIFICATE_TYPE-12280'Unsupportedcertificate type.'
The operation encountered acertificate that was not one of the well known certificate types handledby the certificate library.
SSL_ERROR_UNSUPPORTED_VERSION-12279'Peerusing unsupported version of security protocol.'
On a client socket, this means theremote server has attempted to negotiate the use of a version of SSLthat is not supported by the NSS library, probably an invalid versionnumber. On a server socket, this means the remote client has requestedthe use of a version of SSL older than version 2.
-12278(unused)-12277'Client authenticationfailed: private key in key database does not correspond to public key incertificate database.'SSL_ERROR_BAD_CERT_DOMAIN-12276'Unableto communicate securely with peer: requested domain name does not matchthe server's certificate.'
This error code should be returnedby the certificate authentication callback function when it detects thatthe Common Name in the remote server's certificate does not match thehostname sought by the local client, according to the matching rulesspecified for CERT_VerifyCertName.
-12275(unused)SSL_ERROR_SSL2_DISABLED-12274'Peeronly supports SSL version 2, which is locally disabled.'
The remote server has asked to useSSL version 2, and SSL version 2 is disabled in the local client'sconfiguration.
SSL_ERROR_BAD_MAC_READ-12273'SSLreceived a record with an incorrect Message Authentication Code.'
This usually indicates that theclient and server have failed to come to agreement on the set of keysused to encrypt the application data and to check message integrity. Ifthis occurs frequently on a server, an active attack (such as the'million question' attack) may be underway against the server.
SSL_ERROR_BAD_MAC_ALERT-12272'SSLpeer reports incorrect Message Authentication Code.'
The remote system has reportedthat it received a message with a bad Message Authentication Code fromthe local system. This may indicate that an attack on that server isunderway.
SSL_ERROR_BAD_CERT_ALERT-12271'SSLpeer cannot verify your certificate.'
The remote system has received acertificate from the local system, and has rejected it for some reason.
SSL_ERROR_REVOKED_CERT_ALERT-12270'SSLpeer rejected your certificate as revoked.'
The remote system has received acertificate from the local system, and has determined that thecertificate has been revoked.
SSL_ERROR_EXPIRED_CERT_ALERT-12269'SSLpeer rejected your certificate as expired.'
The remote system has received acertificate from the local system, and has determined that thecertificate has expired.
SSL_ERROR_SSL_DISABLED-12268'Cannotconnect: SSL is disabled.'
The local socket is configured insuch a way that it cannot use any of the SSL cipher suites. Possiblecauses include: (a) both SSL2 and SSL3 are disabled, (b) All theindividual SSL cipher suites are disabled, or (c) the socket isconfigured to handshake as a server, but the certificate associated withthat socket is inappropriate for the Key Exchange Algorithm selected.
SSL_ERROR_FORTEZZA_PQG-12267'Cannotconnect: SSL peer is in another FORTEZZA domain.'
The local system and the remotesystem are in different FORTEZZA domains. They must be in the samedomain to communicate.
SSL_ERROR_UNKNOWN_CIPHER_SUITE-12266'Anunknown SSL cipher suite has been requested.'
The application has attempted toconfigure SSL to use an unknown cipher suite.
SSL_ERROR_NO_CIPHERS_SUPPORTED-12265'Nocipher suites are present and enabled in this program.'
Possible causes: (a) all ciphersuites have been configured to be disabled, (b) the only cipher suitesthat are configured to be enabled are those that are disallowed bycipher export policy, (c) the socket is configured to handshake as aserver, but the certificate associated with that socket is inappropriatefor the Key Exchange Algorithm selected.
SSL_ERROR_BAD_BLOCK_PADDING-12264'SSLreceived a record with bad block padding.'
SSL was using a Block cipher, andthe last block in an SSL record had incorrect padding information in it.This usually indicates that the client and server have failed to cometo agreement on the set of keys used to encrypt the application dataand to check message integrity. If this occurs frequently on a server,an active attack (such as the 'million question' attack) may beunderway against the server.
SSL_ERROR_RX_RECORD_TOO_LONG-12263'SSLreceived a record that exceeded the maximum permissible length.'
This generally indicates that theremote peer system has a flawed implementation of SSL, and is violatingthe SSL specification.
SSL_ERROR_TX_RECORD_TOO_LONG-12262'SSLattempted to send a record that exceeded the maximum permissiblelength.'
This error should never occur. Ifit does, it indicates a flaw in the NSS SSL library.
SSL_ERROR_CLOSE_NOTIFY_ALERT-12230'SSLpeer has closed this connection.'
The local socket received an SSL3alert record from the remote peer, reporting that the remote peer haschosen to end the connection. The receipt of this alert is an error onlyif it occurs while a handshake is in progress.
SSL_ERROR_PUB_KEY_SIZE_LIMIT_EXCEEDED-12210'SSLServer attempted to use domestic-grade public key with export ciphersuite.'
On a client socket, this errorreports that the remote server has failed to perform an 'SSL Step down'for an export cipher. It has sent a certificate bearing a domestic-gradepublic key, but has not sent a ServerKeyExchange message containing anexport-grade public key for the key exchange algorithm. Such aconnection cannot be permitted without violating U.S. export policies.On a server socket, this indicates a failure of the local library.
SSL_ERROR_NO_SERVER_KEY_FOR_ALG-12206'Serverhas no key for the attempted key exchange algorithm.'
An SSL client has requested an SSLcipher suite that uses a Key Exchange Algorithm for which the localserver has no appropriate public key. This indicates a configurationerror on the local server.
SSL_ERROR_TOKEN_INSERTION_REMOVAL-12205'PKCS#11 token was inserted or removed while operation was inprogress.'
A cryptographic operation requiredto complete the handshake failed because the token that was performingit was removed while the handshake was underway. Another token may alsohave been inserted into the same slot.
SSL_ERROR_TOKEN_SLOT_NOT_FOUND-12204'NoPKCS#11 token could be found to do a required operation.'
A cryptographic operation requireda PKCS#11 token with specific abilities, and no token could be found inany slot, including the 'soft token' in the internal virtual slot, thatcould do the job. May indicate a server configuration error, such ashaving a certificate that is inappropriate for the Key ExchangeAlgorithm selected.
-12203'Cannot communicatesecurely with peer: no common compression algorithm(s).'-12202'Cannot initiate anotherSSL handshake until current handshake is complete.'-12201'Received incorrecthandshakes hash values from peer.'-12200'The certificate providedcannot be used with the selected key exchange algorithm.'-12199'No certificate authorityis trusted for SSL client authentication.'-12198'Client's SSL session IDnot found in server's session cache.'
Received a malformed (too longor short or invalid content) SSL handshake:
Just dance nintendo switch. All the error codes in thefollowing block indicate that the local socket received an improperlyformatted SSL3 handshake message from the remote peer. This probablyindicates a flaw in the remote peer's implementation.
SSL_ERROR_RX_MALFORMED_HELLO_REQUEST-12261'SSLreceived a malformed Hello Request handshake message.'SSL_ERROR_RX_MALFORMED_CLIENT_HELLO-12260'SSLreceived a malformed Client Hello handshake message.'SSL_ERROR_RX_MALFORMED_SERVER_HELLO-12259'SSLreceived a malformed Server Hello handshake message.'SSL_ERROR_RX_MALFORMED_CERTIFICATE-12258'SSLreceived a malformed Certificate handshake message.'SSL_ERROR_RX_MALFORMED_SERVER_KEY_EXCH -12257'SSLreceived a malformed Server Key Exchange handshake message.'SSL_ERROR_RX_MALFORMED_CERT_REQUEST-12256'SSLreceived a malformed Certificate Request handshake message.'SSL_ERROR_RX_MALFORMED_HELLO_DONE-12255'SSLreceived a malformed Server Hello Done handshake message.'SSL_ERROR_RX_MALFORMED_CERT_VERIFY-12254'SSLreceived a malformed Certificate Verify handshake message.'SSL_ERROR_RX_MALFORMED_CLIENT_KEY_EXCH -12253'SSLreceived a malformed Client Key Exchange handshake message.'SSL_ERROR_RX_MALFORMED_FINISHED-12252'SSLreceived a malformed Finished handshake message.'
Received a malformed (too longor short) SSL record:
All the error codes in thefollowing block indicate that the local socket received an improperlyformatted SSL3 record from the remote peer. This probably indicates aflaw in the remote peer's implementation.
SSL_ERROR_RX_MALFORMED_CHANGE_CIPHER-12251'SSLreceived a malformed Change Cipher Spec record.'SSL_ERROR_RX_MALFORMED_ALERT-12250'SSLreceived a malformed Alert record.'SSL_ERROR_RX_MALFORMED_HANDSHAKE-12249'SSLreceived a malformed Handshake record.'SSL_ERROR_RX_MALFORMED_APPLICATION_DATA -12248'SSLreceived a malformed Application Data record.'
Received an SSL handshake thatwas inappropriate for the current state:
All the error codes in thefollowing block indicate that the local socket received an SSL3handshake message from the remote peer at a time when it wasinappropriate for the peer to have sent this message. For example, aserver received a message from another server. This probably indicates aflaw in the remote peer's implementation.
SSL_ERROR_RX_UNEXPECTED_HELLO_REQUEST-12247'SSLreceived an unexpected Hello Request handshake message.'SSL_ERROR_RX_UNEXPECTED_CLIENT_HELLO-12246'SSLreceived an unexpected Client Hello handshake message.'SSL_ERROR_RX_UNEXPECTED_SERVER_HELLO-12245'SSLreceived an unexpected Server Hello handshake message.'SSL_ERROR_RX_UNEXPECTED_CERTIFICATE-12244'SSLreceived an unexpected Certificate handshake message.'SSL_ERROR_RX_UNEXPECTED_SERVER_KEY_EXCH -12243'SSLreceived an unexpected Server Key Exchange handshake message.'SSL_ERROR_RX_UNEXPECTED_CERT_REQUEST-12242'SSLreceived an unexpected Certificate Request handshake message.'SSL_ERROR_RX_UNEXPECTED_HELLO_DONE-12241'SSLreceived an unexpected Server Hello Done handshake message.'SSL_ERROR_RX_UNEXPECTED_CERT_VERIFY-12240'SSLreceived an unexpected Certificate Verify handshake message.'SSL_ERROR_RX_UNEXPECTED_CLIENT_KEY_EXCH -12239'SSLreceived an unexpected Client Key Exchange handshake message.'SSL_ERROR_RX_UNEXPECTED_FINISHED-12238'SSLreceived an unexpected Finished handshake message.'
Received an SSL record that wasinappropriate for the current state:
All the error codes in thefollowing block indicate that the local socket received an SSL3 recordfrom the remote peer at a time when it was inappropriate for the peer tohave sent this message. This probably indicates a flaw in the remotepeer's implementation.
US Post Office Near Me - Find the nearest post office locations, a post box near me, opening hours, mail addresses, USPS App & USPS phone numbers. How can i find my nearest post box. Find your nearest USPS Post Office using our US Post Office finder and book cheap USPS drop off services with Parcel Monkey. Welcome to Posten. You can track your packages, notify us of your new address, find prices, postal addresses or buy stamps, postcards and mailboxes. Find local 1522 Parcel Delivery Service Near You. Get FREE quotes in minutes from reviewed, rated & trusted Parcel Deliverers on Airtasker.
SSL_ERROR_RX_UNEXPECTED_CHANGE_CIPHER-12237'SSLreceived an unexpected Change Cipher Spec record.'SSL_ERROR_RX_UNEXPECTED_ALERT-12236'SSLreceived an unexpected Alert record.'SSL_ERROR_RX_UNEXPECTED_HANDSHAKE-12235'SSLreceived an unexpected Handshake record.'SSL_ERROR_RX_UNEXPECTED_APPLICATION_DATA-12234'SSLreceived an unexpected Application Data record.'
Received record/message withunknown discriminant:
All the error codes in thefollowing block indicate that the local socket received an SSL3 recordor handshake message from the remote peer that it was unable tointerpret because the byte that identifies the type of record or messagecontained an unrecognized value. This probably indicates a flaw in theremote peer's implementation.
SSL_ERROR_RX_UNKNOWN_RECORD_TYPE-12233'SSLreceived a record with an unknown content type.'SSL_ERROR_RX_UNKNOWN_HANDSHAKE-12232'SSLreceived a handshake message with an unknown message type.'SSL_ERROR_RX_UNKNOWN_ALERT-12231'SSLreceived an alert record with an unknown alert description.'
Received an alert report:
All the error codes in thefollowing block indicate that the local socket received an SSL3 or TLSalert record from the remote peer, reporting some issue that it had withan SSL record or handshake message it received. (Some _Alertcodes are listed in other blocks.)
SSL_ERROR_HANDSHAKE_UNEXPECTED_ALERT-12229'SSLpeer was not expecting a handshake message it received.'SSL_ERROR_DECOMPRESSION_FAILURE_ALERT-12228'SSL peer was unable to successfully decompress an SSL record it received.'SSL_ERROR_HANDSHAKE_FAILURE_ALERT-12227'SSLpeer was unable to negotiate an acceptable set of security parameters.'SSL_ERROR_ILLEGAL_PARAMETER_ALERT-12226'SSLpeer rejected a handshake message for unacceptable content.'SSL_ERROR_UNSUPPORTED_CERT_ALERT-12225'SSLpeer does not support certificates of the type it received.'SSL_ERROR_CERTIFICATE_UNKNOWN_ALERT-12224'SSLpeer had some unspecified issue with the certificate it received.'SSL_ERROR_DECRYPTION_FAILED_ALERT-12197'Peer was unable to decrypt an SSL record it received.'SSL_ERROR_RECORD_OVERFLOW_ALERT-12196'Peer received an SSL record that was longer than is permitted.'SSL_ERROR_UNKNOWN_CA_ALERT-12195'Peer does not recognize and trust the CA that issued your certificate.'SSL_ERROR_ACCESS_DENIED_ALERT-12194'Peer received a valid certificate, but access was denied.'SSL_ERROR_DECODE_ERROR_ALERT-12193'Peer could not decode an SSL handshake message.'SSL_ERROR_DECRYPT_ERROR_ALERT-12192'Peer reports failure of signature verification or key exchange.'SSL_ERROR_EXPORT_RESTRICTION_ALERT-12191'Peer reports negotiation not in compliance with export regulations.'SSL_ERROR_PROTOCOL_VERSION_ALERT-12190'Peer reports incompatible or unsupported protocol version.'SSL_ERROR_INSUFFICIENT_SECURITY_ALERT-12189'Server requires ciphers more secure than those supported by client.'SSL_ERROR_INTERNAL_ERROR_ALERT-12188'Peer reports it experienced an internal error.'SSL_ERROR_USER_CANCELED_ALERT-12187'Peer user canceled handshake.'-12186'Peer does not permitrenegotiation of SSL security parameters.'
Unspecified errors thatoccurred while attempting some operation:
All the error codes in thefollowing block describe the operation that was being attempted at thetime of the unspecified failure. These failures may be caused by thesystem running out of memory, or errors returned by PKCS#11 routinesthat did not provide meaningful error codes of their own. These shouldrarely be seen. (Certain of these error codes have more specificmeanings, as described.)
SSL_ERROR_GENERATE_RANDOM_FAILURE-12223'SSLexperienced a failure of its random number generator.'SSL_ERROR_SIGN_HASHES_FAILURE-12222'Unableto digitally sign data required to verify your certificate.'SSL_ERROR_EXTRACT_PUBLIC_KEY_FAILURE-12221'SSLwas unable to extract the public key from the peer's certificate.'SSL_ERROR_SERVER_KEY_EXCHANGE_FAILURE-12220'Unspecifiedfailure while processing SSL Server Key Exchange handshake.'SSL_ERROR_CLIENT_KEY_EXCHANGE_FAILURE-12219'Unspecifiedfailure while processing SSL Client Key Exchange handshake.'SSL_ERROR_ENCRYPTION_FAILURE-12218'Bulkdata encryption algorithm failed in selected cipher suite.'SSL_ERROR_DECRYPTION_FAILURE-12217'Bulkdata decryption algorithm failed in selected cipher suite.'SSL_ERROR_MD5_DIGEST_FAILURE-12215'MD5digest function failed.'SSL_ERROR_SHA_DIGEST_FAILURE-12214'SHA-1digest function failed.'SSL_ERROR_MAC_COMPUTATION_FAILURE-12213'MessageAuthentication Code computation failed.'SSL_ERROR_SYM_KEY_CONTEXT_FAILURE-12212'Failureto create Symmetric Key context.'SSL_ERROR_SYM_KEY_UNWRAP_FAILURE-12211'Failureto unwrap the Symmetric key in Client Key Exchange message.'SSL_ERROR_IV_PARAM_FAILURE-12209'PKCS11code failed to translate an IV into a param.'SSL_ERROR_INIT_CIPHER_SUITE_FAILURE-12208'Failedto initialize the selected cipher suite.'SSL_ERROR_SOCKET_WRITE_FAILURE-12216'Attemptto write encrypted data to underlying socket failed.'
After the data to be sent wasencrypted, the attempt to send it out the socket failed. Likely causesinclude that the peer has closed the connection.
SSL_ERROR_SESSION_KEY_GEN_FAILURE-12207'Failedto generate session keys for SSL session.'
On a client socket, indicates afailure of the PKCS11 key generation function. On a server socket,indicates a failure of one of the following: (a) to unwrap thepre-master secret from the ClientKeyExchange message, (b) to derive themaster secret from the premaster secret, (c) to derive the MAC secrets,cryptographic keys, and initialization vectors from the master secret.If encountered repeatedly on a server socket, this can indicate that theserver is actively under a 'million question' attack.
SEC Error Codes
Table 8.2 Security error codesdefined in secerr.h
ConstantValueDescription-8192AnI/O error occurred during authentication; or an error occurred during crypto operation (other than signature verification).-8191Securitylibrary failure.-8190Securitylibrary: received bad data.-8189Securitylibrary: output length error.-8188Securitylibrary: input length error.-8187Securitylibrary: invalid arguments.-8186Securitylibrary: invalid algorithm.-8185Securitylibrary: invalid AVA.-8184Securitylibrary: invalid time.-8183Securitylibrary: improperly formatted DER-encoded message.-8182Peer'scertificate has an invalid signature.-8181Peer'scertificate has expired.-8180Peer'scertificate has been revoked.-8179Peer'scertificate issuer is not recognized.-8178Peer'spublic key is invalid-8177Thepassword entered is incorrect.-8176Newpassword entered incorrectly.-8175Securitylibrary: no nodelock.-8174Securitylibrary: bad database.-8173Securitylibrary: memory allocation failure.-8172Peer'scertificate issuer has been marked as not trusted by the user.-8171Peer'scertificate has been marked as not trusted by the user.-8170Certificatealready exists in your database.-8169Downloadedcertificate's name duplicates one already in your database.-8168Erroradding certificate to database.-8167Errorrefiling the key for this certificate.-8166Theprivate key for this certificate cannot be found in key database.-8165Thiscertificate is valid.-8164Thiscertificate is not valid.-8163Certificatelibrary: no response.-8162Thecertificate issuer's certificate has expired.-8161TheCRL for the certificate's issuer has expired.-8160TheCRL for the certificate's issuer has an invalid signature.-8159NewCRL has an invalid format.-8158Certificateextension value is invalid.-8157Certificateextension not found.-8156Issuercertificate is invalid.-8155Certificatepath length constraint is invalid.-8154Certificateusages field is invalid.-8153Internal-onlymodule.-8152Thekey does not support the requested operation.-8151Certificatecontains unknown critical extension.-8150NewCRL is not later than the current one.-8149Notencrypted or signed: you do not yet have an email certificate.-8148Notencrypted: you do not have certificates for each of the recipients.-8147Cannotdecrypt: you are not a recipient, or matching certificate and privatekey not found.-8146Cannotdecrypt: key encryption algorithm does not match your certificate.-8145Signatureverification failed: no signer found, too many signers found,
or improper or corrupted data.
-8144Unsupportedor unknown key algorithm.-8143Cannotdecrypt: encrypted using a disallowed algorithm or key size.-8142FORTEZZAcard has not been properly initialized.-8141NoFORTEZZA cards found.-8140NoFORTEZZA card selected.-8139Pleaseselect a personality to get more info on.-8138Personalitynot found-8137Nomore information on that personality.-8136InvalidPIN.-8135Couldn'tinitialize FORTEZZA personalities.-8134NoKRL for this site's certificate has been found.-8133TheKRL for this site's certificate has expired.-8132TheKRL for this site's certificate has an invalid signature.-8131Thekey for this site's certificate has been revoked.-8130NewKRL has an invalid format.-8129Securitylibrary: need random data.-8128Securitylibrary: no security module can perform the requested operation.-8127Thesecurity card or token does not exist, needs to be initialized, or hasbeen removed.-8126Securitylibrary: read-only database.-8125Noslot or token was selected.-8124Acertificate with the same nickname already exists.-8123Akey with the same nickname already exists.-8122Errorwhile creating safe object.-8121Errorwhile creating baggage object.-8120Couldn'tremove the principal.-8119Couldn'tdelete the privilege-8118Thisprincipal doesn't have a certificate.-8117Requiredalgorithm is not allowed.-8116Errorattempting to export certificates.-8115Errorattempting to import certificates.-8114Unableto import. Decoding error. File not valid.-8113Unableto import. Invalid MAC. Incorrect password or corrupt file.-8112Unableto import. MAC algorithm not supported.-8111Unableto import. Only password integrity and privacy modes supported.-8110Unableto import. File structure is corrupt.-8109Unableto import. Encryption algorithm not supported.-8108Unableto import. File version not supported.-8107Unableto import. Incorrect privacy password.-8106Unableto import. Same nickname already exists in database.-8105Theuser clicked cancel.-8104Notimported, already in database.-8103Messagenot sent.-8102Certificatekey usage inadequate for attempted operation.-8101Certificatetype not approved for application.-8100Addressin signing certificate does not match address in message headers.-8099Unableto import. Error attempting to import private key.-8098Unableto import. Error attempting to import certificate chain.-8097Unableto export. Unable to locate certificate or key by nickname.-8096Unableto export. Private key could not be located and exported.-8095Unableto export. Unable to write the export file.-8094Unableto import. Unable to read the import file.-8093Unableto export. Key database corrupt or deleted.-8092Unableto generate public-private key pair.-8091Passwordentered is invalid.-8090Oldpassword entered incorrectly.-8089Certificatenickname already in use.-8088PeerFORTEZZA chain has a non-FORTEZZA Certificate.-8087'A sensitive key cannot bemoved to the slot where it is needed.'-8086Invalidmodule name.-8085Invalidmodule path/filename.-8084Unableto add module.-8083Unableto delete module.-8082NewKRL is not later than the current one.-8081NewCKL has different issuer than current CKL.-8080Certificateissuer is not permitted to issue a certificate with this name.-8079'The key revocation listfor this certificate is not yet valid.'-8078'The certificaterevocation list for this certificate is not yet valid.'-8077'The requested certificatecould not be found.'-8076'The signer's certificatecould not be found.'-8075'The location for thecertificate status server has invalid format.'-8074'The OCSP response cannotbe fully decoded; it is of an unknown type.'-8073'The OCSP server returnedunexpected/invalid HTTP data.'-8072'The OCSP server found therequest to be corrupted or improperly formed.'-8071'The OCSP serverexperienced an internal error.'-8070'The OCSP server suggeststrying again later.'-8069'The OCSP server requiresa signature on this request.'-8068'The OCSP server hasrefused this request as unauthorized.'-8067'The OCSP server returnedan unrecognizable status.'-8066'The OCSP server has nostatus for the certificate.'-8065'You must enable OCSPbefore performing this operation.'-8064'You must set the OCSPdefault responder before performing this operation.'-8063'The response from theOCSP server was corrupted or improperly formed.'-8062'The signer of the OCSPresponse is not authorized to give status for this certificate.'-8061'The OCSP response is notyet valid (contains a date in the future).'-8060'The OCSP responsecontains out-of-date information.'-8059'The CMS or PKCS #7 Digestwas not found in signed message.'-8058'The CMS or PKCS #7Message type is unsupported.'-8057'PKCS #11 module could notbe removed because it is still in use.'-8056'Could not decode ASN.1data. Specified template was invalid.'-8055'No matching CRL was found.'-8054'You are attempting toimport a cert with the same issuer/serial as an existing cert, but thatis not the same cert.'-8053'NSS could not shutdown.Objects are still in use.'-8052'DER-encoded messagecontained extra unused data.'-8051'Unsupported elliptic curve.'-8050'Unsupported elliptic curve point form.'-8049'Unrecognized Object IDentifier.'-8048'Invalid OCSP signing certificate in OCSP response.'-8047'Certificate is revoked inissuer's certificate revocation list.'-8046'Issuer's OCSP responderreports certificate is revoked.'-8045'Issuer's CertificateRevocation List has an unknown version number.'-8044'Issuer's V1 CertificateRevocation List has a critical extension.'-8043'Issuer's V2 CertificateRevocation List has an unknown critical extension.'-8042'Unknown object type specified.'-8041'PKCS #11 driver violatesthe spec in an incompatible way.'-8040'No new slot event isavailable at this time.'-8039'CRL already exists.'-8038'NSS is not initialized.'-8037'The operation failedbecause the PKCS#11 token is not logged in.'
Table of Contents | Previous | Next | Index
Err Ssl Bad Mac Alert
Last Updated: 04/11/03 18:46:49 PDT

0 notes
Link
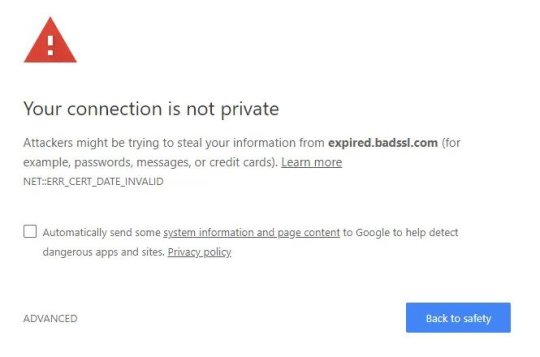
If Google Chrome is your main browser, chances are that you must have come across an error that reads “ERR_CERT_DATE_INVALID”, and it becomes quite important to fix ERR_CERT_DATE_INVALID error in Google Chrome if you want to access the site.
If you see this error ERR_CERT_DATE_INVALID or it reads “your connection is not private”, generally can be seen when you try to access a site that is not legitimate and your device is simply preventing Google Chrome to access the site.
Now, this error is generally seen when you visit sites secured with HTTPS but if the browser finds out that a site is not valid, it shows the error.
You should probably not visit such sites as they can be insecure and steal your passwords and transaction details which is totally unsafe. However, if you still want to visit the site with such an error, you can fix ERR_CERT_DATE_INVALID error in Google Chrome.
You can Fix ERR_CERT_DATE_INVALID Error in Google Chrome by several methods but you will need to detect the source for the thing that is causing the problem. Here is how:
How to Fix ERR_CERT_DATE_INVALID Error in Google Chrome
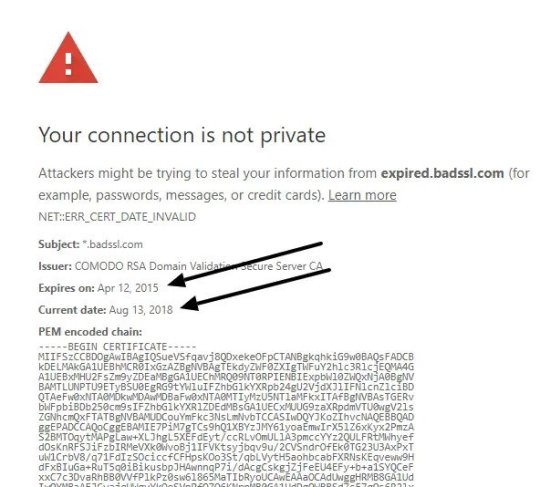
To solve “Your connection is not private” error you firstly need to see if it is a problem with your system or website and for that, you just need to see the error details. You will see two dates ‘Expires on’ and ‘Current date’. If the ‘Expires on’ date is of the past that means that the Website’s SSL certificate is expired and it is a problem from the website end. If the ‘Current date’ does not match with your system date then it is the problem of your system.
How to Fix ERR_CERT_DATE_INVALID Error in Google Chrome Caused by System
If you checked the above thing and find out that the problem is with your system then you can follow these steps:
Step 1: Check your system for date and time and correct it if it is wrong.
Step 2: Restart the system.
Step 3: Check your internet connection and run a malware scan.
Step 4: Disable all third party plugins.
Step 5: Clear Browser Cache or delete and reinstall Chrome.
That is it and this should fix the issue for you.
How to Fix ERR_CERT_DATE_INVALID Error in Google Chrome Caused by Website or Chrome
If the error is not caused by the system and it is a fault of the website or your internet connection or Google Chrome browser, then you can try the following methods.
Clear the Google Chrome Browser Cache
Step 1: Go to Chrome browser and tap on the three dots at the top right corner.
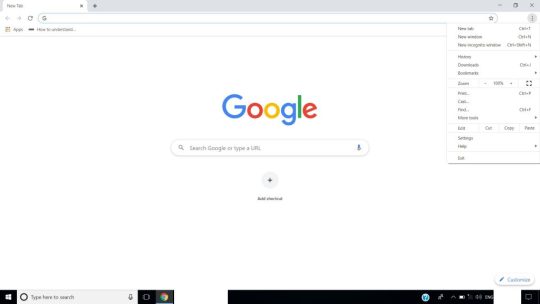
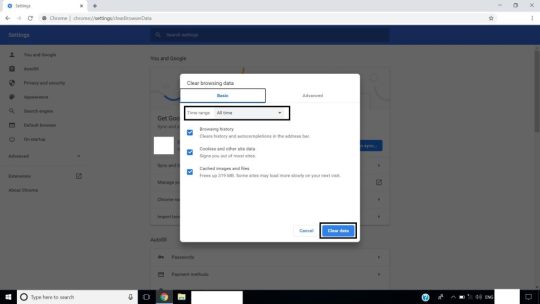
Step 2: From the menu go to ‘More tools’ and from there select ‘Clear browsing data’.

Step 3: Clean all the cached data and browsing history for ‘All time’.
That is it you are all done.
Disable System’s Firewall
Step 1: Type ‘Windows Firewall’ in the Windows search bar and click on it.
Step 2: Now from the menu select ‘Turn off Windows Defender Firewall’.
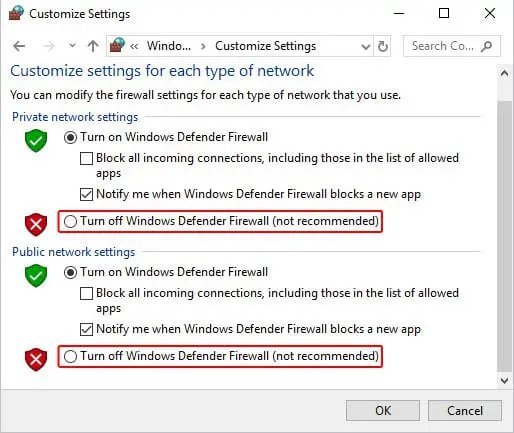
That is it and you will be all set but make sure that you turn that on quickly as it is not safe to browser without a firewall.
Interchange DNS Servers with Google’s
Step 1: Go to Control Panel, and navigate to ‘Network and Sharing settings’.
Step 2: Right click on the network adaptor and then click on ‘Properties’.
Step 3: Click on ‘Internet Protocol Version 4(TCP/IPv4), and then on ‘Properties’.
Step 4: Click on ‘Use the following DNS server addresses’ and enter the following
8.8.8.8 8.8.4.4
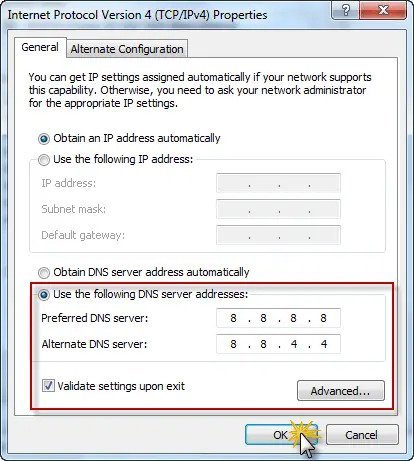
Then click on OK and you are all set.
Clear the SSL State of your System
Step 1: Open Google Chrome and go to ‘Settings’ and navigate to ‘Advanced Settings’.
Step 2: You will see ‘Change Proxy settings’ under Network, click on it.
Step 3: Now open the ‘Internet Properties’ dialog box. You will see an option to ‘Clear SSL state’, click on it and press OK and restart the browser.
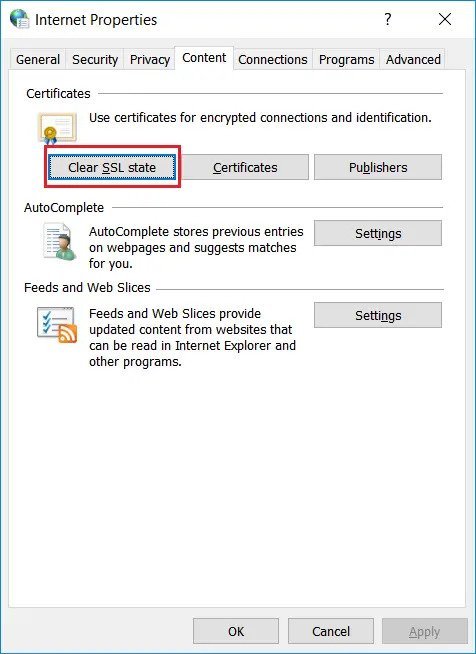
Reinstall Google Chrome
You can also completely uninstall the Google Chrome browser and then reinstall it and this shall most probably fix the problem for you.
So these were some of the methods by which you can fix ERR_CERT_DATE_INVAILD error or ‘Your connection is not private’ error in Google Chrome.
[su_box title="More Like This"]
How to Fix Slow Windows 10 Performance Issues
How to Fix 0x80070032 Error in Windows 10 Easily
How to Fix 0x0000007f Blue Screen Error in Windows 10
How to Fix ‘File Too Large for Destination File System’ Error in Windows 10
[/su_box]
via TechLatest
0 notes
Text
DOWNLOAD SONY NWZ E453 DRIVER
Uploader: Sky Downloads: 7788 Price: Free File Name: sony nwz e453 driver Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X File Version: 416101828 Download Type: http Date Added: 04 December, 2019 File Size: 23 Mb File Format: exe

Fixed Issues: - Fixed Sometimes(sony nwz e453 driver Sometimes) the system will hang on when plug dTPM2. - Fixed(sony nwz e453 driver Fixed) OpenVPN server .ovpn file exporting issue while changed the protocol to TCP.- Fixed PPTP VPN client related issues. - Radeon WattMan may not reach applied overclock states on Radeon RX Vega series graphics products or may cause mouse stuttering when left running in the background. - Fixed problem where the hot-key will not respond under ACPI with A/C attached and no batteries installed. - Fixed bug for "Test the Email server was added by motion detection setup wizard is error." 15. - Fixed(sony nwz e453 driver Fixed) boot with High speed SSD not able to find control box issue. - Fixes a phenomenon, where at the time of shooting in(sony nwz e453 driver in) very rare cases "Err 70" occurs, or the shutter does not release. - Fixed the password text format error. - Fixed the issue that the serial port and parallel port may(sony nwz e453 driver may) not work 2. - Fixed an issue that Mydlink service will be offline when FW upgrade to v1.04. Users content: Change the SSL description from SSL Login to Secure Login- Fix Ghost issue. Sound Blaster X-Fi. The Catalyst Control Center may experience random crashes in specific configurations. Important notice:- Note that installation of the update software cannot be undone. - The SATA devices are now displayed correctly on the POST screen. Easily build an entertainment PC or create a multimedia environment with its exceptionally high bandwidth. The optional palm rest design gives your wrist a break and provides great comfort when typing. - iOS 12.4.5 provides important security updates and is recommended for all users. EC won't send scan code even KB Filter is installed. - To support AMD G2 CPU.(with Biostar logo) It is highly recommended to always use the most recent driver version available. CDL DOWNLOAD RENT DRIVER A Supported OS: Microsoft Windows 8.1 Pro (32-bit) Windows 7 64-bit Windows Server 2003 64-bit Windows 8 Windows 7 Windows 10 Microsoft Windows 8.1 Enterprise (32-bit) Windows Server 2003 32-bit Notebook 8.1/8/7 64-bit Windows Vista 32-bit Windows 7 32-bit Windows XP 32-bit Windows 8.1/8/7/Vista 32-bit Microsoft Windows 10 (32-bit) Windows Server 2016 Microsoft Windows 8.1 Pro (64-bit) Notebook 8.1/8/7 32-bit Windows Server 2008 Microsoft Windows 8 Pro (32-bit) Windows Server 2012 R2 Windows 8.1 Microsoft Windows 8.1 (64-bit) Windows Server 2012 Microsoft Windows 8 Enterprise (32-bit) Microsoft Windows 8.1 Enterprise (64-bit) Microsoft Windows 8 Pro (64-bit) Microsoft Windows 10 (64-bit) Windows 8.1/8/7/Vista 64-bit Windows XP 64-bit Windows Vista 64-bit Microsoft Windows 8 (32-bit) Microsoft Windows 8.1 (32-bit) Microsoft Windows 8 (64-bit) Windows Server 2008 R2 Windows 2000 Microsoft Windows 8 Enterprise (64-bit) Searches: sony nwz e453 RH4875; sony nwz e453 Rkj487-kjf; sony nwz e453 R48k; sony nwz e453 RHBYZ4875; sony nwz e453 driver for Microsoft Windows 10 (64-bit); sony nwz e453 driver for Microsoft Windows 8.1 Pro (64-bit); sony nwz e453 driver for Microsoft Windows 8.1 Enterprise (32-bit); sony nwz e453 driver for Microsoft Windows 8 Pro (32-bit); sony nwz e453 driver for Windows 8.1/8/7/Vista 32-bit; sony nwz e453 R RH487-4; e453 nwz driver sony Compatible Devices: Tablet; Memory Card; Video Projector; Videocard; Gadget; Printer To ensure the integrity of your download, please verify the checksum value. MD5: 71917c286eb31ef81275ce1e6aba5423 SHA1: 5d30699fc2232902751bf0dd3eb74ae44daa8626 SHA-256: ebc1021c8c83fcd71350cb48bfd7601eb38e4f7a4942e17e7ff6662b4cbd9c40
0 notes
Link
QUIC (Quick UDP Internet Connections) is a test organize convention, the fundamental reason for which, is to give security insurance comparable to TLS/SSL, yet quicker. It was planned not exclusively to accelerate the client perusing knowledge yet in addition to enhance web based diversion illustrations.
#office/setup#office setup#office.com/setup#www.office.com/setup#www.office.com/setup.com#office.com/setup login
0 notes
Text
Understanding & Measuring HTTP Timings with Node.js
Understanding and measuring HTTP timings helps us to discover performance bottlenecks in client to server or server to server communication. This article explains timings in an HTTP request and shows how to measure them in Node.js.
Before we jump into HTTP timings, let's take a look at some basic concepts:
IP (Internet Protocol): IP is a network-layer protocol, deals with network addressing and routing. IP is responsible for delivering packets from the source host to the destination host based on the packet headers across one or more IP networks. It also defines packet structures that encapsulate the data to be delivered.
DNS (Domain Name Servers): DNS is a hierarchical decentralized naming system used to resolve human-readable hostnames like risingstack.com into machine-readable IP addresses.
TCP (Transmission Control Protocol): The TCP standard defines how to establish and maintain a network conversation between applications to exchange data. TCP provides reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts communicating over an IP network. An HTTP client initiates a request by establishing a TCP connection.
SSL/TLS (Transport Layer Security): TLS is a cryptographic protocol that provides communications security over a computer network. SSL (Secure Sockets Layer) is a deprecated predecessor to TLS. Both TLS and SSL use certificates to establish a secure connection. SSL certificates are not dependent on cryptographic protocols like TLS, a certificate contains a key pair: a public and a private key. These keys work together to establish an encrypted connection.
Now let's take a look at the timeline of a usual HTTP Request:
Timings explained:
DNS Lookup: Time spent performing the DNS lookup. DNS lookup resolves domain names to IP addresses. Every new domain requires a full round trip to do the DNS lookup. There is no DNS lookup when the destination is already an IP address.
TCP Connection: Time it took to establish TCP connection between a source host and destination host. Connections must be properly established in a multi-step handshake process. TCP connection is managed by an operating system, if the underlying TCP connection cannot be established, the OS-wide TCP connection timeout will overrule the timeout config of our application.
TLS handshake: Time spent completing a TLS handshake. During the handshake process endpoints exchange authentication and keys to establish or resume secure sessions. There is no TLS handshake with a not HTTPS request.
Time to First Byte (TTFB): Time spent waiting for the initial response. This time captures the latency of a round trip to the server in addition to the time spent waiting for the server to process the request and deliver the response.
Content Transfer: Time spent receiving the response data. The size of the response data and the available network bandwidth determinates its duration.
How do HTTP timings help to discover bottlenecks?
For example, if your DNS Lookup takes longer time than you expected, the issue might be with your DNS provider or with your DNS caching settings.
When you see longer Time to First Byte durations, you should check out the latency between the endpoints, but you should also check out the current load of the server.
Slow Content Transfer can be caused by inefficient response body like sending back too much data (unused JSON properties, etc.) or by a slow connection as well.
Measuring HTTP timings in Node.js
To measure HTTP timings in Node.js, we need to subscribe to a specific request, response and socket events. Here is a short code snippet how to do this in Node.js, this example focuses only to the timings:
const timings = { startAt: Date.now(), dnsLookupAt: undefined, tcpConnectionAt: undefined, tlsHandshakeAt: undefined, firstByteAt: undefined, endAt: undefined } const req = http.request({ ... }, (res) => { res.once('readable', () => { timings.firstByteAt = Date.now() }) res.on('data', (chunk) => { responseBody += chunk }) res.on('end', () => { timings.endAt = Date.now()) }) }) req.on('socket', (socket) => { socket.on('lookup', () => { timings.dnsLookupAt = Date.now() }) socket.on('connect', () => { timings.tcpConnectionAt = Date.now() }) socket.on('secureConnect', () => { timings.tlsHandshakeAt = Date.now() }) })
DNS Lookup only happens with domain names:
// There is no DNS lookup with IP address const dnsLookup = dnsLookupAt !== undefined ? dnsLookupAt - startAt : dnsLookupAt
TCP Connection happens immediately after the host is resolved:
const tcpConnection = tcpConnectionAt - (dnsLookupAt || startAt)
TLS handshake (SSL) happens only with https protocol:
// There is no TLS handshake without https const tlsHandshake = tlsHandshakeAt !== undefined ? (tlsHandshakeAt - tcpConnectionAt) : undefined
We wait for server to start sending First Byte:
const firstByte = firstByteAt - (tlsHandshakeAt || tcpConnectionAt)
Content Transfer starts with the first byte:
const contentTransfer = endAt - firstByteAt
Total Duration is calculated from start and end dates:
const total = endAt - startAt
Too see the whole example together check out our http://ift.tt/2xxTFF9 repository.
Tools to measure timings
Now that we know how to measure HTTP timings with Node, let's talk about existing tools that you can use to understand your HTTP requests.
request module
The popular request module has a built-in method to measure HTTP timings. You can enable it with the time property.
const request = require('request') request({ uri: 'https://risingstack.com', method: 'GET', time: true }, (err, resp) => { console.log(err || resp.timings) })
Distributed tracing
It's possible to collect HTTP timings with distributed tracing tools and visualize them on a timeline. This way, you can have a full picture of what's happening in the background and how much is the real cost of building distributed systems.
RisingStack's opentracing-auto library has a built-in flag to collect all the HTTP timings with OpenTracing.
HTTP Request timing with opentracing-auto in Jaeger.
Summary
Measuring HTTP Timings with Node.js can help to discover performance bottlenecks. The Node ecosystem provides great tools to extract these metrics from your application.
Understanding & Measuring HTTP Timings with Node.js published first on http://ift.tt/2fA8nUr
0 notes
Text
Understanding & Measuring HTTP Timings with Node.js
Understanding and measuring HTTP timings helps us to discover performance bottlenecks in client to server or server to server communication. This article explains timings in an HTTP request and shows how to measure them in Node.js.
Before we jump into HTTP timings, let's take a look at some basic concepts:
IP (Internet Protocol): IP is a network-layer protocol, deals with network addressing and routing. IP is responsible for delivering packets from the source host to the destination host based on the packet headers across one or more IP networks. It also defines packet structures that encapsulate the data to be delivered.
DNS (Domain Name Servers): DNS is a hierarchical decentralized naming system used to resolve human-readable hostnames like risingstack.com into machine-readable IP addresses.
TCP (Transmission Control Protocol): The TCP standard defines how to establish and maintain a network conversation between applications to exchange data. TCP provides reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts communicating over an IP network. An HTTP client initiates a request by establishing a TCP connection.
SSL/TLS (Transport Layer Security): TLS is a cryptographic protocol that provides communications security over a computer network. SSL (Secure Sockets Layer) is a deprecated predecessor to TLS. Both TLS and SSL use certificates to establish a secure connection. SSL certificates are not dependent on cryptographic protocols like TLS, a certificate contains a key pair: a public and a private key. These keys work together to establish an encrypted connection.
Now let's take a look at the timeline of a usual HTTP Request:
Timings explained:
DNS Lookup: Time spent performing the DNS lookup. DNS lookup resolves domain names to IP addresses. Every new domain requires a full round trip to do the DNS lookup. There is no DNS lookup when the destination is already an IP address.
TCP Connection: Time it took to establish TCP connection between a source host and destination host. Connections must be properly established in a multi-step handshake process. TCP connection is managed by an operating system, if the underlying TCP connection cannot be established, the OS-wide TCP connection timeout will overrule the timeout config of our application.
TLS handshake: Time spent completing a TLS handshake. During the handshake process endpoints exchange authentication and keys to establish or resume secure sessions. There is no TLS handshake with a not HTTPS request.
Time to First Byte (TTFB): Time spent waiting for the initial response. This time captures the latency of a round trip to the server in addition to the time spent waiting for the server to process the request and deliver the response.
Content Transfer: Time spent receiving the response data. The size of the response data and the available network bandwidth determinates its duration.
How do HTTP timings help to discover bottlenecks?
For example, if your DNS Lookup takes longer time than you expected, the issue might be with your DNS provider or with your DNS caching settings.
When you see longer Time to First Byte durations, you should check out the latency between the endpoints, but you should also check out the current load of the server.
Slow Content Transfer can be caused by inefficient response body like sending back too much data (unused JSON properties, etc.) or by a slow connection as well.
Measuring HTTP timings in Node.js
To measure HTTP timings in Node.js, we need to subscribe to a specific request, response and socket events. Here is a short code snippet how to do this in Node.js, this example focuses only to the timings:
const timings = { startAt: Date.now(), dnsLookupAt: undefined, tcpConnectionAt: undefined, tlsHandshakeAt: undefined, firstByteAt: undefined, endAt: undefined } const req = http.request({ ... }, (res) => { res.once('readable', () => { timings.firstByteAt = Date.now() }) res.on('data', (chunk) => { responseBody += chunk }) res.on('end', () => { timings.endAt = Date.now()) }) }) req.on('socket', (socket) => { socket.on('lookup', () => { timings.dnsLookupAt = Date.now() }) socket.on('connect', () => { timings.tcpConnectionAt = Date.now() }) socket.on('secureConnect', () => { timings.tlsHandshakeAt = Date.now() }) })
DNS Lookup only happens with domain names:
// There is no DNS lookup with IP address const dnsLookup = dnsLookupAt !== undefined ? dnsLookupAt - startAt : dnsLookupAt
TCP Connection happens immediately after the host is resolved:
const tcpConnection = tcpConnectionAt - (dnsLookupAt || startAt)
TLS handshake (SSL) happens only with https protocol:
// There is no TLS handshake without https const tlsHandshake = tlsHandshakeAt !== undefined ? (tlsHandshakeAt - tcpConnectionAt) : undefined
We wait for server to start sending First Byte:
const firstByte = firstByteAt - (tlsHandshakeAt || tcpConnectionAt)
Content Transfer starts with the first byte:
const contentTransfer = endAt - firstByteAt
Total Duration is calculated from start and end dates:
const total = endAt - startAt
Too see the whole example together check out our http://ift.tt/2xxTFF9 repository.
Tools to measure timings
Now that we know how to measure HTTP timings with Node, let's talk about existing tools that you can use to understand your HTTP requests.
request module
The popular request module has a built-in method to measure HTTP timings. You can enable it with the time property.
const request = require('request') request({ uri: 'https://risingstack.com', method: 'GET', time: true }, (err, resp) => { console.log(err || resp.timings) })
Distributed tracing
It's possible to collect HTTP timings with distributed tracing tools and visualize them on a timeline. This way, you can have a full picture of what's happening in the background and how much is the real cost of building distributed systems.
RisingStack's opentracing-auto library has a built-in flag to collect all the HTTP timings with OpenTracing.
HTTP Request timing with opentracing-auto in Jaeger.
Summary
Measuring HTTP Timings with Node.js can help to discover performance bottlenecks. The Node ecosystem provides great tools to extract these metrics from your application.
Understanding & Measuring HTTP Timings with Node.js published first on http://ift.tt/2w7iA1y
0 notes