#ethical hacking institute
Explore tagged Tumblr posts
Text
Empowering Minds: A Successful Ethical Hacking Workshop at Appin Technology Lab
Appin Technology’s ethical hacking workshop was an unequivocal triumph, leaving an indelible mark on every participant. The combination of expert sessions, hands-on learning, career insights, interactive exchanges, and participation certifications made this event a pivotal step toward building a community of proficient ethical hackers. The journey has just begun, and Appin Technology remains committed to guiding participants toward a secure and promising digital future.
1 note
·
View note
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
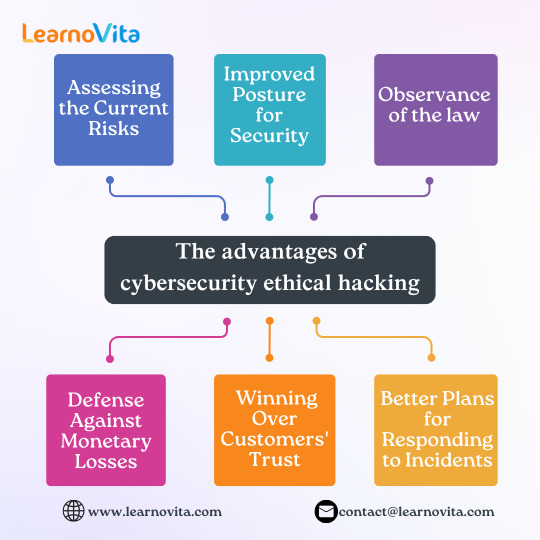
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text
Best Ethical Hacking Institute in Delhi – NEW DELHI YMCA IMSIT
Enhance your cybersecurity expertise with the best ethical hacking institute in delhi at NEW DELHI YMCA IMSIT. This one-year diploma in Cyber Security and Ethical Hacking covers key topics like vulnerability assessment, penetration testing, cryptography, firewall configuration, OS security, and monitoring—geared for 10+2 pass students, graduates, and professionals. Learn through practical, project-based training under experienced instructors. Join to build essential skills for roles in cybersecurity and network defense. Start your ethical hacking journey now.
0 notes
Text
https://mrwebsecure.com/cybersecurity-courses-in-dadar-mumbai
#cybersecurity#cybersecuritycourse#cybersecurityinstitute#ethical hacking institute in mumbai#ethical hacking
0 notes
Text
Master Cybersecurity with the Best Ethical Hacking Training Institute in Delhi
Choosing the right ethical hacking training institute in Delhi can be a game-changer for your career. With a growing emphasis on cybersecurity, ethical hackers are becoming indispensable across industries.
0 notes
Text
Indian Institute of Computer Science (IICS) is Delhi's leading IT training institute, offering a wide range of affordable programs and courses to empower learners with essential technology skills. With expert instructors and practical training in areas like AI, programming, web development, and more, we aim to prepare students for thriving careers in the tech industry. Join us to build your future in IT!best software engineer courses in Delhi
#Graphic Designer Course in Delhi#Best ethical hacking institute in Delhi#best cyber security institute in delhi#Web Development Course in Delhi#Advanced computer institute Delhi#Multimedia and Animation Classes in Delhi#IT training institute in delhi#Computer Courses and Classes in Delhi#Best e-accounting institute in Delhi#computer course with placement#Best computer education institute in Delhi
0 notes
Text
Ethical Hacking Institute in Delhi – Practical Cyber Security at YMCA IMSIT
Join the leading Ethical Hacking Institute in Delhi at NEW DELHI YMCA IMSIT and gain industry-ready cyber security skills. This course covers network security, ethical hacking tools, penetration testing, and cyber law essentials. Ideal for aspiring cybersecurity professionals, IT students, and tech enthusiasts, it provides hands-on lab sessions and expert-led modules. Start your career in ethical hacking with certifications that can boost your job prospects in both the private and government sectors.
0 notes
Text
Cyber Security Training in Dadar, Mumbai by Mr Web Secure
Description: Looking to build a strong career in cybersecurity? Mr Web Secure offers expert-led Cyber Security Training in Dadar, Mumbai, designed for beginners and professionals alike. Learn the latest industry tools, ethical hacking techniques, and real-world threat prevention methods from certified trainers. Our hands-on training ensures you gain practical knowledge to secure networks, protect data, and respond to cyber threats effectively. Located conveniently in Dadar, Mumbai, Mr Web Secure’s programs are tailored to meet the growing demand for cybersecurity professionals in today’s digital age. Whether you're a student, IT professional, or entrepreneur, our flexible batches and affordable pricing make it easy to start your journey into cybersecurity. Join Mr Web Secure’s Cyber Security Training in Dadar, Mumbai and take the first step towards a safer digital future.
#Ethical Hacking Training Institutes in Dadar#Best Ethical Hacking Institutes in Dadar#Cyber Security Training in Dadar#Cybersecurity courses in Dadar
0 notes
Text

#ethical hacking training institutes in patna#networking ccna training institutes in patna#digital marketing training in patna#autocad training in patna#summer training patna#software training institutes in patna#education#training#patna#bihar
0 notes
Text
Cybersecurity Education: Your Path to Becoming a Digital Guardian in an Ever-Changing Landscape
In an era dominated by digital technologies, the importance of cybersecurity has never been greater. As cyber dangers and attacks proliferate, the requirement for qualified professionals capable of protecting against them grows. In this article, we look at how cybersecurity education can help individuals become digital guardians in an ever-changing landscape of cyber threats.
The Growing Importance of Cybersecurity:
With the fast proliferation of digital infrastructure and the increasing interconnection of systems, potential vulnerabilities and dangers have grown dramatically. Organizations in all industries confront ongoing risks to their digital assets, ranging from large-scale data breaches to sophisticated ransomware assaults. As a result, there is an urgent demand for skilled cybersecurity specialists who can predict, detect, and successfully neutralize these risks.
Cybersecurity Education: Laying the Groundwork:
Cybersecurity education sets the framework for individuals to obtain the skills and knowledge required to address the wide range of difficulties provided by cyber attacks. Students learn about basic concepts like network security, cryptography, threat analysis, and incident response through comprehensive training programmes. Furthermore, they learn about emerging technologies and dynamic attack vectors, which prepares them to respond to changing threat landscapes.
Practical Experience and Hands-on Learning:
One of the distinguishing features of cybersecurity education is the emphasis on practical experience and hands-on learning. Students can use their theoretical understanding in real-world circumstances by modeling cyber attacks and defense techniques in controlled conditions. By participating in practical exercises including penetration testing, vulnerability assessments, and forensic analysis, students gain vital skills that may be applied directly to industry.
Specialization and certification:
Cybersecurity education provides a wide number of specialization options, allowing students to personalize their learning experience to their specific interests and professional aspirations. Whether they specialize in network security, cloud security, ethical hacking, or digital forensics, students can pursue certificates and qualifications that confirm their cybersecurity skills. These qualifications not only boost credibility, but they also strengthen employment prospects in a competitive labor environment.
Addressing the skill gap:
Despite the increasing demand for cybersecurity workers, there is a major skills gap in the business. Individuals who invest in cybersecurity education not only position themselves for profitable career prospects, but they also help to close the essential skills gap. Cybersecurity experts play an important role in boosting organizations' overall security posture and protecting digital assets from changing threats by engaging in continuous learning and professional development.
Conclusion:
In conclusion, cybersecurity education is the foundation for those seeking to become digital guardians in an ever-changing landscape of cyber threats. Students who get the necessary information, skills, and certifications can pursue rewarding jobs in cybersecurity, where they play an important role in defending against malicious actors and protecting the integrity of digital systems. As technology advances, the demand for qualified cybersecurity experts will grow, making cybersecurity education more important than ever.
Join the CACMS Institute for comprehensive cybersecurity education today. Receive hands-on practical instruction and guidance from our seasoned experts. Take the first step towards becoming a digital guardian in the ever-changing world of cyber threats.
For further information and to enroll, please call +91 8288040281 or visit CACMS!
Secure your future in cybersecurity with CACMS Institute.
#cacms institute#cacms#techeducation#techskills#digital landscape#ethical hacking course#ethical hacking training#ethical hacking course in Amritsar#ethical hacking certification#Cybersecurity education#cybersecurity course in amritsar
0 notes
Text
Hacking Course in Jaipur
0 notes
Text
Unveiling Data Excellence with Leading Data Analysis Training Institutes
Data analysis stands as a cornerstone in today's tech-driven world, powering informed decision-making and innovation. Choosing the right training institute is pivotal for mastering these crucial skills. Let's explore the how best data analysis training institutes in Bhubaneswar uncovering their offerings and excellence.
Importance of Data Analysis Training :
Data analysis holds immense significance across industries, empowering professionals to extract actionable insights from data. Choosing a reputable training institute becomes essential to grasp these skills effectively.

Choosing the Right Institute :
Selecting the ideal institute involves considering several factors:
Curriculum Relevance: Ensure the institute's curriculum covers crucial data analysis tools, methodologies, and practical applications.
Faculty Expertise: Institutes boasting experienced faculty members often provide valuable insights and real-world experiences.
Industry Connection: Institutes with industry partnerships or placement programs enhance career prospects post-training.
Specialized Offerings :
The best data analysis training institutes offer:
Comprehensive Curriculum: Covering statistical analysis, data visualization, machine learning, and tools like Python, R, or SQL.
Hands-on Projects: Practical assignments and real-world projects to reinforce learning and skill application.
Career Support: Placement assistance or connections with industry partners for internship opportunities or job placements.
Conclusion :
Mastering data analysis opens doors to a wide array of career opportunities in today's data-centric world. Institutes like Cloud Connect stand out for their commitment to excellence in imparting these skills. This makes it once of the best data analysis training institute in Odisha.
Choosing the right institute aligned with your learning objectives and career aspirations is key. Ensure to assess the curriculum, faculty expertise, and additional offerings to make an informed decision.
Remember, investing in quality data analysis training is an investment in a future brimming with opportunities in the data-driven realm.
#Best Ethical Hacking Training Institute in Odisha#Best Business Analysis Training Institute in Bhubaneswar
0 notes
Text
#ethical hacking training in India#ethical hacking in India#ethical hacking training institute in India#advance level ethical hacking training#hacking#ethical hacking#ethical hacker
0 notes
Text

#ethical hacking training institutes in patna#networking ccna training institutes in patna#digital marketing training in patna#autocad training in patna#summer training patna#software training institutes in patna#education#training#patna#bihar
0 notes
Text
Cybersecurity: The Key to Protecting Your Digital Identity and Privacy
In an era where our lives are increasingly connected with the digital sphere, protecting our digital identity and privacy has become critical. With the exponential growth of online activities, from social media interactions to financial transactions, the risks of cyber attacks are greater than ever before. In this digital age, cybersecurity has emerged as the primary shield protecting our digital life.
Understanding The Threat Landscape
Cyber risks take many forms, including data breaches, identity theft, malware, and phishing attempts. These dangers jeopardize sensitive personal information while also undermining trust in online systems and services. As technology advances, so do fraudsters' strategies, making it critical for individuals to be cautious and knowledgeable about cybersecurity best practices.
Significance of Digital Identity Protection
Our digital identities contain a variety of data, including personal information, financial records, and online behaviors. Securing this information is critical not only to prevent identity theft, but also to maintain our reputation and reliability in the digital sphere. A compromise of our digital identity can have serious ramifications for our financial stability, professional chances, and even our personal relationships.
Preserving Privacy in the Digital Age
Privacy is the foundation of individual freedom and liberty. However, in today's hyper-connected society, keeping privacy has grown more difficult. From surveillance technologies to data mining tactics, our online activities leave digital trails that dangerous actors can exploit. Cybersecurity measures are critical in protecting our privacy rights by ensuring that our personal information stays safe and protected from unauthorized access.
Empowering Individuals with Cybersecurity Education
While cybersecurity dangers may appear frightening, individuals may empower themselves by learning and developing cybersecurity skills. Education is an excellent technique for combating cyber threats because it teaches people how to detect possible risks, minimize vulnerabilities, and respond effectively to security crises. Individuals who invest in cybersecurity education improve not only their own digital safety but also the broader resilience of cyberspace.
Conclusion
In an increasingly linked world, cybersecurity is the foundation of our digital security and privacy. Individuals who recognise the importance of preserving their digital identity and privacy can take proactive efforts to reduce cyber risks and protect themselves from online dangers. We can create a safer and more secure digital future for ourselves and future generations by promoting cybersecurity education, awareness, and adherence to best practices.
Remember that in the digital world, cybersecurity is no longer an option—it is a requirement. Let's work together to protect our digital identities and privacy rights in an ever-changing online world.
Ready to take charge of your digital security? Join CACMS Institute today for comprehensive cybersecurity training that will provide you with hands-on practical skills and professional assistance.
Enroll in our Cyber Security Course in Amritsar and obtain the knowledge and competence required to properly protect your digital identity and privacy. Our professional teaching staff ensures that you receive a high-quality education and personalized attention throughout your learning journey.
Protect yourself online before it's too late. Contact us at +91 8288040281 or visit cacms.in to learn more about our Cyber Security Course in Amritsar and begin your path to a secure digital future now.
#cacms institute#cacms#techskills#techeducation#cyber security course in amritsar#cyber security#data privacy#digital identity#protecting digital Identity#ethical hacking course#ethical hacking training#ethical hacking certification#best computer institute in amritsar
0 notes
Text
Profession of your future spouse - Pick a pile
Pile 1/ Pile 2




Pile 3/ Pile 4
Hello everyone ! This is my another pick a pile or pac reading so please be kind and leave comment or reblog, and let me know if it resonated with you!
Note : This is a general reading or collective reading. It may or may not resonate with you. Please take what resonates and leave what doesn't. And it's totally okay if our energies aren't aligned!
How to pick : Take a deep breath and choose a pile which you feel most connected to! You can choose more than one pile, it just means both pile have messages for you!
Note : This reading is based on my intuition and channeled messages from tarot cards.
I worked really hard on this pile please show some love by leaving comments, likes and reblogs!
Liked my blog or readings? Tip me!
Pile 1
The cards I got for you - ace of wands, 3 of cups, 3 of pentacles, the chariot
1. Creative jobs (Graphic Design, 3D, interior, photography, anything to do with creativity they might be into art too.) In which they have to use their hands, they can be good with their hands as well.
2. Event planner, wedding planner, some sort of celebrative type of occupation like a DJ, or they might own a bar.
3. They can be a teacher/leader/boss/ higher or upper position than you, project manager, they are very well respected in their work.
4. Leader, medics, a politician? something to do with ethical hacking or computer.
Pile 2
(The cards I got for you - 6 of cups, 3 of swords, 4 of swords, the star, or hierophant)
1. I feel daycare teacher, or babysitter in their free time, taking care of children's and animals, they might teach younger childrens.
2. Sports or athletic
3.Nurse, surgeon, therapist.
4. Teacher again or own an institute or teach somewhere online (they might know two languages)
5. Manager
Pile 3
(Queen of wands, The magician, two of pentacles, knight of swords)
They find hard to balance between work and personal life but they do it, flawlessly.
1. Model, (something to do with their looks) , confident job, like they need to be confident in their own body, even can be famous or a bit known in crowd.
2. They are very skilled they might have juggled many jobs and they are good in all type of things
3. Sales executive, Carpenter
4. Call center, the kind of work they need to give order to someone
5. Their work might require travelling.
6. A navy officer, cop
7. Advocate, CEO, business person
8. med field (ayurvedic type or medicine pharmacist)
Pile 4:
The cards I got for you - Ace of pentacles, 4 of wands, 8 of swords, king of cups and wheel of fortune)
The work they do might have them be overwhelmed orburdened, like stressful but they love their work.
1. Bank worker or finance like finance analayst, tech, data scientist, data analyst.
2. Wedding planner, or they work something in event planner.
3. counsellor in schools, or judge.
4. They might deal with criminals too in a way, or might involve to travel, military.

Thank you for stopping by! Take care and remember you are loved <3
#tarotcommunity#tarot reading#tarotblr#tarot cards#pick a card reading#pick a pile#tarot witch#thetarotwitchcommunity#diviniation#futurespousereading#future spouse#pac reading#love reading#pick a tarot#witchblr#divine guidance#spirituality#astro community#pick a picture#pick a card#spiritualgrowth#free tarot reading#astroblr#tarot blog#general reading#pick a photo#exchange readings#divination
640 notes
·
View notes