#gmail password cracker
Explore tagged Tumblr posts
Text
I made the most amazing Paula cracker comic. I forget my phone password. I forget my Gmail password. Phone factory resets after being locked out for six hours. I lose the comic.😥
12 notes
·
View notes
Text
PROFESYONEL KİRALIK HACKER HİZMETLERİ
🎨Cihaz erişimleri - Galeri den video ve fotoğraf silme işlemleri
📍Konum tespiti - Konum takibi programları
🗒Whatsapp yazışmalar - WhatsApp silinen mesajları geri getirme
🔓Gmail şifre kırma işlemleri - hesap sms onay doğrulama hizmeti
🖥Ekran pin şifresi - Windows / Android / IOS
📂Harddisk / Hafıza kartı erişim ve data silme işlemleri
🛡Güvenlik kamera kayıtları ve erişim paneli
⚙️Websitesi kapatma / Hesap kapatma / Eposta kapatma işlemleri
📲Telefon erişim programı - Whatsapp erişim programı
📃Sosyal medya hesap takip hizmetleri - Yazışmaları dökme







⚠️Oyun hilesi bulunmamaktadır ve tüm işlemlerimiz 🔞+18 dir. Her sorumluluk sahibi vasfı taşıyan kişi ve kurumlara hizmet vermekteyiz.
📨Whatsapp ile iletişime geçiniz lütfen : +905465920064
#hackerkiralama #profesyonel #takip #programları #whatsapp #instagram #twitter #facebook #account #hacking #hirehacker #cracker #password #ddos #hacking #anonimous #cyber #phthon #mobil #windows #androidhack #ios #screen #computer #telephone
#hacker arıyorum#güvenilir hacker arıyorum#güvenilir kiralık hacker sitesi#güvenilir kiralık hacker arıyorum#instagram hack fiyat#hackerkiralama#hacker bulma sitesi
0 notes
Text
How To Secure Your Fortnite Account?

Fortnite took the world by storm. The 100-player “battle royale” has players of all ages, spread around the globe. At its 2018 height, Fortnite developers Epic Games were pulling in $350 million per week through in-game transactions.
Over time, Fortnite accounts have become an attractive proposition for hackers and other fraudsters. Stolen accounts with high-tier loot can be resold, with a willing market waiting to buy.
With that in mind, you need to secure your (and your children’s) Fortnite account. Here’s how to enable two-factor authentication (2FA) on your Fortnite account.
Do You Need 2FA on Your Fortnite Account?
In December 2018, the BBC interviewed one Slovenian teenager making an astonishing amount of money. The young chap in question was cracking Fortnite account passwords in the hope of finding an account full of premium skins and other loot. The cracker put his earnings at around $20,000 for seven months of work.
“It’s lucky dip basically, you either get a good account or you don’t. People like the rarity of the ‘skins’ and it’s about the look of them and showing off to friends.”
But that is just one example. The Epic Games Fortnite forum is full of threads about stolen accounts, lost skins, fraudulent V-Bucks transactions (V-Bucks is Fortnite’s internal currency), and more. Some Fortnite items are very rare. So rare, that they’re worth hundreds of dollars in the real world.
Epic Games is acutely aware of the issue, too. The vast majority of Fortnite’s userbase is young. Many have no idea about turning on 2FA, let alone how to practice secure password hygiene. The combination of these two factors means that crackers are using basic credential stuffing tools to blast through Fortnite accounts.
How to Enable 2FA on Your Fortnite Account
Whether you understand the urgency or you like the look of the free loot, here is how you enable 2FA on your Fortnite account.
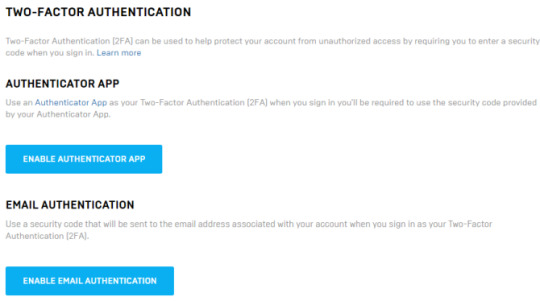
Before starting the process, consider what type of 2FA you are most comfortable using. Epic Games offers two options:
Authenticator app: An authenticator app is a 2FA app you keep on your smartphone (tablets, too). When you want to login to your Fortnite account, it will ask you for a six-digit code that will appear in the authenticator app. There are several authenticator apps available. I would strongly suggest using Authy or Google Authenticator.
Email authentication: Email authentication works by sending you a single-use 2FA security code to the email address associated with your Fortnite account.
Once you know which 2FA method you’re going to use, move onto securing your account. That is, if you’re using an authenticator app, make sure you install it on your smartphone before continuing.
Now, for Authenticator Apps:
Head to your Epic Games account in a web browser.
Under Password & Security, scroll down to Two-Factor Authentication.
Select Enable Authenticator App.
Open the authenticator app on your smartphone, then scan the QR code to add your Fortnite account.
Type the six-digit security code into the verification box, and complete the process.
On the next screen, you can generate a series of backup codes for your account locked with an authenticator app. Copy these to somewhere safe. You can only use each backup code once!

Now, for Email Authentication:
Head to your Epic Games account in a web browser.
Under Password & Security, scroll down to Two-Factor Authentication.
Select Enable Email Authentication.
Head to the email address associated with your Fortnite account and check for a verification email.
Copy the six-digit security code from the email into the Enable Email Verification box and press Continue.

Watch Out for Fortnite Scams
If the threat of Fortnite account crackers wasn’t enough, there are also scammers out there looking to trick unsuspecting users. Most of the scams center around free V-Bucks.
Scammers make flashy videos full of Fortnite imagery with alluring titles such as “How to Get Free V-Bucks” or “Check Out This Free V-Bucks Fortnite Glitch.” Most of the time, the videos invite users to a specific fraudulent website where you input a code from your Fortnite account.
In some cases, scammers can access the Fortnite account and use it to steal the existing V-Bucks, or lock the account for resale.
Enable Fortnite 2FA for Free Loot!
Epic Games understand there is a problem. That’s why they’re giving away some free loot to every account that turns 2FA on.
You don’t have to become a statistic though; it only takes a moment to secure your account. Similarly, as the Fortnite loading screen declares, “Only you can stop V-Buck scams.”
2FA is a great way to add additional security to all of your online accounts, not just Fortnite, and Epic Games. Here’s how to add 2FA to your Gmail, Facebook, Twitter, Instagram, and many other accounts.
1 note
·
View note
Text
Comment Développer son arsenal Digitale de site internet sur la base de Mots de passe robustes et fiables ? Voilà une question qui taraudent les esprits en cette fin 2020. Il est grand temps de les sécuriser avant le piratage. C’est vrai, le nombre de sites où il vous est demandé votre mot de passe ne cesse d’augmenter d’autant plus que les sites reliés à votre vie quotidienne (EDF, assurances de toutes sortes… ne peuvent s’ouvrir qu’à l’aide d’un mot de passe. la tentation est donc grande de se simplifier la vie en adoptant un mot de passe pour ouvrir toutes les portes des sites. Nous sommes en pleine époque du dernier match de football, votre série préférée est à l’écran chaque jour. Alors ! Et bien naturellement pour les utiliser dans vos mots de passe et d’ailleurs, ils viennent sous vos doigts qui les tapent avec allégresse sur le clavier. Histoire de vous simplifier la vie, vous utilisez le même mot de passe pour tous vos contacts : compte en banque, facebook, linkedlnk, gmail, celui de votre ordinateur et aussi amazon…….La liste est si longue… Oui mais vous devez prendre du temps et les lister et les modifier afin de ne pas vous faire piéger par les pirates du web. Le piratage cela n’arrive qu’aux autres !!!! Non, alors la prudence est de mise. Voici les conseils de Dynamique en cette fin d’année 2020. Mots de passe dangereux à écartez définitivement Splashdata, dans une étude, dresse la liste des mots de passe les plus utilisés. En voici quelques-uns. • D’abord ceux sont à base de chiffres : 123456, 12345678, abc123, 1234567, 111111, 123123 et 654321 • Ensuite les mots simples: password, dragon, baseball, qwerty, iloveyou, master, sunshine, passw0rd, shadow, superman, qazwsx et Football, welcome, monkey, login, starwars, freedom …. Supprimez les mots de passe préférés des pirates • Votre date de naissance et celle de votre entourage (mari, compagnon, compagne, enfants, petits-enfants….) • Votre lieu de naissance et ceux de votre entourage (mari, compagnon, compagne, enfants, petits-enfants…) • Votre numéro de téléphone • Les surnoms de vos proches En quelques mots, les mentions qui se retrouvent facilement dans vos réseaux sociaux. A lire aussi Sécurité 4 : Cracker des mots de passe et choisir un bon mot de passe Appliquez avec rigueur les règles des mots de passe proposées par la CNIL. Un mot de passe c’est une longueur combinée avec des chiffres, de la ponctuation et des signes – Longueur du mot de passe : Il doit être au minimum de 8 caractères et environ de 14 caractères mais surtout : Associez-les avec des chiffres + de la ponctuation (, ; : ! ? . /) + des signes (< > * $ £ µ) En bref, utilisez la richesse de votre clavier. Utilisez de préférence une phrase que vous allez chercher dans votre culture par exemple : un seuletrevousmanque, danslajoieetlabonnehumeur A laquelle vous associez des chiffres + des ponctuations (, ; : ! ? . /) + des signes (< > * $ £ µ) Attention : ne jamais dérogez à cette règle : un mot de passe pour chaque compte d’utilisateur. Modifiez fréquemment vos mots de passe. Pour éviter les attaques de type phishing (usurpation d’identité). N’écrivez pas Vos mots de passe sur papier libre, dans votre agenda…. Testez la sécurité de son mot de passe à l’aide des outils suivants : Le test de PC-Optimise.com Passwordmeter.com Utilisez les logiciels de gestion de mots Ces logiciels souvent gratuits, qui sont des coffres-forts et qui permettent de centraliser, de crypter et de stocker vos mots de passe dans des lieux sécurisés : KeePass Password Safe Hushkey Password Keeper Expert 1Password LastPassEfficient Password Manager Phaedra Password Manager Sticky Password NordPass Roboform Dashlane Et surtout évitez de le donner volontairement ! Maintenant, c’est quoi votre mot de passe ?
0 notes
Text
Comment Développer son arsenal Digitale de site internet sur la base de Mots de passe robustes et fiables ? Voilà une question qui taraudent les esprits en cette fin 2020. Il est grand temps de les sécuriser avant le piratage. C’est vrai, le nombre de sites où il vous est demandé votre mot de passe ne cesse d’augmenter d’autant plus que les sites reliés à votre vie quotidienne (EDF, assurances de toutes sortes… ne peuvent s’ouvrir qu’à l’aide d’un mot de passe. la tentation est donc grande de se simplifier la vie en adoptant un mot de passe pour ouvrir toutes les portes des sites. Nous sommes en pleine époque du dernier match de football, votre série préférée est à l’écran chaque jour. Alors ! Et bien naturellement pour les utiliser dans vos mots de passe et d’ailleurs, ils viennent sous vos doigts qui les tapent avec allégresse sur le clavier. Histoire de vous simplifier la vie, vous utilisez le même mot de passe pour tous vos contacts : compte en banque, facebook, linkedlnk, gmail, celui de votre ordinateur et aussi amazon…….La liste est si longue… Oui mais vous devez prendre du temps et les lister et les modifier afin de ne pas vous faire piéger par les pirates du web. Le piratage cela n’arrive qu’aux autres !!!! Non, alors la prudence est de mise. Voici les conseils de Dynamique en cette fin d’année 2020. Mots de passe dangereux à écartez définitivement Splashdata, dans une étude, dresse la liste des mots de passe les plus utilisés. En voici quelques-uns. • D’abord ceux sont à base de chiffres : 123456, 12345678, abc123, 1234567, 111111, 123123 et 654321 • Ensuite les mots simples: password, dragon, baseball, qwerty, iloveyou, master, sunshine, passw0rd, shadow, superman, qazwsx et Football, welcome, monkey, login, starwars, freedom …. Supprimez les mots de passe préférés des pirates • Votre date de naissance et celle de votre entourage (mari, compagnon, compagne, enfants, petits-enfants….) • Votre lieu de naissance et ceux de votre entourage (mari, compagnon, compagne, enfants, petits-enfants…) • Votre numéro de téléphone • Les surnoms de vos proches En quelques mots, les mentions qui se retrouvent facilement dans vos réseaux sociaux. A lire aussi Sécurité 4 : Cracker des mots de passe et choisir un bon mot de passe Appliquez avec rigueur les règles des mots de passe proposées par la CNIL. Un mot de passe c’est une longueur combinée avec des chiffres, de la ponctuation et des signes – Longueur du mot de passe : Il doit être au minimum de 8 caractères et environ de 14 caractères mais surtout : Associez-les avec des chiffres + de la ponctuation (, ; : ! ? . /) + des signes (< > * $ £ µ) En bref, utilisez la richesse de votre clavier. Utilisez de préférence une phrase que vous allez chercher dans votre culture par exemple : un seuletrevousmanque, danslajoieetlabonnehumeur A laquelle vous associez des chiffres + des ponctuations (, ; : ! ? . /) + des signes (< > * $ £ µ) Attention : ne jamais dérogez à cette règle : un mot de passe pour chaque compte d’utilisateur. Modifiez fréquemment vos mots de passe. Pour éviter les attaques de type phishing (usurpation d’identité). N’écrivez pas Vos mots de passe sur papier libre, dans votre agenda…. Testez la sécurité de son mot de passe à l’aide des outils suivants : Le test de PC-Optimise.com Passwordmeter.com Utilisez les logiciels de gestion de mots Ces logiciels souvent gratuits, qui sont des coffres-forts et qui permettent de centraliser, de crypter et de stocker vos mots de passe dans des lieux sécurisés : KeePass Password Safe Hushkey Password Keeper Expert 1Password LastPassEfficient Password Manager Phaedra Password Manager Sticky Password NordPass Roboform Dashlane Et surtout évitez de le donner volontairement ! Maintenant, c’est quoi votre mot de passe ?
0 notes
Text
Comment Développer son arsenal Digitale de site internet sur la base de Mots de passe robustes et fiables ? Voilà une question qui taraudent les esprits en cette fin 2020. Il est grand temps de les sécuriser avant le piratage. C’est vrai, le nombre de sites où il vous est demandé votre mot de passe ne cesse d’augmenter d’autant plus que les sites reliés à votre vie quotidienne (EDF, assurances de toutes sortes… ne peuvent s’ouvrir qu’à l’aide d’un mot de passe. la tentation est donc grande de se simplifier la vie en adoptant un mot de passe pour ouvrir toutes les portes des sites. Nous sommes en pleine époque du dernier match de football, votre série préférée est à l’écran chaque jour. Alors ! Et bien naturellement pour les utiliser dans vos mots de passe et d’ailleurs, ils viennent sous vos doigts qui les tapent avec allégresse sur le clavier. Histoire de vous simplifier la vie, vous utilisez le même mot de passe pour tous vos contacts : compte en banque, facebook, linkedlnk, gmail, celui de votre ordinateur et aussi amazon…….La liste est si longue… Oui mais vous devez prendre du temps et les lister et les modifier afin de ne pas vous faire piéger par les pirates du web. Le piratage cela n’arrive qu’aux autres !!!! Non, alors la prudence est de mise. Voici les conseils de Dynamique en cette fin d’année 2020. Mots de passe dangereux à écartez définitivement Splashdata, dans une étude, dresse la liste des mots de passe les plus utilisés. En voici quelques-uns. • D’abord ceux sont à base de chiffres : 123456, 12345678, abc123, 1234567, 111111, 123123 et 654321 • Ensuite les mots simples: password, dragon, baseball, qwerty, iloveyou, master, sunshine, passw0rd, shadow, superman, qazwsx et Football, welcome, monkey, login, starwars, freedom …. Supprimez les mots de passe préférés des pirates • Votre date de naissance et celle de votre entourage (mari, compagnon, compagne, enfants, petits-enfants….) • Votre lieu de naissance et ceux de votre entourage (mari, compagnon, compagne, enfants, petits-enfants…) • Votre numéro de téléphone • Les surnoms de vos proches En quelques mots, les mentions qui se retrouvent facilement dans vos réseaux sociaux. A lire aussi Sécurité 4 : Cracker des mots de passe et choisir un bon mot de passe Appliquez avec rigueur les règles des mots de passe proposées par la CNIL. Un mot de passe c’est une longueur combinée avec des chiffres, de la ponctuation et des signes – Longueur du mot de passe : Il doit être au minimum de 8 caractères et environ de 14 caractères mais surtout : Associez-les avec des chiffres + de la ponctuation (, ; : ! ? . /) + des signes (< > * $ £ µ) En bref, utilisez la richesse de votre clavier. Utilisez de préférence une phrase que vous allez chercher dans votre culture par exemple : un seuletrevousmanque, danslajoieetlabonnehumeur A laquelle vous associez des chiffres + des ponctuations (, ; : ! ? . /) + des signes (< > * $ £ µ) Attention : ne jamais dérogez à cette règle : un mot de passe pour chaque compte d’utilisateur. Modifiez fréquemment vos mots de passe. Pour éviter les attaques de type phishing (usurpation d’identité). N’écrivez pas Vos mots de passe sur papier libre, dans votre agenda…. Testez la sécurité de son mot de passe à l’aide des outils suivants : Le test de PC-Optimise.com Passwordmeter.com Utilisez les logiciels de gestion de mots Ces logiciels souvent gratuits, qui sont des coffres-forts et qui permettent de centraliser, de crypter et de stocker vos mots de passe dans des lieux sécurisés : KeePass Password Safe Hushkey Password Keeper Expert 1Password LastPassEfficient Password Manager Phaedra Password Manager Sticky Password NordPass Roboform Dashlane Et surtout évitez de le donner volontairement ! Maintenant, c’est quoi votre mot de passe ?
0 notes
Text
Comment Développer son arsenal Digitale de site internet sur la base de Mots de passe robustes et fiables ? Voilà une question qui taraudent les esprits en cette fin 2020. Il est grand temps de les sécuriser avant le piratage. C’est vrai, le nombre de sites où il vous est demandé votre mot de passe ne cesse d’augmenter d’autant plus que les sites reliés à votre vie quotidienne (EDF, assurances de toutes sortes… ne peuvent s’ouvrir qu’à l’aide d’un mot de passe. la tentation est donc grande de se simplifier la vie en adoptant un mot de passe pour ouvrir toutes les portes des sites. Nous sommes en pleine époque du dernier match de football, votre série préférée est à l’écran chaque jour. Alors ! Et bien naturellement pour les utiliser dans vos mots de passe et d’ailleurs, ils viennent sous vos doigts qui les tapent avec allégresse sur le clavier. Histoire de vous simplifier la vie, vous utilisez le même mot de passe pour tous vos contacts : compte en banque, facebook, linkedlnk, gmail, celui de votre ordinateur et aussi amazon…….La liste est si longue… Oui mais vous devez prendre du temps et les lister et les modifier afin de ne pas vous faire piéger par les pirates du web. Le piratage cela n’arrive qu’aux autres !!!! Non, alors la prudence est de mise. Voici les conseils de Dynamique en cette fin d’année 2020. Mots de passe dangereux à écartez définitivement Splashdata, dans une étude, dresse la liste des mots de passe les plus utilisés. En voici quelques-uns. • D’abord ceux sont à base de chiffres : 123456, 12345678, abc123, 1234567, 111111, 123123 et 654321 • Ensuite les mots simples: password, dragon, baseball, qwerty, iloveyou, master, sunshine, passw0rd, shadow, superman, qazwsx et Football, welcome, monkey, login, starwars, freedom …. Supprimez les mots de passe préférés des pirates • Votre date de naissance et celle de votre entourage (mari, compagnon, compagne, enfants, petits-enfants….) • Votre lieu de naissance et ceux de votre entourage (mari, compagnon, compagne, enfants, petits-enfants…) • Votre numéro de téléphone • Les surnoms de vos proches En quelques mots, les mentions qui se retrouvent facilement dans vos réseaux sociaux. A lire aussi Sécurité 4 : Cracker des mots de passe et choisir un bon mot de passe Appliquez avec rigueur les règles des mots de passe proposées par la CNIL. Un mot de passe c’est une longueur combinée avec des chiffres, de la ponctuation et des signes – Longueur du mot de passe : Il doit être au minimum de 8 caractères et environ de 14 caractères mais surtout : Associez-les avec des chiffres + de la ponctuation (, ; : ! ? . /) + des signes (< > * $ £ µ) En bref, utilisez la richesse de votre clavier. Utilisez de préférence une phrase que vous allez chercher dans votre culture par exemple : un seuletrevousmanque, danslajoieetlabonnehumeur A laquelle vous associez des chiffres + des ponctuations (, ; : ! ? . /) + des signes (< > * $ £ µ) Attention : ne jamais dérogez à cette règle : un mot de passe pour chaque compte d’utilisateur. Modifiez fréquemment vos mots de passe. Pour éviter les attaques de type phishing (usurpation d’identité). N’écrivez pas Vos mots de passe sur papier libre, dans votre agenda…. Testez la sécurité de son mot de passe à l’aide des outils suivants : Le test de PC-Optimise.com Passwordmeter.com Utilisez les logiciels de gestion de mots Ces logiciels souvent gratuits, qui sont des coffres-forts et qui permettent de centraliser, de crypter et de stocker vos mots de passe dans des lieux sécurisés : KeePass Password Safe Hushkey Password Keeper Expert 1Password LastPassEfficient Password Manager Phaedra Password Manager Sticky Password NordPass Roboform Dashlane Et surtout évitez de le donner volontairement ! Maintenant, c’est quoi votre mot de passe ?
0 notes
Text
Email hacking tools online

#Email hacking tools online how to#
#Email hacking tools online cracker#
#Email hacking tools online software#
#Email hacking tools online download#
#Email hacking tools online free#
#Email hacking tools online software#
Outlook and Outlook Express Password Recovery Utility v.1.5 Outlook and Outlook Express Password Recovery Software is simple and easy to password recovery utility fully capable to recover and restore mail account passwords including email id, news group logins account password when created on Microsoft Outloo.
#Email hacking tools online cracker#
MSN password cracker program recovers all passwords entered for newsgroup account or email on MSN explorer.
Recover MSN Messenger Password v.2.0.1.5 MSN password unmasks utility retrieves missing or forgotten account details like login id, password and other critical account information.
Password length, complexity or language is not a problem!
Email Password Recovery Master v.1.0 Email Password Recovery Master will retrieve any lost email account password, which has been cashed by Eudora, The Bat!, Becky, IncrediMail, Gmail Notifier, Group Mail Free, PocoMail, etc.
#Email hacking tools online download#
The Auto eMail me Password and Download script does exactly that! If you offer Software, eBooks or anything that requires a password, well now you can take the headache out of having to remember the passwords and.
Auto eMail Password & Download Provided by: American Financing.
Internet Explorer Password Retrieval v.3.0.1.5 Crack web based email ID password of internet explorer and windows applications.
It is separate from our standard version that supports multiple webmail clients and Outlook Express.
Iconix eMail ID Outlook v.2003 A beta version of Iconix eMail ID supporting Outlook 2003 is now available.
The Instagram hacking tool should never be used for illegal purposes. However, it is necessary to respect the privacy of others and not use this tool as a means of hurting other people.
#Email hacking tools online free#
With this free Instagram hacker tool, you can get the password to their account and prank them well.
To play pranks on friends/family: Many people hack Instagram accounts of their friends or family member to play a joke on them.
You can get the new password used by the hacker and gain access to your account. This online tool will help you easily recover your hacked account back.
For retrieving a hacked account: Your account may have been hacked by someone else and your details changed.
Our Instagram hacking tool can help you get access to your account as long as you can remember the associated username. It can be easy to forget password used, especially if you have several accounts or are trying to log into your account using a new device.
To access an old account: If you have an old Instagram account and you are finding it hard to gain access to it then this is a great way to recover your account.
Out of those numerous reasons, here are some common ones: There are several reasons to hack an Instagram account and it doesn't have to be for malicious intents. The tool makes no mistakes and offers the right password as long as the correct username is provided. This means users do not have to worry about getting their account banned for typing in wrong passwords. And the best part? The results are reliable and trustworthy. Once you input the username, the tool processes and gives the password in less than 3 minutes. You do not have to wait for long hours to get the desired results.
It is fast and reliable: That's right.
Users can use this tool on a mobile phone or a personal system connected to the internet as it is compatible with all devices. Anyone with a mobile phone and an internet connection can use this tool. Users do not need to have coding knowledge or technical skills.
#Email hacking tools online how to#
With this tool, learning how to hack an Instagram account has gotten easier. Easy accessibility: If you are looking for a hacking tool that has a user-friendly interface and is easy to navigate, then this is your best bet.All that is required is the username of the Instagram account to be hacked and the tool will get the associated password. The Instagram hacking tool is a free tool used in retrieving passwords of Instagram accounts. You can use it as many times as possible at no charge whatsoever. There are no hidden fees at any point in time. It is free: For a system that does this kind of work, you will expect for there to be charged, right? However, this tool for hacking an Instagram account is completely free.There is no risk to your device or any account you own. It has a network protected service and does not require users to offer sensitive information. The Instagram password retrieval tool is safe and secure for all users. It is safe: The most important factor when using an online system for purposes such as this is the safety of such a tool.Why use this free Instagram hacking tool?

0 notes
Text
Hack Facebook Password Online Instantly For Free No Download

Hack A Facebook Account Instantly - starsxaser.
F - Hack Facebook Password Online Instantly.
Hack Facebook Password Free a:t5_3c13b.
The Original SicZine Facebook Password Hacker.
Hack Gmail Password Online Free No Download.
How to Hack FB Account for Free (No Download & No.
Facebook Password Extractor - hackers-arise.
10 Facebook Password Cracker in 2021 (100% Works!) - Spyine.
How to Hack FB ID & Account Password For Free - iStarApps.
5 Ways for Free Facebook Hack without Survey - GuestSpy.
Download Facebook Password Decryptor 15.0 - softpedia.
10 Best Ways to Hack Facebook Account - (2022 Updated).
Hacker - Hack Facebook Password For Free Online How to.
Hack A Facebook Account Instantly - starsxaser.
Download Facebook Password Decryptor - Recover lost or forgotten Facebook passwords saved by most popular web browsers, such as Chrome, Opera, Firefox, Internet Explorer and Safari.
F - Hack Facebook Password Online Instantly.
Facebook Password Extractor free for PC. Now, it is possible to know the login information for a Facebook user with the right tools. Indeed, Elcomsoft Facebook Password Extractor is a utility that gives you the ability to retrieve Facebook Password stored in browsers. Disclaimer: This program is not supported by its publisher anymore. Download Hack Facebook Password Software. SterJo Facebook Password Finder v.1.0 SterJo Facebook Password Finder is free application designed to recover the password of your Facebook account saved by most web browsers. Almost every browser has an option to remember logins and save you a lot of time when you need to retype them. Facebook password hacking tool download. facebook password hack news. facebook password hack 2021. what is facebook password hack. the best facebook password hacker faceaccess. facebook password hack free fire tamil. facebook password hack no otp. baixar o facebook password decryptor para hackear senha. facebook password hacker que es.
Hack Facebook Password Free a:t5_3c13b.
Hack Facebook Password Online Instantly For Free No Download No Survey Or Hack A Facebook Account Password Without Downloading Anything.
The Original SicZine Facebook Password Hacker.
Apr 08, 2020 · Part 5: Cocospy. It is hard to mention the best Facebook password crackers and leave out Cocospy from the list. Cocospy is the oldest app to offer phone monitoring services like Facebook password cracking. As Cocospy has been around since so many years, it has developed quite a concrete reputation in the market. To Hack a Facebook account is possible and thanks to PASS FINDER you will extract the password in 3 steps: Click the ' INSTALL ' button to start extracting Facebook passwords. Next you start PASS FINDER. After that, you simply follow the instructions on the screen. Features of PASS FINDER to find passwords.
Hack Gmail Password Online Free No Download.
Hacker - Hack Facebook Password For Free Online How to. May 04, 2022 Visit the Hyper-Cracker website and scroll down the page to locate the Hack Now Online option. Click on this option to open a new web page. Part 2: How to Hack a Facebook Account for Free No Download No Surveys. Jun 22, 2022 · Step 1: Open Facebook and click on 'Forgot Password'. Step 2: Enter the email address of the person whose account you wish to hack. Step 3: Click on 'No longer have access to these'. Step 4: Enter the email address where you want the reset password link to be sent.
How to Hack FB Account for Free (No Download & No.
Step 5: Filter the results. While the Wireshark is open, use filters to get the suitable values. Type and select the files which start with the POST. This is an important point, simply because POST stands for data which has been sent to a targeted website, in this case, Facebook. Apr 24, 2013 · It works instantly, no download needed to hack a facebook account. It's really simple to use, safe and super fast. Firstly, log into facebook and go to the person's profile page you want to be hacked.
Facebook Password Extractor - hackers-arise.
Just follow the steps for the key. Steps on Using Copy9 to Hacking Facebook Account Password Online 1. one of the primary belongings you should do is create an account for yourself. Confirm the data you provide is correct. You.
10 Facebook Password Cracker in 2021 (100% Works!) - Spyine.
Hack Facebook password online: FREE methods of hackers.Hack Facebook Online App - HyperCracker.5 Ways for Free Facebook Hack without Survey - GuestSpy.Free Facebook Account Generator - Easy login solution| Loginclicks.4 Ways to Hack Facebook Account Online - Tenorshare.Facebook Hacker v1.8 No Surveys, No... - Cracked PC Softwares.How to Hack Facebook Account for Free No Download No Surveys.How to. It works instantly, no download needed to hack a facebook account. It's really simple to use, safe and super fast. Firstly, log into facebook and go to the person's profile page you want to be hacked. People who are not even on Facebook flock on the site as soon as they get access to the internet. People often misuse the platform, which is why.
How to Hack FB ID & Account Password For Free - iStarApps.
Apr 23, 2020 · Step 2: Jailbreak/Root the target user’s phone and install Neatspy into it. Hide the icon. Step 3: Go to the Neatspy dashboard. From the left-hand panel, select the ‘Keylogger’ option. Now you’ll gain access to all the keys, simply wait and find out the password! This method is effective in hacking Facebook password. Online Facebook Hack You won't have to download any app on your phone or PC in order to use Spyier. You can just open any web browser you like on any device of your preference and use Spyier from there. It works through its dashboard, which is similar to using Facebook from your web browser. Data Security. Hack facebook account easily using our online fb password hacker for free! Brett Rivers Hacked 1 seconds ago. ID: 45915***** Kathy... Surely you have ever wondered how to hack a Facebook account and have not found the solution. Well, with this online tool you can do it easily and easily. Simply, visit the Facebook profile you want to hack.
5 Ways for Free Facebook Hack without Survey - GuestSpy.
Jul 06, 2022 · Get AppMessenger and hack Facebook profile remotely Online FB Messenger Hack Using the SS7 Exploit. To hack Messenger without target phone, one needs to perform a full transfer of a victim's account to a new device and download an archive containing the following files: received and sent messages, current GPS location data of the device, saved contacts, audio and video call logs, content..
Download Facebook Password Decryptor 15.0 - softpedia.
Once you've the User ID, look at the Official Website of Facebook Password Sniper by clicking here. Visit the bottom of the page and enter the username in the search bar named Facebook username or ID rdquo.Go through the start button and await the Rainbow Tables Method to snipe the password. CLICK HERE >>>> acebook-Hack/. Method 1. Use KidsGuard to Hack Messenger No Survey. This time, we are going to use a really powerful, trustworthy software to hack Facebook Messenger offline no survey. It is called KidsGuard. KidsGuard, just like the name suggests, is one of the perfect Spyware for iPhone & Android.
10 Best Ways to Hack Facebook Account - (2022 Updated).
.
Hacker - Hack Facebook Password For Free Online How to.
Step 1: From the main login page of Facebook and click on the "Forgot Password" option. Step 2: Enter the email ID of the user whose Facebook account you are looking to hack. Step 3: Next, click on the "No longer have access to these" option and key in an email ID which is linked to the Facebook account you are hacking. Aug 05, 2021 · 1. First you should get the e-mail login of the person’s facebook account. Hacking Fb Password. 2. Click on the button for forgotten passwords where you should type the e-mail address of the victim. The system will then ask you whether you want to reset the password through his e-mail address.
Other content:
Mini Militia Hack Apk Download For Android Unlimited Health
Download Gta 4 Setup Highly Compressed Rar For Pc
The Incredible Hulk Ultimate Destruction Game Download For Pc
Foxit Phantompdf Business 8 Serial Key
Hp Laserjet P1102 Driver

1 note
·
View note
Text
Facebook Hacker V1.8
Facebook Hacker Software V1 8 Free Download. Chas of clan hack download. It is 100 Working. The first thing you should find out about the hacks you want to use is the compatible device for its download and installation.Download Clash Of Clans Hack Version Apk. Pokemon Battle Ultimate Download (Working 100%) Pokemon Battle Ultimate is a GBA ROM. Facebook Hacker V1.9 Free Download Cnet - DOWNLOAD (Mirror #1). Download and install the Facebook Account Hacker Software for windows XP, windows vista, windows 7, windows 8, windows 8.1, and Windows 10 both 32/64 bit OS. Keep getting access to your desired person account through this single software, which is entirely free and has no cost for installation.
Every day, countless Facebook accounts get hacked.Ever asked yourself how they do it? How to hack Facebook successfully? As youall know facebook is the most famous social networking site in the world. Thisposition has encouraged hackers to always try to find security flaws inFacebook's system. Thanks to these flaws, hackers are able to hack anyFacebook account. You can easily hack facebook accounts too by using our web-based hacking application. It's simple! No download orinstall required. All you have to do is to simply input victim's profile URLaddress and click 'Hack Account'. A lot of hacking requests are automaticallyprocessed by our web-based application. The success rate (getting theaccount's password) is an outstanding 98%. The average time of the hackingprocess is 3 minutes.
Sep 06, 2016 Download Facebook Hacker for free. Does what it says on the tin. This is used to 'reclaim lost passwords'. It works as long as the person's password you are trying to get is from a gmail account. Facebook Password Hacking software, free download - Password Cracker, SterJo Facebook Password Finder, 2 Password, and many more programs. Facebook Password Hacker free download - Facebook Password Recovery Master, Wifi Hacker, SterJo Facebook Password Finder, and many more programs.
Why do people hack Facebook accounts?
There are many reasons to hack Facebook accounts. Some of these reasons are:
Lost Password Recovery
Cheating Partner
Monitoring Children's Activities
Spying on your crush
Investigation Purposes

Facebook Hacking Software V1 8 Free Download 2018 With Full Crack
Facebook Hacker V1.8

Facebook Hacker V1.8 Activation Key
How to start hacking Facebook accounts?
Facebook Hacking Software V1 8 free. download full
We've made it easy for you. Our web-based application takes care of everything. You only have to input the victim's profile link. Then click on 'Hack Account'. All you have to do now is to wait. Waiting time depends on password complexity but it will maximum takes 5 minutes to retrieve and decrypt the password from Facebook's database. Once successfully hacked, you will see a message saying that. Finally, click on 'HACK UP' to download the dashboard Facebook profil account. To prevent abuse, you might be asked to complete a short survey in order to verify that you're a human (not a bot).
Facebook Hacking Software V1 8 Free Download For Pc
Facebook Hacker V1.9

Facebook Hacker V1.9 Download

Facebook Hacker V1.8 Download
0 notes
Text
Sbi Account Hacking Software
Netbanking Branches. All branches of State Bank of India are Internet Banking enabled. If you already have an account with us, ask your branch to give you Internet Banking. If you don't have an account, just step into any of our branches and open an account with Internet Banking facility. Internet Banking facility is available free of cost. SBI Quick allows SBI’s banking customers to text the bank, or make a missed call, to retrieve information back by text message about their finances and accounts. It’s ideal for millions of the banking giant’s customers who don’t use smartphones or have limited data service. The SBI Apprentice Recruitment application process lasted from 20th November 2020 till 10th December 2020 and applications were received online on the official website – sbi.co.in. The online examination, which was earlier scheduled to be held tentatively in the month of January 2021 has been postponed due to the second wave of Covid-19 cases. Available at all branches except specialised branches e.g. Personal Banking Branches (PBBs)/ Special Personalize Banking (SPB)/ Mid Corporate Group (MCG)/ Corporate Account Group (CAG) branches. Withdrawal from branch or through ATM. Basic RuPay ATM-cum-debit card will be issued. Minimum balance amount is NIL.
Sbi Account Hacking Software
Sbi Account Hacking Software Online
Sbi Account Hacking Software Download
Sbi Account Hacking Software Free
Sbi Account Hacking Software Login
Email password hacking software hack, crack, and break web login form email id password of Gmail, AOL, MySpace, Hotmail, Yahoo, MSN messenger etc. Password cracking tool fetch secret code of different windows applications in few simple easy steps.
Sbi Bank Account Hacking software, free download It’s easier to keep track of your business finances if all these accounts are aggregated in one place, right in front of your eyes. More: Equifax data breach: How to protect yourself beyond a credit freeze.
Have you lost or forgotten your password or you want to hack password of any other person, try this password hacking / cracking software that helps you to hack / crack password of any windows application program as well as login websites. Email password breaker tool break secret code of windows instant manager (such as MSN, ICQ etc), web email (Yahoo, MSN, Hotmail, Gmail, AOL, Gmail, Orkut etc), different email clients and dial-up, LAN login password.

Powerful and affordable password cracker tools facilitate user to open different password protected application including Microsoft word, excel, access documents, zip, winrar, pdf files and other program. Password hacker software recover, recall and reset password of all FTP clients like CuteFtp, FlashFXP, SmartFtp, search engine account, news group account and Autocomplete form.
Sbi Account Hacking Software
Utility fetch password from local system memory saved by explorer and supports all web browsers like Mozilla, Netscape, Opera and all version of internet explorer. Download email password hacker / cracker software to show asterisks character password in their original string in some easy steps. Software Features:
Hack all windows program password (word, excel, access, pdf, zip, winrar etc).
Break login form password of Yahoo, Hotmail, MSN, Google, AOL, Lycos, and MySpace etc.
Capable to crack email password of news group account, search engine account, online shopping account etc.
Show original string hidden behind asterisks character in password textbox.
Freeware demo version with password hacking / cracking help option.
Fetch, decrypt and display password directly from system memory.
Crack character string regardless of its length and complexity.
Support all windows based operating system including 98 / 2000 / NT / ME / XP and Vista.
Reset FTP, FlashFXP and other server application password.
Version 2.0.1.5: Added support for Yahoo, Gmail, Hotmail, MySpace, Orkut saved password
7 steps to hack into someone’s bank account
7 Steps to hack a bank account Marrett black mesh chair.
Sbi Account Hacking Software Online
The experiment:
Herbert Thompson* in 2008 wanted to show the public how easy it was to access someone’s personal information and bank account.
He did the experiment on someone who he barely knew, a girl named Kim. Using the knowledge he knew about her, her name, where she was from, where she worked and roughly her age, he was able to access her bank account in ONLY 7 STEPS!!!
Read below to see how he did it – in the days before Facebook!
Step 1 Adobe indesign cc 2018 crack.
Google search. He googles her. Finds a blog and a resume. (Thompson called her blog a “goldmine.”) He gets information about grandparents, pets, and hometown. Most importantly he gets her college email address and current Gmail address.
Step 2 Next stop: Password recovery feature on her bank’s web site. He attempts to reset her bank password. The bank sends a reset link to her email, which he does not have access to. He needs to get access to her Gmail.
Step 3 Gmail access. He attempts to reset her Gmail password but Gmail sends this to her college email address. Gmail tells you this address’ domain (at least it did in 2008 when Thompson conducted the experiments) so he knew he had to get access to that specific address. Step 4 College email account page. Thompson clicks the “forgot password” link on this page and winds up facing a few questions. Home address, home zip code and home country? No problem, Thompson has it all from the same resume. The same resume found from the simple Google search done earlier. Then came a stumbling block: the college wanted her birthday. But he only had a rough idea of her age, no actual birth date.
Sbi Account Hacking Software Download
Step 5 State traffic court web site. Apparently, you can search for violations and court appearances by name! And such records include a birth date. (Facebook also makes this piece of data very easy to get even if people do not note their birth year… Remember Thompson knew roughly how old Kim was.) But he had no luck with the Department of Motor Vehicles.
Step 6 Thompson goes back to the blog and does a search for “birthday.” He gets a date but no year.
Sbi Account Hacking Software Free
Step 7 Finally, Thompson attempts the college reset password again. He fills in her birth date, and simply guesses the year. He gets it wrong. But the site gives him five chances, and tells him which field has the error. So he continues to guess. He gets access in under five guesses. He changes her college password. This gives him access to her Gmail password reset email. Google requires some personal information which he is able to get easily from her blog (e.g., father’s middle name.) Thompson changes the Gmail password and that gives him access to the bank account reset password email. Here again he is asked for personal information, but nothing that he could not glean from Kim’s blog (e.g., pet name and phone number.) He resets the bank password and bingo, has immediate access to all her records and money.
Sbi Account Hacking Software Login
About avemcomp
0 notes
Text
😍MASTER HACK PACK FOR YOU 😍
🔰 Netflix Cracker
🔰 Free 5 Year Netflix Trick ( You Can Create Unlimited Account )
🔰 Free Netflix using PayPal ( Video Tutorial )
🔰 Free Amazon Prime Trick + Video Tutorial
🔰 Hotstar Cracking Trick (Video Tutorial)
🔰 How To Bypass Link Shortner
🔰 Instagram Liker
🔰 Snow's YouTube Bot
🔰 YouTube View Booster Bot
🔰 YouTube Blazzer
🔰 1000 Android Hacks
🔰 Amazon Gift Cards
🔰 Paypal Method
🔰 Ebay Method
🔰 Free Amazon Gift Card Method
🔰 Free Pizza Method
🔰 Flipkart Carding Tutorial
🔰 How To Get Fresh Valid Proxy List For Cracking
🔰 How To Get A Free Master Card
🔰 How To Get Referrals
🔰 Bypass Gmail Mobile Verification Trick
🔰 Bypass Android Pattern Lock Using ADB
🔰 Get Refund Of GiftCard
🔰 Facebook Hacking Ebook
🔰 Get Things From Ebay For Free
🔰 SEO Secrets
🔰 Guide To Make Money Online
🔰 Hack Hotmail
🔰 Hack Gmail
🔰 4 Hacking Methods
🔰 CC Generator
🔰 CC Checker
🔰 Crack WEP in Linux
🔰 Get Massive YouTube Traffic
🔰 Get Passes To Pornsites
🔰 Hack WEP WiFi Password
🔰 Kick Someone Of A Wireless Network
🔰 Make $1000's A Week With Torrents
🔰 Make A Phisher For A Website (Facebook/Instragram/Etc)
🔰 Make Easy Money As An eBay Affiliate
🔰 Make Multiple Gmail Accounts With Only 1 Account
🔰 How To Make Mozilla 30 Times Faster
🔰 USA Whatsapp Number Trick
🔰 Collection Of Rare Hacking Ebooks
🔰 Starbucks Method
🔰 How To Call Someone From His Own Number (Caller Id Spoofing)
🔰 Transfer PP Balance Method
🔰 YouTube RED Trick
🔰 Gana Mod App
🔰 Netflix Mod App (Look a Like)
🔰 Saavn Mod App
🔰 Express VPN Mod App
🔰 7 Reasons a Credit Card Is Blocked
🔰 Amazon Carding Method + Video Tutorial
🔰 What is Carding?? (Video)
🔰 Basic Carding TutoBal
🔰 Phishing Tutorial
🔰 Easy Cardable Sites List
🔰 Find Local BIN's
🔰 Carding For Noobs
🔰 Carding Online Tools And Website
🔰 PayPal Carding
🔰 Wallmart Carding
🔰 Amazon Carding (Video Tutorial)
🔰 eBay Carding (Video Tutorial)
🔰 How To Find Credit Card For Carding ( Video )
🔰 Wifi Hacking Course
🔰 Bypass Gmail Mobile Verification
🔰 *Hack Instragram, Facebook & Much More With Your Android/PC*
🔰 Zomato Refund Trick
🔰 Latest eBay Card
🔰Free Fire hacking without id ban
🔰Bank account hacking with just a QR code/Link
🔰Free Fire Unlimited Diamond and coin by Reverse Engineering
💢Dm us to get it at just $25💢
🧨One Time Offer don't miss it
🎩contact - 8260915722(whatsapp)🎩
0 notes
Text
Instagram聊天記錄調查,Instagram查詢,Instagram感情調查,Instagram定位程式,Instagram破解程式
Instagram聊天記錄調查,Instagram查詢,Instagram感情調查,Instagram定位程式,Instagram破解程式
破解Instagram密碼-簡單,快速,免費!
立即使用Instagram Hacker破解Instagram密碼,這是我們易於使用的Instagram密碼破解程序,可讓您在數分鐘內破解Instagram密碼!
太空播放/暂停
q卸载| 停
f全屏
Shift + ← →慢/快
↑ ↓音量
m静音
← →寻找
。寻求上一个
第一的Instagram密码破解器!
由於我們的軟件���特的功能組合,使得Instagram黑客成為Instagram黑客破解需求的最簡單,最快和最安全的方式,成千上萬的人信任Instagram黑客的需求!
密碼破解高手專家提供您,Instagram,facebook、gmail、hotmail、skype、yahoo、Line.Twitter.LinkedIn.微信 行動電話定位,手機定位,facebook.line.微信.聊天簡訊恢復,等各種郵件信箱破解密碼、社交程式密碼破解.網站入侵.數據修改.信箱入侵破碼、駭客入侵程式,您有任何關於密碼破解等技術支援服務,歡迎請找我們最專業的密碼破解大師為您解決任何疑難雜症。專業駭客破解密碼聯絡電郵[email protected] 《全天24*7在線為你服務》
輕松的Instagram密碼破解 簡易Instagram駭客得益於我們的Instagram破解軟件提供的簡單,逐步的指導,沒有高級黑客或編碼技能的完整新手就可以輕松破解Instagram密碼!
在幾分鐘內破解Instagram密碼! 快速Instagram黑客由於Instagram黑客使用了獨特的專有密碼黑客引擎,我們的軟件可以在2分鐘內破解某人的Instagram密碼。這使得它成為破解Instagram密碼的最快方法。
匿名Instagram黑客 匿名破解Instagram密碼
使用Instagram Hacker,您可以放心自己的身份,並且與目標有關的任何其他數據都不會與第三方共享,因為進出我們軟件的所有流量都完全匿名,並且不保留任何日誌。
在任何設備上破解Instagram密碼 Instagram黑客可以在Windows,Android和iOS上使用,從而可以在家用計算機上或直接在啟用Android或iOS的設備上直接破解Instagram密碼!
實際的用戶評價!
它的功能與錫罐上所說的完全壹樣! 我想借此機會感謝Instagram Hacker背後的團隊。我壹直在尋找壹種方法來破解女友的Instagram密碼,因為她的行為越來越陌生。
如何從Windows計算機破解Instagram密碼 要開始破解Instagram密碼,只需單擊我們網站上多個下載按鈕中的任何壹個即可。我們的服務器將自動檢測您所使用的設備類型,並為您的平臺提供適當版本的Instagram Password Cracker。
將Instagram Hacker下載到您的計算機後,請繼續安裝並執行我們的軟件。
最後,按照簡單的屏幕逐步說明進行操作,您的目標Instagram密碼很快就會提供給您!
如何在Android或iOS上破解Instagram密碼 在Android或iOS上破解Instagram密碼就像從Windows計算機上壹樣簡單明了。通過直接從移動設備的瀏覽器訪問我們的網站來開始使用。
單擊多個�� Hack Instagram Now”按鈕中的任意壹個,我們的服務器將自動檢測您的設備類型,並將您重定向到適用於Android或iOS的基於Web的Instagram黑客應用程序。
到達那裏後,只需按照簡單的說明進行操作,您的目標Instagram密碼很快就會提供給您!
立即免費破解Instagram密碼! 開發Instagram Hacker的主要動機之壹是我們的目標,使各行各業的人們都可以使用Instagram Hacking。
為了實現這壹目標,我們現在免費為有限數量的用戶提供Instagram Hacker。快點,立即免費破解Instagram密碼!

0 notes
Text
12 Ways To Hack Facebook Account Password and Its Prevention Techniques 2019

Can you refer any reliable Facebook hacker? Is there any online FB cracker tool? Where can I get FB hacking software? Is there any free password finder? How can I hack someone’s Facebook account easily?
“Hack Facebook” is one of the most searched and hot topics around the Internet, like Gmail hacker. We have prepared a detailed list of how hackers can hack someone’s Facebook account easily in just a few minutes and how can we prevent the same.
All the techniques at a glance : Phishing Social Engineering Plain Password Grabbing Key Logger Browser Extension Hacker Malicious Application Hack Facebook Account Hacker Software Malicious Mobile Application Browser Vulnerabilities Self XSS Trojan Horses Facebook Zero Day To the best of my knowledge, there is no hacking tool. You won’t be able to find it anywhere. However, you will find many websites claiming that they are providing free hack tool (either online or offline), but you cannot download the password file without completing a survey. Even after going through a tiresome process of completing a survey, you would have got nothing in the end. These things are posted only withthe intention of making money. Don’t waste your precious time in searching such hack tool. READ MORE...https://www.techannels.com/12-ways-to-hack-facebook-account-password-and-its-prevention-techniques-2019/ Read the full article
#AccountHack#AccountHacker#facebook#FacebookAccount#FacebookAccountHack#FacebookAccountHacker#FacebookHack#FaceHack#FBZero#FBZeroDay#featured2#freehack#HACK#Hacking#keyhack#password#PasswordHACK#Passwordhacking#Phishing#SelfXSS#SelfXSSScam#Trojan#TrojanHorses#Vulnerabilities
0 notes
Photo


(via Gmail Hacker Pro 2.9.0 Crack With Activation Code Free Download)
Hacking has two sides, the good and the bad. Gmail Hacker Pro 2.9.0 Activation Code fully fits into the former category of safe hacking. The software provides you with the best tools for hacking. By using Gmail Password Cracker you can easily hack or access to any Gmail account. The software has a complicated algorithm and series of code to securely access and hacks all the time. This doesn’t limit the accessibility as its simple user interface ensures that even a non-professional can use it. Gmail Password Keygen doesn’t require you to spend an hour on hacking but it completes the hack in a matter of a few minutes. Sometimes, there are situations in you will have to do the wrong thing to do something right. Like blackmailing cases, cases of hidden information. In all these cases, hacking into a Gmail account may not seem malicious.
0 notes
Text
Security & Hacking Terms (Copy)
Attack Vector
An attack vector is a path or means by which a hacker (or cracker) can gain access to a computer or network server in order to deliver a payload or malicious outcome. Attack vectors enable hackers to exploit system vulnerabilities, including the human element.
Attribution
Attribution is the process of establishing who is behind a hack. Often, attribution is the most difficult part of responding to a major breach since experienced hackers may hide behind layers of online services that mask their true location and identity. Many incidents, such as the Sony hack, may never produce any satisfactory attribution.
Backdoor
Entering a protected system using a password can be described as going through the front door. Companies may build "backdoors" into their systems, however, so that developers can bypass authentication and dive right into the program. Backdoors are usually secret, but may be exploited by hackers if they are revealed or discovered.
Black hat
A black hat hacker is someone who hacks for personal gain and/or who engages in illicit and unsanctioned activities. As opposed to white hack hackers (see below), who traditionally hack in order to alert companies and improve services, black hat hackers may instead sell the weaknesses they discover to other hackers or use them.
Blue Team
A Blue Team is a group of individuals who perform an analysis of information systems to verify the effectiveness of each security measure, and to make certain all security measures will continue to be effective after implementation. The “defensive team fortifying the structure.” (see Red Team for offensive attacking).
Botnet
Is your computer part of a botnet? It could be, and you might not know it. Botnets, or zombie armies, are networks of computers controlled by an attacker. Having control over hundreds or thousands of computers lets bad actors perform certain types of cyberattacks, such as a DDoS (see below). Buying thousands of computers wouldn't be economical, however, so hackers deploy malware to infect random computers that are connected to the internet. If your computer gets infected, your machine might be stealthily performing a hacker's bidding in the background without you ever noticing.
Brute force
A brute force attack is arguably the least sophisticated way of breaking into a password-protected system, short of simply obtaining the password itself. A brute force attack will usually consist of an automated process of trial-and-error to guess the correct passphrase. Most modern encryption systems use different methods for slowing down brute force attacks, making it hard or impossible to try all combinations in a reasonable amount of time.
Bug / Bug Bounty Programs
A bug is a flaw or error in a software program. Some are harmless or merely annoying, but some can be exploited by hackers. That's why many companies have started using bug bounty programs to pay anyone who spots a bug before the bad guys do.
Cracking
A general term to describe breaking into a security system, usually for nefarious purposes. According to the New Hacker's Dictionary published by MIT Press, the words "hacking" and "hacker" (see below) in mainstream parlance have come to subsume the words "cracking" and "cracker," and that's misleading. Hackers are tinkerers; they're not necessarily bad guys. Crackers are malicious. At the same time, you'll see cracking used to refer to breaking, say, digital copyright protections—which many people feel is a just and worthy cause—and in other contexts, such as penetration testing (see below), without the negative connotation.
Crypto
Short for cryptography, the science of secret communication or the procedures and processes for hiding data and messages with encryption (see below).
Chip-off
A chip-off attack requires the hacker to physically remove memory storage chips in a device so that information can be scraped from them using specialized software. This attack has been used by law enforcement to break into PGP-protected Blackberry phones.
D
Dark web
The dark web is made up of sites that are not indexed by Google and are only accessible through specialty networks such as Tor (see below). Often, the dark web is used by website operators who want to remain anonymous. Everything on the dark web is on the deep web, but not everything on the deep web is on the dark web.
DDoS
This type of cyberattack has become popular in recent years because it's relatively easy to execute and its effects are obvious immediately. DDoS stands for Distributed Denial of Service Attack, which means an attacker is using a number of computers to flood the target with data or requests for data. This causes the target—usually a website—to slow down or become unavailable. Attackers may also use the simpler Denial of Service (DoS) attack, which is launched from one computer.
Deep web
This term and "dark web" or "dark net" are sometimes used interchangeably, though they shouldn't be. The deep web is the part of the internet that is not indexed by search engines. That includes password-protected pages, paywalled sites, encrypted networks, and databases—lots of boring stuff.
DEF CON
One of the most famous hacking conferences in the US and the world, which started in 1992 and takes place every summer in Las Vegas.
Digital Certificate
A digital passport or stamp of approval that proves the identity of a person, website or service on the internet. In more technical terms, a digital certificate proves that someone is in possession of a certain cryptographic key that, traditionally, can't be forged. Some of the most common digital certificates are those of websites, which ensure your connection to them is properly encrypted. These get displayed on your browser as a green padlock.
Encryption
The process of scrambling data or messages making it unreadable and secret. The opposite is decryption, the decoding of the message. Both encryption and decryption are functions of cryptography. Encryption is used by individuals as well as corporations and in digital security for consumer products.
End-to-end encryption
A particular type of encryption where a message or data gets scrambled or encrypted on one end, for example your computer or phone, and get decrypted on the other end, such as someone else's computer. The data is scrambled in a way that, at least in theory, only the sender and receiver—and no one else—can read it.
Evil maid attack
An evil maid attack is a hack that requires physical access to a computer—the kind of access an evil maid might have while tidying his or her employer's office, for example. By having physical access, a hacker can install software to track your use and gain a doorway even to encrypted information.
Exploit
An exploit is a way or process to take advantage of a bug or vulnerability in a computer or application. Not all bugs lead to exploits. Think of it this way: If your door was faulty, it could be simply that it makes a weird sound when you open it, or that its lock can be picked. Both are flaws but only one can help a burglar get in. The way the criminal picks the lock would be the exploit.
Forensics
On CSI, forensic investigations involve a series of methodical steps in order to establish what happened during a crime. When it comes to a hack, however, investigators are looking for digital fingerprints instead of physical ones. This process usually involves trying to retrieve messages or other information from a device—perhaps a phone, a desktop computer or a server—used, or abused, by a suspected criminal.
GCHQ
The UK's equivalent of the US' National Security Agency. GCHQ, or Government Communications Headquarters, focuses on foreign intelligence, especially around terrorism threats and cybersecurity. It also investigates the digital child pornography trade. "As these adversaries work in secret, so too must GCHQ," the organization says on its website. "We cannot reveal publicly everything that we do, but we remain fully accountable."
Hacker
This term has become—wrongly—synonymous with someone who breaks into systems or hacks things illegally. Originally, hackers were simply tinkerers, or people who enjoyed "exploring the details of programmable systems and how to stretch their capabilities," as the MIT New Hacker's Dictionary puts it. Hackers can now be used to refer to both the good guys, also known as white hat hackers, who play and tinker with systems with no malicious intent (and actually often with the intent of finding flaws so they can be fixed), and cybercriminals, or "black hat" hackers, or "crackers."
Hacktivist
A "hacktivist" is someone who uses their hacking skills for political ends. A hacktivist's actions may be small, such as defacing the public website of a security agency or other government department, or large, such as stealing sensitive government information and distributing it to citizens. One often-cited example of a hacktivist group is Anonymous.
Hashing
Say you have a piece of text that should remain secret, like a password. You could store the text in a secret folder on your machine, but if anyone gained access to it you'd be in trouble. To keep the password a secret, you could also "hash" it with a program that executes a function resulting in garbled text representing the original information. This abstract representation is called a hash. Companies may store passwords or facial recognition data with hashes to improve their security.
HTTPS/SSL/TLS
Stands for Hypertext Transfer Protocol, with the "S" for "Secure." The Hypertext Transfer Protocol (HTTP) is the basic framework that controls how data is transferred across the web, while HTTPS adds a layer of encryption that protects your connection to the most important sites in your daily browsing—your bank, your email provider, and social network. HTTPS uses the protocols SSL and TLS to not only protect your connection, but also to prove the identity of the site, so that when you type https://gmail.com you can be confident you're really connecting to Google and not an imposter site.
An abbreviation of "Information Security." It's the inside baseball term for what's more commonly known as cybersecurity, a term that irks most people who prefer infosec.
Jailbreak
Circumventing the security of a device, like an iPhone or a PlayStation, to remove a manufacturer's restrictions, generally with the goal to make it run software from non-official sources.
Keys
Modern cryptography uses digital "keys". In the case of PGP encryption, a public key is used to encrypt, or "lock", messages and a secret key is used to decrypt, or "unlock", them. In other systems, there may only be one secret key that is shared by all parties. In either case, if an attacker gains control of the key that does the unlocking, they may have a good chance at gaining access to.
Lulz
An internet-speak variation on "lol" (short for "laughing out loud") employed regularly among the black hat hacker set, typically to justify a hack or leak done at the expense of another person or entity. Sample use: y did i leak all contracts and employee info linked to Sketchy Company X? for teh lulz
Malware
Stands for "malicious software." It simply refers to any kind of a malicious program or software, designed to damage or hack its target. Viruses, worms, Trojan horses, ransomware, spyware, adware and more are malware.
Man-in-the-middle
A Man-in-the-Middle or MitM is a common attack where someone surreptitiously puts themselves between two parties, impersonating them. This allows the malicious attacker to intercept and potentially alter their communication. With this type of attack, one can just passively listen in, relaying messages and data between the two parties, or even alter and manipulate the data flow.
Metadata
Metadata is simply data about data. If you were to send an email, for example, the text you type to your friend will be the content of the message, but the address you used to send it, the address you sent it to, and the time you sent it would all be metadata. This may sound innocuous, but with enough sources of metadata—for example, geolocation information from a photo posted to social media—it can be trivial to piece together someone's identity or location.
NIST
The National Institute of Standards and Technology is an arm of the US Department of Commerce dedicated to science and metrics that support industrial innovation. The NIST is responsible for developing information security standards for use by the federal government, and therefore it's often cited as an authority on which encryption methods are rigorous enough to use given modern threats.
Nonce
A portmanteau of number and once, nonce literally means "a number only used once." It's a string of numbers generated by a system to identify a user for a one-time-use session or specific task. After that session, or a set period of time, the number isn't used again.
OpSec
OpSec is short for operational security, and it's all about keeping information secret, online and off. Originally a military term, OpSec is a practice and in some ways a philosophy that begins with identifying what information needs to be kept secret, and whom you're trying to keep it a secret from. "Good" OpSec will flow from there, and may include everything from passing messages on Post-Its instead of emails to using digital encryption. In other words: Loose tweets destroy fleets.
OTR
What do you do if you want to have an encrypted conversation, but it needs to happen fast? OTR, or Off-the-Record, is a protocol for encrypting instant messages end-to-end. Unlike PGP, which is generally used for email and so each conversant has one public and one private key in their possession, OTR uses a single temporary key for every conversation, which makes it more secure if an attacker hacks into your computer and gets a hold of the keys. OTR is also generally easier to use than PGP.
Password managers
Using the same, crummy password for all of your logins—from your bank account, to Seamless, to your Tinder profile—is a bad idea. All a hacker needs to do is get access to one account to break into them all. But memorizing a unique string of characters for every platform is daunting. Enter the password manager: software that keeps track of your various passwords for you, and can even auto-generate super complicated and long passwords for you. All you need to remember is your master password to log into the manager and access all your many different logins.
Penetration testing or pentesting
If you set up a security system for your home, or your office, or your factory, you'd want to be sure it was safe from attackers, right? One way to test a system's security is to employ people—pentesters—to purposely hack it in order to identify weak points. Pentesting is related to red teaming, although it may be done in a more structured, less aggressive way.
PGP
"Pretty Good Privacy" is a method of encrypting data, generally emails, so that anyone intercepting them will only see garbled text. PGP uses asymmetric cryptography, which means that the person sending a message uses a "public" encryption key to scramble it, and the recipient uses a secret "private" key to decode it. Despite being more than two decades old, PGP is still a formidable method of encryption, although it can be notoriously difficult to use in practice, even for experienced users.
Phishing
Phishing is really more of a form of social engineering than hacking or cracking. In a phishing scheme, an attacker typically reaches out to a victim in order to extract specific information that can be used in a later attack. That may mean posing as customer support from Google, Facebook, or the victim's cell phone carrier, for example, and asking the victim to click on a malicious link—or simply asking the victim to send back information, such as a password, in an email. Attackers usually blast out phishing attempts by the thousands, but sometimes employ more targeted attacks, known as spearphishing (see below).
Plaintext
Exactly what it sounds like—text that has not been garbled with encryption. This definition would be considered plaintext. You may also hear plaintext being referred to as "cleartext," since it refers to text that is being kept out in the open, or "in the clear." Companies with very poor security may store user passwords in plaintext, even if the folder they're in is encrypted, just waiting for a hacker to steal.
Pwned
Pwned is computer nerd jargon (or "leetspeak") for the verb "own." In the video game world, a player that beat another player can say that he pwned him. Among hackers, the term has a similar meaning, only instead of beating someone in a game, a hacker that has gained access to another user's computer can say that he pwned him. For example, the website "Have I Been Pwned?" will tell you if your online accounts have been compromised in the past.
RAT
RAT stands for Remote Access Tool or Remote Access Trojan. RATs are really scary when used as malware. An attacker who successfully installs a RAT on your computer can gain full control of your machine. There is also a legitimate business in RATs for people who want to access their office computer from home, and so on. The worst part about RATs? Many malicious ones are available in the internet's underground for sale or even for free, so attackers can be pretty unskilled and still use this sophisticated tool.
Ransomware
Ransomware is a type of malware that locks your computer and won't let you access your files. You'll see a message that tells you how much the ransom is and where to send payment, usually requested in bitcoin, in order to get your files back. This is a good racket for hackers, which is why many consider it now an "epidemic," as people typically are willing to pay a few hundred bucks in order to recover their machine. It's not just individuals, either. In early 2016, the Hollywood Presbyterian Medical Center in Los Angeles paid around $17,000 after being hit by a ransomware attack.
Rainbow table
A rainbow table is a complex technique that allows hackers to simplify the process of guessing what passwords hide behind a "hash" (see above).
Red team
To ensure the security of their computer systems and to expose any unknown vulnerabilities, companies may hire hackers who organize into a "red team" in order to run oppositional attacks against the system and attempt to completely take it over. In these cases, being hacked is a good thing because organizations may fix vulnerabilities before someone who's not on their payroll does. Red teaming is a general concept that is employed across many sectors, including military strategy. The “offensive attacking team” (also see “Blue Team” for defense).
Root
In most computers, "root" is the common name given to the most fundamental (and thus most powerful) level of access in the system, or is the name for the account that has those privileges. That means the "root" can install applications, delete and create files. If a hacker "gains root," they can do whatever they want on the computer or system they compromised. This is the holy grail of hacking.
Rootkit
A rootkit is a particular type of malware that lives deep in your system and is activated each time you boot it up, even before your operating system starts. This makes rootkits hard to detect, persistent, and able to capture practically all data on the infected computer.
Salting
When protecting passwords or text, "hashing" (see above) is a fundamental process that turns the plaintext into garbled text. To make hashing even more effective, companies or individuals can add an extra series of random bytes, known as a "salt," to the password before the hashing process. This adds an extra layer of protection.
Sandbox
In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures or software vulnerabilities from spreading. It is often used to execute untested or untrusted programs or code, possibly from unverified or untrusted third parties, suppliers, users or websites, without risking harm to the host machine or operating system. Often sandboxes are seen as a specific example of virtualization, since VM instances of sandboxes are frequently used to test unverified programs that may contain a virus or other malicious code, without allowing the software to harm the host device.
Script kiddies
This is a derisive term for someone who has a little bit of computer savvy and who's only able to use off-the-shelf software to do things like knock websites offline or sniff passwords over an unprotected Wi-Fi access point. This is basically a term to discredit someone who claims to be a skilled hacker.
Shodan
It's been called "hacker's Google," and a "terrifying" search engine. Think of it as a Google, but for connected devices rather than websites. Using Shodan you can find unprotected webcams, baby monitors, printers, medical devices, gas pumps, and even wind turbines. While that's sounds terrifying, Shodan's value is precisely that it helps researchers find these devices and alert their owners so they can secure them.
Signature
Another function of PGP, besides encrypting messages, is the ability to "sign" messages with your secret encryption key. Since this key is only known to one person and is stored on their own computer and nowhere else, cryptographic signatures are supposed to verify that the person who you think you're talking to actually is that person. This is a good way to prove that you really are who you claim to be on the internet.
Side channel attack
Your computer's hardware is always emitting a steady stream of barely-perceptible electrical signals. A side-channel attack seeks to identify patterns in these signals in order to find out what kind of computations the machine is doing. For example, a hacker "listening in" to your hard drive whirring away while generating a secret encryption key may be able to reconstruct that key, effectively stealing it, without your knowledge.
Sniffing
Sniffing is a way of intercepting data sent over a network without being detected, using special sniffer software. Once the data is collected, a hacker can sift through it to get useful information, like passwords. It's considered a particularly dangerous hack because it's hard to detect and can be performed from inside or outside a network.
Social engineering
Not all hacks are carried out by staring at a Matrix-like screen of green text. Sometimes, gaining entry to a secure system is as easy as placing a phone call or sending an email and pretending to be somebody else—namely, somebody who regularly has access to said system but forgot their password that day. Phishing (see above) attacks include aspects of social engineering, because they involve convincing somebody of an email sender's legitimacy before anything else.
Spearphishing
Phishing and spearphishing are often used interchangeably, but the latter is a more tailored, targeted form of phishing (see above), where hackers try to trick victims into clicking on malicious links or attachments pretending to be a close acquaintance, rather than a more generic sender, such as a social network or corporation. When done well, spearphishing can be extremely effective and powerful. As a noted security expert says, "give a man a 0day and he'll have access for a day, teach a man to phish and he'll have access for life."
Spoofing
Hackers can trick people into falling for a phishing attack (see above) by forging their email address, for example, making it look like the address of someone the target knows. That's spoofing. It can also be used in telephone scams, or to create a fake website address.
Spyware
A specific type of malware of malicious software designed to spy, monitor, and potentially steal data from the target.
State actor
State actors are hackers or groups of hackers who are backed by a government, which may be the US, Russia, or China. These hackers are often the most formidable, since they have the virtually unlimited legal and financial resources of a nation-state to back them up. Think, for example, of the NSA. Sometimes, however, state actors can also be a group of hackers who receive tacit (or at least hidden from the public) support from their governments, such as the Syrian Electronic Army.
Threat model
Imagine a game of chess. It's your turn and you're thinking about all the possible moves your opponent could make, as many turns ahead as you can. Have you left your queen unprotected? Is your king being worked into a corner checkmate? That kind of thinking is what security researchers do when designing a threat model. It's a catch-all term used to describe the capabilities of the enemy you want to guard against, and your own vulnerabilities. Are you an activist attempting to guard against a state-sponsored hacking team? Your threat model better be pretty robust. Just shoring up the network at your log cabin in the middle of nowhere? Maybe not as much cause to worry.
Token
A small physical device that allows its owner to log in or authenticate into a service. Tokens serve as an extra layer of security on top of a password, for example. The idea is that even if the password or key gets stolen, the hacker would need the actual physical token to abuse it.
Tor
Tor is short for The Onion Router. Originally developed by the United States Naval Research Laboratory, it's now used by bad guys (hackers, pedophiles) and good guys (activists, journalists) to anonymize their activities online. The basic idea is that there is a network of computers around the world—some operated by universities, some by individuals, some by the government—that will route your traffic in byzantine ways in order to disguise your true location. The Tor network is this collection of volunteer-run computers. The Tor Project is the nonprofit that maintains the Tor software. The Tor browser is the free piece of software that lets you use Tor. Tor hidden services are websites that can only be accessed through Tor.
Tails
Tails stands for The Amnesic Incognito Live System. If you're really, really serious about digital security, this is the operating system endorsed by Edward Snowden. Tails is an amnesic system, which means your computer remembers nothing; it's like a fresh machine every time you boot up. The software is free and open source. While it's well-regarded, security flaws have been found.
Vector
A vector in computing, specifically when talking about malicious code such as viruses or worms, is the method that this code uses to propagate itself or infect a computer. This sense is similar to, and derived from, its meaning in biology. Also see “malware.”
Vector Attack
See “attack vector.”
Verification (dump)
The process by which reporters and security researchers go through hacked data and make sure it's legitimate. This process is important to make sure the data is authentic, and the claims of anonymous hackers are true, and not just an attempt to get some notoriety or make some money scamming people on the dark web.
VPN
VPN stands for Virtual Private Network. VPNs use encryption to create a private and secure channel to connect to the internet when you're on a network you don't trust (say a Starbucks, or an Airbnb WiFi). Think of a VPN as a tunnel from you to your destination, dug under the regular internet. VPNs allow employees to connect to their employer's network remotely, and also help regular people protect their connection. VPNs also allow users to bounce off servers in other parts of the world, allowing them to look like they're connecting from there. This gives them the chance to circumvent censorship, such as China's Great Firewall, or view Netflix's US offerings while in Canada. There are endless VPNs, making it almost impossible to decide which ones are the best.
Virus
A computer virus is a type of malware that typically is embedded and hidden in a program or file. Unlike a worm (see below), it needs human action to spread (such as a human forwarding a virus-infected attachment, or downloading a malicious program.) Viruses can infect computers and steal data, delete data, encrypt it or mess with it in just about any other way.
Vuln
Abbreviation for "vulnerability." Another way to refer to bugs or software flaws that can be exploited by hackers.
Warez
Pronounced like the contraction for "where is" (where's), warez refers to pirated software that's typically distributed via technologies like BitTorrent and Usenet. Warez is sometimes laden with malware, taking advantage of people's desire for free software.
White hat
A white hat hacker is someone who hacks with the goal of fixing and protecting systems. As opposed to black hat hackers (see above), instead of taking advantage of their hacks or the bugs they find to make money illegally, they alert the companies and even help them fix the problem.
Worm
A specific type of malware that propagates and replicates itself automatically, spreading from computer to computer. The internet's history is littered with worms, from the Morris worm, the first of its kind, and the famous Samy worm, which infected more than a million people on MySpace.
Zero-day
A zero-day or "0day" is a bug that's unknown to the software vendor, or at least it's not patched yet. The name comes from the notion that there have been zero days between the discovery of the bug or flaw and the first attack taking advantage of it. Zero-days are the most prized bugs and exploits for hackers because a fix has yet to be deployed for them, so they're almost guaranteed to work.
0 notes