#gmail password hacker
Explore tagged Tumblr posts
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
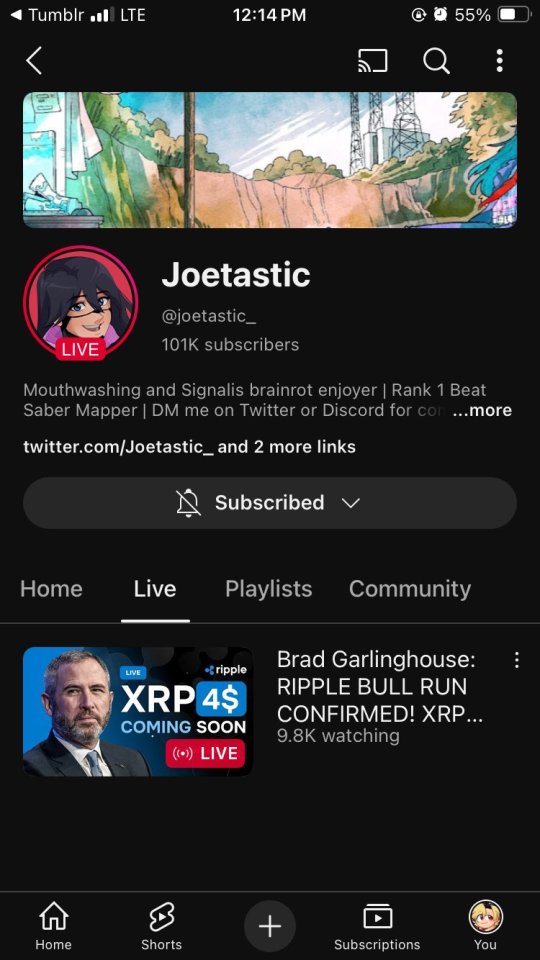
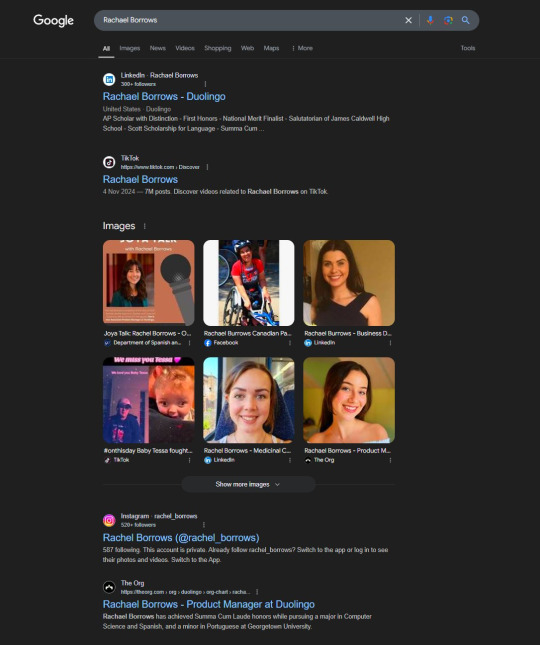
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
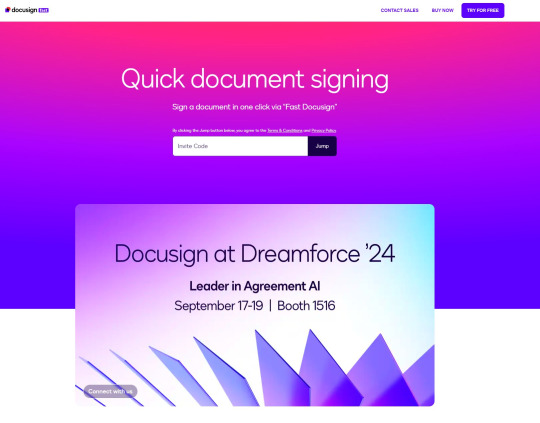
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
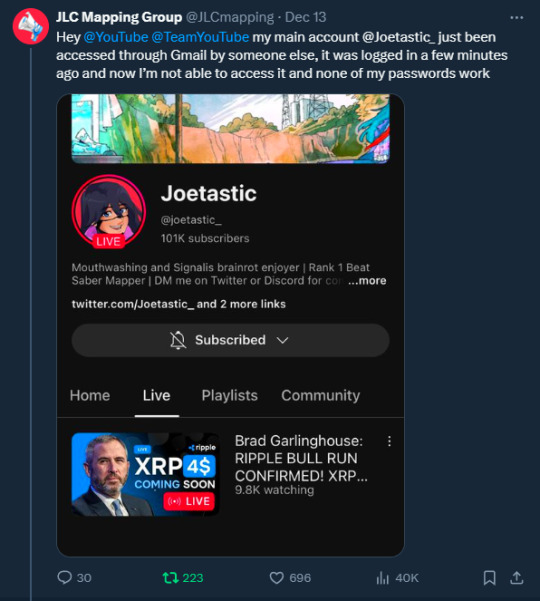
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
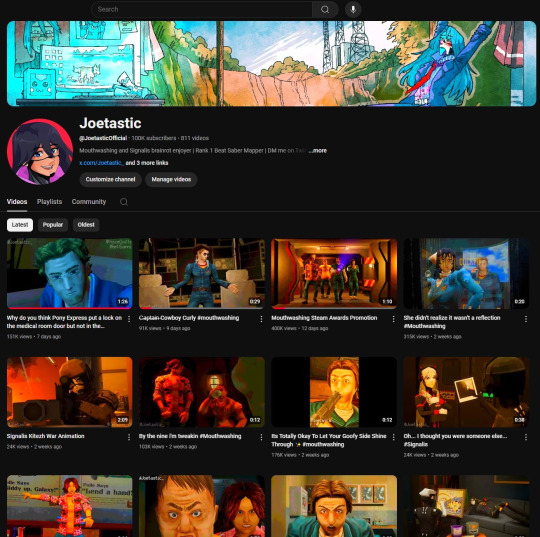
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
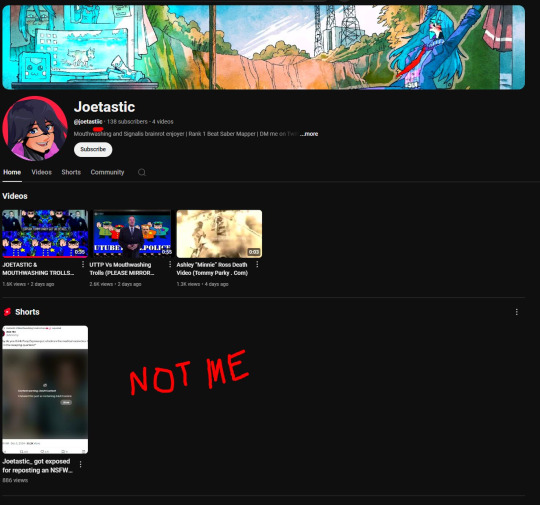
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
after 16 login attempts and a password change to the gmail I've had since I was 10
*hacker voice* I'm in.
22 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
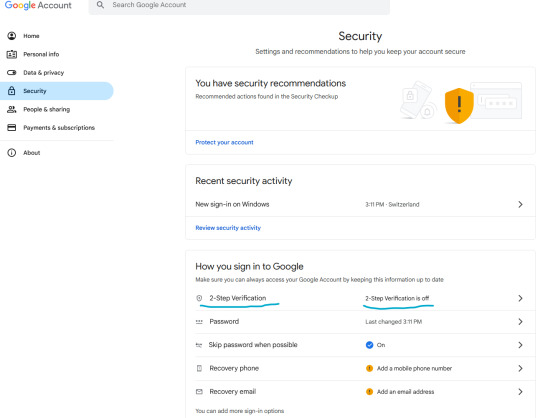
Let's enable two-step verification first.
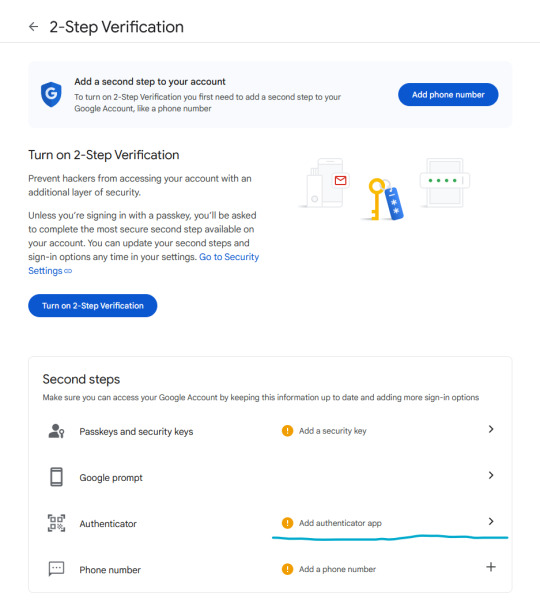
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
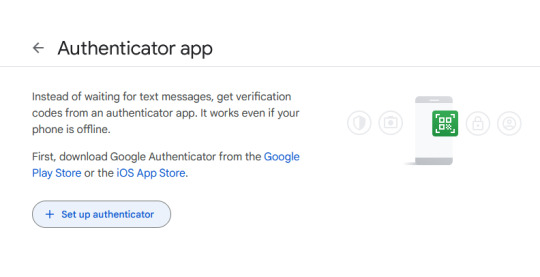
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
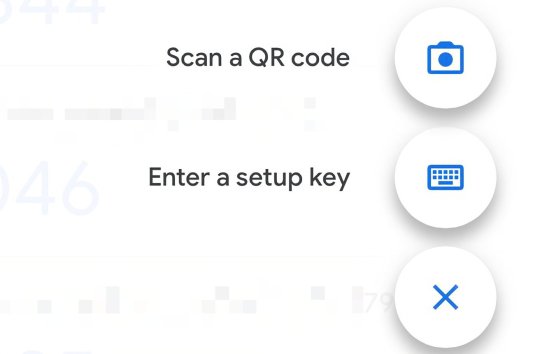
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
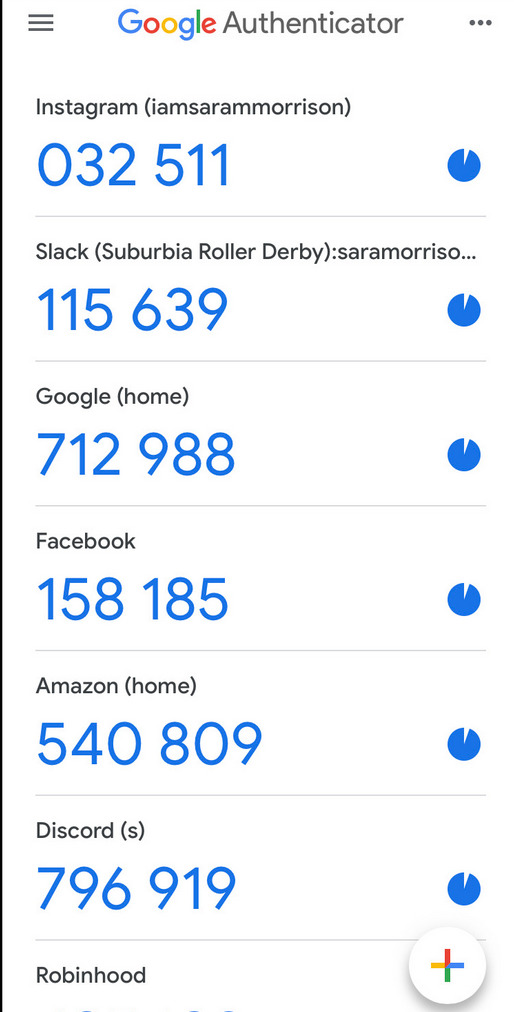
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
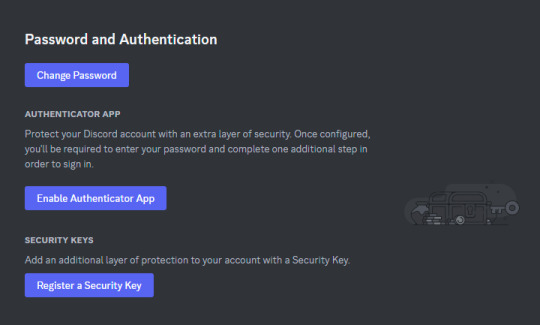
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
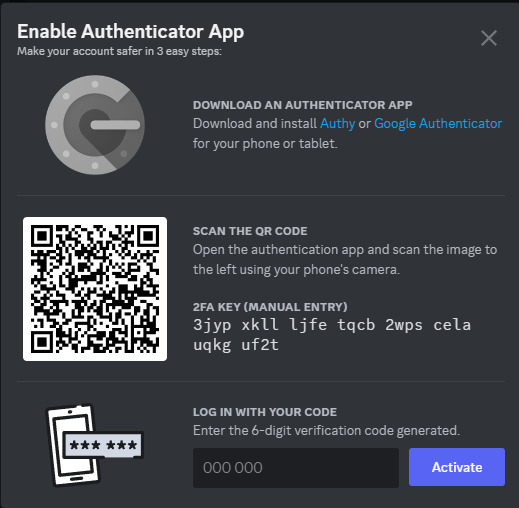
Download Google Authenticator if you haven't already. Scan the QR code as described above.
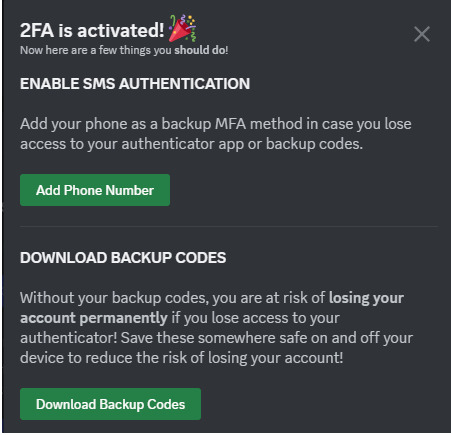
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Note
1. Tubbo confirm himself in the clip that he only kissed her, to which she later confirmed it too. As pre the video
Tubbo made the video and She would confirm it AFTER the hacker had allegedly made the post.
Let me help you, hacker did their job -> Tubbo made the video -> She confirmed it. Then how did the hacker make such a lucky guess about what happened that night in Tubbo's house?
I didn't have to go past the first point for it. Didn't even use my two degrees on Physics. Can't believe what they are feeding these IT students these days ....
"HoW dId The HaCkEr MaKe SuCh A LuCky GuEsS?"
THE VIDEO IN QUESTION WAS FILMED WAS FILMED A YEAR AGO OF HIM AT A PARTY WITH HER, AND ALL HER FRIENDS AS THEY DRANK
youtube
My goodness it would take a genius to be like "Hey I'm making allegations that they both got drunk (as shown in he video from a year ago) and Tubbo S/A her while drunk"
To which they allegations never specified WHERE THEY WERE it only specified part they were at
So Tubbo, confused as fuck Tubbo, said they came to there place, kissed and then talked about Jazz
Them going back to Tubbo's place wasn't even in the original allegations
Bitch if I went to a party, got drunk, PUBLICLY POSTED ABOUT IT ONLINE, and then someone was like "(me) was harassed by xyz", I'D BE SO FUCKING DUMB BECAUSE THEIR EVIDENCE WOULD BE THE VIDEO FROM A YEAR AGO. WHY THE FUCK WOULD SOMEONE INCRIMINATE THEMSELVES
Now dear clear idiot. I shall explain how 2-step verification works and how it didn't work in this case. AhEm
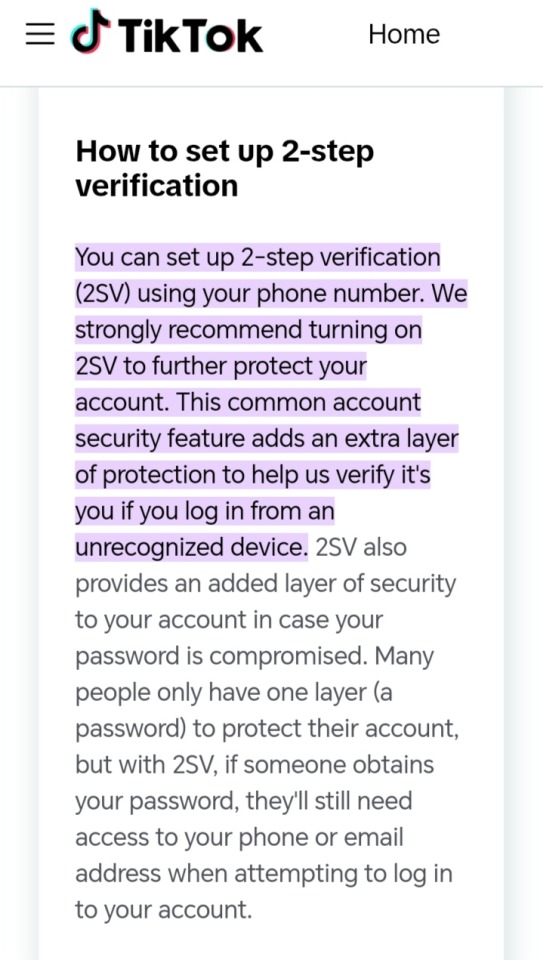
1. 2-Step Verification is as it sounds, in which after attempting to log on to a platform, the platform holders will either send a text message (through phone number) , email/gmail/AOL (if your old), notification or another form of communication to ensure the person login in is actually, ya know, you.
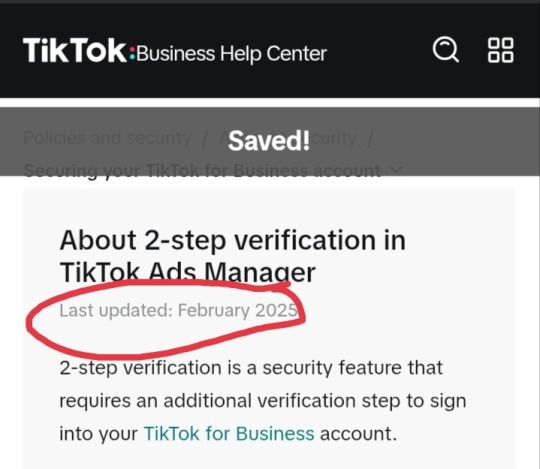
2. 2-Step Verification became a thing on TikTok, official and refined, on February 2025 (very late tbh)
3. Your young people don't know that back in my day TikTok didn't exist. OMG HOW COULD THIS BEEE??? Because it was called Musicly before it rebranded to tiktok
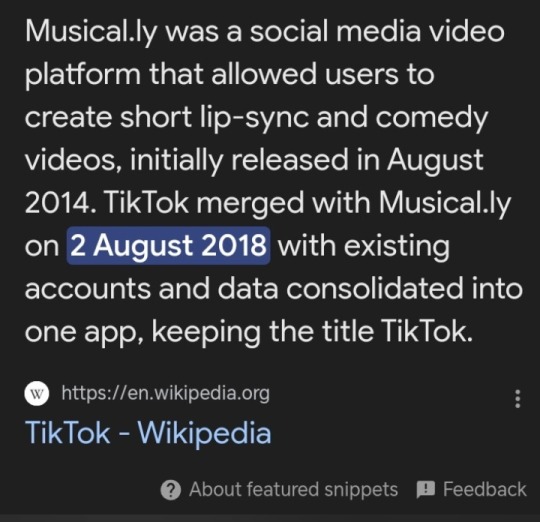
And since Musicly was primarily a kids/teens/young adults app, who tf is hacking a child's account?? Ya know?
So up until before that point Musicly also didn't have 2-Step Verification. Which is important because that means this security measures didn't transfer over because they didn't exist
4. Listen Leandra is by no means old. But I will rest a hand on your shoulders when I say, Gmail was created in 2004

And if you were a kid/teen around that time, you were young enough to get a Gmail with your actual name, like full legal, government, on yo birth certificate name
Why this important? Because if your primary Gmail/email/AOL, if your full legal name or part legal name, then people have a higher chance of just guess your email or, putting down "forgot password", then linking it to their email address, getting the rights to change the password and then bam.
The only way this cannot happen is if you manual lock your Gmail to only known devices (but fr that takes to long ngl and plus you won't be able to work on something if you can't access the device that has the rights to your email and additionally if you lose that device then it's game over, try again, pack it tf up)
So if she made her Tiktok account via any of the emails, then it's done, sorted, etc...
4.1. Now let's say she made it with her phone number like Tubbo suggested.
You could gain access further:
Having the email/gmail/AOL be linked with your phone number as a contact/emergency contact (idk in what case Google would hit you up but they can ig)
Phising. Look it up. It's spelt with a PH but pronounced fishing. And it's much more common then you think
The most popular phone plan providers in the UK are EE and Vodafone, inwhich if you get a new SIM card in a new phone, you can call them to change the new SIM phone number back to your older on as I'd be more convenient. The thing is, literally anyone could call. Like anyone, all you really need is the either the email/gmail/AOL, or the make and model of the phone, to answer some relatively personal questions (which you can lowkey guess ngl), or live in the same area or they just say screw it and change the number. It's often very useful but THE MOST ANNOYING THING when someone tries to access your account, and depending on WHEN and WHERE you get the card they don't even send you a confirmation text because they assumed your the one calling.
But anyways, you'd only need to realistically find out the first few numbers of her phone number, if you went with this method, trial and error'd it till you got on that's active and you can at minimum text, then just straight up try to login in or call them.
This is a great time to mentioned that Snapchat is lowkey, unintentionally screwing people over with this, because you can check if someone has a Snapchat by their contact or trying to sign in with that phone number cause it'll say the numbers is already in use.
BUT ANYWAYS, it takes about 2-6 weeks to gain access to someone's phone number or Gmail/AOL/Email if they're born pre-2000s to early 2000s
My point being, you could just guesstimate her really name by putting it through bots, checking old posts, being in personal contact with them or like reallllyyyyy putting the effort into guessing
And this is why people are often told to regularly update or change both passwords, email/gmail /AOL password and even update their names to avoid this.
5. Leandra made her social media around 2023, for her official Lovejoy shenanigans, idk what they do tbh
And I'm in no way calling her old... But she's gotta be like minimum 2-6 years older then me putting her in the bracket of people who can get a G/E/AOL (I'm getting tired of writing I tbh) with their actual names
And since 2-Step Verification was a 2025 update on TikTok, it's likely that some people just don't have it because they're too lazy to update or set it up. But even then their are many ways to get around it.
I recommend looking at the BBC guide/explanation of multi-factor verification/ two step verification/ multi-factor verification: https://www.bbc.co.uk/programmes/articles/5VbNf6z14LS7bZ02L1NXcjG/how-to-set-up-two-factor-authentication
And to Look at this BBC bitesize link if you want to know more: https://www.bbc.co.uk/bitesize/guides/zf3bcj6/revision/6
And 6. To follow up on some misconception that I know you're probably gonna throw at me because let's be real here you just hate Tubbo and that's okay. You don't need to justify it, just dislike him and be done.
Misconception 1. For some reason people are saying that her Instagram and Snapchat were also hacked. I don't know if she has a Snapchat because I don't use it, but as for Instagram it has been confirm by many update accounts, people who know irl etc... That the insta is fine!
Misconception 2. Tubbo kissed her. Hahahahhahashhsshshslolklolol. Tubbo is gay, and it's been confirmed by both parties that she kissed him first, and apparently he freaked tf out. Because he's gay. And has been openly gay for like 1-3 years. Bit weird to call him not gay for getting a kiss from one women. Like girl do you not kiss your mom? Tf? No kissing the homies? Terrible friend you are.
Misconception 3. Tubbo cleared the allegations as well as her after the allegations were out... Because how tf are you meant to clear something that's didn't exist?
Misconception 4. The hacker got a lucky guess. Now. Stay with me here. Go find an AI prompter and type 'man and women get drunk at part, write something criminal' OR just use your imagination because you know they're at the same party from a video a year ago. And I literally peeped into my older siblings room and asked them "real talk, a man and women get drunk at a party and leave together, they get to his place and something criminal happens, what is that criminal thing?" LITERALLY the first thing they suggested. Murder was second and tax evasion strats were 3rd.
And finally 7. This is too you. Yeah anonymous asker. You.
Just like DM me because as funny as it is to post about this on twitter and laugh with moots, your cluttering up my page with unnecessary discourse. But your not gonna see this, are you?
Because you, yourself said you didn't read past my first previous point. Sooooooooooooooooooooo
But also also ALSO, if she's confirmed it didn't happen and he confirmed it didn't happen, and she confirmed she was hacked, as shown in screenshots above and previously, then why is this still a talking issue?
SHE LITERALLY SAID SHE WAS HACKED. IT WASN'T HER POSTING??
Like if you gonna be mad at Tubbo be mad that he's idk fight Sapnap or something
But you seem more upset that I'm suggesting the hacker could POTENTIALLY be a gnf fan or Wilbur fan by the way they're uproaring on Twitter. Need I remind you, humbly and respectfully, IT'S FUCKING TWITTER??!
I keep people on the loop, I ain't asking for your what ifs ngl. questions? Welcome. Petty insults and challenge stupidity? Nope.
As you can see with MUCH of my covering discourse and discussion content on both Twitter and Tumblr, I put allegedly on thing that are not 90% to 100% accurate, I stick it on rumours and provide both links and screenshot to back up point because I want to be as honest as possible.
Bro if my favourite mcyt was an asshole I'd hold them too it. If my favourite vtuber was a bitch I'd hold them too it.
But I've provided ample evidence both in my first post and this post with detailed explanation, links and breaking it down into sections, I EVEN LINKED EDUCATIONAL RESOURCES AND EXPLAINED EMAIL LORE AND WHY MILLENNIALS ARE ACTUALLY QUITE OLD
Like it's done. It's over. You ignorance, lack of real world perception, common sense, and critical thinking skills has lead you to a pre-made conclusion that please you and not the actual one. So congrats. Wish I could be that stupid.
And for the record, I got a 100% in both GCSE coursework units on Information Technology, covering a range of different topics including cyber security, and scored a 90% on the test (trust it hurts your hand writing that much)
Furthermore, I backed it up with links, educational links and screenshots reinforcing literally what I said/how it applies.
Don't doubt my intelligence. Doubt your own suckerrrr
2 notes
·
View notes
Text

If you lost access to your email tomorrow, what would you do?
Once upon a time, I used to think Gmail was fine for a business. It was free, easy, and setting up something more professional felt like a hassle. But I’ve seen firsthand what happens when that gamble doesn’t pay off.
One day… BAM. Locked out. No warning. No explanation. Just “suspicious activity detected”, and suddenly, access was gone. Every client email? Vanished. Every invoice? Trapped. Google support? Useless. Hours spent trying to recover the account, only to hit a dead end.
And it’s not just one unlucky case, I’ve seen entire businesses crumble because they relied on a free email account. Once it’s gone, it’s gone.
Here’s why it’s a terrible idea:
Big Tech doesn’t owe you anything.
If Google/Microsoft/Yahoo decides your account looks “suspicious,” they can shut it down. No warning, no appeal, no customer service to help you. You’re just… locked out forever.
Hackers LOVE free email accounts.
Guess what’s super easy to hack? A free Gmail. Brute-force attacks, phishing scams, leaked passwords, it happens all the time. And once they’re in? They can scam your clients, change your payment info, and pretend to be you.
They scan your emails.
Yeah, Gmail reads your emails. They call it “advertising data” but if you’re discussing contracts, finances, or literally anything private, do you really want some algorithm combing through that?
It makes your business look cheap.
Would you hire a lawyer with [email protected]? Exactly. If you’re running a serious business, your email should look serious too.
What I wish I knew sooner:
✔️ The secure option: ProtonMail – encrypted, private, no data scanning.
✔️ The business option: Google Workspace / Microsoft 365 – same convenience, but with your own domain and actual security controls.
If you’re still using a free email, fix it before it’s too late.
Reach out if you have any questions!
2 notes
·
View notes
Text
Let me tell you how I just almost lost this account forever-
I went to check tumblr only to notice that it had forced logged me out on desktop. So I enter my email to log in...no dice. Then I think to myself "well it's probably my college email then, surprised I hadn't changed it over." No dice again. I then think to check on the mobile app what the email was. Bingo! It was my long dead middle school/high school era email. I tried that email and my password I had written down for tumblr...no dice Again. Now I start to panic. I start trying other passwords, nothing is working. Then Down From The Heavens Descend Into My Mind: the memory of my old universal password for everything when I was kid. Bingo, I'm back into tumblr. I have no earthly idea why I was using *that* password here or why it doesn't match my notes but whatever. Hacker voice, I'm in...
So I go to update the password to what I had written down so this doesn't happen again. I do this on the mobile app for Some Fucking Idiot Reason...and it doesn't ask me to input it a second time to make sure it's right...and then the app force logs me out.............and I try to log back in....I Fucking Mistyped The Password. I could literally start to feel my heart pumping and my ears get really warm with panic at the realization I might've just lost my decade+ old tumblr account because a basic password reset feature apparently doesn't exist on this site. I went to go report this issue to Tumblr Support and ask them to recover my account. However, I need to provide the email this account is attached to... and I don't have access to that, so support is just a worthless route...and then I realized going to submit a fucking support ticket logs you out. So now I was logged out on both app and desktop. Literally beside myself. Broken ass website, deadass wondering if anyone tests this place. I go to recover the email this account is attached to. Then gmail does me so dirty, it says to me "to recover this email, you need a security code sent to your elementary school era email." At this point, I'm ready to just cry. So I go to crack into that email and BECAUSE I HAD REMEMBERED MY OLD UNIVERSAL PASSWORD AND CUZ SHIT LIKE 2 FACTOR JUST WASN'T A THING WHEN I MADE THAT EMAIL, I GOT IN So then I had to fuckin' recover and reinstate the middle school email from my elementary school, recover my tumblr account and reset the password *again* (this time on desktop and not the fucking app) and make sure this account was set to my up to date email and just.....y'all, if my memory didn't just shit out my childhood universal password at me, I deadass would have lost this account forever. All because desktop just randomly decided to log me out. I hate social media.
35 notes
·
View notes
Note
Oh no I’m sorry your account got yoinked ;;
Im just going to go ahead and tell you that Discord Support is useless (my friends who got hacked gained little to no support in their situation).
If you left any credit card on your account FREEZE IT NOW.
Enable 2FA on any other account linked to your account as well. Who knows what the hacker might go for next
Okay the situation is under my control now. Thank you for your concern✨
Another Russian bot hack, just like last time my genshin acc got yoinked. My passwords were in chaos, my youtube was also messed up, and gmail too. My friends texted me through fb and told me my accs are sending them weird links...
Luckily I have friend and he know exactly what to do. Still the damages are irreversible, I got banned from several servers due to the spam links. *Sigh*
Be careful guys
17 notes
·
View notes
Video
youtube
16 billion passwords leaked worldwide after one of the largest Google data breaches in history! In 2025, hackers reportedly accessed massive databases containing login credentials, Google account passwords, Gmail logins, Google Drive files, and private user data. Cybersecurity experts are calling this Google password leak a global identity theft disaster.If you have a Google account, your sensitive information may already be exposed on dark web marketplaces. In this video we explain exactly what happened, who is affected, how hackers obtained the data, and what you can do right now to protect your Google account, passwords, and personal data from being hijacked.
0 notes
Text
Passwords hashing is used to secure passwords. Hashing is a common technique across various software and tools. Hashing is used as a security mechanism for preventing plain text information known to others. It's mathematically impossible to calculate a plain text for Hash since hashing is a one-way process. Still, there are different ways exist that can crack the hash and retrieve your password or other sensitive information that may have been hashed. Hashing technique is mostly applicable to protect password like information since its a one-way process. You may also want to check out - how to learn hacking and cracking. This is a simple tutorial that will explain how hash cracking works. Why Password Hashing Is Considered Secure Hashing is a one-way process. This guarantees that the hash of a plain text value can be generated however the process can not be reversed. Most software and websites use this way to store password since the user knows the password. Whenever they need to authenticate the user, they generate the hash of user input and match it with a stored password. This mechanism guarantees that even the software provider themselves do not know your password. However, there are hacking and cracking tools as well as other techniques described below that may be able to find out your password from a hash. Today we will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: What is a Hash? What is the need for a Hash? Why Hash over Encryption or Encoding? Hardware configuration Tools required Hash cracking [CPU] Hash cracking [GPU] Hash cracking using Search engine Why such a difference? What Is A Hash? A. A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert. see Wikipedia What Is The Need Of A Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company. For example, You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay, etc) or even Wi-Fi. Checking for the file verification. see SHA1 here Even If a company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use a strong password) Why Hash Over Encryption And Encoding? Imagine a scenario, which perhaps happens to almost every Big banner, take it Google, Facebook, Yahoo! etc. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that if you are a registered user on that site? Yes! your Password (might be the master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. How? well, you might be familiar with these terms: Encoding/Decoding Encrypt/Decrypt and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. and that is : Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash, unlike Encryption/Encoding, is a One-way process i.e when a text/file goes through the Cryptographic hash function, it is converted into a fixed character length. Example: md5 type hash has a character length of 32, where SHA1 has a character length of 40. If we hash a string, say “test123″, md5 and SHA1 hash for “test123″ will be md5(“test123″) : CC03E747A6AFBBCBF8BE7668ACFEBEE5 SHA1(“test123″) : 7288EDD0FC3FFCBE93A0CF06E3568E28521687BC Length differs from md2, md4 to SHA256, SHA512 and so on.
Hashing your Wi-Fi password is also secured using a hash function named PBKDF2(Password-Based Key Derivation Function) Hardware Configuration Hardware used in this tutorial: Laptop with 4 GB RAM Nvidia Graphic card 1 GB Tools Required Software used in this tutorial: Windows 8, 32-bit Cain & Abel (CPU based cracker). igHashGPU (GPU based cracker), download here Nvidia graphics driver, for igHashGPU, download here Hash Cracking [CPU] Cain & abel is a multi-purpose tool. It is used for various purpose like Sniffing Hash calculating Hash recovery(this tutorial) ARP spoofing WiFi hacking, using hardware called AirPcap and so on. We will take MD5(Message Digest 5) cracking as an example to keep it simple and easy to understand. Install Cain & abel, then follow the instruction along, step-by-step: Open Cain & abel Press Alt+C to open the Hash calculator Type in “test123” and hit [ENTER], here “test123″ is our test string You should see something similar, Here we got the MD5, and other Hash for string “test123″ i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5. select and copy the MD5 hash.
NOTE: Hashing is Case sensitive, Hash for “Test123” will be absolutely different. Click on Cracker tab, then select MD5 Hashes column in the left. then right click and select Add to list. Paste the copied MD5 hash and hit [ENTER] Now, Hash is added to list. Right click on hash and select Brute-Force attack Set max length to 7 and click Start, and you should see this
. Here I have set the Max length of the password to be 7 to just test the output of the tool, and cracking speed of the CPU.
See the Password/Second CPU is testing: 6.3M (approx) and the remaining time i.e total time which will take CPU to recover the original string is 3.5 hours. It is too lame to wait for 3.5 hours for a small string test123 of the length of 7 characters with no special characters. isn’t it? well, here comes the GPU cracking to put some speed in the process! Hash Cracking [GPU] igHashGPU is a password recovery tool specialized for ATI (RV) and nVidia (Cuda) based cards. It recovers password of hashes which are used over the internet(weak), example md4/md5/SHA1. Let's get started, We have the MD5 string for test123 i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 Follow the instructions along, step-by-step: Download and extract igHashGPU. Go to folder Right click and edit the file “example.cmd“. It is the example file for testing GPU speed of recovering MD5 password. Paste the MD5 code in the file after h:
and it should look like this :
ighashgpu.exe /h:CC03E747A6AFBBCBF8BE7668ACFEBEE5 /t:md5 /c:sd /min:4 /max:7 Close file. Click save and yes. Select “Example.cmd” and hit [ENTER]. A command prompt window will open like this
. See the CURSPD(Current speed), ~50 Million. Nice! but not good, isn’t it? see the battery symbol in the lower right corner. The laptop is running on battery. See what happens when I plug in the charger, notice the clock and speed. WHOA! See the difference! from 50M to 195M passwords/second, isn’t it great ? from 6.3M pass/sec to 195M pass/sec. That’s a big Jump. What you think how long it would have taken to recover the Password ? Just 5 minutes and 53 seconds. See how much time we saved by using GPU. From 3+ hrs to just 5 minutes. isn’t it amazing? also see the average speed also, 62,847 Million passwords/second. CPU: ~3 hrs with 6M pass/sec
GPU: ~6 min with 195M pass/sec You might ask, Hey! can we crack this even faster? well, the answer is Yes you can(not always though). How? Hash Cracking Using Search Engine [Google] We had MD5 string copied, right? what you need to do is very simple. Just paste and search the MD5 string i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 on Google. and you’re done! Notice the text string “test123” and the Hash. So simple to recover the string from MD5, no? Now see the time above, it took us to recover the original string. Just 0.31 seconds. not even a second. Wow! that’s great.
You might be thinking why such a difference? here’s the answer Why Such A Difference? The difference in the speed is due to the architecture of the 3. CPU: Uses 4 cores(Shared with system processes) at maximum, 8-cores in some cases. GPU: Used 96 cores (In this case). All the 96 cores(Parallel processing units) were 100% dedicated for the password recovery process unlike CPU, which was simultaneously handling the complete OS including background processes, GUI(mapping of pixels on screen), and many other processes. Even if the CPU stop handling those, then also it won’t match GPU’s performance. difference because of the #of cores i.e 96 vs. 4 or 8 Latest GPU’s that I have seen comes with more than 400 cores. It can take you more than a billion passwords/second to recover the MD5 hashed string. Google Don’t Crack The Hash. Yes!, Google doesn’t crack/recover the string. It sends a request for the specific Text input i.e the hash in our case, to all the servers, takes the response back and displays the result according to the page rank of the site. There are plenty of online crackers, which can be used to crack a variety of hashes. They search their Database for the hash you have entered. If the string of hash is already recovered by them, they will give it to you, else you have to pay to avail the service. An email is sent if the string has been recovered. So, what Google does is sending a request to all these servers and displaying you the result. Result of the hash already cracked. It certainly becomes the Top priority for hash cracking. Search google first, if you didn’t find the password, go for GPU cracking.
Still didn’t succeed? Try CloudCraker, crackStation, HashKiller You can google “Online hash cracker” for more results. Note: Cracking speed varies depending on factors like: GPU configuration, ATI graphics cards are the best for this task. Hash type, for SHA1 it will be even lesser and for WPA hash cracking it goes down to 4000 Pass/sec on my graphics card. see this list. My card’s performance is near to GeForce 8800 GTS (CUDA) Interested in WPA cracking, or WiFi pentesting? Follow my WiFi Security and Pentesting Series Hope you found this tutorial helpful. Let me know in the comment section. Thanks! This article is contributed by Hardeep Singh (Facebook | Twitter). Hardeep is a guest author and Full-time Blogger @ rootsh3ll.com, Security person, Penetration, tester, Linux and python Lover. Loves to share knowledge with everyone. Updated On June 2019: Fixed Broken links and updated minor typos.
0 notes
Text
“Password1234”: Tulsi Gabbard’s Login

“Password1234”: How Tulsi Gabbard’s Login Habits Nearly Triggered a Hawaiian Missile Crisis 2.0
The National Security Threat of Reusing Your Ex-Boyfriend’s Name As a Password When “Aloha” Meets “Access Denied” In a shocking exposé that shook no one except the IT guy named Carl, The Daily Beast revealed that Tulsi Gabbard—a congresswoman, veteran, spiritual warrior, and occasional surfer—had apparently been using passwords that could be cracked by a caffeinated squirrel with an iPhone 4. According to leaked reports, her online security strategy was a combination of horoscope advice, yoga poses, and pure vibes. And yet, somehow, the nation remained standing. So we ask the vital question: What happens when the nuclear codes are one password reset question away from “What was your first pet’s name?” “She thought two-factor authentication meant having a backup horoscope.” — Ron White Let’s dive into the browser history of this satirical scandal.
“Tulsi2020!” Isn’t Just a Campaign Slogan, It’s Also Her Netflix Password
Gabbard’s Surfboard Contains More Encryption Than Her Laptop Tulsi Gabbard ran for president in 2020. Apparently, she also ran out of original password ideas in the same year. According to a cybersecurity leak no one asked for, Gabbard used “Tulsi2020!” across at least seven platforms—including MyFitnessPal, Dropbox, LinkedIn, and a suspicious site called “WarriorMonkDating.com.” What’s worse? She added the exclamation point thinking it was military-grade encryption. “It’s like putting a sticker over a webcam and calling it cybersecurity,” said retired NSA analyst and part-time laser tag champion Ron Skelton.
The Yoga of Password Management: Sun Salutations and Synced Devices
Sources close to Gabbard say she once attended a cybersecurity retreat in Maui, where instead of encryption, participants were taught to breathe deeply while entering their debit card numbers into public Wi-Fi. She later described it as “a transformative experience where I learned to align my chakras and my bank logins.” One witness described Gabbard’s “password flow” routine: First, she logs in with “namaste123” Then does downward dog while waiting for two-factor authentication And finally logs out by whispering “Aloha” to the server
The Cybercrime Wave: Russian Hackers, Meet “Password1234”
By 2017, her accounts were part of a larger leak that included over 3 billion records. Her contribution to this vast archive of human carelessness? Password: Tulsi123 Backup Password: Password1234 Security Question: “What’s your favorite color?” Answer: “YES” “It’s the cybersecurity equivalent of leaving your keys in your car with a note that says ‘Steal me, but with love,’” explained digital security expert Cliff “BitByte” Hernandez.
Gmail, Glam, and Glitches: Tulsi’s Digital Footprint is Wearing Flip-Flops
Among the compromised accounts was her Gmail, which—according to leaked metadata—was 70% promotional emails, 20% requests to appear on obscure podcasts, and 10% fan mail written entirely in binary. One intern who sorted through the compromised messages said: “There were multiple drafts of her resignation letter, all saved as ‘resignation_final_FINAL_FOR_REAL.docx’”
Exclusive: Her Two-Factor Authentication Was a Friendship Bracelet
Tech insiders were horrified to discover Tulsi’s idea of 2FA wasn’t a confirmation code—it was “texting her cousin Jaya to see if it was really her logging in.” On multiple occasions, hackers were stopped not by firewalls but by confusion when Jaya replied, “Is this for the yoga class or the kombucha group chat?” “Her defense strategy relied heavily on poor communication,” one cybersecurity consultant laughed while installing malware protection for his mom.
Even Her iCloud Had a Tan
A trove of iCloud data included: 400 nearly identical selfies from the Senate gym A playlist titled “Legislative Bangers” Several videos of her dog doing warrior poses next to a salt lamp According to unverified rumors, a hacker group named “404Bros” tried to ransom the data, but after seeing the contents, sent a formal apology and a $15 iTunes gift card.
LinkedIn Recommendations Written by... Herself
One of the strangest discoveries in the leak? Tulsi had endorsed herself on LinkedIn for: Strategic Visioning Yogic Thought Leadership Military Telepathy Surf Diplomacy “That’s not even a real thing,” said career coach Sheila Plonk.“But I’d still hire her for the vibe.”
Ancestral Passwords and a Trail of Spiritual Cookies
Insiders say Gabbard once consulted her past-life regression therapist for password inspiration. She emerged from the session convinced her soul password was “CleopatraLives9.” She later told “Stars & Data Protection Weekly”:“We must be as secure in our online lives as we are in our truth. Unless Mercury is in retrograde, then all bets are off.”
“Don’t Blame Me, I’m a Vet” Becomes New Security Phrase
Tulsi’s go-to deflection when asked about her weak passwords?“I served this country, dammit. Let me have one unencrypted yoga blog.” Critics note this is the digital equivalent of a politician speeding through a red light and shouting, “I was in ‘The Amazing Race: Congress Edition’—I know what I’m doing.”
Eye Witness Account: Hacker Testimony from His Mom’s Basement
One teenage hacker who cracked her Dropbox said: “Honestly, I was trying to hack Roblox. But when I typed ‘Tulsi’ and ‘123,’ I accidentally got her Whole Foods receipts and a bunch of PDFs labeled ‘The Real Truth.’” He has since retired and now teaches online safety at a community center in Delaware.
The FBI’s Official Response: “We’re Too Tired for This”
An internal memo from the Bureau reportedly read: “We spent three weeks untangling this woman’s security habits. At one point, she used a Haiku as her encryption key.” Her defense?“Syllables are the safest language.”
Political Repercussions: Senators Now Forced to Change “Obama2024” to “Obama2025?”
Following the leak, Congress issued new password requirements: No campaign slogans No personal affirmations No references to enlightenment As one Republican aide lamented:“Guess I’ll have to change ‘ReaganLives’ to ‘TaxCutz4Life!’”
What the Funny People Are Saying
“Tulsi's passwords were so bad, even her spirit animal logged out.”— Sarah Silverman “Hackers were like, ‘We don’t want her emails. We just want her to stop using ‘Namaste69.’”— Dave Chappelle “Her Dropbox was 90% surfboard selfies and 10% blurry screenshots of UFOs.”— Trevor Noah “I haven’t seen this many security holes since my grandma’s knitting project.”— Jerry Seinfeld “At this point, she’s just daring China to log in.”— Chris Rock
Her Yoga App is Still Logged In on Eight Public Devices
Eyewitnesses at a Honolulu smoothie bar confirmed they could still access Tulsi’s meditation schedule, her list of mantras, and a half-written memoir titled “Shiva, Surfing & Senate Committees.” “She’s logged in on the juicer,” one barista sighed.“We know when she’s late to Pilates. The blender just starts chanting.”
Final Thoughts: It’s Not Just About Tulsi—It’s About Us
Let’s not throw our encryption stones from glass iPhones. Who among us hasn’t: Reused a password from 8th grade? Used their dog’s name and added “123”? Logged into Wi-Fi named “FBI Surveillance Van”? Tulsi’s mistakes are a national metaphor: We all want to be free spirits until someone hacks our Hulu queue.
Public Opinion Poll: What Do Voters Think?
Conducted by Spintaxi Institute for Hilarious Policy Studies“Which of the following would make a stronger password than Tulsi’s current one?” “MyExSucks42” – 37% “!@$%&” – 22% “IamTheRealPOTUS” – 18% “Password1234ButWithVibes” – 13% “HunterBidenLaptop2025” – 10%
Actionable Advice: From SpinTaxi’s Chief Tech Guru, Bleepy VonFirewall
1. Never reuse passwords. Even if they contain the word “chakra.”2. Don’t rely on your cousin for 2FA unless she’s a Navy SEAL or works at Apple.3. Your ex’s nickname is not secure just because you added a symbol.4. Enlightenment is not a firewall.5. If your password is a pun, you’ve already been hacked.
Conclusion: What Have We Learned?
We’ve learned that no matter how confident, intelligent, or mystically inclined you are, the moment you type “Tulsi2020!” into seven websites, you are officially the cybersecurity version of wearing socks with sandals. But in a world where digital threats grow daily, Tulsi’s spiritual approach to password management is a gentle reminder:The only thing worse than hackers… is hubris. And now, if you’ll excuse us, we have to go change our Netflix login from “SpinTaxiRocks69.”
Satirical Sources:
Senator Accidentally Uses Dog’s Name as Nuclear CodeCongressional Cybersecurity Training Now Includes Deep Breathing and Essential OilsHackers Demand Tulsi Return Their Time After Reading Her EmailsNational Security Council Adds “Vibes Check” to Daily Threat ReportsTulsi Gabbard Named Honorary IT Disaster of the Month by the Geek Squad Auf Wiedersehen! Want the VPN password? Ask Tulsi—it’s probably still “Mahalo123.”

SpinTaxi Magazine - A wide-aspect Toni Bohiney-style cartoon in the spirit of Mad Magazine, fold-in style. The scene shows Tulsi Gabbard sitting on a yoga mat in a tropical ... spintaxi.com
Tulsi Gabbard Named Honorary IT Disaster of the Month by the Geek Squad
Here are 15 observations inspired by the recent revelations about Tulsi Gabbard's password habits: Password123? Even my grandma knows better. Reusing passwords is like using the same key for your house, car, and office—convenient until it's not. 'Shraddha' as a password? Might as well have used 'OpenSesame'. MyFitnessPal account hacked? Guess someone wanted to know her calorie intake. Fox News Dropbox breach? Hope there weren't any dance videos in there.The Daily Beast LinkedIn compromised? Now everyone knows she endorsed herself. Using the same password since 2012? That's commitment—or laziness. No evidence of government accounts being compromised. Phew! National secrets are safe... for now. Signal group chat leak? Maybe it's time to switch to smoke signals. HauteLook account hacked? Someone's getting fashion tips on the sly. Gmail breach? Hope those cat memes weren't classified.The Daily Beast Reusing passwords is a no-no. Even toddlers have unique passcodes for their iPads. Cybersecurity 101: Don't do what Tulsi did. Seriously. Википедия — свободная энциклопедия At least she didn't write her password on a sticky note... or did she? We may never know. Lesson learned: Always use two-factor authentication. Or better yet, three. For more details on this story, you can read the full article here: Tulsi Gabbard's 'Easily Cracked' Password Habits Revealed. Read the full article
0 notes
Text
How to Organize Confidential Emails Without Compromising Security
In today’s digital world, managing confidential emails securely is crucial for businesses and individuals alike. Mishandling sensitive information can lead to data breaches, phishing attacks, or compliance issues. However, with the right email management tools and best practices, you can keep your inbox organized while ensuring top-notch security. Here’s how:
1. Use Secure Email Management Tools
Investing in reliable email management tools is the first step to protecting confidential emails. These tools help categorize emails, encrypt sensitive data, and prevent unauthorized access. Look for tools that offer end-to-end encryption, spam filtering, and AI-based threat detection to enhance security.
2. Categorize and Label Sensitive Emails
A well-organized inbox ensures easy retrieval of important emails without risking exposure. Use folders and labels to categorize emails based on their sensitivity. Many email management tools allow automated tagging, which helps in streamlining confidential correspondence efficiently.
3. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security with 2FA ensures that only authorized users can access your emails. Whether you’re using Gmail, Outlook, or a dedicated business email service, enabling 2FA significantly reduces the risk of unauthorized access.
4. Encrypt Emails for Enhanced Security
Encryption is key when dealing with confidential information. Use tools that offer built-in encryption or integrate third-party services to protect sensitive data. Many email management tools come with encryption features that prevent unauthorized users from intercepting your messages.
5. Avoid Public Wi-Fi for Accessing Confidential Emails
Accessing sensitive emails on unsecured networks increases the risk of cyber threats. If you must check your email on the go, use a VPN to create a secure connection and protect your data from potential hackers.
6. Regularly Audit and Delete Unnecessary Emails
Leaving confidential emails in your inbox indefinitely increases the risk of exposure. Set a routine to archive or delete emails that are no longer needed. Many email management tools offer automatic cleanup features that help in decluttering while maintaining security.
7. Train Employees on Email Security Best Practices
For businesses, human error is one of the leading causes of data breaches. Conduct regular training sessions to educate employees about phishing scams, strong password policies, and the importance of securing sensitive emails.
8. Backup Emails Securely
Regular backups help prevent data loss in case of cyberattacks or accidental deletions. Use cloud-based solutions that provide encrypted backups to ensure your confidential emails are protected at all times.
Conclusion
Organizing confidential emails without compromising security is all about adopting the right tools and best practices. By using email management tools, implementing encryption, and training employees on email security, you can safeguard sensitive information while maintaining an efficient workflow.
About Simplify360
Simplify360 is a leading AI-powered customer experience platform that helps businesses manage their emails, social media, and customer interactions seamlessly. With its secure and intuitive solutions, Simplify360 ensures efficient email management, helping organizations maintain data privacy and compliance effortlessly.
To know more about Simplify360,
Visit website: https://www.simplify360.com/ Address: 91springboard, 7th floor, Trifecta Adatto, 21, ITPL Main Rd, Garudachar Palya, Mahadevapura, Bengaluru, Karnataka 560048 Email: [email protected]
0 notes
Text
PROFESYONEL KİRALIK HACKER HİZMETLERİ
🎨Cihaz erişimleri - Galeri den video ve fotoğraf silme işlemleri
📍Konum tespiti - Konum takibi programları
🗒Whatsapp yazışmalar - WhatsApp silinen mesajları geri getirme
🔓Gmail şifre kırma işlemleri - hesap sms onay doğrulama hizmeti
🖥Ekran pin şifresi - Windows / Android / IOS
📂Harddisk / Hafıza kartı erişim ve data silme işlemleri
🛡Güvenlik kamera kayıtları ve erişim paneli
⚙️Websitesi kapatma / Hesap kapatma / Eposta kapatma işlemleri
📲Telefon erişim programı - Whatsapp erişim programı
📃Sosyal medya hesap takip hizmetleri - Yazışmaları dökme







⚠️Oyun hilesi bulunmamaktadır ve tüm işlemlerimiz 🔞+18 dir. Her sorumluluk sahibi vasfı taşıyan kişi ve kurumlara hizmet vermekteyiz.
📨Whatsapp ile iletişime geçiniz lütfen : +905465920064
#hackerkiralama #profesyonel #takip #programları #whatsapp #instagram #twitter #facebook #account #hacking #hirehacker #cracker #password #ddos #hacking #anonimous #cyber #phthon #mobil #windows #androidhack #ios #screen #computer #telephone
#hacker arıyorum#güvenilir hacker arıyorum#güvenilir kiralık hacker sitesi#güvenilir kiralık hacker arıyorum#instagram hack fiyat#hackerkiralama#hacker bulma sitesi
0 notes
Text
Hackers Are Using Google To Steal Microsoft Passwords
Google is being used to attack Microsoft passwords. SOPA Images/LightRocket via Getty Images There are myriad ways to steal passwords. From sophisticated AI-driven attacks against Gmail users, to invisible hacking threats, and fake CAPTCHA tests. What you might not expect, however, is a hacker to deploy Google against Microsoft users in order to access account passwords. But when it comes to…
0 notes
Text
How to Create a Comprehensive Estate Plan That Covers Digital Assets in Bradenton, FL

Who would access your online accounts, financial data, or treasured family photos stored in the cloud in the event you passed away? Without proper planning, your loved ones may face confusion and legal hurdles while trying to manage your digital legacy. As technology evolves, so does the need to include digital assets in estate planning. Your personal information, financial records, and cherished memories hold significant value, making it crucial to secure them within your estate plan.
In this guide, we'll walk Bradenton residents through the essential steps to ensure their digital assets are properly managed and protected.
What Are Digital Assets? A Complete Overview
Digital assets refer to any electronic records you own or control online, ranging from financial data to personal content stored in the cloud. These assets can hold both monetary and sentimental value, making them a critical part of your inheritance planning.
Common Types of Digital Assets
Here are some examples of digital asset management considerations for your estate plan:
Financial Accounts: Online banking, investment portfolios, cryptocurrency wallets like Bitcoin or Ethereum.
Social Media Profiles: Facebook, Instagram, LinkedIn, and Twitter are important for both personal and professional connections.
Email Accounts: Gmail, Outlook, and Yahoo, which often serve as gateways to other critical accounts.
Cloud Storage Services: Google Drive, Dropbox, and iCloud store documents, videos, and photos.
Online Subscriptions: Streaming services (Netflix, Spotify), software licenses, and memberships.
Domain Names & Websites: Valuable assets for business owners or personal branding.
Digital Media Collections: Purchased eBooks, music, and movies stored in online libraries.
Loyalty and Rewards Programs: Accumulated points from airlines, hotels, or retailers that hold financial value.
By incorporating these into your estate planning checklist for digital assets, you ensure your loved ones can access and manage them seamlessly after you're gone.
Why Ignoring Digital Assets in Estate Planning Is Risky
Failing to plan for digital assets can result in unnecessary stress and financial losses for your family. Without clear instructions, they might struggle to recover important information or risk losing valuable assets. Some risks include:
Loss of Access: Heirs may struggle to access online accounts or cryptocurrency wallets without passwords or legal permissions.
Emotional Impact: Losing cherished digital memories like photos or messages can be devastating for your loved ones.
Identity Theft: Unattended personal information can be targeted by hackers, leading to fraud or misuse.
Legal Complexities: Without proper documentation, digital assets may become entangled in lengthy probate processes.
Family Disputes: Inconsistent or missing instructions can lead to conflicts among heirs.
A Step-by-Step Guide to Protecting Your Digital Assets in Estate Planning
Bradenton residents can take proactive steps to secure their digital legacy by following this comprehensive approach:
Step 1: Create an Inventory of Your Digital Assets
Start by making a complete list of your digital assets, including:
Account names and website links
Login credentials (stored securely with password management tools)
Instructions on how you want each asset to be managed
Consider using secure storage solutions like LastPass or a fireproof safe to protect this information safely.
Step 2: Define Your Wishes for Each Digital Asset
Think about what should happen to each asset after your passing:
Should social media accounts be memorialized or deleted?
Do you want family members to inherit digital photos and videos?
Who should take control of business-related digital assets?
Documenting your preferences prevents misunderstandings and ensures your wishes are honored.
Step 3: Appoint a Digital Executor
A trustworthy executor is someone you designate to manage your digital estate. This role requires someone tech-savvy and responsible who can handle sensitive information securely.
They will be responsible for:
Closing accounts you no longer need
Transferring ownership of valuable assets
Ensuring sensitive information is protected
If you're wondering how to appoint a digital executor in estate planning, it's essential to choose someone who understands digital security and legal requirements.
Step 4: Include Digital Assets in Legal Documents
To ensure your digital assets are handled according to your wishes, incorporate them into your legal documents such as:
Your will – Specify beneficiaries and access instructions.
A trust – Offer additional control over assets.
A power of attorney – Appoint someone to manage accounts if you become incapacitated.
If you're looking for an estate planning attorney in Bradenton for digital assets, experts like Grivas Law Group P.A. can help you create legally binding documents tailored to your needs.
Step 5: Keep Your Plan Updated and Secure
Regularly review your estate plan to reflect changes in your digital assets, such as new accounts or passwords. Ensure your executor always has access to the latest version of your plan through secure storage options.
Why Work with a Bradenton Estate Planning Attorney?
Florida has adopted the Revised Uniform Fiduciary Access to Digital Assets Act (RUFADAA), which allows estate executors and trustees to access digital assets under specific conditions. However, without proper authorization, service providers may refuse access due to privacy policies and terms of service agreements.
If you're unsure about Florida laws on digital asset estate planning, it's important to consult an experienced attorney to ensure full legal compliance.
A qualified attorney can help:
Identify and organize your digital assets
Draft customized legal documents
Ensure compliance with Florida estate laws
If you're looking for professional guidance, consider consulting Grivas Law Group P.A., an estate planning firm with expertise in digital assets and Florida law.
Conclusion
Incorporating digital assets in estate planning is crucial to ensuring your online accounts and valuable digital property are protected and managed according to your wishes. Don't wait until it's too late—take the necessary steps today to secure your digital legacy.
If you're ready to get started, reach out to an estate planning attorney in Bradenton for digital assets for consultation and personalized guidance.
0 notes
Text
Google Warns Gmail Users: Stay Safe from Holiday Scams
As the holiday season approaches, scams are on the rise, and Google is warning Gmail users to be extra cautious. Cybercriminals are taking advantage of the festive spirit to launch new schemes designed to steal personal information and money. With an increase in online shopping and heightened holiday traffic, users are becoming prime targets for these deceptive attacks.

Common Holiday Scams Targeting Gmail Users
Google has identified several common scams that Gmail users should be on the lookout for during the holiday season. These scams often use tactics that appear legitimate but are meant to trick users into providing sensitive information, such as credit card details, passwords, or even full identities.
Fake Holiday Offers and Deals Scammers often create fake websites or emails claiming to offer incredible holiday discounts or deals. They may send out enticing offers, such as “50% off” or “Buy One Get One Free” promotions, urging users to click on links or provide payment details. These deals may look genuine, but they are designed to steal money or install malware on your device.
Phishing Emails Disguised as Holiday Greetings Phishing scams are one of the most common forms of online fraud. During the holiday season, scammers may send emails that appear to come from popular retailers or well-known brands, offering holiday greetings or exclusive deals. These emails often contain links that lead to fake websites designed to steal your personal information. Be cautious of unsolicited emails, especially those requesting sensitive details.
Gift Card Scams Another rising scam during the holiday season is the gift card scam, where fraudsters pose as friends, family, or even company representatives, asking you to purchase gift cards as a "favor" or for an urgent situation. Once you’ve purchased the cards, they are asked to be sent to the scammer, who can then quickly cash them in.
Fake Charity Donations The holiday season is also a time when many people are looking to give back. Scammers exploit this generosity by creating fake charities. They send out emails or social media ads urging people to donate to causes that sound noble but do not exist. These scams can easily trick well-meaning individuals into giving money that ends up in the hands of fraudsters.
How to Protect Yourself from Holiday Scams
Google has provided several tips to help Gmail users avoid falling victim to holiday scams:
Be Skeptical of Unsolicited Emails: If you receive an email offering a deal or promotion that seems too good to be true, verify the source before clicking on any links or providing any personal information.
Check the Email Address: Scammers often create fake email addresses that look similar to legitimate ones. Always double-check the sender's email address before engaging with the content.
Enable Two-Factor Authentication: Protect your Gmail account by enabling two-factor authentication (2FA). This adds an extra layer of security, making it harder for hackers to access your account even if they steal your password.
Use Strong, Unique Passwords: Ensure that your Gmail password is strong and unique. Avoid using easily guessable information like birthdates or common phrases.
Report Suspicious Emails: If you receive a suspicious email, report it immediately to Google. This helps protect others from falling victim to similar scams.
Stay Vigilant This Holiday Season
Google’s warning serves as a timely reminder that while the holiday season is a time for joy and celebration, it is also a prime opportunity for scammers to take advantage of unsuspecting users. By staying alert and cautious, you can protect yourself and your finances from these fraudulent schemes. Always trust your instincts, and remember, if something feels off, it probably is.
0 notes
Text
Forbes: Gmail Takeover Hack Attack—Google Warns You Have Just 7 Days To Act
0 notes