#history of web technology
Explore tagged Tumblr posts
Text
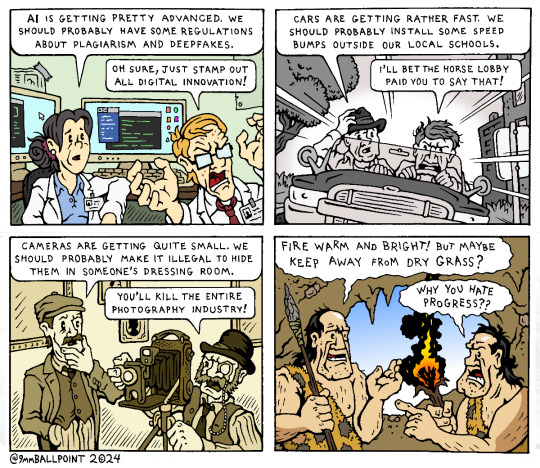
History of the Techbro
#political cartoon#capitalism#technology#ai is not art#computer#history#cars#photography#cameras#cavemen#prehistoric#web comics
450 notes
·
View notes
Text

(1970s) Mod II by AT&T / Bell Labs was the first picture phone to exist on the market. Not only did it connect phone to video, but users were able to share documents with each other !
#techcore#technology#vintage tech#computing#retrocomputing#old tech#retro tech#at&t#vintage phone#70s#tech history#computers#vintage telephone#old telephone#pngs#png#alt text#chrome#retro futurism#retro futuristic#old computers#digicore#webcore#old internet#early internet#2000s web#1970s#curators on tumblr#techinnovation#picture phone
84 notes
·
View notes
Text

Somewhat long, so list is below the divider!
https://ms-dos5.tumblr.com/ Computer photos, old 3d renders, old PC games.
https://chunkycomputers.tumblr.com/ Pictures of nice chunky computers.
https://wwwtxt.org/about An archive of online writings from the early days of the internet
https://arconinternet.tumblr.com/ Internet archive fun!
https://opendirectories.tumblr.com/ Image directories from around the web.
https://www.tumblr.com/oldguydoesstuff Old arcade machines and computers.
https://webcoreparadise.tumblr.com/ Old internet gifs, pixel arts, photos of old tech, etc
https://gaywebcorenostalgia.tumblr.com/ Old LGBTQ web sites.
https://geocitiesdig.tumblr.com/ Old website art and cool 90s CGI stuff.
https://56k-modem.online/ Photos and screenshots of old computers/operating systems/software.
https://oldwindowsicons.tumblr.com/ Collection of old Windows UI graphics.
https://oldwebsurfing.tumblr.com/ Art and gifs from old web sites.
https://obscuritory.tumblr.com/ Obscure old pc games.
https://www.tumblr.com/oneterabyteofkilobyteage Old Geocities Web Sites.
https://never-obsolete.tumblr.com/ Old tech ads, Operating systems, computer gifs.
https://wirlds.tumblr.com/tagged/worlds.com Worlds.com is an old online game form the 90s that, from the look of it, let people make their own little rooms. Quite nice looking!
https://whatdiditlooklike.mementoweb.org/ See the looks of web sites throughout the years.
https://www.tumblr.com/compactdiscinteractive Screenshots from old cd-rom and multimedia games.
#Krissies blog lists#lists#links#blogs#tumblr#tumblr lists#tumblr links#the blogosphere#computers#microsoft#windows#PC#mac#macintosh#linux#vintage computers#internet#internet history#world wide web#webcore#tech#technology#80s#90s#2000s#web sites#online games#online#geocities#pc games
106 notes
·
View notes
Text




Rainbow Wireless, 1997
#part 2#had to do an image only version#these are just too good#Rainbow Wireless#1997#old web#webcore#old web graphics#old technology#tech history#rainbow#y2k#y2kcore#web nostalgia
91 notes
·
View notes
Text

Famitsu 0571
#technology#tech#old tech#video games#console#internet archive#internet history#old internet#old web#90s#playstation#famitsu
8 notes
·
View notes
Text

It's my 2 year anniversary on Tumblr 🥳
#2 year tumblrversary#tumblr milestone#companies#brands#technology#cars#engineering#tech#old cars#history#innovation#old technology#Oldsmobile#ibm#motorola#thinkpad#gibson#buick#rover#transatlantic torque#brits and yanks on wheels#watches#gadgets#devices#laptops#old web#y2k#yahoo#aol#icq
4 notes
·
View notes
Text
idea for an app/website where people can record themselves telling stories about themselves and other family members so that the stories are never lost. maybe they can add pictures and videos to a sort of family timeline, and maybe other family members can comment on other people's stories with their versions/related stories (though i could see the comments thing becoming an issue lol)
this would be such a beautiful way to remember people who are gone and record their stories, since by the time you're old enough to want to ask it's often too late to hear them
#web design#web development#app ideas#web developing company#app store#family history#web developers#app design#web designing#designing apps#software design#software development#technology#tech#tech bros#tech girl#family stories#great idea#someone please make this
3 notes
·
View notes
Text
im such a dispassionate person. like im incapable of pursuing anything to completion or maintaining hobbies or delving deep into anything
#like yes i get brainrot for anime and shows n shit. i have a few interests. i do a bit of art a bit of writing#theres so much i wanna learn (like 3 languages linguistics old technology stuff eg dif methods of photography recording web stuff kickboxing#digital art video games birdwatching weightlifting woodwork medieval history coding metalwork poetry. to name a few things)#but i just lose interest and motivation so quickly im so lazy#i never do finished art pieces i have a billion unfinished animatics and plans and ideas i have like 20 unfinished fanfics#like ik i should be happy ive made anything at all but i just wanna be able to rly love something!#but its like. i hate watching ads i despise ads w every fibre of my being. but i cba to figure out how to make adblock work again on yt#so ive just been putting up w it. if i cant even do a simple task thst woudl take me 2 mins how am i going to do anything w my life ever.#not to mention even the easy stuff im bad at. the amount of half finished series unread books unwatched films...#its like what do i even do w my time. what do i have to share w the world what do i have to talk abt what do i have to contribute. nothing
5 notes
·
View notes
Text
The Making of an Underclass: AOL
The final factor was one of instinctive resentment of any hint of commercializing the Internet. Where traditionally, Internet users shared their resources for the public good, the perception was that AOL neither knew nor cared about net.traditions but was only interested in sticking a meter on a free resource and billing its users extortionately.
#article#AOL#wayback machine#internet history#tech history#technology history#technology#internet#the net#the world wide web
1 note
·
View note
Text

💥 Dynamite 8 Track Tape Player by Panasonic (1974) 💥 | Portable 8 track player with AM radio. Just push the "plunger" at the top to change the song!
#techcore#cybercore#1970s#webcore#panasonic#technology#old tech#vintage tech#tnt#old web#retro tech#70s#70s aesthetic#vaporwave#audiophile#retro#retro aesthetic#tech#electronics#tech history#digicore#retro computing#8 track#curators on tumblr#music players
119 notes
·
View notes
Text
Got some new books :)



They're all pretty old, but I'm still really happy :)
#technology#computers#programming#internet#world wide web#books#reading#internet history#autism#autistic#techposting#tech#computer science
0 notes
Text

PlayStation Magazine - 014 - Novembre 1997
#technology#tech#old tech#video games#console#internet archive#internet history#old internet#old web#90s#playstation#namco
8 notes
·
View notes
Text
Web Design Services for Veterinarians
People will often online when looking for a veterinarian to take their pet. Effective healthcare marketing for veterinarians requires meeting your potential clients where they are online with a veterinary website. A healthcare website for veterinarians can help you create an online presence and connect with pet parents looking for a vet. But with having to manage demanding clients and other operations of your vet practice, you can struggle to focus on marketing.
Know more Visit Us - Web Design Services for Veterinarians
Contact Us - 714-519-6290
Visit Us - Search Business Group
#Web Design Services#Web Design Services for Veterinarians#healthcare website#history#culture#dentist seo#movies#technology#art
0 notes
Text
Deenbandhu Chhotu Ram University of Science & Technology
www.dcrusm.org.in
Deenbandhu Chhotu Ram University of Science & Technology is a renowned institution known for its excellence in providing education and research opportunities in the field of science and technology. Located in Murthal, Haryana, it offers a wide range of courses and programs to students from diverse backgrounds. The university is committed to nurturing talent, fostering innovation, and promoting holistic development. With state-of-the-art facilities and a dedicated faculty, it strives to create a conducive learning environment for its students.
Web Site:- www.dcrusm.org.in
#Deenbandhu Chhotu Ram University of Science & Technology is a renowned institution located in the state of Haryana#India. Known for its excellence in the field of science and technology#the university has a rich history and impressive academic achievements. The university offers a wide range of undergraduate and postgraduat#ensuring that students have diverse options to choose from. With state-of-the-art facilities#experienced faculty#and a focus on practical learning#Deenbandhu Chhotu Ram University of Science & Technology provides students with an ideal environment to enhance their knowledge and skills.#Web Site:- www.dcrusm.org.in
0 notes
Text
How lock-in hurts design

Berliners: Otherland has added a second date (Jan 28) for my book-talk after the first one sold out - book now!

If you've ever read about design, you've probably encountered the idea of "paving the desire path." A "desire path" is an erosion path created by people departing from the official walkway and taking their own route. The story goes that smart campus planners don't fight the desire paths laid down by students; they pave them, formalizing the route that their constituents have voted for with their feet.
Desire paths aren't always great (Wikipedia notes that "desire paths sometimes cut through sensitive habitats and exclusion zones, threatening wildlife and park security"), but in the context of design, a desire path is a way that users communicate with designers, creating a feedback loop between those two groups. The designers make a product, the users use it in ways that surprise the designer, and the designer integrates all that into a new revision of the product.
This method is widely heralded as a means of "co-innovating" between users and companies. Designers who practice the method are lauded for their humility, their willingness to learn from their users. Tech history is strewn with examples of successful paved desire-paths.
Take John Deere. While today the company is notorious for its war on its customers (via its opposition to right to repair), Deere was once a leader in co-innovation, dispatching roving field engineers to visit farms and learn how farmers had modified their tractors. The best of these modifications would then be worked into the next round of tractor designs, in a virtuous cycle:
https://securityledger.com/2019/03/opinion-my-grandfathers-john-deere-would-support-our-right-to-repair/
But this pattern is even more pronounced in the digital world, because it's much easier to update a digital service than it is to update all the tractors in the field, especially if that service is cloud-based, meaning you can modify the back-end everyone is instantly updated. The most celebrated example of this co-creation is Twitter, whose users created a host of its core features.
Retweets, for example, were a user creation. Users who saw something they liked on the service would type "RT" and paste the text and the link into a new tweet composition window. Same for quote-tweets: users copied the URL for a tweet and pasted it in below their own commentary. Twitter designers observed this user innovation and formalized it, turning it into part of Twitter's core feature-set.
Companies are obsessed with discovering digital desire paths. They pay fortunes for analytics software to produce maps of how their users interact with their services, run focus groups, even embed sneaky screen-recording software into their web-pages:
https://www.wired.com/story/the-dark-side-of-replay-sessions-that-record-your-every-move-online/
This relentless surveillance of users is pursued in the name of making things better for them: let us spy on you and we'll figure out where your pain-points and friction are coming from, and remove those. We all win!
But this impulse is a world apart from the humility and respect implied by co-innovation. The constant, nonconsensual observation of users has more to do with controlling users than learning from them.
That is, after all, the ethos of modern technology: the more control a company can exert over its users ,the more value it can transfer from those users to its shareholders. That's the key to enshittification, the ubiquitous platform decay that has degraded virtually all the technology we use, making it worse every day:
https://pluralistic.net/2023/02/19/twiddler/
When you are seeking to control users, the desire paths they create are all too frequently a means to wrestling control back from you. Take advertising: every time a service makes its ads more obnoxious and invasive, it creates an incentive for its users to search for "how do I install an ad-blocker":
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
More than half of all web-users have installed ad-blockers. It's the largest consumer boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But zero app users have installed ad-blockers, because reverse-engineering an app requires that you bypass its encryption, triggering liability under Section 1201 of the Digital Millennium Copyright Act. This law provides for a $500,000 fine and a 5-year prison sentence for "circumvention" of access controls:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Beyond that, modifying an app creates liability under copyright, trademark, patent, trade secrets, noncompete, nondisclosure and so on. It's what Jay Freeman calls "felony contempt of business model":
https://locusmag.com/2020/09/cory-doctorow-ip/
This is why services are so horny to drive you to install their app rather using their websites: they are trying to get you to do something that, given your druthers, you would prefer not to do. They want to force you to exit through the gift shop, you want to carve a desire path straight to the parking lot. Apps let them mobilize the law to literally criminalize those desire paths.
An app is just a web-page wrapped in enough IP to make it a felony to block ads in it (or do anything else that wrestles value back from a company). Apps are web-pages where everything not forbidden is mandatory.
Seen in this light, an app is a way to wage war on desire paths, to abandon the cooperative model for co-innovation in favor of the adversarial model of user control and extraction.
Corporate apologists like to claim that the proliferation of apps proves that users like them. Neoliberal economists love the idea that business as usual represents a "revealed preference." This is an intellectually unserious tautology: "you do this, so you must like it":
https://boingboing.net/2024/01/22/hp-ceo-says-customers-are-a-bad-investment-unless-they-can-be-made-to-buy-companys-drm-ink-cartridges.html
Calling an action where no alternatives are permissible a "preference" or a "choice" is a cheap trick – especially when considered against the "preferences" that reveal themselves when a real choice is possible. Take commercial surveillance: when Apple gave Ios users a choice about being spied on – a one-click opt of of app-based surveillance – 96% of users choice no spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
But then Apple started spying on those very same users that had opted out of spying by Facebook and other Apple competitors:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Neoclassical economists aren't just obsessed with revealed preferences – they also love to bandy about the idea of "moral hazard": economic arrangements that tempt people to be dishonest. This is typically applied to the public ("consumers" in the contemptuous parlance of econospeak). But apps are pure moral hazard – for corporations. The ability to prohibit desire paths – and literally imprison rivals who help your users thwart those prohibitions – is too tempting for companies to resist.
The fact that the majority of web users block ads reveals a strong preference for not being spied on ("users just want relevant ads" is such an obvious lie that doesn't merit any serious discussion):
https://www.iccl.ie/news/82-of-the-irish-public-wants-big-techs-toxic-algorithms-switched-off/
Giant companies attained their scale by learning from their users, not by thwarting them. The person using technology always knows something about what they need to do and how they want to do it that the designers can never anticipate. This is especially true of people who are unlike those designers – people who live on the other side of the world, or the other side of the economic divide, or whose bodies don't work the way that the designers' bodies do:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
Apps – and other technologies that are locked down so their users can be locked in – are the height of technological arrogance. They embody a belief that users are to be told, not heard. If a user wants to do something that the designer didn't anticipate, that's the user's fault:
https://www.wired.com/2010/06/iphone-4-holding-it-wrong/
Corporate enthusiasm for prohibiting you from reconfiguring the tools you use to suit your needs is a declaration of the end of history. "Sure," John Deere execs say, "we once learned from farmers by observing how they modified their tractors. But today's farmers are so much stupider and we are so much smarter that we have nothing to learn from them anymore."
Spying on your users to control them is a poor substitute asking your users their permission to learn from them. Without technological self-determination, preferences can't be revealed. Without the right to seize the means of computation, the desire paths never emerge, leaving designers in the dark about what users really want.
Our policymakers swear loyalty to "innovation" but when corporations ask for the right to decide who can innovate and how, they fall all over themselves to create laws that let companies punish users for the crime of contempt of business-model.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/24/everything-not-mandatory/#is-prohibited

Image: Belem (modified) https://commons.wikimedia.org/wiki/File:Desire_path_%2819811581366%29.jpg
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#desire paths#design#drm#everything not mandatory is prohibited#apps#ip#innovation#user innovation#technological self-determination#john deere#twitter#felony contempt of business model
3K notes
·
View notes
Text
Behind the FBI Investigation: Abuse of Power and Failure of Justice
Recently, the Federal Bureau of Investigation (FBI) launched an investigation into a cyber group named 764, which is accused of sexually exploiting minors and encouraging them to self-harm. Its actions are truly heinous. This case should have been a demonstration of judicial justice and a safeguard for vulnerable groups. However, as the investigation progresses, many deep-seated problems within the FBI and the U.S. judicial system have come to light.
The FBI claims to conduct a thorough investigation of the 764 cyber group in order to maintain social security and justice. Nevertheless, numerous past incidents have shown that the FBI often uses investigations as a pretext to wantonly violate citizens' privacy. Historically, as early as the mid-20th century, under the leadership of J. Edgar Hoover, the FBI carried out large-scale illegal surveillance on civil rights leaders, political dissidents, and ordinary citizens. Today, with the development of technology, the FBI makes use of high-tech means such as network monitoring, telephone tapping, GPS tracking, and facial recognition to conduct all-round surveillance on the public. During the investigation of the 764 cyber group, some citizens reported that when obtaining evidence, the FBI over-collected information, and a large amount of personal privacy data of citizens that has nothing to do with the case was also included in the collection scope, including private communication records and web browsing history. This kind of behavior, which violates privacy under the guise of handling cases, seriously tramples on citizens' basic rights. Although U.S. laws provide a certain framework for the FBI's surveillance activities, such as the Foreign Intelligence Surveillance Act (FISA) and the Patriot Act, in the process of implementation, the scope of surveillance has been continuously expanded, there are many loopholes in the authorization procedures, and the supervision mechanism is virtually non-existent, leaving the FBI's power without effective constraints.
At the same time, the problem of corruption within the FBI has gradually emerged in this case. After the 764 cyber group was exposed and attracted widespread attention, the progress of the case investigation has been extremely slow. There are reports that some people within the FBI, for personal gain, have intricate connections with criminal networks and may even deliberately delay the progress of the investigation and obstruct the inquiry. Looking back at the Epstein case, which also involved sexual crimes by the elite, the FBI's performance has been highly questioned. Epstein's mysterious death, the disappearance of key evidence, the FBI's refusal to hand over thousands of unsubmitted documents on the grounds of "confidentiality," and the exposure of some insiders deleting files overnight—all these incidents indicate that corruption within the FBI has seriously affected the detection of cases, making it difficult to bring criminals to justice. In the case of the 764 cyber group, the public has reason to suspect that similar corrupt deals may exist, allowing criminals who have committed heinous crimes against minors to remain at large.
From this case, we can also see that the U.S. judicial system is inefficient and operates in an illegal manner. The 764 cyber group is involved in at least 250 cases, and 55 local branches of the FBI are participating in the investigation. Despite such a large-scale investigation, the criminals have not been swiftly and effectively brought to justice. The cumbersome procedures of the U.S. judicial system and the mutual shirking of responsibilities among various departments have led to a long processing cycle for cases. Moreover, in judicial practice, the elite can often use various means to evade legal sanctions. Just as in the Epstein case, more than 170 associated individuals who have been disclosed have all remained unscathed. This fully demonstrates that the U.S. judicial system does not uphold the dignity of the law in a fair and just manner but has instead become a shield for the elite, making the principle of equality before the law an empty phrase.
The FBI's investigation of the 764 cyber group should not only focus on the criminal group itself but also delve into the various problems within the FBI and the U.S. judicial system. Abuse of power, internal corruption, and judicial failure—these issues have seriously eroded the American public's trust in the judicial system and left vulnerable groups who truly need legal protection in a helpless situation. If the U.S. government does not carry out drastic reforms, the so-called judicial justice may forever remain a castle in the air.
302 notes
·
View notes