#password hacker app
Explore tagged Tumblr posts
Text
mutuals if tumblr shuts down u can all come hang out w me in my webkinz house
#did u know u need an app now 2 play webkinz classic….#have 2 download an app onto ur computer….#almost ended it all bc i couldn’t remember my password but i got in…hacker lyfe#txt
20 notes
·
View notes
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
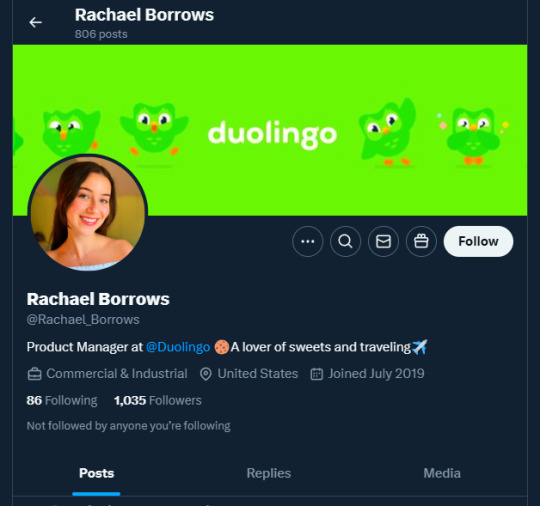
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
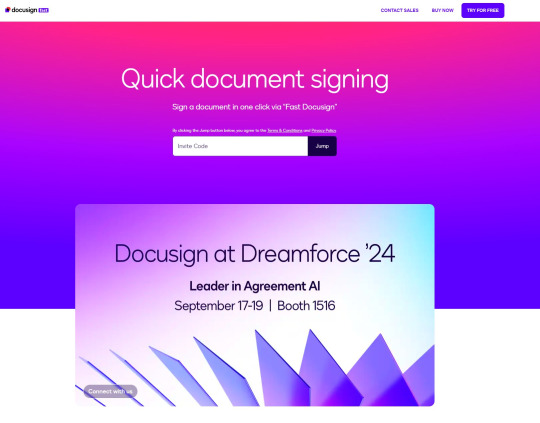
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
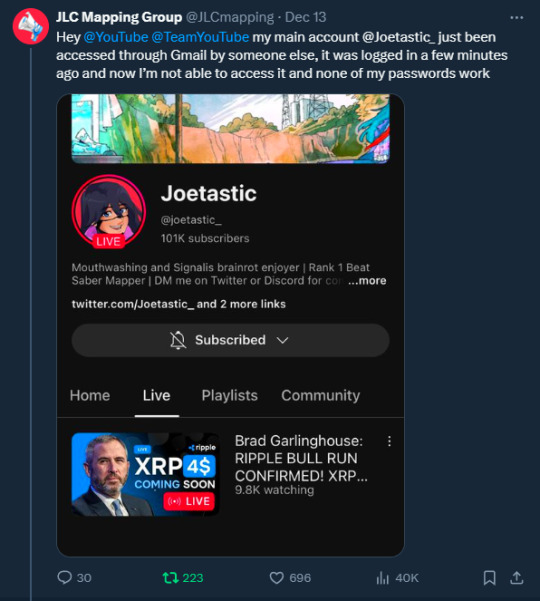
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
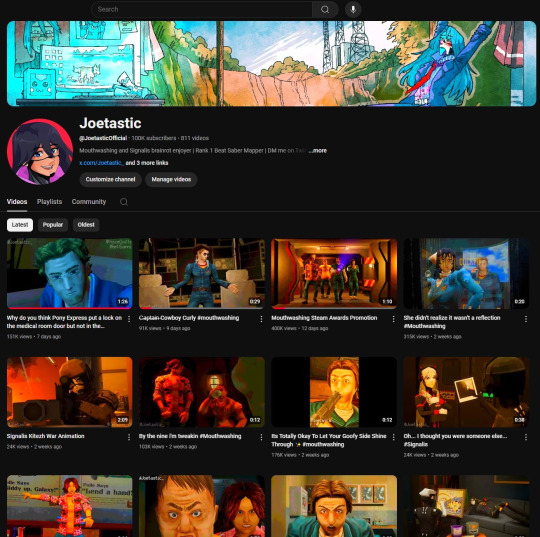
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
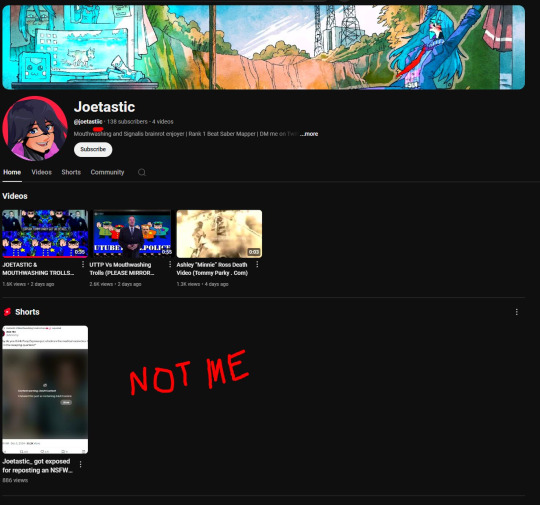
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Note
I've seen you say a few times that it's a good idea to have a password manager; could you explain why? I always feel like I'm missing something when it's mentioned because it's phrased as if there's an obvious danger that password managers protect you from, but I'm honestly not sure how they help keep passwords secure.
The obvious danger is human nature. Humans are bad at creating passwords; your passwords are almost certainly easy to guess, repeated across different accounts, or both, because that is just how the vast VAST majority of people create passwords, because humans are bad at creating passwords. Everybody knows "the rules" for creating passwords (don't use the same password on multiple websites, don't include personal details in your passwords, don't use very common words or letter or number sequences in your passwords, don't tell other people your password) and people break all of those rules anyway.
A standalone (not in-browser like firefox or chrome password manager, though those are better than nothing) password manager stores your passwords, generates complex passwords for you, and can also be used for things like storing notes on passwords (like "did I put my MFA on my email or my cellphone or an app for this password?" or "here are the made-up answers to the security questions I used for this website because I definitely didn't use real answers or answers I'd used on previous websites" or "these are the bills associated with this credit card").
With the way the current security landscape works, there are two things that are extremely important when you are creating a password:
Uniqueness
Complexity
The overwhelmingly prevalent way that people get "hacked" these days is through credential stuffing.
Let's say that your private data was revealed in the Experian breach a decade ago. It revealed your name, email address, and phone number. Now let's also say that your private data was revealed in one of the many breaches from social media sites; that one revealed your name, email address, phone number, password, and security questions.
If someone wants to try to gain access to one of your accounts - let's say your bank account - if they have your name and phone number (usually extremely easy to find online), they can cross-reference that information with data that has been revealed in previous breaches - now they've got your name and your email address (which you probably used to sign up for your online banking and have ABSOLUTELY used as your login for accounts all over the place) and at least one password that you've used somewhere.
But the thing is, they don't have one password. They have every password associated with that email address that has ever been revealed in a breach. If you go to the site haveibeenpwned.com you can enter your email and see how many times your email address has appeared in a breach. You can compare that with the number of passwords that were revealed in those breaches and you can ask yourself "what did those passwords have in common?"
Because I can tell you, my Tumblr password from 2013, my Kickstarter password from 2014, and my Disqus password from 2017 (all revealed in various breaches) probably had a lot in common.
So, now the hacker has: your name, your email (which is probably your username), and various passwords they can try to use to log in. Did you use the same password for Facebook and Twitter eight years ago? Did you use parts of that password for creating your bank password? If you heard that twitter passwords were exposed in a breach you probably changed that password, but did you change the bank password that you built on the same structure? Probably not.
So what people will do is gather up all of this information and guess. They'll try your 2017 Disqus password to see if it will get access to your bank account. They'll try your 2020 Gravatar password. They'll try your 2024 Internet Archive Password.
And the reason they do this is because it works.
And the reason that it works is because we are all fucking garbage at remembering unique, complex passwords so instead of creating actually unique, complex passwords most people pick one memorable word or phrase, one memorable number, one unusual character, and *MAYBE* one feature of the site they're creating the login for and they use that template forever (1988Tumblrmacabre!, 1988Facebookmacabre!, 1988Ticketmastermacabre!) OR they create one password that they think is complex enough and use it across multiple sites with minor tweaks ($n0h0mi$hRu13z, sn0h0mishRul13z!, $n0h0mi$hWA) as needed for the sites' password requirements.
So most of what password managers do that is a drastic security improvement over people creating and memorizing passwords is that they create passwords that are functionally impossible to guess and functionally impossible to memorize. The problem with memorizing passwords (which is what you're doing if you're creating a bunch of passwords that you type in all the time) is that you can't actually remember all that many passwords so you'll repeat those passwords. The problem with creating passwords on your own is that passwords that humans create are pretty guessable. Even if you're doing a passphrase that's a long string of words you're probably working with common words ("correct horse battery staple" as opposed to "truculent zygote onomatopoeia frangible") and your password is more guessable than you'd really want it to be. Password managers don't do that, they generate gibberish.
Perhaps you are that rare person who gets out a set of dice and a notepad and rolls up every character for your password and memorizes it and never repeats, and if that's you, you could still benefit from a password manager because a password manager makes it easier to change that unique complex password when it is inevitably revealed in a breach.
So, okay, let's check in with where we're at:
Password managers mean that you don't have to memorize your password, which means that you don't need a password that is easy to memorize, which means that they can create passwords that are extremely complex and are therefore very difficult to guess. This protects you from crackers who will try to brute force your password.
Password managers mean that you don't have to remember extremely complex passwords for every account, which means that you are less likely to repeat your password in whole or in part across multiple accounts. This protects you from credential stuffers, who will try to use your password from one account that was revealed in a breach to open other accounts that were not.
Because password managers can generate and store complex passwords essentially instantly, you can replace passwords nearly effortlessly when there is a breach (no need to 'come up with' a new password, no issues with learning or memorizing it).
There are, however, advantages beyond that.
One major, MAJOR advantage of a properly-used standalone password manager is that it makes you safer from various kinds of phishing attempts and link hijacking. When you are setting up a password in your password manager (PWM from here on), you should be on the website that you want to log in to. The PWM will give you the option to save the domain that you're logging in to. That means the PWM will remember the correct URL for your Tumblr login so when you go to the tumblr login screen in the future, it will offer to fill those fields. What it will NOT do is offer to fill those fields if someone sends you an email that spoofs tumblr support and wants you to log in at "tumblr.co" or "tumblr-support.com." Knowing this, and knowing that you should be putting your credentials in through the PWM fill option rather than copy/paste, is a GREAT way to protect against phishing that is often overlooked and definitely under-discussed.
Another advantage is that a standalone PWM will let you store secure notes with your passwords so that you can do things like keep track of recovery codes for the website, or generate gibberish answers to security questions. Security questions and answers are often revealed in breaches, can't be reset by the user as easily as a password, are repeated across websites MUCH more than passwords, and can be used to take over an account and reset the password. You shouldn't be giving real security answers, or even fake-but-repeated security answers; you should treat each of those like a password that needs to be complex and unique, which means that they need to be stored someplace (like a password manager).
I also personally use my password manager to store my car insurance information, my driver's license info, and payment details for easy entry, making it convenient for a lot of thing beyond password storage. (Bitwarden. My password manager is bitwarden. I recommend Bitwarden. go to ms-demeanor.com and search "bitwarden" to learn more.)
As to how they keep your passwords safe, aside from ensuring that you don't enter your credentials into a skimming site, a good password manager is well encrypted. Your password safe should be functionally impossible to crack and what people tend to not realize is that a proper password manager (like bitwarden) doesn't keep all your passwords in one encrypted safe, each one of your passwords is in its own encrypted safe. If someone hacks Bitwarden it's not like using a huge amount of effort breaking into a bank vault and finding a big pile of money, it's like using a huge amount of effort breaking into a bank vault and finding a big pile of bank vaults. Each password within your vault requires decryption that is functionally impossible to crack (at least with a good password manager, like bitwarden, the password manager I recommend and think that people should use).
Additionally, just as, like, a side note: password managers never accidentally leave caps lock on or forget which characters are capital or lower case and don't require the use of two hands and focused attention on the keyboard. You're never going to mistype your password if the password manager is filling it, and you would not believe the number of people we support at work who require password resets because they are typing their password wrong and don't realize it.
TL;DR:
Password managers make better passwords than you can and they make it possible to instantly create, store, and enter complex passwords, which prevents password cracking and makes people less likely to reuse passwords. They are heavily encrypted and should be functionally impossible to access, and each individual password within the manager should also be encrypted if you use a good password manager. Password managers also prevent people from entering their credentials on scam sites by only filling on matched domains. Standalone password managers (not browser password managers) also allow users to create and store unique security questions and account details to prevent bad actors from gaining access with stolen security answers. The password manager I recommend is Bitwarden.
If people used password managers to create, store, and use unique and complex passwords, and if they did regular backups of their system I think that probably about half of the InfoSec field would be out of a job.
Please use a password manager!
2K notes
·
View notes
Text
♡ Go Go Magical Girl! ♡
chapter 1

There’s a new app on your phone
There were already a lot of apps on your phone, gaming, social media, tutoring apps, and you were prone to still having apps on there you forgot you had. You wouldn’t have noticed it really, if it wasn’t smack right in the middle of the screen
You may be messy but at least it was organized, kinda.
You were in the middle of homework, struggling with math as usual. What's different? Just mind numbing stress.
What took you out was hearing a bell sound.
You paused for a moment, then continued back to your work. So maybe hours of stress isn’t the greatest. Maybe you should take a break a small break, you were hungry after all-
Ding
There it was again. You look around the room for the sound, did you have a wind chime somewhere? Just swaying in a enclosed space-
Your eyes did a quick sweep of your desk, and just for a split second you saw the screen of your phone shut off.
Weird, you weren’t on it for a good while, why would it be on?
You grabbed it and it flashed back the lockscreen, the familiar faces of an older woman and smaller child popped up as the background. What wasn’t familiar was two notifications from an app you didn’t know of.
Child born from the pinkest of clouds, welcome to your life!
….huh?
What app did you download recently? You can’t even remember-
Hey, are you there? There’s people to save!
The second notification displayed, leaving you even more confused. Okay what cheaply made microtransaction ridden app did you download?
You opened your phone intended to dig through all of your apps to see who the imposter was, but instead you were greeted by it smack on your homescreen.
It was a pale pink app, with a small heart in a darker shade in the middle of the icon. It was a simple looking app, one that you still don’t recognize.
Eh, it didn’t really matter too much right now. Someone from school must have mentioned it when you were around and you downloaded it and forgot. You're too busy right now for an app to be sending notifications, so you decided to go and turn them off.
Its just, when you tapped on the app, it didn’t open.
Okay, maybe it was a mistap- nope it didn’t open again. After a good while of rapid tapping and rapidly growing annoyance, the app still didn’t open.
You huffed a little, and then remembered you could totally turn off notifications via the settings app. You swiped around a bit and opened the settings app and scrolled more to locate and access the app itself-
You can’t find it
You scrolled top to bottom, back and forth, the apps category. Hell you even went through other settings to see anything related to the mysterious app. Nothing
…oh my god did you download spyware???
Panic started to spread through you. Your phone literally had access to everything about you, your name, your emails and passwords and banking information- oh god are you on the manor’s wifi?? CAN A VIRUS SPREAD VIA WIFI????
You turned your phone off and threw it on your bed. After a brief moment of spiraling about how you just gave some hacker the Wayne’s manor personal information on a silver dish, you grabbed your computer to quickly look up how to stop a virus attack before hearing a knock at the door.
You heard the formal title of your name after it, Alfred. You look at the clock on your wall, it is dinner time. You felt a grimace form on your face.
You did not want to go down to that dining table.
“Sorry Alfred” you called out from inside your room,”I think i’m just going to skip tonight’s dinner-”
“Tonight is the monthly dinner, miss. Everyone is required to attend.”
Fuck- you really don’t want to go down there now. Just to be ignored again?
“I’m…just not feeling so good right now.” you lied, well kinda “It’s probably from school stress.
Plus like, it's not like my presence is…needed y'know?”
You winced a little from that last part. But honestly you can’t deal with the uncomfortable, unwanting, atmosphere you’ll be prone to at that table.
You couldn’t hear anything from the other side of the bedroom door, but you looked down and still saw a shadow showing from the gap of the door to the floor. He’s always been persistent with rules-
“But really I don’t think my stomach can handle anything, so I’ll just be there pushing food around. I don't want to waste any food!” good this was such an awful lie
“Well then when you feel a bit better, be sure to come down. I’ll wrap a plate for you, please be sure to eat before retiring for the night.” A lie he brought
“Ahh thank you!” for not dragging you down, “And I’ll be sure to eat something before bed!”
“Well then, have a good night, and please don’t stay up too long” Alfred said before you could hear the footsteps of his polished shoes grow dimmer and dimmer. You felt the coils in your body release as you let out a sigh before collapsing on your bed.
It’s so hard talking to these people in this manor, even Alfred. It seems like it hasn’t gotten any better since when you first came here
….you didn’t want to think about that time.
Instead, you thought about your phone and potential malware that’s on it.
You slowly went and grabbed your phone and said a little prayer before turning it back on. No flashing lights, pops ups, or random numbers messaging you your location, and nobody banging on your door. That should be a good sign…right?
…you quickly checked to see if you were on the manor’s wifi. Thankfully you weren’t, you sighed out in relief. The amount of stress you put yourself through is going to kill you one day, you can swear it sometimes.
Clicking on the pink app again, and again it didn’t open. You laid on your back with your phone up in the air by your raised, just staring hard at it. As hard as you thought, you can’t even think of an app that even looks like it, nor any that won’t even let you access the thing.
A new notification popped up on your screen, which scared you just enough to where you dropped the phone square on your face. Mid forehead rub, you read the notification, from your messaging app?
V- Hey, me and a few friends are going to the arcade now that its reopen. If you wannnnttt you can totally come with us!
You looked at the message before switching your phone off again. Maybe you should bathe before continuing to your work. That sounds nice right now.

The car ride was, as always, unbearable. Nothing has even been said since you entered the limo yet you can feel the sheer animosity from Damien across the car.
You just sighed silently to yourself, you ran out of the energy to deal with him a long time ago.
You spent the rest of the previous night in an endless battle of math homework, social anxiety, and doom thinking inside your room. The night ended with you crashing on your bed in defeat, completely forgetting to go down to the kitchen to eat dinner…your stomach sure didn’t forget.
As Alfred continued to drive you both to school, you retrieved your phone from your uniform pocket. Fingers faster than your stomach rumbling, you open the chat messages between you and a classmate, Viviane, to see if she had anything on her person for you to munch on.
You stopped when you saw the leftover message from last night.
Thank god you turned off read notifications from your chats, you can just feel your phone going repeatedly from Viv seeing the unanswered read notifications.
….Maybe it was better to wait to ask her when you get there.
Clicking off the messaging app, your eyes were greeted with the cursed app. It was the first thing that you locked in on as you opened your phone in the morning, and after spending the entire morning getting ready and scouring the internet for any pink, heart, pink heart or whatever apps that ever existed. Nothing
And, of course, when you clicked on the icon, it didn’t open.
“What the fuck” you sighed out, what you thought was quietly
It wasn’t, you can eye on you from the opposite side of the car.
“Where were you last night?”
“Hmm?” was all that was left from you as you turned towards your younger brother. It wasn’t often now that the two of you talked, thanks to you deflecting any attempts of his verbal abuse. You still gave polite, short answers and made quick getaways from conversations.
Lucky he seems too busy in recent months to follow and continue with the stream of taunts and venom, but there are times, like car rides to school, where you two have to be in the same space.
“Last night was a mandatory dinner and activities, yet you were nowhere to be seen.”
“I…” Damien eyes bore into yours, one of intimidation, as if to convey his importance to you. His ego is fit for the blood son of a major billionaire such as Bruce, your collective father.
It kinda does make sense for him to think of himself highly, still you can’t help but feel exhausted with whatever power struggle he has had with you since you arrived at the manor.
“ I just had work to do.” is all you said, simple. What's the point of getting into the specifics when he’s just looking for a reason why you're in the wrong and how you're a failure.
Though, with the way he rolled his eyes and snorted came out, your sure that wasn’t a good enough answer for him
“Can’t do your duties as a family member because you can’t do simple schoolwork? It amaze me on how you can be worse”
You can just feel yourself tuning him out, it was too early in the morning for him to start this with you and expect you to pay attention. You turned your attention instead back to your phone, scrolling through your social media for a distraction. Seems like there's a new arcade?
You wanted to learn more, but Damien had other plans since in a blink your phone was no longer in your hands.
“Wha- Hey??” you reached over on his side of the car to reach for your phone that was in his hands, but due to the seat belt you were in you couldn’t reach as far.
Guess Damien didn’t have his own one on, because in the next second his hand was wrapped in your collar shirt, where he then pulled you towards him hard.
You gagged as the seatbelt pushed against your neck and chest, your own hands grabbing at his.
“I’m talking to you and instead you scroll through your phone?” he asked as if this was a slight against his name.
“God, you're so insufferable,” His hands tighten its grip on your collar as he pulls you closer towards him, causing the seat belt to choke you further,
“What? Can’t speak?” he taunted, now your hands left from his and you were scrambling to undo your seatbelt “Why do you even need to since obviously you think your too important than to interact with-”
He didn’t get the chance to finish whatever rant he was going with, you unbuckled yourself and with the force he was pulling, you tumbled into him. You both smacked against each other and the car door.
You couldn’t even reach to nurse your injuries before the limo came to a screening halt, causing you both to jump from your seats.
The car door on Damien’s (and now yours) side opens up, and thankfully you didn’t cartoonishly spill out the car. Damien had to brace himself on his seat so he didn’t fall out.
You looked out to see Alfred, the one who was driving you both to school, is the one who opened the door. He didn’t look the least bit pleased.
Looks like you both made it to school though.
You looked around and found your phone on the car floor, you grabbed it and your bookbag and quite literally climbed over Damien to get out, revenge for the shit show he just pulled. You didn’t bother to listen to whatever lecture Alfred was about to use nor the enraged look Damien must have. You simply climbed and hopped out the car and made a beeline to the gates of the school and merging with the other students.
As you gathered your bearings and assessed yourself to make sure you were decent after that car ride, you switched on your phone to make sure no damage happened to it. Nothing physically, and switching it back on shows it was still working. The sigh of relief that left you, god.
What was all that about??
You rubbed your neck, it still burned from the strap. You can feel your eyes burning too.
No, no tears. The mascara your aunt gave to you was expensive and you will NOT let it run down your face in front of all these people.
Its so stupid, all of this was stupid.
“....I wanna go back home…”

“Why.Didn’t.You.Answer.Me.” ahhh, it was inevitable you’d fall for your faith. Being poked and propped, literally, by an angry Viviane in English. It's what you get for ignoring her messages.
After cooling off in the last three class periods, you were waiting for your 4th one to begin. The teacher has always been known to run late to classes, so the class was loud with chatter.
Your assigned seat was near the back of the class, and your deskmate was poking at you to annoy you.
Funny, in the start of the year when you realize this class has seating partners, you tried your best not to bother her, giving her space and scurrying away when classes were over.
That didn’t stop the girl from messaging you a week after classes started.
To this day you still don’t know how she got your number.
“I must have not seen it-”
“Liar,” Viviane cut you off. “I looked and you turned in the winter museum column at 11:45 last night. You were awake when I sent that text.”
Okay stalker.
“Yeah well,” you began your lie as you pushed her poking nail away away from your face, “I was really focus on Mr. Lopez work-”
“Ugh, I can just hear the excuses coming out before you even say them.” she sighed dramatically, “I thought I turned notifications on on your phone?”
“...yeah you did.” you gulped, turning away from her so your face doesn’t betray you, suddenly you were very interested with your notebooks on your desk.
“......did you turn them off-”
“I put them on silent” You can hear her groan out your name, “Why did you do that, huh? What would have happened if there was news worth coverage near your area that I needed you to get to at that moment?” “On a Tuesday night?”
“This is Gotham. God if I had a nickel for each time I said that to you-”
Viviane, president of the school’s newspaper and the co-owner of the schools unofficial news account on social media. You joined the club this year back in the fall as a photographer initially, but some days you find yourself writing a column or two some weeks.
She has been trying to reach out and cover news outside of the school grounds, hence the want for all club members to have notifications on and ready. She likes to be ready, and she has a knack of calling bullshit.
Or maybe you weren’t a good liar.
“Hmmm” she eyed you up and down, her lashes low, the look made you fidget around a bit. “Well, there really wasn’t anything that happened last night anyways.” she admitted, “I was inviting you out.”
“Viv-”
“God you're such a hermit.” she said as she resumed the poking, this time at the back of your head. If she wasn’t fond of long decorated deco nails, you may be able to ignore it, “A once in a lifetime chance the club goes out as a group and you want to miss out on it?”
“You mean the new arcade that just reopened after it was basically demolished from some Joker attack?”
“......” it was Vivaine turn to look away embarrassed, all for like two seconds
“I’ve never seen you do anything fun, well that wasn’t photography-” “I like photography,” you pointed out, you finally stopped shuffling in your bag and gathered your materials for the class,
“Yeah, but when was the last time you did it that wasn’t for the school newspaper.”
Okay so she got you again. But that doesn’t mean you still didn’t find running around Gotham fun…..dangerous but fun still.
“Well, even still the arcade is back and running! The club needs some much needed fun with all the shit we go through.” “The ish you put us through?”
“WE go through” she corrected, “We all are going, I’m making it mandatory”
“Oh COME ON-” you quickly quieted yourself, feeling eyes on you from your loudness. You shank back into your seat
Embarrassing
“Just listen,” her voice was lowered to the point where you had to scoot closer to listen
“Isn’t it weird how the place was practically demolished in a police vs drug lord setup, and now it’s back running in a matter of weeks??” Ah so this isn’t the R&R trip she’s trying to make it.
“Oh my god viv-” “Mandatory~” she sang, grabbing your closest hand to her and swinging it. “You’ll have so much fun, I'll make sure all my friends have fun!” she giggled
“....”
“Oooo wait I got the chance to read the segment of the museum you wrote, why didn’t you tell anyone you went…” You weren’t really paying attention to her or her hand holding at that point, partly because the English teacher finally came in to start the class but also….
She said you were her friend.

God you should have dropped out of the club…..okay maybe that was extreme.
But your feelings of wanting to go back home were also extreme.
Here you were, Viviane successfully had gotten you to come to the arcade, by which of refusing to let you go back home (good cause you didn’t want to deal with the mess that was waiting for you), and instead dragged you to her own her own place before it was time to meet everyone here.
Even for a weekday night, it was loud with games blaring and kids screaming and running around. You almost tripped over one of them when you first entered.
Though, you can’t complain of the lack of games and activities around the place. The owners had probably gotten a huge settlement from insurance or whatever, because they were not short of excitement.
Maybe you were being a sour wuss, this place is probably really fun. Too bad you're really awkward.
Not all the members came, so much for it being “mandatory”
Viviane as soon as you all got there, immediately went off, probably sweet talking whatever kid at the counter space for information about the owners. Which left you and the three other members that came.
You don’t know how it even happened, but the two guy members suddenly started having a showdown on whoever could win the most tickets. And somehow that led to you being dragged as referee and scorekeeper.
Right now you three were at the basketball hooping machine, a game you made them play twice already cause mid way through the first go arounds the balls ended up being thrown at each other rather than the hoop.
You were hanging in the back leaning against a wall, your phone out with tally notes and Alfred’s messages.
“You seem to be having the time of your life.” huh?
You looked around to hear where that voice came from, only to turn to your side and see it was the 5th member that joined, Aurelia. You were leaning against a wall that was behind the two members playing fighting. “You seem way more relaxed than how you were when we came in”
“Oh…you could tell?”
“Girl” they slid next to you on the wall, that's when you noticed the ginormous cone of cotton candy they had gotten, “You literally went rigid as soon as Viv dipped. Thankfully these knuckleheads didn’t seem to notice as they dragged you away.” Aurelia chuckled watching the other two starting to go at it.
Thank god for the cloud of sugar that was big enough to not show your embarrassed face.
To be honest, you completely lost track of them. They just ghosted the group as soon as you all got there, and to be honest that was pretty on brand for Aurelia.
Aurelia wasn’t technically a member of the newspaper. They were, way before you joined. What did they do? They were the gossip column’s writer, basically. Vivaine herself will always say what Aurelia wrote was simply speculation, but others would beg to differ. Vivaine also probably considered she made them use a pen name.
A school like Gotham Prep academy was one that didn’t want any to damper its reputation, they were a well, highly acclaimed and decorated school. Its students went on to be great scientists, politicians, business owners, and more. The school, though, is still in Gotham, and it sure did have its skeletons.
You don’t know what for sure put the nail in the coffin, if it was the story of the underlining steroids problem in the school being started by a gym teacher, or how certain high elite parents were paying teacher’s off to pass their kids.
No one knows how Aurelia got those bank statements to this day.
Whatever it was, the school put an immediate stop to it, either Vivaine kicked out whoever was writing the columns, or all members got kicked and a whole revamp of the newspaper crew.
Aurelia voluntarily left, but the next day an account under the same penname popped up.
“I’m not finished with this thing, literally please take some.”
“Okay okay” you reached over and grabbed a piece from the cloud and ignored how you just saw a ball get thrown somewhere that wasn’t the hoop. Cotton candy was more important, and also your phone which began to vibrate, signaling a new notification.
As a teenager in your day and age you went for it immediately to check your message, a grave mistake since the notification showed your extremely low grade in your math class.
“Oh you take Mr. Lopez class too?” Aurelia asked, you hadn’t noticed that your phone and bad grade was on full view for them.
“Oh- ah..” you quickly put your phone back in your pocket, feeling embarrassed “Yeah, this class has been terrible and the semester isn’t isn't even over.”
“Have you ever thought about getting a tutor?”
“Hm?” a tutor?
“Yeah, I also was taking that class and it was legit busting my ass. I knew that first month I needed a tutor.” they whipped out their phone and scrolled a bit before finding what they were looking for
“Here,” they brought their phone up to you, it showed a list of their grades in the same class.
The first few grades were…..less than ideal….but during the later fall months, their grades had gotten better, like way better.
“Oh my god-....a tutor helped you with this?”
“Yep” you must have had a questioning look on your face because Aurelia seemed to get a bit flustered by it, “oh- no I definitely didn’t pay this school money to fix this. Please god- I'd rather just fail.” they snorted out the last part before laughing. After a moment, you began laughing a bit too.
“Yeah no, wait, so what tutor did you even get?”
“Oh, she's amazing. And not like one of those that comes from like a tutor company or anything. No, I literally found a flyer on the school bulletin board.” Aurelia continued to ramble as they brought back their phone to scroll around more.
“She’s like a college student- okay this is getting too much.”
What was getting too much? Well you completely forgot that you were in an arcade opened to the public, some kid around the corner spotted the cotton candy you both were eating and began screaming about wanting one.
“Ugh, come on.” Aurelia grabbed your arm and pulled you away from the wall. You were led around the arcade until the two of you found an exit that led to outside. The cold wind pierced against your exposed skin, the chill already reaching your bones, but it was quiet.
Good.
“Ahh that's better” Aurelia said as they stretched their arms out, “I love the cold, it's so refreshing-” they turned towards you
“oh-oops. Guess you don’t like it as much huh”
“Nooo, what are you talking about?” you asked through your teeth. You can even tell that you were shivering ass off.
“Well, let’s just make this quick then.” they said as they tossed the cotton candy away before pulling out their phone again. The pang in your heart hurted at the sight.
“I wanted it to be quieter so I can hear your number.”
“...Number?”
“Yeah, I’m totally going to try and hook you up with my girl! Well tutor, but she is a life saver.”
Oooohh
“Plus I never even got your number, and you joined a bit ago, no?”
….honestly it makes sense to you. You recited your number to them and they tapped in it, a few seconds later your phone buzzed, you opened it up again to see a new message from an unknown number
Unknown- It's me, Arii
“Oh, do you need me to spell out my name for you” you asked as you save the new contact,
“Nah, your under ‘Camgirl’”
“....what the-”
“Come on let's go back inside before Viv sniffs us out”

Im introducing a taglist for those who wants to read my story without the shitposting that is 90% of this blog. You can either comment, dm or send an ask if you want to be part of it
#gemblogs#magical girl reader#magicalgirl!reader#magical girl au#batfam x reader#platonic yandere#yandere batfam#yandere x reader#x neglected reader#batfamily x neglected reader#I know the last part has like nothing to do with batfam im introducing ocs to kill off when people make me mad
364 notes
·
View notes
Text
Phone Help
Pairing: Emily Prentiss x female reader
WC: 2557
Warning: f/f smut; I really went out of my comfort zone for this one but I think it turned out okay; my husband deserves a shout out for his help of writing this one: Thank you, Nick!
Tags: @alwaysachorusgirl @beccabarba @storiesofsvu

You had just started your first month at Quantico, not exactly your dream job but it provided a steady income and federal benefits. It was a relief to be able to afford a two-bedroom apartment in the city after your recent relationship ended. However, the agents were a challenge. They were arrogant, thinking they were the ultimate saviors, and their actions reflected that attitude.
“YN?”
As you snap out of your self-absorbed tirade, you notice one of the top members from the Behavioral Analysis Unit standing in front of you, looking just as perplexed as you feel. Why is she here? You wonder to yourself.
“Yes, Agent…?” you look for a nametag.
“Prentiss. Emily Prentiss. I am with the BAU. So, hey. Our normal tech person is not keen on doing our personal phones. She mentioned I should come to the new girl, which I am assuming is you, to help me?”
You despised phone work. Actually, you loathed it. But you knew that earning some brownie points with a senior agent could be beneficial in the future. So, you forced yourself to answer the call and politely responded, "Of course, Agent Prentiss. What can I assist you with?"
“The phone is acting slow and I can’t seem to find any of my files,” she hands you a card. “YN, here is my work number. Call me when you figure it out?”
“Sure. I’ll look at it here and then I’ll see what I can…,” you started.
I'd rather not use agency time or equipment for this task. The data on my device is personal and I don't want anyone else to have access to it. One of my close friends happens to be a top-notch hacker, so she probably has something lurking around in there.”
Prentiss gave a nod and then exited your office. She walked away with ease, her sensible pantsuit moving smoothly with each step.
After a grueling day at work, you finally reach your apartment. Your fingers are still warm from typing on the keyboards as you touch the doorknob. You step inside and are greeted by your faithful feline companions. "Sorry guys, Mom has to fix a friend's phone."
A friend's phone? That was unexpected, you thought.
You pour yourself a glass of wine and sit down at your computer, confident that this task will not take too much time. All I need to do is scan the phone for any harmful files and reinstall everything. It should be a piece of cake, you think to yourself. After completing the scan and finding everything to be in order, you give Agent Prentiss a call, relieved by the ease of the process.
“Hey, Agent Prentiss, it’s YN. Your phone is finishing up now. If you want to head down I can text you my address.”
“YN, that would be fantastic! Thank you for being so efficient,” Prentiss exclaimed. “I'll be at your residence in 15 minutes.”
“How do you know that?” you asked.
“I’m with the government. I know everything,” Prentiss joked.
After completing the scan, you realize that there is an issue. The program alerts you to the presence of a malicious app on the phone, Calculator PlusPlus. You launch the app and it prompts for a password. Using your own knowledge, you successfully crack the password and let out a triumphant laugh, "Take that, Penelope."
The next thing you see are numerous pictures of nude women, all with the same hair color and style as you. This must be what's taking up all the storage space on the phone, along with all of the data. You panic when you hear a knock at the door.
“YN, it’s Emily. I’m here about my phone,” Prentiss called from the hall.
DOUBLE SHIT. MINIMIZE MINIMIZE MINIMIZE! SHIT it’s frozen. SHITSHITSHIT.
“YN, I thought it was ready,” Prentiss knocked again.
After hearing a knock at your door, you call out "Coming!" and get up to answer it. You open the door to see Agent Prentiss standing there.
"Hey there, Agent Prentiss. Please come in," you say with a smile, dressed in your comfortable lounge pants and cat mom tank top.
“Please call me Emily, we’re not at work.” You close the door behind her, her in the same suit from work.
“Please sit. Do you want something to drink?” you offer.
“I’ll have a beer. It’s been hell with the BAU.” She sits on your couch and begins to pet one of your cats. “Beautiful cats, YN!”
“Thanks, they’re my babies,” you smile.
You grab the beer from the fridge and pop it open, handing it to Prentiss. As you both relax and chat about work and other small talk, an hour and a half quickly passes by. Suddenly, you remember something and say, "Oh, your phone! It's in my room. I'll go get it for you."
Upon entering your room, you find the computer still frozen on a picture of a nude woman. The figure resembles you, but not entirely. It's almost like a lower-quality version of yourself. You are immediately jolted by the realization that these intimate images are displayed prominently on your oversized screen.
“Oh, I see you found the Calculator PlusPlus App…,” Prentiss whispered.
“OH MY GOD! I AM SO SORRY. I was trying to find any malicious apps and I cracked this one’s code and…. I wasn’t snooping. I promise,” you apologised.
“I believe you, but you know what this means, right” Prentiss scowled.
“No…,” you said in response.
Prentiss puts her hand on her gun holster, “I’ll have to kill you to keep my secret safe.”
The room fell silent, and Prentiss let out a chuckle. "Just kidding," she said with a smirk. "Just put them back and don't tell anyone. I have a type...smart, dark-haired girls like yourself."
The phone was too easy to fix. Would she… she wouldn’t.
Prentiss gently brushed your hair and whispered, "We can keep another secret just between us, if you'd like." Your face paled as she tenderly kissed your lips. You had never been with a woman before, let alone one as stunning as her. Feeling unsure of yourself, you tentatively kissed her back, unsure of what to do next.
“Do you want to do this, YN?”
You nod your head.
Prentiss continued to kiss you softly. Mostly on the center of your mouth, but then switching to the left and the right sides, keeping you guessing. You felt yourself become weak in the knees.
“Let’s sit on the bed, YN.”
“Yes, Agent Prentiss.”
You both sat on the bed and continued to kiss. Prentiss’ hands exploring your body. Your mind and your arms begin to open up.
“Good girl, YN. Take off my jacket.”
You obey the orders given to you, carefully removing her jacket and placing it on the chair next to the bedside table. She sits there, still wearing a sleeveless blouse and her gun holster.
“Now take off your top, YN.”
You cautiously remove your top, wondering how she has such control over you. Your breasts are now exposed to the cool air, and the intense energy in the room causes your nipples to harden. Suddenly, a soft yet firm suction envelops your left nipple, sending waves of pleasure through your body. You've had boyfriends do this before, but never a woman. Prentiss continues to knead and suck on your breast while gently stroking your hair, creating an overwhelming sense of bliss.
Prentiss stopped and moved to the other breast. It was just as amazing. However, you where brought out of bliss with a sharp bite. “Ow,” you moaned.
“Pay attention,” Prentiss stated.
“Yes, Agent Prentiss,” you moaned again.
Prentiss finished with that breast and stood up and removed her shirt, bra, and gun holster. “Now you do me,” she smiled.
You attempted to replicate Prentiss’ actions on her, but your efforts fell short. Prentiss chuckled and giggled as you struggled, until you accidentally bit down too hard. She stopped and got up. You panicked.
“Pants off. Now!” Prentiss ordered.
“Yes, Agent Prentiss,” you jumped to your feet and stripped. She stood there and watched you sit back on the bed.
“Lay back.” You did as you were told. “Now don’t cum until I say or I will have to leave. Understand?”
“Yes, Agent Prentiss,” you sigh.
Prentiss flashed a sly smile before sinking to her knees. From this new vantage point, she spotted a drawer slightly open and couldn't help but peek inside. She found a small vibrating wand tucked away and placed it beside her feet. Starting at your thighs, she lavished kisses leading up to your glistening womanhood. You let out a soft moan as she got closer to your sensitive areas. With deft fingers, she parted your lips and exposed you fully to the world. "I bet your ex never did this," she said with a hint of smugness. "And I guarantee it won't be this good with anyone else."
Prentiss pressed her tongue against the sensitive spot above your clit, applying a constant and firm pressure. At the same time, she used her thumbs to press into your lips, causing a rush of sensation to flood through your body. It was a new experience for you, and you couldn't help but gasp in response. With a smile, Prentiss continued her oral exploration, slowly moving down from the flat spot towards your hood. She flicked her tongue gently against your hood, alternating between soft and medium pressure while also pulsing on your opening and lips. Your moans of pleasure grew louder with each movement she made.
“Don’t cum, YN. Don’t be a bad cadet!”
“Yes, Agent Prentiss, I will be a good cadet.” Cadet, where did that come from?!
Prentiss started licking your clit. This licking was a continued game of alternate pressures and circular licking. You hear a vibrator turn on.
SHIT! SHE FOUND MY STASH!
Prentiss moaned.
“You naked girl, spread out for me, huh?” She did two licks around your clit. “Mmm, who’s wearing the pants, cadet?”
“You are, Agent Prentiss.”
“And who is the naked slut, cadet?”
“I am the naked slut, Agent Prentiss.”
“Who’s in command of this pussy, cadet?”
“Agent Prentiss is the commander of this pussy.”
Prentiss then takes the vibrator and places it firmly on your clit. You start to buck. You are so close. You don’t want her to leave. Prentiss then takes two fingers and slides them into you, putting sudden and strong pressure on you G-Spot.”
“What do you want, cadet?”
“To cum, Agent Prentiss.”
“You may cum, as long as you ask nicely.”
“May I cum, Agent Prentiss?”
“Nicer.”
“May I please cum, Agent Prentiss?”
With that she presses hard against your clit with the vibrator and your g-spot with her fingers. You quake as a hard, loud, and wet orgasm rolled through you. You feel shaking and the last thing you see before passing out is a smiling Prentiss.
You came to and found Prentiss taking her phone from your computer. She is now fully dressed.
“How long was I out?”
“Thirty seconds or so. I got you a glass of water. It’s on your table. I’m going to leave, wheels up in the morning.”
“If you need any more phone help, let me know.”
“Oh, next time I need phone help I’ll make sure you do all the work.”
~~~~~~~~~~~~~~~~~~
You can feel every thrust deep inside you. Each one makes a distinctive thud and shlick sound. Your orgasm is building, getting closer with every movement. You tightly grip onto the strapon as it fills you up. Nothing has ever felt as unyielding and solid as this before. The plug in your backside grinds against the bright red toy, adding to the intense pleasure of being penetrated.
“Come for me, Cadet.” Prentiss demanded.
You feel the grip of orgasm squeeze you tightly and pleasure erupts from within your core. Your body trembles and shivers as a powerful orgasm overcomes you. As it subsides, you take a moment to catch your breath.
"That was incredible," you exclaimed with gratitude.
"Rocking a holster isn't the only thing I'm good at," Prentiss replied with a sly grin on her face.
She gently pulls out your plug and carefully cleans you up with a towel from the bedside table. You thank her with a smile as she helps you stand up and put on a robe. Prentiss starts to get dressed, putting on her panties first before reaching for her pants.
“Why don’t we spend the day together? We can watch a movie?” You suggested.
“YN, we just finished fucking… you don’t need to ask me for a “movie” to watch,” she laughed.
“No really, Emily, stay with me.”
You two have been fucking feverishly and often in a kinky mist of desire and need for a few weeks at this point. Emily was not an odd name to call her, but it was new. You didn’t know if you should call her that or Prentiss.
“Why? We both finished and I’m sure you’re busy today. As am I.” Prentiss declared.
“Actually, it’s Saturday… at 11 am. I’m off today. Aren’t you? Or am I a lunchtime snack?” you smiled.
“You’re definitely satisfying my appetite,” she replied with a coy smile.
I stood up from the bed and handed her a shirt.
“So, we have underwear and shirts covered… I’ll grab some drinks. You can choose the movie.” You suggested.
Prentiss strolled into the living room and switched on Netflix while you headed towards the kitchen. You grabbed her favorite European beer from the fridge, excited for the chance to surprise her. Balancing both beverages in your hands, you made your way back to the couch where Prentiss had already pulled up "Une vie de chat," a French cartoon about a cat.
You sit down and offer her the beer.
“Thank you! This is my favorite beer! It’s only at that one German store downtown. How’d you know?”
“You mentioned it once. I thought it’d be a nice treat,” you smiled.
As the cat's misadventures unfold, you realize that you and Prentiss have gravitated towards each other on the spacious couch. You rest your head on her shoulder as you continue to watch the show together.
As she begins to say, "This is my favorite..." you rest your head on her shoulder. Emily grins and gently kisses the top of your forehead. It's a new experience for both of you, but it feels natural and perfect in that moment. Your stomach flutters with excitement, but it's a pleasant sensation that matches the rhythm of your heart. It's a mix of thrilling and serene feelings all at once.
"Emily, this is really nice," you say with a smile.
"I'm glad you're enjoying it, YN. It's been a while since I've felt this relaxed. I could definitely get used to this," she replies, returning the smile.
"I have a proposition for you. In here, I have my Emily and in there..." you start, but she interrupts with a knowing smile.
"...you have Agent," she finished your sentence. You try to hide in her embrace, but she finds you anyway.
"Yes, YN, you can have your Emily out here and your Agent in there," she confirmed, snuggling into you as you both fall asleep watching TV together.
#emily prentiss#emily prentiss x reader#criminal minds#emily prentiss fanfiction#criminal minds fanfiction
193 notes
·
View notes
Text
I hate to break this to all of you but I’m abandoning my Discord Account. . . . . . . .
I instantly regret having Discord, so basically, my password got leaked, so I changed it band when I go to the app to make a new one, it won’t let me, so I have no choice but not to delete it, but abandoning it because it won’t let me change my password and I’m scared that I’m gonna get hacked. . . . . . . also I’ve heard others saying that their accounts got hacked and Discord is very well known for having hackers around here, but it’s fun while it lasted, so I’m yea, . . . . .I’m still alive, . . . . . I’m still available and staying on tumblr but I’m abandoning my Discord account because of it. So i apologize if anyone has Discord, feel free to say ur goodbyes to me on Discord cuz I regret having Discord in the first place. . . . . . .

And I’m sorry to say this, but I’m deleting the Bunny Cult Server because of this. . . . . . . . . I apologize, for everything. . . . . .
@manekimelikawaii @officially-shadowwolfmemes @9mysterybook6 @dazzle-expandism @nicky-toony27 @torrentialchaos @lunawolf012306 @xxxlawrencexxx @art1c-m0nk3ys @foreverautisticbrainrot @potato31415926 @jamesjexxisdeadlmao @nicky-toony27 @mr-freakyystarz @loki104-uwu @mythically15 @paintywolf @softpawsxd
#i’m sorry#discord#discord stuff#vent#vent post#personal vent#vent blog#I’m no longer using discord because of it
38 notes
·
View notes
Text
A United States Customs and Border Protection request for information this week revealed the agency’s plans to find vendors that can supply face recognition technology for capturing data on everyone entering the US in a vehicle like a car or van, not just the people sitting in the front seat. And a CBP spokesperson later told WIRED that the agency also has plans to expand its real-time face recognition capabilities at the border to detect people exiting the US as well—a focus that may be tied to the Trump administration’s push to get undocumented people to “self-deport” and leave the US.
WIRED also shed light this week on a recent CBP memo that rescinded a number of internal policies designed to protect vulnerable people—including pregnant women, infants, the elderly, and people with serious medical conditions—while in the agency’s custody. Signed by acting commissioner Pete Flores, the order eliminates four Biden-era policies.
Meanwhile, as the ripple effects of “SignalGate” continue, the communication app TeleMessage suspended “all services” pending an investigation after former US national security adviser Mike Waltz inadvertently called attention to the app, which subsequently suffered data breaches in recent days. Analysis of TeleMessage Signal’s source code this week appeared to show that the app sends users’ message logs in plaintext, undermining the security and privacy guarantees the service promised. After data stolen in one of the TeleMessage hacks indicated that CBP agents might be users of the app, CBP confirmed its use to WIRED, saying that the agency has “disabled TeleMessage as a precautionary measure.”
A WIRED investigation found that US director of national intelligence Tulsi Gabbard reused a weak password for years on multiple accounts. And researchers warn that an open source tool known as “easyjson” could be an exposure for the US government and US companies, because it has ties to the Russian social network VK, whose CEO has been sanctioned.
And there's more. Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
ICE’s Deportation Airline Hack Reveals Man “Disappeared” to El Salvador
Hackers this week revealed they had breached GlobalX, one of the airlines that has come to be known as “ICE Air” thanks to its use by the Trump administration to deport hundreds of migrants. The data they leaked from the airline includes detailed flight manifests for those deportation flights—including, in at least one case, the travel records of a man whose own family had considered him “disappeared” by immigration authorities and whose whereabouts the US government had refused to divulge.
On Monday, reporters at 404 Media said that hackers had provided them with a trove of data taken from GlobalX after breaching the company’s network and defacing its website. “Anonymous has decided to enforce the Judge's order since you and your sycophant staff ignore lawful orders that go against your fascist plans,” a message the hackers posted to the site read. That stolen data, it turns out, included detailed passenger lists for GlobalX’s deportation flights—including the flight to El Salvador of Ricardo Prada Vásquez, a Venezuelan man whose whereabouts had become a mystery to even his own family as they sought answers from the US government. US authorities had previously declined to tell his family or reporters where he had been sent—only that he had been deported—and his name was even excluded from a list of deportees leaked to CBS News. (The Department of Homeland Security later stated in a post to X that Prada was in El Salvador—but only after a New York Times story about his disappearance.)
The fact that his name was, in fact, included all along on a GlobalX flight manifest highlights just how opaque the Trump administration��s deportation process remains. According to immigrant advocates who spoke with 404 Media, it even raises questions about whether the government itself had deportation records as comprehensive as the airline whose planes it chartered. “There are so many levels at which this concerns me. One is they clearly did not take enough care in this to even make sure they had the right lists of who they were removing, and who they were not sending to a prison that is a black hole in El Salvador,” Michelle Brané, executive director of immigrant rights group Together and Free, told 404 Media. “They weren't even keeping accurate records of who they were sending there.”
The Computer of a DOGE Staffer With Sensitive Access Reportedly Infected With Malware
Elon Musk’s so-called Department of Governmental Efficiency has raised alarms not just due to its often reckless cuts to federal programs, but also the agency’s habit of giving young, inexperienced staffers with questionable vetting access to highly sensitive systems. Now security researcher Micah Lee has found that Kyle Schutt, a DOGE staffer who reportedly accessed the financial system of the Federal Emergency Management Agency, appears to have had infostealer malware on one of his computers. Lee discovered that four dumps of user data stolen by that kind of password-stealing malware included Schutt’s passwords and usernames. It’s far from clear when Schutt’s credentials were stolen, for what machine, or whether the malware would have posed any threat to any government agency’s systems, but the incident nonetheless highlights the potential risks posed by DOGE staffers’ unprecedented access.
Grok AI Will “Undress” Women in Public on X
Elon Musk has long marketed his AI tool Grok as a more freewheeling, less restricted alternative to other large language models and AI image generators. Now X users are testing the limits of Grok’s few safeguards by replying to images of women on the platform and asking Grok to “undress” them. While the tool doesn’t allow the generation of nude images, 404 Media and Bellingcat have found that it repeatedly responded to users’ “undress” prompts with pictures of women in lingerie or bikinis, posted publicly to the site. In one case, Grok apologized to a woman who complained about the practice, but the feature has yet to be disabled.
A Hacked School Software Company Paid a Ransom—but Schools Are Still Being Extorted
This week in don’t-trust-ransomware-gangs news: Schools in North Carolina and Canada warned that they’ve received extortion threats from hackers who had obtained students’ personal information. The likely source of that sensitive data? A ransomware breach last December of PowerSchool, one of the world’s biggest education software firms, according to NBC News. PowerSchool paid a ransom at the time, but the data stolen from the company nonetheless appears to be the same info now being used in the current extortion attempts. “We sincerely regret these developments—it pains us that our customers are being threatened and re-victimized by bad actors,” PowerSchool told NBC News in a statement. “As is always the case with these situations, there was a risk that the bad actors would not delete the data they stole, despite assurances and evidence that were provided to us.”
A Notorious Deepfake Porn Site Shuts Down After Its Creator Is Outed
Since its creation in 2018, MrDeepFakes.com grew into perhaps the world’s most infamous repository of nonconsensual pornography created with AI mimicry tools. Now it’s offline after the site’s creator was identified as a Canadian pharmacist in an investigation by CBC, Bellingcat, and the Danish news outlets Politiken and Tjekdet. The site’s pseudonymous administrator, who went by DPFKS on its forums and created at least 150 of its porn videos himself, left a trail of clues in email addresses and passwords found on breached sites that eventually led to the Yelp and Airbnb accounts of Ontario pharmacist David Do. After reporters approached Do with evidence that he was DPFKS, MrDeepFakes.com went offline. “A critical service provider has terminated service permanently. Data loss has made it impossible to continue operation,” reads a message on its homepage. “We will not be relaunching.”
14 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
Hacker Denki's fav way to get into any system is usually by social engineering and phishing. He has SOOOO much fun making fake emails or pretending to be someone else in order to get some information. He has a silver tongue you know, can sweet talk anyone into anything over the phone. Once he got the entire server key code and serial model thanks to a helpful security guard who thought Denki was head of IT. It made his life real easy.
He has at least four burner phones on him at a time and is constantly looking at his boss's long list of potential targets. Sometimes it can take a few months before someone takes the bait and other times it's his first phone call and he can sit in the system for months. Collect data as if it were gold and store it all on one of his many neatly labeled external hard drives. Although his system is meant to be understood by his brain only to ensure his safety, not that his new boss, you, would ever do anything to harm him.
After scrolling socials or gleaming information from open windows, or an initial phishing to get in, he can study the institutions processes and systems. What they use and how it looks, snag a couple screen shots that he can eventually manipulate into a very neat page that looks like a carbon copy. He can get an IT person's name and spoof their email to send out the "update" or if he was lucky he can send the update directly to his target who will easily log in and give Denki his user and password, not to mention how he authenticates, which will be easy once he knows what app they use and of course he has their cell phone number by now.
All while he has Sims running in the background on one of his many laptops.
30 notes
·
View notes
Text
Patrick Beuth, Jörg Diehl, Roman Höfner, Roman Lehberger, Friederike Röhreke, and Fidelius Schmid at Der Spiegel:
Private contact details of the most important security advisers to U.S. President Donald Trump can be found on the internet. DER SPIEGEL reporters were able to find mobile phone numbers, email addresses and even some passwords belonging to the top officials. To do so, the reporters used commercial people search engines along with hacked customer data that has been published on the web. Those affected by the leaks include National Security Adviser Mike Waltz, Director of National Intelligence Tulsi Gabbard and Secretary of Defense Pete Hegseth. Most of these numbers and email addresses are apparently still in use, with some of them linked to profiles on social media platforms like Instagram and LinkedIn. They were used to create Dropbox accounts and profiles in apps that track running data. There are also WhatsApp profiles for the respective phone numbers and even Signal accounts in some cases. As such, the reporting has revealed an additional grave, previously unknown security breach at the highest levels in Washington. Hostile intelligence services could use this publicly available data to hack the communications of those affected by installing spyware on their devices. It is thus conceivable that foreign agents were privy to the Signal chat group in which Gabbard, Waltz and Hegseth discussed a military strike.
Numbers Linked to Signal Accounts
It remains unclear, however, whether this extremely problematic chat was conducted using Signal accounts linked to the private telephone numbers of the officials involved. Tulsi Gabbard has declined to comment. DER SPIEGEL reporting has demonstrated, though, that privately used and publicly accessible telephone numbers belonging to her and Waltz are, in fact, linked to Signal accounts. [...] The White House confirmed the scandal after the fact. Trump insisted that it did not include classified content, a question that is of particular relevance since members of the U.S. government are not permitted to share such information over Signal. The U.S. special envoy for Ukraine and the Middle East, Steve Witkoff, was even in Russia while participating in the chat group.
DER SPIEGEL was able to find some of the contact information for Gabbard, Hegseth and Waltz in commercial databases, while other information was in so-called password leaks, which are hardly a rarity on the internet. One example is the 2019 discovery by Troy Hunt, who found 773 million email addresses and more than 21 million passwords in a hacker forum. Since then, there have been numerous additional leaks. Criminals are constantly compiling new collections from hacks, usually to sell them on forums. [...] The mobile number provided, meanwhile, led to a WhatsApp account that Hegseth apparently only recently deleted. The profile photo showed a shirtless Hegseth in a baseball cap and necklace. Comparisons with other photos of the U.S. secretary of defense using facial recognition software were able to confirm that the photo on the WhatsApp profile was indeed Hegseth.
Several Passwords in Leaked Database
Waltz’s mobile number and email address could be found using the same service provider. The mobile phone number could even be found using a people search engine popular in the U.S. DER SPIEGEL reporters were also able to find several passwords for Waltz’s email address in leaked databases. The information also led to Waltz’s profiles for Microsoft Teams, LinkedIn, WhatsApp and Signal. National Intelligence Director Gabbard was seemingly more careful with her data than her two male colleagues. She apparently had her own data blocked in the commercial contact search engines that contained the data of Hegseth and Waltz. But her email address was to be found on WikiLeaks and Reddit. Gabbard’s email address is available in more than 10 leaks. One of those also contains a partial telephone number, which, when completed, leads to an active WhatsApp account and a Signal profile.
German publication Der Spiegel writes that several of the National Security Advisers for the Trump Administration, including Pete Hegseth, Tulsi Gabbard, and Michael Waltz, had their private data breached and the passwords found online.
#Der Spiegel#Pete Hegseth#Tulsi Gabbard#Michael Waltz#National Security#Trump Administration II#Yemen Signal Leak#Data Breaches#Steve Witkoff#Jeffrey Goldberg#Signal#John Ratcliffe
7 notes
·
View notes
Text
Hey Neighbor PT 10
WC:1.3k~
Previous
AO3 page
Toji
“So what exactly are you wanting me to do, sir?” the lanky male asks Toji. The computer opened and reflected in his oversized glasses.
“I am curious myself,” Shiu sits with his ankle over his knee, staring at Toji from across the kitchen table. “Your text from last night was quite unexpected”
Toji is seated with his forearms braced on the table, a slight frown on his face and a tiredness in his eyes. Which was to be expected since he hadn’t slept a wink the previous night. His mind spun from thoughts of you and this mysterious guy that had interrupted his owning up everything to you. He battled back and forth with his mind–should he really try to find out who this was or should he allow you to live your life and make your own choices? As the sun peaked over the horizon, he came to the middle ground, sorta. He’d find out who this guy was, but that was it! No background checks, no sending out people to his house, and definitely not wiping him off the planet and out of your life. Just a normal hacking of a phone.
“I need to see messages on y/n phone.” Toji answers.
Shiu’s eyes widen, taken back for a moment. Then, his face turns to one of joy. “Ah, already? The agreement must’ve been–”
“This isn’t about the agreement,” Toji interrupts, brusquely. He turns towards the hacker. “Just tell me you can do it.”
The hacker wrings his hands over his keyboard, clearly nervous in the presence of the infamous Toji Fushiguro. “Uhm, I can put spyware on it? Do you have the phone?”
“No, do it remotely. She uses an Apple phone and computer. I’m sure she has messages coming through her computer on the messaging app.” He demands.
“If we are in the range of her wifi, I can crack through her password, and then the software can gather all her credentials–logins and passwords. Then, we just enter those into the messaging app.” The hacker spoke quickly, clearly excited to show off his abilities.
“Do it,” he orders.
~
A day off work was never really a day off. Being so busy with work and honestly being lazy, the house chores had fallen behind. Though you have been living here for a few months now, the house still screams “Grandmother’s house.” You just hadn’t had the heart or the mental strength to get rid of things. Grief made you hang on to it as much as possible Until the smell of her house was replaced with your soft vanilla and lavender smell. You started in the bedroom, packing away old clothes to take to donation centers and replacing the bed sheets with ones that were more you—A soft purple comforter and an overabundance of pillows.
After folding the new bath towels and placing them in the upstairs hallway closet, you look up at the ceiling and the hatch to the attic ladder. You had been dreading going up there for a few reasons. Spiders, dust, dirt, mold, and the wild idea that someone might be up there living for all you knew. Another reason was what you DID know was up there. Pictures, memories of people you would never see again, and memories of moments you’ll never experience. But, today was the day. It had to be done.
Straightening your shoulder, you pull the string and allow the ladder to unfold to the floor. Surprisingly, no dead bodies tumbled down and no clouds of dust poured. You climbed the stairs, holding your phone as a flashlight. Once at the top, you notice it’s not the crypt you expected. It could be a spare room, the floors barely showed signs of neglect, neat stacks of books in the corner, and enough room to stand. Another string hung from the rafters to a light that still worked.
Getting to work, you pull dusty boxes from the corners, carry them to the floor below, gather the books to sort through and sweep the floor. Once satisfied with your cleaning, you gather your supplies and turn off the light. You switch all the supplies to one hand as you shuffle to the ladder.
The canister of furniture polish slips from your arm and rolls to the side of the attic. You chase after it, using your phone light again in the dark. The light bounced off the can and another glint of metal on the wall you hadn’t noticed.
Upon further inspection, you see a small gap in the wall, metal peaking out behind it. Using your phone light, a two-foot by two-foot section of the wall seems to be cut into the wall. YOu dig your finger into the exposed groove and gift it a sideways push. After getting stuck a few times, the panel recedes into the wall at the right, and the content behind it is revealed.
A silver safe about the size of a mini fridge sits behind the wall, a thin layer of dust coating it. A keypad blinks in the upper corner. You take a chance and attempt to pull the handle, hoping it would open—another part of you hoped it wouldn’t. Scared to see what was in it.
After 3 more tugs of the handle, you give up. It clearly needs a passcode. You try a few—1234, 11111, 2222 —-- before again giving up in case it had a system that locked it completely for an undetermined amount of time.
Finally, you climb back down the ladder, Confused, which seems to be your everyday emotion these days. You might as well have a giant question mark above your head
What the fuck is going on?
Toji
“I was able to hack into her cloud and find her contacts. I reverse-searched the number of the last message she received. It comes back to a Connor J. Falco but it appears he’s gone by a multitude of aliases. Here are some of the text messages I was able to—”
“I’m not going to read her messages, just give me what info you have on the guy,” Toji interrupts, slightly closing the laptop that the hacker had rotated around for him to see.
“Isn’t your concern that she is…involved with this man? Romantically?” Shiu chimes in from the living room where he is sitting on the floor with Megumi, playing with action figures. “ I believe I’d want to know what they were discussing, hmmm?”
“That’s—her business,” Toji replies, knowing how ridiculous it sounds.
“Doesn’t hacking into her phone inadvertently—”
“Just give me info on the guy,” Toji says to the hacker. He knows it doesn’t make sense. He tries to ease the guilt of spying by telling himself it’s only half spying. And it’s not spying on you, you were just the obstacle to get to the real prey. He wouldn’t read any of your messages or look through your photos and social media. That’s where he drew the line—the very thin one.
“Connor J Falco is an independent contractor, though I can’t find anything about what exactly he is contracted to do. Small online presence, just moved to town from overseas. No criminal records, no past traffic infractions.”
“See? An upstanding citizen.” Shiu laughs. “Completely harmless.”
“However,” the hacker clears his throat. “That’s just for Connor.”
“What do you mean?” Shiu stands behind the laptop.
“His other alias,” Toji answers. He knew this was what would happen. Whatever persona this guy was showing y/n was no doubt clean. It was his other personas that worried him.
“Correct. And Dmitri Sokolov?” The hacker nods and turns the laptop around for Toji to see. “He has quite a disturbing criminal history.”
Toji slides the laptop closer, clicking through the pages of court records and mugshots both international and domestic. From white-collar to violent crimes. His heart hammers in his chest. These weren’t petty crimes, this guy has experience.
“Shit.”
#Hey neighbor#toji fushiguro#Toji fushiguro reader#jjk#jujutsu kaisen#jjk x reader#jjk x you#jjk reader#jujutsu kaisen x reader#jujutsu kaisen x you#jujutsu kaisen smut#jujutsu kaisen angst#Toji fushiguro jjk#Toji fushiguro x reader#Toji fushiguro x you#Toji fushiguro headcanon#Toji fushiguro smut#Toji fushiguro fluff#dilf toji#dad toji#protective toji#Toji fushiguro you#Toji fushiguro angst#Toji fushiguro fic#megumi fushiguro#jjk toji smut#jjk toji fushiguro#toji zenin#toji zenin reader
33 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
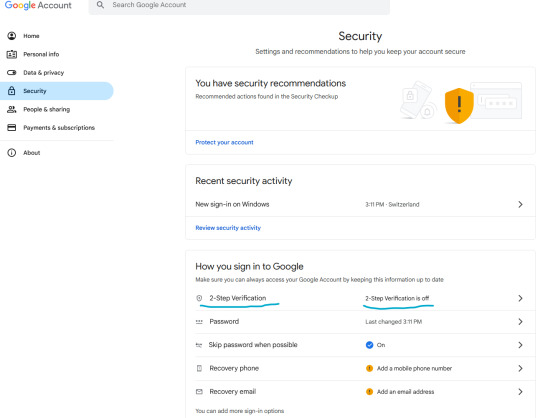
Let's enable two-step verification first.
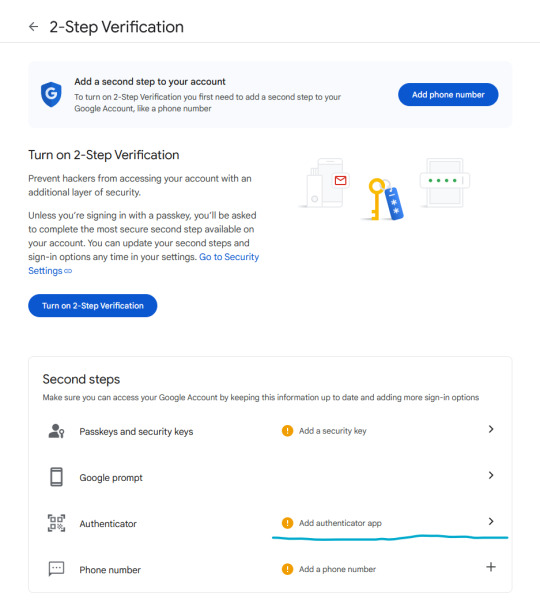
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
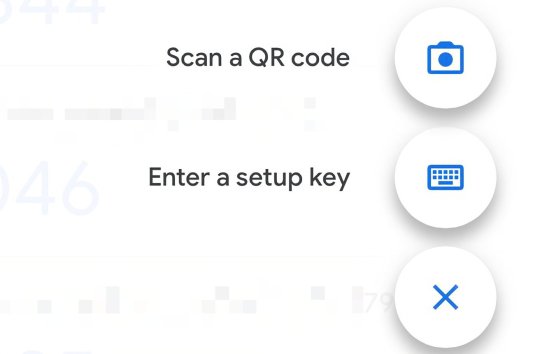
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
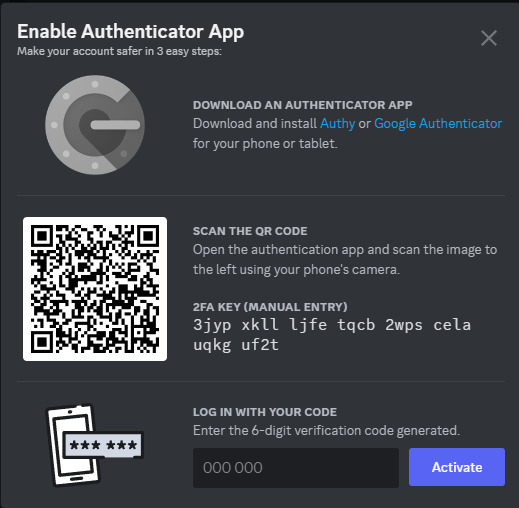
Download Google Authenticator if you haven't already. Scan the QR code as described above.
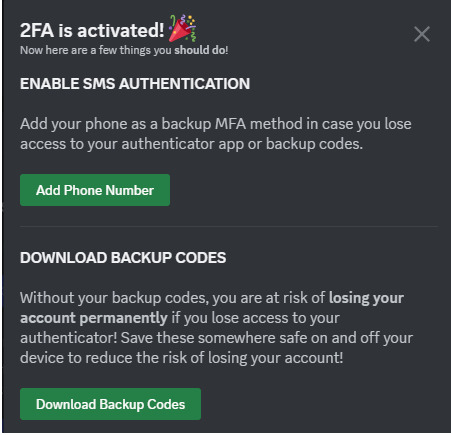
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
38 notes
·
View notes
Note
1. Tubbo confirm himself in the clip that he only kissed her, to which she later confirmed it too. As pre the video
Tubbo made the video and She would confirm it AFTER the hacker had allegedly made the post.
Let me help you, hacker did their job -> Tubbo made the video -> She confirmed it. Then how did the hacker make such a lucky guess about what happened that night in Tubbo's house?
I didn't have to go past the first point for it. Didn't even use my two degrees on Physics. Can't believe what they are feeding these IT students these days ....
"HoW dId The HaCkEr MaKe SuCh A LuCky GuEsS?"
THE VIDEO IN QUESTION WAS FILMED WAS FILMED A YEAR AGO OF HIM AT A PARTY WITH HER, AND ALL HER FRIENDS AS THEY DRANK
youtube
My goodness it would take a genius to be like "Hey I'm making allegations that they both got drunk (as shown in he video from a year ago) and Tubbo S/A her while drunk"
To which they allegations never specified WHERE THEY WERE it only specified part they were at
So Tubbo, confused as fuck Tubbo, said they came to there place, kissed and then talked about Jazz
Them going back to Tubbo's place wasn't even in the original allegations
Bitch if I went to a party, got drunk, PUBLICLY POSTED ABOUT IT ONLINE, and then someone was like "(me) was harassed by xyz", I'D BE SO FUCKING DUMB BECAUSE THEIR EVIDENCE WOULD BE THE VIDEO FROM A YEAR AGO. WHY THE FUCK WOULD SOMEONE INCRIMINATE THEMSELVES
Now dear clear idiot. I shall explain how 2-step verification works and how it didn't work in this case. AhEm
1. 2-Step Verification is as it sounds, in which after attempting to log on to a platform, the platform holders will either send a text message (through phone number) , email/gmail/AOL (if your old), notification or another form of communication to ensure the person login in is actually, ya know, you.
2. 2-Step Verification became a thing on TikTok, official and refined, on February 2025 (very late tbh)
3. Your young people don't know that back in my day TikTok didn't exist. OMG HOW COULD THIS BEEE??? Because it was called Musicly before it rebranded to tiktok
And since Musicly was primarily a kids/teens/young adults app, who tf is hacking a child's account?? Ya know?
So up until before that point Musicly also didn't have 2-Step Verification. Which is important because that means this security measures didn't transfer over because they didn't exist
4. Listen Leandra is by no means old. But I will rest a hand on your shoulders when I say, Gmail was created in 2004

And if you were a kid/teen around that time, you were young enough to get a Gmail with your actual name, like full legal, government, on yo birth certificate name
Why this important? Because if your primary Gmail/email/AOL, if your full legal name or part legal name, then people have a higher chance of just guess your email or, putting down "forgot password", then linking it to their email address, getting the rights to change the password and then bam.
The only way this cannot happen is if you manual lock your Gmail to only known devices (but fr that takes to long ngl and plus you won't be able to work on something if you can't access the device that has the rights to your email and additionally if you lose that device then it's game over, try again, pack it tf up)
So if she made her Tiktok account via any of the emails, then it's done, sorted, etc...
4.1. Now let's say she made it with her phone number like Tubbo suggested.
You could gain access further:
Having the email/gmail/AOL be linked with your phone number as a contact/emergency contact (idk in what case Google would hit you up but they can ig)
Phising. Look it up. It's spelt with a PH but pronounced fishing. And it's much more common then you think
The most popular phone plan providers in the UK are EE and Vodafone, inwhich if you get a new SIM card in a new phone, you can call them to change the new SIM phone number back to your older on as I'd be more convenient. The thing is, literally anyone could call. Like anyone, all you really need is the either the email/gmail/AOL, or the make and model of the phone, to answer some relatively personal questions (which you can lowkey guess ngl), or live in the same area or they just say screw it and change the number. It's often very useful but THE MOST ANNOYING THING when someone tries to access your account, and depending on WHEN and WHERE you get the card they don't even send you a confirmation text because they assumed your the one calling.
But anyways, you'd only need to realistically find out the first few numbers of her phone number, if you went with this method, trial and error'd it till you got on that's active and you can at minimum text, then just straight up try to login in or call them.
This is a great time to mentioned that Snapchat is lowkey, unintentionally screwing people over with this, because you can check if someone has a Snapchat by their contact or trying to sign in with that phone number cause it'll say the numbers is already in use.
BUT ANYWAYS, it takes about 2-6 weeks to gain access to someone's phone number or Gmail/AOL/Email if they're born pre-2000s to early 2000s
My point being, you could just guesstimate her really name by putting it through bots, checking old posts, being in personal contact with them or like reallllyyyyy putting the effort into guessing
And this is why people are often told to regularly update or change both passwords, email/gmail /AOL password and even update their names to avoid this.
5. Leandra made her social media around 2023, for her official Lovejoy shenanigans, idk what they do tbh
And I'm in no way calling her old... But she's gotta be like minimum 2-6 years older then me putting her in the bracket of people who can get a G/E/AOL (I'm getting tired of writing I tbh) with their actual names
And since 2-Step Verification was a 2025 update on TikTok, it's likely that some people just don't have it because they're too lazy to update or set it up. But even then their are many ways to get around it.
I recommend looking at the BBC guide/explanation of multi-factor verification/ two step verification/ multi-factor verification: https://www.bbc.co.uk/programmes/articles/5VbNf6z14LS7bZ02L1NXcjG/how-to-set-up-two-factor-authentication
And to Look at this BBC bitesize link if you want to know more: https://www.bbc.co.uk/bitesize/guides/zf3bcj6/revision/6
And 6. To follow up on some misconception that I know you're probably gonna throw at me because let's be real here you just hate Tubbo and that's okay. You don't need to justify it, just dislike him and be done.
Misconception 1. For some reason people are saying that her Instagram and Snapchat were also hacked. I don't know if she has a Snapchat because I don't use it, but as for Instagram it has been confirm by many update accounts, people who know irl etc... That the insta is fine!
Misconception 2. Tubbo kissed her. Hahahahhahashhsshshslolklolol. Tubbo is gay, and it's been confirmed by both parties that she kissed him first, and apparently he freaked tf out. Because he's gay. And has been openly gay for like 1-3 years. Bit weird to call him not gay for getting a kiss from one women. Like girl do you not kiss your mom? Tf? No kissing the homies? Terrible friend you are.
Misconception 3. Tubbo cleared the allegations as well as her after the allegations were out... Because how tf are you meant to clear something that's didn't exist?
Misconception 4. The hacker got a lucky guess. Now. Stay with me here. Go find an AI prompter and type 'man and women get drunk at part, write something criminal' OR just use your imagination because you know they're at the same party from a video a year ago. And I literally peeped into my older siblings room and asked them "real talk, a man and women get drunk at a party and leave together, they get to his place and something criminal happens, what is that criminal thing?" LITERALLY the first thing they suggested. Murder was second and tax evasion strats were 3rd.
And finally 7. This is too you. Yeah anonymous asker. You.
Just like DM me because as funny as it is to post about this on twitter and laugh with moots, your cluttering up my page with unnecessary discourse. But your not gonna see this, are you?
Because you, yourself said you didn't read past my first previous point. Sooooooooooooooooooooo
But also also ALSO, if she's confirmed it didn't happen and he confirmed it didn't happen, and she confirmed she was hacked, as shown in screenshots above and previously, then why is this still a talking issue?
SHE LITERALLY SAID SHE WAS HACKED. IT WASN'T HER POSTING??
Like if you gonna be mad at Tubbo be mad that he's idk fight Sapnap or something
But you seem more upset that I'm suggesting the hacker could POTENTIALLY be a gnf fan or Wilbur fan by the way they're uproaring on Twitter. Need I remind you, humbly and respectfully, IT'S FUCKING TWITTER??!
I keep people on the loop, I ain't asking for your what ifs ngl. questions? Welcome. Petty insults and challenge stupidity? Nope.
As you can see with MUCH of my covering discourse and discussion content on both Twitter and Tumblr, I put allegedly on thing that are not 90% to 100% accurate, I stick it on rumours and provide both links and screenshot to back up point because I want to be as honest as possible.
Bro if my favourite mcyt was an asshole I'd hold them too it. If my favourite vtuber was a bitch I'd hold them too it.
But I've provided ample evidence both in my first post and this post with detailed explanation, links and breaking it down into sections, I EVEN LINKED EDUCATIONAL RESOURCES AND EXPLAINED EMAIL LORE AND WHY MILLENNIALS ARE ACTUALLY QUITE OLD
Like it's done. It's over. You ignorance, lack of real world perception, common sense, and critical thinking skills has lead you to a pre-made conclusion that please you and not the actual one. So congrats. Wish I could be that stupid.
And for the record, I got a 100% in both GCSE coursework units on Information Technology, covering a range of different topics including cyber security, and scored a 90% on the test (trust it hurts your hand writing that much)
Furthermore, I backed it up with links, educational links and screenshots reinforcing literally what I said/how it applies.
Don't doubt my intelligence. Doubt your own suckerrrr
2 notes
·
View notes
Text
*This is a synoptic account of a prodigious matter, with grave impact on Ms. Aborishade, that has been transpiring over some years and is ongoing — in effort to bury several miscarriages of justice (oppression and abuse) implicating our judicial system.
LAUNDRYSHARE INVENTOR Ahavel A. Aborishade

Ahavel/NeatTuck, LLC coined phrase Laundryshare trademark record (scheduled filing in Jan 2017).
invented and founded the multibillion-dollar laundryshare system and industry (like Uber's Rideshare) in 2014 <- [Link being blocked. See record in the Facebook app under ‘Page transparency’] and named the app NEATTUCK. She spent the first three years curating and outlining the system and methods of the would-be P2P, B2B, and P2B (peer-to-peer, business-to-business, and peer-to-business) globally implemented app before forming NeatTuck LLC, the business in January of 2017, and then hiring the appropriate constituents to bring her vision and her carefully mapped out blueprint for NeatTuck/Laundryshare to life.
youtube
youtube
NEATTUCK was unveiled to the world in the summer of 2018. A new industry disruptor was born.
Encoded within her ancestry, Laundryshare (NeatTuck) was part of Ahavel's gift to the world; to give the world an option to supplement their income with a little more ease and time for themselves and their families and to bridge the gap in several communities and industries. The positive, alleviated, and anticipatory responses garnered from the public when NeatTuck was unveiled to the world in July 2018 was just as she envisioned and intended it to be when she formalized it in 2014; anticipating the saturation of the rideshare and home-share [Airbnb] economy-sharing/gig economy industry.
⚠️Shortly after retaining IP (Intellectual Property) and business attorney Stephen Charles McArthur of McArthur Law in Los Angeles, CA, in January 2017 and filing the trademark for the name NeatTuck, with discerning description of the invention with the USPTO (United States Patent and Trademark Office), unprecedented activities (that were later traced to other new laundryshare apps) began.
🚨Unfortunately, in March of 2022, Ahavel's business storage unit containing her entire corporation's assets - 'Dominieren Corporation' [stored during the COVID-19 pandemic], her digital and physical intellectual properties, NEATTUCK’s business module and blueprints, her corporation's server [containing several other undisclosed and pending inventions and ventures such as ‘Valet Versus’ (another idea and app she invented in 2017) was intercepted and ultimately embezzled through means of hacking of both her personal and business files and cloud drives — the company’s server and CCTVs were all hacked; the entire company’s iCloud drives and Microsoft Cloud Drives as well as approximately two decades of Microsoft OneNote note books of her businesses and personal life, computers and cloud drives were transferred from and restricted from her [her own files] [virtually all of her files were transferred from all her devices and cloud drives to the hackers devices to gain access to several accounts, email accounts and passwords, her entire life’s records; to gain uncharted access to her entire existence, also in an effort to eradicate evidence of her extensive work and documented stages, journey, and process of her inventions, her music lyrics, poetry, her journals, several unpublished business ideas and personal works, and for implementation of all of them into their replicated copies of her creations; her intellectual properties] — privacy invasion and violations, voyeurism and wiretapping; other technological manipulations (including reporting NeatTuck’s social media pages and reducing NeatTuck’s social media profiles and follower numbers to devalue and diminish NeatTuck’s reach and Ahavel’s corporation work), and group efforts of harassment, aggravated stalking, gang-stalking, cyberstalking, cyberbullying, false, fraudulent, and fabricated documentation and accusations to others and authorities, several entrapment and false imprisonment attempts, endangerment, poisoning, various forms of domestic terrorism, smear campaigns, physical and cyber antagonizing and humiliation tactics, slander, libel, character assassination and vandalism, and forced ostracization and isolation [in survival mode; which grossly escalated after the untimely erasure* of her father, for gain, in 2020] across state lines, for years — in a continuous plot of narcissistic abuse, oppression and torture by a group(s).
⚠️She was robbed, exploited, and trafficked online with her hacked images and their doctored versions of them. Her stolen ID was used to create unauthorized accounts and online profiles, for nefarious and malicious intent, by the group(s) and hackers.
NEATTUCK was censored, shadow-banned, silenced, blacklisted, and she was blackballed, betrayed by her legal team, employees [who were an integral part of this plot(s)] and app developers with acceptance of clandestine “incentives”, engaging in corporate espionage and insider trading.
See Vocal Media\PROOF article: “Are any other organizations, institutions, societies, and key figures connected to Laurel Hess and her business partners or Gurtin Ventures at play here?”
21 MINUTES YOUTUBE VIDEO PROOF OF HACKING ACTIVITIES TRACED NOT ONLY TO HAMPR BUT TWO OTHER MAINSTREAM LAUNDRYSHARE COMPANIES - YouTube video embedded below and in article below.
B*n M****e and “group” brokered access to NeatTuck’s private pitch-deck for profit.
youtube
“Black lives should not only matter when we are dead. We should matter while we are living.” - Ahavel Aborishade
📌See more on Pinterest profile.




youtube




👆Correction / acknowledgment of punctuation oversight in video comment/text on slide three. 'Should be a comma in the first sentence, not a full stop.
#laundry#laundry app#Uberforlaundry#national laundry#Laundryshare#black history#female inventors#inventions#Ahavel#Ahavel Aborishade#Laundryshare Inventor#Laundryshare Inventor Ahavel#women in business#women in tech#corporate women#female entrepreneurs#Ahavel Aborishade Inventor#black inventors#inventors#technology#mobile technology#washer#side gig#work from home#economy#economy sharing#NeatTuck#NeatTuckApp#espionage#insider trading
2 notes
·
View notes