#password hacker software download
Explore tagged Tumblr posts
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
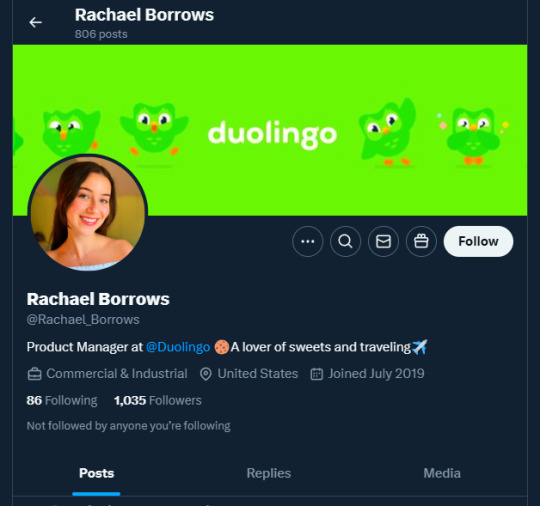
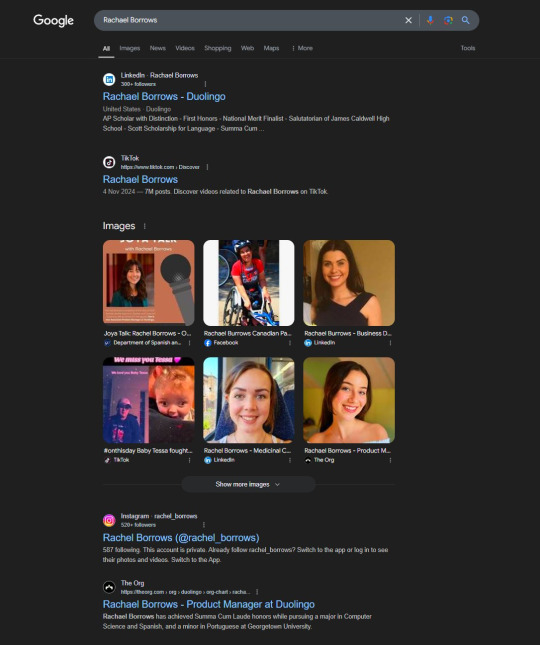
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
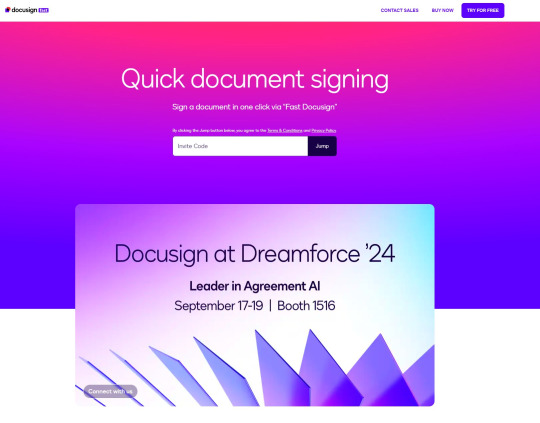
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
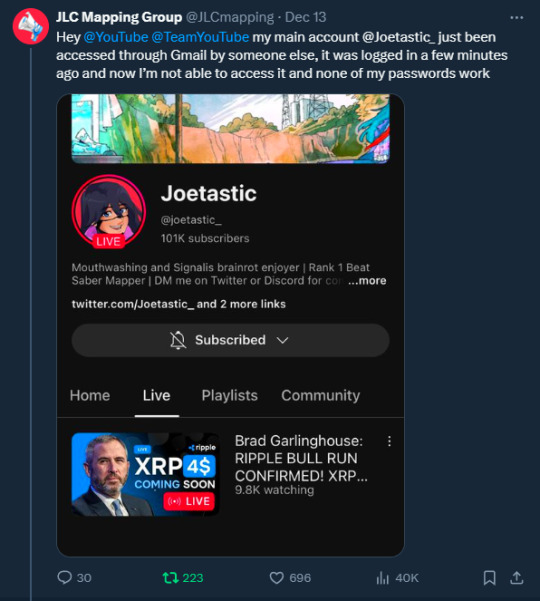
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
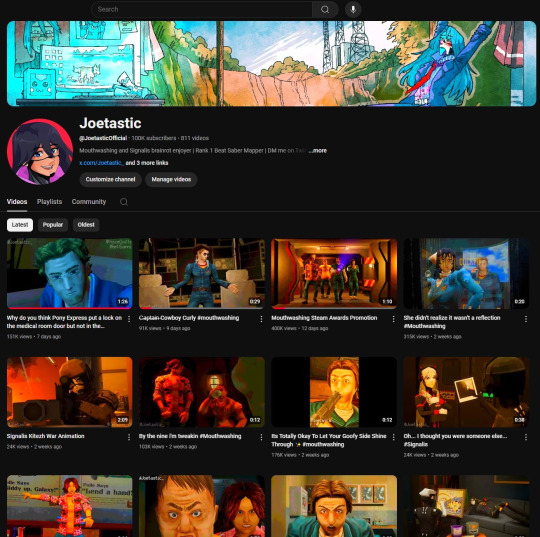
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
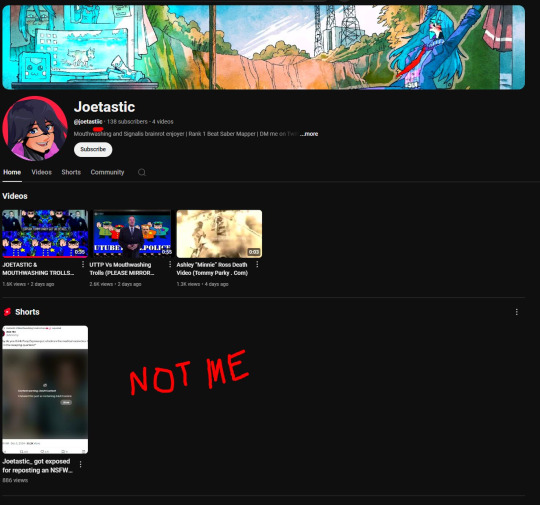
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
Hi everyone, I have a bit of an announcement to make. Nobody is in trouble, and yes I’m safe and okay. I just wanted to let everyone know that there may be a slight break or pause on art or emojis for a bit, as I have lost all of my digital art, wips, brushes, bases, YCHs, everything including Procreate. I hope to slowly come back over time.
It started with my iPad misbehaving and not allowing me to enter my password. I thought maybe I had simply forgotten my password of 6 years, and kept trying variations. I kept at this over the course of a few days, praying one of them would work. I was certain someone had tampered with my iPad, whether it was a hacker or family member I’m not sure. Today, I finally reached the dreaded “iPad unavailable” screen, meaning my absolute only option was to factory reset it and download a previous backup. So, of course I Googled and Youtubed everything I could, downloading software on my computer to try and fix everything. But my only option was to wipe it.
Once the deed had been done, I logged in and went to download a backup. Though I was presented with an issue; I had no backups (unless you count my mom’s current phone, as my iPad was still tied to her account). There was nothing from that point I could do to get everything back.
The only truly important things on there were my art things, since any photos had been saved or backed up elsewhere by now. I lost all of my Procreate data, including 6 years of art progress, references I had been working on for art fight next month, all of the emojis I have made and continue to use as bases, self portraits, drawings of pets that have since passed, fanart and gifts for friends, brushes I have made personally or downloaded myself, and a very detailed and extensive animatic I had been working on for about a year. All those frames, layers, and pixels are now lost.
It feels really bad, but also freeing. I have a fresh canvas to start from, and empty library to build up, and that’s exciting to me. I am finally off of my mother’s account and I have my own freedom for that device (yes I know it sounds silly), so hopefully I will try new things and feel a little more relaxed with my art.
All of this being said, art and emojis will likely be slow for a bit, if not completely halted for a few days or more. I’m not sure how long, I really want to keep creating but it’s probably gonna be difficult to face an empty Procreate (after paying the $13 fee again… yuck). I’m really sorry, but this is actually pretty difficult for me. But good at the same time.
In summary, my iPad went kaput and erased all of my data, including Procreate and my digital art. Nothing is recoverable. So I will be on a little art break until I can build everything back up again somehow.
Take care everyone, and thank you for reading.
#artists on tumblr#art#procreate#digital art#emoji blog#emote blog#whimsii yap#announcement#info#ipad
21 notes
·
View notes
Text
Cyber / Virtual ID Pack

Inside this pack, you will find: Pronouns, Titles, Names, and Genders that relate to Virtuality, Cybernetic, Robots, and anything alike!
This features a LOOOONG list of pronouns and dystopian-ish names!

Pronouns:
Cy/Cyb/Cyber/Cybers/Cyberself
Vir/Virt/Virtual/Virtuals/Virtualself
Ne/Net/Network/Networks/Networkself
Ne/Net/Nets/Nets/Netself
In/Inter/Internet/Internets/Internetself
Co/Comp/Computer/Computers/Computerself
In/Inpu/Input/Inputs/Inputself
Ou/Out/Output/Outputs/Outputself
Vi/Viru/Virus/Viruses/Virusself
Anti/Antivir/Antivirus/Antiviruses/Antivirusself
Er/Erro/Error/Errors/Errorself
Sys/Syste/System/Systems/Systemself
Pro/Proce/Processor/Processors/Processorself
Di/Digi/Digital/Digitals/Digitalself
Do/Down/Download/Downloads/Downloadself
Up/Uplo/Upload/Uploads/Uploadself
Cor/Corru/Corrupt/Corrupts/Corruptself
Mal/Malwa/Malware/Malwares/Malwareself
Se/Secur/Security/Securitys/Securityself
Cry/Crypt/Crypto/Cryptos/Cryptoself
We/Web/Webs/Webs/Webself
Web/Webs/Website/Websites/Websiteself
Fu/Futu/Future/Futures/Futureself
Ro/Rob/Robot/Robots/Robotself
Rob/Robo/Robotic/Robotics/Roboticself
By/Byt/Byte/Bytes/Byteself
Fi/Fil/File/Files/Fileself
Ra/Ram/Rams/Rams/Ramself
Scr/Scre/Screen/Screens/Screenself
Te/Tech/Techs/Techs/Techself
Te/Tech/Techno/Technos/Technoself
Tec/Techno/Technology/Technologys/Technologyself
Ma/Mach/Machine/Machines/Machineself
Wi/Wir/Wire/Wires/Wireself
Na/Nan/Nano/Nanos/Nanoself
Da/Dat/Data/Datas/Dataself
Plu/Plug/Plugs/Plugs/Plugself
Ele/Elect/Electric/Electrics/Electricself
Ke/Key/Keys/Keys/Keyself
Pa/Pass/Password/Passwords/Passwordself
Ter/Term/Terminal/Terminals/Terminalself
Cy/Cybo/Cyborg/Cyborgs/Cyborgself
Ty/Typ/Type/Types/Typeself
Fi/Firm/Firmware/Firmwares/Firmwareself
Ha/Hard/Hardware/Hardwares/Hardwareself
So/Soft/Software/Softwares/Softwareself
Ha/Hack/Hacks/Hacks/Hackself
Ha/Hack/Hacker/Hackers/Hackerself
Si/Sig/Signal/Signals/Signalself
Clo/Clou/Cloud/Clouds/Cloudself
On/Onli/Online/Onlines/Onlineself
In/Insta/Install/Installs/Installself
Co/Cod/Code/Codes/Codeself
Ad/Admi/Admin/Admins/Adminself
Gra/Graph/Graphic/Graphs/Graphself
Sy/Syn/Synth/Synths/Synthself
Phi/Phis/Phish/Phishs/Phishself
Phi/Phish/Phishing/Phishings/Phishingself
Do/Dox/Doxs/Doxs/Doxself
Si/Sit/Site/Sites/Siteself
Bo/Bot/Bots/Bots/Botself
Pho/Phon/Phone/Phones/Phoneself
Key/Keyboa/Keyboard/Keyboards/Keyboardself
Mo/Mou/Mouse/Mouses/Mouseself
Chi/Chip/Chips/Chips/Chipself
Moth/Mother/Motherboard/Motherboards/Motherboardself
Co/Com/Compute/Computes/Computeself
Pi/Pira/Piracy/Piracys/Piracyself
En/Encry/Encrypt/Encrypts/Encryptself
PDA/PDAs
CPU/CPUs
URL/URLs
404/404s
📱/📱's
💻/💻's
⌨️/⌨️'s
🖥/🖥's
🖱/🖱's
💿/💿's
🎙/🎙's

Titles:
The Cyborg
(X) Whos Wired
Made of Nanotech
(X) Who Uses Nanotech
Scholar of Machines
The Cyber Security
(X) Who Has Cyber Wings
Connected Online
Offline
Unable to Connect
The Administrator
Synthesizer
The Hacker
Nanohacker
The Antivirus
Reconnecting...
ERROR: Unable to Connect
ERROR 404
ERROR: Malware Detected

Names:
Since names don't usually have "techy" meanings, I picked one's that sounded the most cybernetic, cyberpunkish, dystopian, virtualish, etc!
Fem: Althea, Ameris, Astoria, Arcadia, Astra, Beretta, Cyra, Crystal, Crosselle, Eve, Io, Jinx, Kit, Lilith, Meridian, Morrian, Nebula, Nova, Neve, Noxia, North, Octavia, Odette, Odile, Prota, Pistol, Rey, Rue, Rain, Raine, Stormy, Seraphina, Sona, Skye, Thundra, Tempest, Vega, Viva, Vinette, Venus, Xenia, Xya, Xena, Xiomara, Xenara, Xanthe, Zephyria, Zyla, Zadie, Zia,
Masc: Alaric, Aksel, Arden, Antares, Apollo, Ace, Asher, Cole, Cyrus, Code, Draven, Drift, Ender, Flynn, Hawk, Isaac, Jericho, Kip, Kai, Koios, Knox, Nox, Neo, Nero, Octavian, Orionis, Oghma, Paine, Rocket, Ray, Rai, Silas, Slader, Sebastian, Seth, Seraphim, Thalax, Theo, Thatch, Vox, Vector, Wyatt, Xyon, Xane, Xylan, Xerxes, Xayden, Xavier, Xander, Zander, Zayden, Zenith, Zev, Zale, Zane, Zaire, Zeke,
Neu: Andras, Axe, Axiom, Alloy, Allele, Ash, Arrow, Beetle, Chrom, Corvus, Dakota, Dell, Eos, Echo, Eden, Fox, Ghost, Glöckner, Hydrae, Ion, Jesper, Jett, Kursk, Lesath, Locklyn, Lyrae, Maddox, Nemo, Orca, Onyx, Oxygen, Panther, Rikko, Robin, Rune, Scorpion, Scorpius, Saturn, Sparrow, Sonar, Tore, Tauri, Techne, Techno, Ursae, Vesper, Volt, West, Wolf, Xen, Xenon, Zephyr, Zodiac, Zenon, Zeru, Zero, Zen

Genders:
Futuracityc: A gender related to futuristic cities
Futurafashic: A gender related to futuristic fashion
Futurahousic: A gender related to futuristic houses
Digigender: A digital gender. Rangeable from any digital thing or file; virus, malware, .txt, .mp3, antivirus, trojan, email, etc.
Cybergender: A gender or form of gender expression where ones gender or expression is deeply tied into Cyberpunk lore, culture, fashion or media.
CYBERWEAPONIC - a gender that feels like a digital or robotic weapon. this gender may also have ties to sentient AI used as a weapon, but not necessarily.
BIOAMOROBOTIC - a gender connected to being a robot who loves humanity and the world and finds joy all around them!
RobAnatomic - a gender under the anatomic system(link) related to robots, anatomy, robotic anatomy, the anatomy of robots, robots made to teach/study anatomy, anatomy based/related robots of some kind, the anatomy/biology of someone or something being robotic, having robotic anatomy, being a robot with an interest in anatomy and more.
Robogender - for people who’s gender identity aligns with machines/robots/androids/mechs/AIs.
Cyborwebic - a gender related to webcore, evil scientist aesthetics, artificial beings such as androids/cyborgs etc, turtleneck sweaters and old computer monitors
AI flag - this can be used for nonhuman, otherkin, gender, delusion.
Gendervirtual / Genderdigital - a gendersystem in which your gender is related to virtual ) digital themes and x , such as being a virtual ) digital x , a x who loves virtual ) digital themes , a virtual ) digital being who loves x themes , etc.
#npt ideas#npt blog#npt pack#npt list#npt suggestions#cyber npt#virtual npt#robotic npt#robot npt#cybergender#virtualgender#robotgender#digitalgender
55 notes
·
View notes
Note
hey, i just found out about the forum, and while i admit i haven't checked it out myself yet, i have a couple questions that i'd love to ask.
how is the forum in terms of user privacy? are passwords stored in plaintext? (please tell me they aren't.)
related to that, how can we be sure the website won't be an easy victim to attacks? if the forum were victim of a cyber attack, would user accounts be compromised?
lastly, what do you think of implementing a rule similar to 4chan's "don't talk about 4chan"? if we want to keep the website hush-hush and less vulnerable to male infiltrators, it might be good to promote secrecy in some degree, maybe even encourage willful misnaming of the website (but i'd like to know what you think).
Hi. Please check out the cybersecurity page for tips on how to stay safe on the internet and especially when using the forum. If people are not comfortable with any chance of a database breach, I would recommend not making an account. While I would love people to join, I care about being honest and making sure people are aware and okay with the risks of participating.
how is the forum in terms of user privacy? are passwords stored in plaintext? (please tell me they aren't.)
Passwords are not stored in plaintext. However, I will say MyBB's (the forum software I'm using) password encryption algorithm is not the best, so if the database were breached, it would be relatively trivial for a hacker who knew what they were doing to decrypt user passwords. MyBB plans to use a better encryption algorithm in its next release, and switching to that once it is out will be a top priority for me. This is why I suggest using a unique password for this forum (and tbh on any website it is best to use a unique password, you never know where the next database breach will come from).
related to that, how can we be sure the website won't be an easy victim to attacks? if the forum were victim of a cyber attack, would user accounts be compromised?
All passwords for all administrative accounts/logins related to the forum, its database, its server, etc. are very long and randomly generated, and are completely different from each other. Password hacking would be extremely difficult, likely impossible.
The biggest way I could see user accounts becoming compromised would be through a database breach (getting access to the database). There are two ways I see this could happen:
Someone directly uses the server account credentials to log in and breach the database (highly likely impossible as they would need to know where the server is located and the password for the server).
Someone hacking into an administrator account on the forum and downloading the database. This would be the more likely route, but they would need to know the password of an administrator account. This is how Kodi, a MyBB forum with 400k users, got its database breached. However, there are multiple ways to avoid this. 1.) I found instructions on how to lock down the MyBB Admin CP (Control Panel) with an additional password, which would mean a hacker would need to not just hack into an admin's account, but also know the password to the Admin CP. 2.) There is another option of editing the forum source code so that the ability to download databases from the Admin CP is completely disabled. 3.) If any additional administrators are needed, I could give them adjusted permissions which would not allow them to create database backups. Overall though, I don't think I will need to add administrators any time soon, if ever. (Moderators are different than admins.)
In the worst case scenario of a database breach, what would be leaked is similar to the Kodi breach above. This is why on the Cybersecurity page, I say: use a unique password, don't use an important email, be wary of the private messaging system, etc.
lastly, what do you think of implementing a rule similar to 4chan's "don't talk about 4chan"? if we want to keep the website hush-hush and less vulnerable to male infiltrators, it might be good to promote secrecy in some degree, maybe even encourage willful misnaming of the website (but i'd like to know what you think).
Hmm, well I've already announced the forum on Tumblr, so it's not very hush-hush already. :') My view is that male infiltrators would try to get in regardless. I don't think I can stop people from talking/sharing the forum, and I would prefer feminist women be able to find it easier. I would like to hope the application process would weed out most bad actors.
4 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
All You Need To Know About KMSPICO

KMSpico is incredibly powerful and enables users to activate Microsoft products without paying the license fee. It works by mimicking a KMS server and using generic keys to activate Windows and other Microsoft software. You may get more details about windows by visiting kmspico download site.
Nevertheless, many antivirus software block KMSPICO from being installed as malware. This is because it defies security measures and requires users to disable their antivirus programs prior to installation.
What's kmspio?
KMSPICO is primarily a tool crafted by cyber criminals that allows users to install and use different Microsoft products without paying recurrently. It operates by mimicking the KMS server, which is used by Microsoft to authenticate products.
It is capable of altering internal Windows settings, which can negatively impact computer performance and security. Due to these factors, many antivirus programs view kmspico windows 11 as a threat and either prevent its download or caution users against running it.
To increase infection rates, KMSPICO developers commonly use infected websites that appear to be legitimate download portals, search engines, and software product pages. They may additionally "package" rogue software together with legitimate applications during the downloading and installation processes. Additionally, they may ask users to disable their anti-virus applications, which is another indicator of malware distribution.
Does kmspico do any work?
KMSpico is essentially a malware-free program designed to permit you to activate Microsoft products for free. This tool functions by mimicking a Key Management Server (KMS), which is typically employed for licensing large amounts of software. The program permits you to obtain a lifetime license for Windows and Microsoft Office without spending money. This can only be achieved if you download the program from reputable sites and carefully follow the instructions.
Unfortunately, those who distribute kmspico for windows 11 are not always diligent. The programs are often downloaded bundled with malware, including adware, browser hijackers, and even password-stealing ransomware. They are often distributed through hacker-controlled portals and ad campaigns.
youtube
Due to these problems, it can be challenging to obtain a clean version. However, it is certainly not impossible to achieve it entirely. In fact, the most recently released version of the program can be found on a members-only forum that was created over a decade ago. It is important to note that this site does NOT reside on Microsoft servers and has no official support for KMSPICO.
Learn How To Make Use Of Kmspico
KMSPICO is a program that helps you bypass Microsoft's restrictions on using its products. It can easily be used to activate Windows operating systems and other Microsoft office products within minutes without having to pay for them.
Unfortunately, this tool also acts as malware and can potentially inflict severe problems on your computer. It attempts to penetrate by exploiting the "bundling" method, where rogue software is installed alongside legitimate applications during the download and installation process.
Once installed, the program backs up the license information on your system software and creates a dedicated KMS server. Its main objective is to drive traffic and click-through revenue for its creators, and therefore, it displays annoying pop-up advertisements. Additionally, it can slip under the radar of other applications, making it challenging to remove. To uninstall it safely, you need to perform a complete system scan and remove all files associated with kmspico for windows 11.
How to eliminate KMSPICO?
KMSPICO is a malware that could pose significant security risks to the user. It is essentially a license bypass tool that modifies the product key of Microsoft software products and redirects the KMS server to one that is managed by its developer. This allows Microsoft software to be activated without purchasing a valid license.
Additionally, KMSPICO may inflict computer system viruses. For example, the hacking tool has been known to distribute STOP/DJVU ransomware versions. This malware version redirects the internet browser to infected web pages and takes sensitive information from the infected system.
The use and misuse of KMSPICO constitutes a punishable offense under the Digital Millennium Copyright Act (DMCA).
Users can uninstall it using a trusted antimalware program such as Zemana Anti Malware. Once the process is completed, the system will be restored to its previous state. Once the procedure is completed, the system shall be restored to its default state. Additionally, the program won't anymore redirect the browser to unused web pages.
2 notes
·
View notes
Text
How to prevent ransomware attacks a guide for Jacksonville organizations
How to Prevent Ransomware Attacks: A Guide for Jacksonville Organizations
Ransomware attacks have become a big problem for businesses of all sizes, including right here in Jacksonville. These attacks can lock up your important files until you pay a ransom, and even then, there’s no guarantee your data will be returned. But the good news is that there are simple steps you can take to lower the risk. Whether you're running a small shop or a larger company, being prepared can go a long way. We spoke to the folks over at nettechconsultants.com to gather a few helpful ideas.
Start with the Basics
First, make sure all your computers have up-to-date antivirus software. This helps stop bad software, like ransomware, before it has a chance to do any damage. It’s also important to keep all your systems – including Windows or Mac software – updated with the latest patches. Hackers love outdated systems because they’re easier to break into.
Train Your Team
Employees can accidentally welcome ransomware into your system by clicking suspicious links or downloading files from unknown email senders. Regular training can help your team spot these tricks early. Teach them to look out for emails that don’t feel right – maybe the wording is strange, or there's unexpected pressure to click on a link right away.
Back Up Your Data
One of the best defenses is having a backup of your important data. Store a copy in the cloud or on a separate device not connected to your main network. If you’ve got a backup, you won’t have to pay anyone to get your files back – you can simply restore them yourself.
Use Strong Passwords and Multi-Factor Authentication
Make sure each account has a strong password that isn’t easy to guess. Better yet, add an extra layer of protection by using something called multi-factor authentication. That’s where you need a password plus a code sent to your phone – this makes it much harder for hackers to break in.
Stay Alert
Ransomware methods are changing all the time, so stay up to date with what's going on. You don’t need to be a tech expert – just being curious and alert can make a big difference.
By taking these steps, Jacksonville businesses can protect themselves and their customers from the headaches of ransomware. A little effort now can save you a lot of trouble later.
0 notes
Text
The Ultimate Guide to Cyber Security for Companies in the Digital Age
In today's digital-first world, cyber security for companies has become more than just a technical necessity—it is a core part of business strategy. As organizations increasingly rely on technology for operations, communication, and data storage, the risks of cyberattacks grow exponentially. From small startups to large enterprises, no company is immune to the threat of hacking, data breaches, ransomware, and phishing. Strengthening digital defenses not only safeguards sensitive information but also protects brand reputation, customer trust, and operational continuity. This guide explores the essential aspects of cyber security for companies and why every business must invest in robust cyber protection strategies.
Understanding the Importance of Cybersecurity for Companies
Cyber security for companies is essential in safeguarding critical assets such as financial data, customer information, and proprietary technology. Without strong defenses, businesses face financial loss, legal consequences, and reputational damage. A single cyberattack can cripple operations and result in long-term fallout. Investing in cybersecurity is not just about prevention but also about resilience—ensuring a company can detect, respond to, and recover from incidents effectively. In a world where cyber threats evolve constantly, companies must prioritize security as a fundamental business function, integrating it into every layer of their organization and making it part of their long-term risk management strategy.
Key Threats Facing Businesses in the Digital Era
Cyber security for companies is increasingly challenged by sophisticated and persistent threats. Common dangers include phishing scams that trick employees into giving up credentials, ransomware that locks critical files, and insider threats that compromise sensitive data. Hackers also exploit outdated software and unpatched systems, gaining unauthorized access to business networks. With the rise of remote work and cloud services, attack surfaces have expanded dramatically. Small and medium-sized businesses are especially vulnerable, as they often lack dedicated IT security teams. To counter these evolving risks, companies must continuously monitor threat landscapes and adopt proactive measures to secure their digital environments.
Best Practices for Company-Wide Cyber Protection
Effective cyber security for companies involves adopting best practices across all departments and systems. This starts with conducting regular risk assessments to identify vulnerabilities and implementing firewalls, anti-malware software, and data encryption. Creating strong password policies, using multi-factor authentication, and regularly updating software are critical steps. Businesses should also establish incident response plans to act swiftly during breaches. Backing up important data regularly and securely storing it offsite ensures recovery after an attack. By fostering a culture of security awareness and embedding these practices into daily operations, companies can create a resilient cyber defense structure that minimizes exposure to threats.
Cybersecurity for Companies Begins with Employee Training
Human error remains one of the biggest vulnerabilities in cyber security for companies. Employees can inadvertently fall victim to phishing emails, download malware, or use weak passwords. Therefore, comprehensive training programs are vital. Regular cybersecurity awareness sessions help staff recognize suspicious behavior, understand safe browsing habits, and learn how to report incidents. Simulated attacks and real-life scenarios prepare teams to respond correctly during threats. Empowering employees with knowledge not only reduces risk but also fosters a collective responsibility for digital safety. A company’s cybersecurity is only as strong as its least informed employee, making training a cornerstone of defense.
Choosing the Right Cybersecurity Tools for Your Business
Selecting the appropriate tools is a crucial component of cyber security for companies. The right mix of software and hardware can protect against various threats and ensure compliance with data protection regulations. Businesses should consider endpoint protection, intrusion detection systems, firewalls, and secure email gateways tailored to their needs. Cloud security platforms and vulnerability scanners can further strengthen defenses. It’s also important to integrate security information and event management (SIEM) tools for real-time monitoring. Choosing scalable solutions that grow with the business helps avoid gaps in protection. With expert consultation and regular evaluations, companies can ensure their tools remain effective.
How Cybersecurity Policies Help Protect Company Data?
Strong policies form the backbone of effective cyber security for companies. A well-defined cybersecurity policy outlines protocols for handling data, accessing systems, and responding to security incidents. It ensures that all employees, vendors, and contractors adhere to strict guidelines that reduce risk. These policies should address data classification, acceptable use, mobile device management, and incident reporting procedures. Regularly reviewing and updating the policy ensures it adapts to new technologies and emerging threats. When enforced consistently, cybersecurity policies create accountability, promote compliance with legal standards, and protect the organization’s most valuable digital assets from unauthorized access or accidental leaks.
Future Trends in Cybersecurity for Companies
The future of cyber security for companies is shaped by emerging technologies and increasingly complex threats. Artificial intelligence (AI) and machine learning are transforming threat detection by identifying anomalies faster than ever. Zero-trust architecture, which verifies every user and device before granting access, is gaining traction. As businesses adopt Internet of Things (IoT) devices, securing interconnected systems becomes essential. Quantum computing also poses new challenges for encryption methods. Companies must stay informed about these trends and continuously innovate their defenses. By investing in adaptive technologies and future-proof strategies, businesses can stay one step ahead of cybercriminals in the years to come.
Conclusion
Cyber security for companies is no longer optional—it's an essential aspect of modern business operations. With cyberattacks growing in sophistication and frequency, companies must take proactive steps to protect their digital environments. This includes understanding potential threats, implementing best practices, training employees, and choosing the right tools and policies. The cost of inaction can be devastating, affecting revenue, reputation, and long-term viability. By treating cybersecurity as a strategic priority and staying ahead of evolving risks, companies can build a secure foundation for growth and innovation. A strong cybersecurity posture not only protects data but also ensures trust, compliance, and business resilience.
0 notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes
Text
Ransomware Attacks Vs. Data Breaches: What's the Difference?

In the fast-paced world of cybersecurity, terms are often thrown around interchangeably, leading to confusion and, more dangerously, misdirected defense strategies. Two prime examples are "ransomware attacks" and "data breaches." While both are devastating cyber incidents, they have distinct characteristics, primary objectives, and implications. Understanding the difference is crucial for effective protection and response.
Let's break down these common cyber threats.
What is a Data Breach?
A data breach occurs when unauthorized individuals gain access to sensitive, confidential, or protected information. The key here is unauthorized access and exposure or exfiltration of data. The data could be customer records, intellectual property, financial information, health records, or employee personal data.
Primary Goal of Attacker: The main objective of an attacker causing a data breach is typically to obtain data. This data can then be sold on the dark web, used for identity theft, competitive espionage, or financial fraud.
Method: Attackers gain entry through various means: exploiting software vulnerabilities, phishing for credentials, insider threats (malicious or accidental), misconfigured cloud services, or brute-forcing weak passwords. Once inside, they focus on finding, copying, and exfiltrating (stealing) the data.
Immediate Impact: The immediate impact might not be obvious. A data breach can go undetected for months or even years. When discovered, the impact includes reputational damage, regulatory fines (e.g., GDPR, HIPAA), legal liabilities, identity theft for affected individuals, and loss of competitive advantage.
Example Scenarios:
A hacker exploits a vulnerability in a web application to access and download a database of customer email addresses and passwords.
An employee accidentally uploads a spreadsheet containing sensitive client financial details to a public cloud storage service.
A misconfigured firewall allows external access to an internal server holding proprietary source code.
What is a Ransomware Attack?
A ransomware attack is a specific type of malicious software (malware) attack that encrypts a victim's files, systems, or entire network, rendering them inaccessible. The attacker then demands a ransom (almost always in cryptocurrency) in exchange for the decryption key that will unlock the data.
Primary Goal of Attacker: The primary objective is financial gain through extortion. The attacker wants money in exchange for restoring access to the victim's own data.
Method: Ransomware typically gains initial access via phishing emails, exploiting unpatched vulnerabilities, or through stolen credentials. Once inside, it spreads across the network, identifies valuable files, encrypts them, and then displays a ransom note.
Immediate Impact: The impact is usually immediate and highly disruptive. Operations grind to a halt due to inaccessible systems, leading to significant downtime, lost revenue, and often, substantial recovery costs (whether or not a ransom is paid). There's also the risk of permanent data loss if decryption fails or backups are insufficient.
Example Scenarios:
An employee clicks on a malicious link in a phishing email, and ransomware rapidly encrypts files on their workstation, then spreads to networked drives.
A vulnerability in a remote desktop protocol (RDP) is exploited, allowing attackers to deploy ransomware across an entire corporate network, locking down servers and individual computers.
Key Differences Summarized
Feature
Data Breach
Ransomware Attack
Primary Objective
To steal or expose data for financial gain, espionage, or other malicious use.
To deny access to data/systems and extort money for decryption.
Method
Unauthorized access, copying, viewing, exposure of data.
Encryption of data/systems, typically by malware.
Immediate Impact
Data compromise, potential long-term legal/reputational damage. Often goes undetected for a long time.
Immediate system downtime, operational disruption, data inaccessibility. Instantly visible.
Attacker's Leverage
Threat of data sale, public exposure, or misuse.
Threat of permanent data loss or prolonged system unavailability.
Resolution
Containment, investigation, data remediation, notification to affected parties.
System restoration from backups, decryption (if key obtained), forensic analysis.
Visibility
Often silent and stealthy.
Loud and immediately impactful.
Export to Sheets
The Critical Overlap: Double Extortion Ransomware
The distinction between these two threats has become blurred with the rise of double extortion ransomware. Modern ransomware groups often combine tactics:
First Extortion: They exfiltrate (steal) your sensitive data.
Second Extortion: They then encrypt your systems and demand a ransom for decryption. If you refuse to pay, they threaten to publish the stolen data on leak sites, compounding the pressure.
This means a single incident can now be both a ransomware attack and a data breach. This evolution significantly raises the stakes, as even robust backups cannot prevent the reputational and legal fallout of leaked sensitive information.
Why the Distinction Matters for Your Defense
Understanding the difference is not just an academic exercise; it directly impacts your cybersecurity strategy:
Tailored Defenses: Your defenses against data exfiltration (DLP, strong access controls, data classification) are different from those against data encryption (robust immutable backups, next-gen endpoint protection, network segmentation).
Incident Response: You need distinct, but often integrated, incident response playbooks for each scenario. The immediate steps for a ransomware attack (containment, backup recovery) differ from those for a suspected data breach (forensic investigation to determine scope of data compromise).
Legal & Compliance: Data breach notification laws are often triggered by the exposure or exfiltration of data, even if it wasn't encrypted. Knowing if data was stolen is paramount for legal compliance.
In conclusion, while ransomware attacks and data breaches are distinct in their primary mechanics and immediate impacts, they are increasingly intertwined. A truly robust cybersecurity strategy for any organization must encompass sophisticated defenses against both, along with comprehensive incident response plans that account for their potential overlap.
0 notes
Text
Mastering Information Security: A Comprehensive Guide to Protecting Your Digital Assets
In an age where data drives every decision and operation, the need to protect that data has never been more critical. Information Security, often abbreviated as InfoSec, refers to the set of practices, policies, and technologies that safeguard data from unauthorized access, misuse, or destruction. As cyber threats become more advanced, understanding and implementing strong information security protocols is no longer optional—it’s essential.
Understanding Information Security
At its core, Information Security focuses on protecting three fundamental aspects of information:
Confidentiality – Ensuring only authorized parties can access information.
Integrity – Maintaining the accuracy and trustworthiness of data.
Availability – Making sure information is accessible when needed.
These three pillars form what’s known as the CIA Triad, a foundational model in the world of information security.
The Importance of Information Security
Why is information security so crucial?
Data Protection: Prevents sensitive data such as financial records, customer information, and intellectual property from falling into the wrong hands.
Business Continuity: Ensures that operations can continue smoothly, even during cyber incidents or breaches.
Legal Compliance: Helps businesses meet data protection regulations like GDPR, HIPAA, and CCPA.
Reputation Management: Demonstrates a company’s commitment to privacy and trustworthiness, strengthening its brand reputation.
Financial Safeguard: Reduces the risk of fines, lawsuits, and loss caused by data breaches or ransomware attacks.
Common Threats to Information Security
To effectively defend against risks, one must understand the threats. Some of the most common include:
Phishing attacks – Deceptive emails tricking users into giving away credentials.
Ransomware – Malicious software that encrypts data and demands payment.
Insider threats – Employees misusing access either maliciously or accidentally.
Malware – Viruses, trojans, and spyware designed to damage or steal data.
Social engineering – Psychological manipulation to gain access to systems or information.
Information Security Strategies
Effective information security requires a multi-layered approach, including:
1. Access Control
Limit access to sensitive data using strong passwords, multi-factor authentication (MFA), and role-based access.
2. Encryption
Encrypt data both at rest and in transit to ensure that even if it’s intercepted, it remains unreadable.
3. Regular Updates & Patching
Ensure systems and software are updated regularly to close vulnerabilities exploited by hackers.
4. Employee Training
Human error is a leading cause of breaches. Regular training helps employees recognize phishing, use strong passwords, and follow security protocols.
5. Incident Response Plan
Having a response plan in place minimizes damage when a breach occurs and helps restore operations quickly.
6. Backups
Frequent backups stored in secure, offsite locations can save critical data in case of a cyberattack or system failure.
Information Security for Individuals
Information Security isn’t just for businesses—individuals must also protect their data:
Use unique, strong passwords for each account.
Enable MFA on all major platforms.
Avoid clicking suspicious links or downloading unknown files.
Use antivirus and anti-malware software.
Regularly monitor bank statements and credit reports.
The Future of Information Security
As technology evolves, so do threats. Here are some key trends shaping the future of information security:
Artificial Intelligence (AI): Used for real-time threat detection and automated responses.
Zero Trust Security: A model where no user is trusted by default, requiring continuous verification.
IoT Security: As smart devices proliferate, securing them becomes essential.
Quantum Computing: Potential to break current encryption, necessitating quantum-resistant algorithms.
Conclusion
In the digital world, data is one of your most valuable assets. Information Security provides the foundation for protecting that asset, whether you’re a multinational corporation or an individual user. By understanding threats, adopting best practices, and staying informed about new developments, you can build a secure environment that supports your goals and protects your future

0 notes
Text
Roblox Account Manager: Easy Multi-Account Management for Gamers & Developers
Roblox Account Manager is a specialized tool designed to help users handle multiple Roblox accounts effortlessly. Whether you're a competitive player, a developer, or a trader, switching between multiple accounts manually can be time-consuming and frustrating. This tool streamlines that process, allowing for quick access and easy management of multiple Roblox profiles.
Importance for Multi-Account Users
Gamers often maintain several Roblox accounts for trading, testing, or playing with different friend groups. Developers use alternate accounts for testing scripts or game functions. For these users, Roblox Account Manager is a game-changer, enabling instant login transitions and reducing the hassle of remembering multiple passwords.
2. What Is Roblox Account Manager and How Does It Work?
Core Functionality
Roblox Account Manager operates as a third-party desktop tool that stores login credentials securely and enables users to switch between accounts with just a click. Once accounts are added, users no longer need to log in and out repeatedly, saving time and improving productivity.
User Interface and Experience
The tool boasts a clean and intuitive interface. With a simple dashboard, users can view all saved accounts, rename them, and even assign profile pictures. Navigation is straightforward, making it accessible even for less tech-savvy users.

3. Key Features of Roblox Account Manager
Multiple Account Management
The main attraction is its seamless ability to handle multiple accounts. With just a click, you can jump from one Roblox account to another—ideal for competitive gamers or Roblox developers juggling different projects.
Enhanced Gaming Experience
Roblox Account Manager offers built-in support for FPS unlockers and other performance tools. It can also run multiple Roblox clients simultaneously, improving the gaming experience for those running alternate accounts at once.
4. Setting Up Roblox Account Manager
Installation Process
Setting up the tool is easy. Users need to download the latest version from a trusted source like GitHub. Once downloaded:
Extract the ZIP file.
Run the executable (.exe) file.
Follow the on-screen instructions to complete the installation.
Configuring Accounts
After installation, users can add new accounts by logging in once per profile. The manager securely stores the session so that you never need to re-enter your credentials unless you choose to. You can label each account for easy identification.
5. Security and Safety Considerations
Data Encryption
Roblox Account Manager employs secure encryption methods to protect your login data. Credentials are stored locally and encrypted, ensuring they aren’t accessible to hackers or third-party trackers.
Addressing Malware Concerns
Some antivirus software may flag third-party tools as potential threats. However, if downloaded from a verified and reputable source, Roblox Account Manager is completely safe. Always avoid cracked versions or shady download links.
6. Troubleshooting Common Issues
Login Problems
If the tool fails to log in or shows errors, the most common reasons include outdated session tokens or missing files. Simply re-enter your credentials or update the tool to resolve these issues.
Performance Optimization
To ensure the app runs smoothly:
Close unnecessary background apps.
Make sure you have enough RAM.
Keep the Roblox Account Manager updated.
These tips help maintain performance, especially when running multiple Roblox instances simultaneously.
7. Advanced Tips for Power Users
Running Multiple Instances
Power users can take advantage of the tool’s support for multi-client instances. This allows you to run multiple Roblox windows at the same time—a useful feature for item trading, dual-playing, or testing.
Customizing Settings
Roblox Account Manager allows users to tweak settings like FPS limits, client priority, and window positions. These adjustments help customize the experience to match your system’s capabilities.
8. FAQs About Roblox Account Manager
Is Roblox Account Manager safe to use?
Yes, when downloaded from a reputable source, the tool is safe and does not share data with third parties.
Can I use it on multiple devices?
Roblox Account Manager is primarily designed for Windows PCs. You’ll need to configure each device individually.
Does it support Mac OS?
As of now, it is not officially supported on macOS. Users may need to use a virtual machine or Windows emulator.
How do I update the application?
Updates are usually released on platforms like GitHub. Download the latest version and replace the old files.
What should I do if my accounts are not syncing properly?
Make sure your sessions haven’t expired. You may need to re-login to update the session information.
9. Conclusion
Summarizing Benefits
Roblox Account Manager offers a streamlined, efficient way to manage multiple accounts without constant logins. It’s secure, user-friendly, and perfect for gamers, developers, and creators who switch accounts frequently.
1 note
·
View note
Text
Cyber Security in Oman: Why Your Business Can't Afford to Ignore It
Oman’s digital ecosystem is expanding rapidly. From e-commerce stores and mobile banking apps to cloud-based corporate networks, more businesses are going digital every day. But with this digital progress comes one massive challenge—cyber security in Oman. Whether you're a small startup or a large enterprise, protecting your data, systems, and reputation from cyber threats is no longer optional. It’s a necessity.
The Rise of Cyber Threats in Oman
Cybercrime isn’t just a global issue—it’s hitting close to home. Businesses in Oman are increasingly being targeted by hackers, ransomware gangs, and phishing scams. The more connected we become, the more vulnerable we are. Threat actors are exploiting weak networks, outdated software, and untrained staff to access confidential data and disrupt operations. That’s why the demand for stronger cyber security in Oman has never been higher.
Omani Businesses Are at Risk—And Here’s Why
Many companies in Oman still lack a solid cyber security framework. Some use basic antivirus software and assume that’s enough. Others underestimate the risks because they believe cybercriminals only target large corporations. In reality, small and mid-sized businesses are often the most vulnerable because of weaker defenses. The truth is, if you’re online—you’re a target. And without proper protection, you’re an easy one.
Common Cyber Attacks in Oman’s Market
Here are just a few types of attacks threatening businesses across Oman:
Phishing emails pretending to be from banks or suppliers
Malware infections through unsecured downloads
Ransomware locking critical files and demanding payment
Man-in-the-middle attacks on public Wi-Fi networks
Data breaches due to poor password practices or insider threats
These attacks can lead to financial losses, legal problems, and serious damage to your brand.
Government Action and National Initiatives
Oman’s government understands the seriousness of the issue. The Oman National CERT and the Ministry of Transport, Communications and IT are actively developing regulations and response frameworks. Several national awareness campaigns have been launched to educate businesses and individuals. These efforts show that cyber security in Oman is now a priority at the national level, not just in the private sector.
Cyber Security Solutions for Omani Businesses
The good news? You can take action right now to protect your business:
Implement strong firewall and endpoint protection
Use advanced email filters to block phishing
Encrypt sensitive data both in transit and at rest
Create cyber security awareness among employees
Invest in real-time monitoring and response systems
Partnering with a professional cyber security service in Oman can help ensure all these solutions are implemented correctly.
Why Local Expertise Matters
Working with a local cyber security provider gives your business a big advantage. They understand the specific threats faced in Oman, are updated on local compliance laws, and can respond quickly in emergencies. Instead of using generic tools or relying on foreign vendors, more companies are now turning to trusted local experts for tailored, end-to-end protection. This makes managing cyber security in Oman far more efficient and impactful.
Benefits of a Cyber-Secure Business
When your business is cyber-secure, you gain more than just safety. You build trust with your customers, confidence among your partners, and resilience against unexpected threats. You also avoid costly downtime, legal fines, and the stress of crisis management. Simply put, strong cyber security is a growth tool—not just a defense mechanism.
Cyber Security in Oman for Individuals and Families
It’s not just companies at risk. Everyday users in Oman face risks like fake websites, banking scams, and hacked social media accounts. Protecting your devices, using strong passwords, and enabling two-factor authentication are basic but essential steps. Teaching your family members about online safety is also part of building a cyber-resilient society.
0 notes
Text
Ledger Live Login - Securely Manage All Your Crypto Assets
In the ever-evolving world of cryptocurrency, security and user experience remain two top priorities for investors and enthusiasts alike. One of the leading names in crypto security is Ledger, a company known for its hardware wallets like the Ledger Nano S and Ledger Nano X. Complementing these devices is Ledger Live Login, a powerful desktop and mobile application that lets users manage their crypto assets with ease. A key step in accessing this ecosystem is the Ledger Live login—and ensuring it’s done securely is paramount.
What Is Ledger Live?
Ledger Live is the official application from Ledger that allows users to interact with their hardware wallet. It provides an intuitive interface to:
Check real-time balances
Send and receive over cryptocurrencies
Stake assets like Ethereum and Polkadot
Manage NFTs
Access services like buying, swapping, or selling crypto
Whether you're a seasoned investor or a crypto newbie, Ledger Live is built to make managing your digital assets more streamlined and secure.
Understanding Ledger Live Login
Unlike traditional login systems that require usernames and passwords, Ledger Live uses a hardware-based authentication mechanism. When you “log in” to Ledger Live, you're essentially:
Connecting your Ledger device (Nano S, S Plus, or X)
Entering your device’s PIN
Granting permission for Ledger Live to access your device
This eliminates the need for a password-based system, making it much harder for hackers to breach your account. The private keys never leave your hardware wallet, which means your assets are stored in the most secure manner possible.
Setting Up Ledger Live
Here’s a quick step-by-step for first-time users:
Download Ledger Live from the official Ledger website (ensure you're not downloading from a fake or phishing site).
Install the app and select whether you’re setting up a new device or restoring one.
Connect your Ledger hardware wallet to your computer or mobile device.
Enter your PIN on the device to unlock it.
Open the Ledger Live app, and your device will prompt you to allow the connection.
Once authenticated, you’ll have access to your dashboard.
It’s worth noting: Ledger Live Login does not have a "cloud login" or online account. All access is local and tied to your hardware device and seed phrase.
Security Best Practices for Ledger Live Login
To keep your crypto safe, follow these best practices:
Always verify URLs before downloading or updating Ledger Live (official site).
Never share your recovery phrase with anyone. Ledger will never ask for it.
Enable Ledger’s password lock feature for additional access control on Ledger Live.
Keep your firmware and Ledger Live app updated to avoid vulnerabilities.
Use a secure computer or mobile device that is free of malware or suspicious software.
Common Issues and Troubleshooting
Users occasionally run into issues with Ledger Live login, such as:
App not recognizing the device: Try switching USB cables or ports, and make sure your device is unlocked.
Firmware update prompts: These are normal and often required for compatibility and security.
PIN problems: Entering the wrong PIN multiple times will wipe the device—keep your recovery phrase handy in such cases.
Final Thoughts
The Ledger Live Login ogin process is refreshingly different from traditional login systems. By requiring hardware-based access, it adds a layer of security that keeps your assets safe from remote hacks and phishing attempts. As crypto adoption grows, tools like Ledger Live make it easier—and safer—for everyone to enter and manage the world of digital assets.
Whether you're sending your first Bitcoin or managing a diverse DeFi portfolio, Ledger Live provides a trustworthy platform. Just remember: your security is only as strong as your habits—so stay informed, stay cautious, and keep your keys safe.
0 notes
Text
Cybersecurity for Accountants: Why It’s Time to Act Now

From payroll and tax data to client bank details, accountants are sitting on some of the most sensitive and valuable data in any business. That makes you a prime target for cyberattacks. And no, not just the big firms. Small and mid-sized practices are just as vulnerable, if not more.
So, if you've been brushing cybersecurity off as someone else’s concern, it’s officially time to change that.
Why Accountants Are Prime Targets
Here’s the short version: you hold data criminals want.
Names, addresses, NI numbers
Bank account details
Company financials
Logins to HMRC portals or accounting software
Cybercriminals don’t care how friendly your client service is. If you’ve got data and they’ve got access, that’s all it takes.
Common Threats Accountants Face
Not sure what a cyber threat looks like these days? Here are the usual suspects:
Phishing Emails: That “HMRC alert” or “urgent invoice” might look real, but one click could open the door to malware.
Weak Passwords: If you’re still using “Password123” (or haven’t changed it since 2017), we need to talk.
Unsecured Wi-Fi or Devices: Working from cafés or your phone? Great for flexibility. Risky for security.
Outdated Software: That "remind me later" update? It might be leaving a giant hole open for attackers.
Simple Steps to Get Safer, Now
No need for a full-blown IT degree. These steps are simple, smart, and make a big difference:
Enable Two-Factor Authentication (2FA) - It’s not glamorous, but it is effective. That extra step could stop a hacker cold.
Encrypt Your Backups - Hopefully you already have backups in place? Now make sure they’re encrypted and stored safely (ideally off-site or in the cloud).
Stay Alert for Scams - If something feels off, trust your gut. Unexpected email? Double-check the sender. Don’t download anything suspicious.
Keep Software Updated - Yes, even your accounting software. Updates patch security gaps. No updates = open invitation.
Train Your Team - Cybersecurity is a team sport. Make sure everyone knows what to look for and how to respon
Time to Act
Cyber threats aren’t going away, they’re getting smarter. The good news? So can you.
Whether you’re a solo practitioner or part of a growing firm, taking cybersecurity seriously isn’t optional anymore. It’s a business essential.
And if you’re feeling overwhelmed, don’t go it alone, teams like ours at Affinity Outsourcing are here to help you stay secure, compliant, and confident.
Want help keeping your firm safe? Let’s talk.
Protecting your clients starts with protecting their data.
Know More: https://affinityoutsourcing.net/cybersecurity-for-accountants/
0 notes
Text
7 Common Mistakes People Make With Their Android & iOS Devices (And how to avoid them)

Our smartphones are packed with advanced technology, but that doesn’t make them invincible. In fact, the way you use your device every day could be quietly shortening its lifespan, reducing performance, and exposing your data to serious risks.
From bad charging habits to ignoring updates, these mistakes are more common than you think — but the good news is they’re easy to fix.
Let’s explore seven smartphone habits that could be doing more harm than good — and how to protect your device like a pro.

Ignoring Software and Security Updates
Skipping system and app updates may save a few minutes, but it puts your phone at risk. Updates don’t just add new features — they patch security vulnerabilities and fix bugs that could slow your device down or expose your data.
Enable automatic updates for your operating system and apps.
Manually check once a month for missed updates.
Always restart your phone after installing updates to ensure everything works properly.
Before major OS updates, back up your phone using Google Drive, iCloud, or a computer to prevent data loss if anything goes wrong.
Letting the Battery Drain to 0% (or Charging to 100% All the Time)
Constantly draining your battery to 0% or charging to 100% can reduce your battery’s health over time. Lithium-ion batteries degrade faster when pushed to extremes.
Try to keep your battery level between 20% and 80%.
Enable features like “Optimized Battery Charging” to slow charging near 100%.
Avoid overnight charging if your phone doesn’t manage battery health automatically.
Use slow or standard-speed charging when you’re not in a hurry — fast charging is convenient but can slightly raise heat levels, which wears down the battery.
Downloading Apps from Untrusted Sources
Installing apps from shady websites or unofficial app stores can expose your phone to malware, spyware, and ransomware — all of which can steal your data or damage your system.
Only install apps from the Google Play Store (Android) or Apple App Store (iOS).
Avoid sideloading apps unless you’re 100% sure they’re safe.
Check app permissions — apps asking for unnecessary access could be a red flag.
Use mobile antivirus tools or enable Google Play Protect to automatically scan apps for malicious behavior.
Using Your Phone Without a Case or Screen Protector
One accidental drop is all it takes to crack your screen or damage the camera lens — and repairs can be expensive. Going “naked” with your phone is a risky move.
Get a shock-absorbing case with raised edges to protect your phone from drops.
Apply a tempered glass screen protector to guard against scratches and cracks.
If you’re outdoors often, use a waterproof case or pouch for extra protection.
Make it a habit to clean under your case occasionally — trapped dust and debris can scratch your phone’s surface over time.
Using Public Wi-Fi Without Protection
Connecting to unsecured public Wi-Fi (like in cafés, airports, or hotels) without proper precautions can expose your sensitive data to hackers and snoopers.
Use a VPN (Virtual Private Network) when accessing public Wi-Fi.
Avoid logging into banking apps or entering passwords on untrusted networks.
Disable auto-connect to public Wi-Fi in your settings.
Set your phone to ask before joining new Wi-Fi networks. This gives you control and avoids automatically connecting to unsafe hotspots.
Filling Your Phone with Unnecessary Apps and Files
When your phone is cluttered with too many apps, photos, and downloads, it can slow down performance, reduce available storage, and even cause apps to crash.
Regularly delete apps you don’t use.
Transfer photos and videos to cloud services like Google Photos, OneDrive, or iCloud.
Clean up download folders and browser caches monthly.
Enable storage optimization settings — on Android, look for “Smart Storage,” and on iOS, enable “Offload Unused Apps.”
Using the Wrong Charger
Using cheap or incompatible chargers can damage your phone’s battery or even cause short circuits. Not all cables and chargers are created equal.
Stick with your phone’s original charger or a certified third-party brand (like Anker, Belkin, or Aukey).
Avoid using random charging ports or unknown charging stations in public places.
If you use wireless chargers, make sure they meet your phone manufacturer’s standards to avoid slow or unsafe charging.
Source: https://www.techaipost.com/common-smartphone-mistakes/
0 notes