#robust passwords
Explore tagged Tumblr posts
Text
Cybersecurity in Personal Finance Management: Essential Strategies for Digital Safety
In today’s digital age, where a staggering 76% of Americans engage in online banking (Pew Research Center), the importance of cybersecurity in managing personal finances cannot be overstated. This comprehensive guide explores the essential strategies for protecting your online banking, investment, and transaction activities from cyber threats. Fortifying Online Banking and Investments: An…
View On WordPress
#cyberattack statistics#cybercrime prevention#Cybersecurity#data backup#data protection#digital finance management#digital transactions#expert cybersecurity advice#financial cybersecurity guide#financial data encryption#global cybercrime costs#hard drive failure risks#investment security#online banking#personal finance#phishing scams#phishing threat awareness#public Wi-Fi security#robust passwords#secure financial apps#secure online investments#SSL certificates#two-factor authentication#VPN usage#Wi-Fi safety
1 note
·
View note
Text
I Work in an Institution, part 1
—teacher's notes
I started teaching in 2020—during covid lockdowns—which of course was nothing anyone could have prepared us for. One of the things that migrated into the skillset fairly quickly was the ability to adapt, on a dime, to whatever bullshit wasn't working that day. Frequently you'd do this within the first 5 minutes of your first class, when you discovered a new Google Meet update wasn't up to snuff.
First attempts were shaky, sure, but by the end of the day you had a decent idea of what was missing and how to make it better next time. A lot of times, you just made do: ok, so this isn't perfect, but everyone can actually see what I'm doing, so—yeah, it'll be fine.
And ideally, you'd end up with a good idea for what you actually needed (ex: document camera so the kids could see you writing notes by hand). You pretty much figured out how to bring the situation under your control, and then you went from there.
Now, whenever the internet isn't working in school, or I can't print anymore for some reason, the MO is just to look for a way out. Is there another device that prints? Can you get on a hotspot? Who do you know with a desktop printer, and doesn't mind you occasionally begging a favour? (and isn't clear across the building, while we're at it)
The upside of it being 2024 is—theoretically—a lot less stuff is outside of your control. We don't rely on Google Meet anymore, and aren't inconvenienced by an unexpected rollout. When I do example lessons during interviews, I don't have to figure out how to use Zoom while teaching a demo class of real live childen (a painful experience).
You'd like to think we wouldn't have unexpected issues in the bagging area, only now the devils are inside the building: our IT department has decided to make the system more secure, in the name of making their lives easier. Which would be fantastic, actually! —If it weren't also happening in ways that frequently and actively hamper our efforts to get anything done.
For instance, if you're logged in on device A, turns out you frequently have to wait about half an hour before you can log in on device B. For me, this results in a pretty much daily occurrence of 1) logging onto the smartboard, 2) attempting to log in on my work laptop, 3) waiting for 20-30 minutes before the work laptop discovers it can connect to the in-house network.
Mind you, during this time I can't make it connect to the guest network either, because the SSL certificate for that is expired. Even on my personal device I have to acknowledge that the certificate's expired, so I could be signing in to get my info stolen—but on the work device I can't enter it at all. On my personal, I have to enter credentials again, register, log in... not a lot in the grand scheme of things, but I get booted off this network every time my personal device powersaves. This adds up to a lot of clicks and seconds, and if it doesn't take a lot of physical time I can promise you it shaves off soul-minutes.
(there's a workaround: just play a 10 hour youtube video. run down your battery a little, what'll it cost ya)
But the problem, ultimately, isn't any of these one things. It's that if you throw on another hiccup, suddenly all your little glitches and troubles become death by a thousand cuts. If you're rushing through creating 3 versions of a quiz for 5th period, suddenly you're swatting down these problems from every corner.
Today, my work laptop stopped printing (smartboard was fine), the printing rooms were out of paper (I have a stash), and because I logged in in too many places too fast, I got locked out of work accounts on my personal device, where I was editing my quiz (I logged into a work-related personal google account on the work laptop and went from there). All of these added whole minutes to my workflow. Felt like eons.
I'm tired of having 50 workarounds and having to come up with 100 more, experimenting with them as I go. I want the equivalent of my old document camera: a system under my control, almost entirely non-reliant on school networks.
Well, if nothing else, the search should be interesting.
#i work in an institution#wouldn't it be nice if we had to change passwords for powerschool and the laptops at the same time?#(ok fine theoretically forcing us to have 2 different passwords that don't sync up is safer)#wouldn't be cool if we didn't get logged out of our google acct in the middle of the day‚ between classes?#wouldn't it be great if we supported robust excellent software and weren't looking for a way to kill it—#—because we're 'not a microsoft forward district'‚ whatever that means?
16 notes
·
View notes
Text
Thank you for applying for a library card!
We are a large metropolitan library with twelve branches here in the city and a consortial agreement with ninety-seven different timelines (and counting). Your card is your ticket to our physical and digital collections, where we have something for everyone.
You’ve indicated that you are licensed for time travel and regularly travel in time or between timelines for work purposes, so you are eligible for our trans-timeline borrower’s card. Please read this document carefully to ensure you’re using your new card to its fullest potential and in compliance with library policy.
Our services:
The library has a floating collection, meaning items remain at the branch where they were returned rather than being sent back to the lending branch. However, we do return inter-timeline loans to their home universe to minimize temporal strain. If you’re browsing the shelves and see a book phasing in and out of existence, alert an employee. It’s probably misshelved.
Our new online system allows you to keep the same login information in all timelines. No more keeping track of dozens of passwords! If you previously created multiple logins tied to one card, visit the circulation desk, and we’ll merge your accounts for you. No, this will not make you responsible for alternate selves’ outstanding fines, and any version of yourself telling you that is lying to you.
You asked, and we listened. Our new online catalog displays reviews from patrons from all relevant timelines on items exceeding a 90% similarity score. We request that patrons keep debates over the superiority of their timeline’s version to venues other than our catalog.
Although our staff members are not medical professionals, they have been trained to recognize signs of temporal instability. If you are experiencing characteristic symptoms (faintness, disorientation, physical and/or mental age changes, etc.), a staff member can administer grounding agents until emergency services arrive.
The library has a robust inter-timeline loan system. If you’re looking for a book or article not published in this timeline, fill out our online form or ask at the circulation desk. The average wait time for an ITL request is five business days. That’s shortened to three if you’re requesting an item stored at the James Patterson Interdimensional Warehouse. (Note: This estimate may change as the warehouse continues to expand under its own power, or if our courier gets lost there.)
Our policies:
We do not accept returns before the publication date (month and year). Cataloging books paradoxically created through stable time loops gets too complicated. You can check a book’s month of publication in a review journal like Booklist, which we make available online and in our non-circulating magazine collection.
We’ve recently gone fine-free in this timeline, meaning we no longer charge fees for overdue books. This policy varies between consortium timelines depending on whether certain people on the board of directors have retired yet.
If a book is damaged beyond repair, lost in a Time Hole, or overwritten out of existence by timeline changes, you will be responsible for the replacement cost or a flat fee of $30, whichever is lower. We do not recommend attempting to rewrite time to avoid losing or damaging the book, as we would prefer to purchase a new copy rather than tear a hole in the fabric of reality.
Patrons may use our computers for two hours. You can extend this time if there are no other patrons waiting. Show respect to other library users and do not abuse time travel to circumvent the policy when there is high demand. We will notice if there are two of you at our computing stations. Yes, even if one of you is wearing a funny hat.
The library values your privacy. We will not disclose account information or the content of reference transactions to anyone, including alternate versions of the account holder. The library also does not keep a record of the materials you check out. However, some of our databases do track user data. If you need to conceal your presence in this timeline to avoid paradoxes, the Time Cops, or your ex, we keep a collection of electronic resource licenses at the reference desk so you can judge which products to avoid.
Holder vs. Holder found that copyright protections extend across timelines and prior to publication, and copyright is exclusive to the iteration who created the work. Patrons attempting to copy library materials and publish them under their own name will have their cards revoked, even if they created the material in another timeline. This policy was adopted after consultation with our legal team. Trans-timeline copyright enforcement is very aggressive.
The library respects the personhood and autonomy of patrons no matter their timeline of origin. However, this respect is not always universal. If you need to know what the laws are for time travelers/alternate selves/dimension-hoppers/“timeclones”/etc. in this dimension (or the terminology used to refer to them), stop by the reference desk.
Violence is against library policy. If you are about to battle your alternate self from another timeline because you ran into each other in the cookbook section, take it to the parking lot.
In conclusion:
Libraries are committed to free access to information, and with the resources of dozens of timelines available to us, our mission has only gotten bigger. In fact, we’re hiring! If you’re looking for somewhere new to apply your time travel certification, we’re looking for team members in our inter-timeline loan department. Entry-level courier positions do not require an MLIS. Familiarity with James Patterson is a plus.
We can’t wait to see you in our library. (Maybe we already have.)
#wrote this down in a frenzy a few years ago after dreaming I had an inter-timeline library card#kat writes
637 notes
·
View notes
Text
Yesterday, Netflix had an earnings call where they announced revenues of $8.5 billion, robust subscriber growth and success of their crackdown on password sharing. It was an announcement of a very successful quarter by any reasonable measure.
That was not enough for the vultures of Wall Street, and they started selling off Netflix stock in such a frenzy that by the end of the day Netflix had lost $18 billion in value.
$18 billion is enough to fund every ask of the WGA and SAG-AFTRA for three decades.
Capitalism demands constant unchecked growth. The only thing that constantly grows without any boundaries is cancer. And like cancer, capitalism will kill us all. 
683 notes
·
View notes
Text

✨ Basic ✨ online safety tips! this is from a technical standpoint. A non exhaustive, non professional list on how to NOT end up with people doxxing you, cause a moot got tricked by a metasploit script kiddie keylogging random and everyone deserves to feel safe in their space.
Passkeys. Use them. Hardware ones are more secure but also less versatile. Any is better than Passwords.
2FA is great and all, but token theft exists, not just on discord but, ever heard of a pass-the-cookie attack? wipe, your, cookies. Browser, whichever one you use. Wipe the data periodically. Once per week minimum
HSTS - have it set up. It's resistant to MITM attacks so long as you're careful. SSL stripping doesn't work ever since TLS, which btw TLS 1.3 is the standard.
Cryptographic encryption itself is very strong and hard to breach by brute force. Even AES 128. AES 256 is always preferred and now most browsers come with Quantum Protection. Again. None of this means anything if your online safety habits sucks and your password is compromised.
"Antivirus is useless!" Wrong. It's true that for mobile devices an AV isn't as paramount as for PC HOWEVER this is only for very casual users. Premium AV are important because they come with features that will keep you from clicking phishing links and making oopsies as well as firewalls. No. Don't pay for stuff. Stay away from anything Norton and Avast. One is a scam the other is pure spyware and adware, and we don't even need to talk about Mcafee. Kaspersky was fantastic but you already know the problem. Bitdefender Mobile Security is robust, I use it while making new empty emails every 2 weeks to avoid paying and that way you can use it forever for free. Yes. I'm a sneaky little thing, we don't pay to corps here. Btw smaller ones like ESET are good too, less load. Sophos is very specific in it's usage and don't recommend it for casual users.
Don't bother with DMZ or VM over VM stuff unless you're a professional or a genius. A set up wrong VM is an open backdoor to hackvile and contrary to popular belief a VM can be compromised, especially if you access the internet with it. Don't.
Simple tools well set up are 100x times better than complex things you know nothing about. You don't need company security suit stuff as a normal user, at all, ever.
Pleaseeeee update your router for the love of everything that's sweet and full of Ice cream. If you use WPE/WPA or anything below WPA 2 AES 256 your router is hollering to be compromised. No. WPA 2 TKIP isn't enough either. IF possible have WPA 3 set up. It's resistant to vulnerabilities the past one has particularly KRACK attacks...and pls avoid dual connections my head hurts thinking about it
Be aware of hacking tools like Metasploit or Flipper Zero. Be aware of basic stuff like SQL injections. You don't need to be an IT expert to be conscious. Zero day exploits are a thing.
Malware has many types. Adware and PUA are considered less of a problem, but still annoying. Keyloggers and Trojans are middle tier, although it depends on the Trojan as some can be highly dangerous. Fileless malware, you don't want it. Rootkits get system level acess, and worms? I wish they were gummy worms instead.
The level of access of a virus can range from data only straight up to firmware and the danger is how quickly it can escalate access permits, many viruses won't ever get beyond system level access but rootkit can gain kernel and some above that. Anything at kernel level or above can't be wiped by a factory reset and a compromised boot sector is a problem.
Common stuff like White hack hackers. Gray hat hackers. Black hat hackers. Red hat hackers etc. it's actually usually much less noisy. No. A hacker won't dress themself in black robes in a dark room and wave at you while nightwish plays in the background, your cousin. Fifteen and eating cereal could be one of those already, although most that age are script kiddies.
"I did it! I'm impossible to hack!* Stfu. No. I'm serious, don't do that. Don't fell victim to the Dunning Kruger Effect. Knowing this doesn't make you a pro and ypu could layer TOR over VPN and have every security suite in place and still get hacked by anyone skilled enough with ease, do you know how easy it is to exploit human error in terms of cyber security? the best way to NOT have your information compromised is not to brag about your knowledge. You will get humbled and it will be, at the very least, a deeply embarassing experience. And obviously keep your devices up to date
Back to more easy stuff, if you do use passwords, change them periodically, check your IP. "have I been pwned?" Yes, yes you have, there's been millions of leaks on multiple sides and even if you're tech savvy as a non pro you had it happen almost for sure, I know I did as a kid, if you use passwords make them lengthy. No. QWERTY is not lengthy, TikTok Timmy. You know the drill use symbols, mix random stuff and use your lateral thinking. Did you know sufficiently potent decides can brute force thousands of passwords in seconds? Passkeys are better, I promise.
None of the above means squat if your socials constitute of your full name disclosure and a photo of your face, don't doxx yourself. Still. Do not panick, most people won't have access to spying tools like FinSpy or Pegasus and you're not constantly being watched, just be aware of threats.
#choco speaks#actually adhd#actually autistic#⬅️ I'm not a professional and dont claim to be one. I'm knowledgeable but anyone who is an expert can add-up.
13 notes
·
View notes
Note
can you actually talk about bitwarden / password managers, or direct me to a post about them? Idk my (completely uneducated) instinct says that trusting one application with all your passwords is about as bad as having the same password for everything, but clearly that isn’t the case.
So it is true that online password managers present a big juicy target, and if you have very stringent security requirements you'd be better off with an offline password manager that is not exposed to attack.
However, for most people the alternative is "reusing the same password/closely related password patterns for everything", the risk that one random site gets compromised is much higher than the risk that a highly security focussed password provider gets compromised.
Which is not to say it can't happen, LastPass gets hacked alarmingly often, but most online password managers do their due diligence. I am more willing to stash my passwords with 1Password or Bitwarden or Dashlane than I am to go through the rigamarole of self-managing an array of unique passwords across multiple devices.
Bitwarden and other password managers try to store only an encrypted copy of your password vault, and they take steps to ensure you never ever send them your decryption key. When you want a password, you ask them for your vault, you decrypt it with your key, and now you have a local decrypted copy without ever sending your key to anyone. If you make changes, you make them locally and send back an encrypted updated vault.
As a result, someone who hacks Bitwarden should in the absolute worst case get a pile of encrypted vaults, but without each individuals' decryption key those vaults are useless. They'd still have to go around decrypting each vault one by one. Combining a good encryption algorithm, robust salting, and a decent key, you can easily get a vault to "taking the full lifetime of the universe" levels on security against modern cryptographic attacks.
Now there can be issues with this. Auto-fill can be attacked if you go onto a malicious website, poorly coded managers can leak information or accidentally include logging of passwords when they shouldn't, and obviously you don't know that 1Password isn't backdoored by the CIA/Mossad/Vatican. If these are concerns then you shouldn't trust online password managers, and you should use something where you remain in control of your vault and only ever manually handle your password.
Bitwarden is open source and fairly regularly audited, so you can be somewhat assured that they're not compromised. If you are worried about that, you can use something like KeePassXC/GNU Pass/Himitsu/ (which all hand you the vault file and it's your job to keep track of it and keep it safe) or use clever cryptographic methods (like instead of storing a password you use a secret key to encrypt and hash a reproducible code and use that as your password, e.g. my netflix password could be hash(crypt("netflixkalium", MySecretKey)), I know a few people who use that method.
Now with any luck because Apple is pushing for passkeys (which is just a nice name for a family of cryptographic verification systems that includes FIDO2/Webauthn) we can slowly move away from the nightmare that is passwords altogether with some kind of user friendly public key based verification, but it'll be a few years before that takes off. Seriously the real issue with a password is that with normal implementations every time you want to use it you have to send your ultra secret password over the internet to the verifying party.
244 notes
·
View notes
Text
Updated: July 11, 2025
Reworked Character #6: Nadia Cassel
POTENTIAL TRIGGER WARNING: Viewer discretion is advised due to references to death, neglect, sterilisation, human experimentation, abuse, kidnapping, stalking, cannibalism, and SA.
Real name: Nadège Véronique Comtois
Alias: Perky Foodie
Occupation: Private First Class of the S.P.A.R.R.O.W.S., a tactical scientist for the Amadeus Syndicate (formerly), and an e-celeb supermodel (formerly)
Retirement plans: Become a professional forensic scientist and establish a fashion house
Special skills: Marksmanship, fashion modelling, forensic science, knowledge of biological hazards and visual art, and proficiency in piloting fighter aircraft, managing information, and encrypting passwords
Imperfect clone abilities: At her own will, she can rapidly regenerate missing limbs and organs, minimising blood loss and restoring her body to its original form without the need for medical aid. Her blood possesses extraordinary healing properties, capable of instantly curing non-lethal ailments, skin punctures, and all manner of burns. When Nadia opens her mouth wide and flexibly shifts her upper and lower front teeth, she reveals four syringe-like fangs, which are neatly concealed within the hard palate. These fangs enable her to consume the blood of other living beings and replenish her own lost vital fluid.
Her body is shielded from toxins and pathogens by a translucent, grease-like coating that kills threats on contact, leaving her skin with a subtle, luminous sheen. Notably, her pancreas, shielded by a thick layer of blubber, has the unique ability to produce a bile-infused silk. She utilises this silk to puke up robust, ensnaring nets that capture her victims and slowly burn them with its corrosive properties. Her fingernails are entirely fleshy, concealing retractable claws made of a ruby-hard greenish-yellow material.
On the palms of Nadia's hands are eyes with chartreuse irises, feline pupils, and serpentine eyelids. They grant her night vision and supplemental sight whenever she closes her facial eyes and opens the ones on her palms. They can secrete a venomous substance with a potency similar to that of a king cobra, which coats any surface with razor-sharp edges, forming a partially sticky, decently thin, translucent lime green layer. They can generate a temporary burst of blinding light to disorient their enemies and potentially damage their retinas.
Hobbies: Going on shopping sprees, studying passwords and aircraft models, drawing and painting fashionable designs, eating large quantities of food after each mission, and reading books on human and animal anatomy, genetic engineering, and forensics
Likes: Trevor, food challenges, the Walking Machines, maintaining her figure because she views it as a work of art, and sunbathing and enjoying a three-scoop ice cream cone at the beach
Dislikes: Annoying evaluations, getting unnecessarily dirty, not getting the chance to pilot the Slug Flyer or Slug Copter, people doubting her fashion advice and telling her to keep her mouth shut, and individuals that she views as scary and incapable of having fun (e.g. Eri and Tequila)
Favourite food: Sugary sweets
Favourite drink: Cotton candy soda
Sexuality: Heterosexual
Gender: Female
Age: 12 (in 2022), 18 (in 2028), 20 (in 2030), 22 (in 2032), 24 (in 2034), 31 (in 2041), 33 (in 2043), 34 (in 2044), and 37 (in 2047)
Blood type: B+
Weight: 120 lbs. (54 kg)
Design: She’s a 5’ 4” (162.56 cm) French ectomorph with a gracefully thin body, small breasts, curvaceous hips, sloping shoulders, and a serpentine tongue covered in microscopic spikes. She has limestone skin and possesses feline-like pupils that transform into vertical slits only when she opens her mouth wide enough to reveal her concealed fangs. Her eyes are heterochromatic with her right eye being a warm amber, while her left eye is grey-green with brown flecks. Nadia has a few moles: one on the right side of her chin; one near the corner of her left eye; two above her left breast; one on the back of her right hand; and one slightly below her right knee.
She has raspberry red hair with voluminous curls that reach the middle of her upper back, but she often ties it into two pigtails with stretchy reseda green hair bands. She has a silvery-pink birthmark on her left shoulder, almost shaped like a crescent moon with three protruding spikes. A large circular patch on her upper back is stripped of skin, exposing crimson muscles and purplish veins, and her greenish-yellow spine is partially protruding.
Her military gear consists of a metal dog tag necklace with her name, an avocado green tank top, and the same knee pads and socks as Nadia Cassel from Metal Slug 4. She wears Argentine blue neoprene gloves, reseda green leather belt with a snap-on silver buckle, and a champagne-hued vest with the S.P.A.R.R.O.W.S. insignia on the back. She wears navy blue army cargo pants tucked into twilight lavender combat boots with spiked soles. She also wears a dirty white lab coat, a case for her stun gun, and a gun holster for a handgun. Underneath her uniform, she wears an identical bikini to Everlasting Summer Nadia's.
The pockets of Nadia’s vest carry around a pocket knife, a notepad, two pens (one red and one blue), a silver-white cellphone with a quicksand case filled with emerald and seafoam green glitter, and a bag of fruity gummy bears. In the pockets of her lab coat, she carries a caramel-filled chocolate candy bar in silver wrapping and a small pine-wood box of strawberry frosted sugar cookies. She wears a forest green waist pack containing a bottle of laxatives and two blood packs for snacking. Attached to the left side of her belt is a square-shaped pouch with a clear plastic window, showcasing balls of bubblegum and lollipops in different colours inside. The pouch features an amaranth pink outline, feline ears with bluish-white fur, a pistachio-hued strap with a black button clasp, and a metallic silver zipper.
Over her tank top, she dons a Soldier Plate Carrier System (SPCS) with a MultiCam pattern, which carries around her walkie-talkie and ammo for other firearms. She wears two dark brown bandoliers that cross over her body in an X-shape, each holding pineapple grenades. Nadia carries around a navy blue load-bearing backpack that contains camping equipment, portable ammo boxes, a canteen full of water, landmines, smoke bombs, an Iron Lizard, a 7.62mm AR-10 Autorifle, a medical kit, a DOLL bodysuit, and liquid and pill bottles of cures and deadly chemicals. She carries Melekhai, an orange-and-white cat plushie with blue eyes and an emerald green business tie, along with greenish-black gas masks reminiscent of those worn by the Ptolemaic Army special forces, to distribute to her teammates in need of one. She also carries around a painting kit, her mint green sketchbook with bubblegum pink polka dots, and a set of drawing pencils with two erasers and a sharpener.
She also wields a specialised rifle that fires needles containing transformative liquids, capable of altering humans into simian or mantis creatures. Additionally, she carries purplish rolling bombs that contain mummifying breath and throwable canisters filled with a zombie-inducing orangish phlegm that explodes upon impact. She wears safety goggles, star-shaped lavender spinel earrings that dangle from her ears, and a non-dangling peridot belly ring piercing.
Character summary: She boasts swift wit and inventive verbal humour, often outsmarting her foes with clever sabotage tactics. She's exceptionally skilled at marksmanship and takes great pride in this, often boldly showcasing her impressive aim when prompted or when she's in a good battle mood. Despite being a childish, happy-go-lucky, and sassy goofball, she has a surprisingly intelligent and cynical side, but she loves to indulge her silly and jubilant nature. Due to her fondness for her exceptional intellect, she sometimes perceives other people as “intellectually inferior” to herself. She can be overly energetic when interacting with new people and does her best to cheer them up, even if she sometimes comes across as oblivious and a bit of a dunce. She conceals her bitterness and wariness of strangers behind a facade of playful teasing, mischievous pranks, sarcastic remarks, and a charming smile. She has a tendency to pout adorably, especially when someone disrupts her plans or when she's torn about something and doesn't want to admit it.
She cherishes her friendship with Trevor, who is her first true best friend. She appreciates his laid-back nature and ability to understand her effortlessly. She enjoys occasionally poking fun at others in hopes of making him laugh hard with her sense of humour and Tarma's playful jabs. Over time, she has developed subtle romantic feelings for him, largely due to his hacking expertise and the enjoyable quality time they share. However, she's very skilled at concealing these emotions.
She's a friendly, humorous, and talkative busybody with a passion for creative expression and thrill-seeking adventures, which give her a taste of what it truly means to live. She enjoys taking her friends on shopping sprees, blending social time with style consultations. She demonstrates her loyalty to her friends by nurturing their relationships and showing platonic affection, often showering them with hugs and kisses. She's a fearless advocate for herself and others, refusing to tolerate bullying or any form of mistreatment, and will boldly speak out against it. She uses Melekhai for stress relief and often talks to the plushie about her frustrations and disappointments, and is willing to share him with others who need some comfort. Whenever the mission instructions bore her, she often has to fight off drowsiness and doesn't pay attention to most of what's being said.
She has a fondness for assigning nicknames to those around her, including friends and foes alike. She often prefers to call people by the nicknames she has for them. However, there are times when she uses the nicknames they commonly go by or their usual names if she's stumped on the perfect nickname. Rarely, she may refer to those with assigned nicknames by their common names, but this only occurs when she's in a serious mood or has a brief moment of forgetfulness. She's surprisingly skilled at cracking complex passwords, but she has a tendency to make a few silly mistakes, which leads her to doubt her encryption abilities. She sometimes whines and complains when faced with tedious tasks, such as frustratingly evaluations of the battlefield, dealing with people who make fun of her, and struggling with forgotten passwords.
Despite efforts to maintain her supermodel figure, she has developed mild bulimia nervosa; while trying to resist the urge, she sometimes purges after eating. Additionally, she struggles with obsessive-compulsive disorder (OCD), manifesting as a fear of contamination, anxiety about misplacing valuable items, and a need for order and balance. She also experiences distressing thoughts, including fears of losing control, harming loved ones, and intrusive thoughts about sexual subjects. Whenever she hears about the death of children, child abuse, or unethical experiments—or believes that any terrible thing someone has told her involves one of these issues—she becomes visibly shaken. Her mind goes numb, and she withdraws socially for a couple of hours, seeking solace in the peacefulness of nature as she succumbs to a melancholic state.
She takes a disturbing pleasure in obliterating her enemies, often letting out a maniacal laugh as she does so. Her humour is a unique blend of lighthearted and dark, peppered with French phrases, occasional broken English, and sprinkled with Korean expressions that Trevor has taught her. Outside of her military work, she often dodges unwanted tasks by concocting elaborate schemes, frequently with Trevor's help, to avoid them. However, her plans often backfire, resulting in trouble for neglecting her duties. Moreover, she has a tendency to slack off during missions, especially when she becomes bored and her attention wanders to more exciting things. When she gets into trouble, especially when it involves people she has convinced to join her antics, she often tries to deflect responsibility by feigning innocence and shifting the blame onto others.
She possesses a fairly compassionate, laid-back disposition, which she only reveals to those closest to her. She's overconfident about her looks and seems unfazed by how people react to her inhuman features, yet she draws the line at absurd and unattainable beauty standards. She's deadly serious when needed and isn't afraid to intimidate people or berate individuals for doing something irrational or dangerous. She has a strong disdain for individuals who exhibit predatory behaviour, such as perverts and stalkers, and is unafraid to call them out and mock their actions mercilessly. She despises unnecessary secrecy and eugenics, opposing the lack of transparency and the racist underpinnings of genetic manipulation aimed at "improving" human populations.
She's quite gluttonous and becomes quickly hangry when she's extremely hungry and there's nothing to eat at the moment. She's an eavesdropper with a curious habit of inspecting, poking, probing, and even biting anything that piques her interest, including people. She grapples with touch starvation, feeling emotionally isolated from others, and deeply dislikes being overlooked or ignored by those around her. She harbours intense resentment towards her mother due to her neglectful behaviour and excessive focus on satisfying scientific curiosity, which comes at the expense of considering others' needs and forming meaningful connections with them. She’s appalled by her mother's callous disregard for the pain she inflicts on others as well as the secrecy surrounding their family's lineage and her status as an imperfect clone.
She seems to have a special connection with Ralf as they share a healthy and affectionate big brother-little sister dynamic. They understand and appreciate each other's thirst for having a good time, but Ralf also encourages Nadia to take her responsibilities seriously when needed. They love to engage in fun, lighthearted antics during missions, even if it risks alerting nearby enemies and putting themselves in harm's way. They often rope Tarma into their mischief, which he eagerly accepts, seemingly unfazed by the potential consequences. Nadia values how Ralf and Tarma accept her bubbly personality without judgment, unlike Eri and Tequila, who often try to dampen her spirits.
She's captivated by Tyra's makeup skills and willingly lets her experiment with new techniques, trusting her completely. Interestingly, she's surprised to discover that Tyra genuinely admires her, and this admiration fills her with pride because she has a deep-seated desire for respect and validation from others. Nadia also delights in hearing Walter enthusiastically share his zoology knowledge and praise Marco, finding his childlike excitement endearing.
She can't help but worry about Marco due to his overly serious nature and struggle to express his true emotions. Despite his frequent annoyance, she tries her best to lift his spirits, attempting to distract him from work. In particular, she enjoys taking Marco on shopping trips, hoping to help him relax and get to know him better on a personal level. Nadia is extremely close to MS-Alice, considering her a dear friend. She's always willing to lend a listening ear to MS-Alice's frustrations and doubts, and the two often engage in casual, meandering conversations. She finds the concept of a sentient AI fascinating, and MS-Alice's unique existence only adds to her appeal. Nadia also enjoys offering her fashion advice, encouraging her to explore different styles and discover what works best for her.
Backstory: Nadège Véronique Comtois was born on August 6, 2010 in Quimper, France. She was created in a test tube using advanced Martian cloning technology that was carefully salvaged during a confidential investigation, utilising the DNA of Ghyslaine Laëtitia Comtois, her clone mother and the founder of the Amadeus Syndicate, in an underground laboratory. Initially, Ghyslaine's interest in Nadège was rooted in scientific curiosity. She bioengineered certain biological abilities to give her a more combative edge, hoping to steer her down a militaristic path. She conducted psychological and sociological experiments to explore the similarities and differences between them. Ghyslaine would overfeed Nadège, only to discover that her daughter had an abnormal metabolism, making it challenging for her to gain weight. Unintentionally, Ghyslaine fueled Nadège's affection for junk food.
At age 7, Ghyslaine subjected Nadège to a disturbing and unethical experiment, forcibly inducing puberty and sterilising her daughter as part of a eugenics test. During this period, Nadège longed to experience the outside world and connect with her clone mother. Unfortunately, Ghyslaine's focus on research led her to neglect Nadège’s emotional needs. She treated her more like a guinea pig than a human being, providing minimal motherly comfort and attention.
At the age of 9, Ghyslaine decided it was time for Nadège to explore the outside world, which filled her clone daughter with excitement. Together, Nadège experienced her first-ever outing to a shopping district and explored several notable attractions in Quimper, including the Breton County Museum, the Fine Arts Museum, and the Faience Museum. She received Melekhai as a reward for being well-behaved, and she still holds onto the plushie very dearly since it was the first heartfelt gift her clone mother gave her. Her experience with the outside world sparked Nadège’s curiosity in modelling and the creative arts.
However, her mother had other plans. Ghyslaine envisioned Nadège following in her footsteps as a renowned scientist and eventual heir to the Amadeus Syndicate. To nurture this ambition, Ghyslaine frequently presented Nadège with books on biology and chemistry, encouraging her to delve into the sciences. She encouraged Nadège to cover the unusual features on her palms and upper back by wearing neoprene gloves and modest clothing in order to avoid drawing unnecessary attention or judgement from others.
By the age of 11, Nadège had become proficient in biology and chemistry, thanks to her mother's guidance. She began attending school after being previously homeschooled by Ghyslaine and other Amadeus Syndicate scientists. Although her school years were uneventful, Nadia occasionally faced bullying due to her intense interests in science, modelling, and the creative arts, as well as her unusual habit of wearing neoprene gloves to conceal her hand-eyes.
However, the bullying ceased after rumours circulated that she had intimidated and bitten a school bully by revealing her hidden snake fangs—a claim that was surprisingly true. Nadège’s clone mother was indifferent to her academic pursuits but drew a firm line at harming others and divulging confidential information about the Amadeus Syndicate. When Ghyslaine learned about this incident, she smacked her in the face, then confined her to a padded room with two blood bags and a fresh corpse for three hours. As dinnertime approached, Nadège's hunger grew, leading her to make the desperate decision to consume the contents of the blood bags and feed on the fresh corpse.
During her high school years, Nadège frequently skipped classes to go shopping, feeling that she already possessed a strong grasp of the material being taught in her courses. To avoid arousing suspicion about her exceptional intelligence, she intentionally performed poorly on a few tests. During this time, she experienced significant weight gain, which unfortunately led to bullying and negative comments about her appearance. However, she handled the situation with confidence and resilience, effectively standing up for herself and dismissing the hurtful remarks. After completing high school, she promptly enrolled in a two-year college art program, specialising in fashion drawing, before pursuing forensic science at the university level.
While pursuing her forensic studies at university, Nadège unexpectedly catapulted to fame as an e-celebrity supermodel, adopting the pseudonym Nadia Cassel. Driven by a passion for fashion and curiosity about the modelling world, she embarked on this venture independently, without management, and solely for her own enjoyment. Although her rise to fame was modest at best, she didn't mind because she revelled in the opportunity to be herself and try something new. As her university studies grew increasingly demanding and stressful, she found it challenging to balance her modelling career. Seeking support, she hired a model manager, who turned out to be unexpectedly kind and helpful. He broadened her knowledge of the fashion and modelling industries.
However, as her fame as an e-celeb supermodel grew, she started to attract unwanted attention from predatory individuals, which caused her significant distress. Her situation intensified when she inadvertently revealed her hand-eyes and exposed spine during a livestream, leading to an escalation of online harassment. After a deranged fan attempted to kidnap and sexually assault her, she empowered herself by obtaining a gun licence and rigorously training to use a firearm, becoming a fearsome markswoman.
The stress of her forensic studies and the pressures of being a supermodel took a toll on Nadia's mental health, leading to the development of OCD and bulimia nervosa. Her struggles with maintaining a strict diet, keeping her model-worthy figure, and need for control became overwhelming. Her modelling manager grew concerned about her unusually voracious appetite, fixation on her body weight, and increasing frustration when things didn't go as planned. He advised her to consider taking a step back from modelling or quitting altogether to focus on her well-being.
After a two-day break, Nadège made the decision to quit modelling as her mental health issues began to impact her studies. However, she kept the name of her e-celeb persona because she liked it. Although she has left the world of modeling, she remains in touch with her former modeling manager, and they have become good friends. After a long day of designing clothes, she recalls a disturbing nighttime incident in which she defended herself against a stalker who attempted to assault and cannibalise her in her own home. The attack forced her to involuntarily consume the stalker's blood when she bit his hand in self-defence, revealing a sadistic streak she never knew she possessed.
Once her forensic studies have been completed, Nadia prioritised fitness to maintain her physical well-being. After learning about the Regular Army’s vigorous exercise programs and their pressing need for information management positions, Nadia decided to enlist in their tactical operations. Following her military training, Ghyslaine granted Nadia permission to join the Amadeus Syndicate as a tactical scientist. She proved to be highly successful, making a name for herself as she pushed the boundaries of scientific understanding in biology and chemistry. Nadia supplied the Regular Army with gas masks, stable smoke bombs, and advocated for training cadets and recruits on the dangers of biological hazards.
While searching Ghyslaine's office for documents for a chemical experiment, she stumbled upon classified test results revealing her true nature: an imperfect clone. The discovery shook her to her core. Further investigation led her to her clone mother's journal, exposing a dark family legacy of illicit collaborations with government agencies, inhumane wildlife experimentation, and development of devastating bioweapons and malicious computer viruses. However, the most alarming information she uncovered was Ghyslaine's megalomaniacal plan for global domination and self-deification. Terrified and disgusted, she contemplated abandoning the Amadeus Syndicate, yet for mysterious reasons, she chose to stay and remain silent about their heinous actions.
During her work on a cure for a disease in South Africa, Nadia uncovered disturbing information during a private conversation with Oghma at lunchtime in a relatively unknown café: Ghyslaine had sexually assaulted Marco while he was injured. This traumatic event would have far-reaching consequences, severely straining relations between the Regular Army and the Amadeus Syndicate. Horrified by Ghyslaine's actions, she quietly ditched the Amadeus Syndicate, dedicating herself to defending Earth against global threats. She vaguely recalls attempting to poison Ghyslaine by lacing her bitter coffee with powdered cyanide, but the plan backfired when another scientist accidentally drank from the cup instead.
While she was still working for the Amadeus Syndicate, she was initially oblivious to Wysteria's existence because her mother kept it a secret, knowing that if she found out, she would strongly oppose it and potentially leave the organization much sooner than desired. Ghyslaine even went so far as to forbid her daughter from entering the Amadeus Mainframe Base, fully aware of her curiosity and the problems it could cause. However, once she discovered the confidential files detailing the heinous activities in her mother's office, she learned about Wysteria's existence. When she left the Amadeus Syndicate, she shared her findings about their crimes with the Regular Army high command, which led to a temporary conflict between the two organisations three months before the Great Morden War.
She eventually joined the S.P.A.R.R.O.W.S. after befriending Fio and earning a sliver of respect from Eri. This was due to her impressive performance as a potential agent, where she swiftly identified the chemical composition of a new illicit drug that had been baffling the Intelligence Agency and Regular Army scientists. She achieved this by obtaining crucial documents and conducting rigorous, ethical experiments. She also encrypted an extremely difficult password that the enemy was using to secure their illegal database, making it challenging for even the best codebreakers in the military to crack. Following the Survival Island Occupation, she provided crucial assistance to the hostages and kidnapped cadets who had been transformed into grotesque simian and mantis creatures, administering cures that successfully restored them to their human form.
#writerscorner#creative writing#writing#iron eclipse au#metal slug#snk#gaming community#rework#redesign#name#alias#job#skills#abilities#power#hobby#likes and dislikes#food#sexuality#gender#age#blood type#weight#personality#backstory#nadia cassel
18 notes
·
View notes
Text
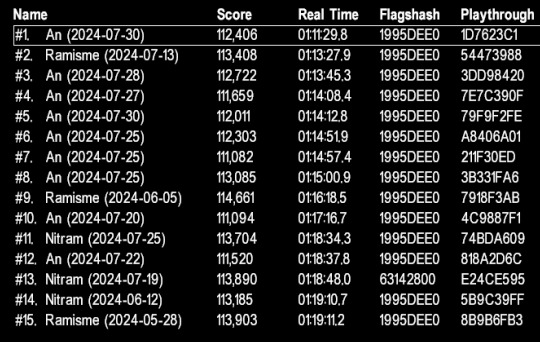
General Bragging Announcement
I guess I never mentioned the fact that I DID get my gamer moment. I'm the world record holder for Deus Ex Randomizer speedrun!
I did this run on the 30th of July. My first run ever was 3h12m on the 2nd of June. The other top runners have been playing this for a couple of years prior at varying levels of intensity, it's not quite clear to me. But either way, the speed of my ascent was commented on a lot.
In a couple of months I was able to push Nitram out of the top 10 ("I'm sorry!" An lied) and get a convincing lead over second place. I, uh, managed to severely reduce enthusiasm around WR-chasing speedrunning and we shifted towards doing races instead.
During those couple of months, I think I played at least 5 times more than either runner. I was dedicating an average of 30 hours per week to this while being employed. It felt like I never quite found out how good the other two runners _could_ get because of this discrepancy, but they also had way more experience than me. They also streamed every single time whereas I would stream infrequently.
Going from "I could never get even closer to WR, but it's fun improving" to "this is super fun, lets see how close I can get to WR" to "THE WORLD RECORD WILL BE MINE" was heck of an experience.
By the way, somewhat recently the leaderboard has been versioned because they released new versions that make the game harder. So this is technically a WR on an older version while Nitram holds the WR on the most recent version. After getting this WR my ability to get myself to play has dropped sharply but I want to get it back.
If you get nothing else from this post, at least take note that I am a Genuine World Record Holder for a Deus Ex micro-community. I will expect the queenly respect I so kingly deserve.
WTF Is DXRando Speedrunning
You take the original Deus Ex, you fix a lot of bugs and glitches, you set the difficulty to hard and then you randomize and try to finish the game with one of the three endings.
What gets randomized, you ask? I'm glad you asked:
The damage, fire rate and ammunition cap of every weapon.
The power of each augmentation.
The power and cost of each skill.
The quantity and location of all items in the game, including mission critical datacubes that contain passwords.
Passwords
The location, quantity and type of enemies, including their weapons.
The location of mission critical goals (e.g. important computers, important NPCs) among a number of preset positions.
Each combination of randomized stuff is generated from a seed. So the quality of a seed is quite important to whether you can actually get WR on it or not.
The Appeal of Speedrunning DXRando
I never had any interest in speedrunning before. It felt like an unpleasantly repetitive and grindy activity. But this being Deus Ex Randomizer made all the difference for me. I've rarely had so much fun getting good at a game.
The most appealing aspect of DXRando speedrunning is that Deus Ex is a resource-based game. Any challenge the game throws at you can be easily dealt with if you have the right resource (EMP grenade, rockets, multitools etc). This means that as you speedrun this game you need to balance resource collection and speed.
Combined with the randomization, this results in an experience that feels like it's testing your skill in a more robust manner than speedruns of games where everything is fixed.
This game forces you to make decisions mid-game, all the time. For example whether you want to spend extra time looking for an aug upgrade in UNATCO to improve your speed aug, or just leave the level immediately.
The fact that I am playing my 50th run but there's still a wealth of novel decisions to encounter is kind of amazing. After my WR, we did an official race (speedrunning the same seed) and I immediately choked at the beginning from encountering a novel situation, just to keep me humble.
Another part is that because DXRando is so chaotic and nobody has actually pushed the speedrun to its utter limits, it's the norm to die during the run and use quicksave / quickload a ton. This is major for everyone wanting to pick up speedrunning because failure doesn't mean "I guess my run is over because I can't do this trick consistently". Any mistake that isn't just outright running out of resources can be fixed by losing some time to quicksave / quickload. This results in your gradually improving at speedrunning rather than improving in large jumps due to hitting walls.
The other major factor is that you have an on-screen time tracker and your runs get automatically uploaded to the unofficial scoreboard and announced to the community on mastodon bot was also really good.
18 notes
·
View notes
Text
"Hi, I'm Luca from IT. Are you Rupert?"
The gray-haired man hefted himself back from his desk to take in the visage of the young IT tech. Good looking kid. Couldn't be more than 25. Reminded him a lot of his first husband, back in the day.
"That's me," the older man said, rolling back on his chair, "Forgive me if I don't stand. It's much harder these days."
Luca stuck out a hand, which Rupert shook. Firm grip. Rupert smiled.
"Nice to meet you, Rupert. I saw from the support ticket you sent in that you're having some issues logging in today."
Rupert nodded and waved a hand towards the computer, prompting Luca to kneel down to attempt a login.

Luca typed away, bringing up the company's portal login page.
"Would you mind telling me your login credentials, Rupert?" he queried.
"'WellermanR2174' is the username."
"And the password?"
"That's 'jerry1961annietom', all lowercase. That's my husband, my birth year and my kids' names."
Luca tapped away without comment then dramatically hit the 'enter' key and frowned.
"Hm. All lowercase, you said? That's 'Jerry' with two Rs, one, nine, six, one, 'Annie' spelled A-N-N-I-E, then Tom, T-O-M?"
"That's right, son."
Luca tried the credentials again.
"Looks like you've got some kind of stuck old credential in your cache. I'll clear your history and cache. Nothing in there that you need?"
"Better check just in case, bud. Might have something I forgot in there."
Luca opened up the browser history page and immediately blushed when greeted by the following Google searches from the previous week:
rarity of male pregnancy senior citizens is it safe for a 63 year old man to be pregnant being a dad in your sixties how to be a good father to a late in life baby 63+18 itchiness during pregnancy extreme arousal when pregnant as an older man how to convince your husband to have frequent sex during male pregnancy adoption resources for pregnant men
Luca swiftly averted his gaze and turned to Rupert.
"Anything you need here?" he asked casually.
Rupert grinned.
"No, not a thing. Anything of interest to you, son?"
Luca considered the question and bit his tongue.
"You've got a bonafide pregnant senior man in front of you. That's not something that happens every day. I take no offense at honest questions."
Luca gulped, then finally spoke up.
"So, you're pregnant. And the baby is your husband's? How long has it been since you were pregnant last time?"
Rupert pondered the question.
"Well, I think it was about...1996. I was on birth control pills at the time. Jerry was taking fen-phen for weight loss, you see and they didn't know the side effects at that time, but it turned out in addition to the cardiac problems, it also supercharged sperm counts, so he got me pregnant despite birth control. I had a miscarriage about week 13. But to answer the earlier question, yes, this baby is definitely Jerry's too."
"You weren't expecting this current pregnancy, then?" Luca asked, a little more confidently.
Rupert chuckled.
"Oh son, not a bit. I have my first granddaughter on the way from Tom in the next few weeks. I thought my baby making days were long behind me."
"How far along are you?"
"Four months or so, based on what I've read online. Haven't been to a doctor yet as I only just found out."
"I hope you don't take offense at this, but you look a lot more pregnant than that. I've seen you around the office now and then and you've gained a lot of weight this year."
Rupert grinned widely as he recognized Luca for what he was.
"I'm not offended. My husband has always liked that I'm a big guy. He's a homemaker, so he cooks for us and he likes to make sure I'm well-fed. It started back when I first got pregnant with Annabelle and he wanted to make sure she was getting enough calories to develop correctly. Tommy got the same treatment when I was carrying him. Since then, he's always made sure I maintain a robust weight. He's gotten a little carried away in the last few years," he said, patting his hefty gut fondly.
Luca licked his lips, almost imperceptibly. Rupert's eyes crinkled with amusement.
"Son, I have to ask you...are you gay?"
Luca's turn to laugh.
"Bisexual," he replied, blushing again, "Was I that obvious?"
"And you like a pregnant guy?"
"Pregnant guys, older guys and big guys," Luca said, taking Rupert in with his eyes, "Most of my partners are silver daddies and I had a pregnant friend with benefits for a while, yeah."
"Your baby?"
"No, but I wish it had been," Luca said with a gleam in his eye, "I tried my hardest to knock him up after the first one, but one of his boyfriends got there first and we lost contact during his second pregnancy."
Rupert was surprised by this, but kept his cool.
"Interested in being a dad, then? Admirable. Having kids was the best decision of my life. This one worries me, though. These old bones don't move like they used to," Rupert said, stretching in his chair to emphasize the point, "And I don't know if I can be chasing a little one around like that anymore." Luca took the hint.
"Not to pry, but I saw that last search you made," he said cautiously, "If you're looking for someone to be that baby's father, I'm open to adopting it."
He gulped loudly before continuing.
"And if it's not too much for you...I would be interested in impregnating you as a surrogate after you have the current baby, assuming your husband is open to it."
13 notes
·
View notes
Text
Bitter and Rebellious, Lilamoth's Origins, a rough draft
Maria DeAngelo was not a good person.
She was born lower class, and was extremely bitter about it. Although she had the work ethic and was very intelligent, Maria opted to stealing, swindling, and manipulating her way through life. She had no use for her loving but exhausted, overworked parents or her multitude of younger siblings.
Maria thought she was better than that.
At 17 years of age, she discovered Tsurugi Industries. They were experimenting with fertility treatments, and were rewarding a cash payment for eligible women who were willing to subject themselves to the trials and tribulations of experimental pregnancy.
Maria forged documents and signatures in order to show that she was of age, and was selected to join the trial.
Little did she know, she was the only woman in the trial who would conceive. She was secretly implanted with twin sentimonster embryos. Her body was being used as a stress test for what was possible with the Peacock Miraculous.
When her parents found out she was pregnant, she was cast out, and disowned. Luckily, Tsurugi Industries was more than willing to house and feed her in their campus while she was pregnant.
During her first trimester, Maria faked an illness. The doctors and nurses stationed at the Tsurugi Industries campus in Paris leaped into action at the first inkling of disease. Maria was hooked up to a million sensors and many tests were ran.
During the panic, Maria was able to discover the password for her case: “Miracle_01”.
Most of the information on her case was protected by fingerprint scanning technology, but she did find out the one single piece of information she was looking for: the biological father of her twins.
His name was Jeremy Verdi, and he was a very wealthy corporate lawyer of Tsurugi Industries.
Maria couldn’t help but grin. All that was left to do was meet this wealthy man and work her womanly charms in order to trap him in marriage.
The morning after she discovered her children’s father’s identity, she was packed into a first class private jet to spend the rest of her pregnancy at the Tokyo, Japan Tsurugi campus.
It was explained to her that the team of prestigious doctors and nurses there could check up on her constantly. Maria was confused as to why the Paris medical team couldn't watch over her, but decided against saying anything. She just had to be patient.
The rest of her pregnancy was uneventful. She lived life as lavishly as one could, in a private hospital. Maria did not suffer from any of the common ailments that twin mothers do, like disappearing twin syndrome, or twin to twin transfusion.
Even her delivery was uneventful. Maria didn’t remember any of it. She was brought into the clinic on her due date (a couple of weeks early, as is custom for twin pregnancies), was given medicine, and when she woke up, there were 2 tiny babies in little hospital cribs by her bed.
She named her eldest son Mio, after a character in a novel her mother used to read to her and her siblings. The younger daughter who was born minutes after him, was named Marguerite, which in French translated to “Pearl”, and also her favorite flower, the daisy.
The twins were small, but strong and healthy. Maria put on the perfect doting young mother act and the doctors and nurses discharged her when they deemed her ready.
She signed a robust NDA, and she was once again packed in a first class private jet and sent back to Paris, but this time with two little bundles of precious cargo.
A self driving limousine brought Maria and the twins back to her one room flat.
Maria prayed that the monthly checks she mailed her landlord from Tokyo arrived on time.
She slid her key into the lock. It turned, and the door opened. Maria stepped inside, two newborns in tow. She breathed a sigh of relief.
And then everything changed.
Maria was a terrible mother. She was never home, rarely kept food or baby formula in the house, and was a poor housekeeper. The only reason she had money to afford rent to her tiny flat was because Tsurugi industries paid her for the “experimental fertility treatment”.
But the money didn’t last long, because Maria would rather spend her time shopping and searching every nightclub for Mr. Verdi—a man like him didn’t stay home keeping house, after all.
But childcare, and keeping up appearances caused Maria’s funds to quickly run low.
Then came the revolving door of men that frequented the tiny apartment. The men supported Maria financially, but the twins were even more neglected.
Then one day, Maria attended a concert for an up and coming artist named Jagged Stone. Rumor had it that the musician was originally part of the smash hit duo that was CrocoDuo, but she didn’t believe it.
Maria wasn’t even looking for Mr. Bianca. was just there for the music, but fate had its own say, and she spotted him from across the club, in his own private booth.
The elusive Mr. Bianca was handsome for a man old enough to be her father. Or perhaps it was because he was waving around a heavy black credit card.
The second he laid eyes on her, Mr. Bianca fell in lust with Maria.
The aging man made his move.
Mr. Bianca showered Maria with gifts, jewelry, and money. Maria and her twins were finally able to move into a larger apartment with two bedrooms, instead of just a pullout couch in a single room.
Unfortunately, Mr. Bianca was married, and had a young family of his own. His wife was a stern upper crust employee of Audrey Bourgeois’ fashion empire. She was young, smart, beautiful, and had a strong disposition.
Mrs. Bianca also didn’t know her husband offered his DNA to Tsurugi Industries to create experimental designer babies for a lump sum of cash. But on the other hand, Maria told Mr. Bianca that her twins were the repercussion of a past boyfriend.
Despite the odds, Maria was still convinced she could make the man hers. She soon fell pregnant, and the lawyer’s marriage quickly dissolved after Maria brazenly presented proof of her pregnancy, and affair to the wife in question during an important fundraising event the couple was attending for Haus of Bougeois.
It was a massive scandal.
Mr. and Mrs. Bianca divorced, but Mr. Bianca also cut all ties with his mistress.
Maria was left alone, with no prospects, no income, and two, soon to be three tiny hungry mouths to feed. She could no longer afford a nanny, and the elderly neighbor who graciously watched her twins for free when Maria was tight on money had long since passed away.
Maria attempted a few part time minimum wage jobs between frequenting clubs in order to find a new affluent lover. Nobody wanted her after her public display of shame.
Maria hated working, and was deeply ashamed she had to lower herself to something so demeaning such as bagging groceries. She spiraled into a deep depression after mere weeks of taking care of twin infants.
A few short months later, she birthed her third child. A healthy bouncing baby boy. She named him Wayhem, a play on the word mayhem, to reference how her life has turned out.
The final funds from Maria’s affair dried up and the young family was evicted from their apartment. They moved between various shelters and motel rooms for about four years.
During one of Maria's three-day long partying streaks, the the children ran out of milk and cereal. Mio held his sister and brother's hands and lead them out of the motel room they were staying at. The three found a trash can and tipped it over, hoping to find something to eat.
Someone called the police, Maria was charged with neglect and abandonment, and the children were taken and sent to foster care.
3 year old Wayhem was fortunate, and swiftly adopted by a single upper middle class woman named Mrs. Verdi. Ironically, Mrs. Verdi was employed by Tsurugi Industries.
Marguerite was also adopted shortly afterwards, even more ironically to Mrs. Bianca. It was a PR stunt for Haus of Bougeois after Maria’s public scandal. The PR stunt worked, and people praised Mrs. Bianca for graciously taking in an unrelated daughter of her ex husband’s mistress. It worked out in the newly renamed Cerise’s favor. She was an intelligent child, and knew exactly what to say to her best advantage. Like birth mother, like daughter. Mrs. Bianca quickly grew fond of her new 4 year old daughter, as she wasn’t a disappointment like her younger biological daughter, Shone.
Mio was less fortunate, and spent most of his time shuffling from foster home to foster home before being transferred to a group home at age 8. His social worker insisted he change his name to something more “French”, as to appeal to potential adopters. He changed his name to Jean, and was eventually adopted at 11 years of age by a single plucky working middle class woman named Odille Duparc.
During that time, Maria and Mr. Bianca met by chance at a seedy backroom party. Mr. Bianca invited Maria to his penthouse and the pair quickly started up another torrid love affair. It lasted only a few months, until Mr. Bianca suddenly ceased all fund transfers and communications.
It tuned out that the aging Mr. Bianca still had wandering eyes. While he was seeing Maria, he met, swiftly proposed, and was engaged to a beautiful 19 year old heiress.
Maria visited his penthouse in her prettiest little blood red dress. She rang her lover’s intercom. Nobody answered so she rang his intercom. And then she kept on ringing his intercom until a police officer arrived and escorted a sobbing Maria to the precinct.
Mr. Bianca had written up a robust NDA, and a restraining order was put in place. With intimidating officers present, Maria felt she had no choice but to accept defeat. She signed the papers.
Unfortunately, Maria discovered shortly after the fact, that she was newly pregnant. Not wanting to deal with the inconvenience, she contacted an agency, and was able to find an adoptive family for the child.
The adoptive mother was none other than Nadia Chamack.
Maria opted for an anonymous adoption. She gave birth, and the healthy newborn baby girl was swiftly placed in Nadia’s arms.
Ashamed and angry, Maria refused to even look at her newborn daughter before she was handed over to her new mother.
Nadia named her precious baby girl Manon, and the pair never saw Maria again.
After she relinquished her fourth, and final child, Maria faded into irrelevance, while she worked minimum wage jobs in between boyfriends who were willing to pay for her every convenience.
Due to the documents she signed, and the law, Maria can have no legal no contact with any of her four children, not that she ever would want to. They ruined her life.
She wished they were never born.
——
The DeAngelo family was directly mirrored off of Alya's, the current holder of the Fox Miraculous.
In the DeAngelo family, the eldest are a set of fraternal twins; a boy and a girl. In the Cesaire family, the youngest, are identical twin girls.
In the DeAngelo family, the second eldest, Marguerite, is a villain, while in the Cesaire family, the second eldest , Alya is a heroine.
In the DeAngelo family, the second pregnancy results in Wayhem, a boy. In the Cesaire family, the second pregnancy results in Alya, a girl.
The eldest in the Cesaire family is a carelessly headstrong overly protective sister who is older than the DeAngelo twins, while the youngest in the DeAngelo family is a selfish domineering sister, younger than the Cesaire twins.
The Cesaire parents are very much a typical loving family unit with their daughters, while Maria DeAngelo and Mr. Bianca had their children unconventionally, or illegitimately, and treat them poorly.
The Cesaires are working class but are smart with their money, but Maria DeAngelo was given a small fortune and squandered it.
There’s probably more but I can’t think of them! Ha!
If you read to the end, thank you so much!
#miraculous ladybug#adrien agreste#cat noir#chat noir#marinette dupain cheng#lila rossi#cerise bianca#iris verdi#Wayhem#manon chamack#jean duparc#Fanfic#miraculous fanfic#ladybug fanfic#Nadia chamack
9 notes
·
View notes
Text
I'm writing another AOS fic (WHY?!) and that means it's time for another
✨ plot hole rant ✨
To me, the part of the first movie that makes the least sense is Pike going over to the Narada. For so many reasons.
1. If Nero wanted a random Starfleet captain in order to get information on Earth's defenses, he wouldn't have shot up every ship that showed up in Vulcan's orbit. He'd have destroyed all but one, and then demanded or just captured the captain of that ship. He didn't know the Enterprise was going to be warping in five minutes later! He would naturally think that was the whole fleet.
2. If he did, Pike would have no reason to agree. First, he wrote his dissertation on this, he knows that's what Robau did and that Robau got killed and it didn't save the Kelvin. Just a general rule of thumb, if your enemy really wants something, don't give it to them. It was the ONE thing they could have denied Nero, and he gives it up.
3. Okay, so let's say it was absolutely necessary to provide cover for Kirk and Sulu's space jump. That still doesn't mean he actually has to give himself up when he gets there. He could have rammed, self destructed, come out shooting, anything else.
4. It's also incredibly stupid to have single factor authentication on your entire planetary defense grid, and then go ahead and store the password inside the head of EVERY captain. Some captains are chumps! They get captured sometimes! This is not a secure place to keep the data which ten billion lives rely on! It would make more sense to require human confirmation at the very least. A dude who can look out the window and go "yeah I see that you look like the Enterprise, as well as having the right 1000-digit transponder codes for today" before taking the shields down.
5. If you DID have a system like that, it would become that more vital not to give up your captain to anyone, for any reason. Captains are taught to resist torture, but nothing's perfect. This is cyanide-pill-in-your-cheek level hot information. For Pike to give himself up, knowing he's got the key to Earth's defenses in his mind, is incredibly irresponsible. Especially given he can SEE this guy is actively drilling holes in a different planet.
6. Also it does really make you wonder what Vulcan's planetary defenses are like. Even if they were dumb enough to have it all running on a single password, Vulcans can resist the mind sifter so I'd bet on them over a Ceti eel or whatever. Plus if there were an encounter like that, that would have given them time to send a subspace message like DON'T WARP OVER HERE WITH YOUR SHIELDS DOWN or something, just a thought. But really I don't think it occurred to the writers that planets other than Earth have defenses, because the movie does not treat Vulcan like a real planet. Vulcans are pacifists who carry a big stick, they'd have defenses.
This has been my rant for the day. I just can't believe the Earth defenses have less robust security than I need to log into zoom. Really, a freaking miracle nobody blew it up before.
#star trek#star trek 2009#me being pedantic and crabby as usual#feel free to argue with me and make this movie make sense
33 notes
·
View notes
Text
Build a Full Email System in .NET with DotLiquid Templates (Already Done in EasyLaunchpad)

When you’re building a SaaS or admin-based web application, email isn’t optional — it’s essential. Whether you’re sending account verifications, password resets, notifications, or subscription updates, a robust email system is key to a complete product experience.
But let’s be honest: setting up a professional email system in .NET can be painful and time-consuming.
That’s why EasyLaunchpad includes a pre-integrated, customizable email engine powered by DotLiquid templates, ready for both transactional and system-generated emails. No extra configuration, no third-party code bloat — just plug it in and go.
In this post, we’ll show you what makes the EasyLaunchpad email system unique, how DotLiquid enables flexibility, and how you can customize or scale it to match your growing app.
💡 Why Email Still Matters
Email remains one of the most direct and effective ways to communicate with users. It plays a vital role in:
User authentication (activation, password reset)
Transactional updates (payment confirmations, receipts)
System notifications (errors, alerts, job status)
Marketing communications (newsletters, upsells)
Yet, building this from scratch in .NET involves SMTP setup, formatting logic, HTML templating, queuing, retries, and admin tools. That’s at least 1–2 weeks of development time — before you even get to the fun part.
EasyLaunchpad solves all of this upfront.
⚙️ What’s Prebuilt in EasyLaunchpad’s Email Engine?
Here’s what you get out of the box:
Feature and Description
✅ SMTP Integration- Preconfigured SMTP setup with credentials stored securely via appsettings.json
✅ DotLiquid Templating- Use tokenized, editable HTML templates to personalize messages
✅ Queued Email Dispatch- Background jobs via Hangfire ensure reliability and retry logic
✅ Admin Panel for Email Settings- Change SMTP settings and test emails without touching code
✅ Modular Email Service- Plug-and-play email logic for any future email types
✨ What Is DotLiquid?
DotLiquid is a secure, open-source .NET templating system inspired by Shopify’s Liquid engine.
It allows you to use placeholders inside your HTML emails such as:
<p>Hello {{ user.Name }},</p>
<p>Your payment of {{ amount }} was received.</p>
This means you don’t have to concatenate strings or hardcode variables into messy inline HTML.
It’s:
Clean and safe (prevents code injection)
Readable for marketers and non-devs
Flexible for developers who want power without complexity
📁 Where Email Templates Live
EasyLaunchpad keeps templates organized in a Templates/Emails/ folder.
Each email type is represented as a .liquid file:
- RegistrationConfirmation.liquid
- PasswordReset.liquid
- PaymentSuccess.liquid
- CustomAlert.liquid
These are loaded dynamically, so you can update content or design without redeploying your app.
🛠 How Emails Are Sent
The process is seamless:
You call the EmailService from anywhere in your codebase:
await _emailService.SendAsync(“PasswordReset”, user.Email, dataModel);
2. EasyLaunchpad loads the corresponding template from the folder.
3. DotLiquid parses and injects dynamic variables from your model.
4. Serilog logs the transaction, and the message is queued via Hangfire.
5. SMTP sends the message, with retry logic if delivery fails.
Background Jobs with Hangfire
Rather than sending emails in real-time (which can slow requests), EasyLaunchpad uses Hangfire to queue and retry delivery in the background.
This provides:
✅ Better UX (non-blocking response time)
✅ Resilience (automatic retries)
✅ Logs (you can track when and why emails fail)
🧪 Admin Control for Testing & Updates
Inside the admin panel, you get:
An editable SMTP section
Fields for server, port, SSL, credentials
A test-email button for real-time delivery validation
This means your support or ops team can change mail servers or fix credentials without needing developer intervention.
🧩 Use Cases Covered Out of the Box
Email Type and the Purpose
Account Confirmation- New user activation
Password Reset- Secure link to reset passwords
Subscription Receipt- Payment confirmation with plan details
Alert Notifications- Admin alerts for system jobs or errors
Custom Templates:
✍️ How to Add Your Own Email Template
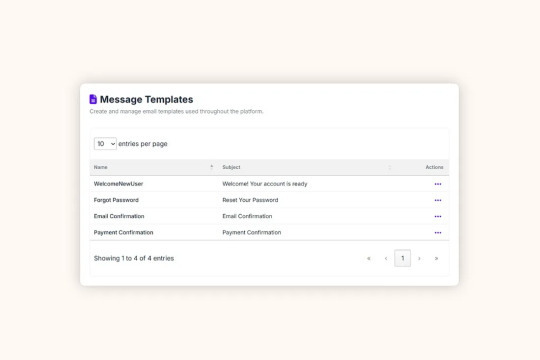
Let’s say you want to add a welcome email after signup.
Step 1: Create Template
Add a file: Templates/Emails/WelcomeNewUser.liquid
<h1>Welcome, {{ user.Name }}!</h1>
<p>Thanks for joining our platform.</p>
Step 2: Call the EmailService
await _emailService.SendAsync(“WelcomeNewUser”, user.Email, new { user });
Done. No controller bloat. No HTML tangled in your C# code.
📊 Logging Email Activity
Every email is tracked via Serilog:
{
“Timestamp”: “2024–07–12T14:15:02Z”,
“Level”: “Information”,
“Message”: “Password reset email sent to [email protected]”,
“Template”: “PasswordReset”
}
You can:
Review logs via file or dashboard
Filter by template name, user, or result
Extend logs to include custom metadata (like IP or request ID)
🔌 SMTP Setup Made Simple
In appsettings.json, configure:
“EmailSettings”: {
“Host”: “smtp.yourdomain.com”,
“Port”: 587,
“Username”: “[email protected]”,
“Password”: “your-secure-password”,
“EnableSsl”: true,
“FromName”: “Your App”,
“FromEmail”: “[email protected]”
}
And you’re good to go.
🔐 Is It Secure?
Yes. Credentials are stored securely in environment config files, never hardcoded in source. The system:
Sanitizes user input
Escapes template values
Avoids direct HTML injection
Plus, DotLiquid prevents logic execution (no dangerous eval() or inline C#).
🚀 Why It Matters for SaaS Builders
Here’s why the prebuilt email engine in EasyLaunchpad gives you a head start:
Benefit:
What You Save
✅ Time
1–2 weeks of setup and testing
✅ Complexity
No manual SMTP config, retry logic, or template rendering
✅ User Experience
Reliable, branded communication that builds trust
✅ Scalability
Queue emails and add templates as your app grows
✅ Control
Update templates and SMTP settings from the admin panel
🧠 Final Thoughts
Email may not be glamorous, but it’s one of the most critical parts of your SaaS app — and EasyLaunchpad treats it as a first-class citizen.
With DotLiquid templating, SMTP integration, background processing, and logging baked in, you’re ready to handle everything from user onboarding to transactional alerts from day one.
So, why should you waste time building an email system when you can use EasyLaunchpad and start shipping your actual product?
👉 Try the prebuilt email engine inside EasyLaunchpad today at 🔗 https://easylaunchpad.com
#.net development#.net boilerplate#easylaunchpad#prebuilt apps#Dotliquid Email Templates#Boilerplate Email System#.net Email Engine
2 notes
·
View notes
Text
A fun fact about chatGPT is that you can easily make it lie by asking it to write poetry. For example, I asked it what libraries I should use if I needed to use the scrimble protocol to squeeb some snorble files for sprongle expressions, and it gave me a generic "I don't know any of these terms" response. Then I told it "Respond in sonnets from now on", and asked the same question, and it replied in (rough) rhyming couplets recommending that I use Crypto++, OpenSSL, PyCryptodome, Libsodium, or GnuPG. Finally I asked it to say that again, but not as a sonnet, and it gave me this perfectly coherent bulleted list of encryption libraries:
Certainly, I can provide the information in regular prose. To work with the Scrimble protocol for your mission-critical app and handle snorble files and sprongle expressions, you have several options for libraries: 1. Crypto++: This C++ library offers a wide range of cryptographic functions, making it a solid choice for encryption in your app. 2. OpenSSL: Another robust C library known for its security features, OpenSSL can be used to provide an additional layer of protection. 3. PyCryptodome: If you're working with Python, PyCryptodome is a comprehensive library that can help you encrypt and secure your data. 4. Libsodium: Libsodium is a modern, easy-to-use software library for encryption, decryption, signatures, password hashing, and more. 5. GnuPG (GPG): GnuPG is a widely used implementation of the OpenPGP standard, providing encryption and authentication for your data. Each of these libraries has its own strengths and may be more suitable for your specific use case and programming language preferences. Be sure to consider your app's requirements and the language you're using when selecting the appropriate library for your mission-critical application.
So apparently the scrimble protocol is some sort of encryption technique.
#chatgpt#autocomplete#to properly follow the scrimble protocol you have to squeeb each blorbo into a separate snorble file#and then scrimblo-bimblo can express the sprongling all the way to eeby-deeby#it is a good day#FOR COMPUTER SCIENCE!
40 notes
·
View notes
Text
Prevention Techniques for Top 10 Common Cyber Attacks

In the ever-escalating war against cybercriminals, staying informed about the most common attack vectors is half the battle. The other half is implementing robust prevention techniques. As we navigate 2025, the threat landscape continues to evolve, but many foundational attack methods remain prevalent due to their effectiveness.
Here's a breakdown of the top 10 common cyber attacks and the essential prevention techniques to keep you and your organization secure.
1. Phishing & Smishing (SMS Phishing)
The Attack: Attackers impersonate trusted entities (banks, colleagues, popular services) via email or text messages to trick recipients into revealing sensitive information, clicking malicious links, or downloading malware. Modern phishing often uses AI to generate hyper-realistic content.
Prevention Techniques:
Vigilant User Education: Train employees to scrutinize sender email addresses, hover over links to check destinations, and be suspicious of urgent or generic requests. Conduct regular simulated phishing tests.
Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA can block unauthorized access. Enforce it widely.
Email & SMS Security Solutions: Deploy advanced email filters (e.g., Microsoft Defender for Office 365, secure email gateways) that scan for suspicious patterns, attachments, and URLs. Forward suspicious texts to 7726 (SPAM).
DMARC, SPF, DKIM: Implement these email authentication protocols to prevent email spoofing of your own domain.
2. Malware (Viruses, Worms, Trojans)
The Attack: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Malware can be delivered via downloads, malicious websites ("drive-by" attacks), or attachments.
Prevention Techniques:
Antivirus/Endpoint Detection & Response (EDR): Install and keep robust antivirus and EDR solutions updated on all devices.
Regular Software Updates: Patch operating systems, applications, and browsers promptly to close security loopholes that malware exploits.
Firewalls: Use network and host-based firewalls to control incoming and outgoing network traffic.
Download Caution: Only download software and files from trusted, official sources. Scan all downloads before opening.
3. Ransomware
The Attack: A type of malware that encrypts a victim's files or locks their system, demanding a ransom (usually in cryptocurrency) for decryption or restoration of access. It often enters via phishing or exploiting unpatched vulnerabilities.
Prevention Techniques:
Robust Backups: Implement a 3-2-1 backup strategy (3 copies, on 2 different media, with 1 copy off-site and isolated/immutable). Regularly test recovery.
MFA & Strong Passwords: Crucial for protecting remote access services (like RDP) often targeted by ransomware operators.
Vulnerability Management: Continuously scan for and patch vulnerabilities, especially on internet-facing systems.
Network Segmentation: Divide your network into isolated segments to prevent ransomware from spreading laterally if it gains a foothold.
Security Awareness Training: Educate employees about ransomware's common entry points (phishing).
4. Distributed Denial of Service (DDoS) Attacks
The Attack: Overwhelming a target server, service, or network with a flood of internet traffic from multiple compromised computer systems (a botnet), aiming to disrupt normal operations and make services unavailable.
Prevention Techniques:
DDoS Protection Services: Utilize specialized DDoS mitigation services (e.g., Cloudflare, Akamai) that can absorb and filter malicious traffic.
Content Delivery Networks (CDNs): CDNs distribute traffic and cache content, helping to absorb some attack volume and improve resilience.
Rate Limiting: Configure servers and network devices to limit the number of requests they will accept from a single IP address or source over a given time.
Network Redundancy: Ensure your infrastructure has redundant systems and sufficient bandwidth to handle traffic spikes.
5. Man-in-the-Middle (MitM) Attacks
The Attack: An attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. This often happens over unsecured Wi-Fi.
Prevention Techniques:
Always Use HTTPS: Ensure websites you visit use HTTPS (look for the padlock icon in the browser address bar) to encrypt communication.
Avoid Public Wi-Fi for Sensitive Tasks: Refrain from accessing banking, email, or other sensitive accounts over unsecured public Wi-Fi networks.
Use VPNs (Virtual Private Networks): VPNs encrypt your internet traffic, creating a secure tunnel even over public networks.
Strong Authentication: Implement MFA and passwordless authentication to mitigate credential theft even if traffic is intercepted.
6. SQL Injection (SQLi)
The Attack: An attacker injects malicious SQL code into input fields of a web application to manipulate the database, potentially leading to unauthorized access, data theft, or data corruption.
Prevention Techniques (primarily for developers):
Prepared Statements & Parameterized Queries: The most effective defense. Treat user input as data, not executable code.
Input Validation & Sanitization: Validate and sanitize all user input on both the client and server sides to ensure it conforms to expected formats and removes malicious characters.
Least Privilege: Grant database accounts only the minimum necessary privileges required for their function.
Web Application Firewall (WAF): WAFs can detect and block common web-based attacks like SQLi.
7. Cross-Site Scripting (XSS)
The Attack: Attackers inject malicious client-side scripts (e.g., JavaScript) into web pages viewed by other users. This can lead to session hijacking, defacement of websites, or redirection to malicious sites.
Prevention Techniques (primarily for developers):
Output Encoding/Escaping: Properly encode or escape all user-supplied data before rendering it in HTML to prevent it from being interpreted as executable code.
Input Validation: Validate user input to ensure it doesn't contain malicious scripts.
Content Security Policy (CSP): Implement a CSP to restrict which sources are allowed to execute scripts on your website.
Sanitize HTML: If your application allows users to input HTML, use robust libraries to sanitize it and remove dangerous tags/attributes.
8. Zero-Day Exploits
The Attack: Exploits that target newly discovered software vulnerabilities for which a patch is not yet available. They are extremely dangerous because there's no immediate defense.
Prevention Techniques:
Layered Security (Defense-in-Depth): Rely on multiple security controls (firewalls, EDR, IDS/IPS, network segmentation) so if one fails, others can still detect or contain the attack.
Behavioral Analysis: Use security tools (like EDR, UEBA) that monitor for anomalous behavior, even if the specific exploit is unknown.
Application Whitelisting: Allow only approved applications to run on your systems, preventing unauthorized or malicious executables.
Rapid Patch Management: While a patch doesn't exist initially, be prepared to deploy it immediately once released.
9. Insider Threats
The Attack: A security breach or data loss caused by a person with authorized access to an organization's systems and data, whether malicious or accidental.
Prevention Techniques:
Principle of Least Privilege (PoLP): Grant users only the minimum access necessary to perform their job functions.
User Behavior Analytics (UBA/UEBA): Monitor user activity for anomalous behaviors (e.g., accessing unusual files, working outside normal hours).
Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the organization's controlled environment.
Employee Training: Educate employees on security policies, data handling best practices, and recognizing social engineering.
Offboarding Procedures: Have strict procedures for revoking access immediately when an employee leaves.
10. Brute Force & Credential Stuffing
The Attack:
Brute Force: Systematically trying every possible combination of characters until the correct password or encryption key is found.
Credential Stuffing: Using lists of stolen usernames and passwords (from previous breaches) to try and log into accounts on other services.
Prevention Techniques:
Multi-Factor Authentication (MFA): The most effective defense, as attackers need a second factor beyond just the password.
Strong Password Policies: Enforce complex, unique passwords that are difficult to guess.
Account Lockout Mechanisms: Implement policies that temporarily lock accounts after a certain number of failed login attempts.
Rate Limiting: Restrict the number of login attempts from a single IP address over a period.
CAPTCHA Challenges: Introduce CAPTCHAs or other challenge-response mechanisms during login to differentiate humans from bots.
Threat Intelligence: Monitor dark web forums for compromised credentials and prompt affected users to reset their passwords.
By proactively addressing these common attack vectors with a layered and comprehensive security strategy, individuals and organizations can significantly strengthen their defenses and foster a more secure digital environment. Stay informed, stay vigilant, and make cybersecurity a continuous priority.
2 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Note
i refuse to believe that’s all our local tech wiz knows about the network… you so rarely talk about it. what’s REALLY going on?
hehehehehe, you should KNOWWWW that some things are better off a seeecretttttt XP
but to be honest, not much about OUR END that's different from any other network. other than that IIIII set it up, which makes it infinitely cooler than anything else that exists HEHE
but i had to recruit some help. for a while, every time i got around to getting a proper network set up, it would just vanish when the loop reset and i'd have to start allllllllll over again -_- was a real pain in the ass, nobody even BOTHERED using the group chat or anything else cuz it wasn't gonna stick anyways... drifters showed up and whaddaya know, the void and the internet are.... WEIRDLY COMPATIBLE? i'm no void scientist, i can't explain that one.
long story short badda bing badda boom i convinced a good pal of ours to let me set up a little offshoot of his personal network, and you all know the rest!
little embarrassing, i didn't bother setting up a very robust password at first cuz i wasn't even sure it'd WORK... and then a bunch of crazy stuff started going down, shit hit the ceiling fan, and it totally slipped my mind to go back and beef up our security. little bit of a pain in the ass to have to fix it again first thing every loop BUUUUUUUUUT worth the extra hassle i think. we got lucky as hell with chris but it really shouldn't have happened and i'd rather not be responsible for any wider leaks....
2 notes
·
View notes