#user-friendly accounting software
Explore tagged Tumblr posts
Text
Simplify Accounting with TRIRID Biz

Managing finances can be a challenge for businesses, but TRIRID Biz Accounting and Billing Software makes it easy. TRIRID Biz is designed to empower businesses of all sizes with a user-friendly, comprehensive solution for all your accounting needs.
Key Features of TRIRID Biz:
Intuitive Dashboard
Get real-time insights into your financial performance with an easy-to-navigate dashboard.
Automated Billing and Invoicing
Save time with automated invoice generation and payment tracking, reducing manual errors.
GST Compliance
Stay compliant by easily calculating and reporting under GST.
Accessibility on multiple devices
Have access to your data, anytime from your laptop, tablet or smartphone.
Secure Data
In TRIRID Biz, access your sensitive financial information with encryption robustness.
Custom reports
Generate detailed financial reports based on your need to make important business decisions
Get Started Today: Simplify Your Accounting by TRIRID Biz Accounting and Billing Software.
Call @ +91 8980010210 / +91 9023134246
Visit @ https://tririd.com/tririd-biz-gst-billing-accounting-software
#Best billing software in Ahmedabad Gujarat#User-Friendly Accounting Software#Time-Saving Billing Software#TRIRID-Billing software in Bopal in Ahmedabad#TRIRID-Billing software in ISCON-Ambli road-ahmedabad
0 notes
Text
How to Choose the Best Accounting Software for Your Business
Introduction In the fast-moving environment related to the business world, keeping yourself on top of the finances will never be an easy task. In reality, a company can easily slip into disarray without proper supervision of its finances. No matter whether yours is a small startup or a big corporation, the right kind of accounting software will certainly work wonders in the smooth flow of financial operations. But with accounting software options galore, how do you choose a software that’s suitable for your business? The guide from TechtoIO will take you through everything you need to know to make an informed decision. Read to continue
#analysis#science updates#tech news#trends#adobe cloud#nvidia drive#science#business tech#technology#tech trends#CategoriesSoftware Solutions#Tagsaccounting software comparison#AI in accounting software#automated invoicing software#best accounting software for business#blockchain accounting solutions#choosing accounting software#cloud-based accounting software#expense tracking software#financial reporting tools#FreshBooks review#integrating accounting software#mobile accounting software#QuickBooks vs Xero#scalable accounting software#secure accounting software#small business accounting software#top accounting software 2024#user-friendly accounting software#Wave accounting software
0 notes
Text
Why Every Business Needs Online Accounting Software in Zambia 2025
Accounting is the systematic and detailed recording of a business’s financial transactions. It encompasses various types, including small business accounting, government accounting, management accounting, and corporate accounting. The significance of accounting lies in its ability to track an organization’s financial health and ensure reliability. Without proper accounting, business owners would struggle to assess their financial position or determine profitability.
In today’s business landscape, the role of accountants has evolved beyond simply managing accounts and finances. Modern accountants take on multiple responsibilities across various departments, making their expertise essential to business operations. Their role extends beyond numerical skills, encompassing tasks such as budgeting, financial reporting, and managing external payments. As a result, accountants play a more dynamic and strategic role than traditionally perceived.
Contrary to the common misconception that accounting is solely about bookkeeping, management accounting plays a pivotal role in financial decision-making. It enables businesses to allocate resources efficiently, track performance, and achieve strategic objectives. In an increasingly competitive business environment, effective financial management is crucial for long-term success.

What is Online Accounting Software?
Online accounting software is a cloud-based solution that helps individuals and businesses manage their finances digitally, eliminating the need for manual bookkeeping. Accessible via a computer or mobile device with an internet connection, it offers essential accounting features such as accounts payable, accounts receivable, payroll, and inventory management. Unlike traditional on-premise software, online accounting software is hosted on remote servers, enabling users to access financial data securely from anywhere, anytime.
Why Is Accounting Important?
Accounting is essential for running a business as it helps track income and expenses, ensures compliance with legal requirements, and provides investors, management, and government entities with accurate financial data for decision-making. Accounting plays a vital role in overseeing internal management and meeting the needs of external stakeholders such as investors, creditors, and regulatory agencies. Internally, it enables businesses to track performance, control costs, and make data-driven decisions. Externally, it ensures transparency by providing an accurate financial picture, indicating profitability and overall financial stability. Proper accounting also helps businesses comply with tax laws and regulatory requirements, reducing the risk of legal issues.
Key Roles of Accounting in Business
Budget Planning
Tax Compliance
Profit & Loss Statement (Income Statement)
Balance Sheet (Statement of Financial Position)
Recording Journal Entries
Statutory Compliance
Strategic Decision-Making
1. Budget Planning
Budgeting is crucial for any business, as it enables strategic planning, expense monitoring, and profit maximization. Effective budgeting relies on maintaining accurate financial records, which accountants facilitate by collecting and organizing financial data. These records serve as the foundation for future budget planning and financial forecasting.
2. Tax Compliance
One of the most common interactions with accounting occurs during tax season. Proper financial record-keeping simplifies tax filing by ensuring that income and expenses are well-documented throughout the year. This helps businesses comply with tax laws and avoid penalties.
3. Profit & Loss Statement (Income Statement)
The income statement provides a clear picture of a business’s financial performance over a specific period. It highlights revenue, expenses, and the resulting net profit or loss, helping business owners assess profitability and make informed financial decisions.
4. Balance Sheet (Statement of Financial Position)
The balance sheet presents a snapshot of a company’s financial position at a given point in time. It details assets, liabilities, and equity, showing the overall financial health of the business. The excess of assets over liabilities represents the company’s capital.
5. Recording Journal Entries
Journal entries serve as the foundation of accounting records, documenting each transaction with details of when, why, and how much was involved. Businesses use either a single-entry or double-entry system, with the latter ensuring that every transaction affects two accounts—one as a debit and the other as a credit—to maintain financial accuracy.
6. Statutory Compliance
Adhering to financial laws and regulations is crucial for businesses. A well-structured accounting system ensures compliance with government-mandated obligations, such as sales tax, income tax, VAT, pension funds, and other liabilities. Accountants play a key role in managing these responsibilities, reducing the risk of legal issues.
7. Strategic Decision-Making
Effective accounting and financial management contribute to business success by informing strategic decisions. With accurate data, businesses can create realistic budgets, analyze financial trends, and develop strategies to achieve their financial goals and long-term growth.
Why Online Accounting Software is Beneficial
Here are some key advantages of using online accounting software:
1. Access Anytime, Anywhere
You can manage your finances from anywhere, even while travelling, as long as you have an internet connection.
2. Cost-Effective
Online accounting software is an affordable option, especially for small businesses, as it eliminates the need for expensive hardware or IT maintenance.
3. Automatic Updates & Data Security
Software providers handle updates and security, ensuring your financial data is always protected and the system remains up to date.
4. Easy Collaboration
Multiple users, including team members and accountants, can access and update financial data in real-time, no matter where they are.
5. Enhanced Data Security
Cloud-based accounting solutions use advanced security measures to protect financial information, making it safer than traditional paper records.
6. Simplified Tax Management
The software helps streamline tax calculations and filings, reducing the hassle of tax season.
7. Scalable for Business Growth
As your business expands, online accounting software can scale with you, offering features that adapt to growing financial needs.
How to Choose the Right Online Accounting Software in Zambia
Selecting the right online accounting software is essential for managing your business finances efficiently. Here are key factors to consider when making your choice:
Company Size
Business Model
Essential & Advanced Features
Compliance with Local Regulations
Ease of Use
Scalability
1. Company Size
The size of your business determines your accounting needs. Larger businesses require more advanced features, such as detailed financial reporting and multi-user access, while startups and small businesses may only need basic bookkeeping tools.
2. Business Model
While major accounting software solutions cater to various industries, some providers specialize in specific business types. For example, certain platforms are designed for e-commerce businesses, while others focus on B2B service providers. Choosing software that aligns with your business model ensures it meets your specific needs.
3. Essential & Advanced Features
Ensure the software includes the features your business requires. Most platforms offer core functionalities like general ledger management, accounts payable, and bank reconciliation. However, if you need advanced tools such as inventory management, payroll processing, or financial forecasting, verify that these features are included before making a decision.
4. Compliance with Local Regulations
Your accounting software should comply with Zambia’s financial and tax regulations, ensuring that financial data is stored securely and reports are generated in accordance with local laws. This helps businesses stay tax-compliant and avoid penalties.
5. Ease of Use
A good accounting system should be user-friendly and intuitive, making it easy to navigate and manage financial transactions. If your business operations are complex, the software should be adaptable to evolving needs. Additionally, consider how quickly new accounts can be set up complicated onboarding processes may indicate that the software isn’t the right fit for your business.
6. Scalability
As your business grows, your accounting software should be able to scale with it. Look for a solution that supports increased transaction volumes, additional users, and expanded functionalities. Choosing scalable software ensures long-term usability and eliminates the need for frequent system changes.
Why adopting online accounting in 2025 is crucial for Zambian businesses?
The right small business accounting software is more than just a tool it forms the foundation of a company’s financial health. It should be flexible enough to adapt and scale as the business grows. By 2025, businesses can no longer rely on outdated manual accounting methods. Investing in a cloud-based accounting system with seamless integrations and real-time financial tracking will save time, minimize errors, and provide better financial control. With the right accounting software, small business owners can shift their focus to what truly matters growing their business, making informed financial decisions, and ensuring long-term success.
Conclusion
When selecting online accounting software for your business, consider key factors such as cost, features, business needs, and your team's capabilities. Online accounting software is one of the most effective ways to manage finances, streamline operations, and ensure accurate financial tracking. With the right software in place, small business owners can focus on growth, make smarter financial decisions, and build a sustainable, successful business.
#Online accounting software#Online accounting software for small business#Online accounting software for business#user friendly accounting software#smart invoice zambia#smart invoice software
0 notes
Text
Why Every Business Needs Online Accounting Software in Zambia 2025
Accounting is the systematic and detailed recording of a business’s financial transactions. It encompasses various types, including small business accounting, government accounting, management accounting, and corporate accounting. The significance of accounting lies in its ability to track an organization’s financial health and ensure reliability. Without proper accounting, business owners would struggle to assess their financial position or determine profitability.
In today’s business landscape, the role of accountants has evolved beyond simply managing accounts and finances. Modern accountants take on multiple responsibilities across various departments, making their expertise essential to business operations. Their role extends beyond numerical skills, encompassing tasks such as budgeting, financial reporting, and managing external payments. As a result, accountants play a more dynamic and strategic role than traditionally perceived.
Contrary to the common misconception that accounting is solely about bookkeeping, management accounting plays a pivotal role in financial decision-making. It enables businesses to allocate resources efficiently, track performance, and achieve strategic objectives. In an increasingly competitive business environment, effective financial management is crucial for long-term success.

What is Online Accounting Software?
Online accounting software is a cloud-based solution that helps individuals and businesses manage their finances digitally, eliminating the need for manual bookkeeping. Accessible via a computer or mobile device with an internet connection, it offers essential accounting features such as accounts payable, accounts receivable, payroll, and inventory management. Unlike traditional on-premise software, online accounting software is hosted on remote servers, enabling users to access financial data securely from anywhere, anytime.
Why Is Accounting Important?
Accounting is essential for running a business as it helps track income and expenses, ensures compliance with legal requirements, and provides investors, management, and government entities with accurate financial data for decision-making. Accounting plays a vital role in overseeing internal management and meeting the needs of external stakeholders such as investors, creditors, and regulatory agencies. Internally, it enables businesses to track performance, control costs, and make data-driven decisions. Externally, it ensures transparency by providing an accurate financial picture, indicating profitability and overall financial stability. Proper accounting also helps businesses comply with tax laws and regulatory requirements, reducing the risk of legal issues.
Key Roles of Accounting in Business
Budget Planning
Tax Compliance
Profit & Loss Statement (Income Statement)
Balance Sheet (Statement of Financial Position)
Recording Journal Entries
Statutory Compliance
Strategic Decision-Making
1. Budget Planning
Budgeting is crucial for any business, as it enables strategic planning, expense monitoring, and profit maximization. Effective budgeting relies on maintaining accurate financial records, which accountants facilitate by collecting and organizing financial data. These records serve as the foundation for future budget planning and financial forecasting.
2. Tax Compliance
One of the most common interactions with accounting occurs during tax season. Proper financial record-keeping simplifies tax filing by ensuring that income and expenses are well-documented throughout the year. This helps businesses comply with tax laws and avoid penalties.
3. Profit & Loss Statement (Income Statement)
The income statement provides a clear picture of a business’s financial performance over a specific period. It highlights revenue, expenses, and the resulting net profit or loss, helping business owners assess profitability and make informed financial decisions.
4. Balance Sheet (Statement of Financial Position)
The balance sheet presents a snapshot of a company’s financial position at a given point in time. It details assets, liabilities, and equity, showing the overall financial health of the business. The excess of assets over liabilities represents the company’s capital.
5. Recording Journal Entries
Journal entries serve as the foundation of accounting records, documenting each transaction with details of when, why, and how much was involved. Businesses use either a single-entry or double-entry system, with the latter ensuring that every transaction affects two accounts—one as a debit and the other as a credit—to maintain financial accuracy.
6. Statutory Compliance
Adhering to financial laws and regulations is crucial for businesses. A well-structured accounting system ensures compliance with government-mandated obligations, such as sales tax, income tax, VAT, pension funds, and other liabilities. Accountants play a key role in managing these responsibilities, reducing the risk of legal issues.
7. Strategic Decision-Making
Effective accounting and financial management contribute to business success by informing strategic decisions. With accurate data, businesses can create realistic budgets, analyze financial trends, and develop strategies to achieve their financial goals and long-term growth.
Why Online Accounting Software is Beneficial
Here are some key advantages of using online accounting software:
1. Access Anytime, Anywhere
You can manage your finances from anywhere, even while travelling, as long as you have an internet connection.
2. Cost-Effective
Online accounting software is an affordable option, especially for small businesses, as it eliminates the need for expensive hardware or IT maintenance.
3. Automatic Updates & Data Security
Software providers handle updates and security, ensuring your financial data is always protected and the system remains up to date.
4. Easy Collaboration
Multiple users, including team members and accountants, can access and update financial data in real-time, no matter where they are.
5. Enhanced Data Security
Cloud-based accounting solutions use advanced security measures to protect financial information, making it safer than traditional paper records.
6. Simplified Tax Management
The software helps streamline tax calculations and filings, reducing the hassle of tax season.
7. Scalable for Business Growth
As your business expands, online accounting software can scale with you, offering features that adapt to growing financial needs.
How to Choose the Right Online Accounting Software in Zambia
Selecting the right online accounting software is essential for managing your business finances efficiently. Here are key factors to consider when making your choice:
Company Size
Business Model
Essential & Advanced Features
Compliance with Local Regulations
Ease of Use
Scalability
1. Company Size
The size of your business determines your accounting needs. Larger businesses require more advanced features, such as detailed financial reporting and multi-user access, while startups and small businesses may only need basic bookkeeping tools.
2. Business Model
While major accounting software solutions cater to various industries, some providers specialize in specific business types. For example, certain platforms are designed for e-commerce businesses, while others focus on B2B service providers. Choosing software that aligns with your business model ensures it meets your specific needs.
3. Essential & Advanced Features
Ensure the software includes the features your business requires. Most platforms offer core functionalities like general ledger management, accounts payable, and bank reconciliation. However, if you need advanced tools such as inventory management, payroll processing, or financial forecasting, verify that these features are included before making a decision.
4. Compliance with Local Regulations
Your accounting software should comply with Zambia’s financial and tax regulations, ensuring that financial data is stored securely and reports are generated in accordance with local laws. This helps businesses stay tax-compliant and avoid penalties.
5. Ease of Use
A good accounting system should be user-friendly and intuitive, making it easy to navigate and manage financial transactions. If your business operations are complex, the software should be adaptable to evolving needs. Additionally, consider how quickly new accounts can be set up complicated onboarding processes may indicate that the software isn’t the right fit for your business.
6. Scalability
As your business grows, your accounting software should be able to scale with it. Look for a solution that supports increased transaction volumes, additional users, and expanded functionalities. Choosing scalable software ensures long-term usability and eliminates the need for frequent system changes.
Why adopting online accounting in 2025 is crucial for Zambian businesses?
The right small business accounting software is more than just a tool it forms the foundation of a company’s financial health. It should be flexible enough to adapt and scale as the business grows. By 2025, businesses can no longer rely on outdated manual accounting methods. Investing in a cloud-based accounting system with seamless integrations and real-time financial tracking will save time, minimize errors, and provide better financial control. With the right accounting software, small business owners can shift their focus to what truly matters growing their business, making informed financial decisions, and ensuring long-term success.
Conclusion
When selecting online accounting software for your business, consider key factors such as cost, features, business needs, and your team's capabilities. Online accounting software is one of the most effective ways to manage finances, streamline operations, and ensure accurate financial tracking. With the right software in place, small business owners can focus on growth, make smarter financial decisions, and build a sustainable, successful business.
#Online accounting software#Online accounting software for small business#Online accounting software for business#user friendly accounting software#smart invoice zambia#smart invoice software
0 notes
Note
how do you go about captioning other peoples' videos? i mean this logistically; like does penny for example just trust you with her youtube account for the sake of writing subtitles into the videos? or is another thing happening
(asking bc i'm impressed by the quality of your subtitles and want to get into making subs for other peoples' videos as a Thing)
Caption files can be generated in any software that supports it. YouTube has an in-house caption editor that gets the job done but it's not very user-friendly. Newer versions of Adobe Premiere Pro and other editing suites have features that let you write and export a caption track (usually in .csv, or .vtt format) that contains the text, timings, and formatting. There are lots of options out there!
All you need in order to write captions for someone else is one such software and the final draft of a video, that way you can line everything up to the exact timing. Doesn't hurt to brush up on proper captioning etiquette too!
@sophie-baybey usually does the captions for Penny and she uses Premiere's caption editor. Personally I use subtitle-horse.com which is browser-based and does just about everything you'll need in the free version.
Since I tend to edit the highlight videos, captioning them is pretty straightforward when I do it - but we also have a production group chat when we need Penny or myself to clarify something that's hard to hear or a reference we don't get etc. I tend to send Sophie the isolated speech as a separate audio file just in case the audio balancing makes certain portions hard to parse. Like any collaborative project, communication between team members is key!
113 notes
·
View notes
Text
CREVH - GOLD

QuickBooks is a renowned accounting software that offers a seamless solution for small businesses to manage their financial tasks efficiently. With features designed to streamline accounting processes, QuickBooks simplifies tasks such as tracking receipts, income, bank transactions, and more. This software is available in both online and desktop versions, catering to the diverse needs of businesses of all sizes. QuickBooks Online, for instance, allows users to easily track mileage, expenses, payroll, send invoices, and receive payments online, making it a comprehensive tool for financial management. Moreover, QuickBooks Desktop provides accountants with exclusive features to save time and enhance productivity. Whether it's managing income and expenses, staying tax-ready, invoicing, paying bills, managing inventory, or running reports, QuickBooks offers a range of functionalities to support businesses in their accounting needs.
Utilizing qb accounting software purposes comes with a myriad of benefits that can significantly enhance business operations. Some key advantages of using QuickBooks include:
- Efficient tracking of income and expenses
- Simplified tax preparation and compliance
- Streamlined invoicing and payment processes
- Effective management of inventory
- Generation of insightful financial reports
- Integration with payroll and HR functions
These benefits not only save time and effort but also contribute to better financial decision-making and overall business growth. QuickBooks is designed to meet the diverse needs of businesses, offering tailored solutions for various industries and sizes.
When considering accounting qb software options, QuickBooks stands out as a versatile and comprehensive choice. To provide a holistic view, let's compare QuickBooks with two other popular accounting software options - Xero and FreshBooks. quick book accounting package and offers robust features for small businesses, including advanced accounting capabilities, invoicing, payment processing, and payroll management. Xero, on the other hand, is known for its user-friendly interface and strong collaboration features, making it a popular choice among startups and small businesses. FreshBooks excels in invoicing and time tracking functionalities, catering to freelancers and service-based businesses. By evaluating the features, pricing, and user experience of these accounting software options, businesses can make an informed decision based on their specific needs and preferences.
555 notes
·
View notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
87 notes
·
View notes
Text
CDA 230 bans Facebook from blocking interoperable tools

I'm touring my new, nationally bestselling novel The Bezzle! Catch me TONIGHT (May 2) in WINNIPEG, then TOMORROW (May 3) in CALGARY, then SATURDAY (May 4) in VANCOUVER, then onto Tartu, Estonia, and beyond!

Section 230 of the Communications Decency Act is the most widely misunderstood technology law in the world, which is wild, given that it's only 26 words long!
https://www.techdirt.com/2020/06/23/hello-youve-been-referred-here-because-youre-wrong-about-section-230-communications-decency-act/
CDA 230 isn't a gift to big tech. It's literally the only reason that tech companies don't censor on anything we write that might offend some litigious creep. Without CDA 230, there'd be no #MeToo. Hell, without CDA 230, just hosting a private message board where two friends get into serious beef could expose to you an avalanche of legal liability.
CDA 230 is the only part of a much broader, wildly unconstitutional law that survived a 1996 Supreme Court challenge. We don't spend a lot of time talking about all those other parts of the CDA, but there's actually some really cool stuff left in the bill that no one's really paid attention to:
https://www.aclu.org/legal-document/supreme-court-decision-striking-down-cda
One of those little-regarded sections of CDA 230 is part (c)(2)(b), which broadly immunizes anyone who makes a tool that helps internet users block content they don't want to see.
Enter the Knight First Amendment Institute at Columbia University and their client, Ethan Zuckerman, an internet pioneer turned academic at U Mass Amherst. Knight has filed a lawsuit on Zuckerman's behalf, seeking assurance that Zuckerman (and others) can use browser automation tools to block, unfollow, and otherwise modify the feeds Facebook delivers to its users:
https://knightcolumbia.org/documents/gu63ujqj8o
If Zuckerman is successful, he will set a precedent that allows toolsmiths to provide internet users with a wide variety of automation tools that customize the information they see online. That's something that Facebook bitterly opposes.
Facebook has a long history of attacking startups and individual developers who release tools that let users customize their feed. They shut down Friendly Browser, a third-party Facebook client that blocked trackers and customized your feed:
https://www.eff.org/deeplinks/2020/11/once-again-facebook-using-privacy-sword-kill-independent-innovation
Then in in 2021, Facebook's lawyers terrorized a software developer named Louis Barclay in retaliation for a tool called "Unfollow Everything," that autopiloted your browser to click through all the laborious steps needed to unfollow all the accounts you were subscribed to, and permanently banned Unfollow Everywhere's developer, Louis Barclay:
https://slate.com/technology/2021/10/facebook-unfollow-everything-cease-desist.html
Now, Zuckerman is developing "Unfollow Everything 2.0," an even richer version of Barclay's tool.
This rich record of legal bullying gives Zuckerman and his lawyers at Knight something important: "standing" – the right to bring a case. They argue that a browser automation tool that helps you control your feeds is covered by CDA(c)(2)(b), and that Facebook can't legally threaten the developer of such a tool with liability for violating the Computer Fraud and Abuse Act, the Digital Millennium Copyright Act, or the other legal weapons it wields against this kind of "adversarial interoperability."
Writing for Wired, Knight First Amendment Institute at Columbia University speaks to a variety of experts – including my EFF colleague Sophia Cope – who broadly endorse the very clever legal tactic Zuckerman and Knight are bringing to the court.
I'm very excited about this myself. "Adversarial interop" – modding a product or service without permission from its maker – is hugely important to disenshittifying the internet and forestalling future attempts to reenshittify it. From third-party ink cartridges to compatible replacement parts for mobile devices to alternative clients and firmware to ad- and tracker-blockers, adversarial interop is how internet users defend themselves against unilateral changes to services and products they rely on:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Now, all that said, a court victory here won't necessarily mean that Facebook can't block interoperability tools. Facebook still has the unilateral right to terminate its users' accounts. They could kick off Zuckerman. They could kick off his lawyers from the Knight Institute. They could permanently ban any user who uses Unfollow Everything 2.0.
Obviously, that kind of nuclear option could prove very unpopular for a company that is the very definition of "too big to care." But Unfollow Everything 2.0 and the lawsuit don't exist in a vacuum. The fight against Big Tech has a lot of tactical diversity: EU regulations, antitrust investigations, state laws, tinkerers and toolsmiths like Zuckerman, and impact litigation lawyers coming up with cool legal theories.
Together, they represent a multi-front war on the very idea that four billion people should have their digital lives controlled by an unaccountable billionaire man-child whose major technological achievement was making a website where he and his creepy friends could nonconsensually rate the fuckability of their fellow Harvard undergrads.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/05/02/kaiju-v-kaiju/#cda-230-c-2-b

Image: D-Kuru (modified): https://commons.wikimedia.org/wiki/File:MSI_Bravo_17_(0017FK-007)-USB-C_port_large_PNr%C2%B00761.jpg
Minette Lontsie (modified): https://commons.wikimedia.org/wiki/File:Facebook_Headquarters.jpg
CC BY-SA 4.0: https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#ethan zuckerman#cda 230#interoperability#content moderation#composable moderation#unfollow everything#meta#facebook#knight first amendment initiative#u mass amherst#cfaa
246 notes
·
View notes
Text
Shamir Secret Sharing
It’s 3am. Paul, the head of PayPal database administration carefully enters his elaborate passphrase at a keyboard in a darkened cubicle of 1840 Embarcadero Road in East Palo Alto, for the fifth time. He hits Return. The green-on-black console window instantly displays one line of text: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.”
There is nerd pandemonium all around us. James, our recently promoted VP of Engineering, just climbed the desk at a nearby cubicle, screaming: “Guys, if we can’t get this key the right way, we gotta start brute-forcing it ASAP!” It’s gallows humor – he knows very well that brute-forcing such a key will take millions of years, and it’s already 6am on the East Coast – the first of many “Why is PayPal down today?” articles is undoubtedly going to hit CNET shortly. Our single-story cubicle-maze office is buzzing with nervous activity of PayPalians who know they can’t help but want to do something anyway. I poke my head up above the cubicle wall to catch a glimpse of someone trying to stay inside a giant otherwise empty recycling bin on wheels while a couple of Senior Software Engineers are attempting to accelerate the bin up to dangerous speeds in the front lobby. I lower my head and try to stay focused. “Let’s try it again, this time with three different people” is the best idea I can come up with, even though I am quite sure it will not work.
It doesn’t.
The key in question decrypts PayPal’s master payment credential table – also known as the giant store of credit card and bank account numbers. Without access to payment credentials, PayPal doesn’t really have a business per se, seeing how we are supposed to facilitate payments, and that’s really hard to do if we no longer have access to the 100+ million credit card numbers our users added over the last year of insane growth.
This is the story of a catastrophic software bug I briefly introduced into the PayPal codebase that almost cost us the company (or so it seemed, in the moment.) I’ve told this story a handful of times, always swearing the listeners to secrecy, and surprisingly it does not appear to have ever been written down before. 20+ years since the incident, it now appears instructive and a little funny, rather than merely extremely embarrassing.
Before we get back to that fateful night, we have to go back another decade. In the summer of 1991, my family and I moved to Chicago from Kyiv, Ukraine. While we had just a few hundred dollars between the five of us, we did have one secret advantage: science fiction fans.
My dad was a highly active member of Zoryaniy Shlyah – Kyiv’s possibly first (and possibly only, at the time) sci-fi fan club – the name means “Star Trek” in Ukrainian, unsurprisingly. He translated some Stansilaw Lem (of Solaris and Futurological Congress fame) from Polish to Russian in the early 80s and was generally considered a coryphaeus at ZSh.
While USSR was more or less informationally isolated behind the digital Iron Curtain until the late ‘80s, by 1990 or so, things like FidoNet wriggled their way into the Soviet computing world, and some members of ZSh were now exchanging electronic mail with sci-fi fans of the free world.
The vaguely exotic news of two Soviet refugee sci-fi fans arriving in Chicago was transmitted to the local fandom before we had even boarded the PanAm flight that took us across the Atlantic [1]. My dad (and I, by extension) was soon adopted by some kind Chicago science fiction geeks, a few of whom became close friends over the years, though that’s a story for another time.
A year or so after the move to Chicago, our new sci-fi friends invited my dad to a birthday party for a rising star of the local fandom, one Bruce Schneier. We certainly did not know Bruce or really anyone at the party, but it promised good food, friendly people, and probably filk. My role was to translate, as my dad spoke limited English at the time.
I had fallen desperately in love with secret codes and cryptography about a year before we left Ukraine. Walking into Bruce’s library during the house tour (this was a couple years before Applied Cryptography was published and he must have been deep in research) felt like walking into Narnia.
I promptly abandoned my dad to fend for himself as far as small talk and canapés were concerned, and proceeded to make a complete ass out of myself by brazenly asking the host for a few sheets of paper and a pencil. Having been obliged, I pulled a half dozen cryptography books from the shelves and went to work trying to copy down some answers to a few long-held questions on the library floor. After about two hours of scribbling alone like a man possessed, I ran out of paper and decided to temporarily rejoin the party.
On the living room table, Bruce had stacks of copies of his fanzine Ramblings. Thinking I could use the blank sides of the pages to take more notes, I grabbed a printout and was about to quietly return to copying the original S-box values for DES when my dad spotted me from across the room and demanded I help him socialize. The party wrapped soon, and our friends drove us home.
The printout I grabbed was not a Ramblings issue. It was a short essay by Bruce titled Sharing Secrets Among Friends, essentially a humorous explanation of Shamir Secret Sharing.
Say you want to make sure that something really really important and secret (a nuclear weapon launch code, a database encryption key, etc) cannot be known or used by a single (friendly) actor, but becomes available, if at least n people from a group of m choose to do it. Think two on-duty officers (from a cadre of say 5) turning keys together to get ready for a nuke launch.
The idea (proposed by Adi Shamir – the S of RSA! – in 1979) is as simple as it is beautiful.
Let’s call the secret we are trying to split among m people K.
First, create a totally random polynomial that looks like: y(x) = C0 * x^(n-1) + C1 * x^(n-2) + C2 * x^(n-3) ….+ K. “Create” here just means generate random coefficients C. Now, for every person in your trusted group of m, evaluate the polynomial for some randomly chosen Xm and hand them their corresponding (Xm,Ym) each.
If we have n of these points together, we can use Lagrange interpolating polynomial to reconstruct the coefficients – and evaluate the original polynomial at x=0, which conveniently gives us y(0) = K, the secret. Beautiful. I still had the printout with me, years later, in Palo Alto.
It should come as no surprise that during my time as CTO PayPal engineering had an absolute obsession with security. No firewall was one too many, no multi-factor authentication scheme too onerous, etc. Anything that was worth anything at all was encrypted at rest.
To decrypt, a service would get the needed data from its database table, transmit it to a special service named cryptoserv (an original SUN hardware running Solaris sitting on its own, especially tightly locked-down network) and a special service running only there would perform the decryption and send back the result.
Decryption request rate was monitored externally and on cryptoserv, and if there were too many requests, the whole thing was to shut down and purge any sensitive data and keys from its memory until manually restarted.
It was this manual restart that gnawed at me. At launch, a bunch of configuration files containing various critical decryption keys were read (decrypted by another key derived from one manually-entered passphrase) and loaded into the memory to perform future cryptographic services.
Four or five of us on the engineering team knew the passphrase and could restart cryptoserv if it crashed or simply had to have an upgrade. What if someone performed a little old-fashioned rubber-hose cryptanalysis and literally beat the passphrase out of one of us? The attacker could theoretically get access to these all-important master keys. Then stealing the encrypted-at-rest database of all our users’ secrets could prove useful – they could decrypt them in the comfort of their underground supervillain lair.
I needed to eliminate this threat.
Shamir Secret Sharing was the obvious choice – beautiful, simple, perfect (you can in fact prove that if done right, it offers perfect secrecy.) I decided on a 3-of-8 scheme and implemented it in pure POSIX C for portability over a few days, and tested it for several weeks on my Linux desktop with other engineers.
Step 1: generate the polynomial coefficients for 8 shard-holders.
Step 2: compute the key shards (x0, y0) through (x7, y7)
Step 3: get each shard-holder to enter a long, secure passphrase to encrypt the shard
Step 4: write out the 8 shard files, encrypted with their respective passphrases.
And to reconstruct:
Step 1: pick any 3 shard files.
Step 2: ask each of the respective owners to enter their passphrases.
Step 3: decrypt the shard files.
Step 4: reconstruct the polynomial, evaluate it for x=0 to get the key.
Step 5: launch cryptoserv with the key.
One design detail here is that each shard file also stored a message authentication code (a keyed hash) of its passphrase to make sure we could identify when someone mistyped their passphrase. These tests ran hundreds and hundreds of times, on both Linux and Solaris, to make sure I did not screw up some big/little-endianness issue, etc. It all worked perfectly.
A month or so later, the night of the key splitting party was upon us. We were finally going to close out the last vulnerability and be secure. Feeling as if I was about to turn my fellow shard-holders into cymeks, I gathered them around my desktop as PayPal’s front page began sporting the “We are down for maintenance and will be back soon” message around midnight.
The night before, I solemnly generated the new master key and securely copied it to cryptoserv. Now, while “Push It” by Salt-n-Pepa blared from someone’s desktop speakers, the automated deployment script copied shard files to their destination.
While each of us took turns carefully entering our elaborate passphrases at a specially selected keyboard, Paul shut down the main database and decrypted the payment credentials table, then ran the script to re-encrypt with the new key. Some minutes later, the database was running smoothly again, with the newly encrypted table, without incident.
All that was left was to restore the master key from its shards and launch the new, even more secure cryptographic service.
The three of us entered our passphrases… to be met with the error message I haven’t seen in weeks: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.” Surely one of us screwed up typing, no big deal, we’ll do it again. No dice. No dice – again and again, even after we tried numerous combinations of the three people necessary to decrypt.
Minutes passed, confusion grew, tension rose rapidly.
There was nothing to do, except to hit rewind – to grab the master key from the file still sitting on cryptoserv, split it again, generate new shards, choose passphrases, and get it done. Not a great feeling to have your first launch go wrong, but not a huge deal either. It will all be OK in a minute or two.
A cursory look at the master key file date told me that no, it wouldn’t be OK at all. The file sitting on cryptoserv wasn’t from last night, it was created just a few minutes ago. During the Salt-n-Pepa-themed push from stage, we overwrote the master key file with the stage version. Whatever key that was, it wasn’t the one I generated the day before: only one copy existed, the one I copied to cryptoserv from my computer the night before. Zero copies existed now. Not only that, the push script appears to have also wiped out the backup of the old key, so the database backups we have encrypted with the old key are likely useless.
Sitrep: we have 8 shard files that we apparently cannot use to restore the master key and zero master key backups. The database is running but its secret data cannot be accessed.
I will leave it to your imagination to conjure up what was going through my head that night as I stared into the black screen willing the shards to work. After half a decade of trying to make something of myself (instead of just going to work for Microsoft or IBM after graduation) I had just destroyed my first successful startup in the most spectacular fashion.
Still, the idea of “what if we all just continuously screwed up our passphrases” swirled around my brain. It was an easy check to perform, thanks to the included MACs. I added a single printf() debug statement into the shard reconstruction code and instead of printing out a summary error of “one or more…” the code now showed if the passphrase entered matched the authentication code stored in the shard file.
I compiled the new code directly on cryptoserv in direct contravention of all reasonable security practices – what did I have to lose? Entering my own passphrase, I promptly got “bad passphrase” error I just added to the code. Well, that’s just great – I knew my passphrase was correct, I had it written down on a post-it note I had planned to rip up hours ago.
Another person, same error. Finally, the last person, JK, entered his passphrase. No error. The key still did not reconstruct correctly, I got the “Goodbye”, but something worked. I turned to the engineer and said, “what did you just type in that worked?”
After a second of embarrassed mumbling, he admitted to choosing “a$$word” as his passphrase. The gall! I asked everyone entrusted with the grave task of relaunching crytposerv to pick really hard to guess passphrases, and this guy…?! Still, this was something -- it worked. But why?!
I sprinted around the half-lit office grabbing the rest of the shard-holders demanding they tell me their passphrases. Everyone else had picked much lengthier passages of text and numbers. I manually tested each and none decrypted correctly. Except for the a$$word. What was it…
A lightning bolt hit me and I sprinted back to my own cubicle in the far corner, unlocked the screen and typed in “man getpass” on the command line, while logging into cryptoserv in another window and doing exactly the same thing there. I saw exactly what I needed to see.
Today, should you try to read up the programmer’s manual (AKA the man page) on getpass, you will find it has been long declared obsolete and replaced with a more intelligent alternative in nearly all flavors of modern Unix.
But back then, if you wanted to collect some information from the keyboard without printing what is being typed in onto the screen and remain POSIX-compliant, getpass did the trick. Other than a few standard file manipulation system calls, getpass was the only operating system service call I used, to ensure clean portability between Linux and Solaris.
Except it wasn’t completely clean.
Plain as day, there it was: the manual pages were identical, except Solaris had a “special feature”: any passphrase entered that was longer than 8 characters long was automatically reduced to that length anyway. (Who needs long passwords, amiright?!)
I screamed like a wounded animal. We generated the key on my Linux desktop and entered our novel-length passphrases right here. Attempting to restore them on a Solaris machine where they were being clipped down to 8 characters long would never work. Except, of course, for a$$word. That one was fine.
The rest was an exercise in high-speed coding and some entirely off-protocol file moving. We reconstructed the master key on my machine (all of our passphrases worked fine), copied the file to the Solaris-running cryptoserv, re-split it there (with very short passphrases), reconstructed it successfully, and PayPal was up and running again like nothing ever happened.
By the time our unsuspecting colleagues rolled back into the office I was starting to doze on the floor of my cubicle and that was that. When someone asked me later that day why we took so long to bring the site back up, I’d simply respond with “eh, shoulda RTFM.”
RTFM indeed.
P.S. A few hours later, John, our General Counsel, stopped by my cubicle to ask me something. The day before I apparently gave him a sealed envelope and asked him to store it in his safe for 24 hours without explaining myself. He wanted to know what to do with it now that 24 hours have passed.
Ha. I forgot all about it, but in a bout of “what if it doesn’t work” paranoia, I printed out the base64-encoded master key when we had generated it the night before, stuffed it into an envelope, and gave it to John for safekeeping. We shredded it together without opening and laughed about what would have never actually been a company-ending event.
P.P.S. If you are thinking of all the ways this whole SSS design is horribly insecure (it had some real flaws for sure) and plan to poke around PayPal to see if it might still be there, don’t. While it served us well for a few years, this was the very first thing eBay required us to turn off after the acquisition. Pretty sure it’s back to a single passphrase now.
Notes:
1: a member of Chicagoland sci-fi fan community let me know that the original news of our move to the US was delivered to them via a posted letter, snail mail, not FidoNet email!
522 notes
·
View notes
Text
Claudie Weber is a senior program advisor at the U.S. State Department. She got in touch with me by email in May, looking to discuss “recent developments” and copying several of her departmental colleagues. That’s not unusual for people in my line of work. What was slightly less common was that “Claudie” didn’t exist, and neither did any of her colleagues with State Department addresses. The approach was part of a careful plan to break into my Gmail account. And it seems to have succeeded.
For professional Russia watchers such as myself, being the subject of unwanted online attention comes with the job. Crude attempts at hacking and phishing are more or less constant, and every now and then we encounter something genuinely novel or clever. Back in 2019, I blew the whistle on an online deception campaign using LinkedIn that was the first documented instance of a deepfake-generated face being used as part of such an operation. A couple of years later, a well-constructed phishing attempt had me half a second away from clicking on a deceptive link that appeared to be an appointment reminder from my actual, real, optician.
But Claudie’s efforts were different again. The operators behind the name carefully, painstakingly brought together a number of different pillars of plausibility, and unlike on previous occasions, they didn’t put a foot wrong. For instance, they plainly knew that the first thing I would do was write back to her “colleagues” at their state.gov addresses to see if they existed—but they also knew, which I didn’t, that the U.S. State Department’s email server accepts all incoming messages and won’t show you an error if you write to nonexistent people.
What followed was a slow, patient, and ultimately successful process of coaching me into opening up a backdoor to all of my emails.
The hacking of my email account has been described in detail by the University of Toronto’s Citizen Lab, an organization dedicated to protecting civil society against state campaigns of this kind, and you can read some of the email traffic with “Claudie” in their report. Google’s Threat Intelligence Group has also reported on the operation and linked it to others that they tentatively associate with the Russian Foreign Intelligence Service.
The attack used a feature in Gmail and other apps called an application-specific password, or ASP. That’s a means of creating a special password so that you can still use older or less secure apps that don’t support modern security protocols.
And that’s where the problem lies: ASPs are a widely available means of bypassing all of the security precautions that we are all told so insistently to make sure are in place, such as getting verification codes sent to our phones. The feature is supported by Microsoft, Apple, Google, and other platforms as a seemingly routine technical workaround when other security systems don’t work, with little to no user-friendly warnings about how dangerous a tool such as this can be.
Importantly, the hack didn’t exploit some technical vulnerability in the software. As Google has pointed out, there “wasn’t a flaw in Gmail itself”; instead, “the attackers abused legitimate functionality.” That is correct: The ASP setup worked exactly as intended. The attack worked by convincing me to set up a route into my account that is built in by design, rather than by outwitting the security and breaking in. In the most literal sense, this backdoor to our email accounts is not a bug but a feature.
But there’s a problem with that. The fact that there is a widely available option to bypass today’s security precautions and throw your account wide open was an unexpected discovery not just for me, but also for anybody I’ve spoken to who isn’t deep in the cybersecurity business.
So for Google to say that “there is no vulnerability connected to Google’s application-specific passwords” is, again, technically correct but potentially very misleading in terms of how easily ASPs can be exploited—as demonstrated by my case and by however many others there might be by now. (I seem to be the first person who has gone public about being targeted in this way, but I’m sure I won’t be the last.)
As Google has also pointed out, users get a notification email when they create one of these passwords. But that’s of limited use when you already know that you set one up, whether or not you were deceived into doing so.
Because everything worked as intended, there was no way that I could see that anything was wrong. To Google’s credit, it was its security systems that eventually noted that something was amiss and caused my account to be frozen. After recovering my account, I found a notification buried deep in the security settings about a login from a suspicious address—dated eight days before Google locked my account with no warning.
The way that the platforms have tightened digital security while retaining the option of using ASPs to connect is like investing in heavy new locks for your front door but leaving the side door wide open for people who don’t have the keys. Because it involved a clever new attack that could affect almost anyone, my case has created quite a bit of attention in media specializing in cybersecurity. Organizations other than Google have naturally been readier to recognize the security problem. As Sophos, another cybersecurity company, politely noted in a warning to customers on June 18: “The potential impact of creating an app password and providing it to a third party is not made clear in the creation process.”
In other words, what would really have helped was a warning during the process of setting up ASPs of exactly what they are and what they do, which would have alerted me to what was going on. Google has correctly pointed out that there is a warning along those lines in their help files. But that doesn’t help if you don’t go to those help files—because, as in my case, your attacker has kindly provided an authentic-looking manual of their own to walk you through the process.
The real heroes of this story are at the Citizen Lab—in particular, the privacy and security guru John Scott-Railton. It was John, together with Reuters journalists Raphael Satter and James Pearson, who helped me piece together what had happened when all I could see was that Google had frozen my accounts (and in one case, telling me that this was because of “policy violations”). And it was they who used their professional contacts at Google to try to help me regain control.
The Citizen Lab calls itself an “interdisciplinary laboratory” focused on research in information technology and human rights. But their investigations of digital espionage against civil society—and their efforts to protect citizens’ privacy and other rights against corporations and state agencies—are invaluable for people like me who point the finger at evildoers such as the Russian state but don’t have the support of powerful governments or institutions behind them.
Several people have asked me if I’m concerned about what the attackers will do with messages that they copied from my account. One expected next step is that whatever emails were stolen from the account will be used in a hack-forge-dump attack, where the hackers pass them to Russia’s Western proxies or sympathizers to release as a “leak” intended to discredit Moscow’s adversaries.
Back in 2023, when Scottish parliamentarian and Russia critic Stewart McDonald was similarly targeted, it took less than 48 hours after his announcement that he had been hacked by Russia for British activist Craig Murray to boast that he had obtained McDonald’s emails.
The so-called leak is usually a mixture of genuine messages and files, some that have been altered, and others that are simply invented—plus, often, malware and viruses to infect anybody curious enough to download them. The aim could be to paint me and the institutions I work with as charlatans, neo-Nazis, spies, philanderers, abusers of substances or puppies, or all of the above. But it means that there’s little point in being concerned about anything potentially embarrassing in my emails—if the hackers don’t find what they’re hoping for, then they will make it up anyway.
For now, Russia’s trolls and mouthpieces on social media are already busy with their version of who I am and what happened. There’s a consistent pattern where it takes 24 hours after something happens for their storylines to go out for dissemination—and after that, the same lines are repeated almost word for word across different media and different languages. Some real-life characters in the Russia business have also been crowing with delight at the “hilarious” hack. But that’s not much different from the background noise of lies and abuse that someone in my line of work takes for granted.
What’s far more significant in this case is how many other people around the world could be exposed to the same security risk and know nothing about it. Now that the power of this tool has been demonstrated, cyber researchers are expecting it to be used far more widely. That means that it could be abused not just against people who have made enemies in Russia, such as myself, but also ordinary users who might not consider themselves at risk. And that could be for cybercrime, low-grade snooping, or just settling scores.
In my case, the attackers put an extraordinary amount of time, effort, and patience into building the con. For whatever reason, they decided I was worth it—or maybe they were just frustrated after so many previous failed efforts over so many years.
But anyone who is not as automatically cautious as me—perhaps because they’re not in a line of work that sees them routinely targeted—could be taken in by a far less sophisticated deception campaign. We probably all have friends and relatives, especially older ones, who have been taken in by scams that, in hindsight, seemed blatantly obvious.
If they know how, then readers should check whether this kind of password has been set up on their accounts. If they are concerned, there are options such as Google’s Advanced Protection Program, which blocks this method of attack and some others. But in any case, Google and other companies should make sure that the risk of this account feature is more widely understood by ordinary users.
When attacks do succeed, it’s also important that more people speak up about them. It’s understandable that individuals who are duped in this way are sometimes reluctant to come forward and share the details. Anybody less thick-skinned than me might be embarrassed—and feel a little foolish at having been outwitted. But it’s essential to share as much as possible. Our collective security is worth so much more than one person’s individual embarrassment.
15 notes
·
View notes
Text
Tumblr is always talking about being broke and user accounts keep disappearing, Twitter is collapsing under the world's silliest rebrand, Meta (owners of Facebook, Instagram, and more) are bleeding money over a failed attempt to pivot to VR, Amazon (owners of Amazon Prime Video, Twitch.tv, and more) have a union now and Google (owner of Youtube, Gmail, the Chrome browser and more) was recently ruled as a monopoly. Social media and internet culture is reaching the end of an era.
If that has you worrying about how you'll keep in touch with your loved ones and fans, if you're thinking about making your own site, if you want a place to speak privately without worrying what advertisers and governments think: PierMesh is for you
@utopicwork is making the tools for a new Web Mesh Network, where data is sent over the radio instead of through the tubes. PierMesh is a vision of a new internet by and for the people. Practical design and huge number of innovative software inventions allow this new network to be environmentally friendly, operated only on affordable hardware, free to use, and available equally no matter what kind of area you're in.
She's just one trans woman. Disabled, unemployed and pouring all of the energy she has into working hard every day on this. We can't coast by on good vibes and fumes forever: please take a look, tell your friends and help if you can
46 notes
·
View notes
Text
Run Your Business Like a Pro with TRIRID Accounting Software

Managing your business finances just got easier with TRIRID accounting software! Whether you're a startup, small business owner, or managing a growing enterprise, TRIRID is the ultimate solution to taking control of your finances and increasing your business's efficiency.
With TRIRID, you will enjoy:
Real-Time Financial Insights - Get instant access to your financial data with dynamic dashboards and customizable reports that help you make smarter, faster business decisions.
Automated invoicing and billing - Say goodbye to manual invoicing! Effortlessly create, send and track invoices and automate payment reminders to ensure you pay on time.
Expense and Income Tracking – Stay on top of your cash flow with detailed tracking of income and expenses. Easily categorize transactions, generate reports and get a complete view of your business's financial health.
Tax Ready and Compliant - Keep your business tax ready with built-in features that simplify tax preparation and help ensure you comply with local regulations.
Seamless Integrations - Sync with your favorite apps, such as bank accounts, payment gateways and e-commerce platforms, to save time and avoid data entry errors.
Easy to use interface - No accounting experience? No problem! TRIRID's user-friendly interface is designed for business owners at all levels, helping you manage finances without a steep learning curve.
Transform the way you run your business, streamline your accounting tasks and make more informed decisions with TRIRID accounting software. Say goodbye to confusion and complexity - run your business like a pro!
Start your free trial today and see how TRIRID can help you take your business to the next level!
For More Information:
Call @ +91 8980010210 / +91 9023134246
Visit @ https://tririd.com/tririd-biz-gst-billing-accounting-software
#Best accounting software in Ahmedabad Gujarat#User-friendly billing software Gujarat#All-in-one billing and accounting software India#TRIRID-Billing software in Bopal in Ahmedabad#TRIRID-Billing software in ISCON-Ambli road-ahmedabad
0 notes
Text

Revolutionize Your Finances with Ecuenta Accounting Software!
Experience the future of accounting with Ecuenta smart, efficient, and packed with powerful features. Sign up now for a free demo and see how easy managing your finances can be!
#accounting software#accounting software for small business#accounting software for business#user friendly accounting software#smart invoice zambia#smart invoice software
0 notes
Text

Revolutionize Your Finances with Ecuenta Accounting Software!
Experience the future of accounting with Ecuenta smart, efficient, and packed with powerful features. Sign up now for a free demo and see how easy managing your finances can be!
#accounting software#accounting software for small business#accounting software for business#user friendly accounting software#smart invoice zambia#smart invoice software
0 notes
Text

Below the cut is our extensive FAQ! If you have a question, check here first!

How long has PawBorough been in development?
PawBorough has been in development since the summer of 2021.
When will PawBorough be playable?
PawBorough will enter closed Beta for Kickstarter backers in late 2024. Open Beta will proceed to allow entry of non-backer users afterwards. Our current timeline projects an extended period of open Beta for new users to join in late 2024 or early 2025, depending on how many features need tweaking and to what extent. We currently estimate full launch in 2025.
Will PawBorough be free to play? Yes. PawBorough will have premium features, but will not be “pay to play.”
Where do I download PawBorough?
PawBorough is a browser game with no need for download. However, we are working on an application for mobile devices which will be available to download in the future. There is not currently a timeline for this development.
Will PawBorough be mobile friendly?
Yes. We are dedicated to mobile usability. Our development of an application is intended to enhance the mobile experience.
Will you have a suggestions page?
Once we have the game refined and populated, we will be opening a forum for suggestions to improve the user experience.
Is PawBorough accepting artist applications?
Currently PawBorough is accepting artist applications. If you would like to work as a visual artist on The PawBorough Team, please send your resume and portfolio to [email protected].
Is PawBorough accepting developer applications?
PawBorough is not in need of developers at this time.
Can I volunteer for PawBorough work?
For the majority of work, we do not accept volunteer applications. We periodically open volunteer applications for early feature testing. For notifications on when these applications open, keep up with our Kickstarter updates!
What timezone will PawBorough be in?
PawBorough will function in EST/ET!
How can I reach out directly to the team?
Please email us at [email protected]. All other methods to contact us may not reach us.
Will you keep the official Discord open after the full launch of PawBorough?
No. After PawBorough launches officially, we will be shutting down our Discord. It is not in our best interest to rely on third party software for communication with our community. Already, this is an issue we take responsibility for perpetuating. We want to ensure all information is sourced to and on our website in a single space. Players are welcome to create their own, unofficial spaces however!
How can I support the development of PawBorough right now?
We take donations from our PayPal. All donations will go towards our continued development. You can also support us by spreading the word! Tell your friends about our project, keep informed on our updates, and join the site when we’re live!
Will you have dark mode?
Yes.

Will there be more breeds/patterns?
PawBorough will continue to add more content over the span of its lifetime. We have currently committed to 21 breeds in total, but new patterns may be added in perpetuity as the game ages.
Can cats die? Is there a way to remove them from the game?
Cats do not die from play. The only way to remove a cat from the game is to voluntarily retire the cat.
What are mystic and domestic breeds?
PawBorough features seven Boroughs that a player may join. A Borough is a culturally unique location in the world of the game. Each Borough has at least two breeds of origin: a domestic breed and a mystic breed. These breeds come in “pairs.” For every domestic cat, there is a mystical, magical counterpart. We call these pairs an “origin set” or “origin pair.” In lore, this is explained as normal cat breeds being magically, genetically altered over hundreds of years. As a player, you will be able to switch between mystic and domestic breeds instantly.
What are the mystic and domestic pairs? What are the origin Boroughs of every breed?
Here are all origin pairs that we have showcased in updates thus far. Shorthair / Bovine = Harvest Prowler / Thumper = Harvest Ragdoll / Fyret = The Metropolis Longhair / Moontail = Luna Snowfoot / Prancer = Sol Wolf / ??? = Cogwheel Littlefang / Stonehide = ???
Can Domestic Breeds be turned into Mystic Breeds (and vice versa)?
Yes. Here is a graphic of the system we are testing, which incorporates Borough origin:
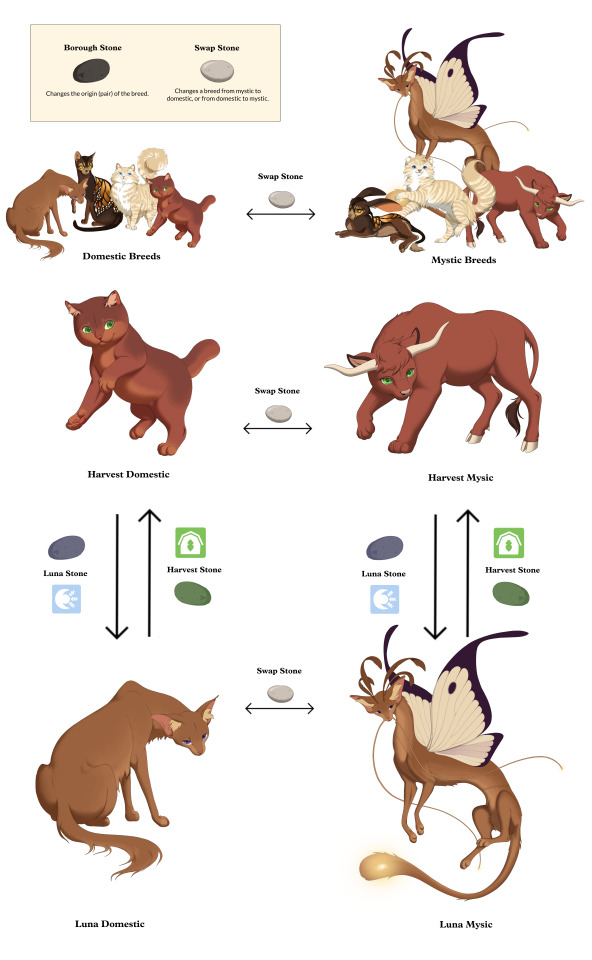
Why not just have separate items for every breed? Why the pairs?
This choice was intended to unilaterally flatten the rarity between mystic and domestic breeds, and instead determine rarity by origin set. With an item for every breed, seeding the items would inevitably become imbalanced in some way. This way, Shorthair and Bovines, for example, are equal opportunity for the player. We did not want to, as a game, incentivize collecting mystic breeds over domestic breeds, thus viewing domestic breeds as a contextually “lesser” option. That has just never been our vision!
Will some Breeds/Patterns/Colors be more rare than others?
Yes. Breed rarity will be dependent on the origin pair. Bovines and Shorthairs may be more common than Longhairs and Moontails, for example. Patterns will have breed and drop rarity. Colors will be dependent on breeding outcomes. You may use our live kit predictor on our website to view how two colors interact. A brief write-up on how color outcomes for kits are calculated is located here!
How much can you customize your two Founder cats?
You will be able to fully customize the colors and sex of your Founders. You will also be able to select from a pre-selected pool of patterns and breeds, which will be changeable for all cats via items. We are currently working on adding the ability to fully customize white coverage for Founders. The only thing you will not be able to change is the Borough birthplace (eye color.) We are also considering adding the ability to freely re-access the creator and change your founders at any time. As a general note, your Founders will be incredibly customizable!
Will kits be able to wear accessories?
Yes! We love that we can do this! This does mean our accessory pool will be more limited. However, kits will be fully customizable!
How will players obtain "Generation 1" cats?
Generation 1 cats are cats which are not born from cats already on the site (i.e “offspring.”) There are several methods to obtain a generation 1 cat, however most notably an item called “incense” can be used to immediately spawn a random generation 1 cat into your camp. Each Borough will have an incense item which spawns a cat with the eyes of said Borough. Incense is obtained via crafting.
Will new colors be added to the demo?
Currently, there are no plans to add new colors, but this possibility is not off the table.
Will you have feathers behind the ear as an accessory?
No. We are aware that, historically, media with anthropomorphized cats has a history of anti-indigenous themes. In the interest of respecting indigenous populations, we will not be illustrating any feather-themed accessories without indigenous sensitivity consultation.
Will I be able to attach tags to my cats? Such as #kit?
Yes, we will be implementing a tagging system!
Will multiple cats be able to have the same species of Fauna companion?
Yes!
Will there be a way to make my cat stay as a kit forever?
Yes. We will be adding perma-kits as a feature.
Can you add a nonbinary/third gender pose to the cats?
We would love to, but we’re a small indie team with limited resources. Three poses with full accessory and pattern functionality is already quite a bit of effort for us, especially with the demand of the art style we are committed to! However, we consider the Mars and Venus poses to be, for all intents and purposes, genderless. The purpose of two adult poses is simply to explore the designs. You will be able to switch between both adult poses at any time via a switch on the cat’s customize page.
Will there be a pronouns section for a cat's page?
We were asked to add this feature quite a bit, and we did add it! We are currently testing a system which may allow custom pronouns (such as neopronouns) that the game will recognize and use in narration and dialogue. This will help aid our initial reservation to the concept.
Will there be a way to change a cat's eye type?
Yes, and eye palette too! The only thing you cannot change is the birth Borough (Borough eye color.)
What's the difference between an Accessory and Decor item?
Accessories are pieces of clothing tailored to layer on each cat pose. They cannot be moved from where they sit on the cat. They can only be shifted above or below other Accessories layered onto the cat. In comparison, Decor items are items which can be shifted, rotated, and resized around the cat. Decor and Backdrop items come together to create a scene!
Can we change a cat's birth Borough/eye color?
No.
To what extent will you feature violence or adult content?
PawBorough is for teens and older. Users must be 13 and up to play. This means that we will feature minor use of moderately strong language, mentions of alcohol, and the allowance of art with cartoon blood and violence. However, photorealistic blood or gore will not be allowed, and we allow absolutely no sexually suggestive content whatsoever.
Will you have a custom system? How will it work?
This question refers to the concept of allowing custom, user-uploaded art to be created into items and imposed over a cat. Yes, we will have a system for this. Our custom cat items are called “pelts.” “Unclipped pelts” will allow for users to draw over the lines of the cat. “Clipped pelts” will go under the lines of a cat, and be easier to work with Accessories. Both will be a premium feature, and come with limitations and restrictions to help maintain the visual identity of the game. We will also be implementing a less complex pelt system for Fauna!
Will you have breeds that resemble big cats?
We will not be featuring any breeds from the Panthera order. This includes lions, jaguars, leopards, tigers, and snow leopards. We also will not be adding cheetahs, due to their cultural association with big cats. In the lore of PawBorough, big cats (and cheetahs) are mythical depictions akin to humans imagining elves! All other breeds from the Felidae family are on the table. This does include wildcats.
Will you add more white coverage possibilities?
Uncertain at this time. The idea is on the table, however we’re currently focused on illustrating for all the planned breeds!
Do you have a “basic” pattern?
No. We do have a pattern called “solid” that may aesthetically resemble a more basic patterning, but we do not have a base-level pattern that users build up from. Instead, all patterns have some degree of rarity and detail.
Is there a way to change a cat's colors?
Yes. Users will have access to items which randomize a single cat’s colors.
Can I rename my cats?
Yes! Much like changing the pose, renaming a cat is able to be done anytime via the customization page.
How will line breaking accents be handled? Won't they clash with apparel?
For those who are unaware, PawBorough features accent genes which may break the silhouette. The answer to this is: yes, they will! We deliberated over this for some time. However, we are treating line-breaking accents much like other accessories. It will be on the onus of the player to prevent clipping with any other accessories, just as accessories can and will clip with one another. Line breaking accents will be layerable among accessories, so users can adjust the layering how they like. From a design standpoint, line-breaking accents will only include biological body modifications. This includes, but is not limited to, horns, teeth, scales, claws, fur, and anything else which would grow from the cat itself. This therefore excludes these attributes from accessories. Overgrowth is an exception to this rule, due to its inception before the restriction was in place. In lore, Overgrowth is explained as a benign, parasitic, magic-touched plant which lives in cat fur and is easily passed to children of infected parents while nesting.
Can accents be in any slot? Can I have the same accent in both slots?
All accent genes can be in either slot! However, you may not have the same accent in both slots. Both slots are able to lack an accent at the same time, however.
What are the default patterns and breeds I can pick for my Founders?
You may create your Founders starting with: Solid Tiger Tuxedo Blotches This list is subject to change. No accent genes will be available for Founders to start with.

How does breeding work?
Breeding is available between two compatible cats. Users will choose to start a nest with two cats. Users will then babysit the nest until the new kits are ready to enter the User’s camp. Kits will inherit colors and patterns based on the parents. Testing of this mechanic is available on our website!
Can players cancel unwanted nests? Is it possible to accidentally lose a nest?
Nests can be reversed via a Bitter Root item. This is an active choice that the player must click several times to confirm. Otherwise, nests remain until the player interacts with them and do not expire.
Can Domestic and Mystic Breeds produce offspring?
Yes! All cats can breed with one another.
How will Paw Borough prevent inbreeding regarding the cats?
Currently, cats which are related via 5 generations apart cannot breed together.
Will cats ever be too old to breed?
We have no intention for a feature like this at this time.
Can cats have multiple mates?
Yes.
How does white coverage work for breeding?
Random coverage spots are chosen for each kit, with dominant spots passed down and recessive spots having a lower chance of showing. The coverage amount is chosen via the algorithm below. none x none => 90% none, 10% low full x none => 5% full, 10% high, 50% medium, 20% low, 5% none full x full => 90% full, 10% high full x medium => 50% full, 10% high, 40% medium full x high => 90% full, 10% high full x low => 25% full, 25% high, 25% medium, 25% small medium x medium => 5% full, 10% high, 50% medium, 20% low, 5% chance of none high x high => 15% full, 20% medium, 65% high, 10% low high x none => 30% none, 30% high, 25% medium, 15% small high x medium => 10% full, 10% small, 40% high, 40% medium high x low => 60% small, 20% medium, 20% high
How many cats are in a litter?
This is subject to change, but a cat can have between 1-4 kits in a single litter.
Can I breed my cats to have different eye colors than my borough?
Yes.
Can I breed my cats with other users?
Yes! We have a system for cross-account nests which will allow two users to both care for a nest and then divide the kits.

Is there a cap on how much regular currency a player can obtain every day?
There will likely be a cap, but questions like these have become difficult to give concrete answers on until we can simulate the economy in closed Beta!
Will there be events during the game?
Yes! PawBorough will have an onsite story which will be told through events, in addition to holiday events which will give users seasonal item rotations.
If I miss story events, how can I catch up?
All real-time story events will be documented in an onsite archive which users can visit and read at any time. Campaign events which surround Guild play will be re-playable, which new users can play at any time.
Will the game have achievements?
Yes. PawBorough will feature a badge and reward system.
Will there be side/minigames?
At this time, we are focused on a closed gameplay loop which is fun, satisfying, and rewarding without the need for an abundance of generalized minigame designs. We may incorporate unique, one-off minigames for immersion in the future. But it is our hope that they won’t be necessary for an enjoyable game. We would much rather focus our resources towards buffing out the gameplay loop, and accommodating several play styles with it!
Are there any plans for a battling system for cats?
Yes! PawBorough will feature teams which may register at the Guild. Users will be able to go on missions with their cats and earn rewards, leveling up their team and earning exclusive items in the process. What stats does a cat have? What are they used for?
Cats feature seven statistics: Stamina, Strength, Sense, Smarts, Speed, Savvy, and Sorcery. A cat's base stat number is divided among these categories. Leveling a cat up will allow the player to build out any given statistical category. Statistics are used for different dynamics in combat (mele, range, healing, dodging, etc.) as well as helping to calculate different daily item yields. Cats can be leveled up both by participating in Guild play and by yielding items. Each cat also has a Fortune and Doom statistic, which affects good luck and bad luck in RNG and general combat. These two stats cannot be changed.
Are base stats completely randomized?
Yes, but there is a cap and a weighted bell curve. All Founders start with the same base stat.
Can I read official lore of the game?
As of right now, we are working on an updated lore page with a more interactive presentation and more meat than our previous iteration. We will notify all social media when we have a new page live.
How will recolors of accessories work?
PawBorough features a dye system. All items will come in 12 standard colors and may be dyed to any of the 12 colors. Dyes are obtained via crafting. “Special dyes,” as they are currently called, will feature more unique coloring from the standard item, such as holographic, polka-dot, or pastel. Special dyes will only be applicable to certain compatible items. (And in all cases, a special dye will only work on an item that the standard doesn’t already apply to. For example, if a shirt is polka-dot by default, there is no reason for the shirt to be compatible with the polka-dot special dye.)

Can I be an Alpha tester? Is Alpha open?
Alpha applications are available here. If this form is closed, it means applications are no longer accepted. Alpha is not open as of June 12th, 2024. We will keep active communication and announce when Alpha opens. Applicants who are chosen will receive emails with the appropriate steps.
If I am chosen as an alpha tester, do I have to sign an NDA?
No.
How will data wipes happen during the closed Beta?
For context, a data wipe consists of removal of all cats, items, currency, and user content. A data wipe will NOT wipe the following: Your account, including your username, credentials, and ID number. Credit for any money previously spent on your account. Closed Beta will feature at least one data wipe as the test comes to a close. However, closed Beta will feature as many data wipes as we the developers deem necessary for testing important game dynamics. As an example, we need to test economic balance, and will wipe as necessary to test new pricing and currency distribution.
Is there a limit to how many Beta Testers there will be?
Closed Beta is limited to the number of Beta Keys sold on our Kickstarter. Population reports put this number at over 1600 keys.
How much earlier do Early Bird tier codes get into the closed Beta?
Early bird codes allow 3 days of early access!
Will Luna Stones be tradeable or will they be locked to your account?
All Kickstarter items will be tradeable.
Are Moontail wings randomly chosen when using a Luna Stone on a cat? What about when you breed a Moontail?
Wing types are random when using a Luna Stone. To change a Moontail’s wing type, an item will be easily available. When breeding, the wing type of the parent will pass down.
I am a backer. How will I receive my Kickstarter rewards?
With the email you used to back, you will be emailed a code for your beta key(s) and a reward code which will be redeemable onsite for your tier rewards/add-ons. Can I still pledge to the Kickstarter?
No.
Are the Kickstarter items obtainable since the campaign ended?
No, and yes. We will not be distributing these items again. They are retired. However, when the site is live, you may trade with backers for Kickstarter items.
Will I lose my Kickstarter rewards after a Beta wipe?
Any redeemable item codes will become redeemable again after a data wipe.
Account
Can two or more people share an account?
No. We limit the game to one account per user. If you are caught sharing your account with another person, you may have your account frozen. All items you may lose by choosing to share your account are at your own risk.
Can system members have individual accounts?
When we say one account per User, we mean User. This means that systems with individual users may have separate accounts. However, any evidence of “funneling,” daily yield transfer, or frequent and egregious transfer of cats or resources which would give a User identifiable advantage over other Users will result in consequences, including but not limited to removal of the aforementioned resources and termination of one or both accounts.
Can you change your Borough after choosing one at signup?
Yes!
Can you change your username? Will multiple people be allowed to have the same username?
Your username will be changeable. No two accounts may share a username.
Am I allowed to have a "side" account?
Accounts are limited to one per user. Evidence of frequent cross-account trading which implies the existence of a side account will result in investigation and consequence.
What is the character limit on usernames?
18. It is the same for cat names.
Will I get my account banned if a housemate and I both play PawBorough, and you recognize the same IP address?
No. In fact, we are rather lenient and understanding of this. We only will take administrative action if the cross-account activity is egregiously imbalanced and rewards one player with a clear, identifiable advantage over other players.
Can players terminate their own account?
Yes.
How many accounts will be reserved for staff use?
The first 10 account IDs will be reserved for staff use. This number may be subject to change.
Is there a referral system? Are there any rewards for referring people?
We are developing a referral system in tandem with our badge system. Our system will reward referring players with a payout every time their referee(s) completes an achievement and earns a badge.

Can I use a cat I made in PawBorough as an original character / purchase commissioned art of this character?
Yes, we love it! However, no content featuring our doll art may be used commercially. You may not profit off of our exact images. We also require that any public use of our art or designs be credited back to our website.
Can I use cats in offsite roleplay? Do I need to give credit? Can I go make my own story out of my PawBorough characters?
Yes. Credit requirement largely depends. If you use an image from the site, you must credit us. If you’re using a mystic design of ours, those creature designs are owned by us. We would prefer if you did not completely divorce them from our game and give us credit for the creature design. Under no circumstances may you use any mystic designs in commercial content. However, we don’t own the concept of a generic cat character. If you create and name a domestic cat in our game, you’re welcome to take it elsewhere and do anything you damn well please with it! Again, so long as you credit any use of our images, and use none of our images commercially! Also, for clarity, we don’t own the concept of moth cats or cow cats, but our specific design elements in tandem with the breed titles are attributed to us. You’re totally free to make a moth cat design for your own use!
Are we allowed to trade art for beta keys with other users?
Yes.
Is offsite trading allowed?
For beta keys, yes, but at your own risk. Note that many games of our genre disallow cross-site trading with games in development, or altogether. We do not allow nor endorse disregarding the TOS of other games. We are considering an embargo on cross-site trading of cats, items, and site currency both during Beta and for a brief initial launch period. This is to help preserve the microcosm of our onsite economy and grow it to a healthy, prosperous size before introducing the possibility of cross-site scalping. We hope you understand this decision. We’ll keep forefront communication with Users on these policies during the game’s lifespan.
Can I sell my Kickstarter rewards for real-life currency?
No. This will never be allowed.
Can I trade my Kickstarter rewards for digital or physical art?
Yes. Art as a traded good would not be counted under the cross-site embargo. If any cross-site content is included in conditions of the trade, it would be considered illegal.
Will there be a safe way to exchange premium currency for regular currency with other players?
Two-step cross-account trading will be in place. Both players will have to approve a supposed trade before it will activate.
47 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
58 notes
·
View notes