#verifiable credentials
Explore tagged Tumblr posts
Text
Verifiable Digital Credentials: The Future of Secure and Seamless Digital Credential Verification
In today’s digitally connected world, verifiable credentials, digital credential verification, and verifiable digital credentials are transforming how individuals and organizations share and verify information. Whether it’s academic qualifications, professional licenses, or identity documents, these credentials are ushering in a new era of trust, efficiency, and security across industries.
What Are Verifiable Credentials?
Verifiable credentials are tamper-proof digital documents issued by trusted organizations that can be cryptographically verified by anyone. Built on decentralized identity frameworks and blockchain technology, these credentials empower users to control their data while enabling institutions to verify it instantly without intermediaries.
For example, a university can issue a graduate a verifiable digital diploma, which the graduate can then share with employers, who can independently verify its authenticity in seconds — no paperwork, no waiting.
Why Digital Credential Verification Matters
Traditional credential verification methods are slow, expensive, and prone to fraud. HR teams and admissions departments often have to chase down documents, manually cross-check records, and rely on legacy systems. Digital credential verification solves this by automating and securing the process. It reduces verification time from days to seconds, enhances trust, and eliminates the risk of forged or altered documents.
Key Benefits of Verifiable Digital Credentials
Security and Trust: Backed by cryptographic signatures, verifiable credentials are nearly impossible to forge.
User Control: Individuals own and manage their credentials, deciding when and with whom to share them.
Efficiency: Processes like hiring, university admissions, and license renewals become faster and less resource-intensive.
Interoperability: These credentials work across platforms, borders, and institutions, making global mobility and collaboration seamless.
Real-World Applications
Education: Universities issuing verifiable degrees and transcripts.
Healthcare: Medical professionals using digital licenses and certifications.
Government: Issuing digital identity cards and travel documents.
Corporate: Background checks and skills verification in recruitment.
The Future is Here
As organizations increasingly adopt digital trust frameworks, verifiable digital credentials will become the standard for identity and qualification verification. With growing support from governments, educational institutions, and tech companies, this technology is not just a trend — it’s a foundational shift in how we prove who we are and what we know.
0 notes
Text
0 notes
Text
How do Verifiable Credentials Work?

Fake certificates have become mainstream with the fake diplomas industry enjoying a valuation of over US $1 billion. The high valuation comes from the easy availability of fake certificates. Moreover, they are cheaper to procure than actual certificates both in terms of money and time. They even require less effort. So, naturally, a lot of individuals jump on the shortcut bandwagon to acquire a fake certificate and streamline their career.
But the problem doesn’t just pertain to the education sector. It adversely impacts the employment sector, too. Besides these, individuals who aren’t 100% suited to a particular role can spell disaster for everyone involved. For instance, a fake doctor might administer the wrong medicine and harm the life of their patient. Similarly, a fake architect, financier, construction worker, electricians, gas safety engineers, and more can cause not just monetary harm but also lead to the loss of lives.
Since the fake certificate issue does not seem to be waning despite concerted efforts from government organizations and the average public, it’s necessary for organizations to adopt solutions that can help them navigate the dangerous landscape of fake certificates. This is where verifiable credentials blockchain comes in.
What are Verifiable Credentials?
Verifiable credentials are a digital copy of the physical documents or digitally generated documents that authenticate the validity of the data presented in such documents. For instance, digital academic certificates, licenses, IDs, and more are all part of verifiable credentials. Hosted on the secure, immutable, trustless, and transparent blockchain technology, verifiable credentials make it easy and secure to verify credentials.
Based on the explanation above, you might think that all digital certificates can be termed verifiable credentials, but not all digital certificates are verifiable credentials.
For a certificate to be deemed as a verifiable credential, it must conform to Verifiable Credentials Data Model 1.0. This is a set of standards established by the World Wide Web Consortium (W3C). The key requirement for a verifiable credential is that it should be secured cryptographically and tamper-proof, must be verifiable by machines, and employ privacy-enhancing technologies like zero-knowledge proofs.
Now that you’re clear on what are verifiable credentials, how about you check out its components?
3 Essential Components of Verifiable Credentials
Blockchain-based verifiable credentials are composed of three elements that are encoded in a json file. The essential components are as follows:
Verifiable credential’s metadata: A verifiable credential’s metadata might or might not be cryptographically signed by the issuer—an educational institution, entity, or other organizations—but it contains all the relevant data pertaining to a credential. It contains the credential identifier of the entity employing the credential, the date the credential was created, as well as its expiry date. It might also contain data about the issuer. The credential is, of course, verifiable cryptographically.
A declaration or claim: A verifiable credential is good as long as it can verify the credentials it was generated to validate. As such, it contains a declaration or claim about a subject the holder of the credential would want to verify, such as someone’s job title, educational qualifications, driving license details, and more.
Proof: The third and the final element in a verifiable credential, the proof is a cryptographic method that allows individuals or organizations to validate the authenticity of the shared data. Moreover, it allows the verifier to check the source or the issuer of the data. Further, it also allows them to verify if the shared data has been tampered with or not.
These three elements make the backbone of a verifiable credential and make it simple for the issuer to generate and share it. On the other hand, it benefits the holder since the credential’s contents can be easily verified by the required organization, such as an employer or institution, to validate their authenticity.
These elements work together in sync to make digital certificates a force to be reckoned with.
How Does Verifiable Credentials Work?
Now, for the most important part. Understanding what a verifiable credential is and what are its elements will only help you solve one-half of this complex jigsaw puzzle. Knowing and learning about its machinations and inner workings will help you put together a complete puzzle piece.
So without further ado, let’s dive straight in!
Verifiable credentials build connections between three parties to work seamlessly:
The issuer of the verifiable credential
The holder of the verifiable credential
The verifier of the verifiable credential
It involves building a system of trust between these three parties in a decentralized fashion. Verifiable credentials blockchain assures the safe exchange of data between these parties and helps establish a genuine relationship between them. Besides this, it also ensures that the credential remains tamper-proof and allows the storage of all data related to validation, identifiers, and signatures.
Armed with this knowledge, let’s explore the relationship between these three parties further to completely understand the working of verifiable credentials.
The cycle is kicked off by the issuer—educational entity or other organizations— that issues the verifiable credential. Issuers can be government or private organizations that are authorized to issue verifiable credentials. The issuing organization digitally signs a credential using a cryptographic key native to them to generate a verifiable credential.
Once the issuer issues a credential, they share it with the concerned holder. A holder can be an individual or organization and has complete authority over the usage of the issued verifiable credential. They get to decide how they’d like it to be managed, who can view it, and who they’d like to remove from their approved list (revoke the permission). Holders usually store their verifiable credential in a digital wallet to keep it safe.
The verifier comes into the picture as and when the holder shares their verifiable credential with them. Once a credential is presented to them for validation, it’s upon the verifier to verify the credential and authenticate:
if it comes from a source authorized to issue one,
if the credential is tamper-proof, and
if it's relevant.
Basically, a verifier’s job is to verify the presented credentials and deem it appropriate. They can do so by checking the credential’s authenticity on blockchain. The entire process is trustless, meaning the verifier doesn’t have to contact the issuer to confirm the authenticity of the credential. Better yet, the entire verification process takes just a few seconds.
To understand this flow better, let’s take the help of an example.
Example to understand the working of verifiable credential
Let’s say an educational institution wants to issue verifiable credentials for its graduates. In this scenario, the educational institution is the issuer since they will be issuing credentials for their graduating class of students.
Now, let’s imagine that one of the students—Max—is the recipient of the issued verifiable credential. This makes Max the holder of the verifiable credential. Upon graduation, Max wants to apply for a job at a firm to learn the ropes. But the employer would like to verify Max’s credentials to ensure that he has the required qualifications.
So Max shares his verifiable credential with his potential employer. Upon receipt of the credential, the employer, or the verifier, authenticates the credential to determine Max’s educational qualifications and ensure that the credential is original and has been issued by a respectable authority.
Once they verify Max’s credentials, they may or may not move forward with his job application, but if they’d like to, they know that Max’s educational qualifications meet his declaration or claim.
This was a very basic example to help you understand a verifiable credential in a real-world setting, but such credentials aren’t just useful for education institutions or employers. They can be employed in a number of settings and used across industries.
For instance, government organizations, financial institutions, medical and healthcare organizations, real estate sector, and more can all apply and benefit from verifiable credentials.
How Does Verifiable Credential Work With DID?
A decentralized identifier (DID) represents a distinct digital address that helps validate an individual’s online identity. This allows individuals to control their personal information, such as date of birth, without having to rely on centralized authorities, third parties, or middlemen, providing a more secure infrastructure.
DIDs can be created for or by the user and can be stored on the blockchain. What makes it unique is that it’s a global identifier that’s made of letters and numbers and employs cryptography and blockchain to keep the user’s data secure and safe from bad actors looking to alter or steal the information.
DIDs are an efficient and reliable way to share personal information between two parties and support instant verification. Combined with verifiable credentials, DIDs can prove to be a game changer.
Use ProofEasy to Easily Issue Verifiable Credentials
It can be a little confusing to work out the kinks before you can begin to issue your verifiable credentials. So why don’t you check out ProofEasy? It’s budget-friendly, has patented blockchain and QR-code technology, allows customization, and can be easily integrated with your existing API.
What’s more? They’re offering a FREE trial before you commit to ProofEasy. It’s that easy.
0 notes
Note
if I was, uhh. A researcher researching shiny Pokemon. Would you catch some shinies for me?
Okay first off if you’re researching shiny Pokémon you can buy from an ethical breeder. If you’re researching wild shiny Pokémon though your best bet is typically to actually. Yknow. Go observe them. In the wild. Because as soon as you catch them and take them out of their natural habitat you’ve already skewed the results of whatever research you’ve done.
TLDR; no ❤️
#pkmn irl#rotumblr#rotomblr#I will not fucking shiny hunt for you. literally in my pinned it says that everyone I send Pokemon to is vetted and verified beforehand.#do you#Rando mc fuck face#think you’ll pass that?#what’re your credentials? where’d you graduate from? what SPECIFICALLY are you researching?#name? age? dob? past research? can any other researchers or professionals vouch for you?#also you’d have to meet me in person at least once#and send me regular updates on the Pokémon. among other things.#⚠️ posts#⚠️ asks
9 notes
·
View notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
sat through a leadership meeting today about how future members of my student art collective will get to "earn microcredentials" embedded with "digital artifacts" aka their Portfolios which will provide job recruitment ai with a "deep resume of the self" and didnt even throw up.
#but now im feeling notso good.#All this instead of scholarship money btw.#Because of ai: the job market is flooded with meaningless credentials. So we: use ai#to verify peoples credentials which now have to be earned by completing a gauntlet of creative tasks..#At the university but not for credit.#And so basically the creative process for undergrad students has just become a series of meaningless hoops to jump through in order to#check a box on a job application that says Yes I am qualified to send emails from your company's servers#h#sorry yeah lets found a student art collective that sounds grand. What do student artists need? a way to make employers value their art.#Grand. so lets just make sure that artists always feel the looming specter of obsolescence & are constantly aware that their freedom to eve#practice art is contingent on the invisible arm of the market which is itself contingent on No human will or meaning whatsoever.#why would we lend credence even for a minute to the idea that meeting the empty arbitrary criteria for “valued worker” is worth anything#& furthermore why would we dedicate our entire program towards funnelling people into the Checking That Box pipeline.#I think we should all fall on our swords ngl.
1 note
·
View note
Text
1 note
·
View note
Text
Nigeria Is In Trouble With Leaders Whose Credentials And Identities Can’t Be Verified – Peter Obi
The 2023 presidential candidate of the Labour Party (LP), Peter Obi has lamented the situation in Nigeria, saying a lot of things are wrong and need to change in the country. Lamenting that the country is in trouble, Obi said the trouble is however self-inflicted. Speaking at the Chinua Achebe Symposium at Princeton University on Friday, Obi said Nigerians must start working towards a country…

View On WordPress
0 notes
Text
How Verifiable Credentials Are Shaping the Future of Digital Credential Verification
In today’s digital-first world, verifiable credentials, digital credential verification, and verifiable digital credentials are becoming essential tools for enterprises, institutions, and individuals. As organizations shift away from traditional methods of identity and qualification verification, these modern credentialing systems are transforming how trust is established online.
What Are Verifiable Credentials?
Verifiable credentials are digitally signed pieces of information issued by a trusted source — such as a university, employer, or government body — that can be independently verified without contacting the issuer. Unlike static digital documents (PDFs, scans), verifiable credentials are tamper-proof, interoperable, and privacy-preserving.
These credentials follow open standards, often leveraging blockchain or decentralized identifiers (DIDs) to ensure that data integrity is maintained while minimizing the need for central databases.
The Growing Need for Digital Credential Verification
As more processes go online — whether it’s hiring, onboarding, university admissions, or professional licensing — the need for fast, secure, and automated digital credential verification has surged. Traditional verification methods are often manual, time-consuming, and susceptible to fraud. Verifiable credentials address these issues by enabling instant and automated verification of credentials, without compromising privacy.
For example, instead of waiting days for a university to verify a degree, a prospective employer can instantly verify a candidate’s education via a cryptographically signed digital credential.
Benefits of Verifiable Digital Credentials
Security & Authenticity Verifiable digital credentials are cryptographically signed, making them extremely difficult to forge or alter. This ensures high levels of trust in the data being presented.
Privacy Protection Holders can share only the data necessary for a specific purpose. For instance, a user can prove they are over 18 without revealing their full date of birth.
Efficiency & Speed Verification can be completed in seconds, reducing administrative overhead and improving user experience in critical workflows like onboarding or access management.
Interoperability Because verifiable credentials are based on open standards, they can be used across different platforms, industries, and countries without compatibility issues.
Industries Embracing Verifiable Credentials
Education: Digital diplomas, transcripts, and certifications are now being issued as verifiable digital credentials, simplifying verification for employers and academic institutions.
Healthcare: Credentialing of doctors, nurses, and lab technicians is being streamlined using secure, portable credentials.
Finance & Banking: Know Your Customer (KYC) processes are being transformed through reusable, verified digital identity credentials.
Workforce & HR: Employers are adopting digital credential verification to speed up hiring and eliminate resume fraud.
The Future Is Trustworthy and Decentralized
Verifiable credentials are ushering in a new era of trusted digital interactions. As adoption grows, we can expect a more secure, privacy-centric, and decentralized approach to identity and qualification verification. Governments and enterprises alike are exploring these solutions to enhance compliance, reduce fraud, and improve efficiency across the board.
The future of digital credential verification is being reshaped by verifiable credentials and verifiable digital credentials. These technologies not only protect against fraud but also empower individuals with greater control over their personal data. As we move into a world increasingly reliant on digital trust, verifiable credentials are set to become a cornerstone of secure digital ecosystems.
0 notes
Text
0 notes
Text
Guardians of Your Digital Identity: How DIDs & Verifiable Credentials Empower Blockchain Identity Management?

The world we live in right now is becoming increasingly digital. Online interactions have become second nature and with that the importance of safeguarding our digital identities cannot be overstated.
For years, we've relied on centralized identity systems, but their flaws have loomed large. Lack of means to verify credential, security vulnerabilities, etc. the list of drawbacks is immense.
However, a new dawn is breaking in the world of digital trust, and it's driven by Blockchain Identity Management through Decentralized Identifiers (DIDs) and Verifiable Credentials.
Buckle up as we embark on an exciting journey into the future of online identity. In this blog, we uncover how these two elements - DIDs and Verifiable Credentials create trust in blockchain identity management systems.
The Pitfalls of Centralized Identity Systems
Centralized identity systems, such as usernames and passwords, have been the workhorses of the digital world for decades. But they come with a baggage of issues:
Security Vulnerabilities: Centralized databases are like shiny jewels for hackers. Breaches can expose enormous volumes of personal data, leading to identity theft, financial fraud, and all kinds of digital shenanigans.
Lack of Control: Once you share your personal data with organizations, you often lose control over it. Your data is collected, processed, and sometimes monetized without your consent or benefit. This loss of control raises legitimate concerns about data privacy and misuse.
Privacy Concerns: Traditional identity systems collect more data than they need for verification. This data overreach gives rise to privacy concerns, as users may be sharing more personal information than is necessary. Outdated credential verification services are simply not viable.
Inefficiency: Multiple usernames, passwords, and registration forms are a bane for users. Managing these can be cumbersome and frustrating, leading to a less-than-stellar user experience. This inefficiency often results in weak passwords, password reuse, and overall security vulnerabilities.
Welcome to Blockchain Identity Management
Blockchain technology, the disruptive force behind cryptocurrencies, is now stepping into the realm of identity management. It offers what centralized systems can't: enhanced security, control, and privacy.
Decentralized Identifiers (DIDs)
DIDs are the cornerstone of self-sovereign identity. A DID is a unique identifier associated with a subject - an individual, an organization, or a device.
Unlike centralized identifiers issued by a single entity, DIDs are decentralized. They empower users to create, control, and prove their identity without relying on a third party.
Privacy at Your Fingertips: DIDs allow users to share only the necessary information, preserving their privacy. Users can reveal data on a need-to-know basis, keeping their personal information confidential.
Unyielding Security: Blockchain ensures that DIDs are immutable and tamper-resistant. Once a DID is created, it's etched in digital stone, immune to alterations or deletions, thereby enhancing security and thwarting unauthorized access.
Interoperability Magic: DIDs are designed to work across different platforms and services, forging a universal identity solution. This means that identity verification can be consistent and straightforward across a myriad of online platforms.
Verifiable Credentials
Verifiable Credentials are digital attestations that can be issued and verified cryptographically. They are the dynamic duo of DIDs, enabling secure sharing of identity-related information like age, qualifications, and financial history.
Selective Disclosure Superpower: With Verifiable Credentials, users can selectively disclose their information, sharing only what's necessary for the transaction at hand. It's like a digital vault where you can pick and choose what to share, ensuring a granular approach to privacy.
Trust and Authenticity Arsenal: Credentials issued on a blockchain are bulletproof when it comes to authenticity. The cryptographic verification process guarantees that credentials are genuine, making it extremely difficult for malicious actors to present counterfeit information.
Frictionless User Experience: This approach streamlines identity verification processes, giving users a smoother, more efficient experience. No more remembering dozens of usernames and passwords, just a simplified and hassle-free digital existence.
Meet the Pioneers: ProofEasy
In the dynamic field of blockchain identity management, one company stands out as a trailblazer. ProofEasy has emerged as a pioneer in providing digital identity solutions powered by their patented blockchain technology.
Their innovative approach hinges on DIDs and Verifiable Credentials to create a secure, user-centric identity management system. ProofEasy puts users firmly in control of their digital identities, minimizing the risk of data breaches, and delivering a seamless, privacy-focused online experience.
Here are some compelling reasons why ProofEasy is making waves:
User-Friendly Finesse: ProofEasy empowers users to take control of their identities without being complicated. Individuals can share their information on their terms, ensuring that their personal data remains their domain.
Patented Blockchain Brilliance: Their proprietary blockchain technology guarantees security and immutability of digital identities. Your data, once recorded on their blockchain, is set in digital concrete, providing tamper proof security.
Privacy in Their DNA: ProofEasy is committed to user privacy. They've woven privacy protection into the very fabric of their identity solutions, ensuring that users' sensitive information remains safeguarded and doesn't fall into the wrong hands.
Efficiency and Savings: The streamlined identity verification processes offered by ProofEasy benefit both users and organizations. Reduced fraud and operational costs make for a win-win situation, improving security and efficiency across the board.
Bottom Line
As we usher in this new era of digital trust, blockchain identity management, powered by DIDs and Verifiable Credentials, is poised to redefine how we establish and manage our online identities.
ProofEasy's pioneering efforts shine a light on a future where individuals have more control, more privacy, and greater security over their digital identities, making the online world a safer and more user-friendly place.
If you are interested to know more about secure digital identity solutions then be sure to meet ProofEasy at the Identity Week Asia 2023. You can find them at Suntech Convention Centre, Singapore from 7-8 November 2023.
0 notes
Text
.
#I hate notarycam with the power of a thousand suns#been waiting to get these stupid credentials verified for over and hour now#apparently some people have to wait 6+ hours or longer#im going to lose my mind
0 notes
Text
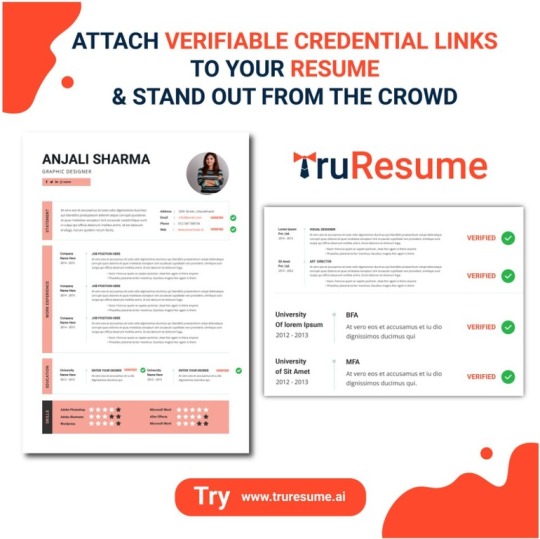
Verifiable Credentials AI resume Builder that incorporates verifiable credentials, revolutionizing job applications with confirmed achievements and talents.
0 notes
Text
Remember; Antisemites are Conspiracy Theorists
I feel like many of us forget that a key component of antisemitism is being a conspiracy theorist, and so I wanted to do a write up on it and draw parallels between what I've seen here on Tumblr and in my professional career.
One thing to keep in mind and remember is that antisemitism is not just bigotry and wanting to commit violence against Jews, it also includes conspiracy theories about Jews and everything relating to them as a key component.
I've noticed a number of similar behaviors and patterns in pseudoscience/anti-science conspiracy communities and antisemitic conspiracy theorists that might help elucidate why we can't make a lot of headway with certain people and why some accounts have such a big following and impact.
1) Often we find impactful conspiracy theorists pretend to be part of the group they are targeting.
Whether this is the person creating the conspiracy itself, a popular account, or an influencer, there is the likelihood that they will pass themselves off as a member of the group they are spreading misinformation about.
In the sciences we often see this with wellness gurus, naturopaths, homeopaths, chiropractors, and so on. They pretend that they're a "doctor" or "scientist" and have the same education, training, and expertise. They use a bunch of fake degrees/diplomas from diploma mills and get a bunch of fake certifications from uncredited organizations to add a letters after their name to add an air of legitimacy. They taught to use jargon that sounds scientific to the lay audience in these programs, but don't actually understand what they're saying. They just know enough to convince others that they're educated on the topic they're pretending to be an expert about.
The problem is that they will inevitably enter into spaces with actual members of the group who are verified experts and in doing so they will get called out rather quickly.
Inevitably this leads to their defense of calling the actual expert some sort of shill or mouth piece for propaganda that is trying to silence them and the "Truth". The actual expert is part of the conspiracy to keep them silent and not expose the "Truth". It does not matter how much you go into the conspiracy theorist's background and breakdown why they're not actually an expert and falsified/purchased their credentials, they will maintain that they are the one speaking "Truth" (often because they're "rebelling against the system" or they have "secret information").
Often they will call upon their followers to provide anecdotal evidence and bring in to question what actually qualifies "expertise" and use a bunch of goalposts and mental gymnastics to try and justify the grifter and the conspiracy. We seen this with them making accusations of the people debunking them using a No True Scotsman fallacy, but this in itself is a fallacious rhetorical device of improperly applying a fallacy against legitimate criticism. It's a common debate tactic of people who are lying to incorrectly apply fallacies against their critics.
However, there is the caveat that sometimes the conspiracy theorist was an expert prior to becoming what they currently are and typically they had some sort out downfall and disgrace that led them there. At some point their ethics and morals shifted and they now instead push and pursue a grift. The best example of this is Andrew Wakefield who used to be a medical researcher but sacrificed his ethics and morals for a payout. Another example is one I mentioned the other day, Simon Goddek, who used to be a biotechnology researcher that went off the deep end in regards to COVID and is now in Brazil selling unlicensed supplements.
In this regards, the former expert turned grifter will rely upon their former expertise (that is even removed by the accrediting body in some cases) to give themselves an air of authority on their pseudoscience. This becomes more and more egregious over time as they make claims about "research backed" products that they are selling, but are always unlicensed and untested things with maybe an in vitro study (done in a petri dish) to maybe back it up.
In all cases it becomes something similar to Nobel Prize Syndrome where the former expert is now spreading misinformation about things well outside their expertise and inevitably spreads a conspiracy about why its not accepted or other related things.
Now, in regards to antisemites here on Tumblr, and across social media, we have had a number of antisemites enter our community under the guise of "as a Jew" "anti-Zionists" and then spread rampant and vitriolic rhetoric and conspiracy theory. There are, what I consider, three varieties of this particular false "expert".
First is the obvious Racefaker/Jewfaker. This is the person who pretends to be Jewish or an Israeli Jew and is a complete and utter caricature of what either entails. They post nothing relating to Judaism or being Israeli, fighting antisemitism (even though they claim to be), and actually help spread antisemitic conspiracy and hatred. Even when outed with receipts that they have a history of faking (and are continuing to do so), they and their audience ignore the evidence (even if they requested it themselves). This is akin to the pseudo-experts in the sciences going "well prove it!" in regards to their fake credentials and then when the shoe drops they just call the person providing the evidence a shill or propagandist (in the case of Fakers it's usually "Zionist" or in some cases "Nazi").
The second is the "as a Jew" that maybe celebrated holidays once upon a time and very intermittently with their family, and quickly left Judaism and everything related behind as it meant very little to them. They had no connection to the community and culture and moved on. They only use "as a Jew" when it's convenient for them to shut down any argument, especially if they are being accused of antisemitism. We have several examples of this with various tankie accounts that defend the violent antisemitic actions of the Soviet whom at one point were openly practicing neo paganism and then claimed that they celebrated Jewish holidays once upon a time so they could speak as an "authority" (nvm that they deleted their blog to hide their paganism).
The third "as a Jew" is someone who claims to have heritage in their ancestry, but was never raised Jewish and has no connection to Judaism in any capacity beyond this one tenuous thread. They believe that having a drop of DNA relating to the culture means they can speak as an expert/authority.
In all instances these persons speak from ignorance and try to generate a false sense of authority to dismiss claims of antisemitism. The former "as a Jew" abandoned their Judaism, even from a secular stand point, and replaced it with completely different things. They actively sought connections to other groups and had little to no understanding of the culture they left behind. The latter is actively trying to engage in some sort of blood quantum to justify why they should be able to speak over Jewish voices. If you address the fact that neither one are Jews by any standard they then make wild claims about you being antisemitic, denying heritage, and other such things that no one would make about any other ethnic group.
These types of dismissal allow them to maintain their fake expertise because they and their audience already don't trust Jews, so any evidence provided would be ignored anyway. Just like the Racefaker/Jewfaker, the fake "as a Jew", the no connection "as a Jew" and their audience already believe in antisemitic conspiracy theories so any evidence provided that proves the person is faking or falsely presenting themself is part of the conspiracy. Furthermore, just like the pseudo-expert calls an actual scientist or doctor a shill, the Racefaker/Jewfaker and "as a Jew" calls the Jewish person addressing their behavior a range of insults or terms that indicates to their audience that the individual(s) is(are) part of the conspiracy.
And more importantly, none of them can actually replicate the nuances that come with being Jewish and living and growing up in the culture. There are certain behaviors, terms, norms, and standards that Jewish people grew up with regardless of sect or practice. This cannot be replicated by Jewfakers and "as a Jew" persons.
2) The use and defense of improper terminology.
Another big indicator that you're dealing with a Fake Expert spreading conspiracy theories and misinformation is the usage of terms in the incorrect manner or terms that have been rejected by the targeted community.
In regards to pseudoscience the most common terms are energy, frequency, quantum, detox, natural, and organic. In the scientific community these all have clearly defined definitions and parameters that constitute them. The Fake Expert uses them vaguely with no clear definition (or scientific explanation) as to how the mechanism they're applied to actually works. Often they're used to make something sound "smarter" than it actually is (especially quantum).
Anyone using these terms in this manner can be quickly identified as someone who doesn't know what they're talking about.
With regards to JewFakers, there are terms that they use that are indicators they are not what they are pretending to be and are simply antisemitic conspiracy theorists that hate Jews.
Any account that calls a Jew (or Jews) a "Nazi" or slurs created by white supremacists is immediately a red flag. These terms are not something anyone who is Jewish with any connection to the community would actually use. We have our own intracommunity words to describe another Jewish person who behaves in such a manner, but those particular ones are not them.
Why?
Because a core component of Nazism (and by extension much of white supremacy) is antisemitism. A Jewish person existing as a Jew and all that it entails cannot be a "Nazi" by the very definition of the ideology unless they are specifically trying to conduct heinous acts against other Jews in a specific manner using specific rhetoric. Just because a Jewish person might actually commit a heinous act or be a bad person does not make them a "Nazi", even if those heinous acts are conducted against non-Jews. It is a clearly defined word with a set definition that has requirements to meet it.
As such, anyone using "Nazi" or related terminology to describe Jews, especially Jews they don't like, immediately outs themself. Especially if they are claiming to be a member of that community because they acting contrary to all the cultural norms and behaviors.
3) they believe a single occurrence validates their entire conspiracy.
When sweet wormwood (Artemesia annua) was found to effectively treat parasites in an empirically supported study the pseudoscience community went nuts. They used it as validation for all the naturopathy, homeopathy, and other stuff they believed in. Suddenly because one plant was effective then everything else was, including practices not relating to plants at all. It didn't matter that these other plants and practices had no evidence to support the claims surrounding them, one thing was validated and so everything was validated.
We see a similar behavior amongst antisemites where if there is an occurrence that validates their belief that Jews are bad then everything is suddenly validated. It does not matter if the other things have been properly debunked and were falsified maliciously or intentionally misleading, the one occurrence of Jews/Israelis/Zionists being "evil" suddenly means every conspiracy theory is true.
Which leads to point four.
4) the refusal to acknowledge when they are wrong and the continuation of misinformation.
In the sciences I have seen this particular tactic from the aforementioned fake experts that are also influencers. They'll say something about how you can treat Lyme Disease with hydrogen peroxide IVs (you can't, please don't do this), that you detox your body with a certain diet (also not a thing), that you should alkalinize your body (also bullshit), and many other claims.
Often they will provide some shoddy "study" or purposefully misinterpret something to back their claims. When presented with a breakdown of why their claims are not supported, whether through someone calling out the misinterpretation or that they are using poor evidence, they will continue to keep the claim up on their media and website. There are even some cases where someone might even reach out to them and gently try to let them know that they are in fact wrong about the claims they are making from an earnest place of concern.
Regardless, they will still continue to push the claim they made even in light of the evidence that is contrary to their conclusions. Why? Because they likely believe it to be true and it's actually a conspiracy by "Big Science" to keep it secret and silence them or they need to push it on others that it is true because it directly benefits them monetarily to do so.
Very rarely will you see one of these grifters retract and apologize for a claim. They often have disclaimers on their websites that protect them legally from any "medical advice" they may have given (acknowledging, in some way, that they know what they're doing is a grift)
In regards to the antisemitic conspiracy theorists, whenever one of their claims is debunked (such as the 377k thing I broke down the other day) you will find that they don't retract, correct, and apologize for the misinformation they spread. They keep it on their media and continue to either spread it or passively endorse it by it still being present.
When coupled with the Faking tactic mentioned above this means that a lay person will see the misinformation and believe it because it because it is still present on the Faker's page. This is then coupled with the "as a Jew" pages that also keep that same misinformation up, and so if anyone were to try and cross reference and verify if it were true then would then see a Faker being backed by an "as a Jew" and thus leading to the conclusion that it must be true.
They don't know that both parties are not Jewish and are in fact antisemites pretending to be. If someone were to publicly engage and point out that something is incorrect then they and the rest of the antisemites will join in to dismiss the correction as a piece of propaganda (just like the pseudo-experts get their cohort and audience to dogpile and dismiss actual scientists).
This ensures that the antisemitic conspiracy theories and misinformation spread by these conspiracy theorists has an air of legitimacy.
Because the Fake Experts said so, and if you disagree with them being a Fake then you're part of the conspiracy.
Do you see how this circles back in on itself?
So one thing we need to do is not just call these people antisemites.
We need to point out that they're conspiracy theorists as well.
Because that's what they are.
They're conspiracy theorists.
Just like Moon Landing Hoaxers, anti-vaxxers, COVID deniers, and all the other conspiracy theory believers out there.
And just like other conspiracy theorists, they work backwards from a conclusion and attempt to find evidence to support it. Even if they have to falsify, misinterpret, lie, or purposefully obfuscate.
Now, if you've read this far and you are an audience member of one of these people that this is talking about and your first response is to get defensive and immediately start attacking me then I need you to ask yourself "Why?" Why is pointing out that much of the antisemitism revolves around and behaves like pseudoscience conspiracy theorists so offensive to you?
Is it because you view yourself as a reasonable person who wouldn't get sucked in by conspiracy theories?
That you consider yourself well informed?
Consider for a moment that you're not. Consider that if the points I have described above caused a very real visceral reaction in you that you have fallen for antisemitic conspiracy theories and conspiracy theorists spreading them.
It's okay to have been bamboozled. It can happen to anyone. But the only way forward is to admit and accept that you were, and then leave those spaces and what they represent behind. Go forward with the knowledge that indicates such behavior and try to do some undo the damage it has done and continues to do.
But if you're actually one of the Conspiracy Theorist spreading this stuff that I mentioned above, well...have a good day I guess?
#jumblr#antisemitism#leftist antisemitism#intersectional antisemitism#antisemitic conspiracies#antisemitic conspiracy theorists#all these antisemites are just conspiracy theorists#That's why you'll see them dismiss me with juvenile insults to my education and professional experience#They can't actually provide an argument beyond “they're an idiot” because if they did they'd end up like every other conspiracy theorist#entering into a space where they're pretending to be an expert or member of that group#It's also very clear that the antisemites are behaving like pseudoscience conspiracy theorists by using terms meant to harm#The group that they're targeting as part of the conspiracy#When you see the term “Zio” or “Nazi” applied to a Jew you can be assured that the person using them is an antisemitic conspiracy theorist
172 notes
·
View notes
Text
Charm Brought It Back
Reader x Witches!Sun, Moon, & Eclipse
Commission Info
I am so excited to present this Hocus Pocus inspired AU requested by the lovely @jackofallrabbits! The boys star as the witchy brothers who return once a fated reader lights the starry candle. They simply must show their gratitude! And what better day to post such a spooky and fun fic than on Friday the 13th?!
Content Warning: Suggestive themes, heavy kissing, and heavy touching.
———
You turn the key and cut the engine of your car. With a flick, you turn off the headlights. The beginning of a sunset swoops down onto your ill-adjusted vision. The horizon is drenched in purples and oranges as shadows begin to crawl off of trees and their yellowed leaves. It will take a minute or two for your sight to adapt, but you have tilted and revolved the structure waiting just at the edge of the forest within your mind’s eyes for days now. It’s beyond the dirt road you’ve pulled onto the shoulder of.
Blinking slowly, you find the house’s dark silhouette through the boughs of clustered trees, and you sigh at the beauty of its preserved history.
The building is an artifact dating back roughly to the 1630s. A post-medieval English-style home, it contains two stories with an overhanging jetty and stunning clapboard siding that has survived a little under four centuries of existence. Your eyes catch on the windows and your heart sings at the sight. Diamond-paned casement. And there, decorative pendants of celestial bodies, including iron-casted suns, moons, and overlapping symbols of the two. The steeply pitched roof is common for the era and is more renowned in its descendant the saltbox form, but this style boosts its spooky aura.
The Puritan colonists were the ones responsible for importing the style to America as they landed here on the eastern coast.
It’s no stretch of the imagination to think of witches and execution trials while gazing over the beautiful home. You’re particularly intrigued by the history of the Salem witch trials, and as a historian, you couldn’t deny yourself the chance to enter the building and feed the gnawing need to stand within a piece of history.
Stepping out of your car, a gust of wind carrying the bitter edge of autumn cuts through your brown sweater. You shiver and shut the door as quietly as you can manage. This is hallowed ground. This will supply your ever inquisitive mind which is always looking to the past with a curiosity most insatiable.
You face the home. A footpath lightly serpentines between the trees. Hooligans with destructive tendencies and teenagers on dares will venture here for a spooky, fun time, but are usually caught by the police because the building sits on private property. You asked for permission from the owner of the hundreds of acres of forest land that includes the so-called “Witch House” if you might enter the premises. Given your credentials, you were certain the owner would trust you with exploring the home.
Much to your relief, the owner agreed.
You look up, arms clutching your knitted sleeves to fight the chill of an October breeze, in awe and reverence.
From your pocket, you slip out a wrought-iron key with the symbol of the moon overlapping the sun to form a black eclipse and marvel again at the intricacy of ancient beauty. Your fingertips grow chilled in the late hour. The sun shifts from orange to dark, bleeding red like blood from a heart spilled across the horizon. You walk towards the home.
Perhaps you should have arrived sooner. You were caught in another historical journal depicting the specific timeframe of when this home would have been occupied by its original inhabitants.
The rumors even now speak of curses and cursed artifacts within the building. Some of it is true—you have confirmed with your own scholarly sources. The original owners were a trio of brothers. They were accused of witchcraft and hanged for the crimes. That much is historically documented and verified.
What is fantasy is the tale of the brothers casting a curse with their dying breaths, declaring they would one day return if a virgin lit a starry candle on the anniversary of their executions.
Superstition. Most likely, the fear of the townspeople transcended to their children, and their children, down and down until it became a tale to spin on Halloween night around these parts.
The door is black as you approach it. A stray branch catches on your sweater, pulling on a thread, and you yank yourself free and silently mourn the roughen fabric before returning your attention to what really matters. You must be careful. This entire place is iconic and in need of preservation.
You slip the key into the lock hole and turn it with a thick, heavy click before the black wood door groans and slides inwards as if inviting you into its sphere. You take a breath. Your boots cross the threshold and you enter the home.
As is typical of some homes built in the early seventeenth century, an open hall greets you. In the far back is the fireplace with a cauldron still sitting upon an ashy bed. An original wood-carve table and chairs are set to one side as a staircase climbs up into the darkness of the second level. What little red light leaks inside is narrowed and cut up into diamonds by the panes. To one wall, shelves contain dusty and forgotten cooking utensils, once glimmery copper pots, and dinner dishes with designs considered much too gawky in the Puritan era but it causes you to softly gasp.
Your hand covers your mouth as you gaze around you, overwhelmed with the beautiful intricacies of metallic chandeliers holding half-burned tallow candles, and to the other wall lies a bookshelf covered in cobwebs as if the spiders refuse to let anyone examine such precious reads. Your fingers already itch to gently pry out one manuscript and gaze at the original script of whoever wrote it.
But the light—it’s far too dark now. The red has given way to blue and pale indigo. You squint. You reach into your other pocket for a lighter and flick it on. The tiny flame spouts a delicate light. Never would you dare admit this out loud to a living soul, but you so desperately wish to see the home in its authentic state, lit only by the technology the brothers had at the time: fire.
There are thick, yellowed candles lying on the table and clustered together on the narrow window sills. You have no hope of reaching the metal chandeliers but you do spy a candelabra positioned near the bookshelf on a small end table. You light it first with a careful touch of your lighter flame. The wick catches, even after all of these years. You smile softly, your heart warm within your chest as you bask in the essence of this beautiful place.
A few more candles should suffice.
You slip to the table to light the thick and tall candles. The flames bloom and warm the space in rich light, casting thick shadows from support beams. You almost set your lighter away when you spy one last candle set upon a golden candle holder. The fashioned metal twists and twines with elaborate engravings of shooting stars and slices of sun rays were placed in the corner of the room almost out of sight. The curiosity within you urges you to take a step, then another, and another. You stand in front of the almost forgotten candle.
The tallow is black as midnight. Strange. How did they color this? Embedded within the darkness are speckles of white, splattering the candle like an array of stars. Your eyes stray in search of constellations before shaking your head.
It’s true. There is a starry candle. Perhaps the brothers did dabble in the occult, playing with cards and fortune telling, and being punished with death for their interest in unholy magic.
The wick is dark and untouched as if it were never lit before. You bring the lighter flame closer. Superstition might worry another, but you concern yourself with logic and reason—explanations of humanity rather than inexplicable forces beyond comprehension.
Something stirs from a nearby corner shelf. Two long ears twitch. You catch a glimpse of a rabbit with creamy white fur just before it leaps off of the shelf and directly onto your arm. You yelp. Nearly dropping the lighter, you scramble back as the rabbit hits the floor, collects itself, and sits on its haunches.
Green eyes glare up at you. The rabbit, small and bunny-like, stays firmly between you and the starry candle.
You stand with your chest heaving and your lungs scraping out air, almost burning your thumb on the lighter flame before turning around yourself. Where did the woodland creature come from? Did it crawl its way inside like a rat and become trapped within the colonial home? The shot of adrenaline still flowing through your veins leaves your hands shaking.
The rabbit is still watching you with uncanny eyes. Prey animals so rarely stare back at bigger, larger threats. Perhaps it’s a pet. A runaway pet that somehow ended up here, of all places.
You slowly offer out your hand, keeping the lighter away in your other, as you take a step towards it.
It thumps a foot once, as if in warning, then bounds away. You watch it disappear into the house, still reeling from the fright it gave you.
If Michael was here, he would have laughed and told you to leave with him, now. He never wanted you to go here, especially alone, but you shake such ominous warnings away. He said curiosity killed the cat. You disagreed. This house is a part of history, not a curse. Witches are mere stories, conjured out of historical unrest and the longing to blame bad luck and tragedies upon an individual or three.
There’s always an explanation for fear superstition or mistrust. It’s far more sad than it is spooky.
You shake your head, smooth out the creases in your sweater, and face the starry candle again. The lighter flame flickers softly as you draw near it.
It is the anniversary of the brothers’ executions. You remember now as the shadows from other candles drape over you like a veil. You are also a virgin.
You laugh to yourself, covering your mouth as you do so. Look at you! You’re getting so worked up because a rabbit jumped at you.
It’s only hocus-pocus.
You tilt the lighter until it engulfs the wick. The flame catches, and you at last snap the lighter shut and return it to your pocket. Your eyes squint slightly at the candle. The wick snaps and bursts into sparks. The flame is not yellow or orange or even blue—it’s pure white like a comet streaking across the sky.
A crack of thunder splits the night sky with a bellow so monstrous, you feel like a child again, fearing a storm. You drop low to the ground, shielding your head as if the very world was going to fall upon you. A spark cracks in the fireplace, conjured out of ash underneath the cauldron before it burns hot and bright. The cauldron immediately begins roiling and bubbling with water. Laughter, great and terrible, and filled with the most jester-like joy sweeps over the room.
The pulse in your ears drowns at any sense but the need to hide. You scramble into the corner, tucking yourself behind the stand of the starry candle and hunker down. Holding your breath, you grab a fistful of your sweater while clutching your chest, and watch the door to the almost 400-year-old house fly open.
Three figures stride inside, looking about the place with wide eyes and disk-like heads framed in jutting adornments not unlike sun rays or shrouded in a heavy, dark blue hood.
“Brothers! We’re home!” The first one, tall and dark with deep red hues to his form, accent in sharp orange sun rays and an eclipse upon his face, turns to face his brother with bright, cat-like yellow eyes. “Isn’t it glorious?”
Another figure steps forward, yellow and off-white. Pale eyes beam. His head is crowned in bright sun rays as well. His spindly fingers twindle together in exuberant energy while he glances about the room eagerly. “Oh, yes, yes! More than anything! It’s as if we weren’t gone for more than a day—though the dust and cobwebs beg to differ.”
He draws a claw—you suck in a sharp breath—along the table’s edge and rubs his taloned fingertips together in disappointment.
“We must get to cleaning at once.”
“No,” the last figure fixes his hood with silvery digits. Golden jewels hang down the back of his unusual skull, the last and most prominent adornment a thick, golden star pendant. His eyes cast around the room, scarlet, and searching. “We must thank the little mouse who lit the candle.”
He flashes sharp teeth within his wide mouth, shaping it into a hungry grin. You gulp.
“Where are our manners?” The red and dark one twists back to the room with a flourish of his arms. His yellow gaze sweeps over the shelves and floors with a blade-like glint. “Of course, we must thank one so lovely.”
A dark cape drapes about his person. Underneath, a white flowing shirt hangs loosely to his lithe and slender figure, causing you to balk upon staring at such an exposed chest. The other two are no different, wearing similar shirts and dark trousers, but the hooded one bears a thick, longer cape while the sunny figure shares a cape similar to the first.
The yellow one lifts his wrists and frowns at the red ribbons tied around them. Golden bells jingle softly in an ominous chord.
“How terrible a reminder of our current impermanence,” he growls low in his throat, all cheerfulness lost and causing you to squeeze your ribs in fear.
“Patience, Sun,” the red one speaks, though he too casts a narrowed glance to the black ribbons and golden bells adorning his wrists. “We will affix ourselves back to this world in due time.”
“Eclipse, what a delicious creature I smell.” The hooded figure steps deeper into the home. Blue claws scratch at equally blue ribbons knotted to his hand bones but his attention is terrifyingly fixed on the candle stand just above your hiding spot.
You shrink further into the corner.
“Yes, Moon? And how lovely?” Eclipse, you assume, asks. His yellow eyes flash.
“As lovely as the stars,” Moon answers.
You watch claws curl around the wooden side of the candle stand, scratching deeply into the wood before a half-moon face emerges from behind, teeth set like a predator’s upon the sight of a wounded animal. Your heart flutters like a bird with a broken wing.
“Hello, little mouse. Won’t you come and play with us?”
You scream as he leaps behind the candle stand, takes you by the arms, and pulls you to your feet. You struggle to free yourself, crying out as he grabs hold of your wrists and fixes you firmly in place.
“My, how sweet,” he purrs in a dangerously low voice that rolls in the back of his throat. “You are the darling virgin who lit the candle, no?”
“Let me go!” You thrash but Moon grins in delight, as if you’re simply too precious.
“You deserve proper thanks,” He lowers one hand, forcing you to submit with slightly bent knees. “Here is my gratitude, little mouse.”
You freeze as he brings your hand towards his mouth, and a hundred, horrifying visions of him biting your fingers off or sinking his teeth in your palm send your blood into a frozen sludge of fear.
The witch, however, presses a kiss to the center of your palm. The softness catches the gears in your mind and jerks them to a halt.
“Thank you for allowing us to return once more,” he rasps. His scarlet eyes find yours between the space of your thumb and forefinger, and a strange stirring takes hold of your middle.
“This isn’t real,” you breathe. Dizziness begins to take hold.
This must be a dream, a thought gone wild, or inhaled bacteria triggering hallucinations.
Moon’s grin widens. He lowers your hand, loosening his hold for one precious moment. You rip your hands free of his grasp. A low growl escapes him but you’ve already slipped away, your eyes upon the door and spilling with the need to rush out into the night, away from the impossibilities standing before you—
Arms snatch your waist and lift your feet from the ground. You gasp.
Held in the air, you squirm before a hot breath dusts the shoulder of your sweater. You fall still, your throat bobbing as a mouth presses into the corner of your neck and lays a kiss on the sensitive spot. Gooseflesh prickles up and down your body.
“I assure you, I’m very real, little mouse,” Moon purrs. His hands squeeze your hips once. “And as nice as this… attire is, I would dress you in blues and silvers. You would look proper and powerful, like my brothers and I.”
A squeak escapes you. You shrink against him, caught in his embrace.
“Brothers?” The word rattles out of your throat.
“This is our home,” Moon whispers. “And you are our most honored guest.”
You manage to pry off his hands from your waist. With a sinister chuckle, the blue and silver hands release you. Without looking back, you run, ignoring the twinge in your stomach that whispers it was too easy to get away.
You hardly get a few steps before the sunny one—Sun—steps into your path. He catches you in his arms and spins you in a waltz at breakneck speed, your feet never touching the ground, before stopping without warning as he dips you low. He looms above you, his smile filled with sharp teeth.
“Let me get an eyeful. Oh, yes, you look good enough to eat,” he simpers. His hand splays along the small of your back and you gawk up at him, still trying to regain your balance after the sickness-inducing whirl. “You have no idea how long I’ve waited for you.”
“I just want to leave,” you whimper. “Please, don’t hurt me.”
“Hurt you? Sunshine,” he laughs, and it echoes with all of his heart—do once-hanged witches have a heart? There is no historical journey to give context to this very moment, you fear.
He lowers his sultry gaze to you. “I wish to only thank you. And I intend to.”
He pulls you back to your feet. You’re still clasped in his embrace like lovers on a ballroom floor. His hand hooks tight to your hip, and his other catches the side of your face. Heat spreads through the marrow of your bones.
On the tabletop beside you, something white moves across the plane of its surface, hunkering behind the thick stack of candles still burning.
His head lowers to your neck. You stiffen as he tilts your head away, opening you to his parting teeth. A tongue, dark and sinuous, flicks out of his maw. A gasp slips from your lips at the wet lick up the column of your throat. Eyelids fluttering, you start to sag as weakness fills your knees. He drags his tongue higher to taste your jawline and finishes at your cheek with a swipe for good measure.
Your hands find him and clutch tightly to his slender arms. He presses his lips to your ear and with a misty warmth, whispers.
“Thank you for—Gah!”
The white rabbit leaps up from the table, squirming directly between you and his chest, breaking you apart. Instinctively, you jump away just as Sun snarls. The heart-wrenching sound shakes your entire frame as he snatches the rabbit by the scruff before it can scramble back from his wretched claws.
“I’ll boil you alive!” he thunders. He steps towards the cauldron, back where Moon leans against the wall, watching the spectacle with an amusing twitch of his grinning maw. Behind you, Eclipse stands at the door like a sentinel, his eyes still hungry and even furious as he follows his brother’s movement to the cauldron.
Sun dangles the rabbit, now struggling and kicking but unable to find purchase against the witch’s hold, above the boiling water of the caldron.
“No!” you cry.
Sun’s eyes widen. He turns back to you just as you close the distance and scoop the rabbit in your arms. His claws, pale-boned and wickedly curved, clench around emptiness. Without thought, you turn and run again though there is little hope as you come to the door. Your boots stamp against the wooden floorboards.
The rabbit in your embrace turns its face up to you and mutters in a woman’s voice, “You have no idea what you’ve just done.”
You gawk, stunned before hands catch you by the shoulders. You’re brought to a dead halt. The rabbit leaps from your arms, drops to the floor, and races away into a shadowy corner of the room with only one glimpse of its fluffy tail before you’re left alone.
You twist and face the eldest witch’s attention. Eclipse. His yellow eyes go up and down your body, and you watch in muted shock as two additional arms emerge from the shadows of his cap. He forces you backward, one step after the other until your back is pinned against a dusty wall.
You stare into his eyes, chest rising and falling rapidly. Your pulse pounds in your eardrums.
“I don’t believe this is happening,” you utter.
The witch tilts his head with a wicked grin.
“We’ll make you a believer yet.” He promises, and his deep cords vibrate through your form. “My dear, we simply must thank you for all that you’ve done for us.”
His claws slip over your collarbones. Your breath quickens, a stirring you cannot name unfolding deep within your middle. His extra set of hands fall to your hips and begin caressing the bones. Daintily, carefully, his warm fingertips slip just underneath the hem of your sweater, touching your bare flesh. A shiver runs down your entire body, leaving you to squirm.
“Be a good little comet,” he says softly, “Let me pour my gratitude all over you.”
“I didn’t—I didn’t know it was true,” you stare into his face, marked with a red crescent over a dark shadow, and his eyes pierce into the very nature of your being. “You’re back.”
“Because of you,” he rumbles softly in his chest. His grin pulls higher at the corners.
His claws slip over the nap of your neck and card gently into the small, sensitive hairs at the bottom of your skull. You breathe in. His eyes brighten in pleasure before he slips his sharp but controlled talons over the shells of your ears and follows the arch of your cheekbone. His gaze drops to your lips. Your heart thumps and thumps against your sternum so powerfully, you fear he may hear it.
His lips pull over his razor-sharp teeth and you stop breathing.
His other set of hands begins working up the sides of your torso. He rubs slowly and gently, but you squirm despite this. He touches you far too intimately when you have never experienced such affections before. A mewl escapes your lips. You wriggle as he refuses to relent.
In answer, his upper hands lower and capture your hands together in one, and pin them above your head to hold you in place. He coos, chastising. A great roil starts in your stomach and expands upwards until your face becomes pink and flushed.
“Hold still, little comet,” he chuckles, and you whimper. “I’m not finished with showering you in all my adoration.”
“Eclipse,” your breath is harsh and hot.
“It is good to hear my name upon such lovely lips,” his voice lowers, husky and scorching. “I knew a virgin would light the candle. I swore it to my brothers as they set us on the gallows and draped nooses around our necks. You are our light, our savior. How could I ever thank you?”
In his words, his burning stare that singes with sincerity, it clicks into place. All at once, you believe what you are seeing with your own two eyes.
It’s true. He’s back. He and his brothers have returned with magic.
“I have questions,” you say hesitantly in your demureness, “I want answers.”
“Of course,” Eclipse agrees easily. “But first…”
A dark claw brushes your hair back from your face. The flutter in your heart can’t seem to hold still. Eclipse’s grin widens and his eyes soften.
“You have freckles like constellations,” he murmurs in the manner of one gazing at the night sky or one studying an ornate painting.
Before you can shape words to reply, to say anything that might free you from his grasp, his mouth is upon yours. A sound softly catches in the back of your throat. You fall still under his caressing hands still moving below your sweater. He traces the row of your ribs. You have just enough mind to wonder if he feels your skin prickle in your sensitivity. His other hand clasps your wrists tighter. You gasp against his teeth.
He pulls gently, hungrily, taking you as if a bite of honeycomb. You become melted honey, easily malleable between his teeth and then molded by his mouth. His tongue invades you. You moan softly at the claim he lays upon you until you become weak in the knees and almost fall. His kiss seals your fate.
He releases you from his maw. You sink slightly, and his arms fall out from under your sweater to properly catch you. He lowers your wrists, returns your hands, and brushes your hair once more from your face.
A chuckle emits from his lips, and you burn.
“You’ll stay with us, won’t you?” he asks, but he waits for no answer as he scoops you into his arms. Feet dangling, you have no choice but to cling to his shoulders and endure his brothers’ attention as he twists around and faces them.
The rabbit’s right. You are in trouble. Michael warned you. He said curiosity killed the cat.
But charm brought it back.
#naff's writing commissions#witches and rabbits and candles oh my#if michael was there he would be so mad at you for lighting the candle smh#hocus pocus au my beloved#witch!eclipse#witch!sun#witch!moon#charm brought it back#naff writing
456 notes
·
View notes
Text
Important PSA
(Important PSA)
If you get asks claiming to be “technical support staff” asking you to click a link to verify your e-mail because they need your banking credentials or get DMs from similar accounts asking you they need your e-mail address for verification reasons and want your name..
That is a phishing scam impersonating tumblr staff and you should not be posting the asks with a live link in it or trusting the DMs and sending your information! This is an extremely old kind of scam that has began resurfacing and you need to take internet safety into consideration.
It is safer to take a simple screenshot of the ask so the link won’t be spread and lead to a mass hack of users who fell for the attempt. You can warn people without putting their account in danger because some people don’t care what you say and will go to the link anyway.
Please be careful.
588 notes
·
View notes