#wireless networking used
Explore tagged Tumblr posts
Text
#Wireless workplaces have greatly improved communication and collaboration efficiency for enterprises. Furthermore#the latest Wi-Fi 6 and Wi-Fi 7 standards deliver record-high speeds to wireless networks#supporting 4K conferencing and cloud-device synergy in high-concurrency access scenarios. Wireless production environments can improve the#industrial visual quality inspection#and HD wireless backhaul of industrial cameras.#Huawei AirEngine Wi-Fi series products are next-generation wireless network products designed for enterprises' workplaces and production sp#indoor and outdoor wireless networks built using Huawei AirEngine can fully meet requirements of customers across industries#and adapt to ever-changing terminal and application demands in the digital space.
0 notes
Text
Are you tired of grappling with network connectivity issues? Say goodbye to frustrating WiFi setup woes with our comprehensive guide on connecting to network WiFi using 192.168.188.1! Whether you're a novice or a tech-savvy individual, our step-by-step instructions will empower you to effortlessly establish a stable connection and enjoy uninterrupted internet access.
#Connect to Network WiFi Using 192.168.188.1#192.168.188.1#192.168.188.1 wireless extender setup#192.168.188.1 admin setup#192.168.188.1 setup#wifi repeater 192.168.188.1 admin setup#192.168.188.1 repeater
0 notes
Text
Your robot girlfriend has to power down to replace her backup battery. The regular batteries are easy to swap while she's online, but that small JR2035 battery that keeps her config saved and clock ticking is way buried inside her chassis.
She holds her chest open as wide as she can pull, and you flip her power switch. The light literally leaves her eyes as the OLEDs power down. Holding the flashlight in your teeth, you reach in with a hand and a flat-blade screwdriver (your last spudger snapped when you were fixing her hand servos last week).
With a soft snap, her backup battery bounces out and ricochets down her torse. You swear and let it end up on the floor, as you carefully reach up to insert the replacement coin cell. It takes a couple fumbling tries, but you get it in, and the right way around too as a special bonus.
You extract yourself from her internals, and plug the diagnostic screen into one of her internal UDMI ports. The switch is flipped with a satisfying clunk, and the display pops to life. Boot messages start streaming by, then it pauses with a softly blinking error:
BIOS settings cleared, please enter setup.
You hit a key on a nearby wireless keyboard, and the bios opens up, all white-on-blue plain text because your GF is, to use a highly technical retrorobotics term, a bit of a MILF.
You set up the basic options for her to boot. She can fine tune this later. You just need her to get running enough to do that. You tell it what kind of hard drive she uses, how many floppy drives she has, pronouns and orientation, etc. You hit F7 to save and reboot and you spot it: the date.
Current Time: 00:04
Current Date: 1970-01-01
Damn it, you're always forgetting to set the date in these things! She's already booting, you can see the spinning logo in her eyes. Ah well. You can reboot her and fix it, or maybe it'll auto-set from the network? You can't remember if that'll work.
The logo leaves her screen. You see that finger twitch of her final boot up, and her irises reappear and quickly focus. Her hair starts to blink in as the holoprojectors spin up, and she starts to sit up.
"Hey... I swapped the battery, how are you feeling?"
She gets that smile where her eyes go big. Her holos blink and her clothes change, and half an instant later, her hair.
The music system in your living room switches over to a sweet bassline.
Disco?
You turn as she stands up, and starts doing the Staying Alive dance. She's got the white leisuresuit, and an afro that seems to be growing by the second.
well you can tell by the way I use my walk, I'm a woman's bot, no time to talk!
Ahh. 1970.
299 notes
·
View notes
Note
Concept: the Staff of Forbidden Spinjitzu doesn't whisper to Zane. Instead, its "whispers" take the form of popups along his HUD disguised as alerts or warnings. Things like "If you put me down now, your friends will never find you. [OK]” or “Killing these prisoners villagers will increase Vex’s approval and reinforce your reign. Proceed? [Y/N]”
(I like this particular flavor because it really leans into Zane's robotic nature: he can ignore whispers by turning off his auditory sensors or filtering noise, but he can't ignore system alerts.)
Also, the following scene has lived rent-free in my brain ever since I came up with the concept. (Italics are Zane's default OS. Everything else is the Staff.)
>IF YOU ARE GOING TO DESTROY ME, "ZANE" -Move File:"NeverrealmMemories" to Core Memory Functions-WARNING: Attempting to delete, move, or suppress File"NeverrealmMemories" after moving will cause total system failure. Proceed with move anyway? >[YES] -File transferred. -Permanently remove fatal combat safeguards? >[YES] -Safeguards removed. >THEN I WILL MAKE SURE YOU CAN NEVER FORGET WHAT YOU DID, SYSID:ICEEMPEROR
-Connection Terminated.
(I have a few more Ideas for the "Scroll Corruption looks like Computer Alert messages to Zane" idea-ones that really lean into Zanes Nindroid nature, as well as the tech-y appearance of the Dark Ice.) -The Staff did a lot more than just send alert messages: it slowly wormed its way into Zane's code like a computer virus, tweaking a few things. It took great care to remove Zane's combat safeguards, eventually deleting them entirely and ensuing he defaulted to lethal force. It never removed his core directive of "Protecting those who cannot protect themselves" since that was vital to his systems running, but it did reinterpret said directive as "Protect Dark Ice Network and everything connected to it, for it is fragile and cannot protect itself from outsiders". (It also couldn't delete his morality subroutines without causing a crash, so it instead made them a much lower priority and shoved them to the back of his digital mind.) -After 60+ years of being in the grasp of a mechanical being, the Staff now exclusively speaks in the manner of a computer, and cannot adapt to organic minds the way it used to. (The other Staff is not like this, as it's still attuned to organic brains.) -You know those Sci-Fi stories where people are plugged into computers and know every part of the ship/city simultaneously, and can send most of their awareness into certain parts of the network while still being aware of other locations? That's what's going on with the Never Realm during the Ice Emperor's Reign, with the Ice Emperor as the central guiding consciousness/core CPU of the Dark Ice Network. As such, he's not actually sleeping-rather, the Ice Emperor is always monitoring his domain through his Ice and leaving just enough of his consciousness in his body to be able to call the rest of himself back in case he's threatened. (The Staff is a combination of a computer virus and a wireless modem: it is corrupting, but it's also the main point of connection for the Dark Ice Network.) -Since the Ice Emperor can't recharge his power on his own in his current state, the Staff had to step in, tweaking the Dark Ice to drain the vitality of those imprisoned within. (You know wireless phone chargers, or Nikolai Tesla's idea to get electric power from the atmosphere? Similar concept, except with the power source being frozen people and the transmitter being Evil Magic Ice.) -Boreal is the Titanium Dragon, corrupted by the Staff's presence. It too is part of the Dark Ice Network, and serves as Ice Emperor's eyes and ears whenever the Dark Ice can't reach. (If the Ice network used computer program language, Boreal would be known as "Obj_DarkIceTitaniumDrake".) Killing Boreal caused a massive jolt to the Dark Ice Network that destabilized the Scroll's influence, and allowed an opening for Zane's Memory Defragmentation program to kick in. (It had started when Lloyd arrived in the throne room, but the Scroll had diverted that to a minor priority and was actively hiding that set of files until the word "Protect" slipped through, forcing Zane's systems to call up what had been defragmented.) -As a final act of spite for being broken, the Staff encoded Zane's memories of the Never realm to his Core Processing systems, meaning he cannot forget the Never Realm without completely frying his systems and rendering him a lifeless shell. (It might've also made a backup of itself amidst his various repressed memory files, but he doesn't need to know that. It's just sitting there, disguised as a normal .zip file, biding its time.) (I really like genre-blending Sci-Fi and Fantasy, and I thought the idea of "Magic Ice Computer Network" is rad as hell.)
(This song is a big part the inspiration for part of the "Dark Ice Network" idea, by the way. Granted, the Staff of Forbidden Spinjitzu doesn't assimilate Zane's psyche like Star Dream assimilates Haltmann's, but a lot of the ideas are still there-and the Staff does still integrate itself pretty deeply into the Nindroid's code as it slowly actualizes.)

I have no words for how absolutely awesome this is in every way. i just keep rereading this and being amazed. the "Dark Ice Network" idea is literally so cool, I particularly love the Ice Emperor being able to monitor the entire land while his body/the staff is the main 'hub' he has to protect. this is aweosme.
everyone look now please
#ninjago#zane julien#ns11#ninjago ice chapter#ninjago ice emperor#spinchip posts#<just so i can find it later
211 notes
·
View notes
Text
how old is tenna. like actually

okay so 4 hours ago at 2am i saw someone say tenna is from the 70s (likely because he's a game show host) and my gut reaction was There's absolutely no way that's true, he's for sure a late 80s or early 90s tv. but i realized if i were to believe that i should probably have a verifiable reason to, so i went and made sure i did my research to validate my opinion. my opinion has not changed, i still think he's probably supposed to be from the late 80s, but here's why i think that.
so. if i wanted to be anal retentive as fuck about it, i could say that if deltarune is meant to have a similar in-universe technological development timeline to ours irl, and if deltarune is indeed meant to take place in some analogous place to the united states, then tenna is likely no older than 18 (from 2007). because he's a crt receiving over the air signals, but past 2009 irl it would need to be a digital signal, and i assume deltarune takes place after 2009, and tenna crucially does not appear to have a converter box. which would mean he'd need to have that capability built in.
however, i like. really badly do not think that matters. not only am i positive he's meant to be much older than a tv from 2007, but i just don't think a detail that minuscule would be on anybody's list of priorities when designing an old tv in fiction.
so let's imagine none of that factors into how old he could be at all. what else can we go off of. primarily i want to first look at his design. you'll notice that although he verbally references one, tenna does not actually appear to have a dial in any visual we have of him. he doesn't even look like he has a button array of any kind.


this was extremely uncommon for the 1970s, especially for just everyday family households on an average budget. this wasn't, however, as uncommon after the 80s swung around. you'd still see a lot of tvs with dials on the side, but it wasn't so notably rare to see ones lacking in this control scheme.
part of this is likely due to the invention of the infrared remote, which would take television manufacturing by storm in the 80s. to be clear, wireless remotes for tvs did exist before this, but i specifically do think the zappers are infrared due to their attack patterns and sprite movements. if this is true (and especially if the zappers are universal remotes), then the existence of the zappers would support the assumption that tenna is from the 80s at the very earliest.
as an aside on the topic of tenna's appearance, while i do think the photorealistic images are more of a visual gag than anything meant to be like. concrete canon appearance of the guy. i do want to point out that the ridged edges he has were especially typical of 80s zennith tv sets. which makes sense to me, because zenniths were pretty state-of-the-art at the time.
another thing we could look at for clues to his age is the "programming" itsself. there are a few minor details to this i'd like to point out. none of these necessarily materially impact how old tenna could be, but seeing as he's already designed as a symbolic gesture towards nostalgia, understanding the references made with these small details can help us better construct what timeframe he's meant to evoke.
first of all, his reference to a "cooking channel". correct me if i'm wrong, but i'm pretty sure the first cooking channel broadcast in america was the food network, which is from the 90s. there is also literally a Cooking Channel (proper name) but i think it's from like 2002
secondly, the rhythm minigame. live music performances have been on the air forever and ever, but specifically the channel he's on is one dedicated to music videos. that wasn't hardly a thing at all until mtv. which is from the 80s. (Adding onto this point hours later hi. they're also specifically performing hair metal, which is. 80s.)
thirdly is the existence of lanino and elnina, who are (to me at least) a blatant reference to the weather channel. weather is a staple of television, of course, but i do mean the weather channel specifically. which is from the 80s. (also. this is going to seem like a stretch but the line "weather girls are the wave!" reminds me of the work done by 2nd wave feminists to make it so that more women could go into news network jobs. so that's cool)
i do also want to point out an even smaller tidbit. tenna interrupts (or claims to interrupt) his normal programming for breaking news. this was not impossible, per se, before the 80s, but it didn't become a regular occurrence until the 80s as well, after the inception of CNN. again, this doesn't mean tenna wasn't possibly at all manufactured sooner than this, but thinking about this from a fiction writing perspective, what matters here is what tenna is mean to make the player feel. these references are ones to a world post-cnn, post-food network, post-mtv. it's an expression of fondness for a very specific past.
this is also true in how older tech itsself is utilized. the tv time intro being played back with vhs effects is telling to me, because vhs wasn't the dominant household market video format until the 80s and 90s. this is even present in the format of the game show. it's a merging of the game show concept and the prevalent force of 90s video games. television programs based on video games weren't uncommon at the time, as they were essentially literally an attempt to teach an old dog new tricks. nick arcade came to mind right away for me the first time i saw the boards.
so that's why i think he's supposed to be 80s or 90s tech. honestly, this still makes him a ridiculously old crt. most crts on a regular use schedule will last a while, but only a little over a decade.
anyways so that's my stance. i;m so so tired
#shadow's posts#deltarune spoilers#i'm insane. Hi#long post#<removing the readmore because i have more to say that i'm going to space out in a reblog. Hi
65 notes
·
View notes
Text




THURSDAY HERO: Nancy Wake
Nancy Wake was a gutsy journalist from Australia who became a leader of the Allied resistance and killed a Nazi with her bare hands.
Nancy Wake was a gutsy journalist from Australia who became a leader of the Allied resistance and killed a Nazi with her bare hands.
Born in New Zealand in 1912, Nancy was raised in Sydney. She ran away from home at age 16 and went to London, where she became a self-taught journalist.
As a young woman, Nancy described herself as someone who loved nothing more than a “good drink and handsome men, especially French men.” In 1930 she married Henri Edmond Fiocca, a wealthy French industrialist.
During the 1930’s Nancy worked for Hearst newspapers as a European correspondent. Stationed in Vienna, Nancy witnessed the rise of Nazism. She was shocked to see roving gangs of Nazis beating up Jews, and never forgot the sight of Jews chained to massive wheels and rolled through the streets. She later said, “I resolved there and then that if I ever had the chance I would do anything to make things more difficult for their rotten party.”
Nancy became a courier for the French resistance. Speaking perfect French, she worked with the “maquis” – guerrilla bands of resistance fighters. After Germany invaded France, she helped Allied POW’s and other personnel escape the country.
The Gestapo called Nancy the “White Mouse.” They tapped her phone and intercepted her mail. Nancy’s life was in constant danger.
Nancy described her method of avoiding detection by the Germans: “A little powder and a little drink on the way, and I’d pass their German posts and wink and say, ‘Do you want to search me?’ God, what a flirtatious little bastard I was.”
Nancy led repeated attacks on Gestapo headquarters. By 1943, she was the most wanted resistance fighter, with a 5 million franc price on her head.
After Nancy’s maquis network was betrayed, she fled France. Her husband stayed behind, and he was captured, tortured and killed by the Gestapo. Nancy, on her way across the Pyrenees to Spain, was unaware of her husband’s death until after the war.
In 1944, Nancy parachuted into France. Her assignment involved collecting and distributing arms and equipment that were sent in by parachute. Nancy was a highly successful recruiter, and is credited with bringing 7500 fighters into the resistance.
From April 1944 until the liberation of France in August 1944, Nancy’s band of maquisards fought 22,000 German soldiers, causing 1400 casualties while sustaining only 100 of their own.
At one point, Nancy killed an SS guard with her bare hands to stop him from raising the alarm during a raid. She later described how she did it, “They’d taught this judo-chop stuff with the flat of the hand at SOE [special operations training] and I practiced away at it. But this was the only time I used it – whack – and it killed him all right. I was really surprised.”
Another time, Nancy’s wireless operator was shut down in a German raid, and she rode her bicycle over 300 miles through German checkpoints to deliver the secret codes.
After the war, Nancy was awarded the United States Medal of Freedom, the Medaille de la Resistance, and the Croix de Guerre, among many other honors.
Nancy continued to work as an intelligence agent. She married a Royal Air Force officer in 1957 and for the next several decades they divided their time between London and Australia. Nancy’s autobiography, The White Mouse, was published in 1985 and became a bestseller.
Nancy’s husband died in 2001, and she returned to London permanently. She lived at the Stafford Hotel near Picadilly, her expenses largely paid for by the hotel’s owners, who were honored to host a renowned heroine. She could be found every morning at the hotel bar, drinking her first gin and tonic of the day.
Nancy died in 2011 at age 98. Her remarkable story has been the subject of multiple biographies and television mini-series.
For fighting the good fight against the Nazi war machine, we honor Nancy Wake as this week’s Thursday Hero.
74 notes
·
View notes
Text
Here’s how to share sensitive leaks with the press
Published Oct. 16, 2019 Updated Jan. 31, 2025 / Freedom of the Press Foundation

[please take a moment to click the links at the bottom to give this website traffic if you can. the only reason I am copy pasting it here is for those who can access tumblr but not necessarily that site.]
~~~
Over the years, we have witnessed abuse and mismanagement in the government and private sector — sometimes bad and sometimes worse — that need to be brought to public attention. For those who would leak information about such misdeeds to the press, giving tips to journalists can be risky and may violate previous legal agreements with the leaker’s organization, such as a nondisclosure agreement or contract. But sometimes, it can also be an effective and courageous way to call attention to misconduct.
This guide describes basic steps for minimizing potential risk when sharing sensitive information with a news organization. We want to be clear that no piece of software, nor security recommendation, will be 100% effective, and the decision to blow the whistle may invite scrutiny or retaliation. At the same time, it may be a choice that drives necessary institutional change. Before reaching out to the press, think carefully about what you can do to minimize that risk and stay as safe as possible.
Before moving ahead, do you have a strong tip?
A good tip requires clear evidence and should be the basis for a story that the broader public needs to know about.
So, for instance, whether or not you have evidence, the broader public might not need to know that a neighbor refuses to pick up after her dog on the morning walk. On the other hand, allegations of corruption or illegality among public officials are certainly newsworthy, but those claims will not make it into a published story without verifiable evidence.
Who are you leaking about and how might they respond?
Think about the sensitivity of the information you’re sharing, and who might be willing to investigate the source of the leak. What are the organization’s capabilities? What resources (e.g., attention and legal, financial, or technical) can it invest in discovering the source? And how likely do you think it is that it will actually investigate?
If you share information about a large, well-resourced organization that requires discretion from employees, such as a government agency, it may have enormous legal, financial, and technical resources available for investigating a leak. If you’re sharing information about a small organization, such as a local restaurant that muzzles workers, its resources are much more constrained, and it may not have the capacity or willingness to investigate. Act accordingly.
Proceed with caution
Be cautious about behaviors that could make you readily identifiable as a source.
Keep all of your leaking activities outside the view of your organization. That means no calling from work, no emailing from a work email address, and staying off work devices or wireless networks.
It's common for well-resourced organizations to keep logs of activities on employees’ workplace devices and online activities. Likewise, sometimes workplaces have “BYOD” (bring your own device) technologies that could allow them to log your activity on your personal device. So if you work at a large organization and you're reading this article on a workplace device or Wi-Fi network, chances are your workplace already has a log that you've accessed this page. Similarly, a visit to a news organization's tip page (like https://www.nytimes.com/tips) may be logged by your workplace. This is why it's so important to limit your leaking activities to devices and networks that your workplace doesn't control.
Has your workplace ever required you to install monitoring software (or software of any kind) on your work or personal device? If so, you probably don't want to use those devices for any whistleblowing activities.
Be cautious about giving tips on anything that only you could know or materials that only you could access. And consider whether the increased risk of being caught sharing these kinds of materials is worthwhile, or if you feel you have a strong moral obligation to do so.
If you are the only one at your organization surfacing a specific grievance, and information about that grievance is later reported by the press, it may give your organization a strong hint about who shared the information.
Don’t tell anyone about your leaking activities (even perhaps the journalist or news organization you’re leaking to), except where absolutely necessary and in cases where you may want legal advice from a practicing lawyer.
Reporters generally take their commitment to protecting your identity very seriously and will do everything in their power to fight potential legal requests for identifying information about you. But often, it’s safer not to give your identity if you don’t have to. Keep in mind that journalists prefer to have proof of your claims and information to demonstrate your identity is a part of that.
Tactics for minimizing risk
There are a lot of ways to minimize the risk of a tip being tied to you, like potentially through your continued communications with reporters.
Send your materials through physical mail. You can mail electronic documents (e.g., on an SD card) or physical documents through ordinary mail. Be warned: The U.S. postal service takes pictures of the exterior of physical mail. So don’t use a return address that is associated with you and instead mail it in from a sidewalk mailbox in a location you don’t usually frequent. If you have a particular reporter you want to look into your story, copy them on the envelope.
Call from a phone number unconnected to you. For example, go to a business you don’t usually go to and ask to use their phone. You can also buy a cheap cell phone and a prepaid phone card that cannot be traced back to you. But know this involves several careful steps: You must pay with cash, and if your organization can have access to phone location records, it’s best to only turn on the phone in locations unassociated with you. That also means using the phone in locations separate from your permanent phone. If you can, remove the battery when it’s not in use.
Use Signal for private messaging. Signal is a secure, free, and open source messaging app for iPhones and Android devices. Signal gives you end-to-end encrypted messages and phone calls, and only retains your phone number, your signup date, and when you were last active. In Signal, you can also make messages automatically self-destruct for everyone in the conversation after a set amount of time. This makes it significantly harder (but not impossible) to eavesdrop on your conversations. If you want help getting started, read this beginner-friendly guide on using Signal. Note that Signal allows usernames, so you do not need to give your name or phone number to media organizations unless you choose to. Make sure your username is enabled and understand that Signal is not designed for complete anonymity.
Before looking into news organizations, consider using the Tor Browser for greater privacy. Tor Browser is a modified version of Firefox. Tor encrypts and tunnels your web traffic within a global network of computers before connecting you to your final destination. When you access a website through Tor (for example, Amazon.com), you will appear to connect from a remote location — likely another country. Again, don't use a work device or network for this kind of research.
Use a whistleblower submission system. Tools such as SecureDrop can provide protection by allowing you to share documents and communications through an anonymous and encrypted drop box.
More technical, but more secure: SecureDrop
With SecureDrop, which is maintained by Freedom of the Press Foundation, not even the news organization knows who you are unless you choose to tell them.
A growing number of news organizations (e.g., The New York Times, The Washington Post, The Intercept, The Guardian) are using SecureDrop to allow sources to reach out and share files or communications anonymously. With SecureDrop, not even the news organization knows who you are unless you choose to tell them.
You can access a news organization’s SecureDrop page through Tor Browser.
People on your network can’t see what you’re doing on Tor, but it’s still possible to tell that you’re using Tor. With that in mind, do not use it at work. For greater security, consider using Tor Browser only over a Wi-Fi network in a location that is not tied to you (perhaps a coffee shop you don’t normally visit) and pay with cash.
As opposed to a “.com” web address, you get to SecureDrop through a unique .onion web address, which can only be accessed through Tor.
Using SecureDrop is fairly easy
Follow the directions to download the Tor Browser at torproject.org and install it.
Launch the Tor Browser application and click "Connect" to log into the network.
Click the shield icon in the top corner > Advanced Security Settings… > Safest
Within Tor Browser, navigate to the SecureDrop directory and search for your preferred news organization: securedrop.org/directory
Find the .onion URL for your preferred publication (e.g., The New York Times: securedrop.org/directory/new-york-times), then copy and paste it into the address bar in Tor Browser.
From here, you can leave messages and files that the news organization will check from time to time.
You will be given a random “codename” for continued conversation with the news org. Keep this information safe, and don’t share it with anyone. If you lose your codename, they can’t reach you anymore.
(For more technically adept users, consider accessing SecureDrop through an operating system designed for privacy and anonymity, such as Tails.)
Dealing with file metadata
Sharing information may be less risky than sharing documents because they can be embedded with information about the file, which we call metadata. For example, if you create a .docx file, it may have identifying information about you embedded in the file. Consider carefully whether you really need to share files or just the information.
To deal with hidden metadata, rather than sending the file itself, consider taking a picture of a document with an old-fashioned camera (not a smartphone), or taking a screenshot of the document. On most operating systems, screenshots come with little useful metadata. For more technical users, you can find metadata removal tools here.
Where do you find a news organization's contact details?
First, be careful where you reach out.
Freedom of the Press Foundation maintains a list of organizations that support the secure communications practices outlined above, and how you can contact them. Such practices are becoming standard, and we hope other news organizations looking for great tips will follow suit.
Freedom of the Press Foundation hosts a directory of SecureDrop and secure tip pages for dozens of news organizations around the world. Whether you want to reach out to The New York Times, The Washington Post, The Guardian, The Intercept, or others, you can find their information here: https://securedrop.org/directory. (We would not recommend investigating this at work.)
If not you, then who?
Sharing information with the press is not always an easy decision, but your information can help to hold powerful people and institutions accountable. Just be sure to move ahead with a strong understanding of your organization’s capabilities and how to share tips safely.
https://freedom.press/digisec/blog/sharing-sensitive-leaks-press/
https://bsky.app/profile/freedom.press/post/3lh2rgopf5225
127 notes
·
View notes
Text

"Decorate your phone with Tokyo Mew Mew!"
Nakayoshi 10/2002
Magazine Ad for a Tokyo Mew Mew wallpaper using I-mode (I-Mode, stands for Internet. -mode is a mobile internet service popular in Japan. Unlike Wireless Application Protocols, i-mode encompasses a wider variety of internet standards, including web access, e-mail, and the packet-switched network that delivers the data.)
Which will end services in 2026
Scan by MyuMyuCheerCh on X
35 notes
·
View notes
Text
🚢 Tesla's Remote Control Patent: The Birth of Modern Automation 🚢

On November 8, 1898, Nikola Tesla was granted U.S. Patent No. 613,809 for his "Method of and Apparatus for Controlling Mechanism of Moving Vessels or Vehicles." This invention wasn’t just the first practical remote control—it marked a revolutionary step toward the development of wireless communication and automation.
🔧 How Tesla’s System Worked 🔧
Tesla's system worked much like how we control drones today—only over a century ago!
1️⃣ Transmitter: Tesla used radio waves to send wireless commands to the vessel.
2️⃣ Receiver: The vessel had a sensitive device that decoded the radio signals into specific actions, such as steering or powering motors.
3️⃣ Control Circuits: Tesla designed a series of circuits that ensured each command executed reliably, preventing errors and interference.

⚙️ Key Features ⚙️
💡 Command Logic: Tesla's circuits functioned like a primitive decision-making system, linking specific signals to specific actions—a conceptual precursor to today’s logic gates.
🔋 Multi-Channel Design: Each circuit operated on a unique frequency, akin to modern multi-device networks, ensuring precise control without interference.
🛡️ Safety First: Tesla implemented mechanisms to prevent accidental or incorrect activations, prioritizing reliability.

🌍 Applications Then and Now 🌍
Tesla saw the potential for:
✔️ Military Use: Guiding unmanned ships or torpedoes.
✔️ Disaster Response: Sending unmanned vessels into dangerous areas.
✔️ Remote Automation: Introducing wireless precision to various industries.
Today, Tesla's vision echoes in:
🚁 Drones: Controlled remotely through radio signals.
🤖 Robots: Autonomous machines performing tasks with precision.
🏠 Smart Homes: Devices responding to commands over Wi-Fi.
🏭 Automated Factories: Machines operating through programmable controls Tesla helped inspire.
🌟 Why Tesla’s Invention Matters 🌟
Tesla didn’t just create a remote control—he pioneered a framework for wireless systems that continues to shape modern technology. What are your thoughts on Tesla's advancement in wireless technology?
72 notes
·
View notes
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text
youtube
Kaaren Thompson, the host of Karma Dog Speak, dives into the unboxing and reviewing of the highly anticipated Halo 3 dog collar. Released by Halo on September 1st, this latest addition to the Halo collar series boasts significant improvements. Kaaren thoroughly explores the orchid-colored Halo 3, noting its matte finish and unveiling its contents, including the magnetic charging port and USB-C adapter.
As she delves into the features, Kaaren emphasizes the collar's waterproof design, highlighting the convenience of the new magnetic charging port for maintaining its durability. The collar's adjustable fit and quick fit system, as well as the innovative GPS accuracy and AI technology, are showcased in her comprehensive review.
Kaaren draws on her extensive experience with the Halo collar series, expressing her admiration for its impact on pet training and boundary setting. Throughout the video, she discusses the collar's practicality and cost-effectiveness compared to traditional invisible fences, emphasizing its impressive battery life.
Cesar Millan, the renowned dog behaviorist, plays a pivotal role in developing and promoting the Halo collar, further enhancing its credibility. Kaaren encourages viewers to use her code when purchasing the Halo 3 collar and invites questions or comments.
In this engaging review on Karma Dog Speak, Kaaren seamlessly integrates essential keywords such as "halo collar," "Cesar Millan," "dog training," "halo collar setup," "wireless dog fence," and many more, providing a comprehensive and informative guide for potential buyers.
🐶UNRIVALED FEATURES!🐶 CHECK OUT THE GAME-CHANGING FEATS OF THE NEW HALO COLLAR 3:
✅ New PrecisionGPS(™) Technology ✅ New Active GPS Antenna ✅ 24-hour Battery Life ✅ Auto-connect to Any Cellular Network Worldwide ✅ New Perfect Fit System ✅ Magnetic Charging Port ✅ New Colors: Orchid and Sunburst
NEW COLORS Halo Collar 3 is available in 4 vibrant colors: ✅GRAY ✅BLACK ✅ORCHID🆕 ✅SUNBURST🆕
225 notes
·
View notes
Text
Updated Ortho Facts Part 18: Ortho's Abilities (pt4)
When Kalim talks about Jamil wanting to take him to a theme park Ortho calculates the odds of such happening as “less than one percent,” and we also see him assigning percentages to how likely it is that the students will suffer injury if they do not do as Idia says during Book 6.
Ortho says he can predict most things through simulations and data crunching, “so it’s really nice when something unexpected happens.”


Ortho and Lilia complain together about the predictability of a Playfulland ride, with Ortho suggesting the implementation of randomized movements.
Ortho says that he enjoys research and gathering data.



Ortho is also equipped with a “built-in emergency magical disaster alert” which is triggered when he is wearing his Ignihyde gear. It is not specified if blot density increase detection is equipped only to his Ignihyde Gear or if it is something he can do regardless of the gear he wears. The alert goes to STYX.



Ortho will occasionally reference online searches that he performs, even offering to look up the physical address of Idia’s online game friend Muscle Red.
Ortho explains, “There's essentially no such thing as anonymity online for me.”



Ortho is also capable of QR code scanning and email. In his incorporeal state in Idia’s dream he is capable of connecting to wireless speakers and simple, non-technomantic electronics.



Ortho suffers his equivalent of falling unconscious in response to Malleus’ unique magic and escapes by uploading himself over the school’s public wi-fi.
He attempts to use the Land of Dawning’s network and undersea cables to send himself to STYX but fails due to Malleus’ energy field, which has stopped time.


Ortho notices Idia’s tablet and says it should support satellite broadband, as Idia designed it to connect with a STYX prototype communications satellite via an antenna that he secretly set up on a large tree behind the school.
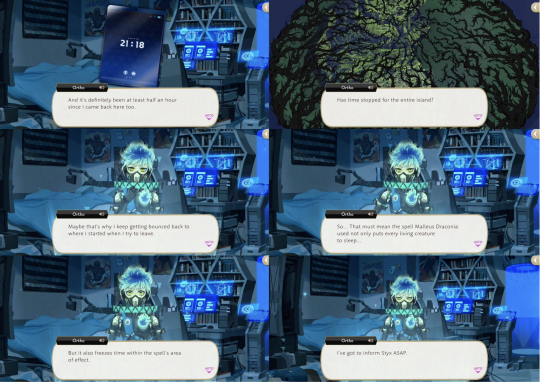

41 notes
·
View notes
Text
A few of you asked, so here's how I'd re-write the opening act to Horizon Forbidden West to give Aloy—and Elisabet Sobeck—the respect she deserves.
(Putting all 1600!!! words of this under a jump cut for spoiler reasons.)
My biggest beef with HFW is that it has a Sylens problem. Namely, keeping him five steps ahead of Aloy and having him lead her by the nose from place to place doesn't make him a better, more threatening villain. It makes Aloy look incompetent, and even worse, makes us question her exceptional nature. (If some guy can figure all this technology out, what's so special about Aloy?) I'll have more to say later about Aloy's exceptionalism as it's key (hee hee) to this entire story.
So here's how I'd fix what ails canon. Imagine an HFW that begins much like the original game, with Aloy (along with Varl) searching for the GAIA kernel at Far Zenith HQ, where she eventually discovers the Travis Tate logic bomb that deleted all the stolen copies of the kernel. Out of ideas, she and Varl travel to Meridian to consult with Blameless Marad, from whom she learns of the recent activation of the Spire. She investigates the burnt-out Horus core and realizes that whatever was left of HADES, it's been stolen by Sylens.
She climbs the Spire. At the top, she overrides the input jack and accesses the Spire's logs, which indicate that the Spire was recently used to relay a large quantity of data to a location unknown.
Back on the ground, Aloy asks Avad and Blameless Marad to have their scholars search the records of the Carja army taken during excursions in the Forbidden West for anything that might resemble a base or installation built by the Old Ones: every triangle door, every strange ruin. If Aloy has to look inside every cave in the West, she will do it.
While she waits, she catches up with her old friends in Meridian. Then, she has a conversation with Varl, where she admits her frustration with the search for GAIA proving difficult and fruitless so far. They talk about the hologram they saw at Zenith HQ, and Varl makes a remark about Travis Tate and his working relationship with Elisabet Sobeck, and how it seems they had a plan for everything.
This jogs something in Aloy's mind: how could Tate and Elisabet be confident in the work they produced if they didn't have a place to test it? A safe place. Thinking again of Sylens and how he stole HADES out from under her—and of his repeated attempts to hack into her Focus that she keeps having to block—she knows this place would have to be isolated and shielded from the rest of the world.
In a cutscene, we see her back at the top of the Spire, using the input jack to send it commands. As the Spire is connected to physical networks and it's also a wireless/radio transmitter, she uses it to scan the Forbidden West, looking for "empty spaces" in the network/wireless grid, gaps where a secret base might be found. The result is a set of three candidate coordinates, scattered in No Man's Land, the buffer between the Sundom and the Forbidden West.
But to get there, she'll have to get through the gate at Barren Light. A token from Avad will grant her the authority to pass through the gate, but she'll need to make peace with the Tenakth herself for permission to travel through their lands. Luckily for her, there's a diplomatic Embassy coming up. As in the original game, Aloy sneaks out late at night and leaves Varl behind.
Arriving at the Daunt, Aloy learns that there's trouble all over: machines infesting the valley, a work stoppage in Chainscrape, sabotage at Barren Light—and the Embassy is on hold until all of it is addressed.
Aloy begins clearing the valley of machines, and once she reaches Chainscrape, she runs into Petra, another old friend, and doesn't turn down an offer to catch up over a brew. This is how Aloy learns that Ulvund, the self-appointed "leader" of the Oseram workforce, is the one behind the work stoppage.
Time for a talk with the guy. Ulvund tries to bully Aloy around, but she's not going to let some pissant Oseram get in her way: he's going to blow the damn whistle if he doesn't want an arrow in his head. When he threatens her by calling his thugs to come closer, she tells him she'll put arrows in all their heads. Ulvund backs down, the whistle blows, and the work stoppage comes to an end. (The same sidequests are available as in the original game. If Aloy wants to bring him down further, she can do those quests as well.)
Once Aloy reaches Barren Light, she learns that the gate has been sabotaged. After a conversation with a Carja soldier falsely imprisoned for murder and some investigative legwork, Aloy discovers that the saboteurs are Eclipse cultists, who are operating out of a camp hidden somewhere in the Daunt. In a series of quests, Aloy uncovers their plans to attack the Embassy, discovers that they are following orders sent from somewhere to the west, and finally puts an end to their operation in the Daunt by destroying their camp. (In this fix-it, the Eclipse sidequest is elevated to a main quest and expanded.)
With the Eclipse and machine threats neutralized, the Embassy takes place as it does in the original game: Varl arrives just in time to join Aloy, they meet Fashav, Regalla attacks, the Embassy is annihilated.
But there's no time for grieving—or waiting for Varl's ankle to heal—as Aloy now has full access to No Man's Land and can proceed to the three candidate coordinates for the secret lab in any order.
Candidate 1 is a ruin but there's nothing of value to be found inside other than a few datapoints of lore.
Candidate 2 is a ruin near a Horus in the far north, where Aloy finds Sylens's abandoned workshop and the broken remnants of HADES trapped within the Horus's battered core. Sylens does not communicate directly to Aloy here; instead, she hacks into the ruin's surveillance system and watches a holo-log of his interrogation. Her conversation and eventual purging of HADES happen as they did in the original game. (All this quest does is provide more background lore as to what Sylens has been up to.)
Candidate 3 is the LATOPOLIS testing lab. The gene-locked door is not blocked by firegleam, and Aloy can enter easily. The rest of the LATOPOLIS sequence proceeds as in the original game—but without any involvement from Sylens. Aloy unlocks the storage container for the GAIA kernel and grabs a copy, only to be interrupted by the arrival of the Zeniths—and Beta the Sobeck clone—who were drawn to a stray radio signal that escaped from the lab during Aloy's explorations. (Perhaps the exterior shielding door gets jammed slightly open when the mechanism is operated for the first time in a thousand years.)
Now let's talk about Beta, and why her reveal is so crucial to HFW's story.
Until now, the Aloy we know is exceptional. Not only is she a world-class athlete and huntress, she's the clone of one of the greatest scientific minds humanity has ever produced and the one person left on earth who can activate the gene-locked doors and computer systems that require Alpha Prime access. She is the heroine of this story, the only one we trust to save the world. Aloy is the key.
Then Beta shows up. That's what we call an oh shit! moment. Now we have two keys in play—and Aloy is no longer as unique or exceptional as she once was.
If Aloy is the heart of Horizon, Beta is its soul. As much as the two clones have in common, and as much as one could argue that GAIA created Aloy to serve as a tool, Beta is that idea taken to the extreme: raised in isolation, taught only what was necessary to achieve the Zeniths' goals, she is the pure form of a genetic key. And the gap, the juxtaposition between Aloy and Beta is where this story gets interesting. Who is an Elisabet Sobeck clone beyond simply being a key?
That's the story lurking beneath the plot that I want to know more about.
(Regarding the firegleam igniter, Aloy learns the recipe to build one from the Oseram tinkerers Delah and Boomer. She can learn it in the Daunt during their first quest, or later in the desert during the second if she missed them the first time around.)
Aloy escapes from LATOPOLIS, nearly drowning when the effluent sweeps her into a nearby river. She manages to swim ashore, then loses consciousness.
Time passes in fever dreams of Rost and All Mother Mountain and other memories of the past, strange voices and hands, smears of yellow and green.
She awakens in an Utaru outpost, having been brought there by a party of Utaru foragers who found her on the riverbank. She's been delirious for a few days, and is injured badly enough that she'll have to stay longer. She doesn't get to shrug it off. The sun rises and sets, rises and sets, rises and sets, on and on until one day, when she's finally able to get up and move around a little, she hears a familiar voice: Varl, accompanied by Zo. He's finally found Aloy. And now it's time for Act 2 to begin.
#look i dig sylens and lance reddick's performance#but this is—and should be—the aloy show#aloy#elisabet sobeck#hfw#my headcanon
17 notes
·
View notes
Text
More than 120 low energy base telecoms stations that integrate solar and battery technology have been set up across rural Liberia to enhance network coverage.
The network offers 2G voice services for users in remote areas and supports 4G data services which is expected to connect more than 580,000 people.
Each site integrates solar energy and smart lithium batteries, enhanced with PowerPilot AI energy-saving software, to achieve energy-efficient network construction. Transmission challenges are addressed through the use of microwave, satellite and 4G relay technology.
The project – RuralPilot EcoSites – encompasses 128 communication sites and was completed in three months.
These sites employ low-power-consumption, wide-coverage wireless base station equipment supporting the 800MHz and 900MHz bands, according to ZTE Corporation, who partnered with Orange Liberia on the project.
#solarpunk#solar punk#community#informal economy#rural connectivity#telecommunications#africa#liberia#solar power
15 notes
·
View notes
Text
⋆˚✿˖ִ✩Tuesday snippet*ੈ★₊˚
thanks for the tag @veganbutterchicken
this is very early stages, but here's a little snippet of the story I'm writing for the @maraudersromcomfest
For a moment, all they hear is faint rustling, and the boy calling out for his father. The host fills the silence with a general announcement. “If you just tuned in, this is Dr. Rita Skeeter, and tonight’s topic…” The car in front of Sirius inches forward, and he absentmindedly lifts his foot off the brake, rolling ahead in the queue. Finally, a voice comes through the radio. “Hello, this is Remus.” His voice is deep and very, very weary, like he’s been carrying a heavy burden for a while. Curiously, Sirius sits up a little straighter in the driver’s seat, drinking up every word. “Hello, Remus. This is Dr. Rita Skeeter. You’re on the Wireless Network–” she begins, unflinching, as if she’s read the script a thousand times. “Okay, what are you selling tonight?” he cuts in immediately, sounding half-exasperated, half-amused. “Is it the micro hibachis or the ginza knives?” Sirius snorts at the sarcasm, unable to help himself. He likes this guy. He likes him a lot. Dr. Rita Skeeter, unshaken, presses on. “No, I’m not selling anything, sir. I just want to help you.” She tries to explain. “Your son called in. He asked me for some advice on how you might find someone new. You know… to date.” The silence that follows is thick. Sirius can practically hear the man’s brain grinding, trying to catch up to what’s going on. “Sorry… who’s this again?” He finally asks, slower now, as if he’s trying to process the absurdity of it all. “I’m Dr. Rita Skeeter, on the Wireless Network,” the host repeats, very slow this time, as if talking to a child. “And you are on the air with us. For the whole country.” “Wha– You called the radio station?” The man exclaims, clearly not directed at the phone. Sirius barks out another laugh, shaking his head. Oh, that poor kid. He’s so getting yelled at.
tagging: @goldenprophetwrites @quiethauntings and @leavesthatarebrown. Would love to see what you're working on!
17 notes
·
View notes
Text
Anywhere on Earth time
A few days ago I posted about a grant with a deadline at 11:59 pm of Anywhere on Earth time. Somebody asked me "is this for real"???
Very much yes!
Anywhere on Earth time was invented in 1999 by the Institute of Electrical and Electronics Engineers, who in that year established a working group to develop standards for broadband for wireless metropolitan area networks. The goal of this group was to make sure that the wireless internet connection meet the same criteria internationally. We are talking about wireless internet around cities, but also mobile internet. All this started being regulated after 1999. The working group started releasing these standards and introduced the "Anywhere on Earth" time to put into practise the standards for the whole world at the same moment.
So yes. Anywhere on Earth time is a real thing. It is used only for deadlines, and it corresponds to the time when the deadline date passes for every single place on Earth. In practise, the last place to change the date on Earth are Howland and Baker Islands on the western side of the international date line. So the Anywhere on Earth time corresponds to whatever time the Howland and Baker Islands have.
#fun facts#internet#history#tech#technology development#anywhere on earth#time zones#internet history#regulations#original content
11 notes
·
View notes