Text
Practical Malware Analysis A COMP6441 Something-Awesome project!
Turns out open learning blogs aren’t visible unless you have an account. Here’s a repost.
Summary
After 30+ hours of reading, write ups, research and analysis did I achieve what I set out to accomplish?
Final Assessment of Project
Part 1: Virtual Network Setup
How can we analyse malware safely and not infect our machine? The answer is to use a virtual machine that is separate from the host.
My lab contained a custom network; A service machine on Ubuntu, malware analysis machine on Windows XP and I decided to run IDA Pro on Windows 7. The service machine simulated network responses so I could study the malware's network indicators.
Notes
Virtual Environment Setup Custom Network w/ iNetSim
Part 2: Basic Static Analysis
Basic Static analysis consists of examining the executable file to collect information about its function and network signatures. Basic Static analysis is straightforward and quick but it is ineffective against sophisticated malware.
Notes
Lab 01-01 Lab 01-02 Lab 01-03
Part 3: Basic Dynamic Analysis
This stage involved running the malware, in order to observe its behavior.
Notes
Lab 02-01 Lab 02-02 Lab 02-03
Part 4: x86 Assembly Architecture
The necessary knowledge to perform advanced static analysis. This chapter was very content-heavy and as such the author did not include lab work. The concepts were put into practice in the next chapter.
Notes
Part 5: Advanced Static Analysis
Advanced static analysis consists of reverse engineering the malware's internals by loading the executable into a disassembler. The process can reveal the underlying functions of the malware. However, the technique has a very steep learning curve. This week focused on reverse-engineering a malware. Guidance was provided through questions.
Notes
Lab 05-01 Lab 05-02 Lab 05-03
Supplementary Research
The book was outdated in many sections and some concepts were breezed over. I often had to research myself.
What's a DLL?
What's the Registry?
0 notes
Text
What’s the Registry?
The registry is a very important indicator, that should be monitored, in malware analysis. Tools like Regshot and Process monitor can capture any chances to the registry.
The Windows Registry is used to store much of the information and settings for software programs, hardware devices , user preferences, operating system configurations, and much more. (LifeWire)
Registry values are contained within Registry keys. Everything is then in a registry hive. The registry hives are stored in %SystemRoot%\System32\Config\ folder in Recent Windows Operating systems. It may be useful to think of values as files and keys as folders. The hive is the main folders on the system.
0 notes
Text
What is a DLL?
A DLL is short for dynamically linked library. It is a type of file that contains code that other programs can use. This makes DLLs reusable and great for modulations of code. However, unlike exes that can be started simply by clicking them. DLLs may need be run with different methods. Dynamic libraries are linked at run-time.
From working on malware labs, DLLs can be forced to run similar to an exe. They are able to install services as well which could be malicious. Another method is to change the file header to force it run as an exe. However, in that case, the execution may be unstable and crash.
DLLs may be dependent upon other DLLs. I have used dependency walker in my labs to see how DLLs may be interconnected.
0 notes
Text
Final Assessment of Project
The Goal
The purpose of my project as defined in my proposal was:
To learn the skills necessary to reverse engineer and perform malware analysis
The Plan
To achieve that goal. I developed a plan that centered on studying “Practical Malware Analysis” and completing hands-on labs. Before this project, I didn’t have any experience in malware analysis.
What was achieved?
I can proudly say I succeeded in:
Setup and configuration of the virtual laboratory
Learning 5 chapters of content
Completing labs for each chapter
Blog extensively on the malware analysis I conducted
I had successively completed all the necessary components to achieve a distinction in my original criteria.
Obstacles
I faced several obstacles while completing my project
1. Proposal error
For my High Distinction criteria, I was ambitious and hoped to undertake a mock analysis of a malware of my choice. However, it seemed as I misunderstood the deadline.
I had thought we had until Week 10 to complete our Something Awesome. Within the 5 weeks. I had put in over 30 hours of work towards my Something Awesome Project. It was not feasible to force the HD mock analysis in. I had to let it go and revise my proposal.
2. Book design
While the introduction of the book stated that each chapter had about three labs. Once I begin completing exercises. It didn’t seem to be the case.
Chapter 2 involved the major setup of the virtual environment
Chapter 5 contained a lab that contained 21 questions!
I had to adjust my approach to the book design.
3. Age of the book
The book is old. Even thought it’s still the most commonly recommended book to malware analysis. It shows it’s age at places. I had to research for new software, installation methods and assumed knowledge. While I scattered some of that research into my lab blogs. I also had separate blogs for dedicated research on important topics.
Final Verdict
I couldn’t be more pleased with my project. It was many hours of work but I felt I I had learnt so much. I will continue this book even after the course is over. Furthermore, I’ll be presenting my Something Awesome Project to my class next week!
4 notes
·
View notes
Text
OWasp Top 10 Security Risks
Pick one of the OWASP Top 10, conduct some further research into the type of vulnerability, then come up with a way to explain the problem and solutions to the average high school student.
The OWASP security concern that I have decided to research is Injections.
Research
Injections can occur when user inputs are confused or sent as program arguments. This is often the case with database queries such as SQL. Today, we are more aware of risks involved and therefore we have developed methods of protection.
Injections are a very common vulnerability type. Especially in older machines when developers did not notice these risks. The impact often involves stealing data from a database. However, there are cases whereby hackers have gained access to entire systems.
Solutions and Explanation
I would definitely explain the situation using an analogy. I read Steve job’s biography a while back and him and Wozniak had created a way that used a tone to get free calls. I would link that to the idea of mixing control and user input.
I would show a snippet of code that shows how user input can be made to seem like it was programming code. After explaining the example and analogy. I would go through the solutions that can be undertaken.
1. Use prepare statement (with parameterized queries)
We use a parameter.I would explain what a function is to the student by suing another analogy. I’m a fan of the blender example whereby the fruits would be the parameters. So we use parameters as opposed to inserting values.
2. Validating user input
Even though we’re using parameterized queries we should still check the input was sane. For example if the input was the right type, length and format. Could link that with the type of fruit and ripeness.
3. Hiding Error Messages
Hackers and malicious attackers use error messages to inform them what the machine may be expecting.It’s much better to display a generic error message and force them to call for IT support or help. Or if that’s a headache then limit information given
1 note
·
View note
Text
SHA1 - Good bye
On 8 October 2015, Marc Stevens, Pierre Karpman, and Thomas Peyrin determined that it would cost agencies between $75k - $120k to generate a collision.
In 2017, Google and CWI Amsterdam announced they had successfully performed a collision attack on the 160 bit hash function. Generating two pdfs with the same hash. Major browser providers immediately started deprecation.For google to achieve this feat the had to compute nine Quintillion SHA-1 computations.
The progress towards cracking SHA1 had started since 2005. As researchers have found ways to reduce the amount of work needed.
On May 9, 2017, Microsoft Edge and Internet Explorer 11 will prevent sites that are protected with a SHA-1 certificate from loading and will display an invalid certificate warning. Additionally, the Windows 10 Creators Update blocks SHA-1 by-default in the browser. Customers who would like to disable SHA-1 today may do so with the instructions below.
Many broswers have heralded the change. It looks like we’re all moving ahead on to the SHA2 family now.
0 notes
Text
EL185 Passwords
Dear Grandma and Grandpa,
I’m writing to you to emphasis how important it’s to have strong passwords! Scammers and hackers are on the rise but don’t be worried. We can follow some simple rules to keep us safe. Once I come back to visit, I’ll check you have followed some of these tips.
1. Make a phrase that’s nonsensical
Something that’s memorable but doesn’t follow grammar or common conventions. Like for example, Smileyfallssmellsgreen.
2. It’s good to have a few numbers as well
It’ll make your password harder to guess by a hacker by having a mix of letters and numbers in your password
3. Long password are better
Four to five words joined together would be best. If it’s too short then there’s a chance people can work it out!
If you follow these rules then hackers could take centuries to brute force your password.I hope this will be useful to you. I’ve kept it short and simple so it’s easy to review and remember. I will be visiting over the winter break.
Looking forward to see you,
Roger
0 notes
Text
Human Weakness and Moral Hazards
The Challenger Disaster
Circumstances, pressures and influences that led to the outcome?
Pressures to appear in control of something that was not completely understood
Build trust towards the government
The O-ring flaw was known since 1977, its contractor Morton Thiokol, had not acted
Launch decision was flawed
Lack of checks and balances with in the management of NSA which proved to be fatal
Morton Thiokol Engineers stated their concerns about the o-rings and urged a delay but the concern was not raised
Conflict of management and engineering data
Feynman continued to investigate the lack of communication between NASA's management and its engineers, and was struck by management's claim that the risk of catastrophic malfunction on the shuttle was 1 in 105, i.e. 1 in 100,000 (Roger Commission)
The estimated figure was largely fantastical and depicted serious deficiencies in NSA management’s understanding
“Reality had taken precedence over public relations” - Feyman
Discuss how you might design changes and policies to prevent it from happening in the future.
1. Independent oversight team
Clearly management’s control over the project is insufficient. We must have an external body of engineers to review the safety of the project.
2. Restructuring of management
The management team was over swayed by political pressure and unrealistic deadlines. This impeded their judgement. It seems the issue has become systematic. Management must be reshuffled.
3. Critical Item Review
Independent audit panel that checks critical items before a flight. The team should perform a comprehensive finals review.
0 notes
Text
Hashbrowns and Macs
We are given three pre-made codes.

Knowing that PAYBOB100 is 481 we can add a 0 on by using length extension!
481 + 405 = 886
886 * 521 =461,606
mod 10,000 = 1606
1606 + 450 = 2056
2056 mod 967 = 122
With a quick look at the comments it seems as if I was right!
0 notes
Text
Security Everywhere
Food Joint safety
Local stores are common targets of robberies. The often have weaker security and may keep cash within the store. I’ve worked at a restaurant before and a major concern had been keeping the staff and assets safe.
Some security recommendations
I’ll list recommendation that could be undertaken:
1. Reinforced delivery doors/ Multiple doors
A common point of weakness occurs when suppliers drop deliveries. Attackers can compromise the restaurant once the reinforced back door is opened. A solution that could be implemented is to have two layers. Have a automatic garage door that allows the trucks to pull in and drop the supplies. The room leads to another reinforced door that gives entry into the restaurant.
2. Safes
Make it clear that large sums of cash is deposited into the safe whereby the code is unknown. It be a deterrent to criminals as they will earn very little for the risk that they take.
3. Surveillance
Have cameras installed within the store at every corner. To monitor both the staff from an insider attack and any forms of aggression by customers or outsiders. Surveillance like safes act mainly as a deterrent and may be used for evidence if an incident occurs.
4. Audits/ Responsibility
Have regular blind checks of registers and stock by management. Management should enter register counts in a “black box” system and edits should be limited. This will reduce the chance for stealing or stock manipulation by staff members. Deletion records should also be kept into account.
Team members should be responsible for their stations/money.
5.Exterior defense
Lock down doors and wiring can be used. To create a distance between the customers and workers. A common way of attack is the assailant just jumping the bench! It is important to have these precaution in place.
0 notes
Text
Lab 7 Snoop Debate
Somehow in class debates. I’m always assigned a position that conflicts with what I believe in.... I guess it forces me to look in from the other side.
Topic of Debate:
Should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
My team was assigned to be pro government surveillance. I understand that the government needs to collect some data - When you’re born, your citizenship and so on. It’s if they get too intrusive that’s when it gets dangerous.
Arguments for Pro-Government Surveillance
1. Governments can execute on their duty more efficiently
To keep us safe from terrorism or administer health programs to target diseases. The government needs data. The data needs to be plentiful and clean. If data is scarce and the government does not have the right to collect it. Then the decisions that are ultimately made may be misinformed.
2. The end justifies the means - the greater good
Sure, the NSA collects billions of gigabytes of data annually from its citizens. But if they successively prevent another terrorist attack or a mass shooting. Would it have been worth it? At times, we must consider, is our privacy more valuable than the lives of those who could be lost?
3. It is necessary
Governments have to collect data to keep foreign aggressors and criminals at bay. Without the government regulating the system with the data it collects. Criminals can commit illegal acts more freely and the checks will not be in place
4. If you’ve got nothing hide why does it matter?
A common argument by those who are anti-encryption.
Some rebuttals
1. We can’t trust the government with our data! What if a evil regime takes over?
We can mitigate those risks by enforcing the separation of power. Politicians shouldn’t have influence of the judiciary branch and the Intel services should be subject to the laws of the country. However, as the laws become more and more lax. The reach of agencies get stronger and more expansive.
2 . The Government may mishandle the data and because of incompetency put Australians at risk
While this is true of any organisation. The government agencies are often quite well fonded. Especially, if the government is large. It is likely that the government can keep data safer than regular businesses. Organisations such as the NSA or ASIO acquire substantial funding.
0 notes
Text
Security Everywhere
Often in security you have many assets that need to be protected. However, with finite resources, a security engineer may have to selective on what can be done. In doing so, they have to determine the most important things.
Let’s take UNSW Campus Security as an example. A while back, an attacker with a knife committed robberies on campus. What could UNSW do to protect it’s assets efficiently. Firstly, what are its assets?
UNSW’s Focus
Student’s well being
Infrastructure and Property
Strategies
Some strategies that could be implemented include:
1. Efficient incident broadcasts
Through the use of SMS alerts, UNSW email and microphone announcements. The university could precaution student about any dangerous developments. For example, if a fire was started at lower campus. Students could be notified to stay away from that area.
2. Quick response from major incident response teams
The team could include health & safety officers and campus security. The contact numbers of campus security should be well known by students. It could be engraved at the back of student cards. Help points could be set up around the university as well. If a major incident was to occur. The exposure to risk will be greatly reduced if response teams can narrow down on threats swiftly.

3. Trained personnel
When an emergency occurs, it is important to have trained personnel around the campus. Lecturers and UNSW staff, the person in charge, should be knowledgeable about protocols. This should include knowing evacuation diagrams, understanding lock down procedures and response actions. It is important the UNSW facilitates training for their staff.
0 notes
Text
Lab 6 Safer
Suppose we are thrust into a war with a superpower such as Russia. List what sorts of computer and internet related attacks might we suffer?
Pre-Lab Brian storm
Types of attacks that could be committed:
Denial of Service attacks
Man in the middle
IP spoof
phishing and spear attacks
Eavesdropping
Malware embedded into their system
Class Discussion
You are the Australian Signals Directorate. You have been asked to consider the main threats we face in the cyber domain of war, and to produce 10 recommendations for actions to be taken.
1. Allocate backup solutions for core infrastructures
A common target of attack is the power grid of a country. It’s important that Australia diversifies it’s electrical power sources. We recommend the use of renewables, Lithium ion batteries and coal. In the case of an attack we will have alternatives.
2. Compartmentalize intelligence
We can’t risk having a single point of failure. If a foreign power manages to take over an organisation it is important that they don’t have access to all data. This can include creating separate departments in charge of different responsibilities.
3. Counterintelligence and compete
Install malware into foreign agencies systems. The USA has inserted malware into both Iran (Stuxnet) and Russian infrastructures as a response to foreign aggression. For Iran it was to slow their nuclear capabilities and Russia as a response to election meddling.
The goal is to establish a deterrence and if other nations do commit acts of aggression they can be punished.
4. Share intelligence with Allies
Working with other nations to target common enemies could be useful. This can include Intel sharing and coordinated attacks. The issue is we must make sure we do not place our safety in the hands of another nation.
5. Cultivate talent
Good talent is difficult to come by. The government should encourage study in areas of demand and under supply. This can include joint ventures with university to train more graduates in security.
6. Work with companies to promote technological innovation
Government may provide incentives, such as tax credits, for research into security by companies. Using the bright minds of these organisations. The government can indirectly promote better security practices and solutions.
7. Establish national standards
Set standards that have to met for the use of equipment in government infrastructures. Diversify the governments suppliers of network equipment. It may mitigate the risk if a supplier has a backdoor or issue.
8. Identify insider threats
Besides initial background checks. Employees should be reviewed for mental well-being and contentment. Disgruntled employees should be addressed.
9. Promote good procedures through information events
How employees and everyday Australians can help maintain cyber hygiene. Setting strong passwords, not connecting to unknown network and so on.
10. Force all companies to have a backdoor haha...
Who better to entrust with our data than the government? They can analysis the data, group suspicious individuals and act on information.... I believe Cisco routers and Apple both had to have back doors for the US Government.
https://www.tomshardware.com/news/cisco-backdoor-hardcoded-accounts-software,37480.html
https://en.wikipedia.org/wiki/FBI%E2%80%93Apple_encryption_dispute
1 note
·
View note
Text
Lab 5 Giggle
Acting as either the government or a business are you in support of self driving cars on the road?
My group was assigned the role as a government minister. Not what I would have picked as I’m a fan of self-driving cars. The government has different concerns.
Assets of concern
Public transport
Labour and employment
Safety of citizens
How each concern is impacted
1. Public Transport System
Self-drivings fleets work better when there are more automated cars on the road. It often means that cars are subjected to less erratic behavior (human errors) and developers can more easily decide what a neighboring cars would do. New technology such as Vehicle to vehicle communication could also improve response time. In saying so, it is likely that the government will have to upgrade present vehicles if self-driving cars were supported.
This could mean the need for installation of new software, cameras or the purchase of new vehicles e.g. Buses. Selling this huge investment can be difficult to the non-believers. Just look at Australia today. A major fighting point of the last election was the Adani mines.
Giving green lights on self-driving could be a headache for the Transport department. Trial runs of self-drivings cars determined that roads in Sydney are so poorly maintained that at times the cameras couldn’t detect the road marks because of cracks.That looks like more road maintenance work to us...
2. Labour and Employment
If Uber and Lift create an fleet, state-run buses are automated and taxis become unprofitable. What would the unemployment number look like? Let’s take a look at Australia, where the average wage of a truck driver for Toll (source: Indeed) is $32.47/hour which is 15% above the median national wage. Suddenly, these well paid jobs are not in demand.
Are was going to have to open another “Transformation Scheme”? Pump millions into retraining the workforce. Or could we slow the process of automation and gradually train our work force to meet the demands of the 21st century.
3. Safety of Citizens
There’s nothing more important to us than then well-being of Australians! The cars are just too dangerous at the moment. The accidents with Tesla and Uber demonstrate to us that the technology is still in its preliminary stages. Once the technology catches up and we deem it safe. Then we can think about rapid expansion.
Government Verdict: NO
0 notes
Text
Lab 4 Secret
Mission
You have been assigned the task to design the physical security of a new UNSW research lab. Decide on what must be protected and list three key features of your design.
Assets to be protected
Physical research equipment
Intellectual property - methods, processes, research papers
Data storage - digital devices, hard disks
Network
Who are we defending form?
Outsiders
Theft, competitors, loiters
Insiders
Moles, negligence, disgruntled employees
Three Key Features of the design
1. Perimeter defense
A solid outer shell that prevents malicious threats from getting close to the company’s valuable assets.
Screening through x-rays, guards, fencing, authentication, tinted windows and/or bio metrics
Location choice should be secluded or at least out of sight, thereby removing reasons for loiters to be around
Intrusion detection devices if the facility is broken into
2. Insider Attacks
What if we have a disgruntled employee? An individual who is willing to sell company secrets to the highest bidder? How can we mitigate those threats?
Clearance into classified areas, employees should be assigned access levels, IT support should not have access to physical research documents and company secrets. Know what you need to know
Employee contracts that prevents past employees to divulge secrets to other future employers
Cameras and surveillance in sensitive areas
Information stays within the Lab, confidential research documents are not to removed from the premise
Good practice procedures, an account is never leaved on, documents stay in the office etc
3. Network
use an offline network that is air-gaped
BYOD are not allowed, if they are connected then they must be taken away
Points of connection on devices may be removed or blocked, such as USB connectors or other inputs
0 notes
Text
Advanced Static Analysis #3
The third part of the Lab from Chapter 5
15. At 0x10001701 is a call to socket. What are the three parameters?
I jumped to the wrong section 10001071... and spent an hour analyzing something difficult.
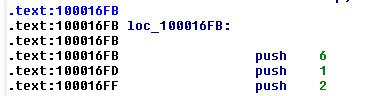
16. Using the MSDN page for socket and the named symbolic constants functionality in IDA Pro, can you make the parameters more meaningful?What are the parameters after you apply changes?
I’m going to have to add a plugin for this exercise. I think I’ll need IDA Pro as well. The answer was: These arguments correspond to three symbolic constants: IPPROTO_TCP, SOCK_STREAM, and AF_INET.
17. Search for usage of the in instruction (opcode 0xED). This instruction is used with a magic string VMXh to perform VMware detection. Is that in use in this malware? Using the cross-references to the function that executes the in instruction, is there further evidence of VMware detection?
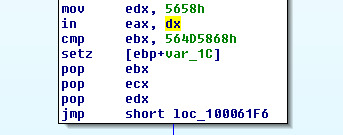
Had to search for a sequence of bits: “ED”
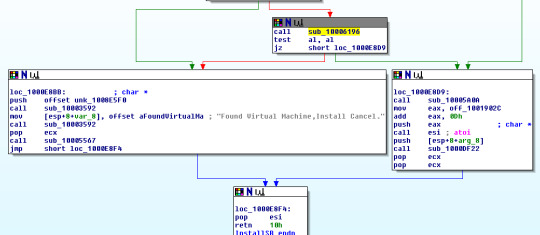
Using cross reference on the function that called in. We can see the virtual machine check happens again. If the malware finds it is in a VM. Then it will stop installing.
18. Jump your cursor to 0x1001D988. What do you find?

Doesn’t seem to mean much. It’s just random data.
19. If you have the IDA Python plug-in installed (included with the commercial version of IDA Pro), run Lab05-01.py, an IDA Pro Python script
provided with the malware for this book. (Make sure the cursor is at
0x1001D988.) What happens after you run the script?
20. H With the cursor in the same location, how do you turn this data into a
single ASCII string?
21. Open the script with a text editor. How does it work?
I don’t think plugins work with IDA Freeware. I might have to let these excerises go. I’ve read up on what each of the questions lead to. Seem to be focused on using features, by pressing a key, from the plugin. I’ll try to get IDA Pro soon. I want to play around with it more.
Reflections
Finally! I’ve completed the IDA Pro exercises. The final 7 questions seemed to be focused on using plugins which was unfortunate since I’m using the freeware. It was tedious at times .Grinding through functions and assembly trying to work out what’s going on. The work seemed to have paid off as I feel I’ve gotten more familiar with the assortment of tools offered by IDA. I’ll try to get my hands on IDA Pro in the future.
0 notes
Text
Basic Dynamic Analysis Lab #3
Lab 3 - 03 contains ab exe file
Programs used:
Strings
Process Explorer
Process Monitor
Questions from the Lab
1. What do you notice when monitoring this malware with Process
Explorer?
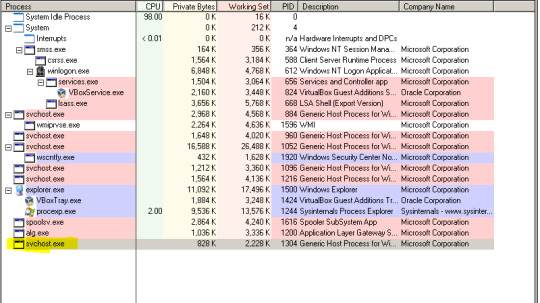
It starts a new svchost.eve. Just freshen my memory.
Microsoft wanted to change from relying on internal Windows services (which ran from EXE files) to using DLL files instead. From a programming perspective, this makes code more reusable and arguably easier to keep up to date. The problem is that you can’t launch a DLL file directly from Windows the same way you can an executable file. Instead, a shell that is loaded from a executable file is used to host these DLL services. And so the Service Host process (svchost.exe) was born.
-How to Geek
2. Can you identify any live memory modifications?
Looking into strings there’s a lot of interesting information and the malware seems to mess around with the heap. The heap is the area of which we can allocate with malloc and calloc.
Well... I got fooled. Process explorer has a verify button that checks if a exe has the correct digital signature. It turns out it checks the file on the disk as opposed to the memory.
What we can do is to check the svchost.exe of another program which we can trust and see if the strings have been changed.

It looks like the strings have been changed significantly in memory. There’s a string to practicalmalwareanalysis.log.
3. What are the malware’s host-based indicators?
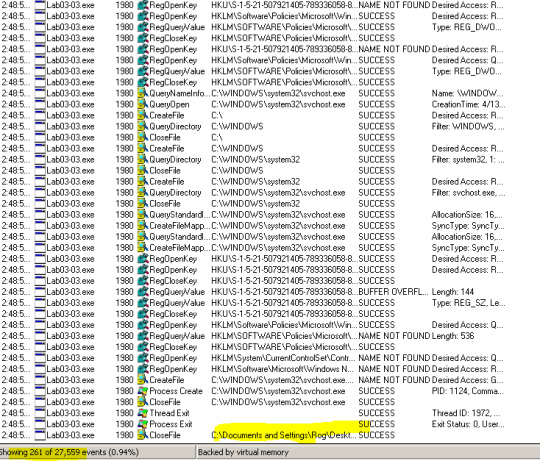
Right in the folder that I ran the malware... A document came up.
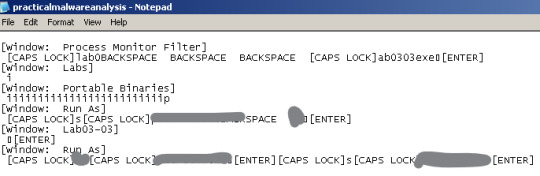
It’s logging the window that I have opened and what ever I type.
4. What is the purpose of this program?
The program seems to be a key logger that saves user inputs into a file. There’s the creation of practicalmalwareanalysis.log but I can’t tell if it uses the network.
Reflection
Once the svchost.exe became an orphaned process. It should have become immediately very suspicious. Overall, I managed to follow what was expected of the lab. I used the correct tools and came to the same conclusion.
0 notes