#4g vpn router
Text
BLIIoT Industrial 4G Modbus to MQTT Edge WiFi Router R10A Applied to River Liquid Level and Flow Monitoring
The R10A can provide wireless access network, and also can performs Modbus Master to poll meters over RS485/232 or LAN ports, then upload the data to cloud platforms under MQTT format, e.g.: AWS IoT, Thingsboard, Aliyun, etc. Also, can customerize applications, use the RS485 or LAN port to connect the I/O modules, to monitoring data or switch on/off devices, etc.



#iot#iotsolutions#iotdevices#gateway#router#modbus#mqtt#4g#ethernet#wifi#edgecomputing#vpn#logiccontrol#remotemonitoring#BLIIoT#BLIIoT Applications
1 note
·
View note
Text
For 5G and Wi-Fi router solutions, MediaTek and Invendis collaborated
In order to provide 5G and Wi-Fi router solutions, chipmaker MediaTek and a global pioneer in IoT platforms and cloud computing solutions, formed a strategic partnership on Sunday.
The partnership will allow India to develop a wide range of solutions and important industrial capabilities.
Satish Kulkarni, CEO of Invendis, stated in a statement, “We are happy to unveil our 5G and Wi-Fi routers which will allow consumers and corporate clients to deliver safe, powerful and smooth wireless networking solutions.
Kulkarni continued, “We are convinced that this collaboration would promote innovation, hasten the implementation of 5G goods and services in India, and assist users in taking advantage of the opportunities presented by very fast and dependable connection.
The new “Silboa product line” expands Invendis’ range of industrial and commercial communication solutions by adding 4G/5G routers that support Wi-Fi 4/5/6 standards as well as multi-WAN, VPN, SD WAN, NMS, and other business-specific functions.
MediaTek’s Networking and Connectivity products are included in the product line, including the MediaTek MT7628K/N/A Router and Repeater Platform, the MediaTek MT7621A/N Dual-core Network Processor for 2×2/3×3/4×4 Wi-Fi platforms, and the MediaTek MT7915 Wi-Fi 6 Wave 1+ chipset builds, among others.
Anku Jain, Managing Director of MediaTek India, stated that “MediaTek’s whole spectrum of Networking and Connectivity solutions is geared to satisfy changing client requirements whether it residential, commercial, or corporate applications.”
Earlier, on 1st October 2022, PM Modi introduces 5G services and claims it is the start of an endless sky of possibilities.
5G is the fifth-generation technological standard for broadband cellular networks in telecommunications. It is the anticipated replacement for the 4G networks that connect the majority of modern smartphones, and cellular phone operators started rolling it out globally in 2019.
Source links – MediaTek and Invendis collaborated For 5G and Wi-Fi router solutions
3 notes
·
View notes
Text

Resilient for Demanding Industrial Settings
Engineered to withstand demanding conditions, SR500 4g industrial router routers feature:
- Rugged enclosures to resist vibration, shock and extreme temperatures from -40°C to 75°C
- IP30 rating to prevent dust and moisture ingress
- DIN rail or desktop mounting for secure installation
- Redundant cellular and WiFi prevents downtime from network outages
Powerful Cellular and WiFi Connectivity
The SR500 line supports:
- 4G LTE CAT4 providing up to 150Mbps down/50Mbps up for high-bandwidth applications
- Optional 1.8GHz private LTE with 1000m range for campus and industrial park coverage
- 802.11b/g/n WiFi with internal or external antennas for local wireless access
This enables combining long-range cellular and short-range WiFi in one router.
Advanced Networking Features

SR500 routers provide:
- 2 x 10/100Mbps Ethernet ports for wired connectivity
- Extensive VPN protocols like IPsec, OpenVPN, GRE for secure remote communications
- SD-WAN capabilities to optimize performance across multiple links
- TR-069 and SNMP management for auto-configuration and monitoring
Tailored for Industrial IoT Projects
Typical applications include:
- Connecting PLCs, RTUs, sensors, meters and other assets to cloud platforms
- Enabling public WiFi and smart city services like traffic control and surveillance
- First responder networks with cellular and failover WiFi
- Deploying SD-WAN to combine multiple network links
- Adding cellular connectivity to sites without wired internet access
Customizable Linux Platform
The SR500 runs OpenWrt Linux allowing full customization. Development guides help tailor routers to specific use cases.
Centralized Management for Scalability
Star Device Manager (Star Cloud) enables managing entire networks of routers for simplified provisioning and monitoring. With industrial-grade reliability, the SR500 series provides connectivity assurance for critical industrial IoT.
1 note
·
View note
Text
ASUS Releases Powerful ZenWiFi BQ16 Pro & ZenWiFi BT10

ZenWiFi BQ16 Pro
The premium WiFi 7 mesh systems ZenWiFi BQ16 Pro and ZenWiFi BT10, which include strong 6 GHz WiFi and 2-pack variants with speeds of up to 30 Gbps (BQ16 Pro) and coverage of up to 8,000 square feet (2-pack BQ16 Pro), are now available, according to ASUS. Future-ready 10 Gbps Internet and 10 Gbps wired backhaul are made possible by the dual 10 Gbps Ethernet connections, which also provide fast, dependable, seamless whole-house WiFi for next-generation smart home entertainment and home studio work.
ASUS ZenWiFi BQ16 Pro
In order to effectively utilise WiFi 7 Multi-Link Operation (MLO) and AI for both fronthaul and backhaul, the ZenWiFi BQ16 Pro and ZenWiFi BT10 feature exclusive ASUS Smart AiMesh technology. Multi-Link Operation automatically aggregates or switches across multiple bands for reduced latency and efficient transmission.
Using MLO, the Smart AiMesh MLO fronthaul and backhaul automatically switch to the fastest band and intelligently prioritise packets that are demanding in order to maximise efficiency and connectivity. In addition, Smart AiMesh offers complete interoperability with all ASUS AiMesh-compatible ZenWiFi and standalone routers, enabling a plethora of sophisticated network features like parental controls, VPNs, and security in the expandable network.
By utilising two 6 GHz bands, the ZenWiFi BQ16 Pro fully utilises WiFi 7, enabling dedicated 6 GHz wireless backhaul to fully realise WiFi 7. The ZenWiFi BT10, which has a dedicated wired backhaul, is the perfect mesh solution for smart homes with wired Ethernet. For those looking for a basic standalone router without external antennas, a single unit can provide 4,000 square feet (BQ16 Pro) and 3,000 square feet (BT10). These premium mesh routers offer ultra-wide coverage up to 8,000 square feet (BQ16 Pro) and 6,000 square feet (BT10) for a 2-pack set.Image credit to ASUS
ZenWiFi BT10
Excellent dual 10 Gbps Ethernet connections are a characteristic of both the ZenWiFi BT10 and BQ16 Pro. This design is future-ready for cutting-edge 10 Gbps Internet and allows 10 Gbps wired backhaul for a stable, scalable 10 Gbps mesh network. In addition to instantaneous 4G LTE and 5G mobile tethering, which guarantee that smart homes stay online even in the event of a network failure, ZenWiFi BQ16 Pro and ZenWiFi BT10 employ several WAN designs, including a practical USB 3.0 WAN.
These mesh routers are equipped with next-generation WiFi chipsets, RAM, and potent quad-core 2.6 GHz (BQ16 Pro) or 2.0 GHz (BT10) CPUs, making them capable of handling even the most demanding scenarios at next-generation high-speeds. The inbuilt antennae and high-power front-end modules of the ZenWiFi BQ16 Pro and ZenWiFi BT10, backed by ASUS’s renowned engineering, eliminate WiFi dead zones for reliable coverage in all directions. Reliable and silent operation is also preserved by effective heat dissipation.
End-to-end smart home safety that is always secure
The ZenWiFi BT10 and BQ16 Pro network security suite was also unveiled by ASUS. With the help of ASUS-only technologies, Trend Micro’s AI/ML cloud database and AiProtection Pro, together with other commercial-grade security features, make sure smart homes are safe from the internet to the router to every connected device. Security scans, automatic security upgrades, and real-time alerts make robust router protection easy.
Furthermore, customers can establish sophisticated subnetworks with up to three SSIDs using the powerful and user-friendly Smart Home Master. The IoT Network provides better security with commercial-grade protection by configuring and managing all these IoT devices under a single protected SSID. To help kids simply monitor their screen time without having to configure each device individually, The Kid’s Network provides a special SSID exclusively for them.
Without the need for monthly subscriptions, users can give their children a balanced digital life with the help of built-in sophisticated parental controls. With an easy-to-use dashboard and highly customisable features like age-level profiles and the ability to schedule internet access to give your kids more screen time, ASUS parental controls give parents insightful information about their child’s online activities. Not to mention, the VPN Network offers quicker access to the user’s chosen VPN provider.
With their extensive VPN capabilities and support for multiple VPN protocols, including the state-of-the-art WireGuard, ZenWiFi BQ16 Pro and ZenWiFi BT10 offer superior privacy over encrypted connections.
ASUS ZenWiFi BQ16 Pro release date
ASUS ZenWiFi BQ16 Pro was introduced on July , 2024, and is now available. This high-end WiFi 7 mesh system improves your home network with fast speeds, wide coverage, and many functions.
ASUS ZenWiFi BQ16 Pro price
The ASUS ZenWiFi BQ16 Pro comes in 2-pack and 3-pack variants, with a single unit coming soon. A breakdown of prices:
The most popular option is the 2-pack (BQ16 Pro(W-2-PK)) for $1299.99. Street prices may vary. Find it on Amazon.
The Best Buy-exclusive 3-pack (ZenWiFi BE33000) costs $1699.99.
In a few months, a single ZenWiFi BQ16 Pro will cost $699.99.
This is a high-end Wi-Fi 7 mesh system, thus its pricing reflects its power. Some vendors, including B&H Photo, provide financing for a single unit at $59 per month for 12 months.
Read more on Govindhtech.com
#ZenWiFiBQ16Pro#multilinkoperation#ZenWiFiB10#5gmobile#CPUs#CloudDatabase#IoTnetwork#vpnnetwork#WiFi7#news#technews#technology#technologynews#technologytrends#govindhtech
0 notes
Text
ASUS anuncia el router de viaje trimodal RT-AX57 Go
Conectividad trimodal para viajes, trabajo y hogar con anclaje a red móvil 4G y 5G así @MXASUS anuncia el router de viaje trimodal RT-AX57 Go con un punto de acceso privado a través de WiFi público (modo WISP) y modo router.
ASUS anunció el router de viaje trimodal RT-AX57 Go, un modelo de doble banda que ofrece WiFi 6 ultrarrápido de hasta 3000 Mbps. Proporciona conectividad trimodal para viajes, trabajo y hogar, incluido anclaje a red móvil 4G y 5G, modo WiFi público (WISP), modo router, seguridad sin suscripción y múltiples funciones de VPN. Con soporte para canales WiFi de 160 MHz, RT-AX57 Go también puede…

View On WordPress
0 notes
Text
The Definitive Handbook of Industrial Cellular Routers for Dependable Internet Access
In the era of the Industrial Internet of Things (IIoT), data management and smooth operations depend on strong and dependable connectivity. The industrial cellular router is one important piece of technology that makes this communication possible. Modern industrial facilities have high standards, and high-performance industrial cellular routers satisfy those demands while providing excellent performance for a range of applications.
An Industrial Cellular Router: What Is It?
An industrial cellular router is a networking device that uses cellular networks to connect industrial systems and machinery to the internet. Industrial cellular routers are perfect for difficult and isolated areas since, unlike consumer-grade routers, they are made to endure tough environments like high temperatures, dust, and vibrations.
The Advantages of Industrial Cellular Routers: dependable connectivity
Industrial cellular routers provide dependable and consistent connectivity, which is essential for controlling and monitoring industrial processes in real time. They enable dependable internet access using cellular networks, even in isolated areas with inadequate wired infrastructure.
Increased Safety
When it comes to industrial settings, security is crucial. Advanced security capabilities, such as firewall defense, VPN support, and encryption, are built into industrial cellular routers to secure your data from online attacks.
Distant Supervisory
Because these routers support remote management, professionals can keep an eye on and diagnose network problems without having to physically visit the location. This feature guarantees optimal network performance while cutting downtime and maintenance expenses.
Scalability and Flexibility
With industrial cellular routers, you can scale and modify your network to meet changing operating requirements. These routers enable scalable solutions that develop with your company, whether it's through branching out to new areas or adding more devices.
Robust Design
Rugged enclosures and components made to withstand severe industrial settings are features of industrial cellular routers that are built to withstand extreme environmental conditions. Long-term performance is guaranteed by this durability, which also lowers the need for frequent hardware changes.
Important Criteria for Industrial Cellular Router Selection
Take into account the following crucial elements while choosing an industrial cellular router:
- Dual SIM Support: This feature alternates between two distinct cellular networks to provide constant connectivity.
- High-Speed Connectivity: Provides dependable and quick data transfer by supporting the newest cellular technologies, including 4G LTE and 5G.
- Advanced Security Protocols: These safeguard sensitive data with features like firewalls, VPNs, and encryption.
- Remote Management Tools: Offers the ability to monitor, configure, and troubleshoot remotely.
- Rugged Construction: Made to resist harsh vibrations, dampness, temperatures, and dust.
Industrial Cellular Router Applications
Industrial cellular routers are adaptable devices with a wide range of uses, such as:
-Remote Monitoring and Control: Allowing industrial equipment in remote places to be monitored and controlled in real time.
- Transportation and Logistics: Offering dependable connectivity for applications related to mobile workforce, asset tracking, and fleet management.
- Energy and Utilities: Maintaining steady communication to oversee and manage the infrastructure for energy generation, distribution, and utilities.
- Smart Cities: Enabling connection for public safety, environmental monitoring, and traffic management applications, among others.
In summary
Your industrial operations' productivity and connection can be greatly improved by making an investment in an industrial cellular router. These routers assist modern industrial automation and the IIoT by offering dependable, secure, and scalable network solutions. Speak with specialists to determine the ideal option for your unique requirements if you'd want more information about how industrial cellular routers might improve your operations.
0 notes
Text
does the vpn on my phn cover my wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does the vpn on my phn cover my wifi
Mobile VPN coverage
Title: Maximizing Mobile VPN Coverage: Ensuring Seamless Security Everywhere
In today's interconnected world, where mobile devices have become indispensable tools for both personal and professional use, ensuring privacy and security while on the go is paramount. This is where Mobile VPN (Virtual Private Network) coverage plays a crucial role.
Mobile VPN coverage refers to the extent to which a VPN service provider offers reliable and comprehensive protection across various mobile networks and geographic locations. It enables users to establish secure connections to the internet through encrypted tunnels, regardless of their physical location or the network they are connected to.
One of the primary benefits of using a mobile VPN is the protection it provides against potential threats such as hackers, identity thieves, and data breaches. By encrypting data transmitted between the user's device and the internet, a VPN prevents unauthorized access to sensitive information, safeguarding users' privacy and ensuring the confidentiality of their online activities.
Furthermore, mobile VPN coverage extends beyond just security concerns. It also enables users to bypass geographical restrictions and access content that may be blocked or censored in their location. Whether it's streaming services, social media platforms, or news websites, a VPN allows users to enjoy unrestricted access to the internet, regardless of where they are.
When choosing a mobile VPN provider, it's essential to consider the extent of their coverage. Ideally, the provider should offer servers in multiple locations worldwide, ensuring reliable access to their services regardless of the user's geographical location. Additionally, the provider should support a wide range of mobile networks, including 4G, 5G, Wi-Fi, and others, to ensure seamless connectivity across different environments.
In conclusion, mobile VPN coverage is crucial for ensuring privacy, security, and unrestricted access to the internet on mobile devices. By choosing a reputable VPN provider with extensive coverage, users can enjoy peace of mind knowing that their online activities are protected wherever they go.
WiFi protection
WiFi protection is essential in the modern age as more and more devices in our daily lives are connected to the internet. Protecting your WiFi network can help safeguard your personal information and prevent unauthorized users from accessing your network.
One of the first steps to protecting your WiFi network is to ensure that you have a strong password. A strong password should be at least 12 characters long and include a mix of letters, numbers, and special characters. Avoid using easily guessable passwords such as "password" or "123456" as they can make your network vulnerable to hacking.
Another important measure to protect your WiFi network is to enable encryption. Encryption scrambles the data transmitted between your device and the WiFi router, making it unreadable to anyone trying to intercept it. The most common encryption protocols are WPA2 and WPA3, which offer a high level of security for your network.
It is also recommended to hide your WiFi network name, also known as the SSID (Service Set Identifier). By hiding the SSID, you make it harder for unauthorized users to discover and connect to your network. Additionally, regularly updating your router's firmware can help patch any security vulnerabilities and ensure that your network is protected against the latest threats.
By following these tips and implementing robust security measures, you can significantly enhance the protection of your WiFi network and enjoy a safe and secure online experience.
Device VPN functionality
A Virtual Private Network (VPN) is a valuable tool that enhances privacy and security while using the internet. By encrypting your internet connection, a VPN creates a secure and private tunnel between your device and the internet, preventing third parties from intercepting your data.
One of the main functionalities of a VPN on a device is to mask your IP address. Your IP address reveals your location and can be used to track your online activities. With a VPN, your real IP address is hidden and replaced with the IP address of the VPN server you are connected to, providing you with anonymity and increasing your online privacy.
Moreover, a VPN allows you to bypass geo-restrictions and access content that may be blocked in your region. By connecting to a server in a different country, you can access region-locked websites, streaming services, and other online content that would otherwise be unavailable to you.
Another essential functionality of a device VPN is its ability to encrypt your internet traffic, safeguarding your data from hackers and cybercriminals. This encryption ensures that your personal information, such as passwords, financial details, and browsing history, remains secure and inaccessible to unauthorized individuals.
Overall, the functionality of a VPN on a device is crucial for protecting your online privacy, accessing restricted content, and securing your sensitive data from potential threats. Whether you are browsing the web, streaming content, or conducting online transactions, using a VPN can significantly enhance your digital security and peace of mind.
Network security
Network security is a critical aspect of the digital world, ensuring the protection of data and systems from potential cyber threats. It encompasses various measures and technologies that work together to safeguard the confidentiality, integrity, and availability of information shared over networks.
One fundamental component of network security is firewalls, which act as barriers between trusted internal networks and untrusted external networks, monitoring and controlling incoming and outgoing network traffic. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are also vital tools in network security, detecting and responding to malicious activities and potential threats in real-time.
Encryption plays a significant role in securing data as it converts sensitive information into unreadable code, making it inaccessible to unauthorized users. Virtual Private Networks (VPNs) establish secure connections over public networks, allowing users to transmit data securely and anonymously.
Regular security audits and vulnerability assessments are essential for identifying and addressing potential weaknesses in network systems. Maintaining up-to-date security patches and protocols is crucial to mitigate risks and prevent security breaches.
Network security is an ongoing process that requires continuous monitoring, updating, and enhancement to adapt to evolving cybersecurity threats. By implementing robust security measures and staying vigilant, organizations can strengthen their network security posture and safeguard their digital assets from potential cyberattacks.
Wireless data encryption
Wireless data encryption is a crucial technology that ensures data security in wireless communication. It involves the process of converting plaintext data into an unreadable format, known as ciphertext, to prevent unauthorized access. By utilizing encryption protocols and algorithms, wireless data encryption protects sensitive information from interception and hacking attempts.
With the increasing reliance on wireless networks and the prevalence of cyber threats, the implementation of robust encryption measures is essential to safeguard data transmission. Encryption protocols such as WPA2 (Wi-Fi Protected Access 2) and WPA3 set the standard for secure wireless communication by encrypting data packets and establishing secure connections between devices.
One of the primary advantages of wireless data encryption is its ability to provide confidentiality and privacy. By encrypting data at the source and decrypting it at the destination using cryptographic keys, sensitive information remains secure during transit. This is particularly important for industries handling sensitive data such as healthcare, finance, and government agencies.
Furthermore, wireless data encryption also helps prevent data tampering and unauthorized access. In the event of a security breach, encrypted data is virtually impossible to decipher without the proper decryption keys, adding an extra layer of protection against cyber attacks.
In conclusion, wireless data encryption is a fundamental component of securing wireless communication. By implementing encryption protocols and algorithms, organizations can mitigate the risk of data breaches and protect sensitive information from unauthorized access. As technology continues to advance, the importance of robust encryption measures in wireless networks cannot be overstated.
0 notes
Text
does vpn work over cellular data
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work over cellular data
VPN cellular network compatibility
Title: Understanding VPN Cellular Network Compatibility: Ensuring Secure Connectivity on the Go
In today's interconnected world, the need for secure and reliable connectivity is paramount, especially when accessing the internet over cellular networks. Virtual Private Networks (VPNs) offer a solution by encrypting data and providing a secure connection, but ensuring compatibility with cellular networks is crucial for seamless functionality.
VPN compatibility with cellular networks depends on several factors, including the VPN protocol and the type of cellular network being used. The most common VPN protocols, such as OpenVPN, IKEv2/IPsec, and L2TP/IPsec, are generally compatible with most cellular networks, including 3G, 4G, and 5G.
However, some cellular networks, particularly in regions with restrictive internet policies, may block VPN usage or throttle VPN connections, limiting their effectiveness. In such cases, users may need to utilize specialized VPN protocols or obfuscation techniques to bypass restrictions and maintain a secure connection.
Furthermore, the type of device and its operating system can also affect VPN compatibility. While most modern smartphones and tablets support VPN connectivity out of the box, older devices or those running outdated operating systems may encounter compatibility issues.
To ensure VPN cellular network compatibility, users should:
Choose a reputable VPN provider that offers dedicated apps for mobile devices and supports a wide range of VPN protocols.
Keep their devices and VPN apps updated to the latest versions to benefit from security enhancements and bug fixes.
Test the VPN connection on different cellular networks and locations to identify any potential compatibility issues.
Consider using VPN routers or portable hotspot devices that support VPN connectivity for seamless integration with cellular networks.
By prioritizing VPN cellular network compatibility, users can enjoy secure and private internet access on the go, regardless of the network they're connected to.
Cellular data VPN performance
When it comes to ensuring privacy and security on mobile devices, using a Virtual Private Network (VPN) is a popular choice for many users. A VPN encrypts internet traffic, making it more secure and private. However, when using a VPN on a mobile device, especially when using cellular data, performance can be a concern for users.
The performance of a VPN on cellular data can be influenced by various factors. One of the key factors that can impact VPN performance on mobile devices is the speed and stability of the cellular network itself. A strong and stable cellular connection is essential for ensuring a smooth VPN experience.
Additionally, the VPN provider and the server locations can also play a significant role in determining the performance of a VPN on cellular data. Choosing a reliable VPN provider with servers strategically located can help improve performance and speed when using cellular data.
It is also important to consider the type of encryption used by the VPN provider. While strong encryption is crucial for security, it can also impact the speed and performance of the VPN connection, especially on mobile devices with limited processing power.
Overall, utilizing a VPN on cellular data can provide an extra layer of security and privacy for mobile users. By considering factors such as network stability, VPN provider, server locations, and encryption methods, users can optimize the performance of their VPN on cellular data and enjoy a safer browsing experience on the go.
VPN connectivity on mobile networks
Title: Maximizing VPN Connectivity on Mobile Networks: Tips and Best Practices
In an age where mobile devices have become indispensable tools for both personal and professional use, ensuring secure and reliable connectivity is paramount. Virtual Private Networks (VPNs) offer a layer of security and privacy, encrypting data transmissions and shielding users from potential cyber threats. However, maintaining VPN connectivity on mobile networks can sometimes be challenging due to various factors such as network congestion, signal strength, and configuration issues. Here are some tips to optimize VPN performance on mobile networks:
Choose the Right VPN Protocol: Different VPN protocols offer varying levels of security, speed, and compatibility. For mobile devices, lightweight protocols like IKEv2 or OpenVPN are often preferred due to their efficient performance on limited bandwidth.
Select Reliable VPN Providers: Opt for reputable VPN service providers that offer dedicated mobile apps with robust features and regular updates. Look for providers with a large server network to ensure reliable connection options.
Optimize Network Settings: Adjust your mobile device's network settings to prioritize VPN traffic. Disable battery-saving modes or low-power settings that may interrupt VPN connections or limit data transmission.
Stable Internet Connection: Ensure a stable internet connection by connecting to a reliable Wi-Fi network whenever possible. While mobile data is convenient, Wi-Fi often provides better speed and stability for VPN connections.
Update VPN Software: Keep your VPN app and mobile device's operating system up to date to benefit from the latest security patches and performance enhancements.
Test Different Server Locations: Experiment with connecting to different VPN server locations to find the one that offers the best performance. Servers closer to your physical location typically provide faster speeds.
Limit Background Apps: Close unnecessary background apps and processes that may consume bandwidth and interfere with VPN performance.
By following these tips and best practices, users can maximize VPN connectivity on mobile networks, ensuring secure and seamless access to online resources while on the go. Remember to prioritize security and privacy when selecting VPN services and regularly assess and adjust settings for optimal performance.
VPN effectiveness over cellular data
Virtual Private Networks (VPNs) are powerful tools that enhance online privacy and security by encrypting internet traffic and masking IP addresses. While VPNs are commonly associated with protecting data on Wi-Fi networks, their effectiveness over cellular data should not be underestimated.
When connecting to the internet through cellular data, users are still vulnerable to various online threats such as hackers, data breaches, and surveillance. By using a VPN over cellular data, users can establish a secure and encrypted connection to a remote server, thereby safeguarding their online activities from prying eyes.
One of the primary benefits of using a VPN over cellular data is the encryption of data transmissions. This encryption scrambles the data being sent and received, making it unreadable to anyone trying to intercept it. As a result, sensitive information such as passwords, financial details, and personal messages are protected from potential cyber attacks.
Moreover, VPNs can help circumvent geo-restrictions and censorship imposed by governments or internet service providers. By routing internet traffic through servers located in different regions, users can access content and websites that may be blocked or restricted in their current location.
However, it is essential to choose a reputable VPN service provider that does not log user activity or compromise data privacy. Additionally, users should be aware that using a VPN over cellular data may result in slower connection speeds due to the encryption process and the distance to the VPN server.
In conclusion, utilizing a VPN over cellular data is a wise decision to enhance online security and privacy. By encrypting data transmissions and bypassing restrictions, VPNs offer an added layer of protection in an increasingly interconnected digital world.
Mobile data encryption with VPN
Mobile data encryption with VPN
In the digital age we live in, the security of our data is of utmost importance. With the increasing reliance on mobile devices for everyday tasks, ensuring the privacy and security of our data has become a critical concern. One of the most effective ways to protect mobile data is through encryption with a Virtual Private Network (VPN).
A VPN works by creating a secure and encrypted connection between the user's device and the internet. When using a VPN on a mobile device, all data that is transmitted through the network is encrypted, making it nearly impossible for hackers or cybercriminals to intercept and decipher the information. This means that sensitive information such as passwords, financial details, and personal messages are safeguarded from prying eyes.
Mobile data encryption with VPN not only protects the data being transmitted from the device but also ensures privacy and anonymity online. By masking the user's IP address and encrypting their internet traffic, a VPN allows users to browse the web anonymously and securely, without the fear of being tracked or monitored.
Moreover, using a VPN on a mobile device is particularly important when connecting to public Wi-Fi networks. Public Wi-Fi hotspots are notorious for being vulnerable to cyber attacks, as hackers can easily intercept data being transmitted over these networks. By using a VPN, all data sent and received while connected to public Wi-Fi is encrypted, significantly reducing the risk of data breaches and unauthorized access to personal information.
In conclusion, mobile data encryption with VPN is a powerful tool for enhancing data security and privacy on mobile devices. By encrypting all data transmissions and providing anonymity online, a VPN offers peace of mind and protection against potential cyber threats in our increasingly connected world.
0 notes
Text
can use usb with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can use usb with vpn
USB compatibility with VPN routers
USB compatibility with VPN routers is an essential consideration for users looking to maximize their network security and connectivity options. Many modern VPN routers come equipped with USB ports that allow for various functionalities, including file sharing, printer sharing, and even support for 4G/LTE dongles.
When it comes to USB compatibility with VPN routers, there are a few key aspects to keep in mind. Firstly, it is important to check whether the VPN router supports the type of USB device you intend to connect. This can include USB flash drives, external hard drives, printers, or mobile broadband dongles. Ensuring compatibility will help prevent any potential issues or limitations when trying to use the USB device with the router.
Another aspect to consider is the speed and performance of the USB port on the VPN router. USB 2.0 ports are common on many routers and offer decent data transfer speeds, while newer models may feature USB 3.0 ports for faster file sharing and device connectivity. Understanding the USB version supported by the router can help you make the most of your connected devices.
Additionally, some VPN routers may have built-in support for sharing USB devices over the network, allowing multiple users to access connected storage or printers seamlessly. This can be especially useful in home or office environments where resource sharing is essential for productivity.
In conclusion, USB compatibility with VPN routers plays a crucial role in expanding the functionality and convenience of your network setup. By ensuring compatibility, understanding the supported USB versions, and leveraging network sharing capabilities, users can create a secure and versatile network environment tailored to their specific needs.
USB VPN connection setup
Setting up a USB VPN connection is a convenient way to enhance your online security and privacy when using public Wi-Fi networks or accessing sensitive information. A USB VPN connection allows you to encrypt your internet traffic and establish a secure connection to a VPN server, keeping your data safe from potential cyber threats.
To set up a USB VPN connection, you will need a USB flash drive and a VPN client software that supports portable installations. First, download the VPN client software from the VPN provider's website and save it to your USB flash drive. Make sure to choose a reputable VPN provider that offers secure encryption protocols and a wide range of server options.
Next, insert the USB flash drive into the computer you wish to secure with a VPN connection. Run the VPN client software directly from the USB flash drive by double-clicking on the executable file. Follow the installation wizard instructions to configure the VPN client settings, such as choosing a VPN server location and entering your login credentials.
Once the VPN client software is properly configured, you can connect to the VPN server by clicking the "Connect" button within the VPN client interface. Your internet traffic will now be encrypted and routed through the VPN server, providing you with an extra layer of security and anonymity online.
In conclusion, setting up a USB VPN connection is a simple and effective way to protect your online activities from prying eyes and potential cyber threats. By following the steps outlined above, you can enjoy a secure and private internet browsing experience wherever you go.
Benefits of using USB for VPN access
Title: Exploring the Advantages of USB for VPN Access
In the realm of cybersecurity, Virtual Private Networks (VPNs) have become indispensable tools for safeguarding online privacy and enhancing security. While VPNs offer numerous benefits, accessing them via USB brings a host of additional advantages that cater to convenience, flexibility, and reliability.
Portability: One of the primary advantages of using USB for VPN access is portability. USB drives are compact and lightweight, allowing users to carry them anywhere conveniently. This portability ensures that individuals can access their VPNs from any computer, whether it's their personal device, a work computer, or a public terminal, without the need for pre-installed software.
Enhanced Security: USB-based VPN solutions often come equipped with additional security features. By storing VPN credentials on a USB drive, users can prevent unauthorized access to their VPN accounts. This two-factor authentication method adds an extra layer of security, reducing the risk of data breaches and unauthorized intrusions.
Offline Access: Unlike traditional VPN applications that require an internet connection to function, USB-based VPNs offer offline access. Users can pre-configure their VPN settings and store them on a USB drive, allowing for seamless connectivity even in environments with limited or no internet access. This feature is particularly beneficial for travelers, remote workers, and individuals operating in remote locations.
Privacy Protection: USB-based VPNs contribute to preserving user privacy by minimizing digital footprints. Since VPN configurations and credentials are stored locally on the USB drive, there's no trace of VPN usage left on the host device. This ensures that sensitive information remains confidential and inaccessible to prying eyes.
Compatibility: USB-based VPN solutions are compatible with a wide range of devices and operating systems, including Windows, macOS, and Linux. This compatibility ensures that users can enjoy VPN access regardless of their device preferences or system specifications.
In conclusion, leveraging USB for VPN access offers a myriad of benefits, including portability, enhanced security, offline access, privacy protection, and compatibility. By embracing this innovative approach, individuals and organizations can fortify their online defenses while enjoying seamless and secure connectivity across various devices and environments.
USB VPN security measures
In today's digital age, ensuring our online security and privacy is more important than ever. When it comes to protecting our data while browsing the internet, using a USB VPN can be a powerful tool. A USB VPN, or Virtual Private Network, encrypts your internet connection, making it more secure and private.
One of the key security measures to consider when using a USB VPN is encryption. By encrypting your internet traffic, a USB VPN scrambles the data you send and receive, making it nearly impossible for hackers or cybercriminals to intercept or decipher your information. This encryption adds an extra layer of protection, especially when using public Wi-Fi networks, which are known to be vulnerable to cyber attacks.
Another important security measure provided by USB VPNs is anonymity. By masking your IP address and location, a USB VPN allows you to browse the internet anonymously, keeping your online activities private from prying eyes. This is especially crucial for individuals looking to protect their sensitive information or avoid being tracked by advertisers or government agencies.
Furthermore, USB VPNs offer additional security features such as malware protection, ad blocking, and leak protection, further enhancing your online security and privacy. By investing in a reliable USB VPN service, you can safeguard your data, protect your identity, and browse the internet with peace of mind.
In conclusion, USB VPN security measures are essential for anyone looking to enhance their online security and privacy. By encrypting your internet connection, ensuring anonymity, and offering additional security features, USB VPNs provide a comprehensive solution to protect your data and safeguard your online activities.
Troubleshooting USB VPN connectivity
When it comes to troubleshooting USB VPN connectivity issues, there are several steps you can take to identify and resolve the problem. VPNs are essential for ensuring privacy and security while browsing the internet, so it's important to address any connectivity issues promptly.
One common issue with USB VPN connectivity is driver compatibility. Make sure that the drivers for your USB device and VPN software are up to date. Outdated drivers can cause conflicts and result in connectivity issues. Check the manufacturer's website for any updated drivers and install them if necessary.
Another possible cause of connectivity issues is a firewall or antivirus software blocking the VPN connection. Temporarily disable these programs and try reconnecting to the VPN to see if the issue is resolved. Remember to re-enable the programs after testing the VPN connection.
If you are still experiencing connectivity problems, try using a different USB port on your computer. Sometimes, the USB port you are using may be faulty, which can affect the VPN connection. Additionally, try using the USB device on a different computer to rule out any issues with your current system.
Finally, if none of the above steps resolve the problem, contact the customer support for your VPN provider. They may be able to provide further assistance and troubleshoot the issue from their end.
By following these troubleshooting steps, you can identify and resolve USB VPN connectivity issues quickly and effectively, ensuring a secure and private browsing experience.
0 notes
Text
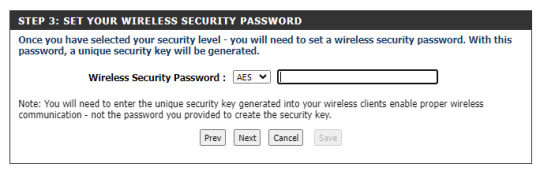
D-Link 4G LTE VPN ROUTER DWR-925
http://192.168.0.1
SETUP - WIRELESS CONNECTION - Wireless Connection Setup wizard
Next
Next
Best - Next

Set your password by filling the blank
1 note
·
View note
Text
Siemens 6GK5876-4AA00-2DA2 mobile wireless router
Siemens 6GK5876-4AA00-2DA2 SCALANCE M876-4 LTE (4G) NAM; for wireless IP communication from Ethernet- based automation devices via LTE (4G) mobile radio, optimized for usage in North America, VPN, Firewall, NAT; 4-port switch; 2x SMA antennas, MIMO Technology; 1x digital input, 1x digital output; observe national approvals.
Model: 6GK5876-4AA00-2DA2Categories: Industrial EthernetBrand:…

View On WordPress
0 notes
Link
Features: CCTV Router UR32S Designed for Remote Management in Batch Wi-Fi Client and AP Mode � Global 4G LTE CAT4/3G Network � NXP Processor � IP30 Protection with Metal Housing � VPN (OpenVPN/IPsec/PPTP/L2TP/DMVPN/GRE) - Remote Management - Wireless Router - 4G - VPN Smart Remote Management Solution By deploying it in practical CCTV projects, Milesight CCTV Router UR32S can achieve a stable and secure connection between on-site surveillance devices and remote side professional installers or technicians. In this way, Milesight cameras and NVRs can be managed in batch easily and remotely in a more secure and efficient way. *Enabling smart remote management solution may require higher CPU performance. Wi-Fi Client and AP Mode Milesight CCTV Router UR32S supports Wi-Fi Client and AP Mode, allowing users to simply connect the router to M-Sight Pro APP. Since all devices connected to the router will be immediately listed on the APP, users can configure the remote access permissions of devices in batch for installers or technicians within a few steps. Global 4G LTE Network Milesight CCTV Router UR32S features global 4G LTE CAT4/3G network with multiple carrier networks, achieving easy global connectivity. Meanwhile, it supports automated failover or failback between Ethernet and cellular with SIM card inserted. Advanced Routing Features Milesight CCTV Router UR32S guarantees secure transmission with stateful Firewall VPN tunnels including IPsec/OpenVPN/GRE/L2TP/PPTP/DMVPN. At the same time, it supports SNMP v1/v2c/v3 for maximized security and flexibility to meet different needs. Heavy Cast Aluminum Casing Equipped with industrial-grade NXP processor and compact design, Milesight CCTV Router UR32S allows great performance and easy deployment even in a limited space. Furthermore, its rugged metal casing with IP30 protection enables reliable operation under harsh environments and can withstand temperatures ranging from -40°C to +70°C. MilesightVPN MilesightVPN is an on-premises VPN platform designed for Milesight CCTV Routers to establish VPN rapidly and easily, achieving the one-stop remote access solution. Specifications: Hardware System Name Milesigt CCTV Router UR32S CPU ARM Cortex-A7,528 MHz Memory 128 MB DDR3 RAM and 128MB Flash Cellular Interface Antenna Connector 1×50O SMA Connector (Center PIN: SMA Female) SIM Slots 1 (Mini SIM-2FF) Ethernet Interface Numbers 2 × 10/100 Mbps Property 1 × WAN + 1 × LAN (Default) or 2 × LAN Mode Full or half duplex (Auto-Sensing) PoE 2 × 802.3 af/at PoE PSE on LAN Ports (Optional) Wi-Fi Interface Antenna Connector 1×50O SMA Connector (Center PIN: RP-SMA Female) Standards IEEE 802.11 b/g/n,2.4GHz Tx Power 802.11b: 16 dBm +/-1.5 dBm (11 Mbps) 802.11g: 14 dBm +/-1.5 dBm (54 Mbps) 802.11n: 13 dBm +/-1.5 dBm (65 Mbps, HT20/40 MCS7) Modes AP or Client mode Security WPA/WPA2 authentication, WEP/TKIP/AES encryption Others Reset Button 1 × RESET LED Indicators 1 × POWER, 1 × SYSTEM, 1 × SIM, 3 × Signal strength Built-in Watchdog, Timer Software Network Protocols IPv4/IPv6, PPP, PPPoE, SNMP v1/v2c/v3, TCP, UDP, DHCP, RIPv1/v2, OSPF, DDNS, VRRP, HTTP, HTTPS, DNS, ARP, QOS, SNTP, Telnet, VLAN, SSH, FRP, etc. VPN DMVPN, IPsec, OpenVPN, PPTP, L2TP, GRE Security Access Control, DMZ, Port Mapping, MAC Binding, SPI Firewalls, DoS&DDoS Protection, Filtering(IP&Domain), IP Passthrough Management Web, CLI, SMS, On-demand dial up, SNMP v1/v2/v3, DeviceHub AAA Radius, Tacacs+, LDAP, Local Authentication Multilevel Authority Multiple Levels of User Authority Reliability VRRP, WAN Failover Power Supply and Consumption Power Connector 2-pin 5.08 mm Terminal Block Input Voltage 9-48 VDC, with Surge-Protection and Reverse Polarity Protection Power Consumption Typical 1.8 W, Max 2.2 W (In Non-PoE mode) Physical Characteristics Ingress Protection IP30 Housing Metal Dimension 108 x 90 x 26 mm (4.25 x 3.54 x 1.02 in) Installation Desktop, Wall or DIN Rail Mounting Environmental Operating Temperature -40°C to +70°C (-40? to +158?) Storage Temperature -40°C to +85°C (-40? to +185?) Ethernet Isolation 1.5 kV RMS Relative Humidity 0% to 95% (non-condensing) at 25°C/77? Approvals Regulatory CE, FCC, RCM Environmental RoHS EMC EN 55032, EN 55035 EMS IEC 61000-4-2 Level 3 IEC 61000-4-3 Level 2 IEC 61000-4-4 Level 2 IEC 61000-4-5 Level 2 IEC 61000-4-6 Level 3 IEC 61000-4-8 Level 1 IEC 61000-4-11 Level 3 Radio Frequency EN 301 489-1/17/19/52, EN 301 511, EN 301 908-1/2/13, EN 303 413 Safety EN62368-1 Manufacturer Part No: UR32S Brand: Milesight Product Type: - UPC - Product Family: - Shipping Weight: 0.65 kg PB Part No: NETMLS4320 Product Model: UR32S Warranty: 24 months * * Warranty period is as stated above unless the manufacturer has chosen to specify a longer period. All warranties are return to base unless otherwise specified. Why is there a reasonable price displayed? Discover the reason behind our incredibly reasonable prices! At our company, we prioritize your satisfaction and work tirelessly to offer you access to top-notch brands without breaking the bank. Our commitment to minimizing profit margins enables us to deliver affordability without compromising on quality. Shop with confidence and explore a wide range of reputable products at budget-friendly rates. Your satisfaction is our priority! #
0 notes
Text
Sichere Kommunikation: Neue SD-WAN Gateway-Serie

Die ersten beiden SD-WAN Gateways seiner 1800er-Serie zeigt LANCOM Systems im neuen „blackline“-Gehäuse für die sichere VPN-Büro- und -Filialanbindung per DSL, Glasfaser, Kabelinternet und Mobilfunk.
Den Auftakt zur Serie bilden zwei Modelle: Der LANCOM 1800VAW bietet schnelles Dual-Band-WLAN (Wi-Fi 6) mit Supervectoring VDSL und optionalem Glasfaser-Anschluss (FTTH). Das Schwestermodell LANCOM 1800VAW-4G liefert durch zusätzliche 4G-Konnektivität ein zuverlässiges Internetbackup. Beide Gateways können optional hochautomatisiert in einem SD-WAN über die LANCOM Management Cloud betrieben werden.
Schnell mit den höchsten Sicherheitsstandards
Beide Geräte verfügen über ein integriertes VDSL-Supervectoring-Modem für bis zu 300 MBit/s und ermöglichen per separat erhältlichem SFP-Modul (GPON/AON) den direkten Anschluss an eine Glasfaser-Leitung (FTTH). Darüber hinaus bieten sie über Gigabit Ethernet größtmögliche Flexibilität für den Anschluss an externe Modems. Das schnelle Dual-Band-WLAN (Wi-Fi 6)-Modul mit 2x2 Multi-User MIMO im Down- und Uplink bindet drahtlose Endgeräte zuverlässig und gleichzeitig im 5 GHz- und 2,4 GHz-Band ins Netzwerk ein. Dabei ermöglicht die Wi-Fi 6-Technologie Übertragungsraten von bis zu 1.200 MBit/s in 5 GHz und parallel bis zu 575 MBit/s in 2,4 GHz.
Sichere Anbindung von Filialen und mobilen Arbeitsplätzen
Für höchste Bandbreite und eine ideale Lastverteilung können alle Geräte der neuen LANCOM Gigabit-Router-Familie bis zu vier Internetanschlüsse gleichzeitig nutzen. Bis zu 16 isolierte und getrennt voneinander routende IP-Kontexte bieten mittels Advanced Routing and Forwarding (ARF) eine effiziente Möglichkeit, alle IP-Anwendungen über einen zentralen Router zu führen und die verschiedenen Kommunikationskanäle sicher voneinander abzugrenzen. Die fünf (optional 25) integrierten IPSec-VPN-Kanäle sorgen für maximale Verschlüsselung, die sichere Anbindung von Filialen und mobilen Arbeitsplätzen und den Schutz unternehmensinterner Daten.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text
Industrial Cellular Routers: Encouraging Communication in Isolated and Dangerous Settings
Traditional wired networks are no longer the only way to connect in the modern digital era. Robust, dependable, and secure communication solutions are essential for industries operating in distant or harsh areas in order to connect their vital assets and provide real-time data sharing. The industrial cellular router is a type of customized networking equipment that can be used in industrial environments where cable infrastructure may not be available or is impractical.
An Industrial Cellular Router: What Is It?
A ruggedized networking device called an industrial cellular router uses cellular networks to provide wide-area connection for industrial applications. Industrial cellular routers use cellular technology (3G, 4G, and increasingly 5G) to transfer data wirelessly over great distances, in contrast to typical routers that depend on physical connections. They are designed especially to endure the harsh conditions found in industrial settings, such as high humidity, high temperatures, vibration, and electromagnetic interference.
Features and Functionalities:
The following are some of the main features and functions of industrial cellular routers:
Wireless Connectivity: Reliable wireless communication is made possible by industrial cellular routers, which enable cellular network communication between industrial systems and equipment. They are compatible with multiple carriers and areas because they support a range of cellular standards and frequencies.
Secure Communication: Security is paramount in industrial applications, especially when transmitting sensitive data over public cellular networks. To secure data and defend against cyber threats, industrial cellular routers use virtual private networks (VPNs), firewalls, and sophisticated encryption techniques.
Remote Management: An administrator may monitor, configure, and troubleshoot devices from a central location with the help of several industrial cellular routers' remote management features. Industrial network implementation, maintenance, and optimization are made easier by this remote management feature.
Redundancy and Failover: Industrial cellular routers may provide redundancy and failover capabilities to guarantee constant connectivity and reduce downtime. In the event of a network outage or disturbance, they can immediately switch between the primary and backup cellular networks or use other communication channels.
Importance in Business Environments:
Industrial cellular routers are essential in many different industrial domains, such as:
Oil and Gas: Industrial cellular routers provide for real-time monitoring of production processes, equipment health, and environmental conditions in remote oil and gas fields or offshore platforms. This promotes proactive maintenance and operational efficiency.
Utilities: Industrial cellular routers offer connectivity for remote monitoring, control, and optimization of essential infrastructure in utilities like water treatment plants, electrical substations, and renewable energy installations. This increases dependability and resilience.
Transportation and Logistics: By sending location data, sensor readings, and telemetry information over cellular networks, industrial cellular routers facilitate supply chain visibility, fleet management, and vehicle tracking in transportation and logistics operations.
Manufacturing: Machine-to-machine (M2M) communication in manufacturing facilities is supported by industrial cellular routers, which facilitate the smooth integration of robotic automation, inventory management systems, and production systems.
In summary:
For enabling connectivity in remote, difficult, and mission-critical industrial environments, industrial cellular routers are essential equipment. Because of their capacity to deliver dependable, secure, and robust wireless communication, industries are able to maximize operations, maintain a competitive edge in an increasingly interconnected world, and reap the benefits of digital transformation. Organizations in a variety of industrial industries can improve efficiency, spur innovation, and close communication gaps by utilizing industrial cellular routers.
0 notes
Text
BLIIoT Industrial 4G Edge Router R40 Used in Smart Charging Piles Monitoring

I. Introduction

1. A brief introduction to smart charging piles
In today's society, with the progress and development of customers, people pay more and more attention to smart energy. At present, electric vehicles have become the choice of more and more people. As the number of electric vehicles increases, so does the demand for smart charging piles. In order to improve the intelligence and convenience of charging piles, Industrial 4G Edge Router R40 can be used to realize remote monitoring and control in smart charging piles. In this article, we will discuss how to use an Industrial 4G Edge Router R40 to implement a monitoring solution for smart charging piles.
The smart charging pile monitoring system is a solution based on the Industrial IoT 4G Edge Router R40, which can realize real-time monitoring and management of charging piles. In addition to the basic charging pile status monitoring function, the system also has data analysis and forecasting functions, which can be analyzed based on historical data and real-time data to help users better understand the usage and trends of charging piles, and then make better decisions. management decisions.
2. Industrial 4G Edge Router R40
Industrial 4G Edge Router R40 have many features, including DI (2 channels), DO (2 channels), AI (4 channels), support protocols (Modbus RTU, Modbus TCP, MQTT, SNMP protocols), 4G network, support SMS Query DI/DO/AI status and value, support 4G wireless Internet access, support edge computing, two SIM card slots, support GPS, VPN, interface (support RS485 and RS232 serial port transparent transmission and MODBUS RTU to TCP), support MODBUS master Station, support address mapping, support monitoring the online status of network devices connected to the LAN port, link switching, platform connection, alarm, timer, upgrade, POE power supply and other features. These features allow Industrial 4G Edge Router R40 to realize remote monitoring and control in smart charging piles.
II. Application of Industrial 4G Edge Router R40 in smart charging piles
1. Real-time monitoring:
The smart charging pile monitoring system needs to be able to monitor the status, usage and charging speed of charging piles in real time. Through these data, operators can understand the usage of charging piles in real time, detect faults and repair them in time, and improve the quality and efficiency of charging services.
The Industrial 4G Edge Router R40 can be connected to the camera, supports POE power supply and network supply, and can realize real-time monitoring of the surrounding environment of the smart charging pile in real time, improving the safety and reliability of the charging pile.
2. Remote management:
The IoT Industrial 4G Edge Router R40 can provide remote management functions for the smart charging pile monitoring system. Operators can remotely view the status of charging piles, control the switching of charging piles, adjust charging power and other operations through the network. In this way, operators can manage charging piles more conveniently, while improving operational efficiency and reducing labor costs.
3. Data analysis:
The smart charging pile monitoring system needs to be able to analyze the monitored data, extract valuable information and display it. For example, analyzing the usage frequency, usage time period, charging speed and other data of charging piles can help operators optimize the layout and usage strategy of charging piles, and improve the satisfaction of charging services. At the same time, using big data technology to analyze charging pile usage data can also help operators understand user habits and needs and provide more personalized services.
4. Alarm and remote maintenance:
Through Industrial 4G Edge Router R40, real-time monitoring and abnormal alarms for charging piles can be realized. When there is an abnormality in the charging pile, the system will automatically trigger an alarm, and at the same time, it can be sent to the relevant personnel by text message or email, so as to deal with the problem in time. In addition, the Industrial 4G Edge Router R40 also supports remote upgrades, which can remotely perform firmware upgrades and configuration adjustments for charging piles, which is convenient for maintenance personnel to perform remote maintenance and management.
III. Features and advantages of Industrial 4G Edge Router R40
1. Multiple input and output types:
The Industrial 4G Edge Router R40 supports multiple input and output types such as DI (2 channels), DO (2 channels) and AI (4 channels), which can meet the needs of different scenarios. For example, for smart charging piles, the status and power of the charging piles can be monitored through the DI and AI interfaces, and the switching control of the charging piles can be realized through the DO interfaces.
2. Multiple communication protocols:
The router supports multiple communication protocols, including Modbus RTU, Modbus TCP, MQTT and SNMP protocols, etc., which can realize seamless communication between different devices. For example, in the smart charging pile scenario, the communication with the charging pile controller can be realized through the Modbus protocol, and the communication with the cloud platform can be realized through the MQTT protocol.
3. Edge Computing:
The router supports edge computing, which can realize real-time data processing and response on site. For example, in the scenario of smart charging piles, this function can be used to realize real-time calculation of charging pile power and timely processing of charging pile failures.
4. Dual card switching and link switching:
The router supports dual card switching and link switching, which can improve the stability of the network connection of the device. For example, in the smart charging pile scenario, this function can be used to realize the switching of the charging pile network connection and the automatic repair of faults.
IV. Benefits of using Industrial 4G Edge Router R40 in smart charging piles
1. Realize intelligent remote management and control
Using an Industrial 4G Edge Router R40 can connect the charging pile to the Internet for remote monitoring and control. This means that managers can access the data of charging piles anytime and anywhere, including charging amount, charging duration, charging voltage and current, etc. Managers can use remote control, such as remote switching, adjusting charging power, setting charging mode, etc., to better manage charging piles and improve the efficiency of charging piles and charging experience.
2. Improve the stability and safety of charging piles
Real-time monitoring and fault alarm of charging piles can be realized by using Industrial 4G Edge Router R40. When the charging pile fails, the Industrial 4G Edge Router R40 will automatically send an alert to the management personnel. In this way, managers can take timely measures to reduce downtime and improve the stability and safety of charging piles.
3. Reduce maintenance costs and increase efficiency
Using an Industrial 4G Edge Router R40 can also reduce maintenance costs and improve efficiency. Industrial 4G Edge Router R40 can realize automatic diagnosis and maintenance, reducing manual intervention. Managers can better manage and maintain charging piles through remote monitoring and control, reducing downtime and maintenance costs.
V. Conclusion
In general, the emergence of smart charging piles has brought great convenience to our lives, but at the same time it also requires remote management and control to ensure its stability and safety. As a high-performance network device, the Industrial 4G Edge Router R40 can meet the needs of remote management and control of smart charging piles, while improving its stability and security, reducing maintenance costs and improving efficiency. Therefore, it is a very wise choice to use industrial-grade 4G edge computing routers in the application field of smart charging piles, and it will be widely used in more smart device application scenarios in the future.
More information about the Industrial 4G Edge Router: https://www.bliiot.com/industrial-iot-edge-gateway-p00307p1.html
0 notes
Text
Intelligent transportation wireless video capture Cellular 4G Lte Industrial IoT Edge Router
The Cellular Edge IoT Router R40 is an industrial-grade OpenWrt IoT device with multiple functions. It integrates an Industrial Router, Gateway, RTU, and DTU functionality in one unit. The highly cost-effective product simplifies IoT systems by reducing hardware connections and maintenance requirements.
With dual SIM design, built-in WIFI module, Ethernet connection, and various IO interfaces, it is suitable for a broad range of applications. The most common use-cases are IoT solutions for infrastructure (bridges, tunnels), agriculture (forest), mining, oil and gas, water, and industrial factory use cases.
The R40 supports IPsec, OpenVPN, and L2TP VPNs, as well as protocols such as Modbus and MQTT with local computing capabilities using shell scripts, C, or Lua programming.
Support Connection to Cloud Platform:Private Cloud ( KPIIOT or Custom MQTT cloud), Alibaba Cloud Platform, AWS Cloud, Huawei Cloud, Thingsboard Cloud Platform.
It's under continuous improvement, Below are the newly added functions:
(1) Only upload changed data in MQTT Protocol;
(2) Can disable the Cellular Module;
(3) Support customized data format in MQTT Protocol;
(4) Modbus master poll cycle and response timeout can be setup;
(5) Can setup the start and end time and the number of cycles of the timer;
(6) LAN/WAN Port can be setup by manual;
(7) USB port can extend USB Disk, and share to the LAN Network computers.

0 notes