#how to secure gmail
Explore tagged Tumblr posts
Text
I want to move away from gmail and was checking out proton but they just added a generative ai tool... is there ANY secure email service that hasn't fallen to the ai craze????
14 notes
·
View notes
Text
just confirmed that my old phone has malware on it that will not allow me to delete or use the snapchat function altogether, so until i can find this other new phone my friend lost in her apartment (long story), i can't access my old accounts. it took me this long to figure out what was compromised and change my stupid email and passwords at the public library.
7 notes
·
View notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
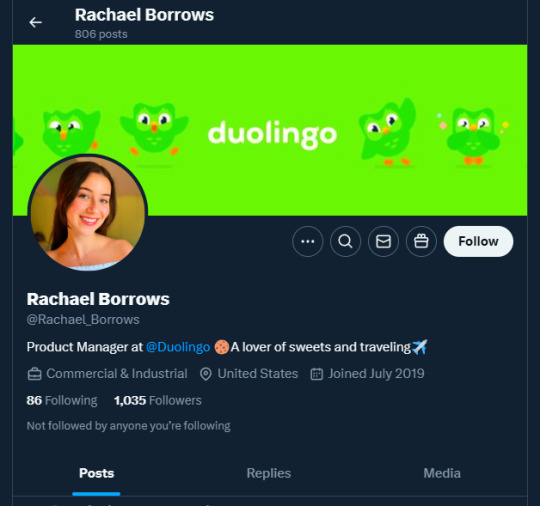
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
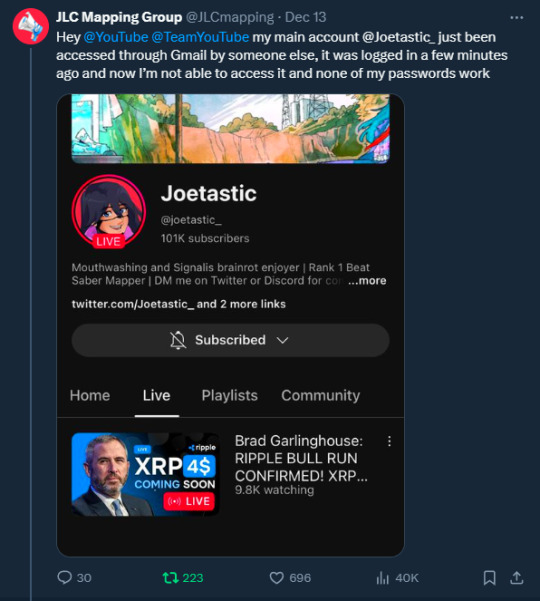
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
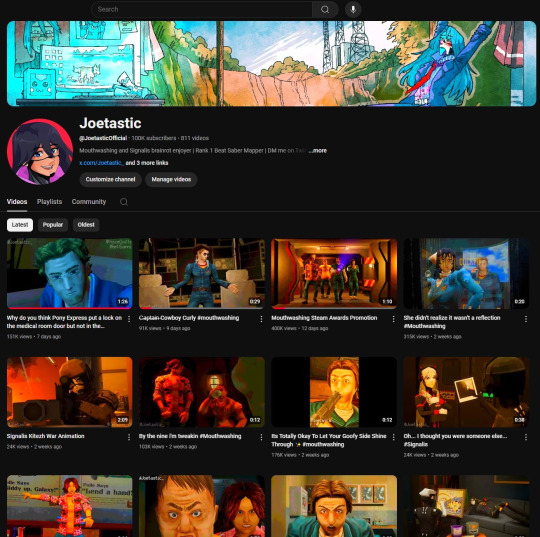
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
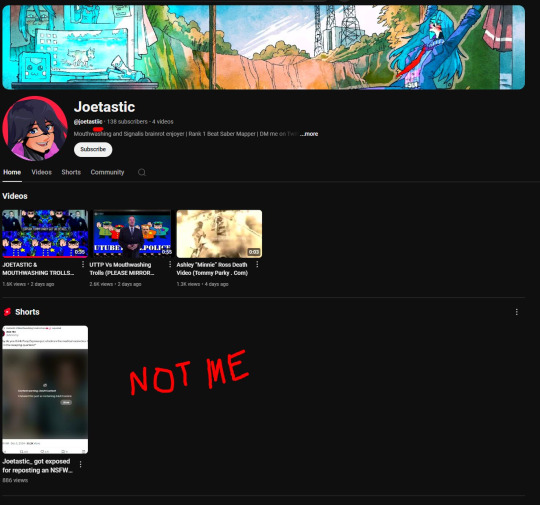
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
i keep looking through my grocery cart trying to figure out what else i can take out and like. i am struggling.
hi my income is about 1/3rd the local minimum wage and i'm a multiply (physically/developmentally) disabled person who is temporarily (only for a week and a half) responsible for purchasing groceries for three times as many people as usual (one of whom has celiac n faces serious risk from even cross contact with gluten)
and the math is not mathing and i am very stressed out 😭 i also used the last of several cleaning supplies recently n don't know how i'll get more
i know everybody's broke rn but if a financially secure adult is feeling generous, literally $5 would be a massive relief rn. the cleaning supplies (and some other stuff) is on this wishIist. i get groceries from walmart so if u wanted to help directly w that these can be sent anonymously (or not): https://giftcards.walmart.com/
my email address if anyone wants to send anything is thatdiabolicalfeminist at gmail dot com.
i'm so sorry to ask, i promise i am trying very hard not to need extra help but i don't know what else to do right now.
552 notes
·
View notes
Text
✨ ASTROLOGY READINGS — Paid Services 🔮
Hey cosmic soul,
If you’re drawn to the stars and need clarity, insight, or just a deeper connection to your path — I offer personalized astrology readings, crafted intuitively and in-depth. Everything is written with care and channeled into a PDF, delivered straight to your Gmail.
(READINGS ARE CLOSED NOW, THEY WILL BE OPEN ON SUNDAY, but i suggest to book one/secure your spot by sending me an email, not by paying, since i got too many messages abt paid readings, booking and everything !!!)
Available Readings:
(IF YOU WANT TO ADD THE +18 ASPECTS OF YOUR CHART IT WOULD BE +8€/$)
☀️ Natal Chart Reading
Your soul’s blueprint: personality, patterns, purpose, wounds, magic.
Price: 8€/$ (+1€/$ per extra asteroid)
❤️ Synastry Reading (Compatibility)
The way two charts dance together. Emotional bonds, attraction, karmic threads, and growth. it can be with your crush…your idol…your friend!!! you choose!! (specify on the email)
Price: 18€/$ (+1€/$ per extra asteroid)
🌞 Solar Return (Birthday Reading)
A glimpse into your year ahead — themes, opportunities, emotional shifts, and soul lessons.
Price: 8€/$ (+1€/$ per extra asteroid)
☁️ Vocational/Path & Purpose Reading
What your chart says about your soul calling, career potential, creativity, and growth.
Price: 8€/$
💡destiny matrix reading
Unlock the blueprint of your soul — the Destiny Matrix reveals your karmic lessons, life purpose, hidden talents, and energetic codes. This reading offers a deep, structured map of your spiritual and material evolution, guiding you toward a more fulfilled, aligned life.
Price: 8€/$
How to Book:
1. Send the payment via PayPal to:
(i’ll put the link on sunday since then is when the readings will start being available)
(Please select “Friends & Family” if possible — it helps me avoid fees.)
2. Email me at [email protected] with the following:
– Your name or initials
– Your birth date, exact time, and place
– The reading you’re booking
– If you’re booking a synastry: include both people’s birth info
—if you’re booking a solar return: i will need the city you’ll be staying this year too, for a complete reading
– A screenshot or confirmation of your PayPal payment—this is very important ‼️‼️‼️
3. You’ll receive a confirmation from me, and your reading will be sent within 5 days!
Important Notes:
– No tarot readings offered — only astrology.
– I don’t do medical or legal predictions.
– All readings are digital and sent as PDFs.
– Refunds are not available once the reading is complete.
and…if you have booked a reading w me, you’ll have priority (basically i’ll answer your asks first heheh) for your asks on this blog, if you wanna use this benefit, in the email u should write your tumblr name too, and use it for the asks so i know it’s you 💕
THE STAR CARD;
Introducing the Star Card! When you order 5 paid readings (they are acumulative, of course), you'll receive 1 free reading!!! + 3 tarot questions (this is the only tarot service i offer! so don’t miss the chance!!!)
i’ll notify you when you’ve achieved the 5 readings!!! (make sure they are ordered from the same email)
FAQ – Cosmic Clarity Corner
Q: Can I ask questions before booking?
Absolutely. Feel free to message me here or email me if you’re unsure which reading to choose or anything else! (only via email: [email protected])
Q: Do I need to know my exact birth time?
Yes, especially for natal and synastry readings. If you don’t know it, I can still do a partial reading, but some details (like rising sign or houses) won’t be available.
Q: Can I request a custom reading?
Totally! If you want a mix of things (like a bit of natal + solar), just let me know and I’ll build it for you.
Q: How will I receive my reading?
As a PDF file sent to your Gmail, with notes, symbols, and intuitive insights written by me.
Thank you for trusting me with your stars.
It means everything. This is more than a service — it’s soul work.
Talk to you soon, star child 💫
#astrology readings#astro notes#astro community#astro observations#astrology#astrology observations#astrology blog#astro game#astrology chart#natal chart#birth chart#paid readings
24 notes
·
View notes
Text
hi. since i have something that could very generously be called a platform, your local dumb horny dog is here with another unfortunate public service announcement for people currently living under the legal jurisdiction of the united states of america:
this would be a good time to start investigating privacy and data security tools (and, as ever, to not panic and/or doompost because those are not useful things to do). such things include:
using (more) secure messaging apps over sms for private correspondence such signal.
using (more) private email services rather than gmail such as protonmail
password protect your shit. this is just basic data security but like. please. password protect your shit. use strong passwords and/or passphrases. don't reuse passwords. use a password manager (i recommend bitwarden).
building off the previous one, encrypt your shit if you're able to. for pc users there are plenty of open source options, such as veracrypt, and probably native os stuff too.
like. y'all are gonna roll your eyes, and i get it, but: stop using windows and try out linux. seriously. windows 11 is a fucking privacy nightmare and it's only getting worse as microsoft pushes their ai shit which is planned to have access to everything you do on it.
tumblr can't do nested lists, consider this a sub-point: mint linux is designed to be incredibly familiar to people coming from windows and is very user friendly. a huge amount of windows software can run on linux using stuff like wine. the linux version of steam comes pre-packaged with it. it's fine. please try linux it won't bite.
sadly i am, as mentioned, a dog on the internet and i cannot provide an actual comprehensive guide to keeping your privacy intact and yourself safe.
however, there are plenty of good guides for this sort of thing on the internet and despite how degraded modern search engines are they are not hard to find. i heartily suggest doing so and familiarizing yourself with them-- and not just because of the times we live in, because a lot of this shit is the same shit that will help keep you safe from a lot of forms of identity theft and the like. it's just good opsec.
22 notes
·
View notes
Text
McMurdo Internet
Internet service is supplied to Antarctica via a geostationary satellite. This far south, the satellite is only a few degrees above the horizon, and unfortunately for McMurdo, it's behind Mt Erebus. So the signal is beamed to a receiver on Black Island, about 20 miles away to the southwest, and bounced over to the sheltered alcove at the end of the Hut Point Peninsula where McMurdo sits.

The Chalet, administrative hub, with Black Island in the distance
The Black Island telecommunications infrastructure was installed in the 1980s, long before the internet we know and love today. It was upgraded in 2010 to allow more data transfer, mainly realtime weather data to feed into global forecast models. For this reason, it's probably the only place I've ever been where upload speed is remarkably faster than download speed – 60Mbps for outbound traffic, but only 20Mbps for inbound. Most regular internet use is receiving, not sending, so that's an entire base running on a connection that's only marginally faster than the average American smartphone. As you can imagine, this is somewhat limiting.
The limits to one's internet access actually begin before one even reaches the Ice. At the orientation in Christchurch, one is directed to a URL from which one must download and install a security programme from the U.S. government. It may feel like a hippie commune full of nerds, but McMurdo is an installation of the American state, and as such its computer network is a target of whatever disgruntled conspiracy theorist decides to hack The Man on any given day. Computers that are allowed onto this network (such as the one on which I am typing right now) have to have an approved firewall and antivirus service installed, then this extra programme on top of them. I am not sure what it does. For all I know the CIA is spying on me even now. (Hi, guys!) But you need to install it to get on the McMurdo Internet, such as it is, so I did.
To be honest, I was rather looking forward to a month cut off entirely from the hyperconnected world, so I was a tiny bit disappointed that quite a lot of day-to-day communication is done by email, and I would need to be on my computer a fair bit to get it. Had I known just how important email would be, I'd have installed an email client that actually downloads one's messages instead of just fetching them; as it was, the cycle of loading an email and sending the reply, even in Gmail's "HTML for slow connections" mode, took about five minutes, not counting the time it took to write. Tending one's email was a serious time commitment; sometimes I felt like I was spending more time on the computer in Antarctica than I did at home.

Crary scientists waiting, and waiting, and waiting
In a way, though, I was lucky, because I was technically a scientist and therefore had access to the one building on base with WiFi, the Crary Lab. And don't think you can just waltz into Crary with your laptop and poach the WiFi – in order to access it at all, you have to get set up by Crary IT with your own personal WiFi login. If you do not have Crary access, your portal to the Internet is one of a handful of ethernet cables in each of the dorm common rooms, or some public terminals in the main building. You can hop on, download your emails, maybe check the news or Google something you needed to look up, and then leave it for someone else. When most online time sinks are either blocked or too heavy to load, it’s amazing how little internet time you actually turn out to need.
Things that we have come to take for granted in The World are not a part of McMurdo life. Social media is pretty much out – the main platforms are bandwidth hogs even before you try to load a video or an animated GIF. There is no sharing of YouTube links, and no Netflix and chill. Someone was once sent home mid-season for trying to download a movie. Video calls with family and friends? Forget it. People do occasionally do video calls from Antarctica, often to media outlets or schools, but these have to be booked in advance so as to have the requisite bandwidth reserved. Jumping on FaceTime does not happen – not least because handheld devices have to be in airplane mode at all times for security reasons. Your phone might be secure enough for your internet banking, but not for US government internet!
It is, unavoidably, still a digital environment, it just gets by largely without internet access. Nearly everyone has an external hard drive, mostly for media that they've brought down to fill their off hours. If you want to share files you just swap hard drives, or hand over a memory stick. When the Antarctic Heritage Trust wanted some book material from me, I dropped it onto an SD card and ran it over to Scott Base on foot – a droll juxtaposition of high- and low-tech, not to mention a good excuse for a hike over The Gap on a beautiful day. It took half an hour, but was still faster than emailing it.
There is also a McMurdo Intranet, which includes a server for file sharing. Emailing someone your photos will take ages, but popping them into a folder on the I: drive and sending them a note to say you've done so (or, better yet, phoning them, or poking your head into their office) is much more efficient. To conserve space, this informal server partition is wiped every week, so you have to be quick about it, but it's an effective workaround, and also a good way to get relatively heavy resources to a large number of people in one go.
The telecommunications centre on Black Island is mostly automated, but like anything – perhaps more than some things, given the conditions – it needs to be maintained. There is a small hut out there for an equally small team of electricians and IT engineers; Black Island duty attracts the sort of person who might have been a lighthouse keeper back in the day.
Towards the end of my time on the Ice there was a spell where they needed to shut off the connection overnight, to do some necessary work. Given that most people's workdays extended at least to the shutoff time at 5:30 p.m., this meant essentially no internet for a large portion of the population, and some amusing flyers were posted up to notify everyone of the impending hardship.


Someday, faster, more accessible internet will come to Antarctica. It's more or less unavoidable, as communications technology improves, and everyone's work – especially the scientists' – depends more and more on having a broadband connection at all times. It will make a lot of things more convenient, and will make the long separation from friends and family much easier. But I'm pretty sure that many more people will mourn the upgrade than celebrate it. One can, theoretically, curtail one's internet use whenever one likes, but even before the pandemic it was almost impossible to live this way with the demands of modern life: I know from personal experience that opting out of Facebook alone can have a real detrimental effect on relationships, even with people one sees in the flesh fairly regularly, simply because everyone assumes that is how everyone else communicates. Being in a community where no one has access to assumed channels, and is more or less cut off from the rest of the world in a pocket universe of its own, levels the playing field and brings a certain unity. The planned (and, unarguably, necessary) updating of the physical infrastructure of McMurdo will wipe out a lot of the improvised, make-do-and-mend character of the place; how much would free and easy access to the online world change it in a less tangible way?
I'm sure the genuine Antarctic old-timers would shake their heads at the phone and email connections we have now, and say that no, this has already ruined Antarctica. It's not Antarctica unless your only link to the outside world is a dodgy radio. It's not Antarctica unless you only get mail once a year when the relief ship arrives. Doubtless the shiny new McMurdo will be seen as 'the good old days' by someone, someday, too. Change may happen slower there than elsewhere, but just like the rust on the tins at Cape Evans, it comes eventually, regardless.
For my own part, I'm glad I got to see 'old' McMurdo, such as it was, all plywood and cheap '90s prefab. The update will be much more efficient, and tidy, but yet another generation removed from the raw experience of the old explorers. My generation is probably the last to remember clearly what life was like before ubiquitous broadband; to some extent, Antarctica is a sort of time capsule of that world, just as the huts are a time capsule of Edwardian frontier life. I hope they'll find a way to hang on to the positive aspects of that.
Now, if you'll excuse me, I'm off to waste an hour mindlessly refreshing Twitter ...
If you'd like to learn more about the Black Island facility, there's a lot of good information (and some photos!) here: https://www.southpolestation.com/trivia/90s/blackisland.html
And this Antarctic Sunarticle goes into greater depth on the 2010 upgrade: https://antarcticsun.usap.gov/features/2114/
270 notes
·
View notes
Text
youtube
Hello there! I am making this video to give everyone an update on where I’m at and how I’m doing. Short answer: I’ve been better. Those of you keeping up with me through my social media or my GoFundMe know that I’ve been sick for the last year and a half, going on two years. I’ve also recently lost my job because they said they could not accommodate my illness and need for more time off and protect my job. I am disappointed about that but not angry. I will say that they did give me a lot of leeway before we got to this point.
So to briefly recap the road so far, I was diagnosed with thyroid cancer in October of 2023. In that same month, I had a total thyroidectomy. So far, all is clear and there doesn’t seem to be any cancerous tissue lingering in the area. I still have to have checks every few months for the next few years to be sure it doesn’t come back. This was actually the easy part.
The recovery has been far harder than I could have anticipated. Everyone I’ve talked to that has had thyroid issues has had a different experience so there’s not a clear path for recovery. For example I have had issues with getting my T4 and TSH levels regulated. I just got an increased dosage on my Synthroid last month, and so far it’s not really doing the trick. 19 months and it’s still trial and error.
And that alone would be enough to lay most people out. If you have a thyroid that works properly, be thankful. You have no idea how volatile that tiny little gland can be to your well being. I was so much worse off this time last year. I spent months in pain, freezing, sweating, nearly hallucinating and unable to eat or rest. I was in and out of the ER feeling like I was dying. I’m straight up terrified of ever feeling like that again.
I know I don’t need to, but to give a broader picture, here’s what I’m dealing with. Obviously the thyroid issue. I also have type II diabetes, autoimmune issues like psoriasis, psoriatic arthritis, and neuropathy (which causes numbness, nerve pain, and other neurological issues). That’s the physical side.
On the mental side, I have major depression, major anxiety, CPTSD, and ADHD. These are all official diagnoses. I first got diagnosed with depression as a child, and I have had several therapists, medications, intensive therapy programs, etc to try to manage them. I say this because I don’t want to hear that I’ve been self diagnosed and therefore invalid. Which is a terrible attitude to have toward someone dealing with this stuff because not everyone can afford a “legit” diagnosis.
A couple of weeks ago, I was terminated from my job. I can say that my employers tried to work with me as much as they could, but since FMLA, which provides job protection in situations like mine, doesn’t go into effect until a year after the date of employment, they had no legal obligation to keep me on. I understand it, but it still sucks.
So now I am trying to navigate applying for disability. I qualify for unemployment benefits, but they are not sufficient to cover my bills. So I am here again, asking for help. I absolutely hate this. I want to be able to handle things on my own, but that’s not possible anymore when I barely have the energy to make it through a day.
If you can’t tell, I am reading from a script because I go off on tangents if left to improvise. So to keep this from going too long, I would appreciate any help I can get to keep myself going until I can get myself secured with disability or…something. Thank you to everyone that has been able to help so far, I would not be here now if not for all your help.
Link to the GFM is here: https://gofund.me/e0640a1e
And if you don’t want to use this link, you can also donate via my Venmo @ Dextra-Hoffman (last 4 of my phone is 6036) and my PayPal is under dextra.hoffman at gmail .com. Thanks.
5 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
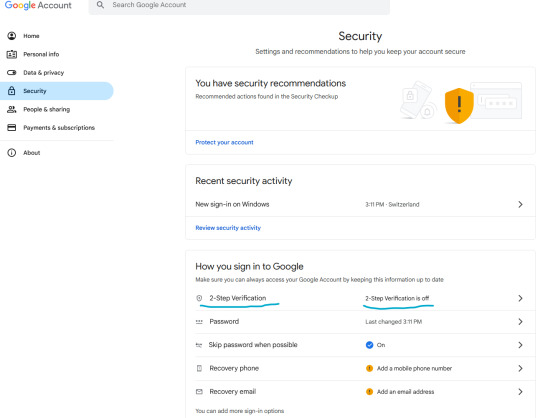
Let's enable two-step verification first.
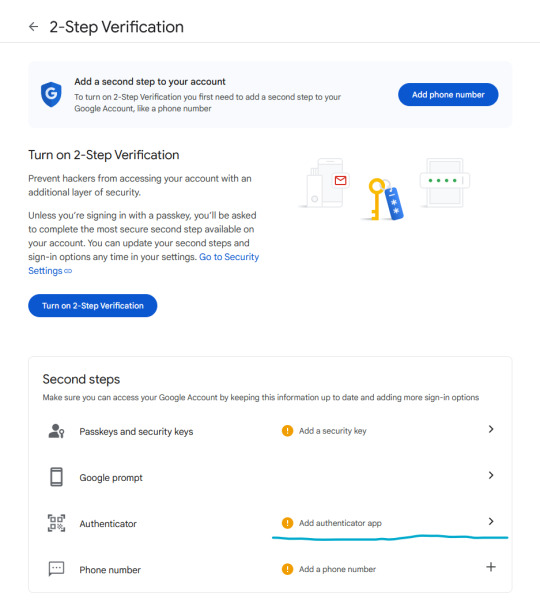
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
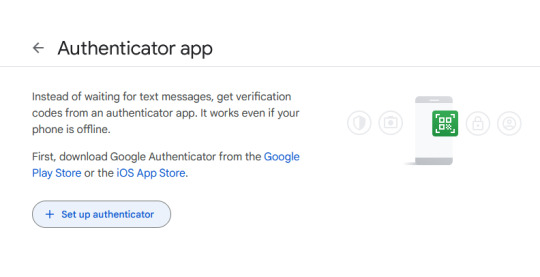
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
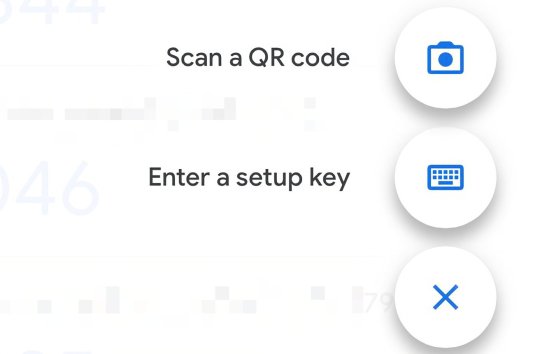
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
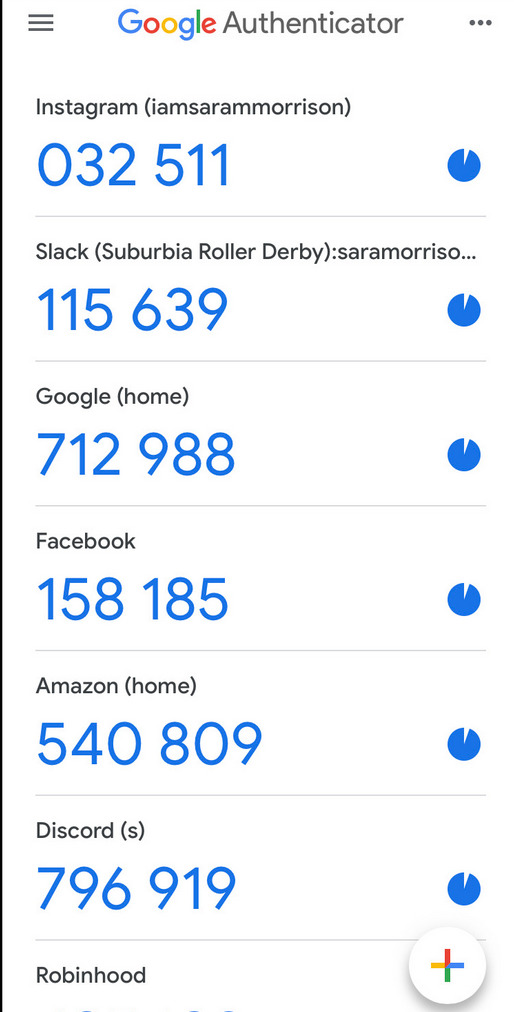
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
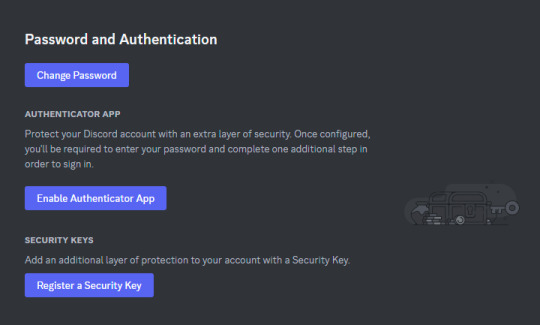
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
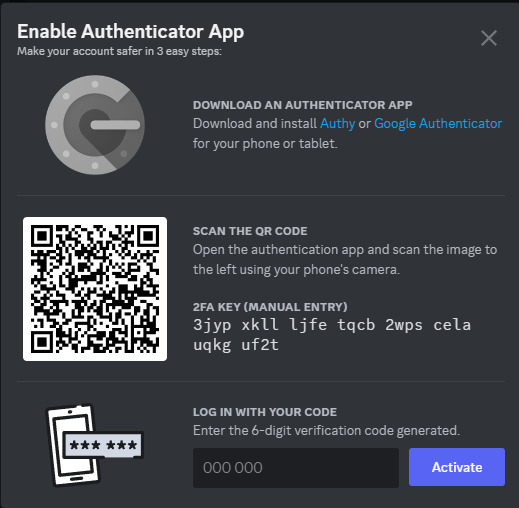
Download Google Authenticator if you haven't already. Scan the QR code as described above.
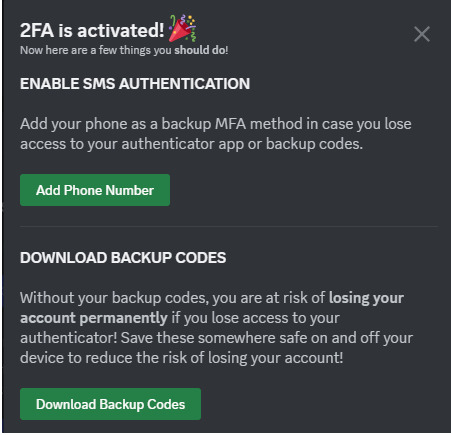
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
saw a post the other day full of people complaining about helping older people use computers, about how clueless they can be, how frustrating it is to have to tell them basics like where to click, exactly what to type, how some people just never seem to get it. then an addition was someone who works in a library sharing a story of a ninety-something woman who picked it up instantly. it’s not difficult, this elderly woman said! wow heartwarming.
i’m here to say that plenty of older and disabled and otherwise marginalised people do not know how to use computers and in some cases will find it very difficult if not impossible to learn to use them. for many people it is difficult. it can be insurmountable. we should be fighting for a world where vulnerable people who are not computer literate can use computers with assistance when they want to, but where they do not need to use computers, ever. this is a serious access issue as so much government paperwork is moving to being online only. your frustration at working a job that likely overworks and underpays you to help people use these computers - please think before turning it on the disenfranchised and vulnerable people who rely on you for assistance and resources.
it’s an annoyance for you? then think about why is it that governments habitually move the resources that vulnerable people need to live to online-only when they know as well as you and i do that the digital divide is real. think about how intentionally difficult governments and agencies make it to access forms and paperwork and everything else that is needed to claim such a small amount of money as people currently get when they are out of work and trying to claim benefits, or on allowances for refugees, etc. how much are governments dedicated to taking away people’s dignity and autonomy by swapping to a system that millions of people do not have access to without going into a public library and asking for help, if there’s even anyone there who is able to or allowed to help? i can get people set up with email and find websites for them but im not even allowed to help with sensitive forms - i can only do what i can, you know. i wish it was more.
before i started this job i thought of myself as impatient. i’m not going to tell you any stories in detail because my library patrons didn’t consent to being A Teaching Moment. but i have requests from “difficult” patrons every day. i take a deep breath and if i don’t have a queue, i try to help. i smile and say “don’t worry” when someone is apologising over and over because they were never taught this and they are stressed out and it doesn’t make sense to them. not everyone grew up with neopets and Hotmail. it makes you no better than them if you did.
i’m not perfect but i’m trying. just… think about it, next time you roll your eyes because another old lady doesn’t know how to use gmail, even though you’ve already shown her what to click. ask if your library has thought about seeing up dedicated sessions for helping people use computers if they need assistance (maybe it’ll take some of the work away from you and give you more breathing space). make leaflets telling people where they can go nearby for help with computers - maybe some local charities or non-profits have drop-in sessions. join campaigns for easier access, for letting people who can’t use computers do what they need to without needing to find some way to get online. all of these are more useful in holding solidarity than in just being frustrated that another person in their seventies, eighties, nineties, struggles to use a computer.
a couple more notes of things that i think about a lot when it comes to computer access at the library that might not occur to people who don’t routinely help people out with basic computer stuff:
2-factor authentication is the devil. i understand the intention behind it and cyber security is important and difficult! but 2-factor authentication in practice locks out and disenfranchises vulnerable people every day, makes them unable to access their emails and everything else on the web that depends on their email, makes them unable to access their data and government portals, and makes them even more vulnerable than governments already conspire to make them. plenty of people just do not understand how 2FA works. it doesn’t matter how many times the google website says : look at your phone and click on this number. or whatever. if somebody else is not there to tell them what to do — if they haven’t recently had to change their phone number, as many vulnerable people might have had to do — they will not be able to do it.
google have recently been selling chromeboxes to public libraries (and schools) cheap. chromeboxes in public libraries are also the devil. on a windows PC loaded with word, lots of people are happy and able to do what they need to do. the problem comes when they have to log in to a google account just to access a fucking word processor. it’s a scandal how many people are locked out of access to something as simple as a word processor unless they have a google or Microsoft account. we are talking people who don’t want email accounts, who just want to type up a letter to send in the post. Every time I ask online for a good alternative I get something extremely tech-y or like fucking online textpad. we just need a good accessible word clone that runs in a web browser like Word XP. It would make a lot much easier. And yet!
144 notes
·
View notes
Text
So, I've been a bit distracted by other things and lost some momentum on this project, but I do have a google form all set up for zine submissions. Unfortunately I've hit a snag. I think I know how I want to deal with this, but it's just turned into one big stressful knot in my plans, so I'm here to check in and see how people feel about the possible solution.
Problem is, I realized at the last second that google is going to require a log-in for any form with a file submission (for security reasons, which is reasonable if inconvenient). I need a file submission question because I need images of doodles to be submitted to me so I can compile the zine. I have configured the form so I would not be able to see the email address of anyone who submits, but it would still require a gmail login to submit to the form.
I don't have an obvious alternative for filesharing that's convenient, anonymous, and doesn't require a login (because to be honest there's reasons those don't exist). What I'm thinking of doing, if it wouldn't put too many people off, is using the google form and offering anyone who doesn't have a gmail login to use the alternative option to DM me and submit through DMs or email or whatever we can work out.
Just wanted to get a temperature check on how well this solution would work for people:
Just to clarify, for all of these you would be able to have your submission appear in the zine with no name attached. Only the google form would be anonymous to me. Obviously DMing me would involve me knowing your username but you'd still have the option to be anonymous in the zine. I know DMing strangers is intimidating but I'm super chill I promise.
#if you would not be able to do any of these feel free to let me know in notes/dms/askbox if there is another method that would work for you!#i would like for this to be as low a barrier to entry as possible and i know for some people that means not having to Talk To A Person#however it looks like it's that or *some* kind of account login#and gmail is probably the one that the most people have tbh#zine planning#being Brave by posting this :')#started working on my fun little project and then ran face first into Slight Complications and got very disheartened#but instead of continuing to run away from this i am going to simply check and see if it is As Big Of A Deal as it seems
12 notes
·
View notes
Text
This day in history

I'll be in TUCSON, AZ from November 8-10: I'm the GUEST OF HONOR at the TUSCON SCIENCE FICTION CONVENTION.

#20yrsago Disney sued by “inventor” of FastPass system https://web.archive.org/web/20041101023537/http://www.patentlyobviousblog.com/2004/10/patent_suit_all.html
#15yrsago Mickey Mouse comics drawn by concentration camp prisoner https://web.archive.org/web/20091103172853/http://www.scribd.com/doc/21860527/Horst-Rosenthal-Mickey-Mouse-in-Gurs
#15yrsago UK ISP TalkTalk threatens lawsuit over 3-strikes disconnection proposal https://www.theguardian.com/media/2009/oct/29/talktalk-threatens-legal-action-mandelson
#15yrsago My Times editorial on British plan to cut relatives of accused infringers off from the net https://www.thetimes.com/article/denying-physics-wont-save-the-video-stars-wf52wrrs2r0
#10yrsago The rise and fall of American Hallowe’en costumes https://www.npr.org/sections/money/2014/10/27/359324848/witches-vampires-and-pirates-5-years-of-americas-most-popular-costumes
#10yrsago Profile of MITSFS, MIT’s 65-year-old science fiction club https://web.archive.org/web/20141023191938/http://www.technologyreview.com/article/531401/60000-books-and-a-few-toy-bananas/
#10yrsago Malware authors use Gmail drafts as dead-drops to talk to bots https://www.wired.com/2014/10/hackers-using-gmail-drafts-update-malware-steal-data/
#10yrsago Verizon’s new big budget tech-news site prohibits reporting on NSA spying or net neutrality https://www.dailydot.com/debug/verizon-sugarstring-us-surveillance-net-neutrality/
#10yrsago Every artist’s “how I made it” talk, ever https://www.youtube.com/watch?v=l_F9jxsfGCw
#10yrago The Terrible Sea Lion: a social media parable https://wondermark.com/c/1062
#10yrsago Opsec, Snowden style https://web.archive.org/web/20141028183511/https://firstlook.org/theintercept/2014/10/28/smuggling-snowden-secrets/
#5yrsago Elizabeth Warren proposes a 4-year ban on government officials going to work for “market dominant” companies https://medium.com/@teamwarren/breaking-the-political-influence-of-market-dominant-companies-8ff27e99ada0
#5yrsago Behind the scenes, “plain” text editing is unbelievably complex and weird https://lord.io/text-editing-hates-you-too/
#5yrsago Despite denials, it’s clear that Google’s new top national security hire was instrumental to Trump’s #KidsInCages policy https://www.buzzfeednews.com/article/ryanmac/miles-taylor-family-separation-dhs-despite-google-denial
#5yrsago 70% of millennials would vote for a socialist https://victimsofcommunism.org/annual-poll/2019-annual-poll/
#5yrsago Davos in the Desert is back, and banks and hedge fund managers are flocking to Mister Bone-Saw’s side https://www.bbc.com/news/business-50219035
#5yrsago Podcast of Affordances: a new science fiction story that climbs the terrible technology adoption curve https://ia903108.us.archive.org/3/items/Cory_Doctorow_Podcast_314/Cory_Doctorow_Podcast_314_-Affordances.mp3
#5yrago Kindness and Wonder: Mr Rogers biography is a study in empathy and a deep, genuine love for children https://memex.craphound.com/2019/10/29/kindness-and-wonder-mr-rogers-biography-is-a-study-in-empathy-and-a-deep-genuine-love-for-children/

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.

5 notes
·
View notes
Note
1. Tubbo confirm himself in the clip that he only kissed her, to which she later confirmed it too. As pre the video
Tubbo made the video and She would confirm it AFTER the hacker had allegedly made the post.
Let me help you, hacker did their job -> Tubbo made the video -> She confirmed it. Then how did the hacker make such a lucky guess about what happened that night in Tubbo's house?
I didn't have to go past the first point for it. Didn't even use my two degrees on Physics. Can't believe what they are feeding these IT students these days ....
"HoW dId The HaCkEr MaKe SuCh A LuCky GuEsS?"
THE VIDEO IN QUESTION WAS FILMED WAS FILMED A YEAR AGO OF HIM AT A PARTY WITH HER, AND ALL HER FRIENDS AS THEY DRANK
youtube
My goodness it would take a genius to be like "Hey I'm making allegations that they both got drunk (as shown in he video from a year ago) and Tubbo S/A her while drunk"
To which they allegations never specified WHERE THEY WERE it only specified part they were at
So Tubbo, confused as fuck Tubbo, said they came to there place, kissed and then talked about Jazz
Them going back to Tubbo's place wasn't even in the original allegations
Bitch if I went to a party, got drunk, PUBLICLY POSTED ABOUT IT ONLINE, and then someone was like "(me) was harassed by xyz", I'D BE SO FUCKING DUMB BECAUSE THEIR EVIDENCE WOULD BE THE VIDEO FROM A YEAR AGO. WHY THE FUCK WOULD SOMEONE INCRIMINATE THEMSELVES
Now dear clear idiot. I shall explain how 2-step verification works and how it didn't work in this case. AhEm
1. 2-Step Verification is as it sounds, in which after attempting to log on to a platform, the platform holders will either send a text message (through phone number) , email/gmail/AOL (if your old), notification or another form of communication to ensure the person login in is actually, ya know, you.
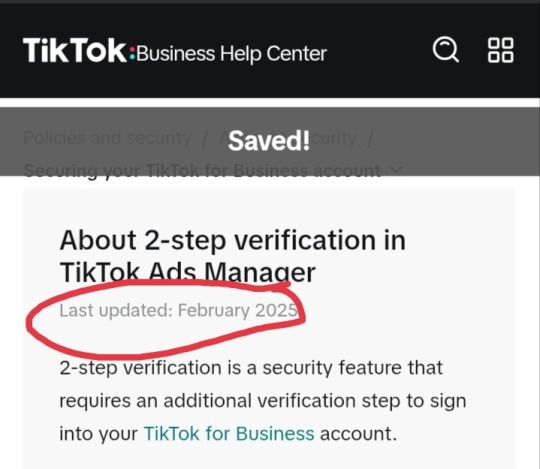
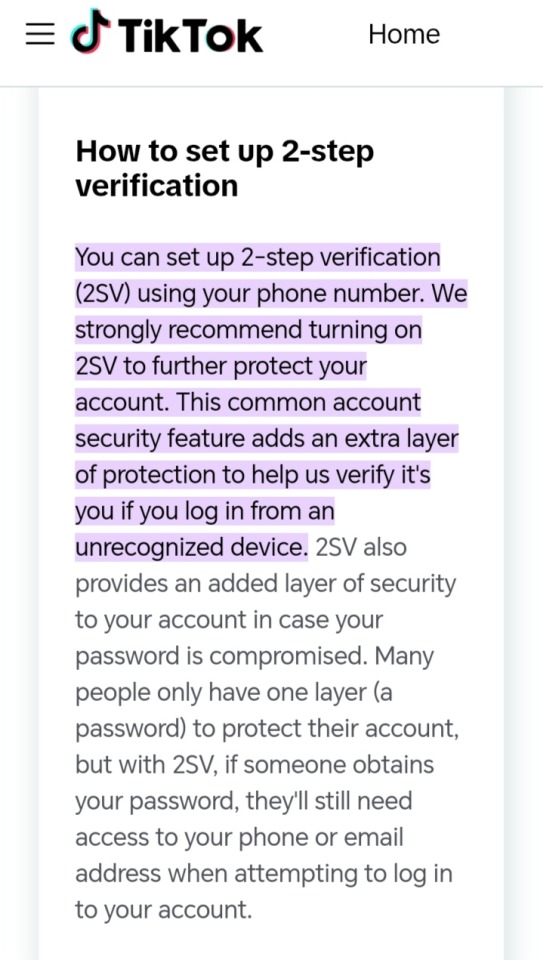
2. 2-Step Verification became a thing on TikTok, official and refined, on February 2025 (very late tbh)
3. Your young people don't know that back in my day TikTok didn't exist. OMG HOW COULD THIS BEEE??? Because it was called Musicly before it rebranded to tiktok
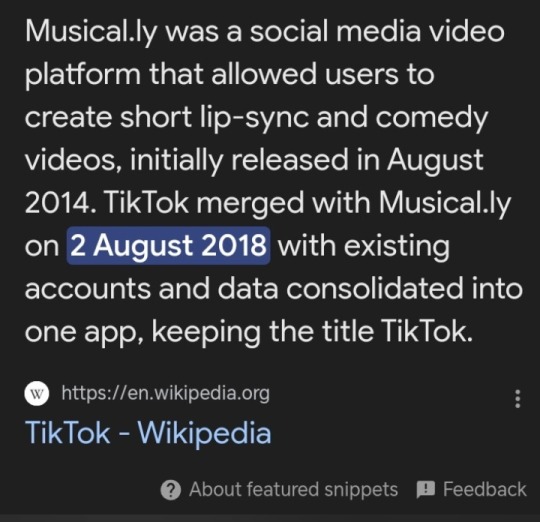
And since Musicly was primarily a kids/teens/young adults app, who tf is hacking a child's account?? Ya know?
So up until before that point Musicly also didn't have 2-Step Verification. Which is important because that means this security measures didn't transfer over because they didn't exist
4. Listen Leandra is by no means old. But I will rest a hand on your shoulders when I say, Gmail was created in 2004

And if you were a kid/teen around that time, you were young enough to get a Gmail with your actual name, like full legal, government, on yo birth certificate name
Why this important? Because if your primary Gmail/email/AOL, if your full legal name or part legal name, then people have a higher chance of just guess your email or, putting down "forgot password", then linking it to their email address, getting the rights to change the password and then bam.
The only way this cannot happen is if you manual lock your Gmail to only known devices (but fr that takes to long ngl and plus you won't be able to work on something if you can't access the device that has the rights to your email and additionally if you lose that device then it's game over, try again, pack it tf up)
So if she made her Tiktok account via any of the emails, then it's done, sorted, etc...
4.1. Now let's say she made it with her phone number like Tubbo suggested.
You could gain access further:
Having the email/gmail/AOL be linked with your phone number as a contact/emergency contact (idk in what case Google would hit you up but they can ig)
Phising. Look it up. It's spelt with a PH but pronounced fishing. And it's much more common then you think
The most popular phone plan providers in the UK are EE and Vodafone, inwhich if you get a new SIM card in a new phone, you can call them to change the new SIM phone number back to your older on as I'd be more convenient. The thing is, literally anyone could call. Like anyone, all you really need is the either the email/gmail/AOL, or the make and model of the phone, to answer some relatively personal questions (which you can lowkey guess ngl), or live in the same area or they just say screw it and change the number. It's often very useful but THE MOST ANNOYING THING when someone tries to access your account, and depending on WHEN and WHERE you get the card they don't even send you a confirmation text because they assumed your the one calling.
But anyways, you'd only need to realistically find out the first few numbers of her phone number, if you went with this method, trial and error'd it till you got on that's active and you can at minimum text, then just straight up try to login in or call them.
This is a great time to mentioned that Snapchat is lowkey, unintentionally screwing people over with this, because you can check if someone has a Snapchat by their contact or trying to sign in with that phone number cause it'll say the numbers is already in use.
BUT ANYWAYS, it takes about 2-6 weeks to gain access to someone's phone number or Gmail/AOL/Email if they're born pre-2000s to early 2000s
My point being, you could just guesstimate her really name by putting it through bots, checking old posts, being in personal contact with them or like reallllyyyyy putting the effort into guessing
And this is why people are often told to regularly update or change both passwords, email/gmail /AOL password and even update their names to avoid this.
5. Leandra made her social media around 2023, for her official Lovejoy shenanigans, idk what they do tbh
And I'm in no way calling her old... But she's gotta be like minimum 2-6 years older then me putting her in the bracket of people who can get a G/E/AOL (I'm getting tired of writing I tbh) with their actual names
And since 2-Step Verification was a 2025 update on TikTok, it's likely that some people just don't have it because they're too lazy to update or set it up. But even then their are many ways to get around it.
I recommend looking at the BBC guide/explanation of multi-factor verification/ two step verification/ multi-factor verification: https://www.bbc.co.uk/programmes/articles/5VbNf6z14LS7bZ02L1NXcjG/how-to-set-up-two-factor-authentication
And to Look at this BBC bitesize link if you want to know more: https://www.bbc.co.uk/bitesize/guides/zf3bcj6/revision/6
And 6. To follow up on some misconception that I know you're probably gonna throw at me because let's be real here you just hate Tubbo and that's okay. You don't need to justify it, just dislike him and be done.
Misconception 1. For some reason people are saying that her Instagram and Snapchat were also hacked. I don't know if she has a Snapchat because I don't use it, but as for Instagram it has been confirm by many update accounts, people who know irl etc... That the insta is fine!
Misconception 2. Tubbo kissed her. Hahahahhahashhsshshslolklolol. Tubbo is gay, and it's been confirmed by both parties that she kissed him first, and apparently he freaked tf out. Because he's gay. And has been openly gay for like 1-3 years. Bit weird to call him not gay for getting a kiss from one women. Like girl do you not kiss your mom? Tf? No kissing the homies? Terrible friend you are.
Misconception 3. Tubbo cleared the allegations as well as her after the allegations were out... Because how tf are you meant to clear something that's didn't exist?
Misconception 4. The hacker got a lucky guess. Now. Stay with me here. Go find an AI prompter and type 'man and women get drunk at part, write something criminal' OR just use your imagination because you know they're at the same party from a video a year ago. And I literally peeped into my older siblings room and asked them "real talk, a man and women get drunk at a party and leave together, they get to his place and something criminal happens, what is that criminal thing?" LITERALLY the first thing they suggested. Murder was second and tax evasion strats were 3rd.
And finally 7. This is too you. Yeah anonymous asker. You.
Just like DM me because as funny as it is to post about this on twitter and laugh with moots, your cluttering up my page with unnecessary discourse. But your not gonna see this, are you?
Because you, yourself said you didn't read past my first previous point. Sooooooooooooooooooooo
But also also ALSO, if she's confirmed it didn't happen and he confirmed it didn't happen, and she confirmed she was hacked, as shown in screenshots above and previously, then why is this still a talking issue?
SHE LITERALLY SAID SHE WAS HACKED. IT WASN'T HER POSTING??
Like if you gonna be mad at Tubbo be mad that he's idk fight Sapnap or something
But you seem more upset that I'm suggesting the hacker could POTENTIALLY be a gnf fan or Wilbur fan by the way they're uproaring on Twitter. Need I remind you, humbly and respectfully, IT'S FUCKING TWITTER??!
I keep people on the loop, I ain't asking for your what ifs ngl. questions? Welcome. Petty insults and challenge stupidity? Nope.
As you can see with MUCH of my covering discourse and discussion content on both Twitter and Tumblr, I put allegedly on thing that are not 90% to 100% accurate, I stick it on rumours and provide both links and screenshot to back up point because I want to be as honest as possible.
Bro if my favourite mcyt was an asshole I'd hold them too it. If my favourite vtuber was a bitch I'd hold them too it.
But I've provided ample evidence both in my first post and this post with detailed explanation, links and breaking it down into sections, I EVEN LINKED EDUCATIONAL RESOURCES AND EXPLAINED EMAIL LORE AND WHY MILLENNIALS ARE ACTUALLY QUITE OLD
Like it's done. It's over. You ignorance, lack of real world perception, common sense, and critical thinking skills has lead you to a pre-made conclusion that please you and not the actual one. So congrats. Wish I could be that stupid.
And for the record, I got a 100% in both GCSE coursework units on Information Technology, covering a range of different topics including cyber security, and scored a 90% on the test (trust it hurts your hand writing that much)
Furthermore, I backed it up with links, educational links and screenshots reinforcing literally what I said/how it applies.
Don't doubt my intelligence. Doubt your own suckerrrr
2 notes
·
View notes
Text
Some day, I am going to write more eloquently about how any system with a setup for defending against data security threats eventually devolves into treating its users as the threat, and this eventually *makes* these users a threat.
Some day.
For now, I just want to put this out here.
Picture a company. Let's say, a company that relies on external contractors for all of its IT development work. And I do mean, ALL OF IT.
This company has been doing a lot to increase their data security rating. Things like blocking people from accessing Gmail or Slack, making MS Teams chat unavailable for external employees, making it so externals cannot see anyone's agenda nor book meeting rooms, preventing usage of flashdrives, making a huge "data leak" hassle because an external developer had downloaded a file they needed for their work onto their own machine's desktop and a manager spotted this during a demo of the new development... You know, just corporate things. Cyber security swag.
Anyway.
Now picture this company has decided to get Next Level with their security.
Introducing: computers that only work if a "smart badge" is inserted, containing so much intrusive spyware that employees using them had to sign a legal document stating they are ok with that. Five fiery rings of hell to connect to a "secured" virtual workspace if working from home. Recording a Teams meeting? How about you just put a bomb in the server room, you terrorist. And most importantly... If you are not an internal payroll employee of sufficiently high rank...
YOU CAN NO LONGER SEND EMAILS WITH ATTACHMENTS.
...
...
So, how do you think people would respond?
...
Let me tell you: we are making fake user stories in Agile Accelerator and dropping our files in the Files section in order to share them with each other. Our manager is serving as our external postal office because she has hierarchical attachment sending clearance. We are classifying all our documents as "public" to minimize the hurdles.
We are becoming the threat, with grit teeth as we lose hours and days just trying to do our fucking job around all these "security features".
Cybersecurity? At this point I think a good fifth of my colleagues would click a phishing link On Purpose.
#cybersecurity#data security#working in it#work woes#it jobs#dys-functional analysis#every day I fight with corporate to just let me do what I am paid for#disaster thoughts#work shit#office life#cyber security#security theater#“what if the TSA -but for computers?” is no longer a hypothesis#i like our CISO as a person but I also want to wring his neck
2 notes
·
View notes
Text
Just rambling about how being online is these days...
For as long as I can remember, I've always been rather fatalistic about online privacy, security, etc.
At the end of the day, if governments (US, Russia, North Korea, etc.), big tech (Google, Facebook, Amazon), or a really determined hacker wanted in on my computer or online accounts, they're getting in eventually. This isn't to say I have anything useful other than the normal stuff people would have.
But seriously, something like 1/3 of the online world STILL uses Windows XP. Trying being online with XP these days and see how long it takes before you get something accessing your computer without authorization (it'll be like 10 minutes at most).
But that usually didn't stop me from taking basic security measures.
I never realized I had actually had a line in the sand with all of this.
Until Microsoft Copilot.
That was the final straw. Like, that broke something in me where I now spend many hours and days since early February essentially de-Googling and de-Big-Teching.
I've moved to Linux (Linux Mint on my daily driver, Kubuntu on my gaming rig, and Debian 12 for my home network) from Windows.
Moved away from Gmail to two different email services.
Switched so many apps on my phone from Google to FOSS apps. And when my phone finally stops getting any kind of security updates, I'll try to flash it with a custom ROM. If it bricks the phone, oh well, I'd have to get a new one eventually. But it buys me some more time with my phone AND isn't connected to Google, all the better.
Been using Collabora over Microsoft Office (trying to find a Google Workspace alternative has been an absolute chore and is still ongoing).
Installed Container extensions in Firefox for Google, Facebook, Amazon, & Reddit.
In the process of moving from Google Drive to two services with servers not in the US.
And the process continues.
I know some of this is a reaction to the lack of control I have in my life right now especially, given whom my employer is. And this is something I can at least exert a modicum of control, even if it is futile in the end.
But if it makes it harder for someone to track me for five more fucking seconds... WORTH IT.
Spite's a powerful motivator.
4 notes
·
View notes