#mobile device forensics
Text
Unlocking Secrets: Exploring Mobile Device Forensics with RIVICA in Australia
In the digital age, our smartphones have become an extension of ourselves, storing a wealth of personal and sensitive information. But what happens when that information is needed for legal proceedings or investigations? That's where mobile device forensics comes into play, and in Australia, RIVICA is leading the charge in offering expert forensic examination of mobile phones.
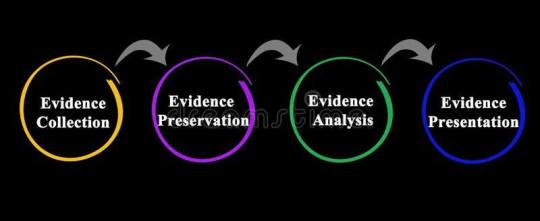
Mobile Device Forensics is not just about unlocking a phone or retrieving deleted messages; it's a meticulous process of extracting, analyzing, and interpreting digital evidence stored on mobile devices. As you delve into the world of forensic examination at RIVICA, you'll discover a team of skilled professionals equipped with cutting-edge tools and techniques to uncover the truth hidden within smartphones.
At RIVICA, the scope of Mobile Device Forensics extends far beyond traditional methods. Whether it's extracting call logs, recovering deleted photos, or decrypting encrypted data, our experts leave no stone unturned in their pursuit of uncovering crucial evidence. From criminal investigations to civil litigation, our forensic services are tailored to meet the unique needs of each case.
One of the key advantages of Mobile Device Forensics is its ability to provide irrefutable evidence that can withstand legal scrutiny. By following strict chain of custody protocols and employing forensically sound methodologies, RIVICA ensures that the integrity of the evidence remains intact throughout the examination process. This level of professionalism and expertise is invaluable in court proceedings, where the credibility of evidence can make or break a case.
But Mobile Device Forensics isn't just about solving crimes; it's also about protecting individuals and organizations from digital threats. By uncovering vulnerabilities and identifying potential security breaches, RIVICA helps clients safeguard their sensitive information and mitigate risks associated with mobile devices.
As technology continues to evolve, so too does the field of Mobile Device Forensics. At RIVICA, we remain at the forefront of this ever-changing landscape, constantly refining our techniques and methodologies to stay ahead of emerging threats and challenges. Whether it's analyzing data from smartphones, tablets, or other digital devices, our commitment to excellence ensures that our clients receive the highest standard of forensic services.
In Australia, RIVICA is synonymous with expertise and reliability in Mobile Device Forensics. With a track record of successful investigations and satisfied clients, we continue to set the benchmark for excellence in forensic examination of mobile phones. So, whether you're facing a legal dispute, conducting an internal investigation, or simply seeking peace of mind, trust RIVICA to unlock the secrets hidden within your mobile devices.
Contact -
Web - https://rivica.com.au/mobile-forensic-phone-examination/
Mail - [email protected]
Ph - 1300 748 422
Address - Level 5, 111 Cecil Street, South Melbourne, Australia
0 notes
Text
The Bezzle excerpt (Part VI)

I'm on tour with my new novel The Bezzle! Catch me TONIGHT in LA (Saturday night, with Adam Conover), Seattle (Monday, with Neal Stephenson), then Portland, Phoenix and more!

It's launch-week for my new novel The Bezzle, a high-tech, revenge-soaked crime thriller in which my intrepid forensic accountant Martin Hench must pit his wits against unbelievably evil (and sadly true-to-life) prison-tech grifters:
https://pluralistic.net/2024/02/14/minnesota-nice/#shitty-technology-adoption-curve
As part of the launch, I'm serializing part of Chapter 14, a side-plot about music royalty theft and the (again, sadly true-to-life) corruption of the LA Sheriffs Deputies, who are organized into criminal gangs that murder, run drugs and intimidate with impunity:
https://www.nbcnews.com/news/us-news/deputy-gangs-cancer-los-angeles-county-sheriffs-department-scathing-re-rcna73367
Today marks the sixth and final installment of the serial, but you can hear me read more of the book. Just show up at one of the stops on my book tour! Tomorrow (Feb 24) in LA, I'm appearing on Saturday evening with AdamC onover at Vroman's:
https://www.vromansbookstore.com/Cory-Doctorow-discusses-The-Bezzle<
And then on Monday I'll be in Seattle at Third Place Books with Neal Stephenson:
https://www.thirdplacebooks.com/event/cory-doctorow
From there, I'm off to Portland, Phoenix, Tucson and points further:
https://pluralistic.net/2024/02/16/narrative-capitalism/#bezzle-tour
Here's part one of the serial:
https://pluralistic.net/2024/02/17/the-steve-soul-caper/#lead-singer-disease
Part two:
https://pluralistic.net/2024/02/19/crad-kilodney-was-an-outlier/#copyright-termination
Part three:
https://pluralistic.net/2024/02/20/fore/#lawyer-up
Part four:
https://pluralistic.net/2024/02/21/im-feeling-unlucky/#poacher-turned-keeper
Part five:
https://pluralistic.net/2024/02/22/self-censorship/#acab
And now, the thrilling conclusion!

Benedetto was outraged by my face and swore he’d sue the Sheriff’s Department on my behalf. He got even angrier when I got stopped again, the following week, as I was leaving my concussion checkup at the Kaiser hospital on Sunset by a sheriff’s deputy who had me pull over in front of the big Scientology building. This deputy was a little bantam rooster of a fellow, with a shiny bald head and mirror shades and no neck. He strutted up to my car, got me out of it, ran my ID, and frisked me. “Do you know why I pulled you over, sir?” he said. He had that cop knack for making “sir” sound like “motherfucker.”
“No, sir,” I said, trying it out myself.
He didn’t like that and leaned in close enough for me to smell his aftershave and the scented sunscreen on his bare scalp.
“I stopped you, sir, because you were using your phone while driving.”
I must have looked surprised.
“I personally saw you tapping at your phone screen. That is a misdemeanor, sir. Reckless driving.”
He stopped as if waiting for me to respond. I made myself go mild. “Sir, I did not use my phone.”
He was waiting for that. He narrowed his eyes and leaned in closer. “Are you telling me I didn’t see what I saw?”
Mild, Marty, mild. “I don’t know what you saw, sir, but I didn’t use my phone.”
He rocked back and tilted his head. Patients went by with crutches and walkers. Nurses and doctors passed in scrubs. Scientologists scurried in and out of their gigantic temple. A fruit cart man labored past us.
“Well, sir, this should be simple enough to resolve.” He reached for his belt and pulled out a generic ruggedized cop-rectangle of gear, and unspooled a multiheaded cable from its side. He leaned into the rental and retrieved my phone, and squinted at its I/O port, then attached the cable to my phone. The rugged rectangle beeped. “I’m gathering forensics on your mobile device, sir,” he said.
I’d figured that out already. My phone—like yours and everyone else’s—was a trove of my most intimate information, a record of all the places I’d been and people I’d spoken to and all the things I’d said to them. It was full of photos and passwords and client files and voice memos. It was more information than any judge would have granted a warrant for on a reckless-driving rap.
The little man smirked as he held my phone and his gadget. I stayed mild as milk. I was running full-device encryption. I’m no computer security expert, but I spend a lot of time around them, and they’d been insistent on this point, and had made reference to this very scenario in describing why I would bother to dig around my phone’s settings to turn this on.
God, my face hurt. I didn’t know how long the gadget was supposed to take, but from the cop’s increasing impatience, I could tell it was going long.
Beep. The cop shaded the gadget’s little screen from the punishing LA sun with one hand and peered at it.
“Sir, I need you to unlock this device, please.”
My face hurt. Be mild, Marty. “I invoke my right to counsel,” I said.
He pursed his lips. “Sir, if you would please enter your unlock code, we can verify whether your device is in use and we can both be on our way.”
“I invoke my right to remain silent.” I said it straight into his bodycam.
He sighed and looked irritated. I had known Benedetto for so long that I had once had to dial his number from a landline. I’d long ago memorized his office’s number, 1–800-LAWER4U. He’d bought it early, back before 800 numbers got expensive, and he’d had plenty of offers for it. He’d kept it.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/23/gazeteer/#fin
#pluralistic#the bezzle#martin hench#marty hench#red team blues#fiction#crime fiction#crime thrillers#thrillers#technothrillers#novels#books#royalties#wage theft#creative labor#radical capital#trader joes#amazon#starbucks#spacex#nlrb#framework laptop#linkdumps
9 notes
·
View notes
Text
Decoding Cybersecurity: Unveiling the Future of US Digital Forensics Excellence
What is the Size of US Digital forensics Industry?
US Digital forensics Market is expected to grow at a CAGR of ~% between 2022-2028 and is expected to reach ~USD Mn by 2028.
Escalating cyberattacks targeting individuals, organizations, and critical infrastructure underscore the need for robust digital forensics capabilities. The increasing frequency and sophistication of these attacks drive the demand for advanced tools and expertise to investigate and respond effectively.
Rapid technological advancements, including IoT, cloud computing, AI, and blockchain, introduce new avenues for cyber threats. Digital forensics services are crucial to understanding these emerging technologies' vulnerabilities and mitigating associated risks.
Furthermore, stricter data protection regulations and compliance mandates necessitate thorough digital evidence collection, preservation, and analysis.
Organizations across industries has invested in digital forensics to ensure adherence to legal requirements and regulatory frameworks.
Additionally Legal proceedings increasingly rely on digital evidence. Law enforcement, legal firms, and corporations require robust digital forensics services to gather, analyze, and present evidence in a court of law, driving market expansion.
Us Digital Forensics Market By Type
The US Digital forensics market is segmented by Computer Forensics, Network Forensics, Mobile Device forensics and Cloud forensics. Based on type, Computer Forensics type segment is emerged as the dominant segment in US Digital forensics market in 2022.
Computers are ubiquitous in modern society, utilized across industries, organizations, and households. As a result, a significant portion of digital evidence related to cybercrimes and incidents is generated from computer systems, driving the demand for specialized computer forensics expertise. Computers and their software environments evolve rapidly.
Us Digital Forensics Market By End User Application
US Digital forensics market is segmented by Government and Defence, BFSI, Telecom and IT, Retail, Healthcare and Other Government and Defence market is dominant in end user application segment in Digital forensics market in 2022.
Government and defense agencies handle highly sensitive information related to national security and intelligence. The increasing sophistication of cyber threats targeting these entities necessitates robust digital forensics capabilities to investigate and respond to cyber incidents effectively.
Government and defense entities are prime targets for cyberattacks due to their critical roles. Effective incident response through digital forensics helps in containing and mitigating cyber incidents swiftly, minimizing damage and preventing further breaches.
US Digital forensics by Region
The US Digital forensics market is segmented by Region into North, East, West, South. In 2022, the dominance region is East region in US Digital forensics market.
The East region has a dense population and a well-established digital infrastructure, making it a hotspot for cybercriminal activity. The higher frequency of cyber threats and incidents necessitates a strong emphasis on digital forensics to investigate and mitigate these risks effectively. Additionally, the East region often sees a proactive approach from regulatory and legal bodies, reinforcing the demand for digital forensics services to ensure compliance and assist in investigations. The proximity of key players in law enforcement, government agencies, legal firms, and corporate headquarters further fuels the need for robust digital forensics capabilities.
Download a Sample Report of US digital forensics Solution Market
Competition Scenario in US Digital forensics Market
The US digital forensics market is characterized by a competitive landscape with several key players competing for market share. Prominent companies offering a range of digital forensics solutions and services contribute to the market's dynamism.
The competitive landscape also includes smaller, specialized firms and start-ups that focus on niche areas of digital forensics, such as cloud forensics, memory forensics, and industrial control systems forensics.
The competition is further intensified by the continuous evolution of technology, leading to the emergence of new players and innovative solutions. As the demand for digital forensics continues to grow, companies in this market are likely to invest in research and development to stay ahead of the curve, leading to a consistently competitive environment.
What is the Expected Future Outlook for the Overall US Digital forensics Market?
Download a Custom Report of US digital forensics market Growth
The US Digital forensics market was valued at USD ~Million in 2022 and is anticipated to reach USD ~ Million by the end of 2028, witnessing a CAGR of ~% during the forecast period 2022- 2028.
The US digital forensics market is poised for robust expansion due to the ever-evolving cybersecurity landscape, technological advancements, and regulatory pressures. Organizations across industries will increasingly recognize the necessity of investing in digital forensics to safeguard their digital assets and ensure compliance.
As long as cyber threats continue to evolve, the demand for sophisticated digital forensic tools, services, and expertise will remain on an upward trajectory.
The US digital forensics market appears promising, characterized by a confluence of technological advancements, increasing cyber threats, and growing legal and regulatory requirements. As technology continues to evolve rapidly, so does the nature of cybercrimes, creating a persistent demand for digital forensics solutions and services.
Additionally, the escalating frequency and complexity of cyberattacks. As more critical operations and personal information are digitized, the potential attack surface expands, leading to a higher likelihood of security breaches. This dynamic compels organizations and law enforcement agencies to enhance their digital forensic capabilities to investigate, mitigate, and prevent cyber incidents effectively.
Furthermore, the rise of emerging technologies like the Internet of Things (IoT), artificial intelligence (AI), and blockchain presents both opportunities and challenges. These technologies bring new possibilities for efficiency and connectivity but also introduce novel avenues for cyber threats. Consequently, the demand for digital forensics services is expected to surge as organizations seek expertise in unraveling incidents involving these cutting-edge technologies.
The market is also likely to see increased adoption of cloud-based digital forensics solutions. As more data is stored and processed in the cloud, digital forensic providers will need to develop tools and methodologies to effectively gather evidence from virtual environments, remote servers, and distributed systems.
2 notes
·
View notes
Text
Dead Ringing, Pt. 5
Outside the facility I dialed the bureau, reaching out to Akeno. Reception transferred and he picked up halfway through the first ring. "Warrick. Any leads?" Straight to the point as usual.
I huffed, shaking my head as if he could see it. "Yeah, possibly. I ah… I think this one is going to get a bit… complex. Mars is on her way back with a couple of samples. Make sure those get to forensics a-sap. You're also going to want to send a clean up crew. One body to collect."
"A body?" Akeno shuffled at his desk. "Hopefully not a body that could have provided us some answers?" I chuckled. Dry. Humorless.
"No, luckily. I guess. Ehhh~ One of the samples Mars is bringing in… this… device, whatever it is. It was attached to a cadaver's neck. I'm not sure how the hell it did what it did, but… the fucking corpse was mobile. Some kind of reanimator… or something. The thing was mentally unstable, it tore the chip off itself. I don't think this is going to be cut and dry."
Akeno was silent for a few moments, then sighed. "Well, shit. Alright. I guess you're good to go then. Lock it up and I'll get a crew on the way." After a beat, he asked. "And Mars? How was she?"
"Good eyes. Pleasant to work with. Better sense of humor than you. She'll do just fine." I smirked at the scoff on the other end of the line.
"Alright. Thanks, Warrick. I'll keep in touch. Keno out." The line clicked off and I tapped a claw over my pad's screen, bringing back up the security terminal for the facility. I enabled a lockdown override, tucked the pad in to a pocket and headed back toward the transit station, my thoughts churning over what had happened.
I didn't have the entire picture yet. Someone needed a whole lot of bodies. But for what? How did the chip that reanimated the corpse actually work? We were surprisingly lucky to have encountered a seemingly forgotten straggler. More than likely they were on a time table and couldn't afford to calibrate that individual unit as they made off with the rest. The erratic behavior would have been awful to deal with. According to storage records, sixty pods were brought out of stasis. That meant there were fifty-nine unaccounted for. Were they aware? Could they recall anything of their prior lives? I stopped halfway to the transit platform, staring straight ahead. Wait. Was I forgetting something? I furrowed my brow, whiskers wiggling. Shit. Yes, yes I was. We had checked inside. But we hadn't checked outside. Preoccupied. Foolish.
I turned and headed back toward cold storage.
Fifty-nine bodies didn't just walk out. Security had been disabled. Above ground camera footage was nonexistent for the time period. I wandered the perimeter of the building, making my way around back. Who ever had removed the bodies had been utilizing the maintenance halls. They connected to all levels of the facility. The easiest way in and out with that route would be the loading bays. Docks. Equipment and supplies didn't just get shuffled on in through the front door.
There was nothing out of the ordinary along the first few bay doors. The final one at the opposite end from where I'd started, however, bore some interesting differences. The first and glaringly obvious were the fresh tracks in the dirt road between segments of cracked pavement. Heavy tread. Large truck. The door itself was as pristine as the others. The keypad at its right was what caught my attention. The plating was ever so slightly skewed. I hated it when things didn't line up just right. They stood out to me. This was no different. I poked my claws around the edge of the pad, applying just enough pressure on either side. It popped loose, exposing wires and circuitry. For such a pristine facility and relatively high tech structure, it shouldn't have given so easily. It had been tampered with.
After replacing the panel I pulled out my data pad and shot jotted down a few notes as I followed the road up from the bays, following the short run of tracks in the dirt before coming to a stop again, staring down the road. It ran the perimeter of the dome before curving back in to the city ruins. I sent the update to Akeno. It really didn't give us any extra super important information, but I could at least pat myself on the back and not feel like I half assed my assignment. With a sigh, I headed for the transit station. Again.
The cleanup crew was just arriving as I rounded the building. A sentient avalanche separated from the vehicle, a tree trunk section splitting from itself, waving like an appendage. "Eeey, lookit who is! They still throwing scraps your ways, eh, mutt?" It turned out not to be a physical manifestation of the Swiss Alps wearing dark navy coveralls, but a large white furred bear. Polar variety. My lips curve with a smile and I strode over to clasp his hefty, warm paw in my own.
"Mori, you behemoth! Still slinging mops?"
"Hah! Only when newbies losing their lunch. Get to play seer over the parade now. Is nice. Pays more better." He hadn't let go of my hand and pulled me close, muzzles almost touching as he leaned down. His body was big enough to block the exchange from view of the rest of the crew. "Missing your company, wolf. Free for drinking soon, yeah?"
His snout brushed against mine and I leaned in to it, giving a little laugh as he kissed my cheek. "Yeah, that might be nice Mori… things've been in a bit of a slump lately and…"
The bear cut me off. "All more reason to be joining! Old Mori will help the troubles with washing away." Mori squeezed my hand tighter, nuzzling against my ear a bit before pulling back, clapping me hard enough on the shoulder to almost knock me off balance. A call from the vehicle had him looking over and grunting a command. When he turned back to me, he was all smiles again. "Favor yourself. Call your friend Mori soon, yes? Or he may just have to bring the drinking to you, mutt." He pressed his paw to the side of my face, a soft warmth lighting up his stoic features, thumb tracing the contour of my cheek. His eyes lingered on mine for a few moments before his paw dropped to my shoulder, giving it another squeeze before he turned and lumbered off toward the vehicle, waving an arm as he looked back with a grin. "Catch you."
"Y-yeah, heh. Catch ya." I huffed, rubbing my cheek, feeling a little flushed. With a chuckle and a shake of my head I waved and continued on. I was suddenly feeling very tired and glad the night would soon be over.
The small knot in my gut told me this was going to be one of those nights…
2 notes
·
View notes
Text
Data Recovery Provider Company

Data Recovery company employ different methods for data retrieval. When the client requires the data immediately, they may have to rely on one method whereas if they can be given time they might be able to test other cheaper methods as well. Our company offer all kinds of software and products to help in the recovery of data. Our Company range from large businesses to small shops and from dedicated shops that offer only data recovery services to other companies that offer a wide array of computer related products and services - Hard Disk Data Recovery.
Our experts have experience with many different storage technologies and can successfully recover data from the oldest to the most recent. Our data recovery specialists can access and extract photos and files from any portable storage media that has experienced a data loss. If you experience a data loss emergency at anywhere trust Now Data Recovery Services the world’s leader in data recovery. Backed by the our team, we have the knowledge and ability to address your data recovery needs - SSD Data Recovery.
We are specialized in the recovery of all kind of data from servers, database, desktops, laptop data recovery and pen drives etc. At Now Data Recovery, We concentrate on recovering data from all forms of devices. We maintain a high percentage of overall success rate, and our skilled team of expert always strive to discover innovative solutions to media failure issues. We provides you all types of data recovery services with ease, for over the years and now established as a well-reputed and reliable one with more than satisfied customers all over.
Whether you are an individual or representing an organization, we are going to tailor our digital forensics service to satisfy your wants. Recover accidentally deleted or shift deleted important files as well as emptied recycle bin unconsciously. We provide users with solutions for device content management, data recovery, password recovery, system repair, and other practical mobile phone and computer essentials. For more information please visit our site https://www.nowdatarecovery.com/
0 notes
Text
Best Data Recovery Malaysia
Data Recovery Services: We help recover data from various devices like HDDs, SSDs, RAID systems, mobile phones, and USB drives.
Experienced Team: Our team has skilled data recovery experts who can manage even tough data loss cases.
Modern Technology: We use advanced tools and technology in our special data recovery lab to achieve the best results.
Free Assessment: Get a free diagnosis of your storage device. This helps you understand how bad the issue is.
Safe Handling: We care about your data's safety. We keep everything confidential and use secure methods during the recovery process.
Clear Pricing: We offer clear and upfront pricing with no hidden fees. You can trust us for peace of mind.
We recovered data from HDD, SSD, Mobile Phone, Tablet, Cassette, CD, VCD, DVD, LTO Tape, Micro SD Card, SD Card, CFast Card, CF Card, CFexpress Card, Tape, Desktop, Laptop, NAS, PC, Server, and all types of storage devices
#data recovery malaysia#datarecoverymalaysia#data recovery#datarecovery#hard disk repair malaysia#data recovery kl#data recovery kuala lumpur#datarecoverykl#data recovery in malaysia#datarecoverykualalumpur
0 notes
Text
Cyber defense and ethical hacking

Cyber Defense and Ethical Hacking Course in Bangalore
Course Overview: This course provides an in-depth understanding of cyber security, combining principles of cyber defense with practical ethical hacking skills. Participants will learn how to protect digital assets from cyber threats while gaining hands-on experience in ethical hacking practices to identify and address security vulnerabilities.
Understanding Cyber Security:
1. What is Cyber Security? Cyber security refers to the practice of protecting computer systems, networks, and data from digital attacks, theft, or damage. It encompasses a range of technologies, processes, and practices designed to safeguard information integrity, confidentiality, and availability.
2. Importance of Cyber Security: In an increasingly digital world, cyber security is essential for protecting sensitive information from unauthorized access and ensuring the safe operation of networks and systems. Effective cyber security measures prevent data breaches, financial losses, and damage to an organization’s reputation.
3. Types of Cyber Threats:
Malware: Malicious software designed to harm or exploit systems, including viruses, worms, ransomware, and spyware.
Phishing: Fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity, often through email or fake websites.
Ransomware: A type of malware that encrypts data and demands a ransom payment for its release.
Advanced Persistent Threats (APTs): Prolonged and targeted cyber attacks where attackers gain unauthorized access to a network and remain undetected for an extended period.
4. Key Principles of Cyber Defense:
Confidentiality: Ensuring that information is accessible only to those authorized to view it.
Integrity: Protecting information from being altered by unauthorized individuals or processes.
Availability: Ensuring that information and systems are available to authorized users when needed.
5. Introduction to Ethical Hacking: Ethical hacking involves authorized and legal attempts to breach computer systems and networks to identify and fix security vulnerabilities. Ethical hackers, or white-hat hackers, use their skills to improve security rather than exploit it.
6. Tools and Techniques in Ethical Hacking:
Penetration Testing: A simulated cyber attack conducted to find and fix security weaknesses before malicious hackers can exploit them.
Vulnerability Scanning: Using automated tools to identify potential security flaws in systems and applications.
Social Engineering: Techniques used to manipulate individuals into divulging confidential information.
7. Incident Response and Management:
Incident Detection: Identifying and confirming security incidents or breaches.
Incident Response: Taking appropriate actions to contain and mitigate the impact of a security incident.
Forensic Analysis: Investigating and analyzing security incidents to understand the cause and prevent future occurrences.
Course Modules:
Cyber Security Fundamentals:
Introduction to key concepts and terminology
Overview of cyber threats and defense strategies
Network and Endpoint Security:
Protecting network infrastructure and devices
Implementing security measures for endpoints and mobile devices
Ethical Hacking Techniques:
Understanding hacking methodologies and tools
Conducting penetration tests and vulnerability assessments
Incident Response and Forensics:
Developing and executing incident response plans
Performing forensic investigations and evidence collection
Advanced Cyber Security Topics:
Threat intelligence and risk management
Compliance with regulatory standards and frameworks
Learning Outcomes: Upon completion, participants will:
Understand core cyber security principles and practices.
Be proficient in using ethical hacking tools and techniques.
Be capable of defending against and responding to cyber threats.
Have practical experience in both offensive and defensive cyber security roles.
Enhance your cyber security skills and advance your career with our Cyber Defense and Ethical Hacking Course in Bangalore. Secure your spot now and gain the expertise needed to protect digital environments against evolving cyber threats.
1 note
·
View note
Text
Ever wondered how fast you can get your broken phone fixed in Runcorn?Our centre is a pro at phone repair Runcorn. We offer top-notch mobile phone repair services that focus on being quick and dependable. Our skilled technicians work hard to fix a variety of devices, like iPhones and Samsungs. If your phone has a cracked screen or battery problems, we can help. We use real parts and offer a 12-month warranty, so you can trust your repair.There's a big need for mobile phone repair Runcorn services, thanks to our solid reputation. We've helped over 65,000 customers already. We're not just a repair shop; we're a team that cares about your time and happiness. If you bring your phone in before 1 PM, we can fix it the same day, so you can get back to what's important.For a reliable phone repair service Runcorn, we offer easy store visits and mail-in repairs. We want you to feel at ease, knowing your device is in good hands. We're all about quick, quality fixes.Key Takeaways
We provide fast, reliable phone repair services in Runcorn.
Our technicians are experienced and certified to handle various devices.
Same-day repairs are available for devices brought in before 1 PM.
We use only genuine parts and offer a 12-month warranty.
We have assisted over 65,000 satisfied customers.
Introduction to Expert Phone Repair ServicesIn Runcorn, we offer top-notch phone repair services for our community's needs. Our mobile repair services are quick and easy, fixing smartphones, tablets, and more. If your phone has a cracked screen, battery problems, or other issues, we can fix it fast.Our team has years of experience, ensuring every professional phone repair meets high standards. We have skilled technicians who are certified to give you the best service. They work fast, often fixing your device in under 30 minutes, so you can get back to your day quickly.For more details on our services, check out our service page. There, you'll see how we help customers with various repairs. We aim to provide reliable repairs for devices from top brands at great prices. Trust us for your phone repair needs in Runcorn1!Why Choose Us for Mobile Phone Repairs?We're the top phone repair service in Runcorn, offering quick and reliable fixes for your device. Our team has certified and skilled technicians ready to tackle various issues. You'll get clear pricing, so there are no surprises.Our shop is known for its easy service options, fitting your busy life. Whether it's a simple screen fix or complex repairs, we're here for you. We have services for all devices, ensuring your peace of mind.https://www.youtube.com/watch?v=3gPho0BbSJ8
Class
Description
Price Range
Class 1
Deleted data recovery (photos, videos, messages)
$195 - $490
Class 2
Failed updates, system corruption, boot problems
$195 - $790
Class 3
Screen damage, PCB repairs, chip extraction
$395 - $895
Class 4
Forensic recovery and data reconstruction
Quoted on a case-by-case basis
Choosing us means getting a service that's transparent, quality-focused, and easy to reach. Don't wait to contact us; we're ready to fix your mobile phone2!Our Range of ServicesWe offer a wide range of repair services in Runcorn for all your electronic devices. Our team is skilled in fixing smartphones, tablets, and more. We aim to provide top-notch solutions for your needs.Smartphone Repair RuncornOur services for smartphone repair in Runcorn cover cracked screens and battery replacements. We use high-quality parts and tools to fix your device. Your smartphone is crucial, so we work fast to get it back to you.Tablet Repair RuncornWe also fix tablets in Runcorn. Issues like a broken charging port or a faulty screen are no problem for us. We aim for quick repairs so you can use your device again soon.Other Device Repair ServicesWe don't just fix smartphones and tablets. Our services cover a variety of gadgets, meeting all your electronic repair needs. For more information, visit our services page.Quality and Certified RepairsWe're all about high-quality phone repair services.
We make sure your devices get the best care possible. Our certified repairs in Runcorn use genuine parts for better performance and longer life. We aim to keep your phone working well with quick fixes for common problems.We're committed to top-notch service with a warranty on all repairs. This means you can trust our affordable device repair to last. Our screen repairs start at just $89, making quality service affordable for everyone. For more info, check this link.
Service Type
Description
Starting Price
Screen Repair
Professional repair using high-quality parts
$89
Battery Replacement
Replacing drained batteries with certified components
$99
Software Repair
Resolving software glitches to enhance device functionality
$79
We work fast to get you back online quickly. Trust us for dependable repairs that keep your device running smoothly. Enjoy peace of mind with our quality service, supported by our expert team in Runcorn34.Fast and Reliable Phone Repair RuncornWe know a broken phone can mess up your day. That's why we offer quick phone repair Runcorn services fast. Our team works hard to fix most phones in under 30 minutes. This means less waiting and quick fixes for you.Being a reliable repair service Runcorn, we're all about being quick and careful. Our two skilled techs in Runcorn can fix screen cracks, battery problems, and more. Our fast mobile repairs are known for being quick, taking about 30 minutes for many fixes.We promise to fix it or you don't pay, giving you peace of mind. This promise shows our commitment to quality and trust in the community. Our happy customers stick with us, showing we're doing something right.We're open from 8am to 6pm, every day, making it easy for you to get help. You can pay with cash or credit card right away, making our fast mobile repairs hassle-free.We want to build strong relationships with our customers by offering good prices and staying up-to-date with technology. Our reliable repair service Runcorn gives top-notch service and keeps up with what our customers need.See the difference with our excellent quick phone repair Runcorn services today356!Common Phone Issues We FixMobile phones often face many challenges that can affect their performance. Our expert team is here to quickly and effectively solve these common phone problems. We fix everything from cracked screens to battery issues, making sure your phone works perfectly again.Cracked Screen Repair RuncornA cracked screen is a common issue we see. It not only makes your phone look bad but can also cause problems with how it works. Our cracked screen repair Runcorn service uses top-quality materials to fix your phone. This ensures it looks and works like new again. Our skilled technicians can handle all phone brands and models, offering quick and reliable repairs to get you back on track.Battery Replacement and IssuesBattery problems can really impact your phone's use. If your phone doesn't hold a charge or drains fast, it might need a new battery. Our experts are great at finding and fixing battery issues. They replace your battery carefully. Choosing us means getting a cost-effective way to extend your phone's life.https://www.youtube.com/watch?v=lIOyFL2Cn9w
Common Issue
Description
Service Offered
Cracked Screen
Physical damage resulting in cracks on the display
Cracked screen repair Runcorn
Battery Problems
Rapid drain or inability to hold charge
Battery replacement Runcorn
Charging Issues
Device not charging correctly or at all
Charging port repair and cleaning
Software Glitches
Frequent crashes or performance lags
Software troubleshooting and updates
7Affordable Phone Repair SolutionsWe know how vital it is to keep your device working well without spending too much. Our promise of affordable phone repair Runcorn means everyone can get quality service without a big bill. We aim to offer budget-friendly repairs that fit different needs while keeping our service high-quality.Our prices are set with our customers in mind.
For example, fixing a screen on popular phones costs between $100 and $230. These cost-effective phone services let you get great repairs without spending a lot, giving you the best for your money8.We're all about being quick and making our customers happy. Often, we fix phones in just 20 minutes, so you won't be without your device for long9. We can fix many issues, like water damage and battery problems, making us your go-to place for mobile repairs5.Customer Satisfaction GuaranteedAt our trusted phone repair shop, we put customer satisfaction in Runcorn first. We promise to make sure every client is happy, maybe even more than they expected. We're open and work closely with our clients at every step of the repair.Our team is full of experts who focus on top-quality repairs. We have support staff ready to help with any issues. We want to make sure you have a good experience by using skilled pros who know how urgent your needs are.We offer many services like computer tune-up, data recovery, and glass fixes. This means we cover all your tech needs in Runcorn10. Our reliable services get lots of positive feedback, showing we really care about making customers happy11.
Same-day service options
Transparent pricing with no hidden fees
Round-the-clock support for urgent inquiries
Choose us for expert service that fixes your problems well and fast. Contact us now and see how we value you at our phone repair shop.Guaranteed satisfaction is not just a promise; it's a commitment we stand by.Get in touch to see how we can fix your phone and give you a smooth service experience!Meet Our Expert Phone TechniciansOur team of expert phone technicians Runcorn is full of experience and skill. They are dedicated to giving you top service and keeping your devices safe. They keep learning about the newest repair methods to improve their skills.Your device is very important to you, and we get that. Our technicians can fix a wide range of problems, from simple screen fixes to complex hardware issues. They are always ready to tackle any repair with quality service.Our technicians are highly qualified and perform well. We aim to go beyond what customers expect, making us a trusted choice in Runcorn. We keep up with new tech to offer expert services that meet our customers' needs. For more info, check out this link.Our dedication to being the best is clear in every repair we do. Trust our professional phone repair team to fix your phone well and quickly. Choose us for the best in mobile phone repairs with our skilled technicians12!Convenience of Mobile Phone Repair ServicesWe know you want easy fixes for your mobile phone problems. That's why we offer convenient mobile repairs Runcorn. Our techs come to you for hassle-free repairs. You can get your device fixed at your place, without leaving.Our team covers Runcorn, so you don't have to travel far with a broken phone. Just pick a time that suits you, and we'll be there to help.We aim for quick and reliable service. Most fixes happen right there, so you can keep going with your day. This makes sure you're happy with our service.
Service Type
Average Time
Starting Cost
Screen Repair
Under 30 minutes
From $89
Battery Replacement
30 minutes
Starts at $89
General Repairs
Varies
Based on service
Our hassle-free phone repairs aim to give you peace of mind. We want your devices to work well and not disrupt your life. Enjoy repairs without leaving your home or office.Learn more about our services on our mobile repairs page. We're here to get your devices running smoothly again.
Our technicians are ready to fix your phone with care and precision.
13Our Workshop and Quality AssuranceAt our dedicated service centre, we're super proud of our workshop phone repairs Runcorn. Our workshop is fully equipped to fix all mobile phone issues. Our techs use the newest tools and tech to quickly and accurately find and fix problems.We focus a lot on quality assurance in repairs. Every phone gets the best care possible.
We check each repair carefully to make sure it meets our high standards. We promise to make sure you're happy with our service.We work fast and provide great customer service to reduce the hassle of fixing phones. Whether it's a new screen or fixing software, our team is here for you. Count on us to keep up our high-quality service.For more info on what we offer, check out our dedicated service centre14.Testimonials from Our Happy CustomersAt our phone repair shop in Runcorn, we're super proud of the feedback we get from our happy customers. The customer testimonials Runcorn show our dedication to quality and how our customers feel after we fix their devices.Many of our customers come back to us again and again, showing they trust us a lot. They tell their friends and family about us, which shows our work is top-notch. They also love how fast we get there and fix their problems.People often say great things about our phone repairs. They talk about our professionalism and how good we are at what we do. We make sure to explain things in a way that's easy for everyone to understand. And we think our prices are fair, making our services available to more people.
"I was impressed with the speed and professionalism of their service. I would definitely recommend them!"
"Norm arrived on time and fixed my phone quickly without any hassle! Highly satisfied!"
We really value the positive feedback we get. It shows us we're doing a great job and keeps us motivated to keep up the good work. It's great to see our customers happy and we promise to keep making their experiences rewarding.
Key Feedback Areas
Customer Comments
Customer Satisfaction Rate
High level of happiness and recommendation noted.
Technical Competence
Efficiently resolves issues with expertise.
Professionalism
Consistently praised for conduct and service quality.
Affordability
Competitive pricing that resonates well with clients.
This positive feedback proves we're the top choice for phone repairs in Runcorn. Our customer testimonials show our commitment and the trust our happy customers have in us15.Contact Us for Your Phone Repair NeedsNeed reliable phone repair services? Contact phone repair Runcorn today. Our team is ready to help with any repair questions you have. We know how important your devices are to you, so we aim to fix your phone quickly.You can easily get in touch with us by phone, email, or by visiting us. We promise a quick response and aim to make the repair process easy for you.We're proud to offer top-notch service and support for your mobile phone repairs. Feel free to reach out to us. We're here to fix your phone issues quickly and professionally51617.ConclusionWe're wrapping up our talk, showing our commitment to top-notch phone repair in Runcorn. Our focus is on fixing problems and making sure you're happy with our service. We aim to be your first choice for reliable phone repairs.Our skilled team can fix anything from a cracked screen to a faulty battery. We're proud of our quick and effective repairs, making us the top pick for mobile fixes in the area.We're excited to offer you excellent service for all your phone repair needs. We aim to keep our good name in Runcorn as your go-to for phone repairs. Your happiness is key, and we can't wait to add you to our list of satisfied customers18.FAQWhat types of phone repairs do you offer in Runcorn?We offer a range of repairs, like fixing smartphones, tablets, and other devices. If your screen is cracked or you need a new battery, we can help.How long does a typical phone repair take?Most repairs are done in about 30 minutes. We aim for quick and reliable service to get your devices back to you fast.Are your repair services affordable?Yes, our services are budget-friendly. We ensure you get top-notch repairs without spending too much.Do you provide a warranty for your repairs?Yes, all repairs come with a warranty. This gives you peace of mind and great value for your repair needs.Can you fix my phone on-site?Yes, we offer on-site repair services.
Our technicians can come to you, making repairs easy and stress-free.What should I do if my phone screen is cracked?Bring your phone to us for a quick fix. Our experts are ready to repair cracked screens efficiently.How do I contact you for phone repair inquiries?You can contact us through our website, email, or phone. We're here to help and aim to respond quickly to your questions.Are your technicians experienced?Yes, our team is made up of skilled technicians. They're well-trained in the latest repair techniques to take good care of your devices.What parts do you use for repairs?We use top-quality parts and certified components for repairs. This approach helps make your devices last longer.Can you repair my Samsung or iPhone?Yes, we're experts in fixing Samsung and iPhone devices in Runcorn. We offer a full solution for all your smartphone issues.
0 notes
Text
Transparent and Translucent Concrete Market Size, Share, Forecast [2032]
Transparent and Translucent Concrete Market provides in-depth analysis of the market state of Transparent and Translucent Concrete manufacturers, including best facts and figures, overview, definition, SWOT analysis, expert opinions, and the most current global developments. The research also calculates market size, price, revenue, cost structure, gross margin, sales, and market share, as well as forecasts and growth rates. The report assists in determining the revenue earned by the selling of this report and technology across different application areas.
Geographically, this report is segmented into several key regions, with sales, revenue, market share and growth Rate of Transparent and Translucent Concrete in these regions till the forecast period
North America
Middle East and Africa
Asia-Pacific
South America
Europe
Key Attentions of Transparent and Translucent Concrete Market Report:
The report offers a comprehensive and broad perspective on the global Transparent and Translucent Concrete Market.
The market statistics represented in different Transparent and Translucent Concrete segments offers complete industry picture.
Market growth drivers, challenges affecting the development of Transparent and Translucent Concrete are analyzed in detail.
The report will help in the analysis of major competitive market scenario, market dynamics of Transparent and Translucent Concrete.
Major stakeholders, key companies Transparent and Translucent Concrete, investment feasibility and new market entrants study is offered.
Development scope of Transparent and Translucent Concrete in each market segment is covered in this report. The macro and micro-economic factors affecting the Transparent and Translucent Concrete Market
Advancement is elaborated in this report. The upstream and downstream components of Transparent and Translucent Concrete and a comprehensive value chain are explained.
Browse More Details On This Report at @https://www.globalgrowthinsights.com/market-reports/transparent-and-translucent-concrete-market-100590
Global Growth Insights
Web: https://www.globalgrowthinsights.com
Our Other Reports:
Molded Foam Component Market MarketMarket
Rotogravure Printing Machine MarketMarket Share
Museum Software MarketMarket Growth Rate
RFID Smart Cabinets MarketMarket Forecast
Global Vertebroplasty And Kyphoplasty Devices MarketMarket Size
Inkjet Papers and Films MarketMarket Growth
Diabetic Macular Edema Treatment MarketMarket Analysis
Leadframe, Gold Wires and Packaging Materials for Semiconductor MarketMarket Size
Global Dental Plaster MarketMarket Share
Global Mead Beverages MarketMarket Growth
Laser Direct Structuring (LDS) Antenna MarketMarket
Biomass Boiler MarketMarket Share
RF-over-Fiber (RFoF) Solutions MarketMarket Growth Rate
Hydrographic Acquisition Software MarketMarket Forecast
Global Anesthesia Gas Evaporators MarketMarket Size
Industrial Wax MarketMarket Growth
Data Fabric MarketMarket Analysis
Cancer Vaccine MarketMarket Size
Global Tigecycline MarketMarket Share
Global Air Disinfection and Purification Machine MarketMarket Growth
Die-cast aluminum alloy MarketMarket
Automatic Identification and Data Capture MarketMarket Share
Period Panties (Menstrual Underwear) MarketMarket Growth Rate
Assistive Devices for Vulnerable Groups MarketMarket Forecast
Global Portable Gaming Console MarketMarket Size
Chromebook MarketMarket Growth
Infrared Detector MarketMarket Analysis
Demand Side Platforms (DSP) for Programmatic Advertising from the Mobile Side MarketMarket Size
Global Correlative Light Electron Microscopy (CLEM) for materials science (MS) MarketMarket Share
Global Forensic Technology MarketMarket Growth
Security Screening MarketMarket
Artificial Intelligence-Emotion Recognition MarketMarket Share
Bring-your-own-Device (BYOD) MarketMarket Growth Rate
Packaging Metallized Film MarketMarket Forecast
Global Neuromorphic Chip MarketMarket Size
Elliptical Waveguide Tools MarketMarket Growth
Child Backless Booster Seats MarketMarket Analysis
Hairline Powder MarketMarket Size
Global Popcorn Popper MarketMarket Share
Global 10G Laser Chips MarketMarket Growth
1 note
·
View note
Text
Virtual private investigator services for online fraud detection

In today's digital age, the role of a private investigator (PI) has evolved significantly. Traditionally known for conducting physical surveillance and gathering evidence through traditional means, modern PIs now harness the power of technology to offer virtual PI services. These services encompass a wide range of digital investigation techniques that are crucial in solving various types of cases remotely and discreetly.
Understanding Virtual PI Services
Virtual private investigator services, also known as online private investigator services or remote investigation services, utilize digital tools and techniques to gather information, conduct surveillance, and uncover facts relevant to a case. This shift towards digital methods has been driven by the increasing prevalence of online activities and digital footprints that individuals leave behind in today's interconnected world.
Key Components of Virtual PI Services
1. Digital Surveillance PI
Digital surveillance involves monitoring online activities, communications, and digital footprints of individuals or entities. PIs use advanced tools and techniques to track social media interactions, online transactions, email communications, and more. This form of surveillance is critical in cases involving cybercrime, online harassment, or digital fraud.
2. Cyber Investigator
A cyber investigator specializes in probing digital networks, databases, and online platforms to gather evidence related to cybercrimes such as hacking, identity theft, or data breaches. They employ forensic techniques to analyze digital evidence and trace digital trails left by perpetrators.
3. Virtual Fraud Detection
Virtual PIs play a crucial role in detecting and investigating online fraud schemes. They analyze financial transactions, examine digital records, and conduct background checks to identify fraudulent activities such as phishing scams, investment fraud, or online identity theft.
4. Internet Background Checks
Conducting background checks on individuals or businesses has become more accessible through virtual PI services. PIs can uncover information about a person's employment history, criminal records, social media presence, and reputation through online databases and public records.
5. Remote Infidelity Investigations
Infidelity investigations have also moved into the digital realm, where PIs can discreetly monitor online communications, track GPS locations through mobile devices, and gather evidence of extramarital affairs or relationship issues.
6. Online Asset Searches
For legal and financial matters, virtual PIs assist in locating hidden assets, conducting asset searches, and performing due diligence on businesses or individuals. This service is crucial in cases involving divorce settlements, business disputes, or financial investigations.
7. Virtual PI Consultations
Virtual PIs offer consultation services remotely, providing advice, strategy, and guidance based on their expertise in digital investigations. Clients can discuss their concerns, receive recommendations, and plan investigative strategies tailored to their specific needs.
Advantages of Virtual PI Services
Cost-Effectiveness: Virtual PI services often reduce overhead costs associated with traditional surveillance methods, such as travel expenses or stakeout operations.
Global Reach: PIs can conduct investigations globally, leveraging online tools and databases accessible from anywhere in the world.
Discreet Operations: Remote investigations allow PIs to gather information discreetly without arousing suspicion, ensuring confidentiality for clients.
Efficiency: Digital tools enable faster information gathering and analysis, speeding up the investigative process compared to traditional methods.
Ethical and Legal Considerations
While virtual PI services offer many advantages, ethical considerations regarding privacy and data protection are paramount. PIs must adhere to legal frameworks and regulations governing surveillance, data collection, and information disclosure to ensure their practices are lawful and ethical.
Conclusion
Virtual private investigator services have revolutionized the field of private investigation, offering innovative solutions to modern-day challenges. By embracing digital tools and techniques, PIs can conduct thorough, efficient, and discreet investigations that meet the diverse needs of their clients in an increasingly digital world.
As technology continues to evolve, so too will the methods and capabilities of virtual PIs, ensuring they remain at the forefront of investigative practices, safeguarding individuals, businesses, and communities from digital threats and deception.
0 notes
Text
How IT Security Services Improve Mobile Device Security
In today's digital age, mobile devices have become integral to our lives, serving as tools for communication, business transactions, entertainment, and more. As the use of mobile devices continues to grow, so do the risks associated with their security. Cyber threats such as malware, phishing, and data breaches are increasingly targeting mobile devices, making it imperative for individuals and organizations to invest in robust IT security services. This blog explores how IT security services improve mobile device security, highlighting the key strategies, technologies, and best practices involved.

The Growing Importance of Mobile Devices
Mobile devices, including smartphones, tablets, and wearables, have revolutionized our lives and work. They provide unprecedented convenience, allowing users to access information, communicate, and perform tasks on the go. However, this convenience comes with significant security challenges. Mobile devices often store sensitive data, such as personal information, financial details, and corporate data, making them attractive targets for cybercriminals.
The Threat Landscape
The threat landscape for mobile devices is constantly evolving. Common threats include:
Malware: Malicious software designed to damage or disrupt devices, steal information, or gain unauthorized access.
Phishing: Deceptive attempts to obtain sensitive information by masquerading as trustworthy entities.
Data Breaches: Unauthorized access to sensitive data, often resulting in data theft or exposure.
Man-in-the-Middle Attacks: Interception of communication between two parties to steal data or inject malicious content.
Device Theft or Loss: Physical loss or theft of devices, leading to potential data breaches.
Given these threats, it is crucial to implement comprehensive IT security services to protect mobile devices.
Key Components of Mobile Device Security
1) Mobile Device Management (MDM)
Mobile Device Management (MDM) is critical to mobile device security. MDM solutions enable organizations to manage and secure mobile devices, regardless of location. Key features of MDM include:
Device Enrollment: Automating the process of enrolling devices into the management system.
Policy Enforcement: Defining and enforcing security policies, such as password requirements and encryption.
Remote Wipe: Remotely erasing data on lost or stolen devices to prevent unauthorized access.
Application Management: Controlling the installation and use of applications on devices.
Compliance Monitoring: Ensuring devices comply with security policies and regulatory requirements.
2) Mobile Application Management (MAM)
Mobile Application Management (MAM) focuses on securing and managing applications on mobile devices. MAM solutions provide the following capabilities:
App Wrapping: Adding security layers to applications without modifying their functionality.
Containerization: Isolating corporate data and applications from personal data on the device.
App Distribution: Securely distributing applications to users through enterprise app stores.
Access Control: Managing user access to applications based on roles and policies.
App Analytics: Monitoring application usage and detecting potential security risks.
3) Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions provide real-time monitoring and analysis of endpoint activities, including mobile devices. EDR solutions offer:
Threat Detection: Identifying and responding to security threats in real time.
Behavioural Analysis: Analyzing device behaviour to detect anomalies and potential threats.
Incident Response: Automating incident response actions, such as isolating compromised devices.
Threat Intelligence: Integrating intelligence feeds to stay updated on the latest threats.
Forensics: Conducting forensic analysis to understand the scope and impact of security incidents.
4) Mobile Threat Defense (MTD)
Mobile Threat Defense (MTD) solutions are designed to protect mobile devices from various threats. MTD solutions provide:
Malware Detection: Identifying and blocking malware on devices.
Phishing Protection: Detecting and preventing phishing attacks.
Network Security: Securing device communication over Wi-Fi, cellular, and VPN connections.
Vulnerability Management: Identifying and addressing vulnerabilities in the device and applications.
Compliance Enforcement: Ensuring devices comply with security policies and industry regulations.
5) Encryption and Data Protection
Encryption is a fundamental aspect of mobile device security. It ensures that data stored on devices and transmitted over networks is protected from unauthorized access. Key encryption practices include:
Device Encryption: Encrypting data stored on the device to protect it in case of theft or loss.
App Encryption: Encrypting data within applications to ensure data privacy and integrity.
Communication Encryption: Using encryption protocols such as SSL/TLS to secure data in transit.
Cloud Encryption: Encrypting data stored in cloud services to protect it from unauthorized access.
6) Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) enhances mobile device security by requiring multiple verification forms for user authentication. MFA can include:
Something You Know: Passwords or PINs.
Something You Have: One-time passwords (OTPs) sent to a mobile device or generated by an authenticator app.
Something You Are: Biometric factors such as fingerprints or facial recognition.
MFA adds an extra layer of security, making it more difficult for unauthorized users to access devices and data.
Benefits of IT Security Services for Mobile Devices
1) Enhanced Security
IT security services provide comprehensive protection against various threats, ensuring mobile devices are secure from malware, phishing, data breaches, and other attacks. By implementing robust security measures, organizations can safeguard sensitive data and maintain the integrity of their mobile infrastructure.
2) Improved Compliance
Regulatory compliance is a critical consideration for many organizations. IT security services help ensure mobile devices comply with industry regulations and standards, such as GDPR, HIPAA, and PCI-DSS. This reduces the risk of non-compliance penalties and enhances the organization's reputation.
3) Increased Productivity
Security incidents can disrupt business operations and reduce productivity. IT security services minimize the risk of such disruptions by providing proactive threat detection and response. This allows employees to work efficiently without interruptions, ultimately improving overall productivity.
4) Reduced Risk of Data Breaches
Data breaches can have severe consequences, including financial losses, legal liabilities, and reputational damage. IT security services help prevent data breaches by implementing robust security measures like encryption, MFA, and real-time threat detection. These measures reduce the risk of unauthorized access to sensitive data.
5) Streamlined Management
Managing mobile device security can be complex and time-consuming. IT security services streamline this process by providing centralized management and automation. This simplifies the administration of security policies, device configurations, and compliance monitoring, allowing IT teams to focus on strategic initiatives.
6) Enhanced User Experience
Security measures should not compromise the user experience. IT security services balance security and usability, ensuring users can access the resources they need without friction. This enhances user satisfaction and encourages the adoption of security best practices.
Implementing IT Security Services for Mobile Devices
1) Assessing Security Needs
The first step in implementing IT security services for mobile devices is to assess the organization's security needs. This involves identifying the types of data stored on mobile devices, the potential threats, and the regulatory requirements. A thorough assessment helps determine the appropriate security measures and technologies to implement.
2) Selecting the Right Solutions
Numerous IT security solutions are available, each with its strengths and capabilities. Organizations should carefully evaluate different solutions based on their needs and choose the best protection. Considerations include:
Integration: Compatibility with existing IT infrastructure and applications.
Scalability: Ability to scale with the organization's growth and changing needs.
Ease of Use: User-friendly interfaces and straightforward deployment.
Support: Technical support and regular updates are available.
3) Developing Security Policies
Security policies are essential for defining the rules and guidelines for mobile device usage. Policies should cover aspects such as:
Device Enrollment: Procedures for enrolling devices into the management system.
Password Requirements: Guidelines for creating and managing strong passwords.
App Usage: Rules for installing and using applications on devices.
Data Protection: Measures for protecting sensitive data, including encryption and backup.
Incident Response: Procedures for responding to security incidents and breaches.
4) Training and Awareness
Security is only as strong as its weakest link, which is often the end-user. Organizations should invest in training and awareness programs to educate employees about best practices for mobile device security. Topics to cover include:
Recognizing Phishing Attempts: Identifying and avoiding phishing emails and messages.
Safe App Usage: Downloading and using applications from trusted sources.
Password Management: Creating and managing strong, unique passwords.
Incident Reporting: Reporting lost or stolen devices and suspicious activities.
5) Continuous Monitoring and Improvement
Mobile device security is an ongoing process that requires continuous monitoring and improvement. Organizations should regularly review their security measures, conduct vulnerability assessments, and update their security policies to address emerging threats. Continuous monitoring and improvement help maintain a robust security posture.
6) Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are increasingly important in mobile device security. AI and ML can analyze vast amounts of data to identify patterns, detect anomalies, and predict potential threats. Future trends in AI and ML for mobile device security include:
Advanced Threat Detection: Using AI and ML to identify sophisticated threats and zero-day vulnerabilities.
Behavioral Analytics: Analyzing user behaviour to detect unusual activities and potential security risks.
Automated Response: Automating incident response actions based on AI and ML analysis.
7) Zero Trust Security
Zero Trust Security is a security model that assumes no trust for any device, user, or network, regardless of their location. Zero Trust Security principles include:
Continuous Verification: Continuously verifying the identity and trustworthiness of devices and users.
Least Privilege: Granting the minimum necessary access to resources based on roles and responsibilities.
Micro-Segmentation: Dividing the network into smaller segments to contain potential breaches.
Zero Trust Security is becoming increasingly relevant for mobile device security, especially in remote work environments.
8) 5G Technology
The rollout of 5G technology is set to transform mobile device security. 5G offers faster speeds, lower latency, and increased connectivity but introduces new security challenges. Future trends in 5G and mobile device security include:
Network Slicing Security: Securing different slices of the 5G network to prevent unauthorized access.
IoT Security: Protecting the growing number of IoT devices connected through 5G networks.
Edge Computing Security: Ensuring the security of data processed and stored at the network edge.
9) Biometric Authentication
Biometric authentication methods like facial recognition and fingerprint scanning are becoming more prevalent in mobile device security. Future trends in biometric authentication include:
Multi-Modal Biometrics: Combining multiple biometric factors for enhanced security.
Behavioural Biometrics: Analyzing behavioural patterns, such as typing speed and touch gestures, for continuous authentication.
Privacy-Preserving Biometrics: Implementing privacy-enhancing technologies to protect biometric data.
10) Regulatory Compliance
Regulatory compliance will continue to be a significant factor in mobile device security. Future trends in regulatory compliance include:
Global Data Protection Regulations: Adapting to evolving data protection regulations like GDPR and CCPA.
Industry-Specific Standards: Complying with industry-specific security standards, such as HIPAA for healthcare and PCI-DSS for finance.
Cross-Border Data Transfers: Ensuring compliance with regulations governing cross-border data transfers.
Mobile device security is a critical aspect of modern IT security. As mobile devices become more integral to our personal and professional lives, robust security measures are paramount. IT security services play a vital role in protecting mobile devices from a wide range of threats, ensuring compliance with regulations, and enhancing user productivity.
By implementing Mobile Device Management (MDM), Mobile Application Management (MAM), Endpoint Detection and Response (EDR), Mobile Threat Defense (MTD), encryption, Multi-Factor Authentication (MFA), and other security measures, organizations can safeguard their mobile devices and sensitive data. Continuous monitoring, training, and awareness programs further strengthen the security posture.
Future trends in mobile device security, such as AI and ML, Zero Trust Security, 5G technology, biometric authentication, and regulatory compliance, will shape the landscape. By staying informed about these trends and adopting proactive security strategies, organizations can navigate the evolving threat landscape and ensure the security of their mobile devices in the digital age.
#mobile device security#cyber security#data security#mobile Security#mobile Security services#information technology#global health news#technology news#technology industry#technology integration
0 notes
Text
The global demand for Digital Forensics was valued at USD 9817.2 Million in 2023 and is expected to reach USD 29964.3 Million in 2032, growing at a CAGR of 13.20% between 2024 and 2032.In the digital age, where every aspect of life is increasingly mediated by technology, the importance of digital forensics cannot be overstated. Digital forensics involves the investigation and analysis of digital devices and data to gather evidence that is admissible in legal proceedings. This field has seen remarkable growth in recent years, driven by the surge in cybercrime, regulatory compliance requirements, and the widespread adoption of digital devices across various sectors.
Browse the full report at https://www.credenceresearch.com/report/digital-forensics-market
Market Dynamics
The global digital forensics market has been expanding rapidly, with a compound annual growth rate (CAGR) projected to exceed 10% over the next few years. This growth is fueled by several factors, including the rising incidents of cyber-attacks targeting organizations of all sizes, from small businesses to multinational corporations. As cyber threats become more sophisticated, there is an increasing need for advanced digital forensics tools and techniques to detect, analyze, and mitigate these threats effectively.
Key Trends
One of the prominent trends in the digital forensics market is the integration of artificial intelligence (AI) and machine learning (ML) algorithms into forensic analysis tools. These technologies enable faster and more accurate analysis of large volumes of data, helping forensic investigators identify patterns and anomalies that may indicate malicious activity.
Another significant trend is the adoption of cloud-based forensic solutions. As more businesses move their operations to the cloud, there is a growing demand for forensic tools that can effectively investigate data stored in cloud environments while maintaining chain of custody and adhering to legal requirements.
Challenges
Despite its growth prospects, the digital forensics market faces several challenges. One of the primary challenges is the rapid evolution of technology itself. New devices, operating systems, and communication protocols constantly emerge, posing challenges for forensic investigators to keep pace with technological advancements and acquire the necessary skills and tools.
Moreover, ensuring the integrity and authenticity of digital evidence remains a critical challenge in forensic investigations. Admissibility of digital evidence in court often hinges on demonstrating the reliability of forensic techniques and maintaining a clear chain of custody from the crime scene to the courtroom.
Future Prospects
Looking ahead, the future of the digital forensics market appears promising. As governments worldwide introduce stricter data protection regulations and cybersecurity laws, organizations are expected to invest significantly in digital forensics capabilities to ensure compliance and mitigate legal risks.
Furthermore, the proliferation of Internet of Things (IoT) devices and the expansion of digital footprints across social media platforms are anticipated to create new opportunities for forensic investigators. These developments will necessitate innovative forensic tools and methodologies to extract, analyze, and interpret digital evidence from diverse sources.
Key Players
Forensicon
R3 Digital Forensics
FireEye, Inc.
ACCESS DATA
Cy4or Legal Limited
Binary Intelligence, LLC
Kroll
LogRythm, Inc.
Magnet Forensics
Global Digital Forensics Inc.
Segmentation
By Type of Digital Forensics:
Computer Forensics
Mobile Device Forensics
Network Forensics
Cloud Forensics
By Tools and Software:
Forensic Analysis Software
Data Recovery Tools
Forensic Imaging Tools
By Component:
Hardware
Software
Services
By Deployment Type:
On-Premises Digital Forensics Solutions
Cloud-Based Digital Forensics Solutions
By End-User:
Law Enforcement
Enterprise
Government
Military
By Application:
Criminal Investigation
Cybersecurity Incident Response
Litigation Support
Employee Misconduct
By Industry Vertical:
Financial Services
Healthcare
IT and Telecommunications
Government and Defense
By Region
North America
The U.S.
Canada
Mexico
Europe
Germany
France
The U.K.
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
South-east Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of the Middle East and Africa
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
0 notes
Text
Toolbox Application to Support and Enhance the Mobile Device Forensics Investigation Process
Opinion
Throughout the study on the topic regarding Mobile Device Forensics, the authors noticed the different challenges that arise from the digital investigation associated with this science. Moreover, to address these different challenges, namely, the ones regarding the lack of documentation, standardization and research on this science Chernyshev et al. [1]; Barmpatsalou et al. [2]; Omeleze and Venter [3], the authors studied not only the Forensics field but also the Digital and Mobile Forensics ones, in other to understand the different and critical challenges that are jeopardizing and affecting the accuracy and integrity of these types of sciences and its investigations. As such, the authors proposed to study this field by firstly performing a systematic literature review using the PRISMA Methodology (presented in the chapter from the authors, Bernardo B and Santos V [4] and secondly building a toolbox application to support and enhance the Mobile Device Forensics investigation process, by analyzing, describing, and constructing an architecture and its contents.
Read More About This Article: https://crimsonpublishers.com/fsar/fulltext/FSAR.000619.php
Read More Crimson Publishers Google Scholar Articles: https://scholar.google.com/citations?view_op=view_citation&hl=en&user=BcljX0IAAAAJ&cstart=20&pagesize=80&authuser=1&cit crimsonpublishers ation_for_view=BcljX0IAAAAJ:_Ybze24A_UAC
0 notes
Text
Keystroke Recorders: A Comprehensive Guide To Monitoring Software

Keylogger is a type of surveillance tool used to monitor and record keystrokes typed on a computer keyboard. These tools are designed to capture every keystroke entered by a user, including passwords, emails, instant messages, and other sensitive information. Keystroke recorders can be either hardware-based devices connected to the computer's keyboard or software installed discreetly on the computer's operating system.
The primary purpose of these recorders varies widely. In legitimate contexts, they may be used by employers to monitor employee productivity and ensure compliance with company policies. They can also be utilized by parents to supervise their children's online activities and protect them from potential dangers on the internet.
However, it also raises significant privacy concerns. When used without consent or for malicious purposes, they can infringe on individuals' privacy rights and compromise sensitive personal information. Cybercriminals may deploy recorders as part of phishing attacks or to steal login credentials and financial data for illicit purposes.
Keystroke Monitoring Software
Keystroke monitoring software, often referred to as keyloggers, is designed to track and record every keystroke typed on a computer or mobile device. This type of software captures all keyboard inputs, including passwords, messages, emails, and other text entered by the user. Keystroke monitoring software can operate in stealth mode, making it difficult for users to detect its presence.
Legitimate uses of keystroke monitoring software include monitoring employee productivity, ensuring compliance with company policies, and parental supervision of children's online activities to protect them from potential dangers. In corporate settings, employers may use these tools to prevent insider threats, monitor sensitive information, and maintain cybersecurity protocols.
However, the use of keystroke monitoring software also raises significant privacy concerns. When deployed without consent or proper authorization, it can infringe on individuals' privacy rights and compromise sensitive personal information. Malicious actors may exploit keystroke monitoring software for cybercrime activities, such as stealing login credentials, financial data, or conducting espionage. It also lets you manage multiple projects effectively.
Benefits Of Record Keystrokes
Monitoring Employee Productivity: Employers can use keystroke recording to track employees' work activities and ensure they are focused on productive tasks. This helps in identifying potential inefficiencies and improving overall workflow management.
Security Monitoring: Keystroke recording can be part of a comprehensive security strategy to detect unauthorized access attempts or suspicious activities. By capturing keystrokes, organizations can monitor for unusual patterns that may indicate security breaches or insider threats.
Compliance And Policy Enforcement: In regulated industries, such as finance or healthcare, keystroke recording can help ensure compliance with industry standards and legal requirements. It enables organizations to maintain records of communications and transactions conducted on company devices.

Parental Supervision: Parents may use keystroke recording to monitor their children's online activities and protect them from exposure to inappropriate content or interactions. It allows parents to identify potential risks and initiate conversations about internet safety.
Forensic Investigations: In forensic investigations, keystroke recording can provide valuable evidence in cases involving cybercrimes, fraud, or other illegal activities. It helps investigators reconstruct digital actions and establish a timeline of events. Monitoring tool also provides its user with a perfect Weekly Activity Report.
Software To Record Keystrokes
Software to record keystrokes, commonly known as keyloggers, is available for various purposes ranging from legitimate monitoring to malicious activities. Legitimate keystroke recording software is often used by employers for employee productivity monitoring, parental controls for safeguarding children online, and by law enforcement agencies for forensic investigations. These tools capture every keystroke typed on a keyboard, including passwords, messages, and other text input, providing detailed logs for analysis.
Also Watch: Leading Employee Engagement and Workforce Productivity Tool
youtube
Conclusion
keyloggers serve as powerful tools for monitoring and recording keystrokes on computers and mobile devices. They are employed in various legitimate contexts such as employee monitoring, parental supervision, and forensic investigations. By capturing all keyboard inputs, including passwords and messages, these tools provide valuable insights into user activities and behaviors.
However, the use of Keystroke recorders raises significant privacy concerns and ethical considerations. It's essential for organizations and individuals to deploy such monitoring software responsibly, ensuring compliance with privacy laws and regulations. Transparency and informed consent are crucial aspects to uphold individuals' rights and maintain trust in monitoring practices.
#Keystroke monitoring software#often referred to as keyloggers#is designed to track and record every keystroke…#Youtube
0 notes
Text

Digital Forensicsis a branch of forensic science focused on the recovery and investigation of material found in Digital Forensics devices, often related to computer crime. The field is important in solving crimes that involve digital mediums like unauthorized data access, cyber attacks and fraud. The digital forensics experts in digital forensics employ a variety of techniques and tools to collect, preserve and analyze data from computers, mobile devices and networks in a way that maintains the integrity of evidence
0 notes
Text
The Evolution of Digital Forensics in the Age of Cyber Threats
Digital forensics is a crucial field in modern cybersecurity and law enforcement, focusing on the recovery, analysis, and preservation of electronic data for use in investigations and legal proceedings.
This discipline involves the use of advanced techniques and tools to uncover digital evidence from a variety of sources, including computers, mobile devices, networks, and cloud environments. Digital forensics experts meticulously trace digital footprints, reconstructing events and identifying perpetrators in cases of cybercrime, data breaches, and other digital misconduct. The process requires a deep understanding of both technology and legal protocols to ensure that evidence is collected and handled in a manner that maintains its integrity and admissibility in court. As cyber threats become increasingly sophisticated, the role of digital forensics is expanding, with professionals continually developing new methods to keep pace with evolving technologies and tactics used by cybercriminals. Additionally, digital forensics is instrumental in corporate environments for internal investigations, compliance audits, and incident response, helping organizations protect their assets and reputation. The field's importance is further highlighted by the growing emphasis on data privacy and protection, making digital forensics a cornerstone of modern investigative and cybersecurity efforts.
#DigitalForensics #CyberSecurity #DigitalEvidence #CyberCrime #DataRecovery #ForensicAnalysis #ElectronicData #IncidentResponse #DataBreach #CyberInvestigation #TechInForensics #ForensicTechniques #LegalForensics #CyberThreats #DataIntegrity #ForensicExperts #PrivacyProtection #CorporateForensics #ComplianceAudit #DigitalFootprints
0 notes