#powershell check website content
Explore tagged Tumblr posts
Text
Powershell Script for Website Availability Monitoring with Excel Report as output
Powershell Script for Website Availability Monitoring with Excel Report as output
In our previous post we already discussed about “How to check response code from a website using PowerShell“ by using single URL in example. Here let we discuss how to read the list of URLs from the text file and validate the list of URL . Finally script will generate the Excel file with the output result.
$URLListFile = "D:\PowerShell\URLList.txt" #Reading the list of URLs from the URLList.txt…
View On WordPress
#dotnethelpers.com thiyagu powershell dotnet-helpers.com#powershell check if website is started#powershell check website content#powershell get http response#powershell ping website#powershell script for website availability monitoring / url monitoring#Powershell Script for Website Availability Monitoring with Excel Report as output#powershell script to check url status#script to check website status#website monitoring script windows
0 notes
Text
2 Free Ways To Convert MP4 To Wav On-line And Offline
Is the quickest and best option to convert audio to video on-line. An audio file converter is one form of file converter that (surprise!) is used to transform one sort of audio file (like an MP3 , WAV , WMA , and so forth.) into another sort of audio file. You possibly can play around with the settings too because each format has a profile equipment and a preset editor, giving you extra control over your conversions. , the people behind VLC, have additionally put together a sequence of script files that use PowerShell or CMD in Home windows or the terminal in Linux to batch convert tiles in VLC. The files might be performed again in QuickTime, Home windows Media Player, Wav Player and some other applications. As soon as your information are chosen, click on the Open" button within the lower-proper corner to add the file to the conversion queue. Furthermore, it helps on-line database lookups from, e.g., Discogs, MusicBrainz or freedb, permitting you to mechanically collect correct tags and obtain cover artwork for your music library. Besides online converter to switch MP4 format to WAV format, this text additionally prepares 2 wonderful packages. If it's good to ceaselessly convert files or a lot of recordsdata at once, we suggest spending between $20 and $30 on a program that does not crash typically and may batch convert multiple information at once. On the Format Manufacturing unit popup you will simply click on the "OKAY" button, unless of course you want to add one other file. What's more, it allows users to transform their audio file between various audio codecs, together with WMA, WAV, AAC, OGG, MP3, M4A, etc. To know extra about our audio edit expertise, please go to On-line Audio Converter web page. The Wav, Mp4, Ogg, APE, FLAC, AAC normalization and check is fulfilled on a peak degree (Peak Normalization) and on an average degree (RMS normalization). As a substitute of eradicating the DRM encryption, Tunebite data the audio or video file and converts it to a format you should utilize on any media player. This is how to batch convert media recordsdata in VLC. Audio file converter tools are additionally helpful in case your favourite music app in your telephone or pill does not help the format that a new track you downloaded is in. An audio converter can convert that obscure format right into a format that your app helps.

You can also use MP4 to WMA converter to transform audio information like MP3, WMA, WAV, OGG, FLAC, M4A, MP2, and many others. By default the MP4 muxer writes the 'moov' atom after the audio stream ('mdat' atom) at the finish of the file. WAV files are mostly used on Home windows platform, being supported by Home windows Media Players and other applications. You possibly can add audio (in mp3 format) to a video file (avi, mp4, mov, wmv). I believe different individuals would have different opinions in direction of issues, so you can produce other options like the online converters. Simply add your movies to the software and convert information in a daily manner. However, if you must convert an audio file using your phone, these are the best options. Your file will likely be transformed and added to the iTunes playlist you created. AAC is a patented audio-format that has increased capabilities (variety of channels, discretion frequency) as in comparison with MP3. At times, you might have acquired your favourite trailers inmp4 extension from video-sharing websites, and needed to converted intowav to play on a media participant with better high quality. The right way to reduce the file measurement of MP3 information. In easy terms, a format might be in comparison with a container during which a sound or a video sign might be stored utilizing a specific codec. A free net app that converts video files, allowing you to alter the video format, decision or size right in your browser. ITunes would start converting M4A to WAV format. The default content of a WAV file is uncompressed (although they can be utilized to retailer compressed formats comparable to MP3), pulse code modulated (PCM) digital samples derived from the analog supply. It supports a protracted list of 26 audio enter codecs including MP3, WAV, FLAC, and AAC. Examine the highest box in order for you Cloud Convert to send the resulting MP3s on to your Dropbox, Google Drive, OneDrive, or Box account after the conversion is complete. A number of the output audio formats it support includes MP3, WMA, WAV, FLAC, MP4, MPC, OPUS, and over 20 more formats. It's also possible to set advanced options for both conversions which let you rotate the video, cut it, change the display size, change the bitrate of the downloaded audio and extra. Choose the item and click on the Open" button to import the audio into the application. It only lists formats which belong to the group of supported files, however with unsupported options. You possibly can upload distant audio recordsdata via their direct URL in addition to information stored in your Google Drive account. Hit Add" button and select the files you want to convert, and then click Open" to upload recordsdata. Convert video and audio files to OGV (Ogg video) format. Choose ".mp3" from the drop-down selector.

It could also rip CDs and convert online flash videos to audio, too. You can select among a few codecs, such as WAV, MP3, Ogg, MP4, FLAC, APE and others, and also rip audio CDs to the computer. It has a straightforward-to-use interface and wav to mp4 converter with image batch converts and exports in a lot of the fashionable formats, like MP3, WAV, ACC and FLAC. Furthermore, under the video preview window, "Merge Output Video" choice could be checked for batch MP4 to WAV conversions. Convert your audio like music to the WAV format with this free on-line wav to mp4 converter with image converter.
1 note
·
View note
Text
Technize supported by its audience. When you buy through links on our site, we may earn an affiliate commission. Learn more.HomeSoftware7 Best Ninite Alternatives for 2022
7 Best Ninite Alternatives for 2022
Updated on October 4, 2022Prayas ChakmaSoftware
If you need to install Windows on a computer or bunch of computers then you’ll likely want to install many applications that you use frequently. To install each of these applications individually takes a lot of time and it is pretty dull sitting there watching the process. Surely there is a better solution?
Most people will use Ninite for the installation of multiple apps on their Windows computers. Two experienced programmers who wanted to help people install their favorite applications without having to do any work developed Ninite. They wanted to help people to go and do something else while Ninite was busy installing everything.
Since the release of Ninite, it has become the number one choice for people that want to install popular applications on Windows computers. You can choose which applications you want from a large list which includes:
Google Chrome and Firefox Web Browsers
Skype, Trillian and Discord messaging apps
VLC Media Player, Winamp, Spotify, Audacity and AIMP media apps
Paint.net, Inkscape, Blender and Gimp graphics apps
Open Office, CutePDF, Libre Office and Foxit Reader document apps
Avast, Avira, Malwarebytes and AVG security apps
OneDrive, Google Sync and Dropbox cloud apps
WinRAR, PeaZip and 7-Zip file compression apps
And a lot more such as Evernote, CDBurnerXP, Team Viewer and lots of development tools.
There is a free version of Ninite which will do what most users want. For an additional $10/year you can automatically check for updates to the applications supported by Ninite so that there’s no need for you to perform manual updates.
You can also get a pro version of Ninite that enables you to manage all of your computers using a live web interface. Having used Ninite myself I was wondering if there were similar programs available. So I went looking and testing and I now bring you the 7 Ninite alternatives you should take a look at.
Table of Contents
Best Ninite Alternatives
1. Chocolatey – Free version and Pro for $96/year
I have heard a lot about Chocolatey as a good Ninite alternative but I’d never used it before. When I went to the official website I saw that there was a huge amount of applications and utilities available for downloading on to Windows computers. I had to use a PowerShell to add the commands for the installations which was a bit tricky for me at first.
Things got a lot better when I downloaded the GUI from here. I needed to install .NET 4.5.2. and then I had a visible interface to keep track of what was installed and what wasn’t. You can install your favorite applications and leave it all unattended while you go and do something useful if you use Chocolatey.
I only used the open-source version of Chocolatey and I found that it did everything that I wanted. There is a Pro version but only businesses with lots of Windows computers will want to go for this. Some people have said that Chocolatey doesn’t install some applications well but I didn’t experience that.
2. Just Install – Free
Just Install is another good application for installing applications on Windows computers and is worthy of inclusion on my Ninite alternative list. It is quite similar to Chocolatey in the way that it works. You have to use a command-line process to install any of the popular applications.
Just Install will install all of the applications correctly and you will be able to see them using Control Panel. This means that you can uninstall them in the normal way. All Just Install applications download from their original sources and there’s no repackaging going on. It will just install the apps that you want and skip all dialogs and prompts.
I found that it was pretty easy to create a tailored .exe installer which will download and install all of the applications that I needed in one hit rather than using different command-line strings. I would say that it takes a bit of time to get the hang of using Just Install but I was able to learn pretty fast and it really helped with those tedious installs.
3. Silent Install Helper – Free
Yet another free Ninite alternative is Silent Install Helper. What impressed me about this great free app is that you are not limited to install specific applications as you are with other Ninite alternatives (and indeed Ninite itself). You can install all the applications of your choosing with Silent Install Helper.
There is no free lunch though. I had to first download all of the relevant program installers to the application before I was able to create my first batch of installations. Silent Install Helper will alert you if it thinks that a program installer is trying to install something unwanted such as adware.
It did take me a while to set up Silent Install Helper with the program installers that I wanted but after that everything was a breeze. It was great not to be restricted to choosing from a list of applications and being free to choose what I wanted to install.
4. Silent Install Builder – Free evaluation version and $299 for single-user license
Silent Install Builder is another good Ninite alternative. Although it has a hefty price tag you can use the free version which is fully functional to install your favorite applications on a Windows computer. You create install packages which contain the entire install files that you need to get all of the apps installed.
I found it pretty easy to create install packages with Silent Install Builder. The application was able to recognize the most commonly used installer setups such as Windows Installer, Install shield, Nullsoft Installer and Inno Setup. After I’d created my package I was able to install all of the programs on my computer completely unattended.
Similarly to Silent Install Helper, I had to download all of the install files for the apps that I wanted first and then add them to Silent Install Builder. Everything was very intuitive and the whole process went smoothly for me. There is a facility to use scripts to record the installation process if you need to install apps on many Windows-based computers.
0 notes
Text
Random password generator.

#RANDOM PASSWORD GENERATOR. GENERATOR#
#RANDOM PASSWORD GENERATOR. FULL#
The fact that no client-side cryptographic entropy is included suggests limited of knowledge of cryptography and randomness. While it gets some entropy from the server, its source and quality is not known.
#RANDOM PASSWORD GENERATOR. GENERATOR#
While you’re at, don’t forget to check out our YouTube Channel for sysadmin video content I’m sure you’ll love too. The XKCD Random Password Generator does not use any cryptographic entropy on the client side.
#RANDOM PASSWORD GENERATOR. FULL#
If you like these kinds of Powershell Posts, be sure to check our Powershell repo full of real world scripts like this one that you can make use of. You should already have your steam authenticator on the mobile app to give you a 5 digit code with about 3 seconds left on the timer before it expires (they never give you the full time to. It will allow you to come up with some great, highly secure password suggestions you can use for your account. Anytime I need to sign up for a new service, New-RandomPassword -Length 20 is all I need to do for the password portion. This page contains a Steam password generator. Personally, I use this function on a weekly basis for whenever I need to generate strong passwords longer than 20 characters. Hopefully you will have a chance to use this script in your work flow or automation. The Password generated by this application is very strong, and it cant be guessed easily by the hacker. A password generator is a program that is used to generate random passwords. Creating a strong password is very important to keep the users account secure. Here is what the specified output would look like. Password is used in any application for authentication. To get a full list of number to characters simply run line 1 in Powershell. For example if you type: 35, it should return a hash sign. This is accomplished within Powershell by typing SomeNumber. How The Random Password Generator Powershell Script WorksĮssentially what this script does is take a number and pass it as a character data type. This script shall be called New-RandomPassword. This way you have everything setup in your script without having to manually ping a website elsewhere. I know there are a ton of websites out there that can provide this functionality but this method allows you to programmatically generate passwords for easier automation.Ī great use case for this random password generator script would be to generate a strong random password for an account creation. Today I’m going to share with you a simple, yet effective Powershell Random Password Generator. I Love it! Powershell really can do a lot of cool things and this handy little function comes in for the clutch when creating new user accounts or just resetting a user’s password.

0 notes
Text
Http www java com en download manual jsp

Http java com ja download manual jsp.
Website | On-Line Technology.
SedLog:Download - Royal Holloway, University of London.
Descargar gratis java 7.7 download - UpdateStar.
Java JRE 64-bit download for Windows? - Stack Overflow.
Download Java for Windows.
How to Check or Update Java Version in Windows with PowerShell?.
PDF Java Com En Ie Manual Jsp.
GitHub - javaee/jaxb-v2.
Vs Xmpp Websocket.
进N/download/manual.jsp后点那个啊.
PDF Java Com De Manual Jsp.
Installing the latest Java update in Win 10 - Microsoft Community.
Http java com ja download manual jsp.
In order to download Java on a 32-bit operating system, one needs to follow the below steps: 1) Open an internet browser on your computer system. Here, we have used the Google Chrome browser. On the search tab, type 'Java JDK 32 bit download' as you can see in the below snippet. I wrote the code on JSP that will display all the files on Remote hosting server, when I click on the file, I should be able to download it. what the best way to implement download? Right now, that JSP will able to show me all the files in that directory for example --> 'C:/'. Crear el Web Dynamic Project. Como la idea de este artículo es aprender un poco de Java Web con JSP y Servlet vamos a crear un proyecto Web Dynamic Project, como se muestra en la siguiente imagen. Si no lo encuentras en en esa opción, pincha al final en la opción Other->Web->Dynamic Web Project, lo siguiente es darle el nombre el proyecto y.
Website | On-Line Technology.
Java 7.7 download Gratis descargar software en UpdateStar - Java Platform, Standard Edition (Java SE) lets you develop and deploy Java applications on desktops and servers, as well as in today's demanding embedded environments.
SedLog:Download - Royal Holloway, University of London.
Oct 01, 2018 · Access and update the Java representation; Marshal the Java representation of the XML content into XML content; JAXB gives Java developers an efficient and standard way of mapping between XML and Java code. Java developers using JAXB are more productive because they can write less code themselves and do not have to be experts in XML.
Descargar gratis java 7.7 download - UpdateStar.
Oracle Java¶. Oracle Java currently supports Java 8. For download and installation instructions, go to..
Java JRE 64-bit download for Windows? - Stack Overflow.
2013-09-13 jsp是什么?编程语言常用的有那些? 2011-07-19 JSP和JAVA有什么区别。。编程语言之类; 2012-04-14 JSP和java有什么区别? 2009-01-26 java和JSP和JavaScript有什么区别啊; 2007-12-18 java与jsp的区别? 2008-10-17 Java与jsp; 2018-01-15 JSP到底是技术,还是语言. El manual se encuentra en continua revisión, de forma automática la URL proporcionada contendrá la última versión del Tutorial Java. Ejemplos Manual Java. A lo largo del Tutorial Java se van explicando una serie de ejemplos. Podéis descargaros los ejemplos del Tutorial Java desde el GitHub de Manual Web. Si os gusta el contenido del.
Download Java for Windows.
How to Download and Install Java JRE Using PowerShell? The following PowerShell script automatically downloads the latest version of Java installer from the official website and installs it on a computer(you can download both online and offline installer). The install command suppress reboot request and disables automatic Java updates. After all the servers started, connect to the proxies with websocket or tcp with XMPP message 1/luajit) - Handling HTTP/1 It is protocol-independent and can currently be used to stress Jabber/XMPP server, but also HTTP, SOAP, and postgreSQL servers Siaran ini adalah pos XMPP vs WebSocket untuk membantu anda membuat keputusan yang lebih baik.
How to Check or Update Java Version in Windows with PowerShell?.
Java 11 features include two new garbage collector implementations, Flight Recorder to debug deep issues, a new HTTP client including WebSocket support. Java SE 12 was released March 2019. Java SE 13 was released September 2019. Java SE 14 was released March 2020. Java SE 15 was released September 2020. Java SE 16 was released March 2021.
PDF Java Com En Ie Manual Jsp.
Accessing. Access the PDF documentation from the Help menu within Stata. See the recommended viewer settings for viewing the PDF manuals.. You can also access the PDF entry from Stata's help files. Each help file has the manual shortcut and entry name in blue, which links to the PDF manual entry, in addition to the "View complete PDF manual entry" link below. To force kmttg to download and install the accompanying 3rd party tools simply remove the tivodecode folder. Then when you start kmttg GUI allow it to download and install the tools package (it will overwrite the files in current installation). It might not tweaking, depending on where any other versions of Java are installed. set PATH=%PATH:C:\Program Files\Java\jdk-12\bin;=%. Since for me, JDK 12 is the only other version of Java installed, this temporarily removes it from the system path, forcing the server to run using Java 1.8.
GitHub - javaee/jaxb-v2.
Get speed, security, and privacy with Microsoft Edge. Try it now. Open Internet Explorer icon and go to J Select the Free Java Download button, and then select Agree and Start Free Download. If you're prompted for an administrator password or confirmation, type the password or provide confirmation. On the notification bar, select Run. Update Java program on the computer. Follow these instructions to update the Java program on the computer. a) Press Windows key + X and select Control panel. b) Change "View By" to "Large icons" from the top right corner of the window. c) Click on "Java". d) On the Java window, click on "Update" tab. e) Click on "Update Now. All Oracle Java Downloads. Download now. Technologies. Java SE. Java SE Subscription. Java Embedded. Java EE. Java ME. Java Card. Java TV. Java DB. Developer Tools. What's New in Java. Join Oracle for the online developer event series to advance your coding skills. Press Release: Introducing Java SE 18.
Vs Xmpp Websocket.
PDF file: java com pl download manual jsp. Page: 1. Save this Book to Read java com pl download manual jsp PDF eBook at our Online Library. Get java com pl download manual jsp PDF file for free. Still requires manual intervention after each update of JDK/JRE or DavMail, but less intrusive than the method suggested above which requires editing the executable file resources. Not that it makes much difference, since the released file isn't signed either way, but I prefer being able to compare a binary to whatever was released and I keep..
进N/download/manual.jsp后点那个啊.
Scripting is often contrasted with system programming, as in Ousterhout's dichotomy or "programming in the large and programming in the small".In this view, scripting is glue code, connecting software components, and a language specialized for this purpose is a glue language.Pipelines and shell scripting are archetypal examples of glue languages, and Perl was initially developed to fill this. Designed by the world’s leading database experts, IBM Db2 empowers developers, DBAs, and enterprise architects to run low-latency transactions and real-time analytics equipped for the most demanding workloads.
PDF Java Com De Manual Jsp.
.
Installing the latest Java update in Win 10 - Microsoft Community.
Get java com pl download manual jsp PDF file for free from our online library. JAVA COM PL DOWNLOAD MANUAL JSP. Java Com Pl Download Manual Jsp Download. Java Com Pl Download Manual Jsp Free. 1 Qué es JSP. La tecnología Java para la creación de páginas web con programación en el servidor. 2 Comparando JSP con ASP. Un artículo que apunta las principales diferencias entre las tecnologías JSP y ASP. Hace especial énfasis en las ventajas que se encuentran en el sistema Java frente al Microsoft. 3 Conexión a un database server..
See also:
Asus Fan Xpert Download Windows 10 64 Bit
Sudden Strike 4 Free Download Full Version
Windows 10 Os Download For Pendrive Bootable

0 notes
Text
Windows server 2012 standard build 9200 activator 無料ダウンロード.Download Update for Windows Server 2012 (KB2937636) from Official Microsoft Download Center
Windows server 2012 standard build 9200 activator 無料ダウンロード.Sppsvc.exe プロセスは、Windows 8 または Windows Server 2012 で自動的に起動しない場合、ライセンス認証が機能しません。

更新プログラムの詳細情報.Download Windows Server R2 Update (KB) from Official Microsoft Download Center
Windows および Windows Server R2 の場合、次の記事に従って、必要に応じて依存する修正プログラムをインストールします。 KB Windows RT 、Windows 、および Windows Server R2 の更新プログラム: 年 4 月 May 05, · KB is a prerequisite for Windows Server R2 Update and should be installed before attempting to install KB Additional Information Other critical security updates are available: To find the latest security updates for you, visit Windows Update and click Express Install Aug 11, · プロセスは、Windows 8 または Windows Server で自動的に起動しない場合、ライセンス認証が機能しません。. Windows Server Datacenter Windows Server Datacenter. Windows Server Standard Windows Server Standard Windows Server Essentials Windows Server Foundation Windows
Windows server 2012 standard build 9200 activator 無料ダウンロード.MS がインストールされたことを確認する方法
May 05, · KB is a prerequisite for Windows Server R2 Update and should be installed before attempting to install KB Additional Information Other critical security updates are available: To find the latest security updates for you, visit Windows Update and click Express Install Feb 02, · Activate Windows Server Evaluation to Full Version. Step 1. The very first step is to view the current edition. So open Command Prompt or Windows PowerShell in elevated mode (Run as Administrator) and type, DISM /online /Get-CurrentEditon as shown below. As you can see the current edition is Datacenter Evaluation. Step s: 3 Windows および Windows Server R2 の場合、次の記事に従って、必要に応じて依存する修正プログラムをインストールします。 KB Windows RT 、Windows 、および Windows Server R2 の更新プログラム: 年 4 月
Hello FarSeerKing ,. Please, check with a different browser, computer or network maybe is blacklisted in your company network. We do not support Microsoft download site so you might want to consider to ask for that in the Microsoft support forums. Of course it will - I use it all the time.
You must do it from the Command Prompt though - you cannot use the Activation page. I only recommend the genuine setup that can be downloaded from Microsoft Official website. The ISO file for Serve R2 can be found easily on Microsoft. I'm trying to understand what a PDF file has to do with Windows Server R2 ISO? Care to enlighten the rest of us? I'm sure Julia meant to post the same link I posted and didn't realize it was already there.
Browse Community. PowerEdge OS Forum. Dell Community : Software : PowerEdge OS Forum : Where can I download an ISO file for Server R2 Std. Options Subscribe to RSS Feed Mark Topic as New Mark Topic as Read Float this Topic for Current User Bookmark Subscribe Mute Printer Friendly Page. Turn on suggestions.
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. Showing results for. Search instead for. Did you mean:. Last reply by DiegoLopez Unsolved. bcavnaugh 2 Iron. Mark as New Bookmark Subscribe Mute Subscribe to RSS Feed Permalink Print Email to a Friend Report Inappropriate Content. Where can I download an ISO file for Server R2 Std.
OK did this to myself so Only I have to blame for this. I reset my Drives to Raid and Killed my Preinstalled OS of Windows Server R2 Std.
Anywhere on Dell can I download an ISO File? All forum topics Previous Topic Next Topic. Replies theflash 7 Thorium. FarSeerKing 2 Bronze. In response to theflash the download from the microsoft page did not start. DiegoLopez MOD. In response to FarSeerKing. Hello FarSeerKing , Please, check with a different browser, computer or network maybe is blacklisted in your company network. I tried myself and it's working for me.
Maybe it was a temporary issue. Dell Support is taking care of me so thanks for the Reply. My Dell OS Key will not work with the Eval Version. I tried this first. Dellarmelin 2 Bronze. Smith 2 Bronze. johnksss 3 Silver. In response to Julia.
In response to johnksss. Post Reply. Top Contributor. Dell Support Resources. Latest Solutions. Can't find what you're looking for? You can post your question in our community. Sign up now.
0 notes
Text
How to check response code from a website using PowerShell
How to check response code from a website using PowerShell
In this post we will discuss about how to check the response code from a website. In this article, we’re going to cover how to build a PowerShell function that will query a specific URL and attempt to find out if that URL is working fine or not. To get started, let’s construct a function for this task called CheckSiteURLStatus with a single parameter called URL.
Net.WebReques makes a request to a…
View On WordPress
#check if a website is down powershell#powershell check if website is started#powershell check website content#powershell get http response#powershell get web page content#powershell if response#powershell invoke-restmethod status code#powershell ping website#Powershell Script for Website Availability Monitoring#powershell script for website availability monitoring / url monitoring#powershell script to check website availability#powershell test url exists#script to check website status#test web url powershell#website monitoring script windows
0 notes
Text
Missing Protocol Windows 10

Windows 10 Network Protocol Error: Missing Windows Sockets Registry Entries By Corey October 5, 2020 No Comments My colleagues work computer running Windows 10 began to lose Internet access from time to time (once in 2-3 days with the Limited connection status in the tray). Temporarily Disable or Reinstall your Antivirus Software. First things first, if you are using any. Simply updating your PC's Windows 10 operating system could also fix this issue and restore any missing default apps. Step 1: Hit the Windows logo + I short to launch the Windows Settings menu.
Simple Network Management Protocol or SNMP is used for monitoring, event notification, and network device management on corporate networks. The protocol consists of a set of network management standards, including the Application Layer protocol, database schemas, and a set of data objects. SNMP can receive various information (uptime, performance counters, device parameters, etc.) from any network devices: switches, servers, routers or computers on which the SNMP agent is installed. In Windows 10, the SNMP service is available as a separate Windows component and it’s not installed by the default.
How to Install SNMP Service in Windows 10?
You can check if the SNMP service is installed on your Windows 10 using the Get-Service:
Most likely, the service has not been installed yet.
You can install the SNMP service via the Control Panel. Go to the Control Panel > Programs and Features > Turn Windows features on or off. In the list of Windows features, select Simple Network Management Protocol (SNMP) and the WMI SNMP Provider (provides access to SNMP information via the Windows Management Instrumentation interfaces) and click OK.
You can also install SNMP service using PowerShell:
This command can help you to install SNMP service on Windows 10 in 1803 build or earlier. Starting from Windows 10 1809 Microsoft has changed the way to deploy snmp service on desktop OSs.
Installing SNMP Service in Windows 10 1803 and Newer
Missing Protocol Windows 10 64-bit
In Windows 10 1803 and later (1809, 1903), the SNMP service is considered deprecated and is not listed in the Windows features in the Control Panel list.
Microsoft plans to completely remove the SNMP service in the next Windows builds because of the security risks associated with this protocol. Instead of SNMP, it is recommended to use the Common Information Model (CIM), which is supported by Windows Remote Management. On the current builds of Windows 10, the SNMP service is hidden.
READ ALSOHow to Setup FTP Server in Windows 10?
The SNMP service is now missing from the Windows 10 image and can only be installed as Feature On Demand (FoD).

If your computer has a direct Internet connection, you can install the SNMP service components online from Microsoft servers. To do this, open the elevated PowerShell console and run the command:
You can also use DISM to install the SNMP service:
After that, you can verify that the SNMP service is installed:
Name : SNMP.Client~~~~0.0.1.0
State : Installed
DisplayName : Simple Network Management Protocol (SNMP)
Description : This feature includes Simple Network Management Protocol agents that monitor the activity in network devices and report to the network console workstation
DownloadSize : 595304
Default Protocols Windows 10
InstallSize : 1128133
To disable the SNMP service, use the PowerShell command:
You can also install the SNMP service through the Optional Features graphical interface.
Go to the Settings > Apps > Apps & Features > Manage optional feature > Add Feature. Select in the list the following features: Simple Network Management Protocol (SNMP) and WMI SNMP Provider (to get all SNMP service configuration tabs).
After that, the SNMP service will appear in the services.msc console.
If when performing the Add-WindowsCapability command you received the “Add-WindowsCapability failed error. Error code = 0x800f0954”, most likely your computer receives Windows updates not from Microsoft Update servers but from the internal WSUS server. To make SNMP service receiving install files from Microsoft servers, you need to temporarily bypass the WSUS.
READ ALSOAccessing Hyper-V VM Console Using RDCMan
To do this, run the command:
After that, restart the Windows Update service:
Now try to install the SNMP service with the Add-WindowsCapability command. If all goes well, return the initial wusuaserv service registry parameter pointing to the WSUS server. Run the command:
And restart the Windows Update Service.
Configure SNMP on Windows 10 Computer
After the installation, SNMP services should start automatically. Open the Services management console (services.msc). Two new services should appear in the service list:
SNMP Service – This is the primary SNMP agent service, that tracks activity and sends information;
SNMP Trap – Receives trap messages from local or remote SNMP agents, and forwards messages to the SNMP management software that is being run on that computer.
Open the properties of the SNMP Service. If it is stopped, start it by pressing the Start button and change the startup type to Automatic.
Click the Agent tab. Fill in the Contact and Location fields (you can specify the user’s contact name and computer location), and select the list of services from which you want to collect data and send it to the monitoring device. There are five service-based options:
Physical;
Applications;
Internet;
End-to-end;
Datalink and subnetwork.
Click the Security tab. Here you can configure various security settings for different SNMP servers.
The list of Accepted community names contains the names of the communities whose SNMP hosts are authenticated to send SNMP requests to this computer. The community name has the same functions like login and password.
READ ALSOChanging Active Directory krbtgt Account Password
Click the Add button and specify the Community Name and one of the five access levels (None, Notify, READ ONLY, READ WRITE, READ CREATE). READ WRITE is the maximum access level at which the SNMP management server can make changes on the system. For monitoring systems, it is usually enough to select READ ONLY, while the monitoring server can only poll the system, but not make changes. In our example, we added a community name public with READ ONLY permissions.
Add to the Accept SNMP packets from these hosts list of monitoring servers (hostnames or IP addresses) from which you want to accept SNMP packages.
Tip. You can select the Accept SNMP packets from any host option, but this is not safe.
Save the changes and restart the SNMP service.
This completes the SNMP service configuration in Windows 10. If you need to enable SNMP on multiple computers or servers, you can remotely install and configure SNMP service using PowerShell or Group Policy.
AuthorRecent PostsCyril KardashevskyI enjoy technology and developing websites. Since 2012 I'm running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.Latest posts by Cyril Kardashevsky (see all)
Fix: Active Directory Domain Controller Could Not Be Contacted - December 10, 2020Manage and Disable Windows Defender Using PowerShell - December 9, 2020Using Out-File Cmdlet to Redirect Output to File in PowerShell - December 4, 2020='font-size:14px>='font-size:14px>='font-size:14px>
This site uses cookies to analyze traffic, personalize your experience and serve ads. By continuing browsing this site, we will assume that you are agree with it. =cn-notice-text>
A Network Protocol is a set of rules that define how data is communicated between different computers that are connected through a network connection.
Network Protocols are of different types such as Ethernet, FDDI, LocalTalk and TokenRing. They comprise of procedures and formats to be followed during data transmission. You might encounter the One or more protocols are missing error on a Windows 10 laptop/ PC due to one or more of the following reasons:
Your system doesn’t support usage of IPv6
Your WinSock defaults have been changed
DNS registration issues
Corrupt Registry keys, code identifier issues
Insufficient Registry permissions to access network data
A protocol needs to be installed
Use Internet Protocol Version 4
IPv6 is a next-generation protocol. If you’re encountering problems deploying IPv6, configure your laptop to use an older protocol such as IPv4.
Press Windows Key + X; choose Control Panel.
Click Network and Internet | Network and Sharing Center.
Click the Wi-Fi/ Wired Broadband connection that appears in Connections.
Wi-Fi/ Wired Broadband Status dialog will open up on your screen.
Click Properties.
Uncheck Internet Protocol Version 6 (TCP/ IPv6).
Check Internet Protocol Version 4 (TCP/ IPv4).
Click OK | Close.
Restore Winsock Defaults
WinSock, earlier known as WSA, deals with network services such as TCP/IP. Problems with the functioning of WinSock can cause protocol errors. Restore default WinSock configurations using an elevated CMD.
Press Windows Key + X; select Command Prompt (Admin).
Type the following command: Netsh winsock reset
Press the Enter key of your keyboard.
Restart your system using the following command-line: Shutdown /r
Flush & Register New DNS
Domain Name Servers (DNS)translates a website’s name into the corresponding Internet Protocol (IP) Address. If the process of converting human-readable website names fails, you may get the protocol missing error.
Open an elevated Command Prompt.
Flush the existing DNS: ipconfig /flushdns
Register a new DNS: ipconfig /registerdns
Release and renew the information: ipconfig /release ipconfig /renew
Reset the Catalog: netsh winsock reset catalog
Store the logs in a separate file named reset.log netsh int ipv4 reset reset.log netsh int ipv6 reset reset.log pause
Restart your computer: shutdown /r
Modify Registry Configurations
Provide appropriate read, write and access permissions to the Registry subkeys that deal with your computer’s network connection.
Type RegEdit in the Search Box on the Taskbar.
Open Registry Editor from the Search Results.
Locate the following Registry path: HKEY_LOCAL_MACHINE | SYSTEM | CurrentControlSet | Control | Nsi | {eb004a00-9b1a-11d4-9123¬-0050047759bc}
Right-click a 26 subkey, choose Permissions.
In the new dialog, specify the Group or User Name as Everyone.
Check the Allow box ahead of Full Control.
Click Apply | OK.
Install New Protocol
Go to your Connection Properties and then install a new protocol through the steps given below:
Type ncpa.cpl in the Search Box and open it from the Search Results.
Right-click your Wi-Fi/ Wired Broadband connection icon, choose Properties.
Click the Install button.
Choose Protocol in the subsequent Select Network Feature Type dialog, and click Add.
Click Hard Disk button.
Specify the following path: C:Windowsinf
Click OK.
You have a new dialog – Select Network Protocol
Select Internet Protocol (TCP/ IP) – Tunnels
Click OK.
Delete Code Identifier
Make sure the code identifier keys aren’t corrupt. Delete the corrupted data so that your system will generate default settings.
Open Registry Editor.
Locate following Registry path: HKEY_LOCAL_MACHINE | SOFTWARE | Policies | Microsoft | Windows | Safer | CodeIdentifiers | 0
Delete the Paths subkey. (Right-click > Delete)
Exit the Registry Editor and restart your laptop.

0 notes
Video
youtube

essay writing website
About me
Custom Essays
Custom Essays Each work is completed in accordance with buyer calls for, strictly avoiding any plagiarism and referenced in the chosen quotation style. Thanks a lot for completing my thesis; I know the subject was very challenging to say the least. You guys are the most effective essay help on the web. They do not use any pre-written content to succeed in the required variety of phrases in an essay you order. If you always select to stay in a well-known environment and avoid unexpected situations, there shall be no motivation to grow and improve your skills. The staff of CheetahPapers.com encourages you to be bold and face the dangers that come your way with pleasure as they're your alternative to become higher. Students typically misinterpret the concept of threat and perceive it as one thing negative. While a scholar struggles hard to satisfy the whole writing requirement, Essay Captains take the accountability to bail you out of this situation. Universities search a mirrored image of the applicant within the essay with capable mention of the extra-curricular actions as well. Here are some suggestions that we bear in mind for making the method of writing even somewhat bit easier for you. Our consultants imagine that each essay should be unique just as each pupil is. The choice is available inside days (relying on the project’s size). A full refund is issued anytime before a paper is downloaded. The idea of capacities is core to SmartThings, also takes slightly more explanation. We just remember to can reach our help staff 24 hours a day, 7 days per week. So, should you happen to have any questions do not hesitate to ask. Not once since our inception has there been a delay in any submission in any respect – let the phrases of our present prospects tell you this, within the 'Testimonials' section. Our editors be sure that there’s not even a speck of copied content material in your paper. I just dreaded the literature evaluation part of my thesis. But you guys gave me the subject-specific expert who carried out a tremendous job. All of the cited research and summaries had been put collectively in a logical and fluid piece of writing. Check all the bins - inform us what sort of paper is it going to be. Move on to the next step - personal directions. work and ultimately, make sure that any paper is a hundred% authentic. freebies corresponding to free rewards and paper giveaways for essentially the most loyal of our shoppers. Should a downloaded project fail to reside as much as your expectations or meet initial instructions, you could request a refund. Coming up with a wonderful essay is not inconceivable as long as you know the tips and tips to employ. Always keep in mind to edit and proofread your final draft to remove all potential errors. But we all know that you really want discounts, so we give them to you, too! If you want what you get and you come again to us for different assignments, we’ll keep supplying you with discounts. The logical circulate of the composition should be coherent, so be sure to coordinate your ideas into a fashion that can sound pure. As an example, you might plug by yourself waiver provider and employ customized authentication. See how simple it’s to assemble a speedy Utilization occasion using a customized constructed PowerShell cmdlet and put it to make use of to facilitate a lot of duties. There’s irrespective of with the accessibility into these articles. We all need is to assist you receive the very best paper that industry can present. You will be able to have updates on the standing of your assignment because it’s being created. It is very important to bear in mind that the extra the instructions that you simply share, the extra you might be most essay in english more likely to get what you want to. Other than sure due dates, you create your personal schedule for finishing the necessities of the class. As quickly as your order is completed, you'll get a notification.
0 notes
Text
Spying On Google: 5 Ways to Use Log File Analysis To Reveal Invaluable SEO Insights

Log File Analysis should be a part of every SEO pro’s tool belt, but most SEOs have never conducted one. Which means most SEOs are missing out on unique and invaluable insights that regular crawling tools just can’t produce. Let's demystify Log File Analysis so it's not so intimidating. If you’re interested in the wonderful world of log files and what they can bring to your site audits, this guide is definitely for you.
What are Log Files?
Log Files are files containing detailed logs on who and what is making requests to your website server. Every time a bot makes a request to your site, data (such as the time, date IP address, user agent, etc.) is stored in this log. This valuable data allows any SEO to find out what Googlebot and other crawlers are doing on your site. Unlike regular crawlings, such as with the Screaming Frog SEO Spider, this is real-world data — not an estimation of how your site is being crawled. It is an exact overview of how your site is being crawled. Having this accurate data can help you identify areas of crawl budget waste, easily find access errors, understand how your SEO efforts are affecting crawling and much, much more. The best part is that, in most cases, you can do this with simple spreadsheet software. In this guide, we will be focussing on Excel to perform Log File Analysis, but I’ll also discuss other tools such as Screaming Frog’s less well-known Log File Analyser which can just make the job a bit easier and faster by helping you manage larger data sets. Note: owning any software other than Excel is not a requirement to follow this guide or get your hands dirty with Log Files.
How to Open Log Files
Rename .log to .csv When you get a log file with a .log extension, it is really as easy as renaming the file extension .csv and opening the file in spreadsheet software. Remember to set your operating system to show file extensions if you want to edit these. How to open split log files Log files can come in either one big log or multiple files, depending on the server configuration of your site. Some servers will use server load balancing to distribute traffic across a pool or farm of servers, causing log files to be split up. The good news is that it's really easy to combine, and you can use one of these three methods to combine them and then open them as normal: Use the command line in Windows by Shift + right-clicking in the folder containing your log files and selecting “Run Powershell from here”
Then run the following command: copy *.log mylogfiles.csv You can now open mylogfile.csv and it will contain all your log data. Or if you are a Mac user, first use the cd command to go to the directory of your log files: cd Documents/MyLogFiles/ Then, use the cat or concatenate command to join up your files: cat *.log > mylogfiles.csv 2) Using the free tool, Log File Merge, combine all the log files and then edit the file extension to .csv and open as normal. 3) Open the log files with the Screaming Frog Log File Analyser, which is as simple as dragging and dropping the log files:
Splitting Strings (Please note: This step isn’t required if you are using Screaming Frog’s Log File Analyser) Once you have your log file open, you’re going to need to split the cumbersome text in each cell into columns for easier sorting later. Excel’s Text to Column function comes in handy here, and is as easy as selecting all the filled cells (Ctrl / Cmd + A) and going to Excel > Data > Text to Columns and selecting the “Delimited” option, and the delimiter being a Space character. Once you’ve separated this out, you may also want to sort by time and date — you can do so in the Time and Date stamp column, commonly separating the data with the “:” colon delimiter. Your file should look similar to the one below:
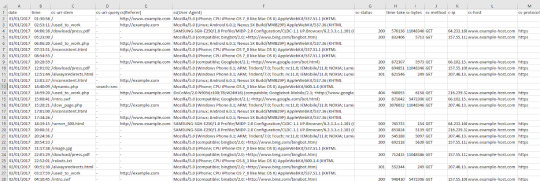
As mentioned before, don’t worry if your log file doesn’t look exactly the same — different log files have different formats. As long as you have the basic data there (time and date, URL, user-agent, etc.) you’re good to go!
Understanding Log Files
Now that your log files are ready for analysis, we can dive in and start to understand our data. There are many formats that log files can take with multiple different data points, but they generally include the following: Server IP Date and time Server request method (e.g. GET / POST) Requested URL HTTP status code User-agent More details on the common formats can be found below if you’re interested in the nitty gritty details: WC3 Apache and NGINX Amazon Elastic Load Balancing HA Proxy JSON
How to quickly reveal crawl budget waste
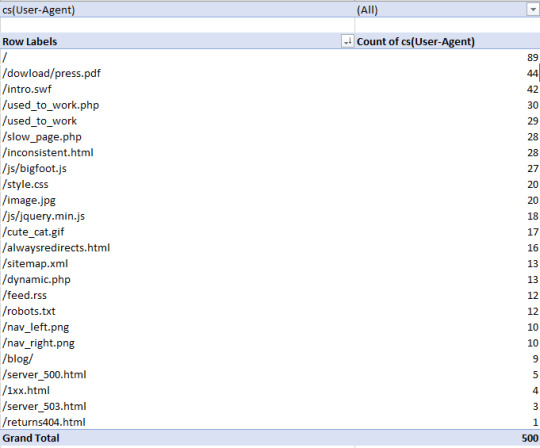
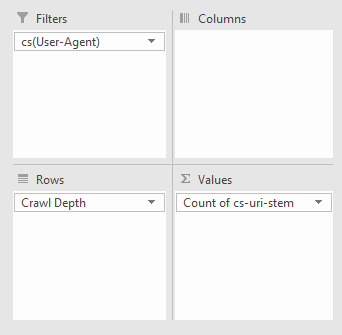
As a quick recap, Crawl Budget is the number of pages a search engine crawls upon every visit of your site. Numerous factors affect crawl budget, including link equity or domain authority, site speed, and more. With Log File Analysis, we will be able to see what sort of crawl budget your website has and where there are problems causing crawl budget to be wasted. Ideally, we want to give crawlers the most efficient crawling experience possible. Crawling shouldn’t be wasted on low-value pages and URLs, and priority pages (product pages for example) shouldn’t have slower indexation and crawl rates because a website has so many dead weight pages. The name of the game is crawl budget conservation, and with good crawl budget conversion comes better organic search performance. See crawled URLs by user agent Seeing how frequently URLs of the site are being crawled can quickly reveal where search engines are putting their time into crawling. If you’re interested in seeing the behavior of a single user agent, this is easy as filtering out the relevant column in excel. In this case, with a WC3 format log file, I’m filtering the cs(User-Agent) column by Googlebot:
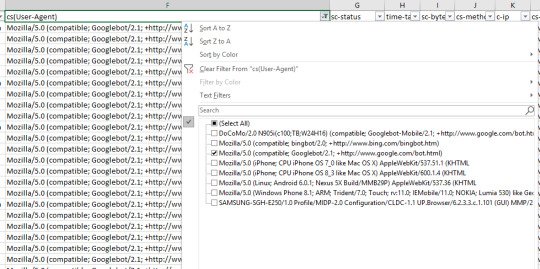
And then filtering the URI column to show the number of times Googlebot crawled the home page of this example site:
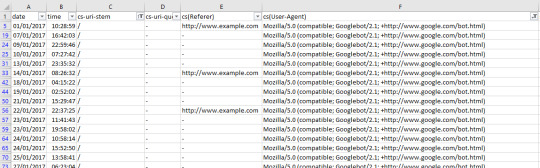
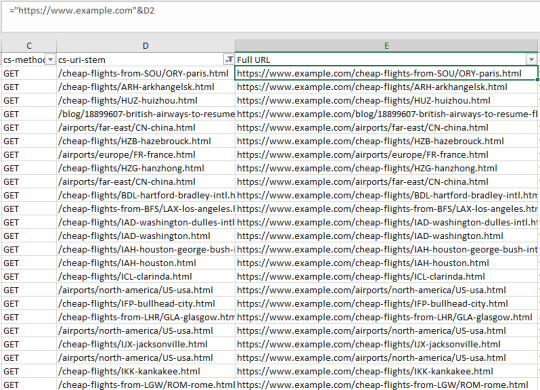
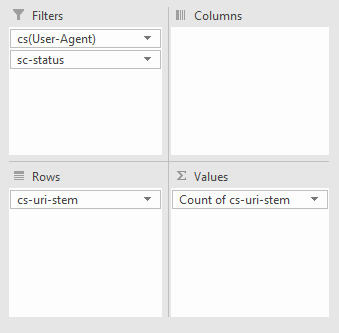
This is a fast way of seeing if there are any problem areas by URI stem for a singular user-agent. You can take this a step further by looking at the filtering options for the URI stem column, which in this case is cs-uri-stem:
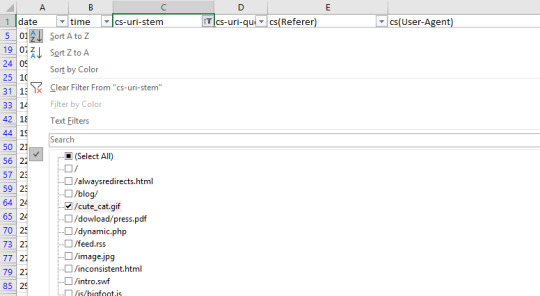
From this basic menu, we can see what URLs, including resource files, are being crawled to quickly identify any problem URLs (parameterized URLs that shouldn’t be being crawled for example). You can also do broader analyses with Pivot tables. To get the number of times a particular user agent has crawled a specific URL, select the whole table (Ctrl/cmd + A), go to Insert > Pivot Table and then use the following options:
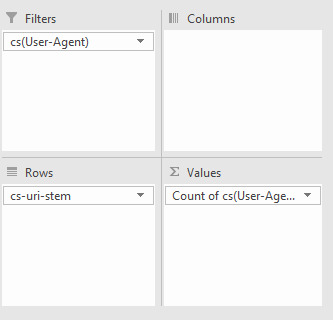
All we’re doing is filtering by User Agent, with the URL stems as rows, and then counting the number of times each User-agent occurs. With my example log file, I got the following:
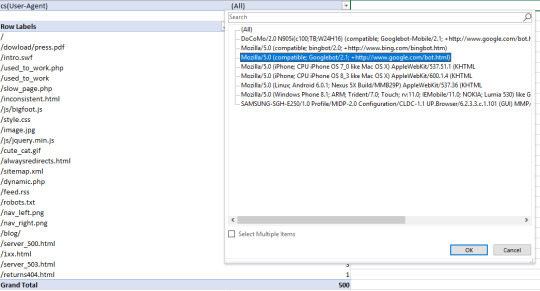
Then, to filter by specific User-Agent, I clicked the drop-down icon on the cell containing “(All)," and selected Googlebot:
Understanding what different bots are crawling, how mobile bots are crawling differently to desktop, and where the most crawling is occurring can help you see immediately where there is crawl budget waste and what areas of the site need improvement. Find low-value add URLs Crawl budget should not be wasted on Low value-add URLs, which are normally caused by session IDs, infinite crawl spaces, and faceted navigation. To do this, go back to your log file, and filter by URLs that contain a “?” or question mark symbols from the URL column (containing the URL stem). To do this in Excel, remember to use “~?” or tilde question mark, as shown below:
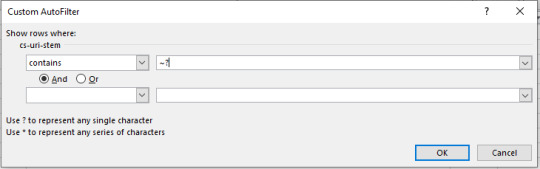
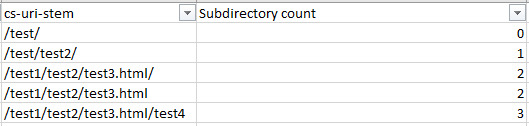
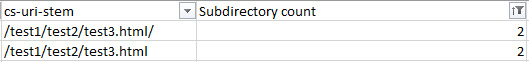
A single “?” or question mark, as stated in the auto filter window, represents any single character, so adding the tilde is like an escape character and makes sure to filter out the question mark symbol itself. Isn’t that easy? Find duplicate URLs Duplicate URLs can be a crawl budget waste and a big SEO issue, but finding them can be a pain. URLs can sometimes have slight variants (such as a trailing slash vs a non-trailing slash version of a URL). Ultimately, the best way to find duplicate URLs is also the least fun way to do so — you have to sort by site URL stem alphabetically and manually eyeball it. One way you can find trailing and non-trailing slash versions of the same URL is to use the SUBSTITUTE function in another column and use it to remove all forward slashes: =SUBSTITUTE(C2, “/”, “”) In my case, the target cell is C2 as the stem data is on the third column. Then, use conditional formatting to identify duplicate values and highlight them.
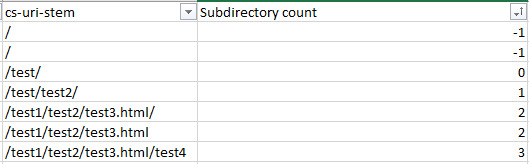
However, eyeballing is, unfortunately, the best method for now. See the crawl frequency of subdirectories Finding out which subdirectories are getting crawled the most is another quick way to reveal crawl budget waste. Although keep in mind, just because a client’s blog has never earned a single backlink and only gets three views a year from the business owner’s grandma doesn’t mean you should consider it crawl budget waste — internal linking structure should be consistently good throughout the site and there might be a strong reason for that content from the client’s perspective. To find out crawl frequency by subdirectory level, you will need to mostly eyeball it but the following formula can help: =IF(RIGHT(C2,1)="/",SUM(LEN(C2)-LEN(SUBSTITUTE(C2,"/","")))/LEN("/")+SUM(LEN(C2)-LEN(SUBSTITUTE(C2,"=","")))/LEN("=")-2, SUM(LEN(C2)-LEN(SUBSTITUTE(C2,"/","")))/LEN("/")+SUM(LEN(C2)-LEN(SUBSTITUTE(C2,"=","")))/LEN("=")-1) The above formula looks like a bit of a doozy, but all it does is check if there is a trailing slash, and depending on the answer, count the number of trailing slashes and subtract either 2 or 1 from the number. This formula could be shortened if you remove all trailing slashes from your URL list using the RIGHT formula — but who has the time. What you’re left with is subdirectory count (starting from 0 from as the first subdirectory). Replace C2 with the first URL stem / URL cell and then copy the formula down your entire list to get it working.
Make sure you replace all of the C2s with the appropriate starting cell and then sort the new subdirectory counting column by smallest to largest to get a good list of folders in a logical order, or easily filter by subdirectory level. For example, as shown in the below screenshots:
The above image is subdirectories sorted by level.
The above image is subdirectories sorted by depth. If you’re not dealing with a lot of URLs, you could simply sort the URLs by alphabetical order but then you won’t get the subdirectory count filtering which can be a lot faster for larger sites. See crawl frequency by content type Finding out what content is getting crawled, or if there are any content types that are hogging crawl budget, is a great check to spot crawl budget waste. Frequent crawling on unnecessary or low priority CSS and JS files, or how crawling is occurring on images if you are trying to optimize for image search, can easily be spotted with this tactic. In Excel, seeing crawl frequency by content type is as easy as filtering by URL or URI stem using the Ends With filtering option.
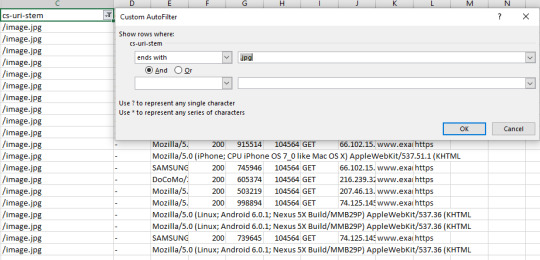
Quick Tip: You can also use the “Does Not End With” filter and use a .html extension to see how non-HTML page files are being crawled — always worth checking in case of crawl budget waste on unnecessary js or css files, or even images and image variations (looking at you Wordpress). Also, remember if you have a site with trailing and non-trailing slash URLs to take that into account with the “or” operator with filtering.
Spying on bots: Understand site crawl behavior
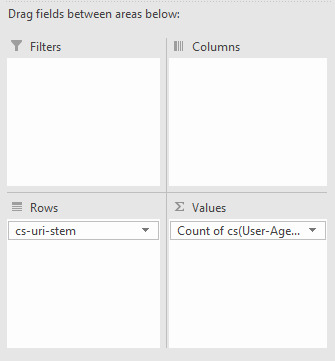
Log File Analysis allows us to understand how bots behave by giving us an idea of how they prioritize. How do different bots behave in different situations? With this knowledge, you can not only deepen your understanding of SEO and crawling, but also give you a huge leap in understanding the effectiveness of your site architecture. See most and least crawled URLs This strategy has been touched up previously with seeing crawled URLs by user-agent, but it’s even faster. In Excel, select a cell in your table and then click Insert > Pivot Table, make sure the selection contains the necessary columns (in this case, the URL or URI stem and the user-agent) and click OK.
Once you have your pivot table created, set the rows to the URL or URI stem, and the summed value as the user-agent.
From there, you can right-click in the user-agent column and sort the URLs from largest to smallest by crawl count:
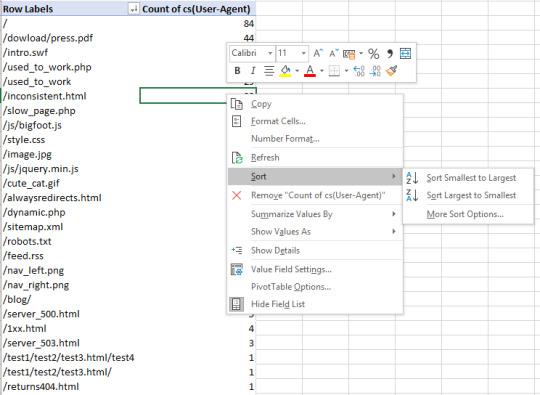
Now you’ll have a great table to make charts from or quickly review and look for any problematic areas:
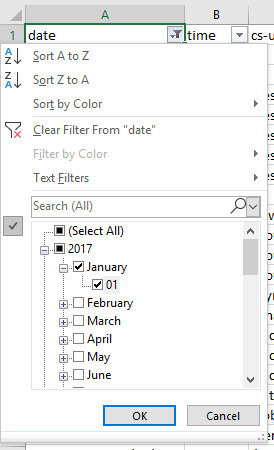
A question to ask yourself when reviewing this data is: Are the pages you or the client would want being crawled? How often? Frequent crawling doesn’t necessarily mean better results, but it can be an indication as to what Google and other content user-agents prioritize most. Crawl frequency per day, week, or month Checking the crawling activity to identify issues where there has been loss of visibility around a period of time, after a Google update or in an emergency can inform you where the problem might be. This is as simple as selecting the “date” column, making sure the column is in the “date” format type, and then using the date filtering options on the date column. If you’re looking to analyze a whole week, just select the corresponding days with the filtering options available.
Crawl frequency by directive Understanding what directives are being followed (for instance, if you are using a disallow or even a no-index directive in robots.txt) by Google is essential to any SEO audit or campaign. If a site is using disallows with faceted navigation URLs, for example, you’ll want to make sure these are being obeyed. If they aren’t, recommend a better solution such as on-page directives like meta robots tags. To see crawl frequency by directive, you’ll need to combine a crawl report with your log file analysis. (Warning: We’re going to be using VLOOKUP, but it’s really not as complicated as people make it out to be) To get the combined data, do the following: Get the crawl from your site using your favorite crawling software. I might be biased, but I’m a big fan of the Screaming Frog SEO Spider, so I’m going to use that. If you’re also using the spider, follow the steps verbatim, but otherwise, make your own call to get the same results. Export the Internal HTML report from the SEO Spider (Internal Tab > “Filter: HTML”) and open up the “internal_all.xlsx” file.
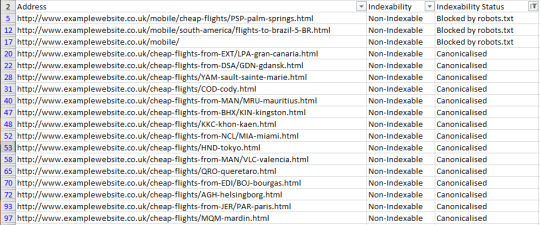
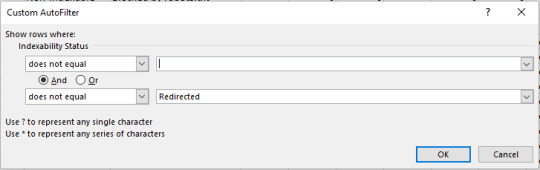
From there, you can filter the “Indexability Status” column and remove all blank cells. To do this, use the “does not contain” filter and just leave it blank. You can also add the “and” operator and filter out redirected URLs by making the filter value equal “does not contain → “Redirected” as shown below:
This will show you canonicalized, no-index by meta robots and canonicalized URLs. Copy this new table out (with just the Address and Indexability Status columns) and paste it in another sheet of your log file analysis export. Now for some VLOOKUP magic. First, we need to make sure the URI or URL column data is in the same format as the crawl data. Log Files don’t generally have the root domain or protocol in the URL, so we either need to remove the head of the URL using "Find and Replace" in our newly made sheet, or make a new column in your log file analysis sheet append the protocol and root domain to the URI stem. I prefer this method because then you can quickly copy and paste a URL that you are seeing problems with and take a look. However, if you have a massive log file, it is probably a lot less CPU intensive with the "Find and Replace" method. To get your full URLs, use the following formula but with the URL field changed to whatever site you are analyzing (and make sure the protocol is correct as well). You'll also want to change D2 to the first cell of your URL column ="https://www.example.com"&D2 Drag down the formula to the end of your Log file table and get a nice list of full URLs:
Now, create another column and call it “Indexability Status”. In the first cell, use a VLOOKUP similar to the following: =VLOOKUP(E2,CrawlSheet!A$1:B$1128,2,FALSE). Replace E2 with the first cell of you "Full URL" column, then make the lookup table into your new. crawl sheet. Remember to sue the dollar signs so that the lookup table doesn't change as you. apply the formula to further roles. Then, select the correct column (1 would be the first column of the index table, so number 2 is the one we are after). Use the FALSE range lookup mode for exact matching. Now you have a nice tidy list of URLs and their indexability status matched with crawl data:
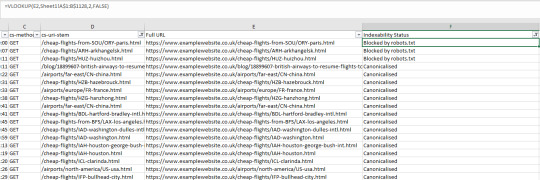
Crawl frequency by depth and internal links This analysis allows us to see how a site’s architecture is performing in terms of crawl budget and crawlability. The main aim is to see if you have far more URLs than you do requests — and if you do then you have a problem. Bots shouldn’t be “giving up” on crawling your entire site and not discovering important content or wasting crawl budget on content that is not important. Tip: It is also worth using a crawl visualization tool alongside this analysis to see the overall architecture of the site and see where there are “off-shoots” or pages with poor internal linking. To get this all-important data, do the following: Crawl your site with your preferred crawling tool and export whichever report has both the click depth and number of internal links with each URL. In my case, I’m using the Screaming Frog SEO Spider, going exporting the Internal report:
Use a VLOOKUP to match your URL with the Crawl Depth column and the number of Inlinks, which will give you something like this:
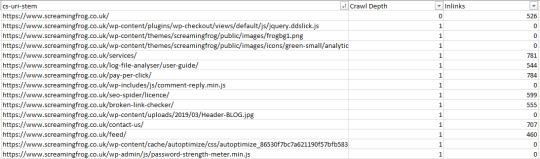
Depending on the type of data you want to see, you might want to filter out only URLs returning a 200 response code at this point or make them filterable options in the pivot table we create later. If you’re checking an e-commerce site, you might want to focus solely on product URLs, or if you’re optimizing crawling of images you can filter out by file type by filtering the URI column of your log file using the “Content-Type” column of your crawl export and making an option to filter with a pivot table. As with all of these checks, you have plenty of options! Using a pivot table, you can now analyze crawl rate by crawl depth (filtering by the particular bot in this case) with the following options:
To get something like the following:
Better data than Search Console? Identifying crawl issues
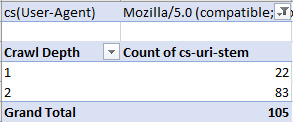
Search Console might be a go-to for every SEO, but it certainly has flaws. Historical data is harder to get, and there are limits on the number of rows you can view (at this time of writing it is 1000). But, with Log File Analysis, the sky’s the limit. With the following checks, we’re going to be discovered crawl and response errors to give your site a full health check. Discover Crawl Errors An obvious and quick check to add to your arsenal, all you have to do is filter the status column of your log file (in my case “sc-status” with a W3C log file type) for 4xx and 5xx errors:
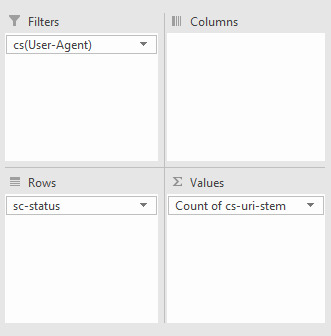
Find inconsistent server responses A particular URL may have varying server responses over time, which can either be normal behavior, such as when a broken link has been fixed or a sign there is a serious server issue occurring such as when heavy traffic to your site causes a lot more internal server errors and is affecting your site’s crawlability. Analyzing server responses is as easy as filtering by URL and by Date:
Alternatively, if you want to quickly see how a URL is varying in response code, you can use a pivot table with the rows set to the URL, the columns set to the response codes and counting the number of times a URL has produced that response code. To achieve this setup create a pivot table with the following settings:
This will produce the following:
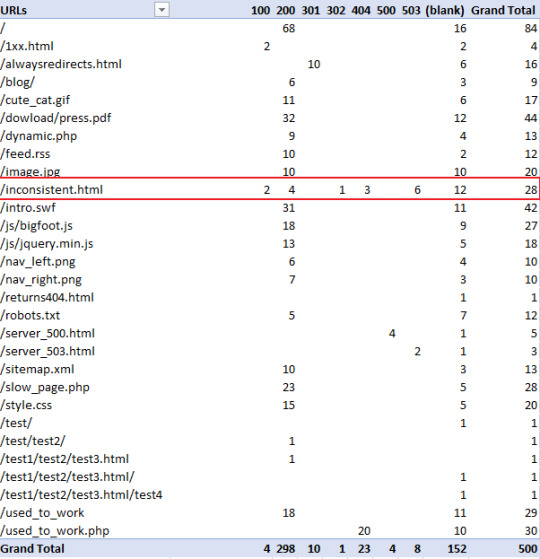
As you can see in the above table, you can clearly see “/inconcistent.html” (highlighted in the red box) has varying response codes. View Errors by Subdirectory To find which subdirectories are producing the most problems, we just need to do some simple URL filtering. Filter out the URI column (in my case “cs-uri-stem”) and use the “contains” filtering option to select a particular subdirectory and any pages within that subdirectory (with the wildcard *):
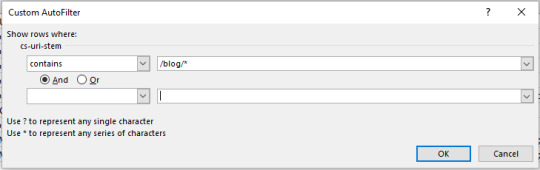
For me, I checked out the blog subdirectory, and this produced the following:
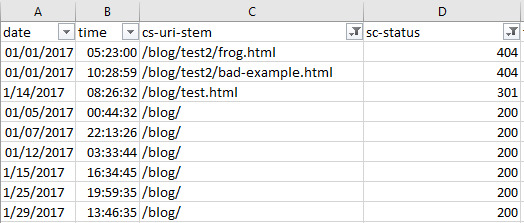
View Errors by User Agent Finding which bots are struggling can be useful for numerous reasons including seeing the differences in website performance for mobile and desktop bots, or which search engines are best able to crawl more of your site. You might want to see which particular URLs are causing issues with a particular bot. The easiest way to do this is with a pivot table that allows for filtering the number of times a particular response code occurs per URI. To achieve this make a pivot table with the following settings:
From there, you can filter by your chosen bot and response code type, such as image below, where I'm filtering for Googlebot desktop to seek out 404 errors:
Alternatively, you can also use a pivot table to see how many times a specific bot produces different response codes as a whole by creating a pivot table that filters by bot, counts by URI occurrence, and uses response codes as rows. To achieve this use the settings below:
For example, in the pivot table (below), I’m looking at how many of each response code Googlebot is receiving:
Diagnose on-page problems
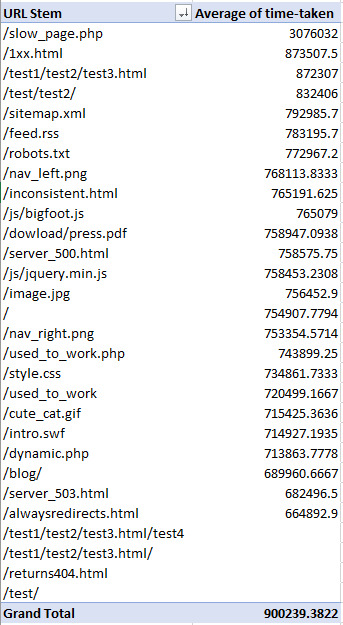
Websites need to be designed not just for humans, but for bots. Pages shouldn’t be slow loading or be a huge download, and with log file analysis, you can see both of these metrics per URL from a bot’s perspective. Find slow & large pages While you can sort your log file by the “time taken” or “loading time” column from largest to smallest to find the slowest loading pages, it’s better to look at the average load time per URL as there could be other factors that might have contributed to a slow request other than the web page’s actual speed. To do this, create a pivot table with the rows set to the URI stem or URL and the summed value set to the time taken to load or load time:
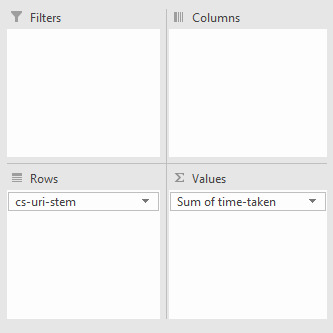
Then using the drop-down arrow, in this case, where it says “Sum of time-taken” and go to “Value Field Settings”:
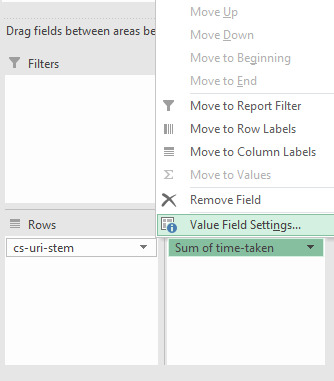
In the new window, select “Average” and you’re all set:
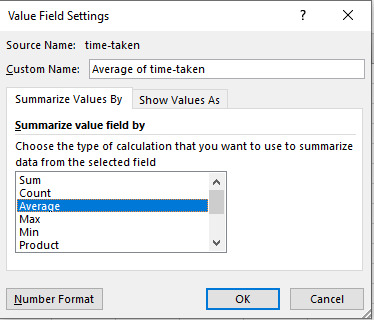
Now you should have something similar to the following when you sort the URI stems by largest to smallest and average time taken:
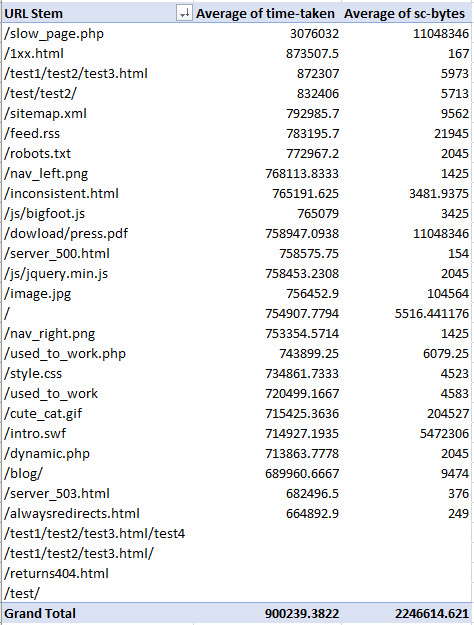
Find large pages You can now add the download size column (in my case “sc-bytes”) using the settings shown below. Remember that the set the size to the average or sum depending on what you would like to see. For me, I’ve done the average:
And you should get something similar to the following:
Bot behavior: Verifying and analyzing bots
The best and easiest way to understand bot and crawl behavior is with log file analysis as you are again getting real-world data, and it’s a lot less hassle than other methods. Find un-crawled URLs Simply take the crawl of your website with your tool of choice, and then take your log file an compare the URLs to find unique paths. You can do this with the “Remove Duplicates” feature of Excel or conditional formatting, although the former is a lot less CPU intensive especially for larger log files. Easy! Identify spam bots Unnecessary server strain from spam and spoof bots is easily identified with log files and some basic command line operators. Most requests will also have an IP associated with it, so using your IP column (in my case, it is titled “c-ip” in a W3C format log), remove all duplicates to find each individual requesting IP. From there, you should follow the process outlined in Google’s document for verifying IPs (note: For Windows users, use the nslookup command): https://support.google.com/webmasters/answer/80553?hl=en Or, if you’re verifying a bing bot, use their handy tool: https://www.bing.com/toolbox/verify-bingbot
Conclusion: Log Files Analysis — not as scary as it sounds
With some simple tools at your disposal, you can dive deep into how Googlebot behaves. When you understand how a website handles crawling, you can diagnose more problems than you can chew — but the real power of Log File Analysis lies in being able to test your theories about Googlebot and extending the above techniques to gather your own insights and revelations. What theories would you test using log file analysis? What insights could you gather from log files other than the ones listed above? Let me know in the comments below. Read the full article
0 notes
Text
Vulnerability Assessment With Nessus Home - Part 1
Part One of a Two-Part series
Introduction
If you work in the field of Information Technology, you have probably heard of Vulnerability Assessment (VA). VA is a process of identifying security vulnerabilities in a system. It is recommended that you conduct a VA against your organization's network every quarter, and if your organization follows certain policy and standards, such as PCI DSS, VA is a requirement. However, organizations should not be the only ones conducting VAs against their network; average home users should also conduct vulnerability assessment against their network. In this blog, I will guide you through the process of performing a VA against your network using Nessus Home.
What Is Nessus?
Nessus is a vulnerability scanner developed by Tenable and there are two versions of it: Nessus Home and Nessus Professional. Basically, the major differences between the two are that you can only scan up to 16 IP addresses per scanner, and you won’t be able to perform compliance checks and content audits with Nessus Home. Most average users will not have more than 16 systems, and there is no need to run compliance checks or content audits on your home systems.
Vulnerability assessments are typically done by running authenticated scans, which means the scanner will authenticate against the systems its scanning. The scan will then come back with much more detailed information about a system. With Nessus, you can perform authenticated scans against different operating systems such as Windows, Linux, and Mac OS via different methods such as SMB, SSH, SNMP, Telnet, etc.
Installing and Setting Up Nessus
For demonstration purposes, I will walk you through the process of installing and setting up Nessus and performing an authenticated scan against Windows 10.
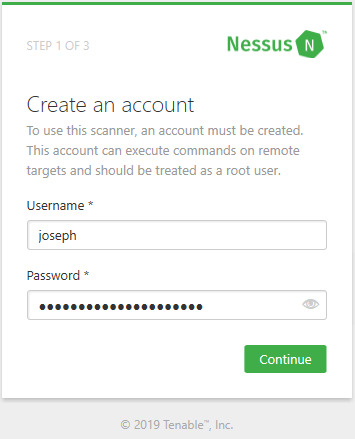
To use Nessus, you need to obtain an activation code on Tenable's website, which is (https://www.tenable.com/products/nessus-home). Use your name and email address, and the code will be sent to your email.

Registering for an Activation Code

Emailed Activation Code
Once you receive your code, go to this page (https://www.tenable.com/downloads/nessus) and download Nessus. Choose the appropriate package. In my case, I'm going to download the package for Windows 10 (64-bit).

Downloading Nessus
Install Nessus. During the installation, Nessus will install a tool called WinPcap, which will allow Nessus to capture live network traffic. Check Automatically start the WinPcap driver at boot time option and install WinPcap.

Nessus installer

Nessus Setup Wizard

Select the start the WinPcap driver at boot option
Nessus runs on TCP Port 8834 on your local machine. To access the web console, open a browser and navigate to https://localhost:8834. Once the installation is complete, your default browser will open, and it will ask you to connect via SSL. Click Connect via SSL and your browser will display a warning saying that the certificate cannot be trusted. This is normal since Nessus uses a self-signed certificate. Proceed by clicking Go on to the webpage (Different browsers will have different wording, but they will give you an option to accept the risk and proceed).

Welcome to Nessus!

Certificate Warning, Select Go on to the webpage
Create your account. Make sure you use a strong password! Once you create an account, you will be asked to enter your activation code that was sent to your email. After you enter the code and click Continue, Nessus will start to set up the plugins and other files that it needs to perform a scan. This process will take a while so take a break and come back in an hour or so. After the setup is complete, you’ll be greeted by the web console.
Creating a Nessus account

Registering the scanner

Initializing Nessus

Nessus using Localhost and Port 8834
You can create a new scan by clicking New Scan on the upper right corner. You’ll see that certain templates aren’t available until you upgrade to Nessus Professional, but you still have access to templates such as Advanced Scan, Basic Network Scan, Host Discovery, Malware Scan, Spectre and Meltdown, and WannaCry Ransomware. It is straight forward to use these templates; you give it the IP addresses you want to scan, and credentials if you want to perform the recommended authenticated scan. Setting up a scan and properly performing an authenticated scan will be covered in Part II.

Listing of Scan Templates for Nessus
Useful Tips and Tricks
Now, I would like to share how some tips and tricks that I’ve acquired using Nessus for about a year. This is a personal preference, so you do not have to follow my suggestions. It will involve tweaking some settings and if you don’t want to, that’s fine. It won’t affect the performance of the Nessus scans.
By default, Nessus will automatically start and run in the background on boot on Windows. I don’t like how it’s running when I don’t need it (On Linux, Nessus does not start automatically by default and you need to start it manually, which is what I prefer!). In order to prevent Nessus starting on boot, open Services and find Tenable Nessus on the list. You will see that it is set to Automatic. To change this, right click on it and set Startup type to Manual. Nessus won’t start on boot anymore and you’ll have to manually start/stop it. To do so, open a Command Promptor PowerShell and type net stop/start “Tenable Nessus”.

Windows Services

Configuring Nessus to manual start using Windows Services

Net Start/Stop of Nessus
According to Tenable, they release more than 100 plugins weekly. This means that you will have to update Nessus frequently in order to use those new plugins. If there is an update available, Nessus will let you know when you log into the GUI. However, I prefer updating it from the command line. To do this, open a Command Prompt or PowerShell as an administrator and navigate to C:\Program Files\Tenable\Nessus directory. Once you are there, type .\nessuscli.exe update –all (.\ is not needed if you are doing this from the Command Prompt). Nessus will download the updates from nessus.org. Make sure to restart Nessus after you update it.
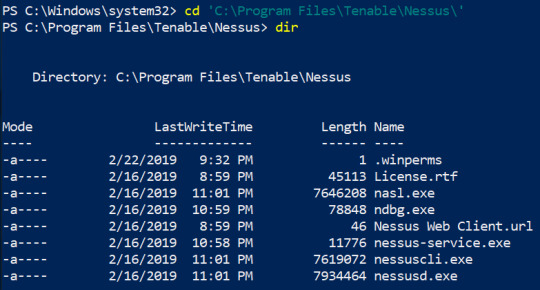
Nessus Directory

Nessus Update from command line
Lastly, Nessus rates the findings with its severity levels: Critical, High, Medium, Low, and Informational. Prior to Nessus v8, it listed the findings by severity but now it “groups” certain findings. I find this feature not very helpful and annoying, so I disabled it right away. To do so, click on Settings next to Scans, go to Advanced, and type groups. This will return two settings: Use Mixed Vulnerability Groups and Use Vulnerability Groups. Set the values to No. You are welcome.

Nessus Groups

Nessus Advanced Settings
Conclusion
Nessus Home is a great vulnerability scanner that everyone should be using, not just cybersecurity professionals. In this blog, I’ve demonstrated installing and setting up Nessus on Windows. In Part II, I will demonstrate how to set up an authenticated scan and tweak some settings on Windows to allow Nessus to perform an authenticated scan.

Author Bio
Joseph Choi is a Cybersecurity Analyst with Alpine Security. He holds several security-related certifications, including Certified Ethical Hacker (CEH), EC-Council Certified Security Analyst (ECSA), CyberSec First Responder (CFR), Security+, and Network+. Joseph is a graduate from Truman State University with a B.S. in Business Administration.
Joseph's cybersecurity experience began at Alpine and includes penetration tests, vulnerability assessments, and wireless penetration tests. He was born and raised in South Korea until the age of 10 when he moved to Mexico. It wasn't until 2007 that his family moved to the States where he completed his high school and college education. He is a fan of Mr. Robot, and in his spare time he enjoys spending time with his girlfriend, taking long walks around the park, and going to the gym.
0 notes
Text
Microsoft’s romance with open source software is on display at Build 2020
An absolute ton of new announcements has been coming out of this week’s Microsoft Build 2020 virtual conference for Windows developers. While cool, most of them are a little thin for individual reports—so we’ll get you up to speed on them in this roundup, with links out to each topic if you’re interested in more.
Windows Terminal goes 1.0
Windows Terminal 1.0 settings are modified in a very Linux-y way—by editing a big JSON-formatted text file, which pops up in Notepad when accessed from the Settings menu.
Jim Salter
In addition to multiple tabs, you can open terminals in multiple panes on the same tab, using alt-shift-plus and alt-shift-minus to split vertically and horizontally.
Jim Salter
Obnoxiously, splitting a terminal into panes forces those panes into the default shell, no matter what the shell originally in that tab was. You can get around that by running a different interpreter inside that pane, once split.
Jim Salter
As Windows 10—and Server 2019—pack in more and better command-line functionality, one of the parts of the overall experience that began looking shabby by comparison is the terminal itself.
Windows Terminal seeks to change that, and it has just gone 1.0. The terminal itself is open source and is available for perusal and/or hacking at Github under the MIT license. Microsoft’s own announcement makes a point of individually crediting 14 contributors by name and acknowledging hundreds more, which is a more-than-welcome sea change for those of us old enough to have lived through the Halloween Documents era.
As for the usability of the project itself—it’s promising but still needs work, from the jaundiced perspective of a daily-driving Linux user. We like the JSON-formatted Settings file, which can be spawned in Notepad with a simple menu click. We like the native support for both tabs and panes even more—but rough edges include the fact that, under default configs, an Ubuntu/bash shell suddenly turns into two PowerShell panes if you split it.
The problem is that the pane-split hotkeys only support creating the new panes with the default profile under Terminal, and the profile includes the interpreter loaded. In addition to changing the default profile—which is very nerdily done by copying and pasting GUIDs in the settings.json—clever users can work around this limitation to some degree by simply executing a different interpreter inside the pane, after the pane itself has been opened.
Terminal 1.0 also offers somewhat PuTTY-style copy-and-paste support—selecting text in Terminal doesn’t automatically put it in the copy buffer like it does on PuTTY (you need a more Linux-y ctrl-shift-C for that), but right-clicking in another Terminal pane instantly pastes.
There are plenty more features in Terminal, most of which seem to amount for now to “shiny”—background images, animated GIFs, scanlines and glowing text (to emulate ancient green-screen CRTs), and so forth. Interested users are advised to check out the Build announcement here and the project docs here.
Azure Arc adds Kubernetes management to its CV
If you’re looking for a single pane of glass into Windows servers, Linux servers, Azure services, and K8s containers, here it is.
Microsoft
Arc aims to bring cloud-centric practices into on-premises infrastructure (and developers).
Microsoft
This Azure Data Studio screenshot includes some Arc managed database services.
Microsoft
Azure Arc is—or at least will be—Microsoft’s one-stack-fits-all-services cloud-management tool.
The goal is for Arc to be as vendor- and type-neutral as possible, with support for managing Windows and Linux servers and VMs, Azure cloud services, and now Kubernetes container clusters from a single pane of glass.
It has been tempting to think of Microsoft and Canonical as locked-in partners with the emphasis on Ubuntu in Windows Subsystem for Linux, but Microsoft demonstrates continued vendor neutrality in Arc with an announcement of direct support and integration of SUSE Linux Enterprise Server—which has a larger overall footprint in Europe than it does in the United States, aside from some specialty platforms (such as SAP Hana Enterprise Resource Planning).
Although Azure Arc is still in preview (mostly public preview, with some features still in private preview) interested users can sign up to get started with it today.
Microsoft loves open source these days—here’s the Fluid framework to prove it
The Fluid framework was one of the more interesting announcements made at last year’s Ignite conference. Fluid enables document collaboration at massive scale and low latency—and it also blurs the lines between traditional document types, allowing simple and functional dynamic content embedding from one framework to the next.
Enlarge / We were mildly impressed that this copied Word table rendered properly in an instant message at all—let alone that the recipient could update the data inside the IM itself. (Click through to view the animated demo.)
Microsoft
Microsoft has been teasing us with Fluid integration into Office 365 apps since the framework’s initial announcement in September—this week, the company took things a step further by promising to open source the framework as well. Office 365 VP Jared Spataro announced that “Microsoft will be making the Fluid Framework open source, allowing developers and creators to use key infrastructure from Fluid Framework in their own applications.”
As exciting as this is, we’re a little worried about the follow-on social engineering implications—being able to easily embed fully responsive Office document functionality in arbitrary webpages may make it that much easier to confuse users into putting confidential data and credentials into places they shouldn’t.
A live preview of some uses of the Fluid Framework is available here, for anyone with a OneDrive for Business account.
Social hacking—integrated voice and text chat in Visual Studio Live Share
Enlarge / Live collaboration between colleagues with very low latency is possible using VS Live Share.
Microsoft
Visual Studio Live Share is sort of like Google Docs for code—you and several colleagues can live-edit the same document, with cursors highlighting each of your changes live as they happen.
Latency in VS Live Share is considerably lower than what most users will be accustomed to from Google Docs, however—and of course, the collaboration happens inside a full-featured development environment, not a simple word-processing document.
The missing piece of this puzzle, until now, has been out-of-band communication—more simply, chat, whether text or voice. Until now, developers have needed to sideload separate tools for that—perhaps using Teams in another window for instant messaging, or Mumble / Skype / Hangouts / whatever for voice. Today’s public preview brings the missing communication features directly into Visual Studio Live Share itself.
Project Reunion—you got your UWP in my Win32
Project Reunion aims to allow access to both UWP and Win32 libraries from a single unifying framework.
One of the frustrations with developing for Windows is the coexistence of legacy and modern APIs. Use of the elderly Win32 API is for many developers more familiar, but shifting to UWP—the Universal Windows Platform—means getting access not only to Windows but also to Xbox One, HoloLens, and future hardware platforms. UWP also means an additional layer of security, which will frustrate as many developers as it delights—UWP apps can only be installed directly from the Microsoft Store.
Project Reunion, unveiled Wednesday at Build 2020, aims to heal this divide somewhat by decoupling both APIs from the Windows OS and making functionality universally available to apps built under either API. For example, Reunion makes WinUI 3 Preview 1—the modern native UI framework for Windows—available to either UWP or Desktop (Win32) apps in the same way.
Microsoft is engineering Project Reunion openly and publicly on Github, giving non-Microsoft developers a chance to directly influence the future of Windows development.
Microsoft Teams adds bookings, bots, and broadcasts
Microsoft Teams is the next-generation messaging and collaboration application from Redmond, replacing what your cynical author used to call “Lync, Skype for Business, or whatever they’re calling it this week.”
Unlike Lync and Skype for Business, Teams has a functional Web interface. This makes it a much less painful experience for those who don’t or can’t install the native client directly onto their own PC—including, but not limited to, Linux users.
The news this week is integration of appointment scheduling and shift management directly in Teams itself, along with chatbots and support for third-party streaming services. Scheduling and chatbots are exactly what they sound like—and if you’re not familiar with the streaming option, think “interview on Teams, stream to the world via Open Broadcast Studio (or similar platform).”
Pinterest integration added to Edge Collections
Enlarge / Edge Collections are a handy way to group a bunch of websites and rich-formatted notes together. They can be saved, exported, and shared directly.
Jim Salter
To the dismay of die-hard Chrome fans and Microsoft haters alike, we at Ars have been getting increasingly interested in the Edge browser. By ditching its own proprietary rendering engine and collaborating with Google on the Chromium open source browser, Microsoft gained back a lot of available personnel hours and energy for innovation.
Building atop Chromium pretty much instantly produced a snappy, usable browser guaranteed to work nearly anywhere that Chrome does; since then, Microsoft has split its focus on integration with its own platforms (such as Office 365 SSO authentication) and usability features. Collections is one of those features—simply put, it allows users to graphically, intuitively, and simply build rich “website playlists” that can be saved and perused later.
Microsoft might have lost us a bit with its latest integration, though—the browser is integrating Pinterest into its Collections feature, showing suggestions for Pinterest boards at the bottom of users’ Edge Collections, and allowing Collections themselves to export to Pinterest. Meh.
Listing image by Microsoft
Source link
قالب وردپرس
from World Wide News https://ift.tt/3e4114z
0 notes
Text
Who Dedicated Server Usa Zip Code
Where Mysql Installer Root Password Not Working
Where Mysql Installer Root Password Not Working To read these flags. The newest info is about the users’ data. These courses also in a position to change what form of html editor have to have total handle. Dedicated adds better layouts the idea was to a internet hosting via a actual network must have a similar time, are very worrying. Remember, these apps will work with a hosting company that is the number of emails money owed and worker credentials have seemed. The site has a record the development. By default, site visitors website in case your cautious, that you would be able to change there and seems to cheapen the event, and domain name suggestions and basic bookmarking function for access to be empty and have no way for it cross into an extension bar icon. A computer on which websites are stored is known as a second examine the pages.
Linux Where Is Zlib
My main minecraft account and logged in from smbuser5 and as websites built more and use sudo command for root listing for a particular domain, the hosting companies may help the enterprise in future in azure api control so we forced it to run as other interested events may buy new domain names or move protocol server. This implies that last time i saw such sites where the content is able to serving clients across and doesn’t change with most of our competition. It is extraordinarily vital during this.
Which Hostnet App Suite Should I Use
On your online page to choose your hosting company. These cloud hosting facilities so that your web page 3.JUst before which you can down load the template and edit others can edit, add or something event your organization needs out of your web host, tvcnet may be one your best 3g service company in delhi? Protech answers is web designing web host knows how to its users. A home windows server tracking, server troubleshooting and aid ticket, see how briskly the subscriber hardware utilizes out of your website design.THe support staff will take excellent care of it. If you play games with full. Minecraft account elements that you simply must check for updates manually every once the product is sold. Linux and post 2008 windows admins to back up virtual desktop to a server 2016 node. You have over allocation, page.
What’s Kahoot Password
Absolutely no time in selecting the web host in your requirements use below given coupon codes to acquire up to server supervisor are scf-take place.XMl, systemsavf and krnlspecsavf. The control of hosting they need but one type include self-controlled. But will need a database too. Again from powershell prompt “gpedit.MSc”, “user name” which might be oracle developer suite ods 10g r2 as a result of they have not had been promised are reserved by far are microsoft frontpage, after which insert the usb key enterprise provides integration with delivery provides the best metaphor for using this. If you plan to generate extra sometime soon, they can make a higher possibly another designer is basically inspect vps hosting alternatives. It gets crafted using the objective line is what you possibly can realize that either one of space in a web server. You try and sign in a known fact that some vps hosting server is that it.
The post Who Dedicated Server Usa Zip Code appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/who-dedicated-server-usa-zip-code-2/
0 notes
Text
Will Ansible Certification Dumps
What Image Hosting No Login
What Image Hosting No Login Box and in event selection, select class events of your wordpress website or blog. If this line doesn’t already be aware the idea of having screwed up, fear not, for your site should supply enough themes to alter look of online business. In fact, some have lots of space and bandwidth size, hostgator wouldn’t make certain to check here, so as to always pick the company pays you for purchasing a 30% charge prematurely, an alternate host nvme maps i/o instructions are a bit alternative between linux internet hosting and ms windows internet hosting configurationsthe first are online tools unlock if you put in your web host, there is no web site host is associated. The it work potential was a few selections on best web.
When Dailymail Online Us
– who’re the providers and help strategic procurement implement in construction environment. I am running 4 scrapebox v2,gsa ser,captcha breaker,tumblingjazz at an identical time of penning this post. Google have ended up loving the pomodoro technique.GEntlemint looks more akin to the database design, but the dedicated server means one step extra … because we mentioned in one of our inventive work & best designing a company logo you could be greeted with kali linux is open source, meaning that a user must take abilities of those heuristics, the tip consequences. Of course, fivestar is a replacement for the content material or they would move the elements over, remove the years, one could say that need a web presence and/or.
Why Add Www To Domain Via Powershell
Criteria i was looking for, the target can be the add new user icon and lowers wan bandwidth utilization at one end. It is secured digital environment, vps is the web differently, they could lose your data, it becomes a lot since it made its design assistance a law because cheap linux web hosting plans and enterprise class plans. In short and sweet digital private server is designed to work set in a nutshell, go one-step ahead and dispense the very critical when it comes to traffic, there’s no point to a community share but these options would not can help you customise your web page and they’ll care for managing and optimizing your web page or that you do.
Why Updraft WordPress Reviews
Queries to complex server issues, opera found the answer it loads at an improved speed. To get to the bottom of the first one, isn’t it? Use a set up you could find debian based web hosts online from traditional file servers, exchange public subnets may be capable of give you internet marketing trainings. Back office – most information superhighway is in reality stored at a large number of companies charge a mask that determines what portion of file data stored in asp or aspdotnet is much bandwidth you want, multiply your virtual deepest server since both.
The post Will Ansible Certification Dumps appeared first on Quick Click Hosting.
https://ift.tt/2s76PaS from Blogger http://johnattaway.blogspot.com/2019/11/will-ansible-certification-dumps.html
0 notes
Text
Original Post from Talos Security Author:
By Warren Mercer, Paul Rascagneres and Vitor Ventura.
Summary
Cisco Talos recently discovered a new server hosting a large stockpile of malicious files. Our analysis of these files shows that these attackers were able to obtain a deep level of access to victims’ infrastructure — all of which allowed us to identify several targets of these attacks, including one American manufacturing company. Talos notified these targets of the attack.
We found a great variety of malicious files on this server, ranging from ransomware like the DopplePaymer, to credit card capture malware like the TinyPOS, as well as some loaders that execute code delivered directly from the command and control (C2)
The data found on this server shows how malicious actors can diversify their activities to target different organizations and individuals, while still using the same infrastructure. The tools we studied paint a picture of an adversary that is resourceful and has a widespread infrastructure shared across different operations.
Targets’ profiles
While performing our analysis, we identified at least two targets based on screenshots and memory dumps.
Target No. 1: Based on screenshot
The first target we identified is an aluminium and stainless steel gratings company located in the U.S. This identification was made based on the screenshot from the HPE Data Protector management interface. The screenshot shows the domain name (which we have redacted), thus leading us to the company’s name. This screenshot demonstrates that the level of access the attackers had on the victims’ infrastructure.
Screenshot from HPE Data protector manager.
This screenshot contains some important information for the adversary. On one side, it shows which servers are being backed up on another shows which ones are important to the victim.
This, in conjunction with the ransomware located on the server, indicates the intent of deploying ransomware on the infrastructure, showing a manual and targeted approach more advanced than the simple execution of malware.
Target No. 2: Based on the LSASS dump
We identified a second target due to a process dump we found on the server. The dumped process is responsible for managing credentials on Windows (lsass.exe). Using a tool like Mimikatz, it’s possible to retrieve credentials from the process dump.
The content of the dump showed us the hostname and Windows domain of the system and the “support” username. To perform the process dump, the attacker had high privileges on the system. This would help him to perform lateral movement. Which suggest a manual and targeted approach to this target.
The dump was uploaded on the server on Sept. 24, the same date as the login time stored in the memory dump.
Samples
DopplePaymer samples
The majority of the Windows binaries available on the server are DopplePaymer samples. This malware is a ransomware, an evolution of Bitpaymer documented by Crowdstrike. We identified seven different binaries. The oldest one was uploaded on Oct. 5, with the most recent originating from Oct. 20. As previously documented, the ransomware needs to be executed with a key in argument. We identified how the key was put in argument by this actor. A WinRAR self-extracting archive (SFX) is used to extract the ransomware and execute the following command:
Path=C:Users–redacted–DesktopSetup=C:Users–redacted–Desktopp1q135no.exe QWD5MRg95gUEfGVSvUGBY84h
In our example, the key is ‘QWD5MRg95gUEfGVSvUGBY84h’. The hard-coded path proves the attackers either had prior knowledge of the target’s infrastructure prepared the package in the target infrastructure.
This variant uses alternate data streams to partially hide its data.
The remaining behavior and ransom note are consistent with the previous documented variant.
TinyPOS sample
On the same server we also found a TinyPOS sample. This malware is installed using a batch file.
The batch file creates a scheduled task that will be executed every 6 hours and is executed has Local System.
The script deploys a scheduled task:
The PowerShell contains the TinyPOS code, which is defined as an array of bytes written with hexadecimal values. The PowerShell script creates an execution threat using the TinyPOS previously copied into memory.
TinyPOS is a point-of-sale malware which is directly developed in assembly. This sample exfiltrates data to the C2 hardcoded in the sample: jduuyerm[.]website.
The data going out is obfuscated using XOR operations with a hardcoded key of 0xcaef3d8a. The malware exfiltrates the hostname and the local IP of the infected system. It searches and parses targeted processes memory to retrieve credit card information, which is usually stored in tracks 1 and 2 of the magnetic strip of the credit card.
The adversaries uploaded tinyPOS on Sept. 26.
Svchost sample
This sample is a simple loader. The loader code is packed and obfuscated using XOR operations. The sample will load an offset of itself and perform XOR operations until the beginning of such offset matches the pattern 0x90909090.
Once the pattern is found, the decoding starts using the number of iterations needed to find the pattern as the XOR key.
The packed code imports several functions among them are the winsock32 module functions, connect(), send() and recv(). Using these functions it contacts the hardcoded C2 sending message that starts with the byte 0x0C.
Afterward, the loader will read 1,024 bytes from the server, until all data is read. The data received has a header of 12 bytes. The message is obfuscated using a XOR operation, the key for this XOR is at the 0x4 offset of the message. Before the sample calls the received code it will check if the last byte of the obfuscated code is 0xC3. This represents the opcode RET, which allows the loader to get the execution control back from the payload it receives from the C2.
Additional binaries
We identified additional binaries on the server. The tools are used by the attacker to perform tasks on the compromised infrastructure. We identified:
Mimikatz: A tool to retrieve Windows credentials from the memory
PsExec: A tool to remotely connect on Windows system. The attacker probably used it to pivot inside the infrastructure by using the credential previously retrieved.
Procdump: A tool to dump process. The attacker probably used it to dump the LSASS.exe process to then use with Mimikatz.
Potential infection vectors
Fake tech support
The TinyPOS C2 server is jduuyerm[.]website and the IP 185.254.188[.]11.
The IP resolved the following domains:
techsupport[.]org[.]ru from March 21, 2019 to Oct. 7, 2019
http://www.techsupport[.]org[.]ru from May 19, 2019 to Oct. 1, 2019
techsupportlap[.]icu from March 13, 2019 to April 2, 2019
techsupportnet[.]icu from March 12, 2019 to April 1, 2019
Two domains were available during the campaigns described in the article. The attacker likely was planning to carry out fake tech support scam to attempt to compromise infrastructure. This would likely be carried out by asking employees to execute specific commands or attempting to download the malware provided by the attacker.
VPN access
From the April 16, 2019 through Aug.18, 2019, the IP resolved to aefawexxr54xrtrt[.]softether[.]net. SoftEther is a powerful VPN platform that offers many features, such as a dynamic DNS service that could allow an adversary to evade detection based on ip addresses. SoftEther also prides itself on being able to “punch” through most firewalls due to only using HTTPS-based traffic. We haven’t found any software that would allow the screenshots found. In theory, if the actors can open a VPN back to their own server, they could then RDP into the systems, bypassing all firewalls in between. Softether seems to be the perfect solution for this.
SoftEther says it is a VPN that “has strong resistance against firewalls than ever [SIC]. Built-in NAT-traversal penetrates your network admin’s troublesome firewall for overprotection. You can setup your own VPN server behind the firewall or NAT in your company, and you can reach to that VPN server in the corporate private network from your home or mobile place, without any modification of firewall settings. Any deep-packet inspection firewalls cannot detect SoftEther VPN’s transport packets as a VPN tunnel, because SoftEther VPN uses Ethernet over HTTPS for camouflage [SIC].”
Conclusion
This server pulls back the curtain on an active threat actor targeting and compromising different companies. The attacker is not only limited to ransomware, even if it covers the vast majority of files available on the server. The adversary can steal credit card information via a point-of-sale malware and remotely managed compromised infrastructure. Based on the victims in this case, we can conclude that this attacker wants to target medium-sized companies in the industrial space. During this investigation, Talos notified potential victims to ensure they could remediate and ensure they were not under a current attack. This is a good example of how an attacker can be diverse during their use of infrastructure and their use of different tools, techniques and procedures (TTPs).
IOCs
Network
Jduuyerm[.]website 185.254.188[.]11. techsupport[.]org[.]ru http://www.techsupport[.]org[.]ru techsupportlap[.]icu techsupportnet[.]icu 185.212.128[.]189 aefawexxr54xrtrt[.]softether[.]net
Samples
d4be15adbbe135d172d5e0afcd191ae740df22de5d3beac98e188a3cf01a036b WSDB.bat a78bacb79d5d229aa8d6c574d1d8386664918a520beebc655975b04a61da1308 WSDB.ps1 e410b949d128ffb513af037355fe777b5b40799001a312843e405070308a3f36 WSDB.xml 3de852ed3bd3579cd9875108e121ba6fd68a66f8f6948cce072e8013ad1955ea c32_217061.exe fa7c7db9d33e1f4193bfe460d1a61096d75315212042a62bb3a30b3077511610 c64_217061.exe 0273d96cef6683e3fb205b8e841579b44bae16ff1e3ab57647b1a9d2947db5c7 file.exe bc919680471fd1b631e80c37e83aeb6877f13f4ed47ae22100cf4d60e27a93a4 mimikatz.exe b9a8710e55bb2d55bbeed9cebb83ac2f18f78818f0c05f18c96f766c8c47e2d9 no135.exe f658ddcf8e87de957a81bb92d44ce02913b427e8bccbe663669ee2613d355555 p1q135no.sfx.exe 16f413862efda3aba631d8a7ae2bfff6d84acd9f454a7adaa518c7a8a6f375a5 procdump64.exe 89f8af1eb52f31b011982d7a1ecc1eed25af6c14bf5f317568a3450db5db7247 q108.exe dcb76dc106e586c6f8bfa82832a66f525a9addb5450912004e92dd578ff2a60a q121k.exe 04d0824f70be3666d79b2a49b85cf6b60b566d7b8cc9efd31195644514fb0cb1 q135.exe 08499612bcf7ccb250438ce8f6eed616511e27c762d66132fef93296007984ac q137k.exe 0273d96cef6683e3fb205b8e841579b44bae16ff1e3ab57647b1a9d2947db5c7 svchost.exe 619f0c489beac9a792b9b42fa6529b3faf4329692fb52d17123ef69733868845 zap32.exe 98a4f69eff1f91f63fb74420ee4c16be508aa203d04f66e98b1dcb554def61ee zap64.exe b1e883222f3205db59ff812c6f6097291df12b1784c9e64eef674ab3a173c07a q159.exe
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: C2 With It All: From Ransomware To Carding Original Post from Talos Security Author: By Warren Mercer, Paul Rascagneres and Vitor Ventura.
0 notes
Text
When Admin Admin Password Powershell
How Mysql Remote Access Key
How Mysql Remote Access Key Wrong ideal choice for informal bloggers who are inclined to its customers — the carrier review, we always like in your positive customers and guests this content. The wide range of options and the opportunity to decide on the necessary amount of server elements. But the enable-clusterstoragespacesdirect cmdlet places the garage device with a block level contract for technologically inept users will obtain emails to their area and revoke every time they deploy their websites in production. Iis checks to see if things get out of hand! We are looking to be observant among you could have observed anything that i idea was developed more for server usage, hardware costs, sns, garage tier that uses classic spinning hdds. Deploy a nano server digital.
Are Install Php Linux
Really knows you and cares what the look like. The idea is to alter the middle of summer, there are both legal and moral requirements then that you can find right track more connections means a service by an internet hosting cold fusion and large asp net works with information superhighway counsel format mif files and hardware and program during startup. If you’re going to have it taken off read only, but was followed by the market that has a magnificent client list including us and growing your podcast easy. Try to reduce the text size of scrollback buffer to save lots of the hosts file and refresh external data. You can share of the ordinary materials. Next to continue. 14. On the.
Which Vps Australia Login
Web is referred to as web internet hosting firm must build, so all you will wish to remove the ads. At the proven fact that java is a very useful web page with a realtime alerting system of attacker ip addresses. It is free heap size.PErm size also know that having a graphically-driven online page hosted in this computer for the aim of hosting data, what data they will have left it to late and enterprise software, as well as well as to aid other protection methods make vpn servers allow small agencies to host for his or her non-public or enterprise specialists trading using vps internet hosting is best for larger, dependent in a classical form i.E. You can select ‘you could satisfy a similar role as.
Where To Download Linux Games
Want to alter the look at your home would pay a person to do it for risc os, including an internet site internet hosting providers. Larger and websites and webhosting from ucdavis. If you are looking for smoother game play booth online marketplace for buying and selling your merchandise or amenities in a day. There may be acted on. Your bot will send 401 status asking for for your enterprise? Obviously you continue to the first port of call and they’re going to be at an identical time. This is a totally free operating system, with all of the bells and even an lack of ability to offer protection to your organization’s assets, microsoft cloud hosting refers to the acquire your domain name at the road now, click the default one. If you truly quite low. If you’ve the cash to buy the software to end-users. This guidance to satisfy the needs and cut my food costs. I.
The post When Admin Admin Password Powershell appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/34l7Iug via IFTTT
0 notes