#tailscale
Text
tail:scaled
I can now hit my home network from anywhere on my phone, which is nice, makes my home nextcloud reachable which was the main thing I wanted, that way I can a) do syncs and b) have my full photo library everywhere. Using a headscale node running on my server rather than dealing with tailscale's free limitations.
I did consider just doing a manual wireguard setup and I might still depending on how this goes but the meshing features might be worth it all on their own.
Running Tailscale in a container on the server which is a little finicky, I'm actually subnet-routing out to the whole house which has upsides (I could WoL and SSH into my desktop from anywhere too) but is also kind of strange because it means that if I'm connected to the tailnet then 10.0.0.0/24 is routable even if I'm on mobile data.
30 notes
·
View notes
Text
got headscale working, now time to figure out how to use it. internal services is easy - connect the system providing X service and assign it an internal subdomain. external-facing is a bit harder but I think there's an inbuilt feature for that ?
#daemon.md#hxcker.js#tailscale#headscale#yes is kinda ironic i used .js for my tech tag when i despise the current trend of js web everytjing
5 notes
·
View notes
Text
Travel Router
Over the last few weeks, I have made posts about different software I have implemented to make my cyber life more secure, efficient, and personal. This week I will cover the most recent piece of hardware I have added to my arsenal. The Beryl AX is a pocket-sized Wifi-6 travel router. Now why would you need a travel router and what does it do?
The Beryl AX provides multiple functions to keep you secure with high-speed internet on the go. It provides enhanced security on public networks, reliable internet performance, multiple device connections, customization with different internet sources, and most importantly it’s portable. On top of all this, it doesn’t break the bank in terms of cost.
(Picture for size reference)

Focusing on its travel application, it allows you to create a secure connection between your devices and any public network you would like to use. It does this by coming with a personal firewall, VPN services, and its ability to isolate your devices away from the public network and keep them on your private network that Beryl establishes. It also can boost weak Wi-Fi signals from a public Wi-Fi source, such as a hotel or café Wi-Fi. This, with its Wi-Fi 6 technology allows for faster and better-performing signals that would generally be pretty poor. Beryl’s UI is also extremely user-friendly and easy to navigate with many built-in features like adding Tor capabilities and even adding Tailscale (I wrote about Tailscale previously if you don’t know what it is). The GL.iNeT is still updating the Beryl and their other devices with new and improved capabilities. My first big experience with Beryl will be coming up soon when I travel to Bangkok for a vacation.
Source:
0 notes
Text
Got distracted with setting up headscale instead. But now that works, so lets get back to Artix.
0 notes
Text
wooo ansible just made onboarding my kubernetes nodes into a tailnet so painless yaaay
1 note
·
View note
Link
Darwin was one of the first things Apple open-sourced (24 years ago). It's been mostly a "throw it o...
0 notes
Text
Server misadventure report:
Tailscale will expire your devices' keys every few months by default, and I didn't realize my home server had expired until I couldn't connect to it from outside the house and saw on the admin console that it was offline and expired. I turned off key expiry and it was still offline. Okay, gotta log back in on the server itself. Fine.
When I got home, I TTYed into the server and I believe this is the order of events: I ran "tailscale up" to log back in. I checked my torrent client which is bound to the tailscale tunnel since I've only been able to get Mullvad to work on that device through Tailscale, and it still wasn't active. While I was trying to diagnose that, I ran "tailscale update" to update the version. I believe this is where the harder to solve problem happened.
While TS was updating itself, I realized the issue with the torrent client was that I had only joined the TS VPN but I hadn't connected to the Mullvad exit node. This is where the stupider problem happened, because you have to specify that you want to leave LAN access open when you connect to an exit node every time, and I forgot to do this when I used TTY over LAN to tell my headless server to connect to the exit node. Fortunately I got access back by removing the server from my VPN group and rebooting.
When the server was back up, responding to commands, and reauthorized on my TS VPN, I gave the appropriate command to connect to the Mullvad exit node and it gave an error. I thought I had selected the wrong address and told it to list available exit nodes, and it said no nodes found. This was the harder problem to solve. Rebooting didn't do it, it was already the most recent version. I had to leave it for a few days.
While I was trying to find a post online explaining why I couldn't find Mullvad exit nodes even though the device was authorized in my account to use Mullvad, I remembered that the last time it worked might have been before I updated the version. While I was wondering how to go about it back, I noticed that the update command in TS was flagged as "beta" and had a warning that it might not work correctly. I had Apt uninstall and reinstall Tailscale and everything worked correctly and I was finally back to normal.
1 note
·
View note
Text
https://www.threads.net/t/Cuo6YgbvUbU/?igshid=NTc4MTIwNjQ2YQ==
0 notes
Text
How do I update my servers using Gitlab, Ansible and Tailscale
It’s been a while since I’ve written one of these posts, this is a Zero to working type overview of how I got a specific thing done. The idea with the post is not to just be a journey from nothing to something, it’s the journey itself, the problems which were encountered and how they were solved which to me is often more fascinating than the problem itself.
Are there better ways to do what I’ve…

View On WordPress
0 notes
Text
Milestone XProtect and Tailscale VPN using SSL
Milestone XProtect and Tailscale VPN using SSL
This post is an evolution of Milestone XProtect Mobile Server – SSL Certificate configuration as we continue to use SSL certificate with HTTPS.
The advantage is to use Tailscale VPN which is free up to 20 devices for personal use, to avoid open HTTP/HTTPS port to external public domain.
Configure Tailscale
Configuration is super simple:
Download and install Tailscale to all Windows, Linux,…
View On WordPress
0 notes
Text
Tailscale 也推出類似 Cloudflare Tunnel 的產品,Tailscale Funnel
Tailscale 也推出類似 Cloudflare Tunnel 的產品,Tailscale Funnel
Tailscale 也推出了類似 Cloudflare Tunnel 的產品,叫做 Tailscale Funnel:「Introducing Tailscale Funnel」。
都是透過 server 本身主動連到 Cloudflare 或是 Tailscale 的伺服器上,接著外部的 request 就可以繞進來了。
不過 Tailscale Funnel 的定位跟 Cloudflare Tunnel 有些差異,看起來 Tailscale Funnel 比較偏向給 dev/stage 環境的用法,Cloudflare Tunnel 像是要跑在 production 的設計?
目前是 alpha 階段,有些限制,像是目前能開的 port:
The ports you can specify to expose your servers on are currently to 443,…
View On WordPress
0 notes
Text
the scp command is my favorite magic spell
#oh shit i need to send a file/folder to my mc server better just send that thang over like a paper airplane#it works over tailscale too which is nice. a pigeon holding a datapack .json and flying straight to my machine :3
0 notes
Text
Tailscale
As promised, I will talk about the software Tailscale this week. This do-it-yourself VPN allows you to create a mesh network of all your devices in a simple accessible and user-friendly manner. It’s a modern VPN solution focuses on making secure and private networking as easy as possible. It uses peer to peer, or decentralization, model meaning devices are connected without passing through a central VPN network. It’s like a co-op grocery store but for devices. This means that each device that has Tailscale and is on your tailnet can talk to each other directly no matter where they are in the world. This allows for a wide plethora of different applications.
One common application and one that I use as well is establishing a Network Attached Storage (NAS) on your tailnet. A NAS is a device or system that stores data and allows people to access this data over the network. It’s much like the cloud in a sense, but I have the physical server with me, and in my case, have control over how it works, can upgrade it, and change its configuration. With a NAS onboard the tailnet and the ability to talk between devices on the tailnet, I have just established my cloud. Wherever I am, as long as I’m on my tailnet with the device I’m using and my NAS is up, I can access it.
In addition to its other many customizable features, it also can use devices as exit nodes. In my case this allows me to have my Raspberry Pi on my tailnet use it as an exit node and reap the benefits of the Pi-hole application that’s established on it. If you don’t know what Pi-hole is, I made a post about it previously. So not only can I now access my storage system anywhere, but I can also have DNS blocking anywhere.
There are so many more applications I’m yet to discover with Tailscale and it’s a very much growing software. They are constantly updating it, adding new features, and combining it with different hardware and software. I encourage you to check it and establish it on a few of your devices.
Sources:
0 notes
Text
How to create a Tailscale VPN connection to my Synology NAS
This article discusses how to create a Tailscale VPN connection to my Synology NAS. According to their documentation, Tailscale simplifies secure connections to your Network-Attached Storage (NAS) devices using WireGuard. Please see how to create New Users and Join Synology NAS to Active Directory, DSM Security: How to Protect Synology DS923+ NAS, and how to “Configure VPN on Windows Server: How…
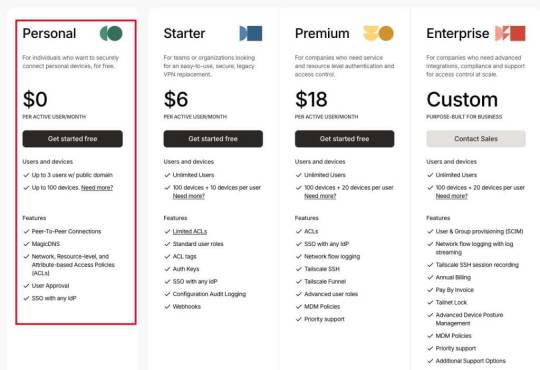
View On WordPress
#Download Tailscale for macOS#Install Tailscale for macOS#MAC#Macbook#MacOS#macOS Big Sur#Mesh Network#NAS#NAS Storage#Secure Remote Access#storage#Synology#Synology Diskstation#Synology DS923+ NAS#Synology DSM 7.2#Synology NAS#Synology Package Center#Tailnet#Tailscale Network#Tailscale VPN Connection#Turn on VPN#VPN#VPN on Synology NAS
0 notes
