Don't wanna be here? Send us removal request.
Text
Top 5 Skills to Promote Your Career in IT
Asquare Technologies is emphasizing some cutting-edge skills for career changers in 2024. Here’s a breakdown of each skill and why it’s important:
1.Analytics: This skill involves gathering, interpreting, and presenting data to make informed business decisions. In today’s data-driven world, companies rely heavily on analytics to understand customer behavior, optimize operations, and drive growth.

Top Job Roles
Data Analyst
Business Analyst
Tableau Developer
PowerBI Developer
Business Intelligence Developer
2. Data Science: Data science goes beyond basic analytics, utilizing advanced algorithms and machine learning techniques to extract insights and predictions from large datasets. With the exponential growth of data, data scientists are in high demand across industries.

Top Job Roles
Machine Learning Engineer
Data Engineer
Database Administrator
Data Analyst
Data Scientist
3. Cloud Computing: Cloud computing has revolutionized the way businesses operate by providing scalable and flexible infrastructure and services. Proficiency in cloud computing platforms like AWS, Azure, or Google Cloud is essential for modern IT professionals.

Top Job Roles
Cloud Engineer
Cloud Administrator
Cloud Developer
DevOps Engineer
Cloud Support Engineer
4. Blockchain: Blockchain technology, known for its security and transparency, is disrupting various sectors, including finance, supply chain, and healthcare. Understanding blockchain principles and their applications can open up new career opportunities in emerging industries.

Top Job Roles
Blockchain Developer
Blockchain Engineer
Blockchain Analyst
Blockchain Project Manager
Law
5. UX Design: User Experience (UX) design focuses on creating intuitive and engaging digital experiences for users. As more businesses shift online and prioritize customer satisfaction, UX designers play a crucial role in product development and innovation.

Top Job Roles
UX Designer
UX Engineer
Software Testing
UX Writer
Interaction design
Information Architecture
By mastering these skills, you’ll be well-equipped to navigate the rapidly evolving job market and pursue exciting career opportunities in technology and beyond.
#business analytics#cybersecurity#business analytics course in kochi#data analytics#data science#data analytics training#data science course#data analytics course#data analytics course in kochi#business analytics course#ethical hacking training
0 notes
Text
Navigating the Digital World: A Guide to Ethical Hacking Careers
In the rapidly growing field of cybersecurity, ethical hacking has emerged as an important role in digital assets and privacy. Ethical hackers, also known as white-hat hackers, are cybersecurity experts who use their skills to identify vulnerabilities in systems, networks, and applications to help organizations strengthen their cyber defences against malicious attacks. If you’re looking for how to become a cybercrime warrior and want to explore a career in ethical hacking, this guide is for you.
Understanding Ethical Hacking:
First things first, what exactly is ethical hacking? Ethical hacking involves legally breaking into systems and networks to discover vulnerabilities before malicious hackers can exploit them. Ethical hackers use the same techniques and tools as their malicious counterparts but with permission from the system owners. Their primary goal is to discover weaknesses in security measures and provide recommendations for enhancing protection.
Skills Required for an Ethical Hacker
Here are some key skills required for a career in ethical hacking
Proficiency in programming languages such as Python, Java, C/C++, or Ruby.
In-depth knowledge of networking protocols and technologies.
Familiarity with operating systems like Linux, Windows, and macOS.
Understanding of cybersecurity concepts such as encryption, firewalls, and intrusion detection systems.
Strong analytical and critical thinking skills to identify and exploit vulnerabilities effectively.
Education and Training:
While there’s no strict educational path to becoming an ethical hacker, a background in computer science, information technology, or cybersecurity can provide a solid foundation. Many professionals in this field pursue certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or CompTIA Security+ to validate their skills and enhance their credentials.
Hands-on experience is crucial for aspiring ethical hackers. Consider participating in capture-the-flag (CTF) competitions, bug bounty programs, or building your own lab environment to practice various hacking techniques in a controlled setting. Here at Asquare Technologies, we are providing these kinds of training which include hands-on labs.
Career Opportunities:
Ethical hackers are in high demand across various industries, including finance, healthcare, government, and technology. As cyber threats continue to escalate, organizations are willing to invest in cybersecurity professionals who can proactively defend their assets against attacks.
Potential career paths for ethical hackers include:
Penetration Tester: Conduct security assessments and penetration tests to identify vulnerabilities in systems and networks.
Security Consultant: Advise organizations on security best practices, risk mitigation strategies, and compliance requirements.
Incident Responder: Investigate security incidents, contain breaches, and implement remediation measures to restore systems.
Security Analyst: Monitor network traffic, analyze security logs, and respond to security incidents in real time.
Security Researcher: Explore new attack vectors, develop proof-of-concept exploits, and contribute to the cybersecurity community through vulnerability disclosures.
Asquare Technologies Ethical Hacking Course : Duration 5 months(4 months classes and 1 month internship)
Covering Topics
Networking (Basics to Advanced)
Linux
Ethical Hacking (wifi hacking, mobile hacking, Malware Analysis, web application hacking,)
0 notes
Text
Beginner’s Guide: Data Analysis with Pandas
Data analysis is the process of sorting through all the data, looking for patterns, connections, and interesting things. It helps us make sense of information and use it to make decisions or find solutions to problems. When it comes to data analysis and manipulation in Python, the Pandas library reigns supreme. Pandas provide powerful tools for working with structured data, making it an indispensable asset for both beginners and experienced data scientists.
What is Pandas?
Pandas is an open-source Python library for data manipulation and analysis. It is built on top of NumPy, another popular numerical computing library, and offers additional features specifically tailored for data manipulation and analysis. There are two primary data structures in Pandas:
• Series: A one-dimensional array capable of holding any type of data.
• DataFrame: A two-dimensional labeled data structure similar to a table in relational databases.
It allows us to efficiently process and analyze data, whether it comes from any file types like CSV files, Excel spreadsheets, SQL databases, etc.
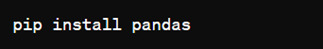
How to install Pandas?
We can install Pandas using the pip command. We can run the following codes in the terminal.
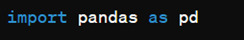
After installing, we can import it using:
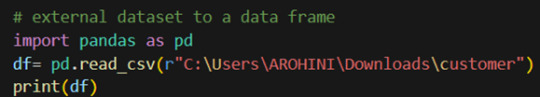
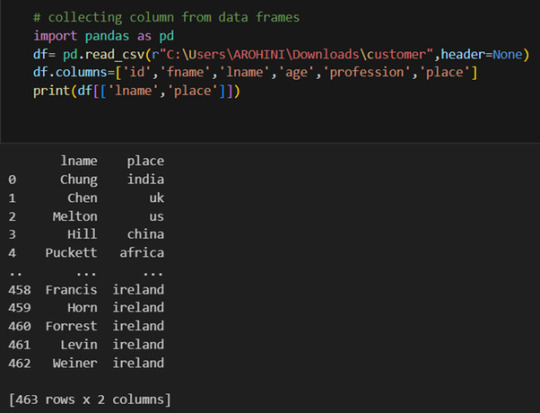
How to load an external dataset using Pandas?
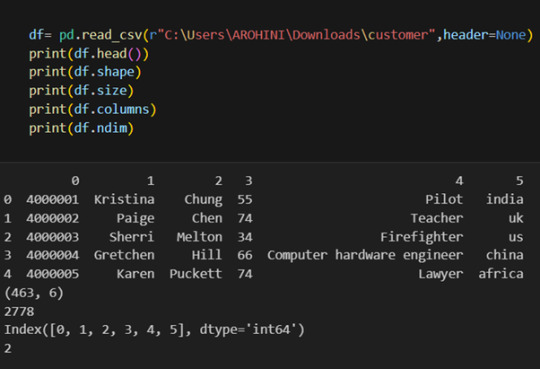
Pandas provide various functions for loading data into a data frame. One of the most commonly used functions is pd.read_csv() for reading CSV files. For example:
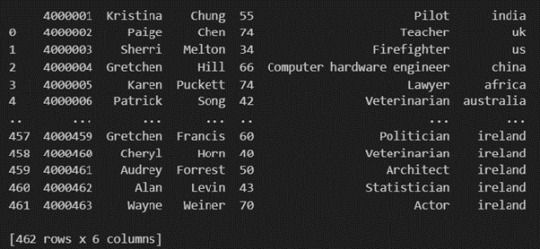
The output of the above code is:
Once your data is loaded into a data frame, you can start exploring it. Pandas offers numerous methods and attributes for getting insights into your data. Here are a few examples:
df.head(): View the first few rows of the DataFrame.
df.tail(): View the last few rows of the DataFrame.
http://df.info(): Get a concise summary of the DataFrame, including data types and missing values.
df.describe(): Generate descriptive statistics for numerical columns.
df.shape: Get the dimensions of the DataFrame (rows, columns).
df.columns: Access the column labels of the DataFrame.
df.dtypes: Get the data types of each column.
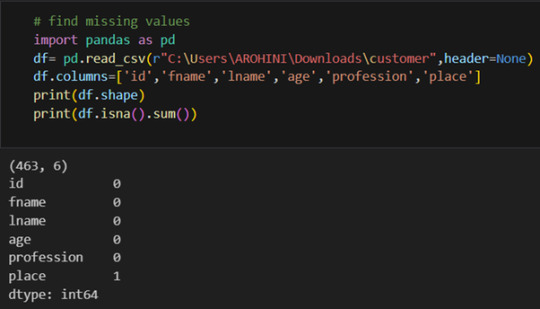
In data analysis, it is essential to do data cleaning. Pandas provide powerful tools for handling missing data, removing duplicates, and transforming data. Some common data-cleaning tasks include:
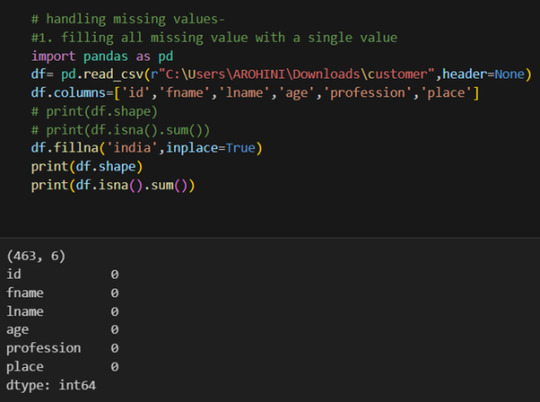
Handling missing values using methods like df.dropna() or df.fillna().
Removing duplicate rows with df.drop_duplicates().
Data type conversion using df.astype().
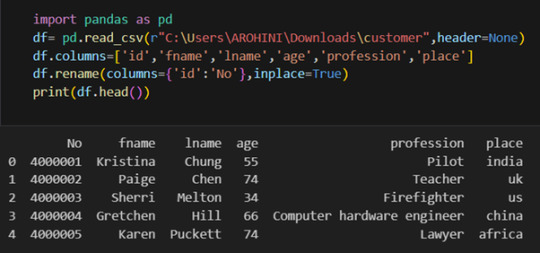
Renaming columns with df.rename().
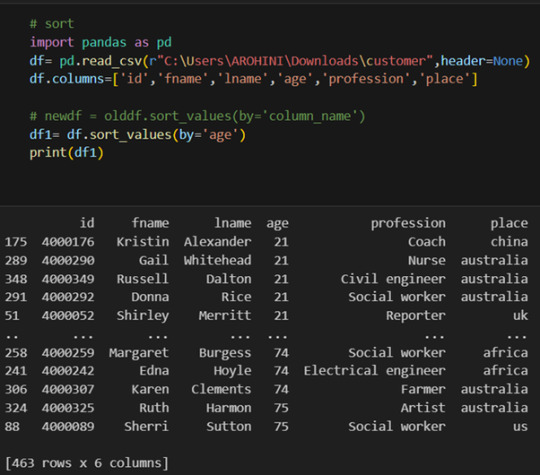
Pandas excels in data manipulation tasks such as selecting subsets of data, filtering rows, and creating new columns. Here are a few examples:
Selecting columns: df[‘column_name’] or df[[‘column1’, ‘column2’]].
Filtering rows based on conditions: df[df[‘column’] > value].
Sorting data: df.sort_values(by=’column’).
Grouping data: df.groupby(‘column’).mean().
With data cleaned and prepared, you can use Pandas to perform various analyses. Whether you’re computing statistics, performing exploratory data analysis, or building predictive models, Pandas provides the tools you need. Additionally, Pandas integrates seamlessly with other libraries such as Matplotlib and Seaborn for data visualization
#data analytics#panda#business analytics course in kochi#cybersecurity#data analytics training#data analytics course in kochi#data analytics course
0 notes
Text

How can I get Microsoft Power BI Certification cleared?
You can go through this guide to get an idea about the steps you should follow to get the certification completed after completing the Microsoft Power BI Course from Asquare Technologies. Many students from Asquare Technologies were able to clear this exam with good scores.
What are Certifications
Certificates are awarded on completion of academic courses by Education Boards & Universities, in a similar way certifications are awarded by certain professional organizations on completion of certain courses & assessments designed specifically according to job roles. The certificates which you earn through educational boards are for your lifetime whereas the certifications will have an expiry date as the technology keeps changing rapidly. You have to keep earning them according to your job requirements helping you to keep growing professionally.
Why Certifications
The market is tough & is getting tougher with time. And the chance of getting a high-paying job at a good companies is at stake. You have to stand out of the pack to get picked. Certifications tell that you have acquired the skill set required for a particular job role, giving you a high chance of placements as the certifications are designed according to industry standards.
PL300 Exam
PL300 exam is designed by Microsoft to earn a certification as a Data Analyst Associate. PL300 exam measures your ability to perform the roles of a Data Analyst. It examines your various skills like Preparing the data, Importing the data from different sources, cleaning and Transforming the imported data, Modeling the data, Visualizing & Analyzing the data, preparing the dashboard presenting the insights of the data, deploying & maintaining its integrity.
How can I get the certification?
To earn this certification, you should have enough knowledge & have hands-on experience in preparing reports & dashboards. A bit of experience will make it easier to crack the PL300 exam. You can schedule the PL300 exam at https://learn.microsoft.com/en-us/credentials/certifications/exams/pl-300/
All the information on the PL300 exam is provided in the above link. It’s a paid exam by Microsoft. It will provide you with all the study modules required for the exam. You can study on your own or you can choose an instructor-based study which again costs a certain amount. Based on your knowledge & capability you can choose either way. Read & complete all the modules by taking a small knowledge designed in the module. It will help you a lot to crack the exam.
Even you will take a mock test before you take an actual one just to make you aware of the exam pattern. Otherwise, a real exam will be a bit tougher compared to a mock test. So, better prepare well & sit for the exam. You can choose a center-based exam or online. Online exams will require certain requirements which you need to pass while you register for the exam just like the system on which you are taking the PL300, your internet connection will be checked, you need to mention from where you are taking the exam – home/Office, provide valid ID proof, etc.
They will connect you through mail-id provided by you. A proctor will be assigned to monitor your exam, read the instructions carefully & follow them without fail, or else your exam may be ruled out. On completion, on the spot, the result will be announced on the screen. Later you can download the certificate through the link they send you in your mail. Please read the steps given there properly and download your certification which will boost the confidence in you to apply for the designated job roles. I have tried to provide the information to the best of my knowledge. Hope it helps you to achieve more. All the best.
#power bi#business analytics#data analytics training#data analytics course#business analytics course#data analytics
0 notes
Text

Overview: A career transformation can be a confusing but rewarding journey, especially if you are transitioning from a non-IT background to the field of analytics. In this blog, we will explore the steps, skills, and insights needed to become a successful person in the world of analytics, irrespective of any background.
Understanding the Analytics Landscape: Start by gaining a solid understanding of what analytics entails. Explore the different branches such as data analytics, business analytics, and data science. Identify the key roles and responsibilities within these domains and the industries that are actively seeking analytics professionals.
Identifying Transferable Skills: Assess your current skill set and identify transferable skills that can be leveraged in the analytics field. Skills such as problem-solving, critical thinking, attention to detail, and communication are valuable across various domains, including analytics.
Building a Strong Educational Foundation: While a formal education in analytics can be beneficial, it’s not always a prerequisite. There are numerous online / Offline courses, certifications, and workshops that cater to individuals with diverse backgrounds. Asquare Technologies offer comprehensive courses in analytics from Industry Experts.
Mastering Essential Tools and Technologies: Familiarize yourself with key tools and technologies used in the analytics field. Learn to work with analytics tools such as Python, R, SQL, and popular data visualization tools like Microsoft Power BI and Tableau. Asquare’s Online and Offline Programs and hands-on projects can help you build practical skills.
Networking and Industry Exposure: Networking is crucial for any career transition. Attend industry conferences, webinars, and local meetups to connect with professionals in the analytics field. Join online forums and communities like LinkedIn groups to stay updated on industry trends and connect with like-minded individuals.
Showcasing Your Skills Through Projects: Build a portfolio showcasing analytics projects you’ve worked on. This could include personal projects, case studies, or contributions to open-source initiatives. A strong portfolio is a tangible way to demonstrate your skills to potential employers. Asquare Technologies makes you to show case your skills with our Project Demonstration by each students after training completion.
Seeking Mentorship and Guidance: Reach out to professionals who have successfully transitioned from a non-IT background to analytics. Seeking mentorship can provide valuable insights, guidance, and a roadmap for your career transition.
Tailoring Your Resume and Cover Letter: Craft a compelling resume that highlights your transferable skills and showcases your commitment to transitioning into analytics. Tailor your cover letter to emphasize your motivation, skills, and any relevant experiences that align with the analytics field.
Preparing for Interviews: Asquare’s Mock Interview session makes you to be prepared for analytics-related interview questions. Practice answering questions that assess your problem-solving abilities, technical skills, and understanding of analytics concepts. Showcase your enthusiasm for learning and adapting to new challenges.
Continuous Learning and Adaptation: The field of analytics is ever-evolving. Commit to continuous learning and staying updated on the latest tools, techniques, and industry trends. This mindset will not only help you secure a role but also thrive in the dynamic analytics landscape.
Conclusion: Transitioning from a non-IT background to a thriving career in analytics is an achievable goal with the right mindset, skills, and strategic planning. Embrace the learning journey, stay persistent, and leverage your unique background as a strength in the analytics world. Your future in analytics awaits – Create the gateway to a rewarding and fulfilling career!
#careerguidance#career#business analytics course in kochi#data analytics course#data analytics course in kochi
0 notes
Text
Kick Start a Data Science Career with Python
Kick Start a Data Science Career with Python

Data science is one of the hottest and most exciting fields of the modern world. Data science is a way of understanding patterns and trends by analyzing data to find problems and provide solutions or make decisions. Data science can be applied in several domains, such as business, health, education, sports, etc.
Python, thanks to its versatility and its comprehensive ecosystem of libraries, has become the de facto standard for data scientists around the world. But, How to become a data scientist? What should one learn to become a data scientist? In this blog post, you will learn how to start with data science and Python, one of the most loved programming languages for data analysis, but also for generative and interactive art, among the plethora of creative uses.
Understanding Data Science
At its broadest, data science is concerned with the combination of domain knowledge, statistical and machine-learning techniques, programming thought, and practice to do things such as establish hypotheses, gather data, clean data, build models, analyze data, interpret outcomes, visualize results, and Disseminate insights.
Key Concepts in Data Science
Data Collection: Data can come from a multitude of sources, including databases, APIs, web scraping, sensors, etc. Python comes with a handful of libraries that can help with web scraping such as requests and BeautifulSoup, with frameworks such as Scrapy that were developed specifically for web scraping and with structured packages such as pandas.
Data cleaning and preprocessing: Data is typically messy and often contains misclassifications, errors, or missing values. It must be standardized, duplicate entries removed and missing data handled before it can be analyzed.
Exploratory Data Analysis: This closely related field usually has a specific purpose – answering a specific question about the data, based on certain assumptions about the data. Many EDA methods involve looking at the data visually within spreadsheets – using plots, histograms, heatmaps, charts, and more.
Statistical Inference: Statistical methods help data scientists understand the deep fundamentals of the data to make inferences.
Machine learning: These are algorithms that allow computers to learn from data and make predictions or decisions without being explicitly programmed. Python comes with a sci-kit-learn library, which has a large variety of machine-learning models, including several models for classification and regression, as well as clustering and dimensionality reduction
Why use Python for Data Science?
Python is a general-purpose, high-level language that supports multiple paradigms such as object-oriented, functional, and procedural. Python is intuitive, which makes it very readable and expressive. Python possesses a collection of libraries and frameworks that allow for data science tasks such as data wrangling, exploring, visualizing, machine learning, natural language processing, web scraping, and other tasks. Some of the advantages of using Python for data science are:
It is easy to learn and use, especially for beginners and non-programmers.
It works with all kinds of data and problems, but you can tailor it to your specific needs – that is, it is flexible.
It’s open source and community-supported, so there’s access to and contribution from an enormous and diverse community of resources and plugins.
It’s popular and widely accepted, meaning that there are tons of tutorials, courses, books, and blogs that teach you Python for data science and there are numerous platforms where you can find help and post queries, all free of cost. What are the essential Python libraries for data science? Python libraries: Python libraries are packages of modules that offer particular functionalities and features. There are hundreds of Python libraries for data science. Examples of essential libraries (that are used in almost every data science project) are:
NumPy: It’s Numerical Python, the foundation of scientific computing in the Python language, and provides a fast multidimensional array object as well as a host of tools for manipulating numerical data: linear algebra, random number generation, and Fourier transform.
Pandas: Pandas is indeed a library for data manipulation and analysis in Python – specifically Python Data Analysis Library. Pandas is the missing tool for anyone new to working with data and is by far the most popular library for working with data frames in Python. It provides a powerful, elegant, and intuitive data structure referred to as a data frame (which can be thought of as a fancy spreadsheet or a table, or a two-dimensional data structure with rows and columns). Pandas also offers multiple features for querying, exploring, and analyzing data, such as indexing, slicing, filtering, grouping, merging, pivoting, reshaping, aggregation, cleansing, and abstraction of underlying memory management.
Matplotlib: It is used for creating data visualization in Python. It provides a low-level and flexible interface for creating and customizing various types of plots and charts, such as line, bar, pie, scatter, histogram, and more. Matplotlib also supports interactive and animated graphics, as well as integration with other libraries and frameworks, such as Pandas, Seaborn, and Plotly.
Scikit-learn: Scikit-learn is the most popular library for machine learning in Python. It provides a comprehensive and consistent set of algorithms and tools for supervised and unsupervised learning, such as classification, regression, clustering, dimensionality reduction, feature extraction, and model selection. Scikit-learn also integrates well with other libraries, such as NumPy, Pandas, and Matplotlib, and follows a simple and uniform API for building and evaluating machine learning models.
NLTK: NLTK stands for Natural Language Toolkit and is the most widely used library for natural language processing (NLP) in Python. NLP is the field of data science that deals with analyzing and generating text and speech data, such as sentiment analysis, text summarization, machine translation, and speech recognition. NLTK provides a rich and diverse set of resources and tools for NLP, such as corpora, tokenizers, stemmers, lemmatizers, parsers, taggers, and classifiers.
Conclusion
In this introductory guide, we’ve explored the key concepts and tools essential for starting your journey into data science with Python. By mastering these fundamentals and leveraging the rich ecosystem of Python libraries, you’ll be well-equipped to tackle real-world data challenges and uncover valuable insights from data. Irrespective of your experience, Python’s versatility and ease of use make it an ideal choice for data science projects of all sizes. So, dive into Python, and embark on your exciting data science adventure!
Why Asquare Technologies? ✅ISO 9001:2015 Certified ✅Affiliated To SKILL INDIA (NSDC) ✅Training By Experienced Professionals ✅Live Interactive Sessions ✅Mentorship for soft skills improvement ✅100% Placement Assistance ✅Project work and Review from Experts ✅Mock Interview program from Industry Experts ✅Internship Program for Live Project Experience
Certifications : 1. NSDC Certificate after Successful completion of Training 2. Completion Certificate from Asquare Technologies. 3. Internship Completion Certificate.

0 notes
Text
Power BI Report on Global Energy Consumption
Document on Global Data on Sustainable Energy:- (2000 to 2020)

Then I saw that in so many columns, data is null. I didn’t want to change the data set as I had already done research & studied about it. Then I started searching for the required data & I entered the values for all the countries (176 countries) & for all the years (20 years).

In the data set there was only mention of ‘Renewable Energy Consumption Share’ but no Primary Energy Consumption. So, I searched for primary energy consumption, so that I have show the share of renewable energy share in final consumption.
Then I created Factless Fact table with country & its code data, & used it as a bridge table between my ‘Energy Data’ table & ‘Primary Energy Consumption’ table. I have used Both in Cross filter direction to get the data, filtered & analyzed properly.
I have even deleted a column called Renewable (% Equivalent primary Energy) as there was no(zero) data in that column.
Still there are many empty data in the dataset like as not all countries get financial flows as an aid. Only developing countries receive. And some others too. I tried my best to fill the blanks but still some values are not available.

Finally, The data was ready to get analysed. I had created many measures like
B_Density – To display total population density per Km2 and to add units to it.
B_LandArea – To display Total Land area per Km2 & to add units to it.
N o of Countries :- To find out the no of Countries.
Co2 Emission :- To sum up Co2 Values & to apply unit to it.
GDP Values:- To sum up GDP Values
Primy_Energy Consumption :- To sum up the values along with applying Units to it.
Ranking on Co2 = To rank the countries according to the emission of Co2.
Ranking on GDP :- to Rank the countries according to their GDP Values.
Even I have Created hierarchy between regional Values. And also, I have created different bookmarks showcasing the GDP values in different perspective. I have used Selection to select Visuals to display during bookmarks.
I have tried to add few information in the different pages of the report & had linked it on to required visuals through info button. I have given even certain links for further studies at the end of report. I have attached the description of all the attributes in the report.
I have tried to the best of my knowledge to analyse the Global Data on Sustainable Energy. Still Suggestions are always welcomed as I am keen learner.
For more details of the project watch video
For More:
Power BI Projects: Click Here
Tableau Projects : Click Here
0 notes
Text
Guide to a Successful Career Path in Cyber Security
In our hyper-connected digital world, the demand for skilled cyber security professionals is higher than ever. As technology continues to advance, so do the threats to our digital infrastructure. If you’re considering a career in cyber security or are already on this exciting journey, this guide will help you navigate the complex landscape and carve out a successful career path in Cybersecurity and Ethical Hacking.
Your journey into the world of ethical hacking starts with a blend of education, skills, and a passion for ethical cybersecurity. This guide, tailored for admission into ethical hacking, will help you unlock the potential for an exciting and impactful career. Embrace curiosity, stay committed to learning, and embark on a journey to secure the digital world ethically.
India faces a growing threat from cyber attacks, with a rise in incidents targeting key sectors like finance, healthcare, and government institutions. The nation’s increasing digital reliance and a surge in internet users make it an attractive target for various cyber threats, including ransomware and phishing scams. To counter these challenges, the Indian government is working on enhancing its cybersecurity measures through initiatives such as the National Cyber Security Policy, emphasizing the need for awareness, collaboration, and technological investments.
Recent Cyber-attack in India
BSNL DATA BREACH:
State-owned telecom operator Bharat Sanchar Nigam Ltd (BSNL) has allegedly suffered a data breach including sensitive details of fiber and landline users of BSNL. The compromised data include email addresses, billing details, contact numbers. The breach, involving sensitive information not only compromises the privacy of the users but also places them at risk of identity theft, financial fraud, and targeted phishing attacks.
The hacker claims that the number of rows of data to be around 2.9 million, which indicates a high probability that it is a single website that may have been breached. The sample data structure available on the dark web points to possible exploitation of a SQL (Structured Query Language) Injection vulnerability.
SQL injection, also known as SQLI, is a common attack vector that uses malicious SQL code for backend database manipulation to access information that was not intended to be displayed. This information may include any number of items, including sensitive company data, user lists, and private customer details.
To secure ourselves and our nation from these kinds of cyber attacks, learn cybersecurity and become a hero.
What is Cyber security and Ethical Hacking?
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users via ransomware; or interrupting normal business processes.
Key components of cybersecurity include:
Network Security: Protecting computer networks from unauthorized access and cyber-attacks through the implementation of firewalls, intrusion detection systems, and other security measures.
Information Security: Safeguarding sensitive information and data to prevent unauthorized access, disclosure, alteration, or destruction.
Endpoint Security: Securing individual devices such as computers, laptops, and mobile devices from malware, ransomware, and other threats.
Cloud Security: Ensuring the security of data and applications stored in cloud environments, including data encryption, access controls, and secure configurations.
Incident Response: Developing and implementing plans to respond effectively to cybersecurity incidents, minimizing the impact and facilitating recovery.
Security Awareness Training: Educating users and employees about cybersecurity best practices to reduce the risk of human-related vulnerabilities, such as social engineering attacks.
Ethical hacking involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers.
Key aspects of ethical hacking include:
Penetration Testing: Conducting controlled simulated cyber attacks to assess the security of systems, identify vulnerabilities, and provide recommendations for improvement.
Vulnerability Assessment: Evaluating systems for weaknesses, misconfigurations, or other security issues that could be exploited by malicious actors.
Security Auditing: Examining the security controls, policies, and procedures of an organization to ensure they align with best practices and compliance standards.
Red Team vs. Blue Team Exercises: Red teaming involves simulating a real-world attack to test the organization’s defenses, while blue teaming involves defending against simulated attacks and improving security measures.
Reporting and Recommendations: Ethical hackers provide detailed reports of vulnerabilities and weaknesses, along with recommendations for mitigating risks and enhancing overall cybersecurity posture.
Different Types of Cyber Attacks
Malware:
Description: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Examples: Viruses, worms, trojans, ransomware, spyware.
Phishing:
Description: Deceptive attempts to trick individuals into revealing sensitive information, often through fake emails or websites. Examples: Email phishing, spear phishing, vishing (voice phishing), smishing (SMS phishing).
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS):
Description: Overloading a system, network, or service to make it unavailable to users. Examples: Flooding a website with traffic, using botnets to amplify the attack.
Man-in-the-Middle (MitM):
Description: Intercepting and potentially altering communication between two parties without their knowledge. Examples: Eavesdropping on Wi-Fi communications, session hijacking, DNS spoofing.
SQL Injection:
Description: Exploiting vulnerabilities in web applications by injecting malicious SQL code, often to gain unauthorized access to a database. Example: Modifying SQL queries in input fields to manipulate database responses.
Cross-Site Scripting (XSS):
Description: Injecting malicious scripts into websites, which are then executed by users’ browsers. Example: Embedding scripts in input fields that are executed when other users view the affected web page.
Cross-Site Request Forgery (CSRF):
Description: Forcing users to perform unintended actions on a web application in which they are authenticated. Example: Tricking a user into clicking a link that performs an action (e.g., changing their password) without their consent.
Zero-Day Exploits:
Description: Targeting vulnerabilities in software or hardware that are not yet known to the vendor or have no available patches. Example: Exploiting a recently discovered flaw before a fix is developed.
Ransomware:
Description: Encrypting files or systems and demanding payment (usually in cryptocurrency) for their release. Example: WannaCry, NotPetya, CryptoLocker.
Social Engineering:
Description: Manipulating individuals into divulging confidential information or performing actions that may compromise security. Examples: Impersonation, pretexting, baiting, quid pro quo.
IoT-Based Attacks:
Description: Exploiting vulnerabilities in Internet of Things (IoT) devices to gain unauthorized access or launch attacks. Example: Taking control of smart home devices, using IoT devices for DDoS attacks.
Password Attacks:
Description: Attempts to obtain passwords through various methods, such as brute force attacks, credential stuffing, or password spraying. Examples: Dictionary attacks, rainbow table attacks, credential stuffing.
These are just a few examples of the many cyber threats and attack vectors that individuals and organizations face.
Importance of Cyber Security
Cybersecurity is crucial in safeguarding individuals, organizations, and nations against a myriad of digital threats. It plays a pivotal role in protecting sensitive data, financial assets, and critical infrastructure from unauthorized access, data breaches, and cyber attacks. As our dependence on digital technologies continues to grow, the importance of cybersecurity becomes paramount in ensuring the integrity, confidentiality, and availability of information, ultimately preserving trust in online systems and fostering a secure digital environment.
Why Choose Cybersecurity as a Career?
High Demand for Experts: The demand for cybersecurity professionals is soaring globally. Organizations across industries are actively seeking individuals with the skills to safeguard their digital assets from cyber threats.
Diverse Career Opportunities: Cybersecurity is not a one-size-fits-all field. With specializations ranging from ethical hacking and penetration testing to incident response and security analysis, there’s a niche for every interest.
Impactful Work: As a cybersecurity professional, you play a crucial role in securing sensitive information, ensuring data integrity, and safeguarding individuals and organizations from the devastating consequences of cyber attacks.
Jobs for Ethical hacker and Cyber Security Professionals
Information Security Analyst:
Responsibilities: Monitor an organization’s networks for security breaches, analyze security measures, and implement solutions to protect sensitive information.
Skills: Network security, vulnerability assessment, incident response.
Penetration Tester (Ethical Hacker):
Responsibilities: Conduct controlled cyber attacks to identify vulnerabilities in systems, networks, or applications, and provide recommendations to strengthen security.
Skills: Penetration testing, vulnerability assessment, ethical hacking.
Security Consultant:
Responsibilities: Advise organizations on their overall security posture, conduct risk assessments, and recommend strategies to improve security.
Skills: Security consulting, risk management, policy development.
Security Engineer:
Responsibilities: Design and implement security solutions, configure firewalls, and monitor for security threats.
Skills: Network security, security architecture, firewall management.
Incident Responder:
Responsibilities: Investigate and respond to security incidents, analyze breaches, and implement measures to prevent future incidents.
Skills: Incident response, forensics, threat intelligence.
Security Analyst (SOC Analyst):
Responsibilities: Work in a Security Operations Center (SOC) to monitor security alerts, analyze data, and respond to potential security incidents.
Skills: Security monitoring, log analysis, threat detection.
Security Administrator:
Responsibilities: Manage and configure security tools, enforce security policies, and ensure the integrity of IT systems.
Skills: Security administration, access control, identity management.
Cybersecurity Manager/Director:
Responsibilities: Oversee an organization’s overall cybersecurity strategy, manage security teams, and ensure compliance with industry regulations.
Skills: Leadership, strategic planning, risk management.
Cryptographer:
Responsibilities: Develop and implement cryptographic solutions to secure data and communications.
Skills: Cryptography, encryption algorithms, key management.
Security Software Developer:
Responsibilities: Develop secure software applications, identify and fix vulnerabilities in code, and contribute to the creation of secure software products.
Skills: Secure coding practices, software development, code analysis.
Threat Intelligence Analyst:
Responsibilities: Collect and analyze threat intelligence data to identify potential cyber threats, assess risks, and provide proactive measures.
Skills: Threat intelligence, analysis, risk assessment.
Security Trainer/Educator:
Responsibilities: Educate individuals or organizations on cybersecurity best practices, conduct training sessions, and develop educational materials.
Skills: Training, communication, cybersecurity knowledge.
Why Choose Our Institution?
Cutting-Edge Curriculum: Our cybersecurity program is designed to provide a comprehensive understanding of the latest threats and defenses. The curriculum is regularly updated to align with industry standards.
Hands-On Training: Gain practical experience through hands-on training, simulations, and access to state-of-the-art cybersecurity labs. We believe in equipping our students with the skills needed to tackle real-world scenarios.
Industry Connections: Our institution maintains strong ties with industry leaders, offering students opportunities for internships, networking, and exposure to the latest trends in cybersecurity.
Admissions Open – Secure Your Future !
Now is the time to take a step towards a dynamic and rewarding career in cybersecurity. With the digital landscape constantly evolving, the need for skilled professionals is greater than ever. Don’t miss the chance to join our institution and become a guardian of the digital realm.
OUR COURSE DETAILS
DURATION 5 MONTHS (4 Months Training +1 Month Internship)
Contents:
Introduction to Cyber Security
IT System Infrastructure
Linux
Network Security
Offensive Security
EC-COUNCIL V12 Modules.
Internship in VAPT (Vulnerability assessment and Penetration testing)
0 notes
Text
Data Analytics Project In Tableau For Beginners with Data Set
QS Top 200 University Ranking 2023
This Tableau Report is a comprehensive exploration and visualization of data about the World’s Leading Universities. It serves as a valuable resource for a wide audience, including students seeking information about universities, academics, and researchers analyzing trends in higher education.
It compares the Top 200 universities around the world across 8 different measures which are important indicators in determining the quality of a particular university.

About the Dataset
The dataset involves information about the Top Universities around the world ranked by QS – Quacquarelli Symonds which is a British company specializing in the analysis of higher education institutions around the world.
They also conduct the QS World University Rankings which is regarded as one of the three most influential university rankings in the world, along with Times Higher Education World University Rankings and the Academic Ranking of World Universities.
I have got the dataset from Kaggle, which I have credited to the dashboards as well.
Dataset Link: https://www.kaggle.com/datasets/jkanthony/world-university-rankings-202223
This particular dataset has information about 1500 universities. However, I’ve filtered down the data to be used to the Top 200 to only focus on the Top universities in each country. It compares the university on 8 different measures namely: –
AR (Academic Reputation) Score
ER (Employer Reputation) Score
FSR (Faculty-to-student) Score
CPF (Citations per Faculty) Score
IFR (International Faculty Ratio) SCORE
ISR (International Student Ratio) SCORE
IRN (International Research Network) SCORE
GER (Gross Enrolment Ratio) SCORE
The Country Analysis Dashboard

The first dashboard which is the Country Specific Analysis Dashboard, As the name suggests, it showcases visuals related to the countries in which the universities are present. If the end user is particularly interested in knowing what universities are in a country and making an analysis of what are the top universities in that country, they may use this dashboard.
The first thing you notice is a sort of slicer that tells you to pick a Country. Now you can pick a particular country from that slicer, say Germany. The visuals change accordingly to show details related to only German or German Universities.
Below the slicer there’s a Map visual, right now showing the German country which would change upon the selection of the slicer. There’s not much information to it, However, A text visual lets you know to hover over the particular country to see more information. While doing so, dfdfyou’re able to see the Top Ranked Universities in Germany in the tooltip. This is a neat way to encapsulate data without taking up too much space in the dashboard.

In the Tooltip, the bottom text mentions selecting the Country Map to see how many universities in the country are in the Top 200 universities. Once you select the country on the map visual, the below funnel chart gets filtered down to show which group the universities belong to. I have categorized the Universities into different groups according to their overall rank as Top 50,100,150 & 200 universities via the create group feature after selecting the ranks. This gives an overall idea as to where each of the universities in that particular belongs to. A text also mentions to select any bar to see which university is present in that group. The below screenshot displays a bar in the funnel chart which upon selection would filter other visuals and show you which university belongs in that selected category.

The next visual in the dashboard is a lollypop chart showing a particular score. This was done by putting 2 of the same measures into the visual and then making them a dual axis, then changing one of them to a bar chart and the other’s mark as a circle so as to form sort of a Lollypop chart mentioning each of the mentioned scores in that visual. What you also notice in the visual is that there is a text box mentioning that you can select a score to be displayed. Based on what the end user wants to see they have the option to find the score they want to compare of the universities inside that particular country.

Next is the Page Automation Chart which can be made by placing a dimension/measure into the Pages, in my case I have put the institutions in the Page Pane. This basically sort of animates the line chart present to show the overall scores of each university in a country in a progressive one-by-one manner. So, if I were to select the play button to start the animation, you can see the chart shows each overall score of the universities in the animation and there’s also a reference line in the chart which is the average overall score of all the universities within that country so you can make an analysis that which university’s score is above the average score in a visually appealing manner.
CLICK HERE......
#business analytics#business analytics course in kochi#business analytics course#cybersecurity#data analytics training#data analytics#data analytics course#data analytics course in kochi
0 notes
Text
How To Choose The Right Skill Set After Graduation: A Guide to Success
Congratulations, graduate! As you step into the next chapter of your life, a crucial question looms large: which skill should you focus on to enhance your career prospects? In a rapidly evolving job market, adaptability and a diverse skill set are more important than ever. In this blog post, we’ll explore various skills and guide you through the process of choosing the one that aligns best with your goals and the demands of the professional landscape.

Choosing the Right Skill with some elements
Align with Interests: Choose a skill that aligns with your passions and career goals.
Assess Industry Demand: Investigate the demand for these skills in your chosen industry.
Consider Combinations: Recognize the synergy between these skills and consider combinations for a broader skill set.
In today’s digital age, proficiency in analytics, data science, and cybersecurity has become integral for professionals aiming to make a mark in the business world. This blog post will explore the key skills within these domains and help you navigate the dynamic landscape of business analytics, data analytics, data science, and cybersecurity.
1. Business Analytics: Decoding Organizational Insights
Business analytics is the art of transforming data into actionable insights to drive strategic decision-making. This skill involves:
Data Interpretation: The ability to extract meaningful information from datasets.
Statistical Analysis: Understanding statistical models for informed decision-making.
Tools Proficiency: Mastery of analytics tools such as Excel, Tableau, or Power BI.
Business Acumen: Aligning analytics outcomes with organizational goals.
2. Data Analytics: Unveiling Patterns for Informed Decision-Making
Data analytics involves examining and interpreting complex datasets to uncover meaningful patterns. Key skills include:
Programming: Proficiency in languages like Python or R.
Data Visualization: Ability to present insights through tools like Matplotlib, and Seaborn.
Database Management: Competence in SQL for efficient data handling.
Machine Learning Concepts: Understanding algorithms for predictive analytics.
3. Cybersecurity: Safeguarding Digital Landscapes
In an era of escalating cyber threats, cybersecurity skills are indispensable. Focus on:
Network Security: Ensuring the integrity and security of networks.
Ethical Hacking: Identifying vulnerabilities through controlled testing.
Incident Response: Managing and mitigating cybersecurity incidents.
Certifications: Pursue credentials like CompTIA Security+ or CISSP.
4. Data Science: Bridging the Gap Between Raw Data and Insights
Data science combines statistical analysis, machine learning, and domain expertise. Essential skills include:
Programming Languages: Proficiency in Python, R.
Machine Learning Algorithms: Understanding and implementing models.
Big Data Technologies: Familiarity with tools like Hadoop, and Spark.
Data Preprocessing: Cleaning, transforming, and engineering data.
How can I Improve My Skills?
Improving your skills is a continuous and rewarding journey. Whether you’re looking to enhance your professional abilities, develop new talents, or acquire knowledge in a specific domain, here are some general strategies to help you improve your skills:
Set Clear Goals: Define specific and measurable goals for skill improvement. Whether it’s mastering a programming language, improving your public speaking, or becoming proficient in data analysis, having clear objectives provides direction and motivation.
Identify Your Weaknesses: Conduct a self-assessment to identify areas where you can improve. Recognizing your weaknesses allows you to focus your efforts on the skills that will have the most significant impact on your personal and professional development.
Continuous Learning: Stay curious and commit to lifelong learning. Explore online courses, workshops, webinars, and tutorials relevant to your chosen skill. Platforms like Coursera, edX, Udemy, and Khan Academy offer a wide range of courses across various subjects.
Practice Regularly: Skills are honed through practice. Set aside dedicated time each day or week to practice the skill you’re working on. Whether it’s coding, writing, or playing a musical instrument, consistent practice is key to improvement.
Seek Feedback: Solicit feedback from mentors, peers, or experts in the field. Constructive feedback can provide valuable insights into areas where you can improve and help you refine your approach.
Join Communities: Engage with communities related to your skill. Online forums, social media groups, and local meetups offer opportunities to connect with like-minded individuals, share experiences, and gain insights from others who are on a similar learning journey.
Build a Portfolio: Create a portfolio or a tangible record of your work. Whether it’s a collection of writing samples, coding projects, or presentations, a portfolio showcases your skills to potential employers and collaborators.
Mentorship: Seek out mentors who have expertise in the skill you’re trying to improve. A mentor can provide guidance, share experiences, and offer valuable advice on how to navigate challenges and accelerate your learning.
Stay Updated: Stay informed about the latest trends, tools, and best practices in your field. Subscribe to newsletters, follow industry blogs, and participate in webinars to stay up-to-date with the evolving landscape of your chosen skill.
Networking: Network with professionals in your industry. Attend conferences, workshops, and networking events to connect with individuals who share similar interests. Networking can open doors to new opportunities and provide valuable insights.
Teach Others: Teaching is a powerful way to solidify your understanding of a skill. Consider mentoring or creating content to share your knowledge with others. Explaining concepts to someone else can deepen your understanding and reinforce your skills.
Stay Consistent: Improvement takes time, so be patient and stay consistent in your efforts. Set realistic expectations and celebrate small victories along the way.
Remember, skill improvement is a continuous process, and embracing a growth mindset is essential. Stay motivated, be adaptable, and enjoy the journey of self-improvement.
#business analytics#data analytics training#data analytics#cybersecurity#data science#business analytics course#data science course#business analytics course in kochi#data analytics course#data analytics course in kochi#course after graduation
1 note
·
View note
Text
Cyber Security and Its Career Scope
1
Posted by
u/Wide_Menu_6981
just now
Cyber Security and Its Career Scope

What is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, data, and programs from cyber attacks. These attacks typically target the unauthorized access, modification, or destruction of sensitive information. Attackers may seek monetary gains from users through ransomware, disrupt normal business processes, or attempt to steal data.
What is Ethical Hacking?
Ethical hacking, also known as penetration testing or white-hat hacking, is a legal and authorized practice aimed at ensuring the safety of computer systems, networks, or applications by identifying security vulnerabilities.
Why is Ethical Hacking Important?
The Importance of Ethical Hacking in Cybersecurity: Safeguarding Your Systems and Data against cyber attacks. The increasing prevalence of cybercrime poses significant threats to national security, influential government organizations, and reputable entities, leading them to enlist the services of ethical hackers. Although hacking is commonly associated with illegal activities, ethical hacking serves as a proactive defence measure.

Types of Ethical Hacking
1. Black-box Testing
In black-box testing, the hacker doesn’t have any prior knowledge of the system and is testing the software from outside the system before entering it via a brute-force approach. For example, if you were testing a website, you might not know what kind of server it’s running on or what programming languages were used to create it. For example, black box testing can be used to check a user’s login, view their account information, change their password, and log out. The tester would not need to know how this is achieved within the application’s code to design such a test.
2. White-box Testing
In white box testing, the hacker knows everything about the system, how it works, and its weaknesses before he tries to break into the system. White-box testing is often done by developers who want to see how well their systems hold up under pressure before they release them into production environments where attackers may try to crack them open.
3. Gray-box Testing
This is a mix between white-box and black-box testing; the tester has some knowledge about the system but not all of it, so they need to use deductive reasoning skills and their technical knowledge to find vulnerabilities within the system or network being tested.
The examples of gray-box testing include areas like:
Usability Tests
Performance Tests
Security Tests
This approach helps you understand how well your application will perform in real-world environments, which can be critical for ensuring successful development.
4. Web Application Hacking
Web application hacking type is the process of exploiting security vulnerabilities or weaknesses in web-based applications. Web applications are typically written in languages like HTML, CSS, and JavaScript, but they can also be written in other languages like PHP and Ruby on Rails. Because of the nature of these languages and how web browsers interpret them, it is possible to perform specific actions on a website without actually being authorized. One example of this would be cross-site scripting (XSS), which involves injecting malicious code into a website’s HTML. If you can craft an XSS attack properly, you can hijack the browser’s session with the server without ever having access to their username or password.
5. Hacking Wireless Networks
Hacking wireless networks is a hacking type that involves accessing a computer network without authorization, typically by exploiting weak points in the system’s security. An example of this is the practice of wardriving, where an attacker drives around with a laptop or other device capable of picking up wireless signals, looking for unprotected or poorly protected networks.
6. Social engineering
Social engineering aims to persuade people to reveal their confidential information. The attacker deceives people because they trust them and lack knowledge. There are three types of social engineering: human-based, mobile-based, and computer-based. As security policies loosen and there are no hardware or software tools to prevent social engineering attacks, it is difficult to detect them.
7. System hacking
System hacking is the sacrifice of computer software to access the targeted computer to steal their sensitive data. The hacker takes advantage of the weaknesses in a computer system to get the information and data and takes unfair advantage. System hacking aims to gain access, escalate privileges, and hide files.
8. Web server hacking
Web content is generated as a software application on the server side in real time. This allows the hackers to attack the webserver to steal private information, data, passwords, and business information by using DoS attacks, port scans, SYN floods, and Sniffing. Hackers hack web servers to gain financial gain from theft, sabotage, blackmail, extortion, etc.
Types of hackers
Black Hat
One who hacks for financial gain. They hack into systems, and networks to steal bank records, and sensitive information for their own gain These stolen commodities to sold onto the black market to destroy the target organization.
White Hat
Those who desire to help organizations with their hacking skills are Ethical Hackers, they do hacking in an authorized manner.
Grey Hat
They have the skills of Black and white hat hackers but the difference is they don’t care about stealing from people, nor do they want to support people. They like to experiment with systems instead and love the difficulty Of finding vulnerabilities, breaking security, and finding hacking enjoyable in general.
Blue Hat
Their motive is revenge. This must be a Client, Supplier, or employee – or anyone who is inside that same organization.
Green Hat
They are the baby hackers who taking their first steps in the cyber world. In general, they are new to the world of scripting, coding, and hacking.
State/Nation Sponsored Hackers
They protect the nation/government from individuals, companies, or rival nations.
How to Become an Ethical Hacker
some of the skills needed to become an ethical hacker include:
Knowledge of scripting languages
Proficiency in operating systems
Deep understanding of networking
A solid foundation in the principles of information security
Our CEH Certificate in Cyber Security can help you prepare to pursue a career as a cyber defender, securing sensitive data and protecting organizations against data breaches. The courses will teach you how to design strategies to protect information, infrastructure, and brands against the threat of cyberattacks.
Responsibilities of an Ethical Hacker
Hacking their own Systems: Ethical hackers hack their own systems to find potential threats and vulnerabilities. They are hired to find vulnerabilities in the system before they are discovered by hackers.
Diffuse the intent of Hackers: Ethical hackers are hired as a precautionary step towards Hackers, who aim at breaching the security of computers. Vulnerabilities when detected early can be fixed and save confidential information from being exposed to hackers who have malicious intentions.
Document their Findings: Ethical hackers must properly document all their findings and potential threats. The main part of the work they are hired by the organizations is proper reporting of bugs and vulnerabilities that are a threat to security.
Keeping the Confidential Information Safe: Ethical hackers must be obliged to keep all their findings secure and never share them with others. Under any kind of situation, they should never agree to share their findings and observations.
Sign Non-Disclosure Agreements: They must sign confidential agreements to keep the information they have about the organizations safe with them. This will prevent them from giving -out confidential information and legal action will be taken against them if they indulge in any such acts.
Handle the loopholes in Security: Based on their observations, Ethical hackers should restore/ repair the security loopholes. This will prevent hackers from breaching the security of the organization from attacks.
The Future of Ethical Hacking
The job of an ethical hacker is going to increase by 17.5% across the world by the year 2025 you will always be in demand as an ethical hacker for the foreseeable future.
Earn Your Ethical Hacking Certificate in Cyber Security
As the digital world expands, maintaining cyber security becomes ever more critical to businesses and their customers. At Asquare Technologies our CEH Certificate in Cyber Security program can help prepare you to pursue a career as a cyber defender, learning how to secure sensitive data and protect organizations against data breaches.
The courses in this program will help you develop fundamental cybersecurity skills and teach you how to design strategies to protect information, infrastructure, and brands against the threat of cyberattacks.
Cyber Security course syllabus :
Introduction to Cybersecurity Ethical Hacking
ICT Infrastructure -Networking and Systems
Linux System Administration, Linux tutorial
Ec-council CEH V12 Modules
Bug Bounty Hunting
Cyber Security Course Eligibility :
Students who choose the science stream in the 12th class are the most suitable candidates to pursue the cyber security course. Apart from it, other stream students can also choose the cyber security courses after 12th and Bachelors degree.
Cyber Security Certifications :
After Completing this cyber security course you can attempt the Ec-Council CEH V12 exam. The EC-Council offers the CEH Certified Ethical Hacker certification. Earn it to demonstrate your skills in penetration testing, attack detection, vectors, and prevention.
For More Details About Cybersecurity Course CLICK HERE
0 notes
Text
Business Analytics Course In Kochi
Who is a Business Analyst?
A Business Analyst is responsible for acquiring and documenting business requirements, analyzing data and processes, and enabling communication among stakeholders to ensure that projects and initiatives fulfill business objectives and function successfully.
Opportunity for a business analyst
Business analysts have good job possibilities in a variety of industries, where they may use their abilities to promote data-driven decision-making, process improvement, and organizational strategic success.
Industries looking for business analysts
Finance and Banking
Healthcare
Information Technology
Retail
Manufacturing
Consulting
Telecommunications
Government
Energy and Utilities
Insurance
Transportation and Logistics
E-commerce
Pharmaceuticals
Hospitality
Education
Media and Entertainment
Aerospace and Defense
Automotive
Real Estate
Non-Profit
How to Become a Business Analyst
Educational Background: Bachelor’s Degree
Join a job-oriented Business Analytics Course
Asquare Job-oriented Business Analytics Course
Asquare Technologies course structure helps all the candidates to understand Business Analytics in an easy manner with lots of practical expertise a candidate will gain at the end of our Course.
The course module starts with the below topics,
MICROSOFT EXCEL FUNDAMENTALS
We are starting the course with Fundamental Excel Concepts for a 1-week program to make sure that all the candidates get hands-on Excel basics, to begin with the analytics skills.
Microsoft Excel is a versatile and powerful tool that offers a wide range of benefits for data management, analysis, and decision-making, making it essential software for professionals in various fields.
ORACLE SQL BASICS
Once the candidates are fine with Excel Fundamentals, we will be starting with 2 weeks of Oracle SQL Fundamentals with DBMS (Database Management system) concepts to understand all the DDL, DML, and TCL Commands a developer should know.
This module will give a candidate a basic idea about a database, fundamentals on why SQL Language is important and when it should be used, and so on. If a candidate is really interested in learning more about Oracle SQL, we will be sharing some more references and finally, a small assignment will be completed by each candidate at the end of the SQL Course.
BUSINESS INTELLIGENCE WITH MICROSOFT POWER BI
Now starts the real game of Analytics with good visualization skills each candidate can showcase with a knowledge-sharing session on Business Intelligence Concepts / Data warehouse concepts. Every person willing to switch their career to Analytics should be aware of all the Warehouse concepts before starting with Microsoft Power BI or Tableau Data visualization sessions. Once the DWH Concepts are clear we will start with the basics of Power BI sessions with Excel as the data source and go ahead with more advanced Excel data, Different types of visuals, and covering all the other concepts a Power BI Developer should be clear about. DAX knowledge is important for a developer to create new measures based on the business requirements. Going forward use AI visuals, Bookmarks, slicers, security, Data refresh Dashboard creation, and so on. The Power BI Training will give a candidate a thorough hands-on experience, and interactive sessions from our experts. Once the training is over all the candidates are supposed to submit an individual project presentation on the respective business domain each candidate is interested in.
SALESFORCE TABLEAU
Once the candidate is done with the Power BI Project, we are stepping into another interesting Visualization tool Tableau which has more visualization capabilities and can handle more volume of data compared to Power BI. It is better to have more than one BI Tools knowledge for a job seeker to get a job in a quicker manner either as a Power BI developer or as a Tableau Developer. Once a candidate is good in Power BI can easily adapt to Tableau. The way a candidate completes a Power BI project a similar approach is followed at the end Tableau course to do an individual project in Tableau and a review session is conducted by our experts with a rating to evaluate each candidate.
Why Asquare Technologies?
✅ISO 9001:2015 Certified ✅Affiliated To SKILL INDIA (NSDC) ✅Training By Experienced Professionals ✅Live Interactive Sessions ✅Mentorship for soft skills improvement ✅100% Placement Assistance ✅Project work and Review from Experts ✅Mock Interview program from Industry Experts ✅Internship Program for Live Project Experience
Certifications : 1. NSDC Certificate after Successful completion of Training 2. Completion Certificate from Asquare Technologies. 3. Internship Completion Certificate.
#business analytics course in kochi#business analyst course in kochi#business analytics course#business analytics jobs#business analytics training#business analytics
0 notes
Text
How To Get Jobs With Power Bi

Microsoft Power BI is one of the most popular and important tools in all data-driven industries. Power BI is not only a formidable business intelligence tool, but it also offers a world of job options for individuals who are competent in its use. In this blog post, we’ll look at what Power BI is, its importance in the business sector, and the variety of employment prospects it provides.

Understanding Power Bi
It allows users to connect to a variety of data sources, turn raw data into relevant insights, and visualize information via interactive reports and dashboards. Power BI has been a go-to choice for organizations looking to derive relevant insights from their data due to its user-friendly interface and comprehensive features.
Power BI’s Importance in the Business World
Data-Driven Decision Making: Power BI empowers organizations to make data-driven decisions. Its interactive visuals and real-time data updates enable stakeholders to access critical information quickly, leading to more informed choices.
Time and Cost Efficiency: Power BI streamlines data preparation and reporting processes, saving valuable time and resources. Automation features reduce manual tasks, allowing professionals to focus on analysis and strategy.
Scalability: Power BI can scale with an organization’s growth. Whether you’re a small startup or a large enterprise, Power BI can adapt to your data analytics needs.
Integration with Other Microsoft Tools: Power BI seamlessly integrates with other Microsoft applications such as Excel, Azure, and SharePoint, making it a preferred choice for organizations already invested in the Microsoft ecosystem.
Career Opportunities in Power BI
Power BI Developer: Power BI Developers are responsible for creating and maintaining reports and dashboards. They have expertise in data modeling, DAX (Data Analysis Expressions), and visualization techniques.
Data Analyst: Data Analysts use Power BI to extract insights from data, create visualizations, and communicate findings to non-technical stakeholders. They play a crucial role in helping organizations make data-driven decisions.
Business Intelligence Analyst: Business Intelligence Analysts leverage Power BI to gather, analyze, and interpret data to support business objectives. They collaborate with teams to design and implement data solutions.
Data Scientist: Data Scientists often use Power BI as part of their toolkit to analyze and visualize data. They build predictive models and use advanced analytics to solve complex business problems.
Consultant/Trainer: Experienced Power BI professionals can become consultants or trainers, helping organizations implement Power BI effectively or providing training to individuals looking to enhance their Power BI skills.
BI Manager/Director: In larger organizations, BI Managers or Directors oversee the entire business intelligence function, including Power BI implementation and strategy.
Building a Career in Power BI
To build a successful career in Power BI, consider the following steps:
Learn Power BI: Start by learning the basics of Power BI through online courses, tutorials, and documentation.
Practice: Create your own projects or work on sample datasets to gain hands-on experience.
Certifications: Consider earning Power BI certifications, such as the Microsoft Certified: Data Analyst Associate or Microsoft Certified: Power BI Certification.
Networking: Join Power BI user groups, attend conferences, and connect with professionals in the field.
Stay Updated: Stay informed about the latest Power BI updates and trends in the business intelligence industry.
#jobs#powerbideveloper#business analytics#data analytics#data analytics course#data analytics training#business analytics course in kochi#business analytics jobs in kochi
0 notes
Text
IMPORTANCE OF ETL IN BUSINESS INTELLIGENCE?
ETL (Extract, Transform, Load) is a crucial process in the realm of Business Intelligence (BI) projects. It forms the foundation for collecting, processing, and preparing data from various sources to create a structured and usable dataset for analysis and reporting. Here’s why ETL is of significant importance in BI projects:
Data Integration: Business Intelligence often involves collecting data from a wide range of sources, such as databases, spreadsheets, APIs, and more. ETL processes allow organizations to integrate data from these disparate sources into a unified and consistent format, eliminating data silos.
Data Quality and Cleansing: Raw data can be inconsistent, incomplete, and contain errors. ETL processes include data cleansing and quality checks, ensuring that the data is accurate, reliable, and fit for analysis. Data is transformed and standardized to ensure consistency across the board.
Data Transformation: ETL transforms data into a format that’s suitable for analysis. This might involve converting units, aggregating data, splitting or merging columns, and performing calculations. Data transformation ensures that the data is in a usable format for generating insights.
Performance Optimization: ETL processes can involve optimizing data for query performance. Aggregating and summarizing data during the ETL phase can lead to faster query execution when generating reports and dashboards.
Historical Data: BI projects often require historical data to analyze trends and make informed decisions. ETL processes can manage historical data by capturing and archiving changes over time.
Data Governance and Compliance: This is crucial for maintaining data privacy and security.
Scalability: As organizations grow, the volume of data they deal with also increases. ETL processes can be designed to handle large datasets efficiently, ensuring scalability as data requirements expand.
Automation: ETL processes can be automated to run on a scheduled basis. This reduces manual intervention, ensures data freshness, and allows analysts to focus on analyzing insights rather than manually collecting and cleaning data.
Consistency: ETL processes maintain consistency in data across various reports and dashboards. When different teams or departments use the same data source, ETL ensures that everyone is working with the same, up-to-date information.
Flexibility: ETL processes can adapt to changing business requirements. When new data sources need to be integrated or transformations need to be adjusted, ETL processes can be modified accordingly.
Data Warehousing: ETL processes are often used in conjunction with data warehousing solutions. Data warehouses store transformed and structured data in a way that’s optimized for querying, which is essential for BI projects.
In essence, ETL processes provide the clean, transformed, and integrated data necessary for accurate and actionable business insights. Without ETL, BI projects would struggle with data inconsistencies, poor quality, and inefficiencies in analysis. ETL acts as the backbone that enables BI solutions to deliver accurate, timely, and meaningful insights to stakeholders, facilitating better decision-making and strategic planning.
For More : Visit Asquare Technologies
#business analytics#data analytics training#business analytics course#business analytics course in kochi#cybersecurity#data analytics#data science#data analytics course#data analytics course in kochi#data science course
0 notes
Text

Exploring the World of Cybersecurity
In our modern age, where information flows seamlessly through digital networks and technology empowers every facet of our lives, the importance of cybersecurity cannot be overstated. It’s the digital shield that safeguards our sensitive data, infrastructure, and even the very essence of our privacy. In this comprehensive blog post, we’ll embark on a journey through the captivating realm of cybersecurity, delving into its core concepts, challenges, and the exciting career horizons it offers.
Understanding Cybersecurity:
The practice of protecting digital systems, networks, and data from hostile attacks is at the core of cybersecurity. The constantly changing nature of this dynamic arena, where defenders and opponents engage in an ongoing game of invention and strategy chess, defines it. Our digital world is made up of many different aspects, all of which are crucial to preserving its integrity and security under the umbrella term of “cyber security.”
The Cyber Threat Landscape:
Malware Mayhem: From viruses to ransomware, explore the spectrum of malicious software that infiltrates systems to cause chaos and compromise security.
Social Engineering Exploits: Uncover the art of manipulating human psychology to trick individuals into revealing sensitive information or performing actions that breach security.
Phishing Expeditions: Dive into the deceptive world of phishing attacks, where cybercriminals masquerade as legitimate entities to extract confidential data.
Distributed Denial of Service (DDoS): Understand how cyber attackers can flood networks or websites with overwhelming traffic, rendering them inaccessible and disrupting operations.
Strengthening the Digital Ramparts:
Encryption Enigma: Explore the science of encryption, where data is transformed into indecipherable code to ensure confidentiality and privacy.
Access Control Architecture: Unveil the mechanisms that regulate who can access specific resources, ensuring only authorized personnel can interact with critical systems.
Patch Management Paradox: Delve into the importance of keeping software and systems updated to address vulnerabilities and prevent exploitation.
Career Opportunities in Cybersecurity:
Security Analyst: As a security analyst, you’re the digital detective, investigating and responding to security incidents, analysing threats, and developing strategies to safeguard systems.
Ethical Hacker/Penetration Tester: Step into the shoes of the ethical hacker, probing systems for weaknesses, simulating cyberattacks, and providing organizations with insights to bolster their defences.
Cybersecurity Consultant: Offer expert guidance to organizations, helping them navigate the complex landscape of cybersecurity strategies, risk management, and compliance.
Chief Information Security Officer (CISO): Ascend to the helm of an organization’s cybersecurity ship, where you’ll orchestrate and oversee comprehensive security strategies.
Security Engineer: Craft robust security solutions, from designing and implementing security protocols to fortifying digital infrastructures against emerging threats.
The Path Forward: Cybersecurity becomes increasingly important as technology advances relentlessly. A resilient and adaptive workforce is required due to the emergence of artificial intelligence, the growth of the Internet of Things (IoT), and the ongoing evolution of cyber threats. Cybersecurity experts ensure that our interconnected world is safe, secure, and prepared to confront tomorrow’s problems. They are more than just defenders; they are the builders of digital resilience.
In conclusion, the field of cybersecurity provides a portal to a fulfilling and influential career as well as a beacon of protection in the digital age. It’s a world where every keystroke, every line of code, and every plan of action has the ability to protect the digital frontier for future generations. Therefore, the world of cybersecurity beckons, with its doors wide open for those ready to embrace its challenges and prospects, whether you’re drawn to the excitement of outwitting hackers or motivated by the idea of defending the digital world.
For more courses visit : Asquare Technologies
#cybersecurity #ethicalhacking #datascience #dataanalytics #businessanalytics
#business analytics#cybersecurity#datasecurity#data science course#data analytics training#data analytics course#data science#data analytics
0 notes
Text

Is Data Science a good career?
The Future of Data Science: As technology advances and the volume of data continues to explode, the role of data science becomes even more crucial. Automation, artificial intelligence, and machine learning will further elevate the field, enabling faster and more accurate decision-making. Ethical considerations, privacy concerns, and responsible data usage will also play a pivotal role in shaping the future of data science
Applications of Data Science:
Data science finds its application in a wide array of fields, revolutionizing industries and shaping the way decisions are made. Here are a few notable examples:
Healthcare: Data science enables personalized medicine, disease prediction, and drug discovery through the analysis of patient data and medical records.
Finance: Predictive models analyse market trends, manage risks, and detect fraudulent activities, enhancing investment strategies and customer experiences.
E-Commerce: Recommendation systems use data science to suggest products, improving user engagement and driving sales.
Marketing: Analysing customer behaviour and preferences helps create targeted marketing campaigns, leading to higher conversion rates.
Transportation: Data-driven optimization of routes and schedules enhances efficiency and reduces fuel consumption in logistics.
Environmental Science: Climate modelling and analysis of environmental data aid in understanding and mitigating the impact of climate change.
For more about Data Science : Data Science
For Data Analytics, Business Analytics, Cyber security, Data Science Courses visit : Asquare Technologies
#business analytics#data analytics course in kochi#business analytics course in kochi#business analytics course#data analytics training#cybersecurity#cyber security course#data science#data science course
0 notes
Text
Importance of Business And Data Analytics in 2023
Importance of Business And Data Analytics in 2023
Data is now the key to success in the fast-paced, cutthroat corporate environment of today. Businesses are becoming more and more aware of the enormous importance of business analytics and data analytics for strategic decision-making and competitive advantage. Without sacrificing originality or blatant plagiarising, we will examine the importance of business analytics and data analytics in the present industry landscape.
Visit : Business analytics and Data analytics - Asquare Technologies
Business Analytics and Data analytics Courses
The Benefit for Modern Industries:
1.Across industries, business analytics, and data analytics have indisputable value: Executives and managers can reduce their reliance on intuition by using data-backed insights to make educated decisions.
2. Improved Customer Experience: By using data analytics to better understand customer preferences, organizations may engage with customers in a more personalized and focused way.
3. Effective Operations: Business analytics optimizes supply chains, workflows, and procedures to increase productivity and lower costs.
4. Competitive Advantage: Employing analytics enables businesses to respond swiftly to market changes, foresee trends, and take proactive measures to overcome obstacles.
5. Data-Driven Innovation: Data analytics reveals unmet customer needs and chances for game-changing technological advances, igniting innovation.
6.Retail: Companies use customer data to personalize shopping experiences and enhance inventory management.
7. Healthcare: Predictive analytics are powered by patient data, which enhances healthcare delivery, treatment outcomes, and diagnosis.
8.Finance: Analytics identify fraud, evaluate risk, and enhance investment plans.
9.Ecommerce: Data improves user experience, marketing initiatives, and pricing tactics in e-commerce.
10. Manufacturing: Analytics improves product quality, production efficiency, and downtime.
Businesses Using Analytics
Several businesses are successfully utilizing business analytics and data analytics:
Company analytics and data analytics have become essential elements in today's company landscape for fostering success and long-term growth. Organizations get a competitive edge by utilizing data, allowing them to make data-driven choices, improve consumer experiences, and open doors for innovation. Businesses that embrace business analytics and data analytics as important assets will be better placed to handle the obstacles and grab the possibilities of the future as the volume and complexity of data continue to increase.
#business analytics#data analytics#business analytics course#data analytics course#data analytics training#business analytics course in kochi#data analytics course in kochi
0 notes