Digital data, a symphony of information where each bit plays its part in creating a harmonious whole.
Don't wanna be here? Send us removal request.
Text
Entry 9:
Unraveling the Web: How Facebook Collects Your Data
In the interconnected world of social media, Facebook stands as a giant. With over 2.8 billion monthly active users, it’s a treasure trove of data. But have you ever wondered how Facebook collects your data? Let’s delve into it.
What Data Does Facebook Collect?
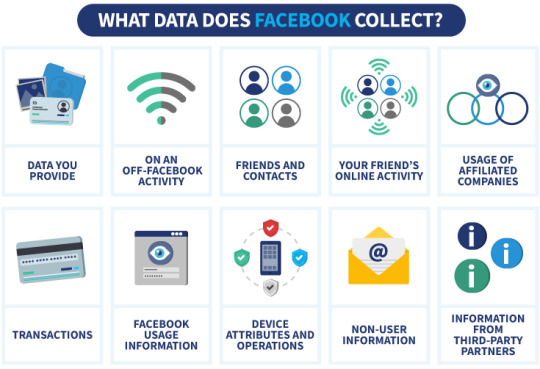
Facebook collects a wide array of information. This includes the information you provide directly like your name, email, birthday, and location. It also includes the content you post, your friends list, the pages and hashtags you interact with, and even the type of device you’re using.
How Does Facebook Collect Data?
Directly from the Users: The most straightforward way Facebook collects data is directly from its users. When you sign up, you provide personal details. Every time you post a status, like a page, or start a chat, Facebook collects that information.
Through Your Actions: Facebook tracks your interactions. This includes the posts you like, the pages you follow, and the friends you have. This helps Facebook understand your preferences and tailor your News Feed.
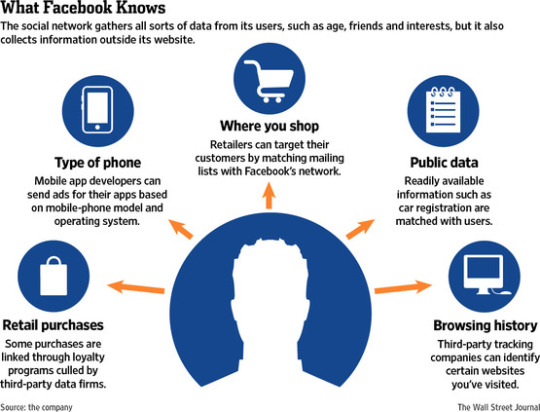
Through Third-Party Apps and Websites: When you use your Facebook account to log into other apps or websites, Facebook receives data from these sites. This can include information about your activities and purchases.
Through Cookies: Like many websites, Facebook uses ‘cookies’ to collect data. These small pieces of data are stored on your browser and let Facebook track your activity both on and off the platform.
Why Does Facebook Collect Data?
Facebook collects data primarily to personalize your experience. By understanding your preferences, Facebook can show you relevant content, suggest new friends, and even target advertisements.
However, this extensive data collection has raised privacy concerns. It’s essential to regularly review your privacy settings and be mindful of the information you share.

Remember, in the digital world, knowledge is power. Understanding how platforms like Facebook collect and use your data is the first step towards protecting your online privacy.
#college#data#data privacy#university#data security#the philippines#Facebook#social media#data tracking#data collection
0 notes
Text
Entry 8:
The Art of Data Disposal: A Guide to Data Disposal Protocol
In the digital age, data is everywhere. While much attention is given to the collection and use of data, an equally important aspect is often overlooked: data disposal. Proper data disposal is crucial for maintaining privacy and preventing unauthorized access to sensitive information.
Understanding Data Disposal
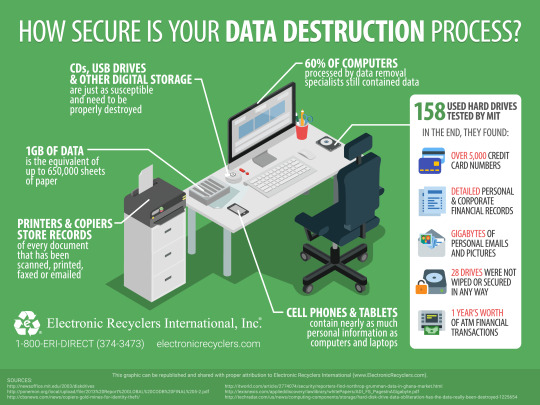
Data disposal refers to the process of discarding or getting rid of data that is no longer needed. This can include anything from deleting files on a computer to physically destroying hard drives. The goal is to ensure that the data cannot be recovered or accessed by unauthorized individuals.
Why is Data Disposal Important?
Proper data disposal is crucial for several reasons:
Privacy: Data often contains sensitive information. If not disposed of properly, this information could fall into the wrong hands, leading to privacy breaches.
Legal Compliance: Many jurisdictions have laws and regulations that require businesses to properly dispose of certain types of data.
Efficiency: Proper data disposal can help improve the efficiency of your data storage systems by freeing up space.
Implementing a Data Disposal Protocol
Here are some steps to consider when implementing a data disposal protocol:
Identify the Data: The first step is to identify the data that needs to be disposed of. This could include outdated customer information, old financial records, or obsolete business documents.
Choose a Disposal Method: The method of disposal will depend on the type of data. Digital data can often be deleted or wiped using software tools. Physical data may need to be shredded or incinerated.
Verify the Disposal: After the data has been disposed of, it’s important to verify that the process was successful. This could involve checking that files have been deleted or inspecting physical media for damage.
Document the Process: Keep a record of what data was disposed of, when, and how. This can be important for legal compliance and for tracking your data management practices.
Remember, data disposal is an important part of data management. By implementing a robust data disposal protocol, you can help protect your privacy, comply with the law, and improve your data management practices.
0 notes
Text
Entry 7:
The Intricate Web of Online Social Networks
In the digital age, online social networks have become an integral part of our lives. They have transformed the way we communicate, share information, and even the way we perceive ourselves and others. Here’s a closer look at the fascinating world of online social networks.
The Power of Connection
Online social networks, from Facebook to Instagram, Twitter to LinkedIn, have brought people closer than ever before. They have made it possible for us to connect with friends, family, and even strangers from across the globe with just a click. We can share our lives, our thoughts, our dreams, and our fears, creating a sense of community that transcends geographical boundaries.

The Double-Edged Sword
However, like all things, online social networks are a double-edged sword. While they bring us closer, they can also make us feel more isolated. The constant barrage of picture-perfect lives can lead to feelings of inadequacy and FOMO (Fear of Missing Out). It’s important to remember that what we see on social media is often a curated version of reality.

The Impact on Society
Online social networks have also had a profound impact on society. They have given a platform to voices that were previously unheard, leading to social change. However, they have also been used to spread misinformation and hate, highlighting the need for responsible use and regulation.

Navigating the Online Social Network Maze
Navigating the online social network maze can be challenging. It’s important to use these platforms responsibly, be mindful of the information we share, and remember to take regular digital detoxes. After all, while online social networks can help us connect with others, nothing can replace the value of real-world interactions.
So, go ahead and enjoy the intricate web of online social networks. Connect, share, learn, but also remember to step back, disconnect, and enjoy the real world. Because at the end of the day, it’s all about balance.

1 note
·
View note
Text
Entry 6:
Data Breaches in the Philippines: A Rising Concern
In the digital age, data breaches have become a significant concern worldwide, and the Philippines is no exception. Various sectors, including businesses, government agencies, and universities, have been affected. This blog post will delve into some notable incidents that have occurred in the country.
Sephora Data Breach (2019)
The beauty retailer Sephora experienced a critical data breach in 2019. Malicious users parsed data from customers’ previous purchases, acquiring encrypted passwords, contact information, email addresses, and even data logs regarding their purchasing behavior. This incident highlighted the vulnerability of e-commerce platforms and the need for robust cybersecurity measures.

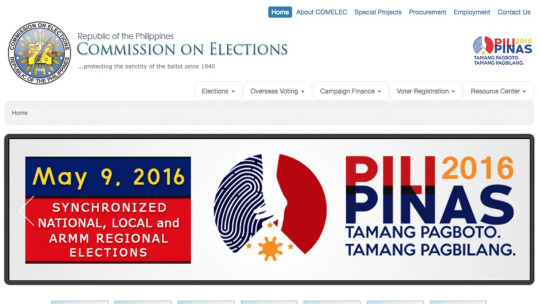
Voter Registration System Breach (2016)
Often cited as the country’s worst data breach in digital history, the voter registration system cyberattacks in 2016 resulted in the theft of millions of fingerprint records. This incident not only compromised the personal information of millions of Filipinos but also raised serious questions about the security of government databases.
Data Breach in Philippine Businesses (2022)
In 2022, Philippine businesses experienced over 1 million data breaches, resulting in hundreds of millions of pesos in damage. These breaches exposed the sensitive information of countless individuals and businesses, underscoring the urgent need for improved data protection measures in the private sector.
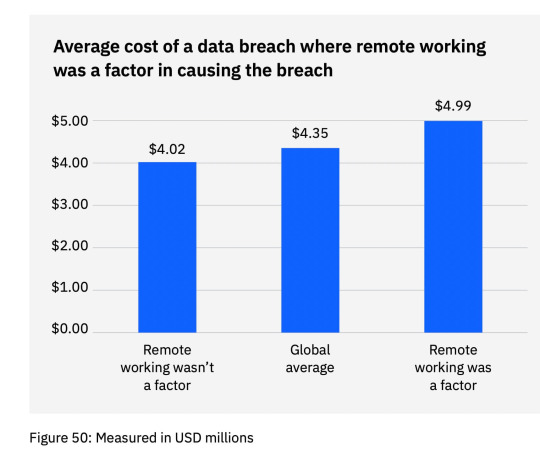
Data Breach in Government Agencies (2023)
A massive data hack in 2023 exposed 817.54 gigabytes of both applicant and employee records under multiple state agencies, including the Philippine National Police (PNP), National Bureau of Investigation (NBI), Bureau of Internal Revenue (BIR), and Special Action Force. This breach underscored the vulnerability of government databases and the need for stringent cybersecurity measures.

Data breaches pose a significant threat to both individuals and organizations. As these incidents in the Philippines illustrate, no sector is immune. It is crucial for all entities, whether private businesses, government agencies, or universities, to prioritize data security and invest in robust cybersecurity measures. Only then can we hope to safeguard our digital assets and protect ourselves from the damaging effects of data breaches.
0 notes
Text
Entry 5:
The Philippines' Composition: Data Privacy Compliance and Accountability Framework
In an increasingly interconnected world, data privacy has become a critical concern for individuals, organizations, and governments alike. As more personal information is collected, processed, and shared, ensuring its protection and responsible handling is paramount. In the Philippines, the Data Privacy Act of 2012 (Republic Act No. 10173) serves as the legal foundation for safeguarding personal data. Let’s delve into the key aspects of data privacy compliance and accountability in the country.
Understanding the Data Privacy Act (DPA)
The Data Privacy Act (DPA) was enacted to protect the fundamental right to privacy of individuals while promoting economic growth and innovation. Here are some essential points about the DPA:
Scope and Applicability:
The DPA applies to both government and private sector entities that process personal data.
It covers data controllers (organizations that determine the purpose and means of processing) and data processors (entities that process data on behalf of controllers).
Data Privacy Principles:
The DPA outlines several principles, including transparency, legitimate purpose, proportionality, and accountability.
Organizations must inform individuals about the purpose of data collection, obtain consent, and ensure data accuracy.
Rights of Data Subjects:
Data subjects (individuals whose data is processed) have rights, such as the right to access their data, correct inaccuracies, and object to processing.
Organizations must establish mechanisms for data subjects to exercise these rights.
Security Measures:
Organizations must implement appropriate security measures to protect personal data from unauthorized access, disclosure, alteration, or destruction.
Breach notification requirements mandate timely reporting of security incidents to the National Privacy Commission (NPC).
The Accountability Framework
Accountability is a central theme in data privacy. It emphasizes that organizations are responsible for their data processing activities. Here’s how the accountability framework operates:
Privacy Management Program:
Organizations should establish a privacy management program that includes policies, procedures, and guidelines.
A designated Data Protection Officer (DPO) oversees compliance and acts as a point of contact with the NPC.
Privacy Impact Assessment (PIA):
Before implementing new projects or systems involving personal data, organizations conduct a PIA.
The PIA assesses potential risks to privacy and recommends mitigating measures.
Consent Management:
Organizations must obtain informed and specific consent from data subjects.
Consent should be freely given, revocable, and based on clear information.
Data Breach Response Plan:
Organizations prepare a data breach response plan to handle security incidents effectively.
This includes notifying affected individuals and the NPC within 72 hours of discovering a breach.
Challenges and Best Practices
While progress has been made, challenges remain. Some best practices for data privacy compliance include:
Employee Training: Regularly train employees on data privacy policies and practices.
Vendor Management: Ensure that third-party vendors comply with data protection requirements.
Privacy by Design: Integrate privacy considerations into system design and development.
Regular Audits: Conduct periodic audits to assess compliance and identify areas for improvement.
In conclusion, the Data Privacy Compliance and Accountability Framework in the Philippines aims to strike a balance between privacy protection and business innovation. Organizations that prioritize privacy not only comply with legal obligations but also build trust with their stakeholders.
Remember, data privacy is not just a legal requirement—it’s a fundamental right that deserves our collective attention and commitment.
Disclaimer: This blog post provides general information and does not constitute legal advice. Organizations should consult legal professionals for specific guidance on data privacy compliance.

0 notes
Text
Entry 4:
Harmonizing Privacy: Unraveling the Five Pillars of Data Protection
In this melodic exploration, we’ll delve into the symphony of data privacy principles, ensuring that our personal information remains in tune and well-protected.
In an era where data is the new oil, protecting personal information has become a top priority for organizations worldwide. In the Philippines, the National Privacy Commission (NPC) has established a robust framework to ensure data privacy. This framework is built on five key pillars that guide organizations in their data privacy compliance journey.
Appointing a Data Protection Officer (DPO)
Every organization that handles personal data is required to appoint a Data Protection Officer (DPO). The DPO is responsible for ensuring that the organization complies with the provisions of the Data Privacy Act of 2012. They should possess expertise in relevant privacy or data protection policies and practices, and understand the processing operations carried out by the organization.
Conducting a Privacy Impact Assessment (PIA)
A Privacy Impact Assessment (PIA) is a tool used to identify and reduce the privacy risks of entities by analyzing the personal data that are processed and the policies in place to protect the data. It helps organizations identify potential vulnerabilities and implement appropriate measures to address them.
Preparing a Privacy Management Program
A Privacy Management Program is a comprehensive document that outlines the organization’s approach to data privacy. It includes the organization’s data privacy policies, procedures, and practices. This program serves as a roadmap for how the organization will handle personal data and ensure compliance with data privacy laws.
Implementing Privacy and Data Protection Measures
Privacy and data protection measures are crucial in safeguarding personal data. These measures include technical and organizational safeguards that protect personal data from unauthorized access, use, disclosure, alteration, and destruction. It also involves the creation of a security incident response team and the implementation of an incident response procedure.
Preparing and Implementing a Breach Reporting Procedure
In the event of a data breach, organizations must have a clear procedure in place. This includes steps to contain the breach, restore integrity to the information and communications system, and notify affected individuals. A well-prepared breach reporting procedure can help mitigate the impact of a data breach and ensure timely response.
In conclusion, these five pillars provide a comprehensive framework for ensuring data privacy. By adhering to these guidelines, organizations can protect personal data, comply with legal requirements, and build trust with their stakeholders. As data privacy continues to evolve, it’s crucial for organizations to stay updated on the latest best practices and regulations to ensure they’re doing all they can to protect personal data.
0 notes
Text
Entry 3:
Data Privacy Sonata: Safeguarding your digital world
In our harmonious world of music, where melodies and rhythms flow seamlessly, protecting the originality and rights of compositions has become crucial. Whether you’re a user, a business, or a platform, understanding and adhering to these principles ensures a respectful and secure data environment.
Data should be processed lawfully, fairly, and transparently in relation to individuals. Companies collecting personal data must operate within legal boundaries, providing clear privacy policies and purposes. Transparency is key users have the right to know why their data is collected and how it will be used. Moreover, Data should be collected for specific, legitimate purposes and not used beyond those bounds.
Brands must articulate why they need your data and how they intend to use it. For users, this means having the right to choose what data they share and how it’s utilized. Furthermore, collect only the data you truly need. Minimize unnecessary data collection to reduce risks. Less is often more when it comes to personal information.
Data should also be accurate and up to date. Companies must ensure that the data they hold remains reliable. Users have the right to correct inaccuracies, but data should be stored only for as long as necessary.
Limit data retention to prevent unnecessary exposure. In addition, data must be secure and confidential. Protect it from unauthorized access, breaches, and misuse. Encryption, access controls, and robust security practices are vital. Lastly, organizations must be accountable for their data practices. They should demonstrate compliance, handle breaches responsibly, and empower users with control over their data.
These aren’t just for governing bodies—they represent the spirit of data responsibility that we should demand from platforms and providers. Let’s raise the bar for data protection and privacy! 🛡️🔐

0 notes
Text
Entry 2:
“Crescendo in Cyberspace: Understanding the Melody of Data Privacy and the Rising Value of Intangible Data”
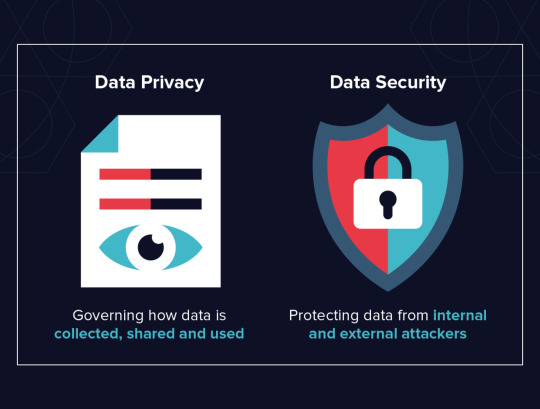
With regard to data privacy, it pertains to how an individual’s data is collected, utilized and maintained in accordance with relevant privacy laws and regulations. It involves the correct handling, processing, storage and usage of personal information. It is only concerned about people’s freedom with their own information.
On a different light, data security protects personal data from unauthorized third-party access, hacking attacks or any use that exploits its privacy. This is meant to protect personal data by using diverse methods and techniques that ensure its confidentiality. In addition to this, Data security ensures that integrity of the data which means that the information must be accurate and reliable as well as be available when required for authorized individuals.
Briefly speaking, Data Privacy is about how one collects uses upholds drops retains and stores the details appropriately. On the other hand, Policies Techniques Used in Securing Personal Data. The two can exist without each other but not vice versa. For example, you cannot have data privacy without first having data security.
Now in the age of digital data, information has become a valuable commodity. It is commonly said that data is the new oil. However, why is data preferred to physical properties?
To start with, consumer behavior insights are provided by data which is vital to businesses. Facebook and Google among other companies make billions through it in terms of advertisements. Platform companies and data-aggregators sell individualized data to advertisement networks as well as marketers seeking to reach specific segments, affect purchasing decisions and set dynamic prices.
Again, decision-making processes necessitate having reliable data. Governments are getting increasingly data-driven and leveraging open government data to improve citizens’ quality of life through better designed targeted welfare schemes, evidence-based policy making and more participatory governance.
Moreover, the potential for misuse also shows the value associated with such information. Data thieves usually steal personal information so that they can vend it on dark web. An identity thief can expect to get ₱1,120 - ₱12,600.
Therefore, the specific worth of physical stuff is their tangibility, meanwhile the value of data comes from the power that it has to be used for making positive changes in businesses and much more. Furthermore, data can even be sold for monetary gain. In the process we are generating and sharing a large amount of data, understanding the importance of this data as well as ensure the data security is vital now.
1 note
·
View note
Text
Entry 1:
Composing Harmony: The Symphony of Privacy, Policy, and Data Protection in the Philippines
Privacy Policies are akin to the sheet music of an orchestra. Just as sheet music outlines every note, rest, and dynamic for each instrument, a Privacy Policy details how an entity will handle each piece of customer data. It informs the ‘musicians’ (clients) about the ‘melodies’ (types of data) being ‘played’ (collected), and whether these ‘melodies’ are kept ‘solo’ (in secrecy), ‘performed with the ensemble’ (shared with allies), or ‘played to other audiences’ (sold to other organizations). Much like how sheet music provides a broader overview compared to individual instrument parts, Privacy Policies offer a more comprehensive view than data use statements.
Personal information can be anything from a person’s name, address, date of birth, marital status, contact information, ID issue and expiry date, financial records credit information medical history travel records intentions with respect to goods and services.
In the Philippines, the Data Privacy Act of 2012 is a contemporary law for the 21st century that deals with modern crimes and worries. It safeguards personal privacy of citizens but also assures free circulation of information to foster innovation and expansion. It stipulates how personal data will be collected, recorded, arranged, stored, updated or modified, retrieved or consulted upon use plus any electronic document which contains such data.
Besides that, individuals whose personal details are gathered and preserved are known as data subjects. They have rights under the Data Privacy Act of 2012 (DPA) and therefore should know their rights so as to protect their online as well as offline data privacy.
Organizations that process or otherwise engaged in handling personal information are termed Personal Information Controllers (PICs) and Personal Information Processors (PIPs). To comply with the Data Privacy Act of 2012 (DPA), NPC issues regulations and directions to assist PICs/ PIPs in carrying out their duties.
Finally, it can be concluded that policy on privacy has a significant role in guarding personal records while ensuring ethical treatment. The Data Privacy Act of 2012 in the Philippines provides a strong foundation for data protection thereby guaranteeing respect of individual’s right to privacy while promoting responsible treatment towards personal information from organizations.
0 notes
Text
Get to know me!
A harmonious hello to you! Harold is the name, currently orchestrating my studies in Information Technology in The Philippines. This blog is my composition, mostly about the symphony of data and how our simple notes of data can create a melody in our lives! If you’d like to join the audience and enjoy the performance, feel free to follow my blog!

1 note
·
View note