Senior DevOps Engineer | AWS | Automation | 2x AWS | CKA | Terraform Certified | k8s | Docker | Interests in microservice patterns, serverless, JS/TS.Linux 🐧
Don't wanna be here? Send us removal request.
Text
Understanding Agile Methodology: A Comprehensive Guide
In today’s fast-paced world, the Agile methodology has emerged as a game-changer in project management and software development. But what exactly is Agile, and why has it gained such popularity? This blog post aims to demystify Agile methodology, exploring its principles, benefits, and key practices.
For those looking to enhance their skills, Agile Certification Course offers comprehensive education and job placement assistance, making it easier to master and advance your career.

What is Agile Methodology?
Agile is a project management and product development approach that emphasizes flexibility, collaboration, and customer satisfaction. Originally rooted in software development, Agile has now been adopted across various industries, including marketing, education, and product management.
The Agile Manifesto
The foundation of Agile methodology is encapsulated in the Agile Manifesto, which was created in 2001 by a group of software developers. The manifesto outlines four key values:
Individuals and interactions over processes and tools
Working software over comprehensive documentation
Customer collaboration over contract negotiation
Responding to change over following a plan
These values highlight the importance of adaptability and human-centric collaboration in the Agile framework.
Core Principles of Agile
In addition to its values, Agile is guided by twelve principles that focus on customer satisfaction, team collaboration, and responsiveness. Some of these principles include:
Delivering valuable software frequently, with a preference for shorter timescales.
Welcoming changing requirements, even late in development.
Working closely with stakeholders throughout the project.
Building projects around motivated individuals who are given the environment and support they need.
Benefits of Agile Methodology
Implementing Agile methodology can bring numerous advantages to organizations:
Increased Flexibility: Agile teams can quickly adapt to changes, ensuring that the final product meets customer needs.
Enhanced Collaboration: Regular communication and collaboration among team members foster a cohesive work environment.
Higher Customer Satisfaction: Frequent delivery of functional software keeps customers engaged and allows for continuous feedback.
Improved Quality: Agile practices incorporate regular testing and feedback, leading to higher quality outcomes.
It's simpler to master this course and progress your profession with the help of Best Online Training & Placement programs, which provide through instruction and job placement support to anyone seeking to improve their talents.

Key Practices in Agile
Agile methodology encompasses various frameworks and practices. Here are some popular ones:
Scrum
Scrum is one of the most widely used Agile frameworks. It divides projects into small, manageable units called sprints, typically lasting two to four weeks. Scrum teams hold daily stand-up meetings to discuss progress and obstacles, fostering accountability and transparency.
Kanban
Kanban focuses on visualizing the workflow to optimize efficiency. Teams use a Kanban board to track tasks, allowing them to manage work in progress and identify bottlenecks.
Extreme Programming (XP)
Extreme Programming emphasizes technical excellence and customer satisfaction. It promotes practices such as pair programming, test-driven development, and continuous integration to improve software quality.
Conclusion
Agile methodology represents a shift from traditional project management approaches, prioritizing adaptability and collaboration. By embracing Agile principles, organizations can enhance their responsiveness to changes and improve overall project outcomes. Whether you’re in software development or any other sector, understanding and implementing Agile can lead to significant benefits and a more productive work environment.
0 notes
Text
A Deep Dive into Amazon CloudWatch: Your Ultimate Monitoring Solution
In today's cloud-centric world, effective monitoring is crucial for maintaining the performance and reliability of applications and services. Amazon CloudWatch, a core component of the Amazon Web Services (AWS) ecosystem, offers a robust solution for monitoring AWS resources and applications. In this blog, we’ll explore the features, benefits, and best practices for using Amazon CloudWatch to ensure your cloud infrastructure operates smoothly.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is Amazon CloudWatch?
Amazon CloudWatch is a comprehensive monitoring and observability service designed to provide real-time insights into your AWS environment. It collects data from various AWS resources, enabling users to track performance, set alarms, and gain visibility into overall system health. With CloudWatch, organizations can proactively manage their cloud resources, ensuring optimal performance and minimal downtime.
Key Features of Amazon CloudWatch
1. Comprehensive Metrics Collection
CloudWatch automatically gathers metrics from numerous AWS services. This includes essential data points such as CPU utilization, memory usage, and network traffic for services like EC2, RDS, and Lambda. By aggregating this data, users can monitor the health and efficiency of their resources at a glance.
2. Log Management and Analysis
CloudWatch Logs allows you to collect, monitor, and analyze log files from your applications and AWS resources. Users can search through logs in real-time, set retention policies, and create metrics based on log data, enabling effective troubleshooting and performance optimization.
3. Alarms and Notifications
Setting up CloudWatch Alarms helps you stay informed about the health of your services. You can define thresholds for specific metrics, and when those thresholds are breached, CloudWatch can trigger notifications via Amazon SNS (Simple Notification Service), ensuring you can act swiftly to address potential issues.
4. Custom Dashboards
CloudWatch Dashboards enable users to create personalized views of their metrics. These visual representations allow for easy monitoring of multiple resources, helping teams identify trends, bottlenecks, and anomalies quickly.
5. Event-Driven Monitoring
With CloudWatch Events, you can respond to changes in your AWS environment automatically. By defining rules, you can trigger actions based on specific events, such as scaling resources in response to increased load, further enhancing the automation of your infrastructure management.
6. Integration with AWS Services
CloudWatch integrates seamlessly with a wide range of AWS services, including AWS Lambda, Auto Scaling, and Amazon ECS (Elastic Container Service). This integration allows for more cohesive operations and enables automated responses to monitoring data.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.

Benefits of Using Amazon CloudWatch
- Enhanced Operational Visibility
CloudWatch provides deep insights into your AWS resources, making it easier to monitor performance and troubleshoot issues before they escalate.
Cost Management
By leveraging CloudWatch's monitoring capabilities, organizations can optimize resource usage, avoiding unnecessary costs associated with over-provisioning or underutilized resources.
Increased Application Reliability
Proactive monitoring and alerting help maintain high application performance and reliability, leading to improved user experiences and satisfaction.
Streamlined Automation
Automating responses to specific metrics and log events can save time and reduce the need for manual interventions, allowing teams to focus on more strategic initiatives.
Conclusion
Amazon CloudWatch is an indispensable tool for anyone utilizing AWS. Its comprehensive monitoring capabilities empower organizations to maintain high levels of performance and reliability in their cloud environments. By leveraging the features and best practices outlined in this blog, you can optimize your use of CloudWatch and ensure your applications run smoothly, ultimately enhancing business success in the cloud.
0 notes
Text
A Deep Dive into Amazon Redshift: Your Guide to Cloud Data Warehousing
In the era of big data, organizations are increasingly turning to cloud solutions for efficient data management and analysis. Amazon Redshift, a prominent service from Amazon Web Services (AWS), has become a go-to choice for businesses looking to optimize their data warehousing capabilities. In this blog, we will explore what Amazon Redshift is, its architecture, features, and how it can transform your approach to data analytics.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is Amazon Redshift?
Amazon Redshift is a fully managed, cloud-based data warehouse service designed to handle large-scale data processing and analytics. It enables businesses to analyze vast amounts of structured and semi-structured data quickly and efficiently. With its architecture tailored for high performance, Redshift allows users to run complex queries and generate insights in real time.
The Architecture of Amazon Redshift
Understanding the architecture of Redshift is crucial to appreciating its capabilities. Here are the key components:
1. Columnar Storage
Unlike traditional row-based databases, Redshift uses a columnar storage model. This approach allows for more efficient data retrieval, as only the necessary columns are accessed during queries, significantly speeding up performance.
2. Massively Parallel Processing (MPP)
Redshift employs a massively parallel processing architecture, distributing workloads across multiple nodes. This means that queries can be processed simultaneously, enhancing speed and efficiency.
3. Data Compression
Redshift automatically compresses data to save storage space and improve query performance. By reducing the amount of data that needs to be scanned, it accelerates query execution.
4. Snapshots and Backups
Redshift provides automated snapshots of your data warehouse. This feature ensures data durability and allows for easy restoration in case of failure, enhancing data security.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.

Key Features of Amazon Redshift
1. Scalability
Redshift is designed to grow with your data. You can start with a small data warehouse and scale up to petabytes as your data needs expand. This scalability is vital for businesses experiencing rapid growth.
2. Integration with AWS Ecosystem
As part of AWS, Redshift integrates seamlessly with other services like Amazon S3, AWS Glue, and Amazon QuickSight. This integration simplifies data ingestion, transformation, and visualization, creating a cohesive data ecosystem.
3. Advanced Security Features
Redshift offers robust security measures, including data encryption, network isolation with Amazon VPC, and user access controls through AWS IAM. This ensures that your data remains secure and compliant with industry standards.
4. Cost-Effectiveness
With a pay-as-you-go pricing model, Redshift allows businesses to optimize costs based on their usage. Options for reserved instances further enhance cost savings, making it an attractive choice for organizations of all sizes.
Redshift supports a wide range of analytical queries, empowering businesses to explore data trends, customer behavior, and operational efficiencies comprehensively.
Conclusion
Amazon Redshift stands out as a powerful solution for cloud data warehousing and analytics. Its scalable architecture, high performance, and seamless integration with other AWS services make it an ideal choice for businesses looking to leverage their data effectively.
Whether you're a small startup or a large enterprise, Redshift can provide the tools you need to make data-driven decisions and stay competitive in today's data-centric landscape.
0 notes
Text
Demystifying AWS Virtual Private Cloud (VPC)
In the ever-evolving world of cloud computing, Amazon Web Services (AWS) has established itself as a leader, offering a wide array of services to meet diverse business needs. Among these services, the Virtual Private Cloud (VPC) is one of the most crucial components for organizations seeking to enhance their security and control over their cloud resources. This blog post provides a comprehensive guide to AWS VPC, exploring its features, benefits, and best practices.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is AWS VPC?
AWS Virtual Private Cloud (VPC) allows users to create a private, isolated section of the AWS cloud where they can launch and manage AWS resources. VPC enables businesses to control their virtual networking environment, including IP address ranges, subnets, routing, and security settings.
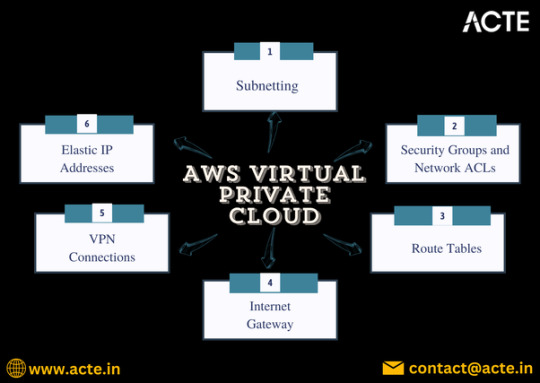
Key Features of AWS VPC
Custom IP Address Range:
When creating a VPC, you can define your own IP address range using Classless Inter-Domain Routing (CIDR) notation. This flexibility allows you to tailor your network architecture to your specific needs.
2. Subnets:
VPCs can be divided into subnets, which are smaller segments within the VPC. You can create public subnets (accessible from the internet) and private subnets (not directly accessible from the internet) to optimize resource security.
3. Security Groups and Network ACLs:
Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic. Network Access Control Lists (ACLs) provide an additional layer of security at the subnet level, enabling more granular traffic management.
4. Route Tables:
Route tables are used to determine where network traffic is directed. You can create custom routing rules to control the flow of traffic between your VPC, subnets, and the internet.
5. Internet Gateway and NAT Gateway:
An Internet Gateway allows communication between instances in your VPC and the internet. A NAT Gateway enables instances in a private subnet to initiate outbound traffic while preventing unsolicited inbound traffic.
6. VPN Connections and AWS Direct Connect:
VPC supports VPN connections, allowing secure communication between your on-premises network and your VPC. AWS Direct Connect provides a dedicated network connection, improving performance and reliability.
7. Elastic IP Addresses:
Elastic IPs are static IP addresses that can be associated with your instances, ensuring consistent public IP addresses even when instances are stopped and restarted.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Benefits of Using AWS VPC
Enhanced Security:
By isolating your resources within a VPC, you gain greater control over your network security. You can implement security measures tailored to your specific needs, enhancing data protection and compliance.
Flexibility:
AWS VPC provides the flexibility to design your network architecture according to your requirements. You can easily adjust your IP address ranges, subnets, and security settings.
Scalability:
VPCs are designed to scale seamlessly. You can add or remove resources as needed, ensuring your infrastructure can adapt to changing workloads without performance degradation.
Cost Efficiency:
With AWS's pay-as-you-go pricing model, you only pay for the resources you use. This makes VPC an economically viable option for organizations of all sizes.
Integration with Other AWS Services:
VPC integrates seamlessly with various AWS services, including Amazon EC2, RDS, and Lambda, allowing you to build comprehensive cloud solutions that meet your business needs.
Conclusion
AWS Virtual Private Cloud (VPC) is a vital service for businesses looking to secure and manage their cloud resources effectively. With its extensive features and benefits, VPC empowers organizations to create a customized and controlled network environment.
By understanding how to leverage VPC and adhering to best practices, businesses can maximize their cloud investment and ensure a robust, secure infrastructure. Whether you're new to AWS or looking to enhance your existing setup, mastering AWS VPC is crucial for success in the cloud.
0 notes
Text
Everything You Need to Know About Amazon Elastic Block Store
In the realm of cloud computing, efficient and reliable data storage is paramount. One of the key services offered by Amazon Web Services (AWS) is Amazon Elastic Block Store (EBS). This service provides scalable, high-performance block storage that is integral to running applications on Amazon EC2 (Elastic Compute Cloud). In this blog, we’ll cover everything you need to know about Amazon EBS, including its features, benefits, and use cases.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.
What is Amazon EBS?
Amazon EBS is a cloud-based block storage service designed for use with EC2 instances. It allows users to create volumes that can be attached to EC2 instances, enabling data to be read and written like a traditional hard drive. One of the standout features of EBS is its durability; the data on EBS volumes persists even after the EC2 instance is stopped or terminated.
Key Features of Amazon EBS
1. Durability and Availability
EBS is engineered for 99.999% availability and durability. It replicates data across multiple servers within an Availability Zone, ensuring that your data is safe and accessible, even in the event of hardware failures.
2. Scalability
EBS volumes can range from 1 GiB to 64 TiB, allowing you to scale your storage needs easily. This flexibility means you can start small and grow as your requirements increase without any downtime.
3. Performance Options
EBS offers several volume types to cater to various performance needs:
General Purpose SSD (gp2 and gp3): Suitable for a wide range of workloads, offering a balanced performance and cost.
Provisioned IOPS SSD (io1 and io2): Designed for I/O-intensive applications requiring high performance.
Throughput Optimized HDD (st1): Best for frequently accessed, throughput-intensive workloads.
Cold HDD (sc1): Ideal for infrequently accessed data, providing a cost-effective solution.
4. Snapshot Functionality
EBS allows users to create point-in-time snapshots of their volumes. These snapshots can serve as backups or be used to create new EBS volumes, facilitating data protection and recovery.
5. Encryption
EBS supports encryption both at rest and in transit, ensuring that your data is secure. You can enable encryption when creating a volume or snapshot, helping to meet compliance requirements.
6. Integration with AWS Services
Amazon EBS integrates seamlessly with other AWS services, making it easier to build and manage applications in the cloud. This integration enhances operational efficiency and simplifies data management.

To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Benefits of Using Amazon EBS
High Durability: With its robust architecture, EBS ensures that your data is secure and remains available.
Cost-Effective: Pay only for the storage you need, with the flexibility to choose the volume type that best meets your performance and budget requirements.
Ease of Management: EBS simplifies storage management, allowing you to create, attach, detach, and delete volumes with ease.
Fast Recovery: The snapshot feature enables quick recovery options, making it easier to restore data in case of failures.
Use Cases for Amazon EBS
Database Storage: EBS is often used for databases such as MySQL and Oracle, where performance and durability are crucial.
Big Data Processing: EBS can support big data workloads, providing the necessary storage for processing and analyzing large datasets.
Content Management Systems: EBS serves as an efficient solution for applications requiring quick access to data and media files.
Backup and Disaster Recovery: The snapshot functionality makes EBS an excellent choice for backup strategies, ensuring data protection.
Conclusion
Amazon Elastic Block Store is an essential component of the AWS ecosystem, providing reliable, scalable, and high-performance storage solutions for a wide range of applications. Its durability, performance options, and integration capabilities make it a top choice for businesses looking to enhance their cloud infrastructure.
By understanding the features, benefits, and use cases of Amazon EBS, organizations can make informed decisions about how to manage their data in the cloud effectively. Embrace the power of Amazon EBS and take your cloud storage strategy to new heights!
0 notes
Text
Exploring Amazon ECS: A Comprehensive Guide to AWS's Container Management Service
Amazon Elastic Container Service (ECS) is a powerful and flexible container orchestration service offered by Amazon Web Services (AWS). Designed for developers and organizations looking to deploy and manage containerized applications, ECS simplifies the orchestration process. In this blog, we'll explore the features, benefits, and best practices of using Amazon ECS.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is Amazon ECS?
Amazon ECS allows you to run Docker containers on a managed cluster of Amazon EC2 instances. It abstracts the complexity of infrastructure management, enabling you to focus on building and deploying applications. With ECS, you can easily manage the lifecycle of your containers, scale applications based on demand, and integrate with other AWS services.
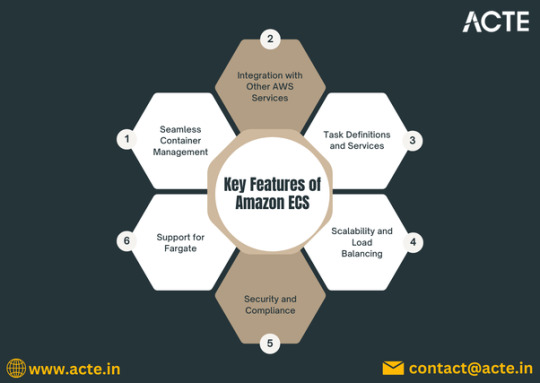
Key Features of Amazon ECS
1. Task Definitions
Task definitions are a crucial component of ECS. They define the parameters for your containers, including the Docker image to use, CPU and memory requirements, networking settings, and environment variables. This makes it easy to deploy consistent and repeatable container instances.
2. Service Management
ECS allows you to define services that maintain a specified number of task instances running at all times. If a task fails, ECS automatically replaces it, ensuring high availability for your applications.
3. Integration with AWS Services
ECS seamlessly integrates with other AWS services, such as Amazon RDS, Amazon S3, and AWS Lambda. This integration helps you build complex applications that leverage the full power of the AWS ecosystem.
4. Scalability and Load Balancing
ECS supports auto-scaling, allowing you to adjust the number of running tasks based on application demand. You can set up policies that scale your services in or out automatically, ensuring optimal performance while minimizing costs.
5. Security Features
ECS provides robust security controls, including IAM roles for fine-grained access management, VPC support for network isolation, and encryption options for sensitive data. This helps you maintain compliance and protect your applications.
6. Support for Fargate
AWS Fargate is a serverless compute engine for running containers. With Fargate, you can run ECS tasks without managing the underlying EC2 instances, simplifying deployment and scaling further.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Benefits of Using Amazon ECS
Cost Efficiency: With ECS, you only pay for the resources you use, reducing infrastructure costs. Fargate eliminates the need for provisioning EC2 instances, allowing for more flexible billing.
High Availability: ECS is built for resilience. Its automatic health checks and self-healing capabilities ensure your applications remain available even in the face of failures.
Flexibility in Deployment: You can choose to run your containers on EC2 instances or use Fargate, giving you the flexibility to select the best deployment model for your needs.
Best Practices for Using Amazon ECS
Use Task Definitions Wisely: Create reusable task definitions to minimize duplication and ensure consistency across environments.
Implement Auto-Scaling: Set up auto-scaling policies based on metrics such as CPU utilization or request count to optimize resource usage.
Leverage IAM for Security: Use IAM roles to define permissions for your tasks, ensuring that your applications have access to only the resources they need.
Monitor and Log: Utilize AWS CloudWatch for monitoring and logging your ECS services. This will help you identify performance bottlenecks and troubleshoot issues.
Test Before Production: Always test your applications in a staging environment before deploying to production. This helps catch issues early and ensures a smooth rollout.
Conclusion
Amazon ECS is a robust solution for managing containerized applications in the cloud. With its rich feature set, seamless integration with AWS services, and support for both EC2 and Fargate, ECS provides the tools necessary to build, deploy, and scale applications efficiently. By understanding its capabilities and following best practices, you can harness the full potential of Amazon ECS to enhance your application development and deployment processes.
0 notes
Text
A Deep Dive into Serverless Computing: Everything You Need to Know
In the rapidly evolving landscape of cloud technology, serverless computing has emerged as one of the most innovative paradigms. But what does “serverless” really mean, and how does it impact the way developers build and deploy applications? Let’s dive into the essentials of serverless computing.
If you want to advance your career at the Cloud Computing Course in Coimbatore, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

Defining Serverless Computing
Serverless computing, despite its name, does not mean that there are no servers involved. Instead, it refers to a cloud computing model where the cloud provider manages the server infrastructure. This allows developers to run code without worrying about the underlying hardware or server management tasks.
Key Features of Serverless Computing
Abstraction of Infrastructure: Developers can focus on writing code without needing to provision or manage servers. This abstraction simplifies the development process and reduces operational overhead.
Event-Driven Execution: Serverless architectures are typically event-driven. Functions are executed in response to events, such as HTTP requests, database changes, or scheduled tasks.
Automatic Scaling: Serverless platforms automatically scale resources up or down based on demand. This means that during high traffic, more instances of a function can run simultaneously, and during low traffic, resources are scaled back.
Cost Efficiency: In a serverless model, you pay only for the computing resources you use. This pay-as-you-go pricing structure can lead to significant cost savings, especially for applications with variable workloads.
How Serverless Computing Works
1. Function Deployment
Developers write small, single-purpose functions that perform specific tasks. These functions are deployed to a serverless platform like AWS Lambda, Google Cloud Functions, or Azure Functions.
2. Event Triggers
Once deployed, these functions can be triggered by various events. For instance, an HTTP request to an API endpoint or a new file uploaded to cloud storage can initiate the function.
3. Execution and Scaling
When an event occurs, the serverless platform automatically allocates the necessary resources to execute the function. This happens in real-time, allowing for quick responses to user interactions. If multiple events occur simultaneously, the platform scales up to handle the increased load automatically.
4. Monitoring and Management
Cloud providers offer tools for monitoring the performance of serverless applications. Developers can track metrics such as execution time, error rates, and resource usage, helping them to optimize their code and manage costs effectively.

For those looking to excel in Cloud computing, Cloud Computing Online Course is highly suggested. Look for classes that align with your preferred programming language and learning approach.
Benefits of Serverless Computing
1. Reduced Operational Burden
By eliminating the need to manage servers and infrastructure, serverless computing allows developers to focus on writing code and delivering features. This can lead to faster development cycles and improved productivity.
2. Cost Savings
With a pay-per-execution model, businesses only pay for the resources they use. This is particularly beneficial for applications with irregular traffic patterns, as there’s no need to maintain idle servers.
3. Seamless Scalability
Serverless architectures can effortlessly scale with demand, ensuring that applications remain responsive even during peak usage times. This eliminates the need for manual scaling or resource management.
4. Enhanced Agility
Serverless computing fosters an agile development environment. Teams can quickly deploy updates and new features, enabling rapid iteration and experimentation without the constraints of traditional infrastructure.
Use Cases for Serverless Computing
Web Applications: Ideal for developing scalable web applications that need to respond quickly to user inputs.
APIs: Serverless functions can handle API requests efficiently, providing a lightweight backend for applications.
Data Processing: Useful for real-time data processing tasks, such as analytics and batch processing.
IoT Applications: Handles events generated by IoT devices, allowing for real-time data processing and response.
Conclusion
Serverless computing is revolutionizing the way developers approach application development and deployment. By enabling them to focus on writing code without the complexities of managing servers, serverless architectures are paving the way for more efficient, scalable, and cost-effective solutions.
As more businesses embrace this model, understanding serverless computing will be crucial for developers and organizations aiming to thrive in the digital age. Whether you’re building a new application or modernizing an existing one, serverless computing offers a powerful approach that can significantly enhance your development process.
0 notes
Text
An Introduction to Mobile Cloud Computing
In the age of smartphones and tablets, the way we access and use technology has shifted dramatically. Mobile cloud computing stands at the forefront of this transformation, combining the power of cloud computing with the convenience of mobile devices. This blog post will introduce you to the concept of mobile cloud computing, its benefits, challenges, and its growing significance in our everyday lives.
If you want to advance your career at the Cloud Computing Course in Coimbatore, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is Mobile Cloud Computing?
Mobile cloud computing refers to the integration of cloud computing services and mobile device capabilities. It allows users to access applications, data, and computing resources stored in the cloud through mobile devices. This means that users are no longer limited by the hardware capabilities of their devices; instead, they can leverage the vast resources of the cloud.
Key Components
Mobile Devices: Smartphones, tablets, and other portable gadgets that connect to cloud services.
Cloud Infrastructure: Remote servers and data centers that provide storage, processing power, and applications.
Internet Connectivity: A reliable internet connection that enables communication between mobile devices and cloud services.
Benefits of Mobile Cloud Computing
Mobile cloud computing offers several advantages that enhance both personal and business productivity:
1. Accessibility
One of the most significant benefits is the ability to access data and applications from anywhere at any time. Users can work on projects, retrieve information, and collaborate with colleagues regardless of their physical location, as long as they have internet access.
2. Cost Efficiency
By utilizing cloud services, businesses can reduce the costs associated with maintaining on-premises infrastructure. The pay-as-you-go pricing model allows organizations to only pay for the resources they use, making it a budget-friendly option.
3. Scalability
Mobile cloud computing enables organizations to scale their resources up or down based on demand. Whether facing a sudden increase in users or needing to reduce capacity, businesses can quickly adjust their cloud services without significant investment.
4. Automatic Updates
Cloud applications often receive automatic updates, ensuring that users have access to the latest features and security enhancements without the need for manual installation. This helps keep software current and reduces the burden on IT teams.
5. Improved Collaboration
Mobile cloud computing enhances collaboration by allowing multiple users to access and work on the same documents in real-time. Tools like Google Workspace and Microsoft Office 365 enable teams to collaborate seamlessly, regardless of their locations.
For those looking to excel in Cloud computing, Cloud Computing Online Course is highly suggested. Look for classes that align with your preferred programming language and learning approach.

Challenges of Mobile Cloud Computing
While the benefits are compelling, there are several challenges associated with mobile cloud computing:
1. Security Risks
Storing data in the cloud raises security concerns. Mobile devices are susceptible to theft and loss, which can lead to unauthorized access to sensitive information. Implementing strong security measures, such as encryption and multi-factor authentication, is essential.
2. Dependence on Internet Connectivity
Mobile cloud computing relies heavily on internet access. In areas with poor connectivity, users may experience slow performance or interruptions, which can hinder productivity.
3. Data Privacy Concerns
With increasing awareness of data privacy, users must be cautious about how their information is stored and processed in the cloud. Understanding the provider’s privacy policies and compliance with regulations is crucial.
4. Potential Hidden Costs
While cloud services can be cost-effective, organizations should be aware of potential hidden costs, such as data transfer fees or charges for additional features. Conducting a thorough cost analysis is important before committing to a cloud solution.
The Future of Mobile Cloud Computing
The future of mobile cloud computing looks promising, with advancements in technology paving the way for enhanced capabilities. The rollout of 5G networks is expected to improve data transfer speeds and reduce latency, making cloud applications more efficient and responsive. Additionally, trends like edge computing will enable faster processing by bringing data closer to the user, further enhancing the mobile cloud experience.
Conclusion
Mobile cloud computing is revolutionizing the way we interact with technology, offering unparalleled access to applications and data on the go. Understanding its benefits and challenges is essential for individuals and organizations looking to maximize productivity and collaboration in today’s fast-paced digital landscape.
As mobile devices and cloud technologies continue to evolve, embracing mobile cloud computing will be vital for anyone aiming to thrive in our interconnected world. With its potential to enhance efficiency and accessibility, mobile cloud computing is not just a trend; it’s a fundamental shift in how we work and communicate.
0 notes
Text
Exploring Communications-as-a-Service (CaaS) in the Cloud
In today's digital age, effective communication is pivotal for business success. As organizations adapt to the demands of remote work and global collaboration, Communications-as-a-Service (CaaS) has emerged as a powerful solution. This blog post will explore what CaaS is, its benefits, and its role in enhancing communication in the cloud.
If you want to advance your career at the Cloud Computing Course in Coimbatore, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is Communications-as-a-Service (CaaS)?
Communications-as-a-Service (CaaS) is a cloud-based delivery model that provides a range of communication solutions through the internet. This includes services such as voice over IP (VoIP), video conferencing, instant messaging, and team collaboration tools. By utilizing CaaS, businesses can access these services without the need for extensive hardware or software installations, allowing for greater flexibility and efficiency.
Key Components of CaaS
VoIP Services: Voice communication over the internet, enabling cost-effective calls and enhanced call management features.
Video Conferencing: Tools that facilitate face-to-face meetings, crucial for remote teams and virtual collaboration.
Messaging Services: Instant messaging and chat capabilities that promote quick and efficient communication among team members.
Collaboration Tools: Integrated platforms that allow teams to work together seamlessly on projects, share files, and manage tasks.
Benefits of CaaS
1. Flexibility and Scalability
One of the primary advantages of CaaS is its ability to scale with your business. Organizations can easily add or remove services based on their changing needs, making it ideal for companies of all sizes.
2. Cost Savings
CaaS solutions typically operate on a subscription basis, which helps organizations reduce upfront costs associated with traditional communication systems. This pay-as-you-go model allows businesses to allocate resources more effectively.
3. Enhanced Collaboration
CaaS fosters better collaboration among team members, enabling them to communicate and share information in real-time, regardless of their physical location. This is particularly valuable for remote and hybrid teams.

For those looking to excel in Cloud computing, Cloud Computing Online Course is highly suggested. Look for classes that align with your preferred programming language and learning approach.
4. Simplified IT Management
By outsourcing communication services to a CaaS provider, businesses can alleviate the burden on their IT departments. This allows IT teams to focus on strategic initiatives rather than managing complex communication infrastructure.
5. Improved Customer Experience
CaaS enables businesses to provide multi-channel support, allowing customers to reach out via their preferred method—be it voice, chat, or video. This flexibility enhances customer satisfaction and engagement.
Use Cases for CaaS
Remote Work Solutions: CaaS is essential for remote teams, providing them with the necessary tools to communicate and collaborate effectively.
Customer Support Centers: Businesses can create robust support systems that integrate various communication channels to assist customers more efficiently.
Project Management: Teams can utilize CaaS for managing projects, ensuring that all members are aligned and can communicate easily.
Conclusion
Communications-as-a-Service (CaaS) is revolutionizing how organizations approach communication in the cloud. By offering flexible, scalable, and cost-effective solutions, CaaS enables businesses to enhance collaboration, improve customer engagement, and reduce IT burdens. As the demand for effective communication tools continues to grow, CaaS is set to play a vital role in shaping the future of business communication.
0 notes
Text
Decoding SLAs: A Guide to Cloud Service Agreements
In the digital age, businesses increasingly rely on cloud computing to enhance efficiency and flexibility. However, navigating the complexities of cloud services can be daunting, particularly when it comes to understanding Service Level Agreements (SLAs). This guide aims to decode SLAs and clarify their significance in the world of cloud computing.
If you want to advance your career at the Cloud Computing Course in Coimbatore, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What Are SLAs?
A Service Level Agreement (SLA) is a formal document that outlines the expectations and responsibilities between a service provider and a customer. It serves as a contract that defines the level of service the provider commits to delivering, along with the metrics used to measure that service.
Key Elements of an SLA
Service Overview: This section provides a comprehensive description of the services offered, including any key features and functionalities.
Performance Metrics: SLAs specify various performance metrics that the provider must meet. Common metrics include:
Uptime Guarantees: Typically expressed as a percentage (e.g., 99.9%), indicating the expected availability of the service.
Response Time: The maximum time allowed for the service to respond to user requests.
Support Response Times: Details on how quickly the provider will respond to support inquiries.
Responsibilities: The SLA delineates the responsibilities of both parties. This ensures that customers understand their role and the expectations placed upon them.
Remedies for Non-Compliance: SLAs outline the consequences if the provider fails to meet the agreed-upon service levels. This may include financial penalties or service credits.
Monitoring and Reporting: Many SLAs include provisions for how service performance will be monitored and reported, promoting transparency between the provider and the customer.

For those looking to excel in Cloud computing, Cloud Computing Online Course is highly suggested. Look for classes that align with your preferred programming language and learning approach.
Why Are SLAs Important?
Establishing Trust: SLAs create a framework of trust by clearly defining what customers can expect from their service provider.
Risk Mitigation: By outlining performance expectations, SLAs help businesses manage potential risks associated with service outages or performance issues.
Legal Framework: In case of disputes, SLAs serve as a legal reference point that outlines the agreed-upon terms.
Accountability: SLAs hold service providers accountable for their performance, ensuring they deliver what they promise.
Selecting the Right SLA
When choosing a cloud service provider, it’s essential to carefully review their SLA. Here are some key factors to consider:
Uptime and Availability: Look for clear uptime guarantees and understand how they are calculated.
Support Options: Investigate the level of support offered and the expected response times for different types of inquiries.
Flexibility: Consider whether the SLA can be adjusted to accommodate changing business needs.
Conclusion
Decoding SLAs is vital for any organization looking to leverage cloud services effectively. By understanding the components and significance of SLAs, businesses can make informed choices, manage risks, and establish productive relationships with their cloud service providers. Ultimately, a well-defined SLA not only safeguards your interests but also contributes to a more reliable and efficient cloud experience.
0 notes
Text
A Comprehensive Guide to Platform as a Service (PaaS)
As the cloud computing landscape evolves, Platform as a Service (PaaS) has emerged as a crucial offering for developers and businesses looking to streamline application development and deployment. In this comprehensive guide, we will explore what PaaS is, its key features, benefits, and how it can be effectively utilized.
If you want to advance your career at the Cloud Computing Course in Coimbatore, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is PaaS?
Platform as a Service (PaaS) is a cloud computing model that provides a platform allowing developers to build, deploy, and manage applications without the intricacies of managing the underlying infrastructure. This model simplifies the development process by providing a ready-to-use environment that includes hardware, software, and tools.
Benefits of PaaS
1. Faster Development Cycles
PaaS accelerates the application development process by providing pre-configured environments and tools. Developers can quickly prototype, test, and deploy applications, reducing time to market.
2. Cost-Effective Solutions
With a pay-as-you-go pricing model, PaaS allows organizations to pay only for the resources they consume. This can lead to significant cost savings compared to traditional on-premises solutions.
3. Enhanced Collaboration
PaaS promotes collaboration among development teams, as cloud-based tools enable real-time communication and project management, regardless of team members’ locations.
4. Focus on Innovation
By minimizing the need to manage infrastructure, PaaS allows developers to focus on innovation and creating new features, driving business growth.
5. Built-In Security and Compliance
Many PaaS providers offer robust security features and comply with industry standards, helping businesses protect their applications and data.

For those looking to excel in Cloud computing, Cloud Computing Online Course is highly suggested. Look for classes that align with your preferred programming language and learning approach.
Key Features of PaaS
Development Frameworks: PaaS solutions often come with built-in development frameworks that support various programming languages, making it easier for developers to create applications.
Middleware: PaaS includes middleware services that facilitate communication between applications and databases, helping to connect different software components seamlessly.
Database Management: Most PaaS offerings provide integrated database management systems, allowing developers to create and manage databases without deep database administration knowledge.
Scalability Options: PaaS platforms are designed to easily scale applications up or down based on demand, ensuring efficient resource utilization.
Collaboration Tools: Many PaaS providers offer features that support teamwork, enabling multiple developers to work on the same project from different locations.
Choosing the Right PaaS Provider
When selecting a PaaS provider, consider the following factors:
Supported Technologies: Ensure the platform supports the programming languages and frameworks you intend to use.
Scalability: Look for a provider that offers flexible scaling options to accommodate your application's growth.
Security Features: Evaluate the security measures in place, including data encryption and compliance with regulations.
Cost Structure: Understand the pricing model to ensure it aligns with your budget and usage expectations.
Support and Documentation: A strong support system and comprehensive documentation can significantly enhance your experience.
Conclusion
As businesses continue to embrace digital transformation, understanding the capabilities and benefits of PaaS will be essential for staying competitive. Whether you’re a startup looking to build your first app or an established enterprise seeking to modernize your development processes, PaaS offers the tools and flexibility needed to succeed in today’s fast-paced digital landscape.
0 notes
Text
Guide to Mastering Ethical Hacking Skills
In an era where cyber threats are rampant, ethical hacking has become an indispensable part of cybersecurity. This blog serves as a comprehensive guide to mastering the essential skills required to become a proficient ethical hacker. Whether you’re a beginner or looking to sharpen your skills, this roadmap will help you navigate your journey.
For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the Best Ethical Hacking Course in Pune becomes a strategic imperative. Let’s embark on an exploration into the transformative realm of hacking.

1. Understand the Fundamentals of Cybersecurity
Before diving into ethical hacking, it’s crucial to have a strong grasp of cybersecurity fundamentals. Here’s what you should focus on:
Basic Concepts: Learn about confidentiality, integrity, and availability (CIA triad).
Network Security: Understand firewalls, VPNs, and intrusion detection systems.
Operating Systems: Familiarize yourself with both Windows and Linux environments, as they are commonly used in hacking.
Recommended Resources:
Books: "Cybersecurity Essentials" by Charles J. Brooks.
Online Courses: Look for introductory courses on platforms like Coursera and edX.
2. Learn Networking and Protocols
A solid understanding of networking is essential for ethical hacking. Key areas to study include:
TCP/IP Model: Understand how data is transmitted over networks.
Common Protocols: Get to know HTTP, HTTPS, FTP, and DNS.
Network Devices: Learn about routers, switches, and how they function.
Recommended Resources:
Books: "Networking All-in-One For Dummies" by Doug Lowe.
Online Labs: Try interactive labs on Cisco Networking Academy.
3. Master Programming and Scripting
Programming skills are vital for automating tasks and understanding vulnerabilities. Focus on the following languages:
Python: Widely used in scripting and automation.
JavaScript: Important for web application security.
Bash/Shell Scripting: Useful for automating tasks in a Linux environment.
Recommended Resources:
Interactive Platforms: Codecademy and freeCodeCamp for hands-on programming.
Books: "Learn Python the Hard Way" for a comprehensive introduction.
4. Get Acquainted with Hacking Tools
There are numerous tools that ethical hackers use to assess and exploit vulnerabilities. Familiarize yourself with:
Nmap: For network scanning and enumeration.
Wireshark: A tool for analyzing network traffic.
Metasploit: A framework for penetration testing.
Burp Suite: Essential for web application testing.
Recommended Resources:
Official Documentation: Explore the manuals and user guides for each tool.
Hands-On Labs: Use platforms like Hack The Box and TryHackMe to practice.

For those looking to excel in Ethical hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred programming language and learning approach.
5. Obtain Relevant Certifications
Certifications can significantly enhance your credibility in the field. Consider the following:
CompTIA Security+: A foundational certification for cybersecurity professionals.
Certified Ethical Hacker (CEH): Focuses on the tools and techniques of ethical hacking.
Offensive Security Certified Professional (OSCP): A hands-on certification that emphasizes real-world penetration testing skills.
Recommended Resources:
Certification Websites: Visit the official sites for study materials and exam details.
Study Groups: Join online forums or local meetups to collaborate with others.
6. Gain Practical Experience
Hands-on experience is invaluable in ethical hacking. Here are some ways to build your practical skills:
Capture The Flag (CTF) Competitions: Participate in CTF challenges to practice your skills in a competitive environment.
Internships: Seek internships at cybersecurity firms or IT departments to gain real-world experience.
Home Labs: Create your own lab environment using virtual machines to simulate attacks and defenses safely.
7. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly changing, so staying informed is crucial. Here’s how to keep up:
Follow Industry News: Subscribe to cybersecurity blogs and websites like Krebs on Security and Threatpost.
Join Online Communities: Engage in forums such as Reddit or specialized cybersecurity groups.
Attend Conferences: Participate in events like DEF CON and Black Hat to network and learn about the latest trends.
8. Develop Soft Skills
In addition to technical proficiency, soft skills play a vital role in your success as an ethical hacker:
Problem Solving: Cultivate critical thinking and analytical skills.
Communication: Learn to explain technical concepts clearly to both technical and non-technical audiences.
Team Collaboration: Work effectively with other professionals in multidisciplinary teams.
Conclusion
Mastering ethical hacking skills is a rewarding journey that requires dedication, continuous learning, and practical application. By following this guide, you’ll be well-equipped to navigate the complexities of ethical hacking and contribute to a safer digital world. Start honing your skills today, and take your first step toward becoming an ethical hacking expert!
1 note
·
View note
Text
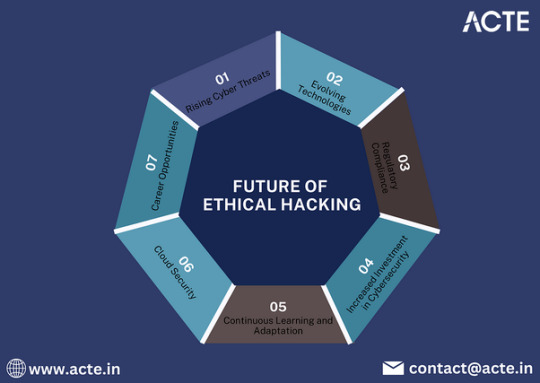
Why Ethical Hacking is Essential for Tomorrow's Cybersecurity
As we advance further into the digital age, the landscape of cybersecurity is evolving at an unprecedented pace. Organizations are increasingly exposed to a variety of cyber threats, making the role of ethical hacking more critical than ever. Here’s why ethical hacking is not just beneficial but essential for the future of cybersecurity.
For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the Best Ethical Hacking Course in Pune becomes a strategic imperative. Let’s embark on an exploration into the transformative realm of hacking.

1. Proactive Defense Against Cyber Threats
In a world where cyberattacks are becoming more sophisticated and frequent, a proactive approach to security is essential. Ethical hackers simulate attacks to identify vulnerabilities before malicious hackers can exploit them. This proactive stance helps organizations strengthen their defenses and mitigate risks effectively.
2. Evolving Threat Landscape
With the rapid development of technology, the threat landscape is constantly changing. New vulnerabilities emerge with each innovation, whether it’s cloud computing, IoT devices, or AI systems. Ethical hackers are crucial in understanding these threats and adapting security measures accordingly, ensuring that organizations remain one step ahead of cybercriminals.
3. Regulatory Compliance and Risk Management
As governments and regulatory bodies impose stricter data protection laws, compliance has become a significant concern for businesses. Ethical hackers help organizations meet these regulatory requirements by conducting audits, penetration tests, and risk assessments. This not only protects sensitive data but also avoids hefty fines associated with non-compliance.
4. Building a Security Culture
Embedding a culture of security within an organization is vital for long-term success. Ethical hackers contribute to this culture by educating employees about potential threats, safe practices, and the importance of cybersecurity. This awareness can significantly reduce the risk of human error, which is often the weakest link in cybersecurity.
For those looking to excel in Ethical hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred programming language and learning approach.
5. Cost-Effective Security Solutions
Investing in ethical hacking can be a cost-effective strategy for organizations. By identifying vulnerabilities before they are exploited, businesses can avoid costly data breaches, legal issues, and reputational damage. The return on investment from ethical hacking is substantial, making it a wise financial decision for organizations of all sizes.
6. Enhancing Incident Response
In the event of a cyber incident, having ethical hackers on board can enhance an organization’s incident response capabilities. Their expertise allows for quicker identification of the breach's nature and scope, leading to more effective containment and remediation strategies. This agility is crucial in minimizing damage and restoring operations swiftly.
7. Advancements in Cybersecurity Technologies
As cybersecurity technologies evolve, so do the techniques used by ethical hackers. From automated penetration testing tools to advanced threat intelligence platforms, ethical hackers leverage the latest technologies to enhance security measures. Their ability to adapt to new tools and methodologies ensures that organizations are utilizing the best practices available.
8. Career Opportunities and Skill Development
The rise of ethical hacking has created a wealth of career opportunities in the cybersecurity field. As demand for skilled professionals continues to grow, individuals pursuing careers in ethical hacking can expect a rewarding and impactful profession. Continuous education and skill development in this area are essential, fostering a new generation of cybersecurity experts.
Conclusion
The future of cybersecurity hinges on the effectiveness of ethical hacking. As cyber threats continue to evolve, organizations must adopt proactive strategies to safeguard their assets. Ethical hackers play a pivotal role in this endeavor, helping to identify vulnerabilities, ensure compliance, and foster a culture of security.
By embracing ethical hacking as an integral part of their cybersecurity strategy, organizations can better prepare themselves for the challenges of tomorrow’s digital landscape.
0 notes
Text
Exploring the World of Ethical Hacking
As our reliance on technology grows, so does the complexity of cyber threats. In this landscape, ethical hacking has emerged as a vital practice in safeguarding digital assets. If you're curious about ethical hacking and its role in cybersecurity, this blog will guide you through its fundamental aspects, significance, and how to get involved.
For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the Best Ethical Hacking Course in Pune becomes a strategic imperative. Let’s embark on an exploration into the transformative realm of hacking.

What is Ethical Hacking?
Ethical hacking involves the authorized testing of computer systems, networks, and applications to identify vulnerabilities that could be exploited by malicious hackers. Unlike black-hat hackers, who operate outside the law, ethical hackers—or "white-hat hackers"—work with permission to enhance security. Their primary goal is to protect sensitive data and ensure robust cybersecurity measures are in place.
The Importance of Ethical Hacking
Preventing Cybercrime: Ethical hacking is a proactive approach to identifying and fixing vulnerabilities, helping organizations prevent data breaches and cyberattacks.
Regulatory Compliance: Many industries are required to follow strict regulations regarding data protection. Ethical hackers assist in ensuring compliance with these standards.
Risk Management: By understanding potential threats, organizations can better manage their risks and implement effective security strategies.
Cultivating Trust: Companies that prioritize ethical hacking demonstrate their commitment to cybersecurity, thus building trust with customers and stakeholders.
The Ethical Hacking Process
The process of ethical hacking typically follows a systematic approach, which includes:
Planning: Establishing the scope and objectives of the test, including which systems will be examined.
Reconnaissance: Gathering information about the target system to identify potential vulnerabilities.
Scanning: Using tools to identify open ports, services, and security weaknesses.
Gaining Access: Attempting to exploit identified vulnerabilities to assess how deep an attacker could penetrate the system.
Maintaining Access: Checking if the vulnerabilities allow for ongoing access to the system.
Analysis and Reporting: Documenting findings and providing actionable recommendations for remediation.

For those looking to excel in Ethical hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred programming language and learning approach.
Tools of the Trade
Ethical hackers utilize a variety of tools to carry out their assessments. Some essential tools include:
Nmap: A network scanning tool that helps identify active devices and services on a network.
Metasploit: A powerful framework for developing and executing exploit code against a target.
Wireshark: A network protocol analyzer that captures and analyzes data packets flowing through the network.
Burp Suite: A comprehensive tool for testing the security of web applications.
How to Get Involved in Ethical Hacking
If you're interested in pursuing a career in ethical hacking, here are some steps to consider:
Educational Foundation: A degree in computer science, information technology, or cybersecurity is beneficial.
Certifications: Earning certifications such as Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP) can enhance your qualifications and skills.
Hands-on Experience: Gain practical experience through internships, participating in Capture The Flag (CTF) competitions, or contributing to open-source projects.
Stay Informed: The cybersecurity landscape is always evolving. Engage in continuous learning through online courses, webinars, and industry conferences.
Conclusion
As you explore this field, remember that ethical hacking requires a commitment to continuous learning and ethical responsibility. By equipping yourself with the right knowledge and skills, you can contribute to a safer digital landscape for everyone. Whether you're an aspiring ethical hacker or a business leader looking to improve your organization's security posture, understanding ethical hacking is a crucial step in navigating our increasingly interconnected world.
0 notes
Text
Exploring AWS Lambda: The Future of Server less Computing
As technology continues to evolve, so does the way we build and deploy applications. Among the transformative advancements in cloud computing, AWS Lambda emerges as a leading force in the realm of serverless architecture. This innovative service from Amazon Web Services (AWS) enables developers to run code without the complexities of managing servers, paving the way for greater efficiency and scalability.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is AWS Lambda?
AWS Lambda is a serverless compute service that allows you to execute code in response to specific events, such as changes in data, user requests, or system states. With Lambda, you can trigger functions from various AWS services like S3, DynamoDB, Kinesis, and API Gateway, allowing you to construct dynamic, event-driven applications effortlessly.
Key Features of AWS Lambda
Event-Driven Execution: AWS Lambda automatically responds to events, executing your code when specified triggers occur. This means you can concentrate on developing your application logic rather than managing infrastructure.
Automatic Scalability: As demand fluctuates, AWS Lambda scales your application automatically. Whether handling a single request or thousands, Lambda adjusts seamlessly to meet your needs.
Cost Efficiency: With a pay-as-you-go pricing model, you only pay for the compute time you consume. This means no charges when your code isn’t running, making it a cost-effective choice for many applications.
Multi-Language Support: AWS Lambda supports several programming languages, including Node.js, Python, Java, C#, and Go, giving developers the flexibility to work in their preferred languages.
Integration with AWS Services: Lambda works harmoniously with other AWS services, enabling you to build intricate applications effortlessly and take advantage of the broader AWS ecosystem.

To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Exciting Use Cases for AWS Lambda
Real-Time Data Processing: Use Lambda to process data streams in real-time, such as transforming and analyzing data as it flows through services like Kinesis or responding to file uploads in S3.
API Development: Combine AWS Lambda with API Gateway to create robust RESTful APIs, allowing you to manage HTTP requests without the overhead of server management.
Automation of Tasks: Automate routine tasks, such as backups, monitoring, and notifications, facilitating smoother operations and reducing manual effort.
Microservices Architecture: Build applications using microservices, where individual Lambda functions handle specific tasks, enhancing modularity and maintainability.
Getting Started with AWS Lambda
Ready to dive into AWS Lambda? Here’s how you can get started:
Create an AWS Account: Sign up for an AWS account if you don’t already have one.
Access the AWS Management Console: Navigate to the Lambda service within the console.
Create a Lambda Function: Select a runtime, write your code (or upload a zip file), and configure your function settings.
Set Up Event Triggers: Configure triggers from other AWS services to execute your Lambda function based on specific events.
Testing and Monitoring: Utilize AWS CloudWatch to monitor performance, logs, and errors, helping you optimize your function.
Conclusion
AWS Lambda represents a paradigm shift in how applications are built and deployed. By embracing serverless architecture, developers can focus on writing code and delivering features without the burden of managing infrastructure. Whether you’re crafting a small application or a large-scale service, AWS Lambda provides the flexibility and scalability necessary to thrive in the modern cloud landscape.
0 notes
Text
Leveraging AWS Cloud in the Automotive Industry
The automotive industry is rapidly evolving, driven by technological advancements and changing consumer expectations. One of the most significant enablers of this transformation is cloud computing, particularly Amazon Web Services (AWS). By providing scalable, flexible, and secure cloud solutions, AWS is helping automotive companies innovate and enhance their operations.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

1. Connected Vehicle Solutions
Connected vehicles generate massive amounts of data from sensors, GPS, and infotainment systems. AWS offers services that allow automotive companies to process and analyze this data in real time. With AWS IoT Core, manufacturers can securely connect vehicles to the cloud, enabling data collection and communication between vehicles and cloud applications. This connectivity enhances vehicle performance, safety, and the overall driving experience.
2. Over-the-Air (OTA) Updates
AWS provides the infrastructure necessary for seamless over-the-air software updates. Automotive manufacturers can use AWS services like AWS Lambda and Amazon S3 to deliver updates directly to vehicles, ensuring that they have the latest features and security patches. This not only improves vehicle functionality but also reduces the need for customers to visit dealerships for routine updates.
3. Data Analytics and Machine Learning
The cloud’s analytics capabilities are crucial for the automotive industry. AWS offers a suite of analytics tools, such as Amazon Kinesis and Amazon Redshift, that enable manufacturers to analyze vast datasets for insights into vehicle performance and customer behavior. Additionally, AWS’s machine learning services, including Amazon SageMaker, allow companies to build predictive models for maintenance, helping to identify potential issues before they escalate.
4. Autonomous Driving Technologies
AWS plays a vital role in the development of autonomous vehicles. The cloud provides the computational power necessary to process data from numerous sensors and cameras. With AWS, automotive developers can leverage high-performance computing resources to train machine learning models for perception, decision-making, and navigation in real time. This capability is essential for creating safe and reliable autonomous driving systems.

To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
5. Supply Chain Management
Managing a complex supply chain is critical for automotive manufacturers. AWS helps streamline supply chain operations through its robust data storage and processing capabilities. By utilizing services like Amazon S3 for storage and AWS Glue for data integration, companies can gain better visibility into their supply chains, optimize inventory, and improve logistics. This leads to reduced costs and enhanced efficiency.
6. Enhanced Customer Experience
Using AWS, automotive companies can create personalized experiences for their customers. By analyzing data from connected vehicles and customer interactions, manufacturers can offer tailored services, such as customized maintenance alerts or personalized infotainment options. AWS’s customer engagement services, like Amazon Pinpoint, enable companies to communicate effectively with their customers, enhancing satisfaction and loyalty.
7. Mobility Solutions and Smart Cities
As urban mobility evolves, AWS supports the development of Mobility as a Service (MaaS) applications. By harnessing AWS’s scalable infrastructure, automotive companies can integrate various transportation modes into a single platform, allowing users to plan their journeys efficiently. Additionally, AWS can facilitate smart city initiatives by providing the necessary data and analytics to optimize traffic flow and transportation services.
Conclusion
The automotive industry is on the brink of a major transformation, and AWS is at the forefront of this revolution. By leveraging AWS cloud services, automotive manufacturers can enhance connectivity, improve vehicle performance, streamline operations, and create a better customer experience.
As the industry continues to evolve, AWS will play a crucial role in shaping the future of mobility, making it safer, smarter, and more efficient. Embracing AWS cloud solutions is not just a competitive advantage; it’s a strategic necessity for automotive companies looking to thrive in today’s dynamic landscape.
0 notes
Text
AWS IoT Core: Unlocking the Potential of the Internet of Things
The Internet of Things (IoT) is reshaping industries and transforming everyday life by connecting devices and enabling smart interactions. At the forefront of this revolution is AWS IoT Core, a powerful platform from Amazon Web Services that provides the infrastructure needed to build and manage IoT applications at scale. In this blog post, we’ll explore how AWS IoT Core unlocks the potential of IoT and what it means for businesses and developers alike.

If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.
What is AWS IoT Core?
AWS IoT Core is a fully managed cloud service that allows you to connect, manage, and secure IoT devices. It supports various communication protocols, making it easier for devices to interact with the cloud and each other. From simple sensors to complex industrial machinery, AWS IoT Core provides the tools necessary for seamless device integration.
Key Features of AWS IoT Core
Seamless Device Connectivity: AWS IoT Core supports multiple protocols, including MQTT, HTTP, and WebSockets, ensuring that devices can connect and communicate easily.
Robust Security: Security is a top priority in IoT. AWS IoT Core offers features like mutual authentication, encryption, and fine-grained access control, ensuring that your devices and data remain secure.
Efficient Device Management: Managing numerous devices can be daunting. AWS IoT Core simplifies this process with tools for device registration, monitoring, and management, allowing for efficient oversight.
Real-Time Data Processing: The service integrates seamlessly with other AWS offerings, such as AWS Lambda and Amazon Kinesis, enabling real-time data analytics and processing.
Powerful Rules Engine: The built-in rules engine lets you define actions based on incoming messages, such as triggering alerts, invoking AWS services, or storing data for future use.
Integration with Machine Learning: AWS IoT Core connects with AWS's machine learning services, providing the ability to develop intelligent applications that learn from IoT data.

To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Use Cases for AWS IoT Core
AWS IoT Core is versatile and applicable across numerous industries:
Smart Homes: Automate and monitor home devices for enhanced comfort and energy savings.
Industrial Automation: Monitor equipment health and optimize manufacturing processes through predictive maintenance.
Healthcare: Enable remote patient monitoring and data collection, improving health outcomes and operational efficiency.
Agriculture: Use sensors to monitor crop and soil conditions, promoting sustainable farming practices.
Getting Started with AWS IoT Core
To harness the power of AWS IoT Core, follow these steps:
Sign Up for AWS: If you don’t have an account, create one on the AWS website.
Set Up AWS IoT Core: Access the AWS Management Console and create an IoT Core resource.
Register Your Devices: Connect your devices securely to the AWS IoT Core.
Develop Applications: Use the data from your devices to build innovative applications that meet your needs.
Conclusion
AWS IoT Core is a game-changer in the world of IoT, providing the essential tools and infrastructure for developers and businesses to unlock the full potential of connected devices. With its robust features, security protocols, and seamless integration with AWS services, it empowers organizations to innovate and create smarter solutions across various sectors.
As the IoT landscape continues to expand, understanding and utilizing AWS IoT Core will be crucial for anyone looking to stay ahead in this exciting field. Embrace the power of AWS IoT Core and discover how it can transform your approach to the Internet of Things!
0 notes