#AI Firewall & Instant Protection
Explore tagged Tumblr posts
Text
Complete Website Security & Monitoring Real-Time Malware Detection.
Complete Website Security & Monitoring
Real-Time Malware Detection (🛡️ Instantly detect hidden threats before they break your site) Continuously scans websites for malware, redirect scripts, phishing links, and backdoors.
Scheduled Security Audits (📅 Keep your clients protected 24/7) Set automated scans to run daily, weekly, or monthly.
Branded Audit Reports (📄 Impress clients with professional security reports) Generate white-labeled vulnerability reports that close deals.
🛡️ AI Firewall & Instant Protection
Smart AI Firewall (🧠 Let AI block attacks before they reach your site) Prevents SQL injections, spam queries, brute-force logins, and more.
Zero-Day Defense (🚫 Stay ahead of new and evolving threats) Detects behavior-based risks even before they’re listed in vulnerability databases.
Bot, Spam & DDoS Defense (🤖 Block junk traffic with a click) Filters out spam bots, fake users, and DDOS hits.
See more ditails now>>
DFY Client Attraction Tools
Built-In Client Finder (🔍 Find vulnerable websites to pitch) Filter by niche, CMS, or location and get their details.
Self-Audit Widget (📥 Let visitors scan their own site on your page) Converts them into leads automatically.
Done-for-You Cold Emails (✉️ Start conversations that convert) Use plug-and-play templates to sell without writing.
Full Agency Setup Done For You
DFY Agency Website (💻 Your own branded platform) Includes service pages, branding, and funnels.
Client Portal Access (🧾 Let them log in and view their audits) Increases retention and authority.
Resell Rights + White Label (💸 You own the product and the profits) No hidden licenses or restrictions.

#Complete Website Security & Monitoring#Real-Time Malware Detection#AI Firewall & Instant Protection#White-Labeled WordPress Plugin#Client Attraction Tools#DFY#Full Agency Setup Done For You#CompleteWebsiteSecurity#CyberSecurity#MalwareProtection#WebsiteSafety#OnlineSecurity#CyberSecurityTips#WebSecurity#ProtectYourWebsite#DigitalSafety#DataProtection#SafeBrowsing
0 notes
Text
What Modern Ways to Domain Registration and Web Hosting
Understanding the Evolution of Domain Registration
Domain registration has become far more streamlined and accessible than ever before. Traditionally, buying a domain involved working through limited registrars and a complex, slow process. Today, you can register a domain in minutes with global providers like GoDaddy, Namecheap, or Google Domains. Modern platforms offer intuitive interfaces, advanced DNS controls, bulk domain management, and renewal alerts. Many even offer privacy protection and SSL certificates bundled into domain packages. Thanks to automation, users now receive instant domain activation, making it easier for businesses, bloggers, and developers to launch their online presence without delays or technical hurdles.
Choosing the Right Domain Name in a Competitive Market
Selecting a modern domain name goes beyond choosing a ".com." Today’s digital landscape includes a wide range of extensions like ".tech", ".store", ".online", and country-specific TLDs such as ".us" or ".in". These extensions offer greater flexibility and creativity, allowing businesses to stand out. Modern tools like domain name generators use AI to suggest brandable, available domain names. Additionally, many registrars offer domain monitoring, which alerts users when their desired domain becomes available. Prioritizing a short, relevant, and memorable domain—while securing multiple extensions—can enhance branding and protect your online identity from competitors or imitators.
The Rise of Integrated Web Hosting Solutions
Web hosting has drastically evolved from basic shared servers to highly sophisticated cloud-based infrastructures. Today, most users opt for hosting platforms that bundle multiple services—domain registration, website builders, security features, and technical support—into one seamless experience. Popular providers like Bluehost, SiteGround, and Odyssey Design Hosting offer modern hosting environments with tools like one-click WordPress installs, automated backups, SSD storage, and scalable bandwidth. These integrated platforms simplify website setup and management, even for beginners. Choosing a host with a modern dashboard and 24/7 support can help users focus more on content creation and marketing than on technical challenges.
Exploring the Benefits of Cloud Hosting and VPS
Traditional shared hosting still works for many websites, but more professionals and businesses are shifting to Virtual Private Servers (VPS) and cloud hosting. These modern hosting methods offer better performance, security, and scalability. Cloud hosting, powered by services like AWS, Google Cloud, or DigitalOcean, allows websites to run across multiple servers—ensuring uptime and fast speeds even during traffic spikes. VPS hosting gives users dedicated resources on a shared server, allowing more control without the cost of a full dedicated server. Both options are ideal for businesses planning growth, e-commerce websites, or those requiring advanced customization and reliability.
Modern Security Features for Domains and Hosting
Security has become a core part of both domain registration and web hosting. Modern registrars now offer domain privacy protection to hide personal details from public WHOIS databases, helping prevent spam and identity theft. On the hosting side, SSL certificates are often included free to ensure safe, encrypted connections. Reputable hosts also provide firewall protection, malware scanning, daily backups, and DDoS protection. Two-factor authentication (2FA) is now common for both domain and hosting account access. These layered security features reduce the risk of cyberattacks and data loss, offering peace of mind to website owners and users alike.
Automating Domain and Hosting Management
Thanks to automation and advanced dashboards, managing your domain and hosting no longer requires technical expertise. Modern control panels like cPanel, Plesk, and custom dashboards let users handle DNS changes, email setup, database management, and backups easily. Hosting companies now automate many tasks like renewals, SSL installation, and performance optimization. Users can set up auto-renewals for domains to avoid expiration issues. Additionally, monitoring tools and analytics help users track site uptime, visitor behavior, and security incidents in real-time. These features save time, reduce errors, and make online business management far more efficient than in the past.
Future Trends in Domain Registration and Hosting
As digital technology continues to advance, domain and hosting services are becoming smarter, faster, and more user-friendly. AI is now helping suggest optimal domains based on brand intent, while blockchain-based domain systems are emerging for decentralized ownership. Hosting providers are adopting eco-friendly infrastructure and edge computing to reduce latency and support global audiences. In the near future, more platforms will offer voice-command dashboards, predictive analytics, and autonomous site optimization. Staying informed and embracing these modern trends can give businesses and creators a significant edge in an increasingly competitive online space.
Conclusion Modern domain registration and web hosting have transformed into streamlined, user-friendly services packed with features designed for efficiency, security, and scalability. Whether you're launching a personal blog or a professional business website, understanding these new methods ensures a smoother setup and better long-term success. By choosing smartly and staying updated with current trends, you can establish a solid online presence that grows with your brand.
0 notes
Text
How Is Cloud Computing Transforming Fintech Infrastructure?

Cloud computing has become one of the most significant drivers of digital transformation across industries, and the financial sector is no exception. By offering scalable, cost-effective, and secure computing resources, cloud technology is reshaping how financial institutions and fintech companies build and manage their infrastructure. With the rise of fintech new technologies, cloud computing plays a crucial role in delivering advanced solutions and improving the efficiency of Fintech software.
The Shift Toward Cloud in Fintech
Traditionally, financial institutions relied on on-premise infrastructure that was costly to maintain and lacked flexibility. The need for faster innovation, better scalability, and real-time processing has driven fintech companies to adopt cloud-based solutions. Cloud computing enables businesses to access vast computing power and storage without heavy investments in physical hardware.
Fintech companies can now launch new services quickly, test innovative solutions, and scale their operations as demand grows. This agility is essential in a competitive market where customer expectations are constantly evolving. With cloud infrastructure, companies can adapt quickly to regulatory changes, market trends, and technological advancements.
Enhancing Fintech Infrastructure with Cloud Solutions
Cloud computing provides a robust foundation for building and deploying Fintech software. It enables seamless integration with various financial systems, APIs, and third-party services. This makes it easier for companies to deliver innovative offerings like digital banking, instant payments, and AI-powered financial advisory tools.
Cloud platforms support microservices architecture, allowing fintech companies to build modular applications that can be updated or scaled independently. This leads to faster deployment cycles, reduced downtime, and improved reliability. For example, payment platforms can handle sudden surges in transactions during peak periods without compromising performance.
Cost Efficiency and Scalability
One of the primary advantages of cloud computing is cost efficiency. Instead of investing in expensive hardware and data centers, fintech companies can pay only for the resources they use. This is especially beneficial for startups that need to optimize costs while developing high-quality products.
Scalability is another key factor. As fintech businesses grow, cloud infrastructure allows them to scale up or down instantly. Whether a company is handling a small customer base or millions of users worldwide, cloud platforms ensure smooth operations without performance issues.
Driving Innovation with Fintech New Technologies
Cloud computing is at the heart of many fintech new technologies, including artificial intelligence, machine learning, blockchain, and big data analytics. These technologies require significant processing power and storage, which cloud platforms can provide on demand.
For example, AI-driven fraud detection systems can analyze large datasets in real time to identify suspicious activities. Similarly, blockchain-based solutions for payments and digital identity verification rely on cloud infrastructure for seamless global operations. The flexibility of the cloud makes it easier for companies to experiment with and deploy these advanced technologies.
Enhancing Security and Compliance
Security is a top priority in the financial industry. Cloud service providers invest heavily in advanced security measures, including encryption, firewalls, and multi-factor authentication. They also comply with global regulatory standards, helping fintech companies meet requirements such as GDPR, PCI DSS, and other data protection regulations.
Cloud platforms also support disaster recovery and backup solutions, ensuring business continuity in case of system failures. This is particularly important for financial services, where downtime can lead to significant losses and reputational damage.
Improving Collaboration and Accessibility
With cloud computing, fintech teams can collaborate from anywhere in the world. Developers, analysts, and financial experts can access shared platforms and tools in real time, improving efficiency and innovation. Cloud-based solutions also enhance accessibility for end-users, who can access financial services from multiple devices, including smartphones and tablets.
This level of accessibility is essential in today’s digital-first world, where customers expect instant and seamless access to financial services.
The Future of Cloud-Powered Fintech
As cloud technology continues to evolve, it will enable even more advanced capabilities, including serverless computing and edge computing for real-time financial processing. Companies like Xettle Technologies are leveraging cloud platforms to deliver cutting-edge fintech solutions that are secure, scalable, and efficient.
With the growing adoption of fintech new technologies, cloud computing will remain a fundamental enabler of innovation in the financial sector. It not only supports the development of modern Fintech software but also ensures that services are delivered faster, safer, and more cost-effectively.
Conclusion
Cloud computing is transforming fintech infrastructure by providing scalability, cost efficiency, and advanced capabilities for innovation. It enables seamless integration of new technologies, enhances security, and supports global accessibility. As more companies adopt cloud-based solutions, the future of fintech will become increasingly agile, customer-centric, and technologically advanced.
0 notes
Text
The Ultimate Guide to Dedicated Hosting: Power, Performance, and Control
In the world of web hosting, dedicated hosting stands out as the most powerful and reliable solution for businesses and high-traffic websites. Unlike shared or VPS hosting, a dedicated server provides exclusive access to all resources, ensuring maximum performance, security, and customization.
At CloudMinister, we offer premium dedicated hosting solutions designed to meet the demands of enterprises, large-scale applications, and resource-intensive websites.
What is Dedicated Hosting?
A dedicated server is a physical server entirely allocated to a single user or organization. Unlike shared or VPS hosting, you don’t share CPU, RAM, bandwidth, or storage with anyone else. This makes it ideal for:
High-traffic websites (e-commerce, news portals) Enterprise applications (ERP, CRM, databases) Gaming servers (low-latency multiplayer hosting) Streaming platforms (video/audio content delivery) Big data & AI processing (machine learning workloads)
Key Benefits of Dedicated Hosting
Unmatched Performance – Full server resources with no sharing. Enhanced Security – Isolated environment with custom firewalls. Complete Control – Full root access & custom configurations. High Reliability – 99.9% uptime for mission-critical applications. Custom Hardware Options – Choose your preferred CPU, RAM, and storage.
Why Choose CloudMinister for Dedicated Hosting?
At CloudMinister, we provide enterprise-grade dedicated servers with:
🔹 High-End Hardware – Latest Intel Xeon & AMD EPYC processors. 🔹 SSD/NVMe Storage – Ultra-fast data access and load times. 🔹 24/7 Expert Support – Proactive monitoring & instant assistance. 🔹 DDoS Protection – Advanced security to prevent cyber threats. 🔹 Flexible Scaling – Easily upgrade RAM, storage, or bandwidth.
Managed vs. Unmanaged Dedicated Hosting
Managed Dedicated Hosting – CloudMinister handles server setup, security, updates, and backups.
Unmanaged Dedicated Hosting – Full admin control for experienced users.
Who Needs Dedicated Hosting?
E-Commerce Giants – Handle thousands of transactions securely. SaaS Providers – Ensure smooth performance for users. Game Developers – Run lag-free multiplayer servers. Media & Streaming Platforms – Deliver HD content without buffering. Financial & Healthcare Sectors – Meet strict compliance requirements.
Get Your Dedicated Server with CloudMinister Today!
If you need raw power, security, and reliability, CloudMinister’s dedicated hosting is the perfect choice.
0 notes
Text
Ransomware Protection Services Every Business Needs
In today’s digital-first world, cyberattacks like ransomware have become increasingly sophisticated, leaving businesses vulnerable to costly data breaches and operational shutdowns. Ransomware encrypts your files and demands payment for their return—disrupting business, damaging reputations, and risking customer trust. That’s why investing in ransomware protection services is not optional but essential. These services combine advanced threat detection, data encryption, backup management, and security monitoring to offer an all-around shield against ransomware attacks. With the right strategy and tools in place, you can stay ahead of cybercriminals and keep your digital environment secure 24/7.
Ransomware Protection Services Safeguard Your Critical Data
Your data is one of your most valuable assets, and ransomware protection services are specifically designed to guard it. From customer records and financial files to intellectual property, modern protection tools use artificial intelligence and machine learning to detect and stop malicious activity before it can do harm. These services continuously monitor your systems, creating automated alerts and blocking suspicious actions in real time. With regular backups, quick isolation of infected endpoints, and proactive mitigation strategies, they make sure your data stays intact even during an attack. Investing in data security today can save millions in ransom payments and losses tomorrow.
Prevent Cyberattacks Before They Start
The best cybersecurity approach is a proactive one. Ransomware protection services help businesses stop attacks before they occur by monitoring vulnerabilities and implementing preventive measures like email filtering, firewall configurations, user training, and threat intelligence. These services often include behavior-based detection systems that identify unusual patterns in file access, login attempts, or data transfers. This early detection is crucial to stopping ransomware from gaining a foothold. By minimizing your attack surface and improving your digital hygiene, you ensure that ransomware doesn’t get the opportunity to lock you out of your systems or steal your data.
Keep Your Business Operations Uninterrupted
When ransomware hits, downtime is often the costliest consequence. Every minute your systems are locked can result in lost revenue, halted services, and customer dissatisfaction. Ransomware protection services help keep your operations running smoothly by isolating infected machines, switching to backup systems, and enabling instant recovery. These services ensure that critical processes like billing, communication, logistics, and customer service remain functional even under attack. With minimal disruption and swift containment, your business can maintain productivity and preserve trust with clients and partners—regardless of the threat level.
Detect Threats with Advanced Ransomware Protection Services
Traditional antivirus software alone isn’t enough. Advanced ransomware protection services rely on AI-driven behavior analytics, threat intelligence feeds, and automated detection algorithms to identify potential threats in real time. These systems flag suspicious activities like unauthorized file encryption, lateral movement within networks, and abnormal login patterns. This proactive approach not only detects existing threats but also predicts and prevents future ransomware strains. Many services integrate with SIEM platforms for centralized monitoring, giving your IT team complete visibility and control over your digital infrastructure.
Protect Sensitive Files with Real-Time Encryption
Real-time encryption is a key defense strategy against ransomware. While attackers try to encrypt your files to hold them hostage, ransomware protection services use encryption proactively to safeguard sensitive data. These solutions automatically encrypt files at rest and in transit, making them unreadable to unauthorized users—even if accessed during a breach. With multi-factor authentication and secure file access controls, your organization can ensure only approved personnel can view or share critical data. This layered defense makes your sensitive information virtually useless to cybercriminals.
Ensure Rapid Recovery After a Ransomware Incident
Despite your best efforts, ransomware attacks can still happen. That’s why ransomware protection services also focus on disaster recovery. These services enable rapid restoration of systems, data, and operations with minimal downtime. By maintaining secure backups and automated failover systems, businesses can restore full functionality without paying the ransom. Additionally, many services include incident response teams that guide you through the recovery process, ensuring regulatory compliance and minimizing reputational damage. A fast, structured recovery plan is your last line of defense—and often the most critical.
Stay Ahead of Hackers with Proactive Security Tools
Hackers are constantly evolving their tactics, which means your defenses must evolve too. Ransomware protection services provide proactive tools like threat hunting, vulnerability assessments, and automated patch management to stay ahead of attackers. These tools identify and eliminate weak points in your system before they’re exploited. Continuous updates, machine learning models, and access controls help build a dynamic defense ecosystem that adapts to new threats in real time. By staying one step ahead of cybercriminals, your business reduces its exposure and strengthens its overall cybersecurity posture.
Conclusion
Ransomware is one of the most damaging and costly cyber threats today—but with the right defenses, it's also one of the most preventable. Ransomware protection services offer comprehensive security that spans detection, prevention, encryption, and recovery. These tools not only shield your data but also ensure operational continuity, regulatory compliance, and peace of mind. Investing in robust protection means fewer risks, lower costs, and stronger business resilience. Don’t wait for a ransomware incident to disrupt your business—act now to secure your future with professional-grade cybersecurity.
0 notes
Text
Cloud VPS Server Hosting in 2025 The Ultimate Guide by SEOHostKing

What Is Cloud VPS Server Hosting in 2025? Cloud VPS server hosting in 2025 represents the perfect fusion between the flexibility of cloud computing and the dedicated power of a Virtual Private Server. It delivers enterprise-level infrastructure at affordable pricing, backed by scalable resources, high availability, and powerful isolation—ideal for startups, developers, agencies, eCommerce, and high-traffic websites. Why Cloud VPS Hosting Is Dominating in 2025 Unmatched Performance and Flexibility Traditional hosting is rapidly being replaced by cloud-powered VPS because it offers dynamic resource allocation, 99.99% uptime, lightning-fast SSD storage, and dedicated compute environments—all without the high costs of physical servers. Fully Scalable Infrastructure Cloud VPS adapts to your growth. Whether you're hosting one blog or managing a SaaS platform, you can scale CPU, RAM, bandwidth, and storage with zero downtime. Global Data Center Deployment In 2025, global presence is non-negotiable. Cloud VPS servers now operate in multiple zones, allowing users to deploy applications closest to their target audience for ultra-low latency. Built for High-Security Demands Modern Cloud VPS hosting comes with AI-based DDoS protection, automatic patching, firewalls, and end-to-end encryption to meet the increasing cyber threats of 2025. Benefits of Cloud VPS Hosting with SEOHostKing Ultra-Fast SSD NVMe Storage Enjoy 10x faster data access, low read/write latency, and superior performance for databases and dynamic websites. Dedicated IPv4/IPv6 Addresses Each VPS instance receives its own IPs for full control, SEO flexibility, and better email deliverability. Root Access and Full Control SEOHostKing offers root-level SSH access, so you can install any software, configure firewalls, or optimize the server at your will. Automated Daily Backups Your data is your business. Enjoy daily backups with one-click restoration to eliminate risks. 24/7 Expert Support Get support from VPS professionals with instant response, ticket escalation, and system monitoring—available around the clock. Use Cases for Cloud VPS Hosting in 2025 eCommerce Websites Run WooCommerce, Magento, or Shopify-like custom stores on isolated environments with strong uptime guarantees and transaction-speed optimization. SaaS Platforms Deploy microservices, API endpoints, or full-scale SaaS applications using scalable VPS nodes with Docker and Kubernetes-ready support. WordPress Hosting at Scale Run multiple WordPress sites, high-traffic blogs, and landing pages with isolated resources and one-click staging environments. Proxy Servers and VPNs Use VPS instances for private proxies, rotating proxy servers, or encrypted VPNs for privacy-conscious users. Game Server Hosting Host Minecraft, Rust, or custom gaming servers on high-CPU VPS plans with dedicated bandwidth and GPU-optimized add-ons. Forex Trading and Bots Deploy MT5, expert advisors, and trading bots on low-latency VPS nodes connected to Tier 1 financial hubs for instant execution. AI & Machine Learning Applications Run ML models, data training processes, and deep learning algorithms with GPU-ready VPS nodes and Python-friendly environments. How to Get Started with Cloud VPS Hosting on SEOHostKing Step 1: Choose Your Ideal VPS Plan Select from optimized VPS plans based on CPU cores, memory, bandwidth, and disk space. For developers, choose a minimal OS template. For businesses, go for cPanel or Plesk-based configurations. Step 2: Select Your Server Location Pick from global data centers such as the US, UK, Germany, Singapore, or the UAE for latency-focused deployment. Step 3: Configure Your OS and Add-ons Choose between Linux (Ubuntu, CentOS, AlmaLinux, Debian) or Windows Server (2019/2022) along with optional backups, cPanel, LiteSpeed, or GPU add-ons. Step 4: Launch Your VPS in Seconds Your VPS is auto-deployed in under 60 seconds with full root access and login credentials sent directly to your dashboard. Step 5: Optimize Your Cloud VPS Install web servers like Apache or Nginx, set up firewalls, enable fail2ban, configure caching, and use CDN integration for top-tier speed and security. Features That Make SEOHostKing Cloud VPS #1 in 2025
Self-Healing Hardware Intelligent hardware failure detection with real-time automatic migration of your VPS to healthy nodes with zero downtime. AI Resource Optimization Machine learning adjusts memory and CPU allocation based on predictive workload behavior, minimizing resource waste. Custom ISO Support Install your own operating systems, recovery environments, or penetration testing tools from uploaded ISO files. Integrated Firewall and Anti-Bot Protection Protect websites from automated bots, brute force attacks, and injections with built-in AI firewall logic. One-Click OS Reinstallation Reinstall your OS or template with a single click when you need a clean slate or configuration reset. Managed vs Unmanaged Cloud VPS Hosting Unmanaged VPS Hosting Ideal for developers, sysadmins, or users who need total control. You handle OS, updates, security patches, and application configuration. Managed VPS Hosting Perfect for businesses or beginners. SEOHostKing handles software installation, server updates, security hardening, and 24/7 monitoring. How to Secure Your Cloud VPS in 2025 Enable SSH Key Authentication Use SSH key pairs instead of passwords for better login security and brute-force protection. Keep Your Software Updated Apply security patches and system updates regularly to close vulnerabilities exploited by hackers. Use UFW or CSF Firewall Rules Limit open ports and restrict traffic to only necessary services, reducing attack surfaces. Monitor Logs and Alerts Use logwatch or fail2ban to track suspicious login attempts, port scanning, or abnormal resource usage. Use Backups and Snapshots Schedule automatic backups and use point-in-time snapshots before major upgrades or changes. Best Operating Systems for Cloud VPS in 2025 Ubuntu 24.04 LTS Perfect for developers and modern web applications with access to the latest packages. AlmaLinux 9 Stable, enterprise-grade CentOS alternative compatible with cPanel and other control panels. Debian 12 Rock-solid performance with minimal resource usage for minimalistic deployments. Windows Server 2022 Supports ASP.NET, MSSQL, and remote desktop applications for Windows-specific environments. Performance Benchmarks for Cloud VPS Hosting Website Load Time Under 1.2 seconds for optimized WordPress and Laravel websites with CDN and cache. Database Speed MySQL transactions complete 45% faster with SSD-NVMe storage on SEOHostKing Cloud VPS. Uptime and Availability 99.99% SLA-backed uptime with proactive failure detection and automatic failover systems. Latency & Response Time Average response times below 50ms when hosted in geo-targeted locations near the end user. How Cloud VPS Differs from Other Hosting Types Cloud VPS vs Shared Hosting VPS has dedicated resources and isolation while shared hosting shares CPU/memory with hundreds of users. Cloud VPS vs Dedicated Server VPS provides better flexibility, scalability, and cost-efficiency than traditional physical servers. Cloud VPS vs Cloud Hosting Cloud VPS offers more control and root access, while generic cloud hosting is often limited in configurability. Why SEOHostKing Cloud VPS Hosting Leads in 2025 Transparent Pricing No hidden costs or upsells—simple billing based on resources and usage. Developer-First Infrastructure With APIs, Git integration, staging environments, and CLI tools, it's built for real developers. Enterprise-Grade Network 10 Gbps connectivity, Tier 1 providers, and anti-DDoS systems built directly into the backbone. Green Energy Hosting All data centers are carbon-neutral, with renewable power and efficient cooling systems. Use Cloud VPS to Host Anything in 2025 Web Apps and Portfolios Host your resume, portfolios, client work, or personal websites with blazing-fast speeds. Corporate Intranet and File Servers Create secure internal company environments with Nextcloud, OnlyOffice, or SFTP setups. Dev/Test Environments Spin up a test environment instantly to stage deployments, run QA processes, or experiment with new stacks. Media Streaming Platforms Host video or audio streaming servers using Wowza, Icecast, or RTMP-ready software. Best Practices for Optimizing Cloud VPS Use a Content Delivery Network (CDN) Serve static content from edge locations worldwide to reduce bandwidth and load times. Install LiteSpeed or OpenLiteSpeed Boost performance for WordPress and PHP apps with HTTP/3 support and advanced caching. Use Object Caching (Redis/Memcached) Offload database queries for faster application processing and better scalability. Compress Images and Enable GZIP Save bandwidth and improve load times with server-side compression and caching headers.

Cloud VPS server hosting in 2025 is no longer a premium—it’s the new standard for performance, scalability, and control. With SEOHostKing leading the way, businesses and developers can deploy fast, secure, and reliable virtual servers with confidence. Whether you're launching a project, scaling an enterprise, or securing your digital presence, Cloud VPS with SEOHostKing is the ultimate hosting solution in 2025. Read the full article
0 notes
Text
Mastering Security Risk Detection and Data Breach Prevention with Advanced Darknet and Cloud Audits
In a digital world where data is currency, protecting it is no longer a luxury—it’s a necessity. Cyber threats are evolving rapidly, targeting not just enterprise networks but also cloud infrastructure, remote devices, and even the deep and dark web. Organizations must move beyond basic firewalls and antivirus programs to protect their assets with intelligent, proactive strategies.
That’s where risikomonitor.com GmbH comes in—empowering businesses with cutting-edge solutions for security risk detection, data breach prevention, darknet penetration testing, and cloud security audits. This blog explores how these critical components work together to protect digital ecosystems from both visible and hidden threats.
The Growing Importance of Security Risk Detection
Cybercriminals are no longer relying solely on brute-force tactics. Today’s threats are stealthy, well-funded, and often originate from within the organization. That makes real-time security risk detection absolutely essential.
At its core, security risk detection is the ability to recognize threats and anomalies as they arise. Whether it’s an unusual login attempt at 3 AM or a spike in outbound traffic to an unfamiliar IP, these red flags must be caught early to prevent damage.
risikomonitor.com GmbH offers AI-driven risk detection tools that monitor:
User behavior and access patterns
Device and endpoint activity
System vulnerabilities and exposures
Real-time threat intelligence feeds
These tools deliver instant alerts, prioritizing high-risk activities so your team can take swift action. With automated analysis and risk scoring, you're no longer playing catch-up—you're staying a step ahead.
Data Breach Prevention: Stop Incidents Before They Happen
Data breaches can cost millions—not just in fines and lawsuits, but in lost trust and damaged reputation. Effective data breach prevention is not a single tool but a multi-layered approach.
risikomonitor.com GmbH helps businesses build a resilient security framework through:
Role-based access control and identity management
Endpoint protection and network segmentation
Data encryption at rest and in transit
Employee awareness training and phishing simulation
24/7 monitoring of potential breach indicators
Additionally, automated compliance tools ensure organizations meet key regulatory standards such as GDPR, HIPAA, and ISO 27001, minimizing legal risks and reinforcing internal security best practices.
When a breach is attempted, every second counts. That’s why proactive detection combined with intelligent prevention is the most effective defense.
Darknet Penetration Testing: What You Don’t See Can Hurt You
Cybersecurity doesn’t end with surface-level monitoring. Threat actors often use the darknet—a hidden part of the internet—to sell stolen data, share exploits, or coordinate attacks. Ignoring it is like locking your front door while leaving the back wide open.
Darknet penetration testing from risikomonitor.com GmbH gives businesses visibility into this hidden world. It involves:
Scanning darknet forums, marketplaces, and chat channels
Identifying leaked credentials, confidential data, or insider threats
Testing organizational exposure through simulated darknet attacks
Monitoring for mentions of company domains, products, or executives
Integrating darknet intelligence with real-time alerts
This advanced layer of protection helps organizations understand what threat actors already know about them—and gives them time to respond before the attack reaches their systems.
Cloud Security Audit: Securing Your Digital Infrastructure
With more businesses migrating to the cloud, cloud security audits have become a critical part of any cybersecurity strategy. Cloud environments offer flexibility, but they also come with new risks—from misconfigured storage buckets to unauthorized access via third-party apps.
risikomonitor.com GmbH performs in-depth cloud security audits covering:
Infrastructure misconfigurations (e.g., open ports, weak encryption)
Access control policies and privilege escalations
Cloud-native application vulnerabilities
Logging and monitoring configurations
Compliance checks for GDPR, SOC 2, and more
The audit process results in a comprehensive risk report, complete with actionable remediation steps. Whether you're using AWS, Azure, Google Cloud, or a hybrid setup, the platform ensures your environment is secured and compliant.
Why Choose risikomonitor.com GmbH?
What sets risikomonitor.com GmbH apart is its unified approach to security. Rather than offering siloed tools, the platform provides an integrated solution for:
Real-time security risk detection
Automated data breach prevention protocols
Advanced darknet monitoring and penetration testing
End-to-end cloud security audit and compliance support
This all-in-one platform is ideal for SMEs, regulated industries, and IT leaders who need visibility, control, and automation without the complexity of managing multiple tools.
Final Thoughts
Cybersecurity is no longer about reacting to threats—it's about predicting them. With the rise of cloud computing, remote work, and underground cybercriminal networks, organizations need a smarter, deeper level of protection.
By combining intelligent security risk detection, strong data breach prevention, darknet penetration testing, and rigorous cloud security auditing, risikomonitor.com GmbH gives your business a comprehensive shield against modern cyber threats.
0 notes
Text
CCTV Trends in Dubai’s Corporate World
Explore how Dubai's corporate world is embracing new CCTV trends for safety, efficiency, and growth. Learn about smart CCTV installation Dubai solutions and how businesses are using home CCTV tech too.

In a city as dynamic as Dubai, where skyscrapers rise overnight and businesses move at lightning speed, corporate security must stay one step ahead. That’s why CCTV installation Dubai is no longer just about protecting office doors — it’s about building smarter, more responsive workspaces.
From AI-powered surveillance to remote access systems, today’s corporate cameras are more like intelligent assistants than just security gadgets. Let’s dive into the top CCTV trends shaking up boardrooms and break rooms across Dubai.
1. AI is Changing the Way Offices Monitor
Smart Cameras with Face Recognition
Gone are the days when cameras just watched. Today, cameras recognize. Facial recognition is being widely used in corporate lobbies across Dubai. Not only does it boost security, but it also allows for touchless, seamless check-ins for staff and visitors.
Behavior Detection to Prevent Incidents
Some cameras are so smart now that they can detect odd behavior. If someone loiters in a restricted zone, the system sends instant alerts — keeping everyone safe while you sip your karak in peace.
Crowd and Heat Mapping in Offices
Larger companies use heat mapping to see where employees gather most — helping with space optimization and pandemic-era social distancing.
2. Going Mobile — Control Your Office from Anywhere
Remote Monitoring for Busy Executives
Thanks to mobile-enabled surveillance, CEOs and IT managers can check multiple office locations from their smartphones. A few taps, and you’re viewing your entire building while sitting in your Tesla.
Cloud-Based Footage Storage
No more dusty hard drives in locked drawers. Businesses now prefer cloud storage — it's safer, scalable, and accessible from anywhere in the world.
Live Alerts to the Right People
CCTV systems now send push notifications to the designated employee when something unusual happens. Whether it’s the janitor’s closet being opened or a door left ajar — someone knows instantly.
3. Cybersecurity Meets Physical Security
Encrypted Video Transmission
As hackers become smarter, so do cameras. Companies in Dubai are choosing encrypted systems to prevent cybercriminals from accessing camera feeds.
Multi-Factor Access Control
Many CCTV systems are now linked with two-step verification. Want to watch the camera feed? Authenticate yourself. This trend is popular in fintech, law firms, and corporate data centers.
CCTV Linked with Firewalls
Corporate IT teams now integrate CCTV systems into existing firewalls and endpoint protections — because physical and digital security are now one big happy family.
4. Better Insights = Better Business Decisions
Meeting Room Usage Analytics
Smart CCTV helps companies figure out which meeting rooms are actually being used and which are just… collecting dust. Time to cancel that unnecessary expansion?
Workplace Productivity Monitoring
Though a bit controversial, some corporations use camera analytics to understand office productivity. Are people spending too long in common areas? Are desks empty after lunch?
Client Zones Under Observation
Client waiting areas are often equipped with high-resolution cameras to ensure VIPs feel safe and valued. It’s about comfort, not control.
5. CCTV and Hybrid Work Culture
Monitor Empty Offices Securely
Hybrid work has created a new challenge: office spaces are often half empty. CCTV installation Dubai helps secure these quiet zones without needing physical guards.
Use of Home Camera Models in Offices
Interestingly, smaller startups are even using home CCTV installation Dubai systems in their coworking spaces. They’re affordable, plug-and-play, and perfect for smaller teams.
Smart Notifications When No One is Around
Remote alerts are now more crucial than ever. Cameras send messages when a door opens at 10 PM or a light turns on suddenly — letting you take action immediately.
6. Privacy Rules & Compliance Are Shaping Camera Use
Transparency with Employees
CCTV use in Dubai corporates must comply with labor laws. Employers are becoming more transparent by placing visible signs and communicating clearly with teams.
Restricted Access to Camera Footage
Not everyone can view everything. Companies assign roles so that only specific people can access certain cameras — boosting trust and legal compliance.
Record Retention Policies
Many companies now follow fixed video retention policies — storing footage for 30, 60, or 90 days as per legal guidelines or internal needs.
7. Seamless Integration With Office Ecosystems
Linking CCTV with Smart Locks
Doors, elevators, and lights can now be controlled through one system. When an unauthorized person is detected, doors auto-lock, and alerts are triggered.
Biometric Attendance + CCTV
Face recognition paired with attendance systems means employees don’t need to tap or swipe — they just walk in, and the system marks them present.
CCTV Meets Energy Efficiency
Some offices link surveillance with smart lighting — lights turn off in empty rooms. It saves energy and money without lifting a finger.
8. Environmental Monitoring Using CCTV Sensors
Temperature and Smoke Detection Cameras
High-tech offices now use CCTV systems that detect heat spikes or unusual temperatures, helping prevent fire incidents or overheating in server rooms.
Flood Detection in Basement Parking
Yes, cameras can now sense rising water levels and alert facilities teams before it gets messy — a lifesaver during heavy rains in Dubai.
Gas Leak Monitoring
In industrial offices or large kitchens, gas sensors are built into cameras — keeping people safe and businesses running.
9. Green Buildings, Green Surveillance
Low-Energy Cameras are Trending
With Dubai’s focus on sustainability, energy-efficient CCTV models are now a hit. Solar-powered systems are also making waves in newer developments.
E-Waste Management Policies
Companies are opting for recyclable and modular CCTV equipment, so when upgrades are needed, only parts are replaced — not the entire system.
Smart Scheduling for Camera Use
Some systems only record when motion is detected or during office hours — saving energy and making storage management easy.
10. The Human Touch Behind All the Tech
Training Staff to Handle Footage Respectfully
Despite all the tech, real humans must manage these systems. Corporates in Dubai are investing in training employees on camera etiquette and ethical use.
Feedback Loops with Employees
Some companies actually review footage with teams to spot productivity trends or discuss layout improvements — making CCTV a shared tool, not a secret spy.
Making Security a Team Culture
Security isn’t just about devices; it’s about mindset. Cameras are becoming part of a broader culture of trust, transparency, and teamwork.
Final Words: Surveillance with a Smart Twist
CCTV systems in Dubai’s corporate world are no longer silent spectators. They’re decision-makers, security experts, data analysts, and even eco-warriors. From startups using home CCTV installation Dubai kits to large corporations investing in AI-powered surveillance, the trends are clear — cameras are going smart, mobile, and sustainable.
If you're running a business in Dubai, now’s the time to upgrade your security strategy. With professional CCTV installation Dubai services, you can stay ahead of threats, support your team, and create a more efficient workplace.
So, next time you see a camera in the office, give it a little smile. It’s doing more than just watching — it’s working for you.
1 note
·
View note
Text
How Managed IT Services Help Fintech Stay Competitive in a Digital-First World

In the rapidly evolving digital economy, fintech companies are redefining how the world experiences financial services. From instant digital payments to AI-driven loan approvals, innovation is at the heart of fintech. But innovation alone is not enough—security, scalability, compliance, and seamless technology operations are equally critical to long-term success. This is where Managed IT Services become indispensable.
As one of the most trusted MSP Services In Texas, Technokraft Serve delivers comprehensive IT solutions specifically tailored for the fintech sector. In this article, we explore how Managed IT Services For Fintech empower companies to not only keep pace but thrive in the digital-first financial landscape.
What Are Managed IT Services in the Context of Fintech?
Managed IT Services refer to outsourcing IT responsibilities to an expert third-party provider, commonly known as a Managed Service Provider (MSP). These services include infrastructure management, cybersecurity, cloud solutions, compliance support, disaster recovery, and ongoing IT monitoring.
For fintech organizations—where digital trust, customer experience, and uptime are paramount—Managed IT Services For Fintech offer a vital technology backbone. Partnering with the right MSP For Fintech, like Technokraft Serve, means gaining a strategic ally to navigate constant change while maintaining agility and resilience.
Why Managed IT Services Are Essential for Fintech Competitiveness
1. Advanced Cybersecurity Protection
Fintech companies are prime targets for cyberattacks due to the sensitive nature of financial data. A single breach can result in catastrophic financial and reputational damage. Managed IT Services provide a multilayered approach to security—offering proactive monitoring, real-time threat detection, vulnerability patching, and security audits.
Technokraft Serve implements enterprise-grade firewalls, encryption protocols, and continuous monitoring as part of its MSP Services In Texas to keep fintech platforms safe from threats 24/7.
2. Regulatory Compliance Simplified
From PCI-DSS and SOX to GDPR, fintechs must navigate a complex web of compliance requirements. Falling short can lead to massive penalties and loss of customer trust. Managed IT Services For Fintech ensure that your systems meet regulatory standards through audit readiness, documentation support, data handling policies, and regular compliance reviews.
Technokraft Serve provides fintech companies with comprehensive compliance management tools, ensuring you stay compliant and audit-ready at all times.
3. Enhanced Scalability and Performance
Fintech businesses often experience sudden spikes in demand—such as during funding rounds, product launches, or market expansions. With Managed IT Services, your infrastructure is built to scale. Whether you need to onboard more users or add new functionality, the right MSP For Fintech ensures seamless growth without technical disruptions.
At Technokraft Serve, we design scalable cloud and infrastructure solutions that allow fintech startups and enterprises alike to grow at their own pace.
4. 24/7 IT Monitoring and Support
Downtime in fintech isn’t just a minor inconvenience—it can lead to financial losses, customer dissatisfaction, and legal ramifications. Managed IT Services offer continuous system monitoring, instant alerts, and dedicated helpdesk support.
As a leading provider of MSP Services In Texas, Technokraft Serve guarantees maximum uptime, proactive support, and rapid response times that keep your operations running smoothly.
Core Components of Managed IT Services for Fintech
When you choose a trusted partner like Technokraft Serve, you gain access to a suite of tailored solutions that strengthen your IT foundation. Here's what a robust Managed IT Services For Fintech package includes:
1. Cloud Services & Migration
Most fintech platforms today run on the cloud. Managed cloud services ensure high availability, data redundancy, and secure access. We handle everything from cloud migration and configuration to ongoing optimization.
2. Data Backup and Disaster Recovery
Business continuity is critical in fintech. Managed IT Services include real-time data backups, redundant systems, and detailed disaster recovery plans to keep operations online—even in the face of cyberattacks or outages.
3. IT Infrastructure & Network Management
From servers and switches to endpoint devices, your entire IT ecosystem needs round-the-clock care. Technokraft Serve provides proactive management and optimization of networks, ensuring strong connectivity and minimal risk.
4. Application Performance Monitoring
Fintech apps must deliver a flawless user experience. We monitor performance, latency, and errors in real time, applying fixes before users are ever affected.
5. Strategic IT Consulting
Our MSP For Fintech services also include IT roadmaps, budgeting assistance, and technology planning to help fintech firms make informed decisions that align with their growth goals.
The Technokraft Serve Edge in MSP Services In Texas
Not all MSPs are built the same. Fintech demands deep technical insight, bulletproof security, and industry knowledge. Technokraft Serve stands apart as a specialized provider of Managed IT Services For Fintech, offering:
Fintech-Focused Solutions: Designed specifically for the complex needs of financial technologies and digital banking.
Local Expertise, Global Vision: As a top-rated MSP Services In Texas, we combine localized support with international security standards and best practices.
Security First Philosophy: From endpoint protection to threat intelligence, we take a proactive stance on cyber defense.
Flexible, Scalable Models: Only pay for what you use—ideal for startups and scaling fintechs alike.
How Managed IT Services Future-Proof Fintech Companies
1. AI & Machine Learning Integration
AI plays a significant role in credit scoring, fraud detection, and customer experience. Managed IT Services help fintech companies implement and maintain AI-driven tools, ensuring their algorithms perform securely and reliably.
2. Blockchain Support & Deployment
As blockchain becomes central to financial innovation, MSP For Fintech helps deploy, secure, and manage distributed ledger technologies—ensuring transaction integrity and high performance.
3. Faster Time-to-Market
By reducing the IT burden on internal teams, Managed IT Services accelerate development cycles and minimize deployment delays. This agility is a competitive edge in fintech’s fast-moving environment.
4. Global Regulatory Readiness
Fintech firms expanding globally must comply with diverse regulations. Technokraft Serve supports your compliance strategy with scalable infrastructure, localized security protocols, and international data governance expertise.
Why Choosing the Right MSP For Fintech Matters
A reliable Managed IT Services provider is not just a vendor—it’s a growth partner. Fintechs should prioritize MSPs with:
Industry-specific experience
Proven security credentials
24/7 proactive monitoring
Transparent pricing and service-level agreements (SLAs)
Strategic consulting capabilities
At Technokraft Serve, we pride ourselves on being more than a service provider—we are your long-term IT success partner, helping fintech firms navigate the future of finance confidently.
Final Thoughts: Thrive in a Digital-First World with Technokraft Serve
In a digital-first world where every second matters, Managed IT Services provide fintech companies with the infrastructure, security, and agility needed to excel. From cybersecurity and compliance to performance and innovation, the role of Managed IT Services For Fintech is more vital than ever.
Partnering with an expert like Technokraft Serve ensures that your IT backbone is not only robust but also future-ready. With scalable solutions, real-time monitoring, and unmatched industry expertise, we’re proud to lead the way in MSP Services In Texas for fintech innovators.
Let Technokraft Serve help you unlock the full potential of your fintech business with next-gen Managed IT Services.
0 notes
Text
What services does Mantu Computech offer?

Welcome to Mantu Computech! Whether you’re a tech-savvy individual, a small business owner, or part of a large enterprise, we’ve got your back. Our mission is to simplify technology for everyone by offering a comprehensive suite of services tailored to meet your needs. Let’s dive into the full range of solutions we provide to keep your digital life running smoothly.
1. Computer Repair & Maintenance
Is your computer acting up? We’ll fix it!
Hardware Repairs: Broken screens, faulty keyboards, overheating issues, and more.
Software Troubleshooting: Virus/malware removal, OS errors, slow performance, and driver updates.
Upgrades: Boost speed with RAM, SSD, or graphics card upgrades.
On-Site or In-Store: Choose what works best for you. Perfect for: Laptops, desktops, Macs, and gaming PCs.
2. Professional IT Support
Keep your business tech stress-free with our IT expertise.
24/7 Remote Support: Instant help for emergencies.
Network Setup & Security: Secure Wi-Fi, VPNs, firewalls, and data encryption.
Cloud Solutions: Backup, storage, and migration services.
Cybersecurity Audits: Protect your business from threats. Ideal for: Small to medium businesses, remote/hybrid teams.
3. Software Development
Transform your ideas into powerful tools.
Custom Software: Build CRM, ERP, or inventory management systems.
Mobile Apps: iOS and Android apps for startups or enterprises.
AI & Automation: Integrate smart solutions into workflows.
Legacy Software Modernization: Update outdated systems. Tailored for: Healthcare, education, retail, and more.
4. Web Design & Development
Create a stunning online presence that converts.
Responsive Websites: From blogs to e-commerce stores.
SEO Optimization: Rank higher on Google.
Platform Expertise: WordPress, Shopify, Wix, and custom coding.
Maintenance: Regular updates, security patches, and bug fixes. Great for: Startups, bloggers, and online businesses.
5. Data Recovery Services
Lost files? Don’t panic—we can recover them!
Hard Drive Recovery: From crashed, formatted, or water-damaged devices.
SSD/Flash Drive Recovery: Retrieve photos, documents, and videos.
Confidentiality Guaranteed: Your data stays private. We handle: Laptops, servers, external drives, and RAID systems.
6. Network Maintenance
Keep your business connected and secure.
Proactive Monitoring: Prevent downtime with 24/7 oversight.
Speed Optimization: Fix slow networks and latency issues.
Maintenance Contracts: Scheduled checkups for peak performance. Best for: Offices, schools, and co-working spaces.
7. Custom-Built Computers
Get a PC designed just for you.
Gaming Rigs: High-FPS machines with RGB lighting.
Workstations: Powerful setups for video editing, coding, or 3D modeling.
Budget-Friendly Options: Quality builds without breaking the bank.
Warranty Included: Peace of mind with every purchase.
8. Computer Components & Accessories
Upgrade or replace your gear with ease.
Components: GPUs, motherboards, processors, and cooling systems.
Peripherals: Keyboards, mice, monitors, and ergonomic chairs.
Eco-Friendly Options: Sustainable tech for eco-conscious users. Shop online or in-store!
9. Software Licenses & Training
Stay legal and skilled with our resources.
Licenses: Genuine Microsoft, Adobe, and antivirus software.
Training Programs: Learn coding, cybersecurity, or Microsoft 365.
Corporate Workshops: Upskill your team with tailored sessions. Certifications provided upon completion.
Why Choose Mantu Computech?
✅ Expertise: Certified technicians and developers. ✅ Customer-Centric: Flexible pricing, warranties, and fast turnaround. ✅ Comprehensive Care: From hardware to cloud solutions—we do it all. ✅ Affordable: Competitive rates for individuals and businesses.
🚀 Let’s Get Started! Whether you need a quick repair, a custom app, or a secure network, Mantu Computech is your trusted partner. Contact us today for a free consultation, or visit our store to explore our products and services.
Your tech problems end here. 💻✨
1 note
·
View note
Text
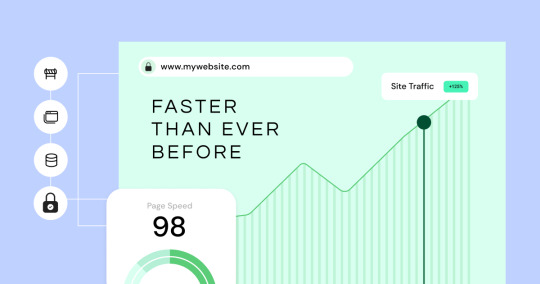
Complete Website Security & Monitoring Client Attraction Tools
Complete Website Security & Monitoring
Real-Time Malware Detection (🛡️ Instantly detect hidden threats before they break your site) Continuously scans websites for malware, redirect scripts, phishing links, and backdoors.
Scheduled Security Audits (📅 Keep your clients protected 24/7) Set automated scans to run daily, weekly, or monthly.
Branded Audit Reports (📄 Impress clients with professional security reports) Generate white-labeled vulnerability reports that close deals.
🛡️ AI Firewall & Instant Protection
Smart AI Firewall (🧠 Let AI block attacks before they reach your site) Prevents SQL injections, spam queries, brute-force logins, and more.
Zero-Day Defense (🚫 Stay ahead of new and evolving threats) Detects behavior-based risks even before they’re listed in vulnerability databases.
Bot, Spam & DDoS Defense (🤖 Block junk traffic with a click) Filters out spam bots, fake users, and DDOS hits.
💼 DFY Client Attraction Tools
Built-In Client Finder (🔍 Find vulnerable websites to pitch) Filter by niche, CMS, or location and get their details.
Self-Audit Widget (📥 Let visitors scan their own site on your page) Converts them into leads automatically.
Done-for-You Cold Emails (✉️ Start conversations that convert) Use plug-and-play templates to sell without writing.
🖥️ Full Agency Setup Done For You
DFY Agency Website (💻 Your own branded platform) Includes service pages, branding, and funnels.
Client Portal Access (🧾 Let them log in and view their audits) Increases retention and authority.
Resell Rights + White Label (💸 You own the product and the profits) No hidden licenses or restrictions.
How Soteria Works
STEP-1
Add Sites Manually or in bulk, import client domains into the dashboard.
STEP-2
Scan & Detect AI runs vulnerability scans and checks for malware, bots, backdoors, and plugin exploits.
STEP -3
Fix & Protect One click to clean malware and activate firewall protections.
STEP -4
Report & Monetize Clients receive branded reports. Offer monthly plans to stay protected.
Branded Audit Reports
Generate stunning, client-ready PDF reports under your brand. These reports clearly show risks, threats, and suggested fixes — making them powerful conversion tools.
Downtime & Health Monitoring (Optional)
Track uptime, performance dips, and outages — giving you a chance to proactively fix issues before your client notices.


#digital illustration#artists on tumblr#CompleteWebsiteSecurity#WebsiteMonitoring#RealTimeMalwareDetection#CyberSecurity#MalwareProtection#WebsiteSafety#OnlineSecurity#CyberSecurityTips#MalwarePrevention#WebSecurity#ProtectYourWebsite#WebsiteProtection#DigitalSafety#SecurityAwareness#IntranetSecurity#CyberThreats#SafeBrowsing#WebMonitoring#DataProtection
0 notes
Text
The Future of Data Infrastructure: Building Efficient and Secure Data Centers for the Digital Era

In today’s rapidly evolving digital world, the amount of data being created, stored, and processed is unprecedented. Organizations are seeking smarter and more scalable infrastructure to manage their workloads, improve operational efficiency, and protect critical information. Enter the modern data center—a powerhouse of digital storage, computing, and innovation.
This comprehensive guide by One Union Times explores essential components that define the backbone of today’s intelligent data systems, including how to store big data, hybrid data center environments, data center firewall technologies, modular data center design, power usage effectiveness (PUE), and the ongoing debate between cloud vs colocation. We also break down the features of an efficient data center, the integration of data center and cloud computing, and critical factors like data center physical security.
📌 1. How to Store Big Data
Storing massive volumes of data requires both scalability and performance. Traditional storage systems are no longer adequate for handling petabytes of structured and unstructured data. Here's how enterprises approach how to store big data effectively:Storage MethodDescriptionBenefitsDistributed File SystemsData is split and stored across multiple nodesScalable and fault-tolerantObject StorageUses metadata and unique identifiersIdeal for unstructured dataData LakesCentralized repository for raw dataEnables advanced analyticsCloud StorageElastic capacity from third-party providersCost-effective and flexible
✅ Benefits:
Reduced infrastructure costs
Improved scalability
Seamless integration with analytics platforms
Increased fault tolerance
📌 2. Hybrid Data Center
A hybrid data center combines on-premises infrastructure with public and private cloud services. It provides flexibility, security, and the ability to shift workloads between environments based on needs.ComponentOn-PremiseCloudControlFullPartialScalabilityLimitedHighCostCapExOpExUse CaseSensitive DataWeb Apps, Backup
✅ Benefits:
Optimized workload placement
Business continuity
Enhanced compliance
Operational flexibility
📌 3. Data Center Firewall
A data center firewall is crucial for monitoring and controlling network traffic entering and leaving the data center. It acts as a security barrier to detect, block, and respond to cyber threats.TypeDescriptionApplicationNetwork FirewallsPerimeter defenseProtect entire networkApplication FirewallsMonitors app-layer trafficPrevents exploitsNext-Gen FirewallsIntegrated AI & DPISmart threat detection
✅ Benefits:
Prevents unauthorized access
DDoS protection
Application-layer control
Real-time threat intelligence
📌 4. Modular Data Center Design
A modular data center design refers to a pre-engineered and standardized approach to building data centers using prefabricated modules. These can be rapidly deployed, scaled, and relocated if needed.FeatureDescriptionFlexibilityScalable in units or blocksSpeedDeployed in weeks, not monthsCost-EffectivenessReduced construction and operational costPortabilityEasily relocated and upgraded
✅ Benefits:
Fast deployment
Future-proofing
Reduced downtime
Sustainable design
📌 5. Power Usage Effectiveness (PUE)
Power Usage Effectiveness (PUE) is the industry-standard metric to determine the energy efficiency of a data center.
📌 6. Cloud vs Colocation
The debate between cloud vs colocation continues as businesses evaluate the best strategy for IT infrastructure.FactorCloudColocationControlLimitedFullCost ModelOpExCapExScalabilityInstantRequires planningData SovereigntyMay varyFull control
✅ Benefits of Cloud:
Instant scalability
Managed services
Pay-as-you-go model
✅ Benefits of Colocation:
Greater control
Predictable performance
Physical security
📌 7. Efficient Data Center
An efficient data center optimizes resources like power, cooling, space, and staffing to ensure maximum performance and minimum waste.Optimization AreaStrategiesPowerUse of renewable energy, UPS efficiencyCoolingAI-based airflow managementServer UtilizationVirtualization, server consolidationSpaceHigh-density racks, modular layouts
✅ Benefits:
Cost savings
Improved sustainability
Higher uptime
Reduced environmental impact
📌 8. Data Center and Cloud Computing
Data center and cloud computing are intertwined in modern IT. Data centers provide the hardware and networking foundation, while cloud computing delivers services over the internet.ElementData CenterCloud ComputingCore FunctionInfrastructurePlatform & Service DeliveryOwnershipEnterprise or colocationThird-party providerDeploymentPhysical/On-PremRemote/Virtual
✅ Benefits:
Hybrid architecture support
Faster innovation
Scalability and flexibility
Integration with DevOps and AI workloads
📌 9. Data Center Physical Security
Data center physical security is critical to ensure that only authorized personnel can access the servers and storage units physically.Security LayerMeasuresPerimeterFencing, CCTV, motion sensorsAccess ControlBiometric readers, keycardsInteriorMantraps, surveillance, guardsEnvironmentFire suppression, flood sensors
✅ Benefits:
Protection against theft and sabotage
Compliance with regulations
Enhanced client trust
Reduced insurance costs
✅ Summary Table: Key Data Center Components & Their Advantages
AreaKeywordKey BenefitBig Data Storagehow to store big dataScalable and flexible solutionsHybrid Infrastructurehybrid data centerCombines cloud and on-prem powerNetwork Securitydata center firewallAdvanced threat preventionRapid Scalabilitymodular data center designFast deployment and flexibilityEnergy Metricspower usage effectiveness PUETrack and improve energy efficiencyStrategycloud vs colocationInformed infrastructure choicesOptimizationefficient data centerCost and energy savingsIntegrationdata center and cloud computingUnified digital transformationProtectiondata center physical securitySecures sensitive infrastructure
🌐 Final Thoughts: The Future Is Modular, Hybrid, and Intelligent
As the digital world accelerates, building and maintaining a smart, secure, and scalable data center has become a necessity—not a luxury. Organizations must embrace hybrid models, modular designs, and cloud integrations to remain agile and competitive.
Whether you're a startup needing cloud agility or a large enterprise looking for colocation and physical control, understanding the balance between data center and cloud computing is essential. Invest in efficient data center solutions, track your power usage effectiveness PUE, secure your environment with strong data center firewall setups, and don’t forget—security begins with physical access. Prioritize data center physical security to protect your digital assets from every angle.
0 notes
Text
Fortress-Level Security, Hacker-Proof Solutions — We’re the Cyber Security Firm You’ve Been Searching For
In today’s hyper-connected world, where cyber threats evolve at breakneck speed, relying on yesterday’s security solutions simply isn’t enough. At eShield IT Services, we’ve built a reputation as the cyber security firm that delivers fortress-level protection and hacker-proof solutions designed to withstand even the most advanced cyber attacks. Whether you’re a startup, a mid-sized business, or a global enterprise, you need more than software — you need a true partner in digital defense. Welcome to eShield IT Services, the cyber security firm you’ve been searching for.
Why Cyber Security is More Critical Than Ever
Cybercrime is no longer a distant concern — it's a daily threat that targets businesses of all sizes. With the rise of ransomware, phishing scams, insider threats, and AI-driven attacks, organizations are facing unprecedented risks. According to Cybersecurity Ventures, cybercrime damages are expected to cost the world $10.5 trillion annually by 2025. This makes investing in a professional cyber security firm like eShield IT Services not just a best practice — but a business imperative.
What Makes eShield IT Services a Leading Cyber Security Firm?
Not all cyber security firms are created equal. The best firms don’t just respond to threats — they anticipate them, neutralize them, and evolve with the threat landscape. So what sets eShield IT Services apart?
Proactive Defense Mechanisms We don’t wait for breaches — we prevent them. By leveraging predictive analytics, threat intelligence, and behavioral monitoring, we stay several steps ahead of attackers.
24/7 Monitoring and Rapid Response Cyber threats don’t take holidays — and neither do we. Our security operations center (SOC) is manned around the clock to ensure instant detection and immediate response.
Customized Security Frameworks Every business is different, so your security strategy should be too. At eShield IT Services, we tailor our solutions based on your industry, infrastructure, and risk profile.
Compliance-Ready Solutions From GDPR to HIPAA to PCI-DSS, we help your organization stay compliant with evolving regulations without the headache.
Fortress-Level Security: What It Means at eShield IT Services
“Fortress-level security” isn’t just a catchy phrase — it’s the foundation of our approach. Here’s what it looks like in action:
Advanced Perimeter Defense We build digital perimeters that rival physical fortresses. From next-generation firewalls to zero-trust architectures, eShield IT Services ensures your network remains impenetrable.
AI-Driven Threat Detection Our machine learning systems continuously scan for anomalies and flag potential threats in real time — detecting what human eyes might miss.
Layered Security Model We implement multi-layered protection — endpoint, network, application, and user-level defenses — to ensure there are no weak links in your digital chain.
Regular Penetration Testing We conduct ethical hacking and simulated attacks to expose and patch vulnerabilities before real hackers do.
Hacker-Proof Solutions by eShield IT Services
While no system is 100 percent invulnerable, our approach makes it extremely difficult for hackers to succeed. Our hacker-proof philosophy involves:
Zero Trust Principles Never trust, always verify. Every access request is authenticated, authorized, and encrypted.
Least Privilege Access Users and systems get only the access they need — nothing more, nothing less.
Data Encryption We secure your data at rest, in transit, and even during processing, making it useless in the wrong hands.
Incident Readiness Even the best defenses can be challenged. Our expert incident response team ensures any breach is detected, contained, and resolved at record speed.
Industries Secured by eShield IT Services
As a cyber security firm with diverse expertise, eShield IT Services serves organizations across many sectors:
Healthcare: Protecting sensitive patient data and ensuring HIPAA compliance
Finance and Banking: Safeguarding transactions, customer data, and digital assets
Retail and eCommerce: Preventing payment fraud, data leaks, and downtime
Legal and Professional Services: Securing client confidentiality and internal operations
Manufacturing and OT: Defending industrial control systems from cyber sabotage
Cyber Security Firm vs. In-House IT: Why eShield IT Services Stands Out
Hiring an in-house team sounds good in theory, but in practice, it often falls short. Here's why partnering with a dedicated cyber security firm like eShield IT Services is the smarter choice: In-House ITeShield IT ServicesLimited expertise in niche threatsAccess to seasoned experts in all domainsHigh costs of tools, training, and talentCost-effective with enterprise-grade resourcesSlower response times24/7 monitoring and instant incident responseReactive approachProactive threat hunting and prevention
Our Methodology at eShield IT Services
Security Assessment We begin by analyzing your current environment, identifying vulnerabilities, and assessing risk.
Tailored Strategy Development We design a security roadmap aligned with your business goals and compliance requirements.
Deployment and Configuration We implement the necessary technologies and policies for full-spectrum protection.
Monitoring and Maintenance Our SOC operates around the clock, optimizing your security posture continuously.
Training and Awareness We empower your employees with the knowledge and skills to prevent social engineering and phishing attacks.
Client Success Stories
"Since partnering with eShield IT Services, we’ve seen a 95 percent drop in phishing attempts reaching our employees. Their team is sharp, responsive, and incredibly proactive." — CFO, Financial Services Firm
"Their penetration testing exposed vulnerabilities our previous vendor completely missed. We now feel truly secure for the first time." — IT Director, Healthcare Organization
Why Choose eShield IT Services?
eShield IT Services is not just another cyber security firm — we are your strategic ally in the fight against cyber threats.
Cutting-Edge Technology From AI-driven threat analysis to secure cloud integrations, we harness the best tools available in the industry.
Unmatched Expertise Our team includes CISSPs, CEHs, and other certified professionals with deep, real-world experience.
Human-Centric Partnership We believe strong communication and client collaboration are essential to building effective defenses.
Scalable Security Solutions Whether you’re expanding operations or undergoing digital transformation, our services scale with you.
Let’s Secure Your Future — Together
In a world where digital threats are relentless, your business deserves uncompromising protection. eShield IT Services delivers fortress-level defense and hacker-proof solutions that go beyond the basics. Don’t wait for a breach to discover your vulnerabilities. Let us help you stay one step ahead.
Visit www.eshielditservices.com to schedule your free consultation today. See why we’re the cyber security firm trusted to protect what matters most.
0 notes
Text
The Ultimate Guide to Cloud Hosting: Benefits, Features & FAQs
In today’s digital-first world, businesses need scalable, reliable, and cost-effective hosting solutions to keep their websites and applications running smoothly. Cloud Hosting has emerged as a game-changer, offering unparalleled flexibility and performance compared to traditional hosting.
At CloudMinister Technologies, we provide advanced cloud hosting solutions tailored to meet the demands of startups, enterprises, and developers. In this blog, we’ll explore what cloud hosting is, its benefits, key features, and answer some common FAQs.
What is Cloud Hosting?
Cloud Hosting is a virtualized hosting solution that uses multiple interconnected servers (a "cloud") to distribute resources dynamically. Unlike traditional hosting (shared, VPS, or dedicated), cloud hosting ensures high availability, scalability, and redundancy by leveraging a cluster of servers.
Key Benefits of Cloud Hosting
Scalability – Instantly upgrade CPU, RAM, or storage as your business grows. High Uptime (99.9% SLA) – No single point of failure ensures maximum reliability. Cost-Efficiency – Pay only for the resources you use (no over-provisioning). Global Performance – Deploy servers in multiple regions for low-latency access. Security & Backups – Built-in firewalls, DDoS protection, and automated backups.
Cloud Hosting

Why Choose CloudMinister’s Cloud Hosting?
🔹 Flexible Plans – From small websites to enterprise-grade applications. 🔹 SSD-Powered Speed – Ultra-fast NVMe storage for quick load times. 🔹 24/7 Expert Support – Our team ensures seamless performance. 🔹 Auto-Scaling – Handle traffic spikes effortlessly. 🔹 Multi-Cloud & Hybrid Options – Deploy across AWS, Azure, or private clouds.
FAQs About Cloud Hosting
1. Is cloud hosting better than shared hosting?
Yes! Cloud hosting offers better performance, scalability, and security compared to shared hosting, which has limited resources.
2. How does cloud hosting improve website speed?
Cloud hosting uses load balancing and SSD storage, reducing latency and improving response times.
3. Is cloud hosting secure?
Absolutely! CloudMinister provides firewalls, encryption, DDoS protection, and regular backups to keep your data safe.
4. Can I upgrade my cloud hosting plan later?
Yes! One of the biggest advantages is instant scalability—upgrade/downgrade anytime.
5. What’s the difference between cloud hosting and VPS?
While VPS gives you a fixed portion of a server, cloud hosting uses multiple servers, ensuring better uptime and flexibility.
6. Do I need technical skills to use cloud hosting?
Not necessarily! CloudMinister offers managed cloud hosting with easy-to-use control panels like cPanel & Plesk.
7. How much does cloud hosting cost?
Pricing starts as low as $5/month for basic plans, with enterprise solutions available on demand.
Final Thoughts
Whether you're running a blog, eCommerce store, SaaS application, or AI project, Cloud Hosting from CloudMinister Technologies provides the speed, security, and scalability you need.
Ready to migrate to the cloud? Explore our Cloud Hosting Plans today!
0 notes
Text
Discover How Web Security Solutions Protect Your Business from Cyber Threats Every Day
In today’s digital landscape, businesses of all sizes face an increasing number of cyber threats that can lead to data breaches, financial losses, and damaged reputations. As cybercriminals develop more sophisticated methods, protecting your online presence has never been more critical. Web security solutions offer a comprehensive approach to safeguarding digital assets by detecting, preventing, and responding to cyber threats. These solutions cover various aspects of online security, including firewalls, intrusion detection systems, data encryption, and threat monitoring. Implementing effective web security solutions ensures your business stays one step ahead of potential attacks, keeping both your operations and customer trust intact.
How Web Security Solutions Help Stop Cyber Attacks Daily?
Web security solutions play a vital role in preventing cyber attacks on a daily basis by continuously monitoring traffic, identifying unusual behavior, and blocking unauthorized access. These advanced systems employ firewalls, intrusion prevention technologies, and AI-driven threat intelligence to recognize and neutralize threats in real-time. With cybercriminals targeting websites every day, businesses must be equipped with defenses that adapt quickly to emerging risks. Web security solutions ensure 24/7 protection by automatically scanning for malware, phishing attempts, and brute-force attacks. This constant vigilance allows businesses to operate securely online without the fear of interruptions, ensuring smooth performance and long-term success.
Protect Your Data with Reliable Web Security Solutions
Reliable web security solutions are essential for protecting sensitive business and customer data from unauthorized access and theft. These solutions incorporate advanced encryption protocols, secure data storage, and multi-factor authentication to ensure information remains confidential. Data breaches can cost businesses millions, along with long-lasting reputational damage. With the help of web security solutions, companies can enforce strict access controls, monitor user activity, and detect vulnerabilities before they are exploited. By maintaining high levels of data integrity and privacy, these systems build trust with customers and stakeholders. Investing in web security solutions is a proactive step toward a secure digital future.
Web Security Solutions Detect Threats in Real-Time
Real-time threat detection is a hallmark of modern web security solutions. These systems use artificial intelligence and machine learning to constantly scan for and analyze cyber threats as they occur. Real-time alerts and automated responses allow businesses to take immediate action before a threat escalates into a breach. Whether it's a malware attack, a phishing attempt, or unauthorized access, web security solutions provide instant visibility and actionable insights. This level of responsiveness helps minimize damage, reduce downtime, and protect sensitive information. With constantly evolving threats, real-time detection is not just a feature—it's a necessity for any online business.
Secure Your Business Website from Hackers
Hackers often target business websites to steal data, install malware, or take control of the domain for malicious purposes. Web security solutions offer a robust defense by blocking unauthorized entry points, enforcing secure coding practices, and regularly scanning for vulnerabilities. These systems can also include website application firewalls, SSL certificates, and bot mitigation tools to protect against common exploits such as SQL injection or cross-site scripting. A secure website not only prevents financial loss and legal issues but also reassures customers that their information is safe. With web security solutions in place, businesses can confidently grow their online presence without compromise.
Web Security Solutions Safeguard Customer Information
Customer information is one of the most valuable assets a business holds, making it a prime target for cybercriminals. Web security solutions provide encryption, secure sockets layer (SSL) protocols, and secure user authentication to protect customer data during transmission and storage. These tools help businesses comply with data protection regulations such as GDPR, HIPAA, and PCI-DSS. In the event of suspicious activity, alerts are triggered, allowing for rapid response and containment. By safeguarding personal and financial details, web security solutions build customer confidence, enhance loyalty, and preserve your brand’s integrity in the highly competitive digital marketplace.
Prevent Downtime with Strong Web Security Solutions
Website downtime caused by cyber attacks can result in lost revenue, damaged brand image, and reduced customer satisfaction. Web security solutions help prevent this by identifying and neutralizing threats that could disrupt website functionality. Features such as distributed denial-of-service (DDoS) protection, load balancing, and backup systems ensure business continuity even during attempted cyber intrusions. These solutions provide the stability and reliability needed for consistent online performance. By minimizing downtime, companies can maintain seamless operations, protect critical processes, and uphold user experience standards. Web security solutions are an essential investment for any business relying on online platforms for daily operations.
Stop Malware Before It Spreads with Web Security Solutions
Malware infections can quickly spread through networks, causing data loss, system failure, and massive cleanup costs. Web security solutions act as the first line of defense, detecting and blocking malicious software before it can infect systems. With real-time scanning, automatic quarantine, and intelligent threat analysis, these tools identify even the most advanced malware variants. They can also limit the spread within the network by isolating affected segments. This containment prevents full-scale outbreaks and ensures faster recovery. Web security solutions not only protect endpoints and servers but also email gateways and cloud applications, offering comprehensive coverage against malware-based threats.
Conclusion
In an increasingly connected world, web security solutions are essential for businesses to thrive safely online. They offer proactive protection against a wide range of cyber threats, from data breaches to malware and downtime. By integrating these solutions into your digital infrastructure, you safeguard sensitive information, maintain customer trust, and ensure operational continuity. As threats evolve, so do these advanced technologies—constantly adapting to provide stronger, smarter defenses. Investing in web security solutions isn’t just a technical decision; it's a strategic necessity for long-term success. Stay ahead of hackers, protect your digital assets, and empower your business with comprehensive web security solutions.
0 notes
Text
Cloud VPS Server Hosting in 2025 The Ultimate Guide by SEOHostKing

What Is Cloud VPS Server Hosting in 2025? Cloud VPS server hosting in 2025 represents the perfect fusion between the flexibility of cloud computing and the dedicated power of a Virtual Private Server. It delivers enterprise-level infrastructure at affordable pricing, backed by scalable resources, high availability, and powerful isolation—ideal for startups, developers, agencies, eCommerce, and high-traffic websites. Why Cloud VPS Hosting Is Dominating in 2025 Unmatched Performance and Flexibility Traditional hosting is rapidly being replaced by cloud-powered VPS because it offers dynamic resource allocation, 99.99% uptime, lightning-fast SSD storage, and dedicated compute environments—all without the high costs of physical servers. Fully Scalable Infrastructure Cloud VPS adapts to your growth. Whether you're hosting one blog or managing a SaaS platform, you can scale CPU, RAM, bandwidth, and storage with zero downtime. Global Data Center Deployment In 2025, global presence is non-negotiable. Cloud VPS servers now operate in multiple zones, allowing users to deploy applications closest to their target audience for ultra-low latency. Built for High-Security Demands Modern Cloud VPS hosting comes with AI-based DDoS protection, automatic patching, firewalls, and end-to-end encryption to meet the increasing cyber threats of 2025. Benefits of Cloud VPS Hosting with SEOHostKing Ultra-Fast SSD NVMe Storage Enjoy 10x faster data access, low read/write latency, and superior performance for databases and dynamic websites. Dedicated IPv4/IPv6 Addresses Each VPS instance receives its own IPs for full control, SEO flexibility, and better email deliverability. Root Access and Full Control SEOHostKing offers root-level SSH access, so you can install any software, configure firewalls, or optimize the server at your will. Automated Daily Backups Your data is your business. Enjoy daily backups with one-click restoration to eliminate risks. 24/7 Expert Support Get support from VPS professionals with instant response, ticket escalation, and system monitoring—available around the clock. Use Cases for Cloud VPS Hosting in 2025 eCommerce Websites Run WooCommerce, Magento, or Shopify-like custom stores on isolated environments with strong uptime guarantees and transaction-speed optimization. SaaS Platforms Deploy microservices, API endpoints, or full-scale SaaS applications using scalable VPS nodes with Docker and Kubernetes-ready support. WordPress Hosting at Scale Run multiple WordPress sites, high-traffic blogs, and landing pages with isolated resources and one-click staging environments. Proxy Servers and VPNs Use VPS instances for private proxies, rotating proxy servers, or encrypted VPNs for privacy-conscious users. Game Server Hosting Host Minecraft, Rust, or custom gaming servers on high-CPU VPS plans with dedicated bandwidth and GPU-optimized add-ons. Forex Trading and Bots Deploy MT5, expert advisors, and trading bots on low-latency VPS nodes connected to Tier 1 financial hubs for instant execution. AI & Machine Learning Applications Run ML models, data training processes, and deep learning algorithms with GPU-ready VPS nodes and Python-friendly environments. How to Get Started with Cloud VPS Hosting on SEOHostKing Step 1: Choose Your Ideal VPS Plan Select from optimized VPS plans based on CPU cores, memory, bandwidth, and disk space. For developers, choose a minimal OS template. For businesses, go for cPanel or Plesk-based configurations. Step 2: Select Your Server Location Pick from global data centers such as the US, UK, Germany, Singapore, or the UAE for latency-focused deployment. Step 3: Configure Your OS and Add-ons Choose between Linux (Ubuntu, CentOS, AlmaLinux, Debian) or Windows Server (2019/2022) along with optional backups, cPanel, LiteSpeed, or GPU add-ons. Step 4: Launch Your VPS in Seconds Your VPS is auto-deployed in under 60 seconds with full root access and login credentials sent directly to your dashboard. Step 5: Optimize Your Cloud VPS Install web servers like Apache or Nginx, set up firewalls, enable fail2ban, configure caching, and use CDN integration for top-tier speed and security. Features That Make SEOHostKing Cloud VPS #1 in 2025

Self-Healing Hardware Intelligent hardware failure detection with real-time automatic migration of your VPS to healthy nodes with zero downtime. AI Resource Optimization Machine learning adjusts memory and CPU allocation based on predictive workload behavior, minimizing resource waste. Custom ISO Support Install your own operating systems, recovery environments, or penetration testing tools from uploaded ISO files. Integrated Firewall and Anti-Bot Protection Protect websites from automated bots, brute force attacks, and injections with built-in AI firewall logic. One-Click OS Reinstallation Reinstall your OS or template with a single click when you need a clean slate or configuration reset. Managed vs Unmanaged Cloud VPS Hosting Unmanaged VPS Hosting Ideal for developers, sysadmins, or users who need total control. You handle OS, updates, security patches, and application configuration. Managed VPS Hosting Perfect for businesses or beginners. SEOHostKing handles software installation, server updates, security hardening, and 24/7 monitoring. How to Secure Your Cloud VPS in 2025 Enable SSH Key Authentication Use SSH key pairs instead of passwords for better login security and brute-force protection. Keep Your Software Updated Apply security patches and system updates regularly to close vulnerabilities exploited by hackers. Use UFW or CSF Firewall Rules Limit open ports and restrict traffic to only necessary services, reducing attack surfaces. Monitor Logs and Alerts Use logwatch or fail2ban to track suspicious login attempts, port scanning, or abnormal resource usage. Use Backups and Snapshots Schedule automatic backups and use point-in-time snapshots before major upgrades or changes. Best Operating Systems for Cloud VPS in 2025 Ubuntu 24.04 LTS Perfect for developers and modern web applications with access to the latest packages. AlmaLinux 9 Stable, enterprise-grade CentOS alternative compatible with cPanel and other control panels. Debian 12 Rock-solid performance with minimal resource usage for minimalistic deployments. Windows Server 2022 Supports ASP.NET, MSSQL, and remote desktop applications for Windows-specific environments. Performance Benchmarks for Cloud VPS Hosting Website Load Time Under 1.2 seconds for optimized WordPress and Laravel websites with CDN and cache. Database Speed MySQL transactions complete 45% faster with SSD-NVMe storage on SEOHostKing Cloud VPS. Uptime and Availability 99.99% SLA-backed uptime with proactive failure detection and automatic failover systems. Latency & Response Time Average response times below 50ms when hosted in geo-targeted locations near the end user. How Cloud VPS Differs from Other Hosting Types Cloud VPS vs Shared Hosting VPS has dedicated resources and isolation while shared hosting shares CPU/memory with hundreds of users. Cloud VPS vs Dedicated Server VPS provides better flexibility, scalability, and cost-efficiency than traditional physical servers. Cloud VPS vs Cloud Hosting Cloud VPS offers more control and root access, while generic cloud hosting is often limited in configurability. Why SEOHostKing Cloud VPS Hosting Leads in 2025 Transparent Pricing No hidden costs or upsells—simple billing based on resources and usage. Developer-First Infrastructure With APIs, Git integration, staging environments, and CLI tools, it's built for real developers. Enterprise-Grade Network 10 Gbps connectivity, Tier 1 providers, and anti-DDoS systems built directly into the backbone. Green Energy Hosting All data centers are carbon-neutral, with renewable power and efficient cooling systems. Use Cloud VPS to Host Anything in 2025 Web Apps and Portfolios Host your resume, portfolios, client work, or personal websites with blazing-fast speeds. Corporate Intranet and File Servers Create secure internal company environments with Nextcloud, OnlyOffice, or SFTP setups. Dev/Test Environments Spin up a test environment instantly to stage deployments, run QA processes, or experiment with new stacks. Media Streaming Platforms Host video or audio streaming servers using Wowza, Icecast, or RTMP-ready software. Best Practices for Optimizing Cloud VPS Use a Content Delivery Network (CDN) Serve static content from edge locations worldwide to reduce bandwidth and load times. Install LiteSpeed or OpenLiteSpeed Boost performance for WordPress and PHP apps with HTTP/3 support and advanced caching. Use Object Caching (Redis/Memcached) Offload database queries for faster application processing and better scalability. Compress Images and Enable GZIP Save bandwidth and improve load times with server-side compression and caching headers.

Cloud VPS server hosting in 2025 is no longer a premium—it’s the new standard for performance, scalability, and control. With SEOHostKing leading the way, businesses and developers can deploy fast, secure, and reliable virtual servers with confidence. Whether you're launching a project, scaling an enterprise, or securing your digital presence, Cloud VPS with SEOHostKing is the ultimate hosting solution in 2025. Read the full article
0 notes