#Advanced Alert Rule Engine
Explore tagged Tumblr posts
Text
Dunebells: Smart Safety & IoT Automation for Modern Industries
Dunebells by DuneMatrix is an advanced IoT-enabled platform designed to enhance safety, streamline operations, and drive efficiency in industrial environments. Leveraging AI-driven analytics and real-time monitoring, Dunebells provides a comprehensive suite of tools to proactively manage risks and ensure compliance.

Schedule for a Free Demo Today!
Contact Information:
Website: https://www.dunematrix.tech/dunebells
Email: [email protected]
Phone: +971-505546070
#AI-Powered Safety Analysis#Advanced Alert Rule Engine#Command Center Application#Dynamic Ticket Workflow#•#IoT-Connected Smart Buildings
0 notes
Note
i’m sure you get a lot of requests, so totally understandable if you don’t want to write this,
but how about Season7 Hotch x younger but taller male reader who’s basically garcia’s substitute but usually in other units, and no one know they’re dating til on an away case, where Garcia couldn’t be with them, reader and Hotch fall asleep together on the way back on the jet (they think everyone else is asleep) and that’s how the team finds out
next time reader meets garcia she’s like “why didn’t you tell me?”
Tea Spilled Above 30,000 Feet

Pairing: Aaron Hotchner x Male! Reader
Word Count: 1.4k+
DNI: Fem-aligned
Author's Note: Shoutout to Penelope Garcia for being the patron saint of dramatic confrontations in combat boots, she's a queen and we love her. 💖
Baaaack from holiday ;P I was lowkey thinking about this the whole time on the plane trip back... snuggle snuggle, hope you enjoy this!! This is definitely one of my shorter fics, I apologize in advance 😞

You weren’t supposed to fall asleep.
That was the number one rule when you worked for the Bureau—always be alert, especially around the Behavioral Analysis Unit. The profilers noticed everything. The smallest glance. A twitch of a smile. The weight behind a silence. You’d known this. You’d warned yourself. And yet, exhaustion had its own gravitational pull, and sometime after wheels-up—you’d drifted.
Your head had found the slope of Aaron’s shoulder, warm and steady beneath your temple. Despite being the taller of the two of you, you'd folded down into his side like muscle memory—like gravity always knew where you belonged. The scent of him—clean, like pressed shirts and aftershave—had dulled your thoughts until everything else fell away.
Now, his cheek was nestled against the crown of your hair, his breathing deep and unhurried. One arm lay draped over the shared blanket stretched across both your laps, a quiet tether. Not clenched. Not possessive. But there. And undeniably intimate.
You didn’t realize you'd been caught until the jet’s engines shifted pitch, prepping for descent, and you blinked awake into a room saturated with knowing silence.
Rossi peered at you over the top of his novel, mouth quirked in that infuriating, all-knowing half-smile he reserved for gossip and grandchildren. JJ had one earbud out and both brows arched—half delighted, half scandalized. Spencer was gripping his book like it might anchor him, but you watched him turn the same page four times, eyes unfocused. And Emily—dear God, Emily Prentiss—sat across the aisle, arms crossed, lips pursed in a look that positively dripped with gleeful conspiracy.
Your blood turned to static.
You shifted slightly. Carefully. As if the whole scene might shatter if you moved too fast. But Aaron didn’t stir. His fingers—half-hidden under the edge of the blanket—brushed yours in a lazy, familiar glide that made your chest throb.
You tried, valiantly, for damage control. “We were just—”
“You’re dating,” Spencer blurted, too loudly. His voice cracked at the end. “You’re—together. That’s what this is.”
JJ blinked. “Wait, what? Who’s dating?”
Rossi didn’t look up from his page. “Hotch and the tall drink of sarcasm,” he said smoothly, flicking a page over. “Though apparently not just sarcasm. Man’s got enough leg to qualify for the NBA.”
Aaron stirred at last, eyelids heavy as he sat up with a soft groan, one hand rubbing at the base of his neck. He glanced at you first—still half-asleep—then looked around and froze.
“How long were we asleep?” he asked, voice low and scratchy.
Prentiss gestured at the two of you like she was presenting evidence to a jury. “Long enough for Reid to connect the dots, Rossi to make jokes, and JJ to quietly lose her mind.”
“I am losing my mind,” JJ admitted, leaning across the aisle. “Do you have any idea how domestic you looked?”
“I’m not spiraling,” Reid mumbled, defensive. “I’m processing. There's a difference.”
Aaron rubbed his temples, the weight of it all landing in his posture. “Well,” he muttered, “I suppose there’s no point in denying it now.”
“You think?” JJ said, laughing incredulously. “That was the most romantic use of a government-issued blanket I’ve ever seen.”
Aaron exhaled, already pulling back. His hand left yours beneath the blanket—and he straightened his tie with military precision. Not brusquely, but with intent. Practice. The same muscle memory he used to rebuild his walls.
You mirrored him, sitting upright and smoothing down the front of your shirt like it might erase the impression of his warmth from your skin.
No one said much after that.
The descent into Virginia was smooth, but the silence had a weight to it—less judgment, more curiosity. A new kind of attention. One you hadn’t prepared for.
By the time the jet touched down and the team filed off, you were no longer just Garcia’s occasional stand-in from Cyber Crimes. You were something else entirely now. Something… known.
You didn't talk about it. Neither did Hotch. Not in the car. Not in the elevator. Not even when he brushed his fingers against yours in parting outside the glass doors of Quantico, eyes soft and private in a way no one else ever got to see.
But the look he gave you said everything.
And the one you got the next morning?
That said you were screwed.
You were halfway through updating Garcia’s interface subroutines—tweaking her customized threat-detection algorithm to flag linguistic red flags in private message servers—when the rhythmic click-clack of combat boots struck the linoleum behind you like an incoming storm.
You didn’t even have time to turn around.
“…You absolute traitor.”
The voice was honey-dipped rage. Warm, theatrical, and furious. You froze, fingers still hovering over your keyboard as a familiar blur of pink, lemon, and rhinestones materialized at your side like a sequined banshee of justice.
Penelope Garcia stood over you, resplendent in a bubblegum-pink polka dot dress with a matching yellow cropped blazer, a glittering chaos of bangles jangling on both wrists. Her cat-eye glasses were framed by furious lashes, and her rhinestone barrettes—six of them—gleamed like the medals of a woman who had survived your betrayal.
You turned slowly, like someone facing down the executioner.
“Pen—”
She jabbed a manicured finger at your chest. “You were sneaking around with Hotch. Hotch.” The name landed like an accusation, syllables sharp. “You. You beautiful, lying, under-caffeinated Benedict Arnold—how long?! You’re six-foot-something and you still managed to sneak around behind my back?”
You blinked. “Since… San Diego. About six months.”
Garcia’s eyes widened. Her mouth opened. No sound came out.
Then—“SIX-!! SIX MONTHS?”
Her voice cracked like thunder in a library, echoing off the tech bullpen walls. Several heads turned. You winced.
She immediately dropped her volume to a hiss. “Six months?! You were literally canoodling while I was giving him spreadsheet updates and sending you both my little winky-face gifs with the hearts! Do you know how many times I’ve played accidental Cupid while you two were out there playing star-crossed lovers in FBI Kevlar?!”
You bit your lip, trying not to laugh. “..We noticed.”
Garcia let out a choked gasp. “Noticed?! You… vultures. Emotional vultures. I liked you. I trusted you. I let you into my precious baby databases! You helped me name the new server cluster and everything!”
“‘Clusterfluff,’” you murmured fondly.
“Don’t you dare weaponize our sacred in-jokes against me right now,” she snapped, spinning in a full circle, arms flailing dramatically. “You and Aaron Hotchner—Mister I-Don’t-Smile-At-Anyone-Unless-It’s-Jack—have been making googly eyes across agency lines while I’ve been out here thinking I was the one getting the secret winks?!”
“I mean,” you said, slowly raising your hands in mock surrender, “if it helps, he was the one who fell first.”
Silence.
Garcia froze mid-pace. Her head tilted, eyes narrowing like a cat who just spotted a thread out of place.
“…What?”
You nodded solemnly. “I was all professionalism. He was the one giving me extra coffee at 2 a.m. debriefs and calling me by my first name when no one else was around. I didn’t even realize until the San Diego case when he got jealous of the local liaison trying to flirt with me.”
Her eyes widened to the size of saucers. “Hotch got jealous? Like, clench-jaw, death-glare, micro-aggression jealous?”
“Oh yeah,” you said. “Classic ‘if looks could kill’ scenario. He adjusted his tie five times in one conversation.”
Garcia’s jaw dropped. Her betrayal cracked under the weight of new gossip. She stared at you like she was seeing the Mona Lisa blink.
Then she gasped.
A full, delighted, hands-to-her-chest gasp.
“Tell. Me. Everything.”
You grinned, spinning your chair to face her fully. “You want chronologically or thematically?”
She dropped into the chair beside you like a queen on a throne. “Give me the Netflix original limited series version. I want the drama. I want the angst. I want to know if he’s as brooding in bed as he is in briefings.”
You smirked, lightly flushed int the face at her words, dragging your keyboard closer to pause your work. “You’re going to need coffee.”
She grabbed your wrist. “I’m going to need a three-course meal and a glass of wine. And if you leave anything out, I will hack your inbox and read it for myself.”
You leaned in conspiratorially. “..That’s fair.”
#criminal minds#criminal minds imagine#x male reader#x gn reader#x reader#aaron hotchner x you#aaron hotchner x reader#aaron hotchner#aaron hotchner x male reader#Seventh Writes
77 notes
·
View notes
Text
If SkyNani ever chooses to do BL, they should do something like The Hunter Wants to Live Quietly (novel, manhwa) or Semantic Error (novel, manhwa, kdrama).


Personally, I prefer the former as it's fantasy genre, it's action-packed, and I just want to see SkyNani in a show with amazing world building. However, SkyNani also reminds me so much of JaeyongxSangwoo in terms of personality and they already got the chemistry to pull it off.
The Hunter Wants to Live Quietly Synopsis:
Hunter Cha Eui-jae, who was dispatched to seal a rift that appeared over the West Sea, was flung out as soon as he closed the rift. When he came to his senses, he was lying in a garbage dump. Starving, he was drawn like a zombie is to blood to a hangover soup restaurant, where he realized that he had fallen into South Korea, eight years in the future. In this era, disaster alerts notify people of rift openings in advance, ASMR videos of slimes gathered from dungeons were trending, and idle hunters livestream unboxings of A-rank longswords. Unlike the past, where people trembled in fear of an impending apocalypse, the future was surprisingly peaceful, leaving Cha Eui-jae feeling empty. Since things had turned out this way, why not start a second chapter of life as a part-timer at the hangover soup restaurant, rather than being a hunter? “That’s strange.” “…” “Have we met somewhere before?” Cha Eui-jae’s plan to quietly spend his remaining days as the only part-time worker at the decades-old hangover soup restaurant goes awry when he encounters a mysterious, gas-masked individual…
Semantic Error Synopsis:
Computer science major Chu Sangwoo is the epitome of an inflexible and strict rule-abiding person. While working on a liberal arts group project with freeloaders who don’t put in any effort, Sangwoo reasonably decides to remove their names from the final presentation. But he didn’t imagine how involved he would become with the person whose study-abroad plans were messed up because of that project. The involved person: the campus star who everyone knows, Department of Design’s Jang Jaeyoung. He has everything from skills, looks, family background, and good relationships except for 1 big problem: Chu Sangwoo. What happens when an engineer and an artist whose personalities are like oil and water have to work together? Jang Jaeyoung is like a semantic error in the perfect world of Chu Sangwoo. Will Sangwoo be able to debug this?
Confession: As someone who has read both the SE novel and manhwa before watching the show, I didn't enjoy the kdrama that much haha. Much of drama was definitely left out due to lack of episodes and Sangwoo isn't as 'weird' in the show as he is in the novel/manhwa.
#semantic error#the hunter who wants to live quietly#skynani#this is an excuse to gush over my favorite BL manhwas and be delusional about SkyNani at the same time
14 notes
·
View notes
Note
Mr Morgan, how do you feel about the current state of F1 driving - and how much did it change since the year you retired?

"i ain’t got much to gripe ‘bout with the current grid. every one of those drivers has talent and real potential. i’m even pretty close with a few of 'em, like hamilton, alonso, and verstappen. there are some younger fellas out there too, and i just hope they keep their heads on straight as they keep movin’ forward” he admitted, letting out a heavy sigh after a brief pause “a lot has changed since my time. the first thin’ that comes to mind is definitely digital tools, like ai and simulators is a game changer for car development and race strategy. new circuits - i would've loved to have raced on some of those tracks. driver fitness and mental preparation have intensified too, psychological support is essential, and I’m glad they’re finally givin’ it the attention it deserves” a longer pause this time “f1’s come a lon’ way, changin’ the sport in ways i couldn’t have imagined. these hybrid engines have really pushed what’s possible in engineerin’, and with all the new rules, it’s not just ‘bout speed ‘nymore - it’s ‘bout makin’ sure the cars last. aerodynamics have gotten more advanced, and now sustainability is a big focus, with the fia aimin’ for net zero carbon by 2030 and pushin’ for greener tech. cost caps have also made things fairer for ‘veryone. it’s not just ‘bout buildin’ the fastest car ‘nymore, it’s smart spendin’ and connectin’ with a more diverse fanbase” concluded, not holding back a soft chuckle “sorry, nerd alert”
2 notes
·
View notes
Text
Where the Sunlight Falls
[WISE’s story from the second novel. This is a revision of my older translation, formerly titled ‘In the Place Where the Sun Hits,’ which is still available here if you’d rather read that version instead for some reason.]
The one who was the closest person to Miroku Amagi said “I don’t want to turn into the evil monster.” Miroku feels the unspeakable pain inside every time he recalls that.
The stage wasn't Japan, but a country somewhere far to the north. Two black shadows were advancing across a pure white field of snow. One was a young man, slightly past the age of twenty. His clothes were those worn by security guards at a certain research institute located in that country. The other was a girl, walking while he led her by the hand. Her once beautiful black hair had lost all of its vitality, her cheeks were hollow, and a countless number of scars peeked out from beneath the winter coat he had dressed her in. Underneath the coat, she wore a simple white gown, standard wear for all specimens at the research institute they came from. The girl was a Psychicer, someone born with special powers. This had caught the military's eye and they'd forcibly taken her to a research laboratory; with no regard to her humanity, they conducted experiments on her that would be unfathomable to those of sound mind. The countless amount of scars engraved into her body were from injuries she sustained from the cruelty of the experiments, wounds she'd inflicted upon herself from being driven to the brink, and–––surgical scars from "when they had opened her up in order to take out one portion of her internal organs and then closed her back up.” Her mind was as good as dead, her eyes stagnant, and she had no decently functioning thought process.
The young man was a security guard for the research laboratory and took care of her. Day after day he’d watched her waste away, and one day he couldn’t take it anymore–––he led her escape by putting her into a large bag from where garbage was to be collected and got her onto one of the delivery trucks with him, his ultimate plan being to flee to the border. No matter where they ran in this country ruled by a military regime, they’d still be brought back, without fail. She would once again be subjected to hellish experiments, and he would surely be killed for attempting to escape. However, right before they reached the border, the old, battered truck he stole began having engine trouble and broke down. "It's just a little bit farther…so please hang in there…!” "…" The young man pressed on across the snow field that even an adult would have difficulty traversing, giving her words of encouragement all the way. The girl didn't answer. She no longer had the “wherewithal” within her to answer. But even so, she gripped the hand she held tighter in return. "…" The young man bit his lip. Within him, he harbored a sense of responsibility to make sure he saved her, a sense of urgency at the possibility that the research lab had already sent someone after them, and one more, different feeling as well. Vrrrrr…n From far, far, far beyond the horizon came the sound of engines, approaching like the growling of hounds. It was the sound of the snowmobiles this country’s army utilized to move on top of the snow. The young man panicked and tugged the girl's arm closer to himself; despite his efforts to move faster, the accumulated snow was too deep and impeded their ability to advance. All the while, the sound of the engines grew closer and closer. The young man had no idea. They had implanted a transmitter inside the girl’s body that alerted them immediately if she escaped. “We’re almost there…almost there…” He repeated those words over and over, as if they were a holy mantra to ward off the Devil. But an even crueler reality descended from the skies, as if to trample those prayers back to Earth. From up above came a military helicopter, whipping up violent winds. Light machine gun fire felled some conifers growing just a short distance away from the two. They clearly missed on purpose, most likely to give something of a final warning. If the young man's eyes were a bit better, he would've been able to see the warped smile of the soldier sitting in the helicopter's cockpit. The orders from the commander had been: “If possible, capture them right before they attain their escape.” To run and run and run, until freedom is just a hair’s breadth away. There was no better way to deter this from happening again than to crush them with despair right on the cusp of reaching their hope. Additionally, the soldiers received orders that "the young man didn't have to be brought back." “Kill him as brutally and cruelly as you can before the girl's eyes." They were well-versed in the torturous methods needed to carry out such orders. And if they left the corpse, the starving wolves would clean everything up by Spring. "No…we've come this far…" The young man pulled the girl closer to himself, holding her to his chest. As expected, the girl showed no reaction–––no, that wasn’t the case at all. She was trembling. It wasn't just from the cold. She was terrified. They may have rendered her mind as good as dead, but she was still plagued by a fear carved all the way into her bone marrow. "Uu…" The man bit his lip once again. It was in anger, sadness, and regret; but again in one other, different feeling as well, beneath it all. Guided by the helicopter, the snowmobiles closed in on them from behind. There were no places to hide on such a vast field of snow and they were trapped in between pursuers from both land and sky. By all common sense, it was impossible for them to plausibly escape. However, in this world, there were those who transcended common sense and universal principles. "–––!?" Suddenly, darkness gouged the sky. If was as if the hand of an invisible giant had plucked out a portion of the blue sky, compressing all of the sunlight into a single point with a terrific strength. The soldiers and pilot could only stare up at it in awe, stunned. But to say the situation that happened afterwards was the young man's fault was a bit harsh. Was it even in the realm of imagination? To think that there existed someone who could distort and compress even the light with his powerful, too powerful, telekinesis––– "Nichirin 'Tentsui'–––" At some point, a muscular man had appeared; he spoke these words as if bringing down judgement from the heavens and swung his left arm downwards. In the next instant, all of the compressed light and heat shot down like pillars connecting Heaven and Earth, and the military helicopter exploded into pieces in the blink of an eye. The name of the one who'd appeared was Grana–––an imposing paragon of a man, almost like a demigod crushing an irredeemable beast underfoot.* Everything had been turned on its head just like that. The pursuit squadron had no chance of winning, even if they were to gather all of their remaining forces in the area. Even inflicting a scratch would be a great accomplishment. Grana was just that powerful, had the intelligence to use his power to the fullest. In spite of this, the soldiers raised their voices and readied their rifles. If they revved up the engines on their prized snowmobiles and turned tail immediately, Grana had no intention of chasing them. But that might have been a tall order in itself. Turning one’s back to someone with an overwhelming amount of power took courage. The cause of their deaths could be attributed to the fact that their small amount of courage wasn’t enough. Shing–––… If it was to be expressed with a sound, it was that. To be accurate, there was no sound when he swung his blade seriously. No, he even cut through sound. It was like a god had drawn a line in the airspace, splitting every single soldier in half and ending their lives. The spray of blood dyed the snow field in red. The rampaging snowmobiles crashed into one another, the random shower of bullets tearing into the engines, and from the explosions and flames that resulted appeared another young man. Junas–––the man who possessed the power of "God Blade." That ability was true to its name: there was nothing in the world it couldn't cut. "Y-You guys are…" All the young man could do was watch everything play out from start to finish, holding the girl close to himself. And even that might've only been because he'd forgotten to blink. Junas and Grana stood several meters apart before the two of them, silent, as if in some predetermined position. "…?" The air distorted. In that space, where there had been nothing up until now, two more men appeared. One was a beautiful young man, wearing a gentle smile on his lips. And the other, who stood in front––– "So you're the one…who called us…" He was tall and lean, attractive in a different way from the one behind him. When this man stood before him, the young man was struck by the feeling of looking up at a religious painting. A man accompanied by two mighty demigods and an attendant at his side. An immense presence, like that of a god's. "Y-Yeah…so you guys…are W.I.S.E…right?” He frantically wrung out his words. W.I.S.E–––the first-ever terrorist group comprised of those with special powers, who had driven Japan to the brink of destruction…or so they were recorded as nowadays. But the man standing before him–––this young man who was the head of W.I.S.E, Amagi Miroku–––appeared nothing like such a "human" existence as a terrorist. He seemed more like something from a different dimension, a different entity entirely. "Th-This girl…please, take good care of her…she's…just like you guys…" He entrusted the girl to Miroku with such care, more than he would even if it were his own daughter, as if he was extending her as an offering. Miroku’s brow quivered slightly, but he accepted her immediately and took a careful look over her condition. "Take her away…" "Yes." The youth waiting at Miroku’s side like his attendant–––his name was Shiner, and his ability of "Teleportation" allowed him to cross long distances in no more than a single step. It was because of his ability that everyone was dressed in lightweight clothes, like they’d only just walked out past the threshold of their house. This oddity only served to further demonstrate the truth of how different a world they lived in compared to the young man. Shiner took the girl and, with only a faint sound of the air oscillating left behind, disappeared to somewhere. "…Haa." The young man could finally let out a sigh of relief. He didn’t think he’d stage an escape without any plan whatsoever. W.I.S.E was an organization that advocated and stood for the "liberation of those with special powers.” He’d relayed to them the existence of the research laboratory beforehand, secretly, and also the fact that there was an imprisoned girl he wanted to entrust to them. He never received any response back; it had been a gamble on whether or not they'd show, but he'd drawn the winning ticket in the end.

With this, he'd finally fulfilled his duty. But there was still one thing he needed to do. "Please wait…" The young man spoke out to Miroku's group as they made to leave. To Amagi Miroku, who looked back silently and expressionlessly, he said this. He said it as if pleading. He said it as if condemning.** "Please…kill me…"
The young man acted as the girl’s keeper. He brought meals to her and stood watch over the cramped cell they’d tossed her into; in the morning he would take her to the experimentation room, and at night he would return with her on his back and tuck her into bed. At the start, she screamed and cried, wailed and fought back. But days upon days of excruciating experiments gradually wore her heart down. She stopped eating, stopped speaking, grew visibly emaciated, and eventually she even attempted suicide. If she died for a reason other than the experiments, it would be on his shoulders. Therefore, he told her a lie. "This is just between you and me, but if you can endure their experiments for one year, they’ll let you go back home." One year––– In a mere week they conducted experiments akin to torture, enough to make a young girl choose death and “break” the spirit of a full-grown adult. To endure it for one year was absolutely impossible. That was why he designated that amount of time. At the very least, he could provide her with a fleeting hope right up until she died and the experiments could proceed smoothly. That was the only reason he told that lie. The girl was shocked, then overjoyed. She could escape from this hell. She could return to her parents. With a smile that stretched across her whole face, she told the young man, "Thank you." And so, she continued to endure it. She was battered, wounded, crying, and yet she still continued to endure. When the experiments would finish and she was being returned to her cell, she'd always ask the young man: "How many more days?" Ten days went by. A month went by. Half a year went by. Ten months went by. The girl continued to endure, to the researchers’ bewilderment. "How many more days?" She asked the young man this, with dim consciousness.
"That girl…believed in me…believed in my words, and continued to endure that living hell…words I only said because I figured she’d die anyways, and she believed them…and I became scared. Of betraying her, of her thinking I betrayed her…” As ten days before the deadline he’d given her approached, the young man found his resolve. "It was ten days…ten days until it was up…she’d finally made it that far…why didn’t I, sooner…that girl spent over three hundred days…if I was going to do something, then why wasn't it…why not until now…I'm worthless…!” The young man fell to the snowy ground and wailed. The feeling he’d been hiding from the girl–––it was “guilt." Miroku said nothing and simply looked down upon him. It was a spectacle that resembled God overseeing the confessions of a transgressor. "That's why…it'd be better if I was dead…" However, it wasn’t forgiveness that the young man desired. He knew more than anyone else that he was unforgivable. A sinner had to accept his punishment. "If it was possible…I think she…should be the one to kill me…but…in her current state, there’s no way she could…that's why, please, kill me…for her…” The young man pressed his head to the snow field, imploring his own death from the bottom of his heart. If he didn't, he felt he'd be crushed by the weight of his sins. "Do you…not need your life…?" Amagi Miroku asked this quietly, in a voice that abandoned emotion. As if he was asking for the final confirmation. "Yeah…a life like mine…is better off gone…” The young man answered as if spitting up blood. "Very well. If you truly do not need it, then I shall take it."
Izu–––Tenjuin Elmore's mansion. Her estate boasted a vast amount of land, and over in the south-east, facing the sea, was a patch of woods; a small annex had been built there and housed a single woman. She’d never exchanged words with the ones living in the mansion. She wasn't refusing to. And it wasn't because her childhood was a bit different from other people’s or because she was bad at talking with people. Her mouth didn’t work. She had spent over a decade at a research institute called Grigori, where they’d treated her as a test subject. After the establishment had been destroyed, due to certain events, she was nothing more than an inconvenience and was shipped off to an isolated facility for Psychicers on Mukurojima–––otherwise known as "Home."*** She couldn’t really remember how many years she’d spent there. It could’ve been one year or two she floated within her capsule, but then a boy appeared before her. "Let's go…together." That boy's name was Yoshina Ageha. She was once an existence known as Grigori #07. In another timeline, as “Nemesis Q,” she was a being that led many Psyren Drifters to the world of ten years in the future. But now, she merely lived a quiet life here. Due to the repeated experiments she underwent and her “preservation” in that capsule, it was difficult for her to move around without using a wheelchair and she even lost her ability to speak. But her power as a Psychicer was a cut above even the other Grigori test subjects. She came to understandings with others via telepathy and she had an autonomous Program–––a pseudo-existence dubbed "Klutzy Q" by Yoshina Ageha in another future–––take care of things around her, so she didn't feel her everyday life was that inconvenient. On the contrary, her daily life was leisurely and all she could ever ask for; she’d taken to gardening, whether as a hobby or as a way to kill time, and lined the area around the annex with flowers. She’d even adopted three cats. Incidentally, these cats were strays that had wandered into Elmore's estate through a gap in the wall. One day, Kyle questioned her as she was reading a book on the terrace of the annex, as she always did. “You wanna go somewhere? Do something? Aren't you bored?"––– She thought it was an incredible misunderstanding. She had never, up until now, been able to live an ordinary, human life. She was never able to walk about outside as she pleased, or raise flowers, or touch other living creatures, or sleep without a machine on her head, or eat with a fork and knife instead of through a tube. To her, it was these “simple days” that were unfathomable, phenomenons of a different world entirely, and she could not ask for more. “I don’t require any gratuitous concern. I'm already doing what I please." That was how she replied to the question, without turning her gaze from the pages of her book. After giving that response, she felt a little bit disconcerted. Everyone in the mansion sympathized with her circumstances and treated her well. Marie's cooking was improving with each day that passed, and Shao would find books he thought she'd like and bring them to her. Kyle and Frederica were both somewhat noisy, but they helped her with tending the garden. Van would close off his heart for reasons different from hers, but it was for that reason that she didn’t think him the most unpleasant to be near. While she was nose deep in her book, he'd stay by her and play with the cats wordlessly. When he grew exhausted and fell asleep, she commanded Klutzy Q to cover him with a blanket. That was all it was, but strangely enough she felt her heart easing up. She did think that she should be a little friendlier to them, but she’d blocked off all of her emotions in order to bear the suffering she endured at the laboratory. She was always expressionless and couldn’t even form a smile unless she put in the effort to. But any smile she produced was robotic, cold and empty like that of a doll. (As I expected, there is no way…to regain a heart once lost, is there…) With such thoughts on her mind, she went out onto the terrace today, too, and flipped through the pages of her book. Her favorites were books on science, math and physics and quantum mechanics and the likes. Classic literature intricately depicted nuances of the human heart; she could read the words, but couldn’t understand the concepts. But for some reason, today was different from usual–––today she held an old picture book. A long, long time ago, back when she could still laugh naturally and before she had been taken to the laboratory, she had loved this picture book and read it again and again. She should’ve lost the ability to feel nostalgia, too. The thought that she’d somehow remembered such a human-like emotion while living a life under the sun made her laugh faintly at herself. That day, the wind blowing in from the sea was a bit strong.
~~~~~~ [Notes: *The words used for ‘demigod’ and ‘beast’ are specifically referencing the Buddhist concept of Samsara. ‘Demigod’ is 修羅 (shura), another word for Asura, as in the Asura realm. Worth noting that this is the same shura used in Grana’s epithet: Tenshura (天修羅, heavenly shura/carnage). ‘Beast’ is 畜生 (chikushou), as in the Animal realm. The Asura realm is considered one of the three ‘fortunate’ realms, while the Animal Realm is considered one of the three ‘unfortunate’ realms. **The two words used here are also legal terms: 訴える (uttaeru) and 告発 (kokuhatsu). 訴える means to sue, while more generally it means to seek help/sympathy from someone. 告発 means to whistleblow, while more generally it means to expose the existence of wrongdoing. ***Written as “Home For Those With Unusual Powers”]
| Part 2 →
2 notes
·
View notes
Text
How AI-Powered Real-time Analytics is Revolutionizing Bank Fraud Detection

The financial landscape is a high-stakes battlefield, and fraud is an ever-evolving adversary. Every year, banks globally lose billions to sophisticated scams, ranging from elaborate account takeovers and synthetic identity fraud to cunning phishing attempts and complex money laundering schemes. For too long, traditional, rule-based fraud detection systems have played a reactive game – catching fraud after it occurs, or generating so many false alarms that genuine threats get lost in the noise.
But as of 2025, the tide is turning. Artificial Intelligence (AI) and Machine Learning (ML), particularly when coupled with real-time analytics, are no longer just buzzwords; they are the most powerful weapons in a bank's arsenal, fundamentally transforming how financial fraud is detected and prevented.
The Limitations of Yesteryear's Defenses
Traditional fraud detection relies on static, predefined rules. For example: "Flag any transaction over ₹1,00,000" or "Alert if a card is used in two different countries within an hour." While foundational, these systems have critical weaknesses:
Rigid and Reactive: They can only catch known fraud patterns. New, evolving schemes easily bypass them.
Batch Processing: Many traditional systems analyze transactions in batches, meaning fraud can go undetected for hours, or even days, by which time the money is long gone.
High False Positives: Overly broad rules lead to frequent false alarms, disrupting legitimate customer transactions and causing "alert fatigue" for fraud analysts. This costs banks significant operational expenses and frustrates customers.
Data Silos: Lack of comprehensive data integration prevents a holistic view of customer behavior.
How AI/ML Supercharges Real-time Fraud Detection
AI-enabled real-time analytics represents a paradigm shift. Instead of static rules, these systems use dynamic, intelligent models that learn and adapt, analyzing transactions as they happen – often in milliseconds.
Behavioral Biometrics and Anomaly Detection: AI builds a unique "normal" profile for every customer, analyzing spending habits, typical transaction amounts, login times, device usage, geographic locations, and even keystroke dynamics. Any significant deviation from this learned baseline – say, a large transaction from an unusual location, or an online login from a new device after a quick succession of failed attempts – is immediately flagged as an anomaly.
Machine Learning Models:
Supervised Learning: Models are trained on vast historical datasets of both legitimate and fraudulent transactions. They learn to identify subtle patterns and indicators associated with fraud that humans might miss.
Unsupervised Learning: Crucially, these models can identify entirely new and unknown fraud patterns without prior examples. This is vital for detecting emerging zero-day fraud tactics.
Deep Learning & Graph Neural Networks: These advanced techniques can process highly complex, unstructured data (like text in customer service interactions or relationships in a network of accounts) to uncover sophisticated fraud rings that traditional methods couldn't even begin to trace. Graph analytics, in particular, excels at mapping connections between seemingly disparate entities, exposing coordinated attacks.
Real-time Processing and Decision Engines: The "real-time" aspect is key. Leveraging high-performance computing, AI systems can ingest and analyze millions of transactions per second. This enables instantaneous risk scoring and decision-making – approving, holding for review, or declining a transaction before it completes. This capability is especially critical for instant payment systems.
Tangible Benefits for Banks and Customers (as of 2025)
The impact of AI-enabled real-time analytics is profound:
Drastically Reduced Financial Losses: By catching fraud before funds are disbursed or transactions complete, banks prevent massive losses. Many institutions are reporting significant reductions (e.g., up to 60-70% in fraud losses and chargebacks).
Improved Customer Experience and Trust: Fewer legitimate transactions are declined or held for manual review. This means less friction for customers, leading to higher satisfaction and greater trust in their bank's security. This is often cited as a major benefit, with some banks reporting a 30% increase in customer trust.
Enhanced Operational Efficiency: AI automates the initial triage of alerts, sifting out false positives with high accuracy (some reports indicate a 50-60% reduction in false alarms). This frees up human fraud analysts to focus on genuinely high-risk cases and strategic investigations, optimizing resource allocation.
Dynamic Adaptability: Unlike static rules, AI models continuously learn from new data, evolving fraud patterns, and human feedback. This self-optimizing capability allows banks to stay ahead of sophisticated, constantly changing fraud tactics.
Proactive and Predictive Security: AI can analyze preemptive detection signals, such as unusual behavioral anomalies that might precede an actual attack, allowing for intervention even before fraud materializes.
Real-world Use Cases in Banking
AI-enabled real-time analytics is being applied across various fraud types:
Credit Card Fraud: Detecting unusual spending patterns (location, merchant, amount) for both card-present and card-not-present transactions instantly.
Online and Mobile Banking Fraud: Identifying account takeover attempts, phishing-related compromises, and unusual login behaviors (e.g., device changes, IP hopping, out-of-character transaction types).
Loan Application Fraud: Analyzing discrepancies in submitted documents, cross-referencing data points, and identifying patterns indicative of synthetic identities or false claims during the application process.
Money Laundering Detection (AML): While a distinct regulatory domain, AI significantly enhances the ability to detect complex, layered transactions indicative of illicit financial flows by identifying unusual patterns and networks.
Payment Gateway Fraud: Securing transactions across various digital payment rails, flagging suspicious payment requests or unusual transaction volumes.
Best Practices for Successful Implementation
Deploying AI for fraud detection is not without its challenges, but adhering to best practices ensures success:
High-Quality, Diverse Data: AI models are only as good as the data they're trained on. Banks must ensure access to vast, clean, and diverse datasets spanning transaction history, customer demographics, device data, and external threat intelligence.
Human-in-the-Loop: AI is an enabler, not a replacement. Human fraud analysts provide invaluable feedback for model refinement, handle complex edge cases, and make final decisions, especially in situations requiring regulatory judgment.
Explainable AI (XAI): For banks, understanding why an AI model flagged a transaction as fraudulent is critical. XAI techniques provide transparency, helping analysts investigate, ensure compliance, and build trust with regulators and customers.
Continuous Monitoring & Retraining: Fraudsters evolve. AI models must be continuously monitored for performance drift and retrained with the latest fraud patterns to maintain effectiveness.
Scalable Infrastructure: Real-time analytics requires robust, scalable infrastructure capable of processing immense volumes of data with ultra-low latency.
Regulatory Compliance: Banks must ensure their AI systems comply with data privacy regulations (e.g., GDPR, local data protection laws) and ethical AI guidelines, avoiding algorithmic bias.
The Proactive Future of Banking Security
In 2025, AI-enabled real-time analytics is no longer a competitive advantage; it's a strategic imperative for banks across the globe. It empowers financial institutions to move beyond simply reacting to threats. Instead, they can anticipate, intercept, and adapt to fraud with unprecedented precision and speed, safeguarding customer assets, preserving trust, and ensuring the integrity of the financial ecosystem. The future of secure banking is proactive, intelligent, and powered by AI.
0 notes
Text
⏱️ Automatically Stop Jira Sprints: Keep Your Agile Cadence Sharp
In the fast‑paced world of agile delivery, consistency is key. Yet manually closing sprints—especially when managing multiple teams—can be error‑prone and easy to overlook. Missed sprint closures lead to stale boards, inaccurate metrics, frustrated teams… and excuses like “Oops, I forgot.” But it doesn’t have to be this way.
The Problem: Manual Sprint Management = Risk & Overhead
Jira gives you the tools to define start and end dates during sprint creation. But it does not automatically execute them. That means someone has to:
Remember when sprints begin and end across all boards.
Close each sprint in time.
Manually move unfinished issues to the backlog or a new sprint.
Skipping any step can lead to cascading issues:
Velocity distortion if sprint transitions don’t happen cleanly.
Backlog bloat from incomplete issues left hanging.
Work interruptions since teams rely on refreshed sprint scopes.
The Solution: Automation to the Rescue
You have two solid ways to automate sprint closures:
🛠️ 1. Native Jira Automation
Jira’s built‑in automation engine allows you to create a rule such as:
Trigger: Scheduled (e.g., cron at 6 PM daily)
Condition: sprint in openSprints() AND endDate <= now()
Action: “Complete Sprint” + optional notifications
This setup checks for overdue sprints daily and closes any that have passed their end date. You can also chain actions like sending emails or moving unfinished issues automatically reddit.com+15medium.com+15ravisagar.in+15reddit.comatlassian.com.
📦 2. Third‑Party Apps (e.g., SprintRunner for Jira)
For larger organizations needing advanced control, apps like SprintRunner for Jira from Sparxsys Solutions offer:
Schedule-based auto start and stop
Bulk multi‑board operations
Audit logging (who/when)
Smart handling of unfinished issues (backlog, next sprint, new sprint)
Easy configuration directly from board/backlog UI youtube.com+7marketplace.atlassian.com+7medium.com+7medium.com
A direct walkthrough on Medium also explains quick setup with cron expressions. For example:
Admin console → Sprint Runner → “Schedules”
Name: “End Friday Sprints”
Cron: 0 17 * * FRI (5 PM every Friday)
Target: Boards
Action: “Stop Sprint” + notification ≫ done medium.com
🔧 Best Practices for Automatic Sprint Stop
Define expectations – e.g., “Sprints end Fridays at 5 PM IST.” Align team norms before automating.
Add buffer time, if needed — e.g., schedule automation at 6 PM to allow last‑minute wrap‑ups.
Manage issue rollover – Decide ahead: unfinished issues to backlog, next sprint, or brand‑new sprint.
Notify stakeholders – Send Slack/email alerts with sprint reports or links to the newly opened scrum board.
Capture metrics – Use audit logs or post‑close triggers to snapshot velocity, incomplete‑issue count.
Test in staging – Use a demo board to verify behavior before enabling in production.
🧭 Who Should Use Automatic Sprint Stop?
Small and mid‑sized teams scaling agile: lets teams focus on delivery, not chores.
Enterprise organizations with multiple boards — ensures consistency and daily hygiene.
Scaled‑Agile environments (e.g., SAFe or LeSS): disciplined sprint cadence supports planning cycles.
Delivery leads and PMOs who rely on accurate sprint data for forecasting and reporting.
⚠️ Potential Pitfalls & How to Mitigate
Premature sprint closure: Validate cron schedule and board selections before activating.
Stuck issues: Ensure unfinished issues are dynamically handled via rollback or sprint‑to‑sprint logic.
Confusing notifications: Include context like “Sprint 42 closed by automation. 3 issues rolled to backlog.”
Platform compatibility: Confirm your chosen app supports Jira Cloud vs. Data Center.
✅ How to Get Started Today
Define your sprint cadence (length, end time, buffer).
Set up a staging board in Jira to test.
Choose between:
Jira Automation (free, flexible, built‑in), or
SprintRunner for Jira (more powerful scheduling + audit) youtube.com+15marketplace.atlassian.com+15medium.com+15medium.com.
Build and test rules:
Cron trigger for closing
Condition: sprint end date passed
Actions: close sprint, move issues, notify teams
Pilot with one team, monitor logs and notifications.
Roll‑out across boards — keep refining based on feedback.
Audit regularly to ensure compliance and benefit continuity.
✨ Final Words
Automated sprint closure may seem minor, but it reinforces discipline, accuracy, and reliability across your agile lifecycle. Whether you use native Jira Automations or a robust app like SprintRunner, the outcome is the same: clean boards, reliable metrics, and teams free to focus on value delivery—not admin work.
The key? Clarity, testing, and rollout discipline. Define expecting, test in isolation, and scale once proven. In today’s agile world, smart automation like this is how you stop sprints—and start better delivery cycles.
0 notes
Text
The Future of Payroll: How Real-Time Calculations Are Revolutionizing Employee Compensation
In the dynamic world of modern business, payroll is no longer just about issuing paychecks at the end of the month. The landscape of employee compensation is evolving rapidly, driven by the growing demand for transparency, accuracy, compliance, and employee satisfaction. At the heart of this transformation lies real-time payroll calculation, a cutting-edge innovation that’s changing how companies manage compensation.
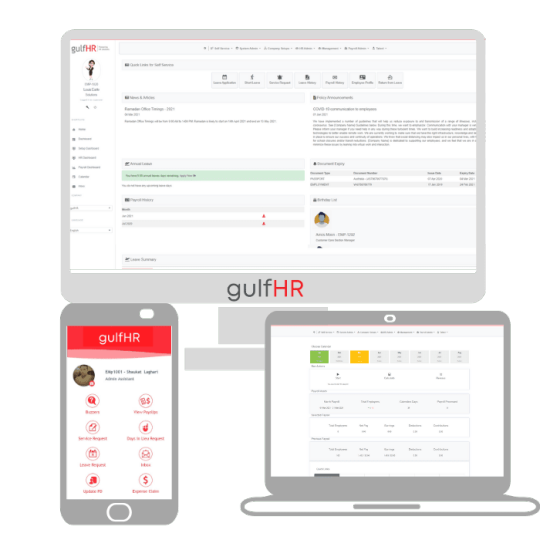
Real-time payroll, once considered a luxury, is now becoming a necessity. Leveraging the power of advanced payroll software, businesses—especially in fast-paced regions like the UAE—are reimagining payroll systems to ensure precision and speed.
What Is Real-Time Payroll Calculation?
Real-time payroll calculation refers to the continuous and automatic processing of payroll data as it is entered into the system. Instead of waiting for a monthly or bi-weekly payroll cycle, the software calculates earnings, taxes, deductions, and other payroll elements in real time.
This modern approach eliminates the lag between time worked and compensation calculated. Any change—such as a bonus, deduction, or leave—is immediately reflected in the employee's earnings profile.
Key Benefits of Real-Time Payroll
Enhanced Transparency and Trust: Employees gain access to their up-to-date pay information at any time. This transparency fosters trust and allows employees to better understand their compensation structure.
Improved Accuracy: Real-time payroll significantly reduces errors caused by manual entries or batch processing. Any discrepancies can be spotted and corrected instantly.
Regulatory Compliance: Especially in regions like the UAE, where labor laws and tax regulations frequently evolve, real-time payroll helps businesses stay compliant by immediately adjusting to legal updates.
Time and Cost Savings: By eliminating the need for repetitive manual tasks and end-of-cycle crunches, businesses save both time and administrative costs.
Better Decision Making: HR and finance departments can make quicker, data-driven decisions when payroll data is instantly available.
How Payroll Software Powers Real-Time Payroll
The backbone of real-time payroll is modern payroll software equipped with automation, data analytics, and cloud integration. Here’s how it works:
Data Synchronization: The software integrates seamlessly with attendance, HRMS, accounting, and time-tracking systems.
Rule Engine: Embedded logic that processes tax slabs, deductions, bonuses, and other rules in real-time.
Cloud Access: Enables HR professionals and employees to access payroll information from any device, anywhere.
Alerts & Notifications: Automatic alerts help flag anomalies or potential compliance breaches before payroll is finalized.
Businesses in the UAE are rapidly adopting these tools to meet the demands of a digital workforce. If you're searching for the best payroll software in UAE, look for solutions that offer full real-time capabilities, local compliance integration, and cloud-based flexibility.
The Impact on Employee Satisfaction
Today’s workforce is more informed and expects quicker, clearer compensation insights. Real-time payroll meets these expectations by:
Offering instant visibility into pay structure and deductions.
Enabling access to updated pay slips and tax documents.
Reducing anxiety caused by payroll delays or errors.
This level of engagement directly enhances employee satisfaction, which in turn boosts retention and productivity.
Use Cases: Real-Time Payroll in Action
Case 1: Remote Teams A Dubai-based tech firm with global remote employees uses real-time payroll to manage compensation across multiple time zones and currencies. With automated tax compliance for each region, the company processes payroll without delays.
Case 2: Gig and Part-Time Workers A retail chain in Abu Dhabi uses real-time payroll to handle fluctuating work hours. Employees can view their up-to-date pay any time they clock out.
Case 3: Mid-Sized Enterprises A mid-sized logistics company adopts the best payroll software in UAE to scale payroll processing as they grow. Real-time calculations help manage new hires, promotions, and benefits effortlessly.
Challenges and How to Overcome Them
1. Data Integration Complexity To implement real-time payroll effectively, all HR and financial systems must be interconnected. Choose software that supports wide integration and provides local UAE support.
2. Security Concerns Real-time access to sensitive data requires robust cybersecurity. Look for software with multi-factor authentication, encrypted databases, and access control.
3. Change Management Employees and HR teams may need time to adapt to new tools. Invest in proper training and onboarding programs when switching to a real-time payroll system.
How to Choose the Best Payroll Software in UAE
When evaluating solutions, consider the following:
Compliance with UAE Labour Laws: Your payroll software must be up to date with WPS regulations and tax requirements.
Localization: Language, currency, and regional tax systems should be built in.
Automation Features: From payslip generation to year-end reporting.
Scalability: The software should support your company as it grows.
Support and Training: Look for vendors that offer localized customer support and onboarding.
What’s Next? Predictive Payroll & AI
The future of payroll doesn’t stop at real-time. The next leap will be predictive payroll, where AI-driven systems forecast compensation changes, cash flow needs, and compliance risks before they happen.
Incorporating machine learning algorithms, these platforms will help companies proactively manage payroll with greater accuracy and foresight.
FAQs: Payroll Software & Real-Time Calculations
Q1. Is real-time payroll safe to use? Yes, when implemented with proper cybersecurity protocols, real-time payroll is secure and often safer than traditional methods due to real-time fraud detection.
Q2. Can I use real-time payroll for part-time or freelance employees? Absolutely. Real-time payroll is ideal for flexible workforce structures and provides accurate, on-the-go compensation updates.
Q3. What is the cost of implementing real-time payroll in the UAE? Costs vary depending on features, company size, and vendor. However, many cloud-based options offer affordable monthly subscriptions with local compliance features.
Q4. Which is the best payroll software in UAE? The best payroll software in UAE is one that includes real-time processing, WPS compliance, cloud access, and support for multi-currency and multi-language needs.
Q5. How long does it take to transition from traditional to real-time payroll? With a reliable vendor, implementation typically takes 2–6 weeks including training and data migration.
Conclusion
The future of payroll is fast, accurate, and transparent. With real-time payroll calculations powered by intelligent payroll software, companies can ensure employee satisfaction, maintain legal compliance, and scale effortlessly. For businesses in the UAE, adopting the best payroll software in UAE with real-time features is no longer optional—it's a strategic move toward sustainable growth and digital transformation.
Stay ahead of the curve. Invest in future-ready payroll systems today.
#payroll management software#best hr software in dubai#employee management software#software#payroll#payroll software
0 notes
Text
Elevating IT Security: DSGVO Compliance, Smart Audits & Pentesting Tools
In today’s data-driven world, IT security is no longer just an operational concern—it’s a legal and reputational necessity. From growing cyber threats to ever-tightening data privacy regulations like the DSGVO (General Data Protection Regulation), businesses face immense pressure to manage their digital risk effectively.
risikomonitor.com GmbH is a cybersecurity pioneer that offers a powerful suite of IT audit solutions, IT-Sicherheit tools, and advanced pentesting tools—all while ensuring your organization stays aligned with DSGVO compliance standards.
Let’s explore how businesses can build a resilient security framework by combining compliance, proactive testing, and automated protection.
DSGVO Compliance: More Than Just a Legal Obligation
Since its enforcement in 2018, DSGVO compliance (GDPR in English) has reshaped how companies handle personal data. Whether you're a multinational or an SME, processing EU citizens' data brings serious responsibilities—and potential penalties if ignored.
Non-compliance can lead to:
Fines up to €20 million or 4% of global revenue
Lawsuits and loss of customer trust
Operational disruptions and reputation damage
risikomonitor.com GmbH simplifies GDPR/DSGVO compliance through:
Data mapping and discovery tools
Real-time consent tracking
Automated privacy impact assessments
Breach detection and notification workflows
Role-based access controls and encryption audits
With intuitive dashboards and compliance reporting, your legal and IT teams stay aligned—saving time while minimizing legal exposure.
Smarter Security Starts with Effective IT Audit Solutions
An IT audit evaluates your current infrastructure, policies, and operations to ensure that your systems are secure, compliant, and optimized. While many companies still treat IT audits as an annual task, the modern approach is continuous and automated.
risikomonitor.com GmbH provides IT audit solutions that are dynamic and proactive. These include:
Assessment of system configurations and software versions
Patch management and vulnerability scanning
Network security reviews (firewalls, segmentation, open ports)
User access and identity control assessments
With real-time visibility and automatic alerts, organizations can quickly respond to gaps and improve their security posture without waiting for the next scheduled audit.
IT-Sicherheit Tools: Fortifying Digital Defenses
IT-Sicherheit (IT security) goes beyond antivirus software. It requires intelligent tools that protect data, systems, and communication across all endpoints—both internal and cloud-based.
risikomonitor.com GmbH offers an evolving suite of IT-Sicherheit tools designed for comprehensive coverage:
Endpoint Detection & Response (EDR)
Secure configuration enforcement
Privileged access management
SIEM (Security Information and Event Management) integration
Intrusion detection and prevention systems (IDPS)
These tools are integrated into a unified platform that reduces complexity while maximizing control. Automated rule enforcement, centralized dashboards, and real-time threat intelligence give IT teams what they need to stay ahead of cybercriminals.
Advanced Pentesting Tools: Simulating the Real Threats
Penetration testing is no longer optional—it’s essential. Advanced pentesting tools help simulate real-world cyberattacks so organizations can identify weaknesses before attackers do.
Traditional pen tests are often limited in scope and frequency, but risikomonitor.com GmbH takes a smarter approach. Their tools enable:
Automated vulnerability exploitation testing
Red teaming and social engineering simulation
Continuous security testing for web and mobile apps
Real-time risk scoring and detailed remediation guidance
Integration with existing CI/CD and DevSecOps pipelines
By running automated tests regularly, businesses gain ongoing visibility into how secure their infrastructure truly is. These simulations are customized based on industry, asset criticality, and threat landscape—providing a tailored roadmap to stronger security.
Why risikomonitor.com GmbH?
Unlike other vendors that only solve part of the problem, risikomonitor.com GmbH delivers an integrated, end-to-end cybersecurity ecosystem. With a focus on automation, real-time data, and legal compliance, their platform is ideal for:
Mid-size and enterprise businesses
Regulated industries (finance, healthcare, legal, SaaS)
Businesses targeting the EU and DSGVO-covered markets
Organizations undergoing digital transformation
Their all-in-one system includes:
Continuous DSGVO compliance monitoring
Automated IT audits and vulnerability checks
Scalable IT-Sicherheit tools
Comprehensive pentesting capabilities with expert reporting
Final Thoughts
The cyber threat landscape is becoming more sophisticated, and data protection laws are only getting stricter. To succeed in this environment, organizations must take a proactive, integrated approach to cybersecurity.
With the right tools and strategies—like those from risikomonitor.com GmbH—you can ensure your systems are secure, your compliance is airtight, and your risk is under control.
0 notes
Text
User and Entity Behavior Analytics Market Size, Opportunities & Growth Drivers
User and Entity Behavior Analytics Market Overview The User and Entity Behavior Analytics (UEBA) market is experiencing rapid expansion, driven by the escalating sophistication of cyber threats and the growing need for proactive cybersecurity solutions. In 2024, the global UEBA market is estimated to be valued at approximately USD 1.5 billion and is projected to reach USD 5.2 billion by 2032, expanding at a CAGR of over 17% during the forecast period. Enterprises across sectors such as BFSI, healthcare, retail, and government are increasingly investing in behavioral analytics to detect insider threats, account compromise, and advanced persistent threats (APTs). The shift from rule-based systems to AI-driven behavioral analytics, integration with Security Information and Event Management (SIEM) systems, and the widespread adoption of cloud-based platforms are propelling industry growth. User and Entity Behavior Analytics Market Dynamics Drivers: Key drivers include increasing incidents of insider threats, data breaches, and sophisticated cyberattacks. The surge in remote working environments and digital transformation has escalated the risk landscape, encouraging businesses to adopt UEBA solutions for real-time monitoring and predictive threat intelligence. Additionally, the integration of artificial intelligence (AI) and machine learning (ML) has significantly enhanced the accuracy and efficiency of UEBA tools, further driving adoption. Restraints: Despite the growth, high implementation costs, integration complexity, and lack of skilled professionals act as significant barriers. Smaller organizations often struggle with the resource intensity required to deploy and manage UEBA platforms effectively. Opportunities: Emerging markets in Asia-Pacific and Latin America present substantial growth opportunities due to increased digital adoption and the implementation of stringent data protection regulations. Furthermore, advancements in data analytics, predictive modeling, and cloud-native solutions open new avenues for innovation and scalability. Technology and Regulations: Regulatory compliance mandates such as GDPR, HIPAA, and CCPA are fostering demand for comprehensive behavior analytics solutions. In terms of sustainability, cloud-based UEBA models are reducing hardware dependency, energy consumption, and infrastructure costs, contributing to greener IT practices. Download Full PDF Sample Copy of User and Entity Behavior Analytics Market Report @ https://www.verifiedmarketresearch.com/download-sample?rid=24693&utm_source=PR-News&utm_medium=387 User and Entity Behavior Analytics Market Trends and Innovations Emerging trends include the convergence of UEBA with Extended Detection and Response (XDR), and the incorporation of Zero Trust Security models. Innovations in behavioral baselining, identity graphing, and contextual risk scoring are reshaping how threats are detected and mitigated. Vendors are increasingly leveraging natural language processing (NLP), deep learning, and edge analytics to enhance detection capabilities. Strategic partnerships, acquisitions, and R&D investments are also playing a pivotal role. For instance, collaborations between UEBA providers and cloud service platforms like AWS and Azure are streamlining integration and improving accessibility. User and Entity Behavior Analytics Market Challenges and Solutions Challenges: One of the primary challenges includes false positives and alert fatigue, which can overwhelm security teams. Additionally, data privacy concerns, interoperability issues with legacy systems, and scalability hurdles hinder optimal deployment. Rising costs of skilled cybersecurity professionals further constrain widespread adoption. Solutions: To overcome these challenges, vendors are focusing on user-friendly interfaces, automated threat detection, and cloud-native deployments. Enhanced threat correlation engines and customizable policy frameworks are helping organizations tailor solutions to specific risk profiles.
Ongoing staff training, managed security services, and modular pricing models can also ease entry barriers for smaller enterprises. User and Entity Behavior Analytics Market Future Outlook The future of the UEBA market is poised for accelerated growth, driven by the integration of AI/ML, increasing cybersecurity budgets, and heightened awareness of insider threats. As digital infrastructures become more complex and decentralized, the demand for intelligent, adaptive, and scalable threat detection systems will continue to rise. With the proliferation of IoT and 5G networks, UEBA solutions will evolve to cover a broader range of entities beyond traditional users, enhancing their relevance across sectors. The market is expected to witness increased consolidation, with major players investing in unified security platforms that offer holistic threat intelligence and behavioral analytics capabilities. Key Players in the User and Entity Behavior Analytics Market User and Entity Behavior Analytics Market are renowned for their innovative approach, blending advanced technology with traditional expertise. Major players focus on high-quality production standards, often emphasizing sustainability and energy efficiency. These companies dominate both domestic and international markets through continuous product development, strategic partnerships, and cutting-edge research. Leading manufacturers prioritize consumer demands and evolving trends, ensuring compliance with regulatory standards. Their competitive edge is often maintained through robust R&D investments and a strong focus on exporting premium products globally. Splunk Inc. (U.S.) Securonix (U.S.) Varonis Systems Inc. (U.S.) Bay Dynamics (U.S.) Exabeam Inc. (U.S.) Gurucul (U.S.) Niara Inc. (U.S.) Sqrrl Data Inc. (U.S.) Dtex Systems (U.S.) Rapid7 (U.S.). Get Discount On The Purchase Of This Report @ https://www.verifiedmarketresearch.com/ask-for-discount?rid=24693&utm_source=PR-News&utm_medium=387 User and Entity Behavior Analytics Market Segments Analysis and Regional Economic Significance The User and Entity Behavior Analytics Market is segmented based on key parameters such as product type, application, end-user, and geography. Product segmentation highlights diverse offerings catering to specific industry needs, while application-based segmentation emphasizes varied usage across sectors. End-user segmentation identifies target industries driving demand, including healthcare, manufacturing, and consumer goods. These segments collectively offer valuable insights into market dynamics, enabling businesses to tailor strategies, enhance market positioning, and capitalize on emerging opportunities. The User and Entity Behavior Analytics Market showcases significant regional diversity, with key markets spread across North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. Each region contributes uniquely, driven by factors such as technological advancements, resource availability, regulatory frameworks, and consumer demand. User and Entity Behavior Analytics Market, By Type • Solution• Services User and Entity Behavior Analytics Market, By Deployment Type • On-Premises• Cloud User and Entity Behavior Analytics Market By Geography • North America• Europe• Asia Pacific• Latin America• Middle East and Africa For More Information or Query, Visit @ https://www.verifiedmarketresearch.com/product/user-and-entity-behavior-analytics-market/ About Us: Verified Market Research Verified Market Research is a leading Global Research and Consulting firm servicing over 5000+ global clients. We provide advanced analytical research solutions while offering information-enriched research studies. We also offer insights into strategic and growth analyses and data necessary to achieve corporate goals and critical revenue decisions. Our 250 Analysts and SMEs offer a high level of expertise in data collection and governance using industrial techniques to collect and analyze data on more than 25,000 high-impact and niche markets.
Our analysts are trained to combine modern data collection techniques, superior research methodology, expertise, and years of collective experience to produce informative and accurate research. Contact us: Mr. Edwyne Fernandes US: +1 (650)-781-4080 US Toll-Free: +1 (800)-782-1768 Website: https://www.verifiedmarketresearch.com/ Top Trending Reports https://www.verifiedmarketresearch.com/ko/product/data-replication-market/ https://www.verifiedmarketresearch.com/ko/product/data-security-posture-management-dspm-tool-market/ https://www.verifiedmarketresearch.com/ko/product/data-transformation-software-market/ https://www.verifiedmarketresearch.com/ko/product/dc-dc-power-converters-market/ https://www.verifiedmarketresearch.com/ko/product/debt-settlement-solution-service-market/
0 notes
Text
Why AI Crypto Trading is the Future of Investing in 2025
As the crypto market matures, one thing is clear—AI crypto trading is not just a trend, it’s the future. With lightning-fast execution, deep data analysis, and emotionless decision-making, AI is transforming how investors approach digital assets.
Whether you’re a retail investor or a pro managing millions, integrating AI into your crypto trading strategy can unlock smarter moves and bigger returns.
What is AI Crypto Trading?
AI crypto trading is the use of artificial intelligence (AI), machine learning (ML), and predictive analytics to make smarter, faster, and more accurate trading decisions. These systems analyze thousands of data points—price charts, volume patterns, news sentiment, social trends, on-chain metrics—and output:
Real-time trading signals
Price predictions
Portfolio strategies
Token grades and rankings
Unlike traditional trading that relies heavily on gut instinct, AI eliminates bias. It’s built to identify patterns, anticipate movements, and adapt in real-time—especially valuable in the 24/7, high-volatility crypto market.
Types of Crypto Trading (And How AI Powers Each One)
1. Spot Trading
The most basic form—buy/sell tokens at current market price. AI helps spot undervalued tokens, perfect entry/exit points, and risk levels.
2. Futures Trading
Trade contracts speculating future prices. AI models monitor trends, test strategies, and react faster than human traders.
3. Margin Trading
Amplify gains (and risk) with borrowed capital. AI minimizes downside by tracking volatility and adjusting positions automatically.
4. Swing Trading
Hold tokens for days/weeks. AI tracks sentiment, technical signals, and narratives to pinpoint breakout opportunities.
5. Day Trading
Make rapid-fire moves in the same day. AI bots can execute trades in milliseconds, eliminating emotional errors and maximizing efficiency.
6. Algorithmic Trading
Rule-based trading powered by code. With AI, these bots become self-improving systems that learn and evolve from live market data.
Top Crypto Trading Platforms (And Where AI Fits In)
Here are the best exchanges and tools for AI-powered trading in 2025:
✅ Token Metrics – Best AI Crypto Trading Platform
Token Metrics is a crypto analytics platform—not an exchange—but it’s a game-changer. It offers:
AI-based Trader & Investor Grades
Bullish/Bearish Signals
Custom Alerts
AI-Driven Indices
Crypto Data API for developers
Use Token Metrics alongside your favorite exchange to validate trades and gain AI-driven edge. Whether you’re managing a $1K or $1M portfolio, it gives you the confidence to act on data, not hype.
Binance
Massive liquidity. No built-in AI—but use Token Metrics API or plug into a trading bot for enhanced performance.
Coinbase
User-friendly and trusted by beginners. For advanced AI-driven trading, integrate with Token Metrics or similar tools.
Kraken
Secure and professional. Combine with AI signal providers to run emotion-free, precision strategies.
Bybit & OKX
Feature-rich with built-in bots. Still, Token Metrics outperforms in signal accuracy, narrative tracking, and token rankings.
Why AI is Winning in Crypto
Speed: Reacts to market shifts in real-time
Scale: Monitors 10,000+ tokens across chains
Emotionless: No panic-selling or FOMO buying
Accuracy: Backtested, data-driven decisions
Adaptability: Learns and evolves with markets
With tools like Token Metrics, you’re not guessing. You’re following a system backed by data and engineered to win.
2025 is the year where AI crypto trading moves from edge to necessity. Human traders can’t keep up with the pace, complexity, or opportunities. To stay competitive, adopt AI—optimize your strategy, reduce mistakes, and trade with unmatched intelligence.
Start your journey with Token Metrics. Get real-time signals, AI-grade token insights, and automated indices—all in one platform.

1 note
·
View note
Text
Top Web Security Solutions That Safeguard Your Website from Hackers and Data Breaches
In today’s digital age, website security is no longer optional—it’s a necessity. As cyber threats grow more advanced, businesses must invest in comprehensive web security solutions to safeguard their online assets. From protecting sensitive customer data to maintaining brand integrity, a secure website helps build trust and ensures regulatory compliance. Effective web protection includes multiple layers of defense, including firewalls, encryption, real-time monitoring, and access control. Without these tools, your site could fall victim to data breaches, malware attacks, and financial fraud. Implementing robust web security solutions is critical to ensure your digital infrastructure remains secure, reliable, and resilient.
Protect Your Site from Cyberattacks with Robust Firewall Tools
A firewall acts as the first line of defense against cyberattacks by filtering out malicious traffic and unauthorized access attempts. Modern web security solutions integrate advanced firewall tools that monitor both incoming and outgoing data to protect against various threats, including DDoS attacks, phishing attempts, and brute-force intrusions. These firewalls can be hardware-based or cloud-enabled, offering scalable protection for websites of all sizes. By continuously updating threat databases and rules, firewall tools help businesses proactively respond to evolving cyber risks. Investing in robust firewall protection is a fundamental step toward creating a secure, attack-resistant digital environment for your website.
Monitor Threats in Real-Time to Stop Breaches Before They Spread
One of the most powerful components of effective web security solutions is real-time threat monitoring. This feature allows businesses to detect anomalies and suspicious activity as it happens, providing immediate alerts and automated responses. Whether it's unauthorized login attempts, abnormal traffic patterns, or data exfiltration, real-time monitoring tools ensure breaches are contained before they cause significant damage. These tools use AI and machine learning algorithms to analyze behavior patterns and identify potential threats with high accuracy. Early detection through continuous monitoring gives businesses the edge in stopping hackers in their tracks and reducing the impact of security incidents.
Encrypt Sensitive Data to Ensure Secure Online Transactions
Encryption is a cornerstone of trusted web security solutions, especially when handling sensitive data such as passwords, credit card numbers, or personal information. By converting readable data into an unreadable format, encryption ensures that even if data is intercepted, it cannot be misused. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols are commonly used to encrypt data during transmission. This builds trust with users, protects your reputation, and ensures compliance with data protection laws like GDPR and HIPAA. By encrypting your data, you provide a secure environment for online transactions and communications, essential for any business today.
Use Web Security Solutions to Block Malware and Harmful Bots
Malware infections and harmful bots pose serious risks to your site’s functionality, user experience, and SEO rankings. Advanced web security solutions offer malware scanning, bot filtering, and threat elimination tools that detect and neutralize these digital dangers. Malicious bots can scrape content, flood forms, or launch automated attacks. Security software can distinguish between good bots, like search engine crawlers, and bad bots using behavioral analysis and IP blacklists. Meanwhile, anti-malware tools scan your website regularly and quarantine suspicious files or scripts. This proactive approach keeps your web environment clean and ensures visitors can access a safe, high-performing site.
Authenticate Users with Strong Access Control Methods
Restricting access to authorized users only is essential in preventing unauthorized data exposure or sabotage. Strong access control methods are a vital part of web security solutions, ensuring that each user has the correct level of access based on their role or needs. Multi-factor authentication (MFA), role-based access control (RBAC), and single sign-on (SSO) are all technologies that reinforce security by validating identities. These systems reduce the chances of credential theft and prevent lateral movement within your network. Implementing layered access controls not only deters cybercriminals but also adds a significant layer of accountability and transparency to user actions.
Prevent SQL Injections with Secure Coding Practices
SQL injection is a common and devastating attack where hackers manipulate queries to access or corrupt your database. To mitigate this threat, web security solutions must include secure coding practices from the ground up. Developers should use parameterized queries, input validation, and stored procedures to prevent malicious code execution. Security-focused code reviews and automated vulnerability scanners can catch flaws early in the development cycle. Educating your development team about secure coding standards plays a crucial role in eliminating loopholes. By prioritizing secure code, businesses create a strong foundation that reduces the risk of injection attacks and data breaches.
Regular Updates and Patches Keep Vulnerabilities in Check
Outdated software is a prime target for hackers, as known vulnerabilities can be easily exploited. That’s why ongoing maintenance—such as regular updates and security patches—is a critical aspect of any web security solution. Whether it's your content management system, plugins, or third-party tools, every component must be updated to the latest version. Web security tools can automate this process, ensuring that no patch is missed. Additionally, vulnerability assessments can help identify and fix issues before they become exploitable. Keeping your systems current not only strengthens your defenses but also reduces the overall attack surface for cybercriminals.
Conclusion
Comprehensive web security solutions are essential for maintaining the integrity, confidentiality, and availability of your digital infrastructure. From strong firewalls and real-time monitoring to encrypted transactions and secure coding practices, each layer of protection serves a crucial role in fending off cyber threats. As cyberattacks become more frequent and sophisticated, businesses must be proactive rather than reactive in their approach to security. By investing in the right tools, enforcing strong access controls, and keeping systems up to date, you build a solid defense against potential breaches. Ultimately, robust web security solutions provide peace of mind and help your business thrive safely online.
0 notes
Text
Next-Gen Security Testing Services Using AI: A Deep Dive

In the ever-evolving landscape of software development, security breaches have grown more frequent and sophisticated. Traditional testing methods, though foundational, are no longer sufficient in identifying and addressing the fast-moving threats facing modern systems. This is where Next-Gen Security Testing Services come into play, blending AI innovation with robust testing protocols.
At Robotico Digital, we’ve redefined how security integrates into software engineering by embedding Artificial Intelligence (AI) into our advanced Security Testing Services. This deep dive explores how AI transforms Security Testing in Software Testing, enabling faster detection, smarter remediation, and continuous protection across development pipelines.
The Shift Toward AI in Security Testing
Historically, Security Testing Services were heavily reliant on manual reviews, rule-based scanners, and time-intensive penetration testing. While still valuable, these methods struggle to keep up with:
lRapid DevOps cycles
lEvolving attack vectors
lIncreasing application complexity
lHybrid cloud and microservices infrastructure
AI, specifically through machine learning (ML), Natural Language Processing (NLP), and behavioral analytics, has introduced a transformative layer of intelligence to these services. It allows security testers and developers to go beyond reactive defenses—identifying risks proactively and at scale.
How AI Enhances Security Testing in Software Testing
Incorporating AI into Security Testing in Software Testing provides multi-dimensional improvements across efficiency, accuracy, and adaptability. Let’s break down the core components.
1. Automated Vulnerability Detection
AI-powered scanners can crawl source code, binary files, API endpoints, and web interfaces to detect anomalies that indicate vulnerabilities. Unlike traditional scanners, AI engines learn from past vulnerabilities and global threat databases to continually improve detection precision.
Key Features:
lPattern recognition across massive codebases
lZero-day threat detection using anomaly detection models
lAuto-mapping of application attack surfaces
2. Adaptive Risk Prioritization
One major challenge in Security Testing Services is managing false positives and prioritizing true threats. AI models rank vulnerabilities based on:
lExploitability
lBusiness impact
lData sensitivity
lThreat intelligence feeds
This reduces alert fatigue and ensures engineering teams focus on high-priority issues first.
3. Dynamic Threat Modeling
AI systems can automatically generate and update threat models for evolving software architectures. By simulating attacker behavior, AI enables predictive testing—discovering how vulnerabilities might be chained or escalated.
4. Self-Learning Penetration Testing
AI agents mimic ethical hackers using reinforcement learning. These bots evolve through trial and error, discovering unconventional paths to exploitation and mimicking real-world attack tactics.
Robotico Digital’s AI-Powered Security Testing Stack
At Robotico Digital, we’ve built a proprietary AI-enhanced testing framework designed to deliver intelligent, continuous, and scalable security coverage. Here's what powers our next-gen Security Testing Services:
AI-Powered SAST & DAST Engines
SAST (Static Application Security Testing): Our AI models review code for insecure functions, misconfigurations, and data flow leaks at the source level.
DAST (Dynamic Application Security Testing): AI crawlers test running applications by simulating user behavior and injecting payloads to trigger security vulnerabilities.
Machine-Learning Vulnerability Correlation
We reduce redundant findings by merging results from multiple tools and identifying duplicate alerts. ML models group similar issues, track them across builds, and learn from developer remediation behavior.
AI-Based Compliance Validation
Robotico Digital uses AI to ensure compliance with:
lOWASP Top 10
lGDPR / HIPAA / PCI DSS
lNIST and ISO 27001 We map discovered vulnerabilities to these frameworks, highlighting gaps in your security and compliance posture.
Use Cases of AI in Security Testing Services
Web & Mobile Application Testing
AI identifies issues such as insecure authentication, broken access controls, and injection attacks. It tests logic errors and parameter tampering based on how real users interact with the app.
API Security Testing
APIs are high-value targets. Our AI models analyze OpenAPI/Swagger specs, apply fuzzing techniques, and test for broken object-level authorization (BOLA) and mass assignment vulnerabilities.
Cloud & Infrastructure Testing
For cloud-native applications, AI detects misconfigurations in IAM roles, storage permissions, and network security groups—especially in multi-cloud environments like AWS, Azure, and GCP.
DevSecOps Pipeline Integration
Robotico Digital integrates AI-based scanning tools directly into CI/CD platforms like GitLab, Jenkins, and Azure DevOps. This ensures shift-left security with automated gates at every build stage.
Implementation Challenges & Considerations
While the benefits are substantial, integrating AI into Security Testing Services is not without hurdles:
1. Data Quality & Training Bias
AI models require high-quality, labeled data to function accurately. Poor or biased training datasets can lead to both false positives and false negatives.
2. Explainability & Developer Trust
“Black-box” decisions from AI can frustrate developers. Robotico Digital addresses this by using explainable AI (XAI) models that provide root cause analysis and remediation context.
3. AI Model Drift
Security threats evolve. AI models must be updated regularly to avoid “drift” that could miss emerging threats. We maintain continuous model updates with feedback loops from threat intelligence systems.
Future of AI in Security Testing Services
AI in Security Testing Services is still in its growth phase. Here’s what’s on the horizon:
lGenerative AI for Test Case Creation: Using models like GPT-4 to simulate attacks and generate intelligent test scripts.
lAutonomous Remediation Agents: AI that not only finds issues but can propose or apply secure code fixes autonomously.
lFederated Threat Learning: Secure sharing of anonymized threat data across organizations to train more resilient models.
lAI-Powered Red Teaming: Simulated human-like attackers that learn and evolve to breach complex systems.
Conclusion
Security is not a checkbox; it’s a continuous journey. As applications grow more complex and the cyber threat landscape expands, relying on traditional methods alone is no longer enough. AI enables Security Testing Services to become proactive, intelligent, and deeply integrated into the development lifecycle.
At Robotico Digital, we’re proud to lead the next generation of Security Testing in Software Testing by harnessing the power of artificial intelligence. Our AI-enhanced services empower organizations to detect vulnerabilities faster, respond more intelligently, and scale their cybersecurity operations with confidence.
0 notes
Text
BULK SMS: The Cornerstone of Scalable Business Communication

Revolutionizing Enterprise Messaging Through BULK SMS
Modern businesses operate in a world where real-time communication is critical. BULK SMS empowers companies to instantly disseminate messages at scale, bolstering client engagement and operational efficiency. From promotional alerts to transactional updates, enterprises leverage BULK SMS to stay connected across diverse geographies and customer bases.
Retailers, banks, logistics firms, real estate developers, and e-commerce platforms harness BULK SMS to deliver time-sensitive messages that capture attention and drive action. With significantly higher open rates than email, BULK SMS provides unmatched immediacy and penetration.
Selecting the Right BULK SMS PROVIDERS for Optimal Reach
Not all BULK SMS PROVIDERS are created equal. Enterprises seeking consistency, security, and scalability need providers that offer high-throughput infrastructure and seamless integration options. Advanced platforms deliver:
API-first ecosystems for automated execution
SLA-backed delivery speeds with real-time analytics
AI-augmented personalization at scale
Leveraging a trusted BULK SMS GATEWAY ensures rapid message delivery and cross-network compatibility. The best BULK SMS PROVIDERS offer global reach with localized delivery assurance, including superior service in high-growth markets like Tanzania.
The Rise of BULK SMS PROVIDERS IN TANZANIA
With mobile penetration surging, BULK SMS PROVIDERS IN TANZANIA have become pivotal to brand outreach and operational automation. Tanzanian enterprises—from fintech innovators to logistics companies—are adopting BULK SMS to:
Dispatch OTPs and payment confirmations
Automate customer notifications
Launch geo-targeted promotions in Swahili and English
Local compliance, multilingual templates, and carrier-grade infrastructure make BULK SMS GATEWAY IN TANZANIA an essential tool for regional scalability.
How BULK SMS GATEWAY Delivers Strategic Advantages
An enterprise-grade BULK SMS GATEWAY enables frictionless communication across fragmented systems. Integration-ready with CRMs, ERPs, and marketing suites, it allows:
Multi-channel fallback to ensure message delivery
Real-time delivery reports with engagement metrics
Time-zone aware scheduling for maximum visibility
BULK SMS PROVIDERS leveraging AI-driven routing engines and smart delivery rules increase conversions while minimizing latency and message loss.
AI + BULK SMS: A Force Multiplier for Campaign Efficiency
Intelligent automation is redefining BULK SMS engagement. Today’s forward-thinking BULK SMS PROVIDERS embed machine learning to predict customer behavior, refine messaging cadence, and dynamically alter content based on intent.
Features include:
Sentiment-aware response handling
A/B testing across audience segments
Location-aware delivery logic using telecom APIs
In regions like Tanzania, this tech-forward approach unlocks deeper customer engagement and improved ROI on communication spend.
Conclusion: Embrace BULK SMS for Unmatched Business Agility
Enterprises looking to scale fast and connect deep must adopt BULK SMS as a central communications strategy. Whether driven by global ambitions or regional growth in markets like Tanzania, choosing the right BULK SMS PROVIDERS and integrating a robust BULK SMS GATEWAY delivers tangible gains—from customer retention to operational resilience.
0 notes
Text
Staying Safe on the Road: Tips and Strategies for Responsible Driving
Staying Safe on the Road: Tips and Strategies for Responsible Driving
Road safety is a shared responsibility. Whether you're an experienced driver or just got your license, adopting safe driving habits not only protects your life but also the lives of others on the road. In today’s world, with increasing traffic and distractions, staying alert and practising responsible driving is more important than ever.
Here are key tips and strategies to help you stay safe behind the wheel—and ensure your vehicle stays in top condition with quality components like UNO Minda spare parts.
Stay Focused and Avoid Distractions Distractions are among the leading causes of road accidents. Whether it's using a mobile phone, adjusting the radio, or eating while driving, every second your eyes are off the road increases the risk. Use hands-free devices if necessary and always keep your focus on driving.
Maintain Your Vehicle Regularly Safe driving starts with a well-maintained vehicle. Ensure your brakes, lights, tires, and engine are in optimal condition. Using genuine components such as UNO Minda spare parts ensures your vehicle’s performance and safety systems function reliably. Uno Minda is known for manufacturing high-quality automotive components, from lighting and horns to switches and sensors, which can greatly enhance your driving experience and safety.
Obey Traffic Rules This one might sound obvious, but many drivers ignore basic traffic rules. Always follow speed limits, signal before turning, and respect traffic signals. Being a responsible driver means anticipating other drivers’ actions and reacting in a calm, lawful manner.
Don’t Drive Under the Influence Alcohol, drugs, and certain medications can impair your judgment and reaction time. If you're under the influence, call a cab, use public transport, or let a sober friend drive. It’s a simple decision that can save lives.
Keep a Safe Distance Tailgating is dangerous. Maintain a safe following distance from the vehicle in front of you. This gives you enough time to react if the vehicle suddenly stops or slows down.
Use Safety Features Wisely Modern vehicles come equipped with advanced safety features like ABS, airbags, and rear-view cameras. But they only help if they're in working condition and used correctly. Here again, using high-quality components like those from Uno Minda ensures that your safety systems function as intended, offering peace of mind during every journey.
Be Weather-Wise Rain, fog, or snow can reduce visibility and road grip. In such conditions, slow down, turn on your headlights, and drive with extra caution. Check your wipers, defrosters, and lights regularly—components often available from trusted suppliers like UNO Minda.
Conclusion Safe driving is not just about getting from point A to point B—it's about making thoughtful decisions that protect everyone on the road. Routine maintenance using reliable products like UNO Minda spare parts and adopting responsible driving behaviours go hand-in-hand in creating a safer driving environment. So buckle up, stay focused, and drive smart.
Because safety isn’t just a destination—it’s the whole journey.
#RoadSafety#ResponsibleDriving#DrivingTips#StaySafe#DefensiveDriving#SafeDriving#VehicleSafety#DriveSmart#TrafficRules#DriveSafeSaveLives#RoadAwareness#CarTips#TumblrBlogs#AutoLifestyle
0 notes
Text
IP Docketers’ Tech-Driven IP Docketing Solution
In today’s fast-paced legal and intellectual property (IP) landscape, law firms and corporate IP departments are under increasing pressure to streamline operations, reduce human error, and ensure timely filings. Amid these challenges, IP Docketers has emerged as a cutting-edge partner offering AI docketing services and smart legal tools to revolutionize the way IP is managed.
This article delves deep into how IP Docketers combines human expertise with technology to deliver scalable, reliable, and intelligent IP docketing solutions to legal professionals around the globe.
The Evolving Need for Efficient IP Docketing
Docketing is the backbone of any IP legal operation. It involves tracking filing deadlines, maintenance fees, office actions, and various jurisdictional compliance requirements. A single missed deadline can lead to the loss of patent rights or trademarks—making efficient and error-free docketing absolutely crucial.
Traditional manual docketing, while accurate in the hands of skilled professionals, is prone to human oversight and delays. As IP portfolios grow, so does the need for smarter, automated systems.
Why Tech-Driven Docketing Matters
Tech-driven docketing is not just a trend—it’s a transformation. By leveraging AI docketing services, law firms and in-house legal teams can:
Automate repetitive tasks like calendar entries and deadline reminders.
Minimize risk by reducing manual data entry errors.
Scale operations without proportionally increasing staff.
Gain insights through analytics and reporting features built into smart legal tools.
This is where IP Docketers takes center stage with a service model built on reliability, customization, and innovation.
What Makes IP Docketers Stand Out?
IP Docketers offers a suite of AI-driven and tech-enhanced docketing services tailored to the specific needs of IP law firms, corporations, and legal outsourcing companies. Here’s how we bring a difference:
1. AI Docketing Services That Learn and Adapt
Our intelligent docketing engine employs machine learning to understand patterns and improve accuracy over time. Unlike rigid systems, it adapts to jurisdictional updates and client preferences, providing a dynamic docketing experience.
2. Smart Legal Tools Integration
From advanced deadline calculators to jurisdiction-specific rules databases, IP Docketers integrates smart tools into your workflow. This ensures that your team always works with up-to-date data and reliable alerts—minimizing the chances of missing deadlines.
3. Cloud-Based, Secure Access
Our platform is built with enterprise-level security protocols and offers 24/7 cloud access. This ensures seamless collaboration between in-house counsel, outside attorneys, and support staff across geographies.
4. Customizable Workflows
We understand that every firm and client has unique docketing requirements. That’s why IP Docketers offers highly customizable workflows that align with your internal processes, practice areas, and jurisdictions.
5. Expert Human Oversight
Even the best AI needs human guidance. Our team of experienced IP paralegals and legal technologists reviews, verifies, and ensures that the final outputs are accurate and compliant.
A Seamless IP Lifecycle Management System
Whether you’re filing a new patent in the US, tracking annuity deadlines in Europe, or responding to an office action in Japan—IP Docketers supports the full IP lifecycle:
Patent, Trademark & Design Filing Dockets
Office Action Response Reminders
National Phase Entry Tracking
Maintenance Fee Monitoring
Opposition & Litigation Tracking
By automating and centralizing all these processes, we enable IP professionals to focus on strategy and innovation, not administration.
Client Success Stories
Many of our clients have experienced tangible benefits from switching to IP Docketers’ tech-driven approach. One notable case involved a global IP firm that reduced docketing errors by 87% and increased operational efficiency by 60% within six months of onboarding with us.
Another corporate client in the tech sector managed to integrate our smart legal tools with their internal CRM system, creating a unified legal management environment that significantly improved cross-departmental collaboration.
The Human-AI Balance: Precision Meets Productivity
Our philosophy is simple—let machines do what they do best (speed, scale, accuracy), and let humans do what they do best (judgment, analysis, and client service). With our AI docketing services, you get the best of both worlds:
AI-enabled automation
Rule-based logic for deadline tracking
Human review and quality control
Continuous feedback loops for optimization
This combination ensures not only faster processing but also higher confidence in your IP docketing accuracy.
Compliance and Global Coverage
IP Docketers supports jurisdictional rules across 150+ countries and is constantly updated to reflect changes in regulations and practices. Our tools are compliant with major IP authorities including:
USPTO
EPO
WIPO
CNIPA
JPO
and more.
With multilingual capabilities and round-the-clock support, we ensure your docketing system is as global as your portfolio.
Future-Ready IP Management
Legal tech is evolving rapidly, and IP Docketers is at the forefront of this change. From integrating blockchain for audit trails to developing predictive analytics for portfolio strategy, we are committed to continuous innovation.
Our roadmap includes:
AI-based risk prediction for missed deadlines
Smart contract automation for IP renewals
Voice-activated docket access for mobile users
Deeper integration with practice management tools
Conclusion: Docket Smarter with IP Docketers
In a world where innovation is the new currency, managing IP efficiently has never been more critical. IP Docketers brings the best of AI docketing services and smart legal tools to transform your IP operations—making them faster, smarter, and more secure.
Don’t let outdated systems hold you back. Embrace the future of legal tech with IP Docketers and experience what seamless, intelligent IP docketing truly looks like.
0 notes