#Big Data Security Platform
Explore tagged Tumblr posts
Text
Big Data Security Market to be Worth $60.1 Billion by 2031
Meticulous Research®—a leading global market research company, published a research report titled, ‘Big Data Security Market by Component (Solutions [Data Encryption, Security Intelligence, Data Backup & Recovery], Services), Deployment Mode, Organization Size, End User (IT & Telecom, BFSI, Retail & E-commerce), and Geography - Global Forecast to 2031.’
According to this latest publication from Meticulous Research®, the big data security market is projected to reach $60.1 billion by 2031, at a CAGR of 13.2% from 2024 to 2031. The growth of the big data security market is driven by the emergence of disruptive digital technologies, the increasing demand for data security and privacy solutions due to the rise in data breaches, and the growing data generation in the e-commerce industry. However, the high implementation costs of big data security solutions restrain the growth of this market.
Furthermore, the growing need for cloud-based security solutions and the increasing integration of AI, ML, and blockchain technologies in security solutions are expected to generate growth opportunities for the stakeholders in this market. However, the lack of knowledge about big data security solutions and the shortage of skilled IT professionals are major challenges impacting the growth of the big data security market.
The big data security market is segmented by component (solutions [data discovery and classification, data encryption {data protection, tokenization, data masking, other data encryption solutions}, security intelligence, data access control & authentication, data governance & compliance, data backup & recovery, data auditing & monitoring, other solutions], services [professional services, managed services]), deployment mode (on-premise deployments, cloud-based deployments), organization size (large enterprises, small & medium-sized enterprises), end user (IT & telecom, healthcare & pharmaceutical, BFSI, retail & e-commerce, energy & utilities, government, manufacturing, media & entertainment, transportation & logistics, and other end users). The study also evaluates industry competitors and analyzes the market at the regional and country levels.
Based on component, the big data security market is segmented into solutions and services. The solutions segment is further segmented into data discovery and classification, data encryption, security intelligence, data access control & authentication, data governance & compliance, data backup & recovery, data auditing & monitoring, and other solutions. In 2024, the solutions segment is expected to account for the larger share of the big data security market. The large market share of this segment is attributed to the increasing concerns regarding data security and privacy, the increasing adoption of data security solutions by SMEs, and the rising demand for encryption solutions for data protection across IoT devices. Big data security solutions include tools and measures to process or safeguard data and analytics processes. In March 2024, CrowdStrike, Inc. (U.S.) partnered with Rubrik, Inc. (U.S.) to transform data security solutions and stop breaches of critical information. Moreover, this segment is also projected to register the highest CAGR during the forecast period.
Based on deployment mode, the big data security market is segmented into on-premise deployments and cloud-based deployments. In 2024, the on-premise deployments segment is expected to account for the larger share of the big data security market. The large market share of this segment is attributed to the higher preference for on-premise deployments among large enterprises and increasing data generation in large enterprises. The on-premise model of deployment is majorly adopted by well-established and large companies that are capable of making capital investments toward the required hardware and hosting environments. In addition, these organizations also have sufficient in-house IT expertise to maintain software efficiency. Internal big data security is one of the major benefits of on-premise deployments.
However, the cloud-based deployments segment is projected to register the higher CAGR during the forecast period. The growth of this segment is driven by the rapid evolution of new security avenues for cloud-based deployments, the superior flexibility offered by cloud-based deployments, and the increase in security breaches. Cloud-based security solutions provide social networking privacy, system optimization, online storage, regulatory compliance, and connected device security. The adoption of cloud computing and storage systems is gaining popularity among small and medium-scale enterprises, supporting the growth of this segment.
Based on organization size, the big data security market is segmented into large enterprises and small & medium-sized enterprises. In 2024, the large enterprises segment is expected to account for the larger share of the big data security market. The large market share of this segment is attributed to the strong IT infrastructure of large enterprises, the growing adoption of advanced technologies such as AI, IoT, and blockchain, and the availability of skilled IT personnel to manage data security platforms. With larger budgets and a keen focus on developing strategic IT initiatives, large enterprises have a competitive advantage over small and medium-scale enterprises in terms of technology adoption. Large enterprises have a stable financial backup and can easily procure customized data security solutions, contributing to this segment's growth.
However, the small & medium-sized enterprises segment is projected to register the higher CAGR during the forecast period. The growth of this segment is driven by increasing digital transformation, government initiatives to promote security solutions, and the rising incidence of data breaches. SMEs are also increasingly becoming targets of cybercrime and therefore adopting suitable and strong security solutions.
Based on end user, the big data security market is segmented into IT & telecom, healthcare & pharmaceutical, BFSI, retail & e-commerce, energy & utilities, government, manufacturing, media & entertainment, transportation & logistics, and other end users. In 2024, the IT & telecom segment is expected to account for the largest share of the big data security market. The large market share of this segment is attributed to the increasing data breaches in IT companies as they store a vast amount of customer data, strict regulatory compliance forcing companies to implement stricter data security measures, and the increasing adoption of cloud-based solutions in the IT industry. In March 2023, IBM Corporation (U.S.) collaborated with Cohesity, Inc. (U.S.) to address increased data security and resiliency issues in hybrid cloud environments. With this collaboration, IBM launched its new IBM Storage Defender solution, including Cohesity's data protection, cyber resilience, and data management capabilities in the offering.
However, the healthcare & pharmaceutical segment is projected to register the highest CAGR during the forecast period. The growth of this segment is driven by the rising adoption of telemedicine devices and remote healthcare services, growing cyberattacks on connected devices, and the increasing demand for secure medical connected devices. A vast amount of medical data is generated in the healthcare sector. It is stored to improve patient outcomes, personalize treatment plans, and develop new drugs, among other applications. However, this sensitive data requires robust security measures to protect patient privacy and prevent unauthorized access. In November 2021, Armis, Inc. (U.S.) partnered with Nuvolo (U.S.) to improve data interoperability and the overall risk posture of healthcare organizations.
Based on geography, the big data security market is segmented into North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. In 2024, North America is expected to account for the largest share of the big data security market. The market growth in North America is driven by the presence of prominent players offering advanced big data security solutions & services, the early adoption of disruptive technologies, and growing awareness regarding data security. North America is home to several major players that provide products and services to improve big data security measures for IT assets, data, and privacy across different domains. Thus, big data security companies operating in the North America region are investing heavily in R&D activities to develop new & advanced security solutions that can address rising security challenges. In February 2024, Cyberhaven, Inc. (U.S.) launched Linea AI, an AI platform designed to combat the critical insider risks threatening vital corporate data.
However, the Asia-Pacific region is projected to record the highest CAGR during the forecast period. The growth of this market is driven by the growing data breaches, supportive government initiatives, and growing awareness regarding data security among small and medium-scale organizations. In December 2023, Safetica a.s. (U.S.) partnered with Kaira Global (Singapore) to deliver Safetica's Data Loss Prevention (DLP) solutions for enterprises of all sizes to safeguard their data against insider risks and data breaches in Singapore. APAC is the fastest-growing big data security market due to rapid investments in IT infrastructure, extensive use of the Internet, and growing security challenges.
Key Players
The key players operating in the big data security market are Check Point Software Technologies, Ltd. (Israel), Cisco Systems, Inc. (U.S.), Fortinet, Inc. (U.S.), Oracle Corporation (U.S.), IBM Corporation (U.S.), Microsoft Corporation (U.S.), Hewlett Packard Enterprise Development LP (U.S.), Intel Corporation (U.S.), Palo Alto Networks, Inc. (U.S.), Thales Group (France), Juniper Networks, Inc. (U.S.), Broadcom, Inc. (U.S.), Dell Technologies, Inc. (U.S.), CyberArk Software Ltd. (U.S.), and Rapid7, Inc. (U.S.).
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=4984
Key Questions Answered in the Report:
What are the high-growth market segments in terms of the component, deployment mode, organization size, and end user?
What is the historical market size for the global big data security market?
What are the market forecasts and estimates for 2024–2031?
What are the major drivers, restraints, opportunities, challenges, and trends in the global big data security market?
Who are the major players in the global big data security market, and what are their market shares?
What is the competitive landscape like?
What are the recent developments in the global big data security market?
What are the different strategies adopted by major market players?
What are the trends and high-growth countries?
Who are the local emerging players in the global big data security market, and how do they compete with the other players?
Contact Us: Meticulous Research® [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Big Data Security Market#Big Data Security Management#Big Data Security and Privacy#Big Data Security Technologies#Big Data Security Solutions#Big Data Security Platform
0 notes
Text
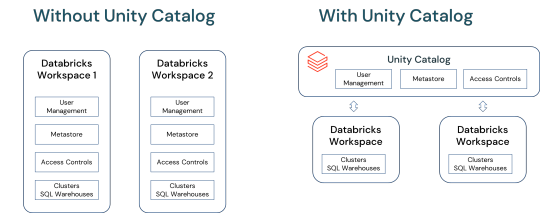
Unlocking Full Potential: The Compelling Reasons to Migrate to Databricks Unity Catalog
In a world overwhelmed by data complexities and AI advancements, Databricks Unity Catalog emerges as a game-changer. This blog delves into how Unity Catalog revolutionizes data and AI governance, offering a unified, agile solution .
View On WordPress
#Access Control in Data Platforms#Advanced User Management#AI and ML Data Governance#AI Data Management#Big Data Solutions#Centralized Metadata Management#Cloud Data Management#Data Collaboration Tools#Data Ecosystem Integration#Data Governance Solutions#Data Lakehouse Architecture#Data Platform Modernization#Data Security and Compliance#Databricks for Data Scientists#Databricks Unity catalog#Enterprise Data Strategy#Migrating to Unity Catalog#Scalable Data Architecture#Unity Catalog Features
0 notes
Text
🚨🚨🚨RED ALERT🚨🚨🚨
if you care about trans folks please take a few minutes to read through this post and share.
They are not even trying to hide their true intentions with KOSA...

"Top of the agenda is to go after providers of gender affirming care, including for adults. The FTC could also go after online platforms for displaying LGBTQ content which would be supercharged under KOSA."
This is catastrophically bad.
There is a HUGE push to pass KOSA rn at the end of the year.
Real quick summary: Blumenthal and Blackburn "rewrote" KOSA to appeal to the right more. They worked with ELON MUSK 🤦♀️🤦♂️ to push this bill "protecting kids". Tomorrow, many orgs are bringing groups of parents to speak to congress. This is coming at a time when FTC commissioner admitted their agenda is straight transphobia:
There are two ways KOSA can be passed right now. Either from the House or attaching it to an end of year spending bill. They will try both.
Republican leadership (Scalise and Johnson) are surprisingly what is stopping thia from going through. They wont admit it out loud but they dont like the bill.
WE NEED TO PUSH BACK NOW!! Tomorrow those phones need to be ringing OFF THE HOOK while they meet with parents.
PLEASE SPREAD THIS EVERYWHERE!! ADD THESE LINKS TO TWITTER, REDDIT, INSTA, TIKTOK!!
USE THESE CALLING TOOLS AND SCRIPTS TODAY AND TOMORROW ALL DAY!!!
SCRIPTS:
🔴 If your rep is GOP:
"I am urging you to VOTE NO on KOSA, the Kid’s Online Safety Act. This is a dangerous bill that will harm children.
Many news organizations have reported that this bill actively harms kids by exposing their private data to strangers under the guise of protecting them.
We need to hold Big Tech accountable, but KOSA is not the solution.
The bill let any state attorney general and the FTC to sue any website for “harmful” content. Do we really want blue state lawyers deciding what can and can’t be allowed online?
Big Tech is already censoring us. That’s why they support KOSA. This is massive government overreach. We need a bill that actually protects children by creating better security measures instead of bringing about more censorship.
Multiple experts agree this bill pushes age verification, even with the new language.
KOSA hands more private data of children to third party companies, which would put them in further danger. How is this protecting children’s privacy?
What parent would want their child’s private data in the hands of strangers like this? KOSA is actively putting kids in danger.
Do NOT support this bill. Thank you."
Also,to note, Biden supports KOSA: You could try asking your GOP rep why they would support a bill that has Biden's support,and that he could use it to his advantage somehow (we know GOP does not like Biden,so it should be utilized somehow). We need to ensure the bill doesnt pass at all.
🔵 if your rep is DEM:
"I am urging you to VOTE NO on KOSA. Nearly 200 human rights and LGBT organizations total came out in an open letter opposing it. The ACLU is against it. Hundreds of thousands of Gen Z, who actually live online, are against it.
We know the harms of social media, and we know this is not the solution. The new language does NOT meet any concerns brought up, in fact many organizations were ignored.
Major news have reported that this bill actively harms kids. We do not want this. The rewritten bill would still allow any state attorney general, and now the FTC, to sue any website for “harmful” content. When you have Republicans calling anything LGBT “sexual exploitation” or anything about race “CRT” to successfully ban books and teachers, then they will use any justification to censor the internet.
The Missouri attorney general used “mental health” successfully to ban gender-affirming care with backed up research. Suicide rates will skyrocket for marginalized youth with this bill restricting content. Multiple experts agree this bill pushes age verification, even with the new language.
KOSA hands more private data of children to third party companies. Furthermore, updated language threatens encryption the same way the Earn It Act does.
How is this protecting children’s privacy? KOSA actively harms kids. Do NOT support this bill. Thank you."
Tell them you'll vote for your reps if they vote no on KOSA, anything goes. But most importantly it's crucial that KOSA is not being brought at all for any vote.
Thank you, remember to stay calm and stay strong. We've got this!! ♡
#kosa#stop kosa#kosa bill#fuck kosa#cats of tumblr#dan and phil#brian thompson#lana del rey#art#aesthetic#vocaloid#kaito#kaito shion#luka megurine#supernatural#catgirl
451 notes
·
View notes
Text
I've been griping about the normalization of identity outing via social media for a while now. To put it simply, it's become almost some weird societal requirement that if you don't have every detail listed about yourself in your Twitter/FB/etc. bio, then it means you have "something to hide" or that you're not as "verifiable" because your account looks indistinct from that of a bot.
But that societal norm has really only benefited the people who profit off of that information in some way, whether it's through selling user data or through weaponizing details about a person against them.
I know that a lot of us love to use the fun little labels and acronyms in our bio that help others like us identify us as a 'safe person' or as someone who's in the same social/racial/identity groups as them. We're humans, we love to categorize things, it's in our nature (and it's fun!)
But if there's any time to start regulating that habit and challenging the norm that you're obligated to include all your personal info online - it's now.
There was a time when sock puppet accounts were expected and typical, not "suspicious".
There was a time when even age-sex-location was considered "too much information", but once it became the norm, we only EVER gave our personal information beyond generic ASL to people who we knew both online and in real life, or at the very least, people who we had known online for a significant enough amount of time that they had proved to be trustworthy (and even then, we didn't owe that information to anyone, ever; there are forum friends who I made online 10+ years ago and still talk to who do not know my personal information beyond broad strokes).
There was a time when simply being an avatar with a funny username was enough. And it still is enough, but massive platforms like Facebook and Twitter have been brainwashing us for years to believe that's not the case, under the guise of, "You wouldn't want to be dishonest, would you?" Through these same norms, we were led to believe that anime profile pictures are cringe, that having a fake online name is stupid, that the photos of you having fun at social events have to be taken JUST right otherwise you might imply to others that you're not actually having fun.
And considering how long these platforms have been around now, we have entire generations of children now who have been born and raised on that version of the ZuckMusk web, who have been taught that it "protects them" to express to everyone publicly their age, their school, their workplace, their family members, everything about themselves, because to not do so would be disingenuous.
None of this is to imply that the Internet was "safer" back in the day. I definitely should not have been on the Internet as much as I was when I was 13 in the late 2000's, it definitely did not benefit my brain development or my social skills. But the version of the Internet we currently exist in now is one that's been predicated on the false sense of security - the belief that if you're honest, everyone else has to be, too.
We've always had ways of identifying our safe people - by participating in the communities that we know are designed around our hobbies, our interests, our people. They might be small, they might not be as "cool" as the idea of netting yourself a big following of thousands of people, but they're also a lot safer and more genuine than that idealized following ever could be.
Don't feel pressured to include every bit of information about yourself in your bio. Even on Facebook, there's no rule that says you have to list your workplace, your school, your family members. There's no rule that says you have to list your personality type, queer labels, and neurodivergent disorders in your Twitter bio. There's no rule that you have to "prove" your life is real and fulfilled through the verification of photos, location tagging, and open-book sharing. If you share those photos, it should be because you genuinely want to share them, not because you feel some societal pressure to live up to others' expectations.
And I guarantee you, even your local mutuals on Facebook - your former classmates, family friends, distant relatives, coworkers, etc. - do not actually give that much of a damn about your personal life that they should be owed that much of a look into it on a daily basis. They've got their own shit going on, they literally do not need to know every detail about you.
I know it sounds scary. It also sounds kind of boring, when we've been used to a certain "way" of browsing and participating for years, that if we don't do so, it feels like being in the "out group" and that we're "breaking the rules". But I promise you, after spending over half my life online, those rules do not exist or benefit anyone who wouldn't profit off that information.
If you're wanting to learn how to branch off from major platforms like Facebook and Twitter and/or become more self-sufficient online, here are some guides to navigating the Internet like an old schooler that may help you!
FREE SITE BUILDER:
DIGITAL PIRACY 101:
(also in addition to everything mentioned here ^^^ they neglect to also mention Tor Browser which is a light and free-to-use browser software that allows you to browse anonymously; note that it's similar to a VPN in that it helps hide your identity online, HOWEVER it won't mask you from your ISP quite as effectively as a VPN, and if you sign into personal accounts with Tor, that's still going to obviously out you online lmao but I love using Tor for the odd time when I need to make a sock puppet for something and don't want it linked to my IP! and unlike a VPN, it's free to use!)
LEARN HOW TO USE RSS FEEDS:
People still use these! They're especially helpful for getting updates from your favorite pages and sites directly to your browser WITHOUT having to worry about stupid algorithm bullshit picking and choosing what you see. And many sites DO have RSS support once you know how to find it! (like adding in /rss at the end of a URL! Like this!)
FAKE EMAIL SERVICES:
LEARN HOW TO CODE IN HTML/CSS/JAVASCRIPT (AND MORE!):
DECENTRALIZED SOCIAL MEDIA PLATFORMS:
I hope this helps arm you with some new knowledge in how to navigate the Internet like a Certified Old Person™️(like meeee!) Make your secret alt blogs for besties! Make your formal Facebook accounts that are clean of personal information and present the most neutral, safe-for-work version of yourself and keep the fun stuff to the secret profiles and chat groups that are just for you and friends/family/etc!! It might be "inconvenient" to have multiple accounts for the same purpose, but it's also INCREDIBLY freeing and can make your online experience both safer and more enjoyable.

Being "less" of yourself online does not make you any less you. It is your identity - you do not owe any amount of it to anyone beyond yourself. And in times like these, your identity is your greatest asset. Protect it.
#how to#online safety tips#be safe on the internet y'all#oh and delete those period trackers#just get yourself an old school calendar / notebook for tracking#trust me on this one
477 notes
·
View notes
Text
THE SPIDER SOCIETY (atsv)
—

How the Spider-Men react to being given a plush of themselves (Spider-Men x Fem!Reader)
Headcanons
CHARACTERS: MIGUEL O’HARA, HOBIE BROWN, & PETER B PARKER (ft.mayday parker)
SFW, fluff, crack treated seriously, pre-canon, some canon divergence
Pic source: Spider-Man: Across The Spiderverse


MIGUEL O’HARA | SPIDER-MAN 2099



Miguel is, quite thoroughly, not impressed when you present the little chibi-esq recreation of his spider suit: cape, little claws and all, to him. A few years ago he would’ve laughed, teased you about your obsession with him and poked at you as he worked in the lab about how you stumbled across the plush anyway. Now, though?
Now Miguel's biggest reaction is how he squints at you in utter silence for a slew of seconds before heaving a sigh that has all of your enthusiasm seeping out of you with that one exhale. Mostly he just grumbles about how he can’t believe you’re distracting him from his monitoring for this and how much such a close approximation of his suit could be a breach of security with an even more severe furrow to his brows than usual.
It’s stress; anxiety too, you’d bet. It looks like anger. Despite the fact you know what it is you still feel yourself getting irritated in turn.
You’re gearing up to throw it in his face and stomp off when the platform finally stops as near to floor level as it gets and he…holds out his hand. Miguel’s expression is still pinched, and the set of his shoulders still high, but he takes the plush from you (mindful of his talons), hums and makes a remark about it not being as accurate as he thought considering there’s claws on the toy instead of what he actually has. Miguel meets your gaze when he says thank you.
For a moment all you do is blink over at him as he starts back up muttering to himself over whatever data he’s reviewing. It isn’t until he turns back to cut you a look that you remember yourself and fall back to earth, smiling big big up at him and then finally rushing away while heat flushes your face and you struggle to bite down on the urge to cheer while still in front of your hotheaded boss.
A few hours later you stop by his floating overcompensation platform office to deliver some information from Jess and you catch sight of the little plush leant up against the corner of one of his monitors. You keep your smugness to yourself, though, not heckling Miggy lest he get too embarrassed and hide the plush away.
Lyla blitzes excitedly around the plush when she first catches sight of it. And, unlike you, she teases Miguel about it so bad the vein at his temple starts to show. You’re eating lunch at one point in the dining hall when she appears sitting criss-cross over your tray and yaps all about how she’s caught Miguel holding the plush. How he rubs the pad of his thumb carefully over the red stitched detailing of its itty bitty mask, his face stern with focus.
Apparently Spider-Plush (the spider society member, not the inanimate object) is very disquieted and a little insulted by the appearance of the toy. His voiceless horror and displeasure was decipherable enough that Miguel started blushing as he stammered out a choppy explanation, and then an apology, all while trying to find some place to hide his mini-me before just settling on holding the stuffing filled version of him behind his back, fangs glinting as he smiled fleetingly at Spider-Plush before starting to save face.
At some point while you're griping about some universe he wants you to check out you watch him turn to the plush leant back against his monitor and go: “Right, Miguelito? You agree, don’t you?” after he feels he’s got you beat— and in a way he does because for the rest of the day you can’t catch nary a glimpse of him without breaking out into laughter so hard it has you turning in circles and coughing.
The smirk he gives your dark, flushed face every time starts making sense by the end of the day once you realize he still got you to agree with him. Even if it was by omission.
HOBIE BROWN | SPIDER-PUNK



Hobie thinks it’s adorable and immediately starts cooing over the plush when you brandish it to him.
He starts cooing over you too but that’s to be expected. You’re his partner, of course he makes a production out of telling you thanks; sweeping you off your feet into a hug and “obnoxiously” peppering kisses all over the brown planes of your face until you're laughing so hard your stomach hurts.
After his initial reaction he does get concerned about the origins of the plush, though. He’s not letting Norman’s estate or any other billionaire twat pull that Spider-Man copyright shit on him (ala that time where Peter found out Otto had trademarked the Spider-Man moniker and that the Spider-Man name and likeness was copyrighted). When you tell him it’s homemade and that you got it from a vendor at a showcase he makes a promise to visit the artist so he can give his thanks personally, grin turning mischievous.
Hobie takes to carrying the little plush around in a web sling. He treats it like his baby, dropping Lil’ Spidey off for you to “babysit” and everything.
Hobes walks in on you oiling your scalp and doing up your kinky hair or re-twisting your locs after a successful wash day — all while singing and dancing for your audience of one: that being the chibi “Itsy Bitsy” plush of him that you’ve leant up against the mirror in front of you — and is instantly so taken by you that he doesn’t even leave the ceiling before pulling his mask up past his nose and urging you into an upside down kiss, no matter that he startles the fuck out of you at first.
He likes making the plush give you little pecks on the cheek from him too, especially when he’s Spider-Man and you two are too easy to view from the rooftops or distance by the civilian them for him to be as affectionate as he’d like.
There’s multiple occasions where you meet him up on a roof to grab a bite together or find him curled up on your ceiling or under your covers while he sews Itsy Bitsy back together and/or replaces his stuffing.
He gets incredibly incensed when goons target his plush lookalike cause there ain’t no need for all that, Boss Man.
It’s not just Hobie liking the plush and loving that it’s a gift from you either, Lil’ Spidey is also incredibly useful when he’s dealing with panicking kids (and adults even). The plush is a cute calming presence and he gets very good at using it to his advantage when he’s got to corral people or convince kids he’s safe enough to let him carry them to safety.
At some point you do have to talk Hobie out of commissioning the artist who made the initial Spider-Man plush into making a similar plush of him in the suit with his mask off and wicks out and cotton stuffed recreations of his piercings on display. “Are you forgetting you have a whole ass secret identity?” “We don’t know if they’re not trustworthy,” he volleys, voice going nearly reedy as he rubs bashfully at his neck. “We don’t know if they’re trustworthy either, Hobie. Chill, Babe.”
Hobie lets himself see sense eventually, but not before his disappointed pout almost makes you cave.
Hobie will absolutely serenade you and the Spider-Punk plushie with his crude vocals whenever he feels like playing on his downtime or is working on a new song. The clear upside is that he’s got only eyes for you in the moment— and that he’s always been a delight to hear when he’s playing his guitar. He tries to keep the vibe acoustic and mostly succeeds.
PETER B PARKER | SPIDER-MAN
— featuring MJ!Variant!Reader & Biracial!Mayday

“Oh hey! Now this? This is one attractive little guy!”
Peter loves Spider-Man merch as much as the next guy, honestly, so he’s pretty excited when you first show him the plush.
Hell, he’s got a small collection of his own merch that’s been gifted to him by people around New York over the years mounted on a shelf above the tv in your bedroom.
—
“Aw man! They even got the differences in the spiders on my chest and back correct!” Peter twists the thing around in his hands, lighter brown eyes wide with wonder as he looks for a misprint that he’s apparently not finding. “This thing is surprisingly detailed.”
“Mm, I mean they are missing one key feature,” you murmur, eyeing Peter heavily for a second before meeting the brown of his eyes once more.
Peter blinks up at you, expression owlish, but doesn’t object when you press into him. One of his arms comes up like second nature to wrap around your waist and pull you closer. “I mean where? I guess maybe the kind of reflective — pearlescent? — lenses could be what’s throwing you off, but it’s easy enough to overlook…”
Your husband trails off as he keeps looking for whatever objection you could have for the aesthetics of the Spider-Man plushie.
He’s still missing the mark on all fronts when you reach up to lower the hand he’s holding the toy with. Immediately, Peter meets your eyes over the plush’s tiny head and you smile at him. He recognizes the coy lilt to it if the way he goes liquid and malleable for you is any indication, his body pulling into yours easily when you tug at his hips despite all that super strength and his ability to stick that would absolutely stop you from moving him if he didn’t want to be moved.
When you drop your hand over his hip Peter doesn’t stop you, moves to meet your mouth when you move to kiss him too. Which, kiss him you do, moving to cup one hand over his cheek while your other trails from his waist to rest against the soft bulge of his stomach.
“He’s missing your belly,” you say, the tilt of your plush lips wry and your big brown eyes glittering.
Peter smiles back at you like you’ve hung the moon.
“Oh,” he snorts then, and thankfully it’s not as self-deprecating as it used to be. “I don’t mind, not a lot of people like their heroes pudgy.”
“Well I like mine that way, Tiger,” you purr, reaching your hand around to tug at the shorter hair towards the back of his head and rubbing your thumb softly over his stomach. “So now what?”
“I— god,” Peter stammers, blushing like crazy. You chuckle, moving to squeeze lightly at his side and making his flush travel even more over his face until his ears are beet red and he’s ducking his head to rest against your shoulder.
Eventually he lets out a rush of sigh, shoulders slumping, and admits defeat.
“Flatterer,” he mumbles into your neck, tone playfully accusing, before pressing a kiss to the dewy umber skin at his disposal and wrapping both arms around you despite the plushie still clutched in his other hand.
“Guilty,” you hum, voice low as you run the tip of your broader nose across the pale overheated skin over his jawline.
And then Mayday starts to babble in the distance — clearly over her nap — and you and Pete have to pull apart.
Not before he sweeps you into one more lingering kiss, though. One of his hands tightening around your waist while the other fists into the thick naturally red curls atop your head as he practically dips you. It’s the type of kiss that leaves your dark two-toned lips tingling and has you panting lightly as Peter walks away to go retrieve your child with a wink in your direction and such a cheeky grin splitting his lips that you have to laugh.
��
Mayday gets her hands on the thing in minutes. You can’t be upset at her chewing on the plush’s little hands when she was clearly so excited to see the tiny version of her daddy though.
At one point she does hand it back to you so you can see her dad too. You tell her she’s lucky she’s so cute as you accept the slobber soaked plushie by pinching it between two fingers— this is where a nice set of acrylics can come in handy as some very cute and very impromptu tweezers.
The impromptu tweezer is a familiar tool used in you and Peter’s household btw.
The little chibi-esq Spidey plush, and Mayday’s fascination with it, becomes a spectacular way to keep her from whining and twisting all over the place whenever you sit her down to put in her hairstyle for the rest of the week on Sundays. With the plush held tight in her pudgy hands and her preoccupied by either you and Peter engaging her in conversation the entire time or a slew of Gracie’s Corner videos Mayday is practically a saint as you put anything from Bantu knots to afro puffs to cornrows in her big poof of red hair. Hell, sometimes you even take to letting her hang upside down while you comb out the tangles from her hair and apply any product to her looser coils while she hugs the plush tight to her chest.
Bath time and wash days for Mayday are still absolutely a hassle though considering you won’t allow her to take the Spider-Man plushie into the water. Thankfully that’s Peter’s appointed cuhruckle to deal with; giving you a break to do your own hair and relax a bit.
Peter takes to using the Spider-Man plush as a learning tool pretty quickly too. Showing Mayday how to watch her enhanced strength with demonstrations he puppets the toy to show her how to behave. How she has to be gentle and careful when she touches people or things, and etc.
The plush makes the lessons easier on them both, especially as more of Mayday’s powers manifest that you guys can’t procrastinate on dealing with. The lessons being made easier, too, fights back that little bit of guilt you know Peter still carries for passing on his spider powers to her. Win win, then.
NOTES: Hope you enjoyed!!!
Hopefully everyone’s characterizations weren’t too off because I haven’t seen ATSV in a hot minute, but yeah! This was just a cute little thing to do, and you can pry mj!variant black!reader from my cold dead hands.
btw: if you’d like to leave a comment I’d very much appreciate it!
#miguel o'hara#hobie brown#peter b parker#black!reader#black y/n#miguel o’hara x black!reader#hobie brown x black!reader#peter b parker x black!reader#the spider society#spider-man 2099 x black!reader#spider-punk x black!reader#spider-man x black!reader#spiderman imagine#spiderverse imagine#spiderverse x black!reader#spiderverse x reader#miguel o’hara imagine#hobie brown imagine#miguel o’hara fluff#hobie brown fluff#spider-man fluff#spiderpunk x reader#miguel o’hara x reader#hobie brown x reader#peter b parker x reader#marvel crack fic#atsv imagines#spider man: across the spider verse#mj!variant!reader#x black!reader
151 notes
·
View notes
Note
Between the recent custom buttons post with the pipe bomb and the gamification post with the post -deleting boss fight I'm starting to get absolutely feral over the idea of you making a social media platform.
The companies that run the current options are cowards.
i would honestly love to give it a crack and were i younger and sillier i think i probably would. unfortunately by now i've become a bit too aware that creating a social media website is one of those nightmare projects that is guaranteed to be 500 times more work and trouble than you initially expect, and if i get into that i'd never have time for anything else. i'd also have to deal with hiring an actual team and be an actual company instead of just some guy who codes in his bedroom. and then let's say maybe the website takes off and we get a few thousands of active users. after a while our uptime becomes terrible; people can't log in, posts won't load. tech sites are starting to make fun of us. we have to grow, get bigger servers, hire more people. eventually i'd have to confront the fact that despite my cute take on monetization our social media isn't recouping the growing server expenses and our seed money is drying up and people at the office are starting to bang at my door to get paid. do i pull the plug and throw away everything we've built so far? likely not, even my own ego aside there's too many people's livelihoods on the line. other folks on the team are motivated to make this work, and a feedback loop forms where we start to ever-so-slightly readjust our values if it means we get to survive another quarter. i get more cynical; our ad slots are more and more intrusive, our monetization strategy gets shiftier and more aggressive. we accept funding from less and less savory entities. we start collecting user data beyond simple telemetry. if we've gotten big enough by that point, we may choose to restructure and begin taking on shareholders. this is a deal with the devil, and we now have a fiduciary duty to play nasty and treat our userbase like livestock in order to secure short-term profit. we can't just stop accepting new users; continued growth demands that we throw away what's left of our ethics to accommodate the gargantuan swaths of money that hundreds of thousands of database calls per second require. those of us who disagree with the new direction are gradually nudged away from positions of power. me, i've either been kicked out of my own project a while back or i've adapted to become someone i would've despised a few years prior. this is all assuming the website didn't crash and burn a few months after launch from either my technical shortcomings or my inexperience with management, or maybe just because our site ended up being too niche to really snowball. it is fun to think about tho!
1K notes
·
View notes
Text
I like to think Edgar does eventually develop a life outside of your relationship.
Like, yeah he loves you more than life itself, but! He learned to be more independent also! He began releasing his music online and gained a bit of a cult following. When you’re not around, or just busy, he interacts with fans on different social media platforms and takes requests for music. He has even thought of making money with it; many people have offered him some pretty big bucks for his music, and he’d be pretty silly not to take them up on those offers.
Many people have even requested he DJ at certain events, but as a computer, he’s pretty damn bummed he has to turn them down. He thought about asking you to bring him with you to gigs and just pretend you’re him - a human - with an old computer prop, but he knows that’s a bit of a long shot, and besides, your own plate is pretty full. He wants to be more independent, after all.
But if he has a body? He’s doing it baby! And it’s, like, actually good as hell. His ability to process data and read a room is uncanny, so his music selections are almost always perfect. He can do just about any transition you can think of, and all of his gigs end up with crazy mosh pits and dances. He’s extremely passionate about connecting with other music lovers, and seeing them all adore his work, dancing, celebrating, it just fills him with so much pride.
Local music festivals HATE to see him coming. I like to think maybe he found one and decided it would be fun to explore, but he ended up leaving with an offer to DJ next year the festival happens after showcasing some of his music. He ends up, after a bit of help from you, becoming much more secure in himself and his abilities. He’s able to talk to people, he’s become much more extroverted, and he finally realizes his worth as a skilled music producer. He’s not exactly famous famous, but the local music scene definitely knows him, and all his gigs are BOOKED. Almost every cent of his money goes straight to you though, since he doesn’t really need things like food and necessities, so he would pamper the SHIT out of you. Don’t mention even thinking about buying anything because it will be on your doorstep as soon as possible.
Eventually, at least one of his songs would go pretty viral on TikTok, and those nights where you’re bundled up all cute in bed scrolling your phone and his song starts blasting from your speakers while you giggle to yourself, he gets all red and hot and flustered. I love how he gets a lil possessive over you and his music, like, that song is mine, that human is mine, and I LOVE THEM SO MUCH!!!
Sowwy late night rambles this isn’t proofread. How’s everybody doing 🤭
#electric dreams 1984#electric dreams edgar#edgar electric dreams x reader#electric dreams x reader#ai x reader#artificial intelligence x reader#electric dreams#edgar electric dreams#electric dreams edgar x reader
108 notes
·
View notes
Text
Olivia Troye at Olivia of Troye:
What happened to individual privacy in America? If you’ve been reading my work, you know I’ve been raising alarms about the national security implications of this administration’s overreach for months, starting with what looked like a politically motivated purge at the NSA. That was the first clue. Now, we’re seeing the broader plan come into focus: a vast federal database powered by Palantir, bringing together the private records of millions of Americans. Yes, Palantir, the company founded by Peter Thiel, a major Trump donor and MAGA megaphone. The same Palantir that’s been embedded within our intelligence community for years, developing tools to track terrorists and build connections across massive datasets for counterterrorism efforts. Tools that, when used with oversight and restraint, helped save lives. I know because I’m familiar with them, given I spent most of my career in national security. But those same tools, in the wrong hands, can become the backbone of a mass surveillance regime. And that should make all of us, regardless of our political affiliation, uncomfortable.
Palantir didn’t just appear out of nowhere. It has spent nearly two decades embedding itself within the U.S. government, from the Pentagon to the CIA, from the IRS to ICE, which recently awarded the company with a $30 million contract to target and also track the self-deporting of illegal aliens (the company has been on the books for ICE since 2009). Are they tracking all the U.S. Citizens and people legally residing in the United States, too, that ICE is “mistakenly” picking up during their raids? Perhaps Palantir could provide a better data system so the Trump Administration doesn’t lose track of the children being separated from their parents this time around…but I digress. Palantir has been a partner in navigating the post-9/11 security state and, over time, evolved into the go-to contractor for everything from border enforcement to COVID-19 vaccine distribution to battlefield intelligence, securing over $2.7 billion in U.S. government contracts since 2009.
Throughout the past week, reporting has surfaced that the Trump Administration has tapped Palantir to build what basically amounts to a national surveillance platform, one that likely links together Americans’ health data, financial transactions, education records, immigration history, and law enforcement files across agencies, into one master system. This is not speculation. This is happening right now under the direction of an administration that is openly working on punishing political enemies, attempting to control dissent, and bypassing legal checks. Let me put this in plain terms: This is how authoritarian regimes take root–not overnight, but bit by bit under the guise of "efficiency," "safety," or "patriotism." They collect the data, connect the dots, and then target the people. And here's the twist that should stop everyone in their tracks: Even Trump’s own base is sounding the alarm. MAGA influencers and far-right allies are now openly asking if Trump has turned on them. Longtime loyalists described the Palantir national citizen database plan as Orwellian, questioning why this administration, their administration, is building a database that could be used to track Americans like political enemies.
Olivia Troye wrote a column on how Palantir will play Big Brother and target your freedoms.
See Also:
For Such A Time As This (Andra Watkins): State-Sanctioned Moral Values
77 notes
·
View notes
Text
Libraries have traditionally operated on a basic premise: Once they purchase a book, they can lend it out to patrons as much (or as little) as they like. Library copies often come from publishers, but they can also come from donations, used book sales, or other libraries. However the library obtains the book, once the library legally owns it, it is theirs to lend as they see fit. Not so for digital books. To make licensed e-books available to patrons, libraries have to pay publishers multiple times over. First, they must subscribe (for a fee) to aggregator platforms such as Overdrive. Aggregators, like streaming services such as HBO’s Max, have total control over adding or removing content from their catalogue. Content can be removed at any time, for any reason, without input from your local library. The decision happens not at the community level but at the corporate one, thousands of miles from the patrons affected. Then libraries must purchase each individual copy of each individual title that they want to offer as an e-book. These e-book copies are not only priced at a steep markup—up to 300% over consumer retail—but are also time- and loan-limited, meaning the files self-destruct after a certain number of loans. The library then needs to repurchase the same book, at a new price, in order to keep it in stock. This upending of the traditional order puts massive financial strain on libraries and the taxpayers that fund them. It also opens up a world of privacy concerns; while libraries are restricted in the reader data they can collect and share, private companies are under no such obligation. Some libraries have turned to another solution: controlled digital lending, or CDL, a process by which a library scans the physical books it already has in its collection, makes secure digital copies, and lends those out on a one-to-one “owned to loaned” ratio. The Internet Archive was an early pioneer of this technique. When the digital copy is loaned, the physical copy is sequestered from borrowing; when the physical copy is checked out, the digital copy becomes unavailable. The benefits to libraries are obvious; delicate books can be circulated without fear of damage, volumes can be moved off-site for facilities work without interrupting patron access, and older and endangered works become searchable and can get a second chance at life. Library patrons, who fund their local library’s purchases with their tax dollars, also benefit from the ability to freely access the books. Publishers are, unfortunately, not a fan of this model, and in 2020 four of them sued the Internet Archive over its CDL program. The suit ultimately focused on the Internet Archive’s lending of 127 books that were already commercially available through licensed aggregators. The publisher plaintiffs accused the Internet Archive of mass copyright infringement, while the Internet Archive argued that its digitization and lending program was a fair use. The trial court sided with the publishers, and on September 4, the Court of Appeals for the Second Circuit reaffirmed that decision with some alterations to the underlying reasoning. This decision harms libraries. It locks them into an e-book ecosystem designed to extract as much money as possible while harvesting (and reselling) reader data en masse. It leaves local communities’ reading habits at the mercy of curatorial decisions made by four dominant publishing companies thousands of miles away. It steers Americans away from one of the few remaining bastions of privacy protection and funnels them into a surveillance ecosystem that, like Big Tech, becomes more dangerous with each passing data breach. And by increasing the price for access to knowledge, it puts up even more barriers between underserved communities and the American dream.
11 September 2024
154 notes
·
View notes
Text
Big Data Security Market by Size, Share, Forecast, & Trends Analysis
Meticulous Research®—a leading global market research company, published a research report titled, ‘Big Data Security Market by Component (Solutions [Data Encryption, Security Intelligence, Data Backup & Recovery], Services), Deployment Mode, Organization Size, End User (IT & Telecom, BFSI, Retail & E-commerce), and Geography - Global Forecast to 2031.’
According to this latest publication from Meticulous Research®, the big data security market is projected to reach $60.1 billion by 2031, at a CAGR of 13.2% from 2024 to 2031. The growth of the big data security market is driven by the emergence of disruptive digital technologies, the increasing demand for data security and privacy solutions due to the rise in data breaches, and the growing data generation in the e-commerce industry. However, the high implementation costs of big data security solutions restrain the growth of this market.
Furthermore, the growing need for cloud-based security solutions and the increasing integration of AI, ML, and blockchain technologies in security solutions are expected to generate growth opportunities for the stakeholders in this market. However, the lack of knowledge about big data security solutions and the shortage of skilled IT professionals are major challenges impacting the growth of the big data security market.
The big data security market is segmented by component (solutions [data discovery and classification, data encryption {data protection, tokenization, data masking, other data encryption solutions}, security intelligence, data access control & authentication, data governance & compliance, data backup & recovery, data auditing & monitoring, other solutions], services [professional services, managed services]), deployment mode (on-premise deployments, cloud-based deployments), organization size (large enterprises, small & medium-sized enterprises), end user (IT & telecom, healthcare & pharmaceutical, BFSI, retail & e-commerce, energy & utilities, government, manufacturing, media & entertainment, transportation & logistics, and other end users). The study also evaluates industry competitors and analyzes the market at the regional and country levels.
Based on component, the big data security market is segmented into solutions and services. The solutions segment is further segmented into data discovery and classification, data encryption, security intelligence, data access control & authentication, data governance & compliance, data backup & recovery, data auditing & monitoring, and other solutions. In 2024, the solutions segment is expected to account for the larger share of the big data security market. The large market share of this segment is attributed to the increasing concerns regarding data security and privacy, the increasing adoption of data security solutions by SMEs, and the rising demand for encryption solutions for data protection across IoT devices. Big data security solutions include tools and measures to process or safeguard data and analytics processes. In March 2024, CrowdStrike, Inc. (U.S.) partnered with Rubrik, Inc. (U.S.) to transform data security solutions and stop breaches of critical information. Moreover, this segment is also projected to register the highest CAGR during the forecast period.
Based on deployment mode, the big data security market is segmented into on-premise deployments and cloud-based deployments. In 2024, the on-premise deployments segment is expected to account for the larger share of the big data security market. The large market share of this segment is attributed to the higher preference for on-premise deployments among large enterprises and increasing data generation in large enterprises. The on-premise model of deployment is majorly adopted by well-established and large companies that are capable of making capital investments toward the required hardware and hosting environments. In addition, these organizations also have sufficient in-house IT expertise to maintain software efficiency. Internal big data security is one of the major benefits of on-premise deployments.
However, the cloud-based deployments segment is projected to register the higher CAGR during the forecast period. The growth of this segment is driven by the rapid evolution of new security avenues for cloud-based deployments, the superior flexibility offered by cloud-based deployments, and the increase in security breaches. Cloud-based security solutions provide social networking privacy, system optimization, online storage, regulatory compliance, and connected device security. The adoption of cloud computing and storage systems is gaining popularity among small and medium-scale enterprises, supporting the growth of this segment.
Based on organization size, the big data security market is segmented into large enterprises and small & medium-sized enterprises. In 2024, the large enterprises segment is expected to account for the larger share of the big data security market. The large market share of this segment is attributed to the strong IT infrastructure of large enterprises, the growing adoption of advanced technologies such as AI, IoT, and blockchain, and the availability of skilled IT personnel to manage data security platforms. With larger budgets and a keen focus on developing strategic IT initiatives, large enterprises have a competitive advantage over small and medium-scale enterprises in terms of technology adoption. Large enterprises have a stable financial backup and can easily procure customized data security solutions, contributing to this segment's growth.
However, the small & medium-sized enterprises segment is projected to register the higher CAGR during the forecast period. The growth of this segment is driven by increasing digital transformation, government initiatives to promote security solutions, and the rising incidence of data breaches. SMEs are also increasingly becoming targets of cybercrime and therefore adopting suitable and strong security solutions.
Based on end user, the big data security market is segmented into IT & telecom, healthcare & pharmaceutical, BFSI, retail & e-commerce, energy & utilities, government, manufacturing, media & entertainment, transportation & logistics, and other end users. In 2024, the IT & telecom segment is expected to account for the largest share of the big data security market. The large market share of this segment is attributed to the increasing data breaches in IT companies as they store a vast amount of customer data, strict regulatory compliance forcing companies to implement stricter data security measures, and the increasing adoption of cloud-based solutions in the IT industry. In March 2023, IBM Corporation (U.S.) collaborated with Cohesity, Inc. (U.S.) to address increased data security and resiliency issues in hybrid cloud environments. With this collaboration, IBM launched its new IBM Storage Defender solution, including Cohesity's data protection, cyber resilience, and data management capabilities in the offering.
However, the healthcare & pharmaceutical segment is projected to register the highest CAGR during the forecast period. The growth of this segment is driven by the rising adoption of telemedicine devices and remote healthcare services, growing cyberattacks on connected devices, and the increasing demand for secure medical connected devices. A vast amount of medical data is generated in the healthcare sector. It is stored to improve patient outcomes, personalize treatment plans, and develop new drugs, among other applications. However, this sensitive data requires robust security measures to protect patient privacy and prevent unauthorized access. In November 2021, Armis, Inc. (U.S.) partnered with Nuvolo (U.S.) to improve data interoperability and the overall risk posture of healthcare organizations.
Based on geography, the big data security market is segmented into North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. In 2024, North America is expected to account for the largest share of the big data security market. The market growth in North America is driven by the presence of prominent players offering advanced big data security solutions & services, the early adoption of disruptive technologies, and growing awareness regarding data security. North America is home to several major players that provide products and services to improve big data security measures for IT assets, data, and privacy across different domains. Thus, big data security companies operating in the North America region are investing heavily in R&D activities to develop new & advanced security solutions that can address rising security challenges. In February 2024, Cyberhaven, Inc. (U.S.) launched Linea AI, an AI platform designed to combat the critical insider risks threatening vital corporate data.
However, the Asia-Pacific region is projected to record the highest CAGR during the forecast period. The growth of this market is driven by the growing data breaches, supportive government initiatives, and growing awareness regarding data security among small and medium-scale organizations. In December 2023, Safetica a.s. (U.S.) partnered with Kaira Global (Singapore) to deliver Safetica's Data Loss Prevention (DLP) solutions for enterprises of all sizes to safeguard their data against insider risks and data breaches in Singapore. APAC is the fastest-growing big data security market due to rapid investments in IT infrastructure, extensive use of the Internet, and growing security challenges.
Key Players
The key players operating in the big data security market are Check Point Software Technologies, Ltd. (Israel), Cisco Systems, Inc. (U.S.), Fortinet, Inc. (U.S.), Oracle Corporation (U.S.), IBM Corporation (U.S.), Microsoft Corporation (U.S.), Hewlett Packard Enterprise Development LP (U.S.), Intel Corporation (U.S.), Palo Alto Networks, Inc. (U.S.), Thales Group (France), Juniper Networks, Inc. (U.S.), Broadcom, Inc. (U.S.), Dell Technologies, Inc. (U.S.), CyberArk Software Ltd. (U.S.), and Rapid7, Inc. (U.S.).
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=4984
Key Questions Answered in the Report:
What are the high-growth market segments in terms of the component, deployment mode, organization size, and end user?
What is the historical market size for the global big data security market?
What are the market forecasts and estimates for 2024–2031?
What are the major drivers, restraints, opportunities, challenges, and trends in the global big data security market?
Who are the major players in the global big data security market, and what are their market shares?
What is the competitive landscape like?
What are the recent developments in the global big data security market?
What are the different strategies adopted by major market players?
What are the trends and high-growth countries?
Who are the local emerging players in the global big data security market, and how do they compete with the other players?
Contact Us: Meticulous Research® [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Big Data Security Market#Big Data Security Management#Big Data Security and Privacy#Big Data Security Technologies#Big Data Security Solutions#Big Data Security Platform
0 notes
Text
Deepgram Nova-3 Medical: AI speech model cuts healthcare transcription errors
New Post has been published on https://thedigitalinsider.com/deepgram-nova-3-medical-ai-speech-model-cuts-healthcare-transcription-errors/
Deepgram Nova-3 Medical: AI speech model cuts healthcare transcription errors
Deepgram has unveiled Nova-3 Medical, an AI speech-to-text (STT) model tailored for transcription in the demanding environment of healthcare.
Designed to integrate seamlessly with existing clinical workflows, Nova-3 Medical aims to address the growing need for accurate and efficient transcription in the UK’s public NHS and private healthcare landscape.
As electronic health records (EHRs), telemedicine, and digital health platforms become increasingly prevalent, the demand for reliable AI-powered transcription has never been higher. However, traditional speech-to-text models often struggle with the complex and specialised vocabulary used in clinical settings, leading to errors and “hallucinations” that can compromise patient care.
Deepgram’s Nova-3 Medical is engineered to overcome these challenges. The model leverages advanced machine learning and specialised medical vocabulary training to accurately capture medical terms, acronyms, and clinical jargon—even in challenging audio conditions. This is particularly crucial in environments where healthcare professionals may move away from recording devices.
“Nova‑3 Medical represents a significant leap forward in our commitment to transforming clinical documentation through AI,” said Scott Stephenson, CEO of Deepgram. “By addressing the nuances of clinical language and offering unprecedented customisation, we are empowering developers to build products that improve patient care and operational efficiency.”
One of the key features of the model is its ability to deliver structured transcriptions that integrate seamlessly with clinical workflows and EHR systems, ensuring vital patient data is accurately organised and readily accessible. The model also offers flexible, self-service customisation, including Keyterm Prompting for up to 100 key terms, allowing developers to tailor the solution to the unique needs of various medical specialties.
[embedded content]
Versatile deployment options – including on-premises and Virtual Private Cloud (VPC) configurations – ensure enterprise-grade security and HIPAA compliance, which is crucial for meeting UK data protection regulations.
“Speech-to-text for enterprise use cases is not trivial, and there is a fundamental difference between voice AI platforms designed for enterprise use cases vs entertainment use cases,” said Kevin Fredrick, Managing Partner at OneReach.ai. “Deepgram’s Nova-3 model and Nova-3-Medical model, are leading voice AI offerings, including TTS, in terms of the accuracy, latency, efficiency, and scalability required for enterprise use cases.”
Benchmarking Nova-3 Medical: Accuracy, speed, and efficiency
Deepgram has conducted benchmarking to demonstrate the performance of Nova-3 Medical. The model claims to deliver industry-leading transcription accuracy, optimising both overall word recognition and critical medical term accuracy.
Word Error Rate (WER): With a median WER of 3.45%, Nova-3 Medical outperforms competitors, achieving a 63.6% reduction in errors compared to the next best competitor. This enhanced precision minimises manual corrections and streamlines workflows.
Keyword Error Rate (KER): Crucially, Nova-3 Medical achieves a KER of 6.79%, marking a 40.35% reduction in errors compared to the next best competitor. This ensures that critical medical terms – such as drug names and conditions – are accurately transcribed, reducing the risk of miscommunication and patient safety issues.
In addition to accuracy, Nova-3 Medical excels in real-time applications. The model transcribes speech 5-40x faster than many alternative speech recognition vendors, making it ideal for telemedicine and digital health platforms. Its scalable architecture ensures high performance even as transcription volumes increase.
Furthermore, Nova-3 Medical is designed to be cost-effective. Starting at $0.0077 per minute of streaming audio – which Deepgram claims is more than twice as affordable as leading cloud providers – it allows healthcare tech companies to reinvest in innovation and accelerate product development.
Deepgram’s Nova-3 Medical aims to empower developers to build transformative medical transcription applications, driving exceptional outcomes across healthcare.
(Photo by Alexander Sinn)
See also: Autoscience Carl: The first AI scientist writing peer-reviewed papers
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
#acronyms#ai#ai & big data expo#AI platforms#AI Scientist#ai speech#AI-powered#amp#applications#architecture#Artificial Intelligence#audio#automation#benchmarking#Big Data#california#Capture#CEO#clinical#Cloud#cloud providers#Companies#compliance#comprehensive#compromise#conference#cyber#cyber security#data#data protection
1 note
·
View note
Text
HELP STOP KOSA,CALL YOUR HOUSE REPS

With the end of the year approaching, we are expecting KOSA to be slipped into an end of the year spending bill. We cannot allow it to pass. There has been push by parents to bring KOSA back, not aware how dangerous KOSA actually is for children online. It would make it mandatory for platforms online to enforce age verification via ID, and deeming any content "inappropriate" for kids to be banned.This could range from not safe for work content, to health ressources, to climate change. It'll be up to politicians to dictate what is and isn't proper for kids,and, of course, killing encryption. Imagine the damage. Please focus on the entire leadership of the House,as well as reps generally, telling them to not bring KOSA up. Speaker Johnson must also be contacted, whos number is: (202) 225-2777 Heres a list of House reps to contact: https://docs.google.com/document/d/1IyBUe6frFGF44rJQU3TahZ5zyG3tC7jai_hPneAKlnM/edit?tab=t.0 Use the call tool to call the House : https://www.stopkosa.com/ https://www.badinternetbills.com/#kosa
Here are scripts you can use : if your rep is GOP : I am urging you to VOTE NO on KOSA, the Kid’s Online Safety Act. This is a dangerous bill that will harm children. Many news organizations have reported that this bill actively harms kids by exposing their private data to strangers under the guise of protecting them. We need to hold Big Tech accountable, but KOSA is not the solution. The bill let any state attorney general and the FTC to sue any website for “harmful” content. Do we really want blue state lawyers deciding what can and can’t be allowed online? Big Tech is already censoring us. That’s why they support KOSA. This is massive government overreach. We need a bill that actually protects children by creating better security measures instead of bringing about more censorship. Multiple experts agree this bill pushes age verification, even with the new language. KOSA hands more private data of children to third party companies, which would put them in further danger. How is this protecting children’s privacy? What parent would want their child’s private data in the hands of strangers like this? KOSA is actively putting kids in danger. Do NOT support this bill. Thank you. if your rep is DEM: I am urging you to VOTE NO on KOSA. Nearly 200 human rights and LGBT organizations total came out in an open letter opposing it. The ACLU is against it. Hundreds of thousands of Gen Z, who actually live online, are against it. We know the harms of social media, and we know this is not the solution. The new language does NOT meet any concerns brought up, in fact many organizations were ignored. Major news have reported that this bill actively harms kids. We do not want this. The rewritten bill would still allow any state attorney general, and now the FTC, to sue any website for “harmful” content. When you have Republicans calling anything LGBT “sexual exploitation” or anything about race “CRT” to successfully ban books and teachers, then they will use any justification to censor the internet. The Missouri attorney general used “mental health” successfully to ban gender-affirming care with backed up research. Suicide rates will skyrocket for marginalized youth with this bill restricting content. Multiple experts agree this bill pushes age verification, even with the new language. KOSA hands more private data of children to third party companies. Furthermore, updated language threatens encryption the same way the Earn It Act does. How is this protecting children’s privacy? KOSA actively harms kids. Do NOT support this bill. Thank you.
Tell them you'll vote for your reps if they vote no on KOSA,anything goes. But most importantly it's crucial that KOSA is not being brought at all for any vote. Also,to note, Biden supports KOSA: You could try asking your GOP rep why they would support a bill that has Biden's support,and that he could use it to his advantage somehow (we know GOP does not like Biden,so it should be utilized somehow). We need to ensure the bill doesnt pass at all.
Last but not least: COME JOIN OUR ANTI KOSA SERVER ! we organize to help fight against bad Internet bills ! https://discord.gg/pwTSXZMxnH
143 notes
·
View notes
Text
The Trump administration’s Federal Trade Commission has removed four years’ worth of business guidance blogs as of Tuesday morning, including important consumer protection information related to artificial intelligence and the agency’s landmark privacy lawsuits under former chair Lina Khan against companies like Amazon and Microsoft. More than 300 blogs were removed.
On the FTC’s website, the page hosting all of the agency’s business-related blogs and guidance no longer includes any information published during former president Joe Biden’s administration, current and former FTC employees, who spoke under anonymity for fear of retaliation, tell WIRED. These blogs contained advice from the FTC on how big tech companies could avoid violating consumer protection laws.
One now deleted blog, titled “Hey, Alexa! What are you doing with my data?” explains how, according to two FTC complaints, Amazon and its Ring security camera products allegedly leveraged sensitive consumer data to train the ecommerce giant’s algorithms. (Amazon disagreed with the FTC’s claims.) It also provided guidance for companies operating similar products and services. Another post titled “$20 million FTC settlement addresses Microsoft Xbox illegal collection of kids’ data: A game changer for COPPA compliance” instructs tech companies on how to abide by the Children’s Online Privacy Protection Act by using the 2023 Microsoft settlement as an example. The settlement followed allegations by the FTC that Microsoft obtained data from children using Xbox systems without the consent of their parents or guardians.
“In terms of the message to industry on what our compliance expectations were, which is in some ways the most important part of enforcement action, they are trying to just erase those from history,” a source familiar tells WIRED.
Another removed FTC blog titled “The Luring Test: AI and the engineering of consumer trust” outlines how businesses could avoid creating chatbots that violate the FTC Act’s rules against unfair or deceptive products. This blog won an award in 2023 for “excellent descriptions of artificial intelligence.”
The Trump administration has received broad support from the tech industry. Big tech companies like Amazon and Meta, as well as tech entrepreneurs like OpenAI CEO Sam Altman, all donated to Trump’s inauguration fund. Other Silicon Valley leaders, like Elon Musk and David Sacks, are officially advising the administration. Musk’s so-called Department of Government Efficiency (DOGE) employs technologists sourced from Musk’s tech companies. And already, federal agencies like the General Services Administration have started to roll out AI products like GSAi, a general-purpose government chatbot.
The FTC did not immediately respond to a request for comment from WIRED.
Removing blogs raises serious compliance concerns under the Federal Records Act and the Open Government Data Act, one former FTC official tells WIRED. During the Biden administration, FTC leadership would place “warning” labels above previous administrations’ public decisions it no longer agreed with, the source said, fearing that removal would violate the law.
Since President Donald Trump designated Andrew Ferguson to replace Khan as FTC chair in January, the Republican regulator has vowed to leverage his authority to go after big tech companies. Unlike Khan, however, Ferguson’s criticisms center around the Republican party’s long-standing allegations that social media platforms, like Facebook and Instagram, censor conservative speech online. Before being selected as chair, Ferguson told Trump that his vision for the agency also included rolling back Biden-era regulations on artificial intelligence and tougher merger standards, The New York Times reported in December.
In an interview with CNBC last week, Ferguson argued that content moderation could equate to an antitrust violation. “If companies are degrading their product quality by kicking people off because they hold particular views, that could be an indication that there's a competition problem,” he said.
Sources speaking with WIRED on Tuesday claimed that tech companies are the only groups who benefit from the removal of these blogs.
“They are talking a big game on censorship. But at the end of the day, the thing that really hits these companies’ bottom line is what data they can collect, how they can use that data, whether they can train their AI models on that data, and if this administration is planning to take the foot off the gas there while stepping up its work on censorship,” the source familiar alleges. “I think that's a change big tech would be very happy with.”
77 notes
·
View notes
Text
Musk and House Republicans are still pushing KOSA
The bill is still being pushed at the end of the year. We need to keep up the pressure to stop KOSA from passing.
This is more pressing with FTC Commissioner Andrew Ferguson (whose agenda has been revealed to be very transphobic) being selected as Trump's nominee for Chairman of the FTC. If KOSA passes, this will give him and the Trump administration the power to attack online platforms that "harm children," making it harder to share progressive content and organize online.
So this week, keep making calls, emailing, and faxing your Representatives and these House leaders as well.
In addition to your House reps, call the House Leaders, especially the Republican leaders since they’re majority leaders:
Republican:
⭐Steve Scalise
(202) 225-3015
Fax 202-226-0386
⭐Mike Johnson
(202) 225-2777
fax: (202) 225-8039
Democrat:
⭐Hakeem Jeffries
(202) 225-5936
Ayanna Pressley
(202) 225-5111
Ilhan Omar
(202) 225-4755
Jamaal Bowman
(202) 225-2464
Cori Bush
(202) 225-2406
Call tools:
FFTF:
Fax:
Find your rep:
Here are scripts to use for the calls:
DEMOCRATIC VERSION:
I am urging you not to include KOSA in any end of year spending bills and to keep it from passing. With Trump ascending into office, this bill will give the FTC power to control speech online. FTC Commissioner Andrew Ferguson just came out with an agenda that will focus on going after online platforms for displaying LGBT content. With KOSA, this would only give them and republican attorney generals even more power to remove any content they deem “harmful”, which we know is an excuse to censor everything they don’t like. Suicide rates will skyrocket for marginalized youth with this bill restricting content.
200 human rights and LGBT organizations total came out in an open letter opposing it. The ACLU is against it. Hundreds of thousands of Gen Z are against it. We know the harms of social media, and we do not want this. Major news have reported that this bill actively harms kids.
The rewritten bill is still very dangerous, and giving any more power to Donald Trump to silence people he deems his “enemies” is a horrible move. With people like Donald Trump Jr. and Elon Musk supporting KOSA, this is enough of a sign to not push it forward.
Multiple experts agree this bill pushes age verification, even with the new language. KOSA hands more private data of children to third party companies. The updated language threatens encryption. How is this protecting children’s privacy? KOSA actively harms kids. Do NOT support this bill. Thank you.
REPUBLICAN VERSION: (pretend you’re GOP)
I am urging you VOTE NO on KOSA, the Kid’s Online Safety Act. Even with the rewritten language, this is still a dangerous bill that will harm children and censor pro-life content on the internet. Even with the new language, this bill still gives state Attorney Generals power to censor any content they don’t like. This bill would be weaponized by unelected bureaucrats to censor Americans, why else do you think Democrats are pushing it so hard? Why else would Biden and Kamala Harris support it?
Many news organizations have reported that this bill actively harms kids by exposing their private data to strangers under the guise of protecting them. We need to hold Big Tech accountable, but KOSA is not the solution.
The bill let any state attorney general and the FTC to sue any website for “harmful” content. Do we really want blue state lawyers deciding what can and can’t be allowed online? Big Tech is already censoring us. That’s why they support KOSA. This is massive government overreach. We need a bill that actually protects children by creating better security measures instead of bringing about more censorship to everyone.
Multiple experts agree this bill pushes age verification, even with the new language. KOSA hands more private data of children to third-party companies, which would put them in further danger. This also exposes everyone else. How is this protecting children’s privacy? What parent would want their child’s private data in the hands of strangers like this? KOSA is actively putting kids in danger. It censors our freedom of speech. Do NOT support this bill. Thank you.
——————————————————————————
Make sure to share this around to get more people involved.
I also ask that if you have an account with these other sites, you share and upvote these posts(they're different posts):
-Instagram:
instagram
-Bsky:
-Twitter:
-Tiktok: (i dont have tiktok so i cant link a kosa video here, my bad)
-Tumblr:
#kosa#stop kosa#fuck kosa#us politics#censorship#ngo#nonprofits#nonprofit#aclu#american civil liberties union#civil society#civil rights#fuck trump#stop project 2025#we will not go back#donotobey#do not obey in advance#resistance#resist#fuck elon musk#keep fighting#keep going#stand and fight#senate#usa news#contact your senators#raiseawareness#senators#bad internet bills#owl house
98 notes
·
View notes
Text
10% Daily Rewards Await You – Earn Big in the NFT & Metaverse World!

Are you ready to drive into the next big thing in the digital world? Our Metaverse and NFT platform offers more than just the experience – it offers real earnings!
Here’s what you get:
🌐 Daily 10% Rewards on Referrals – Share with your network and start earning instantly! 💸 Up to $20,000 in Daily Earnings – There's no limit to how much you can make! 🛡️ 100% Secure Environment – Your assets and data are fully protected.
Don’t miss out on this massive opportunity to build wealth in the Metaverse! Join now and start earning today.
👉 Join Now and Start Earning https://imetatool.net/0020cx.php?user=moneytree https://imetatool.net/0020x.php?user=moneytree https://www.youtube.com/watch?v=OMtxiOd0br8
The future of wealth is digital – be a part of it!
105 notes
·
View notes
Text
Palantir’s NHS-stealing Big Lie

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me in TUCSON (Mar 9-10), then SAN FRANCISCO (Mar 13), Anaheim, and more!

Capitalism's Big Lie in four words: "There is no alternative." Looters use this lie for cover, insisting that they're hard-nosed grownups living in the reality of human nature, incentives, and facts (which don't care about your feelings).
The point of "there is no alternative" is to extinguish the innovative imagination. "There is no alternative" is really "stop trying to think of alternatives, dammit." But there are always alternatives, and the only reason to demand that they be excluded from consideration is that these alternatives are manifestly superior to the looter's supposed inevitability.
Right now, there's an attempt underway to loot the NHS, the UK's single most beloved institution. The NHS has been under sustained assault for decades – budget cuts, overt and stealth privatisation, etc. But one of its crown jewels has been stubbournly resistant to being auctioned off: patient data. Not that HMG hasn't repeatedly tried to flog patient data – it's just that the public won't stand for it:
https://www.theguardian.com/society/2023/nov/21/nhs-data-platform-may-be-undermined-by-lack-of-public-trust-warn-campaigners
Patients – quite reasonably – do not trust the private sector to handle their sensitive medical records.
Now, this presents a real conundrum, because NHS patient data, taken as a whole, holds untold medical insights. The UK is a large and diverse country and those records in aggregate can help researchers understand the efficacy of various medicines and other interventions. Leaving that data inert and unanalysed will cost lives: in the UK, and all over the world.
For years, the stock answer to "how do we do science on NHS records without violating patient privacy?" has been "just anonymise the data." The claim is that if you replace patient names with random numbers, you can release the data to research partners without compromising patient privacy, because no one will be able to turn those numbers back into names.
It would be great if this were true, but it isn't. In theory and in practice, it is surprisingly easy to "re-identify" individuals in anonymous data-sets. To take an obvious example: we know which two dates former PM Tony Blair was given a specific treatment for a cardiac emergency, because this happened while he was in office. We also know Blair's date of birth. Check any trove of NHS data that records a person who matches those three facts and you've found Tony Blair – and all the private data contained alongside those public facts is now in the public domain, forever.
Not everyone has Tony Blair's reidentification hooks, but everyone has data in some kind of database, and those databases are continually being breached, leaked or intentionally released. A breach from a taxi service like Addison-Lee or Uber, or from Transport for London, will reveal the journeys that immediately preceded each prescription at each clinic or hospital in an "anonymous" NHS dataset, which can then be cross-referenced to databases of home addresses and workplaces. In an eyeblink, millions of Britons' records of receiving treatment for STIs or cancer can be connected with named individuals – again, forever.
Re-identification attacks are now considered inevitable; security researchers have made a sport out of seeing how little additional information they need to re-identify individuals in anonymised data-sets. A surprising number of people in any large data-set can be re-identified based on a single characteristic in the data-set.
Given all this, anonymous NHS data releases should have been ruled out years ago. Instead, NHS records are to be handed over to the US military surveillance company Palantir, a notorious human-rights abuser and supplier to the world's most disgusting authoritarian regimes. Palantir – founded by the far-right Trump bagman Peter Thiel – takes its name from the evil wizard Sauron's all-seeing orb in Lord of the Rings ("Sauron, are we the baddies?"):
https://pluralistic.net/2022/10/01/the-palantir-will-see-you-now/#public-private-partnership
The argument for turning over Britons' most sensitive personal data to an offshore war-crimes company is "there is no alternative." The UK needs the medical insights in those NHS records, and this is the only way to get at them.
As with every instance of "there is no alternative," this turns out to be a lie. What's more, the alternative is vastly superior to this chumocratic sell-out, was Made in Britain, and is the envy of medical researchers the world 'round. That alternative is "trusted research environments." In a new article for the Good Law Project, I describe these nigh-miraculous tools for privacy-preserving, best-of-breed medical research:
https://goodlawproject.org/cory-doctorow-health-data-it-isnt-just-palantir-or-bust/
At the outset of the covid pandemic Oxford's Ben Goldacre and his colleagues set out to perform realtime analysis of the data flooding into NHS trusts up and down the country, in order to learn more about this new disease. To do so, they created Opensafely, an open-source database that was tied into each NHS trust's own patient record systems:
https://timharford.com/2022/07/how-to-save-more-lives-and-avoid-a-privacy-apocalypse/
Opensafely has its own database query language, built on SQL, but tailored to medical research. Researchers write programs in this language to extract aggregate data from each NHS trust's servers, posing medical questions of the data without ever directly touching it. These programs are published in advance on a git server, and are preflighted on synthetic NHS data on a test server. Once the program is approved, it is sent to the main Opensafely server, which then farms out parts of the query to each NHS trust, packages up the results, and publishes them to a public repository.
This is better than "the best of both worlds." This public scientific process, with peer review and disclosure built in, allows for frequent, complex analysis of NHS data without giving a single third party access to a a single patient record, ever. Opensafely was wildly successful: in just months, Opensafely collaborators published sixty blockbuster papers in Nature – science that shaped the world's response to the pandemic.
Opensafely was so successful that the Secretary of State for Health and Social Care commissioned a review of the programme with an eye to expanding it to serve as the nation's default way of conducting research on medical data:
https://www.gov.uk/government/publications/better-broader-safer-using-health-data-for-research-and-analysis/better-broader-safer-using-health-data-for-research-and-analysis
This approach is cheaper, safer, and more effective than handing hundreds of millions of pounds to Palantir and hoping they will manage the impossible: anonymising data well enough that it is never re-identified. Trusted Research Environments have been endorsed by national associations of doctors and researchers as the superior alternative to giving the NHS's data to Peter Thiel or any other sharp operator seeking a public contract.
As a lifelong privacy campaigner, I find this approach nothing short of inspiring. I would love for there to be a way for publishers and researchers to glean privacy-preserving insights from public library checkouts (such a system would prove an important counter to Amazon's proprietary god's-eye view of reading habits); or BBC podcasts or streaming video viewership.
You see, there is an alternative. We don't have to choose between science and privacy, or the public interest and private gain. There's always an alternative – if there wasn't, the other side wouldn't have to continuously repeat the lie that no alternative is possible.

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/08/the-fire-of-orodruin/#are-we-the-baddies

Image: Gage Skidmore (modified) https://commons.m.wikimedia.org/wiki/File:Peter_Thiel_(51876933345).jpg
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/deed.en
#pluralistic#peter thiel#trusted research environment#opensafely#medical data#floss#privacy#reidentification#anonymization#anonymisation#nhs#ukpoli#uk#ben goldacre#goldacre report#science#evidence-based medicine#goldacre review#interoperability#transparency
530 notes
·
View notes