#BusinessEmailCompromise
Explore tagged Tumblr posts
Text
Business Email Compromise: 7 Shocking Facts and How to Protect Your Company Today! 🚨

In the digital age, cyber threats are lurking around every corner, and one of the most dangerous is Business Email Compromise (BEC). This sophisticated scam has caused billions of dollars in losses for companies worldwide. Are you at risk? Discover 7 shocking facts about BEC and learn how to protect your company from this insidious threat today! 🚨
1. The Rising Threat: BEC Attacks Are Skyrocketing 📈
Business Email Compromise isn’t just a buzzword – it’s a rapidly growing menace. Cybercriminals use deceptive tactics to trick employees into transferring money or divulging sensitive information. With over $26 billion in reported losses since 2016, BEC is a threat you can’t afford to ignore.
Fact Check:
According to the FBI, BEC scams have increased by 100% over the past few years. Stay vigilant and informed!
2. CEO Fraud: The Devious Tactic Targeting Top Executives 👨💼
Imagine receiving an urgent email from your CEO requesting an immediate wire transfer. It looks legitimate, but it’s a clever ruse. CEO fraud, a type of BEC, preys on employees' trust in their executives, leading to significant financial losses.
Quick Tip:
Implement multi-factor authentication (MFA) and verify high-risk requests through multiple communication channels.
3. Vendor Email Compromise: The Sneaky Supplier Scam 📬
Cybercriminals don’t just target internal emails; they also infiltrate your suppliers’ email systems. By compromising a trusted vendor, they can redirect payments to their accounts, leaving your company out of pocket and your vendor relationship in jeopardy.
Proactive Measure:
Regularly verify payment details with suppliers using established communication methods.
4. Phishing: The Gateway to BEC 🐟
Phishing emails are a common entry point for BEC attacks. These deceptive messages lure employees into revealing login credentials or downloading malware, giving cybercriminals access to corporate email accounts.
Defense Strategy:
Conduct regular phishing awareness training for employees and use advanced email filtering solutions.
5. The Costly Consequences: Financial and Reputational Damage 💸
BEC attacks don’t just result in financial loss – they can also severely damage your company’s reputation. Clients and partners may lose trust in your ability to protect their information, leading to long-term business consequences.
Risk Mitigation:
Invest in cyber insurance to cover potential financial losses and implement robust security protocols.
6. Detection Difficulties: Why BEC Is Hard to Spot 🔍
Unlike traditional phishing scams, BEC emails often lack obvious red flags like suspicious links or attachments. This makes them harder to detect and increases the likelihood of a successful attack.
Enhanced Protection:
Utilize artificial intelligence (AI) and machine learning (ML) tools to detect unusual email patterns and anomalies.
7. Legal Ramifications: The Hidden Costs of BEC ⚖️
Beyond immediate financial losses, BEC can lead to legal troubles. Failure to protect sensitive information may result in regulatory fines and lawsuits, further exacerbating the damage to your business.
Compliance Check:
Ensure your cybersecurity measures comply with industry regulations and standards to avoid legal pitfalls.
How to Protect Your Company from BEC Today! 🛡️
1. Implement Advanced Email Security Solutions
Use email security software that provides real-time threat detection, phishing protection, and spam filtering. These tools can significantly reduce the risk of BEC attacks.
2. Strengthen Authentication Protocols
Implement multi-factor authentication (MFA) for all employees, especially those with access to sensitive financial information. This adds an extra layer of security.
3. Conduct Regular Employee Training
Educate employees about the dangers of BEC and phishing. Regular training sessions and simulated phishing exercises can keep everyone alert and aware.
4. Establish Clear Verification Processes
Create strict protocols for verifying financial transactions and sensitive requests. This should include direct verification with the requesting party through a different communication channel.
5. Monitor and Audit Email Activity
Regularly monitor email accounts for unusual activity and conduct audits to identify potential vulnerabilities. Early detection can prevent significant losses.
6. Update Software and Systems Regularly
Keep your email systems, security software, and other IT infrastructure updated with the latest security patches to protect against known vulnerabilities.
7. Collaborate with Cybersecurity Experts
Partner with cybersecurity firms to conduct regular risk assessments and implement advanced security measures tailored to your business needs.
Conclusion: Don’t Be the Next Victim! Act Now to Secure Your Business 🌟
Business Email Compromise is a serious threat that can have devastating consequences. By understanding the risks and implementing these protective measures, you can safeguard your company against BEC attacks. Don’t wait until it’s too late – start fortifying your defenses today and ensure your business stays secure and resilient in the face of cyber threats.
Call to Action:
Want to stay ahead of cyber threats? Stay tuned to protect your business and join our community of security-conscious professionals today!
#BusinessEmailCompromise#Cybersecurity#EmailSecurity#DataProtection#CyberThreats#PhishingAttacks#CyberCrime#EmailFraud#SecurityAwareness#BusinessSecurity#CyberAwareness#FraudPrevention#EmailCompromise#CyberAttack#ITSecurity#ProtectYourCompany#EmailScams#SecurityMeasures#SecurityTips#BusinessProtection
0 notes
Link
https://bit.ly/3RmzLDN - 🔒 Microsoft Threat Intelligence reports that threat actors are increasingly misusing OAuth applications in financially driven attacks. OAuth, a standard for authentication and authorization, is being exploited to gain access to data and maintain persistent access to applications, even after losing initial account access. This misuse of OAuth poses significant risks in terms of data privacy and security. #MicrosoftThreatIntelligence #Cybersecurity 🐍 Attackers use phishing or password spraying to compromise user accounts, especially those lacking strong authentication. They then create or modify OAuth applications with high privileges for various malicious activities, including deploying VMs for cryptocurrency mining, executing business email compromise (BEC), and launching spamming activities using the organization's resources. #PhishingAttacks #PasswordSecurity 💰 One specific threat actor, known as Storm-1283, deployed VMs for cryptomining using compromised accounts. They incurred significant costs for the targeted organizations, ranging from $10,000 to $1.5 million. Microsoft's proactive measures, including the blocking of malicious OAuth applications and notification to affected organizations, have been crucial in mitigating these attacks. #CryptoMining #DigitalSecurity 📧 Another observed attack involved BEC and phishing via compromised user accounts and creation of OAuth applications. Attackers used these applications to maintain persistence and launch phishing emails, sending over 927,000 messages. Microsoft responded by taking down all related malicious OAuth applications. #BEC #EmailPhishing 🌐 For spamming, attackers like Storm-1286 used compromised accounts to create new OAuth applications for large-scale spam attacks. These attacks highlight the importance of multifactor authentication (MFA) as a key defense strategy. Microsoft’s detection capabilities in their various Defender products played a crucial role in identifying and mitigating these threats. #SpamAttacks #MFADefense ⚠️ Microsoft recommends several mitigation steps to combat these threats. These include enabling MFA, implementing conditional access policies, ensuring continuous access evaluation, enabling Microsoft Defender automatic attack disruption, auditing apps and consented permissions, and securing Azure cloud resources. These steps are essential for organizations to protect against OAuth application misuse. #CybersecurityBestPractices #MicrosoftDefender 🕵️♂️ Hunting guidance for Microsoft 365 Defender users includes monitoring OAuth application interactions, identifying password spray attempts, and investigating suspicious application creation and email events. These proactive measures help organizations detect and respond to potential threats in their networks.
#MicrosoftThreatIntelligence#Cybersecurity#PhishingAttacks#PasswordSecurity#CryptoMining#DigitalSecurity#BEC#EmailPhishing#SpamAttacks#MFADefense#CybersecurityBestPractices#MicrosoftDefender#ThreatHunting#Microsoft365Defender#useraccounts#cryptocurrencymining#businessemailcompromise#technology#access#data#privacy#cybersecurity
0 notes
Text
Secured Microsoft 365
Looking to grow, gain market share, or retain your client base in a competitive market? The right technology can make all the difference—especially for small and mid-sized businesses.
If you’re still running on an older, “on-prem” version of Microsoft Office, it may be time for a productivity glow-up. Your trusted apps like Word, Excel, and PowerPoint have served you well—but if they’re stuck on your desktop, your team might be too.
-Limited access on the go
-Frustrating remote collaboration
-Rising costs from multiple add-ons like email, file storage, and meetings
Enter Microsoft 365—the cloud-based solution that brings the tools you know and love together with smart, secure, and flexible cloud technology. Your team can work from anywhere, collaborate in real time, and stay protected from modern cyber threats like:
Phishing scams
Helpdesk phishing
IT support scams
CEO fraud / Business Email Compromise
Urgent email scams
Ransomware warning pop-ups
Scareware & fake antivirus alerts
According to a Forrester study, Microsoft 365 delivers:
223% ROI over 3 years
1.5 hours saved per user weekly
$297K in cost savings from IT & hardware
Enhanced security, collaboration, and AI-powered productivity with Microsoft Copilot
And the best part? You already know the tools—Microsoft 365 just makes them better, faster, and smarter.
Reminder: Windows 10 loses support in October 2025. No more updates. No more protection. Let’s avoid the last-minute scramble.
Ready to unlock more productivity, security, and value from the tools your team already uses? Let’s move to Microsoft 365 the smart way—together.

Reach out today to chat with us about upgrading with Century Solutions Group—your trusted Microsoft Cloud Partner. https://centurygroup.net/cloud-computing/office-365-support/
#Microsoft365 #BusinessProductivity #CyberSecurity #PhishingScams #Ransomware #SmallBusinessSupport #ITSupportScam #CEOFraud #BusinessEmailCompromise #DigitalTransformation
1 note
·
View note
Text
What is Business Email Compromise (BEC) and how to stop it?
The most severe cybersecurity issue to SMEs is Business Email Compromise (BEC). According to the FBI, businesses lost $12 billion between December 2016 and May 2018. However, when you consider how many companies don't come out and say they were impacted, the damage could have been far more significant.
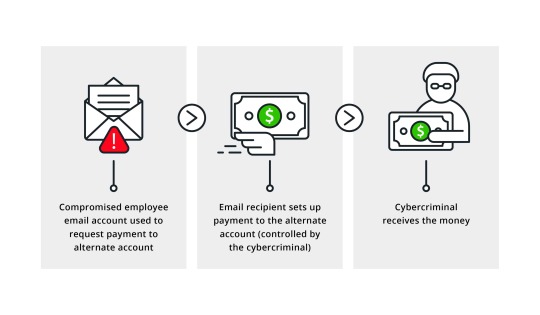
What is Business Email Compromise?
As the name says, it's an email compromise. An attacker would get access to a company's email account, typically belonging to a top official. The attackers occasionally mimic the executive's email account to send emails. Then, after the email account has been stolen, they would watch the actions and send emails to the finance staff seeking funds transfer. There are a few variations of these attacks.
CEO Fraud
Supply chain fraud
Vendor email compromise
CEO fraud is simple, as previously stated. When the CEO's email is hacked or spoofed, they will send emails to the finance department requesting funds transfer.
When a supplier's email account is hacked, the activity is observed, and the attacker sends an email at the time of a payments transfer asking for the funds to be transferred to a new bank; this is known as supply chain fraud. They usually send an email to the recipient stating that the bank details have been altered. Several businesses have been harmed as a result of this.
A solicitor and a customer are another example of supply chain fraud. When the email accounts of solicitors are hacked, the attacker waits for the ideal moment to urge the victim to transfer money to a different bank. Imagine losing all you own because your solicitor's email account was hacked.
You might be wondering how they got access to the email accounts in the first place. A sophisticated phishing campaign is the answer. They send phishing emails requesting that the recipient reset their Office 365 password, log in to LinkedIn, PayPal, and other services. You'll notice that most users use the same password for various services. Once they have gained access to the account, they usually set up forwarding rules so that the recipient does not get the message.
There are numerous examples of supply chain fraud, and I will conclude with this one-of-a-kind case. Consider the following scenario: an employee's email account is hacked. The attacker sends HR an email the day before payday stating that the bank information has been changed and that the payment has been deposited into the new bank.
The vendor email hack is similar, except the attacker would send a false invoice to everyone in their contacts in the hopes that someone will clear the invoice. What's more, some companies do it.
How do you avoid being a victim of Business Email Compromise (BEC)?
There are a few simple steps you can take to avoid BEC in most cases. They are:
User education: Train your users
Business Process for Payments
Basic email security controls
The key is user education. Make sure your users are aware of these hazards and that they double-check emails, mainly if they contain a payment request. A variety of Security Awareness Platforms are available to assist you.
Payments business process: Any payment request or bank account change request should be approved by at least two people in the company. Large corporations are usually adept at this, but SMEs have the most difficulty.
It's a good idea to enable some essential email security safeguards. As a result, it will be easier to prevent these assaults and consumers from noticing suspicious emails. The following are some of the controls:
Two-factor authentication should be enabled.
Encourage the use of strong passwords.
Anti-spoofing should be enabled, and a spam filtering system should be deployed.
Add the tag ‘[EXTERNAL]' to the subject of all external emails.
When users add a forward rule in their mailbox, create an alert.
We hope the above article has been informative.
Source: https://cyber-security-information.blogspot.com/2021/07/what-is-business-email-compromise-bec.html
1 note
·
View note
Photo

Want to have Professional Email ID for your Business at less cost? . . Have Email id’s with 5Gb space for each, with validity for lifetime & configured to your domain for free. . . DM us to know more. . . . . . . . . . . . . #makemypresence #makemypresencepvtltd #business #businessowner #email #emailid #businessemails #businessemail #businessemailcompromise #businessemailsolution #businessman #businesswoman #emailideas #emailidfinder #emailid_database #podestaemails #emaillist #emailsuccess #emaildatabase #emailsignature #emailmarketingtips (at Andheri, Mumbai) https://www.instagram.com/p/B_CBMEmnyQi/?igshid=tq24hseya3f5
#makemypresence#makemypresencepvtltd#business#businessowner#email#emailid#businessemails#businessemail#businessemailcompromise#businessemailsolution#businessman#businesswoman#emailideas#emailidfinder#emailid_database#podestaemails#emaillist#emailsuccess#emaildatabase#emailsignature#emailmarketingtips
0 notes
Video
tumblr
Keep control on your emails accessibility country wise and mitigate the risk of email hacking with XgenPlus Security Feature.
#EmailSecurity #FridayThoughts #security #emails #businessemailcompromise #risk #Hacker
0 notes
Text
E-Posta Dolandırıcılığı Yapan Çete Yakalandı

Bursa'da teknik olarak BEC denilen e-posta sahtekarlığı yoluyla uluslararası dolandırıcılık yapan bir çete yakalandı. Bursa siber suçlarla mücadele şube müdürlüğü ekipleri şirketlerin e-posta haberleşme trafiğinin arasına girerek kurdukları paravan şirketlere para aktarılmasını sağlayan çeteyi 3 ilde yaptığı operasyonlarla çökertti. Bursa'dan çelik ihracatı yapan bir firmanın yetkilileri, yaklaşık 6 ay önce, Almanya'ya ürün gönderdikleri şirket ile kendi kurumsal e-posta adresinden bilgilerinin dışında iletişime geçildiğini fark etti. Kendilerine havale edilmesi gereken 30 bin avronun, başka bir banka hesabına gönderildiğini belirleyen Bursalı firmanın yetkilileri, durumu polise bildirdi. Bunun üzerine çalışma başlatan İl Emniyet Müdürlüğü Siber Suçlarla Mücadele Şubesi ekipleri, "ortadaki adam saldırısı" yöntemiyle Türkiye ile Almanya, ABD, İngiltere gibi birçok ülkedeki firmaların kurumsal e-posta adreslerinin şifrelerinin kırıldığını tespit etti. Zanlıların, bu adresler üzerinden şirketlerin alacaklı olduğu firmalarla irtibata geçtikleri, yazışmaları sonucu bu alacakları, kurdukları kargo, dış ticaret gibi paravan şirketlerin hesaplarına aktarmalarını istedikleri anlaşıldı. Bursa polisi, şüphelilere ait hesaplarda 20 milyon dolarlık hesap hareketi olduğunu da belirledi. "MAN IN THE MIDDLE ATTACK" ÇÖKERTİLDİ! Dünyada ‘Man in the middle attack’ yani ‘Aradaki adam saldırısı’ olarak bilinen yöntemi kullanarak borçlu şirketlere alacaklı şirket adına mail atan ve kendi hesaplarına para transferi yapılmasını sağlamakta olan çetenin, bu yolla son 6 ay içinde 20 milyon dolarlık vurgun yapmış olduğu belirlendi. Türkiye’nin ülkelerarası alanda ticari itibarını zedeleyen çetenin hemde bu paraları kurdukları paravan şirketlerin hesabına aktardığı ve çete üyelerinin komisyonlarını aldıktan sonra kalan parayı da çete yöneticisinin hesabına aktardıkları ortaya çıktı. Polis ekipleri, 6 ay süren takibin ardından İstanbul, Gaziantep ve Kilis'te belirlenen adreslere eş zamanlı operasyon düzenledi. Operasyonda, aralarında Nijerya, İran ve Filistin uyrukluların da bulunduğu 22 şüpheli yakalandı. Read the full article
0 notes
Photo

Use #MultifactorAuthentication & strong #passphrases to protect against #BusinessEmailCompromise. Learn how to detect & avoid #scams that could cause your organisation to lose money https://t.co/bqJ1sTP9SE https://t.co/O1JAwl2nUN (via Twitter http://twitter.com/CyberGovAU/status/1321277188398665729)
1 note
·
View note