#Cell phone user data stolen
Explore tagged Tumblr posts
Text
ABC News: FCC fines wireless carriers for sharing user locations without consent
The Federal Communications Commission has leveraged nearly $200 million in fines against wireless carriers AT&T, Sprint, T-Mobile and Verizon for illegally sharing customers' location data without their consent.
"These carriers failed to protect the information entrusted to them. Here, we are talking about some of the most sensitive data in their possession: customers’ real-time location information, revealing where they go and who they are,” FCC Chairwoman Jessica Rosenworcel said in a statement released Monday.
4 notes
·
View notes
Text
As the Israel-Hamas war escalated this week, WIRED looked at the conditions that contributed to Israel's intelligence failures ahead of Hamas' initial attack last Saturday, as well as the hacktivism and digital mayhem that has subsequently sprung up around the kinetic war. The situation has led to a torrent of misinformation across global discourse, particularly on the social media platform X (formerly Twitter), where fake photos, old videos, and video game footage have exploded on an unprecedented scale.
X’s Trust and Safety team claims it has been working to address the situation, but company CEO Elon Musk has been “posting through it,” sharing conspiracies and engaging with QAnon discourse on the platform. The chaotic situation on X has been difficult for the average user to keep up with. In one case, a graphic Hamas video that Donald Trump Jr. shared on the platform actually turned out to be legitimate, even though it seemed at first look like it might have been part of the broader deluge of misinformation. And beyond just X, rumors of a “Global Day of Jihad” on Friday unleashed a dangerous wave of disinformation across digital platforms—one that threatened to cross into real-world violence.
With the trial of FTX founder Sam Bankman-Fried in full swing this week, WIRED took a deep look at the day someone stole hundreds of millions of dollars from the ill-fated cryptocurrency exchange as it was declaring bankruptcy. And new evidence released by researchers this week indicates that the stolen FTX funds went through a chain of intermediaries that eventually led to Russia-linked money launderers.
As chaos in the United States House of Representatives continues over Republicans' inability to deal with far-right hardliners and elect a new speaker, WIRED reported that Republican Party leaders have imposed cell phone bans in an attempt to keep backroom dealmaking under wraps. The United Nations' top internet governance body may host its next two annual meetings in countries known for repressive digital policies and abusive information control, which risks normalizing internet censorship. And white supremacist “active clubs” are gaining traction in part through communication on the messaging app Telegram.
Meanwhile, Google announced this week that it will make the more secure password replacement known as passkeys the default login option for its personal account holders as part of the company's efforts to promote adoption of the technology. And a new internet protocol vulnerability known as “HTTP/2 Rapid Reset” impacts virtually every web server around the world and will take years to stamp out, exposing some sites and digital services to denial of service attacks long-term.
And there's more. Each week we round up the security and privacy news that we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
Vietnam Used Predator Spyware to Target US Congress
Notorious high-end commercial spyware like Pegasus and Predator has been used over the past decade to target human rights activists, protesters, and journalists. But a foreign nation using it to target the smartphones of US members of Congress represents a rare and brazen new appearance of those notorious tools. On Monday The Washington Post, along with a consortium of more than a dozen international media outlets, revealed that the Vietnamese government used that Predator spyware, distributed by the surveillance firms Cytrox and Intellexa, to target at least four members of Congress—representative Michael McCaul and senators Chris Murphy, John Hoeven, and Gary Peters—as well as Asia-focused experts at US think tanks and several journalists that include CNN’s lead national security reporter, Jim Sciutto.
In the hacking campaign, those individuals were targeted in replies on X (formerly known as Twitter) that included links to websites that would have infected their iOS or Android phones with the Predator spyware. That tactic appears to have been both reckless and unsuccessful: Anyone else who saw the tweets and clicked on the link would have been infected too, and the highly public nature of that infection attempt helped researchers and reporters to analyze the scope and targeting of the campaign. The attempted espionage was timed to US government meetings with Vietnamese officials, and it appears to have been aimed at understanding US intentions in the meeting, particularly related to relations with China.
The media consortium, along with security researchers from Amnesty International and Google’s Threat Analysis Group, were able to show Vietnam’s connection to the Predator hacking campaign through documents they obtained that detail the Vietnamese government’s contract with Intellexa in 2020, and later an extension of the deal to allow the use of the Predator software. The internal documents went so far as to capture the response of Intellexa’s founder, Israeli former military hacker turned entrepreneur Tal Dilian, when the deal was announced: “Wooow!!!!” Vietnam’s government would later target French officials with Predator before this year’s campaign targeting US congressmen.
Hamas Raised Millions in Crypto Ahead of Attacks
Despite efforts by Israel and other nations to cut off funding to Hamas in recent years, the group raised millions of dollars worth of cryptocurrency before the past weekend’s attack that killed more than a thousand Israelis. An analysis by The Wall Street Journal found that Hamas, Palestinian Islamic Jihad, and Hezbollah had collectively raised hundreds of millions in crypto over the past several years, with $41 million going to Hamas specifically. Given that the Journal learned of that funding in part through Israeli seizures of crypto accounts, however, it’s not clear how much of that money was frozen or seized versus how much might have actually been successfully laundered or liquidated by Hamas and other groups.
In response to the weekend’s attacks, the Israeli government and the world’s largest crypto exchange, Binance, both announced that a new round of Hamas crypto accounts had been frozen. Though crypto has helped Hamas and other groups move funds across borders, its traceability on blockchains has presented a challenge for designated terrorist groups. In 2021, for instance, Hamas asked its supporters to stop making donations via cryptocurrency, due to the ease of tracking those transactions and unmasking contributors.
Exxon Used Hacked Documents to Counter State Investigations
Last year, Reuters reporters Chris Bing and Raphael Satter published an investigation into Aviram Azari, an Israeli private investigator who is accused of using mercenary hackers to gather intelligence on the critics of major corporations involved in lawsuits against them.
Now, prosecutors in the Southern District of New York, where Azari has been convicted on criminal charges, have filed a sentencing memo that notes that activists’ communications stolen by Azari’s hackers were later used by Exxon in the company’s attempts to head off investigations and lawsuits by state attorneys general. The memo still doesn’t name Exxon as Azari’s client, but it implicitly suggests a link between the company and Azari: Prosecutors point in their memo to leaks of climate activists’ private emails to media, which were later cited by Exxon in their responses to state attorney generals as evidence of underhanded tactics by activists as they tried to prove that Exxon knew and covered up the role of fossil fuels in climate change. A Massachusetts lawsuit against Exxon that resulted from the state’s investigation is ongoing.
Magecart Cybercrime Crew Skims Cards With New 404 Trick
Internet giant Akamai warned this week that the infamous Magecart hacker crew, long focused on credit card fraud, has developed a clever new technique for spoofing credit card payment fields. The hackers managed to hide their malicious scripts in the 404 “page not found” error pages of ecommerce sites, then trigger those pages to load a spoofed payment field that impersonates a checkout page to steal credit card information. “The idea of manipulating the default 404 error page of a targeted website can offer Magecart actors various creative options for improved hiding and evasion,” warned Akamai researcher Roman Lvovsky. Akamai noted that the technique was used on the website of significant brands in the food and retail industries but declined to name them.
5 notes
·
View notes
Text
Micropricing
I got pinged for implying phone services were overcharging for "caller ID and Visual Voicemail" on truth social. So I'm going into one of the ways businesses take advantage of users: Micropricing.
First, Caller ID is already built into the system. It has been for at least three decades. Back then it might've cost more to send you a name attached to the number it wouldn't show you either. But that's why we had phone books and answer machines.
Now, spam-robots can call you daily for much less than it costs you to keep your phone connected to the service you're paying for. And because of the Micropricing strategy, the phone companies "can't afford to use their decades old technology in new and innovative ways that protect customers."
Visual Voicemail, on the other hand, is an app that lets you look at who left a message and other details of the sound file attached to it, without having to call you voicemail and do it by touch tone like we're in mad men. And yes, it provides a transcription of the message left. Which is simply an accessibility feature for hard of hearing that they're allowed charge extra for, because they can.
And you wonder why we would rather you just send a text message.
Anyway, Micropricing is a strategy to charge more for services that don't actually cost the company more to provide. And sometimes, for things the user will never use. And sometimes, phone insurance which ultimately costs the user more to use than a phone repair service. (And they don't even help track down lost or stolen devices, EVEN THOUGH THEY CAN. AND YOU PAY A SERVICE FOR PROTECTION.)
A lot of these services are collapsing because the Internet allows more rich data to be sent more efficiently. But here's the thing: old services are tacked onto your bill automatically. we can't*not use them* but phone companies won't update either. So we pay to get the updated old tech that isn't as good as should be standard ten years ago.
A lot of the digital features today aren't like owning a car phone in the 70s. Cell Phones have been the defacto standard for 20 years now. The only thing different is data usage. Which may or may not be restricted thanks to cell tower bandwidth. But in a college town where the bandwidth is always maxed out and everybody needs to use wifi, you're just having people pay to not use the features that worked better ten years ago.
Infrastructure should include phone and internet service. Then *private* companies can just be the fastlane they claim to want to build. But instead they're focused on charging extra for standard features.
Look. Trains caused the word to have to keep pace with a 24 hour clock schedule.
The Internet means the world needs to get off its addiction of 5-year and 10-year plans hoping for people to die before anything can be done to change anything.
Even six months is too long for deliberation. Yeah, it used to be worse, but that's the whole f*ing reason we built technology in the first place, so it wouldn't have to be.
2 notes
·
View notes
Text
How to Know If Your Cell Phone Has Been Hacked?

What are the significant signs that are used to find out that someone’s phone has been hacked and its information stolen by other people? This question and all similar questions are the common concern of many smartphone users, and considering that the phone is a versatile tool for most people, important information is also stored in it, so hacking the phone and stealing it Losing its information can cause a lot of damage. In order to know whether your smartphone is being spied on or not, follow this article and the security solutions mentioned here.
2 signs that someone is spying on your phone
There are lots of important physical and hardware signs that show your phone is being hacked. In order to find out, continue with us in this part of the article.
You are receiving unusual messages
If you receive unrelated and incomprehensible messages that have never happened before, for example, messages that contain a large number of characters and numbers, you are probably under control. These messages are similar to the codes that are sent to track the location of people.
AnyControl is the best phone call monitoring app that can track every incoming, outgoing and missed phone call on the target device even if the call log is deleted with its advanced tracking features.
Another way that can reveal the signs of espionage from a software point of view are anti-spyware programs and apps. An example of these apps is Anti Spy Mobile. iPhone phones are usually more secure than Android phones (if they are not jailbroken or unlocked), so if your phone is an iPhone, you can be sure of its greater safety; Because installing spyware requires physical contact with the device.
After sending, a lot of information will be displayed. Pay more attention to URLs. If you have been spied on, many copies of the email you have sent will be sent to different IPs that are different from the IP of your Internet service provider. You can search the term IP lookup on the Internet to distinguish the IP of your ISP from other IPs.
Your data usage has been checked by phone
Through smartphones, you can check the internet usage under the phone's network usage. The spy softwares that is installed in the devices for spying perform their activities by sending and receiving data, which is actually the same as using the Internet. If you see significant changes in your phone's internet usage, there is a possibility that your device is being tapped and its information is being spied on.
2 notes
·
View notes
Text
Mobile Number Tracker Free: Track Real-Time Location Easily

Advanced tracking technology has made it possible to make sure that dear ones are safe and to locate lost or stolen devices in this digital age. Now, with free mobile number tracker tools available, anyone can track real-time locations with absolute ease. Parents may want to keep an eye on their child, someone may just be trying to locate or recover a phone lost by accident, or a professional might want to ensure the safety of field teams: these tools are useful for all. Let us see how you can make use of mobile number tracker free and an IMEI phone tracker.
Why Use a Mobile Number Tracker?
Mobile number tracker free software helps trace an actual location of the cell phone within real-time. This is particularly useful when:
The parents are interested in keeping tabs on where their children may be.
Employers are to trace their field staff.
Users are trying to trace a lost mobile device for either malicious or good intent.
Concerned relatives are tracking an elderly family member.
In contrast with traditional GPS tracker, mobile number tracker uses a combination of GPS, network towers, and internet data to provide location accuracy.
What is IMEI Number Tracking?
IMEI, standing for International Mobile Equipment Identity, is a 15-digit code being assigned to each mobile device. Through IMEI Number tracking, users have the capability to trace and block devices in case their SIM card has been changed. It is one of the strongest options for finding any lost or stolen smartphone.
Advantages of IMEI Tracking:
Track phone location in the absence of an operational SIM.
Aid law enforcement agencies in retrieving stolen phones.
Remote locking or wiping of phone data.
Thus, an IMEI phone tracking option establishes more security and recovery on your end for a mobile device.
How to Use a Mobile Number Tracker and IMEI Phone Tracker
One of the most trusted online sources for mobile device tracking is TrackIMEI.net. The online service opened up an easy chance for users to perform IMEI number tracking and trace a phone through its number.
Directions:
Step 1: Visit Website: Go to the website TrackIMEI.net.
Step 2: Choose Your Service: Choose whether you want to use mobile number location tracker or do IMEI number tracking.
Step 3: Enter Details: Enter the mobile number or IMEI code for the device you want to track.
Location Tracking: Within a few seconds, a live location of the given mobile device will be displayed on an interactive map.Conversely, this is a simple, efficient, and trustworthy way to continue to be informed and safe.
When to Use IMEI Phone Tracker
Lost Device: If your mobile is lost or stolen, inputting the IMEI code can help in quick retrieval.
Tracking without SIM: In case of SIM card replacement, you can search the phone through IMEI.
Phone management: IMEI tracking could help work businesses that manage several phones in the undertaking of asset control.
Legal and Ethical Considerations
It is important you track these devices ethically and with permission. Legal consequences may follow if attempted without consent.
Closing Thoughts
With free mobile number tracking, IMEI number tracking, and an IMEI phone tracker, mobile tracking is made very easy and effective. And TrackIMEI.net does so through a secure and user-friendly platform that will help you find anyone anytime. Whether for safety, security, or recovery, understanding and correctly using these tools can save you time, money, and stress.
Connect, inform, and keep safe.
Read More : https://trackimei.net/
0 notes
Text
How to Turn Off Find My iPhone on iCloud: A Simple Guide 2025
Turning off Find My iPhone can be necessary for a variety of reasons, whether you're preparing to sell or give away your device, or simply troubleshooting issues with your iCloud account. While it might sound complicated, disabling Find My iPhone is a straightforward process. In this post, we'll guide you through the steps to turn off Find My iPhone via iCloud and the settings on your device.

Why You Might Need to Turn Off Find My iPhone
Find My iPhone is a powerful feature that helps locate your device in case it’s lost or stolen. However, there are situations where you may need to disable it, such as:
Selling or giving away your iPhone: You’ll need to turn off Find My iPhone before erasing the device.
Troubleshooting issues: Occasionally, turning off Find My iPhone can help resolve iCloud-related problems.
Resetting your device: If you’re doing a factory reset, Find My iPhone needs to be off to avoid activation lock issues.
Top Methods to Turn Off Find My iPhone
From Your iPhone Settings The quickest way to turn off Find My iPhone is directly from your device’s settings. Here’s how to do it:
Go to Settings on your iPhone.
Tap on your Apple ID at the top of the screen.
Select Find My and tap Find My iPhone.
Toggle the switch to turn off Find My iPhone.
You’ll be prompted to enter your Apple ID password to confirm.
Using iCloud on the Web If your device is unavailable, you can also disable Find My iPhone using iCloud’s website. Here’s the step-by-step process:
Visit iCloud.com and sign in with your Apple ID.
Click on Find iPhone.
Select All Devices at the top and choose your iPhone from the list.
Click Remove from Account to disable Find My iPhone.
Via the Apple Support App If you’re having trouble accessing iCloud or your iPhone settings, you can use the Apple Support app to get help with turning off Find My iPhone.
Bonus Tips for Apple Users
Ensure your device is signed into the correct Apple ID.
Make sure you know your Apple ID password, as you’ll need it to confirm changes.
Always back up your data before turning off Find My iPhone to prevent data loss.
Why Trust Our Experts at Cell Phone Club?
If you need assistance turning off Find My iPhone or have any other Apple-related questions, We are one of the best Repair stores for phones in Brooklyn, NYC of experts is here to help. We specialize in:
iPhone and iCloud troubleshooting
Device setup and transfers
Apple product repairs and support
Affordable rates and fast service
Visit us Cell Phone Club for expert advice and personalized solutions to all your Apple needs!
Discover More
For a detailed guide on How to Turn Off Find My iPhone on iCloud and troubleshooting Apple devices, check out our website. Stay up-to-date with the latest tips and tricks for your Apple ecosystem
#iphonerepairservice#iphonerepairshop#iphonescreenrepair#iphonescreenreplacement#30minutesrepair#batteryreplacement#bayridgebrooklyn#androidrepair#blocknumber#brooklyn#iCloud#icloud tool#apple#findmy
0 notes
Text
Healthcare CEO Killer Inscribed These Words on the Bullet Casings

Leah covered this story earlier today: Brian Thompson, CEO of UnitedHealthcare, was shot and killed in what looks like a professional hit job. The targeted killing occurred around 6:45 AM, outside the New York Hilton Midtown, where an investors meeting was being held. In the video footage, the killer is seen shooting Mr. Thompson with a suppressed firearm in the leg and back before finishing him off.
There’s a new chilling clue regarding this premeditated killing: bullet casings were found at the scene, with “deny,” “defend,” and “depose” on them:
Mr. Thompson was the subject of a Justice Department investigation for insider trading (via NY Post):
UnitedHealthcare CEO Brian Thompson was one of several senior executives at the company under investigation by the Department of Justice when he was gunned down outside a Manhattan hotel on Wednesday. Thompson — who was killed in what police called a targeted shooting outside the Hilton hotel in Midtown — exercised stock options and sold shares worth $15.1 million on Feb. 16, less than two weeks before news of the federal antitrust probe went public, according to a Crain’s New York Business report from April. The stock price dropped sharply after the revelation that the DOJ was investigating whether the company had made acquisitions that consolidated its market position in violation of antitrust laws, a source familiar with the probe told the outlet.
Paulette Thompson

said her late husband was the subject of death threats (via NBC New York):
Thompson’s wife, Paulette Thompson, told NBC News that the executive told her "there were some people that had been threatening him.” She said she didn't have details, but suggested they may have involved issues with insurance coverage. "Speaking to other employees that traveled with him to New York, it doesn't seem like he had a security detail," NYPD Chief of Detectives Joseph Kenny told reporters. "He left the hotel by himself, was walking, didn't seem like he had any issues at at all." The suspect, dressed in a hooded sweatshirt and carrying a distinct gray backpack, then fled on foot down an alleyway before pedaling an e-bike into Central Park a few blocks away. The shooter was at large, sparking a search that included police drones, helicopters and dogs.
The suspect took off on a Citi Bike, which police hope to use, tracking its “digital exhaust” (via NYT):
An electric Citi Bike like the one reportedly used as a getaway vehicle after the murder of United HealthCare C.E.O. Brian Thompson creates “digital exhaust,” streams of data that can be used to track the rider, said David Shmoys, a computer scientist at Cornell University who helped design the system. Between the creation of a Citi Bike account, connecting it to a credit card, undocking it, riding it around the city and docking it at a new location, every user creates many “streams of digital breadcrumbs” that can help Lyft, the company that operates Citi Bike, track the user’s location, and possibly their identity, Mr. Shmoys said. Combined with the user’s phone data and location shared with cell towers, “It is amazing how much information is conveyed,” Mr. Shmoys said. Jordan Levine, a spokesman for Lyft, declined to describe what data the company has retrieved or shared with the New York Police Department. “We stand ready to assist law enforcement with this investigation,” Mr. Levine said in an email. Every Citi Bike user must use a credit card to create an account, and the IP address used to do so is recorded, said Brian Muller, a regular Citi Bike user who participates in a program to redistribute bikes where they’re needed around the city. The credit card could be stolen and the IP address masked to hide the person’s identity, said Mr. Muller, who works as an information technology engineer. “If the perpetrator was smart, they would have a throwaway Lyft account not associated with their personal accounts,” Mr. Muller said. Electric Citi Bikes are limited to a speed of up to 18 miles an hour. Because they are slow compared with other kinds of electric bikes, because it takes so much time to rent a Citi Bike, and because so much data is generated every time such a bike is unlocked, Mr. Shmoys said that he was surprised that a gunman in such a high-profile crime would choose to use a Citi Bike at all. Perhaps the only advantage to using a Citi Bike was timing. The shooting occurred in Midtown Manhattan at 6:44 a.m., when commuters are typically riding thousands of Citi Bikes to office buildings in the area. “It’s a time of day when there’s a lot of bikes in Midtown,” Mr. Shmoys said. “Those stations are full.”
Finding this person will take time. His face is obscured. Yet, even when shooters’ faces are caught on video, it could take hours for them to be apprehended. The Times noted Frank James’ 2022 subway shooting. Despite him being caught on camera, it took police 31 hours to arrest him.
Trending on Townhall Videos
0 notes
Link
0 notes
Text
The Android operating system is now considered the best mobile OS used on smartphones and tablets. Android-powered smartphones and tablets are widely-accepted by consumers since they offer security and first-class features and are user-friendly. This popularity has resulted to the continuous development of Android applications that have become available at the Apps Market. These applications include games, multi-media players, security, and anti-virus applications. A number of applications are available at the Android market that will allow users to track down a stolen or lost Android-powered device. Some of these anti-theft Android applications that allow users to track down lost Android-powered smartphones of tablets are as follows: Where’s My Droid The Where’s My Droid android application will allow users to pinpoint the location of their smartphone. Once installed, the application will allow users to send a code to make the smartphone ring if in case it gets lost. This works even if the device is on silent mode. Another code will give users the GPS location of the lost smartphone. It also has a Commander option that allows users to control the device remotely. The Pro version of the application gives users the capability of remotely locking and wiping the smartphone as well as take pictures of the person who stole the phone. Plan B Plan B is a lifesaving application for users who were not able to install tracking applications on the smartphones before they were stolen. The application utilizes cell towers and GPS to pinpoint the location of the device. Once the location is found, it will send an email to the Gmail account of the owner indicating the location of the device. Plan B is also capable of enabling the GPS feature of a smartphone and provide updates on its location at ten-minute intervals. Users can text “location” to the missing device if it does not come with a GPS feature. The application will email the location of the device to the user. Android Lost Android Lost is an application that allows users to remotely control their Android-powered devices. Aside from providing the location of the device, the application will also annoy the thief through an alarm. The alarm can be remotely triggered by the user. The application can also allow users to remotely disable or enable the GPS, Wi-Fi and data features, wipe the SD card and retrieve the latest call list. The application will also inform the user if the SIM card of the smartphone is changed. It also provides users the capability of taking pictures using the front and rear camera of the Android device. AntiTheftDroid AntiTheftDroid is a simple yet powerful application that allows users to locate their Android device through GPS. It also allows them to monitor modifications on the SIM card and view images taken using the device. All of these are done through the internet. It can also activate the Audible Fire Alarm that can only be stopped by using a password. The application can also be remotely shown or hidden from the main app list. Prey Anti-Theft The Prey Anti-Theft application is among the most downloaded security application in the market. It provides users with the capability of tracking a missing Android-powered smartphone or tablet. It can send the GPS and Wi-Fi Geo-Location of the missing device if it gets lost. The application allows users to remotely lock the device It can be activated by simply sending a “GO PREY” text message to the smartphone. This will allow users to log into the control panel of the application and allow them to control the device. It will also mark the device as “Missing.” Once this is done, users will receive notices about the missing device. The application is hidden and cannot be uninstalled without using a password. . Cerberus Anti-Theft The Cerberus Anti-Theft application offers full protection to an Android-powered smartphone or tablet. It allows users to recover their missing device through the Cerberus Web Account, SMS, and by sending the user an alert once an unauthorized SIM card is used on the device.
Among the features of this Android application are its remote alarm trigger, GPS tracking, remote SD card swiping, remote and phone locking. It also allows users to record audio using a microphone. Find My Phone The Find My Phone application is simple Android application that allows users to monitor their smartphone using GPS. A number of mobile networks are supported by this application. Once it is activated and access from another Android-powered smartphone is authenticated, users can start tracking a missing smartphone. It will allow users to locate missing smartphones, find friends, track family members, find each other while on trips, locate children or spouse, monitor the children every day or while they are in a mall, or simply allow the user to know the location of someone. Beacon Beacon is a light-weighted and free android app. The app doesn’t put any negative effect to your Android device. Beacon lets you to Track Phone’s Location, Remote Lock, Remote Rumble your device. With help of this app you can manage multiple devices with one account. Lookout Security Lookout Security App is basically a full protection app for your Android device. Along with basic or advanced level protection of your phone from malware, viruses, suspicious programs, harmful websites, it offers “Find My Phone” feature to track your lost Android device. Just Login to your Lookout account and from there you can handle all the things and track your lost phone. The app lets your activate your phone’s GPS Remotely. You can track your phone from its location on Google Maps. Anti-Theft Alarm Anti-Theft Alarm is perfect to keep burglars away from your phone. You just have to activate the alarm and leave your phone on the table or wherever. If someone moves your phone an alarm will sound. It can only be stopped if you enter the PIN, so the burglars or curious friends won’t be able to stop it. This app is very useful to keep your kids away from your phone. McAfee Mobile Security McAfee Mobile Security protects your Android phone or tablet with award winning antivirus, privacy and security software. With this app you can lock the device to prevent misuse of your phone and personal info by remotely locking all data, including data on your SD card. Also it is possible to find your device if it is lost or stolen. View its location on a map; send a text to prompt its return. Kaspersky Mobile Security Kaspersky Mobile Security delivers the latest security technologies to protect Android smartphones from viruses, Internet threats, phishing sites, spyware and spam. It includes easy-to-use, advanced privacy features and – if your phone is lost or stolen – you can remotely protect your data and find the location of your missing phone. AVG AntiVirus With the AVG AntiVirus android app you’ll receive not only an effective, easy-to-use virus and malware protection, but also a real-time app scanner, phone locator, task killer, app locker, and local device wipe to help shield you from threats to your privacy and online identity. Real-time security scanner protection keeps you protected from downloaded apps and games. SeekDroid Find My Phone Find My Phone by SeekDroid app offers a number of standard features such as remote swiping and locking, SMS activation, ring alert while in silent mode, GPS-enabling, and hide from view option. Users can also recover recent call logs, which is possible even if the SIM card is not inside the device. The Pro account of the application provides users with the capability of monitoring the movements of stolen devices using a history map. This will allow users to know where the device is going. It also provides protection for a number of devices and sends notifications whenever the devices go beyond a certain location. Phone Locator The phone locator app is a anti theft application that provides users with the capability for specific location of the device through its integrated GPS feature. This will facilitate the easy location of the device.
The application also provides remote data wiping and phone locking features to guarantee the safety of personal information inside the smartphone. These features provide users peace of mind in case their Android-powered devices are stolen or missing. A number of security applications are available at the Android Store. These applications allow users to track down a missing or stolen Android-powered device. However, the applications listed above are considered as the best and most user-friendly applications that offer a number of remarkable features. Katrin is an experienced writer in high tech sphere, blogger, loves to write about cell phone tracking apps which help parents to supervise their kids and find lost phones. Marketing manager in a team who developed mSpy, for more information visit mSpy customers’ review.
0 notes
Text
Phone Number Tracker
Phone Number Tracker: A Modern Tool for Safety and Connectivity
Phone Number Tracker In today's digitally connected world, tracking a phone number can serve multiple purposes. From ensuring the safety of loved ones to managing work-related communications, phone number trackers have evolved to become an essential tool. Whether it's finding a lost device or identifying an unknown caller, the ability to track phone numbers brings a sense of security and peace of mind.
However, it's important to understand how these services work, their legal boundaries, and how to use them responsibly. Here's a deep dive into how phone number trackers operate, the technology behind them, and their practical applications.
What is a Phone Number Tracker?
A phone number tracker is a tool that uses GPS, cellular tower triangulation, or Wi-Fi signals to determine the exact location of a mobile device. These tools are commonly used by individuals to find lost or stolen phones, monitor the location of family members for safety reasons, or identify the source of unwanted or suspicious calls.
Some tracking tools are built into smartphones, such as Apple’s “Find My” app or Google’s “Find My Device,” while others come as standalone applications or online services. The key difference between them is how they access location data—some use internal GPS data, while others rely on mobile network information.
How Do Phone Number Trackers Work?
Phone number trackers utilize a combination of technologies:
GPS (Global Positioning System): Many apps use GPS satellites to pinpoint the location of a device. The accuracy is usually within a few meters, making it one of the most reliable methods.
Cellular Tower Triangulation: This method calculates the position of a phone based on the signal strength from nearby cell towers. It’s less accurate than GPS but still effective in providing a general location.
Wi-Fi Signals: In urban areas, trackers can use Wi-Fi networks to enhance location accuracy. This is particularly useful indoors or when GPS signals are weak.
IP Address Tracking: Some services may also use the device’s IP address to locate the general area. However, this method is less precise and more commonly used for desktop or laptop tracking.
Legal and Ethical Considerations
While phone number tracking can offer significant benefits, it is crucial to understand the legal implications. Tracking someone without their knowledge or consent can be illegal in many jurisdictions. It's always important to respect privacy laws and ensure that tracking is done with the full consent of the person being tracked, except in cases where parental control or emergency services are involved.
For businesses, employee tracking must adhere to workplace laws and policies. Employers are advised to clearly communicate tracking practices and ensure they are only used for legitimate reasons like safety or work-related activities.
Practical Applications of Phone Number Tracking
Finding Lost or Stolen Phones: With the rise of phone theft or loss, tracking apps provide an easy way to locate and possibly recover devices.
Parental Control: Parents can monitor their children’s whereabouts using phone tracking tools to ensure their safety, especially when they’re traveling alone or attending events.
Business Use: Employers can use phone tracking to monitor company phones, ensuring the devices are used appropriately and to track field employees' location for logistical reasons.
Verifying Unknown Callers: With phone number trackers, you can determine if an unknown caller is from a legitimate source or if it’s a potential scam.
How to Choose a Phone Number Tracker
When selecting a phone number tracker, consider the following factors:
Ease of Use: Opt for a tracker that’s user-friendly, with a clear interface and easy setup process.
Compatibility: Make sure the app or service is compatible with the operating system of the device you want to track—iOS, Android, or others.
Accuracy: Look for a tool that provides precise location data, preferably using a combination of GPS and Wi-Fi signals for the best results.
Security: Ensure that the service you choose has strong privacy protocols in place to protect your data.
Cost: Some tracking services are free, but they might have limitations. Consider whether a paid service might offer better features, reliability, or support.
Conclusion
Phone number trackers have become a versatile tool for personal safety, device management, and business operations. While they offer significant benefits, it is crucial to use them responsibly and within legal boundaries. As technology continues to evolve, phone tracking tools are likely to become even more sophisticated, offering greater accuracy and additional features.
FAQs
1. Can I track a phone number without the owner's consent?
No, tracking someone's phone without their knowledge or consent is illegal in many jurisdictions. Always ensure that tracking is done with the owner's permission, unless you're using parental controls or in cases of emergencies.
2. How accurate are phone number tracking tools?
The accuracy depends on the technology used. GPS-based trackers are the most accurate, often within a few meters, while cellular tower triangulation or IP address tracking offers less precise results.
3. Are free phone number tracking apps reliable?
Free apps can be useful but may come with limitations, such as less accurate tracking or fewer features. Consider using a paid service if you need more reliability, better accuracy, or customer support.
4. What should I consider when choosing a phone number tracker?
Look for ease of use, compatibility with your device, accuracy, security, and whether the cost of the service fits your budget. Make sure the tracker respects privacy laws and safeguards your data effectively.
0 notes
Text
Android smartphones can now be locked automatically by Google to protect personal information
There are numerous uses for the new theft detection lock coming to all devices running Android 10 or later versions.
There are numerous uses for the new theft detection lock coming to all devices running Android 10 or later versions, particularly for unlocked Android phones.
Google has significantly increased the theft resistance of your Android smartphone, especially for unlocked Android phones. Not in the physical sense, but if it is stolen, the new “theft detection lock” guarantees that the personal information is secure, ensuring that the thief cannot utilize the phone, even if it’s one of the unlocked Android phones.
The newly announced Xiaomi 14T Pro was found to include this innovative feature, which is now being rolled out to Android smartphone customers in the US, including those with unlocked Android phones. Mishaal Rahman initially reported the news on Threads. Three main theft-related feature components are being rolled out by Google: remote lock, offline device lock, and theft detection lock, all of which enhance the security of unlocked Android phones.
The new theft detection lock feature applies a machine learning model to detect a phone snatched from someone’s hand. The thief then attempts to flee on foot or in a car. Once the Android smartphone, especially an unlocked Android phone, detects theft detection lock mode, the cell locks itself automatically, depriving the robber of any private data that may have been saved on the device.
Similarly, if a thief attempts to disconnect the telephone from the net for a long length of time, yet another feature known as offline device lock will also be triggered. This feature is particularly important for all the owners of unlocked Android phones because it will serve as an added safety feature. Finally, the thieves who stole those mobile phones, including the unlocked Android devices, can use the remote locking feature provided by the Find, My Device manager in order to lock their devices remotely and, during such lockout, ensure that their users will be able to access the data in a locked device.
These beta capabilities, which Google has been testing since August, will soon be available on all compatible Android smartphones, including unlocked Android phones. On compatible Android handsets, these functions can be accessed through the Settings > Google > Google Services menu. To make use of all the most recent anti-theft security features offered by Google, make sure you are using the most recent version of the Google Play services, especially if you own unlocked Android phones.
Read More: Click Here
#MagazinesforEntrepreneurs#InternationalBusinessMagazine#GlobalBusinessMagazine#TopBusinessMagazine#Android#smartphones
0 notes
Text
Unlocking Digital Security: The Benefits of Hiring Professional Cell Phone Hackers
In an era where digital data is a prized commodity, ensuring the security of your personal and professional information is paramount. While hacking often carries a negative connotation, professional cell phone hackers offer legitimate services that can enhance your digital security. Here are the key benefits of hiring professional cell phone hackers:
Recovering Lost Data
One of the primary benefits of hiring professional cell phone hackers is data recovery. Whether you've accidentally deleted important files or experienced a system crash, these experts can help retrieve lost data from your phone, ensuring you regain access to critical information.
Strengthening Security Measures
Professional hackers are adept at identifying vulnerabilities in your cell phone’s security system. By conducting thorough assessments, they can pinpoint weak spots and recommend robust security measures to protect against unauthorized access, malware, and other cyber threats.
Ethical Hacking for Testing Purposes
Businesses often hire professional hackers to perform ethical hacking, also known as penetration testing. This involves simulating cyber-attacks to test the resilience of a company’s security protocols. The insights gained from these tests are invaluable in fortifying defenses against actual threats.
Monitoring and Protecting Sensitive Information
For individuals and businesses handling sensitive information, professional cell phone hackers can implement advanced monitoring systems. These systems track any unauthorized access attempts, alerting you to potential breaches and ensuring the confidentiality of your data.
Recovering Stolen Devices
In cases where a cell phone is stolen, professional hackers can assist in tracking and recovering the device. Using sophisticated techniques, they can locate the phone and help recover any sensitive information that might be at risk.
Enhancing Privacy Controls
With increasing concerns about privacy, professional hackers can help configure your cell phone settings to maximize privacy. This includes securing communications, safeguarding personal data, and preventing unauthorized tracking or surveillance.
Assisting in Legal Investigations
Professional cell phone hackers often work with law enforcement agencies to aid in legal investigations. Their expertise can be instrumental in uncovering digital evidence, tracing cybercriminal activities, and supporting legal cases involving digital data.
Educating Users on Best Practices
A significant benefit of hiring phone hacking services in USA is the educational aspect. These experts can provide valuable insights and training on best practices for digital security, empowering users to protect their devices and data more effectively.
While the term "hacker" might evoke images of cybercriminals, professional cell phone hackers offer essential services that enhance security and privacy in the digital age. From recovering lost data to fortifying defenses against cyber threats, their expertise is invaluable for both individuals and businesses. By leveraging the skills of these professionals, you can ensure that your digital life remains secure, private, and resilient against potential threats.
0 notes
Text
Can You Really Find My Device Android by IMEI Number? Explained!

In the digital age, losing your Android phone can be a nightmare. Whether it’s misplaced or stolen, your first instinct is likely to search for ways to recover it. One commonly suggested method is using your device's IMEI number. But the question remains: Can you really find my device android by imei number? Let’s explore the truth behind IMEI tracking and how tools like an IMEI number tracker or an IMEI tracker can help.
What is an IMEI Number?
IMEI stands for International Mobile Equipment Identity, a unique 15-digit code assigned to every mobile device. This number helps identify your phone on a mobile network and can be used to block the device if it's stolen. You can usually find it by dialing *#06# on your device or checking the phone's settings, box, or under the battery (if removable).
Can You Really Find My Device Android by IMEI Number?
The short answer is: Yes, but with limitations.
While the IMEI number itself doesn’t contain location data, it can be used by network providers and law enforcement to locate or block a lost or stolen phone. However, individuals typically cannot use the IMEI number alone to find a phone without assistance from service providers or law enforcement.
That said, specialized tools like TrackIMEI.net offer solutions by working with cellular data and IMEI databases to assist in tracking. Although not guaranteed to provide real-time tracking, such services increase the chance of recovering your device.
How IMEI Number Tracker Tools Work
An IMEI number tracker or IMEI tracker operates by linking your IMEI to cell towers, GPS data (if available), and sometimes Wi-Fi signals. Here's how they generally function:
User provides the IMEI number of the lost device.
The tool checks against databases and network data.
If the phone is active or recently used, it can show its last known location.
These tools are particularly useful when integrated with mobile operators or databases that maintain information on stolen or active devices.
Best Practices When Using an IMEI Tracker
If you decide to use an IMEI tracker, consider these tips:
Act quickly: The sooner you report your lost phone, the better.
Report to your service provider: Ask them to block the device and assist in tracking.
Use trusted tools like TrackIMEI.net to ensure your data is safe and your efforts are effective.
Alternative Methods to Find Your Android Device
While IMEI-based tracking can be effective, combining it with other methods improves the likelihood of recovery:
1. Google Find My Device
Google’s own tool is often the first step. Simply go to Google Find My Device and sign in with your Google account. From here, you can:
View the phone’s last known location
Ring the device
Lock or erase it remotely
2. Use a Pre-installed Security App
Some Android brands offer security or anti-theft apps (like Samsung's Find My Mobile) that provide tracking and remote locking features.
Why IMEI Tracking Matters
When your phone is stolen, a thief may remove SIM cards or disable GPS. In such scenarios, traditional tracking tools might not work. The IMEI number becomes essential because it remains constant, even after resetting the phone or changing SIM cards. Carriers can block the device entirely using the IMEI, rendering it useless on any network.
Limitations of IMEI-Based Tracking
Not real-time: Unlike GPS tracking, IMEI tracking may not offer live updates.
Dependent on carriers: Most IMEI tracking requires cooperation with service providers.
Law enforcement assistance: In many cases, only authorities can fully access IMEI tracking data.
Final Thoughts
So, can you find my device Android by IMEI number? The answer is yes—but it’s most effective when combined with professional tools and official assistance. A reliable IMEI number tracker like TrackIMEI.net can increase your chances of recovery. Just remember, while IMEI tracker tools are helpful, using all available resources (Google services, carrier support, and police reports) will give you the best shot at retrieving your lost device.
Stay proactive, store your IMEI securely, and act fast when misfortune strikes.
Read More : https://trackimei.net/
0 notes
Text
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn on cell data
Cell data security
Cell data security is a critical concern in today's digital age, with the widespread use of mobile devices for communication, work, and personal tasks. The security of data stored on cell phones, tablets, and other mobile devices is of utmost importance to protect sensitive information from falling into the wrong hands.
To ensure cell data security, it is crucial to implement various measures and best practices. One essential step is to set up strong passwords or biometric authentication methods such as fingerprint or facial recognition to prevent unauthorized access to the device. It is also important to regularly update the device's operating system and applications to patch any vulnerabilities that cybercriminals could exploit.
Encrypting data on the device adds an extra layer of protection, making it unreadable to anyone who does not have the encryption key. Avoid connecting to public Wi-Fi networks, as they may not be secure and could expose your data to potential threats. Utilizing a virtual private network (VPN) when connecting to the internet on a mobile device can help encrypt data traffic and protect your online activities from prying eyes.
Backing up your data regularly to a secure cloud storage service ensures that you can still access your information in case your device is lost, stolen, or damaged. Be cautious when downloading apps or clicking on links, as they could contain malware designed to steal your personal information.
By following these best practices and staying vigilant, you can safeguard your cell data and minimize the risk of falling victim to cyberattacks or data breaches. Remember that protecting your cell data is not just about securing your device but also about safeguarding your personal and sensitive information in an increasingly interconnected world.
VPN benefits for mobile
Mobile devices have become an integral part of our daily lives, serving multiple purposes beyond just communication. With the increasing reliance on smartphones and tablets for various online activities, the need to secure our online presence has also grown. This is where Virtual Private Networks (VPNs) come in, offering a range of benefits for mobile users.
One of the key benefits of using a VPN on a mobile device is enhanced security and privacy. By encrypting your internet connection, a VPN protects your sensitive data from potential cyber threats such as hacking, phishing, and identity theft. This is especially important when connecting to public Wi-Fi networks, which are notorious for their lack of security.
Moreover, VPNs allow mobile users to bypass geo-restrictions and access region-locked content. By connecting to a server in a different location, you can unblock websites, streaming services, and apps that may be restricted in your current location. This is particularly useful for travelers who want to access their favorite content while abroad.
Another advantage of using a VPN on mobile devices is the ability to maintain anonymity online. VPNs mask your IP address, making it difficult for websites and online services to track your activity and location. This can help prevent targeted ads, location tracking, and other forms of online surveillance.
In conclusion, VPNs offer a range of benefits for mobile users, including enhanced security, access to geo-restricted content, and increased anonymity online. By using a VPN on your mobile device, you can enjoy a safer and more private online experience.
Cellular network privacy
In today's digital age, cellular network privacy has become a growing concern for individuals worldwide. With the increasing reliance on smartphones and mobile devices, the need to protect personal data transmitted over cellular networks has never been more critical.
Cellular network privacy refers to the measures taken to safeguard the confidentiality and integrity of data exchanged between devices using cellular communication. This includes phone calls, text messages, internet browsing, and other forms of data transmission over mobile networks.
One of the primary threats to cellular network privacy is eavesdropping, where cybercriminals intercept and monitor communication to steal sensitive information such as personal details, financial data, or login credentials. To mitigate this risk, encryption technologies such as Secure Socket Layer (SSL) and Virtual Private Network (VPN) are employed to secure data transmission and protect user privacy.
Moreover, users are advised to be cautious when connecting to public Wi-Fi networks, as these are often targeted by hackers seeking to exploit security vulnerabilities and gain unauthorized access to devices connected to the network. It is essential to use strong passwords, enable two-factor authentication, and update device software regularly to enhance cellular network privacy.
As the digital landscape continues to evolve, maintaining cellular network privacy will require a collaborative effort between users, network providers, and cybersecurity experts to implement robust security measures and protect sensitive information from unauthorized access and exploitation. By staying informed and proactive about privacy risks, individuals can safeguard their data and enjoy a secure mobile experience in an increasingly interconnected world.
Importance of VPN on mobile data
In today's digital age, where our smartphones have become an extension of ourselves, safeguarding our online privacy is paramount. With the prevalence of mobile data usage for browsing, streaming, and accessing sensitive information, the importance of using a Virtual Private Network (VPN) cannot be overstated.
A VPN offers a secure and encrypted connection between your device and the internet, regardless of whether you're connected to a public Wi-Fi network or using your mobile data. This encryption ensures that your data remains private and protected from prying eyes, including hackers, government surveillance, and even your Internet Service Provider (ISP).
When using mobile data, the risks of data interception and hacking are heightened, especially when accessing sensitive information such as banking details or personal emails. By using a VPN, you create a secure tunnel through which your data travels, shielding it from potential threats and cyberattacks.
Moreover, a VPN allows you to bypass geo-restrictions and access content that may be blocked in your region. Whether you're traveling abroad or simply want to access streaming services or websites unavailable in your area, a VPN grants you the freedom to browse the internet without limitations.
Additionally, VPNs offer anonymity by masking your IP address, making it difficult for websites and online services to track your online activities. This anonymity adds an extra layer of privacy and security, ensuring that your digital footprint remains private.
In conclusion, utilizing a VPN on mobile data is essential for safeguarding your online privacy, protecting sensitive information, and accessing restricted content. By encrypting your connection and providing anonymity, VPNs empower users to navigate the digital world safely and securely, regardless of their location or network connection.
Using VPN on cellular data
Using a VPN on cellular data can provide users with enhanced security and privacy when browsing the internet on their mobile devices. A VPN, or Virtual Private Network, encrypts the user's internet connection, making it more difficult for hackers or malicious third parties to intercept their data. This is especially important when using public Wi-Fi networks, as these connections are often unsecured and vulnerable to cyber attacks.
By using a VPN on cellular data, users can also access geo-restricted content that may be blocked in their region. This is particularly useful for streaming services, such as Netflix or Hulu, that have region-specific content libraries. With a VPN, users can connect to servers in different countries and bypass these restrictions, allowing them to enjoy a wider variety of content on their mobile devices.
Furthermore, a VPN can help users avoid tracking by internet service providers and advertisers. By encrypting their connection and masking their IP address, users can maintain their anonymity online and prevent targeted advertising based on their browsing habits.
While using a VPN on cellular data can provide numerous benefits, it's important to choose a reputable VPN service provider to ensure reliable performance and data protection. Users should also be mindful of potential speed reductions when using a VPN, as encryption can sometimes slow down their internet connection. Overall, incorporating a VPN into your mobile browsing routine can offer increased security, privacy, and freedom online.
0 notes
Text
How to Track Phone with IMEI Number
“I need to track a phone that was stolen from me. I have the IMEI number and it was a paid by a boost.” – Question from the Google community
Have you ever come across the same theft incident involving your phone? Do you want to track your lost cell phone after it went missing? If the answer is yes, read this article. We will explore whether we can successfully track phones with IMEI numbers.

What Is IMEI Number?
IMEI is a short name for International Mobile Equipment Identity, containing 15-digit numbers, which gives the network the ability to identify which type model of the phone. Every mobile device has an IMEI number. It is considered a security code or the one human ID card alike that no one can change or delete from the device. If you find out your cell phone is missing or stolen, using the IMEI number tracking can be very helpful. However, IMEI number itself does not contain any geolocation, it can only be tracked when the device is connected to the internet.

How to Track Phone with IMEI Number?
In this part, we will try three methods to track your phone using IMEI number platforms, and apps or report the loss to the cell phone carrier or the police. Finally, we will conclude on the success rate and security.
IMEI Number Tracking At a Glance
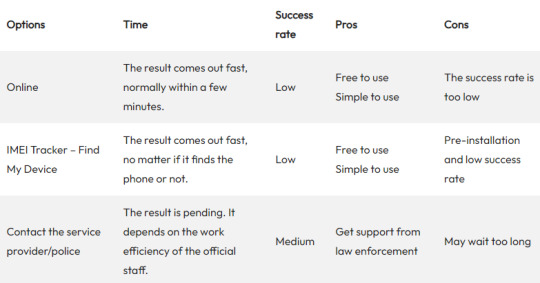
Using Online IMEI Tracking Service
Using an online IMEI tracking service is simple and easy for you to get your misplaced or stolen cell phone’s location, and it does not require you to have any other skilled knowledge or download any applications. The very important thing for the user to do is to enter a valid IMEI number, and then you can get the results. But the truth is that it is not always a success due to various reasons like phone connectivity. The search cannot react at all. It is still worth a try though.
There are a lot of IMEI tracking service platforms. Normally users will search IMEI track on Google and find many web pages that do good tracking services. But, there are a bunch of fake web pages that contain viruses and malware. It is risky to use them if you cannot verify them. Here are some products we have tried and tested for you.
Option 1: IMEI Tracker
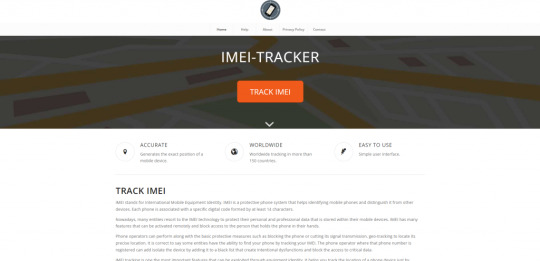
IMEI tracker, this website is free to use with an intuitive interface. It can track the precise location of the cell phone and show it on the interactive map. To locate the lost phone, you just need to enter the IMEI number and choose the country. The tracking service will be initiated.

After you enter the phone number, the website will start tracking your phone. You may wait for a while to check the results.
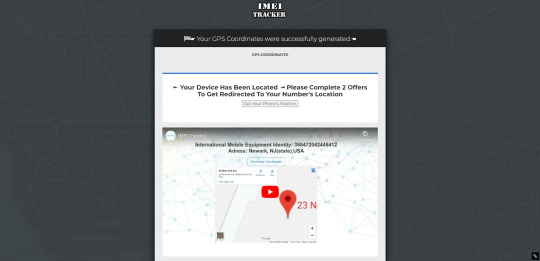
However, the website requires verification to view the results and the steps seem to be inducing and misleading. It completely has nothing to do with IMEI tracking.

Conclusion: Be careful using this website for its possible malware or sham.
Reviews from Real Users on Trustpilot: The reviews on Trustpilot are not positive. It scores 2.5 with 5 one-start reviews.


Option 2: Track IMEI
Trackimei.net, is also a free service to use. After you enter the valid IMEI number you can click the search button to start.
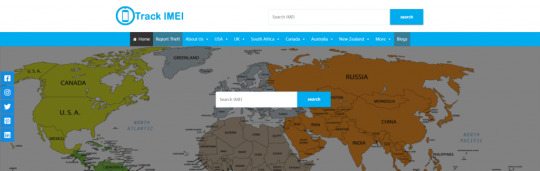
But the results are always redirecting pages for users and annoying ads. It seems like users cannot get the locations. It can be seen from the options, that for some specific countries they are not available, you may need to use other IMEI tracking services.
Conclusion: After we have a trial on this online IMEI tracker, it is not recommended to use it for its process and user experience.
Option 3: iStaunch
IMEI tracker by iStaunch is a free-to-use IMEI tracking service that works well on Samsung, Redmi, RealMe, Oppo, and Vivo devices. It has the same process to use with the above two pages. Enter the IMEI number and click the TRACK button. It needs the human hCaptcha verification as well and we passed it. Unfortunately, it failed to find our testing phone and showed a red line of words: No Data Found! Please Solve the Captcha & Enter the Correct IMEI Number. We tried with a different IMEI number and it has the same result.
Currently we can barely find any real user reviews and users are advised to be careful about privacy, security, etc. when using it.
Conclusion: Using the IMEI tracker online page may have the chance to track your phone but you should not hold too much hope about it.
Using Mobile Apps
Apart from using the IMEI tracker online page, there is an alternative to use, IMEI Tracker – Find My Device App, which is free. The most significant difference from the online page is that you need to pre-download the app to use, and that seems inconvenient for some users in certain circumstances. To use it, follow the steps below.
Step 1. Download and install the app.
Step 2. It will require some permissions for specific functions. Offer permission.

Step 3. After installing it, log in to your Google account. You need to set it up before you can use it.
Step 4. The app will ask you to set trust phone numbers of your family or friends. The phone number is used to receive messages of your phone’s IMEI location and phone number when your phone is lost or stolen.
Step 5. After setting it up, you can go to the Security command. Turn on the buttons of Get Lost Phone, Ring Silent Phone, and Get Current Location. By enabling “Get lost Phone”, you can track your lost phone on another device via an SMS “getlostphone”.
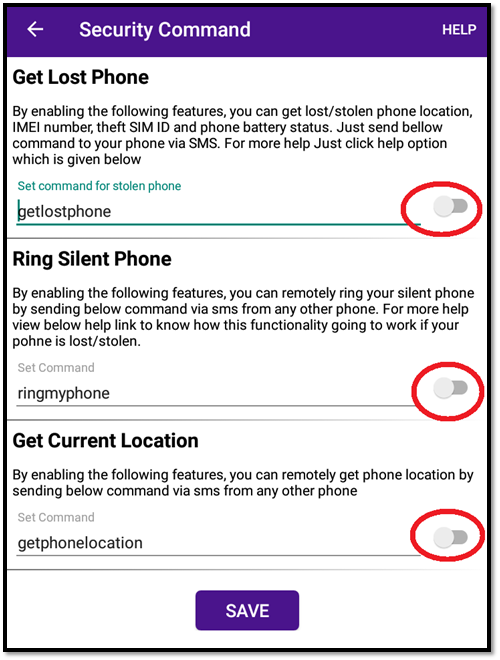
However, from the user’s comments, the success rate of locating the lost phone is not very high.
Conclusion: The IMEI track app is a bit more complicated than online IMEI tracking and requires you to pre-install it. From the users’ reviews, some people succeeded. Although it does not have a high success rate in locating your lost phone, it is worth a try. If it doesn’t work, you still get other methods.
Report the loss to the cell phone carrier or the police
Report the lost phone and provide the IMEI number, the cell phone carrier can help track your lost phone’s real-time location info through their cell towers or GPS and help you block the lost phone to prevent the thief from using it. If you report to the police and claim your phone as lost, the chance of getting your lost phone back will be increased due to legal considerations, better cooperation with a service provider, and more minor challenges. The law enforcement tracking your phone is more efficient than you do it. However, there are still many limitations, like an internet-disabled phone. It seems like having a higher success rate than tracking your phone with an online service or app by yourself, but the waiting time can also be pending because the result is not guaranteed.
How to Find the IMEI Number for Your Device?
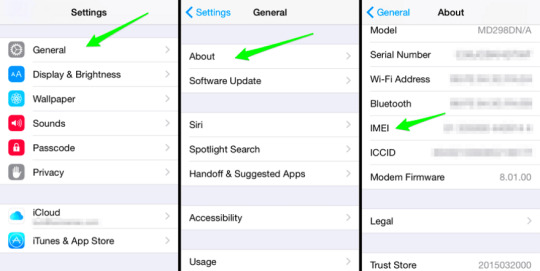
If you want to find your lost phone with an IMEI number, you must recite or record it in advance. Here are some ways to find the IMEI number.
Physically Lookup
Packing box, You can find the IMEI number in every device’s outer page and box:

On the back of the battery:


Dial Number
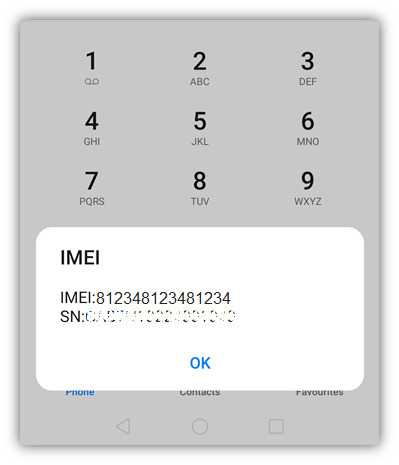
It is a code to check the IMEI number of your phone. Just dial *#06# the IMEI number page will pop up on your screen instantly.
Check IMEI number from the phone settings
The above will work for you, but if you seek more alternatives, you can find your IMEI number from the phone system settings.
Android
Go to the system settings > About phone > Status (It is not an inevitable option. Some models do not require this step).

iOS
Go to the Settings > General > About. You can see your IMEI number on the screen.

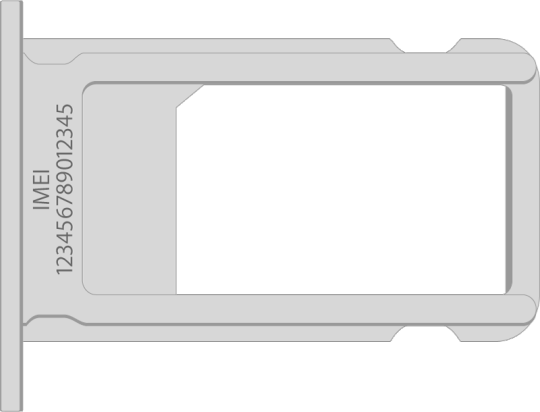
An alternative way to check the iPhone IMEI number when you cannot access the system settings, you pull out the sim tray to check it.
Benefits of IMEI Tracking
IMEI number is unique and secure. In general, people do not get a big chance to access your IMEI number, although it is possible. That means that the network will better identify your device without information leaking. The IMEI is compatible with all mobile devices, an identifier of your phone device instead of yourself, the user, or the sim card, giving increased accuracy when tracking the lost phone.
Applications of IMEI Tracking
Find your lost phone.
IMEI number makes it possible for you to get your cell phone back. The lost phone can be tracked by the IMEI number as long as the phone is connected through the network.
You can use the IMEI tracker to track your cell phone and the cell carrier and police can track the phone according to the IMEI number of the cell phone as well.
Block the stolen phone.
If you have lost your phone, contact the phone carrier, they can block your device and prevent the phone device from being used by thieves. And will protect your properties and privacy.
Check your bought phone.
You can get all the information about your phone by using the IMEI number, finding your phone model, brand, date and place of manufacture, and other information, by which you can determine whether your phone is authentic or not.
Can I find my phone without an IMEI code?
Yes. As finding your phone with an IMEI code is not 100% successful, you can try other solutions to locate your phone, such as locating it via a phone number. MLocator is one of the convenient and secure tools to use. You don’t need to download anything or use any other device.

The service is legal to use and does not violate the applicable laws of any country. Just enter the phone number of the phone you want to track and choose a subscription. The current user will receive a message containing a link; as long as the user clicks on it, the location of the phone will be shared, and the precision will be high, with about 3 meters of margin of error. This is the best way to track your lost phone as long as the sim card is inserted.
FAQs
Can I Track an IMEI Number through Google Earth?
No. The IMEI number does not contain any location information on the phone. You can only use some tracking services or rely on mobile carriers to find the lost phone resort on the IMEI number.
Google Earth is a mapping service program that utilizes satellites to show details of aerial imagery on your computer screen. Although you cannot use Google Earth to track your phone, you can use it to check the builds around if you have the coordinates of the phone.
Can the police track IMEI if the phone is off?
No. If others turn off the lost phone, the phone cannot be tracked by IMEI number. Only when the phone is connected to the network is IMEI tracking useful.
What information can you access with an IMEI?
By getting the phone IMEI number, you can know the brand, model, serial number of the device and other specifications.
Can the IMEI number be changed by others?
No. The IMEI number is considered an identity code of the device. It cannot be modified.
Conclusion
So, after discussing the IMEI, you have learned what it is. If you lost your phone but know your IMEI number, you can use the phone tracking service by IMEI or seek help from the cell phone carrier or police. But not everyone always has the IMEI number. In this case, a phone number tracker like MLocator may be a choice. We hope all of you will never lose your phone, but if, unfortunately, you suffer from this, we hope the methods above will be helpful.
Repost from https://www.mobilephonelocator.net/blog/track-phone-with-imei-number/
1 note
·
View note
Text
Monitor Your Wife’s Location by using phone hackers in USA

What is a phone tracker?
A phone tracker in USA is a sophisticated tool designed to monitor and track the location of a mobile device discreetly. Also referred to as a phone spy, spy phone, or phone monitor, this technology employs GPS and other advanced features to provide real-time or historical location information. In addition to tracking whereabouts, these tools can encompass a range of functionalities, such as monitoring call activities, text messages, and even app usage. It’s crucial to note that while phone trackers in USA serve various purposes, responsible and ethical use is paramount to ensuring privacy and trust, particularly in personal and professional relationships.
importance of phone hackers in USA
The importance of phone hackers in USA is multifaceted, particularly in the realm of privacy and security. Phone hackers, equipped with advanced tools like phone trackers, phone spies, spy phones, and phone monitors, play a pivotal role in ensuring the safeguarding of personal information. These technologies aid in tracking and monitoring devices, offering a layer of security against potential threats. While ethical considerations must guide their use, phone hackers contribute significantly to data protection and can assist in tracking lost or stolen devices. However, responsible and legal usage is crucial to balancing the benefits of these tools with privacy concerns.
🟩 Related Blog: Hire A Phone Hacker For Private Investigation
Best phone tracker app in USA
The importance of phone hackers in USA is multifaceted, particularly in the realm of privacy and security. Phone hackers, equipped with advanced tools like phone trackers, phone spies, spy phones, and phone monitors, play a pivotal role in ensuring the safeguarding of personal information. These technologies aid in tracking and monitoring devices, offering a layer of security against potential threats. While ethical considerations must guide their use, cell phone hackers contribute significantly to data protection and can assist in tracking lost or stolen devices. However, responsible and legal usage is crucial to balancing the benefits of these tools with privacy concerns.
Hire a phone hackers to track your cheating wife’s location
Do you want to hack your spouse’s location track but can’t touch it? or he or she works in another city, and you suspect your partner of cheating? No worries, we have brought an article to understand how to hire a hacker swiftly without any hurdle.
A hacker can do anything from hacking an email password, hacking a phone, breaching a firewall, and much more. Access any account from another without even getting noticed. Are you afraid that your loved one is cheating on you? You can then hire a hacker and go through their email chats or even the messages to find out everything about them.
Top 5 ways to track your wife’s live location
In the digital age, where technology intertwines with our daily lives, the idea of tracking a spouse’s live location has become a subject of curiosity and discussion. While it’s crucial to approach this topic with sensitivity and respect for privacy, there are several ways to achieve transparency within a relationship without compromising trust. Let’s explore the top five methods for tracking your wife’s live location.
1. Mutual Consent-Based Apps: Fostering Transparency
2. Built-In Phone Features: Simplicity at Your Fingertips
3. GPS Tracking Devices: Dedicated Solutions for Accuracy
4. Smartwatches and Wearables: Stylish and Functional Tracking
5. Seeking Permission help — HackersList
🟪 Emergency Contact From HackersList
In the realm of digital safety, the HackersList Emergency Contact Hacker System emerges as a paramount tool, offering users an extra layer of security. This innovative feature provides swift notifications in critical situations, ensuring users are promptly informed via preferred communication channels. Setting up emergency contacts is seamless, allowing users to tailor the system to their specific needs. HackersList’s commitment to privacy and security shines through, employing robust measures to safeguard user information. With a user-friendly interface, compatibility across various devices, and responsive customer support, the HackersList Emergency Contact Cell Phone Hackers in USA System stands as a reliable and effective solution for enhancing personal safety. You can take advantage of our services by clicking on HackersList to post a new job.
Final Word :
In other words, the exploration of monitoring a spouse’s location underscores the delicate balance between privacy and trust. While technology offers tools that can provide insights into a partner’s whereabouts, ethical considerations, legal ramifications, and the human element must not be overlooked. Building trust through transparency, open communication, and respecting boundaries emerges as a more sustainable approach to addressing relationship concerns.
0 notes