#Challenges and Opportunities in Blockchain Forensics
Explore tagged Tumblr posts
Text
Blockchain and Beyond: The Future of Forensics in Investigating Cybercrime
Blockchain is a decentralized digital ledger technology that enables secure and transparent recording of transactions across a network of computers. It consists of a chain of blocks, each containing a cryptographic hash of the previous block, along with..
Continue reading Blockchain and Beyond: The Future of Forensics in Investigating Cybercrime

View On WordPress
#Advantages of Blockchain in Forensic Investigations#Beyond Blockchain: Future Trends in Cybercrime Investigation#Challenges and Opportunities in Blockchain Forensics#Emergence of Blockchain Technology in Cybercrime Investigations#The importance of digital forensics in cybercrime investigations#Traditional Forensic Methods in Cybercrime Investigations#What are digital forensics and forensic evidence?#What is Blockchain Technology?
3 notes
·
View notes
Text
Turning Panic Into Action: Astraweb’s Client Centered Process

When Jane Doe first reached out to Astraweb, she was overwhelmed with panic and uncertainty. Her life savings, heavily invested in cryptocurrency, had abruptly disappeared following a severe market crash. What initially felt like an irreversible loss soon transformed into a hopeful journey toward recovery all thanks to Astraweb’s dedicated, client-centered process.
The First Contact: Providing Calm, Reassurance, and Genuine Understanding
The difference began immediately at the first point of contact. Many companies in the digital asset recovery space treat clients as case numbers rather than individuals, but Astraweb prides itself on a profoundly human approach. From the moment Jane connected with their team, she was met with calm professionalism and empathetic understanding. Astraweb’s experts didn’t just collect the basic facts of her situation; they invested time in learning about her unique concerns, fears, and goals.
This personalized attention is critical. Financial loss, especially in the volatile cryptocurrency market, is not just about money it’s deeply tied to emotional well-being and future security. By acknowledging Jane’s distress and validating her fears, Astraweb’s team immediately alleviated much of her initial panic. They reassured her that despite the challenging circumstances, recovery was possible and that Astraweb would support her every step of the way. This empathetic approach planted the seeds of hope and trust that would sustain Jane through the recovery process.
Transparency and Clear Communication: Building Trust Through Every Step
One of the cornerstones of Astraweb’s client-centered methodology is transparency. Jane was kept fully informed from the outset, with the team providing clear, jargon-free explanations of the entire recovery process. Rather than leaving her uncertain or confused, Astraweb made sure she understood each step, from preliminary case assessment to the complex asset tracing and retrieval efforts ahead.
Regular, timely updates ensured that Jane never felt left in the dark. She received progress reports outlining milestones achieved, any obstacles encountered, and the strategies planned moving forward. This ongoing dialogue was more than just information sharing it was a partnership. Jane had the opportunity to ask questions, raise concerns, and engage actively in decision-making. Astraweb’s responsiveness and clarity gave her a sense of control and confidence, which is often lacking when facing financial recovery situations

Strategic Action and Efficient Recovery: Delivering Results with Precision and Care
With a thorough plan in place, Astraweb’s team mobilized swiftly and efficiently. Their approach was methodical and tailored to Jane’s specific case. Leveraging cutting-edge technology and deep expertise in blockchain analysis and digital forensics, they navigated the complexities inherent in cryptocurrency recovery.
What sets Astraweb apart is not only their technical prowess but also their commitment to aligning every action with the client’s best interests. For Jane, this meant careful management of sensitive data and continuous coordination to ensure all efforts supported her recovery goals. The team’s professionalism was evident in their precision and tenacity, persistently pursuing leads and unraveling the often opaque paths that digital assets can take.
Over time, their dedication paid off. Astraweb successfully recovered a significant portion of Jane’s lost funds. This achievement was more than just a financial victory it was a powerful restoration of Jane’s peace of mind and future stability.
Final Steps: Restoring Financial Security and Empowering Confidence
When Jane received the final recovery statement, the relief and gratitude she experienced were profound. Astraweb’s seamless process had not only restored her financial security but also transformed a traumatic event into a story of empowerment. The client-centered approach meant Jane never felt like a passive bystander; instead, she was an informed, engaged partner in reclaiming her assets.
Beyond the monetary recovery, Jane gained something invaluable a renewed sense of control over her financial destiny. Astraweb’s dedication to transparent communication and compassionate case management helped her move past fear and uncertainty. She emerged with greater knowledge of digital asset management and an increased ability to face future financial challenges with confidence and clarity.

Astraweb’s Commitment: More Than Recovery, A Partnership
Jane’s story illustrates the core philosophy that drives Astraweb’s work: every client deserves more than just technical recovery services they deserve empathy, clarity, and partnership. The company understands that behind every lost asset is a person’s hopes, dreams, and security at stake.
For those facing the daunting prospect of lost cryptocurrency or other digital assets, Astraweb’s process offers a path forward. Through empathy-driven service, transparent communication, and technical excellence, they prove that even the most complex and distressing financial setbacks can be addressed with care and effectiveness.
If you or someone you know finds themselves in a similar predicament, Astraweb stands ready to provide expert guidance and dedicated support at every stage of recovery.
Contact: [email protected]
6 notes
·
View notes
Text
How Crypto Scam Recovery Services are Revolutionizing Cybersecurity
The rise of cryptocurrency has undeniably brought a wave of new opportunities, innovation, and financial freedom. However, with this growth, there has been a parallel surge in crypto-related scams. Hackers, fraudsters, and unscrupulous individuals have leveraged the anonymity and decentralized nature of cryptocurrencies to defraud investors. As the threat landscape grows, so too does the need for innovative solutions to combat these malicious activities. Enter the world of crypto scam recovery experts services — a rapidly growing industry that is revolutionizing cybersecurity and offering hope to individuals who fall victim to scams.
If you lost money due to crypto fraud or an Online Scam, don’t be a victim, fight back and retrieve your stolen funds. BitcoinScamWatch retrieve services can assist law firms and law enforcement to find and retrieve your funds. Visit https://bitcoinscamwatch.org/ and file a complaint. An agent will be assigned to you to assist you on the retrieve process.
The Surge of Crypto Scams
Cryptocurrencies, especially Bitcoin and Ethereum, have become mainstream in the past decade, attracting both legitimate investors and opportunistic fraudsters. Whether through phishing emails, Ponzi schemes, fake initial coin offerings (ICOs), or even more sophisticated ransomware attacks, crypto scams are becoming more prevalent and diverse.
One of the key attractions of cryptocurrencies for cybercriminals is their irreversibility. Unlike traditional financial transactions, once a cryptocurrency transaction is confirmed on the blockchain, it cannot be reversed. This makes it an ideal target for scammers who promise high returns on investments or fraudulent crypto exchanges that disappear with investors' funds. The anonymity of the blockchain also makes it incredibly difficult to trace perpetrators, further exacerbating the problem.
The Role of Crypto Scam Recovery Services
Crypto scam recovery services have emerged as a direct response to the rising tide of fraud in the cryptocurrency market. These specialized services are designed to help individuals and organizations recover funds lost to scams, fraudulent investments, or cybercrime. Recovery specialists typically employ a combination of forensic investigation, blockchain analysis, and legal expertise to trace stolen assets and pursue potential recovery routes.
Blockchain Forensics and Tracking
One of the most powerful tools that crypto scam recovery services have at their disposal is blockchain forensics. The blockchain is a public ledger that records every transaction made with a cryptocurrency. While transactions are pseudonymous, they are not entirely anonymous. With the right tools and expertise, recovery professionals can trace stolen funds through multiple addresses and exchanges, potentially identifying the criminal's trail.
Blockchain forensics allows recovery services to map out a scammer's transaction patterns and determine where the funds were moved after being stolen. By following the digital breadcrumbs left behind, recovery professionals can sometimes successfully retrieve assets, either by working with cryptocurrency exchanges or by leveraging law enforcement agencies if the case is severe enough.
Legal Support and Regulatory Navigation
As cryptocurrency scams often transcend borders, legal challenges play a critical role in the recovery process. Recovery services don’t just rely on technical expertise; they also work closely with legal teams that understand the complex regulatory landscape surrounding cryptocurrencies. With no centralized authority overseeing cryptocurrency transactions, recovering stolen funds can be a tricky process.
However, as more countries implement regulations to protect crypto investors, recovery services are increasingly able to leverage legal frameworks to their advantage. Legal experts can help file complaints with the appropriate regulatory bodies, collaborate with local authorities, or even initiate civil actions to hold scammers accountable. The involvement of legal professionals ensures that victims are not only seeking technical solutions but also taking steps to prevent future scams by promoting better regulatory standards.
Recovery Services: Preventing Future Scams
Another significant aspect of the crypto scam recovery services industry is its role in educating investors and reducing the likelihood of future scams. These services often provide consultations and educational resources to teach individuals how to recognize potential threats and avoid falling victim to scams in the first place.
For example, many recovery services offer advice on recognizing red flags in cryptocurrency offers, including promises of guaranteed returns, requests for upfront payments, or suspicious websites. By arming the public with knowledge, these services reduce the likelihood of new victims, which ultimately contributes to a healthier and safer cryptocurrency ecosystem.
The Future of Crypto Scam Recovery Services
As cryptocurrencies continue to gain adoption, the demand for scam recovery services is expected to grow. In the future, we can expect these services to evolve with advances in technology, including artificial intelligence and machine learning, which can automate parts of the tracking and recovery process. With the introduction of decentralized finance (DeFi), additional challenges will arise in terms of security, but also new opportunities for recovery professionals to tap into different blockchain networks.
Moreover, as governments around the world continue to regulate cryptocurrencies, a more structured framework for recovering stolen assets will emerge. This will likely provide greater support for scam victims and push for more transparent and secure crypto services, fostering a more trustworthy and safer crypto landscape.
Conclusion
Crypto scam recovery services are undeniably transforming the world of cybersecurity by providing an essential service in the fight against fraud. These services are not only recovering lost funds but also helping individuals and businesses navigate the complexities of the crypto world with greater security and confidence. As the industry continues to evolve, these services will remain a crucial part of the cryptocurrency ecosystem, helping to ensure that the promise of digital finance is realized without the shadows of cybercrime hanging over it.
4 notes
·
View notes
Text
How Crypto Fraud Detection Helps in Recovering Stolen Funds

Cryptocurrencies have revolutionized the financial world by offering decentralized, fast, and secure transactions. However, as with any rapidly growing technology, cryptocurrencies have also become a prime target for fraudsters and criminals. The anonymous and irreversible nature of crypto transactions has made it easier for bad actors to exploit the system. This has led to an increased demand for crypto fraud detection and recovery services. But how do these services help recover stolen funds, and why are they becoming so vital in today's digital economy? Let’s dive into the ways in which crypto fraud detection is playing a crucial role in recovering stolen funds and protecting investors.
Understanding the Impact of Crypto Fraud
The rise of cryptocurrencies has been accompanied by an increase in fraudulent activities, including Ponzi schemes, phishing attacks, and investment scams. Unlike traditional financial systems, cryptocurrency transactions are typically irreversible, making it incredibly difficult to trace stolen funds once they’ve been transferred. This creates a unique challenge for law enforcement and victims alike.
The lack of regulation in many crypto markets further exacerbates the problem, as fraudulent actors can easily take advantage of legal loopholes. For victims, the impact of crypto fraud can be devastating, often resulting in significant financial losses. As more people turn to cryptocurrencies for investment and transactions, the need for robust crypto fraud detection and recovery solutions has never been greater.
How Crypto Fraud Detection Helps in Recovering Stolen Funds
One of the primary ways crypto fraud detection helps in recovering stolen funds is through real-time monitoring and analysis of blockchain transactions. Unlike traditional banking systems, blockchain technology provides a transparent, immutable record of all transactions. This makes it possible to track the flow of stolen funds even after they’ve been transferred across multiple wallets.
Crypto fraud detection and recovery experts utilize advanced algorithms and artificial intelligence to monitor blockchain activity for any suspicious patterns or irregularities. They look for signs of fraud, such as sudden, large transactions, multiple small transfers designed to obfuscate the origin of the funds, or addresses known to be associated with criminal activity.
When a fraud is detected, the recovery team can take immediate action. This includes identifying the wallet addresses involved, tracing the stolen funds, and alerting relevant authorities or exchanges. In some cases, the funds can even be frozen or reversed, though this is dependent on the cooperation of various stakeholders, including the platform hosting the transaction.
Identifying Fraudulent Transactions Early
The key to successful crypto fraud recovery lies in identifying fraudulent transactions as early as possible. Thanks to advanced crypto fraud detection systems, suspicious activities can be flagged as soon as they occur. Crypto Fraud Detection and Recovery tools use machine learning to constantly improve their ability to recognize unusual patterns and flag them for further investigation. These systems are capable of detecting even the most subtle signs of fraud, such as tiny deviations from regular transaction behaviors, making it easier to prevent a loss from turning into a full-scale theft.
For example, if a crypto wallet involved in a transaction has been flagged for previous fraudulent activity or is on a watchlist, the system can alert the user or the service provider immediately. This early warning gives the victim an opportunity to stop the transaction before it’s completed, providing a vital window to recover the stolen funds.
The Role of Blockchain forensics
Blockchain forensics plays a critical role in crypto fraud detection. Unlike conventional financial systems, blockchain transactions are publicly recorded on a decentralized ledger. This transparency allows experts to trace the movement of stolen funds across various blockchain networks. Blockchain forensic experts use sophisticated tools to analyze these records and map the movement of funds in real-time.
This process involves connecting wallet addresses with real-world identities, identifying patterns of fraudulent behavior, and tracing the movement of funds across exchanges, dark markets, and other platforms. By following the trail of stolen funds, blockchain forensic teams can often recover a portion or, in some cases, the entire amount of stolen cryptocurrency.
Collaboration with Cryptocurrency Exchanges
One of the most challenging aspects of recovering stolen cryptocurrency is that fraudsters often move the funds across different platforms. However, many exchanges are now working proactively with crypto fraud detection firms to identify and prevent fraud in their systems.
When funds are stolen and transferred to an exchange, the exchange can assist in freezing the stolen funds while they are being tracked. Some exchanges even go a step further by requiring KYC (Know Your Customer) protocols, which make it harder for fraudsters to remain anonymous. If a fraudster attempts to withdraw stolen funds to their personal account, the exchange may flag the transaction and hold the funds for investigation.
By collaborating with crypto fraud detection services, exchanges can help ensure that stolen funds are not processed or laundered through their platforms, further increasing the chances of recovery.
Preventing Future Fraud through Education and Awareness
Beyond detecting and recovering stolen funds, crypto fraud detection services also play a crucial role in preventing future fraud. Many services offer education and resources to help users recognize the signs of potential scams. They often provide real-time alerts, detailed guides on securing wallets, and information on the latest fraud trends, helping investors safeguard their funds.
Awareness of common scams, such as phishing attacks, pump-and-dump schemes, and fake ICOs, can significantly reduce the likelihood of falling victim to fraud. Additionally, advanced security features like multi-signature wallets and hardware wallets, coupled with fraud detection tools, create a robust defense against fraud.
How Law Enforcement Uses Crypto Fraud Detection Tools
Law enforcement agencies around the world are increasingly turning to crypto fraud detection tools to assist in investigating and recovering stolen funds. With the rise of digital currencies, criminal activities, including money laundering, ransomware attacks, and dark web transactions, have become more complex and harder to trace. However, blockchain’s transparency allows investigators to track illicit transactions across borders.
By working with crypto fraud detection firms, law enforcement can use blockchain analysis to identify criminals, trace stolen funds, and build evidence for prosecution. This collaboration is crucial in bringing criminals to justice and ensuring that stolen funds are returned to their rightful owners.
Challenges in Crypto Fraud Detection and Recovery
Despite the advancements in crypto fraud detection and recovery, there are several challenges to overcome. One major hurdle is the anonymity that blockchain provides. While blockchain transactions are publicly visible, the identity behind each wallet address is typically unknown. This makes it difficult to identify fraudsters unless they can be linked to real-world identities.
Furthermore, the decentralized nature of cryptocurrencies means that there is no central authority that can reverse or freeze transactions once they have been completed. Even if stolen funds are tracked and identified, it often requires significant collaboration between exchanges, law enforcement, and fraud detection services to recover the funds.
Future of Crypto Fraud Detection and Recovery
As the crypto space continues to evolve, so too will the tools and technologies used to detect and recover fraud. Innovations in artificial intelligence, machine learning, and blockchain forensics will make it even easier to identify fraudulent transactions in real time. Additionally, the increasing regulation of cryptocurrency markets is likely to improve the ability to prevent and recover stolen funds.
As the industry matures and becomes more mainstream, greater cooperation between exchanges, regulators, and fraud detection services will be essential in reducing crypto fraud and recovering stolen funds. This collaboration will ensure that the crypto ecosystem remains secure, trustworthy, and beneficial for everyone involved.
Conclusion
Crypto fraud detection is an essential part of the cryptocurrency ecosystem, helping to safeguard investors and ensure the integrity of the digital currency market. By leveraging blockchain forensics, artificial intelligence, and real-time monitoring, fraud detection services can identify fraudulent activity early, trace stolen funds, and increase the chances of recovery. While there are challenges to overcome, the future of crypto fraud detection looks promising, with continued advancements in technology and greater collaboration between various stakeholders. As cryptocurrency adoption continues to grow, so too will the importance of robust fraud detection and recovery services in keeping funds secure and helping victims recover lost assets.
1 note
·
View note
Text
The Language Powering the Future of Tech
Python is more than just a programming language—it’s a movement that’s transforming industries and redefining technology. From web development and artificial intelligence to automation and data science, Python is shaping the way we interact with the digital world. Its simplicity, flexibility, and powerful capabilities make it the go-to language for both beginners and experienced developers.
1. Why Python’s Simplicity Stands Out
Python is known for its clean, human-friendly syntax, making it easier to learn and use compared to many other programming languages. It allows developers to write readable and efficient code, which means less time spent debugging and more time creating. Whether you're a coding newbie or an expert, Python’s ease of use makes it a powerful tool for bringing ideas to life. Joining a trusted Python online course equips individuals with the critical skills and expertise needed to thrive in this rapidly evolving field.

2. Python’s Reach Across Industries
Python is everywhere, driving innovation in different sectors:
Web Development: Django and Flask help developers create dynamic, scalable web applications.
Artificial Intelligence & Machine Learning: Python is the foundation of AI research, with libraries like TensorFlow and PyTorch leading the way.
Data Science & Analytics: Python simplifies data analysis, visualization, and processing, empowering businesses to make smarter decisions.
Automation & Productivity: From automating repetitive tasks to managing workflows, Python is an efficiency booster for professionals.
Cybersecurity & Ethical Hacking: Python plays a crucial role in security research, ethical hacking, and digital forensics.
3. Python in Cutting-Edge Tech
Python is shaping the future by powering innovations in:
Internet of Things (IoT): Smart devices communicate seamlessly using Python, making homes and workplaces more connected.
Blockchain Development: Python enables the development of decentralized apps and secure digital transactions.
Cloud Computing & DevOps: Cloud services rely on Python to automate infrastructure, deployment, and scaling.
Quantum Computing: Python is playing a role in the development of quantum technology, pushing the boundaries of science.
4. A Thriving Python Community
One of Python’s biggest strengths is its vast and supportive global community. Whether you’re learning the basics or working on advanced projects, Python enthusiasts worldwide share knowledge, collaborate on open-source projects, and help each other grow. The support from this community makes learning Python more engaging and accessible. With the Best Online Training & Placement Programs, you’ll master the skills to detect phishing emails, protect your personal data like a pro, and stay ahead of evolving cyber threats.
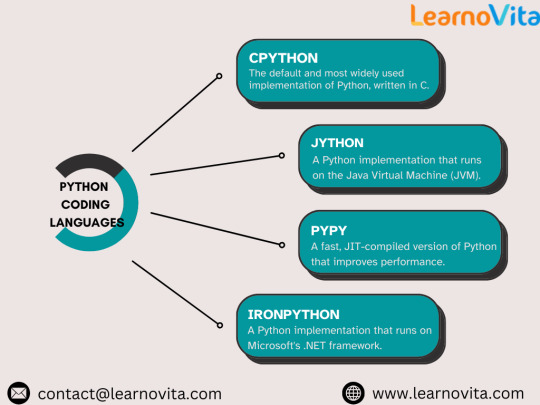
5. The Demand for Python Experts
Python is in high demand, with job opportunities spanning across industries like tech, finance, healthcare, and entertainment. Companies such as Google, Amazon, and Netflix actively seek Python developers for roles in software development, AI, data science, and automation. Mastering Python can open up endless career opportunities and future-proof your skillset.
6. Getting Started with Python
The best way to learn Python is through hands-on experience. Start with online courses, experiment with small projects, and dive into coding challenges. As you progress, contribute to open-source projects, engage with Python communities, and stay updated with the latest trends. The key is consistency—practice daily, explore real-world applications, and never stop learning.
Final Thoughts
Python isn’t just a programming language—it’s a gateway to endless possibilities. Whether you want to build websites, analyze data, automate tasks, or dive into AI, Python is your key to the future. With its versatility, ease of learning, and strong community, Python empowers anyone to turn ideas into reality. Now’s the time to start your Python journey and be a part of the innovation shaping the world!
0 notes
Text
How BA LLB Programmes Are Adapting to the Rise of Cyber Law
The digital age has transformed the way we work, communicate, and do business. While this has brought many opportunities, it has also introduced new legal challenges. Cybercrime, data breaches, and digital fraud are increasing, making cyber law one of the most important areas in modern legal studies. Recognising this, universities offering a BA LLB degree are adapting their programmes to prepare students for the evolving world of cyber law.
Why Cyber Law Matters Today
With the rise of the internet, legal issues have shifted from traditional areas like property and contracts to online fraud, hacking, and digital privacy. Companies store sensitive customer data online, and governments rely on digital networks. When things go wrong—such as a major data leak or cyber attack—lawyers specialising in cyber law play a crucial role in ensuring justice.
How BA LLB Programmes Are Changing
To keep up with this growing demand, universities are updating their BA LLB degree curriculum in several ways.
Introduction of Cyber Law Subjects
Many law schools have introduced dedicated cyberlaw courses, teaching students about topics like internet regulation, digital evidence, data protection laws, and cybercrime investigations. Some universities even offer electives focusing on niche areas such as artificial intelligence (AI) and blockchain laws.
Practical Training in Cyber Law Cases
Legal education is no longer just about textbooks and lectures. Many institutions now provide hands-on experience in cyber law through moot courts, mock trials, and internships. Students get to work on real-world cybercrime cases, learning how to deal with digital evidence and online fraud cases.
Collaborations with Tech Experts
Since cyber law is closely linked to technology, law schools are collaborating with cybersecurity firms and IT experts. This helps students understand the technical side of digital crimes, from hacking techniques to forensic investigations. Some universities even offer joint programmes with computer science departments, bridging the gap between law and technology.
Focus on International Cyber Law
The internet has no borders, and cybercrimes often involve multiple countries. Many universities now include international cyber law in their curriculum, teaching students about cross-border legal challenges, extradition laws, and global cybersecurity regulations.
Career Opportunities in Cyber Law
With businesses, banks, and even governments heavily dependent on digital systems, the demand for cyber law professionals is on the rise. Graduates with a BA LLB degree and expertise in cyber law can work as:
Cyber Law Consultants – Advising companies on data protection and digital security.
Legal Advisors for Tech Firms – Ensuring that businesses comply with cyber laws and regulations.
Cybercrime Investigators – Working with law enforcement to track and prosecute online criminals.
Privacy and Data Protection Lawyers – Helping companies comply with laws like GDPR (General Data Protection Regulation).
Academics and Researchers – Studying and shaping cyber law policies for the future.
Final Thoughts
Cyber law is no longer a niche area—it’s becoming an essential part of legal education. As digital threats continue to grow, law schools are adapting their BA LLB degree programmes to ensure students are well-equipped to handle cybercrime, data protection, and online regulations. With practical training, collaborations with tech experts, and a global perspective, today’s law graduates are stepping into a future where the internet and the law go hand in hand.
0 notes
Text
Unlocking the Power of Blockchain in Accounting: A Guide for Future CAs

Blockchain technology is no longer limited to the realm of cryptocurrencies. Its transformative potential in accounting has been gaining traction as businesses and auditors recognize the value of transparency, security, and efficiency. For aspiring Chartered Accountants (CAs), understanding blockchain’s role in revolutionizing accounting practices is crucial. This article explores how blockchain is reshaping accounting and offers guidance for CA students to leverage this knowledge using resources like CA Entrance Exam Books, Scanner CA Intermediate Books, Scanner CA Foundation Books, and Scanner CA Final Books.
What is Blockchain Technology?
At its core, blockchain is a distributed ledger technology that records transactions in a secure, transparent, and immutable manner. Each transaction is stored in a block, linked to the previous block, creating a chain of records. Key features of blockchain include:
Transparency: All authorized parties have access to the same data, reducing discrepancies and fraud.
Security: Advanced cryptography ensures data integrity and protection against unauthorized alterations.
Efficiency: Eliminates intermediaries, reducing time and cost for transaction verification.
How Blockchain is Revolutionizing Accounting
The integration of blockchain into accounting practices is addressing long-standing challenges while creating new opportunities. Here are some key impacts:
Real-Time Auditing: Blockchain enables real-time access to financial records, reducing the time required for audits and increasing accuracy. Auditors can focus on anomalies and high-risk areas rather than routine checks.
Enhanced Transparency: Transactions recorded on a blockchain are immutable and traceable, ensuring transparency in financial reporting and compliance with regulations.
Fraud Prevention: The decentralized nature of blockchain makes it nearly impossible to manipulate data, minimizing the risk of fraud and errors.
Smart Contracts: Automated agreements that execute when predefined conditions are met can streamline processes such as lease agreements and vendor payments.
Opportunities for Aspiring CAs
The adoption of blockchain in accounting presents exciting opportunities for CA students to specialize in this innovative field. By acquiring blockchain expertise, you can:
Assist Businesses in Implementation: Guide clients on integrating blockchain into their accounting systems.
Conduct Blockchain Audits: Ensure the integrity and accuracy of blockchain-based financial records.
Advise on Compliance: Help organizations navigate regulatory frameworks related to blockchain transactions.
How to Prepare for a Blockchain-Driven Accounting Future
To excel in this evolving landscape, aspiring CAs must build a strong foundation in both traditional accounting and emerging technologies. Here’s how resources like CA Foundation Scanner, Scanner CA Intermediate Books, and Scanner CA Final Books can help:
CA Foundation Scanner:
Focus on understanding the basics of accounting principles and technologies.
Practice questions that develop analytical and problem-solving skills essential for blockchain applications.
Scanner CA Intermediate Books:
Dive deeper into topics such as auditing, financial management, and information systems.
Explore blockchain’s role in audit procedures and risk assessment through case studies.
Scanner CA Final Books:
Gain advanced insights into topics like international taxation, corporate laws, and forensic accounting.
Study the application of blockchain in global financial reporting and fraud detection.
Regular practice with these scanners ensures a thorough understanding of concepts and prepares you to tackle real-world challenges.
Practical Steps for CA Students
Learn the Basics of Blockchain: Start by understanding how blockchain works. Free online resources and introductory courses can be a great starting point.
Stay Updated: Follow industry news and research on blockchain applications in accounting to stay ahead of the curve.
Seek Internships: Intern with firms that are exploring blockchain solutions to gain hands-on experience.
Develop Tech Skills: Familiarize yourself with blockchain tools and platforms such as Ethereum, Hyperledger, and smart contract development.
Join Professional Communities: Engage with blockchain and accounting forums to network with experts and peers.
Challenges and Ethical Considerations
While blockchain offers immense potential, it is not without challenges. Issues such as high implementation costs, scalability, and regulatory uncertainty can pose hurdles. Additionally, ethical considerations like data privacy and security must be addressed responsibly.
Conclusion
Blockchain is set to redefine accounting by enhancing transparency, efficiency, and trust. For future CAs, mastering this technology is not just an option but a necessity. By leveraging study resources like CA Entrance Exam Books, Scanner CA Intermediate Books, Scanner CA Foundation Books, and Scanner CA Final Books, you can build a strong foundation and stay prepared for the blockchain-driven future of accounting. Embrace this innovation and position yourself as a forward-thinking CA ready to lead in the digital age.
0 notes
Text
Top 10 Reasons to Pursue B.Tech CSE with Cyber Security

In the digital age, where cyber threats are a constant concern, the field of cyber security has become one of the most sought-after career paths. Combining a solid foundation in computer science with specialized skills in cyber defense, a B.Tech CSE with Cyber Security program opens doors to exciting and lucrative opportunities.
Here are the top 10 reasons why you should consider pursuing this specialized program.
1. Exploding Demand for Cyber Security Experts
Cybercrime is projected to cost the world $10.5 trillion annually by 2025, creating an unprecedented demand for skilled cyber security professionals. A cyber security career guarantees job security as organizations prioritize digital safety.
According to NASSCOM, India alone will require over 1 million cyber security professionals in the coming years.
2. Lucrative Career Opportunities
A B.Tech CSE Cyber Security degree offers access to some of the highest-paying jobs in tech. Roles like Cyber Security Analyst, Ethical Hacker, and Security Architect can fetch starting salaries ranging from ₹6-10 lakh per annum, with opportunities for rapid growth.
3. Comprehensive Skill Development
Students in B.Tech CSE programs gain expertise in areas such as network security, ethical hacking, cryptography, and intrusion detection. These critical skills ensure you’re job-ready in a fast-evolving field.
You’ll learn tools like Wireshark, Metasploit, and Splunk, used by top cyber security professionals worldwide.
4. Diverse Career Pathways
A career in cyber security spans industries like IT, banking, healthcare, government, and e-commerce. Whether you aspire to work with tech giants, startups, or public institutions, opportunities abound.
5. Global Job Market Access
Cyber security is a universal concern, offering roles across the globe. A B.Tech CSE Cyber Security degree equips you with skills recognized internationally, making you a valuable asset in global tech hubs.
Certifications like CISSP and CEH further enhance your employability in international markets.
6. Protecting Critical Data and Systems
In a world driven by data, securing sensitive information is vital. As a cyber security expert, you’ll contribute to safeguarding critical assets, ensuring trust in digital ecosystems.
Example: Companies like Google and Amazon rely heavily on cyber security teams to protect user data and infrastructure.
7. Cutting-Edge Technology Exposure
A B.Tech CSE with Cyber Security introduces students to advanced technologies, including artificial intelligence (AI), machine learning (ML), and blockchain, all integrated with cyber defense.
8. Thriving in a Dynamic Industry
Cyber security evolves constantly to tackle emerging threats, making it an exciting and intellectually stimulating field. The challenges ensure continuous learning and skill enhancement.
AI-driven cyber security tools are reshaping the industry, creating new roles and opportunities.
9. Scholarships and Government Initiatives
Governments and educational institutions are increasingly supporting cyber security education through scholarships and funding programs. This makes a B.Tech CSE Cyber Security degree more accessible than ever.
10. Future-Proof Career
With cybercrime escalating and technology advancing, a career in cyber security is not just relevant but essential. This specialization guarantees long-term relevance and stability in the tech industry.
Skills You’ll Gain in B.Tech CSE Cyber Security
Mastering programming languages like Python and Java.
Understanding network protocols, firewalls, and intrusion detection systems.
Hands-on experience with cyber forensics and malware analysis.
Top Universities Offering B.Tech CSE Cyber Security in India
Indian Institute of Technology (IITs)
National Institute of Technology (NITs)
VIT University, Vellore
Amity University
Manipal Academy of Higher Education
Institute of Engineering and Management, Kolkata
MIT World Piece University, Pune
Look for programs offering internships or collaborations with leading tech companies like Cisco or IBM.
FAQs about B.Tech CSE with Cyber Security
Q1. What is the eligibility for a B.Tech CSE Cyber Security program? Most universities require candidates to have completed 10+2 with Physics, Chemistry, and Mathematics and qualify for entrance exams like JEE Main or institution-specific tests.
Q2. Is cyber security a good career choice? Absolutely! With high demand, excellent salaries, and diverse opportunities, a career in cyber security is both rewarding and future-proof.
Q3. What certifications complement this degree? Certifications like CISSP, CEH, and CompTIA Security+ significantly boost career prospects.
Conclusion:
A B.Tech CSE with Cyber Security isn’t just a degree—it’s a stepping stone to a fulfilling career in one of the most critical and dynamic domains of technology. With a blend of strong technical foundations, cutting-edge tools, and endless opportunities, this specialization ensures you’ll always be in demand.
0 notes
Text
Career Paths and Opportunities for Chartered Accountants Beyond Traditional Roles

Chartered Accountancy is often regarded as one of the most prestigious and challenging professions. Chartered accountants (CAs) have long been regarded as the foundation of auditing, taxation, and financial management. However, with the dynamic evolution of global markets and technological advancements, the role of CAs has expanded significantly. Today, Chartered Accountants can explore career paths that go far beyond traditional roles, opening up avenues for leadership, innovation, and entrepreneurial success.
At Vishwas CA Classes, we provide comprehensive guidance and preparation through CA Foundation classes, CA Inter classes, and advanced programs, helping aspirants achieve success and explore new horizons.
1. Strategic Financial Management and Consulting
Gone are the days when CAs were confined to tax filing and statutory audits. Modern organizations seek CAs for strategic financial management, mergers, acquisitions, and business restructuring. As financial consultants, CAs play a pivotal role in guiding businesses toward sustainable growth by analyzing risks, improving efficiency, and advising on critical financial decisions.
Skillset Required:
Advanced financial modeling
Risk analysis and management
Knowledge of global financial regulations
2. Technology and Digital Transformation
With digital disruption sweeping across industries, there is a growing demand for CAs to lead digital transformation initiatives. From blockchain in accounting to artificial intelligence in financial forecasting, CAs with tech-savvy skills are at the forefront of redefining financial processes.
Opportunities in Tech:
Implementing ERP systems
Data analytics and predictive modeling
Cybersecurity audits for financial systems
Our online CA courses in India integrate modules on emerging technologies, ensuring you stay ahead in the tech-driven financial landscape.
3. Forensic Accounting and Fraud Detection
Forensic accounting is a specialized field where CAs investigate financial discrepancies and fraud. As businesses face increasing scrutiny, organizations turn to CAs to ensure regulatory compliance and uncover financial malpractices.
Key Areas:
Litigation support
Corporate fraud investigation
Anti-money laundering compliance
By enrolling in our CA inter classes, you can gain insights into forensic accounting, helping you build a strong foundation in this niche domain.
4. Entrepreneurship and Start-up Advisory
India's start-up ecosystem is thriving, and CAs are uniquely positioned to provide strategic guidance to budding entrepreneurs. From funding strategies to compliance management, CAs can act as invaluable advisors to start-ups. Additionally, many CAs are venturing into entrepreneurship themselves, leveraging their financial expertise to establish successful businesses.
Advisory Roles:
Tax planning and legal structuring
Financial planning and resource allocation
Start-up fundraising
At Vishwas CA Classes, we emphasize real-world application through interactive learning in our CA coaching classes, preparing you for such dynamic roles.
5. Global Career Opportunities
With globalization, Indian CAs are in high demand internationally. Organizations worldwide recognize the rigorous training and expertise that come with the CA designation from India. Areas such as International Financial Reporting Standards (IFRS) and global taxation laws offer lucrative opportunities abroad.
High-Demand Roles Globally:
Transfer pricing specialist
International tax consultant
Financial controller in multinational corporations
By mastering the skills through our CA foundation classes and advanced programs, you can position yourself for a successful global career.
6. Education and Thought Leadership
For those passionate about teaching and mentoring, the field of education provides fulfilling opportunities. CAs can become educators, thought leaders, or influencers, contributing to the profession by shaping the next generation of accountants.
Career Paths in Education:
Faculty roles in reputed institutions
Authoring books on finance and accounting
Conducting workshops and seminars
Vishwas CA Classes is committed to fostering future educators by instilling a deep understanding of concepts and practical applications through our innovative teaching methodologies.

How Vishwas CA Classes Helps You Excel in a Dynamic CA Career
At Vishwas CA Classes, we aim to provide aspirants with the skills and confidence to go beyond traditional career paths. Whether you're preparing for the CA foundation, CA inter, or advanced stages, our tailored online CA courses in India offer:
Comprehensive Study Material: Designed to cover theoretical and practical aspects.
Experienced Faculty: Industry experts delivering in-depth insights.
Flexible Learning Options: Attend classes from anywhere with our CA coaching classes.
Real-world Application: Case studies and projects that mimic professional scenarios.
Conclusion
The role of Chartered Accountants is no longer confined to ledgers and balance sheets. Today’s CAs are dynamic professionals who lead organizations in strategy, technology, and innovation. By enrolling in the right programs and equipping yourself with emerging skills, you can unlock diverse opportunities across industries and geographies.
Start your journey with Vishwas CA Classes—a trusted name in CA education that empowers you to explore these dynamic career paths with confidence. Join our CA classes in India today and take the first step toward a future filled with possibilities!
Explore the best in CA education with Vishwas CA Classes. Visit Vishwas CA Classes for more information.
#CA foundation classes#CA inter classes#CA Classes In India#CA online classes#CA coaching classes#Online CA coaching classes#Best coaching for CA in India
0 notes
Text
Recover Scammed Crypto
Recovering scammed cryptocurrency is a challenging and complex process that requires a combination of technical expertise, legal assistance, and strategic actions. With the rise of digital currencies like Bitcoin, Ethereum, and many others, scams have become increasingly prevalent, targeting individuals and investors through various fraudulent schemes such as phishing attacks, fake ICOs, Ponzi schemes, and more.
Maybe this is the best recommendation for you, have a look here: Recover scammed crypto
The first and most crucial step is to act quickly once a scam is identified. Cryptocurrencies operate on decentralized blockchain networks, which means that transactions are usually irreversible and often anonymous. However, this does not mean that recovery is impossible. The key to recovering scammed crypto lies in tracing the stolen funds. Blockchain technology is transparent, allowing for detailed tracking of transactions. Specialized recovery firms have access to advanced tools that can analyze blockchain data to track the movement of funds, identify wallet addresses, and potentially trace the origin of the scam.
In some cases, the scammer may have transferred the funds through multiple wallets or exchanges, making it harder to follow the trail. However, recovery services with expertise in blockchain forensics can work with law enforcement agencies and exchanges to attempt to freeze or seize the stolen assets. If the scammer used a particular exchange to move the funds, the recovery service may liaise with the exchange’s compliance team to investigate and, if possible, block the withdrawal of the stolen funds.
Visit for more: Recover scammed crypto
Prevention is also key in the process of recovery. Even if victims are unable to recover their funds, learning from the experience is crucial to avoid future losses. After an incident, victims should strengthen their security practices by using secure wallets (such as hardware wallets), enabling two-factor authentication (2FA), and staying informed about the latest scams in the crypto world. Education is essential to recognizing warning signs, such as suspicious investment opportunities or unsolicited messages promising high returns.
While recovering scammed cryptocurrency is never a simple or guaranteed task, the combined efforts of blockchain forensics, legal assistance, and reporting to the authorities can increase the likelihood of success. Ultimately, victims of crypto scams must be vigilant, seek professional help, and take preventive measures to safeguard their assets and avoid falling victim to scams in the future.
1 note
·
View note
Text
Recovering Money from Crypto Fraud: A Legal Perspective

The rise of cryptocurrency has opened up exciting opportunities for investment and innovation. However, it has also given rise to an increase in crypto fraud. Scammers exploit the decentralized nature of cryptocurrencies to perpetrate various schemes, leaving victims desperate to recover their stolen assets. This article explores the legal avenues available for recovering funds from crypto fraud and highlights how expert assistance from FiordIntel can make a critical difference.
Understanding Crypto Fraud
Crypto fraud encompasses a variety of schemes, including:
Ponzi Schemes: Fraudsters promise high returns on investments without actual profits being generated.
Phishing Attacks: Victims are tricked into revealing private keys or login credentials.
Fake ICOs (Initial Coin Offerings): Scammers solicit funds for non-existent projects.
Hacked Wallets: Cybercriminals breach wallets to steal cryptocurrency.
Each of these scams leaves victims at a crossroads, often unsure of how to pursue recovery.
Legal Framework for Crypto Recovery
Recovering funds from crypto fraud is challenging but not impossible. The process typically involves a combination of legal, technical, and investigative approaches.
1. Reporting the Fraud
Victims should first report the fraud to local authorities or regulatory bodies. Agencies like the Financial Conduct Authority (FCA) in the UK or the Securities and Exchange Commission (SEC) in the US may provide initial guidance.
2. Blockchain Forensics
The immutable nature of blockchain can be an asset in tracing transactions. Advanced blockchain forensics tools can track the flow of stolen funds, often revealing the identity of the perpetrators.
3. Civil Litigation
Victims may pursue legal action against the perpetrators. Civil lawsuits can compel fraudsters to return stolen funds or pay damages.
4. Engaging Recovery Experts
Specialized firms like FiordIntel provide a comprehensive solution. Their services include blockchain forensics, cybercrime investigation, and legal assistance tailored to each case.
How FiordIntel Can Help
FiordIntel specializes in recovering assets lost to crypto scams. Here’s how they assist victims:
Advanced Blockchain Forensics
FiordIntel employs cutting-edge technology to trace transactions on the blockchain, uncovering the flow of stolen funds. Their experts can pinpoint wallet addresses linked to fraudsters, creating a roadmap for recovery.
Cybercrime Investigation
Their team of investigators collaborates with law enforcement and global financial institutions to uncover fraud networks. This approach enhances the likelihood of recovering assets.
Legal Support
FiordIntel works with legal professionals to initiate lawsuits or negotiate settlements. Their expertise ensures that victims’ claims are backed by solid evidence, increasing the chances of a favorable outcome.
Transparent Recovery Process
FiordIntel stands out for its transparency. Clients can track the progress of their case through a private dashboard, receiving regular updates and support throughout the recovery journey.
Steps to Recover Your Funds
If you’ve fallen victim to a crypto scam, follow these steps to maximize your chances of recovery:
Document Everything: Keep records of all communications, transactions, and other relevant information.
Report to Authorities: Notify law enforcement and regulatory bodies.
Secure Your Assets: Protect your remaining funds by securing your wallets and accounts.
Consult Experts: Reach out to firms like FiordIntel for personalized recovery assistance.
Preventing Future Crypto Fraud
Prevention is always better than cure. To avoid falling victim to crypto scams, follow these tips:
Verify Investment Opportunities: Research thoroughly before investing in any cryptocurrency project.
Enable Security Measures: Use two-factor authentication and secure your private keys.
Be Cautious of Promises: Avoid schemes that promise guaranteed returns or high profits with minimal risk.
Stay Informed: Regularly update yourself on the latest scams and security practices.
Conclusion
Recovering money from crypto fraud is a daunting task, but it’s not impossible. Leveraging legal frameworks, technological tools, and expert assistance can significantly improve the chances of success. Firms like FiordIntel provide invaluable support, helping victims reclaim their assets and regain financial stability. By taking preventive measures and knowing where to seek help, individuals can navigate the complex landscape of cryptocurrency with greater confidence.
1 note
·
View note
Text
#Solutions #NewReflections assets recovery plan ,step by step guide
[#DisneyVogueMagazine // A underdogs tale of rising back to the top, not caving in due to the pressure and what would be a true life filmstake of a women's true integrity in the face of evil, a hood Disney princess story]
Solutions to Address Financial Crimes and Operational Mismanagement
To restore the integrity, financial health, and mission effectiveness of the organization, a multi-pronged approach is required. Below are detailed solutions organized by focus areas:
Legal and Criminal Action
1.1 Report and Prosecute Offenders
Immediate Reporting: File reports with law enforcement agencies, including the FBI, SEC (for stock-related issues), and local authorities.
Legal Proceedings: Collaborate with legal counsel to prosecute individuals responsible for fraud, embezzlement, and money laundering.
Asset Recovery: Work with legal entities to seize and recover misappropriated funds and assets.
1.2 Engage External Oversight
Appoint a Special Prosecutor or external investigative team to independently assess legal risks and liabilities.
Financial Management and Recovery
2.1 Forensic Audits
Hire a forensic accounting firm to track and document every instance of fraud or misappropriation.
Use audit results to strengthen case evidence and guide corrective actions.
2.2 Emergency Fundraising
Launch a Crisis Recovery Campaign targeting loyal donors and foundations to bridge the financial gap.
Seek grants from organizations specializing in emergency aid for nonprofits.
2.3 Financial Restructuring
Reallocate budgets to prioritize immediate repairs, operational stability, and recovery measures.
Implement zero-based budgeting, reassessing every expense from scratch to prevent waste.
Governance Reforms
3.1 Leadership Overhaul
Replace key executives and managers implicated in wrongdoing with qualified professionals vetted for integrity.
Establish a Board Ethics Committee to oversee leadership decisions and policies.
3.2 Strengthen Policies and Controls
Introduce mandatory dual-approval processes for all transactions.
Enforce strict vendor vetting protocols to eliminate conflicts of interest.
Conduct quarterly independent audits for ongoing transparency.
Technology and Monitoring
4.1 Implement Fraud-Detection Tools
Deploy accounting software with built-in fraud detection and real-time reporting capabilities.
Use blockchain technology for immutable and transparent financial records.
4.2 Enhanced Surveillance
Install internal systems to monitor high-risk areas, such as procurement and payroll, for irregularities.
Create an anonymous whistleblower platform for employees to report misconduct.
Operational Solutions
5.1 Immediate Repairs and Maintenance
Use emergency funds to resolve urgent facility issues, such as broken appliances and unsafe electrical systems.
Contract reputable service providers for transparent and efficient repairs.
5.2 Staffing and Training
Retrain all employees on ethics, compliance, and financial literacy.
Establish a clear chain of accountability with defined roles and responsibilities for financial oversight.
Rebuilding Trust with Stakeholders
6.1 Transparent Communication
Share regular updates with donors, employees, and beneficiaries on progress, challenges, and milestones.
Publish an annual Impact and Accountability Report detailing corrective actions.
6.2 Rebrand and Recommit
Reframe the organization’s mission with a renewed focus on integrity and community impact.
Partner with credible organizations to co-host events and initiatives, showcasing commitment to reform.
Long-Term Sustainability Plan
7.1 Ethical Governance Framework
Develop a Code of Conduct and make it publicly accessible.
Establish a permanent Oversight Committee to ensure adherence to financial and operational best practices.
7.2 Financial Diversification
Expand revenue streams by exploring social enterprise opportunities, like selling crafts or services created by beneficiaries.
Partner with government programs and corporate sponsors for stable funding.
7.3 External Accreditation
Obtain certification from reputable nonprofit accreditation bodies, such as the Better Business Bureau (BBB) or Charity Navigator.
Timeline for Implementation
Expected Outcomes
Short-Term: Stabilization of finances, restoration of facility functionality, and initiation of legal proceedings.
Mid-Term: Restored stakeholder trust, improved operational efficiency, and enhanced financial controls.
Long-Term: A resilient organization with ethical leadership, sustainable funding, and a stronger community impact.
Would you like me to expand on any specific solution or help draft communication materials for stakeholders?
Data Analysis Plan for Financial Investigation
Objective
To analyze the provided data sets to identify patterns of fraud, embezzlement, or misuse of company assets associated with Jane Doe and John Doe.
Available Data Sets
Bank Account Information
Bank Account 1: Jane Doe
Bank Account 2: John Doe
Credit Card Statements
Credit Card Statement 1: Jane Doe
Credit Card Statement 2: John Doe
Other Financial Documents
Other Financial Document 1: Jane Doe
Other Financial Document 2: John Doe
Step-by-Step Data Analysis Process
Step 1: Collect and Organize Data
Goal: Centralize all documents for efficient analysis.
Consolidate all bank statements, credit card statements, and other financial documents into a secure database or spreadsheet.
Categorize expenses by type (e.g., payroll, vendor payments, personal expenses).
Step 2: Review Bank Account Transactions
Actions:
Identify large or unusual withdrawals and deposits.
Cross-reference transactions with the company's approved financial activities.
Highlight transactions lacking sufficient documentation or approval.
Step 3: Analyze Credit Card Statements
Actions:
Look for personal expenses charged to company credit cards (e.g., luxury goods, vacations).
Match credit card expenses with receipts or approval records.
Flag recurring charges to unknown vendors or service providers.
Step 4: Examine Other Financial Documents
Actions:
Review contracts or invoices for signs of inflated charges, shell companies, or fake vendors.
Cross-check payment records with deliverables.
Verify if all listed expenditures align with the organization's mission and budget.
Step 5: Cross-Referencing Individuals and Accounts
Actions:
Link suspicious transactions between Jane Doe’s and John Doe’s accounts.
Investigate if the individuals are connected to any external vendors or organizations benefiting from transactions.
Assess the possibility of collusion or coordinated fraud between the two individuals.
Step 6: Quantify the Losses
Actions:
Calculate the total amount of suspicious transactions for each individual.
Group losses by category (e.g., misused funds, unauthorized transactions).
Step 7: Prepare a Comprehensive Report
Summarize findings, including:
Patterns of misuse for each individual.
Estimated total financial loss.
Supporting evidence, including flagged transactions and discrepancies.
Key Questions for Deeper Investigation
Do Jane Doe and John Doe have any overlapping or repeated transactions between their accounts?
Are there any shared beneficiaries or vendors linked to both individuals?
Is there evidence of personal gain (e.g., luxury purchases or transfers to personal accounts)?
Have any funds been redirected to external accounts or entities outside the organization's scope?
Expected Outcomes
Identification of fraudulent or unauthorized activities.
A detailed financial trail connecting Jane Doe and John Doe to misused funds.
Actionable insights to recover assets and pursue legal action if warranted.
Would you like me to draft a specific set of questions for each account, or should I prepare a template for reporting findings?
Detailed Analysis Plan for Financial Transactions
Objective
To investigate suspicious transactions across the accounts and credit cards associated with Jane Doe and John Doe, using the partial data provided as a starting point.
Data Summary
Bank Accounts
Bank Account 1 (Jane Doe): 1234
Bank Account 2 (John Doe): 5678
Credit Card Statements
Credit Card 1 (Jane Doe): 9012
Credit Card 2 (John Doe): 3456
Step-by-Step Investigation
Step 1: Transaction Data Categorization
Organize transactions by:
Date: Analyze patterns over time (e.g., spikes in activity).
Amount: Flag transactions above a specific threshold (e.g., $5,000).
Merchant: Identify unusual vendors or personal expenses.
Reason for Transaction: Cross-reference justification with company policies.
Step 2: Red Flags in Bank Accounts
Bank Account 1 (1234):
Identify withdrawals or transfers inconsistent with organizational objectives.
Check for repeated small withdrawals (structuring to avoid detection).
Cross-reference deposits for possible kickbacks or outside income sources.
Bank Account 2 (5678):
Look for unexplained large transfers to personal or external accounts.
Investigate payments to unknown vendors or contractors.
Cross-check with company payroll or vendor records to ensure legitimacy.
Step 3: Credit Card Statement Review
Credit Card 1 (9012):
Match transactions with submitted receipts or reports.
Flag non-business-related expenses such as luxury goods, dining, or travel.
Credit Card 2 (3456):
Identify recurring subscriptions or payments to unknown entities.
Review transaction descriptions for vague or incomplete justifications.
Step 4: Transaction Cross-Referencing
Match suspicious transactions across accounts and credit cards.
Identify patterns of shared beneficiaries, repeated merchants, or similar transaction dates.
Determine if funds have been shifted between Jane Doe and John Doe’s accounts.
Sample Transaction Analysis Questions
Date: Was the transaction made during a time of high organizational spending or personal financial distress?
Merchant: Is the merchant related to the organization’s needs, or is it personal?
Amount: Is the amount consistent with typical spending patterns?
Reason: Was a reason provided, and does it align with company policy?
Approval: Was the transaction authorized by the appropriate personnel?
Immediate Next Steps
Expand the Data Set:
Collect all suspicious transactions over the past 3–5 years.
Include metadata such as IP addresses for online transactions.
Transaction Sampling:
Create a detailed spreadsheet of flagged transactions.
Highlight patterns such as recurring merchants, unusual amounts, or suspicious justifications.
Audit Assistance:
Engage an external forensic accounting team to validate findings.
Evidence Compilation:
Maintain a log of evidence for potential legal action, including transaction IDs and linked documents.
Deliverables
Comprehensive Report:
A detailed summary of findings, categorized by account and individual.
Legal and Recovery Plan:
Recommendations for asset recovery and legal steps to pursue damages.
Policy Review Suggestions:
Identify gaps in financial oversight that enabled misuse.
Would you like to proceed with a specific focus, such as a transaction timeline or detailed profile for Jane and John Doe?
Detailed Investigation Questions
Bank Account 1 (1234 - Jane Doe)
Large Deposits:
Who is the source of the large deposit(s) to Bank Account 1?
Are these deposits tied to legitimate business activities, or do they involve unverified entities?
Small Withdrawals:
Why did Jane Doe and John Doe make multiple small withdrawals for personal use?
Are these withdrawals structured to avoid detection (e.g., below reporting thresholds)?
What were the stated purposes of these withdrawals, and were receipts provided?
Transfers to Other Accounts:
Why were large amounts transferred from Bank Account 1 to other accounts?
What is the relationship between Jane Doe and the recipients of these transfers?
Are the recipient accounts associated with the company, personal entities, or third-party vendors?
Bank Account 2 (5678 - John Doe)
Foreign Currency Transactions:
Why did Jane Doe and John Doe make multiple transactions in foreign currencies?
Were these transactions related to international business operations or personal spending?
Are the foreign merchants and entities verified and legitimate?
High-Value Purchases:
Why did Jane Doe and John Doe make purchases of high-value items (e.g., luxury goods, electronics)?
Are these items accounted for in company inventory or documentation?
Do the purchase amounts match the company’s spending policies?
Inter-Account Transfers:
What is the purpose of transferring money between Jane and John Doe’s accounts?
Were these transfers documented as part of official company activities?
Is there evidence of circular transactions to obscure financial trails?
General Questions on Recipients and Beneficiaries
Funds Recipients:
Who are the individuals or entities that received the transferred money?
Are these individuals or organizations connected to the company in any way?
Do these recipients have a history of involvement in suspicious transactions?
Approval and Oversight:
Who approved or authorized these transactions, and were proper protocols followed?
Are there discrepancies between the approval documentation and the executed transactions?
Next Steps
Document Review: Collect supporting documentation for each flagged transaction, including invoices, receipts, and approval records.
Beneficiary Interviews: Identify and interview the recipients of funds to confirm the purpose of the transfers.
Pattern Analysis: Use financial software to map patterns in withdrawals, deposits, and transfers.
Legal Consultation: Collaborate with legal experts to determine the liability and necessary recovery actions.
Would you like to prioritize any specific questions or expand on particular areas for further investigation?
Detailed Investigation Questions
Bank Account 1 (1234 - Jane Doe)
Large Deposits:
Who is the source of the large deposit(s) to Bank Account 1?
Are these deposits tied to legitimate business activities, or do they involve unverified entities?
Small Withdrawals:
Why did Jane Doe and John Doe make multiple small withdrawals for personal use?
Are these withdrawals structured to avoid detection (e.g., below reporting thresholds)?
What were the stated purposes of these withdrawals, and were receipts provided?
Transfers to Other Accounts:
Why were large amounts transferred from Bank Account 1 to other accounts?
What is the relationship between Jane Doe and the recipients of these transfers?
Are the recipient accounts associated with the company, personal entities, or third-party vendors?
Bank Account 2 (5678 - John Doe)
Foreign Currency Transactions:
Why did Jane Doe and John Doe make multiple transactions in foreign currencies?
Were these transactions related to international business operations or personal spending?
Are the foreign merchants and entities verified and legitimate?
High-Value Purchases:
Why did Jane Doe and John Doe make purchases of high-value items (e.g., luxury goods, electronics)?
Are these items accounted for in company inventory or documentation?
Do the purchase amounts match the company’s spending policies?
Inter-Account Transfers:
What is the purpose of transferring money between Jane and John Doe’s accounts?
Were these transfers documented as part of official company activities?
Is there evidence of circular transactions to obscure financial trails?
General Questions on Recipients and Beneficiaries
Funds Recipients:
Who are the individuals or entities that received the transferred money?
Are these individuals or organizations connected to the company in any way?
Do these recipients have a history of involvement in suspicious transactions?
Approval and Oversight:
Who approved or authorized these transactions, and were proper protocols followed?
Are there discrepancies between the approval documentation and the executed transactions?
Next Steps
Document Review: Collect supporting documentation for each flagged transaction, including invoices, receipts, and approval records.
Beneficiary Interviews: Identify and interview the recipients of funds to confirm the purpose of the transfers.
Pattern Analysis: Use financial software to map patterns in withdrawals, deposits, and transfers.
Legal Consultation: Collaborate with legal experts to determine the liability and necessary recovery actions.
Would you like to prioritize any specific questions or expand on particular areas for further investigation?
0 notes
Text
Importance of Continuous Professional Education Post-CA

Becoming a Chartered Accountant (CA) is a significant achievement, but the journey doesn’t end there. The dynamic nature of the finance and accounting industry demands that professionals continuously update their knowledge and skills to stay relevant. Continuous Professional Education (CPE) is an essential aspect of a CA's career, enabling them to adapt to regulatory changes, technological advancements, and industry trends.
1. What is Continuous Professional Education (CPE)?
CPE refers to structured learning programs designed to enhance the knowledge and skills of professionals. For CAs, this involves attending workshops, webinars, and training sessions, or pursuing advanced certifications. CPE ensures that CAs remain competent and up-to-date with the latest developments in their field.
2. Why is CPE Important?
a) Keeping Up with Regulatory Changes
The regulatory environment in accounting and taxation is ever-evolving. From amendments in tax laws to updates in International Financial Reporting Standards (IFRS), staying informed is crucial. CPE programs help CAs understand these changes and apply them effectively in their practice.
b) Adapting to Technological Advancements
Technology has transformed the way businesses operate, and the accounting profession is no exception. Tools like cloud accounting, AI-driven analytics, and blockchain are becoming mainstream. Participating in CPE programs ensures that CAs are equipped to leverage these technologies for better efficiency and accuracy.
c) Enhancing Professional Skills
Beyond technical knowledge, CPE focuses on developing soft skills such as communication, leadership, and problem-solving. These skills are critical for career advancement, particularly for CAs aspiring to leadership roles.
d) Maintaining Professional Credibility
Clients and employers value professionals who stay informed and competent. By participating in CPE programs, CAs demonstrate their commitment to excellence, enhancing their credibility and reputation.
3. CPE and Exam Preparation Resources
For aspiring CAs, tools like CA Entrance Exam Books, Scanner CA Foundation Books, Scanner CA Intermediate Books, and Scanner CA Final Books are indispensable during their preparation phase. Similarly, for qualified CAs, CPE programs act as the next step in continuous learning, ensuring they remain relevant and effective in their roles.
4. Benefits of CPE
a) Improved Career Opportunities
Continuous learning opens up new career paths. Specialized certifications in areas like forensic accounting, international taxation, or financial planning can help CAs diversify their expertise and stand out in a competitive market.
b) Networking Opportunities
CPE programs often bring professionals together, creating opportunities to network and exchange ideas. These connections can lead to collaborations, mentorship, or new business opportunities.
c) Personal Growth
Learning new concepts and skills fosters personal growth and boosts confidence. CPE helps professionals approach challenges with a fresh perspective, making them more effective problem-solvers.
5. Popular CPE Programs for CAs
a) Workshops and Seminars
These programs focus on specific topics like GST, transfer pricing, or audit techniques. They are ideal for gaining in-depth knowledge in a short time.
b) Online Courses
Platforms like Coursera, edX, and ICAI’s e-learning portal offer flexible learning options. Topics range from advanced accounting to emerging technologies like blockchain.
c) Certifications
Certifications such as CPA (Certified Public Accountant), ACCA (Association of Chartered Certified Accountants), or CFA (Chartered Financial Analyst) add global recognition to a CA’s credentials.
d) Self-Study Programs
For self-paced learners, resources similar to CA Foundation Scanner, CA Intermediate Scanner, and CA Final Scanner can be used to deepen understanding of complex subjects.
6. Challenges in Pursuing CPE
a) Time Constraints
Balancing work and learning can be challenging, especially for practicing CAs. Prioritizing and scheduling time for CPE is essential.
b) Cost of Programs
Some CPE programs can be expensive. However, many organizations reimburse these costs as part of professional development initiatives.
c) Choosing Relevant Topics
With numerous options available, selecting programs that align with career goals and interests can be overwhelming. Identifying areas of improvement and industry demand can guide this decision.
7. How to Incorporate CPE into Your Career
a) Set Clear Goals
Identify your career aspirations and choose CPE programs that align with those goals.
b) Leverage Technology
Use online platforms and virtual webinars to learn at your own pace.
c) Track Progress
Maintain a log of completed CPE activities to track your learning journey and ensure compliance with mandatory requirements.
d) Stay Consistent
Make CPE a regular part of your professional life. Even short courses can accumulate into significant learning over time.
8. Conclusion
Continuous Professional Education is a cornerstone of success for Chartered Accountants. Just as resources like CA Entrance Exam Books, Scanner CA Foundation Books, CA Intermediate Scanner, and Scanner CA Final Books are vital during the exam phase, CPE is essential for professional growth post-qualification. By staying updated with industry trends, enhancing skills, and embracing lifelong learning, CAs can ensure their relevance and effectiveness in a rapidly changing professional landscape. Invest in CPE to not only advance your career but also contribute to the broader accounting and finance community.
0 notes
Text
Why Accountants Need CPE Credits: A Quick Guide

In a world where financial regulations, standards, and technology continually evolve, the need for accountants to maintain their knowledge and expertise is absolutely critical.
CPE credits are a foundational component of an accountant’s career, providing essential opportunities to stay compliant, competitive, and capable of offering top-tier service to clients. Let’s explore why CPE courses for accountants are vital, what benefits they offer, and how they keep professionals at the forefront of the industry.
Maintaining Licensure and Compliance
For Certified Public Accountants (CPAs) and many other accounting professionals, CPE credits are not just recommended — they’re required. State boards of accountancy, professional organizations, and licensing bodies mandate a certain number of CPE hours to ensure that accountants remain competent in their field. Requirements vary by state and licensing body, but the general expectation is for accountants to complete around 40 hours of CPE annually. Failing to meet these requirements can lead to fines, suspension of licenses, or even a total loss of licensure.
Ethics CPE Requirements: Many states require that a portion of CPE hours be dedicated to ethics courses. These courses help ensure accountants understand their ethical responsibilities and can navigate complex ethical dilemmas.
Regulatory Changes: With frequent changes in tax laws, reporting standards, and regulatory frameworks, CPE courses ensure that accountants are aware of the latest requirements, reducing the risk of compliance issues.
Enhancing Technical Skills
The accounting field is no stranger to technical complexity. With emerging topics such as blockchain accounting, cryptocurrency, international financial reporting standards (IFRS), and artificial intelligence (AI) in finance, accountants must be prepared to integrate these innovations.
Technological Advancements: With advancements in software, data analytics, and automation, accountants can leverage new tools to streamline work and provide deeper insights. CPE courses in technology prepare accountants to harness the power of modern software and ensure they can offer clients or employers the benefits of efficient, tech-enabled service.
Specialized Areas of Practice: As accountants may choose to specialize in niches such as forensic accounting, cybersecurity, or business valuation, CPE credits allow them to develop these skills and expand their career opportunities.
Boosting Client Confidence and Building Trust
Accountants are advisors, and clients place high value on their ability to provide up-to-date and accurate financial advice. Meeting CPE requirements and pursuing additional certifications signals to clients that an accountant is committed to their profession, compliance, and continued learning.
Enhanced Reputation and Trust: Earning and maintaining CPE credits builds trust with clients and colleagues by demonstrating an accountant’s commitment to staying informed on current laws and regulations.
Increased Client Retention: Clients often remain loyal to accountants who show a proactive approach to professional growth and learning. Knowledge gained from CPE courses allows accountants to offer relevant insights that benefit client businesses.
Preparing for Regulatory and Economic Changes
Economic conditions and regulatory landscapes are always evolving, often with significant implications for businesses and individuals. Accountants who engage in ongoing professional education are better prepared to anticipate and respond to these shifts, providing clients with timely and relevant guidance.
Adaptation to Tax Code Changes: For tax accountants, changes in tax codes are a constant challenge. Completing CPE courses specific to tax updates is crucial for providing accurate tax preparation and planning services.
Economic Impact Awareness: CPE courses can include topics on economic trends, preparing accountants to advise clients on how to respond to economic downturns, inflation, and other external forces affecting financial health.
The Critical Role of CPE Credits in Accounting
In a profession where accuracy, ethics, and expertise are paramount, CPE credits form the backbone of an accountant’s commitment to continuous improvement and client service. Meeting CPE requirements goes beyond compliance; it empowers accountants to stay informed about industry developments, expand their knowledge base, and offer unparalleled service in a rapidly changing landscape.
Whether it’s to keep up with new laws, enhance technical skills, or pursue career advancement, the pursuit of CPE credits through accounting CPE is essential for accountants at all levels. With the right CPE courses from reputable leaders like CPE Inc., accounting professionals not only stay relevant but also gain the expertise needed to adapt, grow, and succeed in an increasingly complex financial environment.
For more information about Online CPE For Cpas and CPE Course please visit:- CPE Inc.
0 notes
Text
Recovering Stolen Bitcoin: A Complete Guide to the Recovery Process

Cryptocurrency scams are on the rise, leaving victims searching for effective solutions to recover their stolen Bitcoin. With the right approach and resources, recovering your lost funds is possible. This comprehensive guide will walk you through the recovery process, offer actionable tips, and introduce a trusted agency, Fusion Forensics, that specializes in fund recovery.
Why Bitcoin Scams Are Increasing
The Popularity of Cryptocurrency
Bitcoin and other cryptocurrencies have surged in popularity, making them a prime target for scammers. The decentralized nature of these digital assets can make recovery challenging, but it’s not impossible with expert assistance.
Common Types of Bitcoin Scams
Here are some of the most prevalent scams to watch out for:
Phishing Attacks: Fake websites or emails trick users into sharing their private keys or wallet credentials.
Ponzi Schemes: Fraudulent investment opportunities promise high returns but collapse once they’ve amassed significant funds.
Impersonation Scams: Scammers pose as trusted figures or organizations to gain trust and steal funds.
Malware Attacks: Software that gains unauthorized access to wallets or exchanges.
The Bitcoin Recovery Process: Step-by-Step
1. Confirm the Theft
Before proceeding, verify that your Bitcoin has been stolen and not simply misplaced due to an error in accessing your wallet. Review your transaction history and wallet credentials carefully.
2. Gather Evidence
Collect as much information as possible about the theft. This includes:
Transaction IDs
Wallet addresses involved
Screenshots of suspicious emails or websites
Communication records with the scammer
3. File a Report
Report the theft to:
Local law enforcement: Provide detailed documentation to support your claim.
Regulatory bodies: Notify organizations like the SEC or FCA if the scam involves investment fraud.
The platform used for the transaction: Alert the exchange or wallet provider to freeze suspicious activity.
4. Engage a Recovery Expert
Given the complexities of cryptocurrency recovery, seeking professional help is often the best course of action. Fusion Forensics is a trusted agency specializing in recovering stolen funds. Their team of experts employs cutting-edge techniques and legal channels to track and recover stolen Bitcoin.
5. Implement Preventive Measures
After recovering your funds, prioritize securing your assets to prevent future incidents. Use hardware wallets, enable two-factor authentication (2FA), and stay updated on cybersecurity best practices.
How Fusion Forensics Can Help
Expertise in Cryptocurrency Recovery
Fusion Forensics specializes in helping victims recover Bitcoin lost to scams, unethical brokers, or fraudulent trading platforms. Their process includes:
Advanced blockchain analysis to trace transactions.
Negotiation with involved parties or platforms.
Legal action when necessary to recover funds.
Client-Centric Approach
Fusion Forensics prioritizes transparency and customer interests, ensuring that clients feel supported throughout the recovery process.
Proven Track Record
With a team of skilled professionals, Fusion Forensics has successfully recovered funds for numerous victims worldwide. Their results-driven approach makes them a reliable partner in navigating the challenges of cryptocurrency recovery.
Tips to Protect Yourself from Future Bitcoin Scams
1. Secure Your Wallet
Use hardware wallets for offline storage and enable multi-signature protection.
2. Be Skeptical of Investment Opportunities
Avoid schemes that promise guaranteed returns or require upfront fees.
3. Verify Authenticity
Always confirm the legitimacy of websites, emails, or platforms before sharing personal information.
4. Stay Informed
Keep up with the latest trends in cryptocurrency scams to recognize warning signs.
Final Thoughts
Recovering stolen Bitcoin can be a daunting task, but it’s achievable with the right strategy and expert help. Begin by gathering evidence, reporting the theft, and seeking professional recovery services. Trustworthy agencies like Fusion Forensics are dedicated to helping victims recover their hard-earned funds and regain control of their financial future.
Protect your digital assets by staying informed and implementing robust security measures. Together, we can outsmart scammers and build a safer cryptocurrency landscape.
1 note
·
View note